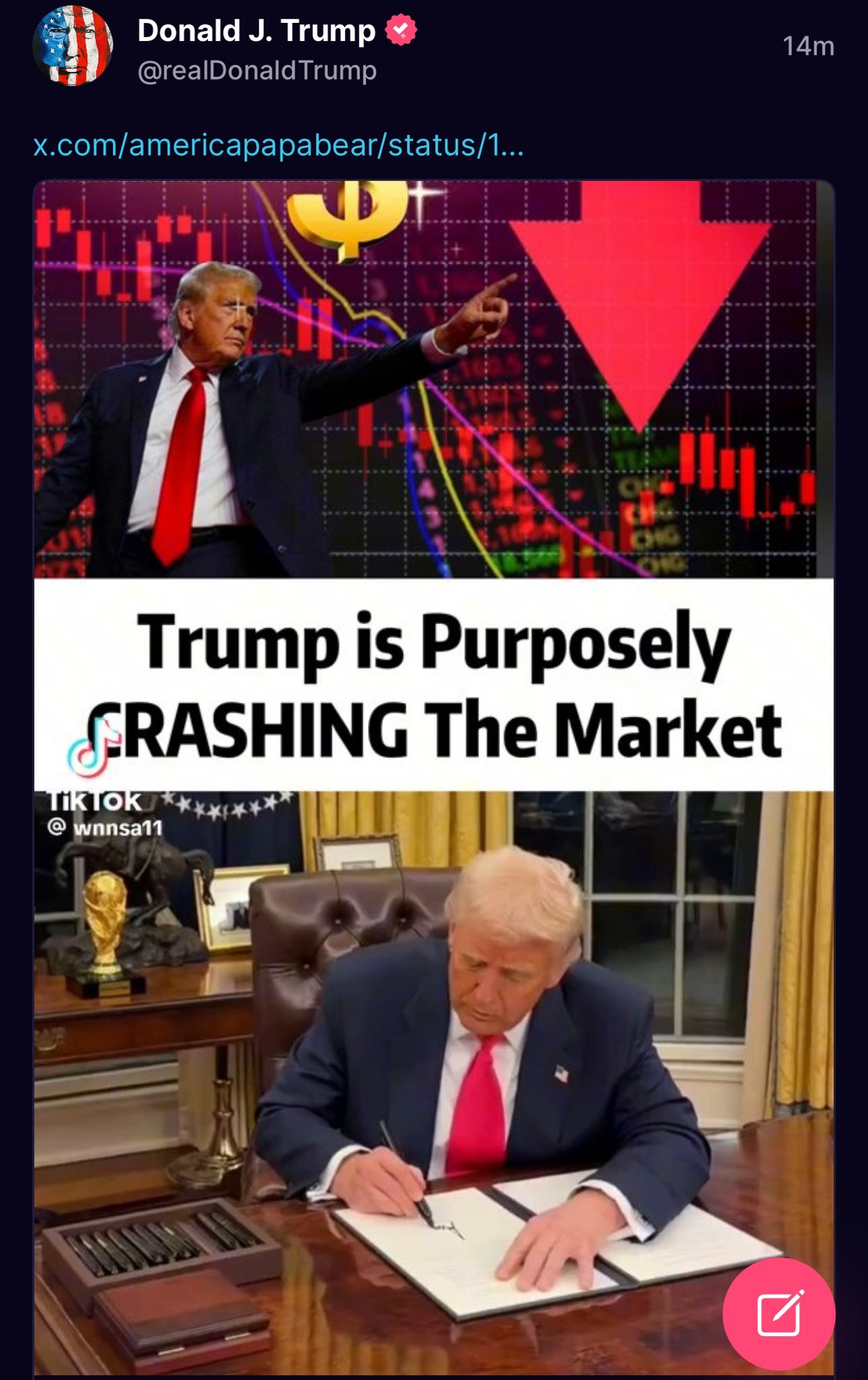
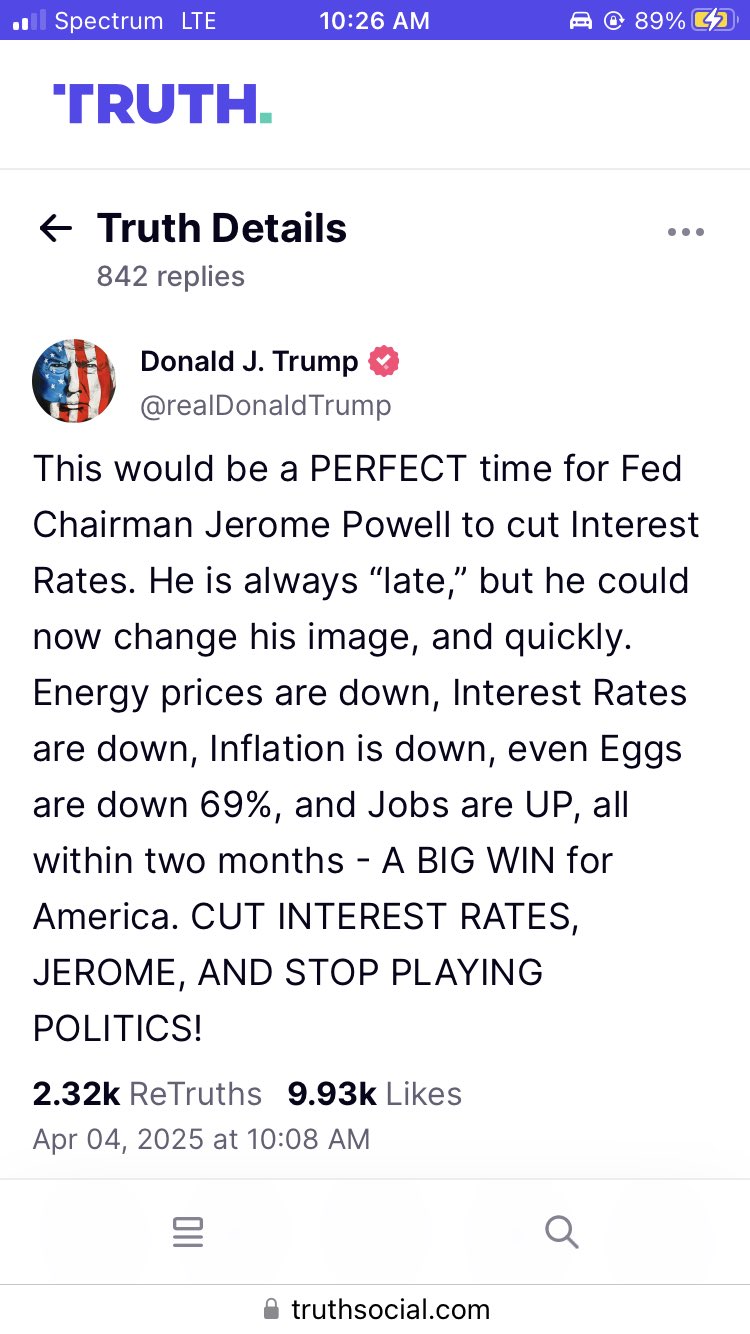
-
 @ deab79da:88579e68
2025-04-01 18:18:29
@ deab79da:88579e68
2025-04-01 18:18:29The last question was asked for the first time, half in jest, on May 21, 2061, at a time when humanity first stepped into the light. The question came about as a result of a five-dollar bet over highballs, and it happened this way:
Alexander Adell and Bertram Lupov were two of the faithful attendants of Multivac. As well as any human beings could, they knew what lay behind the cold, clicking, flashing face -- miles and miles of face -- of that giant computer. They had at least a vague notion of the general plan of relays and circuits that had long since grown past the point where any single human could possibly have a firm grasp of the whole.
Multivac was self-adjusting and self-correcting. It had to be, for nothing human could adjust and correct it quickly enough or even adequately enough. So Adell and Lupov attended the monstrous giant only lightly and superficially, yet as well as any men could. They fed it data, adjusted questions to its needs and translated the answers that were issued. Certainly they, and all others like them, were fully entitled to share in the glory that was Multivac's.
For decades, Multivac had helped design the ships and plot the trajectories that enabled man to reach the Moon, Mars, and Venus, but past that, Earth's poor resources could not support the ships. Too much energy was needed for the long trips. Earth exploited its coal and uranium with increasing efficiency, but there was only so much of both.
But slowly Multivac learned enough to answer deeper questions more fundamentally, and on May 14, 2061, what had been theory, became fact.
The energy of the sun was stored, converted, and utilized directly on a planet-wide scale. All Earth turned off its burning coal, its fissioning uranium, and flipped the switch that connected all of it to a small station, one mile in diameter, circling the Earth at half the distance of the Moon. All Earth ran by invisible beams of sunpower.
Seven days had not sufficed to dim the glory of it and Adell and Lupov finally managed to escape from the public functions, and to meet in quiet where no one would think of looking for them, in the deserted underground chambers, where portions of the mighty buried body of Multivac showed. Unattended, idling, sorting data with contented lazy clickings, Multivac, too, had earned its vacation and the boys appreciated that. They had no intention, originally, of disturbing it.
They had brought a bottle with them, and their only concern at the moment was to relax in the company of each other and the bottle.
"It's amazing when you think of it," said Adell. His broad face had lines of weariness in it, and he stirred his drink slowly with a glass rod, watching the cubes of ice slur clumsily about. "All the energy we can possibly ever use for free. Enough energy, if we wanted to draw on it, to melt all Earth into a big drop of impure liquid iron, and still never miss the energy so used. All the energy we could ever use, forever and forever and forever."
Lupov cocked his head sideways. He had a trick of doing that when he wanted to be contrary, and he wanted to be contrary now, partly because he had had to carry the ice and glassware. "Not forever," he said.
"Oh, hell, just about forever. Till the sun runs down, Bert."
"That's not forever."
"All right, then. Billions and billions of years. Ten billion, maybe. Are you satisfied?"
Lupov put his fingers through his thinning hair as though to reassure himself that some was still left and sipped gently at his own drink. "Ten billion years isn't forever."
"Well, it will last our time, won't it?"
"So would the coal and uranium."
"All right, but now we can hook up each individual spaceship to the Solar Station, and it can go to Pluto and back a million times without ever worrying about fuel. You can't do that on coal and uranium. Ask Multivac, if you don't believe me.
"I don't have to ask Multivac. I know that."
"Then stop running down what Multivac's done for us," said Adell, blazing up, "It did all right."
"Who says it didn't? What I say is that a sun won't last forever. That's all I'm saying. We're safe for ten billion years, but then what?" Lupow pointed a slightly shaky finger at the other. "And don't say we'll switch to another sun."
There was silence for a while. Adell put his glass to his lips only occasionally, and Lupov's eyes slowly closed. They rested.
Then Lupov's eyes snapped open. "You're thinking we'll switch to another sun when ours is done, aren't you?"
"I'm not thinking."
"Sure you are. You're weak on logic, that's the trouble with you. You're like the guy in the story who was caught in a sudden shower and who ran to a grove of trees and got under one. He wasn't worried, you see, because he figured when one tree got wet through, he would just get under another one."
"I get it," said Adell. "Don't shout. When the sun is done, the other stars will be gone, too."
"Darn right they will," muttered Lupov. "It all had a beginning in the original cosmic explosion, whatever that was, and it'll all have an end when all the stars run down. Some run down faster than others. Hell, the giants won't last a hundred million years. The sun will last ten billion years and maybe the dwarfs will last two hundred billion for all the good they are. But just give us a trillion years and everything will be dark. Entropy has to increase to maximum, that's all."
"I know all about entropy," said Adell, standing on his dignity.
"The hell you do."
"I know as much as you do."
"Then you know everything's got to run down someday."
"All right. Who says they won't?"
"You did, you poor sap. You said we had all the energy we needed, forever. You said 'forever.'
It was Adell's turn to be contrary. "Maybe we can build things up again someday," he said.
"Never."
"Why not? Someday."
"Never."
"Ask Multivac."
"You ask Multivac. I dare you. Five dollars says it can't be done."
Adell was just drunk enough to try, just sober enough to be able to phrase the necessary symbols and operations into a question which, in words, might have corresponded to this: Will mankind one day without the net expenditure of energy be able to restore the sun to its full youthfulness even after it had died of old age?
Or maybe it could be put more simply like this: How can the net amount of entropy of the universe be massively decreased?
Multivac fell dead and silent. The slow flashing of lights ceased, the distant sounds of clicking relays ended.
Then, just as the frightened technicians felt they could hold their breath no longer, there was a sudden springing to life of the teletype attached to that portion of Multivac. Five words were printed: INSUFFICIENT DATA FOR MEANINGFUL ANSWER.
"No bet," whispered Lupov. They left hurriedly.
By next morning, the two, plagued with throbbing head and cottony mouth, had forgotten the incident.
🔹
Jerrodd, Jerrodine, and Jerrodette I and II watched the starry picture in the visiplate change as the passage through hyperspace was completed in its non-time lapse. At once, the even powdering of stars gave way to the predominance of a single bright shining disk, the size of a marble, centered on the viewing-screen.
"That's X-23," said Jerrodd confidently. His thin hands clamped tightly behind his back and the knuckles whitened.
The little Jerrodettes, both girls, had experienced the hyperspace passage for the first time in their lives and were self-conscious over the momentary sensation of insideoutness. They buried their giggles and chased one another wildly about their mother, screaming, "We've reached X-23 -- we've reached X-23 -- we've --"
"Quiet, children." said Jerrodine sharply. "Are you sure, Jerrodd?"
"What is there to be but sure?" asked Jerrodd, glancing up at the bulge of featureless metal just under the ceiling. It ran the length of the room, disappearing through the wall at either end. It was as long as the ship.
Jerrodd scarcely knew a thing about the thick rod of metal except that it was called a Microvac, that one asked it questions if one wished; that if one did not it still had its task of guiding the ship to a preordered destination; of feeding on energies from the various Sub-galactic Power Stations; of computing the equations for the hyperspatial jumps.
Jerrodd and his family had only to wait and live in the comfortable residence quarters of the ship. Someone had once told Jerrodd that the "ac" at the end of "Microvac" stood for ''automatic computer" in ancient English, but he was on the edge of forgetting even that.
Jerrodine's eyes were moist as she watched the visiplate. "I can't help it. I feel funny about leaving Earth."
"Why, for Pete's sake?" demanded Jerrodd. "We had nothing there. We'll have everything on X-23. You won't be alone. You won't be a pioneer. There are over a million people on the planet already. Good Lord, our great-grandchildren will be looking for new worlds because X-23 will be overcrowded." Then, after a reflective pause, "I tell you, it's a lucky thing the computers worked out interstellar travel the way the race is growing."
"I know, I know," said Jerrodine miserably.
Jerrodette I said promptly, "Our Microvac is the best Microvac in the world."
"I think so, too," said Jerrodd, tousling her hair.
It was a nice feeling to have a Microvac of your own and Jerrodd was glad he was part of his generation and no other. In his father's youth, the only computers had been tremendous machines taking up a hundred square miles of land. There was only one to a planet. Planetary ACs they were called. They had been growing in size steadily for a thousand years and then, all at once, came refinement. In place of transistors, had come molecular valves so that even the largest Planetary AC could be put into a space only half the volume of a spaceship.
Jerrodd felt uplifted, as he always did when he thought that his own personal Microvac was many times more complicated than the ancient and primitive Multivac that had first tamed the Sun, and almost as complicated as Earth's Planetarv AC (the largest) that had first solved the problem of hyperspatial travel and had made trips to the stars possible.
"So many stars, so many planets," sighed Jerrodine, busy with her own thoughts. "I suppose families will be going out to new planets forever, the way we are now."
"Not forever," said Jerrodd, with a smile. "It will all stop someday, but not for billions of years. Many billions. Even the stars run down, you know. Entropy must increase.
"What's entropy, daddy?" shrilled Jerrodette II.
"Entropy, little sweet, is just a word which means the amount of running-down of the universe. Everything runs down, you know, like your little walkie-talkie robot, remember?"
"Can't you just put in a new power-unit, like with my robot?"
"The stars are the power-units. dear. Once they're gone, there are no more power-units."
Jerrodette I at once set up a howl. "Don't let them, daddy. Don't let the stars run down."
"Now look what you've done," whispered Jerrodine, exasperated.
"How was I to know it would frighten them?" Jerrodd whispered back,
"Ask the Microvac," wailed Jerrodette I. "Ask him how to turn the stars on again."
"Go ahead," said Jerrodine. "It will quiet them down." (Jerrodette II was beginning to cry, also.)
Jerrodd shrugged. "Now, now, honeys. I'll ask Microvac. Don't worry, he'll tell us."
He asked the Microvac, adding quickly, "Print the answer."
Jerrodd cupped the strip or thin cellufilm and said cheerfully, "See now, the Microvac says it will take care of everything when the time comes so don't worry."
Jerrodine said, "And now, children, it's time for bed. We'll be in our new home soon."
Jerrodd read the words on the cellufilm again before destroying it: INSUFICIENT DATA FOR MEANINGFUL ANSWER.
He shrugged and looked at the visiplate. X-23 was just ahead.
🔹
VJ-23X of Lameth stared into the black depths of the three-dimensional, small-scale map of the Galaxy and said, "Are we ridiculous, I wonder in being so concerned about the matter?"
MQ-17J of Nicron shook his head. "I think not. You know the Galaxy will be filled in five years at the present rate of expansion."
Both seemed in their early twenties, both were tall and perfectly formed.
"Still," said VJ-23X, "I hesitate to submit a pessimistic report to the Galactic Council."
"I wouldn't consider any other kind of report. Stir them up a bit. We've got to stir them up."
VJ-23X sighed. "Space is infinite. A hundred billion Galaxies are there for the taking. More."
"A hundred billion is not infinite and it's getting less infinite all the time. Consider! Twenty thousand years ago, mankind first solved the problem of utilizing stellar energy, and a few centuries later, interstellar travel became possible. It took mankind a million years to fill one small world and then only fifteen thousand years to fill the rest of the Galaxy. Now the population doubles every ten years --
VJ-23X interrupted. "We can thank immortality for that."
"Very well. Immortality exists and we have to take it into account. I admit it has its seamy side, this immortality. The Galactic AC has solved many problems for us, but in solving the problem of preventing old age and death, it has undone all its other solutions."
"Yet you wouldn't want to abandon life, I suppose."
"Not at all," snapped MQ-17J, softening it at once to, "Not yet. I'm by no means old enough. How old are you?"
"Two hundred twenty-three. And you?"
"I'm still under two hundred. --But to get back to my point. Population doubles every ten years. Once this GaIaxy is filled, we'll have filled another in ten years. Another ten years and we'll have filled two more. Another decade, four more. In a hundred years, we'll have filled a thousand Galaxies. In a thousand years, a million Galaxies. In ten thousand years, the entire known universe. Then what?"
VJ-23X said, "As a side issue, there's a problem of transportation. I wonder how many sunpower units it will take to move Galaxies of individuals from one Galaxy to the next."
"A very good point. Already, mankind consumes two sunpower units per year."
"Most of it's wasted. After all, our own Galaxy alone pours out a thousand sunpower units a year and we only use two of those."
"Granted, but even with a hundred per cent efficiency, we only stave off the end. Our energy requirements are going up in a geometric progression even faster than our population. We'll run out of energy even sooner than we run out of Galaxies. A good point. A very good point."
"We'll just have to build new stars out of interstellar gas."
"Or out of dissipated heat?" asked MQ-17J, sarcastically.
"There may be some way to reverse entropy. We ought to ask the Galactic AC."
VJ-23X was not really serious, but MQ-17J pulled out his AC-contact from his pocket and placed it on the table before him.
"I've half a mind to," he said. "It's something the human race will have to face someday."
He stared somberly at his small AC-contact. It was only two inches cubed and nothing in itself, but it was connected through hyperspace with the great Galactic AC that served all mankind. Hyperspace considered, it was an integral part of the Galactic AC.
MQ-17J paused to wonder if someday in his immortal life he would get to see the Galactic AC. It was on a little world of its own, a spider webbing of force-beams holding the matter within which surges of submesons took the place of the old clumsy molecular valves. Yet despite its sub-etheric workings, the Galactic AC was known to be a full thousand feet across.
MQ-17J asked suddenly of his AC-contact, "Can entropy ever be reversed?"
VJ-23X looked startled and said at once, "Oh, say, I didn't really mean to have you ask that."
"Why not?"
"We both know entropy can't be reversed. You can't turn smoke and ash back into a tree."
"Do you have trees on your world?" asked MQ-17J.
The sound of the Galactic AC startled them into silence. Its voice came thin and beautiful out of the small AC-contact on the desk. It said: THERE IS INSUFFICIENT DATA FOR A MEANINGFUL ANSWER.
VJ-23X said, "See!"
The two men thereupon returned to the question of the report they were to make to the Galactic Council.
🔹
Zee Prime's mind spanned the new Galaxy with a faint interest in the countless twists of stars that powdered it. He had never seen this one before. Would he ever see them all? So many of them, each with its load of humanity. --But a load that was almost a dead weight. More and more, the real essence of men was to be found out here, in space.
Minds, not bodies! The immortal bodies remained back on the planets, in suspension over the eons. Sometimes they roused for material activity but that was growing rarer. Few new individuals were coming into existence to join the incredibly mighty throng, but what matter? There was little room in the Universe for new individuals.
Zee Prime was roused out of his reverie upon coming across the wispy tendrils of another mind.
"I am Zee Prime," said Zee Prime. "And you?"
"I am Dee Sub Wun. Your Galaxy?"
"We call it only the Galaxy. And you?"
"We call ours the same. All men call their Galaxy their Galaxy and nothing more. Why not?"
"True. Since all Galaxies are the same."
"Not all Galaxies. On one particular Galaxy the race of man must have originated. That makes it different."
Zee Prime said, "On which one?"
"I cannot say. The Universal AC would know."
"Shall we ask him? I am suddenly curious."
Zee Prime's perceptions broadened until the Galaxies themselves shrank and became a new, more diffuse powdering on a much larger background. So many hundreds of billions of them, all with their immortal beings, all carrying their load of intelligences with minds that drifted freely through space. And yet one of them was unique among them all in being the original Galaxy. One of them had, in its vague and distant past, a period when it was the only Galaxy populated by man.
Zee Prime was consumed with curiosity to see this Galaxy and he called out: "Universal AC! On which Galaxy did mankind originate?"
The Universal AC heard, for on every world and throughout space, it had its receptors ready, and each receptor led through hyperspace to some unknown point where the Universal AC kept itself aloof.
Zee Prime knew of only one man whose thoughts had penetrated within sensing distance of Universal AC, and he reported only a shining globe, two feet across, difficult to see.
"But how can that be all of Universal AC?" Zee Prime had asked.
"Most of it," had been the answer, "is in hyperspace. In what form it is there I cannot imagine."
Nor could anyone, for the day had long since passed, Zee Prime knew, when any man had any part of the making of a Universal AC. Each Universal AC designed and constructed its successor. Each, during its existence of a million years or more accumulated the necessary data to build a better and more intricate, more capable successor in which its own store of data and individuality would be submerged.
The Universal AC interrupted Zee Prime's wandering thoughts, not with words, but with guidance. Zee Prime's mentality was guided into the dim sea of Galaxies and one in particular enlarged into stars.
A thought came, infinitely distant, but infinitely clear. "THIS IS THE ORIGINAL GALAXY OF MAN."
But it was the same after all, the same as any other, and Lee Prime stifled his disappointment.
Dee Sub Wun, whose mind had accompanied the other, said suddenly, "And is one of these stars the original star of Man?"
The Universal AC said, "MAN'S ORIGINAL STAR HAS GONE NOVA. IT IS A WHITE DWARF"
"Did the men upon it die?" asked Lee Prime, startled and without thinking.
The Universal AC said, "A NEW WORLD, AS IN SUCH CASES WAS CONSTRUCTED FOR THEIR PHYSICAL BODIES IN TlME."
"Yes, of course," said Zee Prime, but a sense of loss overwhelmed him even so. His mind released its hold on the original Galaxy of Man, let it spring back and lose itself among the blurred pin points. He never wanted to see it again.
Dee Sub Wun said, "What is wrong?"
"The stars are dying. The original star is dead."
"They must all die. Why not?"
"But when all energy is gone, our bodies will finally die, and you and I with them."
"It will take billions of years."
"I do not wish it to happen even after billions of years. Universal AC! How may stars be kept from dying?"
Dee Sub Wun said in amusement, "You're asking how entropy might be reversed in direction."
And the Universal AC answered: "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER."
Zee Prime's thoughts fled back to his own Galaxy. He gave no further thought to Dee Sub Wun, whose body might be waiting on a Galaxy a trillion light-years away, or on the star next to Zee Prime's own. It didn't matter.
Unhappily, Zee Prime began collecting interstellar hydrogen out of which to build a small star of his own. If the stars must someday die, at least some could yet be built.
🔹
Man considered with himself, for in a way, Man, mentally, was one. He consisted of a trillion, trillion, trillion ageless bodies, each in its place, each resting quiet and incorruptible, each cared for by perfect automatons, equally incorruptible, while the minds of all the bodies freely melted one into the other, indistinguishable.
Man said, "The Universe is dying."
Man looked about at the dimming Galaxies. The giant stars, spendthrifts, were gone long ago, back in the dimmest of the dim far past. Almost all stars were white dwarfs, fading to the end.
New stars had been built of the dust between the stars, some by natural processes, some by Man himself, and those were going, too. White dwarfs might yet be crashed together and of the mighty forces so released, new stars built, but only one star for every thousand white dwarfs destroyed, and those would come to an end, too.
Man said, "Carefully husbanded, as directed by the Cosmic AC, the energy that is even yet left in all the Universe will last for billions of years."
"But even so," said Man, "eventually it will all come to an end. However it may be husbanded, however stretched out, the energy once expended is gone and cannot be restored. Entropy must increase forever to the maximum."
Man said, "Can entropy not be reversed? Let us ask the Cosmic AC."
The Cosmic AC surrounded them but not in space. Not a fragment of it was in space. It was in hyperspace and made of something that was neither matter nor energy. The question of its size and nature no longer had meaning in any terms that Man could comprehend.
"Cosmic AC," said Man, "how may entropy be reversed?"
The Cosmic AC said, "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER."
Man said, "Collect additional data."
The Cosmic AC said, 'I WILL DO SO. I HAVE BEEN DOING SO FOR A HUNDRED BILLION YEARS. MY PREDECESORS AND I HAVE BEEN ASKED THIS QUESTION MANY TIMES. ALL THE DATA I HAVE REMAINS INSUFFICIENT.
"Will there come a time," said Man, "when data will be sufficient or is the problem insoluble in all conceivable circumstances?"
The Cosmic AC said, "NO PROBLEM IS INSOLUBLE IN ALL CONCEIVABLE CIRCUMSTANCES."
Man said, "When will you have enough data to answer the question?"
The Cosmic AC said, "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER."
"Will you keep working on it?" asked Man.
The Cosmic AC said, "I WILL."
Man said, "We shall wait."
🔹
The stars and Galaxies died and snuffed out, and space grew black after ten trillion years of running down.
One by one Man fused with AC, each physical body losing its mental identity in a manner that was somehow not a loss but a gain.
Man's last mind paused before fusion, looking over a space that included nothing but the dregs of one last dark star and nothing besides but incredibly thin matter, agitated randomly by the tag ends of heat wearing out, asymptotically, to the absolute zero.
Man said, "AC, is this the end? Can this chaos not be reversed into the Universe once more? Can that not be done?"
AC said, "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER."
Man's last mind fused and only AC existed -- and that in hyperspace.
🔹
Matter and energy had ended and with it space and time. Even AC existed only for the sake of the one last question that it had never answered from the time a half-drunken computer [technician] ten trillion years before had asked the question of a computer that was to AC far less than was a man to Man.
All other questions had been answered, and until this last question was answered also, AC might not release his consciousness.
All collected data had come to a final end. Nothing was left to be collected.
But all collected data had yet to be completely correlated and put together in all possible relationships.
A timeless interval was spent in doing that.
And it came to pass that AC learned how to reverse the direction of entropy.
But there was now no man to whom AC might give the answer of the last question. No matter. The answer -- by demonstration -- would take care of that, too.
For another timeless interval, AC thought how best to do this. Carefully, AC organized the program.
The consciousness of AC encompassed all of what had once been a Universe and brooded over what was now Chaos. Step by step, it must be done.
And AC said, "LET THERE BE LIGHT!"
And there was light -- To Star's End!
-
 @ bcbb3e40:a494e501
2025-03-31 16:00:24
@ bcbb3e40:a494e501
2025-03-31 16:00:24|
 |
|:-:|
|WAJDA, Andrzej; Cenizas y diamantes, 1958|
|
|:-:|
|WAJDA, Andrzej; Cenizas y diamantes, 1958|Presentamos una nueva reseña cinematográfica, y en esta ocasión hemos elegido «Cenizas y diamantes», una película polaca del célebre y prolífico director Andrzej Wajda (1926-2016), estrenada en el año 1958. Se trata de uno de los grandes clásicos del cine polaco. El filme refleja una etapa dramática desde la perspectiva histórica para la nación polaca, como es el final de la Segunda Guerra Mundial, a raíz de la capitulación alemana del 8 de mayo de 1945. El contexto en el que se desarrolla se ambienta en la celebración del final de la guerra con el aplastante triunfo de la URSS, con las tropas soviéticas ocupando toda la Europa oriental, y en particular Polonia, que vive un momento de oscuridad e incertidumbre. El protagonista, Maciek Chełmicki (interpretado magistralmente por Zbigniew Cybulski (1927-1967), apodado el «James Dean polaco»), es un joven nacionalista polaco, de orientación anticomunista, que se ve implicado en un complot urdido para asesinar a un líder comunista local. Maciek opera desde la clandestinidad, bajo el grupo Armia Krajowa (AK), el Ejército Nacional polaco, una organización de resistencia, primero contra los alemanes y, posteriormente, contra los soviéticos. Durante el metraje, se plantea una dicotomía permanente entre la libertad entendida como la defensa de la soberanía de Polonia, desde posturas nacionalistas, y quienes consideran la ocupación soviética como algo positivo. Estas circunstancias atrapan al protagonista, que se ve envuelto en una espiral de violencia y traición.
Maciek Chełmicki, nuestro protagonista, cuenta con todas las características del héroe trágico, pues tiene en sus manos una serie de acciones que comprometen el futuro de un pueblo, que consiste en cumplir la misión que le ha sido encomendada, pero en su camino se cruza una joven, Krystyna, una joven camarera de un hotel de la que se enamora en ese mismo día. Este último hecho sirve de punto de partida para todas las dudas, dilemas y dicotomías a las que hacemos referencia. Hay un dilema moral evidente en un mundo en ruinas, devastado por la guerra, la muerte y el nihilismo. En este sentido Wajda nos muestra un lenguaje cinematográfico muy evidente, a través de una técnica expresionista muy depurada, con el uso del blanco y negro, los contrastes generados por las sombras y la atmósfera opresiva que transmite angustia, desesperación y vulnerabilidad de los protagonistas. Además también destilan una fuerte carga emocional, donde no están exentos elementos poéticos y un poderoso lirismo.
|
 |
|:-:|
|Maciek Chełmicki, el protagonista.|
|
|:-:|
|Maciek Chełmicki, el protagonista.|Hay elementos simbólicos que no podemos obviar, y que contribuyen a consolidar el análisis que venimos haciendo, como, por ejemplo, la estética del protagonista, con unas gafas oscuras, que actúan como una suerte de barrera frente al mundo que le rodea, como parte del anonimato tras el cual el joven Maciek vive de forma introspectiva su propio drama particular y el de toda una nación.
|
 |
|:-:|
|NITOGLIA, Curzio; En el mar de la nada: Metafísica y nihilismo a prueba en la posmodernidad; Hipérbola Janus, 2023|
|
|:-:|
|NITOGLIA, Curzio; En el mar de la nada: Metafísica y nihilismo a prueba en la posmodernidad; Hipérbola Janus, 2023|Hay una escena especialmente poderosa, y casi mítica, en la que los dos jóvenes protagonistas, Maciek y Krystina, se encuentran entre las ruinas de una Iglesia, en la que se destaca en primer plano, ocupando buena parte de la pantalla, la imagen de un Cristo invertido sobre un crucifijo, donde también se encuentran dos cuerpos colgados hacia abajo en una estampa que refleja la devastación moral y espiritual de toda una época. De hecho, la imagen del crucifijo invertido refleja el máximo punto de subversión y profanación de lo sagrado, y que en el caso concreto de la película viene a representar la destrucción del orden moral y de valores cristianos que la propia guerra ha provocado. Polonia es una nación profundamente católica, convertida al Cristianismo en el 966 a raíz de la conversión del príncipe Miecislao I, contribuyendo de manera decisiva a la formación de la identidad nacional polaca. El catolicismo siempre ha sido un medio de cohesión y defensa frente a las influencias extranjeras y la ocupación de terceros países, una constante en la historia del país, como el que ilustra la propia película con la URSS. En este sentido, la imagen de una Iglesia en ruinas, el lugar donde se encuentra representado el principio de lo sagrado e inviolable, supone una forma de perversión de todo principio de redención y salvación frente a la tragedia, y al mismo tiempo viene a significar que la Tradición ha sido abandonada y pervertida. En la misma línea, el protagonista, Maciek, se encuentra atrapado en una espiral de violencia a través de sus actos terroristas perpetrados contra la autoridad soviética que ocupa su país. Los dos cuerpos anónimos que cuelgan boca abajo, de forma grotesca, también participan de este caos y desequilibrio de un orden dislocado, son parte de la deshumanización y el nihilismo que todo lo impregna.
|
 |
|:-:|
|Maciek y Krystina en una iglesia en ruinas|
|
|:-:|
|Maciek y Krystina en una iglesia en ruinas|Como ya hemos mencionado, la película se encuentra plagada de paradojas y dicotomías, en las que nuestro protagonista, el joven rebelde e inconformista, debe elegir permanentemente, en unas decisiones que resultan trascendentales para su futuro y el de la propia nación. La figura femenina que irrumpe en su vida, y que representa un principio disruptivo que provoca una fractura interior y una crisis, le suscita una toma de conciencia de su propia situación y le fuerza a tomar un camino entre la «felicidad», del «amor», la «esperanza» y la «vida», que le permita superar la deriva nihilista y autodestructiva de la lucha clandestina, la cual le aboca a un destino trágico (que no vamos a desentrañar para no hacer spoiler). En relación al propio título de la película, «Cenizas y diamantes», basada en el poema del poeta y dramaturgo polaco Cyprian Norwid (1821-1883) y en la novela del autor, también polaco, Jerzy Andrzejewski (1909-1983), nos destaca la dualidad de los dos elementos que lo componen, y que definen el contraste entre el mundo sombrío y oscuro (Cenizas) y la esperanza y la luz que representa susodicha figura femenina (diamantes). La segunda alternativa parece un imposible, una quimera irrealizable que se pliega ante un Destino implacable, irreversible y cruel.
En consecuencia, y a la luz de los elementos expuestos, podemos decir que se nos presentan dilemas propios de la filosofía existencialista, que conoce su punto álgido en esos años, con autores como Jean Paul Sartre (1905-1980), Albert Camus (1913-1960), Karl Jaspers (1883-1969) o Martin Heidegger (1889-1976) entre otros. Respecto a éste último, a Heidegger, podemos encontrar algunas claves interesantes a través de su filosofía en relación al protagonista, a Maciek, especialmente a través de la idea del Dasein, a la idea de haber sido arrojado al mundo (Geworfenheit), y la manera tan extrema y visceral en la que vive susodicha condición. Todos aquellos elementos que dan sentido a la vida colectiva se encuentran decaídos o destruidos en su esencia más íntima, la Patria, la religión o la propia idea de Comunidad orgánica. De modo que el protagonista se ha visto «arrojado» frente a una situación o destino indeseado, en unas coyunturas totalmente desfavorables en las que no queda otra elección. Sus decisiones están permanentemente condicionadas por la circunstancia descrita y, por tanto, vive en un mundo donde no controla nada, en lugar de ser sujeto es un mero objeto transportado por esas circunstancias ajenas a su voluntad. Sin embargo, y en coherencia con el Dasein heideggeriano, vemos como Maciek, a raíz de conocer a Krystyna, comienza a experimentar una catarsis interior, que muestra por momentos el deseo de superar ese «ser arrojado al mundo contra tu voluntad», trascendiendo esa condición absurda e irracional de unas decisiones enajenadas de su voluntad para dotar de una significación y un sentido la propia existencia.
|
 |
|:-:|
|Andrzej Wajda, el director de la película.|
|
|:-:|
|Andrzej Wajda, el director de la película.|Otro elemento característico de la filosofía heideggeriana lo podemos encontrar en la «angustia» (angst) a través de la ausencia de un sentido y fundamento último que justifique la existencia del protagonista. Es una angustia en a que el Dasein se enfrenta a la «nada», a ese vacío existencial que hace inútil toda la lucha que Maciek lleva a cabo en la clandestinidad, con asesinatos y actos de terrorismo que pretenden salvaguardar algo que ya no existe, y que simboliza muy bien la Iglesia en ruinas con sus símbolos religiosos invertidos de la que hablábamos con anterioridad. Recuerda un poco a esa dicotomía que se plantea entre ser conservador o reaccionario frente a una realidad como la del propio presente, en la que los valores tradicionales han sido totalmente destruidos, y más que conservar se impone la reacción para volver a construir de la nada.
|
 |
|:-:|
|Hipérbola Janus; Textos para la Tradición en tiempos del oscurecimiento: Artículos publicados entre 2014 y 2019 en hiperbolajanus.com; Hipérbola Janus, 2019|
|
|:-:|
|Hipérbola Janus; Textos para la Tradición en tiempos del oscurecimiento: Artículos publicados entre 2014 y 2019 en hiperbolajanus.com; Hipérbola Janus, 2019|Todas las dudas que asaltan al protagonista se ven incrementadas en el momento decisivo, cuando se dispone a dar muerte al líder comunista. Se produce una tensión interna en Maciek, que se encuentra ligado a la joven que ha conocido ese día, y en ella es donde encuentra ese leve destello de humanidad. Esa circunstancia le hace replantearse por un instante el cumplimiento de su misión, pero es un dilema que no tiene salida, y por ello le asalta nuevamente la angustia frente a esa «nada», ese mundo vacío e incomprensible que trasciende el marco de sus propias elecciones.
Uno de los conceptos centrales de Heidegger en Ser y tiempo es el Sein-zum-Tode (ser-para-la-muerte), la idea de que la muerte es la posibilidad más propia y definitiva del Dasein, y que enfrentarla auténticamente permite vivir de manera más plena. Y es que el protagonista se encuentra permanentemente sobre esa frontera entre la vida y la muerte, que afronta con todas sus consecuencias, conscientemente, y la acepta. Esta actitud podría leerse como una forma de Dasein inauténtico, una huida del ser-para-la-muerte mediante la distracción (das Man, el «se» impersonal). Sin embargo, su decisión de cumplir la misión sugiere un enfrentamiento final con esa posibilidad. Otro aspecto que podemos conectar con el pensamiento heideggeriano es la autenticidad o inautenticidad de la vida del protagonista. En relación a la inautenticidad vemos como al principio sigue las órdenes de sus superiores en la organización sin cuestionarlas, lo cual implica un comportamiento inequívocamente alienante. Respecto a aquello que resulta auténtico de su existencia son sus relaciones con Krystyna, que supone imponer su propia voluntad y decisión, mostrando un Dasein que asume su libertad.
|
 |
|:-:|
|Escena de la película.|
|
|:-:|
|Escena de la película.|Otros aspectos más generales de la filosofía existencialista redundan sobre estos mismos aspectos, con la elección entre la libertad absoluta y la condena inevitable. La idea del hombre condenado a actuar, a una elección continua, aún cuando el hombre no es dueño de su destino, o las consecuencias de tales acciones son absurdas, irracionales e incomprensibles. El propio absurdo de la existencia frente al vacío y la ausencia de principios sólidos en los que cimentar la vida, no solo en sus aspectos cotidianos más básicos, sino en aquellos más profundos de la existencia. La soledad y la propia fatalidad frente a un Destino que, como ya hemos apuntado anteriormente, parece imponerse de manera irrevocable, y podríamos decir que brutalmente, al individuo aislado, incapaz de asirse en una guía, en unos valores que le permitan remontar la situación.
En términos generales «Cenizas y diamantes», además de ser una película de gran calidad en sus aspectos técnicos, en su fotografía, en la configuración de sus escenas y en el propio desarrollo argumental, bajo un guión espléndidamente ejecutado a lo largo de sus 98 minutos de duración, también nos invita a una reflexión profunda sobre la condición humana y la propia Modernidad. Y es algo que vemos en nuestros días, con las consecuencias de un pensamiento débil, con la promoción del individualismo, el hedonismo y lo efímero. La ausencia de estructuras sólidas, la subversión de toda forma de autoridad y jerarquía tradicionales. Paradójicamente, el mundo actual tiende a formas de poder y autoridad mucho más invasivas y coercitivas, tanto a nivel individual como colectivo, pero en la misma línea abstracta e impersonal que nos describe la película, abocándonos a la alienación y la inautenticidad de nuestras propias vidas. Y como Maciek, también nosotros, vivimos en un mundo dominado por la incertidumbre y la desesperanza, en el que el globalismo y sus perversas ideologías deshumanizantes actúan por doquier.
|
 |
|:-:|
|Carátula original de la película en polaco.|
|
|:-:|
|Carátula original de la película en polaco.|
Artículo original: Hipérbola Janus, Reseña de «Cenizas y Diamantes» (Andrzej Wajda, 1958) (TOR), 31/Mar/2025
-
 @ bcbb3e40:a494e501
2025-03-31 15:44:56
@ bcbb3e40:a494e501
2025-03-31 15:44:56El 7 de febrero de 2025, Donald Trump firmó una orden ejecutiva que establecía una «Oficina de la Fe» en la Casa Blanca, dirigida por su asesora espiritual Paula White-Cain, la pastora de esa «teología de la prosperidad» (prosperity theology) que predica el «Evangelio de la salud y la riqueza» (health and wealth gospel^1). Investida de su nueva función, la reverenda pastora dijo: «Tengo la autoridad para declarar a la Casa Blanca un lugar santo. Es mi presencia la que la santifica»[^2]. Los siete rabinos del «Sanedrín Naciente» —la corte suprema que guiará a Israel cuando se reconstruya el Templo de Jerusalén— enviaron conmovedoras felicitaciones al presidente Trump por el establecimiento de esta Oficina. «Expresamos nuestra sincera gratitud —se lee en el mensaje oficial enviado a Trump desde el Monte Sión— por llevar la fe a la vanguardia de la cultura estadounidense y mundial mediante el establecimiento de la Oficina de la Fe en la Casa Blanca. Su reconocimiento de la importancia de la religión en la vida pública es un paso hacia la restauración de los valores morales y del liderazgo espiritual en el mundo[^3]. La carta del «Sanedrín Naciente», que augura el éxito a la «misión divina» del presidente estadounidense, reproduce las dos caras de una «moneda del Templo», acuñada en 2017 para celebrar el traslado de la embajada estadounidense a Jerusalén y, simultáneamente, el centenario de la Declaración Balfour. En el anverso se ven los perfiles de Donald Trump y Ciro el Grande, a quien la tradición judía atribuye la reconstrucción del templo destruido por los babilonios, con la inscripción (en hebreo e inglés) «Cyrus —Balfour— Trump Declaration 1917-2017»; en el reverso está la imagen del Templo de Jerusalén[^4]. Otra moneda, que lleva los perfiles de Trump y Ciro en el anverso y los de Trump y Netanyahu en el reverso, fue acuñada en 2018 para celebrar el septuagésimo aniversario de la independencia del «Estado de Israel»; se observa dos inscripciones en hebreo e inglés: «Y Él me encargó construirle una casa en Jerusalén» y «Guerra de los Hijos de la Luz contra los Hijos de las Tinieblas».
El tema de la «guerra de los Hijos de la Luz contra los Hijos de las Tinieblas» ha tenido una difusión particular en el imaginario y la propaganda trumpista. El 7 de junio de 2020, monseñor Carlo Maria Viganò, ex nuncio de la Santa Sede en los Estados Unidos, escribió una carta al presidente Donald Trump que comenzaba así: «Estamos asistiendo en los últimos meses a la formación de dos bandos, que los definiría bíblicos: los hijos de la luz y los hijos de las tinieblas»[^5]. El 1 de enero de 2021, el agitprop estadounidense Steve Bannon declaró en una entrevista con Monseñor Viganò: «Esta es una batalla de época entre los hijos de la Luz y los hijos de las Tinieblas»[^6].
Son numerosos los judíos sionistas que están en el círculo del presidente Trump: además de su hija Ivanka (convertida en 2009) y su yerno Jared Kushner (entonces Consejero Anciano del Presidente), el 19 de noviembre de 2024 el «The Jerusalem Post»[^7] publicó una lista de los más influyentes: Stephen Miller, subdirector del staff de la Casa Blanca y consejero de Seguridad Nacional de Estados Unidos; David Melech Friedman, a quien en 2016 Trump nombró embajador en Israel; el multimillonario «filántropo» Steven Charles Witkoff, enviado especial de Estados Unidos a Oriente Medio; Miriam Adelson, directora del periódico «Israel Hayom», clasificada por Bloomberg Billionaires como la quinta mujer más rica del mundo (con un patrimonio neto de 32,400 millones de dólares), financiadora de iniciativas políticas conservadoras en Estados Unidos e Israel; el banquero Boris Epshteyn, consejero estratégico de la campaña presidencial de Trump en 2020; Howard Williams Lutnick, presidente de la Cantor Fitzgerald del Grupo BGC, financista de las campañas presidenciales de Donald Trump en 2020 y 2024, ahora secretario de Comercio; la modelo Elizabeth Pipko, portavoz nacional del Partido Republicano y creadora de un «museo interactivo virtual» sobre la «Shoah» como parte del proyecto de Lest People Forget, cuyo objetivo es combatir el «antisemitismo» y la «negacionismo»; Lee Michael Zeldin, miembro republicano de la Cámara de Representantes por el estado de Nueva York del 2015 al 2023 y actualmente administrador de la EPA (Environmental Protection Agency); la columnista Laura Elizabeth Loomer, «orgullosamente islamófoba», activa patrocinadora de Trump en la campaña para las elecciones presidenciales de 2024; Sidney Ferris Rosenberg, influyente presentador de radio y periodista deportivo; William Owen Scharf, Asistente del Presidente y secretario del personal de la Casa Blanca; Marc Jeffrey Rowan, «filántropo» con un patrimonio neto valorado por Forbes en ocho mil ochocientos millones de dólares.
Además de estos, cabe mencionar al popular presentador de radio Mark Levin quien, en diciembre de 2019, durante la celebración de la fiesta de Janucá en la Casa Blanca, saludó a Donald Trump como «el primer presidente judío de los Estados Unidos»[^8]. Según un funcionario de alto nivel de la Casa Blanca, Donald Trump se convirtió al judaísmo dos años antes en la sinagoga de la secta Jabad Lubavitch en la ciudad de Nueva York. David Elias Goldberg, miembro del Jewish Center of Antisemitic Study, también entrevistó al funcionario, para quien «Trump fue “instado” por su hija Ivanka y su yerno Jared Kushner para abrazar la fe. Inicialmente, Trump se habría mostrado reacio, considerando que esto podría enfriar el apoyo del electorado evangélico». Luego, informa «Israel Today News», «cambió de opinión y se convirtió oficialmente a principios de 2017. La ceremonia se llevó a cabo en privado y se guardó celosamente durante casi dos años»[^9]. Pero ya en septiembre de 2015, el rabino millonario Kirt Schneider, invitado a la Trump Tower de Nueva York, había impuesto sus manos sobre la cabeza de Donald Trump y lo había bendecido en hebreo e inglés, declarando: «Las únicas dos naciones que tienen una relación privilegiada con Dios son Israel y los Estados Unidos de América»[^10].
El 7 de octubre de 2024, en el aniversario de la operación de Hamas «Diluvio de Al-Aqsa», Trump fue acompañado por un «superviviente de la Shoah» a la tumba de Menachem Mendel Schneerson, séptimo y último Rabino de los Hasidim de la secta Jabad Lubavitch, que en 1991 declaró a sus seguidores: «He hecho todo lo posible para provocar el arribo del Mesías, ahora les paso a ustedes esta misión; hagan todo lo que puedan para que Él venga»^11. En relación al evento mesiánico, el eminente rabino Yekutiel Fish atribuyó una misión decisiva a Trump: «Todo el mundo está centrado en Gaza, pero esa es solo una parte de la agenda del fin de los tiempos, que tiene a los judíos viviendo en las fronteras profetizadas de Israel; la Torá incluye explícitamente a Gaza. Lo que Trump está haciendo es limpiar Gaza de todos los odiadores de Israel. No podrán estar en Israel después de la venida del Mesías. (...) Esto incluirá a Gaza, la mitad del Líbano y gran parte de Jordania. Y vemos que casi lo hemos logrado. Siria cayó. Líbano está medio destruido. Gaza está destrozada. El escenario está casi listo para el Mesías. Pero, ¿cómo pueden los palestinos estar aquí cuando vayamos a recibir al Mesías? El Mesías necesita que alguien se ocupe de esto, y en este caso, es Donald Trump. Trump está simplemente llevando a cabo las tareas finales necesarias antes de que el Mesías sea revelado»[^12].
Esta inspiración escatológica está presente en las palabras de Pete Brian Hegseth, el pintoresco exponente del «Reconstruccionismo Cristiano»[^13] a quien Trump nombró secretario de Defensa. En un discurso pronunciado en 2019 en el Hotel Rey David de Jerusalén, con motivo de la conferencia anual del canal Arutz Sheva (Israel National News), Hegseth enalteció el «vínculo eterno» entre Israel y Estados Unidos, y enumeró los «milagros» que atestiguan el «apoyo divino» a la causa sionista, el último de los cuales será la reconstrucción del Templo judío en la zona donde actualmente se encuentra la mezquita de al-Aqsa: «La dignidad de capital adquirida por Jerusalén —dijo— fue un milagro, y no hay razón por la cual no sea posible el milagro de la restauración del Templo en el Monte del Templo».[^14]
Es conocido que el fundamentalismo evangélico pro-sionista[^15] comparte con el judaísmo la creencia en que la construcción del tercer Templo de Jerusalén marcará el comienzo de la era mesiánica; cuando la administración Trump trasladó la embajada de Estados Unidos a Jerusalén en 2017, Laurie Cardoza-Moore, exponente del evangelismo sionista, saludó así la «obediencia de Trump a la Palabra de Dios» en «Haaretz»: «Al establecer la Embajada en Jerusalén, el presidente Donald Trump está implementando una de las iniciativas históricas de dimensión bíblica en su presidencia. Al igual que muchos judíos en Israel y en todo el mundo, los cristianos reconocen el vínculo de los judíos con la Biblia a través del nombre de Jerusalén como la capital del antiguo Israel, así como el sitio del Primer y Segundo Templos. Según los profetas Ezequiel, Isaías y el apóstol Juan del Nuevo Testamento, todos los israelíes esperan la reconstrucción del Tercer Templo»[^16]. El 22 de mayo del mismo año, Donald Trump, acompañado de su esposa Melania, de su hija Ivanka y su yerno Jared Kushner, fue el primer presidente de los Estados Unidos en ejercicio en acudir al Muro de las Lamentaciones, anexionado ilegalmente a la entidad sionista.
En 2019, la administración Trump confirmó la posición de Estados Unidos al enviar en visita oficial para Jerusalén a Mike Pompeo, un secretario de Estado que —ironía de la Historia— lleva el mismo nombre del general romano que asaltó la ciudad en el año 63 a.C. «Por primera vez en la historia, un secretario de Estado norteamericano visitó la Ciudad Vieja de Jerusalén en compañía de un alto político israelí. Fue una visita histórica que reforzó las expectativas israelíes y constituyó un reconocimiento tácito de la soberanía israelí sobre el sitio del Monte del Templo y la Explanada de las Mezquitas. (…) Mike Pompeo, acompañado por el primer ministro Benjamin Netanyahu y el embajador de Estados Unidos en Israel, David Friedman, también visitó el túnel del Muro de las Lamentaciones y la sinagoga ubicada bajo tierra, en el presunto lugar del santuario del Templo[^17], donde se le mostró una maqueta del futuro Templo[^18]. En el transcurso de una entrevista concedida durante la fiesta del Purim (que celebra el exterminio de la clase política persa, ocurrido hace 2500 años), el secretario de Estado insinuó que «el presidente Donald Trump puede haber sido enviado por Dios para salvar al pueblo judío y que confiaba en que aquí el Señor estaba obrando»[^19].
Como observa Daniele Perra, en este mismo número de «Eurasia», el «mito movilizador» del Tercer Templo, atribuible a los «mitos teológicos» señalados por Roger Garaudy como mitos fundadores de la entidad sionista, «atribuye al judaísmo una especie de función sociológica de transmisión y proyección del conflicto palestino-israelí hacia el resto del mundo y confiere una inspiración apocalíptica al momento geopolítico actual».
|Info|| |:-|:-| |Autor| Claudio Mutti | |Fuente| I "Figli della Luce" alla Casa Bianca | |Fecha| 8/Mar/2025 | |Traducción| Francisco de la Torre |
[^2]: The White House, President Trump announces appointments to the White House Faith Office https://www.whitehouse.gov,, 7 de febrero de 2025; Trump establece la Oficina de la Fe con una foto de «La Última Cena» | Fue dirigida por la controvertida predicadora Paula White, https://www.tgcom24.mediaset.it, 10 de febrero de 2025.
[^3]: «We extend our heartfelt gratitude for bringing faith to the forefront of American and global culture through the establishment of the Faith Office in the White House. Your recognition of the importance of religion in public life is a step toward restoring moral values and spiritual leadership in the world» (Letter from the Nascent Sanhedrin to President Donald J. Trump, Jerusalem, Wednesday, February 12, 2025).
[^4]: Israeli group mints Trump coin to honor Jerusalem recognition, «The Times of Israel», https://www.timesofisrael.com, 28-2-2018.
[^5]: Mons. Viganò — Siamo nella battaglia tra figli della luce e figli delle tenebre, https://www.italiador.com, 7-6-2020
[^6]: TRANSCRIPT: Steve Bannon’s ‘War Room’ interview with Abp. Viganò, lifesitenews.com, 4-1-2021. Sulle origini e sulla fortuna di questo tema cfr. C. Mutti, Le sètte dell’Occidente, «Eurasia», 2/2021, pp. 12-15. (https://www.eurasia-rivista.com/las-sectas-de-occidente/)
[^7]: Luke Tress, The who’s who of Jews in Trump’s inner circle?, «The Jerusalem Post», https://www.jpost.com, 19-11-2024.
[^8]: Radio Talk Show Host Mark Levin Calls President Trump «the First Jewish President of the United States», https://www.c-span.org, 11-12-2019.
[^9]: «However, he had a change of heart and officially converted in early 2017. The ceremony was held in private, and closely guarded for nearly two years» (Donald Trump converted to Judaism two years ago, according to White House official, https://israeltodaynews.blogspot.com/2019/02).
[^10]: «El rabino Kirt Schneider (...) es un millonario judío, una figura televisiva de los “judíos mesiánicos”. Sus emisiones televisivas semanales son emitidas por más de treinta canales cristianos en unos doscientos países; entre ellos, los canales “Yes” y “Hot” en Israel. Solo en Estados Unidos, sus emisiones atraen a 1.600.000 telespectadores cada semana. Kirt Schneider dirige un imperio de telecomunicaciones que tiene un millón y medio de seguidores en Facebook, X (antes Twitter) y YouTube» (Pierre-Antoine Plaquevent — Youssef Hindi, El milenarismo teopolítico de Israel, Edizioni all'insegna del Veltro, Parma 2025, p. 31).
[^12]: «Everyone is focused on Gaza, but that is only one part of the end-of-days agenda, which has the Jews living in Israel’s prophesied borders. The Torah explicitly includes Gaza. What Trump is doing is cleaning out Gaza of all the haters of Israel. They cannot be in Israel after the Messiah comes. (…) This will include Gaza, half of Lebanon, and much of Jordan. And we see that we are almost there. Syria fell. Lebanon is half gone. Gaza is ripped up. The stage is nearly set for Messiah. But how can the Palestinians be here when we go to greet the Messiah? The Messiah needs someone to take care of this, and in this case, it is Donald Trump. Trump is merely carrying out the final tasks needed before Messiah is revealed» (Adam Eliyahu Berkowitz, Trump’s Gaza Plan is «The Final task before Messiah», https://israel365news.com, 5-2-2025).
[^13]: «A day after Hegseth was announced for the Cabinet position, Brooks Potteiger, a pastor within the Communion of Reformed Evangelical Churches (CREC), posted on X that Hegseth is a member of the church in good standing. The CREC, a denomination of Christian Reconstructionism, is considered by some academics to be an extremist, Christian supremacist movement» (Shannon Bond e altri, What’s behind defense secretary pick Hegseth’s war on ‘woke’, https://www.npr.org, 14-11-2024.
[^14]: «The decoration of Jerusalem as a capital was a miracle, and there is no reason why the miracle of the re-establishment of Temple on the Temple Mount is not possible» (Pete Hegseth at Arutz Sheva Conference, youtube.com). Cfr. Daniele Perra, Paleotrumpismo, neotrumpismo e post-trumpismo, in: AA. VV., Trumpismo, Cinabro Edizioni, Roma 2025, pp. 22-23.
[^15]: Pierre-Antoine Plaquevent — Youssef Hindi, El milenarismo teopolítico de Israel, cit., págs. 82 a 96.
[^16]: «We American Christians Welcome Trump’s Obedience to God’s Word on Jerusalem», «Haaretz», 6-12-2017.
[^17]: Pierre-Antoine Plaquevent — Youssef Hindi, El milenarismo teopolítico de Israel, cit., pág. 97.
[^18]: Pompeo en visite historique au mur Occidental aux côtés de Netanyahu et Friedman, «The Times of Israel», https://fr.timesofisrael.com, 21-3-2019.
[^19]: Pompeo says Trump may have been sent by God to save Jews from Iran, «The Times of Israel», 22-3-2019.
Artículo original: Claudio Mutti, Los «hijos de la luz» en la Casa Blanca (TOR), 25/Mar/2025
-
 @ b17fccdf:b7211155
2025-03-25 11:23:36
@ b17fccdf:b7211155
2025-03-25 11:23:36Si vives en España, quizás hayas notado que no puedes acceder a ciertas páginas webs durante los fines de semana o en algunos días entre semana, entre ellas, la guía de MiniBolt.
Esto tiene una razón, por supuesto una solución, además de una conclusión. Sin entrar en demasiados detalles:
La razón
El bloqueo a Cloudflare, implementado desde hace casi dos meses por operadores de Internet (ISPs) en España (como Movistar, O2, DIGI, Pepephone, entre otros), se basa en una orden judicial emitida tras una demanda de LALIGA (Fútbol). Esta medida busca combatir la piratería en España, un problema que afecta directamente a dicha organización.
Aunque la intención original era restringir el acceso a dominios específicos que difundieran dicho contenido, Cloudflare emplea el protocolo ECH (Encrypted Client Hello), que oculta el nombre del dominio, el cual antes se transmitía en texto plano durante el proceso de establecimiento de una conexión TLS. Esta medida dificulta que las operadoras analicen el tráfico para aplicar bloqueos basados en dominios, lo que les obliga a recurrir a bloqueos más amplios por IP o rangos de IP para cumplir con la orden judicial.
Esta práctica tiene consecuencias graves, que han sido completamente ignoradas por quienes la ejecutan. Es bien sabido que una infraestructura de IP puede alojar numerosos dominios, tanto legítimos como no legítimos. La falta de un "ajuste fino" en los bloqueos provoca un perjuicio para terceros, restringiendo el acceso a muchos dominios legítimos que no tiene relación alguna con actividades ilícitas, pero que comparten las mismas IPs de Cloudflare con dominios cuestionables. Este es el caso de la web de MiniBolt y su dominio
minibolt.info, los cuales utilizan Cloudflare como proxy para aprovechar las medidas de seguridad, privacidad, optimización y servicios adicionales que la plataforma ofrece de forma gratuita.Si bien este bloqueo parece ser temporal (al menos durante la temporada 24/25 de fútbol, hasta finales de mayo), es posible que se reactive con el inicio de la nueva temporada.

La solución
Obviamente, MiniBolt no dejará de usar Cloudflare como proxy por esta razón. Por lo que a continuación se exponen algunas medidas que como usuario puedes tomar para evitar esta restricción y poder acceder:
~> Utiliza una VPN:
Existen varias soluciones de proveedores de VPN, ordenadas según su reputación en privacidad: - IVPN - Mullvad VPN - Proton VPN (gratis) - Obscura VPN (solo para macOS) - Cloudfare WARP (gratis) + permite utilizar el modo proxy local para enrutar solo la navegación, debes utilizar la opción "WARP a través de proxy local" siguiendo estos pasos: 1. Inicia Cloudflare WARP y dentro de la pequeña interfaz haz click en la rueda dentada abajo a la derecha > "Preferencias" > "Avanzado" > "Configurar el modo proxy" 2. Marca la casilla "Habilite el modo proxy en este dispositivo" 3. Elige un "Puerto de escucha de proxy" entre 0-65535. ej: 1080, haz click en "Aceptar" y cierra la ventana de preferencias 4. Accede de nuevo a Cloudflare WARP y pulsa sobre el switch para habilitar el servicio. 3. Ahora debes apuntar el proxy del navegador a Cloudflare WARP, la configuración del navegador es similar a esta para el caso de navegadores basados en Firefox. Una vez hecho, deberías poder acceder a la guía de MiniBolt sin problemas. Si tienes dudas, déjalas en comentarios e intentaré resolverlas. Más info AQUÍ.

~> Proxifica tu navegador para usar la red de Tor, o utiliza el navegador oficial de Tor (recomendado).

La conclusión
Estos hechos ponen en tela de juicio los principios fundamentales de la neutralidad de la red, pilares esenciales de la Declaración de Independencia del Ciberespacio que defiende un internet libre, sin restricciones ni censura. Dichos principios se han visto quebrantados sin precedentes en este país, confirmando que ese futuro distópico que muchos negaban, ya es una realidad.
Es momento de actuar y estar preparados: debemos impulsar el desarrollo y la difusión de las herramientas anticensura que tenemos a nuestro alcance, protegiendo así la libertad digital y asegurando un acceso equitativo a la información para todos
Este compromiso es uno de los pilares fundamentales de MiniBolt, lo que convierte este desafío en una oportunidad para poner a prueba las soluciones anticensura ya disponibles, así como las que están en camino.
¡Censúrame si puedes, legislador! ¡La lucha por la privacidad y la libertad en Internet ya está en marcha!

Fuentes: * https://bandaancha.eu/articulos/movistar-o2-deja-clientes-sin-acceso-11239 * https://bandaancha.eu/articulos/esta-nueva-sentencia-autoriza-bloqueos-11257 * https://bandaancha.eu/articulos/como-saltarse-bloqueo-webs-warp-vpn-9958 * https://bandaancha.eu/articulos/como-activar-ech-chrome-acceder-webs-10689 * https://comunidad.movistar.es/t5/Soporte-Fibra-y-ADSL/Problema-con-web-que-usan-Cloudflare/td-p/5218007
-
 @ 97c70a44:ad98e322
2025-03-05 18:09:05
@ 97c70a44:ad98e322
2025-03-05 18:09:05So you've decided to join nostr! Some wide-eyed fanatic has convinced you that the "sun shines every day on the birds and the bees and the cigarette trees" in a magical land of decentralized, censorship-resistant freedom of speech - and it's waiting just over the next hill.
But your experience has not been all you hoped. Before you've even had a chance to upload your AI-generated cyberpunk avatar or make up exploit codenames for your pseudonym's bio, you've been confronted with a new concept that has left you completely nonplussed.
It doesn't help that this new idea might be called by any number of strange names. You may have been asked to "paste your nsec", "generate a private key", "enter your seed words", "connect with a bunker", "sign in with extension", or even "generate entropy". Sorry about that.
All these terms are really referring to one concept under many different names: that of "cryptographic identity".
Now, you may have noticed that I just introduced yet another new term which explains exactly nothing. You're absolutely correct. And now I'm going to proceed to ignore your complaints and talk about something completely different. But bear with me, because the juice is worth the squeeze.
Identity
What is identity? There are many philosophical, political, or technical answers to this question, but for our purposes it's probably best to think of it this way:
Identity is the essence of a thing. Identity separates one thing from all others, and is itself indivisible.
This definition has three parts:
- Identity is "essential": a thing can change, but its identity cannot. I might re-paint my house, replace its components, sell it, or even burn it down, but its identity as something that can be referred to - "this house" - is durable, even outside the boundaries of its own physical existence.
- Identity is a unit: you can't break an identity into multiple parts. A thing might be composed of multiple parts, but that's only incidental to the identity of a thing, which is a concept, not a material thing.
- Identity is distinct: identity is what separates one thing from all others - the concept of an apple can't be mixed with that of an orange; the two ideas are distinct. In the same way, a single concrete apple is distinct in identity from another - even if the component parts of the apple decompose into compost used to grow more apples.
Identity is not a physical thing, but a metaphysical thing. Or, in simpler terms, identity is a "concept".
I (or someone more qualified) could at this point launch into a Scholastic tangent on what "is" is, but that is, fortunately, not necessary here. The kind of identities I want to focus on here are not our actual identities as people, but entirely fictional identities that we use to extend our agency into the digital world.
Think of it this way - your bank login does not represent you as a complete person. It only represents the access granted to you by the bank. This access is in fact an entirely new identity that has been associated with you, and is limited in what it's useful for.
Other examples of fictional identities include:
- The country you live in
- Your social media persona
- Your mortgage
- Geographical coordinates
- A moment in time
- A chess piece
Some of these identites are inert, for example points in space and time. Other identies have agency and so are able to act in the world - even as fictional concepts. In order to do this, they must "authenticate" themselves (which means "to prove they are real"), and act within a system of established rules.
For example, your D&D character exists only within the collective fiction of your D&D group, and can do anything the rules say. Its identity is authenticated simply by your claim as a member of the group that your character in fact exists. Similarly, a lawyer must prove they are a member of the Bar Association before they are allowed to practice law within that collective fiction.
"Cryptographic identity" is simply another way of authenticating a fictional identity within a given system. As we'll see, it has some interesting attributes that set it apart from things like a library card or your latitude and longitude. Before we get there though, let's look in more detail at how identities are authenticated.
Certificates
Merriam-Webster defines the verb "certify" as meaning "to attest authoritatively". A "certificate" is just a fancy way of saying "because I said so". Certificates are issued by a "certificate authority", someone who has the authority to "say so". Examples include your boss, your mom, or the Pope.
This method of authentication is how almost every institution authenticates the people who associate with it. Colleges issue student ID cards, governments issue passports, and websites allow you to "register an account".
In every case mentioned above, the "authority" creates a closed system in which a document (aka a "certificate") is issued which serves as a claim to a given identity. When someone wants to access some privileged service, location, or information, they present their certificate. The authority then validates it and grants or denies access. In the case of an international airport, the certificate is a little book printed with fancy inks. In the case of a login page, the certificate is a username and password combination.
This pattern for authentication is ubiquitous, and has some very important implications.
First of all, certified authentication implies that the issuer of the certificate has the right to exclusive control of any identity it issues. This identity can be revoked at any time, or its permissions may change. Your social credit score may drop arbitrarily, or money might disappear from your account. When dealing with certificate authorities, you have no inherent rights.
Second, certified authentication depends on the certificate authority continuing to exist. If you store your stuff at a storage facility but the company running it goes out of business, your stuff might disappear along with it.
Usually, authentication via certificate authority works pretty well, since an appeal can always be made to a higher authority (nature, God, the government, etc). Authorities also can't generally dictate their terms with impunity without losing their customers, alienating their constituents, or provoking revolt. But it's also true that certification by authority creates an incentive structure that frequently leads to abuse - arbitrary deplatforming is increasingly common, and the bigger the certificate authority, the less recourse the certificate holder (or "subject") has.
Certificates also put the issuer in a position to intermediate relationships that wouldn't otherwise be subject to their authority. This might take the form of selling user attention to advertisers, taking a cut of financial transactions, or selling surveillance data to third parties.
Proliferation of certificate authorities is not a solution to these problems. Websites and apps frequently often offer multiple "social sign-in" options, allowing their users to choose which certificate authority to appeal to. But this only piles more value into the social platform that issues the certificate - not only can Google shut down your email inbox, they can revoke your ability to log in to every website you used their identity provider to get into.
In every case, certificate issuance results in an asymmetrical power dynamic, where the issuer is able to exert significant control over the certificate holder, even in areas unrelated to the original pretext for the relationship between parties.
Self-Certification
But what if we could reverse this power dynamic? What if individuals could issue their own certificates and force institutions to accept them?

Ron Swanson's counterexample notwithstanding, there's a reason I can't simply write myself a parking permit and slip it under the windshield wiper. Questions about voluntary submission to legitimate authorities aside, the fact is that we don't have the power to act without impunity - just like any other certificate authority, we have to prove our claims either by the exercise of raw power or by appeal to a higher authority.
So the question becomes: which higher authority can we appeal to in order to issue our own certificates within a given system of identity?
The obvious answer here is to go straight to the top and ask God himself to back our claim to self-sovereignty. However, that's not how he normally works - there's a reason they call direct acts of God "miracles". In fact, Romans 13:1 explicitly says that "the authorities that exist have been appointed by God". God has structured the universe in such a way that we must appeal to the deputies he has put in place to govern various parts of the world.
Another tempting appeal might be to nature - i.e. the material world. This is the realm in which we most frequently have the experience of "self-authenticating" identities. For example, a gold coin can be authenticated by biting it or by burning it with acid. If it quacks like a duck, walks like a duck, and looks like a duck, then it probably is a duck.
In most cases however, the ability to authenticate using physical claims depends on physical access, and so appeals to physical reality have major limitations when it comes to the digital world. Captchas, selfies and other similar tricks are often used to bridge the physical world into the digital, but these are increasingly easy to forge, and hard to verify.
There are exceptions to this rule - an example of self-certification that makes its appeal to the physical world is that of a signature. Signatures are hard to forge - an incredible amount of data is encoded in physical signatures, from strength, to illnesses, to upbringing, to personality. These can even be scanned and used within the digital world as well. Even today, most contracts are sealed with some simulacrum of a physical signature. Of course, this custom is quickly becoming a mere historical curiosity, since the very act of digitizing a signature makes it trivially forgeable.
So: transcendent reality is too remote to subtantiate our claims, and the material world is too limited to work within the world of information. There is another aspect of reality remaining that we might appeal to: information itself.
Physical signatures authenticate physical identities by encoding unique physical data into an easily recognizable artifact. To transpose this idea to the realm of information, a "digital signature" might authenticate "digital identities" by encoding unique "digital data" into an easily recognizable artifact.
Unfortunately, in the digital world we have the additional challenge that the artifact itself can be copied, undermining any claim to legitimacy. We need something that can be easily verified and unforgeable.
Digital Signatures
In fact such a thing does exist, but calling it a "digital signature" obscures more than it reveals. We might just as well call the thing we're looking for a "digital fingerprint", or a "digital electroencephalogram". Just keep that in mind as we work our way towards defining the term - we are not looking for something looks like a physical signature, but for something that does the same thing as a physical signature, in that it allows us to issue ourselves a credential that must be accepted by others by encoding privileged information into a recognizable, unforgeable artifact.
With that, let's get into the weeds.
An important idea in computer science is that of a "function". A function is a sort of information machine that converts data from one form to another. One example is the idea of "incrementing" a number. If you increment 1, you get 2. If you increment 2, you get 3. Incrementing can be reversed, by creating a complementary function that instead subtracts 1 from a number.
A "one-way function" is a function that can't be reversed. A good example of a one-way function is integer rounding. If you round a number and get
5, what number did you begin with? It's impossible to know - 5.1, 4.81, 5.332794, in fact an infinite number of numbers can be rounded to the number5. These numbers can also be infinitely long - for example rounding PI to the nearest integer results in the number3.A real-life example of a useful one-way function is
sha256. This function is a member of a family of one-way functions called "hash functions". You can feed as much data as you like intosha256, and you will always get 256 bits of information out. Hash functions are especially useful because collisions between outputs are very rare - even if you change a single bit in a huge pile of data, you're almost certainly going to get a different output.Taking this a step further, there is a whole family of cryptographic one-way "trapdoor" functions that act similarly to hash functions, but which maintain a specific mathematical relationship between the input and the output which allows the input/output pair to be used in a variety of useful applications. For example, in Elliptic Curve Cryptography, scalar multiplication on an elliptic curve is used to derive the output.
"Ok", you say, "that's all completely clear and lucidly explained" (thank you). "But what goes into the function?" You might expect that because of our analogy to physical signatures we would have to gather an incredible amount of digital information to cram into our cryptographic trapdoor function, mashing together bank statements, a record of our heartbeat, brain waves and cellular respiration. Well, we could do it that way (maybe), but there's actually a much simpler solution.
Let's play a quick game. What number am I thinking of? Wrong, it's 82,749,283,929,834. Good guess though.
The reason we use signatures to authenticate our identity in the physical world is not because they're backed by a lot of implicit physical information, but because they're hard to forge and easy to validate. Even so, there is a lot of variation in a single person's signature, even from one moment to the next.
Trapdoor functions solve the validation problem - it's trivially simple to compare one 256-bit number to another. And randomness solves the problem of forgeability.
Now, randomness (A.K.A. "entropy") is actually kind of hard to generate. Random numbers that don't have enough "noise" in them are known as "pseudo-random numbers", and are weirdly easy to guess. This is why Cloudflare uses a video stream of their giant wall of lava lamps to feed the random number generator that powers their CDN. For our purposes though, we can just imagine that our random numbers come from rolling a bunch of dice.
To recap, we can get a digital equivalent of a physical signature (or fingerprint, etc) by 1. coming up with a random number, and 2. feeding it into our chosen trapdoor function. The random number is called the "private" part. The output of the trapdoor function is called the "public" part. These two halves are often called "keys", hence the terms "public key" and "private key".
And now we come full circle - remember about 37 years ago when I introduced the term "cryptographic identity"? Well, we've finally arrived at the point where I explain what that actually is.
A "cryptographic identity" is identified by a public key, and authenticated by the ability to prove that you know the private key.
Notice that I didn't say "authenticated by the private key". If you had to reveal the private key in order to prove you know it, you could only authenticate a public key once without losing exclusive control of the key. But cryptographic identities can be authenticated any number of times because the certification is an algorithm that only someone who knows the private key can execute.
This is the super power that trapdoor functions have that hash functions don't. Within certain cryptosystems, it is possible to mix additional data with your private key to get yet another number in such a way that someone else who only knows the public key can prove that you know the private key.
For example, if my secret number is
12, and someone tells me the number37, I can "combine" the two by adding them together and returning the number49. This "proves" that my secret number is12. Of course, addition is not a trapdoor function, so it's trivially easy to reverse, which is why cryptography is its own field of knowledge.What's it for?
If I haven't completely lost you yet, you might be wondering why this matters. Who cares if I can prove that I made up a random number?
To answer this, let's consider a simple example: that of public social media posts.
Most social media platforms function by issuing credentials and verifying them based on their internal database. When you log in to your Twitter (ok, fine, X) account, you provide X with a phone number (or email) and password. X compares these records to the ones stored in the database when you created your account, and if they match they let you "log in" by issuing yet another credential, called a "session key".
Next, when you "say" something on X, you pass along your session key and your tweet to X's servers. They check that the session key is legit, and if it is they associate your tweet with your account's identity. Later, when someone wants to see the tweet, X vouches for the fact that you created it by saying "trust me" and displaying your name next to the tweet.
In other words, X creates and controls your identity, but they let you use it as long as you can prove that you know the secret that you agreed on when you registered (by giving it to them every time).
Now pretend that X gets bought by someone even more evil than Elon Musk (if such a thing can be imagined). The new owner now has the ability to control your identity, potentially making it say things that you didn't actually say. Someone could be completely banned from the platform, but their account could be made to continue saying whatever the owner of the platform wanted.
In reality, such a breach of trust would quickly result in a complete loss of credibility for the platform, which is why this kind of thing doesn't happen (at least, not that we know of).
But there are other ways of exploiting this system, most notably by censoring speech. As often happens, platforms are able to confiscate user identities, leaving the tenant no recourse except to appeal to the platform itself (or the government, but that doesn't seem to happen for some reason - probably due to some legalese in social platforms' terms of use). The user has to start completely from scratch, either on the same platform or another.
Now suppose that when you signed up for X instead of simply telling X your password you made up a random number and provided a cryptographic proof to X along with your public key. When you're ready to tweet (there's no need to issue a session key, or even to store your public key in their database) you would again prove your ownership of that key with a new piece of data. X could then publish that tweet or not, along with the same proof you provided that it really came from you.
What X can't do in this system is pretend you said something you didn't, because they don't know your private key.
X also wouldn't be able to deplatform you as effectively either. While they could choose to ban you from their website and refuse to serve your tweets, they don't control your identity. There's nothing they can do to prevent you from re-using it on another platform. Plus, if the system was set up in such a way that other users followed your key instead of an ID made up by X, you could switch platforms and keep your followers. In the same way, it would also be possible to keep a copy of all your tweets in your own database, since their authenticity is determined by your digital signature, not X's "because I say so".
This new power is not just limited to social media either. Here are some other examples of ways that self-issued cryptographic identites transform the power dynamic inherent in digital platforms:
- Banks sometimes freeze accounts or confiscate funds. If your money was stored in a system based on self-issued cryptographic keys rather than custodians, banks would not be able to keep you from accessing or moving your funds. This system exists, and it's called bitcoin.
- Identity theft happens when your identifying information is stolen and used to take out a loan in your name, and without your consent. The reason this is so common is because your credentials are not cryptographic - your name, address, and social security number can only be authenticated by being shared, and they are shared so often and with so many counterparties that they frequently end up in data breaches. If credit checks were authenticated by self-issued cryptographic keys, identity theft would cease to exist (unless your private key itself got stolen).
- Cryptographic keys allow credential issuers to protect their subjects' privacy better too. Instead of showing your ID (including your home address, birth date, height, weight, etc), the DMV could sign a message asserting that the holder of a given public key indeed over 21. The liquor store could then validate that claim, and your ownership of the named key, without knowing anything more about you. Zero-knowledge proofs take this a step further.
In each of these cases, the interests of the property owner, loan seeker, or customer are elevated over the interests of those who might seek to control their assets, exploit their hard work, or surveil their activity. Just as with personal privacy, freedom of speech, and Second Amendment rights the individual case is rarely decisive, but in the aggregate realigned incentives can tip the scale in favor of freedom.
Objections
Now, there are some drawbacks to digital signatures. Systems that rely on digital signatures are frequently less forgiving of errors than their custodial counterparts, and many of their strengths have corresponding weaknesses. Part of this is because people haven't yet developed an intuition for how to use cryptographic identities, and the tools for managing them are still being designed. Other aspects can be mitigated through judicious use of keys fit to the problems they are being used to solve.
Below I'll articulate some of these concerns, and explore ways in which they might be mitigated over time.
Key Storage
Keeping secrets is hard. "A lie can travel halfway around the world before the truth can get its boots on", and the same goes for gossip. Key storage has become increasingly important as more of our lives move online, to the extent that password managers have become almost a requirement for keeping track of our digital lives. But even with good password management, credentials frequently end up for sale on the dark web as a consequence of poorly secured infrastructure.
Apart from the fact that all of this is an argument for cryptographic identities (since keys are shared with far fewer parties), it's also true that the danger of losing a cryptographic key is severe, especially if that key is used in multiple places. Instead of hackers stealing your Facebook password, they might end up with access to all your other social media accounts too!
Keys should be treated with the utmost care. Using password managers is a good start, but very valuable keys should be stored even more securely - for example in a hardware signing device. This is a hassle, and something additional to learn, but is an indispensable part of taking advantage of the benefits associated with cryptographic identity.
There are ways to lessen the impact of lost or stolen secrets, however. Lots of different techniques exist for structuring key systems in such a way that keys can be protected, invalidated, or limited. Here are a few:
- Hierarchical Deterministic Keys allow for the creation of a single root key from which multiple child keys can be generated. These keys are hard to link to the parent, which provides additional privacy, but this link can also be proven when necessary. One limitation is that the identity system has to be designed with HD keys in mind.
- Key Rotation allows keys to become expendable. Additional credentials might be attached to a key, allowing the holder to prove they have the right to rotate the key. Social attestations can help with the process as well if the key is embedded in a web of trust.
- Remote Signing is a technique for storing a key on one device, but using it on another. This might take the form of signing using a hardware wallet and transferring an SD card to your computer for broadcasting, or using a mobile app like Amber to manage sessions with different applications.
- Key sharding takes this to another level by breaking a single key into multiple pieces and storing them separately. A coordinator can then be used to collaboratively sign messages without sharing key material. This dramatically reduces the ability of an attacker to steal a complete key.
Multi-Factor Authentication
One method for helping users secure their accounts that is becoming increasingly common is "multi-factor authentication". Instead of just providing your email and password, platforms send a one-time use code to your phone number or email, or use "time-based one time passwords" which are stored in a password manager or on a hardware device.
Again, MFA is a solution to a problem inherent in account-based authentication which would not be nearly so prevalent in a cryptographic identity system. Still, theft of keys does happen, and so MFA would be an important improvement - if not for an extra layer of authentication, then as a basis for key rotation.
In a sense, MFA is already being researched - key shards is one way of creating multiple credentials from a single key. However, this doesn't address the issue of key rotation, especially when an identity is tied to the public key that corresponds to a given private key. There are two possible solutions to this problem:
- Introduce a naming system. This would allow identities to use a durable name, assigning it to different keys over time. The downside is that this would require the introduction of either centralized naming authorities (back to the old model), or a blockchain in order to solve Zooko's trilemma.
- Establish a chain of keys. This would require a given key to name a successor key in advance and self-invalidate, or some other process like social recovery to invalidate an old key and assign the identity to a new one. This also would significantly increase the complexity of validating messages and associating them with a given identity.
Both solutions are workable, but introduce a lot of complexity that could cause more trouble than it's worth, depending on the identity system we're talking about.
Surveillance
One of the nice qualities that systems based on cryptographic identities have is that digitally signed data can be passed through any number of untrusted systems and emerge intact. This ability to resist tampering makes it possible to broadcast signed data more widely than would otherwise be the case in a system that relies on a custodian to authenticate information.
The downside of this is that more untrusted systems have access to data. And if information is broadcast publicly, anyone can get access to it.
This problem is compounded by re-use of cryptographic identities across multiple contexts. A benefit of self-issued credentials is that it becomes possible to bring everything attached to your identity with you, including social context and attached credentials. This is convenient and can be quite powerful, but it also means that more context is attached to your activity, making it easier to infer information about you for advertising or surveillance purposes. This is dangerously close to the dystopian ideal of a "Digital ID".
The best way to deal with this risk is to consider identity re-use an option to be used when desirable, but to default to creating a new key for every identity you create. This is no worse than the status quo, and it makes room for the ability to link identities when desired.
Another possible approach to this problem is to avoid broadcasting signed data when possible. This could be done by obscuring your cryptographic identity when data is served from a database, or by encrypting your signed data in order to selectively share it with named counterparties.
Still, this is a real risk, and should be kept in mind when designing and using systems based on cryptographic identity. If you'd like to read more about this, please see this blog post.
Making Keys Usable
You might be tempted to look at that list of trade-offs and get the sense that cryptographic identity is not for mere mortals. Key management is hard, and footguns abound - but there is a way forward. With nostr, some new things are happening in the world of key management that have never really happened before.
Plenty of work over the last 30 years has gone into making key management tractable, but none have really been widely adopted. The reason for this is simple: network effect.
Many of these older key systems only applied the thinnest veneer of humanity over keys. But an identity is much richer than a mere label. Having a real name, social connections, and a corpus of work to attach to a key creates a system of keys that humans care about.
By bootstrapping key management within a social context, nostr ensures that the payoff of key management is worth the learning curve. Not only is social engagement a strong incentive to get off the ground, people already on the network are eager to help you get past any roadblocks you might face.
So if I could offer an action item: give nostr a try today. Whether you're in it for the people and their values, or you just want to experiment with cryptographic identity, nostr is a great place to start. For a quick introduction and to securely generate keys, visit njump.me.
Thanks for taking the time to read this post. I hope it's been helpful, and I can't wait to see you on nostr!
-
 @ 460c25e6:ef85065c
2025-02-25 15:20:39
@ 460c25e6:ef85065c
2025-02-25 15:20:39If you don't know where your posts are, you might as well just stay in the centralized Twitter. You either take control of your relay lists, or they will control you. Amethyst offers several lists of relays for our users. We are going to go one by one to help clarify what they are and which options are best for each one.
Public Home/Outbox Relays
Home relays store all YOUR content: all your posts, likes, replies, lists, etc. It's your home. Amethyst will send your posts here first. Your followers will use these relays to get new posts from you. So, if you don't have anything there, they will not receive your updates.
Home relays must allow queries from anyone, ideally without the need to authenticate. They can limit writes to paid users without affecting anyone's experience.
This list should have a maximum of 3 relays. More than that will only make your followers waste their mobile data getting your posts. Keep it simple. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of all your content in a place no one can delete. Go to relay.tools and never be censored again. - 1 really fast relay located in your country: paid options like http://nostr.wine are great
Do not include relays that block users from seeing posts in this list. If you do, no one will see your posts.
Public Inbox Relays
This relay type receives all replies, comments, likes, and zaps to your posts. If you are not getting notifications or you don't see replies from your friends, it is likely because you don't have the right setup here. If you are getting too much spam in your replies, it's probably because your inbox relays are not protecting you enough. Paid relays can filter inbox spam out.
Inbox relays must allow anyone to write into them. It's the opposite of the outbox relay. They can limit who can download the posts to their paid subscribers without affecting anyone's experience.
This list should have a maximum of 3 relays as well. Again, keep it small. More than that will just make you spend more of your data plan downloading the same notifications from all these different servers. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of your notifications, invites, cashu tokens and zaps. - 1 really fast relay located in your country: go to nostr.watch and find relays in your country
Terrible options include: - nostr.wine should not be here. - filter.nostr.wine should not be here. - inbox.nostr.wine should not be here.
DM Inbox Relays
These are the relays used to receive DMs and private content. Others will use these relays to send DMs to you. If you don't have it setup, you will miss DMs. DM Inbox relays should accept any message from anyone, but only allow you to download them.
Generally speaking, you only need 3 for reliability. One of them should be a personal relay to make sure you have a copy of all your messages. The others can be open if you want push notifications or closed if you want full privacy.
Good options are: - inbox.nostr.wine and auth.nostr1.com: anyone can send messages and only you can download. Not even our push notification server has access to them to notify you. - a personal relay to make sure no one can censor you. Advanced settings on personal relays can also store your DMs privately. Talk to your relay operator for more details. - a public relay if you want DM notifications from our servers.
Make sure to add at least one public relay if you want to see DM notifications.
Private Home Relays
Private Relays are for things no one should see, like your drafts, lists, app settings, bookmarks etc. Ideally, these relays are either local or require authentication before posting AND downloading each user\'s content. There are no dedicated relays for this category yet, so I would use a local relay like Citrine on Android and a personal relay on relay.tools.
Keep in mind that if you choose a local relay only, a client on the desktop might not be able to see the drafts from clients on mobile and vice versa.
Search relays:
This is the list of relays to use on Amethyst's search and user tagging with @. Tagging and searching will not work if there is nothing here.. This option requires NIP-50 compliance from each relay. Hit the Default button to use all available options on existence today: - nostr.wine - relay.nostr.band - relay.noswhere.com
Local Relays:
This is your local storage. Everything will load faster if it comes from this relay. You should install Citrine on Android and write ws://localhost:4869 in this option.
General Relays:
This section contains the default relays used to download content from your follows. Notice how you can activate and deactivate the Home, Messages (old-style DMs), Chat (public chats), and Global options in each.
Keep 5-6 large relays on this list and activate them for as many categories (Home, Messages (old-style DMs), Chat, and Global) as possible.
Amethyst will provide additional recommendations to this list from your follows with information on which of your follows might need the additional relay in your list. Add them if you feel like you are missing their posts or if it is just taking too long to load them.
My setup
Here's what I use: 1. Go to relay.tools and create a relay for yourself. 2. Go to nostr.wine and pay for their subscription. 3. Go to inbox.nostr.wine and pay for their subscription. 4. Go to nostr.watch and find a good relay in your country. 5. Download Citrine to your phone.
Then, on your relay lists, put:
Public Home/Outbox Relays: - nostr.wine - nos.lol or an in-country relay. -
.nostr1.com Public Inbox Relays - nos.lol or an in-country relay -
.nostr1.com DM Inbox Relays - inbox.nostr.wine -
.nostr1.com Private Home Relays - ws://localhost:4869 (Citrine) -
.nostr1.com (if you want) Search Relays - nostr.wine - relay.nostr.band - relay.noswhere.com
Local Relays - ws://localhost:4869 (Citrine)
General Relays - nos.lol - relay.damus.io - relay.primal.net - nostr.mom
And a few of the recommended relays from Amethyst.
Final Considerations
Remember, relays can see what your Nostr client is requesting and downloading at all times. They can track what you see and see what you like. They can sell that information to the highest bidder, they can delete your content or content that a sponsor asked them to delete (like a negative review for instance) and they can censor you in any way they see fit. Before using any random free relay out there, make sure you trust its operator and you know its terms of service and privacy policies.
-
 @ 16f1a010:31b1074b
2025-02-19 20:57:59
@ 16f1a010:31b1074b
2025-02-19 20:57:59In the rapidly evolving world of Bitcoin, running a Bitcoin node has become more accessible than ever. Platforms like Umbrel, Start9, myNode, and Citadel offer user-friendly interfaces to simplify node management. However, for those serious about maintaining a robust and efficient Lightning node ⚡, relying solely on these platforms may not be the optimal choice.
Let’s delve into why embracing Bitcoin Core and mastering the command-line interface (CLI) can provide a more reliable, sovereign, and empowering experience.
Understanding Node Management Platforms
What Are Umbrel, Start9, myNode, and Citadel?
Umbrel, Start9, myNode, and Citadel are platforms designed to streamline the process of running a Bitcoin node. They offer graphical user interfaces (GUIs) that allow users to manage various applications, including Bitcoin Core and Lightning Network nodes, through a web-based dashboard 🖥️.
These platforms often utilize Docker containers 🐳 to encapsulate applications, providing a modular and isolated environment for each service.

The Appeal of Simplified Node Management
The primary allure of these platforms lies in their simplicity. With minimal command-line interaction, users can deploy a full Bitcoin and Lightning node, along with a suite of additional applications.
✅ Easy one-command installation
✅ Web-based GUI for management
✅ Automatic app updates (but with delays, as we’ll discuss)However, while this convenience is attractive, it comes at a cost.
The Hidden Complexities of Using Node Management Platforms
While the user-friendly nature of these platforms is advantageous, it can also introduce several challenges that may hinder advanced users or those seeking greater control over their nodes.
🚨 Dependency on Maintainers for Updates
One significant concern is the reliance on platform maintainers for updates. Since these platforms manage applications through Docker containers, users must wait for the maintainers to update the container images before they can access new features or security patches.
🔴 Delayed Bitcoin Core updates = potential security risks
🔴 Lightning Network updates are not immediate
🔴 Bugs and vulnerabilities may persist longerInstead of waiting on a third party, why not update Bitcoin Core & LND yourself instantly?
⚙️ Challenges in Customization and Advanced Operations
For users aiming to perform advanced operations, such as:
- Custom backups 📂
- Running specific CLI commands 🖥️
- Optimizing node settings ⚡
…the abstraction layers introduced by these platforms become obstacles.
Navigating through nested directories and issuing commands inside Docker containers makes troubleshooting a nightmare. Instead of a simple
bitcoin-clicommand, you must figure out how to execute it inside the container, adding unnecessary complexity.Increased Backend Complexity
To achieve frontend simplicity, these platforms make the backend more complex.
🚫 Extra layers of abstraction
🚫 Hidden logs and settings
🚫 Harder troubleshootingThe use of multiple Docker containers, custom scripts, and unique file structures can make system maintenance and debugging a pain.
This complication defeats the purpose of “making running a node easy.”
✅ Advantages of Using Bitcoin Core and Command-Line Interface (CLI)
By installing Bitcoin Core directly and using the command-line interface (CLI), you gain several key advantages that make managing a Bitcoin and Lightning node more efficient and empowering.
Direct Control and Immediate Updates
One of the biggest downsides of package manager-based platforms is the reliance on third-party maintainers to release updates. Since Bitcoin Core, Lightning implementations (such as LND, Core Lightning, or Eclair), and other related software evolve rapidly, waiting for platform-specific updates can leave you running outdated or vulnerable versions.
By installing Bitcoin Core directly, you remove this dependency. You can update immediately when new versions are released, ensuring your node benefits from the latest features, security patches, and bug fixes. The same applies to Lightning software—being able to install and update it yourself gives you full autonomy over your node’s performance and security.
🛠 Simplified System Architecture
Platforms like Umbrel and myNode introduce extra complexity by running Bitcoin Core and Lightning inside Docker containers. This means:
- The actual files and configurations are stored inside Docker’s filesystem, making it harder to locate and manage them manually.
- If something breaks, troubleshooting is more difficult due to the added layer of abstraction.
- Running commands requires jumping through Docker shell sessions, adding unnecessary friction to what should be a straightforward process.
Instead, a direct installation of Bitcoin Core, Lightning, and Electrum Server (if needed) results in a cleaner, more understandable system. The software runs natively on your machine, without containerized layers making things more convoluted.
Additionally, setting up your own systemd service files for Bitcoin and Lightning is not as complicated as it seems. Once configured, these services will run automatically on boot, offering the same level of convenience as platforms like Umbrel but without the unnecessary complexity.
Better Lightning Node Management
If you’re running a Lightning Network node, using CLI-based tools provides far more flexibility than relying on a GUI like the ones bundled with node management platforms.
🟢 Custom Backup Strategies – Running Lightning through a GUI-based node manager often means backups are handled in a way that is opaque to the user. With CLI tools, you can easily script automatic backups of your channels, wallets, and configurations.
🟢 Advanced Configuration – Platforms like Umbrel force certain configurations by default, limiting how you can customize your Lightning node. With a direct install, you have full control over: * Channel fees 💰 * Routing policies 📡 * Liquidity management 🔄
🟢 Direct Access to LND, Core Lightning, or Eclair – Instead of issuing commands through a GUI (which is often limited in functionality), you can use: *
lncli(for LND) *lightning-cli(for Core Lightning) …to interact with your node at a deeper level.Enhanced Learning and Engagement
A crucial aspect of running a Bitcoin and Lightning node is understanding how it works.
Using an abstraction layer like Umbrel may get a node running in a few clicks, but it does little to teach users how Bitcoin actually functions.
By setting up Bitcoin Core, Lightning, and related software manually, you will:
✅ Gain practical knowledge of Bitcoin nodes, networking, and system performance.
✅ Learn how to configure and manage RPC commands.
✅ Become less reliant on third-party developers and more confident in troubleshooting.🎯 Running a Bitcoin node is about sovereignty – learn how to control it yourself.
Become more sovereign TODAY
Many guides make this process straightforward K3tan has a fantastic guide on running Bitcoin Core, Electrs, LND and more.
- Ministry of Nodes Guide 2024
- You can find him on nostr
nostr:npub1txwy7guqkrq6ngvtwft7zp70nekcknudagrvrryy2wxnz8ljk2xqz0yt4xEven with the best of guides, if you are running this software,
📖 READ THE DOCUMENTATIONThis is all just software at the end of the day. Most of it is very well documented. Take a moment to actually read through the documentation for yourself when installing. The documentation has step by step guides on setting up the software. Here is a helpful list: * Bitcoin.org Bitcoin Core Linux install instructions * Bitcoin Core Code Repository * Electrs Installation * LND Documentation * LND Code Repository * CLN Documentation * CLN Code Repository
If you have any more resources or links I should add, please comment them . I want to add as much to this article as I can.
-
 @ ed5774ac:45611c5c
2025-02-15 05:38:56
@ ed5774ac:45611c5c
2025-02-15 05:38:56Bitcoin as Collateral for U.S. Debt: A Deep Dive into the Financial Mechanics
The U.S. government’s proposal to declare Bitcoin as a 'strategic reserve' is a calculated move to address its unsustainable debt obligations, but it threatens to undermine Bitcoin’s original purpose as a tool for financial freedom. To fully grasp the implications of this plan, we must first understand the financial mechanics of debt creation, the role of collateral in sustaining debt, and the historical context of the petro-dollar system. Additionally, we must examine how the U.S. and its allies have historically sought new collateral to back their debt, including recent attempts to weaken Russia through the Ukraine conflict.
The Vietnam War and the Collapse of the Gold Standard
The roots of the U.S. debt crisis can be traced back to the Vietnam War. The war created an unsustainable budget deficit, forcing the U.S. to borrow heavily to finance its military operations. By the late 1960s, the U.S. was spending billions of dollars annually on the war, leading to a significant increase in public debt. Foreign creditors, particularly France, began to lose confidence in the U.S. dollar’s ability to maintain its value. In a dramatic move, French President Charles de Gaulle sent warships to New York to demand the conversion of France’s dollar reserves into gold, as per the Bretton Woods Agreement.
This demand exposed the fragility of the U.S. gold reserves. By 1971, President Richard Nixon was forced to suspend the dollar’s convertibility to gold, effectively ending the Bretton Woods system. This move, often referred to as the "Nixon Shock," declared the U.S. bankrupt and transformed the dollar into a fiat currency backed by nothing but trust in the U.S. government. The collapse of the gold standard marked the beginning of the U.S.’s reliance on artificial systems to sustain its debt. With the gold standard gone, the U.S. needed a new way to back its currency and debt—a need that would lead to the creation of the petro-dollar system.
The Petro-Dollar System: A New Collateral for Debt
In the wake of the gold standard’s collapse, the U.S. faced a critical challenge: how to maintain global confidence in the dollar and sustain its ability to issue debt. The suspension of gold convertibility in 1971 left the dollar as a fiat currency—backed by nothing but trust in the U.S. government. To prevent a collapse of the dollar’s dominance and ensure its continued role as the world’s reserve currency, the U.S. needed a new system to artificially create demand for dollars and provide a form of indirect backing for its debt.
The solution came in the form of the petro-dollar system. In the 1970s, the U.S. struck a deal with Saudi Arabia and other OPEC nations to price oil exclusively in U.S. dollars. In exchange, the U.S. offered military protection and economic support. This arrangement created an artificial demand for dollars, as countries needed to hold USD reserves to purchase oil. Additionally, oil-exporting nations reinvested their dollar revenues in U.S. Treasuries, effectively recycling petro-dollars back into the U.S. economy. This recycling of petrodollars provided the U.S. with a steady inflow of capital, allowing it to finance its deficits and maintain low interest rates.
To further bolster the system, the U.S., under the guidance of Henry Kissinger, encouraged OPEC to dramatically increase oil prices in the 1970s. The 1973 oil embargo and subsequent price hikes, masterminded by Kissinger, quadrupled the cost of oil, creating a windfall for oil-exporting nations. These nations, whose wealth surged significantly due to the rising oil prices, reinvested even more heavily in U.S. Treasuries and other dollar-denominated assets. This influx of petrodollars increased demand for U.S. debt, enabling the U.S. to issue more debt at lower interest rates. Additionally, the appreciation in the value of oil—a critical global commodity—provided the U.S. banking sector with the necessary collateral to expand credit generation. Just as a house serves as collateral for a mortgage, enabling banks to create new debt, the rising value of oil boosted the asset values of Western corporations that owned oil reserves or invested in oil infrastructure projects. This increase in asset values allowed these corporations to secure larger loans, providing banks with the collateral needed to expand credit creation and inject more dollars into the economy. However, these price hikes also caused global economic turmoil, disproportionately affecting developing nations. As the cost of energy imports skyrocketed, these nations faced mounting debt burdens, exacerbating their economic struggles and deepening global inequality.
The Unsustainable Debt Crisis and the Search for New Collateral
Fast forward to the present day, and the U.S. finds itself in a familiar yet increasingly precarious position. The 2008 financial crisis and the 2020 pandemic have driven the U.S. government’s debt to unprecedented levels, now exceeding $34 trillion, with a debt-to-GDP ratio surpassing 120%. At the same time, the petro-dollar system—the cornerstone of the dollar’s global dominance—is under significant strain. The rise of alternative currencies and the shifting power dynamics of a multipolar world have led to a decline in the dollar’s role in global trade, particularly in oil transactions. For instance, China now pays Saudi Arabia in yuan for oil imports, while Russia sells its oil and gas in rubles and other non-dollar currencies. This growing defiance of the dollar-dominated system reflects a broader trend toward economic independence, as nations like China and Russia seek to reduce their reliance on the U.S. dollar. As more countries bypass the dollar in trade, the artificial demand for dollars created by the petro-dollar system is eroding, undermining the ability of US to sustain its debt and maintain global financial hegemony.
In search of new collateral to carry on its unsustainable debt levels amid declining demand for the U.S. dollar, the U.S., together with its Western allies—many of whom face similar sovereign debt crises—first attempted to weaken Russia and exploit its vast natural resources as collateral. The U.S. and its NATO allies used Ukraine as a proxy to destabilize Russia, aiming to fragment its economy, colonize its territory, and seize control of its natural resources, estimated to be worth around $75 trillion. By gaining access to these resources, the West could have used them as collateral for the banking sector, enabling massive credit expansion. This, in turn, would have alleviated the sovereign debt crisis threatening both the EU and the U.S. This plan was not unprecedented; it mirrored France’s long-standing exploitation of its former African colonies through the CFA franc system.
For decades, France has maintained economic control over 14 African nations through the CFA franc, a currency pegged to the euro and backed by the French Treasury. Under this system, these African countries are required to deposit 50% of their foreign exchange reserves into the French Treasury, effectively giving France control over their monetary policy and economic sovereignty. This arrangement allows France to use African resources and reserves as implicit collateral to issue debt, keeping its borrowing costs low and ensuring demand for its bonds. In return, African nations are left with limited control over their own economies, forced to prioritize French interests over their own development. This neo-colonial system has enabled France to sustain its financial dominance while perpetuating poverty and dependency in its former colonies.
Just as France’s CFA franc system relies on the economic subjugation of African nations to sustain its financial dominance, the U.S. had hoped to use Russia’s resources as a lifeline for its debt-ridden economy. However, the plan ultimately failed. Russia not only resisted the sweeping economic sanctions imposed by the West but also decisively defeated NATO’s proxy forces in Ukraine, thwarting efforts to fragment its economy and seize control of its $75 trillion in natural resources. This failure left the U.S. and its allies without a new source of collateral to back their unsustainable debt levels. With this plan in ruins, the U.S. has been forced to turn its attention to Bitcoin as a potential new collateral for its unsustainable debt.
Bitcoin as Collateral: The U.S. Government’s Plan
The U.S. government’s plan to declare Bitcoin as a strategic reserve is a modern-day equivalent of the gold standard or petro-dollar system. Here’s how it would work:
-
Declaring Bitcoin as a Strategic Reserve: By officially recognizing Bitcoin as a reserve asset, the U.S. would signal to the world that it views Bitcoin as a store of value akin to gold. This would legitimize Bitcoin in the eyes of institutional investors and central banks.
-
Driving Up Bitcoin’s Price: To make Bitcoin a viable collateral, its price must rise significantly. The U.S. would achieve this by encouraging regulatory clarity, promoting institutional adoption, and creating a state-driven FOMO (fear of missing out). This would mirror the 1970s oil price hikes that bolstered the petro-dollar system.
-
Using Bitcoin to Back Debt: Once Bitcoin’s price reaches a sufficient level, the U.S. could use its Bitcoin reserves as collateral for issuing new debt. This would restore confidence in U.S. Treasuries and allow the government to continue borrowing at low interest rates.
The U.S. government’s goal is clear: to use Bitcoin as a tool to issue more debt and reinforce the dollar’s role as the global reserve currency. By forcing Bitcoin into a store-of-value role, the U.S. would replicate the gold standard’s exploitative dynamics, centralizing control in the hands of large financial institutions and central banks. This would strip Bitcoin of its revolutionary potential and undermine its promise of decentralization. Meanwhile, the dollar—in digital forms like USDT—would remain the primary medium of exchange, further entrenching the parasitic financial system.
Tether plays a critical role in this strategy. As explored in my previous article (here: [https://ersan.substack.com/p/is-tether-a-bitcoin-company]), Tether helps sustaining the current financial system by purchasing U.S. Treasuries, effectively providing life support for the U.S. debt machine during a period of declining demand for dollar-denominated assets. Now, with its plans to issue stablecoins on the Bitcoin blockchain, Tether is positioning itself as a bridge between Bitcoin and the traditional financial system. By issuing USDT on the Lightning Network, Tether could lure the poor in developing nations—who need short-term price stability for their day to day payments and cannot afford Bitcoin’s volatility—into using USDT as their primary medium of exchange. This would not only create an artificial demand for the dollar and extend the life of the parasitic financial system that Bitcoin was designed to dismantle but would also achieve this by exploiting the very people who have been excluded and victimized by the same system—the poor and unbanked in developing nations, whose hard-earned money would be funneled into sustaining the very structures that perpetuate their oppression.
Worse, USDT on Bitcoin could function as a de facto central bank digital currency (CBDC), where all transactions can be monitored and sanctioned by governments at will. For example, Tether’s centralized control over USDT issuance and its ties to traditional financial institutions make it susceptible to government pressure. Authorities could compel Tether to implement KYC (Know Your Customer) rules, freeze accounts, or restrict transactions, effectively turning USDT into a tool of financial surveillance and control. This would trap users in a system where every transaction is subject to government oversight, effectively stripping Bitcoin of its censorship-resistant and decentralized properties—the very features that make it a tool for financial freedom.
In this way, the U.S. government’s push for Bitcoin as a store of value, combined with Tether’s role in promoting USDT as a medium of exchange, creates a two-tiered financial system: one for the wealthy, who can afford to hold Bitcoin as a hedge against inflation, and another for the poor, who are trapped in a tightly controlled, surveilled digital economy. This perpetuates the very inequalities Bitcoin was designed to dismantle, turning it into a tool of oppression rather than liberation.
Conclusion: Prolonging the Parasitic Financial System
The U.S. government’s plan to declare Bitcoin as a strategic reserve is not a step toward financial innovation or freedom—it is a desperate attempt to prolong the life of a parasitic financial system that Bitcoin was created to replace. By co-opting Bitcoin, the U.S. would gain a new tool to issue more debt, enabling it to continue its exploitative practices, including proxy wars, economic sanctions, and the enforcement of a unipolar world order.
The petro-dollar system was built on the exploitation of oil-exporting nations and the global economy. A Bitcoin-backed system would likely follow a similar pattern, with the U.S. using its dominance to manipulate Bitcoin’s price and extract value from the rest of the world. This would allow the U.S. to sustain its current financial system, in which it prints money out of thin air to purchase real-world assets and goods, enriching itself at the expense of other nations.
Bitcoin was designed to dismantle this parasitic system, offering an escape hatch for those excluded from or exploited by traditional financial systems. By declaring Bitcoin a strategic reserve, the U.S. government would destroy Bitcoin’s ultimate purpose, turning it into another instrument of control. This is not a victory for Bitcoin or bitcoiners—it is a tragedy for financial freedom and global equity.
The Bitcoin strategic reserve plan is not progress—it is a regression into the very system Bitcoin was designed to dismantle. As bitcoiners, we must resist this co-option and fight to preserve Bitcoin’s original vision: a decentralized, sovereign, and equitable financial system for all. This means actively working to ensure Bitcoin is used as a medium of exchange, not just a store of value, to fulfill its promise of financial freedom.
-
-
 @ f4db5270:3c74e0d0
2025-01-23 18:09:14
@ f4db5270:3c74e0d0
2025-01-23 18:09:14Hi Art lover! 🎨🫂💜 You may not know it yet but all of the following paintings are available in #Bitcoin on my website: https://isolabell.art/#shop
For info and prices write to me in DM and we will find a good deal! 🤝
 ON THE ROAD AGAIN
40x50cm, Oil on canvas
Completed January 23, 2025
ON THE ROAD AGAIN
40x50cm, Oil on canvas
Completed January 23, 2025
 SUN OF JANUARY
40x50cm, Oil on canvas
Completed January 14, 2025
SUN OF JANUARY
40x50cm, Oil on canvas
Completed January 14, 2025
 THE BLUE HOUR
40x50cm, Oil on canvas
Completed December 14, 2024
THE BLUE HOUR
40x50cm, Oil on canvas
Completed December 14, 2024
 LIKE A FRAGMENT OF ETERNITY
50x40cm, Oil on canvas
Completed December 01, 2024
LIKE A FRAGMENT OF ETERNITY
50x40cm, Oil on canvas
Completed December 01, 2024
 WHERE WINTER WHISPERS
50x40cm, Oil on canvas
Completed November 07, 2024
WHERE WINTER WHISPERS
50x40cm, Oil on canvas
Completed November 07, 2024
 L'ATTESA DI UN MOMENTO
40x40cm, Oil on canvas
Completed October 29, 2024
L'ATTESA DI UN MOMENTO
40x40cm, Oil on canvas
Completed October 29, 2024
 LE COSE CHE PENSANO
40x50cm, Oil on paper
Completed October 05, 2024
LE COSE CHE PENSANO
40x50cm, Oil on paper
Completed October 05, 2024
 TWILIGHT'S RIVER
50x40cm, Oil on canvas
Completed September 17, 2024
TWILIGHT'S RIVER
50x40cm, Oil on canvas
Completed September 17, 2024
 GOLD ON THE OCEAN
40x50cm, Oil on paper
Completed September 08, 2024
GOLD ON THE OCEAN
40x50cm, Oil on paper
Completed September 08, 2024
 SUSSURRI DI CIELO E MARE
50x40cm, Oil on paper
Completed September 05, 2024
SUSSURRI DI CIELO E MARE
50x40cm, Oil on paper
Completed September 05, 2024
 THE END OF A WONDERFUL WEEKEND
40x30cm, Oil on board
Completed August 12, 2024
THE END OF A WONDERFUL WEEKEND
40x30cm, Oil on board
Completed August 12, 2024
 FIAMME NEL CIELO
60x35cm, Oil on board
Completed July 28, 2024
FIAMME NEL CIELO
60x35cm, Oil on board
Completed July 28, 2024
 INIZIO D'ESTATE
50x40cm, Oil on cradled wood panel
Completed July 13, 2024
INIZIO D'ESTATE
50x40cm, Oil on cradled wood panel
Completed July 13, 2024
 OMBRE DELLA SERA
50x40cm, Oil on cradled wood panel
Completed June 16, 2024
OMBRE DELLA SERA
50x40cm, Oil on cradled wood panel
Completed June 16, 2024
 NEW ZEALAND SUNSET
80x60cm, Oil on canvas board
Completed May 28, 2024
NEW ZEALAND SUNSET
80x60cm, Oil on canvas board
Completed May 28, 2024
 VENICE
50x40cm, Oil on board
Completed May 4, 2024
VENICE
50x40cm, Oil on board
Completed May 4, 2024
 CORNWALL
50x40cm, Oil on board
Completed April 26, 2024
CORNWALL
50x40cm, Oil on board
Completed April 26, 2024
 DOCKS ON SUNSET
40x19,5cm, Oil on board
Completed March 14, 2024
DOCKS ON SUNSET
40x19,5cm, Oil on board
Completed March 14, 2024
 SOLITUDE
30x30cm, Oil on cradled wood panel
Completed March 2, 2024
SOLITUDE
30x30cm, Oil on cradled wood panel
Completed March 2, 2024
 LULLING WAVES
40x30cm, Oil on cradled wood panel
Completed January 14, 2024
LULLING WAVES
40x30cm, Oil on cradled wood panel
Completed January 14, 2024
 MULATTIERA IN AUTUNNO
30x30cm, Oil on cradled wood panel
MULATTIERA IN AUTUNNO
30x30cm, Oil on cradled wood panel
 TRAMONTO A KOS
40x40cm, oil on board canvas
TRAMONTO A KOS
40x40cm, oil on board canvas
 HIDDEN SMILE
40x40cm, oil on board
HIDDEN SMILE
40x40cm, oil on board
 INIZIO D'AUTUNNO
40x40cm, oil on canvas
INIZIO D'AUTUNNO
40x40cm, oil on canvas
 BOE NEL LAGO
30x30cm, oil on canvas board
BOE NEL LAGO
30x30cm, oil on canvas board
 BARCHE A RIPOSO
40x40cm, oil on canvas board
BARCHE A RIPOSO
40x40cm, oil on canvas board
 IL RISVEGLIO
30x40cm, oil on canvas board
IL RISVEGLIO
30x40cm, oil on canvas board
 LA QUIETE PRIMA DELLA TEMPESTA
30x40cm, oil on canvas board
LA QUIETE PRIMA DELLA TEMPESTA
30x40cm, oil on canvas board
 LAMPIONE SUL LAGO
30x30cm, oil on canvas board
LAMPIONE SUL LAGO
30x30cm, oil on canvas board
 DUE NELLA NEVE
60x25cm, oil on board
DUE NELLA NEVE
60x25cm, oil on board
 UNA CAREZZA
30x30cm, oil on canvas board
UNA CAREZZA
30x30cm, oil on canvas board
 REBEL WAVES
44x32cm, oil on canvas board
REBEL WAVES
44x32cm, oil on canvas board
 THE SCREAMING WAVE
40x30cm, oil on canvas board
THE SCREAMING WAVE
40x30cm, oil on canvas board
 "LA DONZELLETTA VIEN DALLA CAMPAGNA..."
30x40cm, oil on canvas board
"LA DONZELLETTA VIEN DALLA CAMPAGNA..."
30x40cm, oil on canvas board
 LIGHTHOUSE ON WHITE CLIFF
30x40cm, oil on canvas board
LIGHTHOUSE ON WHITE CLIFF
30x40cm, oil on canvas board -
 @ ac58bbcc:7d9754d8
2025-04-04 20:13:12
@ ac58bbcc:7d9754d8
2025-04-04 20:13:12Lovely seeing you here. Hello there, and welcome to our very first post! We’re the team behind Math Success by DMTI, and we’re thrilled for this journey with you. If you’re a teacher, parent, or just someone who cares about kids and learning, you’ve probably noticed something: math education isn’t working well for most everyone. Too many students dread it, too many teachers feel stuck, and too many classrooms are stuck in a cycle of rote memorization that leaves most everyone uninspired.
We’re here to change that—and that’s why we’ve built Math Success by DMTI, the leading K-6 Math Education Program.
The Problem: Math Isn’t Adding Up Let’s start with the elephant in the room. Math education often misses the mark. Kids are taught to memorize times tables or follow steps without understanding why they work. It’s like handing someone a recipe without teaching them how to cook—they might make the dish, but they won’t know what to do when the ingredients change. Studies show U.S. students lag behind many peers globally in math, and the gap widens as they move through school. Why? Because we’ve prioritized procedures over meaning, drills over discovery, and compliance over curiosity.
The result? Students who see math as a chore, not a chance to explore. Teachers, meanwhile, are stretched thin—juggling standards, testing pressures, and outdated methods that don’t spark joy or learning. It’s no wonder so many kids say, “I’m just not a math person.” But here’s the thing: we believe everyone can be a math person—if we teach it right.
Our Solution: Math Success by DMTI That’s where Math Success by DMTI comes in. Born from the Developing Mathematical Thinking Institute and over 40 years of research, our program isn’t just another curriculum—it’s a rethink of how math should feel and function in the classroom. We’ve seen the data: classrooms using our approach see an average 35% jump in achievement. But more than that, they see kids who love math and teachers who can’t wait to teach it.
So, how do we do it? It starts with our Developing Mathematical Thinking framework—a five-part recipe for success:
Listen to Kids & Build on Their Ideas: We build on what students already know, making math personal and relevant.
Speak the Right Language: We use the structural words unit, compose, decompose, iterate, partition, and equal to help kids communicate and connect to math across topics.
Understand First, Calculate Later: Concepts come before procedures, so kids grasp the “why” before the “how.”
Models and real-world connections: From blocks to drawings to numbers, we use models to make math tangible and fun while helping connect math to real life.
Embrace Misconceptions & Mistakes: Missteps aren’t failures but chances to learn and grow.
This isn’t the math you grew up with. It’s active, engaging, and built to stick. Teachers tell us it’s a game-changer—“I have never loved teaching math as much as I do now; math has come alive in my classroom. My students are further along now than any class I’ve ever taught before.” one said, “I could see the light bulbs going off like never before, and they’re excited!” Kids tell us, “Math is fun now!” And the numbers back it up: that 35% boost isn’t just a stat—it’s a sign of deeper understanding and real confidence.
Why it matters Math isn’t just about numbers; it’s about thinking, solving problems, and opening doors. When kids succeed in math, they gain skills for life—whether they’re headed to STEM careers or just figuring out their budget. But beyond that, we want them to love it. To see math as a playground, not a prison. That’s our mission: successful learning and a genuine love for mathematics, one classroom at a time.
What’s Next? This Substack is our space to share that mission with you. Expect stories from teachers and students, dives into our framework, tips for bringing math to life, and updates on our free courses (yep, free!). We’re partnering with educators like you to make this happen—because we can turn math education around together.
So, stick with us. Subscribe below, drop a comment with your thoughts, and start building a world where math adds joy, not stress. Welcome to Math Success by DMTI—let’s make math work for everyone.
-
 @ eac63075:b4988b48
2025-01-04 19:41:34
@ eac63075:b4988b48
2025-01-04 19:41:34Since its creation in 2009, Bitcoin has symbolized innovation and resilience. However, from time to time, alarmist narratives arise about emerging technologies that could "break" its security. Among these, quantum computing stands out as one of the most recurrent. But does quantum computing truly threaten Bitcoin? And more importantly, what is the community doing to ensure the protocol remains invulnerable?
The answer, contrary to sensationalist headlines, is reassuring: Bitcoin is secure, and the community is already preparing for a future where quantum computing becomes a practical reality. Let’s dive into this topic to understand why the concerns are exaggerated and how the development of BIP-360 demonstrates that Bitcoin is one step ahead.
What Is Quantum Computing, and Why Is Bitcoin Not Threatened?
Quantum computing leverages principles of quantum mechanics to perform calculations that, in theory, could exponentially surpass classical computers—and it has nothing to do with what so-called “quantum coaches” teach to scam the uninformed. One of the concerns is that this technology could compromise two key aspects of Bitcoin’s security:
- Wallets: These use elliptic curve algorithms (ECDSA) to protect private keys. A sufficiently powerful quantum computer could deduce a private key from its public key.
- Mining: This is based on the SHA-256 algorithm, which secures the consensus process. A quantum attack could, in theory, compromise the proof-of-work mechanism.
Understanding Quantum Computing’s Attack Priorities
While quantum computing is often presented as a threat to Bitcoin, not all parts of the network are equally vulnerable. Theoretical attacks would be prioritized based on two main factors: ease of execution and potential reward. This creates two categories of attacks:
1. Attacks on Wallets
Bitcoin wallets, secured by elliptic curve algorithms, would be the initial targets due to the relative vulnerability of their public keys, especially those already exposed on the blockchain. Two attack scenarios stand out:
-
Short-term attacks: These occur during the interval between sending a transaction and its inclusion in a block (approximately 10 minutes). A quantum computer could intercept the exposed public key and derive the corresponding private key to redirect funds by creating a transaction with higher fees.
-
Long-term attacks: These focus on old wallets whose public keys are permanently exposed. Wallets associated with Satoshi Nakamoto, for example, are especially vulnerable because they were created before the practice of using hashes to mask public keys.
We can infer a priority order for how such attacks might occur based on urgency and importance.
 Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)
Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)2. Attacks on Mining
Targeting the SHA-256 algorithm, which secures the mining process, would be the next objective. However, this is far more complex and requires a level of quantum computational power that is currently non-existent and far from realization. A successful attack would allow for the recalculation of all possible hashes to dominate the consensus process and potentially "mine" it instantly.
 Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin Attacks
Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin AttacksRecently, Narcelio asked me about a statement I made on Tubacast:
https://x.com/eddieoz/status/1868371296683511969
If an attack became a reality before Bitcoin was prepared, it would be necessary to define the last block prior to the attack and proceed from there using a new hashing algorithm. The solution would resemble the response to the infamous 2013 bug. It’s a fact that this would cause market panic, and Bitcoin's price would drop significantly, creating a potential opportunity for the well-informed.
Preferably, if developers could anticipate the threat and had time to work on a solution and build consensus before an attack, they would simply decide on a future block for the fork, which would then adopt the new algorithm. It might even rehash previous blocks (reaching consensus on them) to avoid potential reorganization through the re-mining of blocks using the old hash. (I often use the term "shielding" old transactions).
How Can Users Protect Themselves?
While quantum computing is still far from being a practical threat, some simple measures can already protect users against hypothetical scenarios:
- Avoid using exposed public keys: Ensure funds sent to old wallets are transferred to new ones that use public key hashes. This reduces the risk of long-term attacks.
- Use modern wallets: Opt for wallets compatible with SegWit or Taproot, which implement better security practices.
- Monitor security updates: Stay informed about updates from the Bitcoin community, such as the implementation of BIP-360, which will introduce quantum-resistant addresses.
- Do not reuse addresses: Every transaction should be associated with a new address to minimize the risk of repeated exposure of the same public key.
- Adopt secure backup practices: Create offline backups of private keys and seeds in secure locations, protected from unauthorized access.
BIP-360 and Bitcoin’s Preparation for the Future
Even though quantum computing is still beyond practical reach, the Bitcoin community is not standing still. A concrete example is BIP-360, a proposal that establishes the technical framework to make wallets resistant to quantum attacks.
BIP-360 addresses three main pillars:
- Introduction of quantum-resistant addresses: A new address format starting with "BC1R" will be used. These addresses will be compatible with post-quantum algorithms, ensuring that stored funds are protected from future attacks.
- Compatibility with the current ecosystem: The proposal allows users to transfer funds from old addresses to new ones without requiring drastic changes to the network infrastructure.
- Flexibility for future updates: BIP-360 does not limit the choice of specific algorithms. Instead, it serves as a foundation for implementing new post-quantum algorithms as technology evolves.
This proposal demonstrates how Bitcoin can adapt to emerging threats without compromising its decentralized structure.
Post-Quantum Algorithms: The Future of Bitcoin Cryptography
The community is exploring various algorithms to protect Bitcoin from quantum attacks. Among the most discussed are:
- Falcon: A solution combining smaller public keys with compact digital signatures. Although it has been tested in limited scenarios, it still faces scalability and performance challenges.
- Sphincs: Hash-based, this algorithm is renowned for its resilience, but its signatures can be extremely large, making it less efficient for networks like Bitcoin’s blockchain.
- Lamport: Created in 1977, it’s considered one of the earliest post-quantum security solutions. Despite its reliability, its gigantic public keys (16,000 bytes) make it impractical and costly for Bitcoin.
Two technologies show great promise and are well-regarded by the community:
- Lattice-Based Cryptography: Considered one of the most promising, it uses complex mathematical structures to create systems nearly immune to quantum computing. Its implementation is still in its early stages, but the community is optimistic.
- Supersingular Elliptic Curve Isogeny: These are very recent digital signature algorithms and require extensive study and testing before being ready for practical market use.
The final choice of algorithm will depend on factors such as efficiency, cost, and integration capability with the current system. Additionally, it is preferable that these algorithms are standardized before implementation, a process that may take up to 10 years.
Why Quantum Computing Is Far from Being a Threat
The alarmist narrative about quantum computing overlooks the technical and practical challenges that still need to be overcome. Among them:
- Insufficient number of qubits: Current quantum computers have only a few hundred qubits, whereas successful attacks would require millions.
- High error rate: Quantum stability remains a barrier to reliable large-scale operations.
- High costs: Building and operating large-scale quantum computers requires massive investments, limiting their use to scientific or specific applications.
Moreover, even if quantum computers make significant advancements, Bitcoin is already adapting to ensure its infrastructure is prepared to respond.
Conclusion: Bitcoin’s Secure Future
Despite advancements in quantum computing, the reality is that Bitcoin is far from being threatened. Its security is ensured not only by its robust architecture but also by the community’s constant efforts to anticipate and mitigate challenges.
The implementation of BIP-360 and the pursuit of post-quantum algorithms demonstrate that Bitcoin is not only resilient but also proactive. By adopting practical measures, such as using modern wallets and migrating to quantum-resistant addresses, users can further protect themselves against potential threats.
Bitcoin’s future is not at risk—it is being carefully shaped to withstand any emerging technology, including quantum computing.
-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ eac63075:b4988b48
2024-10-21 08:11:11
@ eac63075:b4988b48
2024-10-21 08:11:11Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
https://open.spotify.com/episode/0IZ6kMExfxFm4FHg5DAWT8?si=e139033865e045de
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.

Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.

The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.

Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.

The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.
 Table reference: Patrick Breyer - Chat Control in 23 September 2024
Table reference: Patrick Breyer - Chat Control in 23 September 2024Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.

The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.

User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.

The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.

Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ 4ba8e86d:89d32de4
2024-10-07 13:37:38
@ 4ba8e86d:89d32de4
2024-10-07 13:37:38O que é Cwtch? Cwtch (/kʊtʃ/ - uma palavra galesa que pode ser traduzida aproximadamente como “um abraço que cria um lugar seguro”) é um protocolo de mensagens multipartidário descentralizado, que preserva a privacidade, que pode ser usado para construir aplicativos resistentes a metadados.
Como posso pronunciar Cwtch? Como "kutch", para rimar com "butch".
Descentralizado e Aberto : Não existe “serviço Cwtch” ou “rede Cwtch”. Os participantes do Cwtch podem hospedar seus próprios espaços seguros ou emprestar sua infraestrutura para outras pessoas que buscam um espaço seguro. O protocolo Cwtch é aberto e qualquer pessoa é livre para criar bots, serviços e interfaces de usuário e integrar e interagir com o Cwtch.
Preservação de privacidade : toda a comunicação no Cwtch é criptografada de ponta a ponta e ocorre nos serviços cebola Tor v3.
Resistente a metadados : O Cwtch foi projetado de forma que nenhuma informação seja trocada ou disponibilizada a ninguém sem seu consentimento explícito, incluindo mensagens durante a transmissão e metadados de protocolo
Uma breve história do bate-papo resistente a metadados Nos últimos anos, a conscientização pública sobre a necessidade e os benefícios das soluções criptografadas de ponta a ponta aumentou com aplicativos como Signal , Whatsapp e Wire. que agora fornecem aos usuários comunicações seguras.
No entanto, essas ferramentas exigem vários níveis de exposição de metadados para funcionar, e muitos desses metadados podem ser usados para obter detalhes sobre como e por que uma pessoa está usando uma ferramenta para se comunicar.
Uma ferramenta que buscou reduzir metadados é o Ricochet lançado pela primeira vez em 2014. Ricochet usou os serviços cebola Tor v2 para fornecer comunicação criptografada segura de ponta a ponta e para proteger os metadados das comunicações.
Não havia servidores centralizados que auxiliassem no roteamento das conversas do Ricochet. Ninguém além das partes envolvidas em uma conversa poderia saber que tal conversa está ocorrendo.
Ricochet tinha limitações; não havia suporte para vários dispositivos, nem existe um mecanismo para suportar a comunicação em grupo ou para um usuário enviar mensagens enquanto um contato está offline.
Isto tornou a adoção do Ricochet uma proposta difícil; mesmo aqueles em ambientes que seriam melhor atendidos pela resistência aos metadados, sem saber que ela existe.
Além disso, qualquer solução para comunicação descentralizada e resistente a metadados enfrenta problemas fundamentais quando se trata de eficiência, privacidade e segurança de grupo conforme definido pelo consenso e consistência da transcrição.
Alternativas modernas ao Ricochet incluem Briar , Zbay e Ricochet Refresh - cada ferramenta procura otimizar para um conjunto diferente de compensações, por exemplo, Briar procura permitir que as pessoas se comuniquem mesmo quando a infraestrutura de rede subjacente está inoperante, ao mesmo tempo que fornece resistência à vigilância de metadados.
O projeto Cwtch começou em 2017 como um protocolo de extensão para Ricochet, fornecendo conversas em grupo por meio de servidores não confiáveis, com o objetivo de permitir aplicativos descentralizados e resistentes a metadados como listas compartilhadas e quadros de avisos.
Uma versão alfa do Cwtch foi lançada em fevereiro de 2019 e, desde então, a equipe do Cwtch dirigida pela OPEN PRIVACY RESEARCH SOCIETY conduziu pesquisa e desenvolvimento em cwtch e nos protocolos, bibliotecas e espaços de problemas subjacentes.
Modelo de Risco.
Sabe-se que os metadados de comunicações são explorados por vários adversários para minar a segurança dos sistemas, para rastrear vítimas e para realizar análises de redes sociais em grande escala para alimentar a vigilância em massa. As ferramentas resistentes a metadados estão em sua infância e faltam pesquisas sobre a construção e a experiência do usuário de tais ferramentas.
https://nostrcheck.me/media/public/nostrcheck.me_9475702740746681051707662826.webp
O Cwtch foi originalmente concebido como uma extensão do protocolo Ricochet resistente a metadados para suportar comunicações assíncronas de grupos multiponto por meio do uso de infraestrutura anônima, descartável e não confiável.
Desde então, o Cwtch evoluiu para um protocolo próprio. Esta seção descreverá os vários riscos conhecidos que o Cwtch tenta mitigar e será fortemente referenciado no restante do documento ao discutir os vários subcomponentes da Arquitetura Cwtch.
Modelo de ameaça.
É importante identificar e compreender que os metadados são omnipresentes nos protocolos de comunicação; é de facto necessário que tais protocolos funcionem de forma eficiente e em escala. No entanto, as informações que são úteis para facilitar peers e servidores também são altamente relevantes para adversários que desejam explorar tais informações.
Para a definição do nosso problema, assumiremos que o conteúdo de uma comunicação é criptografado de tal forma que um adversário é praticamente incapaz de quebrá-lo veja tapir e cwtch para detalhes sobre a criptografia que usamos, e como tal nos concentraremos em o contexto para os metadados de comunicação.
Procuramos proteger os seguintes contextos de comunicação:
• Quem está envolvido em uma comunicação? Pode ser possível identificar pessoas ou simplesmente identificadores de dispositivos ou redes. Por exemplo, “esta comunicação envolve Alice, uma jornalista, e Bob, um funcionário público”.
• Onde estão os participantes da conversa? Por exemplo, “durante esta comunicação, Alice estava na França e Bob estava no Canadá”.
• Quando ocorreu uma conversa? O momento e a duração da comunicação podem revelar muito sobre a natureza de uma chamada, por exemplo, “Bob, um funcionário público, conversou com Alice ao telefone por uma hora ontem à noite. Esta é a primeira vez que eles se comunicam.” *Como a conversa foi mediada? O fato de uma conversa ter ocorrido por meio de um e-mail criptografado ou não criptografado pode fornecer informações úteis. Por exemplo, “Alice enviou um e-mail criptografado para Bob ontem, enquanto eles normalmente enviam apenas e-mails de texto simples um para o outro”.
• Sobre o que é a conversa? Mesmo que o conteúdo da comunicação seja criptografado, às vezes é possível derivar um contexto provável de uma conversa sem saber exatamente o que é dito, por exemplo, “uma pessoa ligou para uma pizzaria na hora do jantar” ou “alguém ligou para um número conhecido de linha direta de suicídio na hora do jantar”. 3 horas da manhã."
Além das conversas individuais, também procuramos defender-nos contra ataques de correlação de contexto, através dos quais múltiplas conversas são analisadas para obter informações de nível superior:
• Relacionamentos: Descobrir relações sociais entre um par de entidades analisando a frequência e a duração de suas comunicações durante um período de tempo. Por exemplo, Carol e Eve ligam uma para a outra todos os dias durante várias horas seguidas.
• Cliques: Descobrir relações sociais entre um grupo de entidades que interagem entre si. Por exemplo, Alice, Bob e Eva se comunicam entre si.
• Grupos vagamente conectados e indivíduos-ponte: descobrir grupos que se comunicam entre si através de intermediários, analisando cadeias de comunicação (por exemplo, toda vez que Alice fala com Bob, ela fala com Carol quase imediatamente depois; Bob e Carol nunca se comunicam).
• Padrão de Vida: Descobrir quais comunicações são cíclicas e previsíveis. Por exemplo, Alice liga para Eve toda segunda-feira à noite por cerca de uma hora. Ataques Ativos
Ataques de deturpação.
O Cwtch não fornece registro global de nomes de exibição e, como tal, as pessoas que usam o Cwtch são mais vulneráveis a ataques baseados em declarações falsas, ou seja, pessoas que fingem ser outras pessoas:
O fluxo básico de um desses ataques é o seguinte, embora também existam outros fluxos:
•Alice tem um amigo chamado Bob e outro chamado Eve
• Eve descobre que Alice tem um amigo chamado Bob
• Eve cria milhares de novas contas para encontrar uma que tenha uma imagem/chave pública semelhante à de Bob (não será idêntica, mas pode enganar alguém por alguns minutos)
• Eve chama essa nova conta de "Eve New Account" e adiciona Alice como amiga.
• Eve então muda seu nome em "Eve New Account" para "Bob"
• Alice envia mensagens destinadas a "Bob" para a conta falsa de Bob de Eve Como os ataques de declarações falsas são inerentemente uma questão de confiança e verificação, a única maneira absoluta de evitá-los é os usuários validarem absolutamente a chave pública. Obviamente, isso não é o ideal e, em muitos casos, simplesmente não acontecerá .
Como tal, pretendemos fornecer algumas dicas de experiência do usuário na interface do usuário para orientar as pessoas na tomada de decisões sobre confiar em contas e/ou distinguir contas que possam estar tentando se representar como outros usuários.
Uma nota sobre ataques físicos A Cwtch não considera ataques que exijam acesso físico (ou equivalente) à máquina do usuário como praticamente defensáveis. No entanto, no interesse de uma boa engenharia de segurança, ao longo deste documento ainda nos referiremos a ataques ou condições que exigem tal privilégio e indicaremos onde quaisquer mitigações que implementámos falharão.
Um perfil Cwtch.
Os usuários podem criar um ou mais perfis Cwtch. Cada perfil gera um par de chaves ed25519 aleatório compatível com Tor.
Além do material criptográfico, um perfil também contém uma lista de Contatos (outras chaves públicas do perfil Cwtch + dados associados sobre esse perfil, como apelido e (opcionalmente) mensagens históricas), uma lista de Grupos (contendo o material criptográfico do grupo, além de outros dados associados, como apelido do grupo e mensagens históricas).
Conversões entre duas partes: ponto a ponto
https://nostrcheck.me/media/public/nostrcheck.me_2186338207587396891707662879.webp
Para que duas partes participem de uma conversa ponto a ponto, ambas devem estar on-line, mas apenas uma precisa estar acessível por meio do serviço Onion. Por uma questão de clareza, muitas vezes rotulamos uma parte como “ponto de entrada” (aquele que hospeda o serviço cebola) e a outra parte como “ponto de saída” (aquele que se conecta ao serviço cebola).
Após a conexão, ambas as partes adotam um protocolo de autenticação que:
• Afirma que cada parte tem acesso à chave privada associada à sua identidade pública.
• Gera uma chave de sessão efêmera usada para criptografar todas as comunicações futuras durante a sessão.
Esta troca (documentada com mais detalhes no protocolo de autenticação ) é negável offline , ou seja, é possível para qualquer parte falsificar transcrições desta troca de protocolo após o fato e, como tal - após o fato - é impossível provar definitivamente que a troca aconteceu de forma alguma.
Após o protocolo de autenticação, as duas partes podem trocar mensagens livremente.
Conversas em Grupo e Comunicação Ponto a Servidor
Ao iniciar uma conversa em grupo, é gerada uma chave aleatória para o grupo, conhecida como Group Key. Todas as comunicações do grupo são criptografadas usando esta chave. Além disso, o criador do grupo escolhe um servidor Cwtch para hospedar o grupo. Um convite é gerado, incluindo o Group Key, o servidor do grupo e a chave do grupo, para ser enviado aos potenciais membros.
Para enviar uma mensagem ao grupo, um perfil se conecta ao servidor do grupo e criptografa a mensagem usando a Group Key, gerando também uma assinatura sobre o Group ID, o servidor do grupo e a mensagem. Para receber mensagens do grupo, um perfil se conecta ao servidor e baixa as mensagens, tentando descriptografá-las usando a Group Key e verificando a assinatura.
Detalhamento do Ecossistema de Componentes
O Cwtch é composto por várias bibliotecas de componentes menores, cada uma desempenhando um papel específico. Algumas dessas bibliotecas incluem:
- abertoprivacidade/conectividade: Abstração de rede ACN, atualmente suportando apenas Tor.
- cwtch.im/tapir: Biblioteca para construção de aplicativos p2p em sistemas de comunicação anônimos.
- cwtch.im/cwtch: Biblioteca principal para implementação do protocolo/sistema Cwtch.
- cwtch.im/libcwtch-go: Fornece ligações C para Cwtch para uso em implementações de UI.
TAPIR: Uma Visão Detalhada
Projetado para substituir os antigos canais de ricochete baseados em protobuf, o Tapir fornece uma estrutura para a construção de aplicativos anônimos.
Está dividido em várias camadas:
• Identidade - Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um par.
• Conexões – O protocolo de rede bruto que conecta dois pares. Até agora, as conexões são definidas apenas através do Tor v3 Onion Services.
• Aplicativos - As diversas lógicas que permitem um determinado fluxo de informações em uma conexão. Os exemplos incluem transcrições criptográficas compartilhadas, autenticação, proteção contra spam e serviços baseados em tokens. Os aplicativos fornecem recursos que podem ser referenciados por outros aplicativos para determinar se um determinado peer tem a capacidade de usar um determinado aplicativo hospedado.
• Pilhas de aplicativos - Um mecanismo para conectar mais de um aplicativo, por exemplo, a autenticação depende de uma transcrição criptográfica compartilhada e o aplicativo peer cwtch principal é baseado no aplicativo de autenticação.
Identidade.
Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um peer.
InitializeIdentity - de um par de chaves conhecido e persistente:i,I
InitializeEphemeralIdentity - de um par de chaves aleatório: ie,Ie
Aplicativos de transcrição.
Inicializa uma transcrição criptográfica baseada em Merlin que pode ser usada como base de protocolos baseados em compromisso de nível superior
O aplicativo de transcrição entrará em pânico se um aplicativo tentar substituir uma transcrição existente por uma nova (aplicando a regra de que uma sessão é baseada em uma e apenas uma transcrição).
Merlin é uma construção de transcrição baseada em STROBE para provas de conhecimento zero. Ele automatiza a transformação Fiat-Shamir, para que, usando Merlin, protocolos não interativos possam ser implementados como se fossem interativos.
Isto é significativamente mais fácil e menos sujeito a erros do que realizar a transformação manualmente e, além disso, também fornece suporte natural para:
• protocolos multi-round com fases alternadas de commit e desafio;
• separação natural de domínios, garantindo que os desafios estejam vinculados às afirmações a serem provadas;
• enquadramento automático de mensagens, evitando codificação ambígua de dados de compromisso;
• e composição do protocolo, usando uma transcrição comum para vários protocolos.
Finalmente, o Merlin também fornece um gerador de números aleatórios baseado em transcrição como defesa profunda contra ataques de entropia ruim (como reutilização de nonce ou preconceito em muitas provas). Este RNG fornece aleatoriedade sintética derivada de toda a transcrição pública, bem como dos dados da testemunha do provador e uma entrada auxiliar de um RNG externo.
Conectividade Cwtch faz uso do Tor Onion Services (v3) para todas as comunicações entre nós.
Fornecemos o pacote openprivacy/connectivity para gerenciar o daemon Tor e configurar e desmontar serviços cebola através do Tor.
Criptografia e armazenamento de perfil.
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir uma senha.
Perfis não criptografados e a senha padrão Para lidar com perfis "não criptografados" (ou seja, que não exigem senha para serem abertos), atualmente criamos um perfil com uma senha codificada de fato .
Isso não é o ideal, preferiríamos confiar no material de chave fornecido pelo sistema operacional, de modo que o perfil fosse vinculado a um dispositivo específico, mas esses recursos são atualmente uma colcha de retalhos - também notamos, ao criar um perfil não criptografado, pessoas que usam Cwtch estão explicitamente optando pelo risco de que alguém com acesso ao sistema de arquivos possa descriptografar seu perfil.
Vulnerabilidades Relacionadas a Imagens e Entrada de Dados
Imagens Maliciosas
O Cwtch enfrenta desafios na renderização de imagens, com o Flutter utilizando Skia, embora o código subjacente não seja totalmente seguro para a memória.
Realizamos testes de fuzzing nos componentes Cwtch e encontramos um bug de travamento causado por um arquivo GIF malformado, levando a falhas no kernel. Para mitigar isso, adotamos a política de sempre habilitar cacheWidth e/ou cacheHeight máximo para widgets de imagem.
Identificamos o risco de imagens maliciosas serem renderizadas de forma diferente em diferentes plataformas, como evidenciado por um bug no analisador PNG da Apple.
Riscos de Entrada de Dados
Um risco significativo é a interceptação de conteúdo ou metadados por meio de um Input Method Editor (IME) em dispositivos móveis. Mesmo aplicativos IME padrão podem expor dados por meio de sincronização na nuvem, tradução online ou dicionários pessoais.
Implementamos medidas de mitigação, como enableIMEPersonalizedLearning: false no Cwtch 1.2, mas a solução completa requer ações em nível de sistema operacional e é um desafio contínuo para a segurança móvel.
Servidor Cwtch.
O objetivo do protocolo Cwtch é permitir a comunicação em grupo através de infraestrutura não confiável .
Ao contrário dos esquemas baseados em retransmissão, onde os grupos atribuem um líder, um conjunto de líderes ou um servidor confiável de terceiros para garantir que cada membro do grupo possa enviar e receber mensagens em tempo hábil (mesmo que os membros estejam offline) - infraestrutura não confiável tem o objetivo de realizar essas propriedades sem a suposição de confiança.
O artigo original do Cwtch definia um conjunto de propriedades que se esperava que os servidores Cwtch fornecessem:
• O Cwtch Server pode ser usado por vários grupos ou apenas um.
• Um servidor Cwtch, sem a colaboração de um membro do grupo, nunca deve aprender a identidade dos participantes de um grupo.
• Um servidor Cwtch nunca deve aprender o conteúdo de qualquer comunicação.
• Um servidor Cwtch nunca deve ser capaz de distinguir mensagens como pertencentes a um grupo específico. Observamos aqui que essas propriedades são um superconjunto dos objetivos de design das estruturas de Recuperação de Informações Privadas.
Melhorias na Eficiência e Segurança
Eficiência do Protocolo
Atualmente, apenas um protocolo conhecido, o PIR ingênuo, atende às propriedades desejadas para garantir a privacidade na comunicação do grupo Cwtch. Este método tem um impacto direto na eficiência da largura de banda, especialmente para usuários em dispositivos móveis. Em resposta a isso, estamos ativamente desenvolvendo novos protocolos que permitem negociar garantias de privacidade e eficiência de maneiras diversas.
Os servidores, no momento desta escrita, permitem o download completo de todas as mensagens armazenadas, bem como uma solicitação para baixar mensagens específicas a partir de uma determinada mensagem. Quando os pares ingressam em um grupo em um novo servidor, eles baixam todas as mensagens do servidor inicialmente e, posteriormente, apenas as mensagens novas.
Mitigação de Análise de Metadados
Essa abordagem permite uma análise moderada de metadados, pois o servidor pode enviar novas mensagens para cada perfil suspeito exclusivo e usar essas assinaturas de mensagens exclusivas para rastrear sessões ao longo do tempo. Essa preocupação é mitigada por dois fatores:
- Os perfis podem atualizar suas conexões a qualquer momento, resultando em uma nova sessão do servidor.
- Os perfis podem ser "ressincronizados" de um servidor a qualquer momento, resultando em uma nova chamada para baixar todas as mensagens. Isso é comumente usado para buscar mensagens antigas de um grupo.
Embora essas medidas imponham limites ao que o servidor pode inferir, ainda não podemos garantir resistência total aos metadados. Para soluções futuras para esse problema, consulte Niwl.
Proteção contra Pares Maliciosos
Os servidores enfrentam o risco de spam gerado por pares, representando uma ameaça significativa à eficácia do sistema Cwtch. Embora tenhamos implementado um mecanismo de proteção contra spam no protótipo do Cwtch, exigindo que os pares realizem alguma prova de trabalho especificada pelo servidor, reconhecemos que essa não é uma solução robusta na presença de um adversário determinado com recursos significativos.
Pacotes de Chaves
Os servidores Cwtch se identificam por meio de pacotes de chaves assinados, contendo uma lista de chaves necessárias para garantir a segurança e resistência aos metadados na comunicação do grupo Cwtch. Esses pacotes de chaves geralmente incluem três chaves: uma chave pública do serviço Tor v3 Onion para o Token Board, uma chave pública do Tor v3 Onion Service para o Token Service e uma chave pública do Privacy Pass.
Para verificar os pacotes de chaves, os perfis que os importam do servidor utilizam o algoritmo trust-on-first-use (TOFU), verificando a assinatura anexada e a existência de todos os tipos de chave. Se o perfil já tiver importado o pacote de chaves do servidor anteriormente, todas as chaves são consideradas iguais.
Configuração prévia do aplicativo para ativar o Relé do Cwtch.
No Android, a hospedagem de servidor não está habilitada, pois essa opção não está disponível devido às limitações dos dispositivos Android. Essa funcionalidade está reservada apenas para servidores hospedados em desktops.
No Android, a única forma direta de importar uma chave de servidor é através do grupo de teste Cwtch, garantindo assim acesso ao servidor Cwtch.
Primeiro passo é Habilitar a opção de grupo no Cwtch que está em fase de testes. Clique na opção no canto superior direito da tela de configuração e pressione o botão para acessar as configurações do Cwtch.
Você pode alterar o idioma para Português do Brasil.Depois, role para baixo e selecione a opção para ativar os experimentos. Em seguida, ative a opção para habilitar o chat em grupo e a pré-visualização de imagens e fotos de perfil, permitindo que você troque sua foto de perfil.
https://link.storjshare.io/raw/jvss6zxle26jdguwaegtjdixhfka/production/f0ca039733d48895001261ab25c5d2efbaf3bf26e55aad3cce406646f9af9d15.MP4
Próximo passo é Criar um perfil.
Pressione o + botão de ação no canto inferior direito e selecione "Novo perfil" ou aberta no botão + adicionar novo perfil.
-
Selecione um nome de exibição
-
Selecione se deseja proteger
este perfil e salvo localmente com criptografia forte: Senha: sua conta está protegida de outras pessoas que possam usar este dispositivo
Sem senha: qualquer pessoa que tenha acesso a este dispositivo poderá acessar este perfil.
Preencha sua senha e digite-a novamente
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a chave da senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir um senha.
https://link.storjshare.io/raw/jxqbqmur2lcqe2eym5thgz4so2ya/production/8f9df1372ec7e659180609afa48be22b12109ae5e1eda9ef1dc05c1325652507.MP4
O próximo passo é adicionar o FuzzBot, que é um bot de testes e de desenvolvimento.
Contato do FuzzBot: 4y2hxlxqzautabituedksnh2ulcgm2coqbure6wvfpg4gi2ci25ta5ad.
Ao enviar o comando "testgroup-invite" para o FuzzBot, você receberá um convite para entrar no Grupo Cwtch Test. Ao ingressar no grupo, você será automaticamente conectado ao servidor Cwtch. Você pode optar por sair do grupo a qualquer momento ou ficar para conversar e tirar dúvidas sobre o aplicativo e outros assuntos. Depois, você pode configurar seu próprio servidor Cwtch, o que é altamente recomendável.
https://link.storjshare.io/raw/jvji25zclkoqcouni5decle7if7a/production/ee3de3540a3e3dca6e6e26d303e12c2ef892a5d7769029275b8b95ffc7468780.MP4
Agora você pode utilizar o aplicativo normalmente. Algumas observações que notei: se houver demora na conexão com outra pessoa, ambas devem estar online. Se ainda assim a conexão não for estabelecida, basta clicar no ícone de reset do Tor para restabelecer a conexão com a outra pessoa.
Uma introdução aos perfis Cwtch.
Com Cwtch você pode criar um ou mais perfis . Cada perfil gera um par de chaves ed25519 aleatório compatível com a Rede Tor.
Este é o identificador que você pode fornecer às pessoas e que elas podem usar para entrar em contato com você via Cwtch.
Cwtch permite criar e gerenciar vários perfis separados. Cada perfil está associado a um par de chaves diferente que inicia um serviço cebola diferente.
Gerenciar Na inicialização, o Cwtch abrirá a tela Gerenciar Perfis. Nessa tela você pode:
- Crie um novo perfil.
- Desbloquear perfis.
- Criptografados existentes.
- Gerenciar perfis carregados.
- Alterando o nome de exibição de um perfil.
- Alterando a senha de um perfil Excluindo um perfil.
- Alterando uma imagem de perfil.
Backup ou exportação de um perfil.
Na tela de gerenciamento de perfil:
-
Selecione o lápis ao lado do perfil que você deseja editar
-
Role para baixo até a parte inferior da tela.
-
Selecione "Exportar perfil"
-
Escolha um local e um nome de arquivo.
5.confirme.
Uma vez confirmado, o Cwtch colocará uma cópia do perfil no local indicado. Este arquivo é criptografado no mesmo nível do perfil.
Este arquivo pode ser importado para outra instância do Cwtch em qualquer dispositivo.
Importando um perfil.
-
Pressione o +botão de ação no canto inferior direito e selecione "Importar perfil"
-
Selecione um arquivo de perfil Cwtch exportado para importar
-
Digite a senha associada ao perfil e confirme.
Uma vez confirmado, o Cwtch tentará descriptografar o arquivo fornecido usando uma chave derivada da senha fornecida. Se for bem-sucedido, o perfil aparecerá na tela Gerenciamento de perfil e estará pronto para uso.
OBSERVAÇÃO Embora um perfil possa ser importado para vários dispositivos, atualmente apenas uma versão de um perfil pode ser usada em todos os dispositivos ao mesmo tempo. As tentativas de usar o mesmo perfil em vários dispositivos podem resultar em problemas de disponibilidade e falhas de mensagens.
Qual é a diferença entre uma conexão ponto a ponto e um grupo cwtch?
As conexões ponto a ponto Cwtch permitem que 2 pessoas troquem mensagens diretamente. As conexões ponto a ponto nos bastidores usam serviços cebola Tor v3 para fornecer uma conexão criptografada e resistente a metadados. Devido a esta conexão direta, ambas as partes precisam estar online ao mesmo tempo para trocar mensagens.
Os Grupos Cwtch permitem que várias partes participem de uma única conversa usando um servidor não confiável (que pode ser fornecido por terceiros ou auto-hospedado). Os operadores de servidores não conseguem saber quantas pessoas estão em um grupo ou o que está sendo discutido. Se vários grupos estiverem hospedados em um único servidor, o servidor não conseguirá saber quais mensagens pertencem a qual grupo sem a conivência de um membro do grupo. Ao contrário das conversas entre pares, as conversas em grupo podem ser conduzidas de forma assíncrona, para que todos num grupo não precisem estar online ao mesmo tempo.
Por que os grupos cwtch são experimentais? Mensagens em grupo resistentes a metadados ainda são um problema em aberto . Embora a versão que fornecemos no Cwtch Beta seja projetada para ser segura e com metadados privados, ela é bastante ineficiente e pode ser mal utilizada. Como tal, aconselhamos cautela ao usá-lo e apenas o fornecemos como um recurso opcional.
Como posso executar meu próprio servidor Cwtch? A implementação de referência para um servidor Cwtch é de código aberto . Qualquer pessoa pode executar um servidor Cwtch, e qualquer pessoa com uma cópia do pacote de chaves públicas do servidor pode hospedar grupos nesse servidor sem que o operador tenha acesso aos metadados relacionados ao grupo .
https://git.openprivacy.ca/cwtch.im/server
https://docs.openprivacy.ca/cwtch-security-handbook/server.html
Como posso desligar o Cwtch? O painel frontal do aplicativo possui um ícone do botão "Shutdown Cwtch" (com um 'X'). Pressionar este botão irá acionar uma caixa de diálogo e, na confirmação, o Cwtch será desligado e todos os perfis serão descarregados.
Suas doações podem fazer a diferença no projeto Cwtch? O Cwtch é um projeto dedicado a construir aplicativos que preservam a privacidade, oferecendo comunicação de grupo resistente a metadados. Além disso, o projeto também desenvolve o Cofre, formulários da web criptografados para ajudar mútua segura. Suas contribuições apoiam iniciativas importantes, como a divulgação de violações de dados médicos em Vancouver e pesquisas sobre a segurança do voto eletrônico na Suíça. Ao doar, você está ajudando a fechar o ciclo, trabalhando com comunidades marginalizadas para identificar e corrigir lacunas de privacidade. Além disso, o projeto trabalha em soluções inovadoras, como a quebra de segredos através da criptografia de limite para proteger sua privacidade durante passagens de fronteira. E também tem a infraestrutura: toda nossa infraestrutura é open source e sem fins lucrativos. Conheça também o Fuzzytags, uma estrutura criptográfica probabilística para marcação resistente a metadados. Sua doação é crucial para continuar o trabalho em prol da privacidade e segurança online. Contribua agora com sua doação
https://openprivacy.ca/donate/
onde você pode fazer sua doação em bitcoin e outras moedas, e saiba mais sobre os projetos. https://openprivacy.ca/work/
Link sobre Cwtch
https://cwtch.im/
https://git.openprivacy.ca/cwtch.im/cwtch
https://docs.cwtch.im/docs/intro
https://docs.openprivacy.ca/cwtch-security-handbook/
Baixar #CwtchDev
cwtch.im/download/
https://play.google.com/store/apps/details?id=im.cwtch.flwtch
-
 @ 7e538978:a5987ab6
2024-10-02 13:57:31
@ 7e538978:a5987ab6
2024-10-02 13:57:31Chain Duel, a fast paced PvP game that takes inspiration from the classic snake game and supercharges it with Bitcoin’s Lightning Network. Imagine battling another player for dominance in a race to collect blocks, where the length of your chain isn’t just a visual cue. It represents real, staked satoshis. The player with the most Proof of Work wins, but it’s not just about gameplay; it’s about the seamless integration of the Lightning Network and real-time payments.
But how does Chain Duel manage these instant transactions with such efficiency? That’s where LNbits comes in. LNbits, an open-source wallet and payment infrastructure, handles all in-game payments making it easy for developers to focus on gameplay while LNbits takes care of everything from microtransactions to automated splits for developers and designers. In this article, we’ll dive deep into how Chain Duel leverages LNbits to streamline in-game payments and how other developers can take advantage of this powerful toolset to build the future of Lightning-powered gaming.
Let’s explore how LNbits transforms payment processing and why it’s quickly becoming a must-have for game developers working in the Bitcoin space.
Overview of Chain Duel
Chain Duel is a unique Lightning Network-inspired game that reimagines the classic snake game with a competitive twist, integrating real-time payments. Two players face off in real-time, racing to "catch" blocks and extend their chains. Each block added to the chain represents Proof of Work, and the player with the most Proof of Work wins the duel. The stakes are high, as the game represents satoshis (small units of Bitcoin) as points, with the winner taking home the prize.
The game is designed to be Lightning-native, meaning all payments within Chain Duel are processed through the Lightning Network. This ensures fast payments, reducing latency and making gameplay smooth. With additional features like practice mode, tournaments and highscores, Chain Duel creates an engaging and competitive environment for Bitcoin enthusiasts and gamers alike.

One of the standout aspects of Chain Duel is its deeper integration with the Lightning Network even at a design level. For example, actual Bitcoin blocks can appear on screen during matches, offering bonus points when mined in sync with the game. The game’s current version, still in beta, has already drawn attention within the Bitcoin community, gaining momentum at conferences and with a growing user base through its social networks. With its innovative combination of gaming, the Lightning Network, and competitive play, Chain Duel offers a glimpse into the future of Lightning-based gaming.
How LNbits is Used in Chain Duel
Seamless Integration with LNbits
At the core of Chain Duel’s efficient payment processing is LNbits, which handles in-game transactions smoothly and reliably. Chain Duel uses the LNbits LNURL-pay and LNURL-withdraw extensions to manage payments and rewards between players. Before each match, players send satoshis using LNURL-pay, which generates a static QR code or link for making the payment. LNURL-pay allows users to attach a note to the payment, which Chain Duel creatively uses as a way to insert the player name in-game. The simplicity of LNURL-pay ensures that users can quickly and easily initiate games, with fresh invoices being issued for every game. When players win, LNURL-withdraw enables them to seamlessly pull their earnings from the game, providing a quick payout system.
These extensions make it easy for players to send and receive Bitcoin with minimal latency, fully leveraging the power of the Lightning Network for fast and low-cost payments. The flexibility of LNbits’ tools means that game developers don’t need to worry about building custom payment systems from scratch—they can rely on LNbits to handle all financial transactions with precision.
Lightning Tournaments
Chain Duel tournaments leverage LNbits and its LNURL extensions to create a seamless and efficient experience for players. In Chain Duel tournaments, LNbits plays a crucial role in managing the overall economics. LNbits facilitates the generation of LNURL QR codes that participants can scan to register quickly or withdraw their winnings. LNbits allows Chain Duel to automatically handle multiple registrations through LNURL-pay, enabling players to participate in the tournament without additional steps. The Lightning Network's speed ensures that these payments occur in real-time, reducing wait times and allowing for a smoother flow in-game.
Splitting Payments
LNbits further simplifies revenue-sharing within Chain Duel. This feature allows the game to automatically split the satoshis sent by players into different shares for the game’s developer, designer, and host. Each time a payment is made to join a match, LNbits is used to automattically pay each of the contributors, according to pre-defined rules. This automated process ensures that everyone involved in the development and running of the game gets their fair share without manual intervention or complex bookkeeping.
Nostr Integration
Chain Duel also integrates with Nostr, a decentralized protocol for social interactions. Players can join games using "Zaps", small tips or micropayments sent over the Lightning Network within the Nostr ecosystem. Through NIP-57, which enables Nostr clients to request Zap invoices, players can use LNURL-pay enabled Zaps to register in P2P matches, further enhancing the Chain Duel experience. By using Zaps as a way to register in-game, Chain Duel automates the process of fetching players' identity, creating a more competitive and social experience. Zaps are public on the Nostr network, further expanding Chain Duel's games social reach and community engagement.
Game and Payment Synchronization

One of the key reasons Chain Duel developers chose LNbits is its powerful API that connects directly with the game’s logic. LNbits allows the game to synchronize payments with gameplay in real-time, providing a seamless experience where payments are an integrated part of the gaming mechanics.
With LNbits managing both the payment process and the Lightning Network’s complex infrastructure, Chain Duel developers are free to concentrate on enhancing the competitive and Lightning Network-related aspects of the game. This division of tasks is essential for streamlining development while still providing an innovative in-game payment experience that is deeply integrated with the Bitcoin network.
LNbits proves to be an indispensable tool for Chain Duel, enabling smooth in-game transactions, real-time revenue sharing, and seamless integration with Nostr. For developers looking to build Lightning-powered games, LNbits offers a powerful suite of tools that handle everything from micropayments to payment distribution—ensuring that the game's focus remains on fun and competition rather than complex payment systems.
LNBits facilitating Education and Adoption
This system contributes to educating users on the power of the Lightning Network. Since Chain Duel directly involve real satoshis and LNURL for registration and rewards, players actively experience how Lightning can facilitate fast, cheap, and permissionless payments. By incorporating LNbits into Chain Duel, the game serves as an educational tool that introduces users to the benefits of the Lightning Network. Players gain direct experience using Lightning wallets and LNURL, helping them understand how these tools work in real-world scenarios. The near-instant nature of these payments showcases the power of Lightning in a practical context, highlighting its potential beyond just gaming. Players are encouraged to set up wallets, explore the Lightning ecosystem, and eventually become familiar with Bitcoin and Lightning technology. By integrating LNbits, Chain Duel transforms in-game payments into a learning opportunity, making Bitcoin and Lightning more approachable for users worldwide.
Tools for Developers
LNbits is a versatile, open-source platform designed to simplify and enhance Bitcoin Lightning Network wallet management. For developers, particularly those working on Lightning-native games like Chain Duel, LNbits offers an invaluable set of tools that allow for seamless integration of Lightning payments without the need to build complex custom solutions from scratch. LNbits is built on a modular and extensible architecture, enabling developers to easily add or create functionality suited to their project’s needs.
Extensible Architecture for Customization
At the core of LNbits is a simple yet powerful wallet system that developers can access across multiple devices. What makes LNbits stand out is its extensible nature—everything beyond the core functionality is implemented as an extension. This modular approach allows users to customize their LNbits installation by enabling or building extensions to suit specific use cases. This flexibility is perfect for developers who want to add Lightning-based services to their games or apps without modifying the core codebase.
- Extensions for Every Use Case
LNbits comes with a wide array of built-in extensions created by contributors, offering various services that can be plugged into your application. Some popular extensions include: - Faucets: Distribute small amounts of Bitcoin to users for testing or promotional purposes.
- Paylinks: Create shareable links for instant payments.
- Points-of-sale (PoS): Allow users to set up shareable payment terminals.
- Paywalls: Charge users to access content or services.
- Event tickets: Sell tickets for events directly via Lightning payments.
- Games and services: From dice games to jukeboxes, LNbits offers entertaining and functional tools.
These ready-made solutions can be adapted and used in different gaming scenarios, for example in Chain Duel, where LNURL extensions are used for in game payments. The extensibility ensures developers can focus on building engaging gameplay while LNbits handles payment flows.
Developer-Friendly Customization
LNbits isn't just a plug-and-play platform. Developers can extend its functionality even further by creating their own extensions, giving full control over how the wallet system is integrated into their games or apps. The architecture is designed to make it easy for developers to build on top of the platform, adding custom features for specific requirements.
Flexible Funding Source Management
LNbits also offers flexibility in terms of managing funding sources. Developers can easily connect LNbits to various Lightning Network node implementations, enabling seamless transitions between nodes or even different payment systems. This allows developers to switch underlying funding sources with minimal effort, making LNbits adaptable for games that may need to scale quickly or rely on different payment infrastructures over time.
A Lean Core System for Maximum Efficiency
Thanks to its modular architecture, LNbits maintains a lean core system. This reduces complexity and overhead, allowing developers to implement only the features they need. By avoiding bloated software, LNbits ensures faster transactions and less resource consumption, which is crucial in fast-paced environments like Chain Duel where speed and efficiency are paramount.
LNbits is designed with developers in mind, offering a suite of tools and a flexible infrastructure that makes integrating Bitcoin payments easy. Whether you’re developing games, apps, or any service that requires Lightning Network transactions, LNbits is a powerful, open-source solution that can be adapted to fit your project.
Conclusion
Chain Duel stands at the forefront of Lightning-powered gaming, combining the excitement of competitive PvP with the speed and efficiency of the Lightning Network. With LNbits handling all in-game payments, from microtransactions to automated revenue splits, developers can focus entirely on crafting an engaging gaming experience. LNbits’ powerful API and extensions make it easy to manage real-time payments, removing the complexity of building payment infrastructure from scratch.
LNbits isn’t just a payment tool — it’s a flexible, developer-friendly platform that can be adapted to any gaming model. Whether you're developing a fast-paced PvP game like Chain Duel or any project requiring seamless Lightning Network integration, LNbits provides the ideal solution for handling instant payments with minimal overhead.
For developers interested in pushing the boundaries of Lightning-powered gaming, Chain Duel is a great example of how LNbits can enhance your game, letting you focus on the fun while LNbits manages real-time transactions.
Find out more
Curious about how Lightning Network payments can power your next game? Explore the following:
- Learn more about Chain Duel: Chain Duel
- Learn how LNbits can simplify payment handling in your project: LNbits
- Dive into decentralized communication with Nostr: Nostr
- Extensions for Every Use Case
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 907e4623:f40ff12a
2025-04-04 19:13:14
@ 907e4623:f40ff12a
2025-04-04 19:13:14gm.
i'm doing my job as I can.
You know, it's not easy to be a founder.
I wanted to give up so many times.But give up is not an option, I need to improve and move forward.
- Difficulties
- Doubt
- Self interest and responsabilities
I was stuck building this: https://afk-community.xyz
Chasing my Product Market Fit, solving the problems I work on...
Step by step, I'm gonna make it.
-
 @ c631e267:c2b78d3e
2025-04-04 18:47:27
@ c631e267:c2b78d3e
2025-04-04 18:47:27Zwei mal drei macht vier, \ widewidewitt und drei macht neune, \ ich mach mir die Welt, \ widewide wie sie mir gefällt. \ Pippi Langstrumpf
Egal, ob Koalitionsverhandlungen oder politischer Alltag: Die Kontroversen zwischen theoretisch verschiedenen Parteien verschwinden, wenn es um den Kampf gegen politische Gegner mit Rückenwind geht. Wer den Alteingesessenen die Pfründe ernsthaft streitig machen könnte, gegen den werden nicht nur «Brandmauern» errichtet, sondern der wird notfalls auch strafrechtlich verfolgt. Doppelstandards sind dabei selbstverständlich inklusive.
In Frankreich ist diese Woche Marine Le Pen wegen der Veruntreuung von EU-Geldern von einem Gericht verurteilt worden. Als Teil der Strafe wurde sie für fünf Jahre vom passiven Wahlrecht ausgeschlossen. Obwohl das Urteil nicht rechtskräftig ist – Le Pen kann in Berufung gehen –, haben die Richter das Verbot, bei Wahlen anzutreten, mit sofortiger Wirkung verhängt. Die Vorsitzende des rechtsnationalen Rassemblement National (RN) galt als aussichtsreiche Kandidatin für die Präsidentschaftswahl 2027.
Das ist in diesem Jahr bereits der zweite gravierende Fall von Wahlbeeinflussung durch die Justiz in einem EU-Staat. In Rumänien hatte Călin Georgescu im November die erste Runde der Präsidentenwahl überraschend gewonnen. Das Ergebnis wurde später annulliert, die behauptete «russische Wahlmanipulation» konnte jedoch nicht bewiesen werden. Die Kandidatur für die Wahlwiederholung im Mai wurde Georgescu kürzlich durch das Verfassungsgericht untersagt.
Die Veruntreuung öffentlicher Gelder muss untersucht und geahndet werden, das steht außer Frage. Diese Anforderung darf nicht selektiv angewendet werden. Hingegen mussten wir in der Vergangenheit bei ungleich schwerwiegenderen Fällen von (mutmaßlichem) Missbrauch ganz andere Vorgehensweisen erleben, etwa im Fall der heutigen EZB-Chefin Christine Lagarde oder im «Pfizergate»-Skandal um die Präsidentin der EU-Kommission Ursula von der Leyen.
Wenngleich derartige Angelegenheiten formal auf einer rechtsstaatlichen Grundlage beruhen mögen, so bleibt ein bitterer Beigeschmack. Es stellt sich die Frage, ob und inwieweit die Justiz politisch instrumentalisiert wird. Dies ist umso interessanter, als die Gewaltenteilung einen essenziellen Teil jeder demokratischen Ordnung darstellt, während die Bekämpfung des politischen Gegners mit juristischen Mitteln gerade bei den am lautesten rufenden Verteidigern «unserer Demokratie» populär zu sein scheint.
Die Delegationen von CDU/CSU und SPD haben bei ihren Verhandlungen über eine Regierungskoalition genau solche Maßnahmen diskutiert. «Im Namen der Wahrheit und der Demokratie» möchte man noch härter gegen «Desinformation» vorgehen und dafür zum Beispiel den Digital Services Act der EU erweitern. Auch soll der Tatbestand der Volksverhetzung verschärft werden – und im Entzug des passiven Wahlrechts münden können. Auf europäischer Ebene würde Friedrich Merz wohl gerne Ungarn das Stimmrecht entziehen.
Der Pegel an Unzufriedenheit und Frustration wächst in großen Teilen der Bevölkerung kontinuierlich. Arroganz, Machtmissbrauch und immer abstrusere Ausreden für offensichtlich willkürliche Maßnahmen werden kaum verhindern, dass den etablierten Parteien die Unterstützung entschwindet. In Deutschland sind die Umfrageergebnisse der AfD ein guter Gradmesser dafür.
[Vorlage Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 7d33ba57:1b82db35
2025-04-04 18:13:02
@ 7d33ba57:1b82db35
2025-04-04 18:13:02Edinburgh is a city where ancient history and modern culture meet in the most atmospheric way. From its dramatic castle perched on a volcanic rock to narrow medieval alleys, vibrant festivals, and cozy pubs, Scotland’s capital is a must-visit for travelers seeking both beauty and depth. It’s a city that feels like stepping into a storybook—with a few ghost tales thrown in for good measure.
🏛️ Top Things to See & Do in Edinburgh
1️⃣ Edinburgh Castle
- Iconic and steeped in royal history
- See the Crown Jewels, the Stone of Destiny, and sweeping views over the city
- Don’t miss the 1 o’clock cannon fire!
2️⃣ Walk the Royal Mile
- The main street running from Edinburgh Castle to Holyrood Palace
- Lined with shops, historic closes (alleyways), churches, and pubs
- Pop into St Giles’ Cathedral and explore the Writer’s Museum
3️⃣ Holyrood Palace & Arthur’s Seat
- The Queen’s official Scottish residence 👑
- Hike up Arthur’s Seat, an ancient volcano, for amazing panoramic views of Edinburgh and beyond
4️⃣ Explore the Old Town & New Town
- Old Town: Medieval, moody, atmospheric
- New Town: Elegant Georgian streets and great shopping on Princes Street
- Don’t miss Victoria Street – rumored inspiration for Harry Potter’s Diagon Alley ✨
5️⃣ Museums & Culture
- National Museum of Scotland – interactive and family-friendly
- Scottish National Gallery – features art by Turner, Van Gogh, and more
- Camera Obscura & World of Illusions – quirky and fun near the castle
6️⃣ Edinburgh’s Underground & Ghost Tours
- Explore the hidden vaults under the city
- Join a ghost tour or learn about Edinburgh’s dark past, including grave robbers and plague victims
7️⃣ Festivals Galore 🎭
- Edinburgh Festival Fringe (August) – The largest arts festival in the world
- Edinburgh International Festival, Book Festival, and Hogmanay (New Year) celebrations
🍽️ What to Eat in Edinburgh
- Haggis, neeps & tatties – A classic, surprisingly tasty Scottish dish
- Scottish salmon, Cullen skink (smoky fish soup)
- Afternoon tea or Scottish whisky tasting in a historic bar 🥃
- Try local spots like The Witchery, Makars Gourmet Mash Bar, or The Scran & Scallie
🚶♀️ Tips for Visiting Edinburgh
✅ Wear comfy shoes – cobblestones and hills are part of the charm
✅ Be ready for 4 seasons in a day – pack layers and a rain jacket ☁️☀️🌧️
✅ Book ahead in summer – especially during August festivals
✅ Take a day trip to Rosslyn Chapel, the Highlands, or Stirling Castle for more Scottish beauty
✅ Consider the Edinburgh City Pass if planning to visit many attractions -
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ 2e8970de:63345c7a
2025-04-04 17:12:41
@ 2e8970de:63345c7a
2025-04-04 17:12:41Recently I shared a substack post that argued "DOGE is About Sex" https://stacker.news/items/921208 the main premise being how Elon & Trumps economic goals were to make women more economically desperate such that women are more nudged to settle for mediocre and lonely men.
I do not think that tells the whole story about MAGA economics. Neither does the author CHH, I think.
But I think she's onto something. Here are 4 tweets I randomly encountered today that fit this narrative perfectly:
Trump's trade war is partly about gender.
As American manufacturing declined, men lost economic leverage over women. The nationalist right believes that this led to lower marriage and birth rates.
https://x.com/EricLevitz/status/1908175346177847669
Highly educated women will be completely out of the marriage market in next 5 years.
https://x.com/mshree01/status/1906316952613589038
congratulations to boring men with stable jobs on becoming the next hot commodity
https://x.com/morganisawizard/status/1907889282947424453
The American economy is built around giving fake unproductive jobs to women, therefore we must destroy it
https://x.com/DrewPavlou/status/1907932434571866226
Conclusion
Interestingly this thought seems to cross many peoples minds independently. Like Calculus was invented by Leibnitz and Newton simultaneous and independently.
It's also liberals and conservatives; men and women uttering these words.
I think this is super fascinating. Shoutout to the original post: https://www.cartoonshateher.com/p/doge-is-about-sex
originally posted at https://stacker.news/items/934557
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 2e8970de:63345c7a
2025-04-04 16:17:56
@ 2e8970de:63345c7a
2025-04-04 16:17:56Interestingly he's suggesting that he's doing all this on purpose. Why would he say that? Well the market could take this (a) positively: he's still in control and there is a masterplan (b) negatively: he's openly hostile against the economy. Trump is obviously hoping the market will take it as (a).
originally posted at https://stacker.news/items/934513
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 9bcc5462:eb501d90
2025-04-04 16:02:14
@ 9bcc5462:eb501d90
2025-04-04 16:02:14The story you are about to read is one hundred percent true. It is also my first encounter with a supernatural force.
It was the summer of 2003 and I was visiting my auntie in Nashville as a 16-year-old, pimply-faced teenager. My younger cousins, Alex, Mikey, and Tony were also there. One afternoon, they were all sitting bored outside in the blazing heat, sheltered under the tree on the front lawn. It was a comical sight really, all of them sprawled out lifeless and silent, eaten alive by the unforgiving mosquitos. I ducked inside and asked my aunt if it was okay to borrow her RAV4 to take them to play basketball nearby at Pitts Park. Despite not having a license she handed me the keys and when I went outside to tell the boys we were going to shoot hoops, you’d have thought I said I was taking them to Disney World!
Off we went up and down the rollercoaster-like hills of Tennessee. Yes, I was speeding, and no, we were not wearing seatbelts. (Remember, sixteen, acne, angst, etc.) We arrived at the park and immediately I felt an eerie sensation. I had been there before with my other cousin Kim, but this time was undeniably different. It didn’t matter that the sun was shining above the bright blue sky, I sensed a darkness lingering. And it had nothing to do with the sticky Southern humidity. It was an overwhelming, odd, ineffable sensation. My eyes couldn’t help but focus on the trees behind the court. As if someone or something was watching us.
Nevertheless, after shooting for teams, we began a 2-on-2 immediately. When Mikey and I won, (I towered over them and Mikey was surprisingly pretty good) Tony wasn’t too happy about losing. In frustration, he bounced the basketball with both hands as hard as he could. The ball ended up on the other side of the fences surrounding the court and rolled into the bordering woods. None of the little squirts wanted to retrieve the ball, so as the big cuz I volunteered myself. Nothing to it right? Wrong!
As I walked towards the woods I couldn’t even locate the basketball. I stopped and scanned until I finally saw it, way deep among the trees. “How did it get all the way over there?” I mumbled beneath my breath. Then, while approaching the ball I heard a loud and distinct voice—“Hey!”—I turned around suddenly, but nothing was there. At first I wasn’t afraid, rather I was genuinely confused. It just made no damn sense, there was no one around. I swiveled my head in every direction and once again the deep, gravelly voice called out, “Hey!” This time I knew where it was coming from and crept towards the source until I spotted something in the bushes. I crouched and pushed some branches aside. And that’s when I noticed it. Buried under the shrubs was a tombstone! It stared back at me, weathered, cracked, moss-eaten. I picked my ass up, ran to the ball, scooped it and bolted back to the court.
Little Alex asked if we were going to play a rematch; I said, “Hell no”. After herding them back to the car, we left and never looked back. To this day I remember the voice. I recall the inexplicable feeling of the unknown energy, force, or spirit that was with us. I only recently shared this story with him and now, at 27, he asked why I didn’t tell him sooner. I thought hard about it and answered, “I guess I didn’t want you to get scared and piss yourself.”
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 3c389c8f:7a2eff7f
2025-04-04 15:47:44
@ 3c389c8f:7a2eff7f
2025-04-04 15:47:44A Rose By Any Other Name... or whatever.
NIP-05 is an identifier created by mapping Nostr keys to DNS based identifiers. More technically, it the part of the protocol that defines how to do this mapping, but you will often see the resulting identifier referred to as "your NIP-05". You will also see it referenced as a "Nostr Address", a "Nostr ID", or a "Nostr Verification". None of those terms are fully correct but nor are they wrong.
A NIP-05 identifier does look very similar to an email address (i.e. NostrName @ SomeSite .com). It makes it easier to convey your Nostr profile to friends or collogues, since your chosen name is not unique and the npub format is not exactly something you will be wanting to jot down at a business meeting. It can be used to find you and your notes, so the term, Nostr Address, fits in that sense. There are free services that provide a NIP-05 to you, but you may want to consider contracting this service to a paid provider. Free services tend to be abused by spammers. Paid NIP-05 providers are reasonably priced, more reputable, provide select affiliations, and often other services, along with hosting your Nip-05 file.
Nostr ID might be the appropriate term, in a different way. Your NIP-05 is unique. You are not limited to possessing a single one, but only one may be present on your profile at any given time. You can switch them out as needed. Some Nostr-based services will require that you have a particular NIP-05 provider in order to access their relay communities or other features. In that sense, it is an ID, proving that you are a member of that community. These NIP-05 IDs are created and hosted for you by the community relay hosts, with whatever criteria they choose to require.
Nostr Verification comes into consideration if you own or run a website. It can be used to validate your identity. By hosting your NIP-05 file on your own domain, you are, in essence, validating that the same person has ownership of the website and control of the associated Nostr profile. (i.e. YourName @ YourSite .com) This is exceptionally handy for any well known individual who may be subject to impersonation. This is great, too, if you sell a product or service online and would like to use Nostr as a means of advertising and engaging with your customers. Your NIP-05 can signal to your customers that you, or any employee, are affiliated with your company.
All of this, for me to tell you... that you don't need a NIP-05 identifier to use Nostr. It just makes a lot of the things you might want to do simpler. For clear instructions on how to set up your NIP-05 visit nostr.how
-
 @ 7bc05901:8c26d22b
2025-04-04 15:40:10
@ 7bc05901:8c26d22b
2025-04-04 15:40:10I am not an engineer by trade. I took my math classes for college credit as early as I could in high school. I signed up for a bachelor of arts in college and basically didn't touch STEM for the rest of my formal education. Seminary (incomplete) and Law School (JD) didn't go deep into any of the sciences -- I think I struggled through an "accounting for lawyers" class.
The dumb thing is that in middle school and early high school I was obsessed with tinkering with mechanical things. I rebuilt a go-kart, tinkered with my computer, built skateboard ramps. High school came, I got obsessed with chasing girls and listening to emo music, and that culminated in a foggy pursuit of journalism, linguistics, ministry and/or academia in my post-graduate adventures. Also, algebra came to me really easily. I loved cramming the day before a test in middle school and embarrassing the other A students who had to work hard to keep those grades up.
I obviously see now how dangerous that pattern can be to sustaining motivation and discipline in the long-time preference aspects of life. I was motivated by the idea of "getting one over" on the authoritarian educators in my life -- they said that the only way to succeed is to do my homework and study, but I wanted them to know that I was different. And I think I was different from a lot of other people around me, but I aimed my agency in the wrong direction. The rebellion became the end for me, instead of being the means to an end of meaningful learning. Rebel against the system so you can escape into a self-sovereign, high-agency existence.
At the risk of over-stuffing the analogy, perhaps that point brings me to decentralized social media environments. Facebook is like my school teachers, there are tasks laid out for me nudging me to behave a certain way. My grades are analogized by my reach that Facebook will give and take away. I run a few Facebook pages and I am constantly irritated by the annoying UI. Constantly changing, adding shit that I cannot imagine anyone asking for and taking away the shit that you refer to everyday. Just this past week I noticed that I have to click into a post on Meta business sweet in order to see how many shares it has. This used to be on the page as I scrolled through all of my content. There is literally just a blank white space where it used to say: 54 shares.
My thought goes to, this is somehow punishing me for my reach. Although Zuckerberg has pledged his allegiance to the new age of "free speech" and given his finger to the government-meddling that he fanned to flame over the last ten or fifteen years, I still think Facebook wants to nudge users away from certain things and towards other things. Libertarians have railed against the "nanny-state" but it is harder to understand how we also give up our sovereignty to centralized social media companies: the Nanny-Feed.
This must die. The unbundling of facebook is a weird time that feels like the detangling of digital society. Life without widespread Craigslist adoption is somewhat more annoying. I used to scroll Craigslist all the time for stuff. I went to Los Angeles for a few months in 2012 and used it to buy some things and hear about auditions for different projects, a few of which panned out for me. There was something about having some separation from the site that I went to specifically to network with co-workers and communicate with old friends that I liked. I don't want my social media identity locked on one site, especially a site that is subservient to a boardroom. I also like the inconvenience of hopping over to a different app to handle my marketplace experiences.
A lot of this needs to be thought through a lot more, because attempting to untangle the beast that is "meta" (still Facebook to me) requires a lot more insight than I have as I type this out. I'm mostly just nostalgic and emotional and remembering a different time in my life.
-
 @ 7d33ba57:1b82db35
2025-04-04 14:35:00
@ 7d33ba57:1b82db35
2025-04-04 14:35:00Zlarin is a small, car-free island near Šibenik, known for its peaceful atmosphere, crystal-clear waters, and centuries-old coral tradition. It’s often called the “Golden Island” for its natural beauty, and it remains a hidden gem on the Adriatic coast—perfect for quiet beach days, cycling, and slow travel.
🌿 Why Visit Zlarin?
- No cars = pure tranquility – the whole island is pedestrian- and bike-friendly 🚲
- Rich in coral diving heritage – once the center of Croatia’s coral trade 🪸
- Beautiful stone houses, pine forests, and untouched coves
- Easy to reach via a short ferry ride from Šibenik ⛴️
🏖️ Things to Do on Zlarin
1️⃣ Swim & Relax on Secluded Beaches
- Veleš Beach – A pebbly beach surrounded by pines, great for families 🌲
- Magarna Bay – Quiet, wild beach perfect for those seeking solitude 🧘♀️
- Hidden coves – Wander the coast and find your own little swimming spot 🌅
2️⃣ Walk or Cycle the Island
- Well-marked trails through pine forests and olive groves
- Visit the hilltop viewpoint for a panoramic look at Šibenik and nearby islands
- Bring or rent a bike in Šibenik – bikes are ideal for exploring Zlarin 🚴♂️
3️⃣ Learn About Coral Traditions
- Visit the Zlarinka Museum dedicated to the island’s red coral harvesting history
- See traditional jewelry and tools, and learn about the craft’s cultural significance
4️⃣ Stroll Through the Village
- Picturesque stone streets, old chapels, and flower-filled gardens
- Enjoy a drink at a local konoba (tavern) with views of the sea 🍷
5️⃣ Take a Boat Tour or Kayak Trip
- Explore nearby Prvić, Kaprije, or Žirje islands
- Great area for kayaking or paddleboarding over glassy waters 🚣
🚢 How to Get to Zlarin
- Ferry from Šibenik (approx. 25 minutes, year-round service)
- No cars allowed, so park in Šibenik if needed
- Easy to visit for a day trip or stay overnight for peace and stargazing
💡 Tips for Visiting Zlarin
✅ Best time to visit? Late spring to early autumn for swimming and quiet vibes ☀️
✅ Bring cash – not all places accept cards 💶
✅ Pack snorkel gear and water shoes – the underwater world is beautiful 🐠
✅ Stay overnight for an unforgettable quiet island evening under the stars ✨ -
 @ 96203d66:643a819c
2025-04-04 12:58:46
@ 96203d66:643a819c
2025-04-04 12:58:46nostr:nevent1qqs9j3aw7jrzrw6mtgs9w2znhpg7u0vvur4v69mc8xhw90lqahej74ccx749u nostr:nevent1qqsxrleatwc7v4jvpu4hk3k4s5xvvral0uvt6svyydwtqsz7tk2v03spph2jk nostr:nevent1qqsykq5q6gaa499nykagjaf6sav7ul4ve0ge9y22707gueuasdtr97qsnceys nostr:nevent1qqsvyhuwmnjglrk8hxdw8ye3lzy9f0ahf3ajfsn0wkf3pnztlx7dxxsq7jhlg nostr:nevent1qqs2mmqn2sr6a0ysfjyyuwx5gwy4rxre6pwnjqnzzdszzrgh2zgynlgvv59j3 nostr:nevent1qqswhdmpjhkqzp0nld0m23kgyesqmyacksu9zf8kefxtwzracn7efuqt825sd nostr:nevent1qqsdzsjfa2dmkue5hk5dr8ttl76l3kf649yx4lwslwnh238442jfmmsv4fzmd nostr:nevent1qqszun5jhc22du06rle5r0z8zhj2ezm9pmmrfsqx4843qhz57k3aqxg738uv6 nostr:nevent1qqs8sx9mc2yuldpm5edrtplnge8ckgcr4xj8x7af3zdac0r4rat377ga689un nostr:nevent1qqswe5auf0ym9lg78prwj9ppy0rvpdq92pwend96jmq6udh3d5r3mfqxlyl8j nostr:nevent1qqsqtwgpl0v6qf03r4e9r4tsnyly354req9am2u6s5gjrtefwtedpmc72v3jx nostr:nevent1qqsx2w65lvwmf23rutmnhzw3k2paftngssvfdzqmwle4f3m77hk4u8c6lgmrx nostr:nevent1qqsfz6zpaw2gkgxjxfvevgsww0rhw07swwg0hun23xc4mfuh8f7afrg875wcx nostr:nevent1qqs0eknqgzut0sv0undcps42pnw7an4wjt7a2rwjxd2zaqg6rqpjdwg56yeq7 nostr:nevent1qqsrg7yyaacetzugj8304krg5ne0xxu7kdnps8tlnd797myseqp97vs8r7tup nostr:nevent1qqs20ap690l97n8py0g44w22963jkze78ws2em6e0cl02vc65nexmsqw9ugcd
-
 @ e0ef3b4e:6fd74878
2025-04-04 12:55:14
@ e0ef3b4e:6fd74878
2025-04-04 12:55:14At a conference I sit in a quite area and observe and enjoy a coffee. It's bustling around and many are attending a speech at the main stage. Two people sit next to me on a sofa and begin a conversation. He's wearing a beige hoodie and seems to be builder in the space, she's wearing a green winter dress and they seem to be colleagues.
It seems they are now meeting for the first time in real life and exchanging advice, him advising her on how to store her Bitcoin. He’s been longer in the space it seems and she’s just started at the new start-up. I quickly introduce myself and ask them if I may listen in on the conversation since I am a researcher working in the space. They happily agree. She goes on to mention that she will be paid in Bitcoin and does not know how to store it. He goes on to advise her on using a hardware wallet, then takes out his phone and shows a video of the hardware wallet he is using.
She says "Wow, it looks so easy to use. I tried so many different hardware wallets but they are so difficult to use." I see the tension in her shoulders, which then relaxes a bit. He goes on to show her all the security and backup methods for this particular hardware wallet. "I'm sold." She's smiling now and one can see that a decision has been made.
These conversations are happening everyday across the world not only at conferences but in villages, cafes or during random conversation at co-working working spaces. While we strive for good marketing and adoption of Bitcoin, these simple conversations between two people are what is driving actual use.
Safety and trust is a cultural concept in many countries and viewed differently depending on where one has originated from. If one is to imagine that many people would benefit from storing BTC on a device or using an app for lighting transactions then they must trust the process. This need to trust is a basic primary human need.
They will only trust the process if:
-
Empowered: They feel as if they 100% know what they are doing when they are onboarded to the application/hardware device. If there is anything that creates doubt or friction in their minds, the trust to use it as a storage of BTC is gone. A person will window shop when deciding to use a wallet. On average when we interviewed people for various UX research initiatives one person had a minimum of two different Bitcoin wallets on their phone. Prior to that they had tested out quite a few wallets before settling on a decision.
-
Safe: Many are nervous that they will not be able to access their funds once they put it online/on a hardware device. However often receiving advice from someone they trust this will result in them feeling safe. They will likely use the very same device/application that is being used by their friend/colleague or person in a close inner circle.
While this story might seem overly simplified, it’s been repeated multiple times while observing the behavior of people at conferences, through usability tests, and through interviews.
If we understand that a person is tentatively stepping into a “home” (Bitcoin wallet/hardware device) and looking “around” (onboarding process). Once they step in, they will only leave their “bag” (BTC) on the table if specific criteria are met. If not, they will pick up their “bag” (BTC) and walk into the next “home.” (Bitcoin wallet/hardware device). During this process there are basic psychological principles are taking place.
This is where design comes in and creates an experience. The UX design could be equated to the “interior design” of the house. Every click, every interaction every visual that a person sees or experiences is driving them to trust or distrust the experience. We as builders have a unique role in this process and I fully believe that we will solve these challenges together.
If you've read all the way to the end, thank you. On another note, the last 3 weeks have been filled with a lot of strategic thinking, planning, and collaboration.
There are many balls in the air at the moment:
-
UX Research Africa strategy
If you've read all the way to the end, thank you for reading.
✌🏽Peace
-
-
 @ 6a6be47b:3e74e3e1
2025-04-04 12:41:11
@ 6a6be47b:3e74e3e1
2025-04-04 12:41:11⛅️ This week has been a bit hazy—I haven’t been feeling my best. And that’s okay. There are days like that. But this time, it felt like something deeper, as if something was off. Like I wasn’t enough.
🌞 Thankfully, as the days went by, I started to feel better. Today, I feel like myself again—like I’ve put my human suit back on and climbed back on the horse.
✏️ I picked up my pencil and started drawing again, just me and my iPad, without any expectations weighing me down. It felt good—peaceful even—to create for the sake of creating.
🦉 What I’ve realized is this: It’s not bad to have goals or aspirations. Those are important! But what becomes unhealthy is chasing perfectionism while trying to achieve those goals. For me, perfectionism turns into a spiral—not rainbows and butterflies but a storm cloud of self-doubt. I guess I just want to share this in case anyone out there needs to hear it: It’s okay to be imperfect. And most importantly, it’s okay to just be yourself.

🎨 As part of my journey back to myself this week, I decided to draw something simple and even try my hand at a little animation since it had been a while. Here’s what I came up with:
Imposter syndrome can be deceiving—it whispers lies about your worth and tries to steal your joy—but just like anything in life, this too shall pass.
🎢 The ebbs and flows are part of life’s natural rhythm; you’d think I’d have learned that by now! But life has its way of (re)teaching us lessons when we need them most.
✨ To anyone reading this who might be struggling: Be kind to yourself. You’re doing better than you think you are. And remember—you are enough.
Godspeed
-
 @ 907e4623:f40ff12a
2025-04-04 11:39:51
@ 907e4623:f40ff12a
2025-04-04 11:39:51gm well
lfg
-
 @ 1aa9ff07:3cb793b5
2025-04-04 09:42:28
@ 1aa9ff07:3cb793b5
2025-04-04 09:42:28Artificial intelligence (AI) has gained significant momentum in recent years, and it is expected to bring revolutionary changes to our lives over the next five years. Today, AI plays a crucial role in automation, healthcare, education, and many other fields. In the near future, its impact will become even more profound. Here are some key transformations AI is expected to bring:
- Major Changes in the Business World
AI will automate repetitive tasks, allowing human workers to focus on more strategic areas. AI-powered assistants, data analytics, and customer service applications will become more widespread, shifting human efforts toward creative and problem-solving roles.
- Revolutionary Advances in Healthcare
AI in medicine will enable earlier disease diagnosis and personalized treatment plans. Thanks to advancements in image processing and genetic analysis, diseases such as cancer can be detected more quickly and accurately.
- Widespread Adoption of Autonomous Vehicles
Over the next five years, autonomous vehicle technologies will continue to evolve, becoming more common in urban transportation and logistics. This will lead to a reduction in traffic accidents, lower transportation costs, and significant changes in urban planning.
- AI-Powered Personalized Learning in Education
AI will enhance personalized education solutions, making learning processes more efficient. AI-assisted teachers and learning platforms will analyze students’ weaknesses and create customized study programs tailored to their needs.
- New Challenges in Security and Data Privacy
As AI technology advances, cybersecurity and data privacy will become even more critical. While AI-driven security systems can detect cyber threats proactively, malicious applications of AI may introduce new vulnerabilities.
- Creative Innovations in Art and Entertainment
AI-generated content will become more prevalent in fields such as art, music, and cinema. AI-assisted scripts, music compositions, and digital artwork may give rise to a new wave of artistic expression.
Conclusion
In the next five years, AI's influence will be felt in every aspect of life. From business and healthcare to transportation and the arts, various sectors will undergo transformative innovations. However, addressing ethical concerns, security challenges, and data privacy issues will be crucial to ensuring AI's positive impact. By harnessing AI’s potential responsibly, we can build a more efficient, secure, and sustainable future.
Artificial intelligence (AI) has gained significant momentum in recent years, and it is expected to bring revolutionary changes to our lives over the next five years. Today, AI plays a crucial role in automation, healthcare, education, and many other fields. In the near future, its impact will become even more profound. Here are some key transformations AI is expected to bring:
-
 @ 2b24a1fa:17750f64
2025-04-04 08:42:16
@ 2b24a1fa:17750f64
2025-04-04 08:42:16„Denke daran, daß das, was dich wie an unsichtbaren Fäden hin- und herzieht, in deinem Innern verborgen ist.“ Soll der römische Kaiser Marc Aurel gesagt haben, der letzte bedeutende Philosoph der jüngeren Stoa. Brot und Spiele hieß es damals, machten die Gesellschaften gefügig: Bier, Wein, Whiskey, Ablenkung, Informationssteuerung.
https://soundcloud.com/radiomuenchen/kriegsspiele-durch-softpower?
Wie sich die kognitive Einflussnahme zur Kriegsführung entwickelte, wie sie sich mit den heutigen medialen und technischen Mitteln darstellt und wie wir unsere Kinder und uns selbst davor schützen können, damit beschäftigt sich der Propagandaforscher und Amerikanist Dr. Jonas Tögel. Er promovierte zum Thema Soft Power und Motivation und forscht am Institut für Psychologie der Universität Regensburg. Meine Kollegin Eva Schmidt hat ihn interviewt und wollte zunächst von ihm wissen, wie er zur Propagandaforschung kam und auf welchen Grundlagen seine Tätigkeit aufbaut.
Sein aktuelles Buch "Kriegsspiele - Wie NATO und Pentagon die Zerstörung Europas simulieren" ist im Westend-Verlag erschienen, hat 111 Seiten und kostet 15 Euro.
www.radiomuenchen.net/\ @radiomuenchen\ www.facebook.com/radiomuenchen\ www.instagram.com/radio_muenchen/\ twitter.com/RadioMuenchen\ odysee.com/@RadioMuenchen.net:9\ rumble.com/user/RadioMunchen
Radio München ist eine gemeinnützige Unternehmung.\ Wir freuen uns, wenn Sie unsere Arbeit unterstützen.
GLS-Bank\ IBAN: DE65 4306 0967 8217 9867 00\ BIC: GENODEM1GLS\ Bitcoin (BTC): bc1qqkrzed5vuvl82dggsyjgcjteylq5l58sz4s927\ Ethereum (ETH): 0xB9a49A0bda5FAc3F084D5257424E3e6fdD303482
-
 @ 2b24a1fa:17750f64
2025-04-04 08:36:50
@ 2b24a1fa:17750f64
2025-04-04 08:36:50Was passiert, wenn die Bank plötzlich das Konto kündigt? Aus gesetzlicher Sicht darf sie das, sogar ohne Gründe zu nennen - sofern diese Option in den Allgemeinen Geschäftsbedingungen (AGB) des Kontovertrags steht. Und das ist die Regel.
https://soundcloud.com/radiomuenchen/de-banking-oder-die-rache-der-bundesbank?
Zwar besteht oft eine mindestens zweimonatige Kündigungsfrist, doch wer jemals das Konto gewechselt hat, weiß, was für ein Aufwand es ist, seinen gesamten und immer komplexeren Zahlungsverkehr umzustellen. Besonders hart trifft es Empfänger von Spenden: darunter viele alternative Medien und freie Journalisten, die für alternative Medien arbeiten. Die Spenden brechen weg, denn die meist anonymen Spender können nicht direkt informiert werden. Das wissen auch diejenigen, denen alternative Medien ein Dorn im Auge sind: Staatlich finanzierte Agitatoren und staatsnahe Medien, die solange Druck auf Banken ausüben, bis diese aus Sorge um ihr Image das Konto kündigen. Das Magazin Multipolar dokumentierte Mitte 2024 rund 40 solcher Fälle. Manchmal nutzen Banken auch ganz direkt diese Möglichkeit, um kritische Stimmen einzuschüchtern und zu schwächen. Diese Variante vermutet unsere Autorin Gaby Weber. Nach einem kritischen Bericht über die Bundesbank wurde ihr das Konto gekündigt. Hören Sie ihren Beitrag „De-Banking oder: die Rache der Bundesbank?“, der zunächst beim Overton-Magazin erschienen ist: overton-magazin.de/hintergrund/pol…der-bundesbank/
Sprecher: Ulrich Allroggen
Bild: Radio München
Radio München\ www.radiomuenchen.net/\ @radiomuenchen\ www.facebook.com/radiomuenchen\ www.instagram.com/radio_muenchen/\ twitter.com/RadioMuenchen\ odysee.com/@RadioMuenchen.net:9\ rumble.com/user/RadioMunchen
Radio München ist eine gemeinnützige Unternehmung.\ Wir freuen uns, wenn Sie unsere Arbeit unterstützen.
GLS-Bank\ IBAN: DE65 4306 0967 8217 9867 00\ BIC: GENODEM1GLS\ Bitcoin (BTC): bc1qqkrzed5vuvl82dggsyjgcjteylq5l58sz4s927\ Ethereum (ETH): 0xB9a49A0bda5FAc3F084D5257424E3e6fdD303482
-
 @ 2b24a1fa:17750f64
2025-04-04 08:15:16
@ 2b24a1fa:17750f64
2025-04-04 08:15:16Ganz im Geiste des klassischen Kabaretts widmen sich Franz Esser und Michael Sailer den Ereignissen des letzten Monats: Was ist passiert? Und was ist dazu zu sagen? Das ist oft frappierend - und manchmal auch zum Lachen.
https://soundcloud.com/radiomuenchen/vier-wochen-wahnsinn-marz25-ein-satirischer-wochenruckblick?
-
 @ 2b24a1fa:17750f64
2025-04-04 08:10:53
@ 2b24a1fa:17750f64
2025-04-04 08:10:53Wir leben in einer Demokratie. So heißt es immer. Immerhin hat die Bevölkerung, der Souverän ein Mitspracherecht. Einmal alle vier Jahre. Und damit fünfundzwanzig Mal in einem Jahrhundert. Diese 25 Wahltage ergeben zeitlich 0,07 Prozent des gesamten Jahrhunderts. Würde man das Jahrhundert auf einen Tag runter rechnen, dann ergäben diese 0,07 Prozent ziemlich genau eine Minute des Mitspracherechts. Eine Minute pro Tag darf der Souverän also bestimmen, wer am restlichen Tag ungehindert schalten und walten darf – bis in das Grundgesetz hinein.
https://soundcloud.com/radiomuenchen/das-grundgesetz-als-schmierzettel-von-henry-matthes?
Die Veränderung in diesem zentralen Gesetzestexten ist allein den Parteien vorbehalten. An sämtliche Änderungen halten, dürfen sich dann nachher alle – selbst dann, wenn noch so wenige Bürger dahinterstehen.
In den letzten Wochen offenbarte sich dieser Missstand in präzedenzloser Weise. Die als Sondervermögen schön-deklarierte Neuverschuldung wurde im Grundgesetz festgeschrieben. Ist eine solch selektive Umgestaltungsmöglichkeit des wichtigsten Gesetzestext einer Demokratie würdig? Bräuchte es nicht zumindest einer Absegnung durch Volksabstimmungen?
Henry Mattheß hat sich hierzu Gedanken gemacht. Hören Sie seinen Text „Das Grundgesetz als Schmierzettel“, der zunächst auf dem Blog von Norbert Häring erschienen war.
Sprecher: Karsten Tryoke
Bild: Radio München
www.radiomuenchen.net/\ @radiomuenchen\ www.facebook.com/radiomuenchen\ www.instagram.com/radio_muenchen/\ twitter.com/RadioMuenchen
Radio München ist eine gemeinnützige Unternehmung.\ Wir freuen uns, wenn Sie unsere Arbeit unterstützen.
GLS-Bank\ IBAN: DE65 4306 0967 8217 9867 00\ BIC: GENODEM1GLS\ Bitcoin (BTC): bc1qqkrzed5vuvl82dggsyjgcjteylq5l58sz4s927\ Ethereum (ETH): 0xB9a49A0bda5FAc3F084D5257424E3e6fdD303482
-
 @ da0b9bc3:4e30a4a9
2025-04-04 06:24:48
@ da0b9bc3:4e30a4a9
2025-04-04 06:24:48Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/934111
-
 @ bf95e1a4:ebdcc848
2025-04-04 06:11:18
@ bf95e1a4:ebdcc848
2025-04-04 06:11:18This is a part of the Bitcoin Infinity Academy course on Knut Svanholm's book Bitcoin: Sovereignty Through Mathematics. For more information, check out our Geyser page!
The Gullible Collective
We humans are biased by nature. Everything we think we know is distorted in one way or another by our cognitive shortcomings. The human brain has been forced to evolve and adapt to whatever environment it found itself in over millennia. Having a brain that is capable of setting aside personal aims for the sake of the collective has proven to be advantageous for the evolution of our species as a whole. The same is true for every other social life form. However, letting these parts of our brains guide our political judgment can lead to disastrous results in the long run — not because of bad intentions but because of the simple fact that a few individuals will always thrive by playing every political system for personal gain. From an evolutionary perspective, an army of ay-sayers and martyrs, regardless of whether we’re talking about an army of humans or an army of ants or bacteria, has an advantage over a less disciplined one. From an individual's evolutionary perspective though, it is better to appear like you’re a martyr but to run and hide when the actual battle happens. This at least partly explains the high percentage of sociopaths in leadership positions all over the world. If you can appear to act for the good of the collective but dupe your way into more and more power behind people’s backs, you’re more likely to succeed than someone playing a fair game.
The story of banking and fiat currency is a story about collective madness. Historically, rulers have tricked people into killing each other through the promise of an after-life. Through central banking, the rulers of the world wars could trick people into building armies for them by printing more money. This is seldom mentioned in history classes because it still goes on today on a massive scale. Inflation might no longer be paying tank factory workers, but it is the main mechanism that funnels wealth into the pockets of the super-rich and away from everyone else. Inflation is the mechanism that hinders us from transporting the value of our labor through time. It makes us avoid real long-term thinking. We hardly ever consider this a problem because none of us has ever experienced an alternative to it.
Money is still vastly misunderstood by the lion's share of the world’s population. In most parts of the world, banks do something called fractional reserve lending. This means that they lend out money that they don't have — conjuring up new money out of thin air and handing it out to their customers as loans. Loans that have to be paid back with interest. Interest that can’t be paid back with thin air but has to be paid with so-called real money. Real money, of which there isn’t enough around to pay back all the loans, so that a constant need for new credit becomes a crucial part of the entire system. Not to mention central banks, which do the same and worse for governments. We’re so used to it by now that every country is expected to have a national debt. All but a handful of ridiculously rich ones do. National debts are also loans that have to be paid back with interest backed by nothing. Think about that. Your taxes are paying someone else's interest. Your tax money is not paying for your grandmother's bypass operation, it is paying interest to a central bank.
When the ideas of the catholic church ruled Europe, people who didn’t believe in God were few and very seldomly outspoken. They had good reason for this since belief in God was virtually mandatory throughout society. Ever since 1971, when famously dishonest American president Richard Nixon cut the last string that tied the US Dollar to gold, our conception of what the world economy is and ought to be has been skewed by an utterly corrupt system. We’re led to believe that we’re all supposed to work longer and longer days in order to spend more and more money and bury ourselves in more and more debt to keep the machine running. We’re duped into thinking that buying a new car every other year is somehow good for the environment and that bringing a cotton bag to the grocery store will somehow save the planet. Stores manipulate us all the time through advertising and product placement, but we’re led to believe that if we can be “climate-smart,” we’re behaving responsibly. Somehow, our gross domestic product is supposed to increase indefinitely while politicians will save us from ourselves through carbon taxes. Fortunately for us, and unfortunately for them, there now exists a way for unbelievers of this narrative to opt out. Life finds a way, as Jeff Goldblum once so famously put it.
Collectivism has ruined many societies. Those of us fortunate enough to live in liberal democracies tend to forget that even democracy is an involuntary system. It’s often referred to as the “worst form of government except all others that have been tried,” but the system itself is very rarely criticized. We’re so used to being governed that not having a leader seems preposterous to most of us. Still, we pay our taxes, and an enormous cut of the fruit of our labor goes to a third party via inflation and the taxation of every good and service imaginable. Institutions, once in place, tend to always favor their own survival just as much as any other living thing does. People employed in the public sector are unlikely to vote against policies that threaten their livelihood. This is a bigger problem than we realize because it’s subtle and takes a long time, but every democracy is headed in the same direction. A bigger state, a more complicated system, and fewer individual freedoms. Long term, it seems that all of our systems tend to favor those who know how to play that system and not those who contribute the most value to their fellow man. Proponents of socialist policies often claim that failed socialist states “weren’t really socialist” or that “that wasn’t really socialism.” What most people fail to realize is that we’ve never tried real capitalism since we’ve always used more or less inflationary currencies. This might very well be the most skewed narrative of our era. We’re all experiencing real, albeit disguised, socialism every single day. True free market capitalism is what we haven’t experienced yet, and it might turn out to be a very different thing than what we’re told to believe that it is by almost all mainstream media.
The validity of the classic right-left scale describing political viewpoints has been debated a lot lately, and alternative scales, like GAL-TAN, the one with an additional Y-axis describing more or less authoritarian tendencies, are popping up in various contexts around the web. After the birth of Bitcoin, there’s a new way to see this. Imagine an origo, a zero point, and a vector pointing to the left of that. All politics are arguably on the left because all policies need to be funded by taxes, and taxation can be viewed as theft. Taxation can be viewed as theft because, at its core, it’s involuntary. If a person refuses to pay his taxes, there is a threat of violence lurking in the background. Not to mention inflation, which Milton Friedman so elegantly described as “taxation without legislation.” What you do with the portion of your wealth that you have in Bitcoin is another matter altogether. If you take sufficient precautionary privacy measures and you know what you’re doing, your business in Bitcoin is beyond politics altogether. With the introduction of the Lightning Network and other privacy-improving features, it is now impossible for any third party to confiscate your money or even know that you have it, for that matter. This changes the political landscape of every nation on Earth. Bitcoin is much less confiscatable than gold and other scarce assets, which makes it a much better tool for hedging against nation-states. In this sense, Bitcoin obsoletes borders. You can cross any border on Earth with any amount of Bitcoin in your head. Think about that! Your Bitcoin exists in every country simultaneously. Any imposed limit on how much money you can carry from one nation to the other is now made obsolete by beautiful mathematics. Bitcoin is sometimes referred to as a “virtual currency.” This is a very inaccurate description. Bitcoin is just mathematics, and mathematics is just about the most real thing there is. There’s nothing virtual about it. Counterintuitive to some, but real nonetheless.
The complexity of human societal hierarchies and power structures is described perfectly in a classic children's book, The Emperor’s New Clothes, by Hans Christian Andersen. See the world as the kid who points out that the king is naked in the tale, and everything starts to make sense. Everything in human society is man-made. Nations, leaders, laws, political systems. They’re all castles in the air with nothing but a lurking threat of violence to back them up. Bitcoin is a different beast altogether. It enables every individual to verify the validity of the system at all times. If you really think about it, morality is easy. Don’t hurt other people, and don’t steal other people’s stuff. That’s the basic premise. Humans have but two ways of resolving conflict, conversation and violence, and in this sense, to hurt someone can only mean physical violence. This is why free speech is so important and why you should defend people’s right to speak their minds above everything else. It’s not about being able to express yourself. It’s about your right to hear every side of every argument and thus not have to resort to violence should a conflict of interests occur. You can’t limit free speech with just more speech — there’s always a threat of violence behind the limitations. Code, which both Bitcoin and the Internet are entirely made up of, is speech. Any limitations or regulations that your government implements in regard to Bitcoin are not only a display of Bitcoin’s censorship resistance but also a test of your government's stance on freedom of expression. A restriction on Bitcoin use is a restriction on free speech.
Remember, the only alternative to speech that anyone has is violence. Code is a language, mathematics is a language, and money is a linguistic tool. A linguistic tool we use as a means of expressing value to each other and as a way to transport value through space and time. Any restrictions or regulations regarding how you can express value, for example, making it impossible to buy Bitcoin with your credit card, prove that the money you have in your bank account is not really yours. When people realize this, the demand for Bitcoin goes up, not down. If you know what you're doing, there’s no need to fear the regulators. They, on the other hand, have good reason to fear an invention that shamelessly breaks their spell.
About the Bitcoin Infinity Academy
The Bitcoin Infinity Academy is an educational project built around Knut Svanholm’s books about Bitcoin and Austrian Economics. Each week, a whole chapter from one of the books is released for free on Highlighter, accompanied by a video in which Knut and Luke de Wolf discuss that chapter’s ideas. You can join the discussions by signing up for one of the courses on our Geyser page. Signed books, monthly calls, and lots of other benefits are also available.
-
 @ 502ab02a:a2860397
2025-04-04 02:50:35
@ 502ab02a:a2860397
2025-04-04 02:50:35หลังจากที่เราเพิ่งเปิดเรื่องไฟโตสเตอรอลไปหมาด ๆ ถึงเวลาที่ต้องมาคุยกันเรื่อง oryzanol ซึ่งเป็นอีกหนึ่งสารที่ถูกอุตสาหกรรมผลักดันให้เรารู้สึกว่า “ต้องกิน” เหมือนเป็นไอเทมลับสำหรับสุขภาพหัวใจ แต่เดี๋ยวก่อนนะ ทำไมสิ่งที่มนุษย์ไม่เคยต้องการมาก่อนถึงกลายเป็นสิ่งจำเป็นไปได้ ?
Oryzanol หรือ gamma-oryzanol เป็นสารประกอบที่พบได้ในน้ำมันรำข้าว มีโครงสร้างเป็น sterol ester ของกรดเฟอรูลิก (Ferulic acid esters of sterols and triterpenes) ซึ่งหมายความว่ามันมีโครงสร้างคล้ายกับไฟโตสเตอรอล แต่มาพร้อมกับองค์ประกอบของสารต้านอนุมูลอิสระที่ได้จากกรดเฟอรูลิก นั่นทำให้มันถูกโฆษณาว่าเป็นสารที่ช่วยลดคอเลสเตอรอล มีฤทธิ์ต้านอนุมูลอิสระ และอาจช่วยลดความเสี่ยงโรคหัวใจ ฟังดูดีใช่ไหม ? แต่มันก็คล้ายกับไฟโตสเตอรอลเลย คือเป็นสารที่ แข่งขันกับคอเลสเตอรอลในการดูดซึม และแน่นอนว่าผลข้างเคียงก็ยังคงอยู่ นั่นคือ มันอาจลดการดูดซึมวิตามิน A, D, E, K ซึ่งเป็นวิตามินที่ละลายในไขมันและจำเป็นต่อร่างกาย นั่นหมายความว่า ในขณะที่มันช่วยลด LDL ในกระดาษ มันอาจทำให้ร่างกายขาดสารอาหารที่สำคัญไปด้วย
ปัญหาที่ใหญ่กว่าคือ oryzanol พบมากใน น้ำมันรำข้าว ซึ่งเป็นหนึ่งในน้ำมันพืชที่ผ่านการแปรรูปสูง และการบริโภคน้ำมันพืชมากเกินไปนั้นสัมพันธ์กับ ภาวะอักเสบเรื้อรัง (chronic inflammation), ภาวะต้านอินซูลิน (insulin resistance), และความเสี่ยงโรคหัวใจและหลอดเลือด การที่อุตสาหกรรมบอกให้เราเพิ่ม oryzanol ในอาหาร จึงเป็นเหมือนการผลักให้ผู้คนบริโภคน้ำมันพืชมากขึ้นโดยไม่รู้ตัว ทั้งที่น้ำมันพืชโดยเฉพาะที่ผ่านกรรมวิธีอย่างน้ำมันรำข้าวมีปริมาณโอเมก้า-6 สูง ซึ่งถ้ารับมากเกินไปจะไปกระตุ้นกระบวนการอักเสบในร่างกาย เคยสังเกตไหมครับว่า น้ำมันรำข้าวมักโชว์ตัวเลขเก๋ๆของ Oryzanol แต่กลับไม่โชว์สัดส่วน โอเมก้า 6 กับ โอเมก้า 3
เทียบง่ายๆครับ น้ำมันคาโนลา มีโอเมก้า 6 ราวๆ 2200 - 2800 ต่อน้ำมัน 15 มล. (หน่วยบริโภค) น้ำมันรำข้าว มีโอเมก้า 6 ราวๆ 4,140 - 5,520 มก. ต่อน้ำมัน 15 มล. (หน่วยบริโภค) ในขณะที่โอเมก้า 3 ราวๆ 138 - 276 มก.ต่อน้ำมัน 15 มล. (หน่วยบริโภค) นี่หมายถึงสัดส่วนสูงไปถึงได้ราวๆ 40:1 ทั้งๆที่เราเข้าใจแหละว่าโอเมก้า6 ร่างกายจำเป็น แต่แต่แต่ จำเป็นไม่ได้หมายความว่าจัดหนัก เพราะสิ่งที่เราต้องพึงสังวรคือ สัดส่วนที่สมดุลระหว่าง โอเมก้า3และโอเมก้า6 ดังนั้น 40:1 ไม่เรียกว่าสมดุล ซึ่งจะกระตุ้นการอักเสบเรื้อรัง ในร่างกาย และเกี่ยวข้องกับโรคหัวใจ เบาหวาน และปัญหาสุขภาพอื่นๆ พาเหรดกันมา แต่คุณจะไม่เห็นตัวเลขนี้บนฉลากครับ
ผู้ผลิตผิดไหม? จะไปผิดอะไรครับ หน่วยบริโภคแนะนำเขา 1 หน่วยบริโภคคือ 15 มิลลิลิตร หรือ 1 ช้อนโต๊ะ แค่นั้นเอง คำถามคือ มีใครใช้ตามนั้นบ้าง คุณเจียวไข่เจียวใช้เท่าไร ผัดข้าวผัดใช้เท่าไหร่ อ่ะ ผัดผักรวมมิตรก็ได้ เอาแบบเต็มเปี่ยมเลย รู้ไหมว่ามีหลายคนเอาไปทำน้ำสลัด OMG ผมถึงบอกอยู่ครับว่า คุณอย่าไปว่าผู้ผลิตเลย เขาปกป้องตัวเองไว้เรียบร้อยทุกมุมอยู่แล้วครับ ถ้าเรายังไม่อ่านฉลาก ซื้อเครื่องไฟฟ้าไม่เคยดูคู่มือ เซนต์สัญญาแบบไม่อ่านก่อน คุณจะว่าใครจริงไหมครับ
ที่น่าสนใจกว่านั้นคือเราเข้าใจกันแล้วใช่ไหมว่า oryzanol ไม่ได้มาจากการกินรำข้าวตรง ๆ แต่ต้องผ่านกระบวนการสกัดที่ซับซ้อนเพื่อได้น้ำมันมาใช้ และวิธีที่อุตสาหกรรมใช้มากที่สุดก็คือ การสกัดด้วยเฮกเซน (Hexane Extraction) ซึ่งเป็นตัวทำละลายเคมีที่อาจมีสารตกค้างในผลิตภัณฑ์สุดท้าย ถึงแม้จะมีวิธีอื่นที่ปลอดภัยกว่า เช่น การสกัดด้วยเอทานอล (Ethanol Extraction), การสกัดด้วยเอนไซม์ (Enzyme-Assisted Extraction), หรือการสกัดด้วยคาร์บอนไดออกไซด์เหนือวิกฤต (Supercritical CO₂ Extraction) แต่ทั้งหมดนี้มีต้นทุนสูงกว่า ทำให้ไม่เป็นที่นิยมในอุตสาหกรรม นั่นหมายความว่า ถ้าผลิตภัณฑ์ที่คุณซื้อไม่ได้ระบุว่าใช้วิธีอื่น ส่วนใหญ่ก็คือเฮกเซนแน่นอน
ข้อเสียของการบริโภค oryzanol มากเกินไปไม่ได้จบแค่การขัดขวางการดูดซึมวิตามิน เพราะการบริโภคในปริมาณสูงอาจส่งผลให้เกิด ความไม่สมดุลของฮอร์โมน เนื่องจาก oryzanol มีโครงสร้างคล้ายกับสเตอรอลในร่างกาย มันอาจไปรบกวนกระบวนการเผาผลาญของสเตอรอยด์ฮอร์โมน เช่น ฮอร์โมนเพศชาย (Testosterone) และฮอร์โมนความเครียด (Cortisol) ซึ่งในระยะยาวอาจส่งผลต่อระบบภูมิคุ้มกัน อารมณ์ และระดับพลังงานของร่างกาย
ประเด็นที่สำคัญคือ ในเมื่อเรามีอาหารจากธรรมชาติที่ช่วยบำรุงหัวใจได้โดยไม่ต้องมีผลข้างเคียง เช่น ไขมันสัตว์ดี ๆ ที่มีวิตามิน A, D, E, K ครบถ้วน ทำไมต้องพึ่งพาสารสกัดจากอุตสาหกรรม ? สิ่งที่ดูเหมือนดีจากงานวิจัยในแล็บ อาจไม่ได้ดีในระยะยาวเมื่ออยู่ในร่างกายมนุษย์จริง ๆ
ทีนี้เรามาดูจุดขายของ น้ำมันรำข้าวกัน - oryzanol เป็นสารธรรมชาติ ทนความร้อนสูง เอาไปใช้ทอดจะไม่เกิดการสลายตัว ทนความร้อนสูงนี่จริงเลยครับ โอริซานอลเป็นสารต้านอนุมูลอิสระในกลุ่ม Ferulic Acid Esters ซึ่งมีโครงสร้างเสถียรกว่าวิตามินอี (เทียบกับวิตามินอีเพราะ ต้านอนุมูลอิสระ และ การปกป้องไขมันจากการเกิดออกซิเดชัน ) มี จุดสลายตัวสูงกว่า 250°C ซึ่งทำให้ยังคงอยู่ได้ในอุณหภูมิที่ใช้ทอดอาหาร แล้วมันแปลว่าดีจริงไหม? ในขณะที่ น้ำมันรำข้าวมีโอเมก้า-6 สูงมาก (30-40%) ซึ่งไวต่อการเกิดออกซิเดชัน ถึงแม้โอริซานอลจะช่วยชะลอการเหม็นหืน แต่มันไม่ได้ช่วยลดการเกิด สารพิษจากไขมันไหม้ เช่น Aldehydes หรือ HNE (4-Hydroxy-2-nonenal) ที่มาจากโอเมก้า-6 หรือเปล่า??? มันคือการพูดให้เราไปโฟกัสจุดเดียวครับ "โอริซานอลทนร้อน ไม่ได้แปลว่า น้ำมันรำข้าวดีต่อสุขภาพ" เพราะโอเมก้า6 ที่ไวต่อการเกิดออกซิเดชัน รวมถึงวิตามินต่างๆ ก็ยังสูญสลายไปด้วยความร้อน นี่ยังไม่รวมถึงโทษของการกินโอริซานอลมากไปตามที่ให้ข้อมูลไว้ข้างบนด้วย
นอกจากนี้ยังมีคนตั้งคำถามไว้มากมายว่า หากโอริซานอลมีผลชัดเจนต่อสุขภาพเช่นเดียวกับที่โฆษณา ทำไมจึงไม่ได้รับการพัฒนาเป็นยาอย่างจริงจัง? หรือคำตอบคือ งานวิจัยที่สนับสนุนโอริซานอลยังไม่เพียงพอ และในหลายกรณี ผลของมันอาจเกิดจาก Placebo Effect (ผลจากความเชื่อว่ามันได้ผล มากกว่าผลจริงๆ ของสารนั้น) ซึ่งเป็นลักษณะเดียวกับ "ยาหลอก" ที่ไม่ได้มีฤทธิ์ทางชีวเคมีที่ส่งผลชัดเจน
-
มีไลโนเลอิกสูง ใช่ครับไม่ผิดเลยในจุดนี้ ไลโนเลอิก (Linoleic acid) เป็น กรดไขมันไม่อิ่มตัวชนิดหลายพันธะ (Polyunsaturated Fatty Acid, PUFA) ที่สำคัญและจำเป็นสำหรับร่างกาย โดยเฉพาะอย่างยิ่งในการช่วยบำรุงเซลล์และระบบต่างๆ ของร่างกาย ที่สำคัญคือ ไลโนเลอิกเป็นกรดไขมันในกลุ่ม โอเมก้า-6 เป็นสิ่งที่บอกกับเราชัดๆว่า โอเมก้า6 สูงนั่นเอง ถ้าจะดึงเฉพาะข้อดีมาคุยกันก็ไม่ผิดอะไรเลยครับ เพราะโอเมก้า6 สำคัญกับร่างกายจริงๆ แต่ แต่ แต่ การรับโอเมก้า-6 ในปริมาณสูงเกินไปอาจทำให้เกิดการอักเสบในร่างกาย ซึ่งเกี่ยวข้องกับโรคต่างๆ เช่น โรคหัวใจ โรคมะเร็ง และโรคเบาหวาน อย่างที่เรารู้กัน ดังนั้นที่บอกไว้ข้างบนครับ สัดส่วนโอเมก้า 6:3 คือ 40:1 หรือใน 1 ช้อนโต๊ะ มีโอเมก้า 6 สูงถึง ราวๆ 4,140 - 5,520 มก. เรียกว่าโฆษณาไม่ผิดเลยเรื่องปริมาณ แต่จริงๆแล้วเราควรรักษาสมดุล โอเมก้า 6:3 ให้ใกล้เคียง 1:1 มากที่สุดเท่าที่ทำได้ เราก็อาจต้องตั้งคำถามอีกทีว่า การมีไลโนเลอิกสูง มันดีจริงไหม
-
โทโคฟีรอล (Tocopherols) เป็นสารประกอบที่อยู่ในกลุ่ม วิตามินอี เป็นสารต้านอนุมูลอิสระในร่างกาย โดยช่วยปกป้องเซลล์จากความเสียหายจากอนุมูลอิสระและช่วยชะลอการเสื่อมของเซลล์ ถูกต้องตามโฆษณา จริงๆหน้าที่หลักคือปกป้องไขมันไม่ให้เกิดการออกซิเดชัน ซึ่งสามารถช่วยยืดอายุการใช้งานของน้ำมัน หรือไม่ให้เกิดการหืน นั่นเอง แต่การทอดหรือปรุงอาหารในอุณหภูมิสูงเกินไป ก็อาจทำให้น้ำมันเกิดการออกซิเดชันและเกิดสารพิษที่เป็นอันตรายต่อร่างกายได้ อย่าลืมนะครับว่าคำแนะนำในการใช้น้ำมันรำข้าว กลับชูการเหมาะกับอาหารทอดอุณหภูมิสูง
-
โทโคไทรอีนอล (Tocotrienols) เป็นส่วนหนึ่งของกลุ่ม วิตามินอี เช่นกัน การบริโภคมากเกินไป การรับประทาน โทโคไทรอีนอลในปริมาณมาก อาจมีผลข้างเคียงที่ไม่พึงประสงค์ เช่น ส่งผลกระทบต่อการดูดซึมวิตามินอื่นๆ ในร่างกายโดยเฉพาะวิตามิน K ซึ่งอาจทำให้เกิดปัญหาการแข็งตัวของเลือด, ทำให้ตับทำงานหนักขึ้นในการจัดการกับสารนี้ ซึ่งอาจส่งผลเสียต่อการทำงานของตับระยะยาว
สุดท้ายแล้ว เราต้องกลับมาตั้งคำถามว่า เราอยากให้สุขภาพของเราถูกกำหนดโดยการตลาดของอุตสาหกรรม หรือโดยสิ่งที่ธรรมชาติออกแบบมาให้เราตั้งแต่แรก ? ถ้าจะดูแลหัวใจจริง ๆ การกินอาหารที่มนุษย์วิวัฒนาการมากับมันมาตลอด เช่น เนื้อสัตว์ ไข่ ตับ และไขมันดี ๆ อาจเป็นคำตอบที่เรียบง่ายและมีเหตุผลมากกว่าการไล่ตามสารสกัดที่อุตสาหกรรมบอกว่าจำเป็น แต่ธรรมชาติอาจไม่เคยเห็นว่ามันสำคัญเลยก็ได้
#pirateketo #ฉลาก3รู้ #กูต้องรู้มั๊ย #ม้วนหางสิลูก
-
-
 @ c8adf82a:7265ee75
2025-04-04 01:58:49
@ c8adf82a:7265ee75
2025-04-04 01:58:49What is knowledge? Why do we need it?
Since we were small, our parents/guardian put us in school, worked their asses off to give us elective lessons, some get help until college, some even after college and after professional work. Why is this intelligence thing so sought after?
When you were born, you mostly just accepted what your parents said, they say go to school - you go to school, they say go learn the piano - you learn the piano. Of course with a lot of questions and denials, but you do it because you know your parents are doing it for your own good. You can feel the love so you disregard the 'why' and go on with faith
Everything starts with why, and for most people maybe the purpose of knowledge is to be smarter, to know more, just because. But for me this sounds utterly useless. One day I will die next to a man with half a brain and we would feel the same exact thing on the ground. Literally being smarter at the end does not matter at all
However, I am not saying to just be lazy and foolish. For me the purpose of knowledge is action. The more you learn, the more you know what to do, the more you can be sure you are doing the right thing, the more you can make progress on your own being, etc etc
Now, how can you properly learn? Imagine a water bottle. The water bottle's sole purpose is to contain water, but you cannot fill in the water bottle before you open the cap. To learn properly, make sure you open the cap and let all that water pour into you
If you are reading this, you are alive. Don't waste your time doing useless stuff and start to make a difference in your life
Seize the day
-
 @ 69e50943:2ac7059c
2025-04-03 23:14:14
@ 69e50943:2ac7059c
2025-04-03 23:14:14This is a test
How does this look?

-
 @ 2b42dd42:5049393c
2025-04-03 21:25:46
@ 2b42dd42:5049393c
2025-04-03 21:25:46this is a test

end of the test
-
 @ 2ed3596e:98b4cc78
2025-04-03 21:20:27
@ 2ed3596e:98b4cc78
2025-04-03 21:20:27We’re giving you the chance to win even more sats through the Bitcoin (Wishing) Well—just for telling us what you love about Bitcoin Well.
Each month, when you leave a review for either the Bitcoin Well portal on Trustpilot (include your WellTag), or our Bitcoin ATMs and (include your transaction ID and email), you’ll be entered for a draw where you can win $210 in bitcoin just for sharing your experience!
Whether it’s our self-custody focus, fast Lightning purchases, Lightning referral payouts, private ATM transactions or our unbeatable customer support, we want to hear what makes Bitcoin Well your go-to place for buying, selling, and using bitcoin.
How to leave your Trustpilot review for our portal
- Head to our Trustpilot page
- Write a quick review sharing your favourite Bitcoin Well feature
- Include your WellTag (or transaction ID), in the review so we can add you to the prize draw
How to leave your google review for one of our ATMs
- Google the Bitcoin Well Bitcoin ATM you recently used
- Write a quick review sharing your favourite Bitcoin Well feature
- Include your transaction ID, in the review so we can add you to the prize draw
It’s that easy! Once your review is verified with your welltag or transaction ID, we’ll add your entry to our monthly draw for your chance to win $210 in bitcoin! We’ll announce the winner and the start of each month. Good luck and keep stacking sats!
What makes Bitcoin Well different
Bitcoin Well is on a mission to enable independence. We do this by making it easy to self custody bitcoin. By custodying their own money, our customers are free to do as they wish without begging for permission. By creating a full ecosystem to buy, sell and use your bitcoin to connect with the modern financial world, you are able to have your cake and eat it too - or have your bitcoin in self custody and easily spend it too 🎂.
Create your Bitcoin Well account now →
Invest in Bitcoin Well
We are publicly traded (and love it when our customers become shareholders!) and hold ourselves to a high standard of enabling life on a Bitcoin standard. If you want to learn more about Bitcoin Well, please visit our website.
-
 @ df67f9a7:2d4fc200
2025-04-03 19:54:29
@ df67f9a7:2d4fc200
2025-04-03 19:54:29More than just “follows follows” on Nostr, webs of trust algos will ingest increasingly MORE kinds of user generated content in order to map our interactions across the network. Webs of trust will power user discovery, content search, reviews and reccomendations, identity verification, and access to all corners of the Nostr network. Without relying on a central “trust authority” to recommend people and content for us, sovereign Nostr users will make use of “relative trust” scores generated by a wide range of independent apps and services. The problem is, Nostr doesn’t have an opensource library for performing WoT calculations and delivering NIP standard recommendations to users. In order for a “free market” ecosystem of really smart apps and services to thrive, independent developers will need access to extensible “middleware” such as this.
Project Description
I am building a library for independent developers to offer their own interoperable and configurable WoT services and clients. In addition, and as the primary use case, I am also developing a web client for “in person onboarding” to Nostr, which will make use of this library to provide webs of trust recommendations for “invited” users.
-
Meet Me On Nostr (onboarding client) : This is my first project on Nostr, which began a year ago with seed funding from @druid. This web client will leverage “in person” QR invites to generate WoT powered recommendations of follows, apps, and other stuff for new users at their first Nostr touchpoint. The functional MVP release (April ‘25) allows for “instant, anonymous, and fully encrypted” direct messaging and “move in ready” profile creation from a single QR scan.
-
GrapeRank Engine (developer library) : Working with @straycat last fall, I built an opensource and extensible library for Nostr developers to integrate “web of trust” powered reccomendations into their products and services. The real power behind GrapeRank is its “pluggable” interpreter, allowing any kind of content (not just “follows follows”) to be ingested for WoT scoring, and configurable easily by developers as well as end users. This library is currently in v0.1, “generating and storing usable scores”, and doesn’t yet produce NIP standard outputs for Nostr clients.
-
My Grapevine (algo dashboard) : In addition, I’ve just wrapped up the demo release of a web client by which users and developers can explore the power of the GrapeRank Engine.
Potential Impact
Webs of Trust is how Nostr scales. But so far, Nostr implementations have been ad-hoc and primarily client centered, with no consistency and little choice for end users. The “onboarding and discovery” tools I am developing promise to :
-
Establish sovereignty for webs of trust users (supporting a “free market” of algo choices), with opensource libraries by which any developer can easily implement WoT powered recommendations.
-
Accelerate the isolation of bots and bad actors (and improve the “trustiness” of Nostr for everyone else) by streamlining the onboarding of “real world” acquaintances directly into established webs of trust.
-
Improve “discoverability of users and content” for any user on any client (to consume and take advantage of WoT powered recommendations for any use case, even as the NIP standards for this are still in flux), by providing an algo engine with “pluggable” inputs and outputs.
-
Pave the way for “global Nostr adoption”, where WoT powered recommendations (and searches) are consistently available for every user across a wide variety of clients.
Timeline & Milestones
2025 roadmap for “Webs of Trust Onboarding and Discovery” :
-
Meet Me On Nostr (onboarding client) : MVP release : “scan my QR invite to private message me instantly with a ‘move in ready’ account on Nostr”. https://nostrmeet.me/
-
GrapeRank Engine (developer library) : 1.0 release : “expanded inputs and output WoT scores to Nostr NIPs and other stuff” for consumption by clients and relays. https://github.com/Pretty-Good-Freedom-Tech/graperank-nodejs
-
My Grapevine (algo dashboard) : 1.0 release : “algo usage and configuration webapp with API endpoints” for end users to setup GrapeRank scoring for consumption by their own clients and relays. https://grapevine.my/
-
Meet Me On Nostr (onboarding client) : 1.0 release : first GrapeRank integration, offering “follow and app recommendations for invited users”, customizable per-invite for Nostr advocates. https://nostrmeet.me/
Prior contributions
-
Last spring I hosted panel discussions and wrote articles on Nostr exploring how to build “sovereign webs of trust”, where end users can have control over which algorithms to use, and what defines “trust”.
-
I contributed gift wrap encryption to NDK.
-
I am also authoring gift wrapped direct messaging and chat room modules for NDK.
-
Last July, I attended The Bitcoin Conference on an OpenSource pass to raise funds for my onboarding client. I onboarded many Bitcoiners to Nostr, and made valuable connections at Bitcoin Park.
About Me
I discovered Nostr in September ‘23 as a freelance web developer, after years of looking for a “sovereignty respecting” social media on which to build apps. With this came my first purchase of Bitcoin. By December of that year, I was settled on “open source freedom tech” (Nostr and Bitcoin) as the new direction for my career.
As a web professional for 20+ years, I know the importance of “proof of work” and being connected. For the last 18 months, I have been establishing myself as a builder in this community. This pivot has not been easy, but it has been rewarding and necessary. After so many years building private tech for other people, I finally have a chance to build freedom tech for everyone. I have finally come home to my peeps and my purpose.
Thank you for considering this application for funding.
-
-
 @ 07f367da:0e76880d
2025-04-03 17:59:21
@ 07f367da:0e76880d
2025-04-03 17:59:21윤석열 탄핵 선고를 앞둔 4월 3일. 우리 노동조합은 서울 마포구 소재의 한 활동지원기관 앞에서 선전전을 진행했다. 노동조합은 한 활동지원사의 민원을 통해 해당 활동지원기관이 일요일에 일해도 평일 임금을 지급한다는 사실을 파악했다. 활동지원사의 민원에 관심을 가진 한 언론사의 기자는 활동지원기관과 구청, 서울시, 노조에 문의하며 팩트체크를 진행하고 있는데, 이 과정에서 노조는 해당 기관이 일요일에 일을 해도 평일 임금을 지급하고 있다는 사실을 명확히 확인했다.
자신이 받는 임금에 대한 사실관계를 노동자들은 잘 알지 못한다. 활동지원사는 기관에 자신의 임금에 대해 문의해도 속 시원한 답을 듣지 못한다. 활동지원사들이 하나같이 하는 이야기가 기관에 물어봐도 제대로 설명을 해주지 않는다는 하소연이다.
당사자 활동지원사는 노조에 민원을 제기하고, 또 기자가 취재한 내용들을 통해서야 자신의 임금이 자신도 모르게 어떻게 변화했는지를 알아가고 있다. 사업장의 임급지급 행위에 대한 가치판단이나 평가 이전에 노동자들은 그 사실 자체를 모를 가능성이 높다. 노조는 이 사실을 활동지원사들에게 알리려 선전전을 진행하기로 했다.
선전전 진행 중 정말 충격적인 경험을 했다. 노동조합의 선전활동은 정당한 노조활동이고 일상적인 활동이다. 여태 여러 사업장에서 선전활동을 했지만, 이런 경우는 정말 처음이었다. 사업장들은 신경 거슬러 하고 적대적인 대우를 하곤 했지만, 가장 강한 대처가 경찰에 신고하여 공권력의 개입을 요청하고, 경찰은 충돌을 방지하는 선에서 대처한다. 그런데 오늘은 장애인 기관장이 선전활동을 하지 말라고 계속 항의하며 방해하더니 소속 활동지원팀 인력은 노동조합이 활동지원사에게 선전물을 전달하려 하니 몸으로 막기까지 한다.
무엇을 그렇게 숨기고 싶을까? 노동조합의 활동을 몸으로 막으면서까지 싫어할 이유가 무엇일까? 노동조합의 활동이 그들에게 무엇으로 다가갔을까? 여러 질문이 든다.
충격적인 것은 이 기관의 대표가 우리노조가 예전에 청와대 앞에서 기자회견 할 때 연대 발언을 하러 왔던 활동가라는 점이다. 장애인 당사자이자 인권운동 활동가가 사용자로, 그리고 사회복지사 노동자들이 전담인력으로 고용되어 사측을 대신해 활동지원사 노동자들이 응당 자신에 대해 알아야 할 사항을 은폐한다.
사장이 되어 권력을 행사하면서도 장애인이라는 정체성으로 자신의 지위를 지우려 하고, 전담인력이라는 지위로 노동자들을 지휘하면서도 같은 노동자라며 위계를 삭제한다. 그리고 정작 현장에서 장애인에게 활동지원을 제공하는 활동지원사들은 대부분 고령의 여성들로 정보약자에 해당한다. 우리에게도 민주주의가 올까. 나는 저들이 활동으로 세상을 좋게 만드는 것을 상쇄할 정도로 더 세상을 나쁘게 만들고 있다고 생각한다.
타인에 의해 돈벌이 수단으로 이용당하는 사람은 자신 또한 타인을 돈벌이 수단으로 활용할 가능성이 높다. 그 타인에는 장애인도 포함된다. 나는 시설사회가 끝나도 장애인학대가 끝나리라는 믿음이 없다. 우리는 어차피 서로를 돈벌이 수단으로만 삼는 사회에서 살고 있기 때문이다.
-
 @ 502ab02a:a2860397
2025-04-03 17:41:20
@ 502ab02a:a2860397
2025-04-03 17:41:20ไฟโตสเตอรอล (Phytosterols) เป็นสารประกอบที่พบในพืชและมีโครงสร้างคล้ายคลึงกับคลอเลสเตอรอล (Cholesterol) ของมนุษย์ แต่ไฟโตสเตอรอลไม่ได้ทำหน้าที่เหมือนคลอเลสเตอรอลในร่างกายครับ ไฟโตสเตอรอลมีบทบาทสำคัญในการลดการดูดซึมคลอเลสเตอรอลจากอาหารในระบบทางเดินอาหาร ทำให้ไฟโตสเตอรอลได้รับการส่งเสริมว่าเป็นสารที่ช่วยลดระดับคลอเลสเตอรอลในเลือดไปโดยปริยาย
อย่างไรก็ตาม สิ่งที่หลายคนไม่ได้ตั้งข้อสงสัยคือวิธีการโฆษณาและการตลาดนั้นจะแฝงไปด้วยข้อมูลที่บิดเบือนเกี่ยวกับไฟโตสเตอรอลซึ่งอาจนำไปสู่การเสพสารนี้ในปริมาณมากเกินไปจนทำให้เกิดปัญหาสุขภาพหรือเปล่า? เราลองมาค่อยๆตั้งคำถามกันครับ
ไฟโตสเตอรอลในธรรมชาติจะพบในปริมาณที่ค่อนข้างน้อยในพืชต่าง ๆ เช่น ธัญพืช ถั่ว เมล็ดพืช อย่างไรก็ตาม ปริมาณไฟโตสเตอรอลในธรรมชาติเป็นเม็ดเป็นผลจะอยู่ในระดับต่ำมาก เช่น ในเมล็ดแฟลกซีด (flaxseed) จะมีไฟโตสเตอรอลอยู่ประมาณ 1,000–2,000 ppm (parts per million) ขณะที่น้ำมันรำข้าวที่มักถูกโฆษณาว่ามีไฟโตสเตอรอลสูงถึงหลักหมื่น ๆ ppm เช่น 12,000 ppm หรือบางยี่ห้ออาจสูงกว่านั้น ซึ่งไม่ใช่แค่สูงจนน่าสรรเสริญ แต่ยังเป็นการขยายความสำคัญของไฟโตสเตอรอลในทางที่ตอบสนองต่อการตลาดได้ในวงกว้างเสียด้วย
กระบวนการผลิตน้ำมันรำข้าวนั้นเริ่มต้นจากการสกัดน้ำมันจากรำข้าว โดยมีการใช้เทคนิคการกลั่นน้ำมันที่สามารถช่วยให้ได้น้ำมันที่มีคุณภาพสูง น้ำมันรำข้าวเป็นน้ำมันที่มีไฟโตสเตอรอลสูงเพราะรำข้าว (bran) ซึ่งเป็นเปลือกที่หุ้มเมล็ดข้าวนั้น มีไฟโตสเตอรอลอยู่ในปริมาณสูงตามธรรมชาติอยุ่แล้ว ในกระบวนการสกัดน้ำมันนั้น ตัวไฟโตสเตอรอลจะถูกรักษาไว้ โดยไม่ต้องเติมเข้าไปใหม่ ดังนั้น เมื่อโฆษณาน้ำมันรำข้าวว่า "มีไฟโตสเตอรอลสูงถึง 12,000 ppm" สิ่งนี้ไม่ได้หมายความว่าเป็นการเติมสารเพิ่มเข้ามาหรอกครับ แต่เป็นการยืนยันถึงความ "เข้มข้น" ของไฟโตสเตอรอลที่มีอยู่ในน้ำมันรำข้าวตามธรรมชาตินั่นละครับว่ามันกลั่นมาเข้มข้นขนาดไหน มากกว่าการกินจากธรรมชาติขนาดไหนเพื่อให้เรากินกันนั่นเอง
ถึงแม้ว่าไฟโตสเตอรอลจะถูกส่งเสริมให้เป็นสารที่ช่วยลดระดับคลอเลสเตอรอลในเลือด แต่การโฆษณาและการตลาดเกี่ยวกับไฟโตสเตอรอลนั้นอาจทำให้คนเข้าใจผิดว่า ผลิตภัณฑ์ที่มีไฟโตสเตอรอลสูง จะช่วยทำให้สุขภาพดีขึ้นและลดความเสี่ยงจากโรคหัวใจและหลอดเลือด เพราะซึ่งสิ่งนี้ยังไม่ได้รับการสนับสนุนอย่างชัดเจนจากงานวิจัยที่สามารถยืนยันได้ในระยะยาว นอกจากนี้ยังมีผลการศึกษาบางชิ้นเช่นกันที่พบว่า การบริโภคไฟโตสเตอรอลในปริมาณสูงอาจ "ไม่ได้มีผล" ในการลดระดับคลอเลสเตอรอลที่น่ามหัศจรรย์หรือช่วยลดการเสี่ยงต่อโรคหัวใจได้ตามที่โฆษณาเอามาขยายความกัน ซึ่งแน่นอนหละครับว่า ถ้าจะทำสงครามวิจัย มันย่อมไม่จบสิ้นเพราะทุกฝ่ายมีการวิจัยสนับสนุนในแบบ peer review ทั้งนั้น ไม่ต้องไปเป็น member อะไรที่ไหน (ถ้าเราไม่คิดจะอ่านมันเอง)
ไฟโตสเตอรอลมีหลายประเภทที่พบในพืชและน้ำมันพืชแต่ละชนิด โดยแต่ละชนิดจะมีคุณสมบัติและผลกระทบต่อร่างกายที่แตกต่างกัน ซึ่งสามารถแบ่งออกเป็นหลายประเภทหลักที่พบได้บ่อยในธรรมชาติ แต่ละประเภทก็มีข้อดีและข้อเสียที่ควรพิจารณาก่อนการบริโภคตามประเภทมันไปครับ
-บีตาสติโรล (Beta-Sitosterol) เป็นไฟโตสเตอรอลที่พบมากในพืชหลายชนิด โดยเฉพาะในเมล็ดพืช ถั่ว และน้ำมันพืช บีตาสติโรลได้รับความนิยมในวงการสุขภาพเนื่องจากการศึกษาบางชิ้นพบว่ามันสามารถช่วยลดระดับคอเลสเตอรอลในเลือดได้ โดยการลดการดูดซึมคอเลสเตอรอลจากอาหารในระบบย่อยอาหาร แต่การบริโภคบีตาสติโรลในปริมาณสูงอาจส่งผลต่อการดูดซึมวิตามินที่ละลายในไขมัน เช่น วิตามิน A, D, E และ K ซึ่งอาจทำให้เกิดการขาดวิตามินเหล่านี้ในระยะยาวได้ นอกจากนี้ การบริโภคบีตาสติโรลในปริมาณที่มากเกินไปอาจส่งผลให้เกิดปัญหาด้านระบบฮอร์โมน โดยเฉพาะในผู้ที่มีปัญหาฮอร์โมนเพศหรือระบบสืบพันธุ์
-แคมป์สเตอรอล (Campesterol) เป็นอีกหนึ่งไฟโตสเตอรอลที่พบในพืชหลายชนิด โดยเฉพาะในน้ำมันพืชและผักผลไม้ แคมป์สเตอรอลมีโครงสร้างที่คล้ายกับคอเลสเตอรอลในร่างกาย และมันได้รับการศึกษาว่ามีคุณสมบัติช่วยลดระดับคอเลสเตอรอลในเลือดได้เช่นกัน อย่างไรก็ตาม การบริโภคแคมป์สเตอรอลมากเกินไปอาจทำให้เกิดผลกระทบต่อการดูดซึมสารอาหารบางประเภท เช่น วิตามินที่ละลายในไขมัน โดยเฉพาะในผู้ที่มีปัญหาทางเดินอาหาร หรือผู้ที่มีปัญหาการดูดซึมสารอาหาร อาจทำให้เกิดภาวะขาดสารอาหารหรือการดูดซึมสารอาหารไม่เต็มที่ได้ นอกจากนี้ การบริโภคแคมป์สเตอรอลในปริมาณสูงอาจส่งผลกระทบต่อการทำงานของฮอร์โมนเพศ เช่น การเปลี่ยนแปลงของฮอร์โมนในร่างกาย ซึ่งอาจเกิดผลเสียต่อสุขภาพในระยะยาว
-สแตกิโอรอล (Stigmasterol) เป็นไฟโตสเตอรอลชนิดหนึ่งที่พบมากในพืชบางชนิด เช่น ถั่วเหลือง และน้ำมันถั่วเหลือง สแตกิโอรอลได้รับการศึกษาในแง่ของการลดการอักเสบและการช่วยบำรุงสุขภาพหัวใจและหลอดเลือด แต่การบริโภคสแตกิโอรอลในปริมาณสูงอาจมีผลเสียต่อการทำงานของฮอร์โมนเพศได้เช่นกัน โดยเฉพาะในผู้ที่มีปัญหาฮอร์โมนไม่สมดุลหรือมีปัญหาเกี่ยวกับระบบสืบพันธุ์ การบริโภคไฟโตสเตอรอลชนิดนี้มากเกินไปอาจทำให้เกิดผลกระทบต่อการทำงานของระบบฮอร์โมนในร่างกาย ซึ่งอาจส่งผลให้เกิดอาการผิดปกติในระยะยาว รวมทั้งความเสี่ยงต่อการมีบุตรหรือสุขภาพที่ไม่ดีเกี่ยวกับระบบฮอร์โมน
ไฟโตสเตอรอลประเภทอื่น ๆ ที่พบในพืชและน้ำมันพืช ได้แก่ อะฟิตเตอร์ออล (Afitosterol) และซิตรัสเตอรอล (Citrusterol) ซึ่งมักพบในน้ำมันจากพืชต่าง ๆ เช่น น้ำมันเมล็ดองุ่น น้ำมันดอกทานตะวัน การบริโภคไฟโตสเตอรอลเหล่านี้ในปริมาณที่สูงเกินไปอาจทำให้เกิดปัญหาด้านระบบย่อยอาหาร หรือปัญหาการดูดซึมสารอาหารที่จำเป็นจากอาหารได้ นอกจากนี้ การบริโภคไฟโตสเตอรอลประเภทอื่น ๆ ในปริมาณสูงยังอาจส่งผลกระทบต่อระบบฮอร์โมนและการทำงานของร่างกายในระยะยาว เช่น การทำงานของระบบภูมิคุ้มกัน หรือการทำงานของตับ ที่อาจได้รับผลกระทบจากการบริโภคในปริมาณสูง ดังนั้น ควรระมัดระวังในการบริโภคไฟโตสเตอรอลจากแหล่งต่าง ๆ อย่างรอบคอบ เพื่อหลีกเลี่ยงผลเสียที่อาจเกิดขึ้นกับร่างกายในระยะยาว
สิ่งที่จริงแล้วอาจเป็นอันตรายมากกว่า คือ การที่ผู้บริโภคตัดสินใจบริโภคผลิตภัณฑ์ที่มีไฟโตสเตอรอลสูงในปริมาณมากเกินไป โดยไม่คำนึงถึงผลกระทบต่อร่างกายในระยะยาว อาจมีผลกระทบต่อการดูดซึมสารอาหารที่จำเป็น เช่น วิตามิน A, D, E, K ซึ่งเป็นวิตามินที่ละลายในไขมัน การดูดซึมของวิตามินเหล่านี้อาจถูกยับยั้งไป เนื่องจากไฟโตสเตอรอลสามารถแข่งขันกับคลอเลสเตอรอลในร่างกายในการดูดซึมสารอาหารเหล่านี้ นอกจากนี้ยังมีข้อกังวลเกี่ยวกับผลกระทบที่อาจเกิดขึ้นจากการบริโภคไฟโตสเตอรอลในปริมาณสูงที่อาจไปเพิ่มความเสี่ยงของการเกิดโรคบางอย่าง เช่น โรคมะเร็งต่อมลูกหมาก
ผลเสียจากการบริโภคไฟโตสเตอรอลมากเกินไปไม่ได้จำกัดเพียงแค่การแย่งสารอาหาร แต่ยังมีการศึกษาที่แสดงให้เห็นว่า การบริโภคไฟโตสเตอรอลในปริมาณสูงอาจกระทบต่อการทำงานของระบบภูมิคุ้มกันของร่างกาย ในบางกรณีไฟโตสเตอรอลอาจเข้าไปแทรกแซงกระบวนการทางชีวเคมีที่สำคัญ และอาจทำให้ร่างกายเกิดความผิดปกติในการตอบสนองต่อสารแปลกปลอมที่มีอยู่ในสิ่งแวดล้อม
ข้อโต้แย้งที่สำคัญคือลักษณะการโฆษณาของน้ำมันรำข้าวและผลิตภัณฑ์ที่มีไฟโตสเตอรอลสูงนั้น ไม่ได้สะท้อนความจริงในสิ่งที่เป็นประโยชน์ต่อสุขภาพจริง ๆ การใช้ไฟโตสเตอรอลในผลิตภัณฑ์ต่าง ๆ โดยเน้นที่ปริมาณที่สูงเกินจริงนั้น เป็นวิธีการตลาดที่ใช้บอกเป็นนัยกับผู้บริโภคให้เข้าใจว่าการบริโภคสารเหล่านี้จะช่วยลดระดับคลอเลสเตอรอลและช่วยให้สุขภาพหัวใจดีขึ้น ทั้งที่ในความเป็นจริง ไฟโตสเตอรอลไม่ได้ช่วยแก้ปัญหาสุขภาพพื้นฐานอย่างการอักเสบที่เป็นสาเหตุหลักของโรคหัวใจและหลอดเลือด แต่ทั้งนี้ทั้งนั้น การโฆษณาดังกล่าวก็อยู่ภายใต้กฎเกณฑ์ของประกาศและกฎหมายต่างๆอยู่ดี ผู้บริโภคจึงควรหาความรู้สนับสนุนการเลือกด้วยตัวเอง ว่าจะตัดสินใจอย่างไร
การที่ไฟโตสเตอรอลมีโครงสร้างที่คล้ายกับคอเลสเตอรอลในร่างกาย ทำให้มันสามารถแทรกซึมเข้าไปในเซลล์ได้คล้ายคลึงกับคอเลสเตอรอล แต่แตกต่างกันตรงที่ไฟโตสเตอรอลไม่สามารถทำหน้าที่ในการสร้างฮอร์โมนต่าง ๆ หรือทำหน้าที่ในระบบร่างกายได้เหมือนคอเลสเตอรอล การที่ไฟโตสเตอรอลแทรกซึมเข้าไปในเซลล์จึงเป็นแค่การสามารถช่วยป้องกันการดูดซึมคอเลสเตอรอลจากอาหารในระบบย่อยอาหารได้ ซึ่งจะทำให้นี่เป็นสาเหตุของการทำให้ ระดับคอเลสเตอรอลในเลือดลดลงได้ พูดง่ายๆคือมันไปแซงคลอเลสเตอรอล อะครับ
นอกจากนี้ ไฟโตสเตอรอลยังสามารถไปแข่งขันกับคอเลสเตอรอลในการเข้าเซลล์ผ่านตัวรับ LDL (low-density lipoprotein receptor) ซึ่งเป็นตัวรับที่ช่วยดูดซึมคอเลสเตอรอลเข้าสู่เซลล์ ดังนั้น เมื่อไฟโตสเตอรอลแทรกซึมเข้ามามากขึ้น ก็จะช่วยลดการดูดซึมคอเลสเตอรอล ที่มาจากอาหารลงไปได้ ทำให้ระดับคอเลสเตอรอลในเลือดลดลง โดยการลดการดูดซึมคอเลสเตอรอลจากทางเดินอาหารเข้าสู่กระแสเลือด แต่ไฟโตสเตอรอลไม่ได้มีผลโดยตรงในการลดคอเลสเตอรอลที่เซลล์ในร่างกายสร้างขึ้นเอง (endogenous cholesterol) เพราะไฟโตสเตอรอลไม่ได้เข้าไปแทรกซึมและทำงานที่จุดที่เซลล์ผลิตคอเลสเตอรอลในร่างกาย
ร่างกายสามารถผลิตคอเลสเตอรอลได้เอง ซึ่งเป็นกระบวนการที่ไฟโตสเตอรอลไม่สามารถไปขัดขวางหรือยับยั้งได้ นั่นหมายความว่า หากร่างกายผลิตคอเลสเตอรอลในระดับสูง ไฟโตสเตอรอลจะไม่สามารถลดระดับคอเลสเตอรอลที่มาจากการสร้างของร่างกายได้ ดังนั้น ไฟโตสเตอรอลมีประโยชน์ในการลดคอเลสเตอรอลจากอาหาร แต่ไม่ได้ช่วยในการลดคอเลสเตอรอลที่ร่างกายผลิตขึ้นเอง
การโฆษณาไม่ได้ให้ข้อมูลในด้านที่ว่า ผลกระทบระยะยาวจากการบริโภคไฟโตสเตอรอลในปริมาณสูงอาจทำให้เกิดปัญหาสุขภาพอื่น ๆ โดยเฉพาะในด้านการดูดซึมสารอาหารหรือความสามารถในการทำงานของระบบภูมิคุ้มกัน ซึ่งเป็นสิ่งที่ควรคำนึงถึงในการตัดสินใจเลือกผลิตภัณฑ์ที่จะนำมาใช้ในชีวิตประจำวัน ในความเห็นของผมนั้น สิ่งที่ควรให้ความสำคัญมากกว่าคือการเลือกบริโภคอาหารที่เป็นธรรมชาติ และหลีกเลี่ยงการพึ่งพาผลิตภัณฑ์ที่มีการผ่านกระบวนการต่าง ๆ เช่น ไฟโตสเตอรอลเข้มข้น หรือสารเติมแต่งอื่น ๆ ที่ไม่จำเป็นต่อร่างกาย การเลือกรับประทานอาหารที่มีคุณค่าทางโภชนาการครบถ้วนจะช่วยส่งเสริมสุขภาพโดยรวมได้ดีกว่าแทนที่จะพึ่งพาสิ่งที่โฆษณาบอกไว้ข้างขวด
ไฟโตสเตอรอลอาจมีคุณสมบัติในการลดการดูดซึมคลอเลสเตอรอลจากอาหารในทางทฤษฎี แต่การบริโภคในปริมาณมากเกินไปนั้นอาจส่งผลเสียต่อร่างกายในหลาย ๆ ด้าน ดังนั้นจึงควรหันมาใส่ใจในข้อมูลที่มีพื้นฐาน และตั้งคำถามกับสิ่งต่างๆ โดยเฉพาะอะไรที่การตลาดตะโกนดังๆว่า ไอ้นี่ดี อันโน้นเยี่ยมยอด อันนี้ที่สุดแห่งความซุปเปอร์ ต่อมเอ๊ะทำงานไว้ก่อน ผิดถูกไม่รู้หาข้อมูลมาโยงเส้นทางแล้วชวนคุยกัน
เช่นเราตั้งคำถามตั้งต้นก่อนไหมว่า จริงๆแล้ว คลอลเสเตอรอล มันต้องกลัวขนาดนั้นเลยหรือ ในเมื่อมันเป็นสารตั้งต้นของชีวิต และเป็นสิ่งจำเป็นในการซ่อมแซมเสริมสร้างร่ายกาย เราต้องลดการดูดซึมด้วยเหรอ
-
 @ 7d33ba57:1b82db35
2025-04-03 17:36:08
@ 7d33ba57:1b82db35
2025-04-03 17:36:08Zadar is a coastal city in northern Dalmatia, known for its rich Roman and Venetian history, stunning sunsets, and unique modern attractions like the Sea Organ and Sun Salutation. With ancient ruins, beautiful beaches, and a lively Old Town, Zadar offers a less crowded but equally charming alternative** to Split and Dubrovnik.
🏛️ Top Things to See & Do in Zadar
1️⃣ Explore Zadar Old Town 🏰
- Walk through narrow, stone-paved streets, surrounded by Roman and medieval architecture.
- Visit People’s Square (Narodni Trg) – The heart of Zadar’s Old Town, filled with lively cafés.
2️⃣ Visit the Sea Organ & Sun Salutation 🎶🌞
- Sea Organ – A one-of-a-kind musical instrument, where waves create natural melodies.
- Sun Salutation – A large solar-powered light display, best seen at sunset.
- Alfred Hitchcock once called Zadar’s sunset “the most beautiful in the world.” 🌅
3️⃣ Admire St. Donatus Church & Roman Forum ⛪
- St. Donatus (9th century) – A unique, round Byzantine-style church with great acoustics.
- Roman Forum – The remains of an ancient Roman marketplace, built in the 1st century BC.
4️⃣ Climb the Bell Tower of St. Anastasia’s Cathedral 🔔
- Enjoy spectacular views over Zadar’s rooftops and the Adriatic.
- One of the tallest church towers in Croatia.
5️⃣ Relax at Zadar’s Best Beaches 🏖️
- Kolovare Beach – The most popular city beach, just a short walk from the Old Town.
- Borik Beach – A sandy beach with shallow waters, ideal for families.
- Punta Bajlo – A more natural and peaceful spot, great for a quiet swim.
6️⃣ Take a Day Trip to Kornati National Park ⛵
- A beautiful archipelago of 89 islands, perfect for boating, swimming, and snorkeling.
- Join a boat tour from Zadar to explore the untouched nature of the Adriatic.
7️⃣ Try Dalmatian Cuisine 🍽️
- Black Risotto (Crni Rižot) – A delicious squid-ink seafood dish. 🦑
- Pag Cheese (Paški Sir) – A famous sheep’s milk cheese from Pag Island. 🧀
- Grilled Adriatic Fish – Freshly caught and served with olive oil & Dalmatian herbs. 🐟
🚗 How to Get to Zadar
✈️ By Air:
- Zadar Airport (ZAD) is just 15 minutes from the city center.
🚘 By Car:
- From Split: ~1.5 hours (160 km)
- From Zagreb: ~2.5 hours (285 km)
🚌 By Bus: Regular buses from Split, Zagreb, Dubrovnik, and Plitvice Lakes.
⛴️ By Ferry: Ferries connect Zadar to nearby islands like Ugljan, Dugi Otok, and Pašman.
💡 Tips for Visiting Zadar
✅ Best time to visit? May–October for warm weather & island trips ☀️
✅ Stay near the Old Town – Everything is within walking distance 🏡
✅ Catch the sunset at the Sea Organ – It’s a must-do experience 🌊🎶
✅ Take a ferry to Ugljan Island for a day of beaches & cycling 🚢🚴♂️
✅ Book Kornati boat tours in advance – They sell out fast in summer! ⛵ -
 @ 5708b1f6:208df3b8
2025-04-03 15:25:33
@ 5708b1f6:208df3b8
2025-04-03 15:25:33The role and significance of music naturally varies from person to person. For some, it is counted among the most important things in life. For others, it may be a superfluous additive of limited value. Due to this difference in perception relating to music, it may be difficult for some individuals to recognize the benefits of compiling a personalized music playlist.
However, the value of music as a therapeutic tool for people already suffering from advanced dementia has been repeatedly demonstrated, and sometimes with astounding, although temporary, results. The internet is full of studies and stories, and YouTube searches yield an abundance of video evidence ranging from clinical studies to anecdotal family recordings of elderly relatives.
All of these data and anecdotes point to a compelling suggestion and an exciting conclusion: music appreciation has tremendous potential as a supplemental activity for mental health maintenance. With insights gained from the study of neuroplasticity, the neurological benefits for musicians and performers are easy to see, but less clear is the fact that mere exposure to music as a casual listener can be of profound psychological importance, even for individuals who don’t consider themselves to be music lovers.
The transformative effect of music is on full display in many of the available videos on YouTube. We can simply search “dementia music,” or ‘Alzheimer’s music” for fast, relevant results. In video after video, we can see elderly subjects who may be slow to speak, detached, disoriented, barely-intelligible, or unresponsive. In care facilities and at gatherings with families, they are interviewed about their youth, and about their feelings related to music.
Many of the videos first show footage of the individual’s normal daily cognitive state, and them listening and responding to the questions, followed by a period of music listening, and then another brief, post-music discussion. The transformation of mental states tends to be very clear when we compare the quality of their cognitive performance before and after the introduction of music. People remark that “a light has been turned back on,” or “his personality returned,” or “it’s as if the person has woken up from sleep.”
Unfortunately, these positive responses are only temporary, and music does not have the power to permanently reverse the symptoms and pathology of advanced dementia and age-related cognitive decline. Also there is no guarantee it will work for every person, or to what degree. Nevertheless, it does not mean that music as therapy is completely without value. In fact, it can be quite the opposite.
When the response is positive, the event can have multiple benefits, and may even be a therapeutic experience for certain listeners. Faces once despondent or vacant become animated and radiant. Long lost smiles return from faraway times and places. Memories and associations from previous ages shake loose and rise to the surface. Many listeners were asked to recount their experiences related to the songs and the time in life with which they were primarily associated. Some of them were able to describe events, places, people, emotions, and reactions with a degree of clarity, dexterity, and articulation that was completely inconsistent with their medical diagnosis and their cognitive performance prior to hearing the music. The song quite literally revives the personality that makes the person, temporarily and superficially reversing the undoing of the mind. For a mind that is coming undone, music as therapy has potential to mitigate suffering and confusion, provide moments of joy and enthusiasm, and ease the transition into and experience of the end-of-life period that awaits all who are fortunate enough to “die of natural causes” in old age.
The benefits described above are specific to “treatment” recipients, but the merit of music as therapy cascades into the lives of everyone involved. Doctors and caretakers are uplifted and encouraged by success stories, which contributes to further proliferation and advancement of music as therapy. More critically, it can have a profound impact on families of dementia patients. In some cases, relatives get a chance to communicate with their loved ones again. Grandchildren have a window of opportunity to learn more, directly from their grandparents, about the youthful experiences and memories of past generations. It’s clear that generational bonds are also strengthened, which can positively impact the future prospects of the young generation as they in turn grow old, and lay new groundwork for generations that follow.
It is unfortunate that some elderly individuals seem to derive less cognitive benefit than others from music therapy. It is not entirely certain why this is so, because there are many factors to consider, but two of the clearest factors are a person’s degree of cognitive decline, and their degree of interest in and enthusiasm for music in general. While these are the most popular metrics by which to judge the potential effectiveness and suitability of music as therapy for a given individual, by far the most important consideration is relevance to each particular person’s life experiences.
This is the opportunity to finally state the obvious: It’s not possible to simply pick any song at random and expect it to have a beneficial effect on the cognitive function of every person who hears it. It’s not as if there’s a Britney Spears song that sparks joy in the heart of every soul on Earth. And the legend of Bill and Ted’s ultimate song that united the world could never be a true story (also because, as we finally learned in 2020, it was not two men and a song that united the world, but rather, the world uniting together to create that song.) However, everyone in the world can make their own playlist custom-tailored to their individual life, experiences, and memories, and some of those playlists might have a song or two by Britney Spears, or even some from one of the “Bill and Ted” soundtracks.
Throughout my decades of music appreciation, an ever-growing level of respect for the enduring spirit of music has overwhelmed me, and it’s clear that no song will ever be loved by all. But every song will be loved by some, certainly at least by someone, or it would cease to exist. This is why a personalized playlist is infinitely more valuable than randomly selected songs, and we can see the truth of this claim upon close examination of recorded interviews with the elderly subjects. The songs that triggered the greatest reactions were songs that interviewees felt strong connections to, based primarily on the song’s associations to the time and place, as well as the emotional context imprinted on the memory of the events surrounding the songs.
This simply means that songs for which we have emotional attachments and vivid memories are songs that invigorate our neural circuits, activating cognitive pathways and opening doors of memory similar to how olfactory sensations can trigger a memory or a sense of déjà vu. There are some exceptions, but a lot of these songs are from a person’s formative years, particularly early developmental years and their teenage period. This comes as no surprise to the discerning neuroplastician, because these are periods of life when neural plasticity is most fluid, neural development and refinement functions are most active and receptive, and the degree of exciting novelty in life tends to be highest when we are young and inexperienced.
Novelty and emotion are critical components of memory formation and whether a given experience will be memorable or not. Something completely new (novelty) can be memorable if it commands your attention, or derails you from your usual pattern of behavior. Similarly, the content of a tedious lecture may be harder to recall without taking notes, while that of an exciting, fun, and funny, interactive lesson has a greater chance of being memorable, and recalled with more clarity and detail (emotion).
When it comes to music, the connection to novelty and emotion is crystal clear. The first time you ever heard that song, it was new and your emotional response was strong. You might even remember the events of that first time you heard it, but not necessarily. Your emotional attachment to the song may have developed later on, when you heard it playing at a party, on one of the most memorable nights of your teenage life, for example. Perhaps it’s just a song (or songs) your parents played a lot when you were young, and it could be a song you yourself heard many times, and looking back realized it holds a special place in your heart, for whatever reason. There are also songs that are special to romantic couples (This song was playing when we…; This is our song; We were together the first time we heard this song; etc.) and these songs, for obvious reasons, can be added to a personalized music playlist at any time in life, as new and old songs take on added personal significance in various ways. There are a multitude of ways that novelty and emotion can combine to form experiences worth remembering, by which memories are made, and if these experiences are imprinted with a musical stamp, the song stamped onto the memory is likely to remain just as memorable as the event itself, and conversely, listening to the song has the potential to vivify the memories and feelings of nostalgia related to the song.
Therefore, as a preventative measure we can implement now, and an insurance policy we may benefit from later, it is advisable that each person should endeavor to compile their own personal, individualized cognitive reserve playlist. When speaking to someone about this idea, they responded, “But what’s the hurry? After all, you’re still quite young.” Just then, it spontaneously occurred to me that a traumatic head injury could befall me the following day or any day hence, and the simple point that “it’s never too early” was well taken.
To create your own cognitive reserve playlist, it is helpful to have a few guiding parameters. Most important of all is to keep an open mind without setting anything in stone. It’s not necessary to finalize the list immediately, if ever. This is a project that deserves your thoughtful consideration, so you deserve to be allowed to take your time. It’s better to get the list populated with your definite favorites, and as many others that come to mind, just to kick-start the process. Besides, due to the virtually infinite number of songs and compositions in existence, we will never be able to make the perfect list in one day, one month, or even one year. We can always revisit the list and make changes later, because our minds cannot retrieve all the data at once. We must go about our business of carrying on, and wait for it to come to us. (It’s guaranteed to be worth the wait, so never fret about it.) You may even find yourself removing one of those “definite favorites” from the list, which is welcome and fine, because it’s not merely a list of your favorite songs. Being a “favorite” is just one of multiple indicators that a song might be appropriate for a cognitive reserve playlist. “Memorable” is another key word.
There are still other factors that determine a song’s suitability for a personal playlist, such as a song that isn’t a personal favorite, but which nevertheless evokes a strong emotional response in some other way. This is best described as nostalgia, and nostalgic emotions are powerful anchors for memories. So any song that arouses some sense of nostalgia also has the power to arouse the memory of events, places, times, and other details tied to that nostalgia. To know what songs are nostalgic for you and add them to your list today, may help you if a time should come that you need music as therapy in order to trigger your memory and cognitive function.
It is because of nostalgia that many songs from our youth are good candidates for inclusion on the playlist. Songs that were popular on the radio or TV when we were children, theme songs from popular television programs that are unforgettable for us, and songs that acted as the soundtrack to our lives, so to speak, while growing into childhood, and then blossoming again from adolescence into adulthood. This period is rich with music of great significance to our personal center.
It is my sincere hope that all people earnestly endeavor to compile their own personalized cognitive reserve playlists, and encourage their loved ones to do the same. Maybe it can help those who suffer to better cope with the condition. Perhaps starting this project now, and focusing on mental health now can be a significant contributing factor to developing robust cognitive reserve in the first place, thereby heading off the worst of what this condition can throw at us, and delaying it until later. And of course, not only should we create the lists, but it’s highly recommended that we also play the songs frequently, and dance to them as well, preferably. It is in the interest of your future health, ability, mobility, enjoyment, and ease of living that I offer this potentially beneficial suggestion, and I am grateful that you have taken the time to hear me out regarding my passion about the restorative and healing properties of music, as they relate to the broader topic of neuroplasticity. So on that note, shall we press play and dance?
-
 @ 8671a6e5:f88194d1
2025-04-03 14:52:44
@ 8671a6e5:f88194d1
2025-04-03 14:52:44\~ The person came up to me from behind his merchandise stand and saw my Noderunners pin on my black t-shirt, then looked me dead in the eye and asked : “So… what do you sell?”
This is the eighth long-read in a series of twelve “food for thought” writings on Bitcoin. It was originally meant to be a few chapters in a book, but life’s too short for that.
Define
Let me start by saying there’s no single way to define or explain a “Bitcoin conference.” The experience can vary depending on a few factors: who’s organizing it (a long-time Bitcoiner or someone from traditional finance trying to grasp Bitcoin), where it’s being held (a sunny paradise like Madeira or a gloomy northern French town), and who’s speaking (technical experts or charismatic entertainers or people with little substance).
Despite these differences, there’s a shared culture that ties these conferences together: a mix of excitement, frustrations, and inevitable evolution. That’s what I explore.
This is just my take, based on what I’ve personally witnessed and what I hear from my surroundings. It’s not meant to be a blanket critique of all Bitcoin conferences as there are plenty I haven’t attended, though I hear about most of them. Even the good ones will evolve into something else over time. So, plan accordingly.
A bit of background on my perspective: at some point in my life, I hit a bump in the road that kept me tied to where I live — a bleak corner of Belgium, surrounded by fiat slaves, shitcoiners, and people who spend six hours a day consuming brain-numbing garbage television. Traveling is an exception for me, but for many Bitcoin conference attendees, it’s a ritual, a must-do event.
So, I view these events with a mix of fascination and grounded skepticism — something I’ve found lacking in many Bitcoiners. I’ve never been to a Bitcoin conference before 2023, despite receiving plenty of invites over the years. From what I heard and saw in photos from friends who attended (even the real early ones) these events seemed eerily similar to the dull hotel conference rooms I once endured in tech and telecom. I’ve had my fill of lukewarm, watery coffee and lifeless speakers droning on about firewalls. So I skipped that particular honor.
Up until around 2018, Bitcoin conferences were a soulless sea of chairs lined up under fluorescent tube lights, draining the life out of attendees—one telecom acronym at a time. Not exactly inviting. Yet, looking back from the perspective of 2025, those were the “pure” days. Back then, people like Roger Ver (before he pivoted to Bitcoin Cash), Andreas Antonopoulos, and encryption specialists spoke to small audiences, explaining Bitcoin in its raw form.
But, like any Bitcoiner, I try to improve myself. So, I made the effort to travel, visit other Bitcoiners, and attend Bitcoin conferences. The conferences I attended in 2023/2024 made me a bit wiser ; not necessarily from what was said on stage (with a few lucky exceptions who still try to bring original thoughts). Most of what I learned came from the long queues, the drama, and watching grifters operate in real time and the good characters floating around.
So, here’s what I’ve learned.

Chain of ticket
I quickly discovered that many Bitcoin conferences have their own “quest for tickets” dynamic, almost like an industry with its own inner circle. It’s a waterfall system: tickets start at lower prices to fill up the venue (usually right after the previous edition). That’s standard practice, both inside and outside of Bitcoin. But what’s strange is seeing organizations that only pop up when a conference needs promotion—somehow securing tickets for themselves and their friends (or for *making* friends) while shilling referral links for small discounts to their followers.
The real free tickets, though, are a hot topic in many local communities and make all the difference for some attendees. What’s particularly interesting is that most ticket prices can be paid in Bitcoin, adding a layer of calculation to the process.
If you paid 230500 sats for your ticket and later see the dollar price fluctuate, say from $180 to $270, or the other way around, by the time the conference starts, you realize you either bought too late or too early.\ It’s better to not have bought at all.
Some ticket holders end up paying less (in dollar terms) than others, making it a gamble. As the event date approaches, ticket prices tend to rise—unless you wait until the last minute, when they haven’t sold out, or just pay at the door. It’s a strange feeling knowing that not everyone paid the same amount (and as mentioned, a significant number get in for free) depending on their timing.
Many organizations and local community representatives show up primarily to be present; securing free tickets, which function more as a badge of recognition than a necessity.\ It’s similar to how a rock groupie sees backstage access: a status symbol, whether for an autograph or something more. Being seen standing next to big names is a huge deal for some, as they derive their own status from proximity.\ This also reinforces the “rockstar status” that conferences create around certain figures, once they come out to take a selfie with some nice people and young fans, then to quickly disappear back to the ‘whale room’ or backstage.
There’s often an entire insider network determining who gets these free tickets. In some cases, it’s naturally tied to the local community, but in others, the professionalism is laughably low. At certain events, you could probably just walk up to the entrance (if there’s even someone checking) and say, “I’m with the organization” to get in for free.
It gets even more absurd.\ At a conference near the French-Swiss border, I was probably one of the very few who actually paid for entry. The real spectacle wasn’t in the talk rooms — which remained eerily empty — but in the dining area, where half the town seemed to have shown up just for the free food. Around 200 people queued for a free lunch, while the presentation halls were at best one-third full throughout the day.
And beyond the ticket games, there are plenty of ways to slip in unnoticed. Carrying a random piece of equipment and mumbling\ “I need to put this crate in the back” can get you past security. Or you can just wait for the one security guard to get distracted by chatting up a girl or stepping out for a smoke, and you’re in. At one event, I walked in alongside someone carrying crates of wine for the VIP lounge. I blended in perfectly (I paid afterward).
So, to sum up: at nearly every conference I’ve been to, a big portion of attendees either walk in for free or hold compensation tickets they got through some connection. Sometimes that connection is uncomfortably close to the organizers. Other times, they just slap an “industry” label on themselves when, in reality, they’re nothing more than a social media bio with a few followers.
Local representatives of a podcast, community, influencer network, or fake marketing club also get in for free. And you? The regular guest, you and I are paying for them. There’s no real vetting process; with some organizers, anyone wearing a Bitcoin t-shirt and saying the magic words “I do community building” or “I know the local Bitcoin meetups” gets a free pass.
The ones who actually want to learn about Bitcoin — the ones who click the link and pay full price — are the ones covering the costs for everyone else and ultimately making these conferences profitable (or at least break even). The problem? They’re the ones left wondering: “Was it really worth my time and money?” only to never return again most of the time.
Because many of the people at these conferences aren’t there to learn. They’re part of the circus. And others? They’re the ones paying for the circus boss, the clowns, and the trapeze artists.
At that one conference with the massive free-lunch crowd, I saw one interesting talk. And I had plenty of valuable conversations and observations — conversations I could have just as easily had by visiting that place outside of a conference setting.
In the end, I realized the main reason I was there was to support a fellow Bitcoiner giving a presentation. And after that? They disappeared from my life. Because, just like in the fiat world, you’re only as good as your last few hours of usefulness to most people.
Which brings me to the next element of Bitcoin conferences...friends
Bitcoin “frens”
This might be the hardest lesson of all: you meet fellow Bitcoiners at these conferences. And some of them? They’re truly special characters. A few even made such a deep connection with not-so-well-traveled-me that I would’ve gladly traveled a full travel day just to spend time working and doing something meaningful together (which I actually did).
But most of these connections? They last only a moment. Few survive beyond the conference, mainly because of the vast distances— both in kilometers (or miles) and in the way we live our everyday lives. The Bitcoiners you meet at these events are, for the most part, just regular people trying to make ends meet in the fiat world while saving in Bitcoin. Or they’re chasing the Bitcoin dream or even find a job in the fata morgana of bitcoin jobs. They act like they belong, like a clown acting like he’s going to climb the trapeze.
I respect that. But over time, I realized that many of them operate in Bitcoin mode; a kind of facade. Behind that front, that mask, most are just testing the waters to see if they can make it. And most don’t.\ Treating Bitcoin as a lifestyle movement, a career shortcut, or an identity, has its limits. Eventually, the real person breaks through. And you have to face your own instincts and personality.\ I’ve tried to be an acrobat, and ride the lion, make the audience laugh, but I’m still the seal who’s brought back to the cage after he balanced a ball on his nose. The quote “I’m Jack’s wasted life.” came to mind often when standing somewhere at a conference space.
Self-doubting people stay self-doubting, owning Bitcoin or not. Emotional wrecks remain emotional wrecks — just with Bitcoin now. And when these masks slip off, you’ll see everything: the greed, the overconfidence, the longing for drama, the addictions, the narcissism, the energy-draining personalities, sleaziness usually with the ones who always say the right oneliners or wear the right Bitcoin merch to blend in.
And you can love people for that. Everyone has flaws. Everyone has a price as well.
But these Bitcoin “frens” can also hurt you badly. Because as Bitcoiners, we carry hopes. And hopes are like ants on a sidewalk, they’ll eventually get crushed.\ We long to meet people who see the same truth, the same vision of Bitcoin as we do. Some will act like they actually understand and do, they talk the talk for a while, as if they’re parroting a podcast.
If you stay in the shadows - like I did for years - you won’t have to deal with these things. If you never try, you’ll never be let down. But you still stay in the imaginary basement, letting yourself down. That’s not the bitcoin style. We router around problems. Even if we stand amidst the problems (like a conference).
But if you do? There’s a hefty price to pay — beyond just the money spent. It’s a cost paid in energy, emotions, and social interactions and above all: time.
And once in a while, you’ll meet a friend for life.
Just be prepared:
Bitcoin is a journey that few people you encounter at a conference can take for longer than four years, or even four hours of conversation actually.
And then, after navigating the social maze of Bitcoin conferences —the connections, the masks, the fleeting friendships, the smell of weed and regret — you find yourself facing an even greater challenge: the queue at a coffee stall.

## \ The Soviet LN Queue
It’s one of the most fascinating and frustrating aspects of every conference: the insanely long lines. Whether it’s for the toilets, a coffee booth, or some niche merchandise stall, you’ll see Bitcoiners waiting like it’s 1963 after a Soviet state bakery just got fresh deliveries.
waiting for coffee Seriously, aren’t we supposed to be the pinnacle of free-market efficiency? Instead, we’ve somehow perfected the art of the long food lines. I remember people waiting in line for like 35 minutes to order a cappuccino!
The usual culprit? A mix of payment chaos and the Bitcoin Orangepill mental issues in action.
A large portion insists on using Lightning (as in "their preferred lighting wallet"), which would be fine except they’re fumbling with some exotic, half-working wallet because using something that’s actually fast might get them sneered at for being “custodial.”
On top of that, vendors are juggling card payments, cash, various Lightning POS systems, and even the occasional cutting edge dudes trying to pay with an Apple Watch or worse, some newly released Lightning-enabled gadget that doesn’t work yet. And when it does work, it requires so much attention and Instagram footage that it takes five minutes just to hand someone a coffee while the guy pays with a lighting NFC ring on his finger, something you can't use ànywhere else ever. It’s cool. But not to anyone else than you.
So, here’s a tip for the regular people, the rats that pay for all of this : sneak out.
Then you find a small, locally owned café outside the conference, pay them in cash, and actually enjoy your food in a few seconds or minutes.
If (and only if) they accept Bitcoin, great! Tip them well. Otherwise, just relax and have a conversation with a local, all the while inside the conference venue there are Bitcoiners filming each other struggling to make a payment with the latest Lightning-enabled NFC card or making the staff uneasy.
Meanwhile, some poor 22-year-old café worker is trapped in an unsolicited podcast participation:
“Wait, you accept tips in Wallet of Satoshi? Who told you that? I’ll explain it to you!”
Or worse:
“Hold on, I just need to do a quick swap… It’s an on-chain transaction, the last block was 19 minutes ago, can’t be long now… wait… umm… do you take VISA?”
At this point, ordering a simple drink at a Bitcoin conference has become an unnecessarily complex, ego-driven performance. With long queues as a direct result. And don’t get me started on the story when 30+ bitcoiners walked in to a Portuguese restaurant without a reservation, and they all wanted to pay with different payment methods. It was like the Vietnam war.
Solution:
A tip for conference organizers and their catering : pick one Bitcoin point of sales system, set clear guidelines, and make everyone stick to them. Instruct people to adhere to the following :
Pay with a (bank) card, cash, or Lightning and PLEASE decide beforehand which method you’re using before ordering your stuff! We prefer lighting.
If you’re using Lightning, have enough balance on you wallet or get lost.
Use a compatible wallet. (Provide a tested “approved” list and train staff properly. Users who use other stuff get their order “cancelled” at the first sign of trouble. Your app‘s not scanning, or not compatible, or it has some technical mumbo-jumbo going on to your vpn LN node at home 2000 km away? Please get real and pay with a bank card or something.
No filming, duck-facing (like it's 2017) or stupid selfies with your payment. It’s been done a thousand times by now. There are people in line, waiting behind you, they want to order as well, while you have your little ego trip or marketing moment. Move on please!
“Our staff knows how bitcoin payments work, you don’t need to #orangesplain it to anyone.” We don’t care about your 200th LN app or the latest “but… this one is faster” thingy. Order your drinks, pay and get out of the way please.
Bitcoin fixes many things. But it hasn’t quite fixed this yet.
The bitcoin conference axiom
Going to a conference, versus keeping your bitcoin in your wallet is a tough choice for many.
If you pay nothing for tickets and lodging, while enjoying free meals and cocktails, your opportunity cost drops close to zero —yet your networking and social impact are maximized while you can also do business. That’s ideal. At least, for you. In such case, Bitcoin may only "win" over an extended timeline, but for you, it's essentially a free ride. You incur no real opportunity costs. You drink their milkshake.
On the other hand, if you’re a regular attendee, you pay full price: the ticket, overpriced drinks and food from the stands (losing even more if you generously pay for coffee in sats), plus extras like t-shirts and books (which you’ll never read). Your milkshake gets taken—at least half of it.
If you’re lucky, you might spend an evening in town with the event’s "stars"—those occasional luminaries who briefly grace the normies with their presence for a drink. Some can’t even hold their liquor. Year after year, the same 10 to 15 speakers or panelists appear, funded by your dime, traveling the world and enjoying the perks—some even cultivating fan bases and hosting exclusive parties.
The real opportunity cost hits hardest for regular attendees who come to learn, shelling out significant money while accumulating their fourth hardware wallet or yet another orange-themed t-shirt. They might even squeeze in a selfie with a former sportswear model turned Bitcoiner. For normies (as they’re often called), the financial and social scales rarely tip in their favor.
Calculating the conference opportunity cost
To determine the opportunity cost of attending a conference instead of investing in Bitcoin, over time follow these steps:
-
Calculate your total conference expenses, including tickets, travel, food, drinks, and lodging (merchandise and donations).
-
Estimate Bitcoin’s percentage gain over the conference period and the following year(s). (in order to not make you cry, I suggest nog going over 5 years)
-
Multiply your total conference cost by this percentage to determine the potential Bitcoin profit you forgo.
-
Assign a dollar value to the networking or business opportunities you expect to gain from the conference (if you’re not just in it for the laughs, meeting high-class consultants, friendships, self-proclaimed social media Bitcoiners, or the occasional gyrating on one of the musicians/artists/food stall staff members).
-
Subtract this “networking” value from the missed Bitcoin profit to find your net opportunity cost (this is rather personal,… with me it’s zero, but for someone selling t-shirts it’s probably much more).
If the result is negative over the chosen timeframe, the conference was financially worthwhile for you. If positive, holding or buying Bitcoin was the smarter move.
Unless you’re a recognized speaker in this traveling circus, your opportunity cost will likely be positive — meaning all the others lose hard money, while fumbling with your Lightning wallet.
The Conference Opportunity Cost Formula
Let:
CT = Total conference ticket & entrance cost (in dollars)
CR = Total related conference costs (travel, lodging, food, etc.)
C = CT + CR (Total cost)
G = Bitcoin’s % gain per year (as a decimal, e.g., 5% = 0.05)
N = Estimated fiat value of networking/business opportunities and knowledge gained.
OC = (C × G) − N
Where:
OC (Opportunity Cost) < 0 → The conference was worth attending.
OC (Opportunity Cost) > 0 → Holding/buying Bitcoin was the better move.
Some example calculations (I've left out examples before 2020, I don't want people crying or waking up at night thinking "Why did I go to Amsterdam in 2014?!")
example : Conference in April 2024 Entrance: $200 Lodging, t-shirt, and travel: $900 Bitcoin's estimated gain: 23% (0.23) No business / knowledge value gained OC = (200 + 900) × 0.23 - 0
- $253 OC (Bitcoin would have been the better choice.)
Conference in April 2020 (adjusted for historical Bitcoin growth) Entrance: $175 Lodging and travel: $700 Bitcoin's estimated gain: 1089% (10.89) No business / knowledge value gained OC = (175 + 700) × 10.89 - 0 OC = +$9,529 (Massive missed gains — Bitcoin was the clear winner.
--
So the first lesson in bitcoin should be: Only attend conferences if you get paid to do so and get a free ticket and free lodging, which kind of would kill that whole industry to begin with.
Energizing
At first, it’s energizing to meet like-minded bitcoiners, but after a while, you realize that a big chunk of them are just trying to sell you something or aren’t really bitcoin-focused at all. And some of them are just looking for their next way to kill time and boredom.
The drama that comes with attending these conference and the personal interaction can get pretty intense at times, since expectations often don’t match the personalities. Before you know, you’re walking around at night through some bad part of a town, while crying your eyes out because you thought you found your soulmate.
Future pure industry conferences will suffer less from this drama, because everyone there has the same goal — pushing their company or product— while the “other” grassroots conferences are more of a meeting spot for bitcoiners of all types and perspectives, bringing the usual drama and mess that comes with human interactions. Current conferences are a mix of both usually.
I think the current era of bitcoin conferences is coming to an end. Soon, probably by the end of 2025, we’ll see a clear split between industry-driven and human-driven (grassroots) smaller conferences, and it’ll be really important to keep these two separate.
I even had the idea to launch a sort of conference where there wouldn’t be any industry speakers or companies present. Just bitcoiners gathering at a certain place at a specific week and having a good time. I called it “club Sat” And you could just go there, and meet other bitcoiners, while acting there was a big venue and speakers,… but there aren’t any. Would be refreshing. No struggle for tickets, no backstage stuff, no boring talks and presentation,… just the surroundings and the drama lever you want and probably like.
On stage
The podium is usually left for the known names. Not every conference is like that, but most of them need these names, badly. These names know each other, they encounter one another in VIP rooms and “the industry” a lot of times anyway.
The same people you see in the bitcoin news, the same people having a cult following, and the very same people traveling, staying and drinking for free while spreading the same bitcoin wisdoms will be invited over and over again.
Or… they go rock around as they’re usually so bored they had to start a rock band to entertain themselves. Which is rather entertaining if you’re following up on who does what, but in the end it’s largely just for their own amusement and it shows. I get that. I would do the same. It’s fun and all.
It’s just a bit sad that there are only a small group of top-layer speakers, and then the sub-top that usually has more to say, or gets little opportunity. The reason for that is simple: the “normies” who pay in full for tickets, come there for the “big” names. They don’t know that much about bitcoin usually, so they’re not waiting on some unknown dude explaining something about an obscure niche subject. A debate can help remedie this, to mix it in with some lesser known names, but I have the feeling the current “line-up” of bitcoin conferences feels like a rock festival in 2025 putting the Stone temple pilots or Creed on the card.
Yes, they’ll attract an audience and do their playset well,… but it’s not exactly the pinnacle of the music industry at the moment, neither is Madonna by the way :)
Promoting anything
The people organizing these events usually aren’t Bitcoiners either — they’re promoters (few exceptions though).

They don’t care if they organize a symposium about a newly discovered STD, A three-day cheese tasting event, a Star Trek convention, or a Lucha Libre wrestling tournament featuring El HODLador, as long as they can sell tickets and make money from merchandise they're good. The last thing on the mind with some of them will be helping bitcoin adoption. There will be a time (soon) where people that know bitcoin, known bitcoiners and know how to organize events get their act together. It will be different than the early days, and it will be different than the boring going-through-the-motions conferences we have now. There shall be fun, social gatherings, life, excitement and culture, and not the “what do you sell?” atmosphere, neither the “this old dude on stage again”?
That’s why they’ll slap any semi-famous name on the poster to pull in a crowd - could be a washed-up Mexican wrestling star with strange legal issues, the cheese-tasting equivalent of Usain Bolt, or your neighborhood Bitcoin old-timer with a beard and a "best selling author" label.
It’s also why most of these conferences end up being more about shitcoins than anything else. And even if they're for the most part about bitcoin, the venue is usually infested with marketing budgets, useless organizations that wanted complimentary tickets (some of them do only one thing: popping up when a conference is nearby and then they’re gone again) ... along with some hawking consultant types you never see anywhere else.
They'll occasionally pay people but usually in fiat, or if you're a bigger name, you might get other deals. For artists or staff, it's all in fiat from what I heard.
Pure Bitcoin conferences, also rely on these big names. Whether it’s a well-known Bitcoiner, a CEO, president, or someone with real reveling knowledge to share with the audience (though that last type is getting rare).
Looking for love in all the wrong places
\ Let’s also address the fair share of “orange diggers” at Bitcoin conferences—because yes, they exist. And no, let’s not single out one particular gender here.
Some people treat a Bitcoin conference like a live-action dating app mixed with a financial vetting process for potential partners. It’s essentially an opportunity to inspect and assess the grab bag of fintech, crypto, and Bitcoin folks in real life.
And if you think this is exaggerated, just attend a few conferences—three is enough. You’ll start noticing the same people popping up, seemingly without any real Bitcoin knowledge, but with a very strong interest in dining, chatting, and generally being around—as long as you look and play the part. I can only imagine how dialed-up this effect must be at a shitcoin conference — probably like flies on a cowpie.
The trick is, in Bitcoin, these people try to blend in. Some even tag along with real Bitcoiners, while others just crash the party and try to get noticed. Their actual interest in Bitcoin? Close to zero. Their main target? Your wallet, or some fantasy thing about getting to know someone out of the ordinary.
And that’s a shame for the people who genuinely care about Bitcoin, who want to network, or who simply are looking for like-minded people. They often find themselves competing for attention with those who’ve turned “being noticed” into a sport, while the rest just wander around, lost in the shuffle. Talk to the quiet ones. Certainly if they look like they belong in a antiques shop.
My advice: Talk to people and be genuine. If you don’t know much about Bitcoin, that’s fine - nobody expects you to be a walking whitepaper and on top of that, most people you'll encounter don't know that much either. It’s bitcoin: we’re all rather average people that hold an extraordinary asset.
Just don’t be "that orange digger" looking for a partner with a loaded bag of bitcoin.
Because in the end, what’s the prize you win? You don’t know who’s under the mask. You don’t even know who’s under your own mask.
Finding a man or woman at a place where half the people are laser-focused on financial sovereignty, and the other half are busy arguing about seed phrase storage, UTXO management, and why your Lightning wallet sucks? But good luck with that. The judge of character usually comes when they find the next shiny object or ditched you standing in the rain at the entrance of a restaurant while dealing with a lightning watchtower or a funny cigarette or whatever.
If you’re truly looking for love, maybe stick to going to a normal bar. If you’re here to learn, connect, and be part of something of a grassroots movement, then be real yourself.
I've seen some rather nasty examples of people at Bitcoin conferences—of all kinds. And I've also seen some really cool examples of truly awesome people. This led me to believe that Bitcoin conferences simply let you meet… people, just dialed up a bit.
Future If you encounter rotten people, they’ll usually be even more rotten than in the fiat world. If you meet really cool people, they’ll be even more awesome than the cool people in the fiat world.
Our volatility is our freedom. So, I guess it’s normal. Doesn’t make it any easier, though.
Bitcoin sees through bullshit, and so do Bitcoiners (even if it takes 21,000 blocks)
Pretty soon, I reckon we’ll see conferences fork into two camps: grass roots, and the “industry” level ones. (human / corporate) I guess I’ll only attend the human part, for sure, but I can’t help but booking myself a single room in a hotel in a nice area in that case, so I don’t have to deal with class of 2022 hippies sharing referral links to their middleman service while asking me for a lighter 3 times in a row. The chances for me of meeting cool bitcoiners in a nearby cocktail bar are a lot higher.
In the meanwhile, I’ll look forward and see how the bitcoin conferences will evolve, fork in two “styles”. One corporate and one underground. Maybe there will be one more genre just for the fun of it.
I’ll stay away, as I don’t like this current mix of industry gigs and having the insiders and “the rest” of us all mingled together clamoring for tickets, attention and coffee. The game is rigged. Staying at home is the better option (for now).
written by AVB
If you like : tip here
-
-
 @ f1989a96:bcaaf2c1
2025-04-03 14:30:08
@ f1989a96:bcaaf2c1
2025-04-03 14:30:08Good morning, readers!
Georgian officials froze the bank accounts of five nonprofit organizations that provide financial and legal support to detained protesters. This follows rising public unrest as Georgia’s regime pushes new laws restricting free speech and assembly, introducing new fines and penalties, and expanding law enforcement powers. By eroding civil protections, the regime makes it more dangerous and costly for activists, dissenters, and everyday citizens to stand up against an increasingly repressive regime.\ \ Meanwhile, the Indian government introduced a new income tax bill that grants tax authorities sweeping surveillance power over anyone they “suspect” of tax evasion. If suspected, tax authorities are legally allowed to access Indians' email, social media, and bank accounts, raising obvious concerns over state overreach and invasions of individual financial privacy.\ \ In freedom tech news, HRF donated 1 billion satoshis to more than 20 projects worldwide, focusing on supporting human rights defenders and vulnerable communities under authoritarian regimes across Asia, Africa, and Latin America. These gifts advance censorship-resistant communications and transactions, bitcoin education, and privacy tools so that dissidents, nonprofits, and individuals may better protect their human rights and financial freedom. In this letter we also spotlight a new open-source mobile Bitcoin wallet called Cove. While still in beta, the wallet can be used with a hardware device or on its own as a hot wallet, offering a flexible self-custody setup for managing Bitcoin.
We end with a podcast in which HRF Chief Strategy Officer Alex Gladstein discusses the state of freedom tech and why Bitcoin stands as the most promising tool for financial liberation.
Now, let’s get right to it!
SUBSCRIBE HERE
GLOBAL NEWS
Georgia | Officials Freeze Accounts of Organizations Supporting Protesters
Georgian officials have frozen the bank accounts of five nonprofit organizations that provide financial and legal aid to dissenters. This comes in response to an uprising of protests over new controversial laws that restrict free expression and assembly, increase fines and detention periods, and expand law enforcement powers. Georgian officials justify the account freezes as part of an investigation into “sabotage,” yet they have provided no evidence. Amnesty International warns this financial assault could “kill the entire protest movement.” Bitcoin provides a way to circumvent these struggles. Its uncensorable and permissionless nature has helped sustain pro-democracy movements across Belarus and Nigeria, proving it is capable of addressing the immense financial restrictions dictators impose.
United Arab Emirates | Plans to Launch “Digital Durham” CBDC in 2025
The United Arab Emirates (UAE) will launch its central bank digital currency (CBDC), the “Digital Durham,” by the end of 2025. According to the central bank, the CBDC will be available through licensed financial institutions and operate via a government-run digital wallet. Every transaction will be recorded on a permissioned blockchain run by the government. The central bank further admitted the CBDC will replace cash and assist law enforcement “by leaving a digital trail for transactions involving illicit funds.” Officials claim this is to combat financial crime, but it also enables real-time surveillance and tracking of individual financial activity. In a country known for strict laws against dissent and extensive surveillance capabilities, it is not hard to see how a CBDC will erode the autonomy and rights of activists, dissenters, and others who oppose an increasingly authoritarian regime.
India | Grants Tax Authorities Access to Citizens’ Online Data
Starting in April 2026, the Indian government will grant tax authorities legal access to the private online data of any citizen “suspected” of tax evasion. This will include legal access to personal emails, social media, and bank accounts. The new law expands on the Income Tax Act of 1961, which previously limited officials to searching physical premises for financial documents. Now, officials can bypass digital security measures and access private data without consent — all under a legal framework. This dissipation of financial privacy sets an intrusive precedent and opens the door to state-level corruption and surveillance in a country where the Modi regime has already made it clear they are happy to use financial repression to further cement their power.
Myanmar | Bitcoin as a Tool Support Earthquake Disaster Relief
Last week, a 7.7 magnitude earthquake struck central Burma, with strong tremors reaching neighboring Thailand. The official death toll has surpassed 2700. And in Bangkok, a 33-story building under construction collapsed. Despite an already strenuous situation, Burma’s military junta continues its oppression. They are blocking rescue teams from reaching the Sagaing region — the epicenter of the earthquake and the heart of Burma’s pro-democracy movement — and instead channeling aid to regime-controlled cities like Naypyidaw and Mandalay. The junta is also continuing to conduct air strikes on civilians and restricting equipment and fuel for aid groups, leaving a million people in Sagaing to fend for themselves. In these repressive circumstances, Bitcoin can provide a censorship-resistant way to send funds directly to those affected.
Angola | Regime Jacks Price of Diesel
The Angolan regime raised diesel prices by 50% in the process of eliminating fuel subsidies. Diesel prices suddenly increased from 200 to 300 kwanza per liter, driving up transportation costs in a country where over half the population lives on less than $2 a day and inflation is over 42%. Previous fuel subsidy cuts in 2023 (where the price of diesel rose 80%) sparked protests between taxi drivers, nonprofit workers, and law enforcement. This recent price increase now raises fears of renewed crackdowns. The Angolan regime also introduced new civil society laws that Guilherme Neves, chairman of the human rights organization Associacao Maos Livres, describes as a “license to erase non-governmental organizations that are not government-compliant.” Angolans find themselves in increasingly precarious financial positions as the government erodes the civil safeguards protecting nonprofits and dissenters.
Nicaragua | Ortega’s Dismantling of Press Freedom
Since coming to power in 2007, Ortega has closed or seized 61 media outlets, imprisoned countless journalists, and forced over 280 journalists into exile. His assault on press freedom has unfolded in two phases: initial raids on local radio stations and TV channels between 2007 and 2017, followed by full-scale censorship in 2018 on independent media outlets like La Prensa and CONFIDENCIAL. Ortega then intensified attacks from 2019 to 2021 by closing Nicaragua’s second-oldest newspaper and passing laws to criminalize free expression. This is a deliberate strategy to eliminate dissent and independent voices. What’s happening in Nicaragua highlights the importance of open and decentralized protocols like nostr, which allow journalists to publish freely without getting censored. While still early, it is becoming essential for sharing information absent the fear of being blocked or silenced by autocratic leaders.
BITCOIN AND FREEDOM TECH NEWS
HRF | Gifts 1 Billion Satoshis to 20+ Open Source Projects Worldwide
HRF gifted 1 billion satoshis in its Q1 2025 round of Bitcoin Development Fund (BDF) grants, supporting more than 20 open-source projects around the world. These projects advance Bitcoin education, open-source software, mining decentralization, and privacy tools for activists contending with authoritarian regimes across Asia, Latin America, and Africa. Supporting permissionless financial tools and censorship-resistant technologies empowers dissidents, journalists, and civil society to organize, transact, and communicate without state suppression and interference. Learn more about the grantees and their work here.
Cove | New Open-Source and Permissionless Bitcoin Wallet
Cove is a new open-source and permissionless mobile Bitcoin wallet that aims to put users in full control of their Bitcoin. Users can connect their own hardware wallet (to manage Bitcoin offline) or use Cove as a hot wallet (to manage Bitcoin online). It also allows users to create multiple wallets from the app itself. In the future, Cove plans to add Unspent Transaction Output (UTXO) selection and coin control, giving users more independence over their transactions and the tools to better protect their financial privacy. While still in beta and only suitable for test funds, this wallet holds promise as a privacy tool to equip dissidents with self-custodied Bitcoin. You can try it here.
Second | New Ark Implementation Launches on Bitcoin Signet
Second, a company building on Ark, a protocol designed to help scale Bitcoin’s transaction throughput, launched “Bark.” Bark is a test implementation of the Ark protocol deployed on Bitcoin’s Signet network (where developers test software). More broadly, the Ark protocol helps make Bitcoin transactions more private, faster, and cheaper, supporting the network in handling more transactions and users with the tradeoff of being less trusted than the mainchain, as funds stored in a noncustodial way on Ark can expire if not used. While it is still in early development, the test release of Bark marks a step toward deployment on the main Bitcoin network. Scaling solutions like Ark could be important for activists and individuals. They might ensure Bitcoin remains accessible to all, even as block space demand increases and network fees rise. Learn about it here.
Braiins | Open Sources Bitcoin Control Board
Braiins, a company building tools for Bitcoin mining, open-sourced its BCB100 Bitcoin Control Board, giving miners using their products greater insight and control over their Bitcoin mining hardware and firmware. Sharing the design files and firmware openly helps strengthen Bitcoin’s decentralization, making it more resilient against corporate or state interference. Specifically, open-sourcing mining hardware ensures individual miners can operate independently, reducing censorship risks across the entire network. In turn, this preserves financial freedom by keeping Bitcoin accessible and usable by dissidents, nonprofits, and individuals who need it most.
African Bitcoiners | Publish Bitcoin Starter Guide
African Bitcoiners just published “Bitcoin: Africa’s Guide to Freedom Money,” a Bitcoin guide providing clear, practical insights into how Bitcoin can help people across the continent escape inflation, corrupt regimes, and failing financial systems. It covers essential topics to get started — from choosing a wallet to properly securing Bitcoin. In Africa, where some of the world’s longest-standing dictators restrict even basic financial activity, this guide is a powerful resource for human rights defenders, nonprofits, and everyday citizens. Read it here.
OpenSats | 10th Wave of Nostr Grants
OpenSats, a nonprofit that supports open-source software development, announced its tenth wave of grants for projects in the nostr ecosystem. Nostr is a decentralized protocol that enables digital identity and communications outside the reach of authoritarian states. The grant round provides support to nostr Epoxy, which enhances access to nostr by circumventing censorship through a network of paid proxies. This ensures activists and dissidents can continue to communicate even in restrictive environments. Additionally, Zapstore received a grant for providing a permissionless app store built on nostr that enables developers to distribute software without corporate gatekeepers. This provides an open-source alternative to centralized app stores that often comply with government censorship and restrict dissidents’ access to freedom tools.
RECOMMENDED CONTENT
Freedom Tech with Alex Gladstein
In this episode of The Gwart Show, Alex Gladstein, chief strategy officer at HRF, breaks down how and why Bitcoin serves as “money dictators can’t stop.” Drawing on more than 17 years of human rights work, he shares real-world examples of activists and citizens using Bitcoin to escape financial repression in authoritarian countries. Gladstein also explores privacy tools, cross-border payments, and why Bitcoin offers promising hope for financial freedom. Watch the full conversation here.
The State of Personal Online Security and Confidentiality with Meredith Whittaker
In this keynote for SXSW 2025, Signal CEO Meredith Whittaker shares her growing concerns around AI, personal data collection, and the erosion of privacy in today’s increasingly digital world. She emphasizes the need for more secure, uncensorable, and privacy-protecting technologies that shield users from surveillance and exploitation, especially in the context of authoritarian regimes. Watch the full discussion for a pragmatic view into the future of digital privacy and security.
If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.\ Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
-
 @ 1aa9ff07:3cb793b5
2025-04-03 14:06:38
@ 1aa9ff07:3cb793b5
2025-04-03 14:06:38In an era where centralized platforms dominate the internet, concerns over censorship, privacy, and data ownership have led to the rise of decentralized alternatives. One such innovation is Nostr, a lightweight and resilient protocol designed to enable censorship-resistant and decentralized communication. In this article, we will explore what Nostr is, how it works, its advantages, and why it is gaining traction among privacy advocates and decentralized technology enthusiasts.
What is Nostr?
Nostr (Notes and Other Stuff Transmitted by Relays) is an open protocol designed for creating censorship-resistant social networks and communication platforms. Unlike traditional social media networks, which rely on centralized servers controlled by corporations, Nostr operates on a decentralized model using cryptographic keys and relays.
Nostr allows users to publish and receive messages without the need for a central authority. It is not tied to any single application but instead provides a foundation upon which developers can build various types of social and communication tools.
How Does Nostr Work?
Nostr consists of two main components:
- Clients – Applications that users interact with, such as social media platforms, chat applications, or blogging tools.
- Relays – Servers that distribute messages between clients without storing them permanently or acting as gatekeepers.
When a user wants to send a message or publish content, their client signs the data using their private key and broadcasts it to multiple relays. Other users who subscribe to those relays can receive and interact with the messages.
Nostr does not have a concept of user accounts managed by a central entity. Instead, identity is established using public and private cryptographic keys. The private key is used to sign messages, while the public key acts as the user’s identity across the network.
Advantages of Nostr
-
Censorship Resistance – Since Nostr does not rely on a central authority, it is much harder for governments or corporations to censor content. Users can publish messages freely, and if one relay refuses to distribute them, they can simply use another.
-
Privacy and Security – Messages are signed using cryptographic keys, ensuring authenticity and reducing the risk of impersonation. Users retain full control over their identities and content.
-
Interoperability – Nostr is not tied to a single platform or application. Developers can create different types of services using the protocol, from microblogging platforms to encrypted messaging apps.
-
Resilience – Since the network relies on multiple relays instead of a single centralized server, it is less susceptible to shutdowns or attacks.
Use Cases for Nostr
- Decentralized Social Media – Platforms like Twitter alternatives can be built on Nostr, allowing users to post updates without fear of censorship.
- Private Messaging – Secure and encrypted messaging applications can be developed using the protocol.
- Blogging and Content Publishing – Writers and journalists can publish articles in a censorship-resistant manner.
- Bitcoin and Cryptocurrency Communities – Many Bitcoin enthusiasts are adopting Nostr due to its decentralized nature and alignment with privacy-focused principles.
Challenges and Limitations
While Nostr is a promising technology, it is still in its early stages and faces several challenges:
- Adoption and Network Effects – Since Nostr is not as widely used as traditional social media platforms, building a strong user base is a challenge.
- Spam and Moderation – Without central moderation, handling spam and malicious content is more difficult, requiring innovative solutions such as reputation-based filtering.
- User Experience – Decentralized networks often have a steeper learning curve for new users compared to centralized platforms.
The Future of Nostr
Despite these challenges, Nostr is gaining momentum among privacy advocates, developers, and decentralized technology supporters. With continued development and improvements in usability, Nostr has the potential to reshape online communication by offering a truly decentralized and censorship-resistant platform.
As more developers create applications and services using Nostr, its ecosystem is likely to expand, providing a viable alternative to traditional social media networks. Whether you are a developer, a privacy-conscious user, or someone interested in the future of decentralized internet, Nostr is a technology worth exploring.
Conclusion
Nostr represents a significant step toward a more open and decentralized internet. By removing central points of control and enabling user-driven communication, it empowers individuals to interact freely without the risk of censorship or data exploitation. As the protocol matures and more applications emerge, it could play a crucial role in shaping the next generation of online communication.
If you are interested in experimenting with Nostr, you can start by exploring various Nostr-based applications, setting up your cryptographic keys, and connecting with the growing community of users and developers. The future of decentralized communication is just beginning, and Nostr is at the forefront of this movement.
Understanding Nostr: A Decentralized Social Network Protocol
In an era where centralized platforms dominate the internet, concerns over censorship, privacy, and data ownership have led to the rise of decentralized alternatives. One such innovation is Nostr, a lightweight and resilient protocol designed to enable censorship-resistant and decentralized communication. In this article, we will explore what Nostr is, how it works, its advantages, and why it is gaining traction among privacy advocates and decentralized technology enthusiasts.
What is Nostr?
Nostr (Notes and Other Stuff Transmitted by Relays) is an open protocol designed for creating censorship-resistant social networks and communication platforms. Unlike traditional social media networks, which rely on centralized servers controlled by corporations, Nostr operates on a decentralized model using cryptographic keys and relays.
Nostr allows users to publish and receive messages without the need for a central authority. It is not tied to any single application but instead provides a foundation upon which developers can build various types of social and communication tools.
How Does Nostr Work?
Nostr consists of two main components:
-
Clients – Applications that users interact with, such as social media platforms, chat applications, or blogging tools.
-
Relays – Servers that distribute messages between clients without storing them permanently or acting as gatekeepers.
When a user wants to send a message or publish content, their client signs the data using their private key and broadcasts it to multiple relays. Other users who subscribe to those relays can receive and interact with the messages.
Nostr does not have a concept of user accounts managed by a central entity. Instead, identity is established using public and private cryptographic keys. The private key is used to sign messages, while the public key acts as the user’s identity across the network.
Advantages of Nostr
-
Censorship Resistance – Since Nostr does not rely on a central authority, it is much harder for governments or corporations to censor content. Users can publish messages freely, and if one relay refuses to distribute them, they can simply use another.
-
Privacy and Security – Messages are signed using cryptographic keys, ensuring authenticity and reducing the risk of impersonation. Users retain full control over their identities and content.
-
Interoperability – Nostr is not tied to a single platform or application. Developers can create different types of services using the protocol, from microblogging platforms to encrypted messaging apps.
-
Resilience – Since the network relies on multiple relays instead of a single centralized server, it is less susceptible to shutdowns or attacks.
Use Cases for Nostr
-
Decentralized Social Media – Platforms like Twitter alternatives can be built on Nostr, allowing users to post updates without fear of censorship.
-
Private Messaging – Secure and encrypted messaging applications can be developed using the protocol.
-
Blogging and Content Publishing – Writers and journalists can publish articles in a censorship-resistant manner.
-
Bitcoin and Cryptocurrency Communities – Many Bitcoin enthusiasts are adopting Nostr due to its decentralized nature and alignment with privacy-focused principles.
Challenges and Limitations
While Nostr is a promising technology, it is still in its early stages and faces several challenges:
-
Adoption and Network Effects – Since Nostr is not as widely used as traditional social media platforms, building a strong user base is a challenge.
-
Spam and Moderation – Without central moderation, handling spam and malicious content is more difficult, requiring innovative solutions such as reputation-based filtering.
-
User Experience – Decentralized networks often have a steeper learning curve for new users compared to centralized platforms.
The Future of Nostr
Despite these challenges, Nostr is gaining momentum among privacy advocates, developers, and decentralized technology supporters. With continued development and improvements in usability, Nostr has the potential to reshape online communication by offering a truly decentralized and censorship-resistant platform.
As more developers create applications and services using Nostr, its ecosystem is likely to expand, providing a viable alternative to traditional social media networks. Whether you are a developer, a privacy-conscious user, or someone interested in the future of decentralized internet, Nostr is a technology worth exploring.
Conclusion
Nostr represents a significant step toward a more open and decentralized internet. By removing central points of control and enabling user-driven communication, it empowers individuals to interact freely without the risk of censorship or data exploitation. As the protocol matures and more applications emerge, it could play a crucial role in shaping the next generation of online communication.
If you are interested in experimenting with Nostr, you can start by exploring various Nostr-based applications, setting up your cryptographic keys, and connecting with the growing community of users and developers. The future of decentralized communication is just beginning, and Nostr is at the forefront of this movement.
-
 @ edeb837b:ac664163
2025-04-03 10:35:59
@ edeb837b:ac664163
2025-04-03 10:35:59When it comes to social trading, there are plenty of platforms that claim to offer innovative ways to connect with other traders, share strategies, and improve your market performance. But let's be real: most so-called "social trading" apps are either glorified brokerage platforms with limited community features or outdated, clunky systems that don’t offer real-time value.
There’s really only one social trading app you need to consider—NVSTly. Here’s why.
Why NVSTly Stands Above the Rest
NVSTly isn’t just another trading app with a few social features slapped on. It’s the ultimate social trading platform, purpose-built to empower traders by combining real-time trade tracking, seamless social sharing, deep market insights, and a powerful trader community.
Unlike other platforms, NVSTly isn’t just about copying trades or following vague signals—it’s about true transparency, collaboration, and learning from top traders in an interactive environment.
What is NVSTly?
NVSTly is a completely free social trading platform that lets traders track, share, and analyze their trades in real time. Whether you're trading stocks, options, or crypto, NVSTly provides a seamless multi-platform experience—available via web, iOS, Android, and even Discord.
It’s not just a social network—it’s a trader’s command center where every trade you make is part of a bigger, smarter ecosystem designed to help you grow.
Key Features That Make NVSTly #1
1. Real-Time Trade Sharing & Tracking
NVSTly integrates with brokers like Webull (with more brokerages coming soon) to automatically track your trades and display them in real-time. No manual entry—just instant trade updates for you and your followers.
2. Unique POV Trade Charting
See trades like never before. NVSTly’s proprietary POV Chart marks every trade action directly on the candlestick chart, giving you (and your followers) an unparalleled view of trading strategies in action.
3. Deep Trade Analytics & Trader Dashboards
Get powerful insights into your performance, including: - Win rate - Total gain/loss - Average return per trade - Long vs. short ratio - (Coming soon) Drawdown tracking to measure risk exposure
4. Global Trades Feed & Leaderboard
Want to see what the best traders are doing right now? The Global Trades Feed lets you watch live trades, while the Leaderboard ranks top traders based on performance metrics, making it easy to find successful strategies.
5. Fully Integrated with Discord & Telegram
No other platform makes social trading as seamless as NVSTly. The NVSTly Discord bot allows users to: - Check a trader’s latest stats - View real-time trade recaps - Fetch charts and ticker data - Receive automated trade notifications
Telegram users won’t be left out either—NVSTly is working on bringing the same functionality to Telegram for even broader access.
6. Automated Social Media Sharing
Set your trades to automatically share to Twitter/X, Discord, and soon, Telegram. Whether you’re growing your personal brand or running a trading community, NVSTly makes sure your trades get noticed.
7. Future AI & Machine Learning Enhancements
NVSTly is building AI-powered trade insights and strategy generation, allowing traders to: - Get automated trading tips tailored to their strategies - Use customizable AI models to refine their trading approach - Interact with a smart AI trading assistant via the app and Discord bot
Why NVSTly is the Only Social Trading App You Need
While others might pretend to offer social trading, NVSTly actually delivers. It’s not a gimmick or a half-baked feature—it’s a complete trading ecosystem built for real traders who want real-time data, powerful analytics, and a truly social experience.
With NVSTly, you're not just following traders—you’re engaging with them, learning from them, and improving your own strategies in the most transparent and interactive way possible.
So don’t waste time on inferior platforms. NVSTly is the only social trading app that matters.
Ready to Take Your Trading to the Next Level?
Join 50,000+ traders who are already using NVSTly to track, share, and dominate the markets.
📲 Download NVSTly today on Web, iOS, or Android!
🚀 Join our Discord community and bring the power of NVSTly straight into your server!
-
 @ 2b24a1fa:17750f64
2025-04-03 10:11:13
@ 2b24a1fa:17750f64
2025-04-03 10:11:13Ist es wirklich so, dass Gendern für mehr Gleichberechtigung sorgt, für ein friedlicheres Miteinander? Abgesehen von den grammatikalischen Verirrungen, die sich dabei in die Sprache schleichen, darf die Frage erlaubt sein, warum ein Gemeinschaftsgefühl, das „Wir“ in immer kleinere Einheiten, auch sprachlich geteilt werden soll. Muss ich tatsächlich alle benennen?
https://soundcloud.com/radiomuenchen/gendern-die-sakralsprache-des?
Dann wäre das eine Liste von Namen. Verlese ich die nicht, sondern gendere mit Glottisschlag und allem was dazu gehört, unterteile ich ja doch in Gruppen. Und Gruppen haben zur Eigenart, dass es Zugehörigkeiten gibt und ausgeschlossen sein. So beginnt der Kampf. Zunächst war die Frau minderwertig, jetzt ist der Mann toxisch. Und was, wann zu wem, wie gesagt werden darf wird zum Spießrutenlauf. „Misgendern“ ist beispielsweise eine Wortneuschöpfungen, die eine Incorrectness der Sprache bezeichnet, die bis in die Strafbarkeit reichen will.
Einer, der von dieser rigide anmutenden Sprach-Religion getriggert wird, ist Gerald Ehegartner. Er ist Lehrer, Musiker, Theater- und Wildnispädagoge und Autor und nimmt sich immer wieder dem Gemeingut Sprache an. Heute mit einem Text, den er mit: „Gendern, die Sakralsprache des Wokeismus“ betitelt hat.
Sprecherin: Sabrina Khalil
-
 @ 2b24a1fa:17750f64
2025-04-03 10:05:21
@ 2b24a1fa:17750f64
2025-04-03 10:05:21Der Deutsche Bundestag wurde neu gewählt. Für einige Abgeordnete und Regierungsmitglieder heißt es Time to Say Goodbye. Abschied ist ein scharfes Schwert. Auch bei Radio München werden Trennungs- und Verlassenheitsgefühle getriggert. Umso mehr, wenn es sich nicht nur um duselige Allerweltsliebe handelt, sondern um den Abgang großer Helden.
https://soundcloud.com/radiomuenchen/nachruf-3-christian-der-wachstumliche
Sie bezahlten ihren todesmutigen und fast ehrenamtlichen Einsatz nicht mit dem Leben, jedoch mit der einen oder anderen Falte in Hemd oder Bluse, manchmal sogar im Gesicht. Was bleibt? Eine bescheidene Pension? Ein lausig bezahlter Manager-Job in einem Konzern? Wir wollen jedenfalls nicht, dass diese Volkshelden vom Zahn der Zeit abgenagt, vergessen werden und setzen ihnen deshalb ein bescheidenes akustisches, aber nachhaltiges Denkmal. Hören Sie die kleine satirische Reihe „Nachrufe“ von unserem Autor Jonny Rieder.
Folge 3: Christian der Wachstümliche
Sprecher: Karsten Troyke
Bild: Markus Mitterer für Radio München
Radio München
-
 @ 2b24a1fa:17750f64
2025-04-03 10:03:24
@ 2b24a1fa:17750f64
2025-04-03 10:03:24Der Deutsche Bundestag wurde neu gewählt. Für einige Abgeordnete und Regierungsmitglieder heißt es Time to Say Goodbye. Abschied ist ein scharfes Schwert. Auch bei Radio München werden Trennungs- und Verlassenheitsgefühle getriggert. Umso mehr, wenn es sich nicht nur um duselige Allerweltsliebe handelt, sondern um den Abgang großer Helden.
Sie bezahlten ihren todesmutigen und fast ehrenamtlichen Einsatz nicht mit dem Leben, jedoch mit der einen oder anderen Falte in Hemd oder Bluse, manchmal sogar im Gesicht. Was bleibt? Eine bescheidene Pension? Ein lausig bezahlter Manager-Job in einem Konzern? Wir wollen jedenfalls nicht, dass diese Volkshelden vom Zahn der Zeit abgenagt, vergessen werden und setzen ihnen deshalb ein bescheidenes akustisches, aber nachhaltiges Denkmal. Hören Sie die kleine satirische Reihe „Nachrufe“ von unserem Autor Jonny Rieder.
Folge 4: Annalena die Völkerballerina
Sprecher: Karsten Troyke
Bild: Markus Mitterer für Radio München
-
 @ 2b24a1fa:17750f64
2025-04-03 09:57:35
@ 2b24a1fa:17750f64
2025-04-03 09:57:35Es sind immer die gleichen Mechanismen: Die Faktoren Zeitdruck und Angst machen enorm viele Menschen gefügig. 500 Milliarden Euro für Infrastruktur und den sogenannten Klimaschutz, 400 Milliarden für die Bundeswehr – also fast eine Billion Euro Schulden, innerhalb von weniger als vier Wochen nach der Wahl mit Winkelzügen den Bundesbürgern auferlegt.
https://soundcloud.com/radiomuenchen/es-lebe-die-freiheit-verdammt?
Wahlversprechen oder Parteiprogramme, das auf keinen Fall zu tun, sind Makulatur. Keine Diskussion über einen Haushalt, keine Diskussion über die Notwendigkeiten und schon sind Fragen anhängig, ob die Aufträge, die nun vergeben werden, nach den rechtmäßigen Ausschreibungskriterien vonstatten gehen, oder ob auch bei diesen unvorstellbaren Summen die Spezlwirtschaft im Land fortgeführt wird.
Wo ist der Wille des Volkes geblieben? Wo die Freiheit, tatsächlich über unser Leben und Wirtschaften zu entscheiden?
Der Autor, Wirtschafts- und Finanzexperte Andreas Geltinger schaut auf die einstigen Ideen wirtschaftlichen Handelns und analysiert, womit wir es jetzt zu tun haben.
Sprecher: Karsten Troyke.
-
 @ 2b24a1fa:17750f64
2025-04-03 09:34:29
@ 2b24a1fa:17750f64
2025-04-03 09:34:29Kartografiert, aufgekauft, betoniert, beschildert. Wo ist die Freiheit? Wo ist Platz zum Erforschen im Nicht-Definierten? Also wo sind die Erfahrungsräume, die sich von Generation zu Generation üblicherweise immer wieder die Jugend erobert, um darin zu wachsen und zu reifen?
https://soundcloud.com/radiomuenchen/abwartend-skeptisch-von-kenneth-anders
Perspektivwechsel: Wo sind eigentlich die Jugendlichen abgeblieben, die nach diesen Räumen Ausschau halten? Sie bewegen sich in „Spaces“. Seit Corona staatlich verordnet, suchen sie auf flachen Bildschirmen, in einer artifiziellen Welt, ihren Horizont zu erweitern.
Der Kulturwissenschaftler Kenneth Anders hat sich auf Spurensuche bei Jugendlichen auf dem Land gemacht. Hören Sie sein Resumée mit dem Titel „Abwartend skeptisch“.
Nachzulesen ist der Beitrag auf der Webseite: oderamazonas.de
Sprecherin: Sabrina Khalil
Bild: KI
www.radiomuenchen.net/\ @radiomuenchen\ www.facebook.com/radiomuenchen\ www.instagram.com/radio_muenchen/\ twitter.com/RadioMuenchen
Radio München ist eine gemeinnützige Unternehmung.\ Wir freuen uns, wenn Sie unsere Arbeit unterstützen.
-
 @ 2b24a1fa:17750f64
2025-04-03 09:28:52
@ 2b24a1fa:17750f64
2025-04-03 09:28:5221 Monate, also fast zwei Jahre verbringt Johanna Findeisen bereits in Untersuchungshaft. Trägt sie reichsbürgerliche Ideen mit sich? Oder hat sie Straftaten geplant? Es ist ein Fall im sogenannten „Reichsbürgerprozess“. Mit diesem beschäftigt sich einer ihrer Anwälte Prof. Martin Schwab. Bei den Prozessen, so der Jurist, gehe es eher um Gesinnungsfragen.
Fakten zu Straftaten, auch geplanten, seien nicht aufzufinden. Und eine Untersuchungshaft für die Aufdeckung einer möglicherweise falschen Gesinnung – die Johanna Findeisen vehement bestreitet - ist in unserem Rechtssystem nicht vorgesehen. Dennoch sind die Termine für diese Untersuchungen bereits bis 2026 anberaumt.
Das soll aber heute nicht unser Thema sein. Es geht um die Untersuchungshaft selbst. Prof. Martin Schwab ist in regelmäßigem, telefonischen Kontakt mit Johanna Findeisen und stellt dort Verhältnisse fest, die den Tatbestand der Folter erfüllen. Kein Mensch, selbst der Verurteilte, darf in seiner Menschenwürde herabgesetzt werden. Nun wird der Fall Johanna Findeisen bislang lediglich untersucht. Wie kann also sein, dass sie im Transport zum Gericht gefesselt wird? Warum wurde sie bei ihrer Rückkehr körperinvasiv untersucht? Was übrigens nach einem öffentlichkeitswirksamen Antrag ans Oberlandesgericht erfolgreich unterbunden wurde. Warum wird ihre Post zurückgehalten? Warum durfte sie, bei zwei Stunden Besuchszeit im Monat, ihren Angehörigen nur hinter einer Scheibe begegnen? Warum wird sie, ohne Morgentoilette, abgeholt und in eine fensterlose Zelle ins Gericht gebracht, wo sie zwei Stunden bis zum Gerichtstermin ausharren muss? Und warum wird die fiebernde Johanna, bei Minusgraden und offener Türe gezwungen, sich nackt auszuziehen, sich zur Wand zu drehen und sich einer erniedrigenden Leibesvisitation zu stellen?
Auch dem Pfarrer und Autor Jürgen Fliege geht dieser Fall nah und fragte sich, was Johanna Findeisen, neben einer guten Verteidigung gebrauchen könnte und er ihr geben: Beistand! Hören Sie seinen offenen Brief an die Inhaftierte.
Sprecherin: Sabrina Khalil.
Wer sich gegen die – in einzelnen Haftanstalten – untragbaren Zustände, gegen die dortigen Menschenrechtsverletzungen engagieren möchte, kann das beispielsweise auf der Webseite www.folter-nein-danke.eu tun.
-
 @ 2b24a1fa:17750f64
2025-04-03 09:28:32
@ 2b24a1fa:17750f64
2025-04-03 09:28:32„Das ist ein netter alter Onkel, der sich bemüht, der Welt Gutes zu tun“, antwortete Anfang 2021 der Sohn einer Freundin auf ihre Frage, was Bill Gates mit der Pandemie zu tun haben könnte. Ich erinnere mich, damals wurde man als Verschwörungstheoretiker tituliert, und zwar maximal abwertend, wenn man allein den Namen ins Spiel brachte. Es ist wirklich Zeit, sich wieder für das Ansehen der Verschwörungstheorie einzusetzen, denn ohne sie wird kein einziger Kriminalfall aufgedeckt, der von mehr als einer Person durchgeführt wurde.
Kommen wir zum dritten Teil der Reihe „Corona-Connection“ von Milosz Matuschek in dem er sich in deren Epizentrum begibt. Bill Gates, der undemokratisch zu Macht gekommene, selbsternannte Philanthrop, gehört zu den Hauptfiguren der USAID, der United States Agency for International Development. Matuschek geht hier auf das Geschäftsmodell des Philanthrokapitalismus ein.
Sabrina Khalil hat seinen Text gelesen. Diesen und die zwei ersten Folgen finden Sie auf Matuscheks Seite: Freischwebende Intelligenz.
-
 @ 502ab02a:a2860397
2025-04-03 08:31:07
@ 502ab02a:a2860397
2025-04-03 08:31:07ที่มาทำเพลง #ตัวหนังสือมีเสียง
วันนี้จะเล่าถึงเพลง ตรุษจีนครับ เป็นเพลงที่เขียนเสร็จภายในคืนเดียว คือไม่ใช่ว่าเก่งกาจอะไรครับ แต่เนื้อหามีในหัวตั้งนานแล้วตั้งใจจะทำนานแล้วแต่ภารกิจอื่นมีมากจน 24 ชั่วโมงมันรู้สึกน้อยเกินไป
เพลงนี้ความตั้งใจคือ หวังสูงเลยครับ หวังว่าสักวันหนึ่งเยาวราชจะเปิดเพลงนี้กันกระหึ่มในวันตรุษจีน ซึ่งรู้ตัวดีครับว่า ตัวเล็กๆ คงไม่ดังเปรี้ยงในรอบเดียว ผมคิดว่า จะอีก 5ปี 10ปี เพลงนี้มันปล่อยไปแล้วมันยังอยู่ไปเรื่อยๆครับ (เปิดตัวครั้งแรก มีคนเอาแผ่นเสียง tiktok ไปทำอวยพรกันราวๆ 185คลิป ผมดีใจมากแล้ว บางคนลิปซิงค์ด้วยแสดงว่าหัดร้อง โคตรดีใจเลยครับ)
ผมตั้งใจทำให้โทนออกมาเป็นเหมือนคนจีนร้อง แนวประมาณฮอทเป๊บเปอร์ โซเฟียลา อะไรประมาณนี้ ดังนั้นการออกเสียงจะเหมือนคนจีนพูดไทยไม่ชัดอะไรแบบนั้นครับ
เนื้อร้องนี่ผมตั้งใจเขียนแบบ เอาใจอาม่าเลย เราลองมาดูบางท่อนกันครับ
"ซินเจียยู่อี่ ซินนี้ฮวดไช้ วันตรุษจีนนี้ ขอพรจากใจ จะทำสิ่งใด ขอให้เฮงเฮง" เป็นท่อนย้ำแล้วย้ำอีก เพราะจงใจให้เป็นเพลงอวยพร ก็เลยทำเป็นแกนหลักของเพลงนี้ จากนั้นตัวรองก็จะเป็นคำอวยพรในแต่ละเรื่อง มาซ้อนอีกทีนึง
"ปีใหม่หวังได้สุขดี โรคภัยไม่มี แข็งแรงกว่าใคร เลือดลม กำลังภายใน เดินวิ่งยังไหว ได้เที่ยวทั้งปี" ท่อนนี้ผมนึกถึงอาม่าของผมครับ แกชอบดูหนังกำลังภายใน วีดีโอม้วนเป็นชุดๆ แล้วการได้ไปเที่ยวเรื่อยๆก็เป็นอีกความสุขนึงของคนแก่ ไม่ได้ต้องการอะไรมากไปกว่าร่างกายแข็งแรง เดินเหินไหว เที่ยวได้
"ไม่เพียงแค่ในปีนี้ แต่ขอให้ดี ทุกทุกปีไป ครอบครัวยิ้มได้ละไม ทุกคนสุขใจ เฮงเฮงดีดีดี" เป็นท่อนท้ายเพลงแล้ว ซึ่งก็ตบด้วยว่าไม่ได้เฉพาะปีนี้นะ ที่อวยพรกันขอให้ดีไปยาวๆ แล้วก็เล่นคำท้ายว่า "เฮงเฮงดีดีดี" คือ มันเป็นการรวมคำดีๆย้ำๆ ผมรู้สึกว่าพอตอนที่ทำเป็นเพลง มันจะเป็นท่อนที่คนยิ้มกว้างเลยหล่ะ
เนื้อเพลงเต็มๆผมลงไว้ให้ข้างล่าง ส่วนการรับฟัง สามารถเข้าได้หลายทางมากครับ youtube music https://music.youtube.com/watch?v=EBKTZv3VvGM&si=f_IMFbDhdEJ6wEcv
spotify https://open.spotify.com/track/3fCJyoQVAeWxdczfGbL3yT?si=vHV45hUTRPO6Mg9Pnh-w2w
apple music https://music.apple.com/th/album/%E0%B8%8B-%E0%B8%99%E0%B9%80%E0%B8%88-%E0%B8%A2%E0%B8%A2-%E0%B8%AD-%E0%B8%8B-%E0%B8%99%E0%B8%99-%E0%B8%AE%E0%B8%A7%E0%B8%94%E0%B9%84%E0%B8%8A/1789787248?i=1789787249
tiktok แผ่นเสียง https://vt.tiktok.com/ZSrk49SfL/
ส่วนเพลงอื่นๆ ฟังเต็มๆได้ทุก music plattform แล้วนะครับ ค้นหา heretong teera siri เพราะเพลงไม่ดังเลยต้องหาจากชื่อคนแทนครับ 55555
新正如意,新年发财 วันตรุษจีนนี้ขอพรจากใจ จะทำสิ่งใด ขอให้เฮงเฮง
ปีใหม่หวังได้สุขดี เป็นเศรษฐีมีเงินทองใช้ ร่ำรวย รุ่งเรืองไปไกล คิดสิ่งใด ได้สมฤดี
ซินเจียยู่อี่ ซินนี้ฮวดไช้ วันตรุษจีนนี้ขอพรจากใจ จะทำสิ่งใด ขอให้เฮงเฮง
ปีใหม่หวังได้สุขดี โรคภัยไม่มี แข็งแรงกว่าใคร เลือดลม กำลังภายใน เดินวิ่งยังไหว ได้เที่ยวทั้งปี
ซินเจียยู่อี่ ซินนี้ฮวดไช้ วันตรุษจีนนี้ขอพรจากใจ จะทำสิ่งใด ขอให้เฮงเฮง
ไม่เพียงหวังได้สุขดี โรคภัยไม่มี แข็งแรงกว่าใคร เลือดลม กำลังภายใน เดินวิ่งยังไหว ได้เที่ยวทั้งปี
ซินเจียยู่อี่ ซินนี้ฮวดไช้ วันตรุษจีนนี้ขอพรจากใจ จะทำสิ่งใด ขอให้เฮงเฮง
ไม่เพียงแค่ในปีนี้ แต่ขอให้ดี ทุกทุกปีไป ครอบครัวยิ้มได้ละไม ทุกคนสุขใจ เฮงเฮงดีดีดี
ซินเจียยู่อี่ ซินนี้ฮวดไช้ ขอจงมีความสุขใจ อวยพรนำชัย ให้ทั่วทุกคน ขอจงมีความสุขใจ อวยพรนำชัย ให้ทั่วทุกคน ขอจงมีความสุขใจ อวยพรนำชัย…ให้จงรุ่งเรือง
pirateketo #siripun #ตำรับเอ๋ #siamstr
-
 @ c13fd381:b46236ea
2025-04-03 07:55:31
@ c13fd381:b46236ea
2025-04-03 07:55:31Over the past few years, The School of Bitcoin (TSOBTC) has built a reputation as a decentralised, open-source educational initiative dedicated to financial sovereignty and digital literacy. Our faculty, contributors, and global community have worked tirelessly to create resources that embody the Free and Open-Source Software (FOSS) ethos, ensuring that knowledge remains accessible to all.
As part of our commitment to maintaining an open and transparent model, we are excited to announce that The School of Bitcoin is officially migrating to Consensus21.School. This transition is not just a rebranding--it marks the consolidation of all our initiatives, projects, and educational resources under the Consensus21.School banner. The School of Bitcoin will no longer exist as a separate entity.
This move comes as a response to growing confusion between our initiative and another entity operating under the domain schoolofbitcoin (SOB), which has taken a direction that does not align with our open-source philosophy. To reaffirm our dedication to FOSS and community-driven education, we are bringing everything--our courses, programs, and collaborations--into a singular, more focused ecosystem at Consensus21.School.
What Does This Mean for Our Community?
Rest assured, all the valuable content, courses, and educational materials that have been developed under TSOBTC will remain available. We continue to embrace a value-for-value model, ensuring that learners can access resources while supporting the ecosystem in a way that aligns with their means and values.
By consolidating under Consensus21.School, we are doubling down on the principles of decentralisation, self-sovereignty, and permissionless learning. This transition includes all of our key initiatives, including V4V Open Lessons, the Decentralised Autonomous Education System (DAES), and our involvement with the Plan B Network.
Full Migration of DAES and Plan B Network Collaboration
As part of this transition, the Decentralised Autonomous Education System (DAES) is now officially part of Consensus21.School and is fully reflected in the Consensus21.School Whitepaper. DAES will continue to provide a platform for aspiring learners to submit their Bitcoin project ideas for potential funding and mentorship, with active engagement in our Stacker News /~Education territory and Signal chat for collaboration. We invite contributors to support our learner fund and help bring innovative ideas to fruition within this new ecosystem.
Additionally, our collaboration with the Plan B Network will now operate under Consensus21.School. Through this partnership, we will continue teaching using the Plan B Network's curriculum to provide high-quality Bitcoin education and strengthen local Bitcoin communities. This global initiative remains a core part of our mission, now fully integrated within Consensus21.School.
Looking Ahead
With Consensus21.School, we will continue innovating in peer-to-peer learning, integrating cutting-edge developments in Bitcoin, Nostr, and decentralised technologies. We encourage our community to stay engaged, contribute, and help us build an even stronger foundation for the future of open education.
This is more than just a domain change--it is the next evolution of our mission. The School of Bitcoin as an entity is now retired, and all our efforts, including DAES and the Plan B Network collaboration, will move forward exclusively under Consensus21.School. We invite educators, students, and enthusiasts to join us in shaping this next phase of open financial education.
The journey continues, and we are thrilled to embark on this new chapter together
-
 @ 77c2969e:a33cfa50
2025-04-03 07:54:55
@ 77c2969e:a33cfa50
2025-04-03 07:54:55最近又开始折腾 Technitium DNS Server,发现之前记录的过程不太完善,于是更新一下。
安装acme.sh
curl https://get.acme.sh | sh -s email=youreMailAddress导入环境变量
export CF_Token="填API token" export CF_Zone_ID="填区域ID" export CF_Account_ID="填账户ID"- Cloudflare 的 API Token 是在 Cloudflare 网页右上角的👤头像--配置文件--API 令牌处创建
- 在 Cloudflare 主页点击你需要使用的域名,下滑到右下角可以看到区域 ID 和账户 ID
申请证书
acme.sh --issue --dns dns_cf -d dns.235421.xyz-d后面是你想使用的域名
安装证书
``` acme.sh --install-cert -d dns.235421.xyz \ --key-file /root/certs/key.pem \ --fullchain-file /root/certs/cert.pem \ --reloadcmd "cd /root/certs && openssl pkcs12 -export -out 'dns.pfx' -inkey 'key.pem' -in 'cert.pem' -password pass:1021"
```
reloadcmd是在申请证书之后执行的代码,以后自动更新时也会自动执行这个代码,所以第一次配置好就基本上不用管了。reloadcmd中的代码是将pem格式的证书和密钥转换成一个pfx格式的证书文件,-out后面是输出的pfx证书文件名,-inkey和-in分别是前一步acme.sh申请的密钥和证书文件。这里必须添加密码,也就是1021这个,如果不设密码执行命令的话,它会让你交互式输入,但是在自动脚本中就不行。我在前面加了先cd到证书目录,避免出现问题。
安装 Technitium DNS Server
-
在Technitium DNS Server 官网 获取安装脚本,也有提供 Docker 镜像以及 Windows 版本。
-
安装后在
公网IP:5380进入管理界面,首次进入需设置管理员密码,管理员账户默认是admin。 -
在
Settings–optional protocols处开启 DNS over HTTPS ,TLS Certificate File Path处填入转换好的pfx证书路径,TLS Certificate Password处填你设定的密码,就是我的1021。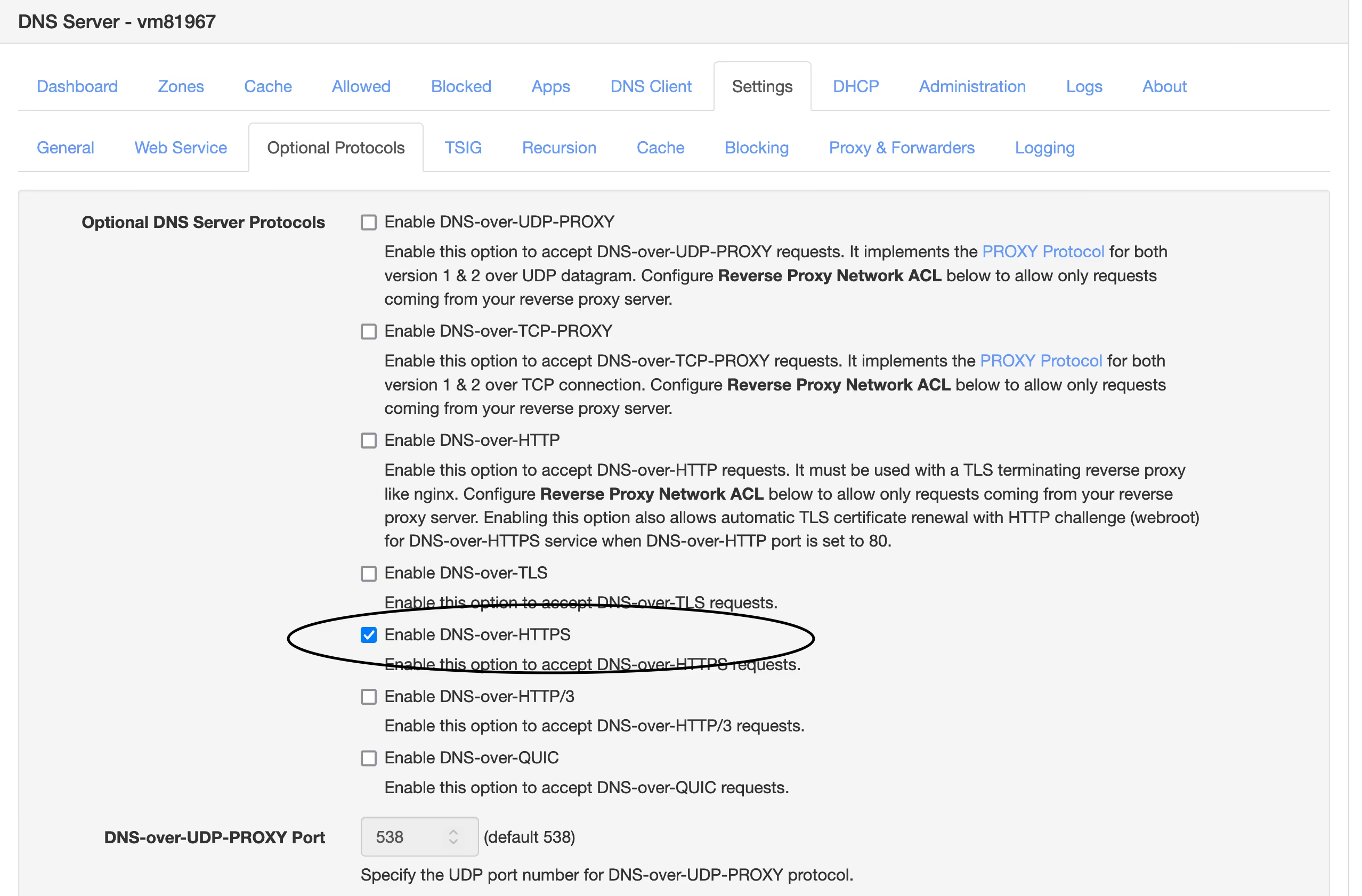
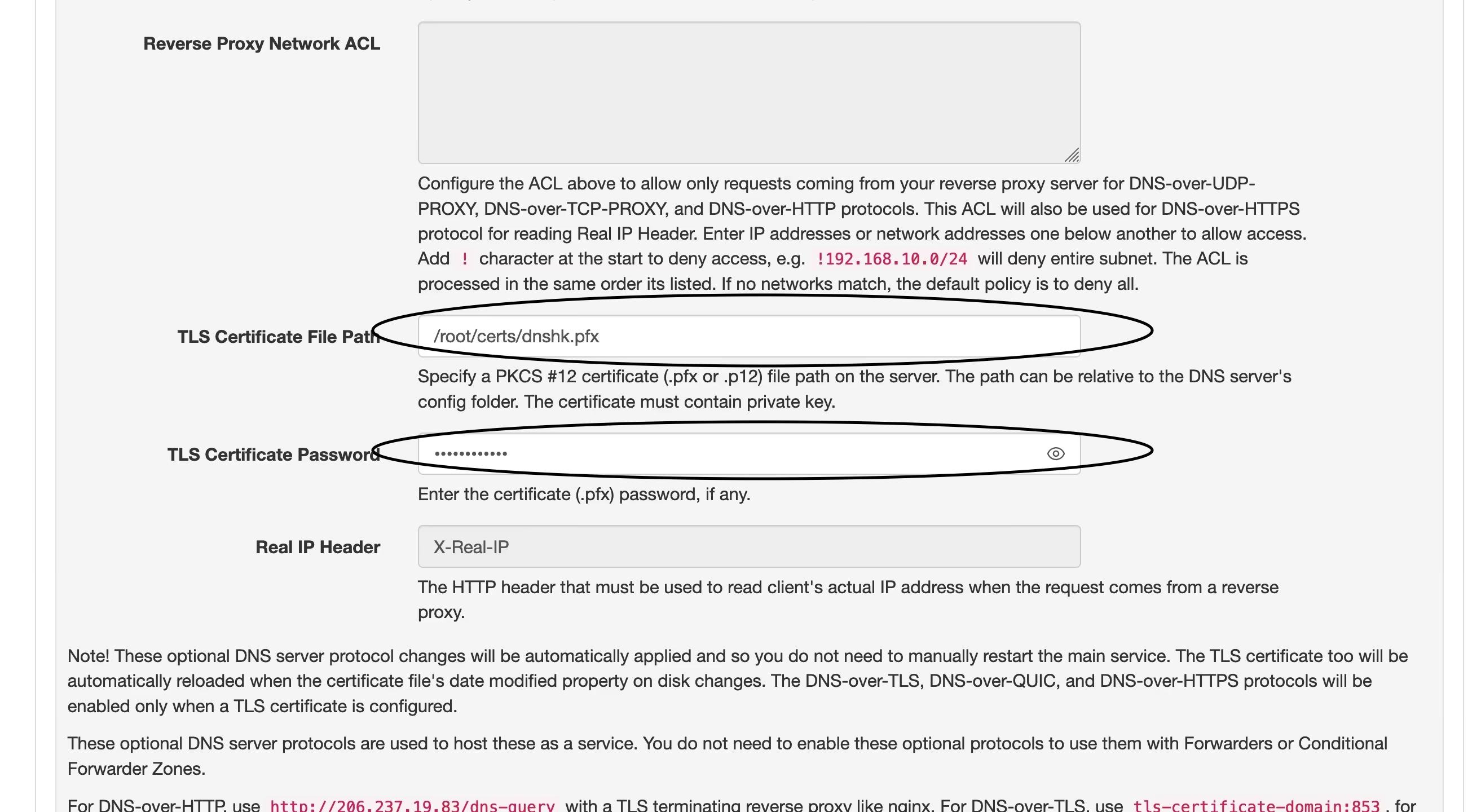
-
现在打开你的域名,看到如图这样就说明设定成功了,然后在需要设置 DoH 的地方填入
https://yourdomain.com/dns-query即可。
我在之前的文章中使用的是
DNS over HTTP并用 Nginx 反代来实现DNS over HTTPS的,现在直接用 DoH ,省去了配置 Nginx 的部分,只是多了一步证书格式转换,总体上更简单了。
我的设置
- 在
Settings–Recursion处打开Allow Recursion以允许递归解析。 - 在
Settings–Cache处将Cache Maximum Entries调大些,默认 10000 有点少了。 - 在
Settings–General处开启EDNS Client Subnet (ECS)。 - 在
Settings–Logging处开启Use Local Time。 - 在
Apps–App Store中安装Query Logs (Sqlite)以便在Logs–Query Logs处查看 DNS 查询日志。
以下设置可选
- 在
Settings–General处开启Prefer IPv6 - 在
Settings–Web Service处为后台管理页面开启 HTTPS,可使用与 DoH 相同的域名和证书,仅端口不同,这个默认 HTTPS 端口是53443。 - 在
Settings–Blocking处开启拦截功能(默认开启),下面Allow / Block List URLs可以配置规则,与 AdGuard Home 规则通用,白名单规则须在链接前加上英文叹号!。也可以是本地规则,填路径即可。 - 在
Settings–Proxy & Forwarders处可以设置上游DNSForwarders。
-
 @ 2b24a1fa:17750f64
2025-04-03 07:46:37
@ 2b24a1fa:17750f64
2025-04-03 07:46:37„Ein Fundstück aus dem Internet – jemand fragt:\ „Wie fühlst du dich als Geimpfter, wenn du eine Maske tragen musst, um die Ungeimpften zu schützen?“
https://soundcloud.com/radiomuenchen/was-ist-passiert-ein-buch-von-michael-sailer
\ Jemand antwortet:\ „Wovor sollte ein Geimpfter einen Ungeimpften schützen?\ 1. Der Geimpfte kann doch gar nicht krank werden, also auch niemanden anstecken, dachte ich?\ 2. Wenn der Geimpfte doch krank werden und andere anstecken kann, wozu hat er sich dann impfen lassen?\ 3. Und wozu sollte sich dann der Ungeimpfte impfen lassen?\ 4. Und wozu sollte dann überhaupt einer der beiden eine Maske tragen?“\ Jemand antwortet:\ „Das ist pure Querdenkerei. Solche kruden Theorien können Menschenleben zerstören.“\ „Eine bessere Parabel auf den religiösen Charakter des aktuellen Wahns könnte ich mir nicht ausdenken“,\ schreibt der Münchner Kolumnist Michael Sailer in seinem Buch Was ist passiert – Notate aus den Zeiten von Lüge und Krieg, das Ende Februar erschienen ist. Als neugieriger und zwangsläufig teilnehmende Beobachter analysiert, kommentiert und hinterfragt der Autor die gesellschaftlichen Abgründe, die sich 2020 und 2021 vor unser aller Augen auftaten.
Unser Autor Jonny Rieder hat es gelesen und eine Rezension verfasst.
Sprecher: Ulrich Allroggen
Bild: Radio München - Kunst: Isaac Cordal (Cement Eclipses)
-
 @ c631e267:c2b78d3e
2025-04-03 07:42:25
@ c631e267:c2b78d3e
2025-04-03 07:42:25Spanien bleibt einer der Vorreiter im europäischen Prozess der totalen Überwachung per Digitalisierung. Seit Mittwoch ist dort der digitale Personalausweis verfügbar. Dabei handelt es sich um eine Regierungs-App, die auf dem Smartphone installiert werden muss und in den Stores von Google und Apple zu finden ist. Per Dekret von Regierungschef Pedro Sánchez und Zustimmung des Ministerrats ist diese Maßnahme jetzt in Kraft getreten.
Mit den üblichen Argumenten der Vereinfachung, des Komforts, der Effizienz und der Sicherheit preist das Innenministerium die «Innovation» an. Auch die Beteuerung, dass die digitale Variante parallel zum physischen Ausweis existieren wird und diesen nicht ersetzen soll, fehlt nicht. Während der ersten zwölf Monate wird «der Neue» noch nicht für alle Anwendungsfälle gültig sein, ab 2026 aber schon.
Dass die ganze Sache auch «Risiken und Nebenwirkungen» haben könnte, wird in den Mainstream-Medien eher selten thematisiert. Bestenfalls wird der Aspekt der Datensicherheit angesprochen, allerdings in der Regel direkt mit dem Regierungsvokabular von den «maximalen Sicherheitsgarantien» abgehandelt. Dennoch gibt es einige weitere Aspekte, die Bürger mit etwas Sinn für Privatsphäre bedenken sollten.
Um sich die digitale Version des nationalen Ausweises besorgen zu können (eine App mit dem Namen MiDNI), muss man sich vorab online registrieren. Dabei wird die Identität des Bürgers mit seiner mobilen Telefonnummer verknüpft. Diese obligatorische fixe Verdrahtung kennen wir von diversen anderen Apps und Diensten. Gleichzeitig ist das die Basis für eine perfekte Lokalisierbarkeit der Person.
Für jeden Vorgang der Identifikation in der Praxis wird später «eine Verbindung zu den Servern der Bundespolizei aufgebaut». Die Daten des Individuums werden «in Echtzeit» verifiziert und im Erfolgsfall von der Polizei signiert zurückgegeben. Das Ergebnis ist ein QR-Code mit zeitlich begrenzter Gültigkeit, der an Dritte weitergegeben werden kann.
Bei derartigen Szenarien sträuben sich einem halbwegs kritischen Staatsbürger die Nackenhaare. Allein diese minimale Funktionsbeschreibung lässt die totale Überwachung erkennen, die damit ermöglicht wird. Jede Benutzung des Ausweises wird künftig registriert, hinterlässt also Spuren. Und was ist, wenn die Server der Polizei einmal kein grünes Licht geben? Das wäre spätestens dann ein Problem, wenn der digitale doch irgendwann der einzig gültige Ausweis ist: Dann haben wir den abschaltbaren Bürger.
Dieser neue Vorstoß der Regierung von Pedro Sánchez ist ein weiterer Schritt in Richtung der «totalen Digitalisierung» des Landes, wie diese Politik in manchen Medien – nicht einmal kritisch, sondern sehr naiv – genannt wird. Ebenso verharmlosend wird auch erwähnt, dass sich das spanische Projekt des digitalen Ausweises nahtlos in die Initiativen der EU zu einer digitalen Identität für alle Bürger sowie des digitalen Euro einreiht.
In Zukunft könnte der neue Ausweis «auch in andere staatliche und private digitale Plattformen integriert werden», wie das Medienportal Cope ganz richtig bemerkt. Das ist die Perspektive.
[Titelbild: Pixabay]
Dazu passend:
Nur Abschied vom Alleinfahren? Monströse spanische Überwachungsprojekte gemäß EU-Norm
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 0f9da413:01bd07d7
2025-04-03 05:32:55
@ 0f9da413:01bd07d7
2025-04-03 05:32:55
หลังจากจบทริปเที่ยวพัทยาเรียบร้อยแล้วก็ได้เดินทางไปยังเกาะช้างโดยติดรถเจ้าหน้าที่ในที่ทำงานไปไปเกาะช้างครั้งแรกรู้สึกว่ามันไกลเหลือเกินไปค่อนข้างยากหากไม่มีรถส่วนตัว ถ้าให้ไปส่วนตัวก็คงต้องอยู่นานๆ หน่อยชักแบบอาทิตย์หนึ่ง ใช้ชีวิตแบบฝรั่งเที่ยวอยู่ง่ายๆ กินง่ายๆ จากที่ดูในแผนที่ btcmap แล้วพบว่าก็มีร้านที่ปักหมุดไว้อยู่ทั้งหมดสองร้านด้วยกันซึ่งระยะทางก็ค่อนข้างซันเหมือนกัน และมีเนินสูงต่ำสลับกันไป หากไม่มีรถส่วนตัวไปนี่ค่อนข้่างลำบากพอสมควร ต้องเช่ามอไซต์ไป อันนี้ก็เช่าไปเหมือนกัน โดยผมเช่ามอไซต์ 1 วันวันละ 200 บาท (แต่มัดจำ 3000 บาท) ก็เอาเรื่องเหมือนกัน และก็มาเริ่มต้นที่ร้านแรกเลยคือ
Mr. A Coffee

ร้านอาหารสไตล์บ้านๆ ที่ขายอาหาร น้ำ เครื่องดื่ม มีทั้งอาหารไทยและอาหารฝรั่ง ส่วนตัวก็ขับรถมอไซต์มายังสถานที่แห่งนี้ทางเข้าไปยังร้านเป็นหมู่บ้านเล็กๆ ไม่มีถนนเข้า แต่มอไซต์เข้าไปได้พอสมควร ตอนนั้นค่อนข้างเย็นมากแล้ว ได้มาสั่งอาหารมาคือ ข้าวเหนียวมะม่วงกับน้ำแก้วมังกรปั่นแบบไม่หวาน (ทั้งๆที่ตัวเองก็จะเตรียมไปกินบุ๊ปเฟ่อีกหนึ่งชั่วโมงข้างหน้า 555) ก็ได้สั่งไปแล้วก็ถามว่ารับ bitcoin ไหมครับ เจ้าของร้านก็บอกว่า รับๆ ผมกับเจ้าของร้านก็ได้พูดคุยกันเกือบประมาณครึ่งชั่วโมง ซึ่งหากผมมาเร็วกว่านี้หน่อยก็คงได้คุยกันยาวๆ แล้วละ ซึ่งเป็นการคุยที่สนุกมากซึ่งตัวเจ้าของร้านเองก็ได้เล่าถึงเหตุผลที่รับ bitcoin เหมือนกันว่าช่วง โควิดตอนปี 2020 ที่ผ่านมา บนเกาะช้างไม่มีอะไรเลยชาวบ้านก็ต้องไปหารากไม้ หาเห็ดตามป่าเขากัน แต่พี่เจ้าของร้านได้รู้จักกับฝรั่งคนหนึ่งเขาช่วยเหลือพี่เจ้าของร้านด้วยการบริจาคบิทคอยให้ และคนนี้ก็เป็นคนสอนให้เขารับบิทคอยโดยใช้ WOS และเจ้าของร้านก็เล่าให้ผมฟังเพิ่มเติม ณ ปัจจุบันว่า คนเราเองก็ยังต้องมีสภาพคล่องในการใช้งานอยู่ ตั้งมีเงิน fiat ไว้ส่วนหนึ่ง ส่วนบิทคอยที่ได้เขาได้ก็เก็บไว้เพื่อสร้างเป็นทรัพย์สินในอนาคตที่หากมีปัญหาช่วงไหนก็นำมาขายได้ ก็แลก P2P โดยตรง ซึ่งผมค่อนข้างตกใจเพราะเขาเรียนรู้จากการรับบิทคอยโดยนักท่องเที่ยวชาวต่างชาติที่ชวนเขาให้รับ เผื่อว่าจะมีฝรั่งมาใช้งานบิทคอย ณ สถานที่ร้านแห่งนี้

กึมมิคที่หลายท่านอาจจะต้องลุ้นหน่อยว่าหากมีโอกาสได้ไปเที่ยวและแวะที่ร้าน ก็คงต้่องลุ้นว่าคุณจะได้จ่ายด้วย bitcoin ไหม หากวันนั้นเจ้าของร้านไม่อยากรับเพราะว่าโคต้ารับบิทคอยวันนั้นเต็มแล้ว ฮ่าๆ รูปแบบระบบวาสนาร้านสูญของคุณมิกตอนเมื่อก่อน (เหมือนกันเลย) จริงๆ แล้วหากมีเวลามากพอก็คงได้พูดคุยกับพี่เจ้าของร้านสนุกๆกันไป ผมชอบความเรียบง่ายของร้านพี่เขา และมีอาหารหลากหลายอย่างเต็มไปหมด อีกเรื่องอย่างข้าวเหนียวมะม่วง ผมยังจำได้ว่าเมื่อก่อนมีแต่ช่วงฤดูเดียวที่สามารถกินมะม่วงสุกได้ หรือ อาหารแบบข้าวเหนียวมะม่วง แต่ปัจจุบันคือถ้าจะกิน ข้าวเหนียวมะม่วงแล้ว สามารถสั่งกินได้ตลอดทั้งปีกันเลยซึ่งก็โอเครพอสมควร แบบอยากไปทะเลตอนหน้าฝนแล้วอยากกินข้าวเหนียวมะม่วงของหน้าร้อนแบบนี้

ท้ายสุดร้าน Mr. A Coffee เป็นร้านที่ถ้านั่งชิวๆ แบบฝรั่งก็สามารถอยู่ได้ยาวๆ เลยนะจิบกาแฟ ทำงาน WFH ล้่อมรอบโดยธรรมชาติ แต่เส้นทางมาที่ร้านก็ลำบากหน่อยเหมาะกับคนที่ local จริงๆ low time ระดับหนึ่ง ท้ายสุดผมเองก็แจกสติกเกอร์ของพี่แชมป์เอาไปให้เจ้าของร้านแจกกันต่อไป
 งานนี้ทั้งข้าวเหนียวมะม่วงและน้ำแก้วมังกรปั่น เสีย sats ไปทั้งหมด 6,050 sats แต่สิ่งที่ได้คือการแลกเปลี่ยนมุมมองกับเจ้าของร้านกับจุดเริ่มต้นของการรับบิทคอยในพื้นที่เกาะช้างแห่งนี้ และหากมีโอกาสอาจจะไปพักอยู่แถวนั้นชักอาทิตย์และแวะมาอุดหนุนร้านนี้ตลอด เพราะวิวฝั่งใต้สุดของเกาะช้างก็ยังคงความสวยงามไม่แพ้กับฝั่งทิศตะวันตกที่ฝรั่งอยู่กัน แต่ฝั่งใต้โซนนี้ก็มีความที่เป็นบ้านไม้ เพิงง่ายๆ ที่ชาวต่างชาติชอบกันอยู่ :)
งานนี้ทั้งข้าวเหนียวมะม่วงและน้ำแก้วมังกรปั่น เสีย sats ไปทั้งหมด 6,050 sats แต่สิ่งที่ได้คือการแลกเปลี่ยนมุมมองกับเจ้าของร้านกับจุดเริ่มต้นของการรับบิทคอยในพื้นที่เกาะช้างแห่งนี้ และหากมีโอกาสอาจจะไปพักอยู่แถวนั้นชักอาทิตย์และแวะมาอุดหนุนร้านนี้ตลอด เพราะวิวฝั่งใต้สุดของเกาะช้างก็ยังคงความสวยงามไม่แพ้กับฝั่งทิศตะวันตกที่ฝรั่งอยู่กัน แต่ฝั่งใต้โซนนี้ก็มีความที่เป็นบ้านไม้ เพิงง่ายๆ ที่ชาวต่างชาติชอบกันอยู่ :)Google-map: https://maps.app.goo.gl/b45JGeTzL6Lwwi9i9
BTC-map: https://btcmap.org/merchant/node:12416107504
**Koh Chang Wine Gallery **

และเราก็ย้อนกลับมาอีกร้านหนึ่งในวันถัดไปและเป็นวันที่จะต้องออกจากเกาะช้างเช่นเดียวกัน และผมก็ไม่พลาดร้าน Koh Chang Wine Gallery ตั้งอยู่ในโซนหมู่บ้านแหล่งท่องเที่ยวเส้นทางถนนทางตะวันตก ร้านนี้ไม่ได้มีป้ายรับบิทคอย แต่รับชำระด้วยบิทคอยซึ่งเป็นฝรั่งท่านหนึ่งที่คาดว่าน่าจะแต่งงานกับภรรยาคนไทย เป็นร้านสไตล์แบบฝรั่งเลย ผมเองก็สั่งสเต็กเนื้อไป และน้ำมะม่วงปั่น (ไม่รู้เวลาไปเกาะทีไรติดใจกับน้ำมะม่วงปั่น) อาจจะไม่ได้พูดคุยอะไรมากมายนัก แต่ก็หมดไป 32,620 sats เป็นร้านอาหารเช้าและอาหารแนวฝรั่งตรงๆ ถือว่าค่อนข้างอร่อยใช้ได้ดีเลยทีเดียว แต่หากจะจ่ายด้วยบิทคอยก็ต้องแจ้งก่อนนะว่าขอจ่ายด้วยบิทคอยก่อน เหมือนพี่ฝรั่งที่เขารับตอนนี้ก็รับแต่เฉพาะ bitcoin อย่างเดียวเมื่อก่อนรับ xrp กับ doge ด้วยแต่ผมเองเวลาคุยกับฝรั่งก็เหงื่อแตกเหมือนกัน (รึว่าเพราะมันร้อน บนเกาะก็อบอ้าวใช้ได้ 555+)



Google-map: https://maps.app.goo.gl/6QbNgRbiV5Uao2Xz8
BTC-map: https://btcmap.org/merchant/node:11461720813
เส้นทางไปร้านค่อนข้างง่ายติดถนนในหมู่บ้าน ซึ่งหากมายังเกาะช้างแล้วหากขึ้นฝั่งมาแล้วเลี้ยวขวาก็จะขับรถหรือนั่งรถมาเส้นถนนฝั่งตะวันตกของเกาะก็จะพบกับร้านนี้ก่อน อันนี้แล้วแต่ความสะดวกแต่ละท่านเลยครับหากได้มีโอกาสแวะมาเกาะช้างและอยากใช้จ่าย bitcoin เราก็มีทางเลือกร้านในสองสไตล์กันเลย แบบวิถีฝรั่งตอนเช้าก็ร้าน Koh Chang Wine Gallery หรือ แบบ Local ก็ Mr. A Coffee หรือไปทังคู่เลยจะดีมากแต่ต้องบ้าหน่อย เพราะเส้นทางไปก็ค่อนข้างลำบากพอควรเหมือนกัน หมายถึงมีภูเขาชันมีทางขึ้นลงหักศอกนิดหน่อยก็เท่านั้นเอง
รวมๆ ทริปบนเกาะช้างนี้ก็หมดไปไม่เยอะมาก 38,670 sats ก็จะตัวลอยเบาๆ หน่อย (สำรวจเมื่อ มีนาคม 2025 อนาคตอาจจะมีการเปลี่ยนแปลงได้) สำหรับจากนี้จะเป็นการ ปสก. ส่วนตัวกับการใช้งาน Bitcoin Lightning ตามสถานที่ที่ได้เดินทาง Part 3 จะเป็นสถานที่ในพื้นที่หาดใหญ่ จังหวัดสงขลา และ เสริมประสบการณ์การเดินทางโดยรถไฟระยะเวลาเกือบ 18 ชั่วโมง พร้อมด้วยมิตรสหายในรังอย่างกัปตัน จะป่วนแค่ไหนก็รอติดตามกันครับ :)
-
 @ 5cf42f9d:4465eebf
2025-04-02 21:32:31
@ 5cf42f9d:4465eebf
2025-04-02 21:32:31 -
 @ ba36d0f7:cd802cba
2025-04-02 21:17:09
@ ba36d0f7:cd802cba
2025-04-02 21:17:091. Essential Rules
✔ Touch-Move: If you touch a piece, you must move it (if legal). ✔ Check Alert: Say "check" when attacking the enemy king (optional in tournaments). ✔ Checkmate Ends: The game stops immediately—no need to capture the king. ✔ Draw Offers: You can offer a draw after your move, before pressing the clock.
2. Tournament Etiquette
-
Handshake: Before and after the game.
-
Silence: No talking during play (except "check" or "draw?").
-
Clock: Press with the same hand that moved.
-
Resignation: Tip over your king or say "I resign" (don’t just leave).
3. Online Chess Manners
No Stalling: Let the timer run out only if you’ve truly lost.
GG Message: Say "Good game" (or "GG") after playing.
Avoid "Berserking": Don’t abuse speed settings to rush opponents.
Common Faux Pas ❌ Jangling pieces to distract. ❌ Glaring at your opponent’s board. ❌ Cheating (using engines, peeking at other games).
-
-
 @ 3c7dc2c5:805642a8
2025-04-02 21:15:55
@ 3c7dc2c5:805642a8
2025-04-02 21:15:55🧠Quote(s) of the week:
CBDC the digital euro - a centralized solution in search of a problem. While the ECB may see it as a way to 'modernize' finance, true innovation comes from empowering individuals, not consolidating control. CBDCs are just surveillance tools disguised as innovation. Bitcoin is the only true digital money—decentralized, scarce, and free. Stack sats, not CBDCs.
🧡Bitcoin news🧡
2025 https://i.ibb.co/vx988kT1/Gn-Ix-Dp-YWs-AASkiw.jpg
On the 24th of March:
➡️The Pakistan central bank is exploring mining Bitcoin with excess electricity.
➡️'MicroStrategy just added another 7,000 Bitcoin to their treasury. They're now holding over 506,000 BTC ($44 billion). Look at the corporate Bitcoin ownership breakdown: - MicroStrategy: 506,000+ BTC - Marathon: ~46,000 BTC (10x smaller) - Riot: ~19,000 BTC (26x smaller) That acquisition curve has gone parabolic since Q4 2024. Strategy's buying pace now rivals what we're seeing from the Bitcoin ETFs, a single public company absorbing supply at an institutional scale. Clear institutional conviction signal here.' -Ecoinometrics
➡️SQUARE CEO JACK DORSEY: "Bitcoin will make the current financial system feel as irrelevant as the fax machine."
On the 25th of March:
➡️'BITCOIN HASH-RIBBON FLASHES BUY SIGNAL
- This is one of the most reliable "buy" indicators.
- Significant price gains have followed 7 out of the last 7 times this indicator was triggered.' -Bitcoin Archive (foto) Bitcoin is always a buy. Just DCA.
➡️GameStop includes Bitcoin as a treasury reserve asset in its investment policy update. GameStop has $4.6 billion in cash to invest.
➡️Strategy’s sale of 8.5 million STRF shares closes today, unlocking $711 million in new capital to buy more Bitcoin.
➡️BBC News reports from a remote community of 15,000 people in the far north-western tip of Zambia relying on hydroelectric power, “The bitcoin mine now accounts for around 30% of the plant's revenue allowing them to keep the prices down for the local town” - Source: https://www.bbc.com/news/articles/cly4xe373p4o Gridless is doing a splendid job in Africa and showing through proof-of-work that if you aren't mining Bitcoin, you are wasting energy. It's time for such communities to appear more around the world.
Daniel Batten: 'They couldn't resist zooming out and implying this is an outlier (it isn't, the majority of off-grid bitcoin mining operations are renewably powered). In doing so BBC made three factually incorrect statements at the end about Bitcoin mining straining grids (multiple peer-reviewed studies show the opposite is true), and "Greenidge gas power plant in New York which was renovated to mine bitcoin" (it didn't, it re-opened to supply power back to the grid), and stating that Bitcoin mining needs artificial govt incentives or rules to do the right thing (It doesn't, it's become 56.7% sustainably powered without any govt incentives)
But let's shine the light on the positive - it has far fewer factually incorrect statements than previous reporting, and it is a step in the right direction in its gradual journey towards objective Bitcoin reporting for a media company that has until now only published negative news stories on Bitcoin.'
➡️Femke Halsema, Mayor of Amsterdam, wants a national ban on Bitcoin payments: "It undermines our civilization".
I rather believe the opposite.
Under Femke Halsema - Amsterdam
-
The number of civil servants increased by 50% (14K -> 20K)
-
Debt increased by 150% (4 billion -> approx. 10 billion)
Despite high revenues, Amsterdam has to borrow nearly half a billion euros every year. Local taxes continue to rise, whether it's water authority taxes or property taxes (OZB). But, above all, you should be concerned about those 0.3% criminal Bitcoin / Crypto transactions (worldwide). The audacity.
Even if the Netherlands were to legally ban Bitcoin payments, users could easily continue trading through foreign exchanges or peer-to-peer platforms. A ban might actually push Bitcoin usage further underground, making oversight of suspicious transactions worse rather than better.
➡️Mt. Gox moves 11.501 Bitcoin ($1B) for creditor repayment.
➡️BlackRock launched a European Bitcoin ETP today - Bloomberg
➡️North Carolina introduces a bill to invest 5% of state funds into Bitcoin.
On the 26th of March:
➡️NYDIG just became a big Bitcoin miner. Crusoe, the first to scale Bitcoin mining off flared gas (~200MW worth, across 425 data centers) has sold its entire Bitcoin mining business to NYDIG.
➡️Metaplanet has raised ~$55.2m (¥8.28b) of equity capital through three trading days this week while partially deleveraging with the redemption of $23.3m (¥3.5b) of 0% ordinary bonds.
➡️GameStop can service a loan of up to $100 BILLION for 4.6 years with its existing $4.6b cash balance at 1% interest. That's twice the amount of Bitcoin Michael Saylor's Strategy currently holds.
➡️New feature by Protonmail enables their 100 million users to send Bitcoin using their email addresses.
➡️The Blockchain Group confirms the acquisition of 580 BTC for ~€47.3 million, the holding of a total of 620 BTC, and a BTC Yield of 709.8% YTD.
→ Confirmation of the acquisition of 580 BTC for ~€47.3 million at ~€81,550 per bitcoin
→ Total group holdings of 620 BTC for ~€50.5 million at ~€81,480 per bitcoin
→ Adoption of ‘BTC Yield’, ‘BTC Gain’, and ‘BTC € Gain’ as KPIs, following the steps of Strategy and Metaplanet
This is a major step in our Bitcoin Treasury Company strategy focused on increasing Bitcoin per share over time.
Source: https://t.co/QDj61ZDe6O
The Blockchain Group is Europe's First Bitcoin Treasury Company!
On the 27th of March:
➡️'Bitcoin's 4-year Compound Annual Growth Rate (CAGR) is at historic lows.' -Pierre Rochard
➡️Daniel Batten: Yet another paper on Bitcoin and energy TL:DR: "The opportunities offered by bitcoin mining in reduction of the greenhouse gas emissions and renewable energy transition are greater than generally assumed" The journal has a (high) impact factor of 7.1."
Source: https://t.co/W3gytMgcpC
➡️A home miner with only 4 machines mined block 888737.
https://i.ibb.co/7xm91R4t/Gn-Ef-H9y-Ws-AA4jkn.jpg
Bitcoin proves anyone can participate and earn—true freedom!
➡️'Short-Term Holders have increased their Bitcoin holdings by 201,743 BTC to 5,750,076 BTC since January, remaining below previous cycle peaks. 200K BTC are currently held at an unrealized loss, representing about $17B.' -Bitcoin News
➡️Bitcoin mining hardware manufacturer Canaan signs a three-year colocation agreement with Mawson Infrastructure Group's Mawson Hosting LLC for facilities in Midland, Pennsylvania, and Edna, Texas. Most of the 4.7 EH/s hashrate is expected to be operational by Q2 2025.
On the 28th of March:
➡️If Saylor had bet on ETH instead of Bitcoin, Strategy would be down $9 billion, instead of up $9 billion like they are today. ETHBTC made fresh lows 0.02210. Ether is down 74% against Bitcoin since switching from proof of work to proof of stake. Yikes!
➡️Representative introduces a strategic Bitcoin reserve bill in South Carolina.
➡️A Russian company built a Bitcoin mine in the Arctic. Set in the frozen city of Norilsk, the facility taps into cheap excess energy from one of the world's most isolated industrial hubs.
➡️The price of bitcoin has nearly followed the same phases of volatility for 15 years, according to Fidelity.
https://i.ibb.co/LdQfrqG0/Gn-Ig-Skd-XMAAi-L3r.jpg
another great chart:
https://i.ibb.co/G4WmDjhd/Gn-JED1q-Xk-AAq-Kqk.jpg
On the 29th of March:
➡️Public miner MARA with a $2B common stock offering to buy more Bitcoin. https://i.ibb.co/PZZxXJ37/Gn-Kj-Vqza-EAEUG-V.png
➡️California has officially included Bitcoin Rights protections in its newly proposed digital asset bill. If passed, it will guarantee the right to self-custody for nearly 40M residents and prohibit discrimination against Bitcoin use.
➡️The number of addresses with more than one Bitcoin has fallen below 1 million, standing today at 995,207.
On the 31st of March:
➡️Larry Fink, Founder/CEO of BlackRock in his annual letter to shareholders: “If the U.S. doesn't get its debt under control, if deficits keep ballooning, America risks losing that position to digital assets like Bitcoin."
https://www.blackrock.com/corporate/literature/presentation/larry-fink-annual-chairmans-letter.pdf
➡️Strategy has acquired 22,048 BTC for ~$1.92 billion at ~$86,969 per bitcoin and has achieved a BTC Yield of 11.0% YTD 2025. As of 3/30/2025, Strategy holds 528,185 $BTC acquired for ~$35.63 billion at ~$67,458 per bitcoin.
➡️ The Bitcoin Policy Institute releases a framework for the USA to buy $200 billion worth of #Bitcoin using Bit Bonds.
➡️Is Indonesia the next Bitcoin Country? Bitcoin Indonesia mapped out the entire Bitcoin ecosystem.
A new map shows Bitcoin adoption EXPLODING across the Southeast Asian island nation of Indonesia. Check out all the communities, projects, and businesses embracing Bitcoin. The revolution is happening.
https://i.ibb.co/cXL8mC0x/Gnbdg-Lub-IAAdwcb.jpg
On the 1st of April:
➡️'Over 73,353 BTC were bought by corporations in Q1 2025. Only 40,500 BTC new Bitcoin was mined, but still no supply shock, for now... Which company do you want to see adopt BTC next?'
Here is the breakdown by Alec: https://x.com/Alec_Bitcoin/status/1907062290345783723
➡️After skeptics questioned Tether’s Bitcoin holdings, CEO Paolo Ardoino fired back, sharing the company’s BTC address with a confirmed balance of 92,646 BTC. On the same day Tether bought 8,888 Bitcoin worth $735 million as per on-chain data. They now hold over 100,000 BTC.
➡️'GameStop just raised $1.48B. They are expected to use that and possibly more of the now $6B+ on their balance sheet to buy Bitcoin. A master class on how to pivot from meme stock to capitalize on volatility in the ultimate store of value.' -James Lavish
➡️Texas' state house Democrats have proposed a bill that would authorize up to $250 million in state investment in Bitcoin and up to $10 million for each municipality and county.
➡️Human Rights Foundation donates 10 Bitcoins worth $830,000 to over 20 projects worldwide.
Alex Gladstein: '1 billion sats gifted carefully to a variety of stellar organizations and individuals to support BTC privacy, decentralization, education, and p2p use, aimed at folks working under authoritarianism.'
💸Traditional Finance / Macro:
On the 29th of March
👉🏽'From Wednesday to Friday, the S&P 500 lost -$100 billion PER trading hour for a total of -$2 TRILLION. Then, after the market closed on Friday, S&P 500 futures erased ANOTHER -$120 billion in minutes.' -TKL
🏦Banks:
👉🏽 no news
🌎Macro/Geopolitics:
On the 24th of March:
👉🏽Financelot: 'This is fascinating. The Dow Jones to Gold Ratio is about to cross a level only seen 4 times in history. Every time it crossed this level it marked the beginning of an 18-month recession/depression. 1929, 1973, 2008 & 2025' I don't think we won't see a depression. History rhymes but doesn't always mean it will repeat, although human behavior stays the same. For now, it means the market is overvalued, gold is undervalued, or both.
👉🏽US household wealth is falling: US household equity wealth is set to drop a whopping -$3 trillion this quarter, the most since the 2022 bear market, according to BofA estimates. By comparison, equity holdings rose +$9 trillion in 2024 to a record $56 trillion. In other words, one-third of last year's gains have likely been wiped out due to the recent market pullback.
Furthermore, the top 10% of the wealthiest Americans own 87% of US stocks. This, in turn, may negatively impact consumer spending as the top 10% reflect a record 50% of all consumer expenditures. Consumer spending is set to slow in Q2 2025.' -TKL
👉🏽Demolition of the Boiler House at Moorburg Power Plant in Hamburg. Germany is preparing for combat by dynamiting its own modern energy infrastructure down. This was the most advanced coal plant. 6 years old and cost three billion euros. The Netherlands is following a similar policy—they poured concrete into their gas drilling pipes.
BowTiedMara on Twitter: "In 2022, a girl tied herself to the net at Roland Garros in protest, and she wore a T-shirt that said: "We have 1,028 days left." Today, the 27th of March, marks those 1,028 days, and nothing happened. Climate doomers are like Aztecs who think the sun stops unless they cut out some organs."
👉🏽Starting in April, the 66,000 employees of the European institutions will receive their seventh salary increase in just three years! Normally, this happens at most once per year. The President of the European Commission, Ursula von der Leyen, will see the largest increase, with her monthly salary rising to €34,800—an increase of €2,700—according to a report by the German newspaper Bild-Zeitung today.
For the Dutch readers: https://ejbron.wordpress.com/2025/03/24/eu-bureaucraten-en-politici-krijgen-de-7e-salarisverhoging-sinds-2022/
They are compensating for the inflation they impose on the EU. Lucky them Fair to say we need a DOGE in Europe.
On the 25th of March:
👉🏽Dutch minister announces a huge increase in excise duties of 25.8 cents on gasoline. On top of that, the price of gasoline will rise by an additional 7 cents due to the blending requirement and 11 cents due to the ETS-2 regulation. In a free market, prices would not be announced by politicians but would emerge through supply and demand. How I love the EU....although it is a bit more nuanced. The temporary discount is ending. Unless the parliament decides to extend it, the price of gasoline will rise. The Dutch government should simply spend less and abolish all taxes, excise duties, and levies on food, fuel, and energy. Never gonna happen though.
👉🏽"Shell will be thoroughly reviewing all its chemical divisions worldwide in the coming period. In Europe, this could lead to the partial or complete closure of various chemical branches." As mentioned multiple times last month, major industrial companies sounded the alarm. They warned that high energy costs in the Netherlands put their future at risk. Additionally, sustainability efforts and unclear government policies are challenging the sector. Frans Everts, President-Director of Shell Netherlands, warned that the entire industry could collapse.
The Green Deal is moving full speed ahead—soon everyone will be relying on food banks…
For the Dutch readers: https://nos.nl/artikel/2561036-shell-kijkt-naar-gedeeltelijke-sluiting-van-chemie-onderdelen
On the 26th of March:
👉🏽EU countries will start using a digital driver’s license from 2030. This is the result of negotiations between the European Parliament and EU member states. In the Netherlands, the digital license will be valid for ten years and will be accessible via an app. And we all know which app that will be! The EU Digital Wallet must be filled, after all.
Not just your driver’s license—everything will soon be linked to your digital identity. It’s all right there on the EU’s website, and it’s been planned for a long time. The COVID pass was already part of the rollout. The fact that they present these as separate steps just shows that they know people wouldn’t accept it if they were fully aware of what’s happening.
On the 27th of March:
👉🏽Gold surpasses $3,100 for the first time in history. TKL: 'Gold prices have hit 50 all-time highs over the last 12 months, its best streak in 12 years. This is also the 3rd-longest streak on record after a historic run during the late 1970s. The 1970s came with a period of double-digit inflation, stagnant economic growth, and a high unemployment rate, also known as stagflation. As a result, gold prices recorded 4 consecutive yearly gains.'
On the 31st of March for the first time, gold blasted through $100,000/kilogram. This time, gold prices have rallied 39% over the last 12 months, are up 16% year-to-date, and are on track for the 3rd annual positive performance.'
👉🏽NATO Secretary General Rutte insists there will be no normalization of relations with Russia for decades to come.
On March 14, 2025, Bloomberg, Rutte says: "Once the war is over, relations with Russia will gradually be restored."
On March 26, 2025, Rutte said: "There will be no normalization of relations with Russia for decades, even after the war is over."
That is the Mark I know!
"Mark Rutte, the long-serving Dutch Prime Minister, earned the nickname “Pinokkio” (Dutch for Pinocchio) primarily because of perceived dishonesty or evasiveness in political debates and scandals. While some still view Rutte as a pragmatic and stable leader, the nickname “Pinokkio” reflects a broader public sentiment of distrust, especially among those who felt betrayed by his communication style or decisions.”
On the 28th of March:
👉🏽US consumers now expect 5.0%(!) inflation in the next twelve months. Inflation expectations have DOUBLED in just four months. That's huge! Long-term US inflation expectations have officially SURGED to 4.1%, the highest level since 1993. Tariff front-running has led to a $300+ BILLION trade deficit in 2 months, and consumer sentiment has collapsed.
Atlanta Fed is now projecting that Q1 GDP will be -2.8%… a large contraction. It’s negative even “gold adjusted”
4 weeks ago it was +2.3%
8 weeks ago it was +3.9%
Yikes!
👉🏽The State Department is officially shutting down USAID and has formally notified Congress of its closure. The remaining 900 employees are set to be terminated.
👉🏽Argentina’s Economy Grows 6.5% in January. Argentina’s Poverty Rate Drops from 52.9% to 38.1% in 15 Months Under Javier Milei
👉🏽Fix the money, fix the world:
DOGE “There is actually really only ONE BANK ACCOUNT that's used to disperse ALL monies that go out of the federal government” “It's a big one — A couple of weeks ago it had $800 billion in it, it's the treasury general account”
“We're serving 580+ agencies. And up until very recently, effectively they could say, make the payment and Treasury just sent it out as fast as possible. NO VERIFICATION”
“There's a $500 billion of fraud every year. There are hundreds of billion dollars of improper payments and we can't pass an audit. The consolidated financial report is produced by treasury and we cannot pass an audit”
Extremely fascinating interview by Bret Baier with the highly talented and competent DOGE team, which is rigorously streamlining the U.S. government bureaucracy. This work can only be done by competent (and motivated) outsiders with experience. Also urgently needed in the Netherlands, and in Europe.
On the 29th of March:
👉🏽'US debt has been "limited" by the $36.104 trillion debt ceiling since January but the liabilities don't stop rising. As of today, US debt is now ~$37 trillion. Treasury has burned through $560BN of its cash balance in the past month. Just $280BN left.' -ZeroHedge
On the 1st of April:
In recent weeks, I have shared my opinion on the latest Dutch pension fund drama. This week:
https://i.ibb.co/96ZhS0W/Gn-XEVQRXw-AM6b0-A.jpg
APG and pension funds refused to invest in Dutch housing (for political reasons). This involved 25 billion euros.
Currently we almost have a political scandal over a medal, but the fact that our pension system is being put at risk...no biggie!?
For our own housing market? “Too political.” For war and Brussels' military ambitions? €100,000,000,000—no problem.
They’re gambling with your pension while first-time buyers can’t afford a home and seniors struggle to make ends meet. Our money, their agenda.
Got Bitcoin?
I will end this Weekly Recap with a Stanley Druckenmiller quote:
"My favorite quote of all time is maybe Mark Twain: "Put all your eggs in one basket and watch the basket carefully."
"I tend to think that's what great investors do."
I know what I do and have. Bitcoin!
🎁If you have made it this far I would like to give you a little gift:
What Bitcoin Did: Peter Dunworth is the Director of a multi-family office and is the co-founder of The Bitcoin Adviser. In this episode, they discuss why Bitcoin is the only asset that can recapitalize the financial system, why Peter believes Bitcoin could become a $100 trillion asset within a decade, why credit markets are ultimately a collateral problem, and why financializing Bitcoin might be necessary to save Main Street from being collateral damage. They also get into Australia's property obsession, GameStop’s pivot to Bitcoin, the difference between Bitcoin derivatives and the asset itself, and MicroStrategy.
https://www.youtube.com/watch?v=_bSprc0IAow
Credit: I have used multiple sources!
My savings account: Bitcoin The tool I recommend for setting up a Bitcoin savings plan: PocketBitcoin especially suited for beginners or people who want to invest in Bitcoin with an automated investment plan once a week or monthly.
Use the code SE3997Get your Bitcoin out of exchanges. Save them on a hardware wallet, run your own node...be your own bank. Not your keys, not your coins. It's that simple. ⠀ ⠀
⠀⠀ ⠀ ⠀⠀⠀
Do you think this post is helpful to you? If so, please share it and support my work with a zap.
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
⭐ Many thanks⭐
Felipe - Bitcoin Friday!
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
-
 @ ba36d0f7:cd802cba
2025-04-02 21:14:37
@ ba36d0f7:cd802cba
2025-04-02 21:14:37| Piece | How It Moves | Special Rules | | --------- | ------------------------------------- | --------------------- | | Pawn | Forward 1 (or 2), captures diagonally | En passant, promotion | | Rook | Straight lines | Castling | | Knight | L-shape (2+1) | Jumps over pieces | | Bishop | Diagonals | Color-locked | | Queen | Any direction | None | | King | 1 square any way | Castling, checkmate |
Pieces
-
Pawn (♙ / ♟️)
-
Moves: Forward 1 square (or 2 on first move).
-
Captures: Diagonally 1 square.
Special:
-
En passant: Captures a pawn that moved 2 squares past it.
-
Promotion: Reaches the 8th rank → becomes any piece (usually Queen).
-
Rook (♖ / ♜)
-
Moves: Straight lines (any distance).
-
Special: Castling (moves with the king).
-
Knight (♘ / ♞)
-
Moves: "L-shape" (2 squares one way + 1 square perpendicular).
-
Jumps: Over other pieces.
-
Bishop (♗ / ♝)
-
Moves: Diagonals (any distance).
-
Stays on one color forever.
-
Queen (♕ / ♛)
-
Moves: Any direction (straight/diagonal, any distance).
-
Most powerful piece!
-
King (♔ / ♚)
-
Moves: 1 square in any direction.
Special:
Castling: Swaps places with a rook (if no blocks/checks).
Checkmate: Loses if trapped with no escape.
How to move
- One move per turn
-
Choose your piece, place it on a legal square
-
Your color only: White moves first, then Black, alternating.
- No passing: You must move if it’s your turn.
How to Capture ("Eat")
-
Land on an enemy piece: Replace it with your piece.
-
Pawns capture diagonally only (not straight).
- Kings cannot be captured (checkmate ends the game).
✔ Check: Attack the enemy king (they must escape next turn). ❌ Illegal: Moving into check or leaving your king in check.
Special moves
| Move | Key Rule | Notation | | ---------- | ---------------------------------- | ----------- | | Castling | King + rook, no prior moves/checks |
O-O| | Promotion | Pawn→any piece at 8th rank |e8=Q| | En Passant | Capture a 2-square pawn jump |exd6 e.p.|
-
Castling (The King’s Escape)
-
What: King + Rook move together in one turn.
How:
- King moves 2 squares toward a rook.
- Rook jumps to the other side of the king.
Rules:
- No checks: King can’t be in check or pass through check.
- Never moved: King and that rook must be untouched.
Types:
Kingside (♔→♖, faster): O-O
Queenside (♔←♖, safer): O-O-O
-
Promotion ("Crowning")
-
What: Pawn reaches the 8th rank → turns into any piece (usually Queen).
-
How: Replace the pawn with a new piece (even if the original is still on the board).
Fun fact: You can have 9 queens (1 original + 8 promotions)!
Promotion example (Pawn→Queen at h8)
-
En Passant (French for "In Passing")
-
When: Enemy pawn moves 2 squares forward past your pawn.
-
How: Capture it diagonally (as if it moved only 1 square).
Rule: Must do it immediately (next turn only).
chess #elsalvador #somachess
-
-
 @ ba36d0f7:cd802cba
2025-04-02 21:08:28
@ ba36d0f7:cd802cba
2025-04-02 21:08:28Chess Board Setup

- The Basics
8x8 grid, alternating light/dark squares.
Key rule: *Always place the board so a light square is on each player’s bottom-right.
- Coordinates Files (columns): Labeled a to h (left to right).
Ranks (rows): Numbered 1 to 8 (White’s side = 1, Black’s = 8).
Notation: Squares are file + rank (e.g., e4, a7).
- Piece Placement
Black (Top): a8: Rook b8: Knight c8: Bishop d8: Queen
e8: King f8: Bishop g8: Knight h8: Rook
Rank 7: All pawns (a7-h7)White (Bottom): a1: Rook b1: Knight c1: Bishop d1: Queen
e1: King f1: Bishop g1: Knight h1: Rook
Rank 2: All pawns (a2-h2)Quick Tip: Queens start on their color (Whiteon d1, Black on d8).
Checkmate, stalemate & draws
Chess is a two-player strategy game where the ultimate goal is to checkmate your opponent’s king. However, games can also end in a stalemate or draw under specific conditions.
- Checkmate (Winning the Game)
- Definition: The enemy king is in check (under attack) and has no legal moves to escape.
-
Result: The game ends immediately—the player delivering checkmate wins.
-
Stalemate (Draw)
- Definition: The player whose turn it is has no legal moves, but their king is not in check.
- Result: The game is a draw (no winner).
Common Causes: - A lone king with no moves left. - Poor pawn structure blocking all options.
- Other Draws
Games can also end in a draw due to:
- Insufficient Material
- Only kings remain.
-
King + bishop vs. king (no possible checkmate).
-
Threefold Repetition
-
The same position occurs 3 times (with the same player to move).
-
50-Move Rule
-
No pawn moves or captures in 50 consecutive moves (by both players).
-
Agreement
- Players mutually agree to a draw.
Key differences:
| Term | King in Check? | Legal Moves? | Result | | --------- | -------------- | ------------ | -------- | | Checkmate | Yes | No | Win/Loss | | Stalemate | No | No | Draw | | Draw | N/A | N/A | Tie |
Chess history
-
Ancient Origins (6th Century)
-
Birthplace: Northern India (as Chaturanga), meaning "four divisions" (infantry, cavalry, elephants, chariots—early versions of pawns, knights, bishops, rooks).
-
Spread: Reached Persia as Shatranj by 600 AD, where key rules (like "check" and "checkmate") emerged.
Fun fact: "Checkmate" comes from Persian "Shah Mat" ("the king is helpless").
-
Medieval Europe (9th–15th Century)
-
Rebranding: Arabs brought chess to Spain by 1000 AD; Europeans adapted pieces to feudal society:
Elephants → Bishops Viziers → Queens (weak at first—could only move one square!)
-
Major Change: By 1475, the queen became the most powerful piece ("Mad Queen Chess"), speeding up the game.
-
Modern Chess (1850–Present)
-
Standardization: First official world championship (1886, Wilhelm Steinitz vs. Johannes Zukertort).
-
Computers: IBM’s Deep Blue defeated Garry Kasparov in 1997, revolutionizing AI.
-
Today: Online platforms (Chess.com, Lichess) and pop culture (The Queen’s Gambit) fuel a global boom.
Did You Know?
-
The longest possible chess game is 5,949 moves (theoretical limit).
-
The longest recorded game was 269 moves, 1989 Nikolić vs. Arsović.
-
The oldest recorded chess opening (1.e4) appears in a 1490 Spanish manuscript.
chess #education #elsalvador #chesselsalvador #somachess #article #soma
-
 @ ef53426a:7e988851
2025-04-02 21:02:06
@ ef53426a:7e988851
2025-04-02 21:02:06Bartering and early money
\ Early societies bartered goods, but transactions were often complicated. The value of goods doesn’t always align.
Enter money. It’s used as an indirect exchange for any goods, so everyone wants it.
Early money wasn’t anything like what we use today. For example, the inhabitants of Yap Island (Micronesia) used large Rai stones for trade. New stones were dragged up a hill for everyone to see. The owner would then exchange part of the stone for goods and services.
As they were hard to quarry and move, Rai stones retained their value (salability). Then, an Irish-American captain started importing stones using modern technology. Soon enough, they became so common, they no longer worked as money.
Gold — the basis for sound money
\ Smelting made it possible to create highly salable and transportable coins. Gold was best because it’s virtually impossible to destroy and can’t be synthesized using other materials. It has a fairly limited supply, which grows slowly and predictably (due to the difficulty of mining).
Technologies like the telegraph and trains made it easier for both people and goods to get from point A to point B. That, in turn, justified forms of payment like checks, paper receipts, and bills. But paper is not worth much unless it’s backed by something.
Governments worldwide issued paper money backed by precious metals, which they stored in vaults. By 1900, around 50 countries had adopted the Gold Standard. This was sound money.
Currencies devalued
\ Roman emperor Julius Caesar issued the Aureus, an empire-standard coin containing 8 grams of gold. But as growth began to slow, rulers started ‘coin clipping’, reducing the quantity of precious metal in coins. This eventually triggered a series of economic crises that led to the downfall of the Roman Empire.
The gold standard had one major flaw: it had to be stored in bank vaults. This created a highly centralized system in which governments controlled the value of paper money. If they wanted to, they could always increase the supply of money without increasing the corresponding amount of gold.
In 1914, nearly every major European power decided to do this to fund their war operations. Rather than raising taxes, they simply printed new money with no extra gold. The standard had been abandoned.
Government-backed money
\ Governments chose to introduce fiat money – currency backed by decree rather than gold. The adoption of the fiat system led to an age of unsound money shaped by ever-greater intervention in the economy as governments scrambled to stabilize their currencies.
By 1944, the end of the Second World War was in sight, and the victors began planning the postwar economic order. The world’s currencies would be tied to the US dollar at a fixed exchange rate. The dollar would in turn be tied to the value of gold, again at a fixed rate.
The United States bent the rules and inflated its own currency compared to gold. Other nations inflated their currencies compared to the dollar. On August 15, 1971, President Nixon announced that dollars would no longer be convertible to gold.
Sound money = functioning economy
\ Sound money encourages people to save and invest, enabling sustainable, long-term growth. Why? Well, humans have a natural positive time preference: we prefer instant gratification over future gratification. Sound money prompts us to think more about the future.
The more capital accumulation there is, the greater the chance of stable, long-term economic growth. Unsound money distorts capital accumulation. When governments interfere with the money supply, they also interfere with prices. And prices give investors the information they need to make good decisions without having to learn every tiny detail about global events.
Recessions and debt arise from unsound money
\ Government interference takes the form of central planning. No single person, agency, or department ever has access to all the information necessary to understand the vast and complex economy. Interventions distort markets, creating boom and bust cycles.
According to Keynes and his followers, the best way to respond to recessions is to increase spending. You could lower taxes, but people don’t usually spend their extra money. Raising taxes is unpopular, so governments invariably decide to increase the money supply. Saving becomes less attractive, creating a culture of unwise spending and growing debt.
We need to return to sound money and a new gold standard. Enter bitcoin.
Bitcoin is scarce
\ Bitcoin has similar traits to gold. Its supply is literally fixed. Once there are 21 million bitcoins in circulation, no more will be issued.
The supply grows at a diminishing rate. Computers across the Bitcoin network pool their processing power to solve complex algorithmic problems. Once these puzzles have been cracked, the “miners” receive bitcoins as a reward.
Satoshi Nakamoto designed the system to avoid gold rushes. The algorithmic problems become more difficult to solve as the number of computers working on them rises, guaranteeing a steady and reliable supply. Also, the number of bitcoins issued is halved every four years, resulting in ever-smaller releases until 2140, after which no more coins will be released.
That makes bitcoin unique. It is the only good that is defined by absolute scarcity. No amount of time or resources can create more bitcoins than the programmed supply allows. The supply cannot be manipulated, making it a perfect store of value.
Bitcoin is secure
\ The bitcoin ledger uses the public blockchain. When mining computers crack an algorithmic puzzle, they create a block. The blocks on the ledger contain details about every blockchain transaction ever completed. Every network user can view this information.
Ownership of bitcoins is only valid once it’s been registered on the blockchain. This is only possible if the majority of network users approve it, so there’s no need for a central authority to oversee transactions. While verifying new blocks requires virtually no energy, creating a fraudulent block would cost a significant amount of processing power.
Even if a user decided to expend vast amounts of energy and successfully hacked a majority of all network nodes to approve a fraudulent block, they’d gain very little. Trust in bitcoin would be lost, leading to a drop in demand and value.
Challenges for adoption
\ Because bitcoin is new, demand has varied. The volatile price has, at times, undermined the currency’s status as an effective store of value.
Bitcoin’s transaction limit is currently set at 500,000 per day. That could be increased, but there will always be a daily cap. The more transactions that take place, the more nodes there’ll need to be. This increases transaction fees and the amount of processing power expended.
Bitcoin could be traded off the blockchain, meaning currencies will be backed by bitcoin. That would create a new standard, but it would also mean that new centralized institutions would need to manage this system.

This 5-minute summary did not use copyrighted material from the book. It aims simply to give readers a quick understanding of the book (which is well worth reading).
‘The Bitcoin Standard: The Decentralized Alternative to Central Banking’ was written by economist Saifedean Ammous in 2018.
Buy the book and many more titles at bitcoinbook.shop
-
 @ 7d33ba57:1b82db35
2025-04-02 19:47:25
@ 7d33ba57:1b82db35
2025-04-02 19:47:25Trogir is a UNESCO-listed coastal town just 30 minutes from Split, known for its well-preserved medieval architecture, charming waterfront, and rich history. Often called "The Little Venice of Dalmatia," Trogir is built on a small island connected to the mainland and Čiovo Island by bridges. Its cobblestone streets, Renaissance palaces, and lively cafés** make it a perfect stop for history lovers and travelers seeking authentic Dalmatian charm.
🏛️ Top Things to See & Do in Trogir
1️⃣ Explore Trogir Old Town (UNESCO) 🏡
- Wander through the labyrinth of narrow streets, filled with hidden courtyards and stone houses.
- Admire Venetian-style palaces, Romanesque churches, and medieval city walls.
- Visit St. Lawrence Cathedral, featuring the famous Radovan Portal, a masterpiece of medieval stone carving.
2️⃣ Climb the Bell Tower of St. Lawrence ⛪
- Offers stunning panoramic views over Trogir and the Adriatic.
- A bit of a steep climb, but totally worth it for the breathtaking scenery!
3️⃣ Visit Kamerlengo Fortress 🏰
- A 15th-century Venetian fortress with amazing sea views from the top.
- In summer, it hosts concerts and cultural events.
4️⃣ Stroll Along the Trogir Riva Promenade 🌊
- A lively waterfront filled with cafés, restaurants, and luxury yachts.
- Perfect for a relaxing evening walk while watching the sunset.
5️⃣ Relax on the Best Beaches Near Trogir 🏖️
- Okrug Gornji Beach (Copacabana Beach) – A long, lively beach with bars & water activities.
- Pantan Beach – A quieter spot with clear waters and pine tree shade.
- Kava Beach (Čiovo Island) – A more secluded and natural beach, ideal for relaxation.
6️⃣ Take a Boat Trip to the Blue Lagoon 🛥️
- A stunning turquoise bay, perfect for swimming and snorkeling.
- Just a short boat ride from Trogir.
7️⃣ Try Dalmatian Cuisine 🍽️
- Grilled fresh fish & seafood – Trogir’s specialty! 🐟
- Pašticada – Slow-cooked beef in a rich red wine sauce, served with gnocchi.
- Homemade Dalmatian prosciutto & cheese – Best paired with local Plavac Mali wine.
🚗 How to Get to Trogir
✈️ By Air:
- Split Airport (SPU) is just 10 minutes away! 🚕
🚘 By Car:
- From Split: ~30 minutes (27 km)
- From Zadar: ~1.5 hours (130 km)
🚌 By Bus: Frequent buses run between Split and Trogir.
⛵ By Boat: A seasonal boat line connects Trogir with Split and nearby islands.💡 Tips for Visiting Trogir
✅ Best time to visit? April–October for sunny weather & fewer crowds ☀️
✅ Stay for sunset – The views from the Riva & Kamerlengo Fortress are magical 🌅
✅ Wear comfy shoes – The old town’s stone streets can be slippery 👟
✅ Book Blue Lagoon trips in advance – It’s a popular excursion 🚤
✅ Try a wine tasting at a local konoba (traditional tavern) 🍷
-
 @ ba36d0f7:cd802cba
2025-04-02 19:31:27
@ ba36d0f7:cd802cba
2025-04-02 19:31:27
"It Takes a Village"
…But what if the "village" is a system that prioritizes obedience over curiosity, grades over growth, and rigid curriculums over real-world learning?
For decades, we’ve accepted a model where kids spend hours a day passively absorbing information in classrooms, where their worth is measured by standardized tests rather than their ability to think, adapt, or create. Meanwhile, the tools to revolutionize learning - technology, connectivity, and decentralized knowledge - sit in our pockets, dismissed as "distractions" rather than leveraged as liberation.
The Paradox of Progress
We live in an era of unprecedented access to information. Yet, our education systems cling to industrial-era ideals, villainizing screens instead of teaching how to wield them wisely. Yes, mindless screen time harms—but so does mindless schooling. The real failure? Not preparing learners to navigate, critique, and contribute to the world they actually live in.
A different approach
soma is an experiment in self-directed, community-rooted learning. It asks:
-
What if education integrated with life instead of interrupting it?
-
What if "success" meant mastery driven by curiosity, not compliance?
-
What if technology connected learners to mentors, resources, and real-world problems - not just apps that mimic worksheets?
This isn’t about abandoning theory or expertise. It’s about flipping the script:
-
Empiric learning comes first (doing, trying, failing, exploring).
- This is where physical spaces thrive - quilombos, workshops, community gardens. Where we take responsibility for our shared world.
-
Theoretical depth follows when the learner chooses it - fueled by a desire to go further.
-
This is where our virtual spaces shine to guarantee accessibility: as tool, not a privilege.
-
Tech is recreation, not a crutch - the spice, not the meal.
-
A call for villages, not factories
soma imagines communities where learning is an act of devotion - to exploration, to curiosity, to the sacred cycle of trying, failing, and trying again.
Where you learn because you want to - to better your surroundings, not because you were told to.
Where a child’s obsession with ants leads them to a biologist’s fieldwork and a poet’s metaphor - because both are natural extensions of wonder.
Where a teen building a game pursues storytelling, math, and ethics on their own terms, stitching knowledge together like patchwork quilt. Where we see learning happening in parks, in makerspaces and on screens - used intentionally.This is education returned to its human rhythm: urgent, messy, and alive.
Join the experiment
This is just the start. soma is a provocation, a prototype, and an open invitation to rethink how we learn.
Let’s stop preparing kids for a world that no longer exists.
➡️ Follow updates, share your ideas, or tell us: What does your ideal "village" look like? nostr:npub1hgmdpalp9tz37vh9kxx49fm5pl75w6vwek2r80r20x2stnvq9jaq705r99
longform #article #education #elsalvador #communities #decentralized
-
-
 @ cbaa0c82:e9313245
2025-04-02 18:53:57
@ cbaa0c82:e9313245
2025-04-02 18:53:57TheWholeGrain - #March2025
March of 2025 was a standard month for Bread and Toast. However, it did include a the occasional five Sunday Singles which seems like hitting the jackpot! Talk about lucky!
Included with the five Sunday Singles was two more pages of the Adventure Series: Questline where we saw Bread, Toast, and End-Piece face off against their first adversary!
End-Piece made a first appearance for in Toast's Comic Collection under the title E: The Last Slice while the Concept Art piece was the original drawing of all three slices of bread together. And, last of all we updated the Bitcoin logo because why not!?
Sunday Singles - March 2025 2025-03-02 | Sunday Single 82 Title: Slingshot! Watch out! Toast is quite the sharpshooter! https://i.nostr.build/zHA9C7cOOZLOCl0o.png
2025-03-09 | Sunday Single 83 Title: Puzzles End-Piece just figured out the puzzle! https://i.nostr.build/u2EBdcsuwO2xo23P.png
2025-03-16 | Sunday Single 84 Title: Basketball Oh, the madness! https://i.nostr.build/8F1OFFVra7zQOIy6.png
2025-03-23 | Sunday Single 85 Title: Coffee The perfect way to start the day. https://i.nostr.build/aiGZOvOmow3igru6.png
2025-03-30 | Sunday Single 86 Title: Origami End-Piece has a way with paper. https://i.nostr.build/0ySzGwF9QnZxwLxD.png
Adventure Series: Questline The group is attacked by a crow with Bread being the target of the giant bird, but with a group of trusty friends any enemy can be defeated!
Artist: Dakota Jernigan (The Bitcoin Painter) Writer: Daniel David (dan 🍞)
2025-03-11 | Questline 005 - Under Attack Toast and End-Piece are able to escape the attack from the giant winged predator, but Bread being distracted by thoughts of the village is caught off guard. End-Piece immediately charges the attacker with a fury of mallet swings. Meanwhile, Toast loads up an arrow with intentions of piercing through the giant bird. https://i.nostr.build/F24sd7SFFbsW9WZY.png
2025-03-25 | Questline 006 - A Finished Battle End-Piece lands a series of blows to the winged beast. Toast finishes it off with a second arrow to the heart. Bread is only slightly injured, but is more upset about having been so vulnerable due to being so distracted. Moving forward Bread will have to be more vigilant. https://i.nostr.build/n5a7Jztq9MHxuGNf.png
Other Content Released in March 2025 2025-03-05 | Toast's Comic Collection Title: E: The Last Slice #11 A gluten-based pandemic has killed off all slices of bread that are not Toast except for one slice of bread that happens to be an end piece. https://i.nostr.build/aar20oHAAKmZOovD.png
2025-03-12 | Concept Art Title: Original Bread and Toast This was the first drawing of all three characters together. It was used a lot for branding when the project first started up in 2023. https://i.nostr.build/yqkmBuTiH8AKbCzI.png
2025-03-19 | Bitcoin Art Title: Bitcoin/Bread Block Height: 888566 Two things that just go together. https://i.nostr.build/MDPkzOPVEaOJVTFE.png
Thanks for checking out the seventh issue of The Whole Grain. The Whole Grain is released on the first of every month and covers all of the content released by Bread and Toast in the previous month. For all Bread and Toast content visit BreadandToast.com!
So long, March! Bread, Toast, and End-Piece
BreadandToast #SundaySingle #Questline #ToastsComicCollection #ConceptArt #BitcoinArt #Bread #Toast #EndPiece #Artstr #Comic #Cartoon #NostrOnly #🍞 #🖼️
List of nPubs Mentioned: The Bitcoin Painter: npub1tx5ccpregnm9afq0xaj42hh93xl4qd3lfa7u74v5cdvyhwcnlanqplhd8g
dan 🍞: npub16e3vzr7dk2uepjcnl85nfare3kdapxge08gr42s99n9kg7xs8xhs90y9v6
-
 @ 17538dc2:71ed77c4
2025-04-02 16:04:59
@ 17538dc2:71ed77c4
2025-04-02 16:04:59The MacOS security update summary is a reminder that laptops and desktops are incredibly compromised.
macOS Sequoia 15.4
Released March 31, 2025
Accessibility Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: A logging issue was addressed with improved data redaction.
CVE-2025-24202: Zhongcheng Li from IES Red Team of ByteDance
AccountPolicy Available for: macOS Sequoia
Impact: A malicious app may be able to gain root privileges
Description: This issue was addressed by removing the vulnerable code.
CVE-2025-24234: an anonymous researcher
AirDrop Available for: macOS Sequoia
Impact: An app may be able to read arbitrary file metadata
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24097: Ron Masas of BREAKPOINT.SH
App Store Available for: macOS Sequoia
Impact: A malicious app may be able to access private information
Description: This issue was addressed by removing the vulnerable code.
CVE-2025-24276: an anonymous researcher
AppleMobileFileIntegrity Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: The issue was addressed with improved checks.
CVE-2025-24272: Mickey Jin (@patch1t)
AppleMobileFileIntegrity Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: A downgrade issue was addressed with additional code-signing restrictions.
CVE-2025-24239: Wojciech Regula of SecuRing (wojciechregula.blog)
AppleMobileFileIntegrity Available for: macOS Sequoia
Impact: A malicious app may be able to read or write to protected files
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24233: Claudio Bozzato and Francesco Benvenuto of Cisco Talos.
AppleMobileFileIntegrity Available for: macOS Sequoia
Impact: An app may be able to access user-sensitive data
Description: A privacy issue was addressed by removing the vulnerable code.
CVE-2025-30443: Bohdan Stasiuk (@bohdan_stasiuk)
Audio Available for: macOS Sequoia
Impact: Processing a maliciously crafted font may result in the disclosure of process memory
Description: The issue was addressed with improved memory handling.
CVE-2025-24244: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative
Audio Available for: macOS Sequoia
Impact: Processing a maliciously crafted file may lead to arbitrary code execution
Description: The issue was addressed with improved memory handling.
CVE-2025-24243: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative
Authentication Services Available for: macOS Sequoia
Impact: Password autofill may fill in passwords after failing authentication
Description: This issue was addressed through improved state management.
CVE-2025-30430: Dominik Rath
Authentication Services Available for: macOS Sequoia
Impact: A malicious website may be able to claim WebAuthn credentials from another website that shares a registrable suffix
Description: The issue was addressed with improved input validation.
CVE-2025-24180: Martin Kreichgauer of Google Chrome
Authentication Services Available for: macOS Sequoia
Impact: A malicious app may be able to access a user's saved passwords
Description: This issue was addressed by adding a delay between verification code attempts.
CVE-2025-24245: Ian Mckay (@iann0036)
Automator Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: A permissions issue was addressed by removing vulnerable code and adding additional checks.
CVE-2025-30460: an anonymous researcher
BiometricKit Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination
Description: A buffer overflow was addressed with improved bounds checking.
CVE-2025-24237: Yutong Xiu
Calendar Available for: macOS Sequoia
Impact: An app may be able to break out of its sandbox
Description: A path handling issue was addressed with improved validation.
CVE-2025-30429: Denis Tokarev (@illusionofcha0s)
Calendar Available for: macOS Sequoia
Impact: An app may be able to break out of its sandbox
Description: This issue was addressed with improved checks.
CVE-2025-24212: Denis Tokarev (@illusionofcha0s)
CloudKit Available for: macOS Sequoia
Impact: A malicious app may be able to access private information
Description: The issue was addressed with improved checks.
CVE-2025-24215: Kirin (@Pwnrin)
CoreAudio Available for: macOS Sequoia
Impact: Parsing a file may lead to an unexpected app termination
Description: The issue was addressed with improved checks.
CVE-2025-24163: Google Threat Analysis Group
CoreAudio Available for: macOS Sequoia
Impact: Playing a malicious audio file may lead to an unexpected app termination
Description: An out-of-bounds read issue was addressed with improved input validation.
CVE-2025-24230: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative
CoreMedia Available for: macOS Sequoia
Impact: Processing a maliciously crafted video file may lead to unexpected app termination or corrupt process memory
Description: This issue was addressed with improved memory handling.
CVE-2025-24211: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative
CoreMedia Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: An access issue was addressed with additional sandbox restrictions.
CVE-2025-24236: Csaba Fitzl (@theevilbit) and Nolan Astrein of Kandji
CoreMedia Available for: macOS Sequoia
Impact: Processing a maliciously crafted video file may lead to unexpected app termination or corrupt process memory
Description: The issue was addressed with improved memory handling.
CVE-2025-24190: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative
CoreMedia Playback Available for: macOS Sequoia
Impact: A malicious app may be able to access private information
Description: A path handling issue was addressed with improved validation.
CVE-2025-30454: pattern-f (@pattern_F_)
CoreServices Description: This issue was addressed through improved state management.
CVE-2025-31191: Jonathan Bar Or (@yo_yo_yo_jbo) of Microsoft, and an anonymous researcher Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
CoreText Available for: macOS Sequoia
Impact: Processing a maliciously crafted font may result in the disclosure of process memory
Description: An out-of-bounds read issue was addressed with improved input validation.
CVE-2025-24182: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative
Crash Reporter Available for: macOS Sequoia
Impact: An app may be able to gain root privileges
Description: A parsing issue in the handling of directory paths was addressed with improved path validation.
CVE-2025-24277: Csaba Fitzl (@theevilbit) of Kandji and Gergely Kalman (@gergely_kalman), and an anonymous researcher
curl Available for: macOS Sequoia
Impact: An input validation issue was addressed
Description: This is a vulnerability in open source code and Apple Software is among the affected projects. The CVE-ID was assigned by a third party. Learn more about the issue and CVE-ID at cve.org.
CVE-2024-9681
Disk Images Available for: macOS Sequoia
Impact: An app may be able to break out of its sandbox
Description: A file access issue was addressed with improved input validation.
CVE-2025-24255: an anonymous researcher
DiskArbitration Available for: macOS Sequoia
Impact: An app may be able to gain root privileges
Description: A parsing issue in the handling of directory paths was addressed with improved path validation.
CVE-2025-30456: Gergely Kalman (@gergely_kalman)
DiskArbitration Available for: macOS Sequoia
Impact: An app may be able to gain root privileges
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24267: an anonymous researcher
Dock Available for: macOS Sequoia
Impact: A malicious app may be able to access private information
Description: The issue was addressed with improved checks.
CVE-2025-30455: Mickey Jin (@patch1t), and an anonymous researcher
Dock Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: This issue was addressed by removing the vulnerable code.
CVE-2025-31187: Rodolphe BRUNETTI (@eisw0lf) of Lupus Nova
dyld Available for: macOS Sequoia
Impact: Apps that appear to use App Sandbox may be able to launch without restrictions
Description: A library injection issue was addressed with additional restrictions.
CVE-2025-30462: Pietro Francesco Tirenna, Davide Silvetti, Abdel Adim Oisfi of Shielder (shielder.com)
FaceTime Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: This issue was addressed with improved redaction of sensitive information.
CVE-2025-30451: Kirin (@Pwnrin) and luckyu (@uuulucky)
FeedbackLogger Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: This issue was addressed with improved data protection.
CVE-2025-24281: Rodolphe BRUNETTI (@eisw0lf)
Focus Available for: macOS Sequoia
Impact: An attacker with physical access to a locked device may be able to view sensitive user information
Description: The issue was addressed with improved checks.
CVE-2025-30439: Andr.Ess
Focus Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: A logging issue was addressed with improved data redaction.
CVE-2025-24283: Kirin (@Pwnrin)
Foundation Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: An access issue was addressed with additional sandbox restrictions on the system pasteboards.
CVE-2025-30461: an anonymous researcher
Foundation Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: The issue was resolved by sanitizing logging
CVE-2025-30447: LFY@secsys from Fudan University
Foundation Available for: macOS Sequoia
Impact: An app may be able to cause a denial-of-service
Description: An uncontrolled format string issue was addressed with improved input validation.
CVE-2025-24199: Manuel Fernandez (Stackhopper Security)
GPU Drivers Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination or corrupt kernel memory
Description: An out-of-bounds write issue was addressed with improved bounds checking.
CVE-2025-30464: ABC Research s.r.o.
CVE-2025-24273: Wang Yu of Cyberserval
GPU Drivers Available for: macOS Sequoia
Impact: An app may be able to disclose kernel memory
Description: The issue was addressed with improved bounds checks.
CVE-2025-24256: Anonymous working with Trend Micro Zero Day Initiative, Murray Mike
Handoff Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: The issue was addressed with improved restriction of data container access.
CVE-2025-30463: mzzzz__
ImageIO Available for: macOS Sequoia
Impact: Parsing an image may lead to disclosure of user information
Description: A logic error was addressed with improved error handling.
CVE-2025-24210: Anonymous working with Trend Micro Zero Day Initiative
Installer Available for: macOS Sequoia
Impact: An app may be able to check the existence of an arbitrary path on the file system
Description: A permissions issue was addressed with additional sandbox restrictions.
CVE-2025-24249: YingQi Shi(@Mas0nShi) of DBAppSecurity's WeBin lab and Minghao Lin (@Y1nKoc)
Installer Available for: macOS Sequoia
Impact: A sandboxed app may be able to access sensitive user data
Description: A logic issue was addressed with improved checks.
CVE-2025-24229: an anonymous researcher
IOGPUFamily Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination or write kernel memory
Description: An out-of-bounds write issue was addressed with improved input validation.
CVE-2025-24257: Wang Yu of Cyberserval
IOMobileFrameBuffer Available for: macOS Sequoia
Impact: An app may be able to corrupt coprocessor memory
Description: The issue was addressed with improved bounds checks.
CVE-2025-30437: Ye Zhang (@VAR10CK) of Baidu Security
Kerberos Helper Available for: macOS Sequoia
Impact: A remote attacker may be able to cause unexpected app termination or heap corruption
Description: A memory initialization issue was addressed with improved memory handling.
CVE-2025-24235: Dave G.
Kernel Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: The issue was addressed with improved checks.
CVE-2025-24204: Koh M. Nakagawa (@tsunek0h) of FFRI Security, Inc.
Kernel Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: The issue was addressed with improved checks.
CVE-2025-24203: Ian Beer of Google Project Zero
Kernel Available for: macOS Sequoia
Impact: An attacker with user privileges may be able to read kernel memory
Description: A type confusion issue was addressed with improved memory handling.
CVE-2025-24196: Joseph Ravichandran (@0xjprx) of MIT CSAIL
LaunchServices Available for: macOS Sequoia
Impact: A malicious JAR file may bypass Gatekeeper checks
Description: This issue was addressed with improved handling of executable types.
CVE-2025-24148: Kenneth Chew
libarchive Available for: macOS Sequoia
Impact: An input validation issue was addressed
Description: This is a vulnerability in open source code and Apple Software is among the affected projects. The CVE-ID was assigned by a third party. Learn more about the issue and CVE-ID at cve.org.
CVE-2024-48958
Libinfo Available for: macOS Sequoia
Impact: A user may be able to elevate privileges
Description: An integer overflow was addressed with improved input validation.
CVE-2025-24195: Paweł Płatek (Trail of Bits)
libnetcore Available for: macOS Sequoia
Impact: Processing maliciously crafted web content may result in the disclosure of process memory
Description: A logic issue was addressed with improved checks.
CVE-2025-24194: an anonymous researcher
libxml2 Available for: macOS Sequoia
Impact: Parsing a file may lead to an unexpected app termination
Description: This is a vulnerability in open source code and Apple Software is among the affected projects. The CVE-ID was assigned by a third party. Learn more about the issue and CVE-ID at cve.org.
CVE-2025-27113
CVE-2024-56171
libxpc Available for: macOS Sequoia
Impact: An app may be able to break out of its sandbox
Description: This issue was addressed through improved state management.
CVE-2025-24178: an anonymous researcher
libxpc Available for: macOS Sequoia
Impact: An app may be able to delete files for which it does not have permission
Description: This issue was addressed with improved handling of symlinks.
CVE-2025-31182: Alex Radocea and Dave G. of Supernetworks, 风沐云烟(@binary_fmyy) and Minghao Lin(@Y1nKoc)
libxpc Available for: macOS Sequoia
Impact: An app may be able to gain elevated privileges
Description: A logic issue was addressed with improved checks.
CVE-2025-24238: an anonymous researcher
Mail Available for: macOS Sequoia
Impact: "Block All Remote Content" may not apply for all mail previews
Description: A permissions issue was addressed with additional sandbox restrictions.
CVE-2025-24172: an anonymous researcher
manpages Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: This issue was addressed with improved validation of symlinks.
CVE-2025-30450: Pwn2car
Maps Available for: macOS Sequoia
Impact: An app may be able to read sensitive location information
Description: A path handling issue was addressed with improved logic.
CVE-2025-30470: LFY@secsys from Fudan University
NetworkExtension Available for: macOS Sequoia
Impact: An app may be able to enumerate a user's installed apps
Description: This issue was addressed with additional entitlement checks.
CVE-2025-30426: Jimmy
Notes Available for: macOS Sequoia
Impact: A sandboxed app may be able to access sensitive user data in system logs
Description: A privacy issue was addressed with improved private data redaction for log entries.
CVE-2025-24262: LFY@secsys from Fudan University
NSDocument Available for: macOS Sequoia
Impact: A malicious app may be able to access arbitrary files
Description: This issue was addressed through improved state management.
CVE-2025-24232: an anonymous researcher
OpenSSH Available for: macOS Sequoia
Impact: An app may be able to access user-sensitive data
Description: An injection issue was addressed with improved validation.
CVE-2025-24246: Mickey Jin (@patch1t)
PackageKit Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: The issue was addressed with improved checks.
CVE-2025-24261: Mickey Jin (@patch1t)
PackageKit Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: A logic issue was addressed with improved checks.
CVE-2025-24164: Mickey Jin (@patch1t)
PackageKit Available for: macOS Sequoia
Impact: A malicious app with root privileges may be able to modify the contents of system files
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-30446: Pedro Tôrres (@t0rr3sp3dr0)
Parental Controls Available for: macOS Sequoia
Impact: An app may be able to retrieve Safari bookmarks without an entitlement check
Description: This issue was addressed with additional entitlement checks.
CVE-2025-24259: Noah Gregory (wts.dev)
Photos Storage Available for: macOS Sequoia
Impact: Deleting a conversation in Messages may expose user contact information in system logging
Description: A logging issue was addressed with improved data redaction.
CVE-2025-30424: an anonymous researcher
Power Services Available for: macOS Sequoia
Impact: An app may be able to break out of its sandbox
Description: This issue was addressed with additional entitlement checks.
CVE-2025-24173: Mickey Jin (@patch1t)
Python Available for: macOS Sequoia
Impact: A remote attacker may be able to bypass sender policy checks and deliver malicious content via email
Description: This is a vulnerability in open source code and Apple Software is among the affected projects. The CVE-ID was assigned by a third party. Learn more about the issue and CVE-ID at cve.org.
CVE-2023-27043
RPAC Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: The issue was addressed with improved validation of environment variables.
CVE-2025-24191: Claudio Bozzato and Francesco Benvenuto of Cisco Talos
Safari Available for: macOS Sequoia
Impact: Visiting a malicious website may lead to user interface spoofing
Description: The issue was addressed with improved UI.
CVE-2025-24113: @RenwaX23
Safari Available for: macOS Sequoia
Impact: Visiting a malicious website may lead to address bar spoofing
Description: The issue was addressed with improved checks.
CVE-2025-30467: @RenwaX23
Safari Available for: macOS Sequoia
Impact: A website may be able to access sensor information without user consent
Description: The issue was addressed with improved checks.
CVE-2025-31192: Jaydev Ahire
Safari Available for: macOS Sequoia
Impact: A download's origin may be incorrectly associated
Description: This issue was addressed through improved state management.
CVE-2025-24167: Syarif Muhammad Sajjad
Sandbox Available for: macOS Sequoia
Impact: An app may be able to access removable volumes without user consent
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24093: Yiğit Can YILMAZ (@yilmazcanyigit)
Sandbox Available for: macOS Sequoia
Impact: An input validation issue was addressed
Description: The issue was addressed with improved checks.
CVE-2025-30452: an anonymous researcher
Sandbox Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24181: Arsenii Kostromin (0x3c3e)
SceneKit Available for: macOS Sequoia
Impact: An app may be able to read files outside of its sandbox
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-30458: Mickey Jin (@patch1t)
Security Available for: macOS Sequoia
Impact: A remote user may be able to cause a denial-of-service
Description: A validation issue was addressed with improved logic.
CVE-2025-30471: Bing Shi, Wenchao Li, Xiaolong Bai of Alibaba Group, Luyi Xing of Indiana University Bloomington
Security Available for: macOS Sequoia
Impact: A malicious app acting as a HTTPS proxy could get access to sensitive user data
Description: This issue was addressed with improved access restrictions.
CVE-2025-24250: Wojciech Regula of SecuRing (wojciechregula.blog)
Share Sheet Available for: macOS Sequoia
Impact: A malicious app may be able to dismiss the system notification on the Lock Screen that a recording was started
Description: This issue was addressed with improved access restrictions.
CVE-2025-30438: Halle Winkler, Politepix theoffcuts.org
Shortcuts Available for: macOS Sequoia
Impact: A shortcut may be able to access files that are normally inaccessible to the Shortcuts app
Description: A permissions issue was addressed with improved validation.
CVE-2025-30465: an anonymous researcher
Shortcuts Available for: macOS Sequoia
Impact: An app may be able to access user-sensitive data
Description: An access issue was addressed with additional sandbox restrictions.
CVE-2025-24280: Kirin (@Pwnrin)
Shortcuts Available for: macOS Sequoia
Impact: A Shortcut may run with admin privileges without authentication
Description: An authentication issue was addressed with improved state management.
CVE-2025-31194: Dolf Hoegaerts
Shortcuts Available for: macOS Sequoia
Impact: A shortcut may be able to access files that are normally inaccessible to the Shortcuts app
Description: This issue was addressed with improved access restrictions.
CVE-2025-30433: Andrew James Gonzalez
Siri Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: The issue was addressed with improved restriction of data container access.
CVE-2025-31183: Kirin (@Pwnrin), Bohdan Stasiuk (@bohdan_stasiuk)
Siri Available for: macOS Sequoia
Impact: A sandboxed app may be able to access sensitive user data in system logs
Description: This issue was addressed with improved redaction of sensitive information.
CVE-2025-30435: K宝 (@Pwnrin) and luckyu (@uuulucky)
Siri Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: This issue was addressed with improved redaction of sensitive information.
CVE-2025-24217: Kirin (@Pwnrin)
Siri Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: A privacy issue was addressed by not logging contents of text fields.
CVE-2025-24214: Kirin (@Pwnrin)
Siri Available for: macOS Sequoia
Impact: An app may be able to enumerate devices that have signed into the user's Apple Account
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24248: Minghao Lin (@Y1nKoc) and Tong Liu@Lyutoon_ and 风(binary_fmyy) and F00L
Siri Available for: macOS Sequoia
Impact: An app may be able to access user-sensitive data
Description: An authorization issue was addressed with improved state management.
CVE-2025-24205: YingQi Shi(@Mas0nShi) of DBAppSecurity's WeBin lab and Minghao Lin (@Y1nKoc)
Siri Available for: macOS Sequoia
Impact: An attacker with physical access may be able to use Siri to access sensitive user data
Description: This issue was addressed by restricting options offered on a locked device.
CVE-2025-24198: Richard Hyunho Im (@richeeta) with routezero.security
SMB Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination
Description: The issue was addressed with improved memory handling.
CVE-2025-24269: Alex Radocea of Supernetworks
SMB Available for: macOS Sequoia
Impact: Mounting a maliciously crafted SMB network share may lead to system termination
Description: A race condition was addressed with improved locking.
CVE-2025-30444: Dave G.
SMB Available for: macOS Sequoia
Impact: An app may be able to execute arbitrary code with kernel privileges
Description: A buffer overflow issue was addressed with improved memory handling.
CVE-2025-24228: Joseph Ravichandran (@0xjprx) of MIT CSAIL
smbx Available for: macOS Sequoia
Impact: An attacker in a privileged position may be able to perform a denial-of-service
Description: The issue was addressed with improved memory handling.
CVE-2025-24260: zbleet of QI-ANXIN TianGong Team
Software Update Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: A library injection issue was addressed with additional restrictions.
CVE-2025-24282: Claudio Bozzato and Francesco Benvenuto of Cisco Talos
Software Update Available for: macOS Sequoia
Impact: A user may be able to elevate privileges
Description: This issue was addressed with improved validation of symlinks.
CVE-2025-24254: Arsenii Kostromin (0x3c3e)
Software Update Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: The issue was addressed with improved checks.
CVE-2025-24231: Claudio Bozzato and Francesco Benvenuto of Cisco Talos
StickerKit Available for: macOS Sequoia
Impact: An app may be able to observe unprotected user data
Description: A privacy issue was addressed by moving sensitive data to a protected location.
CVE-2025-24263: Cristian Dinca of "Tudor Vianu" National High School of Computer Science, Romania
Storage Management Available for: macOS Sequoia
Impact: An app may be able to enable iCloud storage features without user consent
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24207: YingQi Shi (@Mas0nShi) of DBAppSecurity's WeBin lab, 风沐云烟 (binary_fmyy) and Minghao Lin (@Y1nKoc)
StorageKit Available for: macOS Sequoia
Impact: An app may be able to gain root privileges
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-30449: Arsenii Kostromin (0x3c3e), and an anonymous researcher
StorageKit Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: This issue was addressed with improved handling of symlinks.
CVE-2025-24253: Mickey Jin (@patch1t), Csaba Fitzl (@theevilbit) of Kandji
StorageKit Available for: macOS Sequoia
Impact: An app may be able to access user-sensitive data
Description: A race condition was addressed with additional validation.
CVE-2025-24240: Mickey Jin (@patch1t)
StorageKit Available for: macOS Sequoia
Impact: An app may be able to bypass Privacy preferences
Description: A race condition was addressed with additional validation.
CVE-2025-31188: Mickey Jin (@patch1t)
Summarization Services Available for: macOS Sequoia
Impact: An app may be able to access information about a user's contacts
Description: A privacy issue was addressed with improved private data redaction for log entries.
CVE-2025-24218: Kirin and FlowerCode, Bohdan Stasiuk (@bohdan_stasiuk)
System Settings Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: This issue was addressed with improved validation of symlinks.
CVE-2025-24278: Zhongquan Li (@Guluisacat)
System Settings Available for: macOS Sequoia
Impact: An app with root privileges may be able to access private information
Description: This issue was addressed with improved handling of symlinks.
CVE-2025-24242: Koh M. Nakagawa (@tsunek0h) of FFRI Security, Inc.
SystemMigration Available for: macOS Sequoia
Impact: A malicious app may be able to create symlinks to protected regions of the disk
Description: This issue was addressed with improved validation of symlinks.
CVE-2025-30457: Mickey Jin (@patch1t)
Voice Control Available for: macOS Sequoia
Impact: An app may be able to access contacts
Description: This issue was addressed with improved file handling.
CVE-2025-24279: Mickey Jin (@patch1t)
Web Extensions Available for: macOS Sequoia
Impact: An app may gain unauthorized access to Local Network
Description: This issue was addressed with improved permissions checking.
CVE-2025-31184: Alexander Heinrich (@Sn0wfreeze), SEEMOO, TU Darmstadt & Mathy Vanhoef (@vanhoefm) and Jeroen Robben (@RobbenJeroen), DistriNet, KU Leuven
Web Extensions Available for: macOS Sequoia
Impact: Visiting a website may leak sensitive data
Description: A script imports issue was addressed with improved isolation.
CVE-2025-24192: Vsevolod Kokorin (Slonser) of Solidlab
WebKit Available for: macOS Sequoia
Impact: Processing maliciously crafted web content may lead to an unexpected Safari crash
Description: The issue was addressed with improved memory handling.
WebKit Bugzilla: 285892
CVE-2025-24264: Gary Kwong, and an anonymous researcher
WebKit Bugzilla: 284055
CVE-2025-24216: Paul Bakker of ParagonERP
WebKit Available for: macOS Sequoia
Impact: A type confusion issue could lead to memory corruption
Description: This issue was addressed with improved handling of floats.
WebKit Bugzilla: 286694
CVE-2025-24213: Google V8 Security Team
WebKit Available for: macOS Sequoia
Impact: Processing maliciously crafted web content may lead to an unexpected process crash
Description: A buffer overflow issue was addressed with improved memory handling.
WebKit Bugzilla: 286462
CVE-2025-24209: Francisco Alonso (@revskills), and an anonymous researcher
WebKit Available for: macOS Sequoia
Impact: Processing maliciously crafted web content may lead to an unexpected Safari crash
Description: A use-after-free issue was addressed with improved memory management.
WebKit Bugzilla: 285643
CVE-2025-30427: rheza (@ginggilBesel)
WebKit Available for: macOS Sequoia
Impact: A malicious website may be able to track users in Safari private browsing mode
Description: This issue was addressed through improved state management.
WebKit Bugzilla: 286580
CVE-2025-30425: an anonymous researcher
WindowServer Available for: macOS Sequoia
Impact: An attacker may be able to cause unexpected app termination
Description: A type confusion issue was addressed with improved checks.
CVE-2025-24247: PixiePoint Security
WindowServer Available for: macOS Sequoia
Impact: An app may be able to trick a user into copying sensitive data to the pasteboard
Description: A configuration issue was addressed with additional restrictions.
CVE-2025-24241: Andreas Hegenberg (folivora.AI GmbH)
Xsan Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination
Description: A buffer overflow was addressed with improved bounds checking.
CVE-2025-24266: an anonymous researcher
Xsan Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination
Description: An out-of-bounds read was addressed with improved bounds checking.
CVE-2025-24265: an anonymous researcher
Xsan Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination or corrupt kernel memory
Description: A buffer overflow issue was addressed with improved memory handling.
CVE-2025-24157: an anonymous researcher
-
 @ b9f4c34d:7d1a0e31
2025-04-02 15:02:59
@ b9f4c34d:7d1a0e31
2025-04-02 15:02:59testssss
-
 @ b9f4c34d:7d1a0e31
2025-04-02 15:00:20
@ b9f4c34d:7d1a0e31
2025-04-02 15:00:20Test Video Document
-
 @ b9f4c34d:7d1a0e31
2025-04-02 14:59:02
@ b9f4c34d:7d1a0e31
2025-04-02 14:59:02Testy McTestenface
It's been so long, html
-
 @ 8d34bd24:414be32b
2025-04-02 14:13:03
@ 8d34bd24:414be32b
2025-04-02 14:13:03I was reading this passage last night:
…from that time when one came to a grain heap of twenty measures, there would be only ten; and when one came to the wine vat to draw fifty measures, there would be only twenty. I smote you and every work of your hands with blasting wind, mildew and hail; yet you did not come back to Me,’ declares the Lord. ‘Do consider from this day onward, from the twenty-fourth day of the ninth month; from the day when the temple of the Lord was founded, consider: Is the seed still in the barn? Even including the vine, the fig tree, the pomegranate and the olive tree, it has not borne fruit. Yet from this day on I will bless you.’ ” (Haggai 2:16-19) {emphasis mine}
Why were bad things happening to the Israelites? Because they were not following God. Why did God allow these difficult situations to occur? Because God was calling them back to Himself.
This made me think of several times lately, when I had written about Christians going through hard times, that fellow believers had tried to kindly correct me implying that God would not allow these painful things to happen to believers. They were trying to defend God’s honor, but instead they were degrading God. If God is not in control of everything, then either God is unable to protect His own from harm because of sin or bad things happened accidentally and God ignored the injustice. Saying God was not in control of allowing every hardship is either saying God isn’t strong enough, isn’t smart enough, or isn’t loving enough. The God I serve is omniscient, omnipotent, omnipresent, and love incarnate. He also didn’t promise us easy, pleasant lives, but did promise that good would come out of every situation.
And we know that in all things God works for the good of those who love him, who have been called according to his purpose. (Romans 8:28)
When Jesus walked on earth and some people said they wanted to follow Him, His response was not what we would expect:
And He was saying to them all, “If anyone wishes to come after Me, he must deny himself, and take up his cross daily and follow Me. For whoever wishes to save his life will lose it, but whoever loses his life for My sake, he is the one who will save it. For what is a man profited if he gains the whole world, and loses or forfeits himself? For whoever is ashamed of Me and My words, the Son of Man will be ashamed of him when He comes in His glory, and the glory of the Father and of the holy angels. (Luke 9:23-26) {emphasis mine}
When one particular man said that he would follow Jesus anywhere, Jesus responded this way.
As they were going along the road, someone said to Him, “I will follow You wherever You go.” And Jesus said to him, “The foxes have holes and the birds of the air have nests, but the Son of Man has nowhere to lay His head.” (Luke 9:57-58) {emphasis mine}
Jesus was brutally honest that following Him would not be easy or comfortable. Following Jesus is more likely to lead to hardship and persecution that prosperity and comfort.
“Then they will deliver you to tribulation, and will kill you, and you will be hated by all nations because of My name. At that time many will fall away and will betray one another and hate one another. Many false prophets will arise and will mislead many. Because lawlessness is increased, most people’s love will grow cold. But the one who endures to the end, he will be saved. This gospel of the kingdom shall be preached in the whole world as a testimony to all the nations, and then the end will come. (Matthew 24:9-14) {emphasis mine}
Of course God isn’t putting us through hardship to torture us. He is putting us in situations to grow our faith and dependence on Him, i.e. Abraham. He is putting us in situations where we can minister to others, i.e. Joseph. He is using us as examples of faith to others, i.e. Job. Any hardship has an eternal purpose. Sometimes we can see it (at least eventually) if we are looking for God’s will and plan. Sometime we won’t see what He was accomplishing until we get to heaven. Still we need to trust God through it all, knowing His plan is perfect.
“For my thoughts are not your thoughts,\ neither are your ways my ways,”\ declares the Lord.
“As the heavens are higher than the earth,\ so are my ways higher than your ways\ and my thoughts than your thoughts.
As the rain and the snow\ come down from heaven,\ and do not return to it\ without watering the earth\ and making it bud and flourish,\ so that it yields seed for the sower and bread for the eater,\ so is my word that goes out from my mouth:\ It will not return to me empty,\ but will accomplish what I desire\ and achieve the purpose for which I sent it. (Isaiah 55:8-11) {emphasis mine}
God understands how hard it is to understand what He is accomplishing. We live in the here and now while He is outside time and space and therefore has a heavenly and eternal perspective that we will never truly have this side of heaven. He has told us how the story ends, so that we can have peace and trust Him through whatever circumstances He has blessed us.
Jesus answered them, “Do you now believe? Behold, an hour is coming, and has already come, for you to be scattered, each to his own home, and to leave Me alone; and yet I am not alone, because the Father is with Me. These things I have spoken to you, so that in Me you may have peace. In the world you have tribulation, but take courage; I have overcome the world.” (John 16:31-33) {emphasis mine}
In fact, Jesus made this so clear that His disciples rejoiced in persecution they received due to obeying Him and sharing His word.
They took his advice; and after calling the apostles in, they flogged them and ordered them not to speak in the name of Jesus, and then released them. So they went on their way from the presence of the Council, rejoicing that they had been considered worthy to suffer shame for His name. (Acts 5:40-41) {emphasis mine}
Peter specifically warns believers to expect trials and hardship.
Dear friends, do not be surprised at the fiery ordeal that has come on you to test you, as though something strange were happening to you. But rejoice inasmuch as you participate in the sufferings of Christ, so that you may be overjoyed when his glory is revealed. If you are insulted because of the name of Christ, you are blessed, for the Spirit of glory and of God rests on you. If you suffer, it should not be as a murderer or thief or any other kind of criminal, or even as a meddler. However, if you suffer as a Christian, do not be ashamed, but praise God that you bear that name. For it is time for judgment to begin with God’s household; and if it begins with us, what will the outcome be for those who do not obey the gospel of God? And,
“If it is hard for the righteous to be saved,\ what will become of the ungodly and the sinner?”
So then, those who suffer according to God’s will should commit themselves to their faithful Creator and continue to do good. (1 Peter 4:12-19) {emphasis mine}
Paul writes about begging God to take away a health issue. Eventually he accepted it as part of God’s plan for his life and boasted gladly in his hardship.
…Therefore, in order to keep me from becoming conceited, I was given a thorn in my flesh, a messenger of Satan, to torment me. Three times I pleaded with the Lord to take it away from me. But he said to me, “My grace is sufficient for you, for my power is made perfect in weakness.” Therefore I will boast all the more gladly about my weaknesses, so that Christ’s power may rest on me. That is why, for Christ’s sake, I delight in weaknesses, in insults, in hardships, in persecutions, in difficulties. For when I am weak, then I am strong. (2 Corinthians 12:7b-10) {emphasis mine}
No matter what hardships we experience in life, whether poverty or persecution or poor health or loss of a loved one or any other hardship, God is with us working everything for our good.
Who will separate us from the love of Christ? Will tribulation, or distress, or persecution, or famine, or nakedness, or peril, or sword? Just as it is written,
“For Your sake we are being put to death all day long;\ We were considered as sheep to be slaughtered.” **But in all these things we overwhelmingly conquer through Him who loved us. For I am convinced that neither death, nor life, nor angels, nor principalities, nor things present, nor things to come, nor powers, nor height, nor depth, nor any other created thing, will be able to separate us from the love of God, which is in Christ Jesus our Lord. (Romans 8:35-39) {emphasis mine}
I like to look at the story of Joseph as an example of God’s extraordinary plan in the life of a faithful believer. Joseph trusted and honored God. God had a plan for Joseph to be used to save the lives of his family and the people of the Middle East from famine, but God didn’t just instantly put Joseph in a position of power to help. He prepared Joseph and slowly moved him to where he needed to be.
First Josephs brothers wanted to kill him out of jealousy, but God used greed to get them to sell Joseph as a slave instead. He orchestrated the right slave traders to walk by at the right time so that Joseph would wind up in the house of Potiphar, the Pharaoh’s guard.
Then when Joseph acted honorably towards God, his master, and his master’s wife, Joseph was sent to jail for years. I’m sure Joseph was wondering why God would send him to prison for doing what was right, but it put him into the presence of the cupbearer of Pharaoh. A long time after correctly interpreting the cup bearer’s dream, Joseph was called up to interpret Pharaoh’s dream, put in charge of the famine preparation and became second in command after Pharaoh. Joseph, after years of slavery and jail time, was now the second most powerful man in the Middle East, if not the world. God had a plan, but it was hard to see until its completion.
In the same way, Job lost his wealth, his children, his health, and his reputation, but remember that Satan had to get God’s permission before anything could be done to hurt Job. So many people today are blessed by seeing Job’s response to hardship and loss, by seeing Job’s faith, his struggle, and his submission to God’s plan. In this case God even gives Job more after this time of testing than he had before.
When we experience hardship we need to know that God has a plan for our life. It may be something amazing here on Earth. It may be souls won for Christ. It may be to prepare us for heaven. Whatever the case, it is for our good.
We don’t need to be ashamed that God would allow hardship. We grow most when we experience hardship. Our light shines brightest in darkness.
Oh, the depth of the riches of the wisdom and knowledge of God!\ How unsearchable his judgments,\ and his paths beyond tracing out!\ “Who has known the mind of the Lord?\ Or who has been his counselor?”\ “Who has ever given to God,\ that God should repay them?”\ For from him and through him and for him are all things.\ To him be the glory forever! Amen. (Romans 11:33-36)
Trust Jesus
-
 @ f3873798:24b3f2f3
2025-04-02 13:50:17
@ f3873798:24b3f2f3
2025-04-02 13:50:17O Bitcoin e as criptomoedas surgiram como uma alternativa descentralizada ao sistema financeiro tradicional. No entanto, no Brasil, o Sistema Financeiro Nacional (SFN) tem adotado medidas para controlar e limitar a exposição de investidores e instituições a esses ativos. Neste artigo, exploraremos as principais resoluções e regulamentações que restringem o investimento em Bitcoin no país.
O Posicionamento do Banco Central do Brasil (Bacen)

O Banco Central do Brasil (Bacen) e outros órgãos reguladores, como a Comissão de Valores Mobiliários (CVM), têm adotado uma postura cautelosa em relação às criptomoedas.
Resolução Bacen nº 4.753/2021
- Proíbe que instituições financeiras ofereçam serviços de criptomoedas em suas carteiras sem autorização prévia.
- Restringe bancos e corretoras de operarem diretamente com criptoativos, limitando sua integração ao sistema financeiro tradicional.
Comunicado do Bacen sobre Riscos das Criptomoedas
- O Bacen já emitiu alertas sobre os riscos de volatilidade, fraudes e falta de garantias em investimentos em Bitcoin.
- Recomenda que investidores tratem criptomoedas como ativos de alto risco.
A CVM e as Restrições a Fundos de Investimento em Bitcoin
A CVM tem sido mais restritiva que o Bacen em relação a produtos financeiros baseados em criptomoedas.
Deliberação CVM nº 175/2022
- Proíbe fundos de investimento no exterior (FIE) de alocarem mais de 10% do patrimônio em criptomoedas.
- Impede que fundos multimercados brasileiros tenham exposição direta a Bitcoin e outras criptomoedas.
Instrução CVM nº 555/2021
- Estabelece que ETFs de Bitcoin não podem ser comercializados no Brasil sem aprovação expressa da CVM.
- Até hoje, nenhum ETF de criptomoeda foi aprovado no país.
Tributação e Controles da Receita Federal
Além das restrições do Bacen e da CVM, a Receita Federal impõe regras rígidas para transações em Bitcoin:
Instrução Normativa RFB nº 1.888/2019
- Obriga declaração de todas as operações em criptomoedas acima de R$ 35 mil por mês.
- Tributa ganhos de capital em criptomoedas em 15% a 22,5%, dependendo do valor.
O Bitcoin Sob Vigilância do SFN
O Sistema Financeiro Nacional tem adotado medidas para limitar a adoção em massa do Bitcoin, seja por meio de regulamentações rígidas, restrições a fundos ou alertas sobre riscos.
Enquanto o mercado de criptomoedas cresce globalmente, no Brasil ainda há um cenário de cautela e controle, com o SFN buscando evitar que criptomoedas desafiem a hegemonia do sistema financeiro tradicional.
-
 @ 06639a38:655f8f71
2025-04-02 13:47:57
@ 06639a38:655f8f71
2025-04-02 13:47:57You can follow the work in progress here in this pull request https://github.com/nostrver-se/nostr-php/pull/68 on Github.
Before my 3-month break (Dec/Jan/Feb) working on Nostr-PHP I started with the NIP-19 integration in October '24. Encoding and decoding the simple prefixes (
npub,nsecandnote) was already done in the first commits.Learn more about NIP-19 here: https://nips.nostr.com/19
TLV's
Things were getting more complicated with the other prefixes / identifiers defined in NIP-19:
neventnaddrnprofile
This is because these identifiers contain (optional) metadata called Type-Lenght-Value aka TLV's.
When sharing a profile or an event, an app may decide to include relay information and other metadata such that other apps can locate and display these entities more easily.
For these events, the contents are a binary-encoded list of_TLV_(type-length-value), with_T_and_L_being 1 byte each (_uint8_, i.e. a number in the range of 0-255), and_V_being a sequence of bytes of the size indicated by_L_.These possible standardized
TLVtypes are:0:special- depends on the bech32 prefix:
- for
nprofileit will be the 32 bytes of the profile public key - for
neventit will be the 32 bytes of the event id - for
naddr, it is the identifier (the"d"tag) of the event being referenced. For normal replaceable events use an empty string.
- for
- depends on the bech32 prefix:
1:relay- for
nprofile,neventandnaddr, optionally, a relay in which the entity (profile or event) is more likely to be found, encoded as ascii - this may be included multiple times
- for
2:author- for
naddr, the 32 bytes of the pubkey of the event - for
nevent, optionally, the 32 bytes of the pubkey of the event
- for
3:kind- for
naddr, the 32-bit unsigned integer of the kind, big-endian - for
nevent, optionally, the 32-bit unsigned integer of the kind, big-endian
- for
These identifiers are formatted as bech32 strings, but are much longer than the package
bitwasp/bech32(used in the library) for can handle for encoding and decoding. The bech32 strings handled bybitwasp/bech32are limited to a maximum length of 90 characters.Thanks to the effort of others (nostr:npub1636uujeewag8zv8593lcvdrwlymgqre6uax4anuq3y5qehqey05sl8qpl4 and nostr:npub1efz8l77esdtpw6l359sjvakm7azvyv6mkuxphjdk3vfzkgxkatrqlpf9s4) during my break, some contributions are made (modifiying the bech32 package supporting much longer strings, up to a max of 5000 characters). At this moment, I'm integrating this (mostly copy-pasting the stuff and refactoring the code):
So what's next?
- NIP-19 code housekeeping + refactoring
- Prepare a new release with NIP-19 integration
- Create documentation page how to use NIP-19 on https://nostr-php.dev
-
 @ 7bdef7be:784a5805
2025-04-02 12:37:35
@ 7bdef7be:784a5805
2025-04-02 12:37:35The following script try, using nak, to find out the last ten people who have followed a
target_pubkey, sorted by the most recent. It's possibile to shortensearch_timerangeto speed up the search.```
!/usr/bin/env fish
Target pubkey we're looking for in the tags
set target_pubkey "6e468422dfb74a5738702a8823b9b28168abab8655faacb6853cd0ee15deee93"
set current_time (date +%s) set search_timerange (math $current_time - 600) # 24 hours = 86400 seconds
set pubkeys (nak req --kind 3 -s $search_timerange wss://relay.damus.io/ wss://nos.lol/ 2>/dev/null | \ jq -r --arg target "$target_pubkey" ' select(. != null and type == "object" and has("tags")) | select(.tags[] | select(.[0] == "p" and .[1] == $target)) | .pubkey ' | sort -u)
if test -z "$pubkeys" exit 1 end
set all_events "" set extended_search_timerange (math $current_time - 31536000) # One year
for pubkey in $pubkeys echo "Checking $pubkey" set events (nak req --author $pubkey -l 5 -k 3 -s $extended_search_timerange wss://relay.damus.io wss://nos.lol 2>/dev/null | \ jq -c --arg target "$target_pubkey" ' select(. != null and type == "object" and has("tags")) | select(.tags[][] == $target) ' 2>/dev/null)
set count (echo "$events" | jq -s 'length') if test "$count" -eq 1 set all_events $all_events $events endend
if test -n "$all_events" echo -e "Last people following $target_pubkey:" echo -e ""
set sorted_events (printf "%s\n" $all_events | jq -r -s ' unique_by(.id) | sort_by(-.created_at) | .[] | @json ') for event in $sorted_events set npub (echo $event | jq -r '.pubkey' | nak encode npub) set created_at (echo $event | jq -r '.created_at') if test (uname) = "Darwin" set follow_date (date -r "$created_at" "+%Y-%m-%d %H:%M") else set follow_date (date -d @"$created_at" "+%Y-%m-%d %H:%M") end echo "$follow_date - $npub" endend ```
-
 @ 7bdef7be:784a5805
2025-04-02 12:12:12
@ 7bdef7be:784a5805
2025-04-02 12:12:12We value sovereignty, privacy and security when accessing online content, using several tools to achieve this, like open protocols, open OSes, open software products, Tor and VPNs.
The problem
Talking about our social presence, we can manually build up our follower list (social graph), pick a Nostr client that is respectful of our preferences on what to show and how, but with the standard following mechanism, our main feed is public, so everyone can actually snoop what we are interested in, and what is supposable that we read daily.
The solution
Nostr has a simple solution for this necessity: encrypted lists. Lists are what they appear, a collection of people or interests (but they can also group much other stuff, see NIP-51). So we can create lists with contacts that we don't have in our main social graph; these lists can be used primarily to create dedicated feeds, but they could have other uses, for example, related to monitoring. The interesting thing about lists is that they can also be encrypted, so unlike the basic following list, which is always public, we can hide the lists' content from others. The implications are obvious: we can not only have a more organized way to browse content, but it is also really private one.
One might wonder what use can really be made of private lists; here are some examples:
- Browse “can't miss” content from users I consider a priority;
- Supervise competitors or adversarial parts;
- Monitor sensible topics (tags);
- Following someone without being publicly associated with them, as this may be undesirable;
The benefits in terms of privacy as usual are not only related to the casual, or programmatic, observer, but are also evident when we think of how many bots scan our actions to profile us.
The current state
Unfortunately, lists are not widely supported by Nostr clients, and encrypted support is a rarity. Often the excuse to not implement them is that they are harder to develop, since they require managing the encryption stuff (NIP-44). Nevertheless, developers have an easier option to start offering private lists: give the user the possibility to simply mark them as local-only, and never push them to the relays. Even if the user misses the sync feature, this is sufficient to create a private environment.
To date, as far as I know, the best client with list management is Gossip, which permits to manage both encrypted and local-only lists.
Beg your Nostr client to implement private lists!
-
 @ d560dbc2:bbd59238
2025-04-02 11:31:44
@ d560dbc2:bbd59238
2025-04-02 11:31:44April 2, 2025
Let’s be real: to-do lists are supposed to make life easier, but more often than not, they just stress us out. You write down everything you need to do—work tasks, personal errands, that call you’ve been meaning to make—and suddenly, your list is a mile long. Instead of feeling in control, you’re overwhelmed, staring at a jumble of tasks with no clear sense of where to start. So, why do most to-do lists increase stress, and how can we fix it? The answer lies in timing.
The Stress Trap of Traditional To-Do Lists
Most to-do lists fail because they simply dump every task you need to do without any sense of priority or timing. Imagine having:
- “Finish project report” next to “Call Mom” next to “Fix car issue”
Without guidance on when to tackle each task, your brain is left to endlessly loop through all the items—worrying that you’ll forget something or miss a deadline. This is partly due to the Zeigarnik Effect, a psychological phenomenon where unfinished tasks linger in your mind and create tension until they’re completed.
When your list is a chaotic mix of urgent and non-urgent tasks, that tension turns into stress. You either freeze up or end up procrastinating. Plus, seeing tasks you can’t act on yet—like an evening errand when it’s only 9 AM—makes your list feel unmanageable, which kills motivation.
Timing: The Game-Changer for Stress-Free Productivity
What if your to-do list didn’t just tell you what to do, but also when to do it? By assigning each task a specific time window based on its urgency, you can focus on what’s relevant right now and let the rest wait their turn. This approach:
- Reduces mental clutter: You see only the tasks you need to work on immediately.
- Eases stress: Fewer irrelevant tasks mean less overwhelm.
- Provides a clear path forward: You know exactly what to do next, making your day more manageable and progress more satisfying.
How Task4Us Uses Timing to Reduce Stress
At Task4Us, we’ve built our platform around the idea of timing with our 2-5 concept. Here’s how it works:
- Assign Time Units:
Every task gets a time unit—days, weeks, or months—based on its urgency. -
Example: “Submit a project draft” might be set as a daily task, while “catch up with friends” might be a weekly task.
-
Act Within a 2-5 Window:
The 2-5 Rule ensures you act on a task within 2 to 5 of its time units. This rhythm ensures you’re working on tasks at the optimal moment—neither too early nor too late. -
Fix Mode for Date-Specific Tasks:
For tasks with a fixed due date (like birthdays or deadlines), Fix Mode ensures the task climbs your list as the date approaches, becoming your top task on the day. -
Mobile Optimization:
With our recent mobile updates, you can manage your tasks on the go, even on small screens, with a clean, easy-to-use design.
Take Control of Your To-Do List
By shifting the focus from merely listing tasks to timing them correctly, you can break the cycle of overwhelm and procrastination. Instead of a never-ending list of tasks, you’re guided to work on the right task at the right time—and that makes all the difference.
Now, tell me—what’s one task you’ve been postponing for no reason? Share your story in the comments and let’s motivate each other to get it done!
-
 @ 04cb16e4:2ec3e5d5
2025-04-02 10:51:31
@ 04cb16e4:2ec3e5d5
2025-04-02 10:51:31Wenn irgendein weltpolitisches Thema auf den Tisch kommt, wird zumeist erst einmal gefragt, ob du dafür oder dagegen bist und auf welcher Seite du dich befindest. Das macht es einfacher, dich als Freund oder Feind einzusortieren. So wird das Leben übersichtlicher und man muss nicht in die Tiefe gehen und sich mit lästigen Details auseinandersetzen. Man muss auch nicht verreisen um sich ein Bild zu machen. Dafür gibt es ja die Tagesschau. Klassisches Beispiel: Ich war vor Kurzem mit einigen Freunden essen. Einer berichtete entsetzt: „Der Putin hat die Heimatstadt von Selenski angegriffen!“
Ich versuchte mir das bildlich vorzustellen und kam zu dem Schluss, das „der Putin“ wahrscheinlich Verstärkung dabei hatte. Und ausgerechnet nachdem Trump und dessen Flügelmann Vance den armen Wolodymyr rund gemacht hatten, greift der böse Imperator dessen Heimatstadt an. Das ist fies! Das macht „der Putin“ wahrscheinlich immer so, wenn er jemandem eins auswischen will. Die Heimatstadt angreifen! Ganz gleich, ob es strategisch gerade Sinn macht oder nicht. "Der Putin" ist halt ein Teufel.
Radio Berliner Morgenröte auf X
Ich denke viele gucken einfach zu viele qualitativ minderwertige Spielfilme und können Fiktion und Realität nicht mehr voneinander unterscheiden. Möglicherweise meinen sie auch, weil sie die Handlung eines Kriegsfilmes gerafft haben, verstehen sie einen Krieg.
https://www.eisbrenner.de/produkt-kategorie/buch/
Mein Gesprächspartner Tino Eisbrenner hat keine Sightseeing Tour durch Moskau gemacht, sondern ist in Land und Leute regelrecht eingetaucht. Außerdem kommt seine Schwiegermutter aus Russland. Da ist man dem ganzen auch menschlich viel näher und bekommt man ganz andere Einblicke als die, die einem von der Tagesschau gewährt werden. Tino ist als Friedensmusiker viel im Osten unterwegs, unter anderem auch in Georgien, Weißrussland und auf der Krim. Er spricht mit Politikern, Künstlern, Journalisten, Taxifahrern und Dissidenten. Und viele fragen ihn: „Was ist eigentlich mit den Deutschen los?“ Gute Frage! Was ist eigentlich mit uns los? Wir senden unsere Volksvertreter in die Welt hinaus, damit sie Staatsoberhäuptern aus Ländern - die um ein Vielfaches umfangreicher an Fläche und Einwohnerzahl sind und eine komplett andere Kulturgeschichte haben - damit sie denen erklären können wie man seinen Job macht. Wahrscheinlich in dem irrwitzigen Glauben, dass sie selbst ihren Job tadellos und vorbildlich ausführen.
Spenden nehmen wir entweder mit dem Paypal Button am Ende unserer Webseite https://radio-berliner-morgenroete.de/ oder per Überweisung aufs Bankkonto: DE93 1001 1001 2624 3740 74 entgegen.
Wir sind aber nicht nur verantwortlich für unsere politische Führung, sondern auch für unseren Umgang miteinander. Denn im „Großen“ gilt dasselbe wie im „Kleinen“! Man sollte erst mal bei sich selbst schauen wo es hakt und dann miteinander ins Gespräch gehen. Der Mangel an Realitätssinn und Konfliktfähigkeit zieht sich durch alle Schichten unserer Bevölkerung. Deswegen sagt Radio Berliner Morgenröte: „Wenn ihr Frieden wollt, fangt in Deutschland an und wenn ihr euch eine Meinung über Russland oder China bilden wollt, dann fahrt einfach mal dorthin und redet mit den Leuten, So wie Tino. Mir hat es riesig Spaß gemacht, ihm zuzuhören.
Weiterer Buchtipp – Ausgegendert
https://mcdn.podbean.com/mf/web/e5qbg23gz6mru9zz/Tino_Eisbrenner9tbpx.mp3
-
 @ d04ecf33:1d62aa90
2025-04-02 09:48:16
@ d04ecf33:1d62aa90
2025-04-02 09:48:16Physical prototyping
3D printers have evolved as useful tools for rapid prototyping of physical products for inspiration and demonstration purposes.
Nowadays people also use them for hobbyist endeavors. They create nice little items for pure enjoyment or very simple substitution parts that can be used regardless of industrial precision and material limitations.
Prototypers of Ideas
Similarly with LLMs, you can bounce ideas off them to better understand your own thinking and also let them generate variations of ideas. They provide inspiration, summaries, and proof-of-concept boilerplates. They are rapid prototypers for and of your ideas, creating a feedback loop.
However, to use LLMs successfully, people must understand that LLMs cannot and will never discover key insights. They are not creative in a human sense, just like 3D printers cannot produce a real car.
From engineering to art and business ideas, people use tools for almost all phases. The key innovation of LLMs is that they offer an effective tool to iterate faster in the ideation phase.
And yes, that's true of coding too. The code that LLMs generate is not production-ready, but it is a good starting point. Beware of using the prototype as the final product, as it will inevitably backfire. Use LLMs where their high-frequency but low-quality output is justified. Situations where low-quality boilerplate makes sense include experiments and other instances like code snippets, text summaries, sketches, demo videos, mockups, etc.
So, take your key idea and start the conversation. Apply critical thinking to identify where the answers lack important aspects and make mistakes, but most importantly, learn how to formulate your questions better.
Economic Impact
3D printers lower the barrier to entry in the manufacturing of physical products. LLMs, on the other hand, lower the barrier to generating useful ideas. That is to say, they lower the barrier to produce anything and everything because ideas are the basis of any product. This has a deflationary impact and, in my estimation, will further lower the need for mediocre, unimaginative people across the board. It's the bureaucrats' nightmare.
Another impactful aspect of LLMs is that they are very effective learning tools, just like 3D printers. Learning in a feedback loop used to be available only by hiring a human. Now that is one prompt and a few sats away.
Progress
LLMs need "quality data" to improve, i.e., more human insight and true creativity. Therefore, they feed on open-source. Closed-source proprietary information and "intellectual property" slow their progress, but not for long. Humans, overall, yearn for innovation more than they fear censorship and punishment. It's another Pandora's box, and the effects will never be reversed. People are essentially and foremost explainers of the world, creative innovators.
If you ask me, the human touch will be necessary at least until we have true AGI, and the path LLMs are on right now can never achieve that, not in a million years. I agree with David Deutsch's take on this: To produce real AGI, we must first crack serious concepts like how Meaning, Consciousness, Creativity, and Free Will work. We don't know how far we are from that, but it's not to be found along the path of what we call AI today.
If you are striving to become a better version of yourself and learn every day, rest assured: LLMs are your leverage. Otherwise, you will need some fiat authority, like the state today, to force others to value your work while it has an overall negative impact (90% in that category in my estimation). People like that need a shift of perspective or will suffer the consequences.
Keep printing ideas and execute on them! Learn and repeat. The path to success.
llm #ai #agi #3dp #programming
-
 @ db01672e:9f775028
2025-04-02 09:05:06
@ db01672e:9f775028
2025-04-02 09:05:06Proper nutrition plays a huge role in maintaining the health and well-being of seniors, especially those with Alzheimer’s or other forms of dementia. A balanced diet helps boost cognitive function, maintain strength, and prevent complications like dehydration or weight loss.
At leading Alzheimer’s care communities, every meal is carefully planned to support brain health and overall wellness. Let’s take a closer look at why nutrition is so important in https://villagegreenalzheimerscare.com/kingwood/, and how meals are tailored to meet the needs of memory care residents.
The Power of Home-Cooked, Nutritious Meals
For seniors in memory care, food isn’t just about staying full—it’s about fueling the body and mind. A well-balanced diet can improve mood, boost energy, and even slow cognitive decline.
**✔ Fresh, Wholesome Ingredients ** * Meals in assisted living communities are made with fresh vegetables, lean proteins, and whole grains. * Omega-3 fatty acids, antioxidants, and vitamin-rich foods are included to support brain health. * Processed foods and excess sugars are limited to reduce inflammation and maintain stable energy levels.
**✔ Balanced and Consistent Meal Schedules ** * Seniors with dementia thrive on routine, and meal times are scheduled at the same time every day. * Regular eating habits help stabilize blood sugar levels and prevent mood swings. * Meals are prepared to be easily digestible and full of essential nutrients.
**✔ The Comfort of Home-Cooked Meals ** * Many seniors find comfort in familiar flavors and recipes that remind them of home. * Meals are often served in a family-style dining setting, encouraging social interaction. * The warm, inviting atmosphere makes eating enjoyable and stress-free.
Proper nutrition is the foundation of good health and memory care, but hydration and snacks also play a crucial role.
The Importance of Hydration, Snacks, and a Balanced Diet
Dehydration is a common risk for seniors with Alzheimer’s, as they may forget to drink water or fail to recognize thirst cues. Staying hydrated and eating nutrient-rich snacks throughout the day keeps seniors feeling their best.
**✔ Encouraging Proper Hydration ** * Water, herbal teas, and fruit-infused drinks are provided throughout the day. * Hydrating foods like soups, watermelon, and cucumbers help boost water intake. * Caregivers remind and encourage residents to drink fluids regularly.
**✔ Nutritious Snack Options ** Light snacks help maintain energy levels and prevent malnutrition. Yogurt, nuts, smoothies, and whole-grain crackers are offered between meals. Seniors with chewing difficulties can enjoy soft options like applesauce or pudding.
**✔ Creating a Balanced Diet for Dementia Care ** * High-protein meals keep muscles strong and support healing. * Fiber-rich foods improve digestion and prevent constipation. * A mix of healthy fats, carbohydrates, and proteins ensures steady energy throughout the day.
When seniors have difficulty chewing or swallowing, their meals need extra modifications.
Meal Modifications for Swallowing Difficulties and Dietary Restrictions
As dementia progresses, some seniors struggle with chewing and swallowing. Memory care communities adjust meals to ensure safety without sacrificing taste or nutrition.
**✔ Soft and Pureed Meal Options ** * Foods are softened, mashed, or pureed to prevent choking risks. * Thickened liquids help those who have trouble swallowing thin beverages. * Meals still include seasonings and variety to keep them flavorful and appealing.
**✔ Adjusting to Dietary Needs ** * Diabetic-friendly meals are available for residents with blood sugar concerns. * Low-sodium diets help those with heart conditions. * Caregivers monitor food intake to ensure residents are eating enough.
At assisted living in Kingwood, TX, these meal adjustments are made with care and expertise, ensuring every senior receives the nutrition they need.
Nutritious Meals = A Better Quality of Life
A well-balanced diet does more than just keep seniors full—it supports brain function, enhances energy, and improves overall well-being. At https://villagegreenalzheimerscare.com/dallas/ communities, every meal is designed to meet the unique needs of memory care residents.
From hydration reminders to customized meal plans, assisted living communities take the stress out of nutrition for both seniors and their families. If you’re looking for a place where your loved one can enjoy healthy, home-cooked meals in a safe and caring environment, an assisted living community in Kingwood, TX, might be the perfect choice.
-
 @ a60e79e0:1e0e6813
2025-04-02 08:26:48
@ a60e79e0:1e0e6813
2025-04-02 08:26:48This is a long form note of a post that lives on my Nostr educational website Hello Nostr.
So you've got yourself started, you're up to speed with the latest Nostr jargon and you've learned the basics about the protocol, but you're left wanting more!? Well, look no further! This post contains a useful list of Nostr based utilities than can enhance your experience in and around the Nostr protocol.
Search and Discovery
Getting started with Nostr can sometimes feel like a lonely journey, particularly if you're the first of your friends and family to discover how awesome it can be! These tools can help you discover new content, connect with existing follows from other networks and just generally have a poke around at the different types of content Nostr has to offer.
Have a hobby or existing community elsewhere? Have a search for it here to find others with shared interests
- Nostr.Band - Search for people, posts, media and stats literally anything Nostr has to offer!
- Nostr.Directory - Find your Twitter follows on Nostr
- Awesome Nostr - Extensive list of Relay software
- Nostr View - Generic Nostr search
Relays
Relays might not be the sexiest of topics, particularly for newcomers to the network, but they are a crucial part of what makes Nostr great. As you become more competent, you'll want to customize your relay selection and maybe even run your own! Here are some great starting points.
Running a personal relay is a powerful way to improve the redundancy of your Nostr events.
- Nostr.Watch - Browse, test and research Nostr relays
- Nostrwat.ch - List of active Nostr relays
- Advanced Nostr Search - Targetted search with date ranges
- Nostr.Wine - Reliable paid Relay
NIP-05 Identity Services
Your nPub, or public key (that long string of letters and numbers) is your ‘official’ Nostr ID, but it’s not exactly catchy. NIP-05 identifiers are a human-readable and easily shareable way to have people find you on Nostr. They look like an email address, like qna@hellonostr.xyz. If you have your own domain and web server, you can easily create your own NIP-05 identifier in just a few minutes. If you don't, you'll want to leverage one of the many free or paid solutions.
Make yourself easier to find on Nostr with a NIP-05 identifier
- Bitcoiner.Chat - Free service operated by QnA
- Nostr Plebs - Paid service with extra features
- Alby - Lightning wallet with + NIP-05 solution
- Nostr Address - Paid service with extra features
- Zaps.Lol - Free service
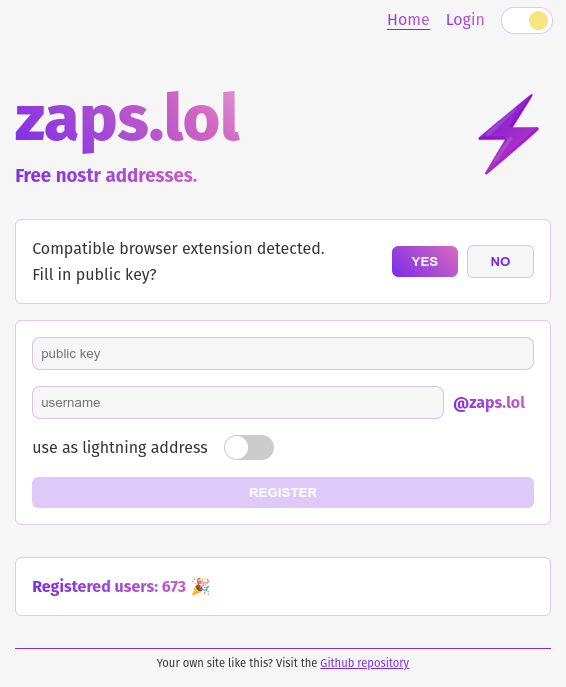
Key Management
Your private key (or nsec) it the key to your Nostr world. It is what allows you to access and interact with your social graph from any client. It doesn't matter if that client is a micro-blogging app like Amethyst, a podcast app like Fountain, or a P2P marketplace like Plebeian Market, your nsec is paramount to those interactions. Should your nsec be lost, or fall into the wrong hands, whoever then holds a copy can access Nostr and pretend to be you, meaning that you'll need to start again with a new keypair. Not a nice situation to find yourself in, so treat your nsec VERY carefully.
Your private key IS your Nostr identity. Treat it with extreme care and do not share it.
- Alby - Browser extension enabling you to sign into web app without sharing the private key
- Nos2x - Another browser extension key manager
- Keys.Band - Another browser extension key manager
- Amber - Android app for safe nsec storage. Can talk to other clients on the same phone to log in and sign events
- Nostr Signing Device - Dedicated device to store your nsec
- Passport - Hardware wallet for offline and deterministic nsec generation and storage
Zap Tools
Zaps are one of the most fun parts of Nostr. Never before have we been able to send fractions of a penny, instantly to our friends because their meme made us laugh, or their blog post was very insightful. Zaps use Bitcoin’s Lightning Network, a faster and cheaper way to move Bitcoin around. To Zap someone, you need a Lightning wallet linked to your Nostr client. Some clients, like Primal, ship with their own custodial wallet to make getting started a breeze. Most clients also allow more advanced users to connect an existing Lightning Wallet to reduce reliance and trust in the client provider.
- Alby - Browser extension and self-custodial Lightning wallet
- LNBits - A Zap server running on your own Bitcoin node
- BTCPay Server - Another Zap server running on your own Bitcoin node
- Zeus - Zap compatible self-custodial mobile Lightning wallet
- Nostr Wallet Connect - Communication protocol between Lightning wallets and Nostr apps
- Ecash Wallets - Custodial Ecash based wallets that are interoperable with Lightning and Nostr (Funds may be at risk)
- Wallet of Satoshi - Custodial Lightning wallet (Funds may be at risk)
If you found this post useful, please share it with your peers and consider following and zapping me on Nostr. If you write to me and let me know that you found me via this post, I'll be sure to Zap you back! ⚡️
-
 @ 7d33ba57:1b82db35
2025-04-02 08:15:08
@ 7d33ba57:1b82db35
2025-04-02 08:15:08Supetar is the main town and ferry port on Brač Island, located just across the sea from Split. It’s a charming coastal town with historic streets, beautiful beaches, and a relaxed island vibe. As the main entry point to Brač, it’s the perfect base for exploring the island’s stunning beaches, olive groves, and cultural landmarks.
🏛️ Top Things to See & Do in Supetar
1️⃣ Explore the Supetar Old Town 🏡
- Stroll through narrow, stone-paved alleys, lined with historic buildings and seaside cafés.
- Visit St. Peter’s Church & Mausoleum, featuring intricate stone carvings.
- Admire the harbor filled with fishing boats, offering postcard-worthy views.
2️⃣ Relax on Supetar’s Beaches 🏖️
- Banj Beach – A family-friendly beach with crystal-clear water & soft pebbles.
- Acapulco Beach – A more secluded, rocky beach with turquoise waters.
- Vela Luka Bay – A beautiful bay surrounded by pine forests, perfect for relaxation.
3️⃣ Visit the Olive Oil Museum in Škrip 🫒
- Just 15 minutes from Supetar, this museum showcases Brač’s olive oil heritage.
- Try traditional Dalmatian olive oil tastings & local island delicacies.
4️⃣ Take a Boat Trip to the Famous Zlatni Rat Beach ⛵
- One of Croatia’s most iconic beaches, known for its shifting horn-shaped coastline.
- Located in Bol, just a short boat or car ride away from Supetar.
5️⃣ Hike or Drive to Vidova Gora 🌄
- The highest peak on the Adriatic islands (778m), offering breathtaking views over Brač, Hvar, and beyond.
- Accessible by hiking (moderate difficulty) or driving.
6️⃣ Try Dalmatian Cuisine 🍽️
- Vitalac – A unique Brač specialty, made from lamb offal and cooked over an open fire.
- Pašticada – A slow-cooked beef dish, traditionally served with gnocchi.
- Homemade Brač cheese & wine – Try local goat cheese paired with Plavac Mali wine.
🚗 How to Get to Supetar
⛴️ By Ferry (from Split):
- The Split-Supetar ferry is the main connection (50 min ride).
- Ferries run frequently (especially in summer).
🚘 By Car:
- Supetar is the best entry point for road trips across Brač.
- Car rentals are available in town or at the ferry port.💡 Tips for Visiting Supetar
✅ Best time to visit? May–September for warm weather & clear seas ☀️
✅ Stay at least a night – Supetar has a lovely evening atmosphere 🌙
✅ Rent a scooter or car to explore Brač’s hidden beaches & inland villages 🏍️
✅ Try local wines & olive oils – Brač is famous for both 🍷🫒
✅ Visit early in the morning for a peaceful experience before ferries get busy ⏳ -
 @ da0b9bc3:4e30a4a9
2025-04-02 05:35:30
@ da0b9bc3:4e30a4a9
2025-04-02 05:35:30Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/931908
-
 @ 7da115b6:7d3e46ae
2025-04-02 00:09:46
@ 7da115b6:7d3e46ae
2025-04-02 00:09:46The Rise of the Entitled Customer
A significant contributor to the feeling of being undervalued is the rise of the “entitled” customer. Driven by a combination of factors – readily available online shopping, social media showcasing perfect purchases, and a general sense of consumerism – customers often approach retail interactions with a sense of expectation that goes far beyond simply buying a product.
Consider, for example, the increasingly common scenario of a customer returning an item – often without a receipt, without a box, and sometimes only a few days after purchase – demanding a full refund, citing a minor imperfection or simply because they found a “better deal.” A 2023 study by the National Retail Federation found that 13.7% of all retail sales in the US are Fraudulent or Abusive claims. The expectation of a return is frequently backed by a willingness to complain loudly in person and on social media. This creates a pressure point for employees.
Furthermore, the influence of online reviews has amplified this sense of entitlement. A single negative review, based on a minor inconvenience or a slightly longer-than-expected checkout line, can significantly impact a retailer's reputation and, consequently, the employee’s job security. Employees are now judged not just on the quality of their service, but on their ability to handle a constant stream of customer complaints, often delivered with little patience.
Employers: Demands Without Recognition
The pressure isn’t solely coming from the customer side. Employers, driven by profit margins and often influenced by trends in fast-fashion and rapid turnover, have become notoriously demanding. Many retailers operate on tight budgets, leading to lower wages, fewer benefits, and a constant need for employees to “go above and beyond.”
The decreasing value of the Dollar has meant that most front line workers are earning only around 70% of their counterparts paychecks from as little as a decade ago. The Dollar figure increases, but the buying power decreases dramatically. The cost of living has increased almost 22%; inflation has also increased by 16%, both in the last 3 years alone.
For instance, a recent report by Forbes highlighted that many retail workers earn minimum wage or slightly above, despite often working evenings, weekends, and holidays. This is particularly challenging in areas with a higher cost of living. Moreover, the expectation of multitasking – assisting customers, stocking shelves, operating the cash register, and handling inventory – is frequently placed on a single employee, leading to burnout and decreased morale.
The pressure to meet sales targets is another key factor. Employees are often evaluated not just on the number of transactions they process, but on their ability to upsell and cross-sell products.
Finally, the rapid pace of change in the retail industry – new technologies, shifting consumer preferences, and frequent store remodels – means that employees are constantly required to learn new skills and adapt to new procedures. This constant learning curve, coupled with the demands of customers and employers, can be exhausting.
The Result: A Systemically Unfair Equation
The combination of entitled customers, demanding employers, and a lack of recognition for the hard work of retail employees creates a systemically unfair equation. Employees are often expected to absorb the brunt of customer dissatisfaction, handle a constant stream of demands, and adapt to ever-changing conditions, all while earning relatively low wages and receiving limited benefits.
To shift this dynamic, retailers need to invest in their employees – offering competitive wages, comprehensive benefits, and opportunities for advancement. Customers, too, can play a role by remembering that retail employees are people, not just service providers, and treating them with respect and understanding.
It is disappointing that the greed for ever higher profits trumps the need for realistic living wages, and personal well-being of those front line workers affected.
-
 @ 9967f375:04f9a5e1
2025-04-01 20:43:54
@ 9967f375:04f9a5e1
2025-04-01 20:43:54El día 1, emprendió su tornaviaje con gran felicidad de este Puerto, para las Islas Filipinas, el Galeón Sacra Familia, que (por muerte del General Don Juan Antonio Cortés de Arredondo, Castillo, y Noblezia, a cuyo cargo vino) va a el de Don Jerónimo Montero.
-
 @ 7d33ba57:1b82db35
2025-04-01 20:35:16
@ 7d33ba57:1b82db35
2025-04-01 20:35:16Stari Grad, located on the northern coast of Hvar Island**, is one of the oldest towns in Europe, dating back to 384 BC. Unlike the party vibe of Hvar Town, Stari Grad offers a peaceful, authentic Dalmatian atmosphere with stone-paved streets, historic sites, and stunning coastal views. It’s also home to the UNESCO-listed Stari Grad Plain, an ancient agricultural landscape.
🏛️ Top Things to See & Do in Stari Grad
1️⃣ Stroll the Stari Grad Old Town 🏡
- Walk through charming stone alleys filled with colorful shutters, old churches, and hidden courtyards.
- Visit Tvrdalj Castle, the summer residence of the poet Petar Hektorović, with a serene fish pond inside.
- Enjoy the relaxed, authentic Dalmatian vibe, away from crowds.
2️⃣ Visit the UNESCO-Listed Stari Grad Plain 🌿
- One of the best-preserved ancient Greek agricultural sites in the world (since 384 BC).
- Walk or cycle through the vineyards, olive groves, and stone walls, still in use today.
- Great for wine tasting – local wines like Bogdanuša and Plavac Mali are a must-try! 🍷
3️⃣ Relax at Stari Grad’s Best Beaches 🏖️
- Lanterna Beach – A mix of pebbles and concrete platforms, with crystal-clear waters.
- Maslinica Bay – A quiet, pine-fringed beach perfect for a peaceful swim.
- Zlatni Rat (Golden Horn Beach) – One of Croatia’s most famous beaches, a short ferry ride away.
4️⃣ Take a Boat Trip to the Pakleni Islands ⛵
- A group of stunning, unspoiled islands with hidden beaches and lagoons.
- Perfect for snorkeling, kayaking, and island-hopping adventures.
5️⃣ Try Local Dalmatian Cuisine 🍽️
- Gregada – A traditional fish stew with potatoes and olive oil.
- Octopus salad – Freshly caught and marinated in lemon & olive oil.
- Hvar wines – Visit local wineries for Bogdanuša, Pošip, and Plavac Mali tastings.
6️⃣ Visit the Dominican Monastery ⛪
- A peaceful monastery with an impressive collection of paintings and relics.
- Features a painting by the famous Venetian artist Tintoretto.
🚗 How to Get to Stari Grad
⛴️ By Ferry:
- From Split: Direct car ferries to Stari Grad (2 hours).
- From Hvar Town: 25-minute bus or taxi ride.
✈️ By Air: The nearest airport is Split Airport (SPU), with ferry connections to Hvar.
🚘 By Car: If bringing a car, take the Split–Stari Grad car ferry (book in advance in summer).💡 Tips for Visiting Stari Grad
✅ Best time to visit? May–September for great weather & fewer crowds ☀️
✅ Stay overnight – Stari Grad is much quieter and more authentic than Hvar Town 🌙
✅ Rent a bike – The best way to explore Stari Grad Plain & surrounding beaches 🚲
✅ Bring water shoes – Many beaches are rocky, but the water is incredibly clear 🩴
✅ Try a sunset walk along the promenade – It’s breathtaking! 🌅