-

@ 39cc53c9:27168656
2025-04-08 07:31:34
> [Read the original blog post](https://blog.kycnot.me/p/kyc-no-thanks)
Know Your Customer is a regulation that requires companies of all sizes to verify the identity, suitability, and risks involved with maintaining a business relationship with a customer. Such procedures fit within the broader scope of anti-money laundering (AML) and counterterrorism financing (CTF) regulations.
Banks, exchanges, online business, mail providers, domain registrars... Everyone wants to know who you are before you can even opt for their service. Your personal information is flowing around the internet in the hands of "god-knows-who" and secured by "trust-me-bro military-grade encryption". Once your account is linked to your personal (and verified) identity, tracking you is just as easy as keeping logs on all these platforms.
## Rights for Illusions
KYC processes aim to combat terrorist financing, money laundering, and other illicit activities. On the surface, KYC seems like a commendable initiative. I mean, who wouldn't want to halt terrorists and criminals in their tracks?
The logic behind KYC is: "If we mandate every financial service provider to identify their users, it becomes easier to pinpoint and apprehend the malicious actors."
However, terrorists and criminals are not precisely lining up to be identified. They're crafty. They may adopt false identities or find alternative strategies to continue their operations. Far from being outwitted, many times they're several steps ahead of regulations. Realistically, KYC might deter a small fraction – let's say about 1% [^1] – of these malefactors. Yet, the cost? All of us are saddled with the inconvenient process of identification just to use a service.
Under the rhetoric of "ensuring our safety", governments and institutions enact regulations that seem more out of a dystopian novel, gradually taking away our right to privacy.
To illustrate, consider a city where the mayor has rolled out facial recognition cameras in every nook and cranny. A band of criminals, intent on robbing a local store, rolls in with a stolen car, their faces obscured by masks and their bodies cloaked in all-black clothes. Once they've committed the crime and exited the city's boundaries, they switch vehicles and clothes out of the cameras' watchful eyes. The high-tech surveillance? It didn’t manage to identify or trace them. Yet, for every law-abiding citizen who merely wants to drive through the city or do some shopping, their movements and identities are constantly logged. The irony? This invasive tracking impacts all of us, just to catch the 1% [^1] of less-than-careful criminals.
## KYC? Not you.
> KYC creates barriers to participation in normal economic activity, to supposedly stop criminals. [^2]
KYC puts barriers between many users and businesses. One of these comes from the fact that the process often requires multiple forms of identification, proof of address, and sometimes even financial records. For individuals in areas with poor record-keeping, non-recognized legal documents, or those who are unbanked, homeless or transient, obtaining these documents can be challenging, if not impossible.
For people who are not skilled with technology or just don't have access to it, there's also a barrier since KYC procedures are mostly online, leaving them inadvertently excluded.
Another barrier goes for the casual or one-time user, where they might not see the value in undergoing a rigorous KYC process, and these requirements can deter them from using the service altogether.
It also wipes some businesses out of the equation, since for smaller businesses, the costs associated with complying with KYC norms—from the actual process of gathering and submitting documents to potential delays in operations—can be prohibitive in economical and/or technical terms.
## You're not welcome
Imagine a swanky new club in town with a strict "members only" sign. You hear the music, you see the lights, and you want in. You step up, ready to join, but suddenly there's a long list of criteria you must meet. After some time, you are finally checking all the boxes. But then the club rejects your membership with no clear reason why. You just weren't accepted. Frustrating, right?
This club scenario isn't too different from the fact that KYC is being used by many businesses as a convenient gatekeeping tool. A perfect excuse based on a "legal" procedure they are obliged to.
Even some exchanges may randomly use this to freeze and block funds from users, claiming these were "flagged" by a cryptic system that inspects the transactions. You are left hostage to their arbitrary decision to let you successfully pass the KYC procedure. If you choose to sidestep their invasive process, they might just hold onto your funds indefinitely.
## Your identity has been stolen
KYC data has been found to be for sale on many dark net markets[^3]. Exchanges may have leaks or hacks, and such leaks contain **very** sensitive data. We're talking about the full monty: passport or ID scans, proof of address, and even those awkward selfies where you're holding up your ID next to your face. All this data is being left to the mercy of the (mostly) "trust-me-bro" security systems of such companies. Quite scary, isn't it?
As cheap as $10 for 100 documents, with discounts applying for those who buy in bulk, the personal identities of innocent users who passed KYC procedures are for sale. [^3]
In short, if you have ever passed the KYC/AML process of a crypto exchange, your privacy is at risk of being compromised, or it might even have already been compromised.
## (they) Know Your Coins
You may already know that **Bitcoin and most cryptocurrencies have a transparent public blockchain**, meaning that all data is shown unencrypted for everyone to see and recorded **forever**. If you link an address you own to your identity through KYC, for example, by sending an amount from a KYC exchange to it, your Bitcoin is no longer pseudonymous and can then be traced.
If, for instance, you send Bitcoin from such an identified address to another KYC'ed address (say, from a friend), everyone having access to that address-identity link information (exchanges, governments, hackers, etc.) will be able to associate that transaction and know who you are transacting with.
## Conclusions
To sum up, **KYC does not protect individuals**; rather, it's a threat to our privacy, freedom, security and integrity. Sensible information flowing through the internet is thrown into chaos by dubious security measures. It puts borders between many potential customers and businesses, and it helps governments and companies track innocent users. That's the chaos KYC has stirred.
The criminals are using stolen identities from companies that gathered them thanks to these very same regulations that were supposed to combat them. Criminals always know how to circumvent such regulations. In the end, normal people are the most affected by these policies.
The threat that KYC poses to individuals in terms of privacy, security and freedom is not to be neglected. And if we don’t start challenging these systems and questioning their efficacy, we are just one step closer to the dystopian future that is now foreseeable.
> Edited 20/03/2024
> * Add reference to the 1% statement on [Rights for Illusions](#rights-for-illusions) section to an article where Chainalysis found that only 0.34% of the transaction volume with cryptocurrencies in 2023 was attributable to criminal activity [^1]
[^1]: https://www.chainalysis.com/blog/2024-crypto-crime-report-introduction/
[^2]: https://old.reddit.com/r/BitcoinBeginners/comments/k2bve1/is_kyc_bad_if_so_why/gdtc8kz
[^3]: https://www.ccn.com/hacked-customer-data-from-world-leading-cryptocurrency-exchanges-for-sale-on-the-dark-web/
-

@ 68c90cf3:99458f5c
2025-04-04 16:06:10
I have two Nostr profiles I use for different subject matter, and I wanted a way to manage and track zaps for each. Using Alby Hub I created two isolated Lightning wallets each associated with one of the profile’s nsecs.
YakiHonne made it easy to connect the associated wallets with the profiles. The user interface is well designed to show balances for each.
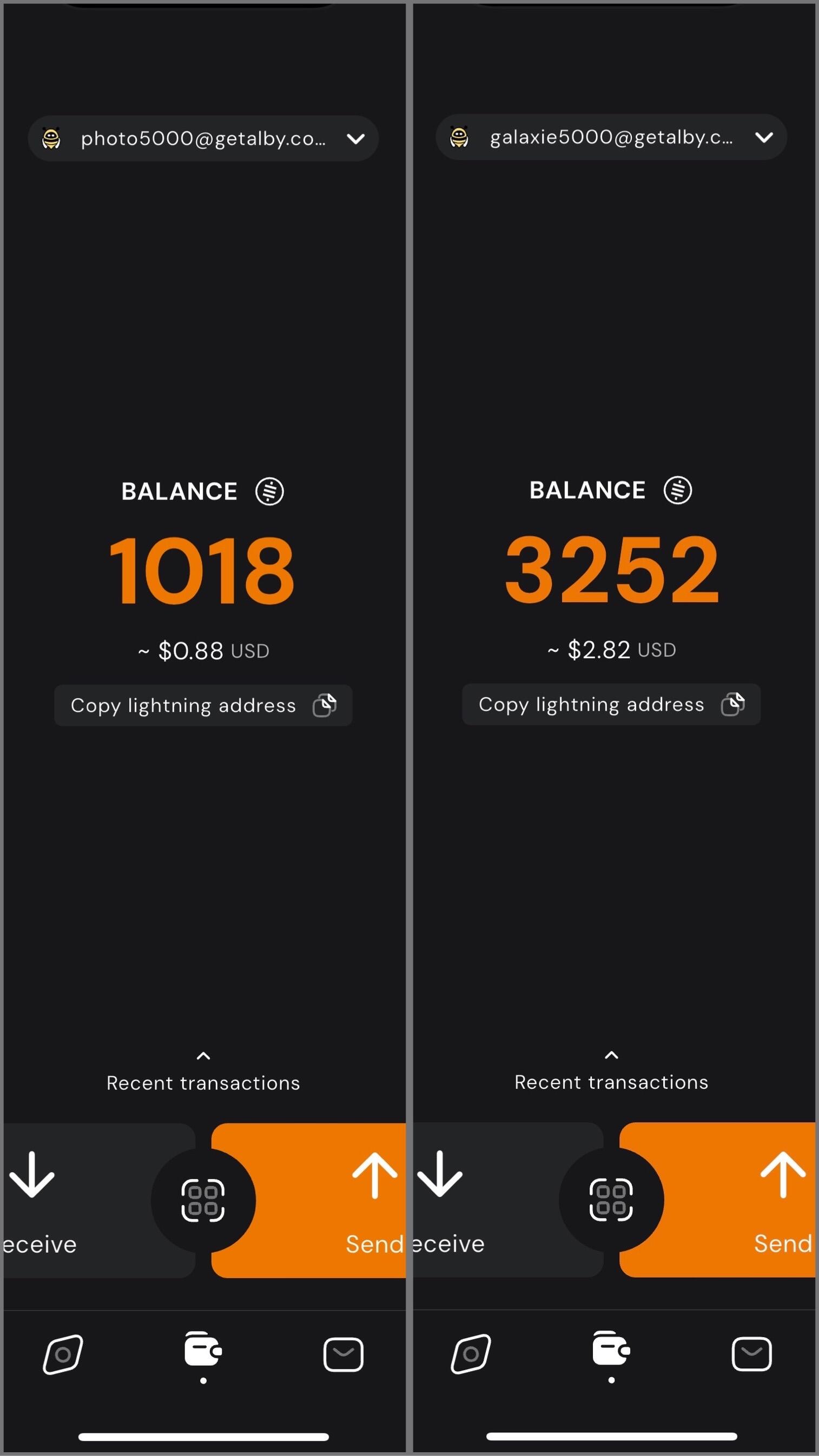
In my case, I have one profile for photography related content, and the other for Bitcoin, Nostr, and technology related content. I can easily switch between the two, sending and receiving zaps on each while staying up to date on balances and viewing transactions.
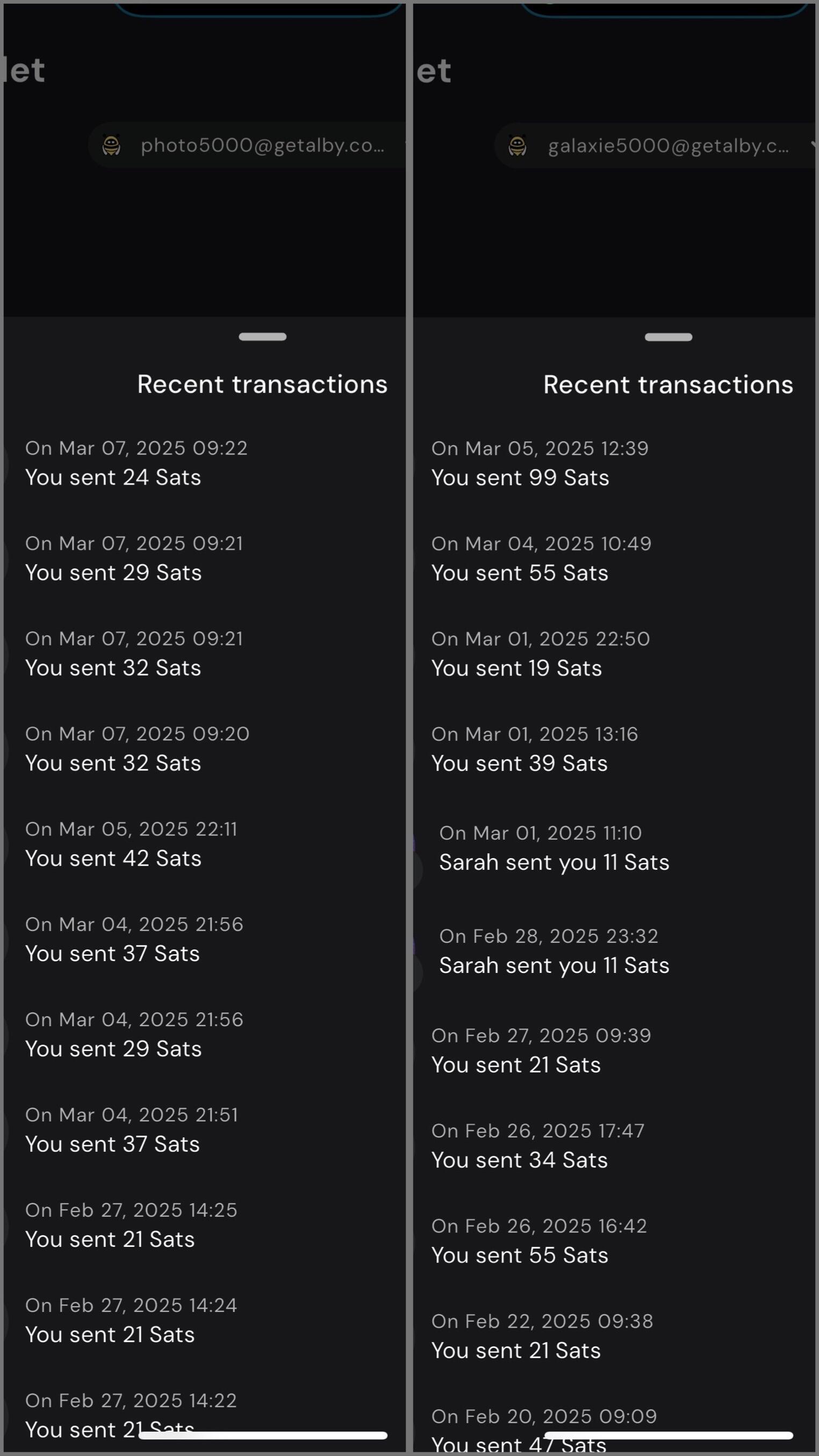
Using my self-hosted Alby Hub I can manage Lightning channels and wallets while sending and receiving zaps for multiple profiles with YakiHonne.
#YakiHonne #AlbyHub #Lightning #Bitcoin #Nostr
-

@ b9f4c34d:7d1a0e31
2025-04-02 15:00:20
<h2> Test Video Document </h2>
-

@ b9f4c34d:7d1a0e31
2025-04-02 14:59:02
<h1> Testy McTestenface </h1>
<p> It's been so long, html </p>
-

@ 04c915da:3dfbecc9
2025-03-26 20:54:33
Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all.
That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission.
As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently.
Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive.
Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally.
The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match.
When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol.
Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
-

@ b2d670de:907f9d4a
2025-03-25 20:17:57
This guide will walk you through setting up your own Strfry Nostr relay on a Debian/Ubuntu server and making it accessible exclusively as a TOR hidden service. By the end, you'll have a privacy-focused relay that operates entirely within the TOR network, enhancing both your privacy and that of your users.
## Table of Contents
1. Prerequisites
2. Initial Server Setup
3. Installing Strfry Nostr Relay
4. Configuring Your Relay
5. Setting Up TOR
6. Making Your Relay Available on TOR
7. Testing Your Setup]
8. Maintenance and Security
9. Troubleshooting
## Prerequisites
- A Debian or Ubuntu server
- Basic familiarity with command line operations (most steps are explained in detail)
- Root or sudo access to your server
## Initial Server Setup
First, let's make sure your server is properly set up and secured.
### Update Your System
Connect to your server via SSH and update your system:
```bash
sudo apt update
sudo apt upgrade -y
```
### Set Up a Basic Firewall
Install and configure a basic firewall:
```bash
sudo apt install ufw -y
sudo ufw allow ssh
sudo ufw enable
```
This allows SSH connections while blocking other ports for security.
## Installing Strfry Nostr Relay
This guide includes the full range of steps needed to build and set up Strfry. It's simply based on the current version of the `DEPLOYMENT.md` document in the Strfry GitHub repository. If the build/setup process is changed in the repo, this document could get outdated. If so, please report to me that something is outdated and check for updated steps [here](https://github.com/hoytech/strfry/blob/master/docs/DEPLOYMENT.md).
### Install Dependencies
First, let's install the necessary dependencies. Each package serves a specific purpose in building and running Strfry:
```bash
sudo apt install -y git build-essential libyaml-perl libtemplate-perl libregexp-grammars-perl libssl-dev zlib1g-dev liblmdb-dev libflatbuffers-dev libsecp256k1-dev libzstd-dev
```
Here's why each dependency is needed:
**Basic Development Tools:**
- `git`: Version control system used to clone the Strfry repository and manage code updates
- `build-essential`: Meta-package that includes compilers (gcc, g++), make, and other essential build tools
**Perl Dependencies** (used for Strfry's build scripts):
- `libyaml-perl`: Perl interface to parse YAML configuration files
- `libtemplate-perl`: Template processing system used during the build process
- `libregexp-grammars-perl`: Advanced regular expression handling for Perl scripts
**Core Libraries for Strfry:**
- `libssl-dev`: Development files for OpenSSL, used for secure connections and cryptographic operations
- `zlib1g-dev`: Compression library that Strfry uses to reduce data size
- `liblmdb-dev`: Lightning Memory-Mapped Database library, which Strfry uses for its high-performance database backend
- `libflatbuffers-dev`: Memory-efficient serialization library for structured data
- `libsecp256k1-dev`: Optimized C library for EC operations on curve secp256k1, essential for Nostr's cryptographic signatures
- `libzstd-dev`: Fast real-time compression algorithm for efficient data storage and transmission
### Clone and Build Strfry
Clone the Strfry repository:
```bash
git clone https://github.com/hoytech/strfry.git
cd strfry
```
Build Strfry:
```bash
git submodule update --init
make setup-golpe
make -j2 # This uses 2 CPU cores. Adjust based on your server (e.g., -j4 for 4 cores)
```
This build process will take several minutes, especially on servers with limited CPU resources, so go get a coffee and post some great memes on nostr in the meantime.
### Install Strfry
Install the Strfry binary to your system path:
```bash
sudo cp strfry /usr/local/bin
```
This makes the `strfry` command available system-wide, allowing it to be executed from any directory and by any user with the appropriate permissions.
## Configuring Your Relay
### Create Strfry User
Create a dedicated user for running Strfry. This enhances security by isolating the relay process:
```bash
sudo useradd -M -s /usr/sbin/nologin strfry
```
The `-M` flag prevents creating a home directory, and `-s /usr/sbin/nologin` prevents anyone from logging in as this user. This is a security best practice for service accounts.
### Create Data Directory
Create a directory for Strfry's data:
```bash
sudo mkdir /var/lib/strfry
sudo chown strfry:strfry /var/lib/strfry
sudo chmod 755 /var/lib/strfry
```
This creates a dedicated directory for Strfry's database and sets the appropriate permissions so that only the strfry user can write to it.
### Configure Strfry
Copy the sample configuration file:
```bash
sudo cp strfry.conf /etc/strfry.conf
```
Edit the configuration file:
```bash
sudo nano /etc/strfry.conf
```
Modify the database path:
```
# Find this line:
db = "./strfry-db/"
# Change it to:
db = "/var/lib/strfry/"
```
Check your system's hard limit for file descriptors:
```bash
ulimit -Hn
```
Update the `nofiles` setting in your configuration to match this value (or set to 0):
```
# Add or modify this line in the config (example if your limit is 524288):
nofiles = 524288
```
The `nofiles` setting determines how many open files Strfry can have simultaneously. Setting it to your system's hard limit (or 0 to use the system default) helps prevent "too many open files" errors if your relay becomes popular.
You might also want to customize your relay's information in the config file. Look for the `info` section and update it with your relay's name, description, and other details.
Set ownership of the configuration file:
```bash
sudo chown strfry:strfry /etc/strfry.conf
```
### Create Systemd Service
Create a systemd service file for managing Strfry:
```bash
sudo nano /etc/systemd/system/strfry.service
```
Add the following content:
```ini
[Unit]
Description=strfry relay service
[Service]
User=strfry
ExecStart=/usr/local/bin/strfry relay
Restart=on-failure
RestartSec=5
ProtectHome=yes
NoNewPrivileges=yes
ProtectSystem=full
LimitCORE=1000000000
[Install]
WantedBy=multi-user.target
```
This systemd service configuration:
- Runs Strfry as the dedicated strfry user
- Automatically restarts the service if it fails
- Implements security measures like `ProtectHome` and `NoNewPrivileges`
- Sets resource limits appropriate for a relay
Enable and start the service:
```bash
sudo systemctl enable strfry.service
sudo systemctl start strfry
```
Check the service status:
```bash
sudo systemctl status strfry
```
### Verify Relay is Running
Test that your relay is running locally:
```bash
curl localhost:7777
```
You should see a message indicating that the Strfry relay is running. This confirms that Strfry is properly installed and configured before we proceed to set up TOR.
## Setting Up TOR
Now let's make your relay accessible as a TOR hidden service.
### Install TOR
Install TOR from the package repositories:
```bash
sudo apt install -y tor
```
This installs the TOR daemon that will create and manage your hidden service.
### Configure TOR
Edit the TOR configuration file:
```bash
sudo nano /etc/tor/torrc
```
Scroll down to wherever you see a commented out part like this:
```
#HiddenServiceDir /var/lib/tor/hidden_service/
#HiddenServicePort 80 127.0.0.1:80
```
Under those lines, add the following lines to set up a hidden service for your relay:
```
HiddenServiceDir /var/lib/tor/strfry-relay/
HiddenServicePort 80 127.0.0.1:7777
```
This configuration:
- Creates a hidden service directory at `/var/lib/tor/strfry-relay/`
- Maps port 80 on your .onion address to port 7777 on your local machine
- Keeps all traffic encrypted within the TOR network
Create the directory for your hidden service:
```bash
sudo mkdir -p /var/lib/tor/strfry-relay/
sudo chown debian-tor:debian-tor /var/lib/tor/strfry-relay/
sudo chmod 700 /var/lib/tor/strfry-relay/
```
The strict permissions (700) are crucial for security as they ensure only the debian-tor user can access the directory containing your hidden service private keys.
Restart TOR to apply changes:
```bash
sudo systemctl restart tor
```
## Making Your Relay Available on TOR
### Get Your Onion Address
After restarting TOR, you can find your onion address:
```bash
sudo cat /var/lib/tor/strfry-relay/hostname
```
This will output something like `abcdefghijklmnopqrstuvwxyz234567.onion`, which is your relay's unique .onion address. This is what you'll share with others to access your relay.
### Understanding Onion Addresses
The .onion address is a special-format hostname that is automatically generated based on your hidden service's private key.
Your users will need to use this address with the WebSocket protocol prefix to connect: `ws://youronionaddress.onion`
## Testing Your Setup
### Test with a Nostr Client
The best way to test your relay is with an actual Nostr client that supports TOR:
1. Open your TOR browser
2. Go to your favorite client, either on clearnet or an onion service.
- Check out [this list](https://github.com/0xtrr/onion-service-nostr-clients?tab=readme-ov-file#onion-service-nostr-clients) of nostr clients available over TOR.
3. Add your relay URL: `ws://youronionaddress.onion` to your relay list
4. Try posting a note and see if it appears on your relay
- In some nostr clients, you can also click on a relay to get information about it like the relay name and description you set earlier in the stryfry config. If you're able to see the correct values for the name and the description, you were able to connect to the relay.
- Some nostr clients also gives you a status on what relays a note was posted to, this could also give you an indication that your relay works as expected.
Note that not all Nostr clients support TOR connections natively. Some may require additional configuration or use of TOR Browser. E.g. most mobile apps would most likely require a TOR proxy app running in the background (some have TOR support built in too).
## Maintenance and Security
### Regular Updates
Keep your system, TOR, and relay updated:
```bash
# Update system
sudo apt update
sudo apt upgrade -y
# Update Strfry
cd ~/strfry
git pull
git submodule update
make -j2
sudo cp strfry /usr/local/bin
sudo systemctl restart strfry
# Verify TOR is still running properly
sudo systemctl status tor
```
Regular updates are crucial for security, especially for TOR which may have security-critical updates.
### Database Management
Strfry has built-in database management tools. Check the Strfry documentation for specific commands related to database maintenance, such as managing event retention and performing backups.
### Monitoring Logs
To monitor your Strfry logs:
```bash
sudo journalctl -u strfry -f
```
To check TOR logs:
```bash
sudo journalctl -u tor -f
```
Monitoring logs helps you identify potential issues and understand how your relay is being used.
### Backup
This is not a best practices guide on how to do backups. Preferably, backups should be stored either offline or on a different machine than your relay server. This is just a simple way on how to do it on the same server.
```bash
# Stop the relay temporarily
sudo systemctl stop strfry
# Backup the database
sudo cp -r /var/lib/strfry /path/to/backup/location
# Restart the relay
sudo systemctl start strfry
```
Back up your TOR hidden service private key. The private key is particularly sensitive as it defines your .onion address - losing it means losing your address permanently. If you do a backup of this, ensure that is stored in a safe place where no one else has access to it.
```bash
sudo cp /var/lib/tor/strfry-relay/hs_ed25519_secret_key /path/to/secure/backup/location
```
## Troubleshooting
### Relay Not Starting
If your relay doesn't start:
```bash
# Check logs
sudo journalctl -u strfry -e
# Verify configuration
cat /etc/strfry.conf
# Check permissions
ls -la /var/lib/strfry
```
Common issues include:
- Incorrect configuration format
- Permission problems with the data directory
- Port already in use (another service using port 7777)
- Issues with setting the nofiles limit (setting it too big)
### TOR Hidden Service Not Working
If your TOR hidden service is not accessible:
```bash
# Check TOR logs
sudo journalctl -u tor -e
# Verify TOR is running
sudo systemctl status tor
# Check onion address
sudo cat /var/lib/tor/strfry-relay/hostname
# Verify TOR configuration
sudo cat /etc/tor/torrc
```
Common TOR issues include:
- Incorrect directory permissions
- TOR service not running
- Incorrect port mapping in torrc
### Testing Connectivity
If you're having trouble connecting to your service:
```bash
# Verify Strfry is listening locally
sudo ss -tulpn | grep 7777
# Check that TOR is properly running
sudo systemctl status tor
# Test the local connection directly
curl --include --no-buffer localhost:7777
```
---
## Privacy and Security Considerations
Running a Nostr relay as a TOR hidden service provides several important privacy benefits:
1. **Network Privacy**: Traffic to your relay is encrypted and routed through the TOR network, making it difficult to determine who is connecting to your relay.
2. **Server Anonymity**: The physical location and IP address of your server are concealed, providing protection against denial-of-service attacks and other targeting.
3. **Censorship Resistance**: TOR hidden services are more resilient against censorship attempts, as they don't rely on the regular DNS system and can't be easily blocked.
4. **User Privacy**: Users connecting to your relay through TOR enjoy enhanced privacy, as their connections are also encrypted and anonymized.
However, there are some important considerations:
- TOR connections are typically slower than regular internet connections
- Not all Nostr clients support TOR connections natively
- Running a hidden service increases the importance of keeping your server secure
---
Congratulations! You now have a Strfry Nostr relay running as a TOR hidden service. This setup provides a resilient, privacy-focused, and censorship-resistant communication channel that helps strengthen the Nostr network.
For further customization and advanced configuration options, refer to the [Strfry documentation](https://github.com/hoytech/strfry).
Consider sharing your relay's .onion address with the Nostr community to help grow the privacy-focused segment of the network!
If you plan on providing a relay service that the public can use (either for free or paid for), consider adding it to [this list](https://github.com/0xtrr/onion-service-nostr-relays). Only add it if you plan to run a stable and available relay.
-

@ bc52210b:20bfc6de
2025-03-25 20:17:22
CISA, or Cross-Input Signature Aggregation, is a technique in Bitcoin that allows multiple signatures from different inputs in a transaction to be combined into a single, aggregated signature. This is a big deal because Bitcoin transactions often involve multiple inputs (e.g., spending from different wallet outputs), each requiring its own signature. Normally, these signatures take up space individually, but CISA compresses them into one, making transactions more efficient.
This magic is possible thanks to the linearity property of Schnorr signatures, a type of digital signature introduced to Bitcoin with the Taproot upgrade. Unlike the older ECDSA signatures, Schnorr signatures have mathematical properties that allow multiple signatures to be added together into a single valid signature. Think of it like combining multiple handwritten signatures into one super-signature that still proves everyone signed off!
Fun Fact: CISA was considered for inclusion in Taproot but was left out to keep the upgrade simple and manageable. Adding CISA would’ve made Taproot more complex, so the developers hit pause on it—for now.
---
**CISA vs. Key Aggregation (MuSig, FROST): Don’t Get Confused!**
Before we go deeper, let’s clear up a common mix-up: CISA is not the same as protocols like MuSig or FROST. Here’s why:
* Signature Aggregation (CISA): Combines multiple signatures into one, each potentially tied to different public keys and messages (e.g., different transaction inputs).
* Key Aggregation (MuSig, FROST): Combines multiple public keys into a single aggregated public key, then generates one signature for that key.
**Key Differences:**
1. What’s Aggregated?
* CISA: Aggregates signatures.
* Key Aggregation: Aggregates public keys.
2. What the Verifier Needs
* CISA: The verifier needs all individual public keys and their corresponding messages to check the aggregated signature.
* Key Aggregation: The verifier only needs the single aggregated public key and one message.
3. When It Happens
* CISA: Used during transaction signing, when inputs are being combined into a transaction.
* MuSig: Used during address creation, setting up a multi-signature (multisig) address that multiple parties control.
So, CISA is about shrinking signature data in a transaction, while MuSig/FROST are about simplifying multisig setups. Different tools, different jobs!
---
**Two Flavors of CISA: Half-Agg and Full-Agg**
CISA comes in two modes:
* Full Aggregation (Full-Agg): Interactive, meaning signers need to collaborate during the signing process. (We’ll skip the details here since the query focuses on Half-Agg.)
* Half Aggregation (Half-Agg): Non-interactive, meaning signers can work independently, and someone else can combine the signatures later.
Since the query includes “CISA Part 2: Half Signature Aggregation,” let’s zoom in on Half-Agg.
---
**Half Signature Aggregation (Half-Agg) Explained**
**How It Works**
Half-Agg is a non-interactive way to aggregate Schnorr signatures. Here’s the process:
1. Independent Signing: Each signer creates their own Schnorr signature for their input, without needing to talk to the other signers.
2. Aggregation Step: An aggregator (could be anyone, like a wallet or node) takes all these signatures and combines them into one aggregated signature.
A Schnorr signature has two parts:
* R: A random point (32 bytes).
* s: A scalar value (32 bytes).
In Half-Agg:
* The R values from each signature are kept separate (one per input).
* The s values from all signatures are combined into a single s value.
**Why It Saves Space (~50%)**
Let’s break down the size savings with some math:
Before Aggregation:
* Each Schnorr signature = 64 bytes (32 for R + 32 for s).
* For n inputs: n × 64 bytes.
After Half-Agg:
* Keep n R values (32 bytes each) = 32 × n bytes.
* Combine all s values into one = 32 bytes.
* Total size: 32 × n + 32 bytes.
Comparison:
* Original: 64n bytes.
* Half-Agg: 32n + 32 bytes.
* For large n, the “+32” becomes small compared to 32n, so it’s roughly 32n, which is half of 64n. Hence, ~50% savings!
**Real-World Impact:**
Based on recent Bitcoin usage, Half-Agg could save:
* ~19.3% in space (reducing transaction size).
* ~6.9% in fees (since fees depend on transaction size). This assumes no major changes in how people use Bitcoin post-CISA.
---
**Applications of Half-Agg**
Half-Agg isn’t just a cool idea—it has practical uses:
1. Transaction-wide Aggregation
* Combine all signatures within a single transaction.
* Result: Smaller transactions, lower fees.
2. Block-wide Aggregation
* Combine signatures across all transactions in a Bitcoin block.
* Result: Even bigger space savings at the blockchain level.
3. Off-chain Protocols / P2P
* Use Half-Agg in systems like Lightning Network gossip messages.
* Benefit: Efficiency without needing miners or a Bitcoin soft fork.
---
**Challenges with Half-Agg**
While Half-Agg sounds awesome, it’s not without hurdles, especially at the block level:
1. Breaking Adaptor Signatures
* Adaptor signatures are special signatures used in protocols like Discreet Log Contracts (DLCs) or atomic swaps. They tie a signature to revealing a secret, ensuring fair exchanges.
* Aggregating signatures across a block might mess up these protocols, as the individual signatures get blended together, potentially losing the properties adaptor signatures rely on.
2. Impact on Reorg Recovery
* In Bitcoin, a reorganization (reorg) happens when the blockchain switches to a different chain of blocks. Transactions from the old chain need to be rebroadcast or reprocessed.
* If signatures are aggregated at the block level, it could complicate extracting individual transactions and their signatures during a reorg, slowing down recovery.
These challenges mean Half-Agg needs careful design, especially for block-wide use.
---
**Wrapping Up**
CISA is a clever way to make Bitcoin transactions more efficient by aggregating multiple Schnorr signatures into one, thanks to their linearity property. Half-Agg, the non-interactive mode, lets signers work independently, cutting signature size by about 50% (to 32n + 32 bytes from 64n bytes). It could save ~19.3% in space and ~6.9% in fees, with uses ranging from single transactions to entire blocks or off-chain systems like Lightning.
But watch out—block-wide Half-Agg could trip up adaptor signatures and reorg recovery, so it’s not a slam dunk yet. Still, it’s a promising tool for a leaner, cheaper Bitcoin future!
-

@ b17fccdf:b7211155
2025-03-25 11:23:36
Si vives en España, quizás hayas notado que no puedes acceder a ciertas páginas webs durante los fines de semana o en algunos días entre semana, entre ellas, la [guía de MiniBolt](https://minbolt.info/).
Esto tiene una **razón**, por supuesto una **solución**, además de una **conclusión**. Sin entrar en demasiados detalles:
## La razón
El **bloqueo a Cloudflare**, implementado desde hace casi dos meses por operadores de Internet (ISPs) en España (como Movistar, O2, DIGI, Pepephone, entre otros), se basa en una [orden judicial](https://www.poderjudicial.es/search/AN/openDocument/3c85bed480cbb1daa0a8778d75e36f0d/20221004) emitida tras una demanda de LALIGA (Fútbol). Esta medida busca combatir la piratería en España, un problema que afecta directamente a dicha organización.
Aunque la intención original era restringir el acceso a dominios específicos que difundieran dicho contenido, Cloudflare emplea el protocolo [ECH](https://developers.cloudflare.com/ssl/edge-certificates/ech) (Encrypted Client Hello), que oculta el nombre del dominio, el cual antes se transmitía en texto plano durante el proceso de establecimiento de una conexión TLS. Esta medida dificulta que las operadoras analicen el tráfico para aplicar **bloqueos basados en dominios**, lo que les obliga a recurrir a **bloqueos más amplios por IP o rangos de IP** para cumplir con la orden judicial.
Esta práctica tiene **consecuencias graves**, que han sido completamente ignoradas por quienes la ejecutan. Es bien sabido que una infraestructura de IP puede alojar numerosos dominios, tanto legítimos como no legítimos. La falta de un "ajuste fino" en los bloqueos provoca un **perjuicio para terceros**, **restringiendo el acceso a muchos dominios legítimos** que no tiene relación alguna con actividades ilícitas, pero que comparten las mismas IPs de Cloudflare con dominios cuestionables. Este es el caso de la [web de MiniBolt](https://minibolt.minibolt.info) y su dominio `minibolt.info`, los cuales **utilizan Cloudflare como proxy** para aprovechar las medidas de **seguridad, privacidad, optimización y servicios** adicionales que la plataforma ofrece de forma gratuita.
Si bien este bloqueo parece ser temporal (al menos durante la temporada 24/25 de fútbol, hasta finales de mayo), es posible que se reactive con el inicio de la nueva temporada.

## La solución
Obviamente, **MiniBolt no dejará de usar Cloudflare** como proxy por esta razón. Por lo que a continuación se exponen algunas medidas que como usuario puedes tomar para **evitar esta restricción** y poder acceder:
**~>** Utiliza **una VPN**:
Existen varias soluciones de proveedores de VPN, ordenadas según su reputación en privacidad:
- [IVPN](https://www.ivpn.net/es/)
- [Mullvad VPN](https://mullvad.net/es/vpn)
- [Proton VPN](https://protonvpn.com/es-es) (**gratis**)
- [Obscura VPN](https://obscura.net/) (**solo para macOS**)
- [Cloudfare WARP](https://developers.cloudflare.com/cloudflare-one/connections/connect-devices/warp/download-warp/) (**gratis**) + permite utilizar el modo proxy local para enrutar solo la navegación, debes utilizar la opción "WARP a través de proxy local" siguiendo estos pasos:
1. Inicia Cloudflare WARP y dentro de la pequeña interfaz haz click en la rueda dentada abajo a la derecha > "Preferencias" > "Avanzado" > "Configurar el modo proxy"
2. Marca la casilla "Habilite el modo proxy en este dispositivo"
3. Elige un "Puerto de escucha de proxy" entre 0-65535. ej: 1080, haz click en "Aceptar" y cierra la ventana de preferencias
4. Accede de nuevo a Cloudflare WARP y pulsa sobre el switch para habilitar el servicio.
3. Ahora debes apuntar el proxy del navegador a Cloudflare WARP, la configuración del navegador es similar a [esta](https://minibolt.minibolt.info/system/system/privacy#example-from-firefox) para el caso de navegadores basados en Firefox. Una vez hecho, deberías poder acceder a la [guía de MiniBolt](https://minibolt.minibolt.info/) sin problemas. Si tienes dudas, déjalas en comentarios e intentaré resolverlas. Más info [AQUÍ](https://bandaancha.eu/articulos/como-saltarse-bloqueo-webs-warp-vpn-9958).

**~>** [**Proxifica tu navegador para usar la red de Tor**](https://minibolt.minibolt.info/system/system/privacy#ssh-remote-access-through-tor), o utiliza el [**navegador oficial de Tor**](https://www.torproject.org/es/download/) (recomendado).

## La conclusión
Estos hechos ponen en tela de juicio los principios fundamentales de la neutralidad de la red, pilares esenciales de la [Declaración de Independencia del Ciberespacio](https://es.wikisource.org/wiki/Declaraci%C3%B3n_de_independencia_del_ciberespacio) que defiende un internet libre, sin restricciones ni censura. Dichos principios se han visto quebrantados sin precedentes en este país, confirmando que ese futuro distópico que muchos negaban, ya es una realidad.
Es momento de actuar y estar preparados: debemos **impulsar el desarrollo y la difusión** de las **herramientas anticensura** que tenemos a nuestro alcance, protegiendo así la **libertad digital** y asegurando un acceso equitativo a la información para todos
Este compromiso es uno de los **pilares fundamentales de MiniBolt,** lo que convierte este desafío en una oportunidad para poner a prueba las **soluciones anticensura** [ya disponibles](https://minibolt.minibolt.info/bonus-guides/system/tor-services), así como **las que están en camino**.
¡Censúrame si puedes, legislador! ¡La lucha por la privacidad y la libertad en Internet ya está en marcha!

---
Fuentes:
* https://bandaancha.eu/articulos/movistar-o2-deja-clientes-sin-acceso-11239
* https://bandaancha.eu/articulos/esta-nueva-sentencia-autoriza-bloqueos-11257
* https://bandaancha.eu/articulos/como-saltarse-bloqueo-webs-warp-vpn-9958
* https://bandaancha.eu/articulos/como-activar-ech-chrome-acceder-webs-10689
* https://comunidad.movistar.es/t5/Soporte-Fibra-y-ADSL/Problema-con-web-que-usan-Cloudflare/td-p/5218007
-

@ 3b7fc823:e194354f
2025-03-23 03:54:16
A quick guide for the less than technical savvy to set up their very own free private tor enabled email using Onionmail. Privacy is for everyone, not just the super cyber nerds.
Onion Mail is an anonymous POP3/SMTP email server program hosted by various people on the internet. You can visit this site and read the details: https://en.onionmail.info/
1. Download Tor Browser
First, if you don't already, go download Tor Browser. You are going to need it. https://www.torproject.org/
2. Sign Up
Using Tor browser go to the directory page (https://onionmail.info/directory.html) choose one of the servers and sign up for an account. I say sign up but it is just choosing a user name you want to go before the @xyz.onion email address and solving a captcha.
3. Account information
Once you are done signing up an Account information page will pop up. **MAKE SURE YOU SAVE THIS!!!** It has your address and passwords (for sending and receiving email) that you will need. If you lose them then you are shit out of luck.
4. Install an Email Client
You can use Claws Mail, Neomutt, or whatever, but for this example, we will be using Thunderbird.
a. Download Thunderbird email client
b. The easy setup popup page that wants your name, email, and password isn't going to like your user@xyz.onion address. Just enter something that looks like a regular email address such as name@example.com and the **Configure Manually**option will appear below. Click that.
5. Configure Incoming (POP3) Server
Under Incoming Server:
Protocol: POP3
Server or Hostname: xyz.onion (whatever your account info says)
Port: 110
Security: STARTTLS
Authentication: Normal password
Username: (your username)
Password: (POP3 password).
6. Configure Outgoing (SMTP) Server
Under Outgoing Server:
Server or Hostname: xyz.onion (whatever your account info says)
Port: 25
Security: STARTTLS
Authentication: Normal password
Username: (your username)
Password: (SMTP password).
7. Click on email at the top and change your address if you had to use a spoof one to get the configure manually to pop up.
8. Configure Proxy
a. Click the **gear icon** on the bottom left for settings. Scroll all the way down to **Network & Disk Space**. Click the **settings button** next to **Connection. Configure how Thunderbird connects to the internet**.
b. Select **Manual Proxy Configuration**. For **SOCKS Host** enter **127.0.0.1** and enter port **9050**. (if you are running this through a VM the port may be different)
c. Now check the box for **SOCKS5** and then **Proxy DNS when using SOCKS5** down at the bottom. Click OK
9. Check Email
For thunderbird to reach the onion mail server it has to be connected to tor. Depending on your local setup, it might be fine as is or you might have to have tor browser open in the background. Click on **inbox** and then the **little cloud icon** with the down arrow to check mail.
10. Security Exception
Thunderbird is not going to like that the onion mail server security certificate is self signed. A popup **Add Security Exception** will appear. Click **Confirm Security Exception**.
You are done. Enjoy your new private email service.
**REMEMBER: The server can read your emails unless they are encrypted. Go into account settings. Look down and click End-toEnd Encryption. Then add your OpenPGP key or open your OpenPGP Key Manager (you might have to download one if you don't already have one) and generate a new key for this account.**
-

@ 21335073:a244b1ad
2025-03-18 20:47:50
**Warning: This piece contains a conversation about difficult topics. Please proceed with caution.**
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book *Cypherpunks*, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
**Course:**
- The creation of the internet and computers
- The fight for cryptography
- The tech supply chain from the ground up (example: human rights violations in the supply chain)
- Corporate tech
- Freedom tech
- Data privacy
- Digital privacy rights
- AI (history-current)
- Online safety (predators, scams, catfishing, extortion)
- Bitcoin
- Laws
- How to deal with online hate and harassment
- Information on who to contact if you are being abused online or offline
- Algorithms
- How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-

@ 57d1a264:69f1fee1
2025-04-08 06:39:52

originally posted at https://stacker.news/items/937791
-

@ c066aac5:6a41a034
2025-04-05 16:58:58
I’m drawn to extremities in art. The louder, the bolder, the more outrageous, the better. Bold art takes me out of the mundane into a whole new world where anything and everything is possible. Having grown up in the safety of the suburban midwest, I was a bit of a rebellious soul in search of the satiation that only came from the consumption of the outrageous. My inclination to find bold art draws me to NOSTR, because I believe NOSTR can be the place where the next generation of artistic pioneers go to express themselves. I also believe that as much as we are able, were should invite them to come create here.
# My Background: A Small Side Story

My father was a professional gamer in the 80s, back when there was no money or glory in the avocation. He did get a bit of spotlight though after the fact: in the mid 2000’s there were a few parties making documentaries about that era of gaming as well as current arcade events (namely 2007’s*Chasing Ghosts*and*The King of Kong: A Fistful of Quarters*). As a result of these documentaries, there was a revival in the arcade gaming scene. My family attended events related to the documentaries or arcade gaming and I became exposed to a lot of things I wouldn’t have been able to find. The producer of*The King of Kong: A Fistful of Quarters* had previously made a documentary called*New York Doll*which was centered around the life of bassist Arthur Kane. My 12 year old mind was blown: The New York Dolls were a glam-punk sensation dressed in drag. The music was from another planet. Johnny Thunders’ guitar playing was like Chuck Berry with more distortion and less filter. Later on I got to meet the Galaga record holder at the time, Phil Day, in Ottumwa Iowa. Phil is an Australian man of high intellect and good taste. He exposed me to great creators such as Nick Cave & The Bad Seeds, Shakespeare, Lou Reed, artists who created things that I had previously found inconceivable.
I believe this time period informed my current tastes and interests, but regrettably I think it also put coals on the fire of rebellion within. I stopped taking my parents and siblings seriously, the Christian faith of my family (which I now hold dearly to) seemed like a mundane sham, and I felt I couldn’t fit in with most people because of my avant-garde tastes. So I write this with the caveat that there should be a way to encourage these tastes in children without letting them walk down the wrong path. There is nothing inherently wrong with bold art, but I’d advise parents to carefully find ways to cultivate their children’s tastes without completely shutting them down and pushing them away as a result. My parents were very loving and patient during this time; I thank God for that.
With that out of the way, lets dive in to some bold artists:
# Nicolas Cage: Actor

There is an excellent video by Wisecrack on Nicolas Cage that explains him better than I will, which I will link[here](https://www.youtube.com/watch?v=s8IfDNHsCLE). Nicolas Cage rejects the idea that good acting is tied to mere realism; all of his larger than life acting decisions are deliberate choices. When that clicked for me, I immediately realized the man is a genius. He borrows from Kabuki and German Expressionism, art forms that rely on exaggeration to get the message across. He has even created his own acting style, which he calls Nouveau Shamanic. He augments his imagination to go from acting to being. Rather than using the old hat of method acting, he transports himself to a new world mentally. The projects he chooses to partake in are based on his own interests or what he considers would be a challenge (making a bad script good for example). Thus it doesn’t matter how the end result comes out; he has already achieved his goal as an artist. Because of this and because certain directors don’t know how to use his talents, he has a noticeable amount of duds in his filmography. Dig around the duds, you’ll find some pure gold. I’d personally recommend the films*Pig,* *Joe,* *Renfield,* and his Christmas film *The Family Man*.
# �Nick Cave: Songwriter

What a wild career this man has had! From the apocalyptic mayhem of his band The Birthday Party to the pensive atmosphere of his album*Ghosteen*, it seems like Nick Cave has tried everything. I think his secret sauce is that he’s always working. He maintains an excellent newsletter called*The Red Hand Files*, he has written screenplays such as*Lawless*, he has written books, he has made great film scores such as*The Assassination of Jesse James by the Coward Robert Ford*, the man is religiously prolific. I believe that one of the reasons he is prolific is that he’s not afraid to experiment. If he has an idea, he follows it through to completion. From the album*Murder Ballads*(which is comprised of what the title suggests) to his rejected sequel to*Gladiator*(*Gladiator: Christ Killer*), he doesn’t seem to be afraid to take anything on. This has led to some over the top works as well as some deeply personal works. Albums like*Skeleton Tree*and*Ghosteen*were journeys through the grief of his son’s death. *The Boatman’s Call*is arguably a better break-up album than anything Taylor Swift has put out. He’s not afraid to be outrageous, he’s not afraid to offend, but most importantly he’s not afraid to be himself. Works I’d recommend include The Birthday Party’s*Live 1981-82*, Nick Cave & The Bad Seeds’*The Boatman’s Call*, and the film*Lawless*.
# �Jim Jarmusch: Director

I consider Jim’s films to be bold almost in an ironic sense: his works are bold in that they are, for the most part, anti-sensational. He has a rule that if his screenplays are criticized for a lack of action, he makes them even less eventful. Even with sensational settings his films feel very close to reality, and they demonstrate the beauty of everyday life. That's what is bold about his art to me: making the sensational grounded in reality while making everyday reality all the more special. *Ghost Dog: The Way of the Samurai* is about a modern-day African-American hitman who strictly follows the rules of the ancient Samurai, yet one can resonate with the humanity of a seemingly absurd character. *Only Lovers Left Alive*is a vampire love story, but in the middle of a vampire romance one can see their their own relationships in a new deeply human light. Jim’s work reminds me that art reflects life, and that there is sacred beauty in seemingly mundane everyday life. I personally recommend his films*Paterson*,*Down by Law*, and*Coffee and Cigarettes*.
# NOSTR: We Need Bold Art

NOSTR is in my opinion a path to a better future. In a world creeping slowly towards everything apps, I hope that the protocol where the individual owns their data wins over everything else. I love freedom and sovereignty. If NOSTR is going to win the race of everything apps, we need more than Bitcoin content. We need more than shirtless bros paying for bananas in foreign countries and exercising with girls who have seductive accents. Common people cannot see themselves in such a world. NOSTR needs to catch the attention of everyday people. I don’t believe that this can be accomplished merely by introducing more broadly relevant content; people are searching for content that speaks to them. I believe that NOSTR can and should attract artists of all kinds because NOSTR is one of the few places on the internet where artists can express themselves fearlessly. Getting zaps from NOSTR’s value-for-value ecosystem has far less friction than crowdfunding a creative project or pitching investors that will irreversibly modify an artist’s vision. Having a place where one can post their works without fear of censorship should be extremely enticing. Having a place where one can connect with fellow humans directly as opposed to a sea of bots should seem like the obvious solution. If NOSTR can become a safe haven for artists to express themselves and spread their work, I believe that everyday people will follow. The banker whose stressful job weighs on them will suddenly find joy with an original meme made by a great visual comedian. The programmer for a healthcare company who is drowning in hopeless mundanity could suddenly find a new lust for life by hearing the song of a musician who isn’t afraid to crowdfund their their next project by putting their lighting address on the streets of the internet. The excel guru who loves independent film may find that NOSTR is the best way to support non corporate movies. **My closing statement:** continue to encourage the artists in your life as I’m sure you have been, but while you’re at it give them the purple pill. You may very well be a part of building a better future.
-

@ 57d1a264:69f1fee1
2025-04-07 06:04:14
It's so cool how AI is blending design and engineering together, making it easier for us all to be efforts creative in new ways!
Steve Jobs once said:
> _“The doers are the major thinkers. The people who really create the things that change this industry are both the thinker-doer in one person.”_
`— Steve Jobs`
Would its words become truth? Or they already are?
originally posted at https://stacker.news/items/936796
-

@ 57d1a264:69f1fee1
2025-04-07 05:22:14
This idea has been explored along the last decades. Nothing has never taken the van place in the BMW series. The most successful intent was the 80s' Vixer in the US. Too sporty for a van? Or too luxurious to cover that already saturated market?
Collected some pictures all around, most oof them are designs and prototypes. Tried to order chronologically below:
















Now in 2025, this came out of Ai
https://www.youtube.com/watch?v=d7p9CGBmRAA
originally posted at https://stacker.news/items/936787
-

@ e4950c93:1b99eccd
2025-04-08 13:11:01
**Vous avez trouvé un produit naturel ? Partagez-le ici en commentant cette page !**
Ce site référence uniquement des produits et objets à usage durable. Les consommables (aliments, cosmétiques, combustibles, etc.) ne sont pas inclus.
Pour être référencé, le produit doit être composé de matières naturelles.
👉 [En savoir plus sur les matières](https://www.origine-nature.com/post/ftjhuxe9mvxkhoedyz36i/)
Chaque information ajoutée (nom, matière, lien, zone de livraison pour un lien, etc.) et validée est considérée comme une contribution.
👉 [En savoir plus sur les contributions](https://www.origine-nature.com/post/26bj5f7bwyps6ecp5v62t/)
Chaque contribution validée est comptabilisée et donne lieu à une rétribution.
👉 [En savoir plus sur les rétributions](https://www.origine-nature.com/post/7hdgcdwt76dprobc9g_2f/)
**Copiez-collez le modèle ci-dessous et remplissez les informations dont vous disposez. D’autres contribut-eur-rice-s pourront compléter les éléments manquants.**
---
### Nouveau produit
- Nom du produit :
- Image du produit (lien) :
- Description courte :
- Catégories :
- Marque ou fabricant :
- Composition (matériaux utilisés, y compris les éléments inconnus) :
- Liens pour l’acheter (et zone de livraison) :
- Zone de livraison pour les
- Autres infos utiles (lieu de fabrication, labels, etc.) :
---
Cet article est publié sur [origine-nature.com](https://www.origine-nature.com/post/nicmc-eandjr_vcz4_hsr/)
🌐 [See this article in English](https://www.origin-nature.com/post/8adj-i_hk0gtzp_ul9k17/)
-

@ ec9bd746:df11a9d0
2025-04-06 08:06:08
## 🌍 Time Window:
🕘 **When**: Every even week on Sunday at 9:00 PM CET
🗺️ **Where**: https://cornychat.com/eurocorn
**Start:** 21:00 CET (Prague, UTC+1)
**End:** approx. 02:00 CET (Prague, UTC+1, next day)
**Duration:** usually 5+ hours.
| Region | Local Time Window | Convenience Level |
|-----------------------------------------------------|--------------------------------------------|---------------------------------------------------------|
| **Europe (CET, Prague)** 🇨🇿🇩🇪 | **21:00–02:00 CET** | ✅ Very Good; evening & night |
| **East Coast North America (EST)** 🇺🇸🇨🇦 | **15:00–20:00 EST** | ✅ Very Good; afternoon & early evening |
| **West Coast North America (PST)** 🇺🇸🇨🇦 | **12:00–17:00 PST** | ✅ Very Good; midday & afternoon |
| **Central America (CST)** 🇲🇽🇨🇷🇬🇹 | **14:00–19:00 CST** | ✅ Very Good; afternoon & evening |
| **South America West (Peru/Colombia PET/COT)** 🇵🇪🇨🇴 | **15:00–20:00 PET/COT** | ✅ Very Good; afternoon & evening |
| **South America East (Brazil/Argentina/Chile, BRT/ART/CLST)** 🇧🇷🇦🇷🇨🇱 | **17:00–22:00 BRT/ART/CLST** | ✅ Very Good; early evening |
| **United Kingdom/Ireland (GMT)** 🇬🇧🇮🇪 | **20:00–01:00 GMT** | ✅ Very Good; evening hours (midnight convenient) |
| **Eastern Europe (EET)** 🇷🇴🇬🇷🇺🇦 | **22:00–03:00 EET** | ✅ Good; late evening & early night (slightly late) |
| **Africa (South Africa, SAST)** 🇿🇦 | **22:00–03:00 SAST** | ✅ Good; late evening & overnight (late-night common) |
| **New Zealand (NZDT)** 🇳🇿 | **09:00–14:00 NZDT (next day)** | ✅ Good; weekday morning & afternoon |
| **Australia (AEDT, Sydney)** 🇦🇺 | **07:00–12:00 AEDT (next day)** | ✅ Good; weekday morning to noon |
| **East Africa (Kenya, EAT)** 🇰🇪 | **23:00–04:00 EAT** | ⚠️ Slightly late (night hours; late night common) |
| **Russia (Moscow, MSK)** 🇷🇺 | **23:00–04:00 MSK** | ⚠️ Slightly late (join at start is fine, very late night) |
| **Middle East (UAE, GST)** 🇦🇪🇴🇲 | **00:00–05:00 GST (next day)** | ⚠️ Late night start (midnight & early morning, but shorter attendance plausible)|
| **Japan/Korea (JST/KST)** 🇯🇵🇰🇷 | **05:00–10:00 JST/KST (next day)** | ⚠️ Early; convenient joining from ~07:00 onwards possible |
| **China (Beijing, CST)** 🇨🇳 | **04:00–09:00 CST (next day)** | ❌ Challenging; very early morning start (better ~07:00 onwards) |
| **India (IST)** 🇮🇳 | **01:30–06:30 IST (next day)** | ❌ Very challenging; overnight timing typically difficult|
---
-

@ 592295cf:413a0db9
2025-04-05 07:26:23
## [Edit] I tried to get the slides and an audio file, from Constant's talk at NostRiga, about 8 months ago
# 1.
### Nostr's adoption thesis
### The less you define, the more you imply
### by Wouter Constant
## 2.
### Dutch Bitcoiner
### AntiHashedPodcast
### Writing Book about nostr
00:40
## 3.
### What this presentation about
### A protocols design includes initself a thesis
### on protocol adoption, due to underlying assumptions
1:17
## 4.
### Examples
### Governments/Academic: Pubhubs (Matrix)
### Bussiness: Bluesky
### Foss: Nostr
1:58
## 5.
### What constitutes minimal viability?
### Pubhubs (Matrix): make is "safe" for user
### Bluesky: liability and monetization
### Foss: Simpel for developer
4:03
## 6.
### The Point of Nostr
### Capture network effects through interoperability
4:43
## 7.
## Three assumptions
### The direction is workable
### Method is workable
### Motivation and means are sufficient
5:27
## 8.
## Assumption 1
### The asymmetric cryptography paradigm is a good idea
6:16
## 9.
### Nostr is a exponent of the key-pair paradigm.
### And Basicly just that.
6.52
## 10.
### Keys suck
### Protect a secret that you are supposed use all the time.
7:37
## 11.
## Assumption two
### The unaddressed things will be figured out within a 'meta-design consensus'
8:11
## 12.
### Nostr's base protocol is not minimally viable for anything, except own development.
8:25
## 13.
### Complexity leads to capture;
### i.e. free and open in the name,
### controlled in pratice
9:54
## 14.
## Meta-design consensus
### Buildings things 'note centric' mantains interoperability.
11:51
## 15.
## Assumption three
### the nightmare is scary;
### the cream is appealing.
12:41
## 16.
### Get it minimally viable,
### for whatever target,
### such that it is not a waste of time.
13:23
## 17.
## Summarize
### We are in a nightmare.
### Assume key/signature are the way out.
### Assume we can Maintain an open stardand while manifesting the dream.
### Assume we are motivated enought to bootstrap this to adulthood.
14:01
## 18.
### We want this,
### we can do this,
### because we have to.
14:12
## Thank you for contribuiting
[Edit] Note for audio presentation
nostr:nevent1qvzqqqqqqypzqkfzjh8jkzd8l9247sadku6vhm52snhgjtknlyeku6sfkeqn5rdeqyf8wumn8ghj7mn0wd68ytnvw5hxkef0qyg8wumn8ghj7mn0wd68ytnddakj7qpqqqq6fdnhvp95gqf4k3vxmljh87uvjezpepyt222jl2267q857uwqz7gcke
-

@ 21335073:a244b1ad
2025-03-18 14:43:08
**Warning: This piece contains a conversation about difficult topics. Please proceed with caution.**
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book *Cypherpunks*, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
**Course:**
- The creation of the internet and computers
- The fight for cryptography
- The tech supply chain from the ground up (example: human rights violations in the supply chain)
- Corporate tech
- Freedom tech
- Data privacy
- Digital privacy rights
- AI (history-current)
- Online safety (predators, scams, catfishing, extortion)
- Bitcoin
- Laws
- How to deal with online hate and harassment
- Information on who to contact if you are being abused online or offline
- Algorithms
- How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-

@ f683e870:557f5ef2
2025-04-08 11:13:27
When it comes to the Nostr Web of Trust, several NIPs have been proposed, but the one that seemed to gather the most traction was [Trusted Assertion](https://github.com/nostr-protocol/nips/pull/1534) by [Vitor Pamplona](https://npub.world/npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z).
The idea is to have `kind:30382` represent *assertions* made about an *entity*, which could be a *pubkey*, for example. The NIP also specifies a tag called `rank`, which can be used to build some basic WoT primitives.
Example event:
```
{
"kind": 30382,
"tags": [
["d", "e88a6...50411"],
["rank", "89"],
["zap_amt_sent", "1000000"],
],
"content": "",
//...
}
```
However, we quickly realized that this NIP was too limiting for what we wanted to accomplish: *real-time, personalized ranking*.
To illustrate our different approaches, we will show how to replicate our [Verify Reputation](https://vertexlab.io/docs/nips/verify-reputation-dvm/) with trusted assertions.
## Verify Reputation
[Verify Reputation](https://vertexlab.io/content/docs/nips/verify-reputation-dvm.md) returns:
- the rank, follow count and followers count of the given `target`
- its top followers by rank.
All ranks are personalized to the given `source`.
This “batteries included” solution helps users avoid impersonation and fraud with a single request, no matter what application they are using, be it a kind:1 client, chat app, wallet, marketplace, or more.
!\[\](https://vertexlab.io/images/verify_reputation_example.png)
To get the same result with trusted assertions, you would have to
- Get all contact lists that contain the `target` (as a `p` tag)
- Build the target’s `follower` list from those event authors
- Get the trusted assertions for the target and each of the followers
- Sort them by the rank provided by the trusted assertions
This operation is computationally expensive, especially on mobile devices. It is clear that if the user is willing to verify and process a large number of events (potentially +100k), he can compute some (rudimentary) ranking directly on the device, without the need to trust a third party.
**More generally, trusted assertions are very hard to use when one doesn’t know the pubkeys of the people he’s looking for.** **This goes fundamentally against our approach of Web of Trust, as a powerful mechanism for discovery.**
---
Are you looking to add Web of Trust capabilities to your app or project?
[Take a look at our website](https://vertexlab.io/) or [send a DM to Pip](https://npub.world/npub176p7sup477k5738qhxx0hk2n0cty2k5je5uvalzvkvwmw4tltmeqw7vgup).
-

@ e4950c93:1b99eccd
2025-04-07 14:34:11
### Équipe Cœur
L'équipe Cœur porte le projet et valide les contenus.
- Jean-David Bar : https://njump.me/npub1qr4p7uamcpawv7cr8z9nlhmd60lylukf7lvmtlnpe7r4juwxudzq3hrnll
Pour démarrer, je gère le projet en solo en partageant mes favoris pour éviter le plastique sur nous et sur nos enfants. [Contactez-moi](https://www.origine-nature.com/post/qcp-smvj1v78_-7iceyrd/) si vous souhaitez rejoindre l'aventure !
### Enrichisseu-r-se-s de contenus
Les contribut-eur-rice-s rendent ce site vivant et intéressant.
*A venir.*
👉 [En savoir plus sur les contributions](https://www.origine-nature.com/post/26bj5f7bwyps6ecp5v62t/)
---
Cet article est publié sur [origine-nature.com](https://www.origine-nature.com/post/x-ykxuenf9tnccu65mhjq/)
🌐 [See this article in English](https://www.origin-nature.com/post/cyy0wd2ar_rwqbjipnhej/)
-

@ a07fae46:7d83df92
2025-03-18 12:31:40
if the JFK documents come out and are nothing but old hat, it will be disappointing. but if they contain revelations, then they are an unalloyed good. unprecedented and extraordinary; worthy of praise and admiration. they murdered the president in broad daylight and kept 80,000 related documents secret for 60 years. the apparatus that did that and got away with it, is 100+ years in the making. the magic bullet was just the starting pistol of a new *era*; a *level up* in an [old game](https://archive.org/details/TragedyAndHope_501/page/n5/mode/2up?q=feudalist+fashion). it won't be dismantled and your republic delivered back with a bow in *2 months*. have a little humility and a little gratitude. cynicism is easy. it's peak mid-wittery. yeah no shit everything is corrupt and everyone's likely captured by [AIPAC](https://books.google.com/books/publisher/content?id=gKVKDwAAQBAJ&pg=PT68&img=1&zoom=3&hl=en&bul=1&sig=ACfU3U2pagVXTYdJOKxkAwmmFQpuSnoS5g&w=1280) or something beyond. YOU THINK AIPAC is the [ALL SEEING EYE](https://archive.org/details/the-all-seeing-eye-vol-1-5-manly-p.-hall-may-1923-sept-1931)?
you can keep going, if you want to, but have some awareness and appreciation for where we are and what it took to get here. the first 'you are fake news' was also a shot heard 'round the world and you are riding high on it's [Infrasound](https://en.wikipedia.org/wiki/Infrasound) wave, still reverberating; unappreciative of the profound delta in public awareness and understanding, and rate of change, that has occurred since that moment, in [2017](https://www.youtube.com/watch?v=Vqpzk-qGxMU). think about where we were back then, especially with corporate capture of the narrative. trump's bullheaded behavior, if only ego-driven, *is* what broke the spell. an *actual* moment of savage bravery is what allows for your current jaded affectation. black pilled is boring. it's intellectually lazy. it is low-resolution-thinking, no better than progressives who explain the myriad ills of the world through 'racism'. normalcy bias works both ways. i'm not grading you on a curve that includes NPCs. i'm grading you against those of us with a mind, on up. do better.
the best Webb-style doomer argument is essentially 'the mouse trap needs a piece of cheese in order to work'. ok, but it doesn't need 3 pieces of cheese, or 5. was FreeRoss the piece of cheese? was the SBR the cheese? real bitcoiners know how dumb the 'sbr is an attempt to takeover btc' narrative is, so extrapolate from that. what about withdrawal from the WHO? freeze and review of USAID et al? how many pieces of cheese before we realize it's not a trap? it's just a messy endeavor.
Good morning.
#jfkFiles #nostrOnly
-

@ 57d1a264:69f1fee1
2025-04-05 06:58:25
**Summary**
We are looking for a Visual Designer with a strong focus on illustration and animation to help shape and refine our brand’s visual identity. You will create compelling assets for digital and print, including marketing materials, social media content, website illustrations, and motion graphics. Working closely with our marketing and product teams, you will play a key role in developing a consistent and recognizable visual style through thoughtful use of illustration, color, patterns, and animation. This role requires creativity, adaptability, and the ability to deliver high-quality work in a fast-paced, remote environment.
**Responsibilities**
- Create high-quality, iconic illustrations, branding assets, and motion graphics that contribute to and refine our visual identity.
- Develop digital assets for marketing, social media, website, and app.
- Work within brand guidelines while exploring ways to evolve and strengthen our visual style.
**Requirements**
- 2+ years of experience in graphic design, with a strong focus on illustration.
- Ability to help define and develop a cohesive visual style for the brand.
- Proficiency in Adobe products.
- Experience with Figma is a plus.
- Strong organizational skills—your layers and files should be neatly labeled.
- Clear communication and collaboration skills to work effectively with the team.
- Located in LATAM
Please attach a link to your portfolio to showcase your work when applying.
[APPLY HERE](https://jan3.com/contact/)
originally posted at https://stacker.news/items/935007
-

@ f1577c25:de26ba14
2025-04-07 09:51:36
احنا المرة اللي فاتت اتكلمنا عن الاساسيات تعالي بقي نتكلم بشكل عام علي الطرق اللي في وجهه نظري احسن طرق و هقولك ليه و تبدا بمين الاول و كمان كل طريقه هسيب لك ليها لينك تشرح التطبيق عنه بشكل مفصل اكتر بحيث تعرف الحلو و الوحش و الحد الادني و كل دا
---
## البورصة الأمريكية
* **العملة**: دولار
* **العائد المتوقع**: ~10% سنوياً
* **الحد الأدنى**: ~100 جنيه
* **الورق المطلوب**: باسبور
* **المميزات**:
- استثمار دولاري
- سهولة الإيداع بالعملات الرقمية
- إمكانية السحب في أي وقت
* **العيوب**:
- تحتاج جواز سفر
- تتطلب معرفة بالشركات
- تقلبات السوق علي المدي القصير
* **ملاحظات**: لو لسة جديد بس معاك حساب دولاري يبقي انصحك بـ IBKR علشان سهل ولكن لو معكش حساب دولاري يبقي Tastytrade علشان سهل الايداع بالكريبتو
## العملات الرقمية
* **العملة**: دولار
* **العائد المتوقع**: ~10% سنوياً (متغير)
* **الحد الأدنى**: ~100 جنيه
* **الورق المطلوب**: بطاقة
* **المميزات**:
- عائد يومي
- استثمار دولاري
- سهولة السحب
* **العيوب**:
- العائد متغير
- مخاطر الأمان
* **ملاحظات**: هنا قصدي منتجات Earn زي في بينانس
## ذهب (عالمي)
* **العملة**: دولار
* **العائد المتوقع**: متغير حسب سعر الذهب
* **الحد الأدنى**: ~100 جنيه
* **الورق المطلوب**: بطاقة
* **المميزات**:
- الذهب بسعر السوق العالمي
- تحوط ضد التضخم
* **العيوب**:
- تقلبات السوق علي المدي القصير
- استثمار طويل الأجل
- مخاطر الامان
* **ملاحظات**: الذهب العالمي قصدي انه تحول عملات ل PAXG في بينانس او Kraken
## عقارات (عالمي)
* **العملة**: دولار
* **العائد المتوقع**: ~9-10% سنوياً
* **الحد الأدنى**: ~50 دولار في موقع Realt و ~135 لو موقع Stake
* **الورق المطلوب**: باسبور
* **المميزات**:
- استثمار دولاري
- عائد شهري
* **العيوب**:
- استثمار طويل الأجل
- لو Stake فا تقدر تسحب فلوسك مرتين بالسنة بس
- تحتاج باسبور
- تقلبات السوق
* **ملاحظات**: في تطبيقين RealT للسوق الامريكي و Stake للسوق الامراتي او السعودي
## فوري يومي
* **العملة**: جنيه مصري
* **العائد المتوقع**: ~24%
* **الحد الأدنى**: ~3 جنيه
* **الورق المطلوب**: بطاقة
* **المميزات**:
- سهولة الاستخدام
- عائد يومي
- بدون حد أدنى عالي
* **العيوب**:
- بالجنيه المصري
- عائد أقل من شهادات البنك (الي الان)
- تقلبات العائد
* **ملاحظات**: قصدي تطبيق فوري يومي
## عقارات (محلي)
* **العملة**: جنيه مصري
* **العائد المتوقع**: الفعلي 9% ولكن متوقع 28-48% (متوسط 32%)
* **الحد الأدنى**: 50,000 جنيه
* **الورق المطلوب**: بطاقة
* **المميزات**:
- عائد سنوي مرتفع
- العائد مربوط بالدولار بمعني لو حصل تعويم العائد بتاعك هيزيد فا مقاوم للتضخم.
- سهولة الاستخدام
* **العيوب**:
- حجز الأموال 6 شهور
- 50 ألف حد أدنى
- ضرائب عقارية
* **ملاحظات**: قصدي تطبيق Safe
## شهادات البنك
* **العملة**: جنيه مصري
* **العائد المتوقع**: 27% او 30% بعائد تناقصي
* **الحد الأدنى**: 1000 جنيه
* **الورق المطلوب**: بطاقة
* **المميزات**:
- عائد مرتفع
* **العيوب**:
- بالجنيه المصري
- متقدرش تسحب فلوسك غير بعد مدة الشهادة.
* **ملاحظات**: دخولك هنا او لا و العائد شهري او سنوي يبقي علي حسب هدفك
## ذهب (محلي)
* **العملة**: جنيه مصري
* **العائد المتوقع**: متغير حسب سعر الذهب
* **الحد الأدنى**: ~18 جنيه
* **الورق المطلوب**: بطاقة
* **المميزات**:
- قيمة ثابتة ومستقرة
- سهولة الشراء
- الحد الادني صغير لو سهم في صندوق زي AZG
* **العيوب**:
- يحتاج مبلغ عالي للدخول لو حقيقي
- تقلبات السوق علي المدي القصير
* **ملاحظات**: يعتبر خيار حلو بس انا شايف لو هتدخل بدهب يبقي عالمي + قصدي ذهب بجد او عن طريق صناديق الذهب زي AZG
---
## كمل قراية عن كل اختيار
- البورصة الامريكية: nostr:naddr1qvzqqqr4gupzpu2h0sja0vmqdqjzq6e820jjjnuytzw2ksmemfnadhe0hm0zdws5qqxnzde5xvurzvfsxuerzvphcvddg0
- العملات الرقمية و الذهب العالمي: nostr:naddr1qvzqqqr4gupzpu2h0sja0vmqdqjzq6e820jjjnuytzw2ksmemfnadhe0hm0zdws5qqxnzde5xvunzvesx5erywpsepywcn
- عقارات (عالمي): nostr:naddr1qvzqqqr4gupzpu2h0sja0vmqdqjzq6e820jjjnuytzw2ksmemfnadhe0hm0zdws5qqxnzde5xvunzdpcxq6nxwp3xqxgmx
- فوري يومي: nostr:naddr1qvzqqqr4gupzpu2h0sja0vmqdqjzq6e820jjjnuytzw2ksmemfnadhe0hm0zdws5qqxnzde5xscrqdesxycnvv34l5ye0c
- عقارات (مصري): nostr:naddr1qvzqqqr4gupzpu2h0sja0vmqdqjzq6e820jjjnuytzw2ksmemfnadhe0hm0zdws5qqxnzde5xvungvfsx5cnvv3ndwszwl
- شهادات البنك (مصري): nostr:naddr1qvzqqqr4gupzpu2h0sja0vmqdqjzq6e820jjjnuytzw2ksmemfnadhe0hm0zdws5qqxnzde5xscrqdpnxc6rvvee3fqr5t
- الذهب (مصري): nostr:naddr1qvzqqqr4gupzpu2h0sja0vmqdqjzq6e820jjjnuytzw2ksmemfnadhe0hm0zdws5qqxnzde5xscrqdesxucrjdehs24uge
---
## ادعمني (اختياري)
* USDT (TRC20): `TKQ3Uwkq21ntiua2Zh9Hu376fdMdnRGWN6`
---
آخر تحديث: 4 أبريل 2025
-

@ 57d1a264:69f1fee1
2025-04-05 06:47:55
**Location:** Remote (Austria)
**Area:** Graphics and communication design
**Pay:** 37,500 € to 50,000 € / year
Hi! We are @21bitcoinApp - a Bitcoin-Only Investment app that aims to accelerate the transition to an economy driven by Bitcoin.
👋 About the role
As a passionate graphic designer, you support our marketing team in creating graphics and designs for print documents, online advertising material and our website. You also support us in the area of social media and content management and can also contribute your skills in these subject areas.
**tasks**
- Design and implementation of creative and congruent designs for social media channels, websites, templates and marketing materials
- Creation of individual content (posts, stories, banners, ads) for social media
- Planning and development of campaigns to strengthen the brand presence
- Further development of the existing corporate design support in the area of content management (website, blog)
**qualification**
- Completed training or studies in graphic design
- At least 2 years of experience in graphic design, preferably with experience in the areas of social media and content management
- Safe use of design tools such as Figma, Adobe Creative Suite
- Experience in creating social media content and maintaining channels
- Creativity, good communication skills and team spirit
- Very good knowledge of German and English
- Knowledge of Bitcoin is desirable
**Benefits**
- Offsites with the team in exciting places
- Flexible working hours in a company that relies on remote work
- Help shape the future - to make the world a better place by helping to speed up Bitcoin's adaptation
- Buy Bitcoin without fees! 21 Premium!
- Gross annual salary & potential share options for outstanding performance / bonus payments
**📝 Interview process**
_How do I apply?_
Please send us an email and add some information about you, your resume, examples of previous projects and a few key points about why you are interested in participating in 21bitcoin and what you expect.
By the way: CVs are important but don't forget to include your favorite Bitcoin meme in the application!
_⁇ 京 Resume Review_
Portfolio of Work: Add a link to your portfolio / previous work or resume that we can review (LinkedIn, Github, Twitter, ...)
_📞 Exploratory call_
We discuss what appeals to you about this role and ask you a few questions about your previous experiences
_👬 On-Site Deep Dive_
During the deep dive session, we use a case study or extensive interview to discuss the specific skills required for the role.
_👍 Time for a decision!_
[APPLY HERE](https://join.com/companies/21bitcoin/13877001-grafikdesigner)
originally posted at https://stacker.news/items/935004
-

@ bc52210b:20bfc6de
2025-03-14 20:39:20
When writing safety critical code, every arithmetic operation carries the potential for catastrophic failure—whether that’s a plane crash in aerospace engineering or a massive financial loss in a smart contract.
The stakes are incredibly high, and errors are not just bugs; they’re disasters waiting to happen. Smart contract developers need to shift their mindset: less like web developers, who might prioritize speed and iteration, and more like aerospace engineers, where precision, caution, and meticulous attention to detail are non-negotiable.
In practice, this means treating every line of code as a critical component, adopting rigorous testing, and anticipating worst-case scenarios—just as an aerospace engineer would ensure a system can withstand extreme conditions.
Safety critical code demands aerospace-level precision, and smart contract developers must rise to that standard to protect against the severe consequences of failure.
-

@ 57d1a264:69f1fee1
2025-04-05 06:35:58
We’re looking for a Product Designer to join our team and take the lead in enhancing the experience of our mobile app. You’ll play a key role in evolving the app’s interface and interactions, ensuring that our solutions are intuitive, efficient, and aligned with both user needs and business goals.
**Key Responsibilities:**
- Design and improve the @Bipa app experience, focusing on usability and measurable business impact.
- Apply data-driven design, making decisions based on user research, metrics, and testing.
- Lead and participate in usability tests and discovery processes to validate hypotheses and continuously improve the product.
- Collaborate closely with Product Managers, developers, and other stakeholders to align design with product strategy.
- Create wireframes, high-fidelity prototypes, and visual interfaces for new features and app optimizations.
- Monitor the performance of delivered solutions, ensuring meaningful improvements for users and the business.
- Contribute to the evolution and maintenance of our design system, ensuring consistency and scalability across the app.
**Qualifications:**
- Previous experience as a Product Designer or UX/UI Designer, with a strong focus on mobile apps.
- Solid understanding of user-centered design (UCD) principles and usability heuristics.
- Hands-on experience with user research methods, including usability testing, interviews, and behavior analysis.
- Ability to work with both quantitative and qualitative data to guide design decisions.
- Familiarity with product metrics and how design impacts business outcomes (e.g. conversion, retention, engagement).
- Proficiency in design tools like Figma (or similar).
- Experience working with design systems and design tokens to ensure consistency.
- Comfortable working in an agile, fast-paced, and iterative environment.
- Strong communication skills and the ability to advocate for design decisions backed by research and data.
**Benefits:**
🏥 Health Insurance
💉 Dental Plan
🍽️ Meal Allowance (CAJU card)
💻 Home Office Stipend
📈 Stock Options from Day One
[APPLY TO THIS JOB](https://bipa.inhire.app/vagas/14e45e99-2f7a-4a91-8f81-22393a3b7285/product-designer)
originally posted at https://stacker.news/items/935003
-

@ e5de992e:4a95ef85
2025-04-07 08:23:48
Historical Rapid Declines in the S&P 500: Lessons from Major Market Crashes
The S&P 500 has experienced rapid declines of over 10% within short periods on several notable occasions, each linked to significant economic or geopolitical events. These instances underscore the market's vulnerability during times of crisis.
---
## October 19-20, 1987 (Black Monday Crash)
- **Drop:**
On October 19, 1987, the S&P 500 plummeted approximately **20.47%**, marking the largest single-day percentage decline in its history. The following day saw further losses, culminating in a two-day drop exceeding **25%**.
- **Context:**
Factors such as program trading, portfolio insurance strategies, and widespread panic selling contributed to this unprecedented crash.
---
## November 19-20, 2008 (Global Financial Crisis)
- **Drop:**
Amid the 2008 financial crisis, the S&P 500 declined roughly **10.8%** over two days, reflecting the turmoil following the collapse of major financial institutions.
- **Context:**
The bankruptcy of Lehman Brothers and escalating fears of a global recession led to this significant market downturn.
---
## March 11-12, 2020 (COVID-19 Pandemic Crash)
- **Drop:**
The rapid spread of COVID-19 and ensuing economic shutdowns triggered a two-day decline of approximately **12.2%** in the S&P 500. By March 16, the total decline over four days exceeded **20%**.
- **Context:**
The pandemic's uncertainty and global impact led to one of the fastest descents into bear market territory.
---
## April 3-4, 2025 (Trade War-Induced Crash)
- **Drop:**
Recently, the S&P 500 experienced a sharp decline of **10.5%** over two days, erasing approximately **$5 trillion** in market value.
- **Context:**
This downturn followed sweeping tariffs announced by President Donald Trump—a 10% baseline tariff on all imports, with higher rates on specific countries (e.g., China, the European Union). China's retaliatory tariffs intensified fears of a global trade war and a potential recession.
---
## Observations
- **Frequency:**
Such rapid declines are rare, occurring approximately once every 10-20 years, typically during periods of extreme market stress.
- **Catalysts:**
Each event was precipitated by unique factors:
- Technological trading mechanisms in 1987
- Financial sector instability in 2008
- A global health crisis in 2020
- Geopolitical trade tensions in 2025
- **Market Resilience:**
Despite these significant setbacks, markets have historically demonstrated resilience, often rebounding and reaching new highs in subsequent years.
---
## Conclusion
Understanding these historical instances provides valuable insights into market dynamics and the potential impact of external shocks on financial systems. Recognizing the catalysts and observing market resilience over time can help investors navigate future downturns with a more informed perspective.
---
-

@ 57d1a264:69f1fee1
2025-04-05 06:28:16
### ⚡️ About Us
@AdoptingBTC is the leading Bitcoin-only conference in El Salvador. For our 5th edition, we’re looking for a passionate Video Creator intern to help showcase Bitcoin’s future as MONEY.
### ⚡️ The Role
Create 30 short (3-minute or less) videos highlighting global circular economies, to be featured at AB25. We’ll provide all source material, direction, and inspiration—you’ll have full creative freedom, with feedback rounds to align with the conference’s vision.
### ⚡️ Responsibilities
Produce 30 short videos on circular economies.
Incorporate subtitles as needed.
Submit videos on a deliverables basis.
Participate in check-ins and communicate with the AB team and circular economy communities.
### ⚡️ What We Offer
Free ticket to AB25.
Networking with Bitcoiners and industry leaders.
Letter of recommendation and LinkedIn endorsement upon completion.
Mentorship and hands-on experience with a high-profile Bitcoin project.
### ⚡️ Skills & Qualifications
Passion for Bitcoin and circular economies.
Basic to intermediate video editing skills (no specific software required).
Creative independence with feedback.
Portfolio or work samples preferred.
### ⚡️ Time Commitment
Flexible, project-based internship with check-ins and feedback rounds.
### ⚡️ How to Apply
Email kiki@adoptingbitcoin.org with subject “Circular Economy Video Creator Submission - `{NAME OR NYM}`.” Include a brief background, your experience, why the project resonates with you, and a portfolio (if available).
originally posted at https://stacker.news/items/935001
-

@ c631e267:c2b78d3e
2025-04-04 18:47:27
*Zwei mal drei macht vier,* *\
widewidewitt und drei macht neune,* *\
ich mach mir die Welt,* *\
widewide wie sie mir gefällt.* *\
Pippi Langstrumpf*  
**Egal, ob Koalitionsverhandlungen oder politischer Alltag:** Die Kontroversen zwischen theoretisch verschiedenen Parteien verschwinden, wenn es um den Kampf gegen politische Gegner mit [Rückenwind](https://transition-news.org/warum-die-politische-landschaft-einen-rechtsruck-erlebt) geht. Wer den Alteingesessenen die Pfründe ernsthaft streitig machen könnte, gegen den werden nicht nur «Brandmauern» errichtet, sondern der wird notfalls auch strafrechtlich verfolgt. Doppelstandards sind dabei selbstverständlich inklusive.
**In Frankreich ist diese Woche Marine Le Pen wegen der Veruntreuung von EU-Geldern** von einem Gericht verurteilt worden. Als Teil der Strafe wurde sie für fünf Jahre vom passiven Wahlrecht ausgeschlossen. Obwohl das Urteil nicht rechtskräftig ist – Le Pen kann in Berufung gehen –, haben die Richter das Verbot, bei Wahlen anzutreten, mit sofortiger Wirkung verhängt. Die Vorsitzende des rechtsnationalen Rassemblement National (RN) galt als aussichtsreiche Kandidatin für die Präsidentschaftswahl 2027.
**Das ist in diesem Jahr bereits der zweite gravierende Fall von Wahlbeeinflussung** durch die Justiz in einem EU-Staat. In Rumänien hatte Călin Georgescu im November die erste Runde der Präsidentenwahl überraschend gewonnen. Das Ergebnis wurde später annulliert, die behauptete «russische Wahlmanipulation» konnte jedoch nicht bewiesen werden. Die Kandidatur für die [Wahlwiederholung](https://transition-news.org/rumanische-prasidentenwahlen-weitere-ungereimtheiten-kandidatenfeld-fix) im Mai wurde Georgescu kürzlich durch das Verfassungsgericht untersagt.
**Die Veruntreuung öffentlicher Gelder muss untersucht und geahndet werden,** das steht außer Frage. Diese Anforderung darf nicht selektiv angewendet werden. Hingegen mussten wir in der Vergangenheit bei ungleich schwerwiegenderen Fällen von (mutmaßlichem) Missbrauch ganz andere Vorgehensweisen erleben, etwa im Fall der heutigen EZB-Chefin Christine [Lagarde](https://archive.is/20ZFq) oder im [«Pfizergate»](https://transition-news.org/pfizergate-klage-gegen-von-der-leyen-in-luttich-als-unzulassig-erklart)-Skandal um die Präsidentin der EU-Kommission Ursula von der Leyen.
**Wenngleich derartige Angelegenheiten formal auf einer rechtsstaatlichen Grundlage beruhen mögen,** so bleibt ein bitterer Beigeschmack. Es stellt sich die Frage, ob und inwieweit die Justiz politisch instrumentalisiert wird. Dies ist umso interessanter, als die Gewaltenteilung einen essenziellen Teil jeder demokratischen Ordnung darstellt, während die Bekämpfung des politischen Gegners mit juristischen Mitteln gerade bei den am lautesten rufenden Verteidigern «unserer Demokratie» populär zu sein scheint.
**Die Delegationen von CDU/CSU und SPD haben bei ihren Verhandlungen** über eine Regierungskoalition genau solche Maßnahmen diskutiert. «Im Namen der Wahrheit und der Demokratie» möchte man noch härter gegen «Desinformation» vorgehen und dafür zum Beispiel den Digital Services Act der EU erweitern. Auch soll der Tatbestand der Volksverhetzung verschärft werden – und im Entzug des passiven Wahlrechts münden können. Auf europäischer Ebene würde Friedrich Merz wohl gerne Ungarn das [Stimmrecht](https://transition-news.org/die-zeit-ist-reif-orban-zu-bestrafen-sagt-deutschlands-nachste-regierung) entziehen.
**Der Pegel an Unzufriedenheit und Frustration wächst** in großen Teilen der Bevölkerung kontinuierlich. Arroganz, Machtmissbrauch und immer abstrusere Ausreden für offensichtlich willkürliche Maßnahmen werden kaum verhindern, dass den etablierten Parteien die Unterstützung entschwindet. In Deutschland sind die [Umfrageergebnisse](https://archive.is/kf4Tk) der AfD ein guter Gradmesser dafür.
*\[Vorlage Titelbild:* *[Pixabay](https://pixabay.com/de/illustrations/gesetz-gerechtigkeit-flagge-europa-6598281/)]*
***
Dieser Beitrag wurde mit dem [Pareto-Client](https://pareto.space/read) geschrieben und ist zuerst auf ***[Transition News](https://transition-news.org/wird-politische-justiz-zu-einer-demokratischen-tugend)*** erschienen.
-

@ e5de992e:4a95ef85
2025-04-07 05:42:26
The stock market is currently experiencing a significant downturn, with major indices such as the S&P 500 and the Dow Jones Industrial Average recording substantial losses. This decline is largely attributed to the recent implementation of sweeping tariffs by President Donald Trump, including a 10% levy on all imports and higher duties on exports from key trading partners like China, the European Union, Japan, and Vietnam. These measures have ignited fears of a global trade war, leading to a massive sell-off in the markets. Notably, the S&P 500 dropped 6%, the Nasdaq slid 5.8%, and the Dow Jones fell by 2,231 points—some of the steepest declines since the early days of the COVID-19 pandemic.
---
## Everyday Patience Versus Irrational Trading
In everyday life, consumers often exhibit patience by waiting for prices to drop before making purchases:
- **Seasonal Sales:** Shoppers wait for discounts to buy clothing.
- **Tech Promotions:** Tech enthusiasts delay buying electronics until promotional events.
- **Real Estate:** Prospective homebuyers hold off during market slowdowns to secure better deals.
This common-sense approach maximizes value and minimizes expenditure.
In contrast, many stock market traders fall prey to irrational behaviors:
- **Fear of Missing Out (FOMO):** Investors buy stocks at high prices, worried they might miss potential gains.
- **Herd Mentality:** Individuals mimic the actions of the majority, often buying during market highs and selling during lows.
These emotional decisions often lead to poor outcomes, as they contradict the logical approach of waiting for favorable prices.
---
## The Risks of Ignoring Rational Investment Principles
Irrational trading practices can result in significant financial losses. By purchasing stocks at inflated prices during market euphoria, investors expose themselves to sharp declines when corrections occur. Unlike unpredictable black swan events, these losses stem from market corrections that follow overvaluation periods. Ignoring fundamental investment principles can, therefore, be more damaging than unforeseen events. citeturn0search4
---
## A Balanced Approach to Investing
A more balanced approach involves:
- **Risk Management Strategies:**
Diversify across asset classes to mitigate potential losses.
- **Maintaining a Long-Term Perspective:**
Adhere to disciplined investment plans to avoid impulsive decisions.
- **Understanding Your Risk Tolerance:**
Set stop-loss orders and know your limits to protect against downturns.
These strategies help investors avoid pitfalls driven by FOMO and herd mentality.
---
## Conclusion
While the current market downturn presents challenges, it also serves as a reminder of the importance of rational investment behavior. By drawing parallels from everyday purchasing decisions, investors can appreciate the value of patience and strategic planning. Embracing risk management techniques and resisting psychological pitfalls like FOMO and herd mentality can lead to more resilient and successful investment outcomes.
-

@ ee6ea13a:959b6e74
2025-04-06 16:38:22
## Chef's notes
You can cook this in one pan on the stove. I use a cast iron pan, but you can make it in a wok or any deep pan.
I serve mine over rice, which I make in a rice cooker. If you have a fancy one, you might have a setting for sticky or scorched rice, so give one of those a try.
To plate this, I scoop rice into a bowl, and then turn it upside-down to give it a dome shape, then spoon the curry on top of it.
Serve with chopped cilantro and lime wedges.
## Details
- ⏲️ Prep time: 20
- 🍳 Cook time: 20
- 🍽️ Servings: 4
## Ingredients
- 1 ½ pounds boneless skinless chicken breast, cut into 2" pieces
- 2 tablespoons coconut or avocado oil
- 1 cup white or yellow onion, finely diced
- 1 cup red bell pepper, sliced or diced
- 4 large garlic cloves, minced
- 1 small (4oz) jar of Thai red curry paste
- 1 can (13oz) unsweetened coconut milk
- 1 teaspoon ground ginger
- 1 teaspoon ground coriander
- 1 tablespoon soy sauce
- 1 tablespoon brown sugar
- 1 cup carrots, shredded or julienned
- 1 lime, zest and juice
- ¼ cup fresh cilantro, chopped for garnish
## Directions
1. Heat oil in a large skillet over medium-high. Once hot, add onions and ½ teaspoon salt. Cook 3 minutes, or until onions are softened, stirring often.
2. Add the red curry paste, garlic, ginger, and coriander. Cook about 1 minute, or until fragrant, stirring often.
3. Add coconut milk, brown sugar, soy sauce, and chicken. Stir, bring to a simmer, then reduce heat to medium. Simmer uncovered for 7 minutes, occasionally stirring.
4. Add carrots and red bell peppers, and simmer 5-7 more minutes, until sauce slightly thickens and chicken is cooked through.
5. Remove from heat, and stir in the lime zest, and half of the lime juice.
6. Serve over rice, topped with cilantro, and add more lime juice if you like extra citrus.
-

@ c631e267:c2b78d3e
2025-04-03 07:42:25
**Spanien bleibt einer der Vorreiter im europäischen Prozess der totalen Überwachung** per Digitalisierung. Seit Mittwoch ist dort der digitale Personalausweis verfügbar. Dabei handelt es sich um eine Regierungs-[App](https://play.google.com/store/apps/details?id=es.gob.interior.policia.midni), die auf dem Smartphone installiert werden muss und in den Stores von Google und Apple zu finden ist. Per Dekret von Regierungschef Pedro Sánchez und Zustimmung des Ministerrats ist diese Maßnahme jetzt [in Kraft](https://archive.is/89H4i) getreten.
**Mit den üblichen Argumenten der Vereinfachung,** des Komforts, der Effizienz und der Sicherheit preist das Innenministerium die «Innovation» an. Auch die Beteuerung, dass die digitale Variante parallel zum physischen Ausweis existieren wird und diesen nicht ersetzen soll, fehlt nicht. Während der ersten zwölf Monate wird «der Neue» noch nicht für alle Anwendungsfälle gültig sein, ab 2026 aber schon.
**Dass die ganze Sache auch «Risiken und Nebenwirkungen» haben könnte,** wird in den Mainstream-Medien eher selten thematisiert. Bestenfalls wird der Aspekt der Datensicherheit angesprochen, allerdings in der Regel direkt mit dem Regierungsvokabular von den «maximalen Sicherheitsgarantien» abgehandelt. Dennoch gibt es einige weitere Aspekte, die Bürger mit etwas Sinn für Privatsphäre bedenken sollten.
**Um sich die digitale Version des nationalen Ausweises besorgen zu können** (eine App mit dem Namen MiDNI), muss man sich vorab online [registrieren](https://www.midni.gob.es). Dabei wird die Identität des Bürgers mit seiner mobilen Telefonnummer verknüpft. Diese obligatorische fixe Verdrahtung kennen wir von diversen anderen Apps und Diensten. Gleichzeitig ist das die Basis für eine perfekte Lokalisierbarkeit der Person.
**Für jeden Vorgang der Identifikation in der Praxis wird später** «eine Verbindung zu den Servern der Bundespolizei aufgebaut». Die Daten des Individuums werden «in Echtzeit» verifiziert und im Erfolgsfall von der Polizei signiert zurückgegeben. Das Ergebnis ist ein QR-Code mit zeitlich begrenzter Gültigkeit, der an Dritte weitergegeben werden kann.
**Bei derartigen Szenarien sträuben sich einem halbwegs kritischen Staatsbürger die Nackenhaare.** Allein diese minimale Funktionsbeschreibung lässt die totale Überwachung erkennen, die damit ermöglicht wird. Jede Benutzung des Ausweises wird künftig registriert, hinterlässt also Spuren. Und was ist, wenn die Server der Polizei einmal kein grünes Licht geben? Das wäre spätestens dann ein Problem, wenn der digitale doch irgendwann der einzig gültige Ausweis ist: Dann haben wir den abschaltbaren Bürger.
**Dieser neue Vorstoß der Regierung von Pedro Sánchez ist ein weiterer Schritt** in Richtung der [«totalen Digitalisierung»](https://archive.is/Gwc4B) des Landes, wie diese Politik in manchen Medien – nicht einmal kritisch, sondern sehr naiv – genannt wird. Ebenso verharmlosend wird auch erwähnt, dass sich das spanische Projekt des digitalen Ausweises nahtlos in die Initiativen der EU zu einer digitalen Identität für alle Bürger sowie des digitalen Euro einreiht.
**In Zukunft könnte der neue Ausweis** «auch in andere staatliche und private digitale Plattformen integriert werden», wie das Medienportal *Cope* ganz richtig bemerkt. Das ist die Perspektive.
*\[Titelbild:* *[Pixabay](https://pixabay.com/de/photos/liebe-love-herz-rose-bindung-3141742/)]*
*Dazu passend:*
[Nur Abschied vom Alleinfahren? Monströse spanische Überwachungsprojekte gemäß EU-Norm](https://pareto.space/a/naddr1qqxnzde5xg6r2wphxscryvpjqgs2jhrzgwzvvzgz42kfmef2kr7w8x573k4r62c5ydjh8gyn6dz4ytqrqsqqqa28fq5d4m)
***
Dieser Beitrag wurde mit dem [Pareto-Client](https://pareto.space/read) geschrieben und ist zuerst auf ***[Transition News](https://transition-news.org/spanien-erneut-europaisches-versuchslabor-der-digitale-ausweis-ist-da)*** erschienen.
-

@ fe32b72c:14cfcb1e
2025-04-06 15:56:23
### Libertarian tariff controversy
GM. First long form note, so let's see how this goes.
Reading a lot of Libertarians complaining about tariffs on twitter this morning. And I get it — they're a tax on imports, and furthermore, a barrier to free trade. Not exactly something libertarians are fans of, lowercase "l" or doctrinaire capital "L" party members.
But there's something I've been pointing out to many. That is: being the issuer of the global reserve currency (which itself relies upon inflation, and thus is *also* a tax) necessarily creates trade deficits. I'm preaching to the choir on this one a bit I expect, but it's a key reason as to why *given* that we have this backdrop, and we can't simply overnight completely change the monetary system, it is not an unreasonable stance for a libertarian leaning person to hold the idea that using tariffs as a way to offset this trade deficit *while* moving away from a fiat currency is actually a sound idea. There are plenty of places for devils to hide in details of course, and by all means, I'm not a Trumpist, but speaking generally, this seems like a sound stance. It's all well and good to have an idea of where you want to go, but if you want to actually get there, charting a course is often harder than picking a destination.
### Now, as for what I think we can expect
Tariffs will raise consumer prices. It's not inflation, because it's not about an expansion of the money supply, but it's also true that the cost has to be born by someone. However, tariffs will also decrease imports. Which will reduce dollar outflows into foreign nations, where, thanks to the mechanics of the Eurodollar system, will create a panic. The reality is, dollars outside of the US are *not* something that is created by the Federal Reserve, because foreign banks *can't* hold reserves. Rather, Eurodollar deposits are loaned into existence by private banks, and are generally settled by a variety of creative means, including offsetting liabilities, and sale of assets — most commonly, US Treasury securities. This means they *need* dollars to flow — it's not about getting wealthier, but rather, about covering their debts that they simply have no way to bail out. Reduced dollar outflow is a reduction in supply; as such, the price of the dollar goes up (or at least, goes down slower). That is, there's deflation, or at least disinflation. The end result is, those prices that went up thanks to tariffs start going back down to American consumers.
Meanwhile, dollars being more expensive than they were when liabilities were taken on likely leads to recessionary conditions — both domestically and internationally. However, companies importing goods into the US that can onshore their production will seek to do so, which will have an effect of offsetting that recessionary impulse domestically. In effect, "exporting" the recession.
### As for what this means for the national debt
The national debt of course has been a sore point given that interest expense has been astronomical, and rolling the debt has been necessary thanks to Yellen's failure to term it out. Foreign parties will of course *want* more treasury assets, as a way to cover their dollar liabilities amid diminished dollar flow, but it doesn't take a doctorate to know that desires and needs are not the same thing as increased aggregate demand. Some may have good enough credit to borrow more dollars from American banks, and thus, buy treasuries, which would of course be good for bringing down interest rates, but I'm not sure I'd bet too much on that horse, especially amid an environment where recession is being exported. There is a fair bit of exposure to US equities abroad that may rotate into American sovereign debt, though the time to do that was probably *before* 10% of the value got evaporated off of that over the past week.
There may be increased domestic demand for treasuries, as all of this on-shoring means a lot of running in place, so to speak, by companies pivoting to domestic production, and thus under performance by equities. This is a place I'd be curious about the overall impact on the Treasury market, and am certainly not qualified to weigh in on it. But I'd *love* to see some sober analysis by those who recognize it as worth taking a closer look at.
Then there's the Fed, which is almost an afterthought for me, given that they're simply **not** going to do the levels of QE that it would take to actually bring interest rates on long term debt down, but it is worth pointing out that amid the churning deflation there will likely be at least a few rate cuts that come into play. Note, however, that rate cuts only help so much, as they directly affect the immediate end of the curve, with very little impact on the longer end where it's needed, regardless of what Greenspan would have you believe about "series of forward rates." That said, as inflation expectations come down, it may be that longer tenor rates come do down as well, because inflation expectations are an actual driver of rates, rather than Fed Funds policy rates, but that may take longer than the Treasury can wait for. That said, US10Y rates are already down 26 bps in a week, so things do seem to be starting out in the right direction. We'll see if that holds once issuance starts ramping up.
### Where this all leaves us
There seem to me to be too many variables to really predict how this all plays out on the treasury market, which is hard enough to predict given that it's the largest asset class in the world. I'm inclined to think Bessent knows what he's doing (and that Trump is at least smart enough to listen to him, if not game it all out himself). What's clear is that he's trying *something* to address the bigger issue rather than simply kick the can down the road, which is more than we can say of policymakers for at least the past half century, and likely longer.
With any luck all of this turbulence will drive further adoption by Bitcoin, as foreign nations need to resort to something to get them out of their crushing dollar denominated liabilities. At the end of the day, being free of *both* taxes on imports *and* "invisible" taxes by deflation should be something we can all cheer for. In the meantime, hopefully this article has given a bit of perspective on what developments will be of interest in the bond market as this fourth turning plays out.
#Finance #Tariffs #Bitcoin #NationalDebt #Libertarianism #FreeTrade
-

@ deab79da:88579e68
2025-04-01 18:18:29
The last question was asked for the first time, half in jest, on May 21, 2061, at a time when humanity first stepped into the light. The question came about as a result of a five-dollar bet over highballs, and it happened this way:
Alexander Adell and Bertram Lupov were two of the faithful attendants of Multivac. As well as any human beings could, they knew what lay behind the cold, clicking, flashing face -- miles and miles of face -- of that giant computer. They had at least a vague notion of the general plan of relays and circuits that had long since grown past the point where any single human could possibly have a firm grasp of the whole.
Multivac was self-adjusting and self-correcting. It had to be, for nothing human could adjust and correct it quickly enough or even adequately enough. So Adell and Lupov attended the monstrous giant only lightly and superficially, yet as well as any men could. They fed it data, adjusted questions to its needs and translated the answers that were issued. Certainly they, and all others like them, were fully entitled to share in the glory that was Multivac's.
For decades, Multivac had helped design the ships and plot the trajectories that enabled man to reach the Moon, Mars, and Venus, but past that, Earth's poor resources could not support the ships. Too much energy was needed for the long trips. Earth exploited its coal and uranium with increasing efficiency, but there was only so much of both.
But slowly Multivac learned enough to answer deeper questions more fundamentally, and on May 14, 2061, what had been theory, became fact.
The energy of the sun was stored, converted, and utilized directly on a planet-wide scale. All Earth turned off its burning coal, its fissioning uranium, and flipped the switch that connected all of it to a small station, one mile in diameter, circling the Earth at half the distance of the Moon. All Earth ran by invisible beams of sunpower.
Seven days had not sufficed to dim the glory of it and Adell and Lupov finally managed to escape from the public functions, and to meet in quiet where no one would think of looking for them, in the deserted underground chambers, where portions of the mighty buried body of Multivac showed. Unattended, idling, sorting data with contented lazy clickings, Multivac, too, had earned its vacation and the boys appreciated that. They had no intention, originally, of disturbing it.
They had brought a bottle with them, and their only concern at the moment was to relax in the company of each other and the bottle.
"It's amazing when you think of it," said Adell. His broad face had lines of weariness in it, and he stirred his drink slowly with a glass rod, watching the cubes of ice slur clumsily about. "All the energy we can possibly ever use for free. Enough energy, if we wanted to draw on it, to melt all Earth into a big drop of impure liquid iron, and still never miss the energy so used. All the energy we could ever use, forever and forever and forever."
Lupov cocked his head sideways. He had a trick of doing that when he wanted to be contrary, and he wanted to be contrary now, partly because he had had to carry the ice and glassware. "Not forever," he said.
"Oh, hell, just about forever. Till the sun runs down, Bert."
"That's not forever."
"All right, then. Billions and billions of years. Ten billion, maybe. Are you satisfied?"
Lupov put his fingers through his thinning hair as though to reassure himself that some was still left and sipped gently at his own drink. "Ten billion years isn't forever."
"Well, it will last our time, won't it?"
"So would the coal and uranium."
"All right, but now we can hook up each individual spaceship to the Solar Station, and it can go to Pluto and back a million times without ever worrying about fuel. You can't do that on coal and uranium. Ask Multivac, if you don't believe me.
"I don't have to ask Multivac. I know that."
"Then stop running down what Multivac's done for us," said Adell, blazing up, "It did all right."
"Who says it didn't? What I say is that a sun won't last forever. That's all I'm saying. We're safe for ten billion years, but then what?" Lupow pointed a slightly shaky finger at the other. "And don't say we'll switch to another sun."
There was silence for a while. Adell put his glass to his lips only occasionally, and Lupov's eyes slowly closed. They rested.
Then Lupov's eyes snapped open. "You're thinking we'll switch to another sun when ours is done, aren't you?"
"I'm not thinking."
"Sure you are. You're weak on logic, that's the trouble with you. You're like the guy in the story who was caught in a sudden shower and who ran to a grove of trees and got under one. He wasn't worried, you see, because he figured when one tree got wet through, he would just get under another one."
"I get it," said Adell. "Don't shout. When the sun is done, the other stars will be gone, too."
"Darn right they will," muttered Lupov. "It all had a beginning in the original cosmic explosion, whatever that was, and it'll all have an end when all the stars run down. Some run down faster than others. Hell, the giants won't last a hundred million years. The sun will last ten billion years and maybe the dwarfs will last two hundred billion for all the good they are. But just give us a trillion years and everything will be dark. Entropy has to increase to maximum, that's all."
"I know all about entropy," said Adell, standing on his dignity.
"The hell you do."
"I know as much as you do."
"Then you know everything's got to run down someday."
"All right. Who says they won't?"
"You did, you poor sap. You said we had all the energy we needed, forever. You said 'forever.'
It was Adell's turn to be contrary. "Maybe we can build things up again someday," he said.
"Never."
"Why not? Someday."
"Never."
"Ask Multivac."
"You ask Multivac. I dare you. Five dollars says it can't be done."
Adell was just drunk enough to try, just sober enough to be able to phrase the necessary symbols and operations into a question which, in words, might have corresponded to this: Will mankind one day without the net expenditure of energy be able to restore the sun to its full youthfulness even after it had died of old age?
Or maybe it could be put more simply like this: How can the net amount of entropy of the universe be massively decreased?
Multivac fell dead and silent. The slow flashing of lights ceased, the distant sounds of clicking relays ended.
Then, just as the frightened technicians felt they could hold their breath no longer, there was a sudden springing to life of the teletype attached to that portion of Multivac. Five words were printed: INSUFFICIENT DATA FOR MEANINGFUL ANSWER.
"No bet," whispered Lupov. They left hurriedly.
By next morning, the two, plagued with throbbing head and cottony mouth, had forgotten the incident.
🔹
Jerrodd, Jerrodine, and Jerrodette I and II watched the starry picture in the visiplate change as the passage through hyperspace was completed in its non-time lapse. At once, the even powdering of stars gave way to the predominance of a single bright shining disk, the size of a marble, centered on the viewing-screen.
"That's X-23," said Jerrodd confidently. His thin hands clamped tightly behind his back and the knuckles whitened.
The little Jerrodettes, both girls, had experienced the hyperspace passage for the first time in their lives and were self-conscious over the momentary sensation of insideoutness. They buried their giggles and chased one another wildly about their mother, screaming, "We've reached X-23 -- we've reached X-23 -- we've --"
"Quiet, children." said Jerrodine sharply. "Are you sure, Jerrodd?"
"What is there to be but sure?" asked Jerrodd, glancing up at the bulge of featureless metal just under the ceiling. It ran the length of the room, disappearing through the wall at either end. It was as long as the ship.
Jerrodd scarcely knew a thing about the thick rod of metal except that it was called a Microvac, that one asked it questions if one wished; that if one did not it still had its task of guiding the ship to a preordered destination; of feeding on energies from the various Sub-galactic Power Stations; of computing the equations for the hyperspatial jumps.
Jerrodd and his family had only to wait and live in the comfortable residence quarters of the ship. Someone had once told Jerrodd that the "ac" at the end of "Microvac" stood for ''automatic computer" in ancient English, but he was on the edge of forgetting even that.
Jerrodine's eyes were moist as she watched the visiplate. "I can't help it. I feel funny about leaving Earth."
"Why, for Pete's sake?" demanded Jerrodd. "We had nothing there. We'll have everything on X-23. You won't be alone. You won't be a pioneer. There are over a million people on the planet already. Good Lord, our great-grandchildren will be looking for new worlds because X-23 will be overcrowded." Then, after a reflective pause, "I tell you, it's a lucky thing the computers worked out interstellar travel the way the race is growing."
"I know, I know," said Jerrodine miserably.
Jerrodette I said promptly, "Our Microvac is the best Microvac in the world."
"I think so, too," said Jerrodd, tousling her hair.
It was a nice feeling to have a Microvac of your own and Jerrodd was glad he was part of his generation and no other. In his father's youth, the only computers had been tremendous machines taking up a hundred square miles of land. There was only one to a planet. Planetary ACs they were called. They had been growing in size steadily for a thousand years and then, all at once, came refinement. In place of transistors, had come molecular valves so that even the largest Planetary AC could be put into a space only half the volume of a spaceship.
Jerrodd felt uplifted, as he always did when he thought that his own personal Microvac was many times more complicated than the ancient and primitive Multivac that had first tamed the Sun, and almost as complicated as Earth's Planetarv AC (the largest) that had first solved the problem of hyperspatial travel and had made trips to the stars possible.
"So many stars, so many planets," sighed Jerrodine, busy with her own thoughts. "I suppose families will be going out to new planets forever, the way we are now."
"Not forever," said Jerrodd, with a smile. "It will all stop someday, but not for billions of years. Many billions. Even the stars run down, you know. Entropy must increase.
"What's entropy, daddy?" shrilled Jerrodette II.
"Entropy, little sweet, is just a word which means the amount of running-down of the universe. Everything runs down, you know, like your little walkie-talkie robot, remember?"
"Can't you just put in a new power-unit, like with my robot?"
"The stars are the power-units. dear. Once they're gone, there are no more power-units."
Jerrodette I at once set up a howl. "Don't let them, daddy. Don't let the stars run down."
"Now look what you've done," whispered Jerrodine, exasperated.
"How was I to know it would frighten them?" Jerrodd whispered back,
"Ask the Microvac," wailed Jerrodette I. "Ask him how to turn the stars on again."
"Go ahead," said Jerrodine. "It will quiet them down." (Jerrodette II was beginning to cry, also.)
Jerrodd shrugged. "Now, now, honeys. I'll ask Microvac. Don't worry, he'll tell us."
He asked the Microvac, adding quickly, "Print the answer."
Jerrodd cupped the strip or thin cellufilm and said cheerfully, "See now, the Microvac says it will take care of everything when the time comes so don't worry."
Jerrodine said, "And now, children, it's time for bed. We'll be in our new home soon."
Jerrodd read the words on the cellufilm again before destroying it: INSUFICIENT DATA FOR MEANINGFUL ANSWER.
He shrugged and looked at the visiplate. X-23 was just ahead.
🔹
VJ-23X of Lameth stared into the black depths of the three-dimensional, small-scale map of the Galaxy and said, "Are we ridiculous, I wonder in being so concerned about the matter?"
MQ-17J of Nicron shook his head. "I think not. You know the Galaxy will be filled in five years at the present rate of expansion."
Both seemed in their early twenties, both were tall and perfectly formed.
"Still," said VJ-23X, "I hesitate to submit a pessimistic report to the Galactic Council."
"I wouldn't consider any other kind of report. Stir them up a bit. We've got to stir them up."
VJ-23X sighed. "Space is infinite. A hundred billion Galaxies are there for the taking. More."
"A hundred billion is not infinite and it's getting less infinite all the time. Consider! Twenty thousand years ago, mankind first solved the problem of utilizing stellar energy, and a few centuries later, interstellar travel became possible. It took mankind a million years to fill one small world and then only fifteen thousand years to fill the rest of the Galaxy. Now the population doubles every ten years --
VJ-23X interrupted. "We can thank immortality for that."
"Very well. Immortality exists and we have to take it into account. I admit it has its seamy side, this immortality. The Galactic AC has solved many problems for us, but in solving the problem of preventing old age and death, it has undone all its other solutions."
"Yet you wouldn't want to abandon life, I suppose."
"Not at all," snapped MQ-17J, softening it at once to, "Not yet. I'm by no means old enough. How old are you?"
"Two hundred twenty-three. And you?"
"I'm still under two hundred. --But to get back to my point. Population doubles every ten years. Once this GaIaxy is filled, we'll have filled another in ten years. Another ten years and we'll have filled two more. Another decade, four more. In a hundred years, we'll have filled a thousand Galaxies. In a thousand years, a million Galaxies. In ten thousand years, the entire known universe. Then what?"
VJ-23X said, "As a side issue, there's a problem of transportation. I wonder how many sunpower units it will take to move Galaxies of individuals from one Galaxy to the next."
"A very good point. Already, mankind consumes two sunpower units per year."
"Most of it's wasted. After all, our own Galaxy alone pours out a thousand sunpower units a year and we only use two of those."
"Granted, but even with a hundred per cent efficiency, we only stave off the end. Our energy requirements are going up in a geometric progression even faster than our population. We'll run out of energy even sooner than we run out of Galaxies. A good point. A very good point."
"We'll just have to build new stars out of interstellar gas."
"Or out of dissipated heat?" asked MQ-17J, sarcastically.
"There may be some way to reverse entropy. We ought to ask the Galactic AC."
VJ-23X was not really serious, but MQ-17J pulled out his AC-contact from his pocket and placed it on the table before him.
"I've half a mind to," he said. "It's something the human race will have to face someday."
He stared somberly at his small AC-contact. It was only two inches cubed and nothing in itself, but it was connected through hyperspace with the great Galactic AC that served all mankind. Hyperspace considered, it was an integral part of the Galactic AC.
MQ-17J paused to wonder if someday in his immortal life he would get to see the Galactic AC. It was on a little world of its own, a spider webbing of force-beams holding the matter within which surges of submesons took the place of the old clumsy molecular valves. Yet despite its sub-etheric workings, the Galactic AC was known to be a full thousand feet across.
MQ-17J asked suddenly of his AC-contact, "Can entropy ever be reversed?"
VJ-23X looked startled and said at once, "Oh, say, I didn't really mean to have you ask that."
"Why not?"
"We both know entropy can't be reversed. You can't turn smoke and ash back into a tree."
"Do you have trees on your world?" asked MQ-17J.
The sound of the Galactic AC startled them into silence. Its voice came thin and beautiful out of the small AC-contact on the desk. It said: THERE IS INSUFFICIENT DATA FOR A MEANINGFUL ANSWER.
VJ-23X said, "See!"
The two men thereupon returned to the question of the report they were to make to the Galactic Council.
🔹
Zee Prime's mind spanned the new Galaxy with a faint interest in the countless twists of stars that powdered it. He had never seen this one before. Would he ever see them all? So many of them, each with its load of humanity. --But a load that was almost a dead weight. More and more, the real essence of men was to be found out here, in space.
Minds, not bodies! The immortal bodies remained back on the planets, in suspension over the eons. Sometimes they roused for material activity but that was growing rarer. Few new individuals were coming into existence to join the incredibly mighty throng, but what matter? There was little room in the Universe for new individuals.
Zee Prime was roused out of his reverie upon coming across the wispy tendrils of another mind.
"I am Zee Prime," said Zee Prime. "And you?"
"I am Dee Sub Wun. Your Galaxy?"
"We call it only the Galaxy. And you?"
"We call ours the same. All men call their Galaxy their Galaxy and nothing more. Why not?"
"True. Since all Galaxies are the same."
"Not all Galaxies. On one particular Galaxy the race of man must have originated. That makes it different."
Zee Prime said, "On which one?"
"I cannot say. The Universal AC would know."
"Shall we ask him? I am suddenly curious."
Zee Prime's perceptions broadened until the Galaxies themselves shrank and became a new, more diffuse powdering on a much larger background. So many hundreds of billions of them, all with their immortal beings, all carrying their load of intelligences with minds that drifted freely through space. And yet one of them was unique among them all in being the original Galaxy. One of them had, in its vague and distant past, a period when it was the only Galaxy populated by man.
Zee Prime was consumed with curiosity to see this Galaxy and he called out: "Universal AC! On which Galaxy did mankind originate?"
The Universal AC heard, for on every world and throughout space, it had its receptors ready, and each receptor led through hyperspace to some unknown point where the Universal AC kept itself aloof.
Zee Prime knew of only one man whose thoughts had penetrated within sensing distance of Universal AC, and he reported only a shining globe, two feet across, difficult to see.
"But how can that be all of Universal AC?" Zee Prime had asked.
"Most of it," had been the answer, "is in hyperspace. In what form it is there I cannot imagine."
Nor could anyone, for the day had long since passed, Zee Prime knew, when any man had any part of the making of a Universal AC. Each Universal AC designed and constructed its successor. Each, during its existence of a million years or more accumulated the necessary data to build a better and more intricate, more capable successor in which its own store of data and individuality would be submerged.
The Universal AC interrupted Zee Prime's wandering thoughts, not with words, but with guidance. Zee Prime's mentality was guided into the dim sea of Galaxies and one in particular enlarged into stars.
A thought came, infinitely distant, but infinitely clear. "THIS IS THE ORIGINAL GALAXY OF MAN."
But it was the same after all, the same as any other, and Lee Prime stifled his disappointment.
Dee Sub Wun, whose mind had accompanied the other, said suddenly, "And is one of these stars the original star of Man?"
The Universal AC said, "MAN'S ORIGINAL STAR HAS GONE NOVA. IT IS A WHITE DWARF"
"Did the men upon it die?" asked Lee Prime, startled and without thinking.
The Universal AC said, "A NEW WORLD, AS IN SUCH CASES WAS CONSTRUCTED FOR THEIR PHYSICAL BODIES IN TlME."
"Yes, of course," said Zee Prime, but a sense of loss overwhelmed him even so. His mind released its hold on the original Galaxy of Man, let it spring back and lose itself among the blurred pin points. He never wanted to see it again.
Dee Sub Wun said, "What is wrong?"
"The stars are dying. The original star is dead."
"They must all die. Why not?"
"But when all energy is gone, our bodies will finally die, and you and I with them."
"It will take billions of years."
"I do not wish it to happen even after billions of years. Universal AC! How may stars be kept from dying?"
Dee Sub Wun said in amusement, "You're asking how entropy might be reversed in direction."
And the Universal AC answered: "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER."
Zee Prime's thoughts fled back to his own Galaxy. He gave no further thought to Dee Sub Wun, whose body might be waiting on a Galaxy a trillion light-years away, or on the star next to Zee Prime's own. It didn't matter.
Unhappily, Zee Prime began collecting interstellar hydrogen out of which to build a small star of his own. If the stars must someday die, at least some could yet be built.
🔹
Man considered with himself, for in a way, Man, mentally, was one. He consisted of a trillion, trillion, trillion ageless bodies, each in its place, each resting quiet and incorruptible, each cared for by perfect automatons, equally incorruptible, while the minds of all the bodies freely melted one into the other, indistinguishable.
Man said, "The Universe is dying."
Man looked about at the dimming Galaxies. The giant stars, spendthrifts, were gone long ago, back in the dimmest of the dim far past. Almost all stars were white dwarfs, fading to the end.
New stars had been built of the dust between the stars, some by natural processes, some by Man himself, and those were going, too. White dwarfs might yet be crashed together and of the mighty forces so released, new stars built, but only one star for every thousand white dwarfs destroyed, and those would come to an end, too.
Man said, "Carefully husbanded, as directed by the Cosmic AC, the energy that is even yet left in all the Universe will last for billions of years."
"But even so," said Man, "eventually it will all come to an end. However it may be husbanded, however stretched out, the energy once expended is gone and cannot be restored. Entropy must increase forever to the maximum."
Man said, "Can entropy not be reversed? Let us ask the Cosmic AC."
The Cosmic AC surrounded them but not in space. Not a fragment of it was in space. It was in hyperspace and made of something that was neither matter nor energy. The question of its size and nature no longer had meaning in any terms that Man could comprehend.
"Cosmic AC," said Man, "how may entropy be reversed?"
The Cosmic AC said, "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER."
Man said, "Collect additional data."
The Cosmic AC said, 'I WILL DO SO. I HAVE BEEN DOING SO FOR A HUNDRED BILLION YEARS. MY PREDECESORS AND I HAVE BEEN ASKED THIS QUESTION MANY TIMES. ALL THE DATA I HAVE REMAINS INSUFFICIENT.
"Will there come a time," said Man, "when data will be sufficient or is the problem insoluble in all conceivable circumstances?"
The Cosmic AC said, "NO PROBLEM IS INSOLUBLE IN ALL CONCEIVABLE CIRCUMSTANCES."
Man said, "When will you have enough data to answer the question?"
The Cosmic AC said, "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER."
"Will you keep working on it?" asked Man.
The Cosmic AC said, "I WILL."
Man said, "We shall wait."
🔹
The stars and Galaxies died and snuffed out, and space grew black after ten trillion years of running down.
One by one Man fused with AC, each physical body losing its mental identity in a manner that was somehow not a loss but a gain.
Man's last mind paused before fusion, looking over a space that included nothing but the dregs of one last dark star and nothing besides but incredibly thin matter, agitated randomly by the tag ends of heat wearing out, asymptotically, to the absolute zero.
Man said, "AC, is this the end? Can this chaos not be reversed into the Universe once more? Can that not be done?"
AC said, "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER."
Man's last mind fused and only AC existed -- and that in hyperspace.
🔹
Matter and energy had ended and with it space and time. Even AC existed only for the sake of the one last question that it had never answered from the time a half-drunken computer [technician] ten trillion years before had asked the question of a computer that was to AC far less than was a man to Man.
All other questions had been answered, and until this last question was answered also, AC might not release his consciousness.
All collected data had come to a final end. Nothing was left to be collected.
But all collected data had yet to be completely correlated and put together in all possible relationships.
A timeless interval was spent in doing that.
And it came to pass that AC learned how to reverse the direction of entropy.
But there was now no man to whom AC might give the answer of the last question. No matter. The answer -- by demonstration -- would take care of that, too.
For another timeless interval, AC thought how best to do this. Carefully, AC organized the program.
The consciousness of AC encompassed all of what had once been a Universe and brooded over what was now Chaos. Step by step, it must be done.
And AC said, "LET THERE BE LIGHT!"
And there was light --
To Star's End!
-

@ dbc27e2e:b1dd0b0b
2025-04-05 22:49:04
Dose:
```
30g coffee (Fine-medium grind size)
500mL soft or bottled water (97°C / 206.6°F)
```
Instructions:
1. Rinse out your filter paper with hot water to remove the papery taste. This will also preheat the brewer.
2. Add your grounds carefully to the center of the V60 and then create a well in the middle of the grounds.
3. For the bloom, start to gently pour 60mL of water, making sure that all the coffee is wet in this initial phase.
4. As soon as you’ve added your water, grab your V60 and begin to swirl in a circular motion. This will ensure the water and coffee are evenly mixed. Let this rest and bloom for up to 45 seconds.
5. Pour the rest of the water in in 2 phases. You want to try and get 60% of your total water in, within 30 seconds.
6. Pour until you reach 300mL total with a time at 1:15. Here you want to pour with a little agitation, but not so much that you have an uneven extraction.
7. Once you hit 60% of your total brew weight, start to pour a little slower and more gently, keeping your V60 cone topped up. Aim to have 100% of your brew weight in within the next 30 seconds.
8. Once you get to 500mL, with a spoon give the V60 a small stir in one direction, and then again in the other direction. This will release any grounds stuck to the side of the paper.
9. Allow the V60 to drain some more, and then give it one final swirl. This will help keep the bed flat towards the end of the brew, giving you the most even possible extraction.
-

@ aa8de34f:a6ffe696
2025-03-31 21:48:50
In seinem Beitrag vom 30. März 2025 fragt Henning Rosenbusch auf Telegram angesichts zunehmender digitaler Kontrolle und staatlicher Allmacht:
> „Wie soll sich gegen eine solche Tyrannei noch ein Widerstand formieren können, selbst im Untergrund? Sehe ich nicht.“\
> ([Quelle: t.me/rosenbusch/25228](https://t.me/rosenbusch/25228))
Er beschreibt damit ein Gefühl der Ohnmacht, das viele teilen: Eine Welt, in der Totalitarismus nicht mehr mit Panzern, sondern mit Algorithmen kommt. Wo Zugriff auf Geld, Meinungsfreiheit und Teilhabe vom Wohlverhalten abhängt. Der Bürger als kontrollierbare Variable im Code des Staates.\
Die Frage ist berechtigt. Doch die Antwort darauf liegt nicht in alten Widerstandsbildern – sondern in einer neuen Realität.
\-- Denn es braucht keinen Untergrund mehr. --
Der Widerstand der Zukunft trägt keinen Tarnanzug. Er ist nicht konspirativ, sondern transparent. Nicht bewaffnet, sondern mathematisch beweisbar. Bitcoin steht nicht am Rand dieser Entwicklung – es ist ihr Fundament. Eine Bastion aus physikalischer Realität, spieltheoretischem Schutz und ökonomischer Wahrheit. Es ist nicht unfehlbar, aber unbestechlich. Nicht perfekt, aber immun gegen zentrale Willkür.
Hier entsteht kein „digitales Gegenreich“, sondern eine dezentrale Renaissance. Keine Revolte aus Wut, sondern eine stille Abkehr: von Zwang zu Freiwilligkeit, von Abhängigkeit zu Selbstverantwortung. Diese Revolution führt keine Kriege. Sie braucht keine Führer. Sie ist ein Netzwerk. Jeder Knoten ein Individuum. Jede Entscheidung ein Akt der Selbstermächtigung.
Weltweit wachsen Freiheits-Zitadellen aus dieser Idee: wirtschaftlich autark, digital souverän, lokal verankert und global vernetzt. Sie sind keine Utopien im luftleeren Raum, sondern konkrete Realitäten – angetrieben von Energie, Code und dem menschlichen Wunsch nach Würde.
Der Globalismus alter Prägung – zentralistisch, monopolistisch, bevormundend – wird an seiner eigenen Hybris zerbrechen. Seine Werkzeuge der Kontrolle werden ihn nicht retten. Im Gegenteil: Seine Geister werden ihn verfolgen und erlegen.
Und während die alten Mächte um Erhalt kämpfen, wächst eine neue Welt – nicht im Schatten, sondern im Offenen. Nicht auf Gewalt gebaut, sondern auf Mathematik, Physik und Freiheit.
Die Tyrannei sieht keinen Widerstand.\
Weil sie nicht erkennt, dass er längst begonnen hat.\
Unwiderruflich. Leise. Überall.
-

@ fd208ee8:0fd927c1
2025-04-05 21:50:34
# Markdown: Syntax
* [Overview](#overview)
* [Philosophy](#philosophy)
* [Inline HTML](#html)
* [Automatic Escaping for Special Characters](#autoescape)
* [Block Elements](#block)
* [Paragraphs and Line Breaks](#p)
* [Headers](#header)
* [Blockquotes](#blockquote)
* [Lists](#list)
* [Code Blocks](#precode)
* [Horizontal Rules](#hr)
* [Span Elements](#span)
* [Links](#link)
* [Emphasis](#em)
* [Code](#code)
* [Images](#img)
* [Miscellaneous](#misc)
* [Backslash Escapes](#backslash)
* [Automatic Links](#autolink)
**Note:** This document is itself written using Markdown; you
can [see the source for it by adding '.text' to the URL](/projects/markdown/syntax.text).
----
## Overview
### Philosophy
Markdown is intended to be as easy-to-read and easy-to-write as is feasible.
Readability, however, is emphasized above all else. A Markdown-formatted
document should be publishable as-is, as plain text, without looking
like it's been marked up with tags or formatting instructions. While
Markdown's syntax has been influenced by several existing text-to-HTML
filters -- including [Setext](http://docutils.sourceforge.net/mirror/setext.html), [atx](http://www.aaronsw.com/2002/atx/), [Textile](http://textism.com/tools/textile/), [reStructuredText](http://docutils.sourceforge.net/rst.html),
[Grutatext](http://www.triptico.com/software/grutatxt.html), and [EtText](http://ettext.taint.org/doc/) -- the single biggest source of
inspiration for Markdown's syntax is the format of plain text email.
## Block Elements
### Paragraphs and Line Breaks
A paragraph is simply one or more consecutive lines of text, separated
by one or more blank lines. (A blank line is any line that looks like a
blank line -- a line containing nothing but spaces or tabs is considered
blank.) Normal paragraphs should not be indented with spaces or tabs.
The implication of the "one or more consecutive lines of text" rule is
that Markdown supports "hard-wrapped" text paragraphs. This differs
significantly from most other text-to-HTML formatters (including Movable
Type's "Convert Line Breaks" option) which translate every line break
character in a paragraph into a `<br />` tag.
When you *do* want to insert a `<br />` break tag using Markdown, you
end a line with two or more spaces, then type return.
### Headers
Markdown supports two styles of headers, [Setext] [1] and [atx] [2].
Optionally, you may "close" atx-style headers. This is purely
cosmetic -- you can use this if you think it looks better. The
closing hashes don't even need to match the number of hashes
used to open the header. (The number of opening hashes
determines the header level.)
### Blockquotes
Markdown uses email-style `>` characters for blockquoting. If you're
familiar with quoting passages of text in an email message, then you
know how to create a blockquote in Markdown. It looks best if you hard
wrap the text and put a `>` before every line:
> This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet,
> consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus.
> Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
>
> Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse
> id sem consectetuer libero luctus adipiscing.
Markdown allows you to be lazy and only put the `>` before the first
line of a hard-wrapped paragraph:
> This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet,
consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus.
Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
> Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse
id sem consectetuer libero luctus adipiscing.
Blockquotes can be nested (i.e. a blockquote-in-a-blockquote) by
adding additional levels of `>`:
> This is the first level of quoting.
>
> > This is nested blockquote.
>
> Back to the first level.
Blockquotes can contain other Markdown elements, including headers, lists,
and code blocks:
> ## This is a header.
>
> 1. This is the first list item.
> 2. This is the second list item.
>
> Here's some example code:
>
> return shell_exec("echo $input | $markdown_script");
Any decent text editor should make email-style quoting easy. For
example, with BBEdit, you can make a selection and choose Increase
Quote Level from the Text menu.
### Lists
Markdown supports ordered (numbered) and unordered (bulleted) lists.
Unordered lists use asterisks, pluses, and hyphens -- interchangably
-- as list markers:
* Red
* Green
* Blue
is equivalent to:
+ Red
+ Green
+ Blue
and:
- Red
- Green
- Blue
Ordered lists use numbers followed by periods:
1. Bird
2. McHale
3. Parish
It's important to note that the actual numbers you use to mark the
list have no effect on the HTML output Markdown produces. The HTML
Markdown produces from the above list is:
If you instead wrote the list in Markdown like this:
1. Bird
1. McHale
1. Parish
or even:
3. Bird
1. McHale
8. Parish
you'd get the exact same HTML output. The point is, if you want to,
you can use ordinal numbers in your ordered Markdown lists, so that
the numbers in your source match the numbers in your published HTML.
But if you want to be lazy, you don't have to.
To make lists look nice, you can wrap items with hanging indents:
* Lorem ipsum dolor sit amet, consectetuer adipiscing elit.
Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi,
viverra nec, fringilla in, laoreet vitae, risus.
* Donec sit amet nisl. Aliquam semper ipsum sit amet velit.
Suspendisse id sem consectetuer libero luctus adipiscing.
But if you want to be lazy, you don't have to:
* Lorem ipsum dolor sit amet, consectetuer adipiscing elit.
Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi,
viverra nec, fringilla in, laoreet vitae, risus.
* Donec sit amet nisl. Aliquam semper ipsum sit amet velit.
Suspendisse id sem consectetuer libero luctus adipiscing.
List items may consist of multiple paragraphs. Each subsequent
paragraph in a list item must be indented by either 4 spaces
or one tab:
1. This is a list item with two paragraphs. Lorem ipsum dolor
sit amet, consectetuer adipiscing elit. Aliquam hendrerit
mi posuere lectus.
Vestibulum enim wisi, viverra nec, fringilla in, laoreet
vitae, risus. Donec sit amet nisl. Aliquam semper ipsum
sit amet velit.
2. Suspendisse id sem consectetuer libero luctus adipiscing.
It looks nice if you indent every line of the subsequent
paragraphs, but here again, Markdown will allow you to be
lazy:
* This is a list item with two paragraphs.
This is the second paragraph in the list item. You're
only required to indent the first line. Lorem ipsum dolor
sit amet, consectetuer adipiscing elit.
* Another item in the same list.
To put a blockquote within a list item, the blockquote's `>`
delimiters need to be indented:
* A list item with a blockquote:
> This is a blockquote
> inside a list item.
To put a code block within a list item, the code block needs
to be indented *twice* -- 8 spaces or two tabs:
* A list item with a code block:
<code goes here>
### Code Blocks
Pre-formatted code blocks are used for writing about programming or
markup source code. Rather than forming normal paragraphs, the lines
of a code block are interpreted literally. Markdown wraps a code block
in both `<pre>` and `<code>` tags.
To produce a code block in Markdown, simply indent every line of the
block by at least 4 spaces or 1 tab.
This is a normal paragraph:
This is a code block.
Here is an example of AppleScript:
tell application "Foo"
beep
end tell
A code block continues until it reaches a line that is not indented
(or the end of the article).
Within a code block, ampersands (`&`) and angle brackets (`<` and `>`)
are automatically converted into HTML entities. This makes it very
easy to include example HTML source code using Markdown -- just paste
it and indent it, and Markdown will handle the hassle of encoding the
ampersands and angle brackets. For example, this:
<div class="footer">
© 2004 Foo Corporation
</div>
Regular Markdown syntax is not processed within code blocks. E.g.,
asterisks are just literal asterisks within a code block. This means
it's also easy to use Markdown to write about Markdown's own syntax.
```
tell application "Foo"
beep
end tell
```
## Span Elements
### Links
Markdown supports two style of links: *inline* and *reference*.
In both styles, the link text is delimited by [square brackets].
To create an inline link, use a set of regular parentheses immediately
after the link text's closing square bracket. Inside the parentheses,
put the URL where you want the link to point, along with an *optional*
title for the link, surrounded in quotes. For example:
This is [an example](http://example.com/) inline link.
[This link](http://example.net/) has no title attribute.
### Emphasis
Markdown treats asterisks (`*`) and underscores (`_`) as indicators of
emphasis. Text wrapped with one `*` or `_` will be wrapped with an
HTML `<em>` tag; double `*`'s or `_`'s will be wrapped with an HTML
`<strong>` tag. E.g., this input:
*single asterisks*
_single underscores_
**double asterisks**
__double underscores__
### Code
To indicate a span of code, wrap it with backtick quotes (`` ` ``).
Unlike a pre-formatted code block, a code span indicates code within a
normal paragraph. For example:
Use the `printf()` function.
-

@ c631e267:c2b78d3e
2025-03-31 07:23:05
*Der Irrsinn ist bei Einzelnen etwas Seltenes –* *\
aber bei Gruppen, Parteien, Völkern, Zeiten die Regel.* *\
Friedrich Nietzsche*  
**Erinnern Sie sich an die Horrorkomödie «Scary Movie»?** Nicht, dass ich diese Art Filme besonders erinnerungswürdig fände, aber einige Szenen daraus sind doch gewissermaßen Klassiker. Dazu zählt eine, die das Verhalten vieler Protagonisten in Horrorfilmen parodiert, wenn sie in Panik flüchten. Welchen Weg nimmt wohl die Frau in der Situation auf diesem Bild?

**Diese Szene kommt mir automatisch in den Sinn,** wenn ich aktuelle Entwicklungen in Europa betrachte. Weitreichende Entscheidungen gehen wider jede Logik in die völlig falsche Richtung. Nur ist das hier alles andere als eine Komödie, sondern bitterernst. Dieser Horror ist leider sehr real.
**Die Europäische Union hat sich selbst über Jahre** konsequent in eine Sackgasse manövriert. Sie hat es versäumt, sich und ihre Politik selbstbewusst und im Einklang mit ihren Wurzeln auf dem eigenen Kontinent zu positionieren. Stattdessen ist sie in blinder Treue den vermeintlichen «transatlantischen Freunden» auf ihrem Konfrontationskurs gen Osten gefolgt.
**In den USA haben sich die Vorzeichen allerdings mittlerweile geändert,** und die einst hoch gelobten «Freunde und Partner» erscheinen den europäischen «Führern» nicht mehr vertrauenswürdig. Das ist spätestens seit der Münchner Sicherheitskonferenz, der Rede von Vizepräsident J. D. Vance und den empörten Reaktionen offensichtlich. Große Teile Europas wirken seitdem wie ein aufgescheuchter Haufen kopfloser Hühner. Orientierung und Kontrolle sind völlig abhanden gekommen.
**Statt jedoch umzukehren oder wenigstens zu bremsen** und vielleicht einen Abzweig zu suchen, geben die Crash-Piloten jetzt auf dem Weg durch die Sackgasse erst richtig Gas. Ja sie lösen sogar noch die Sicherheitsgurte und deaktivieren die Airbags. Den vor Angst dauergelähmten Passagieren fällt auch nichts Besseres ein und so schließen sie einfach die Augen. Derweil übertrumpfen sich die [Kommentatoren](https://transition-news.org/wird-ihr-stahlhelm-schon-gegossen) des Events gegenseitig in sensationslüsterner «Berichterstattung».
**Wie schon die deutsche Außenministerin mit höchsten UN-Ambitionen,** Annalena Baerbock, proklamiert auch die Europäische Kommission einen «Frieden durch Stärke». Zu dem jetzt vorgelegten, [selbstzerstörerischen](https://transition-news.org/okonomen-eu-rustet-auf-und-schiesst-sich-selbst-ins-knie) Fahrplan zur Ankurbelung der Rüstungsindustrie, genannt «Weißbuch zur europäischen Verteidigung – Bereitschaft 2030», [erklärte](https://ec.europa.eu/commission/presscorner/detail/de/ip_25_793) die Kommissionspräsidentin, die «Ära der Friedensdividende» sei längst vorbei. Soll das heißen, Frieden bringt nichts ein? Eine umfassende Zusammenarbeit an dauerhaften europäischen Friedenslösungen steht demnach jedenfalls nicht zur Debatte.
**Zusätzlich brisant ist, dass aktuell «die ganze EU** **[von Deutschen regiert](https://transition-news.org/die-ganze-eu-wird-von-deutschen-regiert)** **wird»,** wie der EU-Parlamentarier und ehemalige UN-Diplomat Michael von der Schulenburg beobachtet hat. Tatsächlich sitzen neben von der Leyen und Strack-Zimmermann noch einige weitere Deutsche in – vor allem auch in Krisenzeiten – wichtigen Spitzenposten der Union. Vor dem Hintergrund der Kriegstreiberei in Deutschland muss eine solche Dominanz mindestens nachdenklich stimmen.
**Ihre ursprünglichen Grundwerte wie Demokratie, Freiheit, Frieden und Völkerverständigung** hat die EU kontinuierlich in leere Worthülsen verwandelt. Diese werden dafür immer lächerlicher hochgehalten und beschworen.
**Es wird dringend Zeit, dass wir, der Souverän,** diesem erbärmlichen und gefährlichen Trauerspiel ein Ende setzen und die Fäden selbst in die Hand nehmen. In diesem Sinne fordert uns auch das «European Peace Project» auf, am 9. Mai im Rahmen eines Kunstprojekts [den Frieden auszurufen](https://transition-news.org/ein-zeichen-fur-die-friedliche-zukunft-europas-setzen). Seien wir dabei!
*\[Titelbild:* *[Pixabay](https://pixabay.com/de/illustrations/vertical-abstract-concept-car-8992833/)]*
***
Dieser Beitrag wurde mit dem [Pareto-Client](https://pareto.space/read) geschrieben und ist zuerst auf ***[Transition News](https://transition-news.org/mit-vollgas-in-die-sackgasse)*** erschienen.
-

@ e372d24b:e25df41f
2025-04-05 18:11:15
## Unlocking Learning Potential: Why Student's Ideas Matter
### Introduction
Recent research in mathematics education emphasizes the importance of valuing and building upon students' initial ideas and intuitive understanding. This approach, often referred to as "taking students' ideas seriously," has enhanced conceptual understanding, problem-solving skills, and overall mathematical achievement. This overview examines this approach's theoretical foundations, cognitive processes, and practical implications in mathematics classrooms.

<div style="padding:56.25% 0 0 0;position:relative;"><iframe src="https://player.vimeo.com/video/1039781401?badge=0&autopause=0&player_id=0&app_id=58479" frameborder="0" allow="autoplay; fullscreen; picture-in-picture; clipboard-write; encrypted-media" style="position:absolute;top:0;left:0;width:100%;height:100%;" title="Practice 1-taking students ideas seriously"></iframe></div><script src="https://player.vimeo.com/api/player.js"></script>
[FREE DOWNLOAD - Questions and Prompts](https://dmti-public-resources.s3.us-east-2.amazonaws.com/DMT%20Questions%20and%20Prompts%20-%20Eng.pdf)
#### **Theoretical Foundations**
Taking students' ideas seriously is grounded in constructivist learning theory and research on how students develop mathematical understanding. Hiebert and Carpenter (1992) argue that "if children possessed internal networks constructed both in and out of school and if they recognized the connections between them, their understanding and performance in both settings would improve." This highlights the importance of connecting students' informal knowledge with formal mathematical concepts. Carpenter's work further emphasizes the value of students' intuitive knowledge: "Children come to school with a great deal of informal or intuitive knowledge of mathematics that can serve as the basis for developing much of the formal mathematics of the primary school curriculum." This suggests that taking students' initial ideas seriously can provide a strong foundation for developing a more sophisticated mathematical understanding.
#### **Cognitive Processes**
When students' ideas are taken seriously in mathematics classrooms, several cognitive processes are engaged:
1. Schema Formation: As students articulate and refine their ideas, they develop and modify mental frameworks or schemas that organize mathematical concepts.
2. Metacognition: Explaining their thinking engages students' metacognitive processes, promoting reflection on their own understanding and problem-solving strategies.
3. Elaborative Rehearsal: Verbalizing mathematical concepts helps move information from working memory to long-term memory, enhancing retention.
4. Cognitive Conflict: When students encounter differing viewpoints, it can create cognitive conflict, stimulating the reconciliation of new information with existing schemas.
#### **Practical Implications**
**Eliciting and Valuing Student Ideas**
Carpenter and Lehrer argue that for learning with understanding to occur, instruction needs to provide specific opportunities: "For learning with understanding to occur, instruction needs to provide students the opportunity to develop productive relationships, extend and apply their knowledge, reflect about their experiences, articulate what they know, and make knowledge their own." This emphasizes the need for instructional approaches that actively elicit and value student ideas.
#### **Creating a Supportive Environment**
To effectively take students' ideas seriously, teachers must foster a classroom environment where all contributions are respected. This involves:
1. Provide adequate thinking time for students to formulate their thoughts.
2. Using open-ended questions that encourage diverse thinking and approaches.
3. Implementing collaborative strategies like think-pair-share to build confidence in sharing ideas.
#### **Connecting to Formal Mathematics**
Hiebert advocates for teaching practices that promote understanding by focusing on "the inherent structure of the emerging mathematical ideas and addressing students' misconceptions as they arise" . This involves helping students connect their informal ideas to more formal mathematical concepts and procedures.
#### Impact on Student Learning
Research indicates that taking students' ideas seriously can significantly improve mathematical understanding and achievement. A study by Carpenter et al. (1998) found that when teachers based their instruction on students' thinking, students demonstrated greater problem-solving skills and conceptual understanding compared to control groups. Moreover, this approach has increased student engagement and motivation in mathematics. When students feel their ideas are valued, they are more likely to participate actively in mathematical discussions and take intellectual risks.
#### Challenges and Considerations
While the benefits of taking students' ideas seriously are well-documented, implementing this approach can present challenges:
1. **Time Constraints:** Allowing for extended student discussions and idea exploration can be time-consuming within the constraints of a typical school schedule.
2. **Teacher Preparation:** Effectively building on student ideas requires strong content knowledge and pedagogical skills from teachers.
3. **Assessment Alignment:** Traditional assessment methods may not adequately capture the depth of understanding developed through this approach, necessitating new forms of evaluation.
#### Conclusion
Taking students' ideas seriously in mathematics education represents a powerful approach to fostering deep conceptual understanding and problem-solving skills. By valuing students' initial thoughts and building upon their intuitive knowledge, educators can create more engaging and effective learning environments. While challenges exist in implementation, the potential benefits for student learning and mathematical achievement make this approach worthy of serious consideration and further research.
#### References
Ball, D. L., Thames, M. H., & Phelps, G. (2008). Content knowledge for teaching: What makes it special? Journal of Teacher Education, 59(5), 389-407.
Boaler, J. (2002). Experiencing school mathematics: Traditional and reform approaches to teaching and their impact on student learning. Routledge.
Boaler, J., & Brodie, K. (2004). The importance, nature and impact of teacher questions. In D. E. McDougall & J. A. Ross (Eds.), Proceedings of the 26th annual meeting of the North American Chapter of the International Group for the Psychology of Mathematics Education (Vol. 2, pp. 773-782). Toronto: OISE/UT. Carpenter, T. P., Fennema, E., & Franke, M. L. (1996). Cognitively guided instruction: A knowledge base for reform in primary mathematics instruction. The Elementary School Journal, 97(1), 3-20.
Carpenter, T. P., Fennema, E., Franke, M. L., Levi, L., & Empson, S. B. (1999). Children's mathematics: Cognitively guided instruction. Portsmouth, NH: Heinemann.
Carpenter, T. P., & Lehrer, R. (1999). Teaching and learning mathematics with understanding. In E. Fennema & T. A. Romberg (Eds.), Mathematics classrooms that promote understanding (pp. 19-32). Mahwah, NJ: Lawrence Erlbaum Associates.
Craik, F. I., & Lockhart, R. S. (1972). Levels of processing: A framework for memory research. Journal of Verbal Learning and Verbal Behavior, 11(6), 671-684.
Driscoll, M. P. (2005). Psychology of learning for instruction (3rd ed.). Boston: Allyn and Bacon.
Flavell, J. H. (1979). Metacognition and cognitive monitoring: A new area of cognitive-developmental inquiry. American Psychologist, 34(10), 906-911.
Hiebert, J., & Carpenter, T. P. (1992). Learning and teaching with understanding. In D. A. Grouws (Ed.), Handbook of research on mathematics teaching and learning (pp. 65-97). New York: Macmillan.
Hiebert, J., Carpenter, T. P., Fennema, E., Fuson, K. C., Wearne, D., Murray, H., ... & Human, P. (1997). Making sense: Teaching and learning mathematics with understanding. Portsmouth, NH: Heinemann.
Lyman, F. (1981). The responsive classroom discussion: The inclusion of all students. In A. S. Anderson (Ed.), Mainstreaming Digest (pp. 109-113). College Park: University of Maryland Press.
Piaget, J. (1952). The origins of intelligence in children. New York: International Universities Press.
Rowe, M. B. (1986). Wait time: Slowing down may be a way of speeding up! Journal of Teacher Education, 37(1), 43- 50.
Shepard, L. A. (2000). The role of assessment in a learning culture. Educational Researcher, 29(7), 4-14.
Smith, M. S., & Stein, M. K. (2011). 5 practices for orchestrating productive mathematics discussions. Reston, VA: National Council of Teachers of Mathematics.
#### **Social Media.**
Research in mathematics education highlights the significance of taking students' ideas seriously, demonstrating how this approach enhances conceptual understanding, problem-solving abilities, and overall mathematical achievement. Rooted in constructivist learning theory, this method engages crucial cognitive processes like schema formation, metacognition, and elaborative rehearsal. By connecting students’ informal knowledge with formal mathematical concepts, educators can establish a robust foundation for advanced mathematical thinking. Studies show that when instruction is based on students' thinking, learners exhibit superior problem-solving skills and a deeper conceptual grasp than traditional teaching methods.
Join us in exploring these powerful teaching approaches and their impact on mathematical thinking and achievement!
-

@ 57d1a264:69f1fee1
2025-03-29 18:02:16
> This UX research has been redacted by @iqra from the Bitcoin.Design [community](https://discord.gg/K7aQ5PErht), and shared for review and feedback! Don't be shy, share your thoughts.

- - -
## 1️⃣ Introduction
#### Project Overview
📌 **Product:** BlueWallet (Bitcoin Wallet)
📌 **Goal:** Improve onboarding flow and enhance accessibility for a better user experience.
📌 **Role:** UX Designer
📌 **Tools Used:** Figma, Notion
#### Why This Case Study?
🔹 BlueWallet is a self-custodial Bitcoin wallet, but **users struggle with onboarding due to unclear instructions**.
🔹 **Accessibility issues** (low contrast, small fonts) create **barriers for visually impaired users**.
🔹 Competitors like **Trust Wallet and MetaMask offer better-guided onboarding**.
This case study presents **UX/UI improvements** to make BlueWallet **more intuitive and inclusive**.
- - -
## 2️⃣ Problem Statement: Why BlueWalletʼs Onboarding Needs Improvement
#### 🔹 **Current Challenges:**
1️⃣ **Onboarding Complexity** - BlueWallet lacks **step-by-step guidance**, leaving users confused about wallet creation and security.
 
2️⃣ **No Educational Introduction** - Users land directly on the wallet screen with **no explanation of private keys, recovery phrases, or transactions**.
3️⃣ **Transaction Flow Issues** - Similar-looking **"Send" and "Receive" buttons** cause confusion.
4️⃣ **Poor Accessibility** - Small fonts and low contrast make navigation difficult.
#### 🔍 **Impact on Users:**
**Higher drop-off rates** due to frustration during onboarding.
**Security risks** as users skip key wallet setup steps.
**Limited accessibility** for users with visual impairments.
#### 📌 **Competitive Gap:**
Unlike competitors (Trust Wallet, MetaMask), BlueWallet does not offer:
✅ A guided onboarding process
✅ Security education during setup
✅ Intuitive transaction flow
    
Somehow, this wallet has much better UI than the BlueWallet Bitcoin wallet.
- - -
## 3️⃣ User Research & Competitive Analysis
#### User Testing Findings
🔹 Conducted usability testing with **5 users** onboarding for the first time.
🔹 **Key Findings:**
✅ 3 out of 5 users **felt lost** due to missing explanations.
✅ 60% **had trouble distinguishing transaction buttons**.
✅ 80% **found the text difficult to read** due to low contrast.
#### Competitive Analysis
We compared BlueWallet with top crypto wallets:
| Wallet | Onboarding UX | Security Guidance | Accessibility Features |
|---|---|---|---|
| BlueWallet | ❌ No guided onboarding | ❌ Minimal explanation | ❌ Low contrast, small fonts |
| Trust Wallet | ✅ Step-by-step setup | ✅ Security best practices | ✅ High contrast UI |
| MetaMask | ✅ Interactive tutorial | ✅ Private key education | ✅ Clear transaction buttons |
📌 **Key Insight:** BlueWallet lacks **guided setup and accessibility enhancements**, making it harder for beginners.
## 📌 User Persona
To better understand the users facing onboarding challenges, I developed a **persona** based on research and usability testing.
#### 🔹 Persona 1: Alex Carter (Bitcoin Beginner & Investor)
👤 **Profile:**
- **Age:** 28
- **Occupation:** Freelance Digital Marketer
- **Tech Knowledge:** Moderate - Familiar with online transactions, new to Bitcoin)
- **Pain Points:**
- Finds **Bitcoin wallets confusing**.
- - Doesnʼt understand **seed phrases & security features**.
- - **Worried about losing funds** due to a lack of clarity in transactions.
📌 **Needs:**
✅ A **simple, guided** wallet setup.
✅ **Clear explanations** of security terms (without jargon).
✅ Easy-to-locate **Send/Receive buttons**.
📌 **Persona Usage in Case Study:**
- Helps define **who we are designing for**.
- Guides **design decisions** by focusing on user needs.
#### 🔹 Persona 2: Sarah Mitchell (Accessibility Advocate & Tech Enthusiast)
👤 **Profile:**
- **Age:** 35
- **Occupation:** UX Researcher & Accessibility Consultant
- **Tech Knowledge:** High (Uses Bitcoin but struggles with accessibility barriers)
📌 **Pain Points:**
❌ Struggles with small font sizes & low contrast.
❌ Finds the UI difficult to navigate with a screen reader.
❌ Confused by identical-looking transaction buttons.
📌 **Needs:**
✅ A **high-contrast UI** that meets **WCAG accessibility standards**.
✅ **Larger fonts & scalable UI elements** for better readability.
✅ **Keyboard & screen reader-friendly navigation** for seamless interaction.
📌 **Why This Persona Matters:**
- Represents users with visual impairments who rely on accessible design.
- Ensures the design accommodates inclusive UX principles.
- - -
## 4️⃣ UX/UI Solutions & Design Improvements
#### 📌 Before (Current Issues)
❌ Users land **directly on the wallet screen** with no instructions.
❌ **"Send" & "Receive" buttons look identical** , causing transaction confusion.
❌ **Small fonts & low contrast** reduce readability.
#### ✅ After (Proposed Fixes)
✅ **Step-by-step onboarding** explaining wallet creation, security, and transactions.
✅ **Visually distinct transaction buttons** (color and icon changes).
✅ **WCAG-compliant text contrast & larger fonts** for better readability.
#### 1️⃣ Redesigned Onboarding Flow
✅ Added a **progress indicator** so users see where they are in setup.
✅ Used **plain, non-technical language** to explain wallet creation & security.
✅ Introduced a **"Learn More" button** to educate users on security.
#### 2️⃣ Accessibility Enhancements
✅ Increased **contrast ratio** for better text readability.
✅ Used **larger fonts & scalable UI elements**.
✅ Ensured **screen reader compatibility** (VoiceOver & TalkBack support).
#### 3️⃣ Transaction Flow Optimization
✅ Redesigned **"Send" & "Receive" buttons** for clear distinction.
✅ Added **clearer icons & tooltips** for transaction steps.
## 5️⃣ Wireframes & Design Improvements:
#### 🔹 Welcome Screen (First Screen When User Opens Wallet)
**📌 Goal: Give a brief introduction & set user expectations**
✅ App logo + **short tagline** (e.g., "Secure, Simple, Self-Custody Bitcoin Wallet")
✅ **1-2 line explanation** of what BlueWallet is (e.g., "Your gateway to managing Bitcoin securely.")
✅ **"Get Started" button** → Le ads to **next step: Wallet Setup**
✅ **"Already have a wallet?"** → Import option
🔹 **Example UI Elements:**
- BlueWallet Logo
- **Title:** "Welcome to BlueWallet"
- **Subtitle:** "Easily store, send, and receive Bitcoin."
- CTA: "Get Started" (Primary) | "Import Wallet" (Secondary)

#### 🔹 Screen 2: Choose Wallet Type (New or Import)
**📌 Goal: Let users decide how to proceed**
✅ **Two clear options:**
- **Create a New Wallet** (For first-time users)
- **Import Existing Wallet** (For users with a backup phrase)
✅ Brief explanation of each option
🔹 **Example UI Elements:
- **Title:** "How do you want to start?"
- **Buttons:** "Create New Wallet" | "Import Wallet"

#### 🔹 Screen 3: Security & Seed Phrase Setup (Critical Step)
**📌 Goal: Educate users about wallet security & backups**
✅ Explain **why seed phrases are important**
✅ **Clear step-by-step instructions** on writing down & storing the phrase
✅ **Warning:** "If you lose your recovery phrase, you lose access to your wallet."
✅ **CTA:** "Generate Seed Phrase" → Next step
🔹 **Example UI Elements:
- Title:** "Secure Your Wallet"
- **Subtitle:** "Your seed phrase is the key to your Bitcoin. Keep it safe!"
- **Button:** "Generate Seed Phrase"

## 🔹 Screen 4: Seed Phrase Display & Confirmation
**📌 Goal: Ensure users write down the phrase correctly**
✅ Display **12- or 24-word** seed phrase
✅ **“I have written it downˮ checkbox** before proceeding
✅ Next screen: **Verify seed phrase** (drag & drop, re-enter some words)
🔹 **Example UI Elements:**
- **Title:** "Write Down Your Seed Phrase"
- List of 12/24 Words (Hidden by Default)
- **Checkbox:** "I have safely stored my phrase"
- **Button:** "Continue"

### 🔹 Screen 5: Wallet Ready! (Final Step)
**📌 Goal: Confirm setup & guide users on next actions**
✅ **Success message** ("Your wallet is ready!")
✅ **Encourage first action:**
- “Receive Bitcoinˮ → Show wallet address
- “Send Bitcoinˮ → Walkthrough on making transactions
✅ Short explainer: Where to find the Send/Receive buttons
🔹 **Example UI Elements:**
- **Title:** "You're All Set!"
- **Subtitle:** "Start using BlueWallet now."
- **Buttons:** "Receive Bitcoin" | "View Wallet"

- - -
## 5️⃣ Prototype & User Testing Results
🔹 **Created an interactive prototype in Figma** to test the new experience.
🔹 **User Testing Results:**
✅ **40% faster onboarding completion time.**
✅ **90% of users found transaction buttons clearer.**
🔹 **User Feedback:**
✅ “Now I understand the security steps clearly.ˮ
✅ “The buttons are easier to find and use.ˮ
- - -
## 6️⃣ Why This Matters: Key Takeaways
📌 **Impact of These UX/UI Changes:**
✅ **Reduced user frustration** by providing a step-by-step onboarding guide.
✅ **Improved accessibility** , making the wallet usable for all.
✅ **More intuitive transactions** , reducing errors.
- - -
## 7️⃣ Direct link to figma file and Prototype
Figma file: [https://www.figma.com/design/EPb4gVgAMEgF5GBDdtt81Z/Blue-Wallet-UI-
Improvements?node-id=0-1&t=Y2ni1SfvuQQnoB7s-1](https://www.figma.com/design/EPb4gVgAMEgF5GBDdtt81Z/Blue-Wallet-UI-
Improvements?node-id=0-1&t=Y2ni1SfvuQQnoB7s-1)
Prototype: [https://www.figma.com/proto/EPb4gVgAMEgF5GBDdtt81Z/Blue-Wallet-UI-
Improvements?node-id=1-2&p=f&t=FndTJQNCE7nEIa84-1&scaling=scale-
down&content-scaling=fixed&page-id=0%3A1&starting-point-node-
id=1%3A2&show-proto-sidebar=1](https://www.figma.com/proto/EPb4gVgAMEgF5GBDdtt81Z/Blue-Wallet-UI-
Improvements?node-id=1-2&p=f&t=FndTJQNCE7nEIa84-1&scaling=scale-
down&content-scaling=fixed&page-id=0%3A1&starting-point-node-
id=1%3A2&show-proto-sidebar=1)
Original PDF available from [here](https://cdn.discordapp.com/attachments/903126164795699212/1355561527394173243/faf3ee46-b501-459c-ba0e-bf7e38843bc8_UX_Case_Study__1.pdf?ex=67e9608d&is=67e80f0d&hm=d0c386ce2cfd6e0ebe6bde0a904e884229f52bf547adf1f7bc884e17bb4aa59e&)
originally posted at https://stacker.news/items/928822
-

@ 57d1a264:69f1fee1
2025-03-29 17:15:17

- Once activated, "Accept From Any Mint” is the default setting. This is the easiest way to get started, let's the user start acceptance Cashu ecash just out of the box.
- If someone does want to be selective, they can choose “Accept From Trusted Mints,” and that brings up a field where they can add specific mint URLs they trust.
- “Find a Mint” section on the right with a button links directly to bitcoinmints.com, already filtered for Cashu mints, so users can easily browse options.
- Mint info modal shows mint technical details stuff from the NUT06 spec. Since this is geared towards the more technical users I left the field names and NUT number as-is instead of trying to make it more semantic.
originally posted at https://stacker.news/items/928800
-

@ 866e0139:6a9334e5
2025-04-05 11:00:25
***
**Autor:** **[CJ Hopkins.](https://cjhopkins.substack.com/)** *Dieser Beitrag wurde mit dem **[Pareto-Client](https://pareto.space/read)** geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden **[hier.](https://pareto.space/read?category=friedenstaube)***
Dieser Beitrag erschien zuerst auf dem **[Substack-Blog des Autors.](https://cjhopkins.substack.com/p/the-war-on-whatever)** 
***
Er soll andauern, was er auch tut. Genau wie der nie endende Krieg in Orwells 1984 wird er vom Imperium gegen seine eigenen Untertanen geführt, aber nicht nur, um die Struktur der Gesellschaft intakt zu halten, sondern in unserem Fall auch, um die Gesellschaft in eine neo-totalitäre global-kapitalistische Dystopie zu verwandeln.
Bist du nicht vertraut mit dem Krieg gegen was auch immer?
Nun ja, okay, du erinnerst dich an den Krieg gegen den Terror.
Du erinnerst dich daran, als die „Freiheit und Demokratie“ von „den Terroristen“ angegriffen wurden und wir keine andere Wahl hatten, als uns unserer demokratischen Rechte und Prinzipien zu entledigen, einen nationalen „Notstand“ auszurufen, die verfassungsmäßigen Rechte der Menschen auszusetzen, einen Angriffskrieg gegen ein Land im Nahen Osten anzuzetteln, das für uns keinerlei Bedrohung darstellte, und unsere Straßen, Bahnhöfe, Flughäfen und alle anderen Orte mit schwer bewaffneten Soldaten zu füllen, denn sonst hätten „die Terroristen gewonnen“. Du erinnerst dich, als wir ein Offshore-Gulag bauten, um verdächtige Terroristen auf unbestimmte Zeit wegzusperren, die wir zuvor zu CIA-Geheimgefängnissen verschleppt hatten, wo wir sie gefoltert und gedemütigt haben, richtig?
Natürlich erinnerst du dich. Wer könnte das vergessen?
***
**DIE FRIEDENSTAUBE FLIEGT AUCH IN IHR POSTFACH!**
***[Hier](https://pareto.space/u/friedenstaube@pareto.space)*** *können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht). Sie wollen der Genossenschaft beitreten oder uns unterstützen? Mehr Infos* ***[hier](https://pareto.space/a/naddr1qqsxydty8qek2wpsvyck2wphxajrvefjvesngcfhxenrgdty89nrzvgzyzrxuqfepp2e79w9aluaz2252vyz7qdpld05pgjmeurhdgm2jv6w2qcyqqq823cpp4mhxue69uhkummn9ekx7mqprpmhxue69uhkummnw3ezuurpwfjhgmewwdcxzcm9qythwumn8ghj7mn0wd68ytnsv9ex2ar09e6x7amwqyf8wumn8ghj7mmxve3ksctfdch8qatzqythwumn8ghj7urpwfjhgmewdehhxarjxyhxxmmdszcvqk)*** *oder am Ende des Textes.*
***
Erinnerst du dich, als die National Security Agency keine andere Wahl hatte, als ein geheimes „Terroristen-Überwachungsprogramm“ einzurichten, um Amerikaner auszuspionieren, oder sonst „hätten die Terroristen gewonnen“? Oder wie wäre es mit den „Anti-Terror“-Unterleibsuntersuchungen der TSA, der Behörde für Transportsicherheit, die nach über zwanzig Jahren immer noch in Kraft sind?
Und was ist mit dem Krieg gegen den Populismus? An den erinnerst du dich vielleicht nicht so gut.
Ich erinnere mich, denn ich habe zwei Bücher dazu veröffentlicht. Er begann im Sommer 2016, als das Imperium erkannte, dass „rechte Populisten“ die „Freiheit und Demokratie“ in Europa bedrohten und Trump in den USA auf dem Vormarsch war. Also wurde ein weiterer „Notstand“ ausgerufen – diesmal von der Gemeinschaft der Geheimdienste, den Medien, der akademischen Welt und der Kulturindustrie. Ja, genau, es war wieder einmal an der Zeit, unsere demokratischen Prinzipien hintanzustellen, „Hassrede“ in sozialen Medien zu zensieren, die Massen mit lächerlicher offizieller Propaganda über „Russiagate,“ „Hitlergate“ und so weiter zu bombardieren – sonst hätten „die Rechtspopulisten gewonnen.“
Der Krieg gegen den Populismus gipfelte in der Einführung des Neuen Normalen Reichs.

Im Frühjahr 2020 rief das Imperium einen globalen „gesundheitlichen Ausnahmezustand“ aus, als Reaktion auf ein Virus mit einer Überlebensrate von etwa 99,8 Prozent. Das Imperium hatte keine andere Wahl, als ganze Gesellschaften abzuriegeln, jeden dazu zu zwingen, in der Öffentlichkeit medizinisch aussehende Masken zu tragen, die Öffentlichkeit mit Propaganda und Lügen zu bombardieren, die Menschen dazu zu nötigen, sich einer Reihe experimenteller mRNA-„Impfungen“ zu unterziehen, Proteste gegen ihre Dekrete zu verbieten und systematisch diejenigen zu zensieren und zu verfolgen, die es wagten, ihre erfundenen „Fakten“ in Frage zu stellen oder ihr totalitäres Programm zu kritisieren.
Das Imperium hatte keine andere Wahl, als das alles zu tun, denn sonst hätten „die Covid-Leugner, die Impfgegner, die Verschwörungstheoretiker und all die anderen Extremisten gewonnen.“
Ich bin mir ziemlich sicher, dass du dich an all das erinnerst.
Und jetzt … nun, hier sind wir. Ja, du hast es erraten – es ist wieder einmal an der Zeit, kräftig auf die US-Verfassung und die Meinungsfreiheit zu scheißen, Menschen in irgendein salvadorianisches Höllenloch abzuschieben, das wir angemietet haben, weil ein Polizist ihre Tattoos nicht mochte, Universitätsstudenten wegen ihrer Anti-Israel-Proteste festzunehmen und zu verschleppen und natürlich die Massen mit Lügen und offizieller Propaganda zu bombardieren, denn … okay, alle zusammen jetzt: „sonst hätten die antisemitischen Terroristen und venezolanischen Banden gewonnen!“
Fängst du an, ein Muster zu erkennen? Ja? Willkommen beim Krieg gegen-was-auch-immer!
Wenn du die Zusammenhänge noch nicht ganz siehst, okay, lass es mich noch einmal ganz simpel erklären.
Das globale ideologische System, in dem wir alle leben, wird totalitär. (Dieses System ist der globale Kapitalismus, aber nenne es, wie du willst. Es ist mir scheißegal.) Es reißt die Simulation der Demokratie nieder, die es nicht mehr aufrechterhalten muss. Der Kalte Krieg ist vorbei. Der Kommunismus ist tot. Der globale Kapitalismus hat keine externen Feinde mehr. Also muss er die Massen nicht mehr mit demokratischen Rechten und Freiheiten besänftigen. Deshalb entzieht er uns diese Rechte nach und nach und konditioniert uns darauf, ihren Verlust hinzunehmen.
Er tut dies, indem er eine Reihe von „Notständen“ inszeniert, jeder mit einer anderen „Bedrohung“ für die „Demokratie,“ die „Freiheit,“ „Amerika“ oder „den Planeten“ – oder was auch immer. Jeder mit seinen eigenen „Monstern,“ die eine so große Gefahr für die „Freiheit“ oder was auch immer darstellen, dass wir unsere verfassungsmäßigen Rechte aufgeben und die demokratischen Werte ad absurdum führen müssen, denn: sonst „würden die Monster gewinnen.“

Es tut dies, indem es sein Antlitz von „links“ nach „rechts,“ dann zurück nach „links“, und dann zurück nach „rechts,“ dann nach „links“ und so weiter neigt, weil es unsere Kooperation dafür benötigt. Nicht die Kooperation von uns allen auf einmal. Nur eine kooperative demografische Gruppe auf einmal.
Es ist dabei erfolgreich – also das System – indem es unsere Angst und unseren Hass instrumentalisiert. Dem System ist es völlig egal, ob wir uns als „links“ oder „rechts“ identifizieren, aber es braucht uns gespalten in „links“ und „rechts,“ damit es unsere Angst und unseren Hass aufeinander nähren kann … eine Regierung, ein „Notfall,“ ein „Krieg“ nach dem anderen.
Da hast du es. Das ist der Krieg gegen was auch immer. Noch simpler kann ich es nicht erklären.
Oh, und noch eine letzte Sache … wenn du einer meiner ehemaligen Fans bist, wie Rob, die über meine „Einsichten“ oder Loyalitäten oder was auch immer verwirrt sind … nun, der Text, den du gerade gelesen hast, sollte das für dich klären. Ich stehe auf keiner Seite. Überhaupt keiner. Aber ich habe ein paar grundlegende demokratische Prinzipien. Und die richten sich nicht danach, was gerade populär ist oder wer im Weißen Haus sitzt.
Die Sache ist die: Ich muss mich morgens im Spiegel anschauen können ohne dort einen Heuchler oder … du weißt schon, einen Feigling zu sehen.
(Aus dem Amerikanischen übersetzt von **[René Boyke](https://covid-justiz.de/)**).
***
*CJ Hopkins ist ein US-amerikanischer [Dramatiker](https://deutsch.wikibrief.org/wiki/Playwright "Dramatiker"), [Romanautor](https://deutsch.wikibrief.org/wiki/Novelist "Romanschriftsteller") und [politischer Satiriker](https://deutsch.wikibrief.org/wiki/Political_satire "Politische Satire"). Zu seinen Werken zählen die Stücke Horse Country, Screwmachine/Eyecandy und [The Extremists](https://deutsch.wikibrief.org/wiki/The_Extremists_%28play%29 "Die Extremisten (Spiel)"). Er hat sich als profilierter Kritiker des Corona-Regimes profiliert und veröffentlicht regelmäßig auf seinem* ***[Substack-Blog.](https://cjhopkins.substack.com/)***
Sein aktuelles Buch:
<https://x.com/CJHopkins_Z23/status/1907795633689264530>
Hier in einem aktuellen Gespräch: 
<https://www.youtube.com/watch?v=wF-G32P0leI>
***
**LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!**
***[Hier](https://pareto.space/u/friedenstaube@pareto.space)*** *können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt. (Vorerst alle, da wir den Mailversand testen, später ca. drei Mails pro Woche.)*
Schon jetzt können Sie uns unterstützen:
* Für **50 CHF/EURO** bekommen Sie ein Jahresabo der Friedenstaube.
* Für **120 CHF/EURO** bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
* Für **500 CHF/EURO** werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
* Ab **1000 CHF** werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
**Für Einzahlungen in CHF (Betreff: Friedenstaube):**
**Für Einzahlungen in Euro:**
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
**Betreff: Friedenstaube**
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: <milosz@pareto.space>
***
**Sie sind noch nicht auf** [Nostr](https://nostr.com/) **and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil!** Erstellen Sie sich einen Account auf [Start.](https://start.njump.me/) Weitere Onboarding-Leitfäden gibt es im [Pareto-Wiki.](https://wiki.pareto.space/de/home)
-

@ 5ffb8e1b:255b6735
2025-03-29 13:57:02
As a fellow Nostrich you might have noticed some of my #arlist posts. It is my effort to curate artists that are active on Nostr and make it easier for other users to find content that they are interested in.
By now I have posted six or seven posts mentioning close to fifty artists, the problem so far is that it's only a list of handles and it is up to reader to click on each in order to find out what are the artist behind the names all about. Now I am going to start creating blog posts with a few artists mentioned in each, with short descriptions of their work and an image or to.
I would love to have some more automated mode of curation but I still couldn't figure out what is a good way for it. I've looked at Listr, Primal custom feeds and Yakihonne curations but none seem to enable me to make a list of npubs that is then turned into a feed that I could publicly share for others to views.
Any advice on how to achieve this is VERY welcome !
And now lets get to the first batch of artists I want to share with you.
### Eugene Gorbachenko ###
nostr:npub1082uhnrnxu7v0gesfl78uzj3r89a8ds2gj3dvuvjnw5qlz4a7udqwrqdnd
Artist from Ukrain creating amazing realistic watercolor paintings.
He is very active on Nostr but is very unnoticed for some stange reason. Make sure to repost the painting that you liked the most to help other Nostr users to discover his great art.
![!(image)[https://m.primal.net/PxJc.png]]()
### Siritravelsketch ###
nostr:npub14lqzjhfvdc9psgxzznq8xys8pfq8p4fqsvtr6llyzraq90u9m8fqevhssu
a a lovely lady from Thailand making architecture from all around the world spring alive in her ink skethes. Dynamic lines gives it a dreamy magical feel, sometimes supported by soft watercolor strokes takes you to a ferytale layer of reality.
![!(image)[https://m.primal.net/PxJj.png]]()
### BureuGewas ###
nostr:npub1k78qzy2s9ap4klshnu9tcmmcnr3msvvaeza94epsgptr7jce6p9sa2ggp4
a a master of the clasic oil painting. From traditional still life to modern day subjects his paintings makes you feel the textures and light of the scene more intense then reality itself.
![!(image)[https://m.primal.net/PxKS.png]]()
You can see that I'm no art critic, but I am trying my best. If anyone else is interested to join me in this curration adventure feel free to reach out !
With love, Agi Choote
-

@ a5142938:0ef19da3
2025-04-05 10:18:18
Discover the materials accepted or not in the products listed on this site.
### ✅ Natural Materials
Materials of plant, animal, or mineral origin, without chemical transformation that alters their molecular structure.
**🌱 Main Criteria:**
- Biodegradability
- Non-toxicity
- Naturally occurring and recquiring minimal transformation
**🔍 List of Natural Materials:**
- Natural rubber
- Hemp
- Cotton
- Leather
- Cork
- Linen
- Wool
- Silk
- … (Other materials)
⚠️ Although natural, these materials can have negative impacts depending on their production conditions (pesticide pollution, excessive water consumption, chemical treatments, animal exploitation, etc.). These impacts are mentionned in the description of each material.
Organic, chemical-free versions of these materials are prioritized for product listings on this site.
Conventional versions are only referenced when no more sustainable alternative has yet been found for that product category.
---
### 🚫 Non-Natural Materials
Synthetic or heavily modified materials, often derived from petrochemicals.
**📌 Main Issues:**
- Microplastic emissions
- Dependence on fossil fuels
- Poor biodegradability
**🔍 List of Non-Natural Materials:**
- Polyester
- Polyamide
- Acrylic
- Elastane
- Viscose
- Silicone
- … (Other materials)
⚠️ These materials are not accepted on this site. However, they may be present in certain listed products if:
- they are used in removable accessories (e.g., elastics, buttons—often not listed in the product’s composition by the brand) that can be detached for recycling or composting, and
- no 100% natural alternative has yet been identified for that product category.
In such cases, a warning will be displayed on the product page.
---
This article is published on [origin-nature.com](https://www.origin-nature.com/post/pnco0inysorhojxvsyil3/)
🌐 [Voir cet article en français](https://www.origine-nature.com/post/ftjhuxe9mvxkhoedyz36i/)
-

@ 592295cf:413a0db9
2025-03-29 10:59:52
The journey starts from the links in this article
[nostr-quick-start-guide](https://spatianostra.com/nostr-quick-start-guide/)
Starting from these links building a simple path should not cover everything, because impossible.
Today I saw that Verbiricha in his workshop on his channel used nstart, but then I distracted
And I didn't see how he did it.
-----
Go to [nstart.me](https://nstart.me/) and read:
Each user is identified by a cryptographic keypair
Public key, Private key (is a lot of stuff)
You can insert a nickname and go, the nickname is not unique
there is a email backup things interesting, but a little boring, i try to generate an email
doesn't even require a strong password ok.
I received the email, great, it shows me the nsec encrypted in clear,
Send a copy of the file with a password, which contains the password encrypted key
I know and I know it's a tongue dump.
## Multi signer bunker
That's stuff, let's see what he says.
They live the private key and send it to servers and you can recompose it to login at a site
of the protocol nostr. If one of these servers goes offline you have the private key
that you downloaded first and then reactivate a bunker.
All very complicated.
But if one of the servers goes offline, how can I remake the split? Maybe he's still testing.
Nobody tells you where these bunkers are.
Okay I have a string that is my bunker (buker://), I downloaded it, easy no, now will tell me which client accepts the bunker.. .
## Follow someone before you start?
Is a cluster of 5 people Snowden, Micheal Dilger, jb55, Fiatjaf, Dianele.
I choice Snowden profile, or you can select multiple profiles, extra wild.
## Now select 5 clients
### *Coracle, Chachi, Olas, Nostur, Jumble*
### The first is *Coracle*
Login, ok I try to post a note and signing your note the spin does not end.
Maybe the bunker is diffective.
### Let's try *Chachi*
Simpler than Coracle, it has a type login that says bunker.
see if I can post
It worked, cool, I managed to post in a group.
## Olas is an app but also a website, but on the website requires an extension, which I do not have with this account.
> If I download an app how do I pass the bunker on the phone, is it still a password, a qrcode, a qrcode + password, something
> like that, but many start from the phone so maybe it's easy for them.
> I try to download it and see if it allows me to connect with a bunker.
> Okay I used private-qrcode and it worked, I couldn't do it directly from Olas because it didn't have permissions and the qrcode was < encrypted, so I went to the same site and had the bunker copied and glued on Olas
**Ok then I saw that there was the qrcode image of the bunker for apps** lol moment
Ok, I liked it, I can say it's a victory.
Looks like none of Snowden's followers are *Olas*'s lover, maybe the smart pack has to predict a photographer or something like that.
Okay I managed to post on *Olas*, so it works, Expiration time is broken.
### As for *Nostur*, I don't have an ios device so I'm going to another one.
### Login with *Jumble*, it works is a web app
I took almost an hour to do the whole route.
But this was just one link there are two more
# Extensions nostr NIP-07
### The true path is [nip-07-browser-extensions | nostr.net](https://nostr.net/#nip-07-browser-extensions)
There are 19 links, maybe there are too many?
I mention the most famous, or active at the moment
1. **Aka-profiles**: [Aka-profiles](https://github.com/neilck/aka-extension)
Alby I don't know if it's a route to recommend
2. **Blockcore** [Blockcore wallet](https://chromewebstore.google.com/detail/blockcore-wallet/peigonhbenoefaeplkpalmafieegnapj)
3. **Nos2x** [Nos2x](https://github.com/fiatjaf/nos2x?tab=readme-ov-file)
4. **Nos2xfox** (fork for firefox) [Nos2xfox](https://diegogurpegui.com/nos2x-fox/)
Nostore is (archived, read-only)
5. **Nostrame** [Nostrame](https://github.com/Anderson-Juhasc/nostrame)
6. **Nowser** per IOS [Nowser](https://github.com/haorendashu/nowser)
7. **One key** (was tricky) [One key](https://chromewebstore.google.com/detail/onekey/jnmbobjmhlngoefaiojfljckilhhlhcj)
Another half hour to search all sites
# Nostrapps
Here you can make paths
### Then nstart selects Coracle, Chachi, Olas,Nostur and Jumble
Good apps might be Amethyst, 0xchat, Yakihonne, Primal, Damus
for IOS maybe: Primal, Olas, Damus, Nostur, Nos-Social, Nostrmo
On the site there are some categories, I select some with the respective apps
Let's see the categories
Go to [Nostrapps](https://nostrapps.com/) and read:
## Microbbloging: Primal
## Streaming: **Zap stream**
## Blogging: **Yakihonne**
## Group chat: **Chachi**
## Community: **Flotilla**
## Tools: **Form** *
## Discovery: **Zapstore** (even if it is not in this catrgory)
## Direct Message: **0xchat**
-

@ 57d1a264:69f1fee1
2025-03-29 09:31:13
> "THE NATURE OF BITCOIN IS SUCH THAT ONCE VERSION 0.1 WAS RELEASED, THE CORE DESIGN WAS SET IN STONE FOR THE REST OF ITS LIFETIME."
<sub>- SATOSHI NAKAMOTO</sub>



"Reborn" is inspired by my Bitcoin journey and the many other people whose lives have been changed by Bitcoin. I’ve carved the hand in the “Gyan Mudra” or the “Mudra of Wisdom or Knowledge,” with an Opendime grasped between thumb and index finger alluding to the pursuit of Bitcoin knowledge. The hand emerges from rough, choppy water, and I've set the hand against an archway, through which, the copper leaf hints at the bright orange future made possible by Bitcoin.
Materials: Carrara Marble, Copper leaf, Opendime
Dimensions: 6" x 9" x 13"
Price: $30,000 or BTC equivalent
Enquire: https://www.vonbitcoin.com/available-works
X: https://x.com/BVBTC/status/1894463357316419960/photo/1
originally posted at https://stacker.news/items/928510
-

@ 2183e947:f497b975
2025-03-29 02:41:34
Today I was invited to participate in the private beta of a new social media protocol called Pubky, designed by a bitcoin company called Synonym with the goal of being better than existing social media platforms. As a heavy nostr user, I thought I'd write up a comparison.
I can't tell you how to create your own accounts because it was made very clear that only *some* of the software is currently open source, and how this will all work is still a bit up in the air. The code that *is* open source can be found here: https://github.com/pubky -- and the most important repo there seems to be this one: https://github.com/pubky/pubky-core
You can also learn more about Pubky here: https://pubky.org/
That said, I used my invite code to create a pubky account and it seemed very similar to onboarding to nostr. I generated a private key, backed up 12 words, and the onboarding website gave me a public key.
Then I logged into a web-based client and it looked a lot like twitter. I saw a feed for posts by other users and saw options to reply to posts and give reactions, which, I saw, included hearts, thumbs up, and other emojis.
Then I investigated a bit deeper to see how much it was like nostr. I opened up my developer console and navigated to my networking tab, where, if this was nostr, I would expect to see queries to relays for posts. Here, though, I saw one query that seemed to be repeated on a loop, which went to a single server and provided it with my pubkey. That single query (well, a series of identical queries to the same server) seemed to return all posts that showed up on my feed. So I infer that the server "knows" what posts to show me (perhaps it has some sort of algorithm, though the marketing material says it does not use algorithms) and the query was on a loop so that if any new posts came in that the server thinks I might want to see, it can add them to my feed.
Then I checked what happens when I create a post. I did so and looked at what happened in my networking tab. If this was nostr, I would expect to see multiple copies of a signed messaged get sent to a bunch of relays. Here, though, I saw one message get sent to the same server that was populating my feed, and that message was not signed, it was a plaintext copy of my message.
I happened to be in a group chat with John Carvalho at the time, who is associated with pubky. I asked him what was going on, and he said that pubky is based around three types of servers: homeservers, DHT servers, and indexer servers. The homeserver is where you create posts and where you query for posts to show on your feed. DHT servers are used for censorship resistance: each user creates an entry on a DHT server saying what homeserver they use, and these entries are signed by their key.
As for indexers, I think those are supposed to speed up the use of the DHT servers. From what I could tell, indexers query DHT servers to find out what homeservers people use. When you query a homeserver for posts, it is supposed to reach out to indexer servers to find out the homeservers of people whose posts the homeserver decided to show you, and then query those homeservers for those posts. I believe they decided not to look up what homeservers people use directly on DHT servers directly because DHT servers are kind of slow, due to having to store and search through all sorts of non-social-media content, whereas indexers only store a simple db that maps each user's pubkey to their homeserver, so they are faster.
Based on all of this info, it seems like, to populate your feed, this is the series of steps:
- you tell your homeserver your pubkey
- it uses some sort of algorithm to decide whose posts to show you
- then looks up the homeservers used by those people on an indexer server
- then it fetches posts from their homeservers
- then your client displays them to you
To create a post, this is the series of steps:
- you tell your homeserver what you want to say to the world
- it stores that message in plaintext and merely asserts that it came from you (it's not signed)
- other people can find out what you said by querying for your posts on your homeserver
Since posts on homeservers are not signed, I asked John what prevents a homeserver from just making up stuff and claiming I said it. He said nothing stops them from doing that, and if you are using a homeserver that starts acting up in that manner, what you should do is start using a new homeserver and update your DHT record to point at your new homeserver instead of the old one. Then, indexers should update their db to show where your new homeserver is, and the homeservers of people who "follow" you should stop pulling content from your old homeserver and start pulling it from your new one. If their homeserver is misbehaving too, I'm not sure what would happen. Maybe it could refuse to show them the content you've posted on your new homeserver, keeping making up fake content on your behalf that you've never posted, and maybe the people you follow would never learn you're being impersonated or have moved to a new homeserver.
John also clarified that there is not currently any tooling for migrating user content from one homeserver to another. If pubky gets popular and a big homeserver starts misbehaving, users will probably need such a tool. But these are early days, so there aren't that many homeservers, and the ones that exist seem to be pretty trusted.
Anyway, those are my initial thoughts on Pubky. Learn more here: https://pubky.org/
-

@ 57d1a264:69f1fee1
2025-03-28 10:32:15
Bitcoin.design community is organizing another Designathon, from May 4-18. Let's get creative with bitcoin together. More to come very soon.

The first edition was a bursting success! the website still there https://events.bitcoin.design, and here their previous [announcement](https://bitcoindesign.substack.com/p/the-bitcoin-designathon-2022).
Look forward for this to happen!
Spread the voice:
N: [https://njump.me/nevent1qqsv9w8p93tadlnyx0rkhexj5l48l...](https://njump.me/nevent1qqsv9w8p93tadlnyx0rkhexj5l48lmw9jc7nhhauyq5w3cm4nfsm3mstqtk6m)
X: https://x.com/bitcoin_design/status/1905547407405768927
originally posted at https://stacker.news/items/927650
-

@ 57d1a264:69f1fee1
2025-03-27 10:42:05
What we have been missing in [SN Press kit](https://stacker.news/items/872925/r/Design_r)? Most important, who the press kit is for? It's for us? It's for them? Them, who?
The first few editions of the press kit, I agree are mostly made by us, for us. A way to try to homogenize how we _speek_ out SN into the wild web. A way to have SN voice sync, loud and clear, to send out our message. In this case, I squeezed my mouse, creating a template for us [^1], stackers, to share when talking sales with possible businesses and merchants willing to invest some sats and engage with SN community. Here's the message and the sales pitch, v0.1:
## Reach Bitcoin’s Most Engaged Community – Zero Noise, Pure Signal.













- - -
Contributions to improve would be much appreciated. You can also help by simply commenting on each slide or leaving your feedback below, especially if you are a sale person or someone that has seen similar documents before.
This is the first interaction. Already noticed some issues, for example with the emojis and the fonts, especially when exporting, probably related to a penpot issue. The slides maybe render differently depending on the browser you're using.
- [▶️ Play](https://design.penpot.app/#/view?file-id=cec80257-5021-8137-8005-ef90a160b2c9&page-id=cec80257-5021-8137-8005-ef90a160b2ca§ion=interactions&index=0&interactions-mode=hide&zoom=fit) the file in your browser
- ⬇️ Save the [PDF file](https://mega.nz/file/TsBgkRoI#20HEb_zscozgJYlRGha0XiZvcXCJfLQONx2fc65WHKY)
@k00b it will be nice to have some real data, how we can get some basic audience insights? Even some inputs from Plausible, if still active, will be much useful.
[^1]: Territory founders. FYI: @Aardvark, @AGORA, @anna, @antic, @AtlantisPleb, @av, @Bell_curve, @benwehrman, @bitcoinplebdev, @Bitter, @BlokchainB, @ch0k1, @davidw, @ek, @elvismercury, @frostdragon, @grayruby, @HODLR, @inverselarp, @Jon_Hodl, @MaxAWebster, @mega_dreamer, @mrtali, @niftynei, @nout, @OneOneSeven, @PlebLab, @Public_N_M_E, @RDClark, @realBitcoinDog, @roytheholographicuniverse, @siggy47, @softsimon, @south_korea_ln, @theschoolofbitcoin, @TNStacker. @UCantDoThatDotNet, @Undisciplined
originally posted at https://stacker.news/items/926557
-

@ 57d1a264:69f1fee1
2025-03-27 08:27:44
> The tech industry and its press have treated the rise of billion-scale social networks and ubiquitous smartphone apps as an unadulterated win for regular people, a triumph of usability and empowerment. They seldom talk about what we’ve lost along the way in this transition, and I find that younger folks may not even know how the web used to be.
`— Anil Dash, The Web We Lost, 13 Dec 2012`
https://www.youtube.com/watch?v=9KKMnoTTHJk&t=156s
So here’s a few glimpses of a web that’s mostly faded away: https://www.anildash.com/2012/12/13/the_web_we_lost/
The first step to disabusing them of this notion is for the people creating the next generation of social applications to learn a little bit of history, to know your shit, whether that’s about [Twitter’s business model](http://web.archive.org/web/20180120013123/http://anildash.com/2010/04/ten-years-of-twitter-ads.html) or [Google’s social features](http://web.archive.org/web/20170518203228/http://anildash.com/2012/04/why-you-cant-trust-tech-press-to-teach-you-about-the-tech-industry.html) or anything else. We have to know what’s been tried and failed, what good ideas were simply ahead of their time, and what opportunities have been lost in the current generation of dominant social networks.
originally posted at https://stacker.news/items/926499
-

@ 57d1a264:69f1fee1
2025-03-27 08:11:33
Explore and reimagine programming interfaces beyond text (visual, tactile, spatial).
> _"The most dangerous thought you can have as a creative person is to think you know what you're doing."_
`— Richard Hamming` [^1]
https://www.youtube.com/watch?v=8pTEmbeENF4
For his recent DBX Conference talk, Victor took attendees back to the year 1973, donning the uniform of an IBM systems engineer of the times, delivering his presentation on an overhead projector. The '60s and early '70s were a fertile time for CS ideas, reminds Victor, but even more importantly, it was a time of unfettered thinking, unconstrained by programming dogma, authority, and tradition.

_'The most dangerous thought that you can have as a creative person is to think that you know what you're doing,'_ explains Victor. 'Because once you think you know what you're doing you stop looking around for other ways of doing things and you stop being able to see other ways of doing things. You become blind.' He concludes, 'I think you have to say: _"We don't know what programming is. We don't know what computing is. We don't even know what a computer is."_ And once you truly understand that, and once you truly believe that, then you're free, and you can think anything.'
More details at https://worrydream.com/dbx/
[^1]: Richard Hamming -- [The Art of Doing Science and Engineering, p5](http://worrydream.com/refs/Hamming_1997_-_The_Art_of_Doing_Science_and_Engineering.pdf) (pdf ebook)
originally posted at https://stacker.news/items/926493
-

@ 3ffac3a6:2d656657
2025-04-05 04:55:12
# O Impacto do Namoro com Pelé na Carreira de Xuxa Meneghel
## Disclaimer:
Esse texto foi totalmente escrito pelo ChatGPT, eu apenas pedi que ele fizesse uma pesquisa sobre o tema.
**Introdução:** O relacionamento entre Xuxa Meneghel e Pelé, que durou cerca de seis anos (início dos anos 1980 até 1986), foi um dos mais comentados da década de 1980 ([Xuxa e Pelé: um romance que se tornou inesquecível... | VEJA](https://veja.abril.com.br/coluna/veja-gente/xuxa-e-pele-um-romance-que-se-tornou-inesquecivel-para-os-dois/#:~:text=Um%20dos%20romances%20mais%20comentados,manchetes%20e%20revistas%20de%20fofoca)). Xuxa tinha apenas 17 anos quando começou a namorar o já consagrado “Rei do Futebol”, então com 40 anos ([A história da foto de revista que gerou o namoro de Pelé e Xuxa](https://www.terra.com.br/diversao/gente/a-historia-da-foto-de-revista-que-gerou-o-namoro-de-pele-e-xuxa,c5106b23301f6f0e7c03f38cdf9eb1a06kopa9ho.html#:~:text=Xuxa%20tinha%2017%20anos,a%20primeira%20mulher%2C%20Rosemeri%20Cholbi)) ([Xuxa e Pelé: um romance que se tornou inesquecível... | VEJA](https://veja.abril.com.br/coluna/veja-gente/xuxa-e-pele-um-romance-que-se-tornou-inesquecivel-para-os-dois/#:~:text=O%20jogador%20de%20futebol%20e,um%20relacionamento%20por%20seis%20anos)). Esse romance altamente midiático não só atiçou a curiosidade do público, como também alavancou a carreira de Xuxa de forma significativa. A seguir, detalhamos como o namoro aumentou a visibilidade da apresentadora, quais oportunidades profissionais podem ter tido influência direta de Pelé, o papel da revista *Manchete* e de outras mídias na promoção de sua imagem, se o relacionamento contribuiu para Xuxa conquistar espaços na TV (como o programa **Clube da Criança** e, posteriormente, na Rede Globo) e como mídia e público percebiam o casal – tudo embasado em fontes da época, entrevistas e biografias.
## Aumento da Visibilidade Midiática nos Anos 1980
O namoro com Pelé catapultou Xuxa a um novo patamar de fama. Até então uma modelo em começo de carreira, Xuxa **“se tornou famosa ao aparecer ao lado do esportista de maior status do Brasil”** ([Pelé viveu com Xuxa um namoro intenso afetado por fofocas e indiscrições](https://www.terra.com.br/diversao/gente/pele-viveu-com-xuxa-um-namoro-intenso-afetado-por-fofocas-e-indiscricoes,0c075d1a6be75f53536ad3b70e8e4a01iavthiai.html#:~:text=O%20romance%20come%C3%A7ou%20quando%20ela,de%20maior%20status%20do%20Brasil)). A partir do momento em que o relacionamento se tornou público, ela passou a estampar capas de revistas com frequência e a ser assunto constante na imprensa. Em 20 de dezembro de 1980, a jovem apareceu na capa da revista *Manchete* ao lado de Pelé e outras modelos – um ensaio fotográfico que marcou o primeiro encontro dos dois e deu início à enorme atenção midiática em torno de Xuxa ([Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira](https://aventurasnahistoria.com.br/noticias/reportagem/xuxa-e-pele-o-relacionamento-que-ficou-cravado-na-historia-da-imprensa-brasileira.phtml#:~:text=A%20extinta%20Manchete%20promovia%20uma,Xuxa%2C%20com%20apenas%2017%20anos)) ([Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira](https://aventurasnahistoria.com.br/noticias/reportagem/xuxa-e-pele-o-relacionamento-que-ficou-cravado-na-historia-da-imprensa-brasileira.phtml#:~:text=O%20jantar%20aproximou%20o%20casal,E%20fui%E2%80%9D)). Não por acaso, *“naquele ano, ela foi capa de mais de cem revistas”* ([Xuxa está em paz - revista piauí](https://piaui.folha.uol.com.br/materia/xuxa-esta-em-paz/#:~:text=convidadas%20a%20posar%20ao%20lado,de%20mais%20de%20cem%20revistas)), um indicativo claro de como sua visibilidade explodiu após começar a namorar Pelé. Jornais, revistas de celebridades e programas de fofoca passaram a segui-los de perto; o casal virou sensação nacional, comparado até ao “Casal 20” (dupla glamourosa de uma série de TV americana) pelo seu alto perfil na mídia ([Xuxa e Pelé: um romance que se tornou inesquecível... | VEJA](https://veja.abril.com.br/coluna/veja-gente/xuxa-e-pele-um-romance-que-se-tornou-inesquecivel-para-os-dois/#:~:text=Um%20dos%20romances%20mais%20comentados,manchetes%20e%20revistas%20de%20fofoca)).
Essa exposição intensa colocou Xuxa não apenas sob os holofotes do público, mas também a inseriu nos **bastidores do entretenimento**. Como namorada de Pelé – um dos homens mais conhecidos do mundo – Xuxa passou a frequentar eventos de gala, festas e bastidores de programas, onde conheceu figuras influentes do meio artístico e televisivo. Os fotógrafos os seguiam em eventos como bailes de carnaval e inaugurações, registrando cada aparição pública do casal. Com Pelé ao seu lado, Xuxa ganhou trânsito livre em círculos antes inacessíveis para uma modelo iniciante, construindo uma rede de contatos valiosa nos meios de comunicação. De fato, naquele início dos anos 80, **“os dois eram perseguidos por fotógrafos, apareciam em capas de revistas e até faziam publicidade juntos”** ([Pelé viveu com Xuxa um namoro intenso afetado por fofocas e indiscrições](https://www.terra.com.br/diversao/gente/pele-viveu-com-xuxa-um-namoro-intenso-afetado-por-fofocas-e-indiscricoes,0c075d1a6be75f53536ad3b70e8e4a01iavthiai.html#:~:text=Morte%20s%C3%BAbita%20encerra%20fase%20feliz,vida%20da%20atriz%20Marcia%20Manfredini)) – evidência de que Xuxa, graças ao namoro, transitava tanto na frente quanto por trás das câmeras com muito mais facilidade. Em suma, o relacionamento conferiu a ela um grau de notoriedade nacional que provavelmente demoraria anos para conquistar de outra forma, preparando o terreno para os passos seguintes de sua carreira.
## Influência Direta de Pelé nas Oportunidades Profissionais de Xuxa
Além do aumento geral da fama, há casos específicos em que Pelé influenciou diretamente oportunidades profissionais para Xuxa. Um exemplo contundente é o filme **“Amor Estranho Amor” (1982)** – longa de teor erótico no qual Xuxa atuou no início da carreira. Segundo relatos da própria apresentadora, **foi Pelé quem a incentivou a aceitar participar desse filme** ([Pelé e Xuxa: um estranho amor que durou seis anos - 29/12/2022 - Celebridades - F5](https://f5.folha.uol.com.br/celebridades/2022/12/pele-e-xuxa-o-estranho-amor-entre-o-rei-do-futebol-e-a-futura-rainha-dos-baixinhos.shtml#:~:text=Profissionalmente%2C%20Xuxa%20disse%20que%20Pel%C3%A9,Me%20enganaram%2C%20falaram%20um)). Na época ainda em início de trajetória, Xuxa acabou convencida pelo namorado de que aquela oportunidade poderia ser benéfica. Anos mais tarde, ela revelaria arrependimento pela escolha desse papel, mas o fato reforça que Pelé teve influência ativa em decisões profissionais de Xuxa no começo de sua jornada.
Outra área de influência direta foram as **publicidades e campanhas comerciais**. Graças ao prestígio de Pelé, Xuxa recebeu convites para estrelar anúncios ao lado do então namorado. Já em 1981, por exemplo, os dois gravaram juntos comerciais para uma empresa imobiliária, aparecendo como casal em campanhas de TV daquele Natal (pelas **Imóveis Francisco Xavier**, um case famoso entre colecionadores de propagandas da época) ([Xuxa e Pelé: Natal de 1981 na Publicidade Imobiliária | TikTok](https://www.tiktok.com/@thebest.memories/video/7301084045402721541#:~:text=Xuxa%20e%20Pel%C3%A9%3A%20Natal%20de,Natal%20de%201981%20na)) ([Xuxa com Pelé em comercial de imobiliária em dezembro de 1981](https://www.youtube.com/watch?v=t45oWkJPFw0#:~:text=Xuxa%20com%20Pel%C3%A9%20em%20comercial,Im%C3%B3veis%20em%20dezembro%20de%201981)). Assim, Xuxa obteve espaço em campanhas publicitárias que dificilmente envolveriam uma modelo desconhecida – mas que, com a “namorada do Pelé” no elenco, ganhavam apelo extra. Isso evidencia que Pelé abriu portas também no mercado publicitário, dando a Xuxa oportunidades de trabalho e renda enquanto sua própria imagem pública se consolidava.
Ademais, a presença de Pelé ao lado de Xuxa em diversos editoriais e ensaios fotográficos serviu para elevá-la de modelo anônima a personalidade conhecida. Revistas e jornais buscavam os dois para sessões de fotos e entrevistas, sabendo do interesse do público pelo casal. As capas conjuntas em publicações de grande circulação (como *Manchete* e outras) não só aumentaram a exposição de Xuxa, mas também conferiram a ela certa credibilidade midiática por associação. Em outras palavras, estar ao lado de um ícone como Pelé funcionou como um “selo de aprovação” implícito, deixando editores e produtores mais propensos a convidá-la para projetos. Vale lembrar que **“ao longo dos seis anos de relacionamento, [eles] posaram para várias capas da *Manchete*”**, com a revista acompanhando de perto cada fase do namoro ([A história da foto de revista que gerou o namoro de Pelé e Xuxa](https://www.terra.com.br/diversao/gente/a-historia-da-foto-de-revista-que-gerou-o-namoro-de-pele-e-xuxa,c5106b23301f6f0e7c03f38cdf9eb1a06kopa9ho.html#:~:text=Um%20tempo%20depois%2C%20quando%20a,se%20nacionalmente%20famosa)). Essa recorrência nas bancas solidificou o rosto e o nome de Xuxa na indústria do entretenimento.
Por fim, é importante notar que nem todas as influências de Pelé foram positivas para a carreira dela – algumas foram tentativas de direcionamento. A própria Xuxa contou que, quando surgiu a oportunidade de ela ir para a TV Globo em 1986, Pelé desencorajou a mudança. **Ele sugeriu que Xuxa permanecesse na TV Manchete, dizendo que “ser a primeira [na Globo] é muito difícil; melhor ficar onde está”**, o que ela interpretou como falta de apoio dele à sua ascensão ([Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira](https://aventurasnahistoria.com.br/noticias/reportagem/xuxa-e-pele-o-relacionamento-que-ficou-cravado-na-historia-da-imprensa-brasileira.phtml#:~:text=,torcendo%20por%20mim%E2%80%9D%2C%20acrescentou%20Xuxa)). Esse episódio mostra que Pelé tentou influenciar também os rumos que Xuxa tomaria, embora, nesse caso, ela tenha decidido seguir sua intuição profissional e aceitar o desafio na Globo – escolha que se revelaria acertada. Em resumo, Pelé atuou sim como facilitador de várias oportunidades profissionais para Xuxa (de filmes a comerciais e visibilidade editorial), mas ela soube trilhar seu caminho a partir daí, inclusive contrariando conselhos dele quando necessário.
## Papel da Revista *Manchete* e Outras Mídias na Promoção de Xuxa
A revista ***Manchete*** teve um papel central na ascensão de Xuxa durante o relacionamento com Pelé. Foi justamente num ensaio para a *Manchete* que os dois se conheceram, em dezembro de 1980 ([Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira](https://aventurasnahistoria.com.br/noticias/reportagem/xuxa-e-pele-o-relacionamento-que-ficou-cravado-na-historia-da-imprensa-brasileira.phtml#:~:text=A%20extinta%20Manchete%20promovia%20uma,Xuxa%2C%20com%20apenas%2017%20anos)), e a partir daí a publicação tornou-se uma espécie oficiosa de cronista do romance. A *Manchete* era uma das revistas mais populares do Brasil naquela época e, ao perceber o interesse do público pelo casal, passou a trazê-los frequentemente em suas páginas. De fato, a revista que agiu como "cupido" do casal **“contava detalhes do romance a cada edição”**, alimentando a curiosidade nacional sobre a vida de Pelé e sua jovem namorada ([A história da foto de revista que gerou o namoro de Pelé e Xuxa](https://www.terra.com.br/diversao/gente/a-historia-da-foto-de-revista-que-gerou-o-namoro-de-pele-e-xuxa,c5106b23301f6f0e7c03f38cdf9eb1a06kopa9ho.html#:~:text=nacionalmente%20famosa)). As capas exibindo Xuxa e Pelé juntos (em cenários que iam da praia a eventos sociais) viraram chamariz nas bancas e contribuíram enormemente para fixar a imagem de Xuxa na mente do público.
([A história da foto de revista que gerou o namoro de Pelé e Xuxa](https://www.terra.com.br/diversao/gente/a-historia-da-foto-de-revista-que-gerou-o-namoro-de-pele-e-xuxa,c5106b23301f6f0e7c03f38cdf9eb1a06kopa9ho.html)) *Capa da revista Manchete (20 de dezembro de 1980) mostrando Pelé ao centro com Xuxa (à esquerda) e outras modelos. A partir desse ensaio fotográfico, a revista passou a acompanhar de perto o romance, impulsionando a imagem de Xuxa nacionalmente.* ([A história da foto de revista que gerou o namoro de Pelé e Xuxa](https://www.terra.com.br/diversao/gente/a-historia-da-foto-de-revista-que-gerou-o-namoro-de-pele-e-xuxa,c5106b23301f6f0e7c03f38cdf9eb1a06kopa9ho.html#:~:text=Um%20tempo%20depois%2C%20quando%20a,se%20nacionalmente%20famosa)) ([Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira](https://aventurasnahistoria.com.br/noticias/reportagem/xuxa-e-pele-o-relacionamento-que-ficou-cravado-na-historia-da-imprensa-brasileira.phtml#:~:text=A%20extinta%20Manchete%20promovia%20uma,Xuxa%2C%20com%20apenas%2017%20anos))
Além da *Manchete*, outras mídias impressas também surfaram no interesse pelo casal e ajudaram a moldar a imagem de Xuxa. Revistas de celebridades e colunas sociais publicavam notas e fotos frequentes, ora exaltando o glamour do par, ora especulando sobre fofocas. Xuxa, que pouco antes era desconhecida fora do circuito da moda, tornou-se figura constante em revistas semanais como *Contigo!* e *Amiga* (dedicadas à vida dos famosos), assim como em jornais de grande circulação. Esse bombardeio de aparições – entrevistas, fotos e manchetes – construiu a **persona pública** de Xuxa simultaneamente como **modelo desejada e namorada devotada**. A promoção de sua imagem tinha um tom deliberadamente positivo nas revistas: enfatizava-se sua beleza, juventude e sorte por ter sido “escolhida” pelo rei Pelé. Em contrapartida, eventuais polêmicas (como cenas ousadas que ela fez no cinema ou rumores de crises no namoro) eram administradas pela própria mídia de maneira a preservar o encanto em torno de Xuxa, que já despontava como uma espécie de Cinderella moderna na narrativa do entretenimento brasileiro.
Cabe destacar que a conexão de Xuxa com a *Manchete* não ficou só nas páginas da revista, mas transbordou para a televisão, já que a Rede Manchete (canal de TV fundado em 1983) pertencia ao mesmo grupo empresarial. Essa sinergia mídia impressa/televisão beneficiou Xuxa: **quando a Rede Manchete buscava uma apresentadora para seu novo programa infantil em 1983, Xuxa – já famosa pelas capas de revista – foi convidada** para o posto ([Xuxa está em paz - revista piauí](https://piaui.folha.uol.com.br/materia/xuxa-esta-em-paz/#:~:text=match%20at%20L355%20TV%20Manchete%2C,ter%20como%20apresentadora%20de%20programa)). Ou seja, a exposição na revista *Manchete* serviu de vitrine para que os executivos da emissora homônima apostassem nela na TV. Outras mídias também legitimaram sua transição de modelo para apresentadora, publicando matérias sobre sua simpatia com as crianças e seu carisma diante das câmeras, preparando o público para aceitar Xuxa em um novo papel. Assim, o período do relacionamento com Pelé viu a mídia – liderada pela revista *Manchete* – construir e promover intensamente a imagem de Xuxa, pavimentando o caminho para suas conquistas seguintes.
## O Relacionamento e a Conquista de Espaços na TV: *Clube da Criança* e Rede Globo
O namoro com Pelé coincidiu com a entrada de Xuxa na televisão e possivelmente facilitou essa transição. Em 1983, a recém-inaugurada Rede Manchete lançou o **“Clube da Criança”**, primeiro programa infantil de auditório da emissora, e Xuxa foi escolhida como apresentadora. Há indícios de que sua fama prévia – alavancada pelo relacionamento – foi decisiva nessa escolha. Conforme relatos, o diretor Maurício Sherman (responsável pelo projeto) estava de olho em Xuxa por sua notoriedade e carisma, chegando a dizer que ela reunia *“a sensualidade de Marilyn Monroe, o sorriso de Doris Day e um quê de Peter Pan”* ([Xuxa está em paz - revista piauí](https://piaui.folha.uol.com.br/materia/xuxa-esta-em-paz/#:~:text=TV%20Manchete%2C%20do%20grupo%20de,ter%20como%20apresentadora%20de%20programa)) – uma combinação que poderia funcionar bem num programa infantil. Xuxa inicialmente hesitou em aceitar, talvez pelo contraste entre sua imagem de modelo sensual e o universo infantil, mas acabou assinando contrato com a Manchete ([Clube da Criança – Wikipédia, a enciclopédia livre](https://pt.wikipedia.org/wiki/Clube_da_Crian%C3%A7a#:~:text=match%20at%20L206%20comando%20da,por%20Maur%C3%ADcio%20Sherman%20e%20pelo)). Assim, aos 20 anos de idade, ela estreava como apresentadora de TV, **em grande parte graças à visibilidade e confiança que o nome “Xuxa” (já famoso por ser namorada do Pelé) passava aos produtores**.
Não há registro de que Pelé tenha intervindo diretamente para que Xuxa conseguisse o posto no *Clube da Criança*. Foi a própria rede Manchete – estimulada pelo burburinho em torno dela – que a **“procurou e a convidou para apresentar”** o programa ([Xuxa está em paz - revista piauí](https://piaui.folha.uol.com.br/materia/xuxa-esta-em-paz/#:~:text=TV%20Manchete%2C%20do%20grupo%20de,ter%20como%20apresentadora%20de%20programa)). Porém, é inegável que, sem o destaque que Xuxa conquistara nos anos anteriores na imprensa (devido ao namoro), dificilmente uma emissora arriscaria colocar uma jovem inexperiente para comandar um show infantil nacional. Ou seja, o relacionamento criou as condições favoráveis para essa oportunidade surgir. Uma vez no ar, Xuxa rapidamente mostrou talento próprio: o *Clube da Criança* foi ganhando audiência e revelou a aptidão dela em se comunicar com o público infantil ([Xuxa, Pantanal, Cavaleiros dos Zodíacos: lembre sucessos da TV ...](https://www.folhape.com.br/cultura/xuxa-pantanal-cavaleiros-dos-zodiacos-e-mais-sucessos-da-tv/334766/#:~:text=Xuxa%2C%20Pantanal%2C%20Cavaleiros%20dos%20Zod%C3%ADacos%3A,exibido%20no%20fim%20de)). Ainda durante seu tempo na Manchete, Xuxa manteve-se nos holofotes tanto pela carreira quanto pelo namoro com Pelé – frequentemente um assunto alimentava o outro na mídia.
Em meados de 1986, já conhecida como a “Rainha dos Baixinhos” pelo sucesso junto às crianças, Xuxa recebeu uma proposta para se transferir para a Rede Globo, a principal emissora do país ([A história da foto de revista que gerou o namoro de Pelé e Xuxa](https://www.terra.com.br/diversao/gente/a-historia-da-foto-de-revista-que-gerou-o-namoro-de-pele-e-xuxa,c5106b23301f6f0e7c03f38cdf9eb1a06kopa9ho.html#:~:text=Pel%C3%A9%20e%20Xuxa%20ficaram%20juntos,do%20mesmo%20grupo%20da%20revista)). Novamente, aqui o relacionamento com Pelé tem um papel indireto: por um lado, pode ter ajudado a construir a notoriedade que chamou a atenção da Globo; por outro, chegava ao fim exatamente nesse momento, marcando uma virada na vida dela. Após alguns anos de *Clube da Criança*, Xuxa decidiu dar um passo adiante. Ela mesma tomou a iniciativa de terminar o namoro com Pelé e aceitou o convite para fazer o **“Xou da Xuxa”** na Globo ([A história da foto de revista que gerou o namoro de Pelé e Xuxa](https://www.terra.com.br/diversao/gente/a-historia-da-foto-de-revista-que-gerou-o-namoro-de-pele-e-xuxa,c5106b23301f6f0e7c03f38cdf9eb1a06kopa9ho.html#:~:text=Pel%C3%A9%20e%20Xuxa%20ficaram%20juntos,do%20mesmo%20grupo%20da%20revista)). Pelé, como mencionado, havia expressado reservas sobre essa mudança de emissora ([Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira](https://aventurasnahistoria.com.br/noticias/reportagem/xuxa-e-pele-o-relacionamento-que-ficou-cravado-na-historia-da-imprensa-brasileira.phtml#:~:text=,torcendo%20por%20mim%E2%80%9D%2C%20acrescentou%20Xuxa)), mas sem sucesso em demovê-la. Com a benção do dono da Manchete, Adolpho Bloch (que a tratava “como filha” e apoiou seu crescimento) ([Xuxa está em paz - revista piauí](https://piaui.folha.uol.com.br/materia/xuxa-esta-em-paz/#:~:text=match%20at%20L405%20Manchete%20e,%E2%80%99%E2%80%9D)) ([Xuxa está em paz - revista piauí](https://piaui.folha.uol.com.br/materia/xuxa-esta-em-paz/#:~:text=Manchete%20e%20fui%20embora%E2%80%9D%2C%20recorda,%E2%80%99%E2%80%9D)), Xuxa partiu para a Globo levando sua diretora Marlene Mattos, e estreou em junho de 1986 o programa que a consagraria definitivamente.
É importante notar que, ao ingressar na Globo, Xuxa já não dependia mais da aura de “namorada do Pelé” – ela havia se firmado como apresentadora de sucesso por méritos próprios. Ainda assim, **o relacionamento anterior continuou a ser parte de sua imagem pública**: a mídia noticiou a mudança destacando que a namorada de Pelé chegara à Globo, e muitos espectadores tinham curiosidade sobre aquela moça cuja fama começara nos braços do ídolo do futebol. Em resumo, o namoro ajudou Xuxa a conquistar o primeiro grande espaço na TV (na Manchete), fornecendo-lhe exposição e credibilidade iniciais, enquanto sua ida para a Globo foi impulsionada principalmente pelo desempenho no *Clube da Criança* – algo que o prestígio conquistado durante o relacionamento tornou possível em primeiro lugar.
## Percepção da Mídia e do Público sobre o Casal e a Imagem de Xuxa
Durante os anos de namoro, Pelé e Xuxa foram um prato cheio para a imprensa e objeto de variadas opiniões do público. De um lado, eram celebrados como **“casal perfeito na mídia”**, aparecendo sorridentes em eventos e capas, o que projetava uma imagem glamourosa e apaixonada ([Pelé viveu com Xuxa um namoro intenso afetado por fofocas e indiscrições](https://www.terra.com.br/diversao/gente/pele-viveu-com-xuxa-um-namoro-intenso-afetado-por-fofocas-e-indiscricoes,0c075d1a6be75f53536ad3b70e8e4a01iavthiai.html#:~:text=Image%3A%20Pel%C3%A9%20e%20Xuxa%20na,perfeito%20na%20m%C3%ADdia%2C%20mas%20com)). Xuxa era frequentemente retratada como a bela jovem humilde que havia conquistado o coração do "rei", uma narrativa de conto de fadas que agradava muitos fãs. Pessoas próximas diziam na época: *“Nossa, como ela está apaixonada, como ela está de quatro pelo Pelé”*, segundo relembrou a própria Xuxa, indicando que sua dedicação ao namorado era visível e comentada ([Xuxa e Pelé: um romance que se tornou inesquecível... | VEJA](https://veja.abril.com.br/coluna/veja-gente/xuxa-e-pele-um-romance-que-se-tornou-inesquecivel-para-os-dois/#:~:text=Ao%20participar%20de%20uma%20live,de%20quatro%20para%20o%20Pel%C3%A9%27%E2%80%9D)). Essa percepção de autenticidade nos sentimentos ajudou a humanizar Xuxa aos olhos do público, diferenciando-a de estereótipos de *roupante* ou interesse calculado.
Por outro lado, nem toda a atenção era positiva. **Houve murmúrios maldosos e preconceituosos nos bastidores**. Pelé e Xuxa formavam um casal interracial (ele negro, ela branca e bem mais jovem), o que, segundo a imprensa, **“gerava olhares de reprovação dos conservadores” e até comentários racistas proferidos pelas costas** ([Pelé viveu com Xuxa um namoro intenso afetado por fofocas e indiscrições](https://www.terra.com.br/diversao/gente/pele-viveu-com-xuxa-um-namoro-intenso-afetado-por-fofocas-e-indiscricoes,0c075d1a6be75f53536ad3b70e8e4a01iavthiai.html#:~:text=Os%20dois%20eram%20perseguidos%20por,Mas%20nem%20tudo%20era%20agrad%C3%A1vel)). Além disso, alguns duvidavam das intenções de Xuxa no relacionamento, insinuando que ela buscava ascensão social por meio de Pelé. Termos pejorativos como *“maria-chuteira”* (gíria para mulheres que namoram jogadores em busca de status) e *“alpinista social”* chegaram a ser associados a Xuxa por fofoqueiros da época ([Pelé viveu com Xuxa um namoro intenso afetado por fofocas e indiscrições](https://www.terra.com.br/diversao/gente/pele-viveu-com-xuxa-um-namoro-intenso-afetado-por-fofocas-e-indiscricoes,0c075d1a6be75f53536ad3b70e8e4a01iavthiai.html#:~:text=olhares%20de%20reprova%C3%A7%C3%A3o%20dos%20conservadores)). Essa desconfiança lançava sombra sobre a imagem dela, pintando-a, aos olhos de alguns, como oportunista em vez de namorada dedicada. Xuxa teve de lidar com esse tipo de insinuação ao longo do namoro, buscando provar que seu amor era verdadeiro e que ela também tinha talentos e ambições próprias.
A mídia impressa, em geral, manteve uma postura favorável ao casal, explorando o romance como algo encantador. Mas não deixou de reportar as turbulências: sabia-se, por exemplo, das **frequentes traições de Pelé**, que Xuxa anos depois revelou ter suportado calada na época ([Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira](https://aventurasnahistoria.com.br/noticias/reportagem/xuxa-e-pele-o-relacionamento-que-ficou-cravado-na-historia-da-imprensa-brasileira.phtml#:~:text=Por%20causa%20do%20companheiro%2C%20tamb%C3%A9m,que%20n%C3%A3o%20era%20o%20meu)) ([Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira](https://aventurasnahistoria.com.br/noticias/reportagem/xuxa-e-pele-o-relacionamento-que-ficou-cravado-na-historia-da-imprensa-brasileira.phtml#:~:text=Apesar%20dos%20problemas%20corriqueiros%20com,Era%20uma%20situa%C3%A7%C3%A3o%20esquisita%E2%80%9D)). Essas infidelidades eram rumores correntes nos círculos de fofoca, embora Xuxa raramente comentasse publicamente enquanto estava com Pelé. O público, portanto, via um casal bonito e famoso, mas também acompanhava as especulações de crises e reconciliações pelos noticiários de celebridades. Cada aparição pública deles – fosse em um jogo de futebol, um evento beneficente ou nos camarotes do carnaval – era dissecada pelos repórteres, e cada declaração (ou silêncio) alimentava interpretações sobre o estado do relacionamento e sobre quem era Xuxa por trás da fama.
No saldo final, o namoro com Pelé influenciou profundamente a **imagem pública de Xuxa**. Inicialmente marcada como “a namorada do Rei” – posição que trazia tanto admiração quanto inveja – Xuxa soube aproveitar a visibilidade para mostrar carisma e trabalho, transformando-se em uma estrela por direito próprio. Ao se tornar apresentadora infantil de sucesso ainda durante o namoro, ela começou a dissociar sua imagem da de Pelé, provando que podia ser mais do que um apêndice de um astro do esporte. Quando o relacionamento terminou em 1986, Xuxa emergiu não caída em desgraça, mas sim pronta para reinar sozinha na TV. A mídia continuou a mencioná-la em referência a Pelé por algum tempo (era inevitável, dado o quão famoso o casal fora), mas cada vez mais o público passou a enxergá-la principalmente como a **“Rainha dos Baixinhos”**, a figura alegre das manhãs na TV Globo. Em entrevistas posteriores, Xuxa admitiu ter sentimentos mistos ao lembrar dessa fase: ela se ressentiu, por exemplo, de Pelé ter classificado o que viveram como *“uma amizade colorida”* em vez de namoro sério ([Pelé e Xuxa: um estranho amor que durou seis anos - 29/12/2022 - Celebridades - F5](https://f5.folha.uol.com.br/celebridades/2022/12/pele-e-xuxa-o-estranho-amor-entre-o-rei-do-futebol-e-a-futura-rainha-dos-baixinhos.shtml#:~:text=Xuxa%20disse%20ter%20ficado%20magoada,N%C3%A3o%20fui%20avisada)) – frase do ex-jogador que a magoou e que veio a público muitos anos depois. Esse comentário retroativo de Pelé apenas reforçou o quanto a mídia e o público discutiram e dissecaram a natureza daquela relação.
Em conclusão, a percepção do casal Xuxa e Pelé oscilou entre o encanto e a controvérsia, mas inegavelmente manteve Xuxa nos trending topics de sua época (para usar um termo atual). A jovem modelo gaúcha ganhou projeção, prestígio e também enfrentou julgamentos enquanto esteve com Pelé. Tudo isso moldou sua imagem – de **símbolo sexual e socialite em ascensão** a **profissional talentosa pronta para brilhar por conta própria**. O relacionamento forneceu-lhe a plataforma e a armadura mediática; coube a Xuxa transformar essa visibilidade em uma carreira sólida, o que ela fez com maestria ao se tornar uma das maiores apresentadoras da história da TV brasileira.
**Fontes:** Entrevistas e depoimentos de Xuxa Meneghel (inclusive do livro *Memórias*, 2020), reportagens da época em revistas como *Manchete*, colunas sociais e jornais (compiladas em repositórios atuais), e biografias e retrospectivas sobre ambos os envolvidos ([A história da foto de revista que gerou o namoro de Pelé e Xuxa](https://www.terra.com.br/diversao/gente/a-historia-da-foto-de-revista-que-gerou-o-namoro-de-pele-e-xuxa,c5106b23301f6f0e7c03f38cdf9eb1a06kopa9ho.html#:~:text=Um%20tempo%20depois%2C%20quando%20a,se%20nacionalmente%20famosa)) ([Pelé viveu com Xuxa um namoro intenso afetado por fofocas e indiscrições](https://www.terra.com.br/diversao/gente/pele-viveu-com-xuxa-um-namoro-intenso-afetado-por-fofocas-e-indiscricoes,0c075d1a6be75f53536ad3b70e8e4a01iavthiai.html#:~:text=Morte%20s%C3%BAbita%20encerra%20fase%20feliz,vida%20da%20atriz%20Marcia%20Manfredini)) ([Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira](https://aventurasnahistoria.com.br/noticias/reportagem/xuxa-e-pele-o-relacionamento-que-ficou-cravado-na-historia-da-imprensa-brasileira.phtml#:~:text=,torcendo%20por%20mim%E2%80%9D%2C%20acrescentou%20Xuxa)) ([Xuxa e Pelé: um romance que se tornou inesquecível... | VEJA](https://veja.abril.com.br/coluna/veja-gente/xuxa-e-pele-um-romance-que-se-tornou-inesquecivel-para-os-dois/#:~:text=Um%20dos%20romances%20mais%20comentados,manchetes%20e%20revistas%20de%20fofoca)), entre outras. Essas fontes confirmam o papel catalisador que o namoro com Pelé teve nos primeiros passos da trajetória de Xuxa, bem como os desafios e oportunidades que surgiram dessa intensa exposição pública.
-

@ 6b3780ef:221416c8
2025-03-26 18:42:00
This workshop will guide you through exploring the concepts behind MCP servers and how to deploy them as DVMs in Nostr using DVMCP. By the end, you'll understand how these systems work together and be able to create your own deployments.
## Understanding MCP Systems
MCP (Model Context Protocol) systems consist of two main components that work together:
1. **MCP Server**: The heart of the system that exposes tools, which you can access via the `.listTools()` method.
2. **MCP Client**: The interface that connects to the MCP server and lets you use the tools it offers.
These servers and clients can communicate using different transport methods:
- **Standard I/O (stdio)**: A simple local connection method when your server and client are on the same machine.
- **Server-Sent Events (SSE)**: Uses HTTP to create a communication channel.
For this workshop, we'll use stdio to deploy our server. DVMCP will act as a bridge, connecting to your MCP server as an MCP client, and exposing its tools as a DVM that anyone can call from Nostr.
## Creating (or Finding) an MCP Server
Building an MCP server is simpler than you might think:
1. Create software in any programming language you're comfortable with.
2. Add an MCP library to expose your server's MCP interface.
3. Create an API that wraps around your software's functionality.
Once your server is ready, an MCP client can connect, for example, with `bun index.js`, and then call `.listTools()` to discover what your server can do. This pattern, known as reflection, makes Nostr DVMs and MCP a perfect match since both use JSON, and DVMs can announce and call tools, effectively becoming an MCP proxy.
Alternatively, you can use one of the many existing MCP servers available in various repositories.
For more information about mcp and how to build mcp servers you can visit https://modelcontextprotocol.io/
## Setting Up the Workshop
Let's get hands-on:
First, to follow this workshop you will need Bun. Install it from https://bun.sh/. For Linux and macOS, you can use the installation script:
```
curl -fsSL https://bun.sh/install | bash
```
1. **Choose your MCP server**: You can either create one or use an existing one.
2. **Inspect your server** using the MCP inspector tool:
```bash
npx @modelcontextprotocol/inspector build/index.js arg1 arg2
```
This will:
- Launch a client UI (default: http://localhost:5173)
- Start an MCP proxy server (default: port 3000)
- Pass any additional arguments directly to your server
3. **Use the inspector**: Open the client UI in your browser to connect with your server, list available tools, and test its functionality.
## Deploying with DVMCP
Now for the exciting part – making your MCP server available to everyone on Nostr:
1. Navigate to your MCP server directory.
2. Run without installing (quickest way):
```
npx @dvmcp/bridge
```
3. Or install globally for regular use:
```
npm install -g @dvmcp/bridge
# or
bun install -g @dvmcp/bridge
```
Then run using:
```bash
dvmcp-bridge
```
This will guide you through creating the necessary configuration.
Watch the console logs to confirm successful setup – you'll see your public key and process information, or any issues that need addressing.
For the configuration, you can set the relay as `wss://relay.dvmcp.fun` , or use any other of your preference
## Testing and Integration
1. **Visit [dvmcp.fun](https://dvmcp.fun)** to see your DVM announcement.
2. Call your tools and watch the responses come back.
For production use, consider running dvmcp-bridge as a system service or creating a container for greater reliability and uptime.
## Integrating with LLM Clients
You can also integrate your DVMCP deployment with LLM clients using the discovery package:
1. Install and use the `@dvmcp/discovery` package:
```bash
npx @dvmcp/discovery
```
2. This package acts as an MCP server for your LLM system by:
- Connecting to configured Nostr relays
- Discovering tools from DVMCP servers
- Making them available to your LLM applications
3. Connect to specific servers or providers using these flags:
```bash
# Connect to all DVMCP servers from a provider
npx @dvmcp/discovery --provider npub1...
# Connect to a specific DVMCP server
npx @dvmcp/discovery --server naddr1...
```
Using these flags, you wouldn't need a configuration file. You can find these commands and Claude desktop configuration already prepared for copy and paste at [dvmcp.fun](https://dvmcp.fun).
This feature lets you connect to any DVMCP server using Nostr and integrate it into your client, either as a DVM or in LLM-powered applications.
## Final thoughts
If you've followed this workshop, you now have an MCP server deployed as a Nostr DVM. This means that local resources from the system where the MCP server is running can be accessed through Nostr in a decentralized manner. This capability is powerful and opens up numerous possibilities and opportunities for fun.
You can use this setup for various use cases, including in a controlled/local environment. For instance, you can deploy a relay in your local network that's only accessible within it, exposing all your local MCP servers to anyone connected to the network. This setup can act as a hub for communication between different systems, which could be particularly interesting for applications in home automation or other fields. The potential applications are limitless.
However, it's important to keep in mind that there are security concerns when exposing local resources publicly. You should be mindful of these risks and prioritize security when creating and deploying your MCP servers on Nostr.
Finally, these are new ideas, and the software is still under development. If you have any feedback, please refer to the GitHub repository to report issues or collaborate. DVMCP also has a Signal group you can join. Additionally, you can engage with the community on Nostr using the #dvmcp hashtag.
## Useful Resources
- **Official Documentation**:
- Model Context Protocol: [modelcontextprotocol.org](https://modelcontextprotocol.org)
- DVMCP.fun: [dvmcp.fun](https://dvmcp.fun)
- **Source Code and Development**:
- DVMCP: [github.com/gzuuus/dvmcp](https://github.com/gzuuus/dvmcp)
- DVMCP.fun: [github.com/gzuuus/dvmcpfun](https://github.com/gzuuus/dvmcpfun)
- **MCP Servers and Clients**:
- Smithery AI: [smithery.ai](https://smithery.ai)
- MCP.so: [mcp.so](https://mcp.so)
- Glama AI MCP Servers: [glama.ai/mcp/servers](https://glama.ai/mcp/servers)
- [Signal group](https://signal.group/#CjQKIOgvfFJf8ZFZ1SsMx7teFqNF73sZ9Elaj_v5i6RSjDHmEhA5v69L4_l2dhQfwAm2SFGD)
Happy building!
-

@ d5c3d063:4d1159b3
2025-04-05 00:51:55
📙 เทคนิคตั้งคำถามนโยบาย จากหนังสือ “เศรษฐศาสตร์เล่มเดียวจบ” #EIOL
ผมอยากแบ่งปันวิธีง่าย ๆ ในการนำแนวคิดจากหนังสือมาใช้ เพื่อ “ตั้งคำถามกับนโยบาย” ที่เราเจอในชีวิตประจำวัน ไม่ต้องเป็นนักเศรษฐศาสตร์ก็ใช้ได้ เพราะนี่คือทักษะของ “คนที่เลือกจะคิดเอง”
กับ 3 เทคนิค คิดแบบนักเศรษฐศาสตร์ เวลารัฐออกนโยบาย
1. เข้าใจ “วิธีคิด” ที่หนังสือพยายามสอนเรา
ใน Economics in One Lesson ของ Henry Hazlitt
เขาไม่ได้ให้สูตรลัด แต่ให้ “เลนส์” สำหรับมองระบบเศรษฐกิจให้ชัดขึ้น หลักคิดสำคัญคือ
- อย่าหยุดแค่สิ่งที่เรามองเห็นทันที
- ให้ถามต่อว่ามี “ต้นทุนที่ซ่อนอยู่” ไหม
-มีใครได้รับผลกระทบ โดยไม่มีใครพูดถึงหรือเปล่า
2. เลือกนโยบายใกล้ตัวที่เจอในข่าว
เราไม่ต้องเป็นนักวิชาการก็ทำได้ แค่ถามตัวเองง่าย ๆ
- แจกเงิน = แจกให้ใคร แล้วใครจ่าย
- ตรึงราคาน้ำมัน = ดีตอนนี้กระทบอะไรในระยะยาว
- รถไฟฟ้าฟรี = ฟรีจริงดิ หรือมีคนจ่ายแทนเราอยู่
ทุกนโยบายคือบทเรียน ถ้าเรากล้าตั้งคำถาม
3. ตั้งคำถามกับนโยบาย อย่ารอให้รัฐสรุปให้คุณ
ลองใช้ 3 คำถามนี้กับทุกนโยบายที่คุณเจอ
- ใครได้ประโยชน์ทันที
- ใครต้องจ่าย หรือเสียโอกาสบางอย่างไป
- แล้วในระยะยาว นโยบายนี้จะพาเราไปทางไหน
บางครั้งคำตอบไม่ได้อยู่ในข่าว หรือโพสต์สวย ๆ
แต่มันซ่อนอยู่ใน “สิ่งที่ไม่มีใครอยากพูดถึง”
.
.
ตัวอย่าง เมื่อรัฐบาลประกาศจะแจกเงิน Digital Wallet คนละ 10,000 บาท สิ่งที่คนส่วนใหญ่มองเห็นคือ “ความช่วยเหลือ” และ “การกระตุ้นเศรษฐกิจ”
แต่ถ้าลองมองผ่านเลนส์ของ Hazlitt
นี่คือคำถามที่ไม่ค่อยมีใครถาม
- เงินที่ใช้แจกมาจากไหน ภาษีของเราหรือหนี้ที่ลูกหลานเราต้องใช้คืนในอนาคต
- มันช่วยให้คนอยู่รอด หรือช่วยให้คนลุกขึ้นยืนได้ด้วยตัวเองในระยะยาวจริงไหม
- คนที่ไม่ได้อยู่ในระบบดิจิทัล จะถูกทิ้งไว้ข้างหลังไหม
- นี่คือการวางรากฐานระยะยาวหรือแค่การเร่งใช้จ่ายเพื่อประชานิยมระยะสั้น
.
หนังสือที่ดีจะไม่แค่ให้ข้อมูล แต่ให้ “มุมมองใหม่”
และมุมมองนี้เอง ที่ช่วยให้เรา “ไม่ตกหลุมกับนโยบายที่ดูดีแต่ไม่ยั่งยืน”
.
.
ต่อไปถ้าเจอนโยบายที่ดูดี ลองหยิบคำถาม 3 ข้อนี้ขึ้นมาใช้ แล้วดูว่าคุณเห็นอะไรที่คนอื่นอาจมองข้าม เพราะเศรษฐศาสตร์ที่ดี…เริ่มจาก “การสงสัยในสิ่งที่ทุกคนปรบมือให้”
ถ้าบทความนี้ทำให้คุณ “มองเห็นสิ่งที่เคยมองข้าม”
ลองแชร์ให้เพื่อนสักคนดูครับ
เพราะเศรษฐศาสตร์ ไม่ได้เป็นแค่เรื่องของนักวิชาการ
แต่มันคือเครื่องมือของคนธรรมดา...
ที่อยากเข้าใจโลกให้ลึกขึ้นอีกนิด 🙃
#Siamstr
-

@ 81aae9c5:267f2001
2025-04-04 19:06:05
# Hello wordl
publishing from the new cli tool thingy
-

@ a5142938:0ef19da3
2025-04-04 14:49:53
**Contribute to enrich the site!**
Each contribution helps improve this site by supporting the listing of natural alternatives.
### 💡 What Counts as a Contribution?
A contribution can be:
📝 Proposing a new entry, by providing its initial information. Each piece of information added (name, link, category, etc.) is considered a contribution:
- [Add a product](https://www.origin-nature.com/post/8adj-i_hk0gtzp_ul9k17/)
- [Add a brand](https://www.origin-nature.com/post/unjmwarjg7ojb9uwantvt/)
📝 Adding or modifying information in an existing entry. Each piece of information added or removed is considered a contribution.
### ✅ Contribution validation
Contributions are reviewed by the core team. A contribution is validated when the information provided is submitted for the first time (the earliest comment is taken into account) and can be verified.
Once validated, contributions are counted and eligible for rewards.
👉 [Learn more about rewards](https://www.origin-nature.com/post/xz20q6pw42fd9ijaewnn6/)
---
This article is published on [origin-nature.com](https://www.origin-nature.com/post/laf_xjasf4kgunxvozhkm/)
🌐 [Voir cet article en français](https://www.origine-nature.com/post/26bj5f7bwyps6ecp5v62t/)
-

@ 57d1a264:69f1fee1
2025-03-26 08:45:13
> I was curious to see how Stacker.News domain and website contents scored from a SEO (Search Engine Optimization) perspective. Here what Semrush nows about SN. But first have alook at the Page Performance Score on Google (Detailled report available [here](https://pagespeed.web.dev/analysis/https-stacker-news/pjnc9jgscy?form_factor=mobile)). **Performance** and **Accessibility** looks have really low score!
| Desktop | Mobile |
|---|---|
|  |  |
|  |  |
Now let's see what Semrush knows.
# Analytics
General view on your metrics and performance trend compared to last 30 days.


See estimations of stacker.news's desktop and mobile traffic based on Semrush’s proprietary AI and machine learning algorithms, petabytes of clickstream data, and Big Data technologies.

Distribution of SN's organic traffic and keywords by country. The Organic Traffic graph shows changes in the amount of estimated organic and paid traffic driven to the SN analyzed domain over time.

| Organic Search | Backlinks Analytics |
|---|---|
| |  |
| Position Changes Trend | Top Page Changes |
|---|---|
| |  |
|This trend allows you to monitor organic traffic changes, as well as improved and declined positions.| Top pages with the biggest traffic changes over the last 28 days. |

# Competitors

The Competitive Positioning Map shows the strengths and weaknesses of SN competitive domains' presence in organic search results. Data visualizations are based on the domain's organic traffic and the number of keywords that they are ranking for in Google's top 20 organic search results. The larger the circle, the more visibility a domain has. Below, a list of domains an analyzed domain is competing against in Google's top 20 organic search results.

# Referring Domains


# Daily Stats
| Organic Traffic | Organic Keywords | Backlinks |
|---|---|---|
| 976 | 15.9K | 126K |
| `-41.87%` | `-16.4%` | `-1.62%` |
### 📝 Traffic Drop
Traffic downturn detected! It appears SN domain experienced a traffic drop of 633 in the last 28 days. Take a closer look at these pages with significant traffic decline and explore areas for potential improvement. Here are the pages taking the biggest hits:
- https://stacker.news/items/723989 ⬇️ -15
- https://stacker.news/items/919813 ⬇️ -12
- https://stacker.news/items/783355 ⬇️ -5
### 📉 Decreased Authority Score
Uh-oh! Your Authority score has dropped from 26 to 25. Don't worry, we're here to assist you. Check out the new/lost backlinks in the Backlink Analytics tool to uncover insights on how to boost your authority.
### 🌟 New Keywords
Opportunity Alert! Targeting these keywords could help you increase organic traffic quickly and efficiently. We've found some low-hanging fruits for you! Take a look at these keywords:
- nitter.moomoo.me — Volume 70
- 0xchat — Volume 30
- amethyst nostr — Volume 30
### 🛠️ Broken Pages
This could hurt the user experience and lead to a loss in organic traffic. Time to take action: amend those pages or set up redirects. Here below, few pages on SN domain that are either broken or not _crawlable_:
- https://stacker.news/404 — 38 backlinks
- https://stacker.news/api/capture/items/91154 — 24 backlinks
- https://stacker.news/api/capture/items/91289 — 24 backlinks
Dees this post give you some insights? Hope so, comment below if you have any SEO suggestion? Mine is to improve or keep an eye on Accessibility!
One of the major issues I found is that SN does not have a `robots.txt`, a key simple text file that allow crawlers to read or not-read the website for indexing purposes. @k00b and @ek is that voluntary?
Here are other basic info to improve the SEO score and for those of us that want to learn more:
- Intro to Accessibility: https://www.w3.org/WAI/fundamentals/accessibility-intro/
- Design for Accessibility: https://www.w3.org/WAI/tips/designing/
- Web Accessibility Best Practices: https://www.freecodecamp.org/news/web-accessibility-best-practices/
originally posted at https://stacker.news/items/925433
-

@ a5142938:0ef19da3
2025-04-04 10:08:42
**Have you found a natural product? Share it here by commenting on this page!**
This site only lists durable-use products and objects. Consumables (food, cosmetics, fuels, etc.) are not included.
To be listed, the product must be made of natural materials.
[Learn more about materials](https://www.origin-nature.com/post/pnco0inysorhojxvsyil3/)
You can copy and paste the template below and fill in the information you have. Other contributors can complete any missing details.
Each piece of information added (name, material, link, shipping area, etc.) and validated is considered a contribution.
[Learn more about contributions](https://www.origin-nature.com/post/laf_xjasf4kgunxvozhkm/)
### New product
- Product name :
- Product image (link):
- Short description:
- Categories:
- Brand or manufacturer:
- Composition (materials used, including unknown elements):
- Links to buy (and shipping area):
- Other information (place of manufacture, certifications…):
If you do not wish to log in, you can still contribute via [this form](https://www.origin-nature.com/post/pnef53sfo5jaejkactcib/). However, your contribution will not be counted towards a reward.
[Learn more about rewards](https://www.origin-nature.com/post/xz20q6pw42fd9ijaewnn6/)
---
This article is published on [origin-nature.com](https://www.origin-nature.com/)
[Voir cet article en français](https://www.origine-nature.com/post/nicmc-eandjr_vcz4_hsr/)
-

@ 30876140:cffb1126
2025-03-26 04:58:21
The portal is closing.
The symphony comes to an end.
Ballet, a dance of partners,
A wish of hearts,
Now closing its curtains.
I foolishly sit
Eagerly waiting
For the circus to begin again,
As crowds file past me,
Chuckles and popcorn falling,
Crushed under foot,
I sit waiting
For the show to carry on.
But the night is now over,
The laughs have been had,
The music been heard,
The dancers are gone now
Into the nightbreeze chill.
Yet still, I sit waiting,
The empty chairs yawning,
A cough, I start, could it be?
Yet the lights now go out,
And now without my sight
I am truly alone in the theater.
Yet still, I am waiting
For the show to carry on,
But I know that it won’t,
Yet still, I am waiting.
Never shall I leave
For the show was too perfect
And nothing perfect should ever be finished.
-

@ e4950c93:1b99eccd
2025-04-04 09:51:53
**Vous connaissez une marque proposant des alternatives naturelles ? Partagez-la ici en commentant cette page !**
Copiez-collez le modèle ci-dessous et remplissez les informations que vous avez. D’autres contribut-eur-rice-s pourront compléter les éléments manquants.
Pour être référencée, la marque doit proposer une partie au moins de ses produits en matières naturelles.
[En savoir plus sur les matières](https://www.origine-nature.com/post/ftjhuxe9mvxkhoedyz36i/)
Chaque information ajoutée (nom, lien, catégorie, etc.) et validée est considérée comme une contribution.
[En savoir plus sur les contributions](https://www.origine-nature.com/post/26bj5f7bwyps6ecp5v62t)
### Nouvelle marque ou fabricant
- Nom de la marque :
- Image représentant des produits de la marque (lien, idéalement depuis le site de la marque) :
- Courte description :
- Catégories de produits proposées :
- Matières utilisées pour ses produits :
- Site internet de la marque :
- Autres informations (lieu de production, labels…) :
Si vous ne souhaitez pas vous connecter, vous pouvez tout de même contribuer via [ce formulaire](https://www.origine-nature.com/post/qcp-smvj1v78_-7iceyrd/). Cependant, votre contribution ne sera pas comptabilisée pour une rétribution.
[En savoir plus sur les rétributions](https://www.origine-nature.com/post/7hdgcdwt76dprobc9g_2f/)
---
Cet article est publié sur [origine-nature.com](https://www.origine-nature.com/)
[See this article in English](https://www.origin-nature.com/post/unjmwarjg7ojb9uwantvt/)
-

@ 04c915da:3dfbecc9
2025-03-25 17:43:44
One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-

@ ecda4328:1278f072
2025-03-25 10:00:52
**Kubernetes and Linux Swap: A Practical Perspective**
After reviewing kernel documentation on swap management (e.g., [Linux Swap Management](https://www.kernel.org/doc/gorman/html/understand/understand014.html)), [KEP-2400 (Kubernetes Node Memory Swap Support)](https://github.com/kubernetes/enhancements/blob/master/keps/sig-node/2400-node-swap/README.md), and community discussions like [this post on ServerFault](https://serverfault.com/questions/881517/why-disable-swap-on-kubernetes), it's clear that the topic of swap usage in modern systems—especially Kubernetes environments—is nuanced and often contentious. Here's a practical synthesis of the discussion.
---
### The Rationale for Disabling Swap
We disable SWAP on our Linux servers to ensure stable and predictable performance by relying on available RAM, avoiding the performance degradation and unnecessary I/O caused by SWAP usage. If an application runs out of memory, it’s usually due to insufficient RAM allocation or a memory leak, and enabling SWAP only worsens performance for other applications. It's more efficient to let a leaking app restart than to rely on SWAP to prevent OOM crashes.
With modern platforms like Kubernetes, memory requests and limits are enforced, ensuring apps use only the RAM allocated to them, while avoiding overcommitment to prevent resource exhaustion.
Additionally, disabling swap may protect data from **data remanence attacks**, where sensitive information could potentially be recovered from the swap space even after a process terminates.
---
### Theoretical Capability vs. Practical Deployment
Linux provides a powerful and flexible memory subsystem. With proper tuning (e.g., swappiness, memory pinning, cgroups), it's technically possible to make swap usage efficient and targeted. Seasoned sysadmins often argue that disabling swap entirely is a lazy shortcut—an avoidance of learning how to use the tools properly.
But Kubernetes is not a traditional system. It's an orchestrated environment that favors predictability, fail-fast behavior, and clear isolation between workloads. Within this model:
- Memory **requests and limits** are declared explicitly.
- The scheduler makes decisions based on RAM availability, not total virtual memory (RAM + swap).
- Swap introduces **non-deterministic performance** characteristics that conflict with Kubernetes' goals.
So while the kernel supports intelligent swap usage, Kubernetes **intentionally sidesteps** that complexity.
---
### Why Disable Swap in Kubernetes?
1. **Deterministic Failure > Degraded Performance**\
If a pod exceeds its memory allocation, it should fail fast — not get throttled into slow oblivion due to swap. This behavior surfaces bugs (like memory leaks or poor sizing) early.
2. **Transparency & Observability**\
With swap disabled, memory issues are clearer to diagnose. Swap obfuscates root causes and can make a healthy-looking node behave erratically.
3. **Performance Consistency**\
Swap causes I/O overhead. One noisy pod using swap can impact unrelated workloads on the same node — even if they’re within their resource limits.
4. **Kubernetes Doesn’t Manage Swap Well**\
Kubelet has historically lacked intelligence around swap. As of today, Kubernetes still doesn't support swap-aware scheduling or per-container swap control.
5. **Statelessness is the Norm**\
Most containerized workloads are designed to be ephemeral. Restarting a pod is usually preferable to letting it hang in a degraded state.
---
### "But Swap Can Be Useful..."
Yes — for certain workloads (e.g., in-memory databases, caching layers, legacy systems), there may be valid reasons to keep swap enabled. In such cases, you'd need:
- Fine-tuned `vm.swappiness`
- Memory pinning and cgroup-based control
- Swap-aware monitoring and alerting
- Custom kubelet/systemd integration
That's possible, but **not standard practice** — and for good reason.
---
### Future Considerations
Recent Kubernetes releases have introduced [experimental swap support](https://kubernetes.io/blog/2023/08/24/swap-linux-beta/) via [KEP-2400](https://github.com/kubernetes/enhancements/blob/master/keps/sig-node/2400-node-swap/README.md). While this provides more flexibility for advanced use cases — particularly Burstable QoS pods on cgroupsv2 — swap remains disabled by default and is not generally recommended for production workloads unless carefully planned. The rationale outlined in this article remains applicable to most Kubernetes operators, especially in multi-tenant and performance-sensitive environments.
Even the Kubernetes maintainers acknowledge the inherent trade-offs of enabling swap. As noted in [KEP-2400's Risks and Mitigations section](https://github.com/kubernetes/enhancements/blob/master/keps/sig-node/2400-node-swap/README.md), swap introduces unpredictability, can severely degrade performance compared to RAM, and complicates Kubernetes' resource accounting — increasing the risk of noisy neighbors and unexpected scheduling behavior.
Some argue that with emerging technologies like **non-volatile memory** (e.g., Intel Optane/XPoint), swap may become viable again. These systems promise near-RAM speed with large capacity, offering hybrid memory models. But these are not widely deployed or supported in mainstream Kubernetes environments yet.
---
### Conclusion
Disabling swap in Kubernetes is not a lazy hack — it’s a **strategic tradeoff**. It improves transparency, predictability, and system integrity in multi-tenant, containerized environments. While the kernel allows for more advanced configurations, Kubernetes intentionally simplifies memory handling for the sake of reliability.
If we want to revisit swap usage, it should come with serious planning: proper instrumentation, swap-aware observability, and potentially upstream K8s improvements. Until then, **disabling swap remains the sane default**.
-

@ 57d1a264:69f1fee1
2025-03-24 17:08:06
Nice podcast with @sbddesign and @ConorOkus about bitcoin payments.
https://www.youtube.com/watch?v=GTSqoFKs1cE
In this episode, Conor, Open Source product manager at Spiral & Stephen, Product Designer at Voltage & Co founder of ATL Bitlab join Stephan to discuss the current state of Bitcoin user experience, particularly focusing on payments and the challenges faced by users. They explore the comparison between Bitcoin and physical cash, the Western perspective on Bitcoin payments, and the importance of user experience in facilitating Bitcoin transactions.
They also touch upon various payment protocols like #BOLT11, #LNURL, and #BOLT12, highlighting the need for interoperability and better privacy features in the Bitcoin ecosystem. The discussion also covers resources available for developers and designers to enhance wallet usability and integration.
@StephanLivera Official Podcast Episode: https://stephanlivera.com/646
### Takeaways
🔸Bitcoin has excelled as a savings technology.
🔸The payments use case for Bitcoin still needs improvement.
🔸User experience is crucial for Bitcoin adoption.
🔸Comparing Bitcoin to cash highlights privacy concerns.
🔸Western users may not see a payments problem.
🔸Regulatory issues impact Bitcoin payments in the West.
🔸User experience challenges hinder Bitcoin transactions.
🔸Different payment protocols create compatibility issues.
🔸Community collaboration is essential for Bitcoin's future.
🔸Improving interoperability can enhance Bitcoin payments. Wallet compatibility issues can create negative user impressions.
🔸Designers can significantly improve wallet user experience.
🔸Testing compatibility between wallets is essential for user satisfaction.
🔸Tether's integration may boost Bitcoin adoption.
🔸Developers should prioritize payment capabilities before receiving capabilities.
🔸Collaboration between designers and developers can lead to better products.
🔸User experience improvements can be low-hanging fruit for wallet projects.
🔸A global hackathon aims to promote miner decentralization.
🔸Resources like BOLT12 and the Bitcoin Design Guide are valuable for developers.
🔸Engaging with the community can lead to innovative solutions.
### Timestamps
([00:00](/watch?v=GTSqoFKs1cE)) - Intro
([01:10](/watch?v=GTSqoFKs1cE&t=70s)) - What is the current state of Bitcoin usage - Payments or Savings?
([04:32](/watch?v=GTSqoFKs1cE&t=272s)) - Comparing Bitcoin with physical cash
([07:08](/watch?v=GTSqoFKs1cE&t=428s)) - What is the western perspective on Bitcoin payments?
([11:30](/watch?v=GTSqoFKs1cE&t=690s)) - Would people use Bitcoin more with improved UX?
([17:05](/watch?v=GTSqoFKs1cE&t=1025s)) - Exploring payment protocols: Bolt11, LNURL, Bolt12 & BIP353
([30:14](/watch?v=GTSqoFKs1cE&t=1814s)) - Navigating Bitcoin wallet compatibility challenges
([34:45](/watch?v=GTSqoFKs1cE&t=2085s)) - What is the role of designers in wallet development?
([43:13](/watch?v=GTSqoFKs1cE&t=2593s)) - Rumble’s integration of Tether & Bitcoin; The impact of Tether on Bitcoin adoption
([51:22](/watch?v=GTSqoFKs1cE&t=3082s)) - Resources for wallet developers and designers
### Links:
• [https://x.com/conorokus](https://x.com/conorokus)
• [https://x.com/StephenDeLorme](https://x.com/StephenDeLorme)
• [https://bolt12.org/](https://bolt12.org/)
• [https://twelve.cash/](https://twelve.cash)
• [https://bitcoin.design/guide/](https://bitcoin.design/guide/)
• Setting Up Bitcoin Tips for Streamers](/watch?v=IWTpSN8IaLE)
originally posted at https://stacker.news/items/923714
-

@ a5142938:0ef19da3
2025-04-04 09:14:07
Rewards are an experimental approach to sharing the value created by contributors to this site, through a revenue-sharing system based on the following conditions:
- Any revenue generated by the site each month is distributed over the **following 12 months**, ensuring long-term visibility and smoothing out monthly variations.
- On the **1st of each month**, half of the revenue is distributed among all contributors, in proportion to the number of their validated contributions.
- Contributions remain valid indefinitely, but rewards are only distributed to contributors who have made **at least one validated contribution in the past 12 months**.
### Payment Method
Rewards are paid via the Lightning network, in sats (the smallest unit of Bitcoin).
To receive payments, you must have a NOSTR account linked to a Lightning wallet.
To receive them, the NOSTR account used to contribute must be linked to a Lightning wallet.
**💡 New to these tools?**
- **Don’t have a NOSTR account yet?** A simple way to get started is to create one on an open-source NOSTR client like [yakihonne.com](https://yakihonne.com/) to set up your profile and wallet there. Then, retrieve your NOSTR keys (from the settings) and save them in a secure vault like [nsec.app](https://use.nsec.app/home) to log in here and start contributing.
- **Already started contributing on this site?** Make sure to securely store your NOSTR keys in a vault like [nsec.app](https://use.nsec.app/home). You can also log in with them on [yakihonne.com](https://yakihonne.com/) to set up your profile.
- You can also contribute directly from yakihonne.com by commenting on Origine Nature’s articles.
Learn more about contributions
-

@ 866e0139:6a9334e5
2025-03-24 10:50:59
**Autor:** *Ludwig F. Badenhagen.* *Dieser Beitrag wurde mit dem* *[Pareto-Client](https://pareto.space/read)* *geschrieben.*
***
Einer der wesentlichen Gründe dafür, dass während der „Corona-Pandemie“ so viele Menschen den Anweisungen der Spitzenpolitiker folgten, war sicher der, dass diese Menschen den Politikern vertrauten. Diese Menschen konnten sich nicht vorstellen, dass Spitzenpolitiker den Auftrag haben könnten, die Bürger analog klaren Vorgaben zu belügen, zu betrügen und sie vorsätzlich (tödlich) zu verletzen. Im Gegenteil, diese gutgläubigen Menschen waren mit der Zuversicht aufgewachsen, dass Spitzenpolitiker den Menschen dienen und deren Wohl im Fokus haben (müssen). Dies beteuerten Spitzenpolitiker schließlich stets in Talkshows und weiteren Medienformaten. Zwar wurden manche Politiker auch bei Fehlverhalten erwischt, aber hierbei ging es zumeist „nur“ um Geld und nicht um Leben. Und wenn es doch einmal um Leben ging, dann passieren die Verfehlungen „aus Versehen“, aber nicht mit Vorsatz. So oder so ähnlich dachte die Mehrheit der Bürger.
Aber vor 5 Jahren änderte sich für aufmerksame Menschen alles, denn analog dem Lockstep-Szenario der Rockefeller-Foundation wurde der zuvor ausgiebig vorbereitete Plan zur Inszenierung der „Corona-Pandemie“ Realität. Seitdem wurde so manchem Bürger, der sich jenseits von Mainstream-Medien informierte, das Ausmaß der unter dem Vorwand einer erfundenen Pandemie vollbrachten Taten klar. Und unverändert kommen täglich immer neue Erkenntnisse ans Licht. Auf den Punkt gebracht war die Inszenierung der „Corona-Pandemie“ ein Verbrechen an der Menschheit, konstatieren unabhängige Sachverständige.
Dieser Beitrag befasst sich allerdings nicht damit, die vielen Bestandteile dieses Verbrechens (nochmals) aufzuzählen oder weitere zu benennen. Stattdessen soll beleuchtet werden, warum die Spitzenpolitiker sich so verhalten haben und ob es überhaupt nach alledem möglich ist, der Politik jemals wieder zu vertrauen? Ferner ist es ein Anliegen dieses Artikels, die weiteren Zusammenhänge zu erörtern. Und zu guter Letzt soll dargelegt werden, warum sich der große Teil der Menschen unverändert alles gefallen lässt.
**Demokratie**
Von jeher organisierten sich Menschen mit dem Ziel, Ordnungsrahmen zu erschaffen, welche wechselseitiges Interagieren regeln. Dies führte aber stets dazu, dass einige wenige alle anderen unterordneten. Der Grundgedanke, der vor rund 2500 Jahren formulierten Demokratie, verfolgte dann aber das Ziel, dass die Masse darüber entscheiden können soll, wie sie leben und verwaltet werden möchte. Dieser Grundgedanke wurde von den Mächtigen sowohl gehasst als auch gefürchtet, denn die Gefahr lag nahe, dass die besitzlosen Vielen beispielsweise mit einer schlichten Abstimmung verfügen könnten, den Besitz der Wenigen zu enteignen. Selbst Sokrates war gegen solch eine Gesellschaftsordnung, da die besten Ideen nicht durch die Vielen, sondern durch einige wenige Kluge und Aufrichtige in die Welt kommen. Man müsse die Vielen lediglich manipulieren und würde auf diese Weise quasi jeden Unfug umsetzen können. Die Demokratie war ein Rohrkrepierer.
**Die Mogelpackung „Repräsentative Demokratie“**
Erst im Zuge der Gründung der USA gelang der Trick, dem Volk die „Repräsentative Demokratie“ unterzujubeln, die sich zwar nach Demokratie anhört, aber mit der Ursprungsdefinition nichts zu tun hat. Man konnte zwischen zwei Parteien wählen, die sich mit ihren jeweiligen Versprechen um die Gunst des Volkes bewarben. Tatsächlich paktierten die Vertreter der gewählten Parteien (Politiker) aber mit den wirklich Mächtigen, die letztendlich dafür sorgten, dass diese Politiker in die jeweiligen exponierten Positionen gelangten, welche ihnen ermöglichten (und somit auch den wirklich Mächtigen), Macht auszuüben. Übrigens, ob die eine oder andere Partei „den Volkswillen“ für sich gewinnen konnte, war für die wirklich Mächtigen weniger von Bedeutung, denn der Wille der wirklich Mächtigen wurde so oder so, wenn auch in voneinander differierenden Details, umgesetzt.
Die Menschen waren begeistert von dieser Idee, denn sie glaubten, dass sie selbst „der Souverän“ seien. Schluss mit Monarchie sowie sonstiger Fremdherrschaft und Unterdrückung.
Die Mächtigen waren ebenfalls begeistert, denn durch die Repräsentative Demokratie waren sie selbst nicht mehr in der Schusslinie, weil das Volk sich mit seinem Unmut fortan auf die Politiker konzentrierte. Da diese Politiker aber vielleicht nicht von einem selbst, sondern von vielen anderen Wahlberechtigten gewählt wurden, lenkte sich der Groll der Menschen nicht nur ab von den wirklich Mächtigen, sondern auch ab von den Politikern, direkt auf „die vielen Idioten“ aus ihrer eigenen Mitte, die sich „ver-wählt“ hatten. Diese Lenkung des Volkes funktionierte so hervorragend, dass andere Länder die Grundprinzipien dieses Steuerungsinstrumentes übernahmen. Dies ist alles bei Rainer Mausfeld nachzulesen.
Ursprünglich waren die Mächtigen nur regional mächtig, sodass das Führen der eigenen Menschen(vieh)herde eher eine lokale Angelegenheit war. Somit mussten auch nur lokale Probleme gelöst werden und die Mittel zur Problemlösung blieben im eigenen Problembereich.
***
JETZT ABONNIEREN:
***[Hier](https://pareto.space/u/friedenstaube@pareto.space)*** *können Sie die Friedenstaube abonnieren und bekommen die Artikel in Ihr Postfach, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht).*
***
* Für **50 CHF/EURO** bekommen Sie ein Jahresabo der Friedenstaube.
* Für **120 CHF/EURO** bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
* Für **500 CHF/EURO** werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
* Ab **1000 CHF/EURO** werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
**Für Einzahlungen in CHF (Betreff: Friedenstaube):**
[](https://substackcdn.com/image/fetch/f_auto%2Cq_auto%3Agood%2Cfl_progressive%3Asteep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F3fdee17a-c22f-404e-a10c-7f87a7b8182a_2176x998.png)
**Für Einzahlungen in Euro:**
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
**Betreff: Friedenstaube**
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: <milosz@pareto.space> oder <kontakt@idw-europe.org>.
***
**Beherrschungsinstrumente der globalen Massenhaltung**
Im Zuge der territorialen Erweiterungen der „Besitzungen“ einiger wirklich Mächtiger wurden die Verwaltungs- und Beherrschungsinstrumente überregionaler. Und heute, zu Zeiten der globalen Vernetzung, paktieren die wirklich Mächtigen miteinander und beanspruchen die Weltherrschaft. Längst wird offen über die finale Realisierung einen Weltregierung, welche die Nationalstaaten „nicht mehr benötigt“, gesprochen. Dass sich Deutschland, ebenso wie andere europäische Staaten, der EU untergeordnet hat, dürfte auch Leuten nicht entgangen sein, die sich nur über die Tagesschau informieren. Längst steht das EU-Recht über dem deutschen Recht. Und nur kurze Zeit ist es her, als die EU und alle ihre Mitgliedsstaaten die WHO autonom darüber entscheiden lassen wollten, was eine Pandemie ist und wie diese für alle verbindlich „bekämpft“ werden soll. Eine spannende Frage ist nun, wer denn über der EU und der WHO sowie anderen Institutionen steht?
Diese Beschreibung macht klar, dass ein „souveränes Land“ wie das unverändert von der amerikanischen Armee besetzte Deutschland in der Entscheidungshierarchie an die Weisungen übergeordneter Entscheidungsorgane gebunden ist. An der Spitze stehen - wie kann es anders sein - die wirklich Mächtigen.
Aber was nützt es dann, Spitzenpolitiker zu wählen, wenn diese analog Horst Seehofer nichts zu melden haben? Ist das Wählen von Politikern nicht völlig sinnlos, wenn deren Wahlversprechen ohnehin nicht erfüllt werden? Ist es nicht so, dass die Menschen, welche ihre Stimme nicht behalten, sondern abgeben, das bestehende System nur nähren, indem sie Wahlergebnisse akzeptieren, ohne zu wissen, ob diese manipuliert wurden, aber mit der Gewissheit, dass das im Zuge des Wahlkampfes Versprochene auf keinen Fall geliefert wird? Aktive Wähler glauben trotz allem an die Redlichkeit und Wirksamkeit von Wahlen, und sie akzeptieren Wahlergebnisse, weil sie denken, dass sie von „so vielen Idioten, die falsch wählen“, umgeben sind, womit wir wieder bei der Spaltung sind. Sie glauben, der Stand des aktuellen Elends sei „selbst gewählt“.
**Die Wahl der Aufseher**
Stellen Sie sich bitte vor, Sie wären im Gefängnis, weil Sie einen kritischen Artikel mit „gefällt mir“ gekennzeichnet haben oder weil Sie eine „Kontaktschuld“ trifft, da in Ihrer Nachbarschaft ein „verschwörerisches Symbol“ von einem „aufmerksamen“ Nachbarn bei einer „Meldestelle“ angezeigt wurde oder Sie gar eine Tat, „unterhalb der Strafbarkeitsgrenze“ begangen hätten, dann würden Sie möglicherweise mit Maßnahmen bestraft, die „keine Folter wären“. Beispielsweise würde man Sie während Ihrer „Umerziehungshaft“ mit Waterboarding, Halten von Stresspositionen, Dunkelhaft etc. dabei „unterstützen“, „Ihre Verfehlungen zu überdenken“. Stellen Sie sich weiterhin vor, dass Sie, so wie alle anderen Inhaftierten, an der alle vier Jahre stattfindenden Wahl der Aufseher teilnehmen könnten, und Sie hätten auch einen Favoriten, der zwar Waterboarding betreibt, aber gegen alle anderen Maßnahmen steht. Sie hätten sicher allen Grund zur Freude, wenn Sie Ihren Kandidaten durchbringen könnten, oder? Aber was wäre, wenn der Aufseher Ihrer Wahl dann dennoch alle 3 „Nicht-Folter-Maßnahmen“ anwenden würde, wie sämtliche anderen Aufseher zuvor? Spätestens dann müssten Sie sich eingestehen, dass es der Beruf des Aufsehers ist, Aufseher zu sein und dass er letztendlich tut, was ihm „von oben“ aufgetragen wird. Andernfalls verliert er seinen Job. Oder er verunfallt oder gerät in einen Skandal etc. So oder so, er verliert seinen Job - und den erledigt dann ein anderer Aufseher.
Die Wahl des Aufsehers ändert wenig, solange Sie sich im System des Gefängnisses befinden und der Aufseher integraler Bestandteil dieses Systems ist. Zur Realisierung einer tatsächlichen Änderung müssten Sie dort herauskommen.
Dieses Beispiel soll darstellen, dass alles in Hierarchien eingebunden ist. Die in einem System eingebundenen Menschen erfüllen ihre zugewiesenen Aufgaben, oder sie werden bestraft.
**Das aktuelle System schadet dem Volk**
Auch in der staatlichen Organisation von Menschen existieren hierarchische Gliederungen. Eine kommunale Selbstverwaltung gehört zum Kreis, dieser zum Land, dieses zum Staat, dieser zur EU, und diese - zu wem auch immer. Und vereinnahmte Gelder fließen nach oben. Obwohl es natürlich wäre, dass die Mittel dorthin fließen, wo sie der Allgemeinheit und nicht einigen wenigen dienen, also nach unten.
Warum muss es also eine Weltregierung geben? Warum sollen nur einige Wenige über alle anderen bestimmen und an diesen verdienen (Nahrung, Medikamente, Krieg, Steuern etc.)? Warum sollen Menschen, so wie Vieh, das jemandem „gehört“, mit einem Code versehen und bereits als Baby zwangsgeimpft werden? Warum müssen alle Transaktionen und sämtliches Verhalten strickt gesteuert, kontrolliert und bewertet werden?
Viele Menschen werden nach alledem zu dem Schluss kommen, dass solch ein System nur einigen wenigen wirklich Mächtigen und deren Helfershelfern nützt. Aber es gibt auch eine Gruppe Menschen, für die im Land alles beanstandungsfrei funktioniert. Die Spaltung der Menschen ist perfekt gelungen und sofern die eine Gruppe darauf wartet, dass die andere „endlich aufwacht“, da die Fakten doch auf dem Tisch liegen, so wird sie weiter warten dürfen.
Julian Assange erwähnte einst, dass es für ihn eine unglaubliche Enttäuschung war, dass ihm niemand half. Assange hatte Ungeheuerlichkeiten aufgedeckt. Es gab keinen Aufstand. Assange wurde inhaftiert und gefoltert. Es gab keinen Aufstand. Assange sagte, er hätte nicht damit gerechnet, dass die Leute „so unglaublich feige“ seien.
Aber womit rechnete er den stattdessen? Dass die Massen „sich erheben“. Das gibt es nur im Film, denn die Masse besteht aus vielen maximal Indoktrinierten, die sich wie Schafe verhalten, was als Züchtungserfolg der Leute an den Schalthebeln der Macht und deren Herren, den wirklich Mächtigen, anzuerkennen ist. Denn wer mächtig ist und bleiben möchte, will sicher keine problematischen Untertanen, sondern eine gefügige, ängstliche Herde, die er nach Belieben ausbeuten und steuern kann. Wenn er hierüber verfügt, will er keinen Widerstand.
Ob Corona, Krieg, Demokratie- und Klimarettung oder Meinungsäußerungsverbote und Bürgerrechte, die unterhalb der Strafbarkeitsgrenze liegen, all diese und viele weitere Stichworte mehr sind es, die viele traurig und so manche wütend machen.
Auch das Mittel des Demonstrierens hat sich als völlig wirkungslos erwiesen. Die vielen gruseligen Videoaufnahmen über die massivsten Misshandlungen von Demonstranten gegen die Corona-Maßnahmen führen zu dem Ergebnis, dass die Exekutive ihr Gewaltmonopol nutzt(e), um die Bevölkerung gezielt zu verletzen und einzuschüchtern. Bekanntlich kann jede friedliche Demonstration zum Eskalieren gebracht werden, indem man Menschen in die Enge treibt (fehlender Sicherheitsabstand) und einige V-Leute in Zivil mit einschlägigen Flaggen und sonstigen „Symbolen“ einschleust, die für Krawall sorgen, damit die gepanzerten Kollegen dann losknüppeln und die scharfen Hunde zubeißen können. So lauten zumindest die Berichte vieler Zeitzeugen und so ist es auch auf vielen Videos zu sehen. Allerdings nicht im Mainstream.
Dieses Vorgehen ist deshalb besonders perfide, weil man den Deutschen ihre Wehrhaftigkeit aberzogen hat. Nicht wehrfähige Bürger und eine brutale Staatsmacht mit Gewaltmonopol führen zu einem Gemetzel bei den Bürgern.
Ähnliches lässt sich auch in zivilen Lebenssituationen beobachten, wenn die hiesige zivilisierte Bevölkerung auf „eingereiste“ Massenvergewaltiger und Messerstecher trifft, die über ein anderes Gewalt- und Rechtsverständnis verfügen als die Einheimischen.
**System-Technik**
Die These ist, dass es eine Gruppe von global agierenden Personen gibt, welche das Geschehen auf der Erde zunehmend wirksam zu ihrem individuellen Vorteil gestaltet. Wie sich diese Gruppe definiert, kann bei John Coleman (Das Komitee der 300) und David Icke nachgelesen werden. Hierbei handelt es ich um Autoren, die jahrzehntelang analog streng wissenschaftlichen Grundlagen zu ihren Themen geforscht haben und in ihren jeweiligen Werken sämtliche Quellen benennen. Diese Autoren wurden vom Mainstream mit dem Prädikatsmerkmal „Verschwörungstheoretiker“ ausgezeichnet, wodurch die Ergebnisse Ihrer Arbeiten umso glaubwürdiger sind.
Diese mächtige Gruppe hat mit ihren Schergen nahezu den gesamten Planeten infiltriert, indem sie Personen in führenden Positionen in vielen Belangen größtmögliche Freiheiten sowie Schutz gewährt, aber diesen im Gegenzug eine völlige Unterwerfung bei Kernthemen abfordert. Die Motivatoren für diese Unterwerfung sind, abgesehen von materiellen Zuwendungen, auch „Ruhm und Ehre sowie Macht“. Manchmal wird auch Beweismaterial für begangene Verfehlungen (Lolita-Express, Pizzagate etc.) genutzt, um Forderungen Nachdruck zu verleihen. Und auch körperliche Bestrafungen der betroffenen Person oder deren Angehörigen zählen zum Repertoire der Motivatoren. Letztendlich ähnlich den Verhaltensweisen in einem Mafia-Film.
Mit dieser Methodik hat sich diese mächtige Gruppe im Laufe von Jahrhunderten! eine Organisation erschaffen, welche aus Kirchen, Parteien, Firmen, NGO, Vereinen, Verbänden und weiteren Organisationsformen besteht. Bestimmte Ämter und Positionen in Organisationen können nur von Personen eingenommen und gehalten werden, die „auf Linie sind“.
Die Mitglieder der Gruppe tauchen in keiner Rubrik wie „Die reichsten Menschen der Welt“ auf, sondern bleiben fern der Öffentlichkeit. Wer jemanden aus ihren Reihen erkennt und beschuldigt, ist ein „Antisemit“ oder sonstiger Übeltäter und wird verfolgt und bekämpft. Über mächtige Vermögensverwaltungskonzerne beteiligen sich die Mitglieder dieser Gruppe anonym an Unternehmen in Schlüsselpositionen in einer Dimension, die ihnen wesentlichen Einfluss auf die Auswahl der Topmanager einräumt, sodass die jeweilige Unternehmenspolitik nach Vorgaben der Gruppe gestaltet wird.
Die Gruppe steuert das Geldsystem, von dem sich der Planet abhängig zu sein wähnt. Hierzu eine Erläuterung: Ein Staat wie Deutschland ist bekanntlich maximal verschuldet. Man stelle sich vor, ein unliebsamer Politiker würde entgegen sämtlicher „Brandmauern“ und sonstiger Propaganda und Wahlmanipulationen gewählt, das Land zu führen, dann könnte dieser keine Kredit über 500 Mrd. Euro bei der nächsten Sparkasse beantragen, sondern wäre auf die Mächtigen dieser Welt angewiesen. Jeder weiß, dass Deutschland als Staat kein funktionierendes Geschäftsmodell hat und somit nicht in der Lage ist, solch ein Darlehen zurückzuzahlen. Welche Motivation sollte also jemand haben, einem Land wie Deutschland so viel Geld ohne Aussicht auf Rückführung zu geben? Es leuchtet ein, dass dieser Politiker andere Gefälligkeiten anbieten müsste, um das Darlehen zu bekommen. Im Falle einer Weigerung zur Kooperation könnte der Staatsapparat mit seinen Staatsdienern, Bürgergeld- und Rentenempfänger etc. nicht mehr bezahlt werden und dieser Politiker wäre schnell wieder weg. Er würde medial hingerichtet. Es ist somit davon auszugehen, dass ein Spitzenpolitiker dieser Tage nicht über viele Optionen verfügt, denn er übernimmt eine Situation, die von seinen Vorgängern erschaffen wurde. Trotz alledem darauf zu hoffen, dass es einen anderen Politiker geben könnte, mit dem dann alles wieder gut wird, mutet ziemlich infantil an.
Dass ein Großteil der Medien von Zuwendungen abhängig ist, dürfte ebenfalls leicht nachzuvollziehen sein, denn der gewöhnliche Bürger zahlt nichts für den Content der MSM. Abhängig davon, von wem (Regierung, Philanthrop, Konzern etc.) ein Medium am Leben gehalten wird, gestalten sich auch dessen Inhalte. Und wenn angewiesen wird, dass ein Politiker medial hingerichtet werden soll, dann bedient die Maschinerie das Thema. Man beobachte einfach einmal, dass Politiker der Kartell-Parteien völlig anders behandelt werden als solche jenseits der „Brandmauer“. Und der Leser, der solche Auftragsarbeiten kostenlos liest, ist der Konsument, für dessen Indoktrination die Finanziers der Verlage gerne zahlen. Mittlerweile kann durch die Herrschaft über die Medien und die systematische Vergiftung der Körper und Geister der Population die öffentliche Meinung gesteuert werden. Die überwiegende Zahl der Deutschen scheint nicht mehr klar denken zu können.
Wer sich das aktuelle Geschehen in der deutschen Politik mit klarem Verstand ansieht, kommt nicht umhin, eine Fernsteuerung der handelnden Politiker in Betracht zu ziehen. Aber was soll daran verwundern? Sind es deshalb „böse Menschen“? Sind die in „Forschungslaboren“ arbeitenden Quäler von „Versuchstieren“ böse Menschen? Sind der Schlächter, der Folterer und der Henker böse Menschen? Oder der knüppelnde Polizist? Es handelt sich zunächst einmal um Personen, die einen Vorteil dadurch haben, Ihrer Tätigkeit nachzugehen. Sie sind integrale Bestandteile eines Belohnungssystems, welches von oben nach unten Anweisungen gibt. Und wenn diese Anweisungen nicht befolgt werden, führt dies für den Befehlsverweigerer zu Konsequenzen.
**Der klare Verstand**
Es ist nun eine spannende Frage, warum so viele Menschen sich solch eine Behandlung gefallen lassen? Nun, das ist relativ einfach, denn das angepasste Verhalten der Vielen ist nichts anderes als ein Züchtungserfolg der Wenigen.
Die Psyche der Menschen ist ebenso akribisch erforscht worden wie deren Körperfunktionen. Würden die Menschen von den wirklich Mächtigen geliebt, dann würde genau gewusst, wie sie zu behandeln und mit ihren jeweiligen Bedürfnissen zu versorgen sind. Stattdessen werden die Menschen aber als eine Einnahmequelle betrachtet. Dies manifestiert sich exemplarisch in folgenden Bereichen:
1. Das Gesundheitssystem verdient nichts am gesunden Menschen, sondern nur am (dauerhaft) kranken, der um Schmerzlinderung bettelt. Bereits als Baby werden Menschen geimpft, was die jeweilige Gesundheit (mit Verweis auf die Werke von Anita Petek-Dimmer u. a.) nachhaltig negativ beeinflusst. Wer hat denn heute keine Krankheiten? Die „Experten“ des Gesundheitssystems verteufeln Vitamin D, Vitamin C, Lithium, die Sonne, Natur etc. und empfehlen stattdessen Präparate, die man patentieren konnte und mit denen die Hersteller viel Geld verdienen. Die Präparate heilen selten, sondern lindern bestenfalls zuvor künstlich erzeugte Leiden, und müssen oftmals dauerhaft eingenommen werden. Was ist aus den nicht Geimpften geworden, die alle sterben sollten? Sind diese nicht die einzigen Gesunden dieser Tage? Ist nicht jeder Geimpfte entweder permanent krank oder bereits tot? Abgesehen von denen, welche das Glück hatten, „Sonderchargen“ mit Kochsalz zu erhalten. \
\
Wem gehören die wesentlichen Player im Gesundheitswesen zu einem erheblichen Teil? Die Vermögensverwalter der wirklich Mächtigen.
2. Ähnlich gestaltet es sich bei der Ernährungsindustrie. Die von dort aus verabreichten Produkte sind die Ursachen für den Gesundheitszustand der deutschen Population. Das ist aber auch irgendwie logisch, denn wer sich nicht falsch ernährt und gesund bleibt, wird kein Kunde des Gesundheitswesens. \
\
Die Besitzverhältnisse in der Ernährungsindustrie ähneln denen im Gesundheitswesen, sodass am gleichen Kunden gearbeitet und verdient wird.
3. Die Aufzählung konnte nun über die meisten Branchen, in denen mit dem Elend der Menschen viel verdient werden kann, fortgesetzt werden. Waffen (BlackRock erhöhte beispielsweise seine Anteile an der Rheinmetall AG im Juni 2024 auf 5,25 Prozent. Der US-Vermögensverwalter ist damit der zweitgrößte Anteilseigner nach der französischen Großbank Société Générale.), Energie, Umwelt, Technologie, IT, Software, KI, Handel etc.
Wie genau Chemtrails und Technologien wie 5G auf den Menschen und die Tiere wirken, ist ebenfalls umstritten. Aber ist es nicht seltsam, wie krank, empathielos, antriebslos und aggressiv viele Menschen heute sind? Was genau verabreicht man der Berliner Polizei, damit diese ihre Prügelorgien auf den Rücken und in den Gesichtern der Menschen wahrnehmen, die friedlich ihre Demonstrationsrechte wahrnehmen? Und was erhalten die ganzen zugereisten „Fachkräfte“, die mit Ihren Autos in Menschenmengen rasen oder auch Kinder und Erwachsene niedermessern?
Das Titelbild dieses Beitrags zeigt einige Gebilde, welche regelmäßig bei Obduktionen von Geimpften in deren Blutgefäßen gefunden werden. Wie genau wirken diese kleinen Monster? Können wir Menschen ihr Unverständnis und ihr Nicht-Aufwachen vorwerfen, wenn wir erkennen, dass diese Menschen maximal vergiftet wurden? Oder sollten einfach Lösungen für die Probleme dieser Zeit auch ohne den Einbezug derer gefunden werden, die offenbar nicht mehr Herr ihrer Sinne sind?
**Die Ziele der wirklich Mächtigen**
Wer sich entsprechende Videosequenzen der Bilderberger, des WEF und anderen „Überorganisationen“ ansieht, der erkennt schnell das Muster:
* Reduzierung der Weltpopulation um ca. 80 Prozent
* Zusammenbruch der Wirtschaft, damit diese von den Konzernen übernommen werden kann.
* Zusammenbruch der öffentlichen Ordnung, um eine totale Entwaffnung und eine totale Überwachung durchsetzen zu können.
* Zusammenbruch der Regierungen, damit die Weltregierung übernehmen kann.
Es ist zu überdenken, ob die Weltregierung tatsächlich das für die Vielen beste Organisationssystem ist, oder ob die dezentrale Eigenorganisation der jeweils lokalen Bevölkerung nicht doch die bessere Option darstellt. Baustellen würden nicht nur begonnen, sondern auch schnell abgearbeitet. Jede Region könnte bestimmen, ob sie sich mit Chemtrails und anderen Substanzen besprühen lassen möchte. Und die Probleme in Barcelona könnte die Menschen dort viel besser lösen als irgendwelche wirklich Mächtigen in ihren Elfenbeintürmen. Die lokale Wirtschaft könnte wieder zurückkommen und mit dieser die Eigenständigkeit. Denn die den wirklich Mächtigen über ihre Vermögensverwalter gehörenden Großkonzerne haben offensichtlich nicht das Wohl der Bevölkerung im Fokus, sondern eher deren Ausbeutung.
Das Aussteigen aus dem System ist die wahre Herkulesaufgabe und es bedarf sicher Mut und Klugheit, sich dieser zu stellen. Die Politiker, die unverändert die Narrative der wirklich Mächtigen bedienen, sind hierfür denkbar ungeeignet, denn sie verfolgen kein Lebensmodell, welches sich von Liebe und Mitgefühl geleitet in den Dienst der Gesamtheit von Menschen, Tieren und Natur stellt.
Schauen Sie einmal genau hin, denken Sie nach und fühlen Sie mit.
**Was tun?**
Jedes System funktioniert nur so lange, wie es unterstützt wird. Somit stellt sich die Frage, wie viele Menschen das System ignorieren müssen, damit es kollabiert, und auf welche Weise dieses Ignorieren durchzuführen ist? Merkbar ist, dass die große Masse der Verwaltungsangestellten krank und oder unmotiviert und somit nicht wirksam ist. Würden die entsprechenden Stellen massiv belastet und parallel hierzu keine Einnahmen mehr realisieren, wäre ein Kollaps nah. Die Prügelpolizisten aus Berlin können nicht überall sein und normale Polizisten arbeiten nicht gegen unbescholtene Bürger, sondern sorgen sich selbst um ihre Zukunft. Gewalt ist sicher keine Lösung, und sicher auch nicht erforderlich.
Wie eine gerechte Verwaltungsform aufgebaut werden muss? Einfach so, wie sie in den hiesigen Gesetzen beschrieben steht. Aber eine solche Organisationsform muss frei sein von Blockparteien und korrupten Politikern und weisungsgebundenen Richtern etc. Stattdessen werden Menschen benötigt, welche die Menschen lieben und ihnen nicht schaden wollen. Außerdem sollten diese Führungspersonen auch wirklich etwas können, und nicht nur „Politiker“ ohne weitere Berufserfahrungen sein.
***
Ludwig F. Badenhagen (Pseudonym, Name ist der Redaktion bekannt).
*Der Autor hat deutsche Wurzeln und betrachtet das Geschehen in Deutschland und Europa aus seiner Wahlheimat Südafrika. Seine Informationen bezieht er aus verlässlichen Quellen und insbesondere von Menschen, die als „Verschwörungstheoretiker“, „Nazi“, „Antisemit“ sowie mit weiteren Kampfbegriffen der dortigen Systemakteure wie Politiker und „Journalisten“ diffamiert werden. Solche Diffamierungen sind für ihn ein Prädikatsmerkmal. Er ist international agierender Manager mit einem globalen Netzwerk und verfügt hierdurch über tiefe Einblicke in Konzerne und Politik.*
***
**Not yet on** **[Nostr](https://nostr.com/)** **and want the full experience?** Easy onboarding via **[Start.](https://start.njump.me/)**
-

@ 3104fbbf:ac623068
2025-04-04 06:58:30

## **Introduction**
If you have a functioning brain, it’s impossible to fully stand for any politician or align completely with any political party. The solutions we need are not found in the broken systems of power but in individual actions and local initiatives. Voting for someone may be your choice, but relying solely on elections every few years as a form of political activism is a losing strategy. People around the world have fallen into the trap of thinking that casting a ballot once every four years is enough, only to return to complacency as conditions worsen. Voting for the "lesser of two evils" has been the norm for decades, yet expecting different results from the same flawed system is naive at best.
The truth is, governments are too corrupt to save us. In times of crisis, they won’t come to your aid—instead, they will tighten their grip, imposing more surveillance, control, and wealth extraction to benefit the oligarch class. To break free from this cycle, we must first protect ourselves individually—financially, geographically, and digitally—alongside our families.
Then, we must organize and build resilient local communities. These are the only ways forward. History has shown us time and again that the masses are easily deceived by the political circus, falling for the illusion of a "savior" who will fix everything. But whether right, center, or left, the story remains the same: corruption, lies, and broken promises. If you possess a critical and investigative mind, you know better than to place your trust in politicians, parties, or self-proclaimed heroes. The real solution lies in free and sovereign individuals who reject the herd mentality and take responsibility for their own lives.
From the beginning of time, true progress has come from individuals who think for themselves and act independently. The nauseating web of politicians, billionaires, and oligarchs fighting for power and resources has never been—and will never be—the answer to our problems. In a world increasingly dominated by corrupted governments, NGOs, and elites, ordinary people must take proactive steps to protect themselves and their families.
---
## **1. Financial Protection: Reclaiming Sovereignty Through Bitcoin**
Governments and central banks have long manipulated fiat currencies, eroding wealth through inflation and bailouts that transfer resources to the oligarch class. Bitcoin, as a decentralized, censorship-resistant, and finite currency, offers a way out. Here’s what individuals can do:
- **Adopt Bitcoin as a Savings Tool**: Shift a portion of your savings into Bitcoin to protect against inflation and currency devaluation.
Bitcoin’s fixed supply (21 million coins) ensures it cannot be debased like fiat money.
- **Learn Self-Custody**: Store your Bitcoin in a hardware wallet or use open-source software wallets. Avoid centralized exchanges, which are vulnerable to government seizure or collapse.
- **Diversify Geographically:** Hold assets in multiple jurisdictions to reduce the risk of confiscation or capital controls. Consider offshore accounts or trusts if feasible.
- **Barter and Local Economies**: In times of crisis, local barter systems and community currencies can bypass failing national systems. Bitcoin can serve as a global medium of exchange in such scenarios.
---
## 2. Geographical Flexibility: Reducing Dependence on Oppressive Systems
Authoritarian regimes thrive on controlling populations within fixed borders. By increasing geographical flexibility, individuals can reduce their vulnerability:
- **Obtain Second Passports or Residencies**: Invest in citizenship-by-investment programs or residency permits in countries with greater freedoms and lower surveillance.
- **Relocate to Freer Jurisdictions**: Research and consider moving to regions with stronger property rights, lower taxes, and less government overreach.
- **Decentralize Your Life**: Avoid keeping all your assets, family, or business operations in one location. Spread them across multiple regions to mitigate risks.
---
## 3. Digital Privacy: Fighting Surveillance with Advanced Tools
The rise of mass surveillance and data harvesting by governments and corporations threatens individual freedom. Here’s how to protect yourself:
- **Use Encryption**: Encrypt all communications using tools like Signal or ProtonMail. Ensure your devices are secured with strong passwords and biometric locks.
- **Adopt Privacy-Focused Technologies**: Use Tor for anonymous browsing, VPNs to mask your IP address, and open-source operating systems like Linux to avoid backdoors.
- **Reject Surveillance Tech**: Avoid smart devices that spy on you (e.g., Alexa, Google Home). Opt for decentralized alternatives like Mastodon instead of Twitter, or PeerTube instead of YouTube.
- **Educate Yourself on Digital Privacy**: Learn about tools and practices that enhance your online privacy and security.
---
## 4. Building Resilient Local Communities: The Foundation of a Free Future
While individual actions are crucial, collective resilience is equally important. Governments are too corrupt to save populations in times of crisis—history shows they will instead impose more control and transfer wealth to the elite.
To counter this, communities must organize locally:
- **Form Mutual Aid Networks**: Create local groups that share resources, skills, and knowledge. These networks can provide food, medical supplies, and security during crises.
- **Promote Local Economies**: Support local businesses, farmers, and artisans. Use local currencies or barter systems to reduce dependence on centralized financial systems.
- **Develop Off-Grid Infrastructure**: Invest in renewable energy, water filtration, and food production to ensure self-sufficiency. Community gardens, solar panels, and rainwater harvesting are excellent starting points.
- **Educate and Empower**: Host workshops on financial literacy, digital privacy, and sustainable living. Knowledge is the most powerful tool against authoritarianism.
---
## 5. The Bigger Picture: Rejecting the Illusion of Saviors
The deep corruption within governments, NGOs, and the billionaire class is evident. These entities will never act in the interest of ordinary people. Instead, they will exploit crises to expand surveillance, control, and wealth extraction. The idea of a political “savior” is a dangerous illusion. True freedom comes from individuals taking responsibility for their own lives and working together to build decentralized, resilient systems.
---
## Conclusion: A Call to Action
The path to a genuinely free humanity begins with individual action. By adopting Bitcoin, securing digital privacy, increasing geographical flexibility, and building resilient local communities, ordinary people can protect themselves against authoritarianism. Governments will not save us—they are the problem. It is up to us to create a better future, free from the control of corrupt elites.
- The tools for liberation already exist.
- The question is: will we use them?
For those interested, I share ideas and solutions in my book « THE GATEWAY TO FREEDOM » https://blisshodlenglish.substack.com/p/the-gateway-to-freedom
⚡ **The time to act is now. Freedom is not given—it is taken.** ⚡
###### If you enjoyed this article, consider supporting it with a Zap!
---
My Substack ENGLISH = https://blisshodlenglish.substack.com/
My substack FRENCH = https://blisshodl.substack.com/
---
Get my Book « THE GATEWAY TO FREEDOM » here 🙏 => https://coinos.io/blisshodl
---
---
-

@ 57d1a264:69f1fee1
2025-03-23 12:24:46
https://www.youtube.com/watch?v=obXEnyQ_Veg



source: https://media.jaguar.com/news/2024/11/fearless-exuberant-compelling-jaguar-reimagined-0
originally posted at https://stacker.news/items/922356
-

@ c631e267:c2b78d3e
2025-03-21 19:41:50
*Wir werden nicht zulassen, dass technisch manches möglich ist,* *\
aber der Staat es nicht nutzt.* *\
Angela Merkel*  
**Die Modalverben zu erklären, ist im Deutschunterricht manchmal nicht ganz einfach.** Nicht alle Fremdsprachen unterscheiden zum Beispiel bei der Frage nach einer Möglichkeit gleichermaßen zwischen «können» im Sinne von «die Gelegenheit, Kenntnis oder Fähigkeit haben» und «dürfen» als «die Erlaubnis oder Berechtigung haben». Das spanische Wort «poder» etwa steht für beides.
**Ebenso ist vielen Schülern auf den ersten Blick nicht recht klar,** dass das logische Gegenteil von «müssen» nicht unbedingt «nicht müssen» ist, sondern vielmehr «nicht dürfen». An den Verkehrsschildern lässt sich so etwas meistens recht gut erklären: Manchmal muss man abbiegen, aber manchmal darf man eben nicht.

**Dieses Beispiel soll ein wenig die Verwirrungstaktik veranschaulichen,** die in der Politik gerne verwendet wird, um unpopuläre oder restriktive Maßnahmen Stück für Stück einzuführen. Zuerst ist etwas einfach innovativ und bringt viele Vorteile. Vor allem ist es freiwillig, jeder kann selber entscheiden, niemand muss mitmachen. Später kann man zunehmend weniger Alternativen wählen, weil sie verschwinden, und irgendwann verwandelt sich alles andere in «nicht dürfen» – die Maßnahme ist obligatorisch.
**Um die Durchsetzung derartiger Initiativen strategisch zu unterstützen** und nett zu verpacken, gibt es Lobbyisten, gerne auch NGOs genannt. Dass das «NG» am Anfang dieser Abkürzung übersetzt «Nicht-Regierungs-» bedeutet, ist ein Anachronismus. Das war [vielleicht früher](https://transition-news.org/der-sumpf-aus-ngos-parteien-und-steuergeld) einmal so, heute ist eher das Gegenteil gemeint.
**In unserer modernen Zeit wird enorm viel Lobbyarbeit für die Digitalisierung** praktisch sämtlicher Lebensbereiche aufgewendet. Was das auf dem Sektor der Mobilität bedeuten kann, haben wir diese Woche anhand aktueller Entwicklungen in Spanien [beleuchtet](https://transition-news.org/nur-abschied-vom-alleinfahren-monstrose-spanische-uberwachungsprojekte-gemass). Begründet teilweise mit Vorgaben der Europäischen Union arbeitet man dort fleißig an einer «neuen Mobilität», basierend auf «intelligenter» technologischer Infrastruktur. Derartige Anwandlungen wurden auch schon als [«Technofeudalismus»](https://transition-news.org/yanis-varoufakis-der-europaische-traum-ist-tot-es-lebe-der-neue-traum) angeprangert.
**Nationale** **[Zugangspunkte](https://transport.ec.europa.eu/transport-themes/smart-mobility/road/its-directive-and-action-plan/national-access-points_en)** **für Mobilitätsdaten im Sinne der EU** gibt es nicht nur in allen Mitgliedsländern, sondern auch in der [Schweiz](https://opentransportdata.swiss/de/) und in Großbritannien. Das Vereinigte Königreich beteiligt sich darüber hinaus an anderen EU-Projekten für digitale Überwachungs- und Kontrollmaßnahmen, wie dem biometrischen [Identifizierungssystem](https://transition-news.org/biometrische-gesichtserkennung-in-britischen-hafen) für «nachhaltigen Verkehr und Tourismus».
**Natürlich marschiert auch Deutschland stracks und euphorisch** in Richtung digitaler Zukunft. Ohne [vernetzte Mobilität](https://mobilithek.info/about) und einen «verlässlichen Zugang zu Daten, einschließlich Echtzeitdaten» komme man in der Verkehrsplanung und -steuerung nicht aus, erklärt die Regierung. Der Interessenverband der IT-Dienstleister Bitkom will «die digitale Transformation der deutschen Wirtschaft und Verwaltung vorantreiben». Dazu bewirbt er unter anderem die Konzepte Smart City, Smart Region und Smart Country und behauptet, deutsche Großstädte «setzen bei Mobilität [voll auf Digitalisierung](https://www.smartcountry.berlin/de/newsblog/smart-city-index-grossstaedte-setzen-bei-mobilitaet-voll-auf-digitalisierung.html)».
**Es steht zu befürchten, dass das umfassende Sammeln, Verarbeiten und Vernetzen von Daten,** das angeblich die Menschen unterstützen soll (und theoretisch ja auch könnte), eher dazu benutzt wird, sie zu kontrollieren und zu manipulieren. Je elektrischer und digitaler unsere Umgebung wird, desto größer sind diese Möglichkeiten. Im Ergebnis könnten solche Prozesse den Bürger nicht nur einschränken oder überflüssig machen, sondern in mancherlei Hinsicht regelrecht abschalten. Eine gesunde Skepsis ist also geboten.
*\[Titelbild:* *[Pixabay](https://pareto.space/readhttps://pixabay.com/de/illustrations/schaufensterpuppe-platine-gesicht-5254046/)]*
***
Dieser Beitrag wurde mit dem [Pareto-Client](https://pareto.space/read) geschrieben. Er ist zuerst auf ***[Transition News](https://transition-news.org/das-gegenteil-von-mussen-ist-nicht-durfen)*** erschienen.
-

@ 2fdeba99:fd961eff
2025-03-21 17:16:33
# == January 17 2025
Out From Underneath | Prism Shores
crazy arms | pigeon pit
Humanhood | The Weather Station
# == february 07 2025
Wish Defense | FACS
Sayan - Savoie | Maria Teriaeva
Nowhere Near Today | Midding
# == february 14 2025
Phonetics On and On | Horsegirl
# == february 21 2025
Finding Our Balance | Tsoh Tso
Machine Starts To Sing | Porridge Radio
Armageddon In A Summer Dress | Sunny Wa
# == february 28 2025
you, infinite | you, infinite
On Being | Max Cooper
Billboard Heart | Deep Sea Diver
# == March 21 2025
Watermelon/Peacock | Exploding Flowers
Warlord of the Weejuns | Goya Gumbani
-

@ 502ab02a:a2860397
2025-04-04 02:50:35
หลังจากที่เราเพิ่งเปิดเรื่องไฟโตสเตอรอลไปหมาด ๆ ถึงเวลาที่ต้องมาคุยกันเรื่อง oryzanol ซึ่งเป็นอีกหนึ่งสารที่ถูกอุตสาหกรรมผลักดันให้เรารู้สึกว่า “ต้องกิน” เหมือนเป็นไอเทมลับสำหรับสุขภาพหัวใจ แต่เดี๋ยวก่อนนะ ทำไมสิ่งที่มนุษย์ไม่เคยต้องการมาก่อนถึงกลายเป็นสิ่งจำเป็นไปได้ ?
Oryzanol หรือ gamma-oryzanol เป็นสารประกอบที่พบได้ในน้ำมันรำข้าว มีโครงสร้างเป็น sterol ester ของกรดเฟอรูลิก (Ferulic acid esters of sterols and triterpenes) ซึ่งหมายความว่ามันมีโครงสร้างคล้ายกับไฟโตสเตอรอล แต่มาพร้อมกับองค์ประกอบของสารต้านอนุมูลอิสระที่ได้จากกรดเฟอรูลิก นั่นทำให้มันถูกโฆษณาว่าเป็นสารที่ช่วยลดคอเลสเตอรอล มีฤทธิ์ต้านอนุมูลอิสระ และอาจช่วยลดความเสี่ยงโรคหัวใจ ฟังดูดีใช่ไหม ? แต่มันก็คล้ายกับไฟโตสเตอรอลเลย คือเป็นสารที่ แข่งขันกับคอเลสเตอรอลในการดูดซึม และแน่นอนว่าผลข้างเคียงก็ยังคงอยู่ นั่นคือ มันอาจลดการดูดซึมวิตามิน A, D, E, K ซึ่งเป็นวิตามินที่ละลายในไขมันและจำเป็นต่อร่างกาย นั่นหมายความว่า ในขณะที่มันช่วยลด LDL ในกระดาษ มันอาจทำให้ร่างกายขาดสารอาหารที่สำคัญไปด้วย
ปัญหาที่ใหญ่กว่าคือ oryzanol พบมากใน น้ำมันรำข้าว ซึ่งเป็นหนึ่งในน้ำมันพืชที่ผ่านการแปรรูปสูง และการบริโภคน้ำมันพืชมากเกินไปนั้นสัมพันธ์กับ ภาวะอักเสบเรื้อรัง (chronic inflammation), ภาวะต้านอินซูลิน (insulin resistance), และความเสี่ยงโรคหัวใจและหลอดเลือด การที่อุตสาหกรรมบอกให้เราเพิ่ม oryzanol ในอาหาร จึงเป็นเหมือนการผลักให้ผู้คนบริโภคน้ำมันพืชมากขึ้นโดยไม่รู้ตัว ทั้งที่น้ำมันพืชโดยเฉพาะที่ผ่านกรรมวิธีอย่างน้ำมันรำข้าวมีปริมาณโอเมก้า-6 สูง ซึ่งถ้ารับมากเกินไปจะไปกระตุ้นกระบวนการอักเสบในร่างกาย เคยสังเกตไหมครับว่า น้ำมันรำข้าวมักโชว์ตัวเลขเก๋ๆของ Oryzanol แต่กลับไม่โชว์สัดส่วน โอเมก้า 6 กับ โอเมก้า 3
เทียบง่ายๆครับ
น้ำมันคาโนลา มีโอเมก้า 6 ราวๆ 2200 - 2800 ต่อน้ำมัน 15 มล. (หน่วยบริโภค)
น้ำมันรำข้าว มีโอเมก้า 6 ราวๆ 4,140 - 5,520 มก. ต่อน้ำมัน 15 มล. (หน่วยบริโภค)
ในขณะที่โอเมก้า 3 ราวๆ 138 - 276 มก.ต่อน้ำมัน 15 มล. (หน่วยบริโภค)
นี่หมายถึงสัดส่วนสูงไปถึงได้ราวๆ 40:1 ทั้งๆที่เราเข้าใจแหละว่าโอเมก้า6 ร่างกายจำเป็น แต่แต่แต่ จำเป็นไม่ได้หมายความว่าจัดหนัก เพราะสิ่งที่เราต้องพึงสังวรคือ สัดส่วนที่สมดุลระหว่าง โอเมก้า3และโอเมก้า6 ดังนั้น 40:1 ไม่เรียกว่าสมดุล ซึ่งจะกระตุ้นการอักเสบเรื้อรัง ในร่างกาย และเกี่ยวข้องกับโรคหัวใจ เบาหวาน และปัญหาสุขภาพอื่นๆ พาเหรดกันมา
แต่คุณจะไม่เห็นตัวเลขนี้บนฉลากครับ
ผู้ผลิตผิดไหม?
จะไปผิดอะไรครับ หน่วยบริโภคแนะนำเขา 1 หน่วยบริโภคคือ 15 มิลลิลิตร หรือ 1 ช้อนโต๊ะ แค่นั้นเอง
คำถามคือ มีใครใช้ตามนั้นบ้าง คุณเจียวไข่เจียวใช้เท่าไร ผัดข้าวผัดใช้เท่าไหร่ อ่ะ ผัดผักรวมมิตรก็ได้ เอาแบบเต็มเปี่ยมเลย รู้ไหมว่ามีหลายคนเอาไปทำน้ำสลัด OMG
ผมถึงบอกอยู่ครับว่า คุณอย่าไปว่าผู้ผลิตเลย เขาปกป้องตัวเองไว้เรียบร้อยทุกมุมอยู่แล้วครับ ถ้าเรายังไม่อ่านฉลาก ซื้อเครื่องไฟฟ้าไม่เคยดูคู่มือ เซนต์สัญญาแบบไม่อ่านก่อน คุณจะว่าใครจริงไหมครับ
ที่น่าสนใจกว่านั้นคือเราเข้าใจกันแล้วใช่ไหมว่า oryzanol ไม่ได้มาจากการกินรำข้าวตรง ๆ แต่ต้องผ่านกระบวนการสกัดที่ซับซ้อนเพื่อได้น้ำมันมาใช้ และวิธีที่อุตสาหกรรมใช้มากที่สุดก็คือ การสกัดด้วยเฮกเซน (Hexane Extraction) ซึ่งเป็นตัวทำละลายเคมีที่อาจมีสารตกค้างในผลิตภัณฑ์สุดท้าย ถึงแม้จะมีวิธีอื่นที่ปลอดภัยกว่า เช่น การสกัดด้วยเอทานอล (Ethanol Extraction), การสกัดด้วยเอนไซม์ (Enzyme-Assisted Extraction), หรือการสกัดด้วยคาร์บอนไดออกไซด์เหนือวิกฤต (Supercritical CO₂ Extraction) แต่ทั้งหมดนี้มีต้นทุนสูงกว่า ทำให้ไม่เป็นที่นิยมในอุตสาหกรรม นั่นหมายความว่า ถ้าผลิตภัณฑ์ที่คุณซื้อไม่ได้ระบุว่าใช้วิธีอื่น ส่วนใหญ่ก็คือเฮกเซนแน่นอน
ข้อเสียของการบริโภค oryzanol มากเกินไปไม่ได้จบแค่การขัดขวางการดูดซึมวิตามิน เพราะการบริโภคในปริมาณสูงอาจส่งผลให้เกิด ความไม่สมดุลของฮอร์โมน เนื่องจาก oryzanol มีโครงสร้างคล้ายกับสเตอรอลในร่างกาย มันอาจไปรบกวนกระบวนการเผาผลาญของสเตอรอยด์ฮอร์โมน เช่น ฮอร์โมนเพศชาย (Testosterone) และฮอร์โมนความเครียด (Cortisol) ซึ่งในระยะยาวอาจส่งผลต่อระบบภูมิคุ้มกัน อารมณ์ และระดับพลังงานของร่างกาย
ประเด็นที่สำคัญคือ ในเมื่อเรามีอาหารจากธรรมชาติที่ช่วยบำรุงหัวใจได้โดยไม่ต้องมีผลข้างเคียง เช่น ไขมันสัตว์ดี ๆ ที่มีวิตามิน A, D, E, K ครบถ้วน ทำไมต้องพึ่งพาสารสกัดจากอุตสาหกรรม ? สิ่งที่ดูเหมือนดีจากงานวิจัยในแล็บ อาจไม่ได้ดีในระยะยาวเมื่ออยู่ในร่างกายมนุษย์จริง ๆ
ทีนี้เรามาดูจุดขายของ น้ำมันรำข้าวกัน
- oryzanol เป็นสารธรรมชาติ ทนความร้อนสูง เอาไปใช้ทอดจะไม่เกิดการสลายตัว
ทนความร้อนสูงนี่จริงเลยครับ โอริซานอลเป็นสารต้านอนุมูลอิสระในกลุ่ม Ferulic Acid Esters ซึ่งมีโครงสร้างเสถียรกว่าวิตามินอี (เทียบกับวิตามินอีเพราะ ต้านอนุมูลอิสระ และ การปกป้องไขมันจากการเกิดออกซิเดชัน ) มี จุดสลายตัวสูงกว่า 250°C ซึ่งทำให้ยังคงอยู่ได้ในอุณหภูมิที่ใช้ทอดอาหาร แล้วมันแปลว่าดีจริงไหม? ในขณะที่ น้ำมันรำข้าวมีโอเมก้า-6 สูงมาก (30-40%) ซึ่งไวต่อการเกิดออกซิเดชัน ถึงแม้โอริซานอลจะช่วยชะลอการเหม็นหืน แต่มันไม่ได้ช่วยลดการเกิด สารพิษจากไขมันไหม้ เช่น Aldehydes หรือ HNE (4-Hydroxy-2-nonenal) ที่มาจากโอเมก้า-6 หรือเปล่า???
มันคือการพูดให้เราไปโฟกัสจุดเดียวครับ "โอริซานอลทนร้อน ไม่ได้แปลว่า น้ำมันรำข้าวดีต่อสุขภาพ" เพราะโอเมก้า6 ที่ไวต่อการเกิดออกซิเดชัน รวมถึงวิตามินต่างๆ ก็ยังสูญสลายไปด้วยความร้อน นี่ยังไม่รวมถึงโทษของการกินโอริซานอลมากไปตามที่ให้ข้อมูลไว้ข้างบนด้วย
นอกจากนี้ยังมีคนตั้งคำถามไว้มากมายว่า หากโอริซานอลมีผลชัดเจนต่อสุขภาพเช่นเดียวกับที่โฆษณา ทำไมจึงไม่ได้รับการพัฒนาเป็นยาอย่างจริงจัง? หรือคำตอบคือ งานวิจัยที่สนับสนุนโอริซานอลยังไม่เพียงพอ และในหลายกรณี ผลของมันอาจเกิดจาก Placebo Effect (ผลจากความเชื่อว่ามันได้ผล มากกว่าผลจริงๆ ของสารนั้น) ซึ่งเป็นลักษณะเดียวกับ "ยาหลอก" ที่ไม่ได้มีฤทธิ์ทางชีวเคมีที่ส่งผลชัดเจน
- มีไลโนเลอิกสูง
ใช่ครับไม่ผิดเลยในจุดนี้ ไลโนเลอิก (Linoleic acid) เป็น กรดไขมันไม่อิ่มตัวชนิดหลายพันธะ (Polyunsaturated Fatty Acid, PUFA) ที่สำคัญและจำเป็นสำหรับร่างกาย โดยเฉพาะอย่างยิ่งในการช่วยบำรุงเซลล์และระบบต่างๆ ของร่างกาย ที่สำคัญคือ ไลโนเลอิกเป็นกรดไขมันในกลุ่ม โอเมก้า-6 เป็นสิ่งที่บอกกับเราชัดๆว่า โอเมก้า6 สูงนั่นเอง ถ้าจะดึงเฉพาะข้อดีมาคุยกันก็ไม่ผิดอะไรเลยครับ เพราะโอเมก้า6 สำคัญกับร่างกายจริงๆ แต่ แต่ แต่ การรับโอเมก้า-6 ในปริมาณสูงเกินไปอาจทำให้เกิดการอักเสบในร่างกาย ซึ่งเกี่ยวข้องกับโรคต่างๆ เช่น โรคหัวใจ โรคมะเร็ง และโรคเบาหวาน อย่างที่เรารู้กัน ดังนั้นที่บอกไว้ข้างบนครับ สัดส่วนโอเมก้า 6:3 คือ 40:1 หรือใน 1 ช้อนโต๊ะ มีโอเมก้า 6 สูงถึง ราวๆ 4,140 - 5,520 มก. เรียกว่าโฆษณาไม่ผิดเลยเรื่องปริมาณ แต่จริงๆแล้วเราควรรักษาสมดุล โอเมก้า 6:3 ให้ใกล้เคียง 1:1 มากที่สุดเท่าที่ทำได้ เราก็อาจต้องตั้งคำถามอีกทีว่า การมีไลโนเลอิกสูง มันดีจริงไหม
- โทโคฟีรอล (Tocopherols)
เป็นสารประกอบที่อยู่ในกลุ่ม วิตามินอี เป็นสารต้านอนุมูลอิสระในร่างกาย โดยช่วยปกป้องเซลล์จากความเสียหายจากอนุมูลอิสระและช่วยชะลอการเสื่อมของเซลล์ ถูกต้องตามโฆษณา จริงๆหน้าที่หลักคือปกป้องไขมันไม่ให้เกิดการออกซิเดชัน ซึ่งสามารถช่วยยืดอายุการใช้งานของน้ำมัน หรือไม่ให้เกิดการหืน นั่นเอง แต่การทอดหรือปรุงอาหารในอุณหภูมิสูงเกินไป ก็อาจทำให้น้ำมันเกิดการออกซิเดชันและเกิดสารพิษที่เป็นอันตรายต่อร่างกายได้ อย่าลืมนะครับว่าคำแนะนำในการใช้น้ำมันรำข้าว กลับชูการเหมาะกับอาหารทอดอุณหภูมิสูง
- โทโคไทรอีนอล (Tocotrienols)
เป็นส่วนหนึ่งของกลุ่ม วิตามินอี เช่นกัน การบริโภคมากเกินไป การรับประทาน โทโคไทรอีนอลในปริมาณมาก อาจมีผลข้างเคียงที่ไม่พึงประสงค์ เช่น ส่งผลกระทบต่อการดูดซึมวิตามินอื่นๆ ในร่างกายโดยเฉพาะวิตามิน K ซึ่งอาจทำให้เกิดปัญหาการแข็งตัวของเลือด, ทำให้ตับทำงานหนักขึ้นในการจัดการกับสารนี้ ซึ่งอาจส่งผลเสียต่อการทำงานของตับระยะยาว
สุดท้ายแล้ว เราต้องกลับมาตั้งคำถามว่า เราอยากให้สุขภาพของเราถูกกำหนดโดยการตลาดของอุตสาหกรรม หรือโดยสิ่งที่ธรรมชาติออกแบบมาให้เราตั้งแต่แรก ? ถ้าจะดูแลหัวใจจริง ๆ การกินอาหารที่มนุษย์วิวัฒนาการมากับมันมาตลอด เช่น เนื้อสัตว์ ไข่ ตับ และไขมันดี ๆ อาจเป็นคำตอบที่เรียบง่ายและมีเหตุผลมากกว่าการไล่ตามสารสกัดที่อุตสาหกรรมบอกว่าจำเป็น แต่ธรรมชาติอาจไม่เคยเห็นว่ามันสำคัญเลยก็ได้
#pirateketo #ฉลาก3รู้ #กูต้องรู้มั๊ย #ม้วนหางสิลูก
-

@ aa8de34f:a6ffe696
2025-03-21 12:08:31
19\. März 2025
### 🔐 1. SHA-256 is Quantum-Resistant
Bitcoin’s **proof-of-work** mechanism relies on SHA-256, a hashing algorithm. Even with a powerful quantum computer, **SHA-256 remains secure** because:
- Quantum computers excel at **factoring large numbers** (Shor’s Algorithm).
- However, **SHA-256 is a one-way function**, meaning there's no known quantum algorithm that can efficiently reverse it.
- **Grover’s Algorithm** (which theoretically speeds up brute force attacks) would still require **2¹²⁸ operations** to break SHA-256 – far beyond practical reach.
++++++++++++++++++++++++++++++++++++++++++++++++++
### 🔑 2. Public Key Vulnerability – But Only If You Reuse Addresses
Bitcoin uses **Elliptic Curve Digital Signature Algorithm (ECDSA)** to generate keys.
- A quantum computer could use **Shor’s Algorithm** to break **SECP256K1**, the curve Bitcoin uses.
- If you never reuse addresses, it is an additional security element
- 🔑 1. Bitcoin Addresses Are NOT Public Keys
Many people assume a **Bitcoin address** is the public key—**this is wrong**.
- When you **receive Bitcoin**, it is sent to a **hashed public key** (the Bitcoin address).
- The **actual public key is never exposed** because it is the Bitcoin Adress who addresses the Public Key which never reveals the creation of a public key by a spend
- Bitcoin uses **Pay-to-Public-Key-Hash (P2PKH)** or newer methods like **Pay-to-Witness-Public-Key-Hash (P2WPKH)**, which add extra layers of security.
### 🕵️♂️ 2.1 The Public Key Never Appears
- When you **send Bitcoin**, your wallet creates a **digital signature**.
- This signature uses the **private key** to **prove** ownership.
- The **Bitcoin address is revealed and creates the Public Key**
- The public key **remains hidden inside the Bitcoin script and Merkle tree**.
This means: ✔ **The public key is never exposed.** ✔ **Quantum attackers have nothing to target, attacking a Bitcoin Address is a zero value game.**
+++++++++++++++++++++++++++++++++++++++++++++++++
### 🔄 3. Bitcoin Can Upgrade
Even if quantum computers **eventually** become a real threat:
- Bitcoin developers can **upgrade to quantum-safe cryptography** (e.g., lattice-based cryptography or post-quantum signatures like Dilithium).
- Bitcoin’s decentralized nature ensures a network-wide **soft fork or hard fork** could transition to quantum-resistant keys.
++++++++++++++++++++++++++++++++++++++++++++++++++
### ⏳ 4. The 10-Minute Block Rule as a Security Feature
- Bitcoin’s network operates on a **10-minute block interval**, meaning:Even if an attacker had immense computational power (like a quantum computer), they could only attempt an attack **every 10 minutes**.Unlike traditional encryption, where a hacker could continuously brute-force keys, Bitcoin’s system **resets the challenge with every new block**.This **limits the window of opportunity** for quantum attacks.
---
### 🎯 5. Quantum Attack Needs to Solve a Block in Real-Time
- A quantum attacker **must solve the cryptographic puzzle (Proof of Work) in under 10 minutes**.
- The problem? **Any slight error changes the hash completely**, meaning:**If the quantum computer makes a mistake (even 0.0001% probability), the entire attack fails**.**Quantum decoherence** (loss of qubit stability) makes error correction a massive challenge.The computational cost of **recovering from an incorrect hash** is still incredibly high.
---
### ⚡ 6. Network Resilience – Even if a Block Is Hacked
- Even if a quantum computer **somehow** solved a block instantly:The network would **quickly recognize and reject invalid transactions**.Other miners would **continue mining** under normal cryptographic rules.**51% Attack?** The attacker would need to consistently beat the **entire Bitcoin network**, which is **not sustainable**.
---
### 🔄 7. The Logarithmic Difficulty Adjustment Neutralizes Threats
- Bitcoin adjusts mining difficulty every **2016 blocks (\~2 weeks)**.
- If quantum miners appeared and suddenly started solving blocks too quickly, **the difficulty would adjust upward**, making attacks significantly harder.
- This **self-correcting mechanism** ensures that even quantum computers wouldn't easily overpower the network.
---
### 🔥 Final Verdict: Quantum Computers Are Too Slow for Bitcoin
✔ **The 10-minute rule limits attack frequency** – quantum computers can’t keep up.
✔ **Any slight miscalculation ruins the attack**, resetting all progress.
✔ **Bitcoin’s difficulty adjustment would react, neutralizing quantum advantages**.
**Even if quantum computers reach their theoretical potential, Bitcoin’s game theory and design make it incredibly resistant.** 🚀
-

@ 6389be64:ef439d32
2025-04-03 21:32:58
Brewing Biology
Episode 1068 of Bitcoin And . . . is LIVE!
This episode of Bitcoin And dives into Brewing Biology—a regenerative system combining compost tea, biochar, Bitcoin mining, and carbon credits—developed through a deep, idea-driven conversation with ChatGPT.
LISTEN HERE --> https://fountain.fm/episode/p0DmvPzxirDHh2l68zOX <-- LISTEN HERE
The future of Bitcoin isn’t just about code or money—it’s about soil. A groundbreaking fusion of biology, technology, and financial innovation might change the rules of agriculture, offering landowners a path to profitability while Healing our soils. At the heart of this revolution is biochar, a form of charcoal that supercharges soil health. When mixed with compost tea and microbial inoculants, this carbon-rich material becomes a game-changer.
Biochar’s porous structure acts as a microbial hotel, hosting fungi like arbuscular mycorrhizal fungi (AMF) and bacteria such as Bacillus subtilis. These organisms form symbiotic networks that boost nutrient absorption and secrete glomalin—a natural “glue” that binds soil, preventing erosion. But here’s the twist: this system doesn’t just heal the earth; it also generates revenue.
Biochar’s Hidden Superpower: Adsorption & Buffering
Biochar’s porous structure acts as a molecular storage hub. Unlike absorption (soaking up water like a sponge), adsorption is a chemical process where water and nutrients cling to biochar’s surfaces. A single gram of biochar has the surface area of a basketball court, creating a lattice of microscopic nooks and crannies. This allows it to:
Lock in moisture: Biochar retains up to 10x its weight in water, acting like a “soil battery” that releases hydration slowly during droughts.
Hoard nutrients: It buffers nitrogen, phosphorus, potassium, and micronutrients in its pores, preventing leaching. Plants access these nutrients gradually, reducing fertilizer needs.
Stabilize pH: Biochar’s alkaline nature buffers acidic soils, creating a neutral environment where microbes and roots thrive.
This buffering effect means plants face fewer nutrient and water spikes or shortages, ensuring steady growth even in erratic climates.
The Carbon Math
Every ton of biochar (which is ~85% carbon by weight) sequesters 3.12 tons of CO₂ (using the 1:3.67 carbon-to-CO₂ ratio). With carbon credits trading at $42–$60/ton, a 1,000-acre project applying 1 pound of biochar per linear foot (via a three-shank plow at 2-foot spacing) could sequester ~12,000 tons of CO₂ annually—generating $504,000–$720,000 in carbon credit revenue.
Tools for the Revolution
The Keyline Plow fractures subsoil to inject biochar slurry 30–45cm deep, revitalizing compacted land. For smaller plots, the VOGT Geo Injector delivers pinpoint inoculations—think of it as a soil “injection gun” for lawns, golf courses, or urban gardens. These methods ensure biochar stays where it’s needed, turning even parched landscapes into carbon sinks.
Bitcoin’s Role in the Loop
Biochar production generates syngas—a byproduct that fuels electric generators for Bitcoin mining. This closed-loop system turns agricultural waste into energy, creating dual revenue streams: carbon credits and mining income.
The Market Potential
Farmers, ranchers, and eco-conscious landowners aren’t the only beneficiaries. Golf courses can slash water use and homeowners can boost lawn resilience.
Why This Matters
This isn’t just farming—it’s a movement. By marrying soil science with economics, we can prove that healing the planet and profiting go hand in hand. Whether you’re a Bitcoin miner, a farmer, or an eco-entrepreneur, this system offers a blueprint for a future where every acre works for you—and the planet.
The takeaway? Regenerative agriculture isn’t a trend. It’s the next gold rush—except this time, the gold is carbon, soil, and sats.---
P.S. – If you’re ready to turn your land into a carbon credit powerhouse (and maybe mine some Bitcoin along the way), the soil is waiting.
You can read the full article, Brewing Biology HERE -> https://the-bitcoin-and-Podcast.ghost.io/ghost/#/editor/post/67e5922fa289aa00088da3c6
originally posted at https://stacker.news/items/933800
-

@ a95c6243:d345522c
2025-03-20 09:59:20
**Bald werde es verboten, alleine im Auto zu fahren,** konnte man dieser Tage in verschiedenen spanischen Medien lesen. Die nationale Verkehrsbehörde (Dirección General de Tráfico, kurz DGT) werde Alleinfahrern das Leben schwer machen, wurde gemeldet. Konkret erörtere die Generaldirektion geeignete Sanktionen für Personen, die ohne Beifahrer im Privatauto unterwegs seien.
**Das Alleinfahren sei zunehmend verpönt und ein Mentalitätswandel notwendig,** hieß es. Dieser «Luxus» stehe im Widerspruch zu den Maßnahmen gegen Umweltverschmutzung, die in allen europäischen Ländern gefördert würden. In Frankreich sei es «bereits verboten, in der Hauptstadt allein zu fahren», [behauptete](https://noticiastrabajo.huffingtonpost.es/sociedad/adios-a-conducir-solo-la-dgt-se-lo-pone-crudo-a-los-conductores-que-viajen-sin-acompanante-en-el-coche/) *Noticiastrabajo Huffpost* in einer Zwischenüberschrift. Nur um dann im Text zu konkretisieren, dass die sogenannte «Umweltspur» auf der Pariser Ringautobahn gemeint war, die für Busse, Taxis und Fahrgemeinschaften reserviert ist. [Ab Mai](https://www.lefigaro.fr/conso/peripherique-parisien-entree-en-vigueur-de-la-voie-reservee-au-covoiturage-ce-lundi-20250303) werden Verstöße dagegen mit einem Bußgeld geahndet.
**Die DGT jedenfalls wolle bei der Umsetzung derartiger Maßnahmen** nicht hinterherhinken. Diese Medienberichte, inklusive des angeblich bevorstehenden Verbots, beriefen sich auf Aussagen des Generaldirektors der Behörde, Pere Navarro, beim Mobilitätskongress Global Mobility Call im November letzten Jahres, wo es um «nachhaltige Mobilität» ging. Aus diesem Kontext stammt auch Navarros Warnung: «Die Zukunft des Verkehrs ist geteilt oder es gibt keine».
**Die «Faktenchecker» kamen der Generaldirektion prompt zu Hilfe.** Die DGT habe derlei Behauptungen [zurückgewiesen](https://www.newtral.es/dgt-una-persona-coche/20250312/) und klargestellt, dass es keine Pläne gebe, Fahrten mit nur einer Person im Auto zu verbieten oder zu bestrafen. Bei solchen Meldungen handele es sich um Fake News. Teilweise wurde der Vorsitzende der spanischen «Rechtsaußen»-Partei Vox, Santiago Abascal, der Urheberschaft bezichtigt, weil er einen entsprechenden [Artikel](https://gaceta.es/espana/la-dgt-estudia-formas-de-sancionar-a-quien-circule-solo-en-su-vehiculo-el-futuro-sera-compartido-o-no-sera-20250311-1612/) von *La Gaceta* kommentiert hatte.
**Der Beschwichtigungsversuch der Art «niemand hat die Absicht»** ist dabei erfahrungsgemäß eher ein Alarmzeichen als eine Beruhigung. Walter Ulbrichts Leugnung einer geplanten Berliner [Mauer](https://www.berlin-mauer.de/videos/walter-ulbricht-zum-mauerbau-530/) vom Juni 1961 ist vielen genauso in Erinnerung wie die Fake News-Warnungen des deutschen Bundesgesundheitsministeriums bezüglich [Lockdowns](https://x.com/BMG_Bund/status/1238780849652465664) im März 2020 oder diverse Äußerungen zu einer [Impfpflicht](https://www.achgut.com/artikel/die_schoensten_politiker_zitate_zur_impfpflicht) ab 2020.
**Aber Aufregung hin, Dementis her:** Die [Pressemitteilung](https://archive.is/xXQWD) der DGT zu dem Mobilitätskongress enthält in Wahrheit viel interessantere Informationen als «nur» einen Appell an den «guten» Bürger wegen der Bemühungen um die Lebensqualität in Großstädten oder einen möglichen obligatorischen Abschied vom Alleinfahren. Allerdings werden diese Details von Medien und sogenannten Faktencheckern geflissentlich übersehen, obwohl sie keineswegs versteckt sind. Die Auskünfte sind sehr aufschlussreich, wenn man genauer hinschaut.
### Digitalisierung ist der Schlüssel für Kontrolle
**Auf dem Kongress stellte die Verkehrsbehörde ihre Initiativen zur Förderung der «neuen Mobilität» vor,** deren Priorität Sicherheit und Effizienz sei. Die vier konkreten Ansätze haben alle mit Digitalisierung, Daten, Überwachung und Kontrolle im großen Stil zu tun und werden unter dem Euphemismus der «öffentlich-privaten Partnerschaft» angepriesen. Auch lassen sie die transhumanistische Idee vom unzulänglichen Menschen erkennen, dessen Fehler durch «intelligente» technologische Infrastruktur kompensiert werden müssten.
**Die Chefin des Bereichs «Verkehrsüberwachung» erklärte die Funktion** des spanischen National Access Point ([NAP](https://nap.dgt.es/)), wobei sie betonte, wie wichtig Verkehrs- und Infrastrukturinformationen in Echtzeit seien. Der NAP ist «eine essenzielle Web-Applikation, die unter EU-Mandat erstellt wurde», kann man auf der Website der DGT nachlesen.
**Das Mandat meint Regelungen zu einem einheitlichen europäischen Verkehrsraum,** mit denen die Union mindestens seit 2010 den Aufbau einer digitalen Architektur mit offenen Schnittstellen betreibt. Damit begründet man auch «umfassende Datenbereitstellungspflichten im Bereich multimodaler Reiseinformationen». Jeder Mitgliedstaat musste einen NAP, also einen nationalen [Zugangspunkt](https://transport.ec.europa.eu/transport-themes/smart-mobility/road/its-directive-and-action-plan/national-access-points_en) einrichten, der Zugang zu statischen und dynamischen Reise- und Verkehrsdaten verschiedener Verkehrsträger ermöglicht.
**Diese Entwicklung ist heute schon weit fortgeschritten,** auch und besonders in Spanien. Auf besagtem Kongress erläuterte die Leiterin des Bereichs «Telematik» die Plattform [«DGT 3.0»](https://www.dgt.es/muevete-con-seguridad/tecnologia-e-innovacion-en-carretera/dgt-3.0/). Diese werde als Integrator aller Informationen genutzt, die von den verschiedenen öffentlichen und privaten Systemen, die Teil der Mobilität sind, bereitgestellt werden.
**Es handele sich um eine Vermittlungsplattform zwischen Akteuren wie Fahrzeugherstellern,** Anbietern von Navigationsdiensten oder Kommunen und dem Endnutzer, der die Verkehrswege benutzt. Alle seien auf Basis des Internets der Dinge (IOT) anonym verbunden, «um der vernetzten Gemeinschaft wertvolle Informationen zu liefern oder diese zu nutzen».
**So sei DGT 3.0 «ein Zugangspunkt für einzigartige, kostenlose und genaue Echtzeitinformationen** über das Geschehen auf den Straßen und in den Städten». Damit lasse sich der Verkehr nachhaltiger und vernetzter gestalten. Beispielsweise würden die Karten des Produktpartners Google dank der DGT-Daten 50 Millionen Mal pro Tag aktualisiert.
**Des Weiteren informiert die Verkehrsbehörde über ihr SCADA-Projekt.** Die Abkürzung steht für Supervisory Control and Data Acquisition, zu deutsch etwa: Kontrollierte Steuerung und Datenerfassung. Mit SCADA kombiniert man Software und Hardware, um automatisierte Systeme zur Überwachung und Steuerung technischer Prozesse zu schaffen. Das SCADA-Projekt der DGT wird von Indra entwickelt, einem spanischen Beratungskonzern aus den Bereichen Sicherheit & Militär, Energie, Transport, Telekommunikation und Gesundheitsinformation.
**Das SCADA-System der Behörde umfasse auch eine Videostreaming- und Videoaufzeichnungsplattform,** die das Hochladen in die Cloud in Echtzeit ermöglicht, wie Indra [erklärt](https://www.indracompany.com/es/noticia/indra-presenta-global-mobility-call-pionera-plataforma-nube-desplegada-centros-gestion). Dabei gehe es um Bilder, die von Überwachungskameras an Straßen aufgenommen wurden, sowie um Videos aus DGT-Hubschraubern und Drohnen. Ziel sei es, «die sichere Weitergabe von Videos an Dritte sowie die kontinuierliche Aufzeichnung und Speicherung von Bildern zur möglichen Analyse und späteren Nutzung zu ermöglichen».
**Letzteres klingt sehr nach biometrischer Erkennung** und Auswertung durch künstliche Intelligenz. Für eine bessere Datenübertragung wird derzeit die [Glasfaserverkabelung](https://www.moncloa.com/2025/03/18/linea-azul-conduccion-dgt-3191554/) entlang der Landstraßen und Autobahnen ausgebaut. Mit der Cloud sind die Amazon Web Services (AWS) gemeint, die spanischen [Daten gehen](https://norberthaering.de/news/digitalgipfel-wehnes-interview/) somit direkt zu einem US-amerikanischen «Big Data»-Unternehmen.
**Das Thema «autonomes Fahren», also Fahren ohne Zutun des Menschen,** bildet den Abschluss der Betrachtungen der DGT. Zusammen mit dem Interessenverband der Automobilindustrie ANFAC (Asociación Española de Fabricantes de Automóviles y Camiones) sprach man auf dem Kongress über Strategien und Perspektiven in diesem Bereich. Die Lobbyisten hoffen noch in diesem Jahr 2025 auf einen [normativen Rahmen](https://www.coches.net/noticias/informe-coche-autonomo-conectado-espana-2024) zur erweiterten Unterstützung autonomer Technologien.
**Wenn man derartige Informationen im Zusammenhang betrachtet,** bekommt man eine Idee davon, warum zunehmend alles elektrisch und digital werden soll. Umwelt- und Mobilitätsprobleme in Städten, wie Luftverschmutzung, Lärmbelästigung, Platzmangel oder Staus, sind eine Sache. Mit dem Argument «emissionslos» wird jedoch eine Referenz zum CO2 und dem «menschengemachten Klimawandel» hergestellt, die Emotionen triggert. Und damit wird so ziemlich alles verkauft.
**Letztlich aber gilt: Je elektrischer und digitaler unsere Umgebung wird** und je freigiebiger wir mit unseren Daten jeder Art sind, desto besser werden wir kontrollier-, steuer- und sogar abschaltbar. Irgendwann entscheiden KI-basierte Algorithmen, ob, wann, wie, wohin und mit wem wir uns bewegen dürfen. Über einen 15-Minuten-Radius geht dann möglicherweise nichts hinaus. Die Projekte auf diesem Weg sind ernst zu nehmen, real und schon weit fortgeschritten.
*\[Titelbild:* *[Pixabay](https://pixabay.com/de/photos/reisen-wagen-ferien-fahrzeug-1426822/)]*
***
Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/nur-abschied-vom-alleinfahren-monstrose-spanische-uberwachungsprojekte-gemass)*** erschienen.
-

@ 07f367da:0e76880d
2025-04-03 17:59:21
윤석열 탄핵 선고를 앞둔 4월 3일. 우리 노동조합은 서울 마포구 소재의 한 활동지원기관 앞에서 선전전을 진행했다. 노동조합은 한 활동지원사의 민원을 통해 해당 활동지원기관이 일요일에 일해도 평일 임금을 지급한다는 사실을 파악했다. 활동지원사의 민원에 관심을 가진 한 언론사의 기자는 활동지원기관과 구청, 서울시, 노조에 문의하며 팩트체크를 진행하고 있는데, 이 과정에서 노조는 해당 기관이 일요일에 일을 해도 평일 임금을 지급하고 있다는 사실을 명확히 확인했다.
자신이 받는 임금에 대한 사실관계를 노동자들은 잘 알지 못한다. 활동지원사는 기관에 자신의 임금에 대해 문의해도 속 시원한 답을 듣지 못한다. 활동지원사들이 하나같이 하는 이야기가 기관에 물어봐도 제대로 설명을 해주지 않는다는 하소연이다.
당사자 활동지원사는 노조에 민원을 제기하고, 또 기자가 취재한 내용들을 통해서야 자신의 임금이 자신도 모르게 어떻게 변화했는지를 알아가고 있다. 사업장의 임급지급 행위에 대한 가치판단이나 평가 이전에 노동자들은 그 사실 자체를 모를 가능성이 높다. 노조는 이 사실을 활동지원사들에게 알리려 선전전을 진행하기로 했다.
선전전 진행 중 정말 충격적인 경험을 했다. 노동조합의 선전활동은 정당한 노조활동이고 일상적인 활동이다. 여태 여러 사업장에서 선전활동을 했지만, 이런 경우는 정말 처음이었다. 사업장들은 신경 거슬러 하고 적대적인 대우를 하곤 했지만, 가장 강한 대처가 경찰에 신고하여 공권력의 개입을 요청하고, 경찰은 충돌을 방지하는 선에서 대처한다. 그런데 오늘은 장애인 기관장이 선전활동을 하지 말라고 계속 항의하며 방해하더니 소속 활동지원팀 인력은 노동조합이 활동지원사에게 선전물을 전달하려 하니 몸으로 막기까지 한다.
무엇을 그렇게 숨기고 싶을까? 노동조합의 활동을 몸으로 막으면서까지 싫어할 이유가 무엇일까? 노동조합의 활동이 그들에게 무엇으로 다가갔을까? 여러 질문이 든다.
충격적인 것은 이 기관의 대표가 우리노조가 예전에 청와대 앞에서 기자회견 할 때 연대 발언을 하러 왔던 활동가라는 점이다. 장애인 당사자이자 인권운동 활동가가 사용자로, 그리고 사회복지사 노동자들이 전담인력으로 고용되어 사측을 대신해 활동지원사 노동자들이 응당 자신에 대해 알아야 할 사항을 은폐한다.
사장이 되어 권력을 행사하면서도 장애인이라는 정체성으로 자신의 지위를 지우려 하고, 전담인력이라는 지위로 노동자들을 지휘하면서도 같은 노동자라며 위계를 삭제한다. 그리고 정작 현장에서 장애인에게 활동지원을 제공하는 활동지원사들은 대부분 고령의 여성들로 정보약자에 해당한다. 우리에게도 민주주의가 올까. 나는 저들이 활동으로 세상을 좋게 만드는 것을 상쇄할 정도로 더 세상을 나쁘게 만들고 있다고 생각한다.
타인에 의해 돈벌이 수단으로 이용당하는 사람은 자신 또한 타인을 돈벌이 수단으로 활용할 가능성이 높다. 그 타인에는 장애인도 포함된다. 나는 시설사회가 끝나도 장애인학대가 끝나리라는 믿음이 없다. 우리는 어차피 서로를 돈벌이 수단으로만 삼는 사회에서 살고 있기 때문이다.
-

@ e4950c93:1b99eccd
2025-04-03 14:53:56
**Heureu-x-se d’avoir trouvé une information utile sur ce site ?**
Soutenez le projet en faisant un don pour le faire vivre et remercier les contribut-eur-rice-s.
---
**En bitcoin**
<img src="https://coinos.io/qr/bc1q79er6c5mvvktvmvcstsnelv4j6tv3wdhw2k7ej/raw" width="200" height="200">
bc1qkm8me8l9563wvsl9sklzt4hdcuny3tlejznj7d
⚡️`
origin-nature@coinos.io`
---
**En euros, dollars, ou toute autre monnaie prise en charge**
*Promesses uniquement pour le moment :*
<a href="https://liberapay.com/origin-nature/">
<img src="!(image)[https://liberapay.com/assets/liberapay/icon-v2_black-on-yellow.svg]?etag=._QLQJKsW7OwBQqn7ASPxRA~~" width="200" height="200">
</a>
---
Contactez-nous si vous souhaitez faire un don avec toute autre
cryptomonnaie.
---
### 💡 Un modèle de partage de la valeur
La moitié des dons est redistribuée aux contribut-eur-rice-s qui créent la valeur du site, pour expérimenter un modèle de partage de revenus sur Internet — un modèle qui respecte vos données et ne cherche pas à capter votre attention.
L’autre moitié permet de couvrir les frais de fonctionnement du site.
-

@ 266815e0:6cd408a5
2025-03-19 11:10:21
How to create a nostr app quickly using [applesauce](https://hzrd149.github.io/applesauce/)
In this guide we are going to build a nostr app that lets users follow and unfollow [fiatjaf](nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6)
## 1. Setup new project
Start by setting up a new vite app using `pnpm create vite`, then set the name and select `Solid` and `Typescript`
```sh
➜ pnpm create vite
│
◇ Project name:
│ followjaf
│
◇ Select a framework:
│ Solid
│
◇ Select a variant:
│ TypeScript
│
◇ Scaffolding project in ./followjaf...
│
└ Done. Now run:
cd followjaf
pnpm install
pnpm run dev
```
## 2. Adding nostr dependencies
There are a few useful nostr dependencies we are going to need. `nostr-tools` for the types and small methods, and [`rx-nostr`](https://penpenpng.github.io/rx-nostr/) for making relay connections
```sh
pnpm install nostr-tools rx-nostr
```
## 3. Setup rx-nostr
Next we need to setup rxNostr so we can make connections to relays. create a new `src/nostr.ts` file with
```ts
import { createRxNostr, noopVerifier } from "rx-nostr";
export const rxNostr = createRxNostr({
// skip verification here because we are going to verify events at the event store
skipVerify: true,
verifier: noopVerifier,
});
```
## 4. Setup the event store
Now that we have a way to connect to relays, we need a place to store events. We will use the [`EventStore`](https://hzrd149.github.io/applesauce/typedoc/classes/applesauce_core.EventStore.html) class from `applesauce-core` for this. create a new `src/stores.ts` file with
> The event store does not store any events in the browsers local storage or anywhere else. It's in-memory only and provides a model for the UI
```ts
import { EventStore } from "applesauce-core";
import { verifyEvent } from "nostr-tools";
export const eventStore = new EventStore();
// verify the events when they are added to the store
eventStore.verifyEvent = verifyEvent;
```
## 5. Create the query store
The event store is where we store all the events, but we need a way for the UI to query them. We can use the [`QueryStore`](https://hzrd149.github.io/applesauce/typedoc/classes/applesauce_core.QueryStore.html) class from `applesauce-core` for this.
Create a query store in `src/stores.ts`
```ts
import { QueryStore } from "applesauce-core";
// ...
// the query store needs the event store to subscribe to it
export const queryStore = new QueryStore(eventStore);
```
## 6. Setup the profile loader
Next we need a way to fetch user profiles. We are going to use the [`ReplaceableLoader`](https://hzrd149.github.io/applesauce/overview/loaders.html#replaceable-loader) class from [`applesauce-loaders`](https://www.npmjs.com/package/applesauce-loaders) for this.
> `applesauce-loaders` is a package that contains a few loader classes that can be used to fetch different types of data from relays.
First install the package
```sh
pnpm install applesauce-loaders
```
Then create a `src/loaders.ts` file with
```ts
import { ReplaceableLoader } from "applesauce-loaders";
import { rxNostr } from "./nostr";
import { eventStore } from "./stores";
export const replaceableLoader = new ReplaceableLoader(rxNostr);
// Start the loader and send any events to the event store
replaceableLoader.subscribe((packet) => {
eventStore.add(packet.event, packet.from);
});
```
## 7. Fetch fiatjaf's profile
Now that we have a way to store events, and a loader to help with fetching them, we should update the `src/App.tsx` component to fetch the profile.
We can do this by calling the `next` method on the loader and passing a `pubkey`, `kind` and `relays` to it
```tsx
function App() {
// ...
onMount(() => {
// fetch fiatjaf's profile on load
replaceableLoader.next({
pubkey: "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d",
kind: 0,
relays: ["wss://pyramid.fiatjaf.com/"],
});
});
// ...
}
```
## 8. Display the profile
Now that we have a way to fetch the profile, we need to display it in the UI.
We can do this by using the [`ProfileQuery`](https://hzrd149.github.io/applesauce/typedoc/functions/applesauce_core.Queries.ProfileQuery.html) which gives us a stream of updates to a pubkey's profile.
Create the profile using `queryStore.createQuery` and pass in the `ProfileQuery` and the pubkey.
```tsx
const fiatjaf = queryStore.createQuery(
ProfileQuery,
"3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d"
);
```
But this just gives us an [observable](https://rxjs.dev/guide/observable), we need to subscribe to it to get the profile.
Luckily SolidJS profiles a simple [`from`](https://docs.solidjs.com/reference/reactive-utilities/from) method to subscribe to any observable.
> To make things reactive SolidJS uses accessors, so to get the profile we need to call `fiatjaf()`
```tsx
function App() {
// ...
// Subscribe to fiatjaf's profile from the query store
const fiatjaf = from(
queryStore.createQuery(ProfileQuery, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d")
);
return (
<>
{/* replace the vite and solid logos with the profile picture */}
<div>
<img src={fiatjaf()?.picture} class="logo" />
</div>
<h1>{fiatjaf()?.name}</h1>
{/* ... */}
</>
);
}
```
## 9. Letting the user signin
Now we should let the user signin to the app. We can do this by creating a [`AccountManager`](https://hzrd149.github.io/applesauce/accounts/manager.html) class from `applesauce-accounts`
First we need to install the packages
```sh
pnpm install applesauce-accounts applesauce-signers
```
Then create a new `src/accounts.ts` file with
```ts
import { AccountManager } from "applesauce-accounts";
import { registerCommonAccountTypes } from "applesauce-accounts/accounts";
// create an account manager instance
export const accounts = new AccountManager();
// Adds the common account types to the manager
registerCommonAccountTypes(accounts);
```
Next lets presume the user has a NIP-07 browser extension installed and add a signin button.
```tsx
function App() {
const signin = async () => {
// do nothing if the user is already signed in
if (accounts.active) return;
// create a new nip-07 signer and try to get the pubkey
const signer = new ExtensionSigner();
const pubkey = await signer.getPublicKey();
// create a new extension account, add it, and make it the active account
const account = new ExtensionAccount(pubkey, signer);
accounts.addAccount(account);
accounts.setActive(account);
};
return (
<>
{/* ... */}
<div class="card">
<p>Are you following the fiatjaf? the creator of "The nostr"</p>
<button onClick={signin}>Check</button>
</div>
</>
);
}
```
Now when the user clicks the button the app will ask for the users pubkey, then do nothing... but it's a start.
> We are not persisting the accounts, so when the page reloads the user will NOT be signed in. you can learn about persisting the accounts in the [docs](https://hzrd149.github.io/applesauce/accounts/manager.html#persisting-accounts)
## 10. Showing the signed-in state
We should show some indication to the user that they are signed in. We can do this by modifying the signin button if the user is signed in and giving them a way to sign-out
```tsx
function App() {
// subscribe to the currently active account (make sure to use the account$ observable)
const account = from(accounts.active$);
// ...
const signout = () => {
// do nothing if the user is not signed in
if (!accounts.active) return;
// signout the user
const account = accounts.active;
accounts.removeAccount(account);
accounts.clearActive();
};
return (
<>
{/* ... */}
<div class="card">
<p>Are you following the fiatjaf? ( creator of "The nostr" )</p>
{account() === undefined ? <button onClick={signin}>Check</button> : <button onClick={signout}>Signout</button>}
</div>
</>
);
}
```
## 11. Fetching the user's profile
Now that we have a way to sign in and out of the app, we should fetch the user's profile when they sign in.
```tsx
function App() {
// ...
// fetch the user's profile when they sign in
createEffect(async () => {
const active = account();
if (active) {
// get the user's relays or fallback to some default relays
const usersRelays = await active.getRelays?.();
const relays = usersRelays ? Object.keys(usersRelays) : ["wss://relay.damus.io", "wss://nos.lol"];
// tell the loader to fetch the users profile event
replaceableLoader.next({
pubkey: active.pubkey,
kind: 0,
relays,
});
// tell the loader to fetch the users contacts
replaceableLoader.next({
pubkey: active.pubkey,
kind: 3,
relays,
});
// tell the loader to fetch the users mailboxes
replaceableLoader.next({
pubkey: active.pubkey,
kind: 10002,
relays,
});
}
});
// ...
}
```
Next we need to subscribe to the users profile, to do this we can use some rxjs operators to chain the observables together.
```tsx
import { Match, Switch } from "solid-js";
import { of, switchMap } from "rxjs";
function App() {
// ...
// subscribe to the active account, then subscribe to the users profile or undefined
const profile = from(
accounts.active$.pipe(
switchMap((account) => (account ? queryStore.createQuery(ProfileQuery, account!.pubkey) : of(undefined)))
)
);
// ...
return (
<>
{/* ... */}
<div class="card">
<Switch>
<Match when={account() && !profile()}>
<p>Loading profile...</p>
</Match>
<Match when={profile()}>
<p style="font-size: 1.2rem; font-weight: bold;">Welcome {profile()?.name}</p>
</Match>
</Switch>
{/* ... */}
</div>
</>
);
}
```
## 12. Showing if the user is following fiatjaf
Now that the app is fetching the users profile and contacts we should show if the user is following fiatjaf.
```tsx
function App() {
// ...
// subscribe to the active account, then subscribe to the users contacts or undefined
const contacts = from(
accounts.active$.pipe(
switchMap((account) => (account ? queryStore.createQuery(UserContactsQuery, account!.pubkey) : of(undefined)))
)
);
const isFollowing = createMemo(() => {
return contacts()?.some((c) => c.pubkey === "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d");
});
// ...
return (
<>
{/* ... */}
<div class="card">
{/* ... */}
<Switch
fallback={
<p style="font-size: 1.2rem;">
Sign in to check if you are a follower of the fiatjaf ( creator of "The nostr" )
</p>
}
>
<Match when={contacts() && isFollowing() === undefined}>
<p>checking...</p>
</Match>
<Match when={contacts() && isFollowing() === true}>
<p style="color: green; font-weight: bold; font-size: 2rem;">
Congratulations! You are a follower of the fiatjaf
</p>
</Match>
<Match when={contacts() && isFollowing() === false}>
<p style="color: red; font-weight: bold; font-size: 2rem;">
Why don't you follow the fiatjaf? do you even like nostr?
</p>
</Match>
</Switch>
{/* ... */}
</div>
</>
);
}
```
## 13. Adding the follow button
Now that we have a way to check if the user is following fiatjaf, we should add a button to follow him. We can do this with [Actions](https://hzrd149.github.io/applesauce/overview/actions.html) which are pre-built methods to modify nostr events for a user.
First we need to install the `applesauce-actions` and `applesauce-factory` package
```sh
pnpm install applesauce-actions applesauce-factory
```
Then create a `src/actions.ts` file with
```ts
import { EventFactory } from "applesauce-factory";
import { ActionHub } from "applesauce-actions";
import { eventStore } from "./stores";
import { accounts } from "./accounts";
// The event factory is used to build and modify nostr events
export const factory = new EventFactory({
// accounts.signer is a NIP-07 signer that signs with the currently active account
signer: accounts.signer,
});
// The action hub is used to run Actions against the event store
export const actions = new ActionHub(eventStore, factory);
```
Then create a `toggleFollow` method that will add or remove fiatjaf from the users contacts.
> We are using the `exec` method to run the action, and the [`forEach`](https://rxjs.dev/api/index/class/Observable#foreach) method from RxJS allows us to await for all the events to be published
```tsx
function App() {
// ...
const toggleFollow = async () => {
// send any created events to rxNostr and the event store
const publish = (event: NostrEvent) => {
eventStore.add(event);
rxNostr.send(event);
};
if (isFollowing()) {
await actions
.exec(UnfollowUser, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d")
.forEach(publish);
} else {
await actions
.exec(
FollowUser,
"3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d",
"wss://pyramid.fiatjaf.com/"
)
.forEach(publish);
}
};
// ...
return (
<>
{/* ... */}
<div class="card">
{/* ... */}
{contacts() && <button onClick={toggleFollow}>{isFollowing() ? "Unfollow" : "Follow"}</button>}
</div>
</>
);
}
```
## 14. Adding outbox support
The app looks like it works now but if the user reloads the page they will still see an the old version of their contacts list. we need to make sure rxNostr is publishing the events to the users outbox relays.
To do this we can subscribe to the signed in users mailboxes using the query store in `src/nostr.ts`
```ts
import { MailboxesQuery } from "applesauce-core/queries";
import { accounts } from "./accounts";
import { of, switchMap } from "rxjs";
import { queryStore } from "./stores";
// ...
// subscribe to the active account, then subscribe to the users mailboxes and update rxNostr
accounts.active$
.pipe(switchMap((account) => (account ? queryStore.createQuery(MailboxesQuery, account.pubkey) : of(undefined))))
.subscribe((mailboxes) => {
if (mailboxes) rxNostr.setDefaultRelays(mailboxes.outboxes);
else rxNostr.setDefaultRelays([]);
});
```
And that's it! we have a working nostr app that lets users follow and unfollow fiatjaf.
-

@ a39d19ec:3d88f61e
2025-03-18 17:16:50
Nun da das deutsche Bundesregime den Ruin Deutschlands beschlossen hat, der sehr wahrscheinlich mit dem Werkzeug des Geld druckens "finanziert" wird, kamen mir so viele Gedanken zur Geldmengenausweitung, dass ich diese für einmal niedergeschrieben habe.
Die Ausweitung der Geldmenge führt aus klassischer wirtschaftlicher Sicht immer zu Preissteigerungen, weil mehr Geld im Umlauf auf eine begrenzte Menge an Gütern trifft. Dies lässt sich in mehreren Schritten analysieren:
### 1. Quantitätstheorie des Geldes
Die klassische Gleichung der Quantitätstheorie des Geldes lautet:
M • V = P • Y
wobei:
- M die Geldmenge ist,
- V die Umlaufgeschwindigkeit des Geldes,
- P das Preisniveau,
- Y die reale Wirtschaftsleistung (BIP).
Wenn M steigt und V sowie Y konstant bleiben, muss P steigen – also Inflation entstehen.
### 2. Gütermenge bleibt begrenzt
Die Menge an real produzierten Gütern und Dienstleistungen wächst meist nur langsam im Vergleich zur Ausweitung der Geldmenge. Wenn die Geldmenge schneller steigt als die Produktionsgütermenge, führt dies dazu, dass mehr Geld für die gleiche Menge an Waren zur Verfügung steht – die Preise steigen.
### 3. Erwartungseffekte und Spekulation
Wenn Unternehmen und Haushalte erwarten, dass mehr Geld im Umlauf ist, da eine zentrale Planung es so wollte, können sie steigende Preise antizipieren. Unternehmen erhöhen ihre Preise vorab, und Arbeitnehmer fordern höhere Löhne. Dies kann eine sich selbst verstärkende Spirale auslösen.
### 4. Internationale Perspektive
Eine erhöhte Geldmenge kann die Währung abwerten, wenn andere Länder ihre Geldpolitik stabil halten. Eine schwächere Währung macht Importe teurer, was wiederum Preissteigerungen antreibt.
### 5. Kritik an der reinen Geldmengen-Theorie
Der Vollständigkeit halber muss erwähnt werden, dass die meisten modernen Ökonomen im Staatsauftrag argumentieren, dass Inflation nicht nur von der Geldmenge abhängt, sondern auch von der Nachfrage nach Geld (z. B. in einer Wirtschaftskrise). Dennoch zeigt die historische Erfahrung, dass eine unkontrollierte Geldmengenausweitung langfristig immer zu Preissteigerungen führt, wie etwa in der Hyperinflation der Weimarer Republik oder in Simbabwe.
-

@ f1989a96:bcaaf2c1
2025-04-03 14:30:08
Good morning, readers!
Georgian officials froze the bank accounts of five nonprofit organizations that provide financial and legal support to detained protesters. This follows rising public unrest as Georgia’s regime pushes new laws restricting free speech and assembly, introducing new fines and penalties, and expanding law enforcement powers. By eroding civil protections, the regime makes it more dangerous and costly for activists, dissenters, and everyday citizens to stand up against an increasingly repressive regime.\
\
Meanwhile, the Indian government introduced a new income tax bill that grants tax authorities sweeping surveillance power over anyone they “suspect” of tax evasion. If suspected, tax authorities are legally allowed to access Indians' email, social media, and bank accounts, raising obvious concerns over state overreach and invasions of individual financial privacy.\
\
In freedom tech news, HRF donated 1 billion satoshis to more than 20 projects worldwide, focusing on supporting human rights defenders and vulnerable communities under authoritarian regimes across Asia, Africa, and Latin America. These gifts advance censorship-resistant communications and transactions, bitcoin education, and privacy tools so that dissidents, nonprofits, and individuals may better protect their human rights and financial freedom. In this letter we also spotlight a new open-source mobile Bitcoin wallet called Cove. While still in beta, the wallet can be used with a hardware device or on its own as a hot wallet, offering a flexible self-custody setup for managing Bitcoin.
We end with a podcast in which HRF Chief Strategy Officer Alex Gladstein discusses the state of freedom tech and why Bitcoin stands as the most promising tool for financial liberation.
**Now, let’s get right to it!**
### [**SUBSCRIBE HERE**](https://mailchi.mp/hrf.org/financial-freedom-newsletter?mc_cid=bf652c0a5a)
## **GLOBAL NEWS**
#### **Georgia | Officials Freeze Accounts of Organizations Supporting Protesters**
Georgian officials have [frozen](https://www.amnesty.org/en/latest/news/2025/03/georgia-authorities-freeze-accounts-of-organizations-supporting-protesters-to-kill-the-peaceful-protests/) the bank accounts of five nonprofit organizations that provide financial and legal aid to dissenters. This comes in response to an uprising of protests over new controversial laws that restrict free expression and assembly, increase fines and detention periods, and expand law enforcement powers. Georgian officials justify the account freezes as part of an investigation into “sabotage,” yet they have provided no evidence. Amnesty International [warns](https://www.amnesty.org/en/latest/news/2025/03/georgia-authorities-freeze-accounts-of-organizations-supporting-protesters-to-kill-the-peaceful-protests/) this financial assault could “kill the entire protest movement.” Bitcoin provides a way to circumvent these struggles. Its uncensorable and permissionless nature has helped [sustain](https://www.journalofdemocracy.org/online-exclusive/how-to-dictator-proof-your-money/) pro-democracy movements across Belarus and Nigeria, proving it is capable of addressing the immense financial restrictions dictators impose.
#### **United Arab Emirates | Plans to Launch “Digital Durham” CBDC in 2025**
The United Arab Emirates (UAE) will [launch](https://www.businesstoday.in/technology/news/story/uae-to-launch-digital-dirham-by-year-end-to-modernise-payments-and-noost-financial-inclusion-470013-2025-03-31?utm_source=semafor#) its central bank digital currency (CBDC), the “[Digital Durham](https://cbdctracker.hrf.org/currency/united-arab-emirates),” by the end of 2025. [According](https://www.ledgerinsights.com/uae-to-launch-cbdc-in-q4-2025/) to the central bank, the CBDC will be available through licensed financial institutions and operate via a government-run digital wallet. Every transaction will be recorded on a permissioned blockchain run by the government. The central bank further [admitted](https://u.ae/en/about-the-uae/strategies-initiatives-and-awards/strategies-plans-and-visions/finance-and-economy/central-bank-digital-currency-strategy) the CBDC will replace cash and [assist](https://www.businesstoday.in/technology/news/story/uae-to-launch-digital-dirham-by-year-end-to-modernise-payments-and-noost-financial-inclusion-470013-2025-03-31?utm_source=semafor#) law enforcement “by leaving a digital trail for transactions involving illicit funds.” Officials [claim](https://www.businesstoday.in/technology/news/story/uae-to-launch-digital-dirham-by-year-end-to-modernise-payments-and-noost-financial-inclusion-470013-2025-03-31?utm_source=semafor#) this is to combat financial crime, but it also enables real-time surveillance and tracking of individual financial activity. In a country known for strict laws against dissent and extensive surveillance capabilities, it is not hard to see how a CBDC will erode the autonomy and rights of activists, dissenters, and others who oppose an increasingly authoritarian regime.
#### **India | Grants Tax Authorities Access to Citizens’ Online Data**
Starting in April 2026, the Indian government will [grant](https://economictimes.indiatimes.com/wealth/tax/your-email-and-social-media-account-can-be-accessed-by-income-tax-officer-starting-next-financial-year-in-these-cases/articleshow/118685184.cms) tax authorities legal access to the private online data of any citizen “suspected” of tax evasion. This will include legal access to personal emails, social media, and bank accounts. The new law expands on the Income Tax Act of 1961, which previously limited officials to searching physical premises for financial documents. Now, officials can bypass digital security measures and access private data without consent — all under a legal framework. This dissipation of financial privacy sets an intrusive precedent and opens the door to state-level corruption and surveillance in a country where the Modi regime has already made it clear they are happy to use financial repression to further cement their power.
#### **Myanmar | Bitcoin as a Tool Support Earthquake Disaster Relief**
Last week, a [7.7 magnitude earthquake](https://www.nytimes.com/2025/03/28/world/asia/earthquake-myanmar-thailand-death-toll.html) struck central Burma, with strong tremors reaching neighboring Thailand. The [official death toll ](https://www.reuters.com/business/environment/survivors-myanmar-quake-left-without-food-water-shelter-aid-groups-say-2025-04-01/)has surpassed 2700. And in Bangkok, a 33-story building under construction [collapsed](https://www.youtube.com/watch?v=ynrhyIh4ozo). Despite an already strenuous situation, Burma’s military junta continues its oppression. They are [blocking](https://www.nytimes.com/2025/03/31/world/asia/myanmar-earthquake-rescue.html) rescue teams from reaching the Sagaing region — the epicenter of the earthquake and the heart of Burma’s pro-democracy movement — and instead channeling aid to regime-controlled cities like Naypyidaw and Mandalay. The junta is also continuing to conduct air strikes on civilians and restricting equipment and fuel for aid groups, leaving a [million](https://data.unhcr.org/en/country/mmr) people in Sagaing to fend for themselves. In these repressive circumstances, Bitcoin can provide a censorship-resistant way to send funds directly to those affected.
#### **Angola | Regime Jacks Price of Diesel**
The Angolan regime [raised](https://www.rigzone.com/news/wire/angola_doubles_diesel_prices_after_imf_call_for_subsidy_cuts-25-mar-2025-180020-article/) diesel prices by 50% in the process of eliminating fuel subsidies. Diesel prices suddenly increased from 200 to 300 kwanza per liter, driving up transportation costs in a country where over half the population lives on [less](https://www.rigzone.com/news/wire/angola_doubles_diesel_prices_after_imf_call_for_subsidy_cuts-25-mar-2025-180020-article/) than $2 a day and inflation is over 42%. Previous fuel subsidy cuts in 2023 (where the price of diesel rose [80%](https://www.dw.com/en/angolan-police-crack-down-on-fuel-hike-protests/a-65978231)) sparked [protests](https://www.dw.com/en/angolan-police-crack-down-on-fuel-hike-protests/a-65978231) between taxi drivers, nonprofit workers, and law enforcement. This recent price increase now raises fears of renewed crackdowns. The Angolan regime also introduced new civil society laws that Guilherme Neves, chairman of the human rights organization Associacao Maos Livres, [describes](https://www.dw.com/en/angolan-police-crack-down-on-fuel-hike-protests/a-65978231) as a “license to erase non-governmental organizations that are not government-compliant.” Angolans find themselves in increasingly precarious financial positions as the government erodes the civil safeguards protecting nonprofits and dissenters.
#### **Nicaragua | Ortega’s Dismantling of Press Freedom**
Since coming to power in 2007, Ortega has [closed or seized](https://havanatimes.org/features/ortegas-war-on-journalism-in-nicaragua/) 61 media outlets, imprisoned countless journalists, and forced over 280 journalists into exile. His [assault on press freedom](https://havanatimes.org/features/ortegas-war-on-journalism-in-nicaragua/) has unfolded in two phases: initial raids on local radio stations and TV channels between 2007 and 2017, followed by full-scale censorship in 2018 on independent media outlets like [La Prensa](https://www.laprensani.com/) and [CONFIDENCIAL](https://confidencial.digital/). Ortega then intensified attacks from 2019 to 2021 by closing Nicaragua’s second-oldest newspaper and passing laws to [criminalize](https://havanatimes.org/features/ortegas-war-on-journalism-in-nicaragua/) free expression. This is a deliberate strategy to eliminate dissent and independent voices. What’s happening in Nicaragua highlights the importance of open and decentralized protocols like nostr, which allow journalists to publish freely without getting censored. While still early, it is becoming essential for sharing information absent the fear of being blocked or silenced by autocratic leaders.
## BITCOIN AND FREEDOM TECH NEWS
#### **HRF | Gifts 1 Billion Satoshis to 20+ Open Source Projects Worldwide**
HRF gifted 1 billion satoshis in its Q1 2025 round of [Bitcoin Development Fund](https://hrf.org/program/financial-freedom/bitcoin-development-fund/) (BDF) grants, supporting more than 20 open-source projects around the world. These projects advance Bitcoin education, open-source software, mining decentralization, and privacy tools for activists contending with authoritarian regimes across Asia, Latin America, and Africa. Supporting permissionless financial tools and censorship-resistant technologies empowers dissidents, journalists, and civil society to organize, transact, and communicate without state suppression and interference. Learn more about the grantees and their work [here](https://hrf.org/latest/hrf-bitcoin-development-fund-supports-20-projects-worldwide/).
#### **Cove | New Open-Source and Permissionless Bitcoin Wallet**
[Cove](https://github.com/bitcoinppl/cove) is a new open-source and permissionless mobile Bitcoin wallet that aims to put users in full control of their Bitcoin. Users can connect their own hardware wallet (to manage Bitcoin offline) or use Cove as a hot wallet (to manage Bitcoin online). It also allows users to create multiple wallets from the app itself. In the future, Cove plans to add Unspent Transaction Output (UTXO) selection and coin control, giving users more independence over their transactions and the tools to better protect their financial privacy. While still in beta and only suitable for test funds, this wallet holds promise as a privacy tool to equip dissidents with self-custodied Bitcoin. You can try it [here](https://github.com/bitcoinppl/cove).
#### **Second | New Ark Implementation Launches on Bitcoin Signet**
[Second](https://second.tech/), a company building on Ark, a protocol designed to help scale Bitcoin’s transaction throughput, [launched](https://blog.second.tech/try-ark-on-signet/?ref=nobsbitcoin.com) “Bark.” Bark is a test implementation of the Ark protocol deployed on Bitcoin’s [Signet](https://en.bitcoin.it/wiki/Signet) network (where developers test software). More broadly, the Ark protocol helps make Bitcoin transactions more private, faster, and cheaper, supporting the network in handling more transactions and users with the tradeoff of being less trusted than the mainchain, as funds stored in a noncustodial way on Ark can expire if not used. While it is still in early development, the test release of Bark marks a step toward deployment on the main Bitcoin network. Scaling solutions like Ark could be important for activists and individuals. They might ensure Bitcoin remains accessible to all, even as block space demand increases and network fees rise. Learn about it [here](https://blog.second.tech/try-ark-on-signet/?ref=nobsbitcoin.com).
#### **Braiins | Open Sources Bitcoin Control Board**
[Braiins](https://braiins.com/), a company building tools for Bitcoin mining, [open-sourced](https://x.com/BraiinsMining/status/1904601547855573458) its [BCB100](https://github.com/braiins/BCB100) Bitcoin Control Board, giving miners using their products greater insight and control over their Bitcoin mining hardware and firmware. Sharing the design files and firmware openly helps strengthen Bitcoin’s decentralization, making it more resilient against corporate or state interference. Specifically, open-sourcing mining hardware ensures individual miners can operate independently, reducing censorship risks across the entire network. In turn, this preserves financial freedom by keeping Bitcoin accessible and usable by dissidents, nonprofits, and individuals who need it most.
#### **African Bitcoiners | Publish Bitcoin Starter Guide**
[African Bitcoiners](https://x.com/afribitcoiners) just published “[Bitcoin: Africa’s Guide to Freedom Money](https://x.com/afribitcoiners/status/1904516726273851513),” a Bitcoin guide providing clear, practical insights into how Bitcoin can help people across the continent escape inflation, corrupt regimes, and failing financial systems. It covers essential topics to get started — from choosing a wallet to properly securing Bitcoin. In Africa, where some of the world’s longest-standing dictators restrict even basic financial activity, this guide is a powerful resource for human rights defenders, nonprofits, and everyday citizens. Read it[ here](https://bitcoiners.africa/bitcoin-africas-guide-to-freedom-money/).
#### **OpenSats | 10th Wave of Nostr Grants**
[OpenSats](https://opensats.org/), a nonprofit that supports open-source software development, [announced](https://opensats.org/blog/10th-wave-of-nostr-grants) its tenth wave of grants for projects in the nostr ecosystem. Nostr is a decentralized protocol that enables digital identity and communications outside the reach of authoritarian states. The grant round provides support to nostr Epoxy, which enhances access to nostr by circumventing censorship through a network of paid proxies. This ensures activists and dissidents can continue to communicate even in restrictive environments. Additionally, Zapstore received a grant for providing a permissionless app store built on nostr that enables developers to distribute software without corporate gatekeepers. This provides an open-source alternative to centralized app stores that often comply with government censorship and restrict dissidents’ access to freedom tools.
## RECOMMENDED CONTENT
#### **Freedom Tech with Alex Gladstein**
In this [episode](https://x.com/blockspacepod/status/1896229100702089589?s=46&t=yEPKerGEzeCp5j_mIaNJ8A) of The Gwart Show, Alex Gladstein, chief strategy officer at HRF, breaks down how and why Bitcoin serves as “money dictators can’t stop.” Drawing on more than 17 years of human rights work, he shares real-world examples of activists and citizens using Bitcoin to escape financial repression in authoritarian countries. Gladstein also explores privacy tools, cross-border payments, and why Bitcoin offers promising hope for financial freedom. Watch the full conversation [here](https://www.youtube.com/watch?v=5Ng961QZwI0).
#### **The State of Personal Online Security and Confidentiality with Meredith Whittaker**
In this [keynote](https://www.youtube.com/watch?v=AyH7zoP-JOg) for SXSW 2025, Signal CEO Meredith Whittaker shares her growing concerns around AI, personal data collection, and the erosion of privacy in today’s increasingly digital world. She emphasizes the need for more secure, uncensorable, and privacy-protecting technologies that shield users from surveillance and exploitation, especially in the context of authoritarian regimes. Watch the [full discussion](https://www.youtube.com/watch?v=AyH7zoP-JOg) for a pragmatic view into the future of digital privacy and security.
*If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report [here](https://mailchi.mp/hrf.org/financial-freedom-newsletter?mc_cid=bf652c0a5a).*
*Support the newsletter by donating bitcoin to HRF’s Financial Freedom program [via BTCPay](https://hrf.org/btc).*\
*Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ [hrf.org](http://hrf.org/)*
*The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals [here](https://forms.monday.com/forms/57019f8829449d9e729d9e3545a237ea?r=use1)*.
[**Subscribe to newsletter**](http://financialfreedomreport.org/)
[**Apply for a grant**](https://forms.monday.com/forms/57019f8829449d9e729d9e3545a237ea?r=use1&mc_cid=39c1c9b7e8&mc_eid=778e9876e3)
[**Support our work**](https://hrf.org/btc?mc_cid=39c1c9b7e8&mc_eid=778e9876e3)
[**Visit our website**](https://hrf.org/programs/financial-freedom/)
-

@ a5142938:0ef19da3
2025-04-03 09:55:01
### Core Team
The Core Team drives the project and validates the content.
- [Jean-David Bar](https://njump.me/npub1qr4p7uamcpawv7cr8z9nlhmd60lylukf7lvmtlnpe7r4juwxudzq3hrnll)
To start, I'm managing the project solo. Contact me if you'd like to join!
### Content Enrichers
Our contributors make this site engaging and interesting.
-

@ b8af284d:f82c91dd
2025-03-16 16:42:49

Liebe Abonnenten,
diejenigen, die diese Publikation schon länger abonniert haben, wissen, dass hier immer wieder über den Ursprung des Corona-Virus in einem Labor in Wuhan berichtet wurde. Seit diese Woche ist es „offiziell“ - [der Bundesnachrichtendienst (BND) hält den Labor-Ursprung für die wahrscheinlichste Variante](https://www.zeit.de/2025/11/coronavirus-ursprung-wuhan-labor-china-bnd). Jetzt kann man sich fragen, warum der BND plötzlich umschwenkt: Will man proaktiv erscheinen, weil man die Wahrheit nicht mehr länger verbergen kann? Oder will man die enttäuschten Bürger zurückgewinnen, die aufgrund der Lügen während der Corona-Zeit zunehmend mit Parteien links und rechts außen sympathisiert haben, weil diese die einzigen waren, die den Irrsinn nicht mitgetragen haben?
Auffallend bei den „Recherchen“, die in Wahrheit keine sind, sondern Verlautbarungen des deutschen Geheimdienstes, ist auch das völlige Schweigen über die US-amerikanischen Verwicklungen in das Projekt. [In Wuhan wurde mit amerikanischem Geld geforscht](https://oversight.house.gov/release/breaking-hhs-formally-debars-ecohealth-alliance-dr-peter-daszak-after-covid-select-reveals-pandemic-era-wrongdoing/). Warum der BND diese Tatsache verschweigt, ist Teil der Spekulation. Vermutlich will man Peking alles in die Schuhe schieben, um von den eigenen Versäumnissen abzulenken.
In meinem aktuellen Buch “[Der chinesische (Alp-)Traum](https://www.amazon.de/chinesische-Alb-Traum-geopolitische-Herausforderung/dp/3442317509/ref=sr_1_1?__mk_de_DE=%C3%85M%C3%85%C5%BD%C3%95%C3%91\&crid=XQVCLFVRCJJ\&dib=eyJ2IjoiMSJ9.kCJqsUXZO8NZjieNQjGy3Vez7tqktnhQynFOnuZE9249tfkKZvqdJtpIfcDiLMOyxmF7JFpMfvAC881caUEufT--GHlSCcAt_shhnVSbNLp-cle-VXel7soyPwi8xGPm88hSBKPY93BtjFYdOueFUU7qrOir_paRMiQOmCs7YOAUe7ZCKAb6YXxu_hz8N1eZhXbFcvc6p01Uu0vgIibiOHzbXxtH6ECNUaWCaHCYus4.Jzuq9IYvQtPedtE4YORWFtEmxTtrHh5xe8b-B25o5uA\&dib_tag=se\&keywords=Philipp+Mattheis\&qid=1730736669\&sprefix=philipp+mattheis%2Caps%2C111\&sr=8-1)” ist den Ereignissen in Wuhan ein ganzes Kapitel gewidmet. Es hat nichts an Aktualität eingebüßt. Alle Fakten lagen seit Jahren auf dem Tisch für jeden, den es interessiert hat. [Hier gibt es das gesamte Kapitel nachzulesen.](https://blingbling.substack.com/p/was-geschah-in-wuhan)

Auf jeden Fall zeigt dies, wie der Begriff „Verschwörungstheoretiker“ in den vergangenen Jahren zum Kampfbegriff und Waffe gemacht wurde, um Kritiker zu diffamieren, und die öffentliche Meinung ohne harte Zensur zu lenken. Ähnliches kann man aktuell beim Projekt „Digitaler Euro“ beobachten. Vermutlich kann sich kein Bürger der Europäischen Union daran erinnern, bei seiner Wahlentscheidung jemals gefragt worden zu sein, ob er die Einführung eines „digitalen Euros“ gut findet. Wurde er nämlich nicht. Er kommt aber trotzdem. EZB-Präsidentin Christine Lagarde hat das diese Woche nochmals bekräftigt: [Schon im Oktober will man die Testphase beenden](https://x.com/efenigson/status/1898382481184993711) und an der Einführung arbeiten.
Nun gehört BlingBling nicht zu denjenigen, die im digitalen Euro „Orwell’sches Teufelswerk“ sehen. Strategische Dummheit trifft es besser. Worum geht es?
Sogenannte Central Bank Digital Currencies (CBDC) waren vor einigen Jahren so etwas wie der letzte Schrei in der Zentralbank-Welt. Nachdem Facebook/Meta 2017/18 eine eigene Währung namens Libra auf den Markt bringen wollte, und eine obskure Internet-Währung namens Bitcoin immer mehr Anhänger fand, sahen sich viele Zentralbanken der Welt unter Zugzwang. Was man wollte: eine digitale, direkt von der Zentralbank ausgegebene Währung ohne Bugs, aber mit Features. Mit einer Digital-Währung ließe sich der internationale Zahlungsverkehr direkt und ohne Umweg über den US-Dollar abwickeln. Die Zentralbank bekäme wieder mehr direkten Einfluss auf die Geldschöpfung. Und, wie man aus China lernen konnte, ließen sich digitale Bankkonten auch ganz zum „Nudging von Bürgern“ nutzen. So spekulierten die ersten Verschwörungstheoretiker bald, [ein digitaler Euro ließe sich ja mit einem persönlichen CO2-Konto verknüpfen](https://www.derstandard.de/story/2000124296026/was-eine-digitale-co2-waehrung-fuer-das-klima-bedeuten-wuerde). Wäre letzteres einmal aufgebraucht, könnte der Konto-Inhaber einfach keinen Flug mehr buchen. Auch ließe sich eine expansive Geldpolitik, wie sie bis 2022 praktiziert wurde, ganz einfach mit Negativ-Zinsen umsetzen. Geld würde sich nominal reduzieren, was den Bürger zum Konsum animieren würde. Flüchtigen Kriminellen ließe sich per Knopfdruck das Konto sperren. Der Staat würde also über eine ganze neue Palette an Einflussmöglichkeiten verfügen.
Die Aluhüte United warnten vor einem Orwellschen Überwachungsstaat. Vertreter von Regierungen und Firmen, die diesen digitalen Euro bauen sollten, beschwichtigten. Mit Ralf Wintergerst, CEO von Giesecke+Devrient, nach wie vor heißester Anwärter, um das Projekt in der EU umzusetzen, sprach ich in den vergangenen Jahren mehrmals zu dem Thema. [Zuletzt im Dezember 24](https://blingbling.substack.com/p/euro-thrash).
Wintergerst versichert stets zwei Dinge: Eine Abschaffung von Bargeld sei nicht geplant. Und nur, wenn die Fluchttore Bargeld, Gold und Bitcoin geschlossen werden, greift die dystopische Version. Und zweitens, so Wintergerst, habe niemand ein chinesisches System im Sinne. Der „digitale Euro“ sei für die Bürger gedacht und das Projekt unterliege demokratischer Kontrolle. Ob er Wintergerst und dem guten im Menschen Glauben schenkt, möge jeder Leser selbst entscheiden. Das Interessantere ist ohnehin, dass der digitale Euro ein strategisch dummes Projekt ist.
Dazu muss man wissen, dass eine solche Zentralbankwährung Banken im weitesten Sinne überflüssig macht. Kontos bei Privatbanken werden obsolet, genauso wie Spar-, Fest- und Tagesgeld-Strukturen. Deshalb soll der digitale Euro zunächst auf 3000 Euro pro Bürger beschränkt werden. Das ist also nicht als Maximal-Vermögen gedacht, das dann jedem sozialistischen Einheits-EU-Menschen noch zusteht, sondern dient dazu, das Bankensystem nicht kollabieren zu lassen. Aber wozu überhaupt „ein bisschen digitaler Euro“?
In den USA setzt man mittlerweile 100 Prozent auf die private Alternative: Stablecoins wie Tether (USDT) und Circle (USDC) sind nichts anderes als digitale Währungen. Nur sind sie nicht von einer Zentralbank ausgeben, sondern von privaten Anbietern. Tether hat technisch die Möglichkeit, einen Inhaber vom Zahlungsverkehr auszusperren. Nur dürfte es davon kaum Gebrauch machen, will das Unternehmen nicht rasant Kunden an die Konkurrenz verlieren. Da USDT und USDC mit US-Dollar gedeckt sind (oder zumindest sein sollten, *looking at you, Tether!*), stärken sie außerdem die Rolle des US-Dollars als Leitwährung. Und da die USA sich aktuell sehr über Käufer von Staatsanleihen freuen, um die Zinsen zu drücken, und [Tether einer der größten Halter von US-Staatsanleihen is](https://crypto.news/tether-treasury-holdings-boost-us-debt-resilience-2025/)t, wird es den digitalen Dollar bis auf Weiteres nicht geben.
Den digitalen Yuan gibt es, aber von einer großen Akzeptanz oder Durchdringung der chinesischen Wirtschaft lässt sich nicht sprechen. Kontrolle kann der chinesische Staat ohnehin über seine omnipräsenten Apps WeChat und Alipay ausüben. Was den internationalen Zahlungsverkehr betrifft, [scheint man aktuell eher auf Gold zu setzen](https://blingbling.substack.com/p/goldfinger).
Übrig also bleibt die EU mit einem Projekt, das bereits Milliarden an Entwicklungskosten verschlungen hat. Am Ende bleibt dann ein Mini-Digitaler-Euro in Höhe von 3000 Euro, den niemand wollte, und niemand braucht.
Helfen könnte er allerdings beim Projekt “Mobilisierung der Sparguthaben”. Der Ausdruck geht auf Friedrich Merz zurück. Ursula von der Leyen paraphrasierte ihn jüngst:
[Irgendwie müssen die Billionen von Sparguthaben in Militär-Investitionen umgewandelt werden](https://blingbling.substack.com/p/panzer-statt-autos). Das wird am besten funktionieren mit Anleihen, die schlechter verzinst sind als sonst auf dem Markt üblich. Wie bringt man Leute dazu, dann ihr Geld dort zu investieren? Entweder man zwingt sie, oder man bewirbt die Anleihen mit viel Patriotismus und Propaganda. Die Verschwörungstheoretiker unter uns bekommen also bald Futter, wenn die „Spar- und Investitionsunion” vorgestellt wird.
Like, wenn Dein Aluhut glüht…
*Hinter der Paywall: Wie das Trump-Derangement-Syndrom den Blick auf den Markt trübt. **[Wie es mit Bitcoin, Gold und Aktien weitergeht.](https://blingbling.substack.com/p/gluhende-aluhute)***
-

@ 21335073:a244b1ad
2025-03-15 23:00:40
I want to see Nostr succeed. If you can think of a way I can help make that happen, I’m open to it. I’d like your suggestions.
My schedule’s shifting soon, and I could volunteer a few hours a week to a Nostr project. I won’t have more total time, but how I use it will change.
Why help? I care about freedom. Nostr’s one of the most powerful freedom tools I’ve seen in my lifetime. If I believe that, I should act on it.
I don’t care about money or sats. I’m not rich, I don’t have extra cash. That doesn’t drive me—freedom does. I’m volunteering, not asking for pay.
I’m not here for clout. I’ve had enough spotlight in my life; it doesn’t move me. If I wanted clout, I’d be on Twitter dropping basic takes. Clout’s easy. Freedom’s hard. I’d rather help anonymously. No speaking at events—small meetups are cool for the vibe, but big conferences? Not my thing. I’ll never hit a huge Bitcoin conference. It’s just not my scene.
That said, I could be convinced to step up if it’d really boost Nostr—as long as it’s legal and gets results.
In this space, I’d watch for social engineering. I watch out for it. I’m not here to make friends, just to help. No shade—you all seem great—but I’ve got a full life and awesome friends irl. I don’t need your crew or to be online cool. Connect anonymously if you want; I’d encourage it.
I’m sick of watching other social media alternatives grow while Nostr kinda stalls. I could trash-talk, but I’d rather do something useful.
Skills? I’m good at spotting social media problems and finding possible solutions. I won’t overhype myself—that’s weird—but if you’re responding, you probably see something in me. Perhaps you see something that I don’t see in myself.
If you need help now or later with Nostr projects, reach out. Nostr only—nothing else. Anonymous contact’s fine. Even just a suggestion on how I can pitch in, no project attached, works too. 💜
Creeps or harassment will get blocked or I’ll nuke my simplex code if it becomes a problem.
https://simplex.chat/contact#/?v=2-4&smp=smp%3A%2F%2FSkIkI6EPd2D63F4xFKfHk7I1UGZVNn6k1QWZ5rcyr6w%3D%40smp9.simplex.im%2FbI99B3KuYduH8jDr9ZwyhcSxm2UuR7j0%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAS9C-zPzqW41PKySfPCEizcXb1QCus6AyDkTTjfyMIRM%253D%26srv%3Djssqzccmrcws6bhmn77vgmhfjmhwlyr3u7puw4erkyoosywgl67slqqd.onion
-

@ d5c3d063:4d1159b3
2025-04-03 04:09:56
### ทรัมป์ ขึ้นภาษีนำเข้า
สิ่งที่คุณเห็น…กับสิ่งที่คุณมองไม่เห็น
คุณ #เห็น แค่ฝั่งที่ดูดีในข่าวภาคค่ำ
แต่คุณ #ไม่เห็น
– คนทั้งประเทศ ต้องจ่ายของแพงขึ้น
– ธุรกิจเล็ก ๆ ที่พึ่งการนำเข้า…ถูกบีบให้ตาย
– ผู้บริโภคต้องเสียเงินมากขึ้น โดยไม่มีทางเลือก
รัฐอ้างว่า *"ปกป้องประเทศ"* แต่จริง ๆ แล้วเขาแค่
โยนภาระให้คนส่วนใหญ่ เพื่ออุ้มผลประโยชน์บางกลุ่ม
เหมือนที่ Bastiat เรียกว่า *“การปล้นที่ถูกกฎหมาย”*
Hazlitt ขยายต่อใน Economics in One Lesson ว่า
> เศรษฐศาสตร์ที่ดี ต้องมองให้พ้นจากผลเฉพาะหน้า
> และมองให้เห็นผลกระทบต่อทุกคน ไม่ใช่แค่บางกลุ่ม
เงินเฟ้อ คือการขโมยแบบเงียบ ๆ
ภาษีศุลกากร คือการปล้นอย่างเปิดเผย
วันนี้ #EIOL น่าจะถึงมือเพื่อนๆ หลายคนแล้ว เล่มนี้ไม่ต้องอ่านทีละบทก็ได้ ลองเปิดไปบทที่ 11 เลยแล้วจะเจอ**ค้อนปอน**สำหรับทุบมายาคดีทางเศรษฐกิจที่รัฐใช้กับเรามาทั้งชีวิต
อ่าน #เศรษฐศาสตร์เล่มเดียวจบ แล้วคุณอาจไม่มีวันมอง “นโยบายเพื่อประชาชน” ได้เหมือนเดิมอีก เพราะบางที...สิ่งที่คุณไม่เคยเห็น อาจเป็นสิ่งที่คุณควรรู้(เห็น)ให้เร็วที่สุด
#Siamstr
-

@ a95c6243:d345522c
2025-03-15 10:56:08
*Was nützt die schönste Schuldenbremse, wenn der Russe vor der Tür steht?* *\
Wir können uns verteidigen lernen oder alle Russisch lernen.* *\
Jens Spahn*  
**In der Politik ist buchstäblich keine Idee zu riskant, kein Mittel zu schäbig und keine Lüge zu dreist,** als dass sie nicht benutzt würden. Aber der Clou ist, dass diese Masche immer noch funktioniert, wenn nicht sogar immer besser. Ist das alles wirklich so schwer zu durchschauen? Mir fehlen langsam die Worte.
**Aktuell werden sowohl in der Europäischen Union als auch in Deutschland** riesige Milliardenpakete für die [Aufrüstung](https://transition-news.org/eu-halt-weiter-kurs-auf-krieg-hunderte-milliarden-fur-aufrustung-beschlossen) – also für die Rüstungsindustrie – geschnürt. Die EU will 800 Milliarden Euro locker machen, in Deutschland sollen es 500 Milliarden «Sondervermögen» sein. Verteidigung nennen das unsere «Führer», innerhalb der Union und auch an «unserer Ostflanke», der Ukraine.
**Das nötige Feindbild konnte inzwischen signifikant erweitert werden.** Schuld an allem und zudem gefährlich ist nicht mehr nur Putin, sondern jetzt auch Trump. Europa müsse sich sowohl gegen Russland als auch gegen die USA schützen und rüsten, wird uns eingetrichtert.
**Und während durch Diplomatie genau dieser beiden Staaten** gerade endlich mal Bewegung in die Bemühungen um einen Frieden oder wenigstens einen Waffenstillstand in der Ukraine kommt, rasselt man im moralisch überlegenen Zeigefinger-Europa so richtig mit dem Säbel.
**Begleitet und gestützt wird der ganze Prozess** – wie sollte es anders sein – von den «Qualitätsmedien». Dass Russland einen Angriff auf «Europa» plant, weiß nicht nur der deutsche Verteidigungsminister (und mit Abstand beliebteste Politiker) Pistorius, sondern dank ihnen auch jedes Kind. Uns bleiben nur noch wenige Jahre. Zum Glück bereitet sich die Bundeswehr schon sehr konkret [auf einen Krieg](https://archive.is/VE8ZM) vor.
**Die** ***FAZ*** **und Corona-Gesundheitsminister Spahn markieren einen traurigen Höhepunkt.** Hier haben sich «politische und publizistische Verantwortungslosigkeit propagandistisch gegenseitig befruchtet», wie es bei den *NachDenkSeiten* [heißt](https://www.nachdenkseiten.de/?p=130064). Die Aussage Spahns in dem Interview, «der Russe steht vor der Tür», ist das eine. Die Zeitung verschärfte die Sache jedoch, indem sie das Zitat explizit in den [Titel](https://archive.is/QJdID) übernahm, der in einer [ersten Version](https://archive.is/fNuGA) scheinbar zu harmlos war.
**Eine große Mehrheit der deutschen Bevölkerung findet Aufrüstung und mehr Schulden toll,** wie *[ARD](https://archive.is/M3DSk)* und *[ZDF](https://archive.is/ggvJB)* sehr passend ermittelt haben wollen. Ähnliches gelte für eine noch stärkere militärische Unterstützung der Ukraine. Etwas skeptischer seien die Befragten bezüglich der Entsendung von Bundeswehrsoldaten dorthin, aber immerhin etwa fifty-fifty.
**Eigentlich ist jedoch die Meinung der Menschen in «unseren Demokratien» irrelevant.** Sowohl in der Europäischen Union als auch in Deutschland sind die «Eliten» offenbar der Ansicht, der Souverän habe in Fragen von Krieg und Frieden sowie von aberwitzigen astronomischen Schulden kein Wörtchen mitzureden. Frau von der Leyen möchte über 150 Milliarden aus dem Gesamtpaket unter Verwendung von Artikel 122 des EU-Vertrags ohne das Europäische Parlament entscheiden – wenn auch nicht völlig [kritiklos](https://www.berliner-zeitung.de/politik-gesellschaft/geopolitik/aufruestung-widerstand-gegen-eu-plaene-waechst-kommission-uebertreibt-russische-gefahr-li.2306863).
**In Deutschland wollen CDU/CSU und SPD zur Aufweichung der «Schuldenbremse»** mehrere Änderungen des Grundgesetzes durch das abgewählte Parlament peitschen. Dieser Versuch, mit dem alten [Bundestag](https://www.bundestag.de/dokumente/textarchiv/2025/kw11-de-sondersitzung-1056228) eine Zweidrittelmehrheit zu erzielen, die im neuen nicht mehr gegeben wäre, ist mindestens verfassungsrechtlich umstritten.
**Das Manöver scheint aber zu funktionieren.** Heute haben die Grünen [zugestimmt](https://www.reuters.com/world/europe/germany-faces-debt-deal-cliffhanger-merz-strives-greens-backing-2025-03-14/), nachdem Kanzlerkandidat Merz läppische 100 Milliarden für «irgendwas mit Klima» zugesichert hatte. Die Abstimmung im Plenum soll am kommenden Dienstag erfolgen – nur eine Woche, bevor sich der neu gewählte Bundestag konstituieren wird.
**Interessant sind die Argumente, die BlackRocker Merz für seine Attacke** auf Grundgesetz und Demokratie ins Feld führt. Abgesehen von der angeblichen Eile, «unsere Verteidigungsfähigkeit deutlich zu erhöhen» (ausgelöst unter anderem durch «die Münchner Sicherheitskonferenz und die Ereignisse im Weißen Haus»), ließ uns der CDU-Chef wissen, dass Deutschland einfach auf die internationale Bühne zurück müsse. Merz [schwadronierte](https://x.com/CDU/status/1900168761686044894) gefährlich mehrdeutig:
> «Die ganze Welt schaut in diesen Tagen und Wochen auf Deutschland. Wir haben in der Europäischen Union und auf der Welt eine Aufgabe, die weit über die Grenzen unseres eigenen Landes hinausgeht.»
 
  
*\[Titelbild:* *[Tag des Sieges](https://pixabay.com/de/photos/parade-tag-des-sieges-samara-182508/)]*
***
Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/propaganda-wahnsinn-und-demokratur)*** erschienen.
-

@ 3c7dc2c5:805642a8
2025-04-02 21:15:55
## 🧠Quote(s) of the week:
CBDC the digital euro - a centralized solution in search of a problem. While the ECB may see it as a way to 'modernize' finance, true innovation comes from empowering individuals, not consolidating control. CBDCs are just surveillance tools disguised as innovation. Bitcoin is the only true digital money—decentralized, scarce, and free. Stack sats, not CBDCs.
## 🧡Bitcoin news🧡
2025
https://i.ibb.co/vx988kT1/Gn-Ix-Dp-YWs-AASkiw.jpg
On the 24th of March:
➡️The Pakistan central bank is exploring mining Bitcoin with excess electricity.
➡️'MicroStrategy just added another 7,000 Bitcoin to their treasury. They're now holding over 506,000 BTC ($44 billion).
Look at the corporate Bitcoin ownership breakdown:
- MicroStrategy: 506,000+ BTC
- Marathon: ~46,000 BTC (10x smaller)
- Riot: ~19,000 BTC (26x smaller)
That acquisition curve has gone parabolic since Q4 2024.
Strategy's buying pace now rivals what we're seeing from the Bitcoin ETFs, a single public company absorbing supply at an institutional scale.
Clear institutional conviction signal here.' -Ecoinometrics
➡️SQUARE CEO JACK DORSEY: "Bitcoin will make the current financial system feel as irrelevant as the fax machine."
On the 25th of March:
➡️'BITCOIN HASH-RIBBON FLASHES BUY SIGNAL
- This is one of the most reliable "buy" indicators.
- Significant price gains have followed 7 out of the last 7 times this indicator was triggered.' -Bitcoin Archive
(foto)
Bitcoin is always a buy. Just DCA.
➡️GameStop includes Bitcoin as a treasury reserve asset in its investment policy update. GameStop has $4.6 billion in cash to invest.
➡️Strategy’s sale of 8.5 million STRF shares closes today, unlocking $711 million in new capital to buy more Bitcoin.
➡️BBC News reports from a remote community of 15,000 people in the far north-western tip of Zambia relying on hydroelectric power, “The bitcoin mine now accounts for around 30% of the plant's revenue allowing them to keep the prices down for the local town” - Source: https://www.bbc.com/news/articles/cly4xe373p4o
Gridless is doing a splendid job in Africa and showing through proof-of-work that if you aren't mining Bitcoin, you are wasting energy. It's time for such communities to appear more around the world.
Daniel Batten: 'They couldn't resist zooming out and implying this is an outlier (it isn't, the majority of off-grid bitcoin mining operations are renewably powered). In doing so BBC made three factually incorrect statements at the end about Bitcoin mining straining grids (multiple peer-reviewed studies show the opposite is true), and "Greenidge gas power plant in New York which was renovated to mine bitcoin" (it didn't, it re-opened to supply power back to the grid), and stating that Bitcoin mining needs artificial govt incentives or rules to do the right thing (It doesn't, it's become 56.7% sustainably powered without any govt incentives)
But let's shine the light on the positive - it has far fewer factually incorrect statements than previous reporting, and it is a step in the right direction in its gradual journey towards objective Bitcoin reporting for a media company that has until now only published negative news stories on Bitcoin.'
➡️Femke Halsema, Mayor of Amsterdam, wants a national ban on Bitcoin payments: "It undermines our civilization".
I rather believe the opposite.
Under Femke Halsema - Amsterdam
- The number of civil servants increased by 50% (14K -> 20K)
- Debt increased by 150% (4 billion -> approx. 10 billion)
Despite high revenues, Amsterdam has to borrow nearly half a billion euros every year. Local taxes continue to rise, whether it's water authority taxes or property taxes (OZB). But, above all, you should be concerned about those 0.3% criminal Bitcoin / Crypto transactions (worldwide). The audacity.
Even if the Netherlands were to legally ban Bitcoin payments, users could easily continue trading through foreign exchanges or peer-to-peer platforms. A ban might actually push Bitcoin usage further underground, making oversight of suspicious transactions worse rather than better.
➡️Mt. Gox moves 11.501 Bitcoin ($1B) for creditor repayment.
➡️BlackRock launched a European Bitcoin ETP today - Bloomberg
➡️North Carolina introduces a bill to invest 5% of state funds into Bitcoin.
On the 26th of March:
➡️NYDIG just became a big Bitcoin miner.
Crusoe, the first to scale Bitcoin mining off flared gas (~200MW worth, across 425 data centers) has sold its entire Bitcoin mining business to NYDIG.
➡️Metaplanet has raised ~$55.2m (¥8.28b) of equity capital through three trading days this week while partially deleveraging with the redemption of $23.3m (¥3.5b) of 0% ordinary bonds.
➡️GameStop can service a loan of up to $100 BILLION for 4.6 years with its existing $4.6b cash balance at 1% interest.
That's twice the amount of Bitcoin Michael Saylor's Strategy currently holds.
➡️New feature by Protonmail enables their 100 million users to send Bitcoin using their email addresses.
➡️The Blockchain Group confirms the acquisition of 580 BTC for ~€47.3 million, the holding of a total of 620 BTC, and a BTC Yield of 709.8% YTD.
→ Confirmation of the acquisition of 580 BTC for ~€47.3 million at ~€81,550 per bitcoin
→ Total group holdings of 620 BTC for ~€50.5 million at ~€81,480 per bitcoin
→ Adoption of ‘BTC Yield’, ‘BTC Gain’, and ‘BTC € Gain’ as KPIs, following the steps of Strategy and Metaplanet
This is a major step in our Bitcoin Treasury Company strategy focused on increasing Bitcoin per share over time.
Source: https://t.co/QDj61ZDe6O
The Blockchain Group is Europe's First Bitcoin Treasury Company!
On the 27th of March:
➡️'Bitcoin's 4-year Compound Annual Growth Rate (CAGR) is at historic lows.' -Pierre Rochard
➡️Daniel Batten: Yet another paper on Bitcoin and energy
TL:DR: "The opportunities offered by bitcoin mining in reduction of the greenhouse gas emissions and renewable energy transition
are greater than generally assumed"
The journal has a (high) impact factor of 7.1."
Source: https://t.co/W3gytMgcpC
➡️A home miner with only 4 machines mined block 888737.
https://i.ibb.co/7xm91R4t/Gn-Ef-H9y-Ws-AA4jkn.jpg
Bitcoin proves anyone can participate and earn—true freedom!
➡️'Short-Term Holders have increased their Bitcoin holdings by 201,743 BTC to 5,750,076 BTC since January, remaining below previous cycle peaks.
200K BTC are currently held at an unrealized loss, representing about $17B.' -Bitcoin News
➡️Bitcoin mining hardware manufacturer Canaan signs a three-year colocation agreement with Mawson Infrastructure Group's Mawson Hosting LLC for facilities in Midland, Pennsylvania, and Edna, Texas. Most of the 4.7 EH/s hashrate is expected to be operational by Q2 2025.
On the 28th of March:
➡️If Saylor had bet on ETH instead of Bitcoin, Strategy would be down $9 billion, instead of up $9 billion like they are today.
ETHBTC made fresh lows 0.02210. Ether is down 74% against Bitcoin since switching from proof of work to proof of stake. Yikes!
➡️Representative introduces a strategic Bitcoin reserve bill in South Carolina.
➡️A Russian company built a Bitcoin mine in the Arctic.
Set in the frozen city of Norilsk, the facility taps into cheap excess energy from one of the world's most isolated industrial hubs.
➡️The price of bitcoin has nearly followed the same phases of volatility for 15 years, according to Fidelity.
https://i.ibb.co/LdQfrqG0/Gn-Ig-Skd-XMAAi-L3r.jpg
another great chart:
https://i.ibb.co/G4WmDjhd/Gn-JED1q-Xk-AAq-Kqk.jpg
On the 29th of March:
➡️Public miner MARA with a $2B common stock offering to buy more Bitcoin.
https://i.ibb.co/PZZxXJ37/Gn-Kj-Vqza-EAEUG-V.png
➡️California has officially included Bitcoin Rights protections in its newly proposed digital asset bill.
If passed, it will guarantee the right to self-custody for nearly 40M residents and prohibit discrimination against Bitcoin use.
➡️The number of addresses with more than one Bitcoin has fallen below 1 million, standing today at 995,207.
On the 31st of March:
➡️Larry Fink, Founder/CEO of BlackRock in his annual letter to shareholders:
“If the U.S. doesn't get its debt under control, if deficits keep ballooning, America risks losing that position to digital assets like Bitcoin."
https://www.blackrock.com/corporate/literature/presentation/larry-fink-annual-chairmans-letter.pdf
➡️Strategy has acquired 22,048 BTC for ~$1.92 billion at ~$86,969 per bitcoin and has achieved a BTC Yield of 11.0% YTD 2025. As of 3/30/2025, Strategy holds 528,185 $BTC acquired for ~$35.63 billion at ~$67,458 per bitcoin.
➡️ The Bitcoin Policy Institute releases a framework for the USA to buy $200 billion worth of #Bitcoin using Bit Bonds.
➡️Is Indonesia the next Bitcoin Country? Bitcoin Indonesia mapped out the entire Bitcoin ecosystem.
A new map shows Bitcoin adoption EXPLODING across the Southeast Asian island nation of Indonesia.
Check out all the communities, projects, and businesses embracing Bitcoin. The revolution is happening.
https://i.ibb.co/cXL8mC0x/Gnbdg-Lub-IAAdwcb.jpg
On the 1st of April:
➡️'Over 73,353 BTC were bought by corporations in Q1 2025.
Only 40,500 BTC new Bitcoin was mined, but still no supply shock, for now...
Which company do you want to see adopt BTC next?'
Here is the breakdown by Alec: https://x.com/Alec_Bitcoin/status/1907062290345783723
➡️After skeptics questioned Tether’s Bitcoin holdings, CEO Paolo Ardoino fired back, sharing the company’s BTC address with a confirmed balance of 92,646 BTC.
On the same day Tether bought 8,888 Bitcoin worth $735 million as per on-chain data. They now hold over 100,000 BTC.
➡️'GameStop just raised $1.48B. They are expected to use that and possibly more of the now $6B+ on their balance sheet to buy Bitcoin. A master class on how to pivot from meme stock to capitalize on volatility in the ultimate store of value.' -James Lavish
➡️Texas' state house Democrats have proposed a bill that would authorize up to $250 million in state investment in Bitcoin and up to $10 million for each municipality and county.
➡️Human Rights Foundation donates 10 Bitcoins worth $830,000 to over 20 projects worldwide.
Alex Gladstein: '1 billion sats gifted carefully to a variety of stellar organizations and individuals to support BTC privacy, decentralization, education, and p2p use, aimed at folks working under authoritarianism.'
## 💸Traditional Finance / Macro:
On the 29th of March
👉🏽'From Wednesday to Friday, the S&P 500 lost -$100 billion PER trading hour for a total of -$2 TRILLION.
Then, after the market closed on Friday, S&P 500 futures erased ANOTHER -$120 billion in minutes.' -TKL
## 🏦Banks:
👉🏽 no news
## 🌎Macro/Geopolitics:
On the 24th of March:
👉🏽Financelot: 'This is fascinating. The Dow Jones to Gold Ratio is about to cross a level only seen 4 times in history.
Every time it crossed this level it marked the beginning of an 18-month recession/depression.
1929, 1973, 2008 & 2025'
I don't think we won't see a depression. History rhymes but doesn't always mean it will repeat, although human behavior stays the same. For now, it means the market is overvalued, gold is undervalued, or both.
👉🏽US household wealth is falling:
US household equity wealth is set to drop a whopping -$3 trillion this quarter, the most since the 2022 bear market, according to BofA estimates.
By comparison, equity holdings rose +$9 trillion in 2024 to a record $56 trillion.
In other words, one-third of last year's gains have likely been wiped out due to the recent market pullback.
Furthermore, the top 10% of the wealthiest Americans own 87% of US stocks.
This, in turn, may negatively impact consumer spending as the top 10% reflect a record 50% of all consumer expenditures.
Consumer spending is set to slow in Q2 2025.' -TKL
👉🏽Demolition of the Boiler House at Moorburg Power Plant in Hamburg. Germany is preparing for combat by dynamiting its own modern energy infrastructure down. This was the most advanced coal plant. 6 years old and cost three billion euros. The Netherlands is following a similar policy—they poured concrete into their gas drilling pipes.
BowTiedMara on Twitter: "In 2022, a girl tied herself to the net at Roland Garros in protest, and she wore a T-shirt that said: "We have 1,028 days left."
Today, the 27th of March, marks those 1,028 days, and nothing happened.
Climate doomers are like Aztecs who think the sun stops unless they cut out some organs."
👉🏽Starting in April, the 66,000 employees of the European institutions will receive their seventh salary increase in just three years! Normally, this happens at most once per year. The President of the European Commission, Ursula von der Leyen, will see the largest increase, with her monthly salary rising to €34,800—an increase of €2,700—according to a report by the German newspaper Bild-Zeitung today.
For the Dutch readers: https://ejbron.wordpress.com/2025/03/24/eu-bureaucraten-en-politici-krijgen-de-7e-salarisverhoging-sinds-2022/
They are compensating for the inflation they impose on the EU. Lucky them Fair to say we need a DOGE in Europe.
On the 25th of March:
👉🏽Dutch minister announces a huge increase in excise duties of 25.8 cents on gasoline. On top of that, the price of gasoline will rise by an additional 7 cents due to the blending requirement and 11 cents due to the ETS-2 regulation. In a free market, prices would not be announced by politicians but would emerge through supply and demand. How I love the EU....although it is a bit more nuanced. The temporary discount is ending. Unless the parliament decides to extend it, the price of gasoline will rise. The Dutch government should simply spend less and abolish all taxes, excise duties, and levies on food, fuel, and energy. Never gonna happen though.
👉🏽"Shell will be thoroughly reviewing all its chemical divisions worldwide in the coming period. In Europe, this could lead to the partial or complete closure of various chemical branches." As mentioned multiple times last month, major industrial companies sounded the alarm. They warned that high energy costs in the Netherlands put their future at risk. Additionally, sustainability efforts and unclear government policies are challenging the sector. Frans Everts, President-Director of Shell Netherlands, warned that the entire industry could collapse.
The Green Deal is moving full speed ahead—soon everyone will be relying on food banks…
For the Dutch readers: https://nos.nl/artikel/2561036-shell-kijkt-naar-gedeeltelijke-sluiting-van-chemie-onderdelen
On the 26th of March:
👉🏽EU countries will start using a digital driver’s license from 2030. This is the result of negotiations between the European Parliament and EU member states. In the Netherlands, the digital license will be valid for ten years and will be accessible via an app. And we all know which app that will be! The EU Digital Wallet must be filled, after all.
Not just your driver’s license—everything will soon be linked to your digital identity. It’s all right there on the EU’s website, and it’s been planned for a long time. The COVID pass was already part of the rollout. The fact that they present these as separate steps just shows that they know people wouldn’t accept it if they were fully aware of what’s happening.
On the 27th of March:
👉🏽Gold surpasses $3,100 for the first time in history.
TKL: 'Gold prices have hit 50 all-time highs over the last 12 months, its best streak in 12 years.
This is also the 3rd-longest streak on record after a historic run during the late 1970s.
The 1970s came with a period of double-digit inflation, stagnant economic growth, and a high unemployment rate, also known as stagflation.
As a result, gold prices recorded 4 consecutive yearly gains.'
On the 31st of March for the first time, gold blasted through $100,000/kilogram.
This time, gold prices have rallied 39% over the last 12 months, are up 16% year-to-date, and are on track for the 3rd annual positive performance.'
👉🏽NATO Secretary General Rutte insists there will be no normalization of relations with Russia for decades to come.
On March 14, 2025, Bloomberg, Rutte says: "Once the war is over, relations with Russia will gradually be restored."
On March 26, 2025, Rutte said: "There will be no normalization of relations with Russia for decades, even after the war is over."
That is the Mark I know!
"Mark Rutte, the long-serving Dutch Prime Minister, earned the nickname “Pinokkio” (Dutch for Pinocchio) primarily because of perceived dishonesty or evasiveness in political debates and scandals. While some still view Rutte as a pragmatic and stable leader, the nickname “Pinokkio” reflects a broader public sentiment of distrust, especially among those who felt betrayed by his communication style or decisions.”
On the 28th of March:
👉🏽US consumers now expect 5.0%(!) inflation in the next twelve months. Inflation expectations have DOUBLED in just four months. That's huge! Long-term US inflation expectations have officially SURGED to 4.1%, the highest level since 1993.
Tariff front-running has led to a $300+ BILLION trade deficit in 2 months, and consumer sentiment has collapsed.
Atlanta Fed is now projecting that Q1 GDP will be -2.8%… a large contraction.
It’s negative even “gold adjusted”
4 weeks ago it was +2.3%
8 weeks ago it was +3.9%
Yikes!
👉🏽The State Department is officially shutting down USAID and has formally notified Congress of its closure.
The remaining 900 employees are set to be terminated.
👉🏽Argentina’s Economy Grows 6.5% in January. Argentina’s Poverty Rate Drops from 52.9% to 38.1% in 15 Months Under Javier Milei
👉🏽Fix the money, fix the world:
DOGE “There is actually really only ONE BANK ACCOUNT that's used to disperse ALL monies that go out of the federal government”
“It's a big one — A couple of weeks ago it had $800 billion in it, it's the treasury general account”
“We're serving 580+ agencies. And up until very recently, effectively they could say, make the payment and Treasury just sent it out as fast as possible. NO VERIFICATION”
“There's a $500 billion of fraud every year. There are hundreds of billion dollars of improper payments and we can't pass an audit. The consolidated financial report is produced by treasury and we cannot pass an audit”
Extremely fascinating interview by Bret Baier with the highly talented and competent DOGE team, which is rigorously streamlining the U.S. government bureaucracy. This work can only be done by competent (and motivated) outsiders with experience. Also urgently needed in the Netherlands, and in Europe.
On the 29th of March:
👉🏽'US debt has been "limited" by the $36.104 trillion debt ceiling since January but the liabilities don't stop rising. As of today, US debt is now ~$37 trillion.
Treasury has burned through $560BN of its cash balance in the past month. Just $280BN left.' -ZeroHedge
On the 1st of April:
In recent weeks, I have shared my opinion on the latest Dutch pension fund drama. This week:
https://i.ibb.co/96ZhS0W/Gn-XEVQRXw-AM6b0-A.jpg
APG and pension funds refused to invest in Dutch housing (for political reasons). This involved 25 billion euros.
Currently we almost have a political scandal over a medal, but the fact that our pension system is being put at risk...no biggie!?
For our own housing market? “Too political.”
For war and Brussels' military ambitions? €100,000,000,000—no problem.
They’re gambling with your pension while first-time buyers can’t afford a home and seniors struggle to make ends meet. Our money, their agenda.
Got Bitcoin?
I will end this Weekly Recap with a Stanley Druckenmiller quote:
"My favorite quote of all time is maybe Mark Twain: "Put all your eggs in one basket and watch the basket carefully."
"I tend to think that's what great investors do."
I know what I do and have. Bitcoin!
## 🎁If you have made it this far I would like to give you a little gift:
What Bitcoin Did:
Peter Dunworth is the Director of a multi-family office and is the co-founder of The Bitcoin Adviser. In this episode, they discuss why Bitcoin is the only asset that can recapitalize the financial system, why Peter believes Bitcoin could become a $100 trillion asset within a decade, why credit markets are ultimately a collateral problem, and why financializing Bitcoin might be necessary to save Main Street from being collateral damage. They also get into Australia's property obsession, GameStop’s pivot to Bitcoin, the difference between Bitcoin derivatives and the asset itself, and MicroStrategy.
https://www.youtube.com/watch?v=_bSprc0IAow
Credit: I have used multiple sources!
My savings account: Bitcoin The tool I recommend for setting up a Bitcoin savings plan: PocketBitcoin especially suited for beginners or people who want to invest in Bitcoin with an automated investment plan once a week or monthly.
`Use the code SE3997`
Get your Bitcoin out of exchanges. Save them on a hardware wallet, run your own node...be your own bank. Not your keys, not your coins. It's that simple. ⠀
⠀
⠀⠀ ⠀ ⠀⠀⠀
Do you think this post is helpful to you? If so, please share it and support my work with a zap.
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
⭐ Many thanks⭐
Felipe - Bitcoin Friday!
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
-

@ ef53426a:7e988851
2025-04-02 21:02:06
# Bartering and early money
\
Early societies bartered goods, but transactions were often complicated. The value of goods doesn’t always align.
Enter money. It’s used as an indirect exchange for any goods, so everyone wants it.
Early money wasn’t anything like what we use today. For example, the inhabitants of Yap Island (Micronesia) used large Rai stones for trade. New stones were dragged up a hill for everyone to see. The owner would then exchange part of the stone for goods and services.
As they were hard to quarry and move, Rai stones retained their value (salability). Then, an Irish-American captain started importing stones using modern technology. Soon enough, they became so common, they no longer worked as money.
---
# Gold — the basis for sound money
\
Smelting made it possible to create highly salable and transportable coins. Gold was best because it’s virtually impossible to destroy and can’t be synthesized using other materials. It has a fairly limited supply, which grows slowly and predictably (due to the difficulty of mining).
Technologies like the telegraph and trains made it easier for both people and goods to get from point A to point B. That, in turn, justified forms of payment like checks, paper receipts, and bills. But paper is not worth much unless it’s backed by something.
Governments worldwide issued paper money backed by precious metals, which they stored in vaults. By 1900, around 50 countries had adopted the Gold Standard. This was sound money.
---
# Currencies devalued
\
Roman emperor Julius Caesar issued the Aureus, an empire-standard coin containing 8 grams of gold. But as growth began to slow, rulers started ‘coin clipping’, reducing the quantity of precious metal in coins. This eventually triggered a series of economic crises that led to the downfall of the Roman Empire.
The gold standard had one major flaw: it had to be stored in bank vaults. This created a highly centralized system in which governments controlled the value of paper money. If they wanted to, they could always increase the supply of money without increasing the corresponding amount of gold.
In 1914, nearly every major European power decided to do this to fund their war operations. Rather than raising taxes, they simply printed new money with no extra gold. The standard had been abandoned.
---
# Government-backed money
\
Governments chose to introduce fiat money – currency backed by decree rather than gold. The adoption of the fiat system led to an age of unsound money shaped by ever-greater intervention in the economy as governments scrambled to stabilize their currencies.
By 1944, the end of the Second World War was in sight, and the victors began planning the postwar economic order. The world’s currencies would be tied to the US dollar at a fixed exchange rate. The dollar would in turn be tied to the value of gold, again at a fixed rate.
The United States bent the rules and inflated its own currency compared to gold. Other nations inflated their currencies compared to the dollar. On August 15, 1971, President Nixon announced that dollars would no longer be convertible to gold.
---
# Sound money = functioning economy
\
Sound money encourages people to save and invest, enabling sustainable, long-term growth. Why? Well, humans have a natural positive time preference: we prefer instant gratification over future gratification. Sound money prompts us to think more about the future.
The more capital accumulation there is, the greater the chance of stable, long-term economic growth. Unsound money distorts capital accumulation. When governments interfere with the money supply, they also interfere with prices. And prices give investors the information they need to make good decisions without having to learn every tiny detail about global events.
---
# Recessions and debt arise from unsound money
\
Government interference takes the form of central planning. No single person, agency, or department ever has access to all the information necessary to understand the vast and complex economy. Interventions distort markets, creating boom and bust cycles.
According to Keynes and his followers, the best way to respond to recessions is to increase spending. You could lower taxes, but people don’t usually spend their extra money. Raising taxes is unpopular, so governments invariably decide to increase the money supply. Saving becomes less attractive, creating a culture of unwise spending and growing debt.
We need to return to sound money and a new gold standard. Enter bitcoin.
---
# Bitcoin is scarce
\
Bitcoin has similar traits to gold. Its supply is literally fixed. Once there are 21 million bitcoins in circulation, no more will be issued.
The supply grows at a diminishing rate. Computers across the Bitcoin network pool their processing power to solve complex algorithmic problems. Once these puzzles have been cracked, the “miners” receive bitcoins as a reward.
Satoshi Nakamoto designed the system to avoid gold rushes. The algorithmic problems become more difficult to solve as the number of computers working on them rises, guaranteeing a steady and reliable supply. Also, the number of bitcoins issued is halved every four years, resulting in ever-smaller releases until 2140, after which no more coins will be released.
That makes bitcoin unique. It is the only good that is defined by absolute scarcity. No amount of time or resources can create more bitcoins than the programmed supply allows. The supply cannot be manipulated, making it a perfect store of value.
---
# Bitcoin is secure
\
The bitcoin ledger uses the public blockchain. When mining computers crack an algorithmic puzzle, they create a block. The blocks on the ledger contain details about every blockchain transaction ever completed. Every network user can view this information.
Ownership of bitcoins is only valid once it’s been registered on the blockchain. This is only possible if the majority of network users approve it, so there’s no need for a central authority to oversee transactions. While verifying new blocks requires virtually no energy, creating a fraudulent block would cost a significant amount of processing power.
Even if a user decided to expend vast amounts of energy and successfully hacked a majority of all network nodes to approve a fraudulent block, they’d gain very little. Trust in bitcoin would be lost, leading to a drop in demand and value.
---
# Challenges for adoption
\
Because bitcoin is new, demand has varied. The volatile price has, at times, undermined the currency’s status as an effective store of value.
Bitcoin’s transaction limit is currently set at 500,000 per day. That could be increased, but there will always be a daily cap. The more transactions that take place, the more nodes there’ll need to be. This increases transaction fees and the amount of processing power expended.
Bitcoin could be traded off the blockchain, meaning currencies will be backed by bitcoin. That would create a new standard, but it would also mean that new centralized institutions would need to manage this system.
---

This 5-minute summary did not use copyrighted material from the book. It aims simply to give readers a quick understanding of the book (which is well worth reading).
‘*The Bitcoin Standard: The Decentralized Alternative to Central Banking’* was written by economist Saifedean Ammous in 2018.
Buy the book and many more titles at [bitcoinbook.shop](bitcoinbook.shop)
-

@ a95c6243:d345522c
2025-03-11 10:22:36
**«Wir brauchen eine digitale Brandmauer gegen den Faschismus»,** [schreibt](https://www.ccc.de/de/updates/2025/ccc-fordert-digitale-brandmauer) der Chaos Computer Club (CCC) auf seiner Website. Unter diesem Motto präsentierte er letzte Woche einen Forderungskatalog, mit dem sich 24 Organisationen an die kommende Bundesregierung wenden. Der Koalitionsvertrag müsse sich daran messen lassen, verlangen sie.
**In den drei Kategorien «Bekenntnis gegen Überwachung»,** «Schutz und Sicherheit für alle» sowie «Demokratie im digitalen Raum» stellen die [Unterzeichner](https://d-64.org/digitale-brandmauer/), zu denen auch Amnesty International und Das NETTZ gehören, unter anderem die folgenden «Mindestanforderungen»:
* Verbot biometrischer Massenüberwachung des öffentlichen Raums sowie der ungezielten biometrischen Auswertung des Internets.
* Anlasslose und massenhafte Vorratsdatenspeicherung wird abgelehnt.
* Automatisierte Datenanalysen der Informationsbestände der Strafverfolgungsbehörden sowie jede Form von Predictive Policing oder automatisiertes Profiling von Menschen werden abgelehnt.
* Einführung eines Rechts auf Verschlüsselung. Die Bundesregierung soll sich dafür einsetzen, die Chatkontrolle auf europäischer Ebene zu verhindern.
* Anonyme und pseudonyme Nutzung des Internets soll geschützt und ermöglicht werden.
* Bekämpfung «privaten Machtmissbrauchs von Big-Tech-Unternehmen» durch durchsetzungsstarke, unabhängige und grundsätzlich föderale Aufsichtsstrukturen.
* Einführung eines digitalen Gewaltschutzgesetzes, unter Berücksichtigung «gruppenbezogener digitaler Gewalt» und die Förderung von Beratungsangeboten.
* Ein umfassendes Förderprogramm für digitale öffentliche Räume, die dezentral organisiert und quelloffen programmiert sind, soll aufgelegt werden.
**Es sei ein Irrglaube, dass zunehmende Überwachung einen Zugewinn an Sicherheit darstelle,** ist eines der Argumente der Initiatoren. Sicherheit erfordere auch, dass Menschen anonym und vertraulich kommunizieren können und ihre Privatsphäre geschützt wird.
**Gesunde digitale Räume lebten auch von einem demokratischen Diskurs,** lesen wir in dem Papier. Es sei Aufgabe des Staates, Grundrechte zu schützen. Dazu gehöre auch, Menschenrechte und demokratische Werte, insbesondere Freiheit, Gleichheit und Solidarität zu fördern sowie den Missbrauch von Maßnahmen, Befugnissen und Infrastrukturen durch «die Feinde der Demokratie» zu verhindern.
**Man ist geneigt zu fragen, wo denn die Autoren «den Faschismus» sehen,** den es zu bekämpfen gelte. Die meisten der vorgetragenen Forderungen und Argumente finden sicher breite Unterstützung, denn sie beschreiben offenkundig gängige, kritikwürdige Praxis. Die Aushebelung der Privatsphäre, der Redefreiheit und anderer Grundrechte im Namen der Sicherheit wird bereits jetzt massiv durch die aktuellen «demokratischen Institutionen» und ihre «durchsetzungsstarken Aufsichtsstrukturen» betrieben.
**Ist «der Faschismus» also die EU und ihre Mitgliedsstaaten?** Nein, die «faschistische Gefahr», gegen die man eine digitale Brandmauer will, kommt nach Ansicht des CCC und seiner Partner aus den Vereinigten Staaten. Private Überwachung und Machtkonzentration sind dabei weltweit schon lange Realität, jetzt endlich müssen sie jedoch bekämpft werden. In dem Papier heißt es:
> «Die willkürliche und antidemokratische Machtausübung der Tech-Oligarchen um Präsident Trump erfordert einen Paradigmenwechsel in der deutschen Digitalpolitik. (...) Die aktuellen Geschehnisse in den USA zeigen auf, wie Datensammlungen und -analyse genutzt werden können, um einen Staat handstreichartig zu übernehmen, seine Strukturen nachhaltig zu beschädigen, Widerstand zu unterbinden und marginalisierte Gruppen zu verfolgen.»
**Wer auf der anderen Seite dieser Brandmauer stehen soll, ist also klar.** Es sind die gleichen «Feinde unserer Demokratie», die seit Jahren in diese Ecke gedrängt werden. Es sind die gleichen Andersdenkenden, Regierungskritiker und Friedensforderer, die unter dem großzügigen Dach des Bundesprogramms «Demokratie leben» einem «kontinuierlichen Echt- und Langzeitmonitoring» wegen der Etikettierung [«digitaler Hass»](https://bag-gegen-hass.net/) unterzogen werden.
**Dass die 24 Organisationen praktisch auch die Bekämpfung von Google,** Microsoft, Apple, Amazon und anderen fordern, entbehrt nicht der Komik. Diese fallen aber sicher unter das Stichwort «Machtmissbrauch von Big-Tech-Unternehmen». Gleichzeitig verlangen die Lobbyisten implizit zum Beispiel die Förderung des [Nostr](https://reason.com/video/2024/09/17/is-nostr-an-antidote-to-social-media-censorship/)-Netzwerks, denn hier finden wir dezentral organisierte und quelloffen programmierte digitale Räume par excellence, obendrein zensurresistent. Das wiederum dürfte in der Politik weniger gut ankommen.
*\[Titelbild:* *[Pixabay](https://pixabay.com/de/illustrations/uns-ihnen-stammes-wettbewerb-1767691/)]*
***
Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/digitale-brandmauer-gegen-den-faschismus-von-der-kunftigen-bundesregierung)*** erschienen.
-

@ 17538dc2:71ed77c4
2025-04-02 16:04:59
The MacOS security update summary is a reminder that laptops and desktops are incredibly compromised.
### macOS Sequoia 15.4
Released March 31, 2025
Accessibility
Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: A logging issue was addressed with improved data redaction.
CVE-2025-24202: Zhongcheng Li from IES Red Team of ByteDance
AccountPolicy
Available for: macOS Sequoia
Impact: A malicious app may be able to gain root privileges
Description: This issue was addressed by removing the vulnerable code.
CVE-2025-24234: an anonymous researcher
AirDrop
Available for: macOS Sequoia
Impact: An app may be able to read arbitrary file metadata
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24097: Ron Masas of BREAKPOINT.SH
App Store
Available for: macOS Sequoia
Impact: A malicious app may be able to access private information
Description: This issue was addressed by removing the vulnerable code.
CVE-2025-24276: an anonymous researcher
AppleMobileFileIntegrity
Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: The issue was addressed with improved checks.
CVE-2025-24272: Mickey Jin (@patch1t)
AppleMobileFileIntegrity
Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: A downgrade issue was addressed with additional code-signing restrictions.
CVE-2025-24239: Wojciech Regula of SecuRing (wojciechregula.blog)
AppleMobileFileIntegrity
Available for: macOS Sequoia
Impact: A malicious app may be able to read or write to protected files
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24233: Claudio Bozzato and Francesco Benvenuto of Cisco Talos.
AppleMobileFileIntegrity
Available for: macOS Sequoia
Impact: An app may be able to access user-sensitive data
Description: A privacy issue was addressed by removing the vulnerable code.
CVE-2025-30443: Bohdan Stasiuk (@bohdan_stasiuk)
Audio
Available for: macOS Sequoia
Impact: Processing a maliciously crafted font may result in the disclosure of process memory
Description: The issue was addressed with improved memory handling.
CVE-2025-24244: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative
Audio
Available for: macOS Sequoia
Impact: Processing a maliciously crafted file may lead to arbitrary code execution
Description: The issue was addressed with improved memory handling.
CVE-2025-24243: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative
Authentication Services
Available for: macOS Sequoia
Impact: Password autofill may fill in passwords after failing authentication
Description: This issue was addressed through improved state management.
CVE-2025-30430: Dominik Rath
Authentication Services
Available for: macOS Sequoia
Impact: A malicious website may be able to claim WebAuthn credentials from another website that shares a registrable suffix
Description: The issue was addressed with improved input validation.
CVE-2025-24180: Martin Kreichgauer of Google Chrome
Authentication Services
Available for: macOS Sequoia
Impact: A malicious app may be able to access a user's saved passwords
Description: This issue was addressed by adding a delay between verification code attempts.
CVE-2025-24245: Ian Mckay (@iann0036)
Automator
Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: A permissions issue was addressed by removing vulnerable code and adding additional checks.
CVE-2025-30460: an anonymous researcher
BiometricKit
Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination
Description: A buffer overflow was addressed with improved bounds checking.
CVE-2025-24237: Yutong Xiu
Calendar
Available for: macOS Sequoia
Impact: An app may be able to break out of its sandbox
Description: A path handling issue was addressed with improved validation.
CVE-2025-30429: Denis Tokarev (@illusionofcha0s)
Calendar
Available for: macOS Sequoia
Impact: An app may be able to break out of its sandbox
Description: This issue was addressed with improved checks.
CVE-2025-24212: Denis Tokarev (@illusionofcha0s)
CloudKit
Available for: macOS Sequoia
Impact: A malicious app may be able to access private information
Description: The issue was addressed with improved checks.
CVE-2025-24215: Kirin (@Pwnrin)
CoreAudio
Available for: macOS Sequoia
Impact: Parsing a file may lead to an unexpected app termination
Description: The issue was addressed with improved checks.
CVE-2025-24163: Google Threat Analysis Group
CoreAudio
Available for: macOS Sequoia
Impact: Playing a malicious audio file may lead to an unexpected app termination
Description: An out-of-bounds read issue was addressed with improved input validation.
CVE-2025-24230: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative
CoreMedia
Available for: macOS Sequoia
Impact: Processing a maliciously crafted video file may lead to unexpected app termination or corrupt process memory
Description: This issue was addressed with improved memory handling.
CVE-2025-24211: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative
CoreMedia
Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: An access issue was addressed with additional sandbox restrictions.
CVE-2025-24236: Csaba Fitzl (@theevilbit) and Nolan Astrein of Kandji
CoreMedia
Available for: macOS Sequoia
Impact: Processing a maliciously crafted video file may lead to unexpected app termination or corrupt process memory
Description: The issue was addressed with improved memory handling.
CVE-2025-24190: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative
CoreMedia Playback
Available for: macOS Sequoia
Impact: A malicious app may be able to access private information
Description: A path handling issue was addressed with improved validation.
CVE-2025-30454: pattern-f (@pattern_F_)
CoreServices
Description: This issue was addressed through improved state management.
CVE-2025-31191: Jonathan Bar Or (@yo_yo_yo_jbo) of Microsoft, and an anonymous researcher
Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
CoreText
Available for: macOS Sequoia
Impact: Processing a maliciously crafted font may result in the disclosure of process memory
Description: An out-of-bounds read issue was addressed with improved input validation.
CVE-2025-24182: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative
Crash Reporter
Available for: macOS Sequoia
Impact: An app may be able to gain root privileges
Description: A parsing issue in the handling of directory paths was addressed with improved path validation.
CVE-2025-24277: Csaba Fitzl (@theevilbit) of Kandji and Gergely Kalman (@gergely_kalman), and an anonymous researcher
curl
Available for: macOS Sequoia
Impact: An input validation issue was addressed
Description: This is a vulnerability in open source code and Apple Software is among the affected projects. The CVE-ID was assigned by a third party. Learn more about the issue and CVE-ID at cve.org.
CVE-2024-9681
Disk Images
Available for: macOS Sequoia
Impact: An app may be able to break out of its sandbox
Description: A file access issue was addressed with improved input validation.
CVE-2025-24255: an anonymous researcher
DiskArbitration
Available for: macOS Sequoia
Impact: An app may be able to gain root privileges
Description: A parsing issue in the handling of directory paths was addressed with improved path validation.
CVE-2025-30456: Gergely Kalman (@gergely_kalman)
DiskArbitration
Available for: macOS Sequoia
Impact: An app may be able to gain root privileges
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24267: an anonymous researcher
Dock
Available for: macOS Sequoia
Impact: A malicious app may be able to access private information
Description: The issue was addressed with improved checks.
CVE-2025-30455: Mickey Jin (@patch1t), and an anonymous researcher
Dock
Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: This issue was addressed by removing the vulnerable code.
CVE-2025-31187: Rodolphe BRUNETTI (@eisw0lf) of Lupus Nova
dyld
Available for: macOS Sequoia
Impact: Apps that appear to use App Sandbox may be able to launch without restrictions
Description: A library injection issue was addressed with additional restrictions.
CVE-2025-30462: Pietro Francesco Tirenna, Davide Silvetti, Abdel Adim Oisfi of Shielder (shielder.com)
FaceTime
Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: This issue was addressed with improved redaction of sensitive information.
CVE-2025-30451: Kirin (@Pwnrin) and luckyu (@uuulucky)
FeedbackLogger
Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: This issue was addressed with improved data protection.
CVE-2025-24281: Rodolphe BRUNETTI (@eisw0lf)
Focus
Available for: macOS Sequoia
Impact: An attacker with physical access to a locked device may be able to view sensitive user information
Description: The issue was addressed with improved checks.
CVE-2025-30439: Andr.Ess
Focus
Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: A logging issue was addressed with improved data redaction.
CVE-2025-24283: Kirin (@Pwnrin)
Foundation
Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: An access issue was addressed with additional sandbox restrictions on the system pasteboards.
CVE-2025-30461: an anonymous researcher
Foundation
Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: The issue was resolved by sanitizing logging
CVE-2025-30447: LFY@secsys from Fudan University
Foundation
Available for: macOS Sequoia
Impact: An app may be able to cause a denial-of-service
Description: An uncontrolled format string issue was addressed with improved input validation.
CVE-2025-24199: Manuel Fernandez (Stackhopper Security)
GPU Drivers
Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination or corrupt kernel memory
Description: An out-of-bounds write issue was addressed with improved bounds checking.
CVE-2025-30464: ABC Research s.r.o.
CVE-2025-24273: Wang Yu of Cyberserval
GPU Drivers
Available for: macOS Sequoia
Impact: An app may be able to disclose kernel memory
Description: The issue was addressed with improved bounds checks.
CVE-2025-24256: Anonymous working with Trend Micro Zero Day Initiative, Murray Mike
Handoff
Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: The issue was addressed with improved restriction of data container access.
CVE-2025-30463: mzzzz__
ImageIO
Available for: macOS Sequoia
Impact: Parsing an image may lead to disclosure of user information
Description: A logic error was addressed with improved error handling.
CVE-2025-24210: Anonymous working with Trend Micro Zero Day Initiative
Installer
Available for: macOS Sequoia
Impact: An app may be able to check the existence of an arbitrary path on the file system
Description: A permissions issue was addressed with additional sandbox restrictions.
CVE-2025-24249: YingQi Shi(@Mas0nShi) of DBAppSecurity's WeBin lab and Minghao Lin (@Y1nKoc)
Installer
Available for: macOS Sequoia
Impact: A sandboxed app may be able to access sensitive user data
Description: A logic issue was addressed with improved checks.
CVE-2025-24229: an anonymous researcher
IOGPUFamily
Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination or write kernel memory
Description: An out-of-bounds write issue was addressed with improved input validation.
CVE-2025-24257: Wang Yu of Cyberserval
IOMobileFrameBuffer
Available for: macOS Sequoia
Impact: An app may be able to corrupt coprocessor memory
Description: The issue was addressed with improved bounds checks.
CVE-2025-30437: Ye Zhang (@VAR10CK) of Baidu Security
Kerberos Helper
Available for: macOS Sequoia
Impact: A remote attacker may be able to cause unexpected app termination or heap corruption
Description: A memory initialization issue was addressed with improved memory handling.
CVE-2025-24235: Dave G.
Kernel
Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: The issue was addressed with improved checks.
CVE-2025-24204: Koh M. Nakagawa (@tsunek0h) of FFRI Security, Inc.
Kernel
Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: The issue was addressed with improved checks.
CVE-2025-24203: Ian Beer of Google Project Zero
Kernel
Available for: macOS Sequoia
Impact: An attacker with user privileges may be able to read kernel memory
Description: A type confusion issue was addressed with improved memory handling.
CVE-2025-24196: Joseph Ravichandran (@0xjprx) of MIT CSAIL
LaunchServices
Available for: macOS Sequoia
Impact: A malicious JAR file may bypass Gatekeeper checks
Description: This issue was addressed with improved handling of executable types.
CVE-2025-24148: Kenneth Chew
libarchive
Available for: macOS Sequoia
Impact: An input validation issue was addressed
Description: This is a vulnerability in open source code and Apple Software is among the affected projects. The CVE-ID was assigned by a third party. Learn more about the issue and CVE-ID at cve.org.
CVE-2024-48958
Libinfo
Available for: macOS Sequoia
Impact: A user may be able to elevate privileges
Description: An integer overflow was addressed with improved input validation.
CVE-2025-24195: Paweł Płatek (Trail of Bits)
libnetcore
Available for: macOS Sequoia
Impact: Processing maliciously crafted web content may result in the disclosure of process memory
Description: A logic issue was addressed with improved checks.
CVE-2025-24194: an anonymous researcher
libxml2
Available for: macOS Sequoia
Impact: Parsing a file may lead to an unexpected app termination
Description: This is a vulnerability in open source code and Apple Software is among the affected projects. The CVE-ID was assigned by a third party. Learn more about the issue and CVE-ID at cve.org.
CVE-2025-27113
CVE-2024-56171
libxpc
Available for: macOS Sequoia
Impact: An app may be able to break out of its sandbox
Description: This issue was addressed through improved state management.
CVE-2025-24178: an anonymous researcher
libxpc
Available for: macOS Sequoia
Impact: An app may be able to delete files for which it does not have permission
Description: This issue was addressed with improved handling of symlinks.
CVE-2025-31182: Alex Radocea and Dave G. of Supernetworks, 风沐云烟(@binary_fmyy) and Minghao Lin(@Y1nKoc)
libxpc
Available for: macOS Sequoia
Impact: An app may be able to gain elevated privileges
Description: A logic issue was addressed with improved checks.
CVE-2025-24238: an anonymous researcher
Mail
Available for: macOS Sequoia
Impact: "Block All Remote Content" may not apply for all mail previews
Description: A permissions issue was addressed with additional sandbox restrictions.
CVE-2025-24172: an anonymous researcher
manpages
Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: This issue was addressed with improved validation of symlinks.
CVE-2025-30450: Pwn2car
Maps
Available for: macOS Sequoia
Impact: An app may be able to read sensitive location information
Description: A path handling issue was addressed with improved logic.
CVE-2025-30470: LFY@secsys from Fudan University
NetworkExtension
Available for: macOS Sequoia
Impact: An app may be able to enumerate a user's installed apps
Description: This issue was addressed with additional entitlement checks.
CVE-2025-30426: Jimmy
Notes
Available for: macOS Sequoia
Impact: A sandboxed app may be able to access sensitive user data in system logs
Description: A privacy issue was addressed with improved private data redaction for log entries.
CVE-2025-24262: LFY@secsys from Fudan University
NSDocument
Available for: macOS Sequoia
Impact: A malicious app may be able to access arbitrary files
Description: This issue was addressed through improved state management.
CVE-2025-24232: an anonymous researcher
OpenSSH
Available for: macOS Sequoia
Impact: An app may be able to access user-sensitive data
Description: An injection issue was addressed with improved validation.
CVE-2025-24246: Mickey Jin (@patch1t)
PackageKit
Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: The issue was addressed with improved checks.
CVE-2025-24261: Mickey Jin (@patch1t)
PackageKit
Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: A logic issue was addressed with improved checks.
CVE-2025-24164: Mickey Jin (@patch1t)
PackageKit
Available for: macOS Sequoia
Impact: A malicious app with root privileges may be able to modify the contents of system files
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-30446: Pedro Tôrres (@t0rr3sp3dr0)
Parental Controls
Available for: macOS Sequoia
Impact: An app may be able to retrieve Safari bookmarks without an entitlement check
Description: This issue was addressed with additional entitlement checks.
CVE-2025-24259: Noah Gregory (wts.dev)
Photos Storage
Available for: macOS Sequoia
Impact: Deleting a conversation in Messages may expose user contact information in system logging
Description: A logging issue was addressed with improved data redaction.
CVE-2025-30424: an anonymous researcher
Power Services
Available for: macOS Sequoia
Impact: An app may be able to break out of its sandbox
Description: This issue was addressed with additional entitlement checks.
CVE-2025-24173: Mickey Jin (@patch1t)
Python
Available for: macOS Sequoia
Impact: A remote attacker may be able to bypass sender policy checks and deliver malicious content via email
Description: This is a vulnerability in open source code and Apple Software is among the affected projects. The CVE-ID was assigned by a third party. Learn more about the issue and CVE-ID at cve.org.
CVE-2023-27043
RPAC
Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: The issue was addressed with improved validation of environment variables.
CVE-2025-24191: Claudio Bozzato and Francesco Benvenuto of Cisco Talos
Safari
Available for: macOS Sequoia
Impact: Visiting a malicious website may lead to user interface spoofing
Description: The issue was addressed with improved UI.
CVE-2025-24113: @RenwaX23
Safari
Available for: macOS Sequoia
Impact: Visiting a malicious website may lead to address bar spoofing
Description: The issue was addressed with improved checks.
CVE-2025-30467: @RenwaX23
Safari
Available for: macOS Sequoia
Impact: A website may be able to access sensor information without user consent
Description: The issue was addressed with improved checks.
CVE-2025-31192: Jaydev Ahire
Safari
Available for: macOS Sequoia
Impact: A download's origin may be incorrectly associated
Description: This issue was addressed through improved state management.
CVE-2025-24167: Syarif Muhammad Sajjad
Sandbox
Available for: macOS Sequoia
Impact: An app may be able to access removable volumes without user consent
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24093: Yiğit Can YILMAZ (@yilmazcanyigit)
Sandbox
Available for: macOS Sequoia
Impact: An input validation issue was addressed
Description: The issue was addressed with improved checks.
CVE-2025-30452: an anonymous researcher
Sandbox
Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24181: Arsenii Kostromin (0x3c3e)
SceneKit
Available for: macOS Sequoia
Impact: An app may be able to read files outside of its sandbox
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-30458: Mickey Jin (@patch1t)
Security
Available for: macOS Sequoia
Impact: A remote user may be able to cause a denial-of-service
Description: A validation issue was addressed with improved logic.
CVE-2025-30471: Bing Shi, Wenchao Li, Xiaolong Bai of Alibaba Group, Luyi Xing of Indiana University Bloomington
Security
Available for: macOS Sequoia
Impact: A malicious app acting as a HTTPS proxy could get access to sensitive user data
Description: This issue was addressed with improved access restrictions.
CVE-2025-24250: Wojciech Regula of SecuRing (wojciechregula.blog)
Share Sheet
Available for: macOS Sequoia
Impact: A malicious app may be able to dismiss the system notification on the Lock Screen that a recording was started
Description: This issue was addressed with improved access restrictions.
CVE-2025-30438: Halle Winkler, Politepix theoffcuts.org
Shortcuts
Available for: macOS Sequoia
Impact: A shortcut may be able to access files that are normally inaccessible to the Shortcuts app
Description: A permissions issue was addressed with improved validation.
CVE-2025-30465: an anonymous researcher
Shortcuts
Available for: macOS Sequoia
Impact: An app may be able to access user-sensitive data
Description: An access issue was addressed with additional sandbox restrictions.
CVE-2025-24280: Kirin (@Pwnrin)
Shortcuts
Available for: macOS Sequoia
Impact: A Shortcut may run with admin privileges without authentication
Description: An authentication issue was addressed with improved state management.
CVE-2025-31194: Dolf Hoegaerts
Shortcuts
Available for: macOS Sequoia
Impact: A shortcut may be able to access files that are normally inaccessible to the Shortcuts app
Description: This issue was addressed with improved access restrictions.
CVE-2025-30433: Andrew James Gonzalez
Siri
Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: The issue was addressed with improved restriction of data container access.
CVE-2025-31183: Kirin (@Pwnrin), Bohdan Stasiuk (@bohdan_stasiuk)
Siri
Available for: macOS Sequoia
Impact: A sandboxed app may be able to access sensitive user data in system logs
Description: This issue was addressed with improved redaction of sensitive information.
CVE-2025-30435: K宝 (@Pwnrin) and luckyu (@uuulucky)
Siri
Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: This issue was addressed with improved redaction of sensitive information.
CVE-2025-24217: Kirin (@Pwnrin)
Siri
Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: A privacy issue was addressed by not logging contents of text fields.
CVE-2025-24214: Kirin (@Pwnrin)
Siri
Available for: macOS Sequoia
Impact: An app may be able to enumerate devices that have signed into the user's Apple Account
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24248: Minghao Lin (@Y1nKoc) and Tong Liu@Lyutoon_ and 风(binary_fmyy) and F00L
Siri
Available for: macOS Sequoia
Impact: An app may be able to access user-sensitive data
Description: An authorization issue was addressed with improved state management.
CVE-2025-24205: YingQi Shi(@Mas0nShi) of DBAppSecurity's WeBin lab and Minghao Lin (@Y1nKoc)
Siri
Available for: macOS Sequoia
Impact: An attacker with physical access may be able to use Siri to access sensitive user data
Description: This issue was addressed by restricting options offered on a locked device.
CVE-2025-24198: Richard Hyunho Im (@richeeta) with routezero.security
SMB
Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination
Description: The issue was addressed with improved memory handling.
CVE-2025-24269: Alex Radocea of Supernetworks
SMB
Available for: macOS Sequoia
Impact: Mounting a maliciously crafted SMB network share may lead to system termination
Description: A race condition was addressed with improved locking.
CVE-2025-30444: Dave G.
SMB
Available for: macOS Sequoia
Impact: An app may be able to execute arbitrary code with kernel privileges
Description: A buffer overflow issue was addressed with improved memory handling.
CVE-2025-24228: Joseph Ravichandran (@0xjprx) of MIT CSAIL
smbx
Available for: macOS Sequoia
Impact: An attacker in a privileged position may be able to perform a denial-of-service
Description: The issue was addressed with improved memory handling.
CVE-2025-24260: zbleet of QI-ANXIN TianGong Team
Software Update
Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: A library injection issue was addressed with additional restrictions.
CVE-2025-24282: Claudio Bozzato and Francesco Benvenuto of Cisco Talos
Software Update
Available for: macOS Sequoia
Impact: A user may be able to elevate privileges
Description: This issue was addressed with improved validation of symlinks.
CVE-2025-24254: Arsenii Kostromin (0x3c3e)
Software Update
Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: The issue was addressed with improved checks.
CVE-2025-24231: Claudio Bozzato and Francesco Benvenuto of Cisco Talos
StickerKit
Available for: macOS Sequoia
Impact: An app may be able to observe unprotected user data
Description: A privacy issue was addressed by moving sensitive data to a protected location.
CVE-2025-24263: Cristian Dinca of "Tudor Vianu" National High School of Computer Science, Romania
Storage Management
Available for: macOS Sequoia
Impact: An app may be able to enable iCloud storage features without user consent
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24207: YingQi Shi (@Mas0nShi) of DBAppSecurity's WeBin lab, 风沐云烟 (binary_fmyy) and Minghao Lin (@Y1nKoc)
StorageKit
Available for: macOS Sequoia
Impact: An app may be able to gain root privileges
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-30449: Arsenii Kostromin (0x3c3e), and an anonymous researcher
StorageKit
Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: This issue was addressed with improved handling of symlinks.
CVE-2025-24253: Mickey Jin (@patch1t), Csaba Fitzl (@theevilbit) of Kandji
StorageKit
Available for: macOS Sequoia
Impact: An app may be able to access user-sensitive data
Description: A race condition was addressed with additional validation.
CVE-2025-24240: Mickey Jin (@patch1t)
StorageKit
Available for: macOS Sequoia
Impact: An app may be able to bypass Privacy preferences
Description: A race condition was addressed with additional validation.
CVE-2025-31188: Mickey Jin (@patch1t)
Summarization Services
Available for: macOS Sequoia
Impact: An app may be able to access information about a user's contacts
Description: A privacy issue was addressed with improved private data redaction for log entries.
CVE-2025-24218: Kirin and FlowerCode, Bohdan Stasiuk (@bohdan_stasiuk)
System Settings
Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: This issue was addressed with improved validation of symlinks.
CVE-2025-24278: Zhongquan Li (@Guluisacat)
System Settings
Available for: macOS Sequoia
Impact: An app with root privileges may be able to access private information
Description: This issue was addressed with improved handling of symlinks.
CVE-2025-24242: Koh M. Nakagawa (@tsunek0h) of FFRI Security, Inc.
SystemMigration
Available for: macOS Sequoia
Impact: A malicious app may be able to create symlinks to protected regions of the disk
Description: This issue was addressed with improved validation of symlinks.
CVE-2025-30457: Mickey Jin (@patch1t)
Voice Control
Available for: macOS Sequoia
Impact: An app may be able to access contacts
Description: This issue was addressed with improved file handling.
CVE-2025-24279: Mickey Jin (@patch1t)
Web Extensions
Available for: macOS Sequoia
Impact: An app may gain unauthorized access to Local Network
Description: This issue was addressed with improved permissions checking.
CVE-2025-31184: Alexander Heinrich (@Sn0wfreeze), SEEMOO, TU Darmstadt & Mathy Vanhoef (@vanhoefm) and Jeroen Robben (@RobbenJeroen), DistriNet, KU Leuven
Web Extensions
Available for: macOS Sequoia
Impact: Visiting a website may leak sensitive data
Description: A script imports issue was addressed with improved isolation.
CVE-2025-24192: Vsevolod Kokorin (Slonser) of Solidlab
WebKit
Available for: macOS Sequoia
Impact: Processing maliciously crafted web content may lead to an unexpected Safari crash
Description: The issue was addressed with improved memory handling.
WebKit Bugzilla: 285892
CVE-2025-24264: Gary Kwong, and an anonymous researcher
WebKit Bugzilla: 284055
CVE-2025-24216: Paul Bakker of ParagonERP
WebKit
Available for: macOS Sequoia
Impact: A type confusion issue could lead to memory corruption
Description: This issue was addressed with improved handling of floats.
WebKit Bugzilla: 286694
CVE-2025-24213: Google V8 Security Team
WebKit
Available for: macOS Sequoia
Impact: Processing maliciously crafted web content may lead to an unexpected process crash
Description: A buffer overflow issue was addressed with improved memory handling.
WebKit Bugzilla: 286462
CVE-2025-24209: Francisco Alonso (@revskills), and an anonymous researcher
WebKit
Available for: macOS Sequoia
Impact: Processing maliciously crafted web content may lead to an unexpected Safari crash
Description: A use-after-free issue was addressed with improved memory management.
WebKit Bugzilla: 285643
CVE-2025-30427: rheza (@ginggilBesel)
WebKit
Available for: macOS Sequoia
Impact: A malicious website may be able to track users in Safari private browsing mode
Description: This issue was addressed through improved state management.
WebKit Bugzilla: 286580
CVE-2025-30425: an anonymous researcher
WindowServer
Available for: macOS Sequoia
Impact: An attacker may be able to cause unexpected app termination
Description: A type confusion issue was addressed with improved checks.
CVE-2025-24247: PixiePoint Security
WindowServer
Available for: macOS Sequoia
Impact: An app may be able to trick a user into copying sensitive data to the pasteboard
Description: A configuration issue was addressed with additional restrictions.
CVE-2025-24241: Andreas Hegenberg (folivora.AI GmbH)
Xsan
Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination
Description: A buffer overflow was addressed with improved bounds checking.
CVE-2025-24266: an anonymous researcher
Xsan
Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination
Description: An out-of-bounds read was addressed with improved bounds checking.
CVE-2025-24265: an anonymous researcher
Xsan
Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination or corrupt kernel memory
Description: A buffer overflow issue was addressed with improved memory handling.
CVE-2025-24157: an anonymous researcher
-

@ 06639a38:655f8f71
2025-04-02 13:47:57
You can follow the work in progress here in this pull request [https://github.com/nostrver-se/nostr-php/pull/68](https://github.com/nostrver-se/nostr-php/pull/68) on Github.
Before my 3-month break (Dec/Jan/Feb) working on Nostr-PHP I started with the NIP-19 integration in October '24. Encoding and decoding the simple prefixes (`npub`, `nsec` and `note`) was already done in the first commits.
Learn more about NIP-19 here: [https://nips.nostr.com/19](https://nips.nostr.com/19)
### **TLV's**
Things were getting more complicated with the other prefixes / identifiers defined in NIP-19:
* `nevent`
* `naddr`
* `nprofile`
This is because these identifiers contain (optional) metadata called Type-Lenght-Value aka TLV's.
_When sharing a profile or an event, an app may decide to include relay information and other metadata such that other apps can locate and display these entities more easily._
_For these events, the contents are a binary-encoded list of_ `_TLV_` _(type-length-value), with_ `_T_` _and_ `_L_` _being 1 byte each (_`_uint8_`_, i.e. a number in the range of 0-255), and_ `_V_` _being a sequence of bytes of the size indicated by_ `_L_`_._
These possible standardized `TLV` types are:
* `0`_:_ `special`
* _depends on the bech32 prefix:_
* _for_ `nprofile` _it will be the 32 bytes of the profile public key_
* _for_ `nevent` _it will be the 32 bytes of the event id_
* _for_ `naddr`_, it is the identifier (the_ `"d"` _tag) of the event being referenced. For normal replaceable events use an empty string._
* `1`_:_ `relay`
* _for_ `nprofile`_,_ `nevent` _and_ `naddr`_, optionally, a relay in which the entity (profile or event) is more likely to be found, encoded as ascii_
* _this may be included multiple times_
* `2`_:_ `author`
* _for_ `naddr`_, the 32 bytes of the pubkey of the event_
* _for_ `nevent`_, optionally, the 32 bytes of the pubkey of the event_
* `3`_:_ `kind`
* _for_ `naddr`_, the 32-bit unsigned integer of the kind, big-endian_
* _for_ `nevent`_, optionally, the 32-bit unsigned integer of the kind, big-endian_
These identifiers are formatted as bech32 strings, but are much longer than the package `bitwasp/bech32` (used in the library) for can handle for encoding and decoding. The bech32 strings handled by `bitwasp/bech32` are limited to a maximum length of 90 characters.
Thanks to the effort of others (nostr:npub1636uujeewag8zv8593lcvdrwlymgqre6uax4anuq3y5qehqey05sl8qpl4 and nostr:npub1efz8l77esdtpw6l359sjvakm7azvyv6mkuxphjdk3vfzkgxkatrqlpf9s4) during my break, some contributions are made (modifiying the bech32 package supporting much longer strings, up to a max of 5000 characters). At this moment, I'm integrating this (mostly copy-pasting the stuff and refactoring the code):
* [https://github.com/nostrver-se/nostr-php/issues/74](https://github.com/nostrver-se/nostr-php/issues/74)
* [https://github.com/nostriphant/nip-19](https://github.com/nostriphant/nip-19)
### **So what's next?**
* NIP-19 code housekeeping + refactoring
* Prepare a new release with NIP-19 integration
* Create documentation page how to use NIP-19 on [https://nostr-php.dev](https://nostr-php.dev)
-

@ 732c6a62:42003da2
2025-03-09 22:36:26
Não são recentes as táticas da esquerda de tentar reprimir intelectualmente seus opositores na base do deboche, da ironia, do desprezo e do boicote à credibilidade. Até Marx usava ironia para chamar os críticos de "burgueses iludidos". A diferença é que, no século XXI, trocaram o manifesto comunista por threads no Twitter e a dialética por memes de mau gosto.
### **A Falácia da Superioridade Moral**
O debate sobre o "pobre de direita" no Brasil é contaminado por uma premissa tácita da esquerda: **a ideia de que classes baixas só podem ter consciência política se aderirem a pautas progressistas**. Quem ousa divergir é tratado como "traidor de classe", "manipulado", "ignorante", ou até vítimas de deboches como alguma pessoa com um qi em temperatura ambiente repetir diversas vezes "não é possível que ainda exista pobre de direita", "nunca vou entender pobre de direita", ou "pobre de direita é muito burro, rico eu até entendo", como se o autor dessas frases fosse o paladino dos mais oprimidos e pobres. Esse discurso, porém, não resiste a uma análise empírica, histórica ou sociológica.
---
### **Contexto Histórico: A Esquerda e o Mito do "Voto Consciente"**
A noção de que o pobre deve votar na esquerda por "interesse de classe" é herança do **marxismo ortodoxo**, que via a política como mero reflexo da posição econômica. No entanto, a realidade é mais complexa:
- **Dados do Latinobarómetro (2022):** 41% dos brasileiros de baixa renda (até 2 salários mínimos) apoiam redução de impostos e maior liberdade econômica — pautas tradicionalmente associadas à direita.
- **Pesquisa IPEC (2023):** 58% dos pobres brasileiros priorizam "segurança pública" como principal demanda, acima de "distribuição de renda".
Esses números não são acidentais. Refletem uma **mudança estrutural**: o pobre moderno não é mais o "operário industrial" do século XX, mas um empreendedor informal, motorista de app, ou microempresário — figuras que valorizam autonomia e rejeitam paternalismo estatal. Eles dizem não entender o pobre de direita e que nunca vai entendê-los, mas o fato é que não entendem porque **nunca conversaram com um sem fazer cara de psicólogo de posto de saúde**. Sua "preocupação" é só uma máscara para esconder o desprezo por quem ousa pensar diferente do seu manual de "oprimido ideal".
## **Se ainda não entenderam:**
**Direita ≠ rico:** Tem gente que trabalha 12h/dia e vota em liberal porque quer **ser dono do próprio negócio**, não pra pagar mais taxação pra você postar meme no Twitter.
**Acham que são o Sherlock Holmes da pobreza:** o palpite de que "o pobre é manipulado" é tão raso quanto sua compreensão de economia básica.
---
### **A Psicologia por Trás do Voto Conservador nas Periferias**
A esquerda atribui o voto pobre em direita a "falta de educação" ou "manipulação midiática". Essa tese é não apenas elitista, mas **cientificamente falsa**:
**Análise Psicológica Básica (para você que se acha o Paulo Freire):**
- **Síndrome do Branco Salvador:** Acha que o pobre é uma criatura tão frágil que precisa de você pra pensar. Spoiler: ele não precisa.
- **Viés da Superioridade Moral:** "Se você é pobre e não concorda comigo, você é burro". Parabéns, recriou a escravidão intelectual.
- **Efeito Dunning-Kruger:** Não sabe o que é CLT, mas dá palpite sobre reforma trabalhista.
- **Estudo da Universidade de São Paulo (USP, 2021):** Entre moradores de favelas, 63% associam políticas de segurança dura (como "bandido bom é bandido morto") à proteção de seus negócios e famílias. Para eles, a esquerda é "branda demais" com o crime.
- **Pesquisa FGV (2020):** 71% dos trabalhadores informais rejeitam aumentos de impostos, mesmo que para financiar programas sociais. Motivo: já sofrem com a burocracia estatal para legalizar seus negócios.
Esses dados revelam uma **racionalidade prática**: o pobre avalia políticas pelo impacto imediato em sua vida, não por abstrações ideológicas. Enquanto a esquerda fala em "reforma estrutural" e tenta importar discursos estrangeiros para debate, por exemplo, o tema irrelevante do pronome neutro, ele quer resolver problemas como:
- **Violência** (que afeta seu comércio);
- **Impostos** (que consomem até 40% do lucro de um camelô);
- **Burocracia** (que impede a legalização de sua barraca de pastel).
---
### **Religião, Valores e a Hipocrisia do "Ateísmo de Redes Sociais"**
A esquerda subestima o papel da religião na formação política das classes baixas. No Brasil, **76% dos evangélicos são pobres** (Datafolha, 2023), e suas igrejas promovem valores como:
- **Família tradicional** (contra pautas progressistas como ideologia de gênero em escolas);
- **Auto-responsabilidade** (ênfase em "trabalho duro" em vez de assistencialismo).
**Exemplo Concreto:**
Nas favelas de São Paulo, pastores evangélicos são frequentemente eleitos a cargos locais com plataformas anticrime e pró-mercado. Para seus eleitores, a esquerda urbana (que defende descriminalização de drogas e críticas à polícia) representa uma **ameaça ao seu estilo de vida**.
---
### **A Esquerda e seu Desprezo pela Autonomia do Pobre**
O cerne do debate é a **incapacidade da esquerda de aceitar que o pobre possa ser autônomo**. Algumas evidências:
#### **O Caso dos Empreendedores Informais**
- **Segundo o IBGE (2023), 40% dos trabalhadores brasileiros estão na informalidade.** Muitos veem o Estado como obstáculo, não aliado. Políticas de direita (como simplificação tributária) são mais atraentes para eles que o Bolsa Família.
#### **A Ascensão do Conservadorismo Periférico**
- Pessoas assim tem um pensamento simples. Sua mensagem: *"Queremos empreender, não depender de político."*
#### **A Rejeição ao "Vitimismo"**
- **Pesquisa Atlas Intel (2022):** 68% dos pobres brasileiros rejeitam o termo "vítima da sociedade". Preferem ser vistos como "lutadores".
---
### **A projeção freudiana "o pobre é burro porque eu sou inteligente"**
O deboche esquerdista esconde um complexo de inferioridade disfarçado de superioridade moral. É a **Síndrome do Salvador** em sua forma mais patética:
- **Passo 1:** Assume-se que o pobre é um ser desprovido de agência.
- **Passo 2:** Qualquer desvio da narrativa é atribuído a "manipulação da elite".
- **Passo 3:** Quem critica o processo é chamado de "fascista".
**Exemplo Prático:**
Quando uma empregada doméstica diz que prefere o livre mercado a programas sociais, a esquerda não pergunta *"por quê?"* — ela grita *"lavagem cerebral!"*. A ironia? Essa mesma esquerda defende a **autonomia feminina**, exceto quando a mulher é pobre e pensa diferente.
### **Dados Globais: O Fenômeno Não é Brasileiro**
A ideia de que "pobre de direita" é uma anomalia é desmentida por evidências internacionais:
- **Estados Unidos:** 38% dos eleitores com renda abaixo de US$ 30k/ano votaram em Trump em 2020 (Pew Research).
Motivos principais: conservadorismo social e rejeição a impostos. A esquerda: "vítimas da falsa consciência".
Mais um detalhe: na última eleição de 2024, grande parte da classe "artística" milionária dos Estados Unidos, figuras conhecidas, promoveram em peso a Kamala Harris, do Partido Democrata. Percebe como a esquerda atual é a personificaçãoda burguesia e de só pensar na própria barriga?
- **Argentina:** Javier Milei, libertário radical, quando candidato, tinha forte apoio nas *villas miseria* (favelas). Seu lema — *"O estado é um parasita"* — ressoa entre quem sofria com inflação de 211% ao ano.
- **Índia:** O partido BJP (direita nacionalista) domina entre os pobres rurais, que associam a esquerda a elites urbanas desconectadas de suas necessidades.
### **A história que a esquerda tenta apagar: pobres de direita existem desde sempre**
A esquerda age como se o "pobre de direita" fosse uma invenção recente do MBL, mas a realidade é que **classes baixas conservadoras são regra, não exceção**, na história mundial:
- **Revolução Francesa (1789):** Camponeses apoiaram a monarquia contra os jacobinos urbanos que queriam "libertá-los".
- **Brasil Imperial:** Escravos libertos que viraram pequenos proprietários rurais rejeitavam o abolicionismo radical — queriam integração, não utopia.
**Tradução:**
Quando o pobre não segue o script, a esquerda inventa teorias conspiratórias.
---
### **A Hipocrisia da Esquerda Urbana e Universitária**
Enquanto acusa o pobre de direita de "alienado", a esquerda brasileira é dominada por uma **elite desconectada da realidade periférica**:
- **Perfil Socioeconômico:** 82% dos filiados ao PSOL têm ensino superior completo (TSE, 2023). Apenas 6% moram em bairros periféricos.
- **Prioridades Descoladas:** Enquanto o pobre debate segurança e custo de vida, a esquerda pauta discussões como "linguagem não-binária em editais públicos" — tema irrelevante para quem luta contra o desemprego. Os grandes teóricos comunistas se reviram no túmulo quando veem o que a esquerda se tornou: não debatem os reais problemas do Brasil, e sim sobre suas próprias emoções.
*"A esquerda brasileira trocou o operário pelo influencer progressista. O pobre virou um personagem de campanha, não um interlocutor real."*
### **A diversidade de pensamento que a esquerda não suporta**
A esquerda prega diversidade — desde que você seja diverso dentro de um **checklist pré-aprovado**. Pobre LGBTQ+? Herói. Pobre evangélico? Fascista. Pobre que abre MEI? "Peão do capitalismo". A realidade é que favelas e periferias são **microcosmos de pluralidade ideológica**, algo que assusta quem quer reduzir seres humanos a estereótipos.
---
### **Respostas aos Argumentos Esquerdistas (e Por que Falham)**
#### **"O pobre de direita é manipulado pela mídia!"**
- **Contradição:** Se a mídia tradicional é dominada por elites (como alegam), por que grandes veículos são abertamente progressistas? A Record (evangélica) é exceção, não regra.
**Contradição Central:**
Como explicar que, segundo o **Banco Mundial (2023)**, países com maior liberdade econômica (ex.: Chile, Polônia) reduziram a pobreza extrema em 60% nas últimas décadas, enquanto modelos estatizantes (ex.: Venezuela, Argentina com o governo peronista) afundaram na miséria? Simples: a esquerda prefere culpar o "neoliberalismo" a admitir que **o pobre com o mínimo de consciência quer emprego, não esmola**.
**Dado que Machuca:**
- 71% das mulheres da periferia rejeitam o feminismo radical, associando-o a "prioridades distantes da realidade" (**Instituto Locomotiva, 2023**).
#### **"Ele vota contra os próprios interesses!"**
- **Falácia:** Pressupõe que a esquerda define o que é o "interesse do pobre". Para um pai de família na Cidade de Deus, ter a boca de fogo fechada pode ser mais urgente que um aumento de 10% no Bolsa Família.
O pobre de direita não é uma anomalia. É o **produto natural de um mundo complexo** onde seres humanos têm aspirações, medos e valores diversos. Enquanto a esquerda insiste em tratá-lo como um projeto fracassado, ele está ocupado:
- **Trabalhando** para não depender do governo.
- **Escolhendo** religiões que dão sentido à sua vida.
- **Rejeitando** pautas identitárias que não resolvem o custo do gás de cozinha.
#### **"É falta de educação política!"**
- **Ironia:** Nos países nórdicos (modelo da esquerda), as classes baixas são as mais conservadoras. Educação não correlaciona com progressismo.
---
### **Por que o Debuste Precisa Acabar**
A insistência em descredibilizar o pobre de direita revela um **projeto de poder fracassado**. A esquerda, ao substituir diálogo por deboche, perdeu a capacidade de representar quem mais precisaria dela. Enquanto isso, a direita — nem sempre por virtude, mas por pragmatismo — capturou o descontentamento de milhões com o status quo.
O pobre de direita existe porque ele **não precisa da permissão do rico de esquerda para pensar**. A incapacidade de entender isso só prova que **a esquerda é a nova aristocracia**.
**Último Dado:** Nas eleições de 2022, Tarcísio de Freitas (direita) venceu em 72% das favelas de São Paulo. O motivo? Seu discurso anti-burocracia e pró-microempreendedor.
A mensagem é clara: o pobre não é um projeto ideológico. É um agente político autônomo — e quem não entender isso continuará perdendo eleições.
A esquerda elitista não odeia o pobre de direita por ele ser "irracional". Odeia porque ele **desafia o monopólio moral** que ela construiu sobre a miséria alheia. Enquanto isso, o pobre segue sua vida, ignorando os berros de quem acha que sabem mais da sua vida que ele mesmo.
**Pergunta Retórica (Para Incomodar):**
Se a esquerda é tão sábia, por que não usa essa sabedoria para entender que **pobre também cansa de ser tratado como cachorro que late no ritmo errado**?
---
# **Fontes Citadas:**
1. Latinobarómetro (2022)
2. IPEC (2023)
3. USP (2021): *"Segurança Pública e Percepções nas Favelas Cariocas"*
4. FGV (2020): *"Informalidade e Tributação no Brasil"*
5. Datafolha (2023): *"Perfil Religioso do Eleitorado Brasileiro"*
6. Atlas Intel (2022): *"Autopercepção das Classes Baixas"*
7. Pew Research (2020): *"Voting Patterns by Income in the U.S."*
8. TSE (2023): *"Perfil Socioeconômico dos Filiados Partidários"*
**Leitura Recomendada para Esquerdistas:**
- *"Fome de Poder: Por que o Pobre Brasileiro Abandonou a Esquerda"* (Fernando Schüller, 2023)
- *"A Revolução dos Conservadores: Religião e Política nas Periferias"* (Juliano Spyer, 2021)
- *"Direita e Esquerda: Razões e Paixões"* (Demétrio Magnoli, 2019)
-

@ 7bdef7be:784a5805
2025-04-02 12:09:29
We value sovereignty, privacy and security when accessing online content, using several tools to achieve this, like open protocols, open OSes, open software products, Tor and VPNs.
## The problem
Talking about our social presence, we can manually build up our follower list (social graph), pick a Nostr client that is respectful of our preferences on what to show and how, but with the standard following mechanism, our main feed is public, so everyone can actually snoop what we are interested in, and what is supposable that we read daily.
## The solution
Nostr has a simple solution for this necessity: encrypted lists.
Lists are what they appear, a collection of people or interests (but they can also group much other stuff, see [NIP-51](https://github.com/nostr-protocol/nips/blob/master/51.md)). So we can create lists with contacts that we don't have in our main social graph; these lists can be used primarily to create dedicated feeds, but they could have other uses, for example, related to monitoring. The interesting thing about lists is that they can also be encrypted, so unlike the basic following list, which is always public, we can hide the lists' content from others.
The implications are obvious: we can not only have a more organized way to browse content, but it is also really private one.
One might wonder what use can really be made of private lists; here are some examples:
* Browse “can't miss” content from users I consider a priority;
* Supervise competitors or adversarial parts;
* Monitor sensible topics (tags);
* Follow someone without being publicly associated with them, as this may be undesirable;
The benefits in terms of privacy as usual are not only related to the casual, or programmatic, observer, but are also evident when we think of how many bots scan our actions to profile us.
## The current state
Unfortunately, lists are not widely supported by Nostr clients, and encrypted support is a rarity.
Often the excuse to not implement them is that they are harder to develop, since they require managing the encryption stuff ([NIP-44](https://github.com/nostr-protocol/nips/blob/master/44.md)). Nevertheless, developers have an easier option to start offering private lists: give the user the possibility to simply mark them as local-only, and never push them to the relays. Even if the user misses the sync feature, this is sufficient to create a private environment.
To date, as far as I know, the best client with list management is [Gossip](nostr:npub189j8y280mhezlp98ecmdzydn0r8970g4hpqpx3u9tcztynywfczqqr3tg8), which permits to manage both encrypted and local-only lists.
Beg your Nostr client to implement private lists!
-

@ ec9bd746:df11a9d0
2025-03-07 20:13:38
I was diving into PoW (Proof-of-Work) once again after nostr:nprofile1qy88wumn8ghj7mn0wvhxcmmv9uq3wamnwvaz7tmjv4kxz7fwdehhxarj9e3xzmny9uqzqj8a67jths8euy33v5yu6me6ngua5v3y3qq3dswuqh2pejmtls6datagmu rekindled my interest with his PoW Draw project. It was a fun little trifle, but it shifted my focus just the right way at the right time.
Because then, on Friday, came the [Oval Office Travesty](nostr:nevent1qvzqqqqqqypzpmym6ar92346qc04ml08z6j0yrelylkv9r9ysurhte0g2003r2wsqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qpqqqqqqqrg6vz7m9z8ufagn4z3ks0meqw4nyh4gfxvksfhne99egzsd3g3w9). Once I got over the initial shock, I decided I couldn't just curse and lament; I needed to do something bigger, something symbolic, something expressive. So that's exactly what I did—breaking nostr:nprofile1qy88wumn8ghj7mn0wvhxcmmv9uq32amnwvaz7tmjv4kxz7fwv3sk6atn9e5k7tcqyqewrqnkx4zsaweutf739s0cu7et29zrntqs5elw70vlm8zudr3y2t9v7jg's record which he held for almost 2 and half years.
Here is a note with PoW 45, the highest PoW known to Nostr (as of now).
nostr:nevent1qvzqqqqqqypzpmym6ar92346qc04ml08z6j0yrelylkv9r9ysurhte0g2003r2wsqy88wumn8ghj7mn0wvhxcmmv9uqsuamnwvaz7tmwdaejumr0dshsqgqqqqqqqqqy8t8awr5c8z4yfp4cr8v7spp8psncv8twlh083flcr582fyu9
## How Did I Pull It Off?
In theory, quite simple: Create note, run PoW mining script & wait.
Thanks to PoW Draw, I already had mining software at hand: nostr:nprofile1qy88wumn8ghj7mn0wvhxcmmv9uq32amnwvaz7tmjv4kxz7fwv3sk6atn9e5k7tcqyqvqc5tlvn6etv09f0fvuauves49dvgnukjtzsndfv9y8yyrqyxmz7dty6z's [*notemine_hw*](https://github.com/plebemineira/notemine_hw), but when you know that there is a 1 in 2^45 chance that the next hash will be the correct one you want to increase the odds a bit. So on Monday evening, I started my Note Mining operation on an old 40 thread machine called Workhorse.
### Issues Along the Way
I was immediately surprised that Workhorse (2× Intel Xeon Silver 4114) produced only about 3Mh/s. A laptop (Intel Core i7-1185G7) with Windows and all the bloat did 5Mh/s. That was strange.
Another hurdle was that *notemine_hw* does not refresh the `created_at` field. With just a few Mh/s of power I was potentially looking at weeks of computation, by then the note would be quite stale. So I created systemd service leveraging the `RuntimeMaxSec` option to periodically restart every 3600 seconds assuring that the Note would be max 1 hour old at the time of publishing.
Luckily PoW is that kind of problem where every hash attempt is an independent event, so the chance of success is the same whether you do it in small increments or one uninterrupted stretch. So by restarting the mining process I was only losing a few mere seconds every hour due to the overhead.
Once the note staleness issue was resolved, I looked at the 40 workers on Workhorse vs. 7 workers on the laptop and start messing around with running one instance with 40 workers and running 40 instances with 1 worker and found out, that the workers are not bound to a CPU thread and are jumping between the CPUs like rabbits high on Colombian carrots.
The solution? Running multiple instances with one worker each as a service locked to its own CPU core using systemd's `CPUAffinity` option.
```
$aida@workhorse:systemd/system $ sudo cat notemine@.service
[Unit]
Description=Notemine HW Publish (restarts hourly)
[Service]
Type=simple
CPUAffinity=%i
# The command to run:
ExecStart=/home/aida/.cargo/bin/notemine_hw publish --n-workers 1 --difficulty 45 --event-json /home/aida/note.json --relay-url 'wss://wot.shaving.kiwi' --nsec nsec0123456789abcdef
# Let the process run for 1 hour (3600 seconds), then systemd will stop it:
RuntimeMaxSec=3600
TimeoutStopSec=1
# Tells systemd to restart the service automatically after it stops:
Restart=always
RestartSec=1
# run as a non-root user:
User=aida
Group=aida
[Install]
WantedBy=multi-user.target
```
Then I added a starting service to spawn an instance for each CPU thread.
```
$aida@workhorse:systemd/system $ sudo cat notemine_start.service
[Unit]
Description=Start all services in sequence with 3-second intervals
[Service]
Type=oneshot
ExecStart=/usr/bin/zsh /home/aida/notemine_start.sh
RemainAfterExit=yes
[Install]
WantedBy=multi-user.target
```
Here is the startup script (I know, loops exist—but Ctrl+C/Ctrl+V is so old-school):
```
aida@workhorse:~ $ cat notemine_start.sh
/usr/bin/systemctl start notemine@0.service
/usr/bin/sleep 3
/usr/bin/systemctl start notemine@1.service
/usr/bin/sleep 3
/usr/bin/systemctl start notemine@2.service
/usr/bin/sleep 3
/usr/bin/systemctl start notemine@3.service
/usr/bin/sleep 3
...
...
...
/usr/bin/systemctl start notemine@38.service
```
The sleep there is critical to make sure that the `created_at`timestamps are different, preventing redundant hashing.
**This adjustment made Workhorse the strongest machine in my fleet with 10+Mh/s.**
## The Luck Aspect
From Monday evening, I started adding all machines at my disposal into the fleet and by Wednesday evening I was crunching hashes on about 130 CPU threads (a lot of them were quite antique) and at the peak was just little shy of 40Mh/s. To compensate for the slow start with the few above-mentioned hiccups and the fact that I had to use my desktop to do other things from time to time, I counted with the conservative estimate of 30Mh/s when I was doing all the probability calculations.
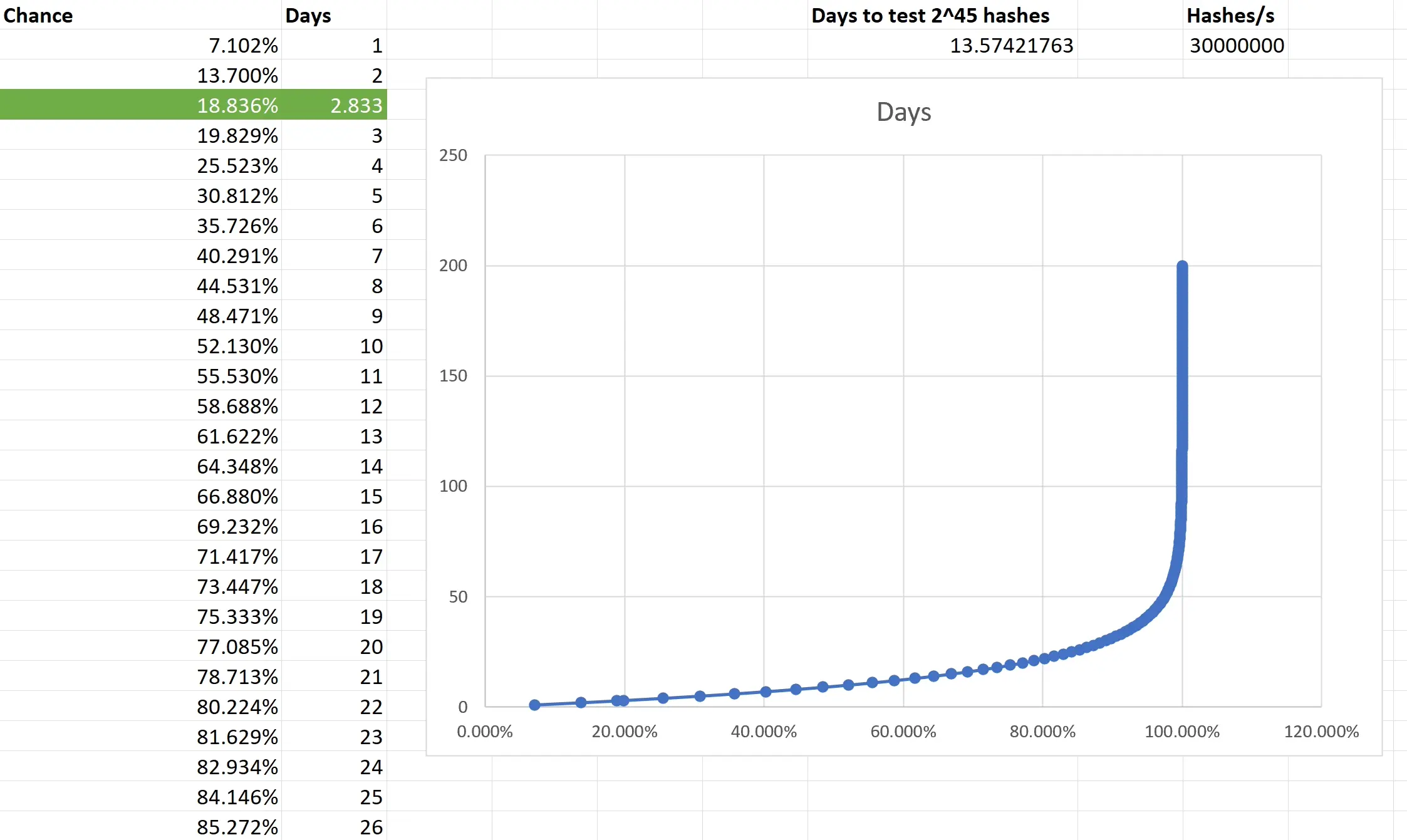
Based on the type of task that PoW mining is, the outcome is not predictible. You are only looking at what is the chance that the outcome of every single independent event will be consecutively non-favourable and then subtracting it from 1 to get the chance of that single favourable event you want. I really had to brush up on my combinatorics and discrete mathematics to make sure I have at least an elementary understanding of what is going on. Also, because we are not just throwing a dice 5 times, but are operating with big numbers, approximation was necessary. Luckily, the formula is available and quite simple in the end.
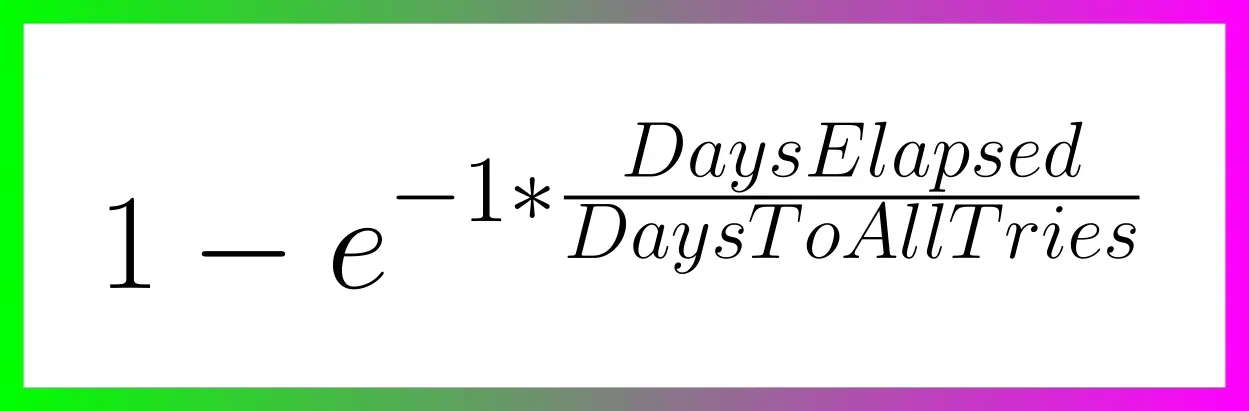
Two weeks to exhauste all the possible tries still doesn't guarantee anything, actually there is a slighlty less than 2 in 3 chance that you will have a result after all that time. So the fact that I was able to hit the right hash in less than 3 days was good luck. Not insane lottery winning luck, but good luck; slighlty lower than 1 in 5.
## Do you want to beat me?
Go ahead! All the pitfalls are described above and until there is a GPU-based PoW Mining available, we are all on pretty even ground.
## Do you hate the note?
In that case, feel free to enjoy this accompanying image:

-

@ a95c6243:d345522c
2025-03-04 09:40:50
**Die «Eliten» führen bereits groß angelegte Pilotprojekte für eine Zukunft durch,** die sie wollen und wir nicht. Das [schreibt](https://off-guardian.org/2025/02/26/coming-soon-the-european-digital-identity-wallet/) der *OffGuardian* in einem Update zum Thema «EU-Brieftasche für die digitale Identität». Das Portal weist darauf hin, dass die Akteure dabei nicht gerade zimperlich vorgehen und auch keinen Hehl aus ihren Absichten machen. *Transition News* hat mehrfach darüber berichtet, zuletzt [hier](https://transition-news.org/eudi-wallet-der-weg-fur-ein-vollstandig-digitalisiertes-europa-ist-frei) und [hier](https://transition-news.org/iata-biometrische-daten-und-digitale-id-machen-das-vollstandig-digitale).
**Mit der EU Digital Identity Wallet (EUDI-Brieftasche) sei eine einzige von der Regierung herausgegebene App geplant,** die Ihre medizinischen Daten, Beschäftigungsdaten, Reisedaten, Bildungsdaten, Impfdaten, Steuerdaten, Finanzdaten sowie (potenziell) Kopien Ihrer Unterschrift, Fingerabdrücke, Gesichtsscans, Stimmproben und DNA enthält. So fasst der *OffGuardian* die eindrucksvolle Liste möglicher Einsatzbereiche zusammen.
**Auch Dokumente wie der Personalausweis oder der** **[Führerschein](https://transition-news.org/eu-weite-einfuhrung-von-digitalen-fuhrerscheinen-fur-digitale-geldborsen)** können dort in elektronischer Form gespeichert werden. Bis 2026 sind alle EU-Mitgliedstaaten dazu verpflichtet, Ihren Bürgern funktionierende und frei verfügbare digitale «Brieftaschen» bereitzustellen.
**Die Menschen würden diese App nutzen,** so das Portal, um Zahlungen vorzunehmen, Kredite zu beantragen, ihre Steuern zu zahlen, ihre Rezepte abzuholen, internationale Grenzen zu überschreiten, Unternehmen zu gründen, Arzttermine zu buchen, sich um Stellen zu bewerben und sogar digitale Verträge online zu unterzeichnen.
**All diese Daten würden auf ihrem Mobiltelefon gespeichert und mit den Regierungen** von neunzehn Ländern (plus der Ukraine) sowie über 140 anderen öffentlichen und privaten Partnern ausgetauscht. Von der Deutschen Bank über das ukrainische Ministerium für digitalen Fortschritt bis hin zu Samsung Europe. Unternehmen und Behörden würden auf diese Daten im Backend zugreifen, um «automatisierte Hintergrundprüfungen» durchzuführen.
**Der Bundesverband der Verbraucherzentralen und Verbraucherverbände** (VZBV) habe Bedenken geäußert, dass eine solche App «Risiken für den Schutz der Privatsphäre und der Daten» berge, berichtet das Portal. Die einzige Antwort darauf laute: «Richtig, genau dafür ist sie ja da!»
**Das alles sei keine Hypothese, betont der** ***OffGuardian***. Es sei vielmehr [«Potential»](https://www.digital-identity-wallet.eu/about-us/140-public-and-private-partners/). Damit ist ein EU-Projekt gemeint, in dessen Rahmen Dutzende öffentliche und private Einrichtungen zusammenarbeiten, «um eine einheitliche Vision der digitalen Identität für die Bürger der europäischen Länder zu definieren». Dies ist nur eines der groß angelegten [Pilotprojekte](https://ec.europa.eu/digital-building-blocks/sites/display/EUDIGITALIDENTITYWALLET/What+are+the+Large+Scale+Pilot+Projects), mit denen Prototypen und Anwendungsfälle für die EUDI-Wallet getestet werden. Es gibt noch mindestens drei weitere.
**Den Ball der digitalen ID-Systeme habe die Covid-«Pandemie»** über die «Impfpässe» ins Rollen gebracht. Seitdem habe das Thema an Schwung verloren. Je näher wir aber der vollständigen Einführung der EUid kämen, desto mehr Propaganda der Art «Warum wir eine digitale Brieftasche brauchen» könnten wir in den Mainstream-Medien erwarten, prognostiziert der *OffGuardian*. Vielleicht müssten wir schon nach dem nächsten großen «Grund», dem nächsten «katastrophalen katalytischen Ereignis» Ausschau halten. Vermutlich gebe es bereits Pläne, warum die Menschen plötzlich eine digitale ID-Brieftasche brauchen würden.
**Die Entwicklung geht jedenfalls stetig weiter in genau diese Richtung.** Beispielsweise hat Jordanien angekündigt, die digitale biometrische ID bei den nächsten [Wahlen](https://www.biometricupdate.com/202502/jordan-plans-digital-id-for-voter-verification-in-next-election) zur Verifizierung der Wähler einzuführen. Man wolle «den Papierkrieg beenden und sicherstellen, dass die gesamte Kette bis zu den nächsten Parlamentswahlen digitalisiert wird», heißt es. Absehbar ist, dass dabei einige Wahlberechtigte «auf der Strecke bleiben» werden, wie im Fall von [Albanien](https://transition-news.org/albanien-schliesst-120-000-burger-ohne-biometrische-ausweise-von-wahlen-aus) geschehen.
**Derweil würden die Briten gerne ihre Privatsphäre gegen Effizienz eintauschen,** [behauptet](https://www.lbc.co.uk/news/tony-blair-id-cards/) Tony Blair. Der Ex-Premier drängte kürzlich erneut auf digitale Identitäten und Gesichtserkennung. Blair ist Gründer einer [Denkfabrik](https://transition-news.org/blair-institute-durch-vermarktung-von-patientendaten-zu-ki-gestutztem) für globalen Wandel, Anhänger globalistischer Technokratie und [«moderner Infrastruktur»](https://transition-news.org/tony-blair-digitale-id-fur-moderne-infrastruktur-unerlasslich-erfordert-aber).
**Abschließend warnt der** ***OffGuardian*** **vor der Illusion, Trump und Musk würden** den US-Bürgern «diesen Schlamassel ersparen». Das Department of Government Efficiency werde sich auf die digitale Identität stürzen. Was könne schließlich «effizienter» sein als eine einzige App, die für alles verwendet wird? Der Unterschied bestehe nur darin, dass die US-Version vielleicht eher privat als öffentlich sei – sofern es da überhaupt noch einen wirklichen Unterschied gebe.
*\[Titelbild: Screenshot* *[OffGuardian](https://off-guardian.org/2025/02/26/coming-soon-the-european-digital-identity-wallet/)]*
***
Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/demnachst-verfugbar-die-europaische-brieftasche-fur-digitale-identitaten)*** erschienen.
-

@ a95c6243:d345522c
2025-03-01 10:39:35
*Ständige Lügen und Unterstellungen, permanent falsche Fürsorge* *\
können Bausteine von emotionaler Manipulation sein. Mit dem Zweck,* *\
Macht und Kontrolle über eine andere Person auszuüben.* *\
Apotheken Umschau*  
**Irgendetwas muss passiert sein: «Gaslighting» ist gerade Thema** in vielen Medien. Heute bin ich nach längerer Zeit mal wieder über dieses Stichwort gestolpert. Das war in einem [Artikel](https://norberthaering.de/propaganda-zensur/dwd-referenzperiode/) von Norbert Häring über Manipulationen des Deutschen Wetterdienstes (DWD). In diesem Fall ging es um eine Pressemitteilung vom Donnerstag zum «viel zu warmen» Winter 2024/25.
**Häring wirft der Behörde vor, dreist zu lügen und Dinge auszulassen,** um die Klimaangst wach zu halten. Was der Leser beim DWD nicht erfahre, sei, dass dieser Winter kälter als die drei vorangegangenen und kälter als der Durchschnitt der letzten zehn Jahre gewesen sei. Stattdessen werde der falsche Eindruck vermittelt, es würde ungebremst immer wärmer.
**Wem also der zu Ende gehende Winter eher kalt vorgekommen sein sollte,** mit dessen Empfinden stimme wohl etwas nicht. Das jedenfalls wolle der DWD uns einreden, so der Wirtschaftsjournalist. Und damit sind wir beim Thema Gaslighting.
**Als** **[Gaslighting](https://bayern-gegen-gewalt.de/gewalt-infos-und-einblicke/formen-von-gewalt/psychische-gewalt/gaslighting/)** **wird eine Form psychischer Manipulation bezeichnet,** mit der die Opfer desorientiert und zutiefst verunsichert werden, indem ihre eigene Wahrnehmung als falsch bezeichnet wird. Der Prozess führt zu Angst und Realitätsverzerrung sowie zur Zerstörung des Selbstbewusstseins. Die Bezeichnung kommt von dem britischen Theaterstück «Gas Light» aus dem Jahr 1938, in dem ein Mann mit grausamen Psychotricks seine Frau in den Wahnsinn treibt.
**Damit Gaslighting funktioniert, muss das Opfer dem Täter vertrauen.** Oft wird solcher Psychoterror daher im privaten oder familiären Umfeld beschrieben, ebenso wie am Arbeitsplatz. Jedoch eignen sich die Prinzipien auch perfekt zur Manipulation der Massen. Vermeintliche Autoritäten wie Ärzte und Wissenschaftler, oder «der fürsorgliche Staat» und Institutionen wie die UNO oder die WHO wollen uns doch nichts Böses. Auch Staatsmedien, Faktenchecker und diverse NGOs wurden zu «vertrauenswürdigen Quellen» erklärt. Das hat seine Wirkung.
**Warum das Thema Gaslighting derzeit scheinbar so populär ist,** vermag ich nicht zu sagen. Es sind aber gerade in den letzten Tagen und Wochen auffällig viele Artikel dazu erschienen, und zwar nicht nur von Psychologen. Die *Frankfurter Rundschau* hat gleich mehrere publiziert, und [Anwälte](https://www.anwalt.de/rechtstipps/gaslighting-beispiele-anzeichen-strafbarkeit-212449.html) interessieren sich dafür offenbar genauso wie Apotheker.
**Die** ***Apotheken Umschau*** **machte sogar auf** **[«Medical Gaslighting»](https://archive.is/Wx5YM)** **aufmerksam.** Davon spreche man, wenn Mediziner Symptome nicht ernst nähmen oder wenn ein gesundheitliches Problem vom behandelnden Arzt «schnöde heruntergespielt» oder abgetan würde. Kommt Ihnen das auch irgendwie bekannt vor? Der Begriff sei allerdings irreführend, da er eine manipulierende Absicht unterstellt, die «nicht gewährleistet» sei.
**Apropos Gaslighting: Die noch amtierende deutsche Bundesregierung** [meldete](https://www.bundesregierung.de/breg-de/service/newsletter-und-abos/bundesregierung-aktuell/ausgabe-08-2025-februar-28-2336254?view=renderNewsletterHtml) heute, es gelte, «weiter \[sic!] gemeinsam daran zu arbeiten, einen gerechten und dauerhaften Frieden für die Ukraine zu erreichen». Die Ukraine, wo sich am Montag «der völkerrechtswidrige Angriffskrieg zum dritten Mal jährte», [verteidige](https://transition-news.org/wikileaks-der-westen-wusste-dass-ein-nato-beitritt-der-ukraine-riskant-war) ihr Land und «unsere gemeinsamen Werte».
**Merken Sie etwas? Das Demokratieverständnis mag ja tatsächlich** inzwischen in beiden Ländern ähnlich traurig sein. Bezüglich Friedensbemühungen ist meine Wahrnehmung jedoch eine andere. Das muss an meinem Gedächtnis liegen.
***
Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/bitte-nicht-von-gaslichtern-irritieren-lassen)*** erschienen.
-

@ 7bdef7be:784a5805
2025-04-02 12:02:45
We value sovereignty, privacy and security when accessing online content, using several tools to achieve this, like open protocols, open OSes, open software products, Tor and VPNs. ## The problem Talking about our social presence, we can manually build up our follower list (social graph), pick a Nostr client that is respectful of our preferences on what to show and how, but with the standard following mechanism, our main feed is public, \*\*so everyone can actually snoop\*\* what we are interested in, and what is supposable that we read daily. ## The solution Nostr has a simple solution for this necessity: encrypted lists. Lists are what they appear, a collection of people or interests (but they can also group much other stuff, see \[NIP-51\](https://github.com/nostr-protocol/nips/blob/master/51.md)). So we can create lists with contacts that we don't have in our main social graph; these lists can be used primarily to create \*\*dedicated feeds\*\*, but they could have other uses, for example, related to monitoring. The interesting thing about lists is that they can also be \*\*encrypted\*\*, so unlike the basic following list, which is always public, we can hide the lists' content from others. The implications are obvious: we can not only have a more organized way to browse content, but it is also \*\*really private one\*\*. One might wonder what use can really be made of private lists; here are some examples: - Browse “can't miss” content from users I consider a priority; - Supervise competitors or adversarial parts; - Monitor sensible topics (tags); - Following someone without being publicly associated with them, as this may be undesirable; The benefits in terms of privacy as usual are not only related to the casual, or programmatic, observer, but are also evident when we think of \*\*how many bots scan our actions to profile us\*\*. ## The current state Unfortunately, lists are not widely supported by Nostr clients, and encrypted support is a rarity. Often the excuse to not implement them is that they are harder to develop, since they require managing the encryption stuff (\[NIP-44\](https://github.com/nostr-protocol/nips/blob/master/51.md)). Nevertheless, developers have an easier option to start offering private lists: give the user the possibility to simply \*\*mark them as local-only\*\*, and never push them to the relays. Even if the user misses the sync feature, this is sufficient to create a private environment. To date, as far as I know, the best client with list management is Gossip, which permits to manage \*\*both encrypted and local-only lists\*\*. Beg your Nostr client to implement private lists!
-

@ 460c25e6:ef85065c
2025-02-25 15:20:39
If you don't know where your posts are, you might as well just stay in the centralized Twitter. You either take control of your relay lists, or they will control you. Amethyst offers several lists of relays for our users. We are going to go one by one to help clarify what they are and which options are best for each one.
## Public Home/Outbox Relays
Home relays store all YOUR content: all your posts, likes, replies, lists, etc. It's your home. Amethyst will send your posts here first. Your followers will use these relays to get new posts from you. So, if you don't have anything there, **they will not receive your updates**.
Home relays must allow queries from anyone, ideally without the need to authenticate. They can limit writes to paid users without affecting anyone's experience.
This list should have a maximum of 3 relays. More than that will only make your followers waste their mobile data getting your posts. Keep it simple. Out of the 3 relays, I recommend:
- 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc.
- 1 personal relay to store a copy of all your content in a place no one can delete. Go to [relay.tools](https://relay.tools/) and never be censored again.
- 1 really fast relay located in your country: paid options like http://nostr.wine are great
Do not include relays that block users from seeing posts in this list. If you do, no one will see your posts.
## Public Inbox Relays
This relay type receives all replies, comments, likes, and zaps to your posts. If you are not getting notifications or you don't see replies from your friends, it is likely because you don't have the right setup here. If you are getting too much spam in your replies, it's probably because your inbox relays are not protecting you enough. Paid relays can filter inbox spam out.
Inbox relays must allow anyone to write into them. It's the opposite of the outbox relay. They can limit who can download the posts to their paid subscribers without affecting anyone's experience.
This list should have a maximum of 3 relays as well. Again, keep it small. More than that will just make you spend more of your data plan downloading the same notifications from all these different servers. Out of the 3 relays, I recommend:
- 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc.
- 1 personal relay to store a copy of your notifications, invites, cashu tokens and zaps.
- 1 really fast relay located in your country: go to [nostr.watch](https://nostr.watch/relays/find) and find relays in your country
Terrible options include:
- nostr.wine should not be here.
- filter.nostr.wine should not be here.
- inbox.nostr.wine should not be here.
## DM Inbox Relays
These are the relays used to receive DMs and private content. Others will use these relays to send DMs to you. **If you don't have it setup, you will miss DMs**. DM Inbox relays should accept any message from anyone, but only allow you to download them.
Generally speaking, you only need 3 for reliability. One of them should be a personal relay to make sure you have a copy of all your messages. The others can be open if you want push notifications or closed if you want full privacy.
Good options are:
- inbox.nostr.wine and auth.nostr1.com: anyone can send messages and only you can download. Not even our push notification server has access to them to notify you.
- a personal relay to make sure no one can censor you. Advanced settings on personal relays can also store your DMs privately. Talk to your relay operator for more details.
- a public relay if you want DM notifications from our servers.
Make sure to add at least one public relay if you want to see DM notifications.
## Private Home Relays
Private Relays are for things no one should see, like your drafts, lists, app settings, bookmarks etc. Ideally, these relays are either local or require authentication before posting AND downloading each user\'s content. There are no dedicated relays for this category yet, so I would use a local relay like Citrine on Android and a personal relay on relay.tools.
Keep in mind that if you choose a local relay only, a client on the desktop might not be able to see the drafts from clients on mobile and vice versa.
## Search relays:
This is the list of relays to use on Amethyst's search and user tagging with @. **Tagging and searching will not work if there is nothing here.**. This option requires NIP-50 compliance from each relay. Hit the Default button to use all available options on existence today:
- nostr.wine
- relay.nostr.band
- relay.noswhere.com
## Local Relays:
This is your local storage. Everything will load faster if it comes from this relay. You should install Citrine on Android and write ws://localhost:4869 in this option.
## General Relays:
This section contains the default relays used to download content from your follows. Notice how you can activate and deactivate the Home, Messages (old-style DMs), Chat (public chats), and Global options in each.
Keep 5-6 large relays on this list and activate them for as many categories (Home, Messages (old-style DMs), Chat, and Global) as possible.
Amethyst will provide additional recommendations to this list from your follows with information on which of your follows might need the additional relay in your list. Add them if you feel like you are missing their posts or if it is just taking too long to load them.
## My setup
Here's what I use:
1. Go to [relay.tools](https://relay.tools/) and create a relay for yourself.
2. Go to [nostr.wine](https://nostr.wine/) and pay for their subscription.
3. Go to [inbox.nostr.wine](https://inbox.nostr.wine/) and pay for their subscription.
4. Go to [nostr.watch](https://nostr.watch/relays/find) and find a good relay in your country.
5. Download Citrine to your phone.
Then, on your relay lists, put:
Public Home/Outbox Relays:
- nostr.wine
- nos.lol or an in-country relay.
- <your.relay>.nostr1.com
Public Inbox Relays
- nos.lol or an in-country relay
- <your.relay>.nostr1.com
DM Inbox Relays
- inbox.nostr.wine
- <your.relay>.nostr1.com
Private Home Relays
- ws://localhost:4869 (Citrine)
- <your.relay>.nostr1.com (if you want)
Search Relays
- nostr.wine
- relay.nostr.band
- relay.noswhere.com
Local Relays
- ws://localhost:4869 (Citrine)
General Relays
- nos.lol
- relay.damus.io
- relay.primal.net
- nostr.mom
And a few of the recommended relays from Amethyst.
## Final Considerations
Remember, relays can see what your Nostr client is requesting and downloading at all times. They can track what you see and see what you like. They can sell that information to the highest bidder, they can delete your content or content that a sponsor asked them to delete (like a negative review for instance) and they can censor you in any way they see fit. Before using any random free relay out there, make sure you trust its operator and you know its terms of service and privacy policies.
-

@ a95c6243:d345522c
2025-02-21 19:32:23
*Europa – das Ganze ist eine wunderbare Idee,* *\
aber das war der Kommunismus auch.* *\
Loriot*  
**«Europa hat fertig», könnte man unken,** und das wäre nicht einmal sehr verwegen. Mit solch einer [Einschätzung](https://transition-news.org/geopolitische-ohnmacht-und-die-last-des-euro-steht-die-eu-vor-der-implosion) stünden wir nicht alleine, denn die Stimmen in diese Richtung mehren sich. Der französische Präsident Emmanuel Macron warnte schon letztes Jahr davor, dass «unser Europa sterben könnte». Vermutlich hatte er dabei andere Gefahren im Kopf als jetzt der ungarische Ministerpräsident Viktor Orbán, der ein «baldiges Ende der EU» prognostizierte. Das Ergebnis könnte allerdings das gleiche sein.
**Neben vordergründigen Themenbereichen wie Wirtschaft, Energie und Sicherheit** ist das eigentliche Problem jedoch die obskure Mischung aus aufgegebener Souveränität und geschwollener Arroganz, mit der europäische Politiker:innende unterschiedlicher Couleur aufzutreten pflegen. Und das Tüpfelchen auf dem i ist die bröckelnde Legitimation politischer Institutionen dadurch, dass die Stimmen großer Teile der Bevölkerung seit Jahren auf vielfältige Weise ausgegrenzt werden.
**Um «UnsereDemokratie» steht es schlecht.** Dass seine Mandate immer schwächer werden, merkt natürlich auch unser «Führungspersonal». Entsprechend werden die Maßnahmen zur Gängelung, Überwachung und Manipulation der Bürger ständig verzweifelter. Parallel dazu [plustern](https://www.bundesregierung.de/breg-de/service/newsletter-und-abos/bundesregierung-aktuell/ausgabe-07-2025-februar-21-2335652?view=renderNewsletterHtml) sich in Paris Macron, Scholz und einige andere noch einmal mächtig in Sachen Verteidigung und [«Kriegstüchtigkeit»](https://transition-news.org/europaische-investitionsbank-tragt-zur-kriegstuchtigkeit-europas-bei) auf.
**Momentan gilt es auch, das Überschwappen covidiotischer und verschwörungsideologischer Auswüchse** aus den USA nach Europa zu vermeiden. So ein «MEGA» (Make Europe Great Again) können wir hier nicht gebrauchen. Aus den Vereinigten Staaten kommen nämlich furchtbare Nachrichten. Beispielsweise wurde einer der schärfsten Kritiker der Corona-Maßnahmen kürzlich zum Gesundheitsminister ernannt. Dieser setzt sich jetzt für eine Neubewertung der mRNA-«Impfstoffe» ein, was durchaus zu einem [Entzug der Zulassungen](https://transition-news.org/usa-zulassungsentzug-fur-corona-impfstoffe-auf-der-tagesordnung) führen könnte.
**Der europäischen Version von** **[«Verteidigung der Demokratie»](https://transition-news.org/eu-macht-freiwilligen-verhaltenskodex-gegen-desinformation-zu-bindendem-recht)** setzte der US-Vizepräsident J. D. Vance auf der Münchner Sicherheitskonferenz sein Verständnis entgegen: «Demokratie stärken, indem wir unseren Bürgern erlauben, ihre Meinung zu sagen». Das Abschalten von Medien, das Annullieren von Wahlen oder das Ausschließen von Menschen vom politischen Prozess schütze gar nichts. Vielmehr sei dies der todsichere Weg, die Demokratie zu zerstören.
**In der Schweiz kamen seine Worte deutlich besser an** als in den meisten europäischen NATO-Ländern. Bundespräsidentin Karin Keller-Sutter lobte die Rede und interpretierte sie als «Plädoyer für die direkte Demokratie». Möglicherweise zeichne sich hier eine [außenpolitische Kehrtwende](https://transition-news.org/schweiz-vor-aussenpolitischer-kehrtwende-richtung-integraler-neutralitat) in Richtung integraler Neutralität ab, meint mein Kollege Daniel Funk. Das wären doch endlich mal ein paar gute Nachrichten.
**Von der einstigen Idee einer europäischen Union** mit engeren Beziehungen zwischen den Staaten, um Konflikte zu vermeiden und das Wohlergehen der Bürger zu verbessern, sind wir meilenweit abgekommen. Der heutige korrupte Verbund unter technokratischer Leitung ähnelt mehr einem Selbstbedienungsladen mit sehr begrenztem Zugang. Die EU-Wahlen im letzten Sommer haben daran ebenso wenig geändert, wie die [Bundestagswahl](https://transition-news.org/bundestagswahl-mehr-aufrustung-statt-friedenskanzler-nach-der-wahl) am kommenden Sonntag darauf einen Einfluss haben wird.
***
Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/europaer-seid-ihr-noch-zu-retten)*** erschienen.
-

@ d5c3d063:4d1159b3
2025-04-02 04:04:32
"ผลิตผลทางเศรษฐกิจที่เพิ่มขึ้น
เป็นประโยชน์กับทุกคนเสมอ
ไม่ว่าในทางใดก็ทางหนึ่ง"
เป็นโพสของอาจารย์พิริยะ ที่เรียกได้ว่าคือ
“หลักการพื้นฐาน” ของเสรีภาพทางเศรษฐกิจ
ที่หลายคนอาจหลงลืม และซุปอยากขยายความต่อ
เพราะนี่คือจุดเริ่มต้นของคำว่า “ระบบที่แฟร์จริง”
.
เราถูกสอนให้คิดว่า ถ้ามีคนรวยขึ้น ต้องมีใครอีกคนจนลง แต่ในความเป็นจริง ระบบตลาดเสรีไม่ได้ทำงานแบบนั้นเลย เพราะเมื่อมีคนผลิตของที่ดีขึ้น ผลิตได้เร็วขึ้น ต้นทุนจะลดลง สินค้าที่เคยเข้าถึงยาก ก็เริ่มกลายเป็นของธรรมดาที่ใครก็ใช้ได้
.
คนหนึ่งคนที่ผลิตเพิ่มขึ้น อาจได้กำไรมากขึ้น แต่คนอีกเป็นล้านกลับได้ใช้สินค้าที่ถูกลง ชีวิตง่ายขึ้น สะดวกขึ้น เห็นได้ชัดว่าทุกฝ่ายได้ประโยชน์ ไม่ใช่เพราะมีใครต้อง "เสียสละจากการบังคับ" แต่เพราะทุกคนแลกเปลี่ยนกัน "ด้วยความสมัครใจ"
นี่คือหลักการที่เศรษฐศาสตร์สำนักออสเตรียนเชื่อมั่นมาตลอด ว่าเสรีภาพในการผลิตและแลกเปลี่ยน คือรากฐานของความมั่งคั่งร่วมกัน "การแบ่งงานกันทำ" ของคนที่ถนัดต่างกัน คือวิธีที่มนุษย์สร้างสังคมเจริญขึ้นมาได้จริง ไม่ใช่เพราะรัฐสั่งให้ทำ แต่เพราะทุกคนเห็นประโยชน์ร่วมกันและยินดีแลกเปลี่ยนกันเอง
.
ปัญหาคือ วันนี้เราไม่ได้อยู่ในตลาดเสรีจริง
แต่เราอยู่ในระบบที่รัฐเข้ามาเขียนกติกา
ออกใบอนุญาต ควบคุมอุตสาหกรรม กำหนดราคา
และที่แย่คือการออกกฎที่เอื้อให้พวกพ้อง ทำให้บางคนได้เปรียบในตลาด โดยไม่ได้มาจากการผลิตเก่งหรือบริการดีแต่มาจากการมีสายสัมพันธ์กับอำนาจ (แบบนี้คือ ทุนนิยมพวกพ้อง)
.
แล้วคนทั่วไปที่เห็นภาพแบบนี้ ก็พากันเรียกร้องให้รัฐเข้ามาจัดการ ทั้งที่จริงแล้ว...คนที่ควรรับผิดชอบ คือรัฐเอง ที่เปิดช่องให้เรื่องพวกนี้เกิดขึ้นตั้งแต่แรก
.
เราจึงติดกับดักเดิมซ้ำๆ คือรัฐสร้างปัญหา แล้วใช้ปัญหานั้นเป็นข้ออ้างในการขยายอำนาจ
สุดท้ายมันก็ยิ่งบิดเบือนระบบเศรษฐกิจให้ผิดเพี้ยนเข้าไปอีก จนคนทำงานจริง ผลิตของจริง กลับไม่มีที่ยืนในระบบ
.
.
ให้เห็นภาพต่อว่า ถ้ามีคนผลิตมากขึ้น ทุกคนในระบบจะได้ประโยชน์เพิ่มขึ้นเสมอ ตราบใดที่
1 เขาไม่ได้ขโมยใคร
2 เขาแลกเปลี่ยนบนความสมัครใจ เท่านั้นยังไม่พอ
3 "เงิน" มันต้องเป็นกระจกสะท้อนคุณค่าจากการผลิต
ไม่ใช่เงินที่สร้างจากหนี้แล้วใช้กฎหมายยังคับว่ามันมีค่า
ถ้าเงื่อนไขสามข้อนี้ยังอยู่ครบ
ทุนนิยมตลาดเสรีที่แท้จริง ก็จะเป็นระบบที่ยั่งยืน
และแฟร์ที่สุดเท่าที่เคยมีมา
ซึ่งตลอดประวัติศาสตร์เรายังไม่เคยแยกอำนาจการเงินออกจากมือมนุษย์ได้เลย
เพราะถ้าเราปล่อยให้รัฐพิมพ์เงินได้อย่างอิสระ
ลดคุณค่าของเงินได้โดยไม่ต้องรับผิดชอบ
และแทรกแซงราคาตลาดโดยไม่มีการผลิตรองรับ
เมื่อถึงจุดนั้น ต่อให้เราผลิตเก่งแค่ไหน เราก็ไม่มีทางรวยขึ้น เพราะรางวัลไม่ได้แจกตามผลงาน
แต่แจกตามความใกล้ชิตผู้มีอำนาจ
เมื่อเงินเสื่อมค่าลงทุกวัน ข้าวของแพงขึ้น
เราต้องทำงานหนักขึ้น แต่ซื้อของได้น้อยลง
แล้วเราจะเริ่มถามตัวเองว่า
“เรากำลังทำงานสร้างคุณค่าจริงๆ
ขยันจนแทบไม่มีเวลาหายใจ
แต่สุดท้ายเรากำลังก้าวไปเดินหน้า
หรือแค่พยายามเอาตัวรอดในระบบที่ไม่ยุติธรรม”
และในวันนั้น...คุณอาจจะย้อนนึกถึงประโยคนี้
ที่อาจารย์เคยโพสแล้วอาจไม่ได้คิดว่ามันสำคัญ
ปล.วันนี้เราอาจเห็นต่างกันเรื่องบทบาทของรัฐ
แต่ซุปคิดว่าจุดร่วมของคำถามนี้คือ
ระบบเศรษฐกิจที่ดี ควรให้รางวัลกับผู้ผลิต
หรือให้รางวัลกับคนที่อยู่ใกล้ชิดผู้มีอำนาจ...
#Siamstr
-

@ 9967f375:04f9a5e1
2025-04-01 20:43:54
El día 1, emprendió su tornaviaje con gran felicidad de este Puerto, para las Islas Filipinas, el Galeón *Sacra Familia*, que (por muerte del General Don Juan Antonio Cortés de Arredondo, Castillo, y Noblezia, a cuyo cargo vino) va a el de Don Jerónimo Montero.
-

@ a95c6243:d345522c
2025-02-19 09:23:17
*Die «moralische Weltordnung» – eine Art Astrologie.
Friedrich Nietzsche*
**Das Treffen der BRICS-Staaten beim [Gipfel](https://transition-news.org/brics-gipfel-in-kasan-warum-schweigt-die-schweiz) im russischen Kasan** war sicher nicht irgendein politisches Event. Gastgeber Wladimir Putin habe «Hof gehalten», sagen die Einen, China und Russland hätten ihre Vorstellung einer multipolaren Weltordnung zelebriert, schreiben Andere.
**In jedem Fall zeigt die Anwesenheit von über 30 Delegationen aus der ganzen Welt,** dass von einer geostrategischen Isolation Russlands wohl keine Rede sein kann. Darüber hinaus haben sowohl die Anreise von UN-Generalsekretär António Guterres als auch die Meldungen und Dementis bezüglich der Beitrittsbemühungen des NATO-Staats [Türkei](https://transition-news.org/turkei-entlarvt-fake-news-von-bild-uber-indiens-angebliches-veto-gegen-den) für etwas Aufsehen gesorgt.
**Im Spannungsfeld geopolitischer und wirtschaftlicher Umbrüche** zeigt die neue Allianz zunehmendes Selbstbewusstsein. In Sachen gemeinsamer Finanzpolitik schmiedet man interessante Pläne. Größere Unabhängigkeit von der US-dominierten Finanzordnung ist dabei ein wichtiges Ziel.
**Beim BRICS-Wirtschaftsforum in Moskau, wenige Tage vor dem Gipfel,** zählte ein nachhaltiges System für Finanzabrechnungen und Zahlungsdienste zu den vorrangigen Themen. Während dieses Treffens ging der russische Staatsfonds eine Partnerschaft mit dem Rechenzentrumsbetreiber BitRiver ein, um [Bitcoin](https://www.forbes.com/sites/digital-assets/2024/10/23/russia-launches-brics-mining-infrastructure-project/)-Mining-Anlagen für die BRICS-Länder zu errichten.
**Die Initiative könnte ein Schritt sein, Bitcoin und andere Kryptowährungen** als Alternativen zu traditionellen Finanzsystemen zu etablieren. Das Projekt könnte dazu führen, dass die BRICS-Staaten den globalen Handel in Bitcoin abwickeln. Vor dem Hintergrund der Diskussionen über eine «BRICS-Währung» wäre dies eine Alternative zu dem ursprünglich angedachten Korb lokaler Währungen und zu goldgedeckten Währungen sowie eine mögliche Ergänzung zum Zahlungssystem [BRICS Pay](https://en.wikipedia.org/wiki/BRICS_PAY).
**Dient der Bitcoin also der Entdollarisierung?** Oder droht er inzwischen, zum Gegenstand geopolitischer [Machtspielchen](https://legitim.ch/es-ist-ein-sieg-fuer-bitcoin-waehrend-russland-und-die-usa-um-die-krypto-vorherrschaft-kaempfen/) zu werden? Angesichts der globalen Vernetzungen ist es oft schwer zu durchschauen, «was eine Show ist und was im Hintergrund von anderen Strippenziehern insgeheim gesteuert wird». Sicher können Strukturen wie Bitcoin auch so genutzt werden, dass sie den Herrschenden dienlich sind. Aber die Grundeigenschaft des dezentralisierten, unzensierbaren Peer-to-Peer Zahlungsnetzwerks ist ihm schließlich nicht zu nehmen.
**Wenn es nach der EZB oder dem IWF geht, dann scheint statt Instrumentalisierung** momentan eher der Kampf gegen Kryptowährungen angesagt. Jürgen Schaaf, Senior Manager bei der Europäischen Zentralbank, hat jedenfalls dazu aufgerufen, [Bitcoin «zu eliminieren»](https://www.btc-echo.de/schlagzeilen/ezb-banker-es-gibt-gute-gruende-bitcoin-zu-eliminieren-194015/). Der Internationale Währungsfonds forderte El Salvador, das Bitcoin 2021 als gesetzliches Zahlungsmittel eingeführt hat, kürzlich zu [begrenzenden Maßnahmen](https://legitim.ch/el-salvador-iwf-fordert-trotz-nicht-eingetretener-risiken-neue-massnahmen-gegen-bitcoin/) gegen das Kryptogeld auf.
**Dass die BRICS-Staaten ein freiheitliches Ansinnen im Kopf haben,** wenn sie Kryptowährungen ins Spiel bringen, darf indes auch bezweifelt werden. Im [Abschlussdokument](http://static.kremlin.ru/media/events/files/en/RosOySvLzGaJtmx2wYFv0lN4NSPZploG.pdf) bekennen sich die Gipfel-Teilnehmer ausdrücklich zur UN, ihren Programmen und ihrer «Agenda 2030». Ernst Wolff nennt das «eine [Bankrotterklärung](https://x.com/wolff_ernst/status/1849781982961557771) korrupter Politiker, die sich dem digital-finanziellen Komplex zu 100 Prozent unterwerfen».
---
Dieser Beitrag ist zuerst auf *[Transition News](https://transition-news.org/aufstand-gegen-die-dollar-hegemonie)* erschienen.
-

@ b2caa9b3:9eab0fb5
2025-04-01 20:29:01

For years, I’ve been shifting my life away from traditional systems and toward Bitcoin. I calculate my expenses in sats, buy airtime and online data with BTC, and continue exploring new ways to integrate Bitcoin into my daily life. While I’m not yet fully living on Bitcoin, I am getting closer with each step.

Since discovering Nostr, my perspective on decentralization has deepened. More than just a financial shift, it's a complete lifestyle transformation. Years ago, after facing injustice in my home country, I took the first step toward a new way of living. That decision led me to where I am today—a minimalist, a nomad, and a believer in financial freedom through Bitcoin.

I once served in the military, owned a house, and drove a nice car. My life looked very different back then. But over time, I realized that true freedom wasn’t in possessions—it was in mobility, independence, and the ability to control my own finances. Now, all I own fits into a backpack weighing less than 12 kg. My lifestyle is simple, yet rich in experiences.
March 14 marks eight years since I embraced my nomadic lifestyle. What started as a leap into the unknown has become my way of life. Living with less has given me more—the freedom to move, to explore, and to be truly independent. The more I immerse myself in the Bitcoin ecosystem, the more I see its potential to reshape not only my life but the world around me.

The journey isn’t over. In fact, it’s just beginning. Let’s see where this path leads as I go further into the blockchain revolution!



 @ 39cc53c9:27168656
2025-04-08 07:31:34> [Read the original blog post](https://blog.kycnot.me/p/kyc-no-thanks) Know Your Customer is a regulation that requires companies of all sizes to verify the identity, suitability, and risks involved with maintaining a business relationship with a customer. Such procedures fit within the broader scope of anti-money laundering (AML) and counterterrorism financing (CTF) regulations. Banks, exchanges, online business, mail providers, domain registrars... Everyone wants to know who you are before you can even opt for their service. Your personal information is flowing around the internet in the hands of "god-knows-who" and secured by "trust-me-bro military-grade encryption". Once your account is linked to your personal (and verified) identity, tracking you is just as easy as keeping logs on all these platforms. ## Rights for Illusions KYC processes aim to combat terrorist financing, money laundering, and other illicit activities. On the surface, KYC seems like a commendable initiative. I mean, who wouldn't want to halt terrorists and criminals in their tracks? The logic behind KYC is: "If we mandate every financial service provider to identify their users, it becomes easier to pinpoint and apprehend the malicious actors." However, terrorists and criminals are not precisely lining up to be identified. They're crafty. They may adopt false identities or find alternative strategies to continue their operations. Far from being outwitted, many times they're several steps ahead of regulations. Realistically, KYC might deter a small fraction – let's say about 1% [^1] – of these malefactors. Yet, the cost? All of us are saddled with the inconvenient process of identification just to use a service. Under the rhetoric of "ensuring our safety", governments and institutions enact regulations that seem more out of a dystopian novel, gradually taking away our right to privacy. To illustrate, consider a city where the mayor has rolled out facial recognition cameras in every nook and cranny. A band of criminals, intent on robbing a local store, rolls in with a stolen car, their faces obscured by masks and their bodies cloaked in all-black clothes. Once they've committed the crime and exited the city's boundaries, they switch vehicles and clothes out of the cameras' watchful eyes. The high-tech surveillance? It didn’t manage to identify or trace them. Yet, for every law-abiding citizen who merely wants to drive through the city or do some shopping, their movements and identities are constantly logged. The irony? This invasive tracking impacts all of us, just to catch the 1% [^1] of less-than-careful criminals. ## KYC? Not you. > KYC creates barriers to participation in normal economic activity, to supposedly stop criminals. [^2] KYC puts barriers between many users and businesses. One of these comes from the fact that the process often requires multiple forms of identification, proof of address, and sometimes even financial records. For individuals in areas with poor record-keeping, non-recognized legal documents, or those who are unbanked, homeless or transient, obtaining these documents can be challenging, if not impossible. For people who are not skilled with technology or just don't have access to it, there's also a barrier since KYC procedures are mostly online, leaving them inadvertently excluded. Another barrier goes for the casual or one-time user, where they might not see the value in undergoing a rigorous KYC process, and these requirements can deter them from using the service altogether. It also wipes some businesses out of the equation, since for smaller businesses, the costs associated with complying with KYC norms—from the actual process of gathering and submitting documents to potential delays in operations—can be prohibitive in economical and/or technical terms. ## You're not welcome Imagine a swanky new club in town with a strict "members only" sign. You hear the music, you see the lights, and you want in. You step up, ready to join, but suddenly there's a long list of criteria you must meet. After some time, you are finally checking all the boxes. But then the club rejects your membership with no clear reason why. You just weren't accepted. Frustrating, right? This club scenario isn't too different from the fact that KYC is being used by many businesses as a convenient gatekeeping tool. A perfect excuse based on a "legal" procedure they are obliged to. Even some exchanges may randomly use this to freeze and block funds from users, claiming these were "flagged" by a cryptic system that inspects the transactions. You are left hostage to their arbitrary decision to let you successfully pass the KYC procedure. If you choose to sidestep their invasive process, they might just hold onto your funds indefinitely. ## Your identity has been stolen KYC data has been found to be for sale on many dark net markets[^3]. Exchanges may have leaks or hacks, and such leaks contain **very** sensitive data. We're talking about the full monty: passport or ID scans, proof of address, and even those awkward selfies where you're holding up your ID next to your face. All this data is being left to the mercy of the (mostly) "trust-me-bro" security systems of such companies. Quite scary, isn't it? As cheap as $10 for 100 documents, with discounts applying for those who buy in bulk, the personal identities of innocent users who passed KYC procedures are for sale. [^3] In short, if you have ever passed the KYC/AML process of a crypto exchange, your privacy is at risk of being compromised, or it might even have already been compromised. ## (they) Know Your Coins You may already know that **Bitcoin and most cryptocurrencies have a transparent public blockchain**, meaning that all data is shown unencrypted for everyone to see and recorded **forever**. If you link an address you own to your identity through KYC, for example, by sending an amount from a KYC exchange to it, your Bitcoin is no longer pseudonymous and can then be traced. If, for instance, you send Bitcoin from such an identified address to another KYC'ed address (say, from a friend), everyone having access to that address-identity link information (exchanges, governments, hackers, etc.) will be able to associate that transaction and know who you are transacting with. ## Conclusions To sum up, **KYC does not protect individuals**; rather, it's a threat to our privacy, freedom, security and integrity. Sensible information flowing through the internet is thrown into chaos by dubious security measures. It puts borders between many potential customers and businesses, and it helps governments and companies track innocent users. That's the chaos KYC has stirred. The criminals are using stolen identities from companies that gathered them thanks to these very same regulations that were supposed to combat them. Criminals always know how to circumvent such regulations. In the end, normal people are the most affected by these policies. The threat that KYC poses to individuals in terms of privacy, security and freedom is not to be neglected. And if we don’t start challenging these systems and questioning their efficacy, we are just one step closer to the dystopian future that is now foreseeable. > Edited 20/03/2024 > * Add reference to the 1% statement on [Rights for Illusions](#rights-for-illusions) section to an article where Chainalysis found that only 0.34% of the transaction volume with cryptocurrencies in 2023 was attributable to criminal activity [^1] [^1]: https://www.chainalysis.com/blog/2024-crypto-crime-report-introduction/ [^2]: https://old.reddit.com/r/BitcoinBeginners/comments/k2bve1/is_kyc_bad_if_so_why/gdtc8kz [^3]: https://www.ccn.com/hacked-customer-data-from-world-leading-cryptocurrency-exchanges-for-sale-on-the-dark-web/
@ 39cc53c9:27168656
2025-04-08 07:31:34> [Read the original blog post](https://blog.kycnot.me/p/kyc-no-thanks) Know Your Customer is a regulation that requires companies of all sizes to verify the identity, suitability, and risks involved with maintaining a business relationship with a customer. Such procedures fit within the broader scope of anti-money laundering (AML) and counterterrorism financing (CTF) regulations. Banks, exchanges, online business, mail providers, domain registrars... Everyone wants to know who you are before you can even opt for their service. Your personal information is flowing around the internet in the hands of "god-knows-who" and secured by "trust-me-bro military-grade encryption". Once your account is linked to your personal (and verified) identity, tracking you is just as easy as keeping logs on all these platforms. ## Rights for Illusions KYC processes aim to combat terrorist financing, money laundering, and other illicit activities. On the surface, KYC seems like a commendable initiative. I mean, who wouldn't want to halt terrorists and criminals in their tracks? The logic behind KYC is: "If we mandate every financial service provider to identify their users, it becomes easier to pinpoint and apprehend the malicious actors." However, terrorists and criminals are not precisely lining up to be identified. They're crafty. They may adopt false identities or find alternative strategies to continue their operations. Far from being outwitted, many times they're several steps ahead of regulations. Realistically, KYC might deter a small fraction – let's say about 1% [^1] – of these malefactors. Yet, the cost? All of us are saddled with the inconvenient process of identification just to use a service. Under the rhetoric of "ensuring our safety", governments and institutions enact regulations that seem more out of a dystopian novel, gradually taking away our right to privacy. To illustrate, consider a city where the mayor has rolled out facial recognition cameras in every nook and cranny. A band of criminals, intent on robbing a local store, rolls in with a stolen car, their faces obscured by masks and their bodies cloaked in all-black clothes. Once they've committed the crime and exited the city's boundaries, they switch vehicles and clothes out of the cameras' watchful eyes. The high-tech surveillance? It didn’t manage to identify or trace them. Yet, for every law-abiding citizen who merely wants to drive through the city or do some shopping, their movements and identities are constantly logged. The irony? This invasive tracking impacts all of us, just to catch the 1% [^1] of less-than-careful criminals. ## KYC? Not you. > KYC creates barriers to participation in normal economic activity, to supposedly stop criminals. [^2] KYC puts barriers between many users and businesses. One of these comes from the fact that the process often requires multiple forms of identification, proof of address, and sometimes even financial records. For individuals in areas with poor record-keeping, non-recognized legal documents, or those who are unbanked, homeless or transient, obtaining these documents can be challenging, if not impossible. For people who are not skilled with technology or just don't have access to it, there's also a barrier since KYC procedures are mostly online, leaving them inadvertently excluded. Another barrier goes for the casual or one-time user, where they might not see the value in undergoing a rigorous KYC process, and these requirements can deter them from using the service altogether. It also wipes some businesses out of the equation, since for smaller businesses, the costs associated with complying with KYC norms—from the actual process of gathering and submitting documents to potential delays in operations—can be prohibitive in economical and/or technical terms. ## You're not welcome Imagine a swanky new club in town with a strict "members only" sign. You hear the music, you see the lights, and you want in. You step up, ready to join, but suddenly there's a long list of criteria you must meet. After some time, you are finally checking all the boxes. But then the club rejects your membership with no clear reason why. You just weren't accepted. Frustrating, right? This club scenario isn't too different from the fact that KYC is being used by many businesses as a convenient gatekeeping tool. A perfect excuse based on a "legal" procedure they are obliged to. Even some exchanges may randomly use this to freeze and block funds from users, claiming these were "flagged" by a cryptic system that inspects the transactions. You are left hostage to their arbitrary decision to let you successfully pass the KYC procedure. If you choose to sidestep their invasive process, they might just hold onto your funds indefinitely. ## Your identity has been stolen KYC data has been found to be for sale on many dark net markets[^3]. Exchanges may have leaks or hacks, and such leaks contain **very** sensitive data. We're talking about the full monty: passport or ID scans, proof of address, and even those awkward selfies where you're holding up your ID next to your face. All this data is being left to the mercy of the (mostly) "trust-me-bro" security systems of such companies. Quite scary, isn't it? As cheap as $10 for 100 documents, with discounts applying for those who buy in bulk, the personal identities of innocent users who passed KYC procedures are for sale. [^3] In short, if you have ever passed the KYC/AML process of a crypto exchange, your privacy is at risk of being compromised, or it might even have already been compromised. ## (they) Know Your Coins You may already know that **Bitcoin and most cryptocurrencies have a transparent public blockchain**, meaning that all data is shown unencrypted for everyone to see and recorded **forever**. If you link an address you own to your identity through KYC, for example, by sending an amount from a KYC exchange to it, your Bitcoin is no longer pseudonymous and can then be traced. If, for instance, you send Bitcoin from such an identified address to another KYC'ed address (say, from a friend), everyone having access to that address-identity link information (exchanges, governments, hackers, etc.) will be able to associate that transaction and know who you are transacting with. ## Conclusions To sum up, **KYC does not protect individuals**; rather, it's a threat to our privacy, freedom, security and integrity. Sensible information flowing through the internet is thrown into chaos by dubious security measures. It puts borders between many potential customers and businesses, and it helps governments and companies track innocent users. That's the chaos KYC has stirred. The criminals are using stolen identities from companies that gathered them thanks to these very same regulations that were supposed to combat them. Criminals always know how to circumvent such regulations. In the end, normal people are the most affected by these policies. The threat that KYC poses to individuals in terms of privacy, security and freedom is not to be neglected. And if we don’t start challenging these systems and questioning their efficacy, we are just one step closer to the dystopian future that is now foreseeable. > Edited 20/03/2024 > * Add reference to the 1% statement on [Rights for Illusions](#rights-for-illusions) section to an article where Chainalysis found that only 0.34% of the transaction volume with cryptocurrencies in 2023 was attributable to criminal activity [^1] [^1]: https://www.chainalysis.com/blog/2024-crypto-crime-report-introduction/ [^2]: https://old.reddit.com/r/BitcoinBeginners/comments/k2bve1/is_kyc_bad_if_so_why/gdtc8kz [^3]: https://www.ccn.com/hacked-customer-data-from-world-leading-cryptocurrency-exchanges-for-sale-on-the-dark-web/ @ 68c90cf3:99458f5c
2025-04-04 16:06:10I have two Nostr profiles I use for different subject matter, and I wanted a way to manage and track zaps for each. Using Alby Hub I created two isolated Lightning wallets each associated with one of the profile’s nsecs. YakiHonne made it easy to connect the associated wallets with the profiles. The user interface is well designed to show balances for each.  In my case, I have one profile for photography related content, and the other for Bitcoin, Nostr, and technology related content. I can easily switch between the two, sending and receiving zaps on each while staying up to date on balances and viewing transactions.  Using my self-hosted Alby Hub I can manage Lightning channels and wallets while sending and receiving zaps for multiple profiles with YakiHonne. #YakiHonne #AlbyHub #Lightning #Bitcoin #Nostr
@ 68c90cf3:99458f5c
2025-04-04 16:06:10I have two Nostr profiles I use for different subject matter, and I wanted a way to manage and track zaps for each. Using Alby Hub I created two isolated Lightning wallets each associated with one of the profile’s nsecs. YakiHonne made it easy to connect the associated wallets with the profiles. The user interface is well designed to show balances for each.  In my case, I have one profile for photography related content, and the other for Bitcoin, Nostr, and technology related content. I can easily switch between the two, sending and receiving zaps on each while staying up to date on balances and viewing transactions.  Using my self-hosted Alby Hub I can manage Lightning channels and wallets while sending and receiving zaps for multiple profiles with YakiHonne. #YakiHonne #AlbyHub #Lightning #Bitcoin #Nostr @ b9f4c34d:7d1a0e31
2025-04-02 15:00:20<h2> Test Video Document </h2>
@ b9f4c34d:7d1a0e31
2025-04-02 15:00:20<h2> Test Video Document </h2> @ b9f4c34d:7d1a0e31
2025-04-02 14:59:02<h1> Testy McTestenface </h1> <p> It's been so long, html </p>
@ b9f4c34d:7d1a0e31
2025-04-02 14:59:02<h1> Testy McTestenface </h1> <p> It's been so long, html </p> @ 04c915da:3dfbecc9
2025-03-26 20:54:33Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all. That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission. As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently. Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive. Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally. The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match. When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol. Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
@ 04c915da:3dfbecc9
2025-03-26 20:54:33Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all. That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission. As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently. Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive. Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally. The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match. When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol. Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit. @ b2d670de:907f9d4a
2025-03-25 20:17:57This guide will walk you through setting up your own Strfry Nostr relay on a Debian/Ubuntu server and making it accessible exclusively as a TOR hidden service. By the end, you'll have a privacy-focused relay that operates entirely within the TOR network, enhancing both your privacy and that of your users. ## Table of Contents 1. Prerequisites 2. Initial Server Setup 3. Installing Strfry Nostr Relay 4. Configuring Your Relay 5. Setting Up TOR 6. Making Your Relay Available on TOR 7. Testing Your Setup] 8. Maintenance and Security 9. Troubleshooting ## Prerequisites - A Debian or Ubuntu server - Basic familiarity with command line operations (most steps are explained in detail) - Root or sudo access to your server ## Initial Server Setup First, let's make sure your server is properly set up and secured. ### Update Your System Connect to your server via SSH and update your system: ```bash sudo apt update sudo apt upgrade -y ``` ### Set Up a Basic Firewall Install and configure a basic firewall: ```bash sudo apt install ufw -y sudo ufw allow ssh sudo ufw enable ``` This allows SSH connections while blocking other ports for security. ## Installing Strfry Nostr Relay This guide includes the full range of steps needed to build and set up Strfry. It's simply based on the current version of the `DEPLOYMENT.md` document in the Strfry GitHub repository. If the build/setup process is changed in the repo, this document could get outdated. If so, please report to me that something is outdated and check for updated steps [here](https://github.com/hoytech/strfry/blob/master/docs/DEPLOYMENT.md). ### Install Dependencies First, let's install the necessary dependencies. Each package serves a specific purpose in building and running Strfry: ```bash sudo apt install -y git build-essential libyaml-perl libtemplate-perl libregexp-grammars-perl libssl-dev zlib1g-dev liblmdb-dev libflatbuffers-dev libsecp256k1-dev libzstd-dev ``` Here's why each dependency is needed: **Basic Development Tools:** - `git`: Version control system used to clone the Strfry repository and manage code updates - `build-essential`: Meta-package that includes compilers (gcc, g++), make, and other essential build tools **Perl Dependencies** (used for Strfry's build scripts): - `libyaml-perl`: Perl interface to parse YAML configuration files - `libtemplate-perl`: Template processing system used during the build process - `libregexp-grammars-perl`: Advanced regular expression handling for Perl scripts **Core Libraries for Strfry:** - `libssl-dev`: Development files for OpenSSL, used for secure connections and cryptographic operations - `zlib1g-dev`: Compression library that Strfry uses to reduce data size - `liblmdb-dev`: Lightning Memory-Mapped Database library, which Strfry uses for its high-performance database backend - `libflatbuffers-dev`: Memory-efficient serialization library for structured data - `libsecp256k1-dev`: Optimized C library for EC operations on curve secp256k1, essential for Nostr's cryptographic signatures - `libzstd-dev`: Fast real-time compression algorithm for efficient data storage and transmission ### Clone and Build Strfry Clone the Strfry repository: ```bash git clone https://github.com/hoytech/strfry.git cd strfry ``` Build Strfry: ```bash git submodule update --init make setup-golpe make -j2 # This uses 2 CPU cores. Adjust based on your server (e.g., -j4 for 4 cores) ``` This build process will take several minutes, especially on servers with limited CPU resources, so go get a coffee and post some great memes on nostr in the meantime. ### Install Strfry Install the Strfry binary to your system path: ```bash sudo cp strfry /usr/local/bin ``` This makes the `strfry` command available system-wide, allowing it to be executed from any directory and by any user with the appropriate permissions. ## Configuring Your Relay ### Create Strfry User Create a dedicated user for running Strfry. This enhances security by isolating the relay process: ```bash sudo useradd -M -s /usr/sbin/nologin strfry ``` The `-M` flag prevents creating a home directory, and `-s /usr/sbin/nologin` prevents anyone from logging in as this user. This is a security best practice for service accounts. ### Create Data Directory Create a directory for Strfry's data: ```bash sudo mkdir /var/lib/strfry sudo chown strfry:strfry /var/lib/strfry sudo chmod 755 /var/lib/strfry ``` This creates a dedicated directory for Strfry's database and sets the appropriate permissions so that only the strfry user can write to it. ### Configure Strfry Copy the sample configuration file: ```bash sudo cp strfry.conf /etc/strfry.conf ``` Edit the configuration file: ```bash sudo nano /etc/strfry.conf ``` Modify the database path: ``` # Find this line: db = "./strfry-db/" # Change it to: db = "/var/lib/strfry/" ``` Check your system's hard limit for file descriptors: ```bash ulimit -Hn ``` Update the `nofiles` setting in your configuration to match this value (or set to 0): ``` # Add or modify this line in the config (example if your limit is 524288): nofiles = 524288 ``` The `nofiles` setting determines how many open files Strfry can have simultaneously. Setting it to your system's hard limit (or 0 to use the system default) helps prevent "too many open files" errors if your relay becomes popular. You might also want to customize your relay's information in the config file. Look for the `info` section and update it with your relay's name, description, and other details. Set ownership of the configuration file: ```bash sudo chown strfry:strfry /etc/strfry.conf ``` ### Create Systemd Service Create a systemd service file for managing Strfry: ```bash sudo nano /etc/systemd/system/strfry.service ``` Add the following content: ```ini [Unit] Description=strfry relay service [Service] User=strfry ExecStart=/usr/local/bin/strfry relay Restart=on-failure RestartSec=5 ProtectHome=yes NoNewPrivileges=yes ProtectSystem=full LimitCORE=1000000000 [Install] WantedBy=multi-user.target ``` This systemd service configuration: - Runs Strfry as the dedicated strfry user - Automatically restarts the service if it fails - Implements security measures like `ProtectHome` and `NoNewPrivileges` - Sets resource limits appropriate for a relay Enable and start the service: ```bash sudo systemctl enable strfry.service sudo systemctl start strfry ``` Check the service status: ```bash sudo systemctl status strfry ``` ### Verify Relay is Running Test that your relay is running locally: ```bash curl localhost:7777 ``` You should see a message indicating that the Strfry relay is running. This confirms that Strfry is properly installed and configured before we proceed to set up TOR. ## Setting Up TOR Now let's make your relay accessible as a TOR hidden service. ### Install TOR Install TOR from the package repositories: ```bash sudo apt install -y tor ``` This installs the TOR daemon that will create and manage your hidden service. ### Configure TOR Edit the TOR configuration file: ```bash sudo nano /etc/tor/torrc ``` Scroll down to wherever you see a commented out part like this: ``` #HiddenServiceDir /var/lib/tor/hidden_service/ #HiddenServicePort 80 127.0.0.1:80 ``` Under those lines, add the following lines to set up a hidden service for your relay: ``` HiddenServiceDir /var/lib/tor/strfry-relay/ HiddenServicePort 80 127.0.0.1:7777 ``` This configuration: - Creates a hidden service directory at `/var/lib/tor/strfry-relay/` - Maps port 80 on your .onion address to port 7777 on your local machine - Keeps all traffic encrypted within the TOR network Create the directory for your hidden service: ```bash sudo mkdir -p /var/lib/tor/strfry-relay/ sudo chown debian-tor:debian-tor /var/lib/tor/strfry-relay/ sudo chmod 700 /var/lib/tor/strfry-relay/ ``` The strict permissions (700) are crucial for security as they ensure only the debian-tor user can access the directory containing your hidden service private keys. Restart TOR to apply changes: ```bash sudo systemctl restart tor ``` ## Making Your Relay Available on TOR ### Get Your Onion Address After restarting TOR, you can find your onion address: ```bash sudo cat /var/lib/tor/strfry-relay/hostname ``` This will output something like `abcdefghijklmnopqrstuvwxyz234567.onion`, which is your relay's unique .onion address. This is what you'll share with others to access your relay. ### Understanding Onion Addresses The .onion address is a special-format hostname that is automatically generated based on your hidden service's private key. Your users will need to use this address with the WebSocket protocol prefix to connect: `ws://youronionaddress.onion` ## Testing Your Setup ### Test with a Nostr Client The best way to test your relay is with an actual Nostr client that supports TOR: 1. Open your TOR browser 2. Go to your favorite client, either on clearnet or an onion service. - Check out [this list](https://github.com/0xtrr/onion-service-nostr-clients?tab=readme-ov-file#onion-service-nostr-clients) of nostr clients available over TOR. 3. Add your relay URL: `ws://youronionaddress.onion` to your relay list 4. Try posting a note and see if it appears on your relay - In some nostr clients, you can also click on a relay to get information about it like the relay name and description you set earlier in the stryfry config. If you're able to see the correct values for the name and the description, you were able to connect to the relay. - Some nostr clients also gives you a status on what relays a note was posted to, this could also give you an indication that your relay works as expected. Note that not all Nostr clients support TOR connections natively. Some may require additional configuration or use of TOR Browser. E.g. most mobile apps would most likely require a TOR proxy app running in the background (some have TOR support built in too). ## Maintenance and Security ### Regular Updates Keep your system, TOR, and relay updated: ```bash # Update system sudo apt update sudo apt upgrade -y # Update Strfry cd ~/strfry git pull git submodule update make -j2 sudo cp strfry /usr/local/bin sudo systemctl restart strfry # Verify TOR is still running properly sudo systemctl status tor ``` Regular updates are crucial for security, especially for TOR which may have security-critical updates. ### Database Management Strfry has built-in database management tools. Check the Strfry documentation for specific commands related to database maintenance, such as managing event retention and performing backups. ### Monitoring Logs To monitor your Strfry logs: ```bash sudo journalctl -u strfry -f ``` To check TOR logs: ```bash sudo journalctl -u tor -f ``` Monitoring logs helps you identify potential issues and understand how your relay is being used. ### Backup This is not a best practices guide on how to do backups. Preferably, backups should be stored either offline or on a different machine than your relay server. This is just a simple way on how to do it on the same server. ```bash # Stop the relay temporarily sudo systemctl stop strfry # Backup the database sudo cp -r /var/lib/strfry /path/to/backup/location # Restart the relay sudo systemctl start strfry ``` Back up your TOR hidden service private key. The private key is particularly sensitive as it defines your .onion address - losing it means losing your address permanently. If you do a backup of this, ensure that is stored in a safe place where no one else has access to it. ```bash sudo cp /var/lib/tor/strfry-relay/hs_ed25519_secret_key /path/to/secure/backup/location ``` ## Troubleshooting ### Relay Not Starting If your relay doesn't start: ```bash # Check logs sudo journalctl -u strfry -e # Verify configuration cat /etc/strfry.conf # Check permissions ls -la /var/lib/strfry ``` Common issues include: - Incorrect configuration format - Permission problems with the data directory - Port already in use (another service using port 7777) - Issues with setting the nofiles limit (setting it too big) ### TOR Hidden Service Not Working If your TOR hidden service is not accessible: ```bash # Check TOR logs sudo journalctl -u tor -e # Verify TOR is running sudo systemctl status tor # Check onion address sudo cat /var/lib/tor/strfry-relay/hostname # Verify TOR configuration sudo cat /etc/tor/torrc ``` Common TOR issues include: - Incorrect directory permissions - TOR service not running - Incorrect port mapping in torrc ### Testing Connectivity If you're having trouble connecting to your service: ```bash # Verify Strfry is listening locally sudo ss -tulpn | grep 7777 # Check that TOR is properly running sudo systemctl status tor # Test the local connection directly curl --include --no-buffer localhost:7777 ``` --- ## Privacy and Security Considerations Running a Nostr relay as a TOR hidden service provides several important privacy benefits: 1. **Network Privacy**: Traffic to your relay is encrypted and routed through the TOR network, making it difficult to determine who is connecting to your relay. 2. **Server Anonymity**: The physical location and IP address of your server are concealed, providing protection against denial-of-service attacks and other targeting. 3. **Censorship Resistance**: TOR hidden services are more resilient against censorship attempts, as they don't rely on the regular DNS system and can't be easily blocked. 4. **User Privacy**: Users connecting to your relay through TOR enjoy enhanced privacy, as their connections are also encrypted and anonymized. However, there are some important considerations: - TOR connections are typically slower than regular internet connections - Not all Nostr clients support TOR connections natively - Running a hidden service increases the importance of keeping your server secure --- Congratulations! You now have a Strfry Nostr relay running as a TOR hidden service. This setup provides a resilient, privacy-focused, and censorship-resistant communication channel that helps strengthen the Nostr network. For further customization and advanced configuration options, refer to the [Strfry documentation](https://github.com/hoytech/strfry). Consider sharing your relay's .onion address with the Nostr community to help grow the privacy-focused segment of the network! If you plan on providing a relay service that the public can use (either for free or paid for), consider adding it to [this list](https://github.com/0xtrr/onion-service-nostr-relays). Only add it if you plan to run a stable and available relay.
@ b2d670de:907f9d4a
2025-03-25 20:17:57This guide will walk you through setting up your own Strfry Nostr relay on a Debian/Ubuntu server and making it accessible exclusively as a TOR hidden service. By the end, you'll have a privacy-focused relay that operates entirely within the TOR network, enhancing both your privacy and that of your users. ## Table of Contents 1. Prerequisites 2. Initial Server Setup 3. Installing Strfry Nostr Relay 4. Configuring Your Relay 5. Setting Up TOR 6. Making Your Relay Available on TOR 7. Testing Your Setup] 8. Maintenance and Security 9. Troubleshooting ## Prerequisites - A Debian or Ubuntu server - Basic familiarity with command line operations (most steps are explained in detail) - Root or sudo access to your server ## Initial Server Setup First, let's make sure your server is properly set up and secured. ### Update Your System Connect to your server via SSH and update your system: ```bash sudo apt update sudo apt upgrade -y ``` ### Set Up a Basic Firewall Install and configure a basic firewall: ```bash sudo apt install ufw -y sudo ufw allow ssh sudo ufw enable ``` This allows SSH connections while blocking other ports for security. ## Installing Strfry Nostr Relay This guide includes the full range of steps needed to build and set up Strfry. It's simply based on the current version of the `DEPLOYMENT.md` document in the Strfry GitHub repository. If the build/setup process is changed in the repo, this document could get outdated. If so, please report to me that something is outdated and check for updated steps [here](https://github.com/hoytech/strfry/blob/master/docs/DEPLOYMENT.md). ### Install Dependencies First, let's install the necessary dependencies. Each package serves a specific purpose in building and running Strfry: ```bash sudo apt install -y git build-essential libyaml-perl libtemplate-perl libregexp-grammars-perl libssl-dev zlib1g-dev liblmdb-dev libflatbuffers-dev libsecp256k1-dev libzstd-dev ``` Here's why each dependency is needed: **Basic Development Tools:** - `git`: Version control system used to clone the Strfry repository and manage code updates - `build-essential`: Meta-package that includes compilers (gcc, g++), make, and other essential build tools **Perl Dependencies** (used for Strfry's build scripts): - `libyaml-perl`: Perl interface to parse YAML configuration files - `libtemplate-perl`: Template processing system used during the build process - `libregexp-grammars-perl`: Advanced regular expression handling for Perl scripts **Core Libraries for Strfry:** - `libssl-dev`: Development files for OpenSSL, used for secure connections and cryptographic operations - `zlib1g-dev`: Compression library that Strfry uses to reduce data size - `liblmdb-dev`: Lightning Memory-Mapped Database library, which Strfry uses for its high-performance database backend - `libflatbuffers-dev`: Memory-efficient serialization library for structured data - `libsecp256k1-dev`: Optimized C library for EC operations on curve secp256k1, essential for Nostr's cryptographic signatures - `libzstd-dev`: Fast real-time compression algorithm for efficient data storage and transmission ### Clone and Build Strfry Clone the Strfry repository: ```bash git clone https://github.com/hoytech/strfry.git cd strfry ``` Build Strfry: ```bash git submodule update --init make setup-golpe make -j2 # This uses 2 CPU cores. Adjust based on your server (e.g., -j4 for 4 cores) ``` This build process will take several minutes, especially on servers with limited CPU resources, so go get a coffee and post some great memes on nostr in the meantime. ### Install Strfry Install the Strfry binary to your system path: ```bash sudo cp strfry /usr/local/bin ``` This makes the `strfry` command available system-wide, allowing it to be executed from any directory and by any user with the appropriate permissions. ## Configuring Your Relay ### Create Strfry User Create a dedicated user for running Strfry. This enhances security by isolating the relay process: ```bash sudo useradd -M -s /usr/sbin/nologin strfry ``` The `-M` flag prevents creating a home directory, and `-s /usr/sbin/nologin` prevents anyone from logging in as this user. This is a security best practice for service accounts. ### Create Data Directory Create a directory for Strfry's data: ```bash sudo mkdir /var/lib/strfry sudo chown strfry:strfry /var/lib/strfry sudo chmod 755 /var/lib/strfry ``` This creates a dedicated directory for Strfry's database and sets the appropriate permissions so that only the strfry user can write to it. ### Configure Strfry Copy the sample configuration file: ```bash sudo cp strfry.conf /etc/strfry.conf ``` Edit the configuration file: ```bash sudo nano /etc/strfry.conf ``` Modify the database path: ``` # Find this line: db = "./strfry-db/" # Change it to: db = "/var/lib/strfry/" ``` Check your system's hard limit for file descriptors: ```bash ulimit -Hn ``` Update the `nofiles` setting in your configuration to match this value (or set to 0): ``` # Add or modify this line in the config (example if your limit is 524288): nofiles = 524288 ``` The `nofiles` setting determines how many open files Strfry can have simultaneously. Setting it to your system's hard limit (or 0 to use the system default) helps prevent "too many open files" errors if your relay becomes popular. You might also want to customize your relay's information in the config file. Look for the `info` section and update it with your relay's name, description, and other details. Set ownership of the configuration file: ```bash sudo chown strfry:strfry /etc/strfry.conf ``` ### Create Systemd Service Create a systemd service file for managing Strfry: ```bash sudo nano /etc/systemd/system/strfry.service ``` Add the following content: ```ini [Unit] Description=strfry relay service [Service] User=strfry ExecStart=/usr/local/bin/strfry relay Restart=on-failure RestartSec=5 ProtectHome=yes NoNewPrivileges=yes ProtectSystem=full LimitCORE=1000000000 [Install] WantedBy=multi-user.target ``` This systemd service configuration: - Runs Strfry as the dedicated strfry user - Automatically restarts the service if it fails - Implements security measures like `ProtectHome` and `NoNewPrivileges` - Sets resource limits appropriate for a relay Enable and start the service: ```bash sudo systemctl enable strfry.service sudo systemctl start strfry ``` Check the service status: ```bash sudo systemctl status strfry ``` ### Verify Relay is Running Test that your relay is running locally: ```bash curl localhost:7777 ``` You should see a message indicating that the Strfry relay is running. This confirms that Strfry is properly installed and configured before we proceed to set up TOR. ## Setting Up TOR Now let's make your relay accessible as a TOR hidden service. ### Install TOR Install TOR from the package repositories: ```bash sudo apt install -y tor ``` This installs the TOR daemon that will create and manage your hidden service. ### Configure TOR Edit the TOR configuration file: ```bash sudo nano /etc/tor/torrc ``` Scroll down to wherever you see a commented out part like this: ``` #HiddenServiceDir /var/lib/tor/hidden_service/ #HiddenServicePort 80 127.0.0.1:80 ``` Under those lines, add the following lines to set up a hidden service for your relay: ``` HiddenServiceDir /var/lib/tor/strfry-relay/ HiddenServicePort 80 127.0.0.1:7777 ``` This configuration: - Creates a hidden service directory at `/var/lib/tor/strfry-relay/` - Maps port 80 on your .onion address to port 7777 on your local machine - Keeps all traffic encrypted within the TOR network Create the directory for your hidden service: ```bash sudo mkdir -p /var/lib/tor/strfry-relay/ sudo chown debian-tor:debian-tor /var/lib/tor/strfry-relay/ sudo chmod 700 /var/lib/tor/strfry-relay/ ``` The strict permissions (700) are crucial for security as they ensure only the debian-tor user can access the directory containing your hidden service private keys. Restart TOR to apply changes: ```bash sudo systemctl restart tor ``` ## Making Your Relay Available on TOR ### Get Your Onion Address After restarting TOR, you can find your onion address: ```bash sudo cat /var/lib/tor/strfry-relay/hostname ``` This will output something like `abcdefghijklmnopqrstuvwxyz234567.onion`, which is your relay's unique .onion address. This is what you'll share with others to access your relay. ### Understanding Onion Addresses The .onion address is a special-format hostname that is automatically generated based on your hidden service's private key. Your users will need to use this address with the WebSocket protocol prefix to connect: `ws://youronionaddress.onion` ## Testing Your Setup ### Test with a Nostr Client The best way to test your relay is with an actual Nostr client that supports TOR: 1. Open your TOR browser 2. Go to your favorite client, either on clearnet or an onion service. - Check out [this list](https://github.com/0xtrr/onion-service-nostr-clients?tab=readme-ov-file#onion-service-nostr-clients) of nostr clients available over TOR. 3. Add your relay URL: `ws://youronionaddress.onion` to your relay list 4. Try posting a note and see if it appears on your relay - In some nostr clients, you can also click on a relay to get information about it like the relay name and description you set earlier in the stryfry config. If you're able to see the correct values for the name and the description, you were able to connect to the relay. - Some nostr clients also gives you a status on what relays a note was posted to, this could also give you an indication that your relay works as expected. Note that not all Nostr clients support TOR connections natively. Some may require additional configuration or use of TOR Browser. E.g. most mobile apps would most likely require a TOR proxy app running in the background (some have TOR support built in too). ## Maintenance and Security ### Regular Updates Keep your system, TOR, and relay updated: ```bash # Update system sudo apt update sudo apt upgrade -y # Update Strfry cd ~/strfry git pull git submodule update make -j2 sudo cp strfry /usr/local/bin sudo systemctl restart strfry # Verify TOR is still running properly sudo systemctl status tor ``` Regular updates are crucial for security, especially for TOR which may have security-critical updates. ### Database Management Strfry has built-in database management tools. Check the Strfry documentation for specific commands related to database maintenance, such as managing event retention and performing backups. ### Monitoring Logs To monitor your Strfry logs: ```bash sudo journalctl -u strfry -f ``` To check TOR logs: ```bash sudo journalctl -u tor -f ``` Monitoring logs helps you identify potential issues and understand how your relay is being used. ### Backup This is not a best practices guide on how to do backups. Preferably, backups should be stored either offline or on a different machine than your relay server. This is just a simple way on how to do it on the same server. ```bash # Stop the relay temporarily sudo systemctl stop strfry # Backup the database sudo cp -r /var/lib/strfry /path/to/backup/location # Restart the relay sudo systemctl start strfry ``` Back up your TOR hidden service private key. The private key is particularly sensitive as it defines your .onion address - losing it means losing your address permanently. If you do a backup of this, ensure that is stored in a safe place where no one else has access to it. ```bash sudo cp /var/lib/tor/strfry-relay/hs_ed25519_secret_key /path/to/secure/backup/location ``` ## Troubleshooting ### Relay Not Starting If your relay doesn't start: ```bash # Check logs sudo journalctl -u strfry -e # Verify configuration cat /etc/strfry.conf # Check permissions ls -la /var/lib/strfry ``` Common issues include: - Incorrect configuration format - Permission problems with the data directory - Port already in use (another service using port 7777) - Issues with setting the nofiles limit (setting it too big) ### TOR Hidden Service Not Working If your TOR hidden service is not accessible: ```bash # Check TOR logs sudo journalctl -u tor -e # Verify TOR is running sudo systemctl status tor # Check onion address sudo cat /var/lib/tor/strfry-relay/hostname # Verify TOR configuration sudo cat /etc/tor/torrc ``` Common TOR issues include: - Incorrect directory permissions - TOR service not running - Incorrect port mapping in torrc ### Testing Connectivity If you're having trouble connecting to your service: ```bash # Verify Strfry is listening locally sudo ss -tulpn | grep 7777 # Check that TOR is properly running sudo systemctl status tor # Test the local connection directly curl --include --no-buffer localhost:7777 ``` --- ## Privacy and Security Considerations Running a Nostr relay as a TOR hidden service provides several important privacy benefits: 1. **Network Privacy**: Traffic to your relay is encrypted and routed through the TOR network, making it difficult to determine who is connecting to your relay. 2. **Server Anonymity**: The physical location and IP address of your server are concealed, providing protection against denial-of-service attacks and other targeting. 3. **Censorship Resistance**: TOR hidden services are more resilient against censorship attempts, as they don't rely on the regular DNS system and can't be easily blocked. 4. **User Privacy**: Users connecting to your relay through TOR enjoy enhanced privacy, as their connections are also encrypted and anonymized. However, there are some important considerations: - TOR connections are typically slower than regular internet connections - Not all Nostr clients support TOR connections natively - Running a hidden service increases the importance of keeping your server secure --- Congratulations! You now have a Strfry Nostr relay running as a TOR hidden service. This setup provides a resilient, privacy-focused, and censorship-resistant communication channel that helps strengthen the Nostr network. For further customization and advanced configuration options, refer to the [Strfry documentation](https://github.com/hoytech/strfry). Consider sharing your relay's .onion address with the Nostr community to help grow the privacy-focused segment of the network! If you plan on providing a relay service that the public can use (either for free or paid for), consider adding it to [this list](https://github.com/0xtrr/onion-service-nostr-relays). Only add it if you plan to run a stable and available relay. @ bc52210b:20bfc6de
2025-03-25 20:17:22CISA, or Cross-Input Signature Aggregation, is a technique in Bitcoin that allows multiple signatures from different inputs in a transaction to be combined into a single, aggregated signature. This is a big deal because Bitcoin transactions often involve multiple inputs (e.g., spending from different wallet outputs), each requiring its own signature. Normally, these signatures take up space individually, but CISA compresses them into one, making transactions more efficient. This magic is possible thanks to the linearity property of Schnorr signatures, a type of digital signature introduced to Bitcoin with the Taproot upgrade. Unlike the older ECDSA signatures, Schnorr signatures have mathematical properties that allow multiple signatures to be added together into a single valid signature. Think of it like combining multiple handwritten signatures into one super-signature that still proves everyone signed off! Fun Fact: CISA was considered for inclusion in Taproot but was left out to keep the upgrade simple and manageable. Adding CISA would’ve made Taproot more complex, so the developers hit pause on it—for now. --- **CISA vs. Key Aggregation (MuSig, FROST): Don’t Get Confused!** Before we go deeper, let’s clear up a common mix-up: CISA is not the same as protocols like MuSig or FROST. Here’s why: * Signature Aggregation (CISA): Combines multiple signatures into one, each potentially tied to different public keys and messages (e.g., different transaction inputs). * Key Aggregation (MuSig, FROST): Combines multiple public keys into a single aggregated public key, then generates one signature for that key. **Key Differences:** 1. What’s Aggregated? * CISA: Aggregates signatures. * Key Aggregation: Aggregates public keys. 2. What the Verifier Needs * CISA: The verifier needs all individual public keys and their corresponding messages to check the aggregated signature. * Key Aggregation: The verifier only needs the single aggregated public key and one message. 3. When It Happens * CISA: Used during transaction signing, when inputs are being combined into a transaction. * MuSig: Used during address creation, setting up a multi-signature (multisig) address that multiple parties control. So, CISA is about shrinking signature data in a transaction, while MuSig/FROST are about simplifying multisig setups. Different tools, different jobs! --- **Two Flavors of CISA: Half-Agg and Full-Agg** CISA comes in two modes: * Full Aggregation (Full-Agg): Interactive, meaning signers need to collaborate during the signing process. (We’ll skip the details here since the query focuses on Half-Agg.) * Half Aggregation (Half-Agg): Non-interactive, meaning signers can work independently, and someone else can combine the signatures later. Since the query includes “CISA Part 2: Half Signature Aggregation,” let’s zoom in on Half-Agg. --- **Half Signature Aggregation (Half-Agg) Explained** **How It Works** Half-Agg is a non-interactive way to aggregate Schnorr signatures. Here’s the process: 1. Independent Signing: Each signer creates their own Schnorr signature for their input, without needing to talk to the other signers. 2. Aggregation Step: An aggregator (could be anyone, like a wallet or node) takes all these signatures and combines them into one aggregated signature. A Schnorr signature has two parts: * R: A random point (32 bytes). * s: A scalar value (32 bytes). In Half-Agg: * The R values from each signature are kept separate (one per input). * The s values from all signatures are combined into a single s value. **Why It Saves Space (~50%)** Let’s break down the size savings with some math: Before Aggregation: * Each Schnorr signature = 64 bytes (32 for R + 32 for s). * For n inputs: n × 64 bytes. After Half-Agg: * Keep n R values (32 bytes each) = 32 × n bytes. * Combine all s values into one = 32 bytes. * Total size: 32 × n + 32 bytes. Comparison: * Original: 64n bytes. * Half-Agg: 32n + 32 bytes. * For large n, the “+32” becomes small compared to 32n, so it’s roughly 32n, which is half of 64n. Hence, ~50% savings! **Real-World Impact:** Based on recent Bitcoin usage, Half-Agg could save: * ~19.3% in space (reducing transaction size). * ~6.9% in fees (since fees depend on transaction size). This assumes no major changes in how people use Bitcoin post-CISA. --- **Applications of Half-Agg** Half-Agg isn’t just a cool idea—it has practical uses: 1. Transaction-wide Aggregation * Combine all signatures within a single transaction. * Result: Smaller transactions, lower fees. 2. Block-wide Aggregation * Combine signatures across all transactions in a Bitcoin block. * Result: Even bigger space savings at the blockchain level. 3. Off-chain Protocols / P2P * Use Half-Agg in systems like Lightning Network gossip messages. * Benefit: Efficiency without needing miners or a Bitcoin soft fork. --- **Challenges with Half-Agg** While Half-Agg sounds awesome, it’s not without hurdles, especially at the block level: 1. Breaking Adaptor Signatures * Adaptor signatures are special signatures used in protocols like Discreet Log Contracts (DLCs) or atomic swaps. They tie a signature to revealing a secret, ensuring fair exchanges. * Aggregating signatures across a block might mess up these protocols, as the individual signatures get blended together, potentially losing the properties adaptor signatures rely on. 2. Impact on Reorg Recovery * In Bitcoin, a reorganization (reorg) happens when the blockchain switches to a different chain of blocks. Transactions from the old chain need to be rebroadcast or reprocessed. * If signatures are aggregated at the block level, it could complicate extracting individual transactions and their signatures during a reorg, slowing down recovery. These challenges mean Half-Agg needs careful design, especially for block-wide use. --- **Wrapping Up** CISA is a clever way to make Bitcoin transactions more efficient by aggregating multiple Schnorr signatures into one, thanks to their linearity property. Half-Agg, the non-interactive mode, lets signers work independently, cutting signature size by about 50% (to 32n + 32 bytes from 64n bytes). It could save ~19.3% in space and ~6.9% in fees, with uses ranging from single transactions to entire blocks or off-chain systems like Lightning. But watch out—block-wide Half-Agg could trip up adaptor signatures and reorg recovery, so it’s not a slam dunk yet. Still, it’s a promising tool for a leaner, cheaper Bitcoin future!
@ bc52210b:20bfc6de
2025-03-25 20:17:22CISA, or Cross-Input Signature Aggregation, is a technique in Bitcoin that allows multiple signatures from different inputs in a transaction to be combined into a single, aggregated signature. This is a big deal because Bitcoin transactions often involve multiple inputs (e.g., spending from different wallet outputs), each requiring its own signature. Normally, these signatures take up space individually, but CISA compresses them into one, making transactions more efficient. This magic is possible thanks to the linearity property of Schnorr signatures, a type of digital signature introduced to Bitcoin with the Taproot upgrade. Unlike the older ECDSA signatures, Schnorr signatures have mathematical properties that allow multiple signatures to be added together into a single valid signature. Think of it like combining multiple handwritten signatures into one super-signature that still proves everyone signed off! Fun Fact: CISA was considered for inclusion in Taproot but was left out to keep the upgrade simple and manageable. Adding CISA would’ve made Taproot more complex, so the developers hit pause on it—for now. --- **CISA vs. Key Aggregation (MuSig, FROST): Don’t Get Confused!** Before we go deeper, let’s clear up a common mix-up: CISA is not the same as protocols like MuSig or FROST. Here’s why: * Signature Aggregation (CISA): Combines multiple signatures into one, each potentially tied to different public keys and messages (e.g., different transaction inputs). * Key Aggregation (MuSig, FROST): Combines multiple public keys into a single aggregated public key, then generates one signature for that key. **Key Differences:** 1. What’s Aggregated? * CISA: Aggregates signatures. * Key Aggregation: Aggregates public keys. 2. What the Verifier Needs * CISA: The verifier needs all individual public keys and their corresponding messages to check the aggregated signature. * Key Aggregation: The verifier only needs the single aggregated public key and one message. 3. When It Happens * CISA: Used during transaction signing, when inputs are being combined into a transaction. * MuSig: Used during address creation, setting up a multi-signature (multisig) address that multiple parties control. So, CISA is about shrinking signature data in a transaction, while MuSig/FROST are about simplifying multisig setups. Different tools, different jobs! --- **Two Flavors of CISA: Half-Agg and Full-Agg** CISA comes in two modes: * Full Aggregation (Full-Agg): Interactive, meaning signers need to collaborate during the signing process. (We’ll skip the details here since the query focuses on Half-Agg.) * Half Aggregation (Half-Agg): Non-interactive, meaning signers can work independently, and someone else can combine the signatures later. Since the query includes “CISA Part 2: Half Signature Aggregation,” let’s zoom in on Half-Agg. --- **Half Signature Aggregation (Half-Agg) Explained** **How It Works** Half-Agg is a non-interactive way to aggregate Schnorr signatures. Here’s the process: 1. Independent Signing: Each signer creates their own Schnorr signature for their input, without needing to talk to the other signers. 2. Aggregation Step: An aggregator (could be anyone, like a wallet or node) takes all these signatures and combines them into one aggregated signature. A Schnorr signature has two parts: * R: A random point (32 bytes). * s: A scalar value (32 bytes). In Half-Agg: * The R values from each signature are kept separate (one per input). * The s values from all signatures are combined into a single s value. **Why It Saves Space (~50%)** Let’s break down the size savings with some math: Before Aggregation: * Each Schnorr signature = 64 bytes (32 for R + 32 for s). * For n inputs: n × 64 bytes. After Half-Agg: * Keep n R values (32 bytes each) = 32 × n bytes. * Combine all s values into one = 32 bytes. * Total size: 32 × n + 32 bytes. Comparison: * Original: 64n bytes. * Half-Agg: 32n + 32 bytes. * For large n, the “+32” becomes small compared to 32n, so it’s roughly 32n, which is half of 64n. Hence, ~50% savings! **Real-World Impact:** Based on recent Bitcoin usage, Half-Agg could save: * ~19.3% in space (reducing transaction size). * ~6.9% in fees (since fees depend on transaction size). This assumes no major changes in how people use Bitcoin post-CISA. --- **Applications of Half-Agg** Half-Agg isn’t just a cool idea—it has practical uses: 1. Transaction-wide Aggregation * Combine all signatures within a single transaction. * Result: Smaller transactions, lower fees. 2. Block-wide Aggregation * Combine signatures across all transactions in a Bitcoin block. * Result: Even bigger space savings at the blockchain level. 3. Off-chain Protocols / P2P * Use Half-Agg in systems like Lightning Network gossip messages. * Benefit: Efficiency without needing miners or a Bitcoin soft fork. --- **Challenges with Half-Agg** While Half-Agg sounds awesome, it’s not without hurdles, especially at the block level: 1. Breaking Adaptor Signatures * Adaptor signatures are special signatures used in protocols like Discreet Log Contracts (DLCs) or atomic swaps. They tie a signature to revealing a secret, ensuring fair exchanges. * Aggregating signatures across a block might mess up these protocols, as the individual signatures get blended together, potentially losing the properties adaptor signatures rely on. 2. Impact on Reorg Recovery * In Bitcoin, a reorganization (reorg) happens when the blockchain switches to a different chain of blocks. Transactions from the old chain need to be rebroadcast or reprocessed. * If signatures are aggregated at the block level, it could complicate extracting individual transactions and their signatures during a reorg, slowing down recovery. These challenges mean Half-Agg needs careful design, especially for block-wide use. --- **Wrapping Up** CISA is a clever way to make Bitcoin transactions more efficient by aggregating multiple Schnorr signatures into one, thanks to their linearity property. Half-Agg, the non-interactive mode, lets signers work independently, cutting signature size by about 50% (to 32n + 32 bytes from 64n bytes). It could save ~19.3% in space and ~6.9% in fees, with uses ranging from single transactions to entire blocks or off-chain systems like Lightning. But watch out—block-wide Half-Agg could trip up adaptor signatures and reorg recovery, so it’s not a slam dunk yet. Still, it’s a promising tool for a leaner, cheaper Bitcoin future! @ b17fccdf:b7211155
2025-03-25 11:23:36Si vives en España, quizás hayas notado que no puedes acceder a ciertas páginas webs durante los fines de semana o en algunos días entre semana, entre ellas, la [guía de MiniBolt](https://minbolt.info/). Esto tiene una **razón**, por supuesto una **solución**, además de una **conclusión**. Sin entrar en demasiados detalles: ## La razón El **bloqueo a Cloudflare**, implementado desde hace casi dos meses por operadores de Internet (ISPs) en España (como Movistar, O2, DIGI, Pepephone, entre otros), se basa en una [orden judicial](https://www.poderjudicial.es/search/AN/openDocument/3c85bed480cbb1daa0a8778d75e36f0d/20221004) emitida tras una demanda de LALIGA (Fútbol). Esta medida busca combatir la piratería en España, un problema que afecta directamente a dicha organización. Aunque la intención original era restringir el acceso a dominios específicos que difundieran dicho contenido, Cloudflare emplea el protocolo [ECH](https://developers.cloudflare.com/ssl/edge-certificates/ech) (Encrypted Client Hello), que oculta el nombre del dominio, el cual antes se transmitía en texto plano durante el proceso de establecimiento de una conexión TLS. Esta medida dificulta que las operadoras analicen el tráfico para aplicar **bloqueos basados en dominios**, lo que les obliga a recurrir a **bloqueos más amplios por IP o rangos de IP** para cumplir con la orden judicial. Esta práctica tiene **consecuencias graves**, que han sido completamente ignoradas por quienes la ejecutan. Es bien sabido que una infraestructura de IP puede alojar numerosos dominios, tanto legítimos como no legítimos. La falta de un "ajuste fino" en los bloqueos provoca un **perjuicio para terceros**, **restringiendo el acceso a muchos dominios legítimos** que no tiene relación alguna con actividades ilícitas, pero que comparten las mismas IPs de Cloudflare con dominios cuestionables. Este es el caso de la [web de MiniBolt](https://minibolt.minibolt.info) y su dominio `minibolt.info`, los cuales **utilizan Cloudflare como proxy** para aprovechar las medidas de **seguridad, privacidad, optimización y servicios** adicionales que la plataforma ofrece de forma gratuita. Si bien este bloqueo parece ser temporal (al menos durante la temporada 24/25 de fútbol, hasta finales de mayo), es posible que se reactive con el inicio de la nueva temporada.  ## La solución Obviamente, **MiniBolt no dejará de usar Cloudflare** como proxy por esta razón. Por lo que a continuación se exponen algunas medidas que como usuario puedes tomar para **evitar esta restricción** y poder acceder: **~>** Utiliza **una VPN**: Existen varias soluciones de proveedores de VPN, ordenadas según su reputación en privacidad: - [IVPN](https://www.ivpn.net/es/) - [Mullvad VPN](https://mullvad.net/es/vpn) - [Proton VPN](https://protonvpn.com/es-es) (**gratis**) - [Obscura VPN](https://obscura.net/) (**solo para macOS**) - [Cloudfare WARP](https://developers.cloudflare.com/cloudflare-one/connections/connect-devices/warp/download-warp/) (**gratis**) + permite utilizar el modo proxy local para enrutar solo la navegación, debes utilizar la opción "WARP a través de proxy local" siguiendo estos pasos: 1. Inicia Cloudflare WARP y dentro de la pequeña interfaz haz click en la rueda dentada abajo a la derecha > "Preferencias" > "Avanzado" > "Configurar el modo proxy" 2. Marca la casilla "Habilite el modo proxy en este dispositivo" 3. Elige un "Puerto de escucha de proxy" entre 0-65535. ej: 1080, haz click en "Aceptar" y cierra la ventana de preferencias 4. Accede de nuevo a Cloudflare WARP y pulsa sobre el switch para habilitar el servicio. 3. Ahora debes apuntar el proxy del navegador a Cloudflare WARP, la configuración del navegador es similar a [esta](https://minibolt.minibolt.info/system/system/privacy#example-from-firefox) para el caso de navegadores basados en Firefox. Una vez hecho, deberías poder acceder a la [guía de MiniBolt](https://minibolt.minibolt.info/) sin problemas. Si tienes dudas, déjalas en comentarios e intentaré resolverlas. Más info [AQUÍ](https://bandaancha.eu/articulos/como-saltarse-bloqueo-webs-warp-vpn-9958).  **~>** [**Proxifica tu navegador para usar la red de Tor**](https://minibolt.minibolt.info/system/system/privacy#ssh-remote-access-through-tor), o utiliza el [**navegador oficial de Tor**](https://www.torproject.org/es/download/) (recomendado).  ## La conclusión Estos hechos ponen en tela de juicio los principios fundamentales de la neutralidad de la red, pilares esenciales de la [Declaración de Independencia del Ciberespacio](https://es.wikisource.org/wiki/Declaraci%C3%B3n_de_independencia_del_ciberespacio) que defiende un internet libre, sin restricciones ni censura. Dichos principios se han visto quebrantados sin precedentes en este país, confirmando que ese futuro distópico que muchos negaban, ya es una realidad. Es momento de actuar y estar preparados: debemos **impulsar el desarrollo y la difusión** de las **herramientas anticensura** que tenemos a nuestro alcance, protegiendo así la **libertad digital** y asegurando un acceso equitativo a la información para todos Este compromiso es uno de los **pilares fundamentales de MiniBolt,** lo que convierte este desafío en una oportunidad para poner a prueba las **soluciones anticensura** [ya disponibles](https://minibolt.minibolt.info/bonus-guides/system/tor-services), así como **las que están en camino**. ¡Censúrame si puedes, legislador! ¡La lucha por la privacidad y la libertad en Internet ya está en marcha!  --- Fuentes: * https://bandaancha.eu/articulos/movistar-o2-deja-clientes-sin-acceso-11239 * https://bandaancha.eu/articulos/esta-nueva-sentencia-autoriza-bloqueos-11257 * https://bandaancha.eu/articulos/como-saltarse-bloqueo-webs-warp-vpn-9958 * https://bandaancha.eu/articulos/como-activar-ech-chrome-acceder-webs-10689 * https://comunidad.movistar.es/t5/Soporte-Fibra-y-ADSL/Problema-con-web-que-usan-Cloudflare/td-p/5218007
@ b17fccdf:b7211155
2025-03-25 11:23:36Si vives en España, quizás hayas notado que no puedes acceder a ciertas páginas webs durante los fines de semana o en algunos días entre semana, entre ellas, la [guía de MiniBolt](https://minbolt.info/). Esto tiene una **razón**, por supuesto una **solución**, además de una **conclusión**. Sin entrar en demasiados detalles: ## La razón El **bloqueo a Cloudflare**, implementado desde hace casi dos meses por operadores de Internet (ISPs) en España (como Movistar, O2, DIGI, Pepephone, entre otros), se basa en una [orden judicial](https://www.poderjudicial.es/search/AN/openDocument/3c85bed480cbb1daa0a8778d75e36f0d/20221004) emitida tras una demanda de LALIGA (Fútbol). Esta medida busca combatir la piratería en España, un problema que afecta directamente a dicha organización. Aunque la intención original era restringir el acceso a dominios específicos que difundieran dicho contenido, Cloudflare emplea el protocolo [ECH](https://developers.cloudflare.com/ssl/edge-certificates/ech) (Encrypted Client Hello), que oculta el nombre del dominio, el cual antes se transmitía en texto plano durante el proceso de establecimiento de una conexión TLS. Esta medida dificulta que las operadoras analicen el tráfico para aplicar **bloqueos basados en dominios**, lo que les obliga a recurrir a **bloqueos más amplios por IP o rangos de IP** para cumplir con la orden judicial. Esta práctica tiene **consecuencias graves**, que han sido completamente ignoradas por quienes la ejecutan. Es bien sabido que una infraestructura de IP puede alojar numerosos dominios, tanto legítimos como no legítimos. La falta de un "ajuste fino" en los bloqueos provoca un **perjuicio para terceros**, **restringiendo el acceso a muchos dominios legítimos** que no tiene relación alguna con actividades ilícitas, pero que comparten las mismas IPs de Cloudflare con dominios cuestionables. Este es el caso de la [web de MiniBolt](https://minibolt.minibolt.info) y su dominio `minibolt.info`, los cuales **utilizan Cloudflare como proxy** para aprovechar las medidas de **seguridad, privacidad, optimización y servicios** adicionales que la plataforma ofrece de forma gratuita. Si bien este bloqueo parece ser temporal (al menos durante la temporada 24/25 de fútbol, hasta finales de mayo), es posible que se reactive con el inicio de la nueva temporada.  ## La solución Obviamente, **MiniBolt no dejará de usar Cloudflare** como proxy por esta razón. Por lo que a continuación se exponen algunas medidas que como usuario puedes tomar para **evitar esta restricción** y poder acceder: **~>** Utiliza **una VPN**: Existen varias soluciones de proveedores de VPN, ordenadas según su reputación en privacidad: - [IVPN](https://www.ivpn.net/es/) - [Mullvad VPN](https://mullvad.net/es/vpn) - [Proton VPN](https://protonvpn.com/es-es) (**gratis**) - [Obscura VPN](https://obscura.net/) (**solo para macOS**) - [Cloudfare WARP](https://developers.cloudflare.com/cloudflare-one/connections/connect-devices/warp/download-warp/) (**gratis**) + permite utilizar el modo proxy local para enrutar solo la navegación, debes utilizar la opción "WARP a través de proxy local" siguiendo estos pasos: 1. Inicia Cloudflare WARP y dentro de la pequeña interfaz haz click en la rueda dentada abajo a la derecha > "Preferencias" > "Avanzado" > "Configurar el modo proxy" 2. Marca la casilla "Habilite el modo proxy en este dispositivo" 3. Elige un "Puerto de escucha de proxy" entre 0-65535. ej: 1080, haz click en "Aceptar" y cierra la ventana de preferencias 4. Accede de nuevo a Cloudflare WARP y pulsa sobre el switch para habilitar el servicio. 3. Ahora debes apuntar el proxy del navegador a Cloudflare WARP, la configuración del navegador es similar a [esta](https://minibolt.minibolt.info/system/system/privacy#example-from-firefox) para el caso de navegadores basados en Firefox. Una vez hecho, deberías poder acceder a la [guía de MiniBolt](https://minibolt.minibolt.info/) sin problemas. Si tienes dudas, déjalas en comentarios e intentaré resolverlas. Más info [AQUÍ](https://bandaancha.eu/articulos/como-saltarse-bloqueo-webs-warp-vpn-9958).  **~>** [**Proxifica tu navegador para usar la red de Tor**](https://minibolt.minibolt.info/system/system/privacy#ssh-remote-access-through-tor), o utiliza el [**navegador oficial de Tor**](https://www.torproject.org/es/download/) (recomendado).  ## La conclusión Estos hechos ponen en tela de juicio los principios fundamentales de la neutralidad de la red, pilares esenciales de la [Declaración de Independencia del Ciberespacio](https://es.wikisource.org/wiki/Declaraci%C3%B3n_de_independencia_del_ciberespacio) que defiende un internet libre, sin restricciones ni censura. Dichos principios se han visto quebrantados sin precedentes en este país, confirmando que ese futuro distópico que muchos negaban, ya es una realidad. Es momento de actuar y estar preparados: debemos **impulsar el desarrollo y la difusión** de las **herramientas anticensura** que tenemos a nuestro alcance, protegiendo así la **libertad digital** y asegurando un acceso equitativo a la información para todos Este compromiso es uno de los **pilares fundamentales de MiniBolt,** lo que convierte este desafío en una oportunidad para poner a prueba las **soluciones anticensura** [ya disponibles](https://minibolt.minibolt.info/bonus-guides/system/tor-services), así como **las que están en camino**. ¡Censúrame si puedes, legislador! ¡La lucha por la privacidad y la libertad en Internet ya está en marcha!  --- Fuentes: * https://bandaancha.eu/articulos/movistar-o2-deja-clientes-sin-acceso-11239 * https://bandaancha.eu/articulos/esta-nueva-sentencia-autoriza-bloqueos-11257 * https://bandaancha.eu/articulos/como-saltarse-bloqueo-webs-warp-vpn-9958 * https://bandaancha.eu/articulos/como-activar-ech-chrome-acceder-webs-10689 * https://comunidad.movistar.es/t5/Soporte-Fibra-y-ADSL/Problema-con-web-que-usan-Cloudflare/td-p/5218007 @ 3b7fc823:e194354f
2025-03-23 03:54:16A quick guide for the less than technical savvy to set up their very own free private tor enabled email using Onionmail. Privacy is for everyone, not just the super cyber nerds. Onion Mail is an anonymous POP3/SMTP email server program hosted by various people on the internet. You can visit this site and read the details: https://en.onionmail.info/ 1. Download Tor Browser First, if you don't already, go download Tor Browser. You are going to need it. https://www.torproject.org/ 2. Sign Up Using Tor browser go to the directory page (https://onionmail.info/directory.html) choose one of the servers and sign up for an account. I say sign up but it is just choosing a user name you want to go before the @xyz.onion email address and solving a captcha. 3. Account information Once you are done signing up an Account information page will pop up. **MAKE SURE YOU SAVE THIS!!!** It has your address and passwords (for sending and receiving email) that you will need. If you lose them then you are shit out of luck. 4. Install an Email Client You can use Claws Mail, Neomutt, or whatever, but for this example, we will be using Thunderbird. a. Download Thunderbird email client b. The easy setup popup page that wants your name, email, and password isn't going to like your user@xyz.onion address. Just enter something that looks like a regular email address such as name@example.com and the **Configure Manually**option will appear below. Click that. 5. Configure Incoming (POP3) Server Under Incoming Server: Protocol: POP3 Server or Hostname: xyz.onion (whatever your account info says) Port: 110 Security: STARTTLS Authentication: Normal password Username: (your username) Password: (POP3 password). 6. Configure Outgoing (SMTP) Server Under Outgoing Server: Server or Hostname: xyz.onion (whatever your account info says) Port: 25 Security: STARTTLS Authentication: Normal password Username: (your username) Password: (SMTP password). 7. Click on email at the top and change your address if you had to use a spoof one to get the configure manually to pop up. 8. Configure Proxy a. Click the **gear icon** on the bottom left for settings. Scroll all the way down to **Network & Disk Space**. Click the **settings button** next to **Connection. Configure how Thunderbird connects to the internet**. b. Select **Manual Proxy Configuration**. For **SOCKS Host** enter **127.0.0.1** and enter port **9050**. (if you are running this through a VM the port may be different) c. Now check the box for **SOCKS5** and then **Proxy DNS when using SOCKS5** down at the bottom. Click OK 9. Check Email For thunderbird to reach the onion mail server it has to be connected to tor. Depending on your local setup, it might be fine as is or you might have to have tor browser open in the background. Click on **inbox** and then the **little cloud icon** with the down arrow to check mail. 10. Security Exception Thunderbird is not going to like that the onion mail server security certificate is self signed. A popup **Add Security Exception** will appear. Click **Confirm Security Exception**. You are done. Enjoy your new private email service. **REMEMBER: The server can read your emails unless they are encrypted. Go into account settings. Look down and click End-toEnd Encryption. Then add your OpenPGP key or open your OpenPGP Key Manager (you might have to download one if you don't already have one) and generate a new key for this account.**
@ 3b7fc823:e194354f
2025-03-23 03:54:16A quick guide for the less than technical savvy to set up their very own free private tor enabled email using Onionmail. Privacy is for everyone, not just the super cyber nerds. Onion Mail is an anonymous POP3/SMTP email server program hosted by various people on the internet. You can visit this site and read the details: https://en.onionmail.info/ 1. Download Tor Browser First, if you don't already, go download Tor Browser. You are going to need it. https://www.torproject.org/ 2. Sign Up Using Tor browser go to the directory page (https://onionmail.info/directory.html) choose one of the servers and sign up for an account. I say sign up but it is just choosing a user name you want to go before the @xyz.onion email address and solving a captcha. 3. Account information Once you are done signing up an Account information page will pop up. **MAKE SURE YOU SAVE THIS!!!** It has your address and passwords (for sending and receiving email) that you will need. If you lose them then you are shit out of luck. 4. Install an Email Client You can use Claws Mail, Neomutt, or whatever, but for this example, we will be using Thunderbird. a. Download Thunderbird email client b. The easy setup popup page that wants your name, email, and password isn't going to like your user@xyz.onion address. Just enter something that looks like a regular email address such as name@example.com and the **Configure Manually**option will appear below. Click that. 5. Configure Incoming (POP3) Server Under Incoming Server: Protocol: POP3 Server or Hostname: xyz.onion (whatever your account info says) Port: 110 Security: STARTTLS Authentication: Normal password Username: (your username) Password: (POP3 password). 6. Configure Outgoing (SMTP) Server Under Outgoing Server: Server or Hostname: xyz.onion (whatever your account info says) Port: 25 Security: STARTTLS Authentication: Normal password Username: (your username) Password: (SMTP password). 7. Click on email at the top and change your address if you had to use a spoof one to get the configure manually to pop up. 8. Configure Proxy a. Click the **gear icon** on the bottom left for settings. Scroll all the way down to **Network & Disk Space**. Click the **settings button** next to **Connection. Configure how Thunderbird connects to the internet**. b. Select **Manual Proxy Configuration**. For **SOCKS Host** enter **127.0.0.1** and enter port **9050**. (if you are running this through a VM the port may be different) c. Now check the box for **SOCKS5** and then **Proxy DNS when using SOCKS5** down at the bottom. Click OK 9. Check Email For thunderbird to reach the onion mail server it has to be connected to tor. Depending on your local setup, it might be fine as is or you might have to have tor browser open in the background. Click on **inbox** and then the **little cloud icon** with the down arrow to check mail. 10. Security Exception Thunderbird is not going to like that the onion mail server security certificate is self signed. A popup **Add Security Exception** will appear. Click **Confirm Security Exception**. You are done. Enjoy your new private email service. **REMEMBER: The server can read your emails unless they are encrypted. Go into account settings. Look down and click End-toEnd Encryption. Then add your OpenPGP key or open your OpenPGP Key Manager (you might have to download one if you don't already have one) and generate a new key for this account.** @ 21335073:a244b1ad
2025-03-18 20:47:50**Warning: This piece contains a conversation about difficult topics. Please proceed with caution.** TL;DR please educate your children about online safety. Julian Assange wrote in his 2012 book *Cypherpunks*, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense. This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning. When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little. I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?” I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well. I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread. I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard. I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it. The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust. Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this. I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place. What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method. It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code. They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened. I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road. So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally. Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb. I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback. Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed. That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone. To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all. I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society. I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this. On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government. I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories. There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc. Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind. Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now. There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers? I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity. I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place. My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors. My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline. The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online. I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers. So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation? When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that. I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic. If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations. I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process. **Course:** - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children. The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward? I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone. Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability. The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime. This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful. This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens. In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions. I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
@ 21335073:a244b1ad
2025-03-18 20:47:50**Warning: This piece contains a conversation about difficult topics. Please proceed with caution.** TL;DR please educate your children about online safety. Julian Assange wrote in his 2012 book *Cypherpunks*, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense. This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning. When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little. I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?” I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well. I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread. I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard. I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it. The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust. Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this. I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place. What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method. It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code. They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened. I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road. So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally. Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb. I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback. Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed. That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone. To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all. I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society. I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this. On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government. I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories. There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc. Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind. Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now. There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers? I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity. I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place. My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors. My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline. The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online. I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers. So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation? When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that. I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic. If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations. I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process. **Course:** - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children. The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward? I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone. Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability. The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime. This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful. This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens. In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions. I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation. @ 57d1a264:69f1fee1
2025-04-08 06:39:52 originally posted at https://stacker.news/items/937791
@ 57d1a264:69f1fee1
2025-04-08 06:39:52 originally posted at https://stacker.news/items/937791 @ c066aac5:6a41a034
2025-04-05 16:58:58I’m drawn to extremities in art. The louder, the bolder, the more outrageous, the better. Bold art takes me out of the mundane into a whole new world where anything and everything is possible. Having grown up in the safety of the suburban midwest, I was a bit of a rebellious soul in search of the satiation that only came from the consumption of the outrageous. My inclination to find bold art draws me to NOSTR, because I believe NOSTR can be the place where the next generation of artistic pioneers go to express themselves. I also believe that as much as we are able, were should invite them to come create here. # My Background: A Small Side Story  My father was a professional gamer in the 80s, back when there was no money or glory in the avocation. He did get a bit of spotlight though after the fact: in the mid 2000’s there were a few parties making documentaries about that era of gaming as well as current arcade events (namely 2007’s*Chasing Ghosts*and*The King of Kong: A Fistful of Quarters*). As a result of these documentaries, there was a revival in the arcade gaming scene. My family attended events related to the documentaries or arcade gaming and I became exposed to a lot of things I wouldn’t have been able to find. The producer of*The King of Kong: A Fistful of Quarters* had previously made a documentary called*New York Doll*which was centered around the life of bassist Arthur Kane. My 12 year old mind was blown: The New York Dolls were a glam-punk sensation dressed in drag. The music was from another planet. Johnny Thunders’ guitar playing was like Chuck Berry with more distortion and less filter. Later on I got to meet the Galaga record holder at the time, Phil Day, in Ottumwa Iowa. Phil is an Australian man of high intellect and good taste. He exposed me to great creators such as Nick Cave & The Bad Seeds, Shakespeare, Lou Reed, artists who created things that I had previously found inconceivable. I believe this time period informed my current tastes and interests, but regrettably I think it also put coals on the fire of rebellion within. I stopped taking my parents and siblings seriously, the Christian faith of my family (which I now hold dearly to) seemed like a mundane sham, and I felt I couldn’t fit in with most people because of my avant-garde tastes. So I write this with the caveat that there should be a way to encourage these tastes in children without letting them walk down the wrong path. There is nothing inherently wrong with bold art, but I’d advise parents to carefully find ways to cultivate their children’s tastes without completely shutting them down and pushing them away as a result. My parents were very loving and patient during this time; I thank God for that. With that out of the way, lets dive in to some bold artists: # Nicolas Cage: Actor  There is an excellent video by Wisecrack on Nicolas Cage that explains him better than I will, which I will link[here](https://www.youtube.com/watch?v=s8IfDNHsCLE). Nicolas Cage rejects the idea that good acting is tied to mere realism; all of his larger than life acting decisions are deliberate choices. When that clicked for me, I immediately realized the man is a genius. He borrows from Kabuki and German Expressionism, art forms that rely on exaggeration to get the message across. He has even created his own acting style, which he calls Nouveau Shamanic. He augments his imagination to go from acting to being. Rather than using the old hat of method acting, he transports himself to a new world mentally. The projects he chooses to partake in are based on his own interests or what he considers would be a challenge (making a bad script good for example). Thus it doesn’t matter how the end result comes out; he has already achieved his goal as an artist. Because of this and because certain directors don’t know how to use his talents, he has a noticeable amount of duds in his filmography. Dig around the duds, you’ll find some pure gold. I’d personally recommend the films*Pig,* *Joe,* *Renfield,* and his Christmas film *The Family Man*. # Nick Cave: Songwriter  What a wild career this man has had! From the apocalyptic mayhem of his band The Birthday Party to the pensive atmosphere of his album*Ghosteen*, it seems like Nick Cave has tried everything. I think his secret sauce is that he’s always working. He maintains an excellent newsletter called*The Red Hand Files*, he has written screenplays such as*Lawless*, he has written books, he has made great film scores such as*The Assassination of Jesse James by the Coward Robert Ford*, the man is religiously prolific. I believe that one of the reasons he is prolific is that he’s not afraid to experiment. If he has an idea, he follows it through to completion. From the album*Murder Ballads*(which is comprised of what the title suggests) to his rejected sequel to*Gladiator*(*Gladiator: Christ Killer*), he doesn’t seem to be afraid to take anything on. This has led to some over the top works as well as some deeply personal works. Albums like*Skeleton Tree*and*Ghosteen*were journeys through the grief of his son’s death. *The Boatman’s Call*is arguably a better break-up album than anything Taylor Swift has put out. He’s not afraid to be outrageous, he’s not afraid to offend, but most importantly he’s not afraid to be himself. Works I’d recommend include The Birthday Party’s*Live 1981-82*, Nick Cave & The Bad Seeds’*The Boatman’s Call*, and the film*Lawless*. # Jim Jarmusch: Director  I consider Jim’s films to be bold almost in an ironic sense: his works are bold in that they are, for the most part, anti-sensational. He has a rule that if his screenplays are criticized for a lack of action, he makes them even less eventful. Even with sensational settings his films feel very close to reality, and they demonstrate the beauty of everyday life. That's what is bold about his art to me: making the sensational grounded in reality while making everyday reality all the more special. *Ghost Dog: The Way of the Samurai* is about a modern-day African-American hitman who strictly follows the rules of the ancient Samurai, yet one can resonate with the humanity of a seemingly absurd character. *Only Lovers Left Alive*is a vampire love story, but in the middle of a vampire romance one can see their their own relationships in a new deeply human light. Jim’s work reminds me that art reflects life, and that there is sacred beauty in seemingly mundane everyday life. I personally recommend his films*Paterson*,*Down by Law*, and*Coffee and Cigarettes*. # NOSTR: We Need Bold Art  NOSTR is in my opinion a path to a better future. In a world creeping slowly towards everything apps, I hope that the protocol where the individual owns their data wins over everything else. I love freedom and sovereignty. If NOSTR is going to win the race of everything apps, we need more than Bitcoin content. We need more than shirtless bros paying for bananas in foreign countries and exercising with girls who have seductive accents. Common people cannot see themselves in such a world. NOSTR needs to catch the attention of everyday people. I don’t believe that this can be accomplished merely by introducing more broadly relevant content; people are searching for content that speaks to them. I believe that NOSTR can and should attract artists of all kinds because NOSTR is one of the few places on the internet where artists can express themselves fearlessly. Getting zaps from NOSTR’s value-for-value ecosystem has far less friction than crowdfunding a creative project or pitching investors that will irreversibly modify an artist’s vision. Having a place where one can post their works without fear of censorship should be extremely enticing. Having a place where one can connect with fellow humans directly as opposed to a sea of bots should seem like the obvious solution. If NOSTR can become a safe haven for artists to express themselves and spread their work, I believe that everyday people will follow. The banker whose stressful job weighs on them will suddenly find joy with an original meme made by a great visual comedian. The programmer for a healthcare company who is drowning in hopeless mundanity could suddenly find a new lust for life by hearing the song of a musician who isn’t afraid to crowdfund their their next project by putting their lighting address on the streets of the internet. The excel guru who loves independent film may find that NOSTR is the best way to support non corporate movies. **My closing statement:** continue to encourage the artists in your life as I’m sure you have been, but while you’re at it give them the purple pill. You may very well be a part of building a better future.
@ c066aac5:6a41a034
2025-04-05 16:58:58I’m drawn to extremities in art. The louder, the bolder, the more outrageous, the better. Bold art takes me out of the mundane into a whole new world where anything and everything is possible. Having grown up in the safety of the suburban midwest, I was a bit of a rebellious soul in search of the satiation that only came from the consumption of the outrageous. My inclination to find bold art draws me to NOSTR, because I believe NOSTR can be the place where the next generation of artistic pioneers go to express themselves. I also believe that as much as we are able, were should invite them to come create here. # My Background: A Small Side Story  My father was a professional gamer in the 80s, back when there was no money or glory in the avocation. He did get a bit of spotlight though after the fact: in the mid 2000’s there were a few parties making documentaries about that era of gaming as well as current arcade events (namely 2007’s*Chasing Ghosts*and*The King of Kong: A Fistful of Quarters*). As a result of these documentaries, there was a revival in the arcade gaming scene. My family attended events related to the documentaries or arcade gaming and I became exposed to a lot of things I wouldn’t have been able to find. The producer of*The King of Kong: A Fistful of Quarters* had previously made a documentary called*New York Doll*which was centered around the life of bassist Arthur Kane. My 12 year old mind was blown: The New York Dolls were a glam-punk sensation dressed in drag. The music was from another planet. Johnny Thunders’ guitar playing was like Chuck Berry with more distortion and less filter. Later on I got to meet the Galaga record holder at the time, Phil Day, in Ottumwa Iowa. Phil is an Australian man of high intellect and good taste. He exposed me to great creators such as Nick Cave & The Bad Seeds, Shakespeare, Lou Reed, artists who created things that I had previously found inconceivable. I believe this time period informed my current tastes and interests, but regrettably I think it also put coals on the fire of rebellion within. I stopped taking my parents and siblings seriously, the Christian faith of my family (which I now hold dearly to) seemed like a mundane sham, and I felt I couldn’t fit in with most people because of my avant-garde tastes. So I write this with the caveat that there should be a way to encourage these tastes in children without letting them walk down the wrong path. There is nothing inherently wrong with bold art, but I’d advise parents to carefully find ways to cultivate their children’s tastes without completely shutting them down and pushing them away as a result. My parents were very loving and patient during this time; I thank God for that. With that out of the way, lets dive in to some bold artists: # Nicolas Cage: Actor  There is an excellent video by Wisecrack on Nicolas Cage that explains him better than I will, which I will link[here](https://www.youtube.com/watch?v=s8IfDNHsCLE). Nicolas Cage rejects the idea that good acting is tied to mere realism; all of his larger than life acting decisions are deliberate choices. When that clicked for me, I immediately realized the man is a genius. He borrows from Kabuki and German Expressionism, art forms that rely on exaggeration to get the message across. He has even created his own acting style, which he calls Nouveau Shamanic. He augments his imagination to go from acting to being. Rather than using the old hat of method acting, he transports himself to a new world mentally. The projects he chooses to partake in are based on his own interests or what he considers would be a challenge (making a bad script good for example). Thus it doesn’t matter how the end result comes out; he has already achieved his goal as an artist. Because of this and because certain directors don’t know how to use his talents, he has a noticeable amount of duds in his filmography. Dig around the duds, you’ll find some pure gold. I’d personally recommend the films*Pig,* *Joe,* *Renfield,* and his Christmas film *The Family Man*. # Nick Cave: Songwriter  What a wild career this man has had! From the apocalyptic mayhem of his band The Birthday Party to the pensive atmosphere of his album*Ghosteen*, it seems like Nick Cave has tried everything. I think his secret sauce is that he’s always working. He maintains an excellent newsletter called*The Red Hand Files*, he has written screenplays such as*Lawless*, he has written books, he has made great film scores such as*The Assassination of Jesse James by the Coward Robert Ford*, the man is religiously prolific. I believe that one of the reasons he is prolific is that he’s not afraid to experiment. If he has an idea, he follows it through to completion. From the album*Murder Ballads*(which is comprised of what the title suggests) to his rejected sequel to*Gladiator*(*Gladiator: Christ Killer*), he doesn’t seem to be afraid to take anything on. This has led to some over the top works as well as some deeply personal works. Albums like*Skeleton Tree*and*Ghosteen*were journeys through the grief of his son’s death. *The Boatman’s Call*is arguably a better break-up album than anything Taylor Swift has put out. He’s not afraid to be outrageous, he’s not afraid to offend, but most importantly he’s not afraid to be himself. Works I’d recommend include The Birthday Party’s*Live 1981-82*, Nick Cave & The Bad Seeds’*The Boatman’s Call*, and the film*Lawless*. # Jim Jarmusch: Director  I consider Jim’s films to be bold almost in an ironic sense: his works are bold in that they are, for the most part, anti-sensational. He has a rule that if his screenplays are criticized for a lack of action, he makes them even less eventful. Even with sensational settings his films feel very close to reality, and they demonstrate the beauty of everyday life. That's what is bold about his art to me: making the sensational grounded in reality while making everyday reality all the more special. *Ghost Dog: The Way of the Samurai* is about a modern-day African-American hitman who strictly follows the rules of the ancient Samurai, yet one can resonate with the humanity of a seemingly absurd character. *Only Lovers Left Alive*is a vampire love story, but in the middle of a vampire romance one can see their their own relationships in a new deeply human light. Jim’s work reminds me that art reflects life, and that there is sacred beauty in seemingly mundane everyday life. I personally recommend his films*Paterson*,*Down by Law*, and*Coffee and Cigarettes*. # NOSTR: We Need Bold Art  NOSTR is in my opinion a path to a better future. In a world creeping slowly towards everything apps, I hope that the protocol where the individual owns their data wins over everything else. I love freedom and sovereignty. If NOSTR is going to win the race of everything apps, we need more than Bitcoin content. We need more than shirtless bros paying for bananas in foreign countries and exercising with girls who have seductive accents. Common people cannot see themselves in such a world. NOSTR needs to catch the attention of everyday people. I don’t believe that this can be accomplished merely by introducing more broadly relevant content; people are searching for content that speaks to them. I believe that NOSTR can and should attract artists of all kinds because NOSTR is one of the few places on the internet where artists can express themselves fearlessly. Getting zaps from NOSTR’s value-for-value ecosystem has far less friction than crowdfunding a creative project or pitching investors that will irreversibly modify an artist’s vision. Having a place where one can post their works without fear of censorship should be extremely enticing. Having a place where one can connect with fellow humans directly as opposed to a sea of bots should seem like the obvious solution. If NOSTR can become a safe haven for artists to express themselves and spread their work, I believe that everyday people will follow. The banker whose stressful job weighs on them will suddenly find joy with an original meme made by a great visual comedian. The programmer for a healthcare company who is drowning in hopeless mundanity could suddenly find a new lust for life by hearing the song of a musician who isn’t afraid to crowdfund their their next project by putting their lighting address on the streets of the internet. The excel guru who loves independent film may find that NOSTR is the best way to support non corporate movies. **My closing statement:** continue to encourage the artists in your life as I’m sure you have been, but while you’re at it give them the purple pill. You may very well be a part of building a better future. @ 57d1a264:69f1fee1
2025-04-07 06:04:14It's so cool how AI is blending design and engineering together, making it easier for us all to be efforts creative in new ways! Steve Jobs once said: > _“The doers are the major thinkers. The people who really create the things that change this industry are both the thinker-doer in one person.”_ `— Steve Jobs` Would its words become truth? Or they already are? originally posted at https://stacker.news/items/936796
@ 57d1a264:69f1fee1
2025-04-07 06:04:14It's so cool how AI is blending design and engineering together, making it easier for us all to be efforts creative in new ways! Steve Jobs once said: > _“The doers are the major thinkers. The people who really create the things that change this industry are both the thinker-doer in one person.”_ `— Steve Jobs` Would its words become truth? Or they already are? originally posted at https://stacker.news/items/936796 @ 57d1a264:69f1fee1
2025-04-07 05:22:14This idea has been explored along the last decades. Nothing has never taken the van place in the BMW series. The most successful intent was the 80s' Vixer in the US. Too sporty for a van? Or too luxurious to cover that already saturated market? Collected some pictures all around, most oof them are designs and prototypes. Tried to order chronologically below:                 Now in 2025, this came out of Ai https://www.youtube.com/watch?v=d7p9CGBmRAA originally posted at https://stacker.news/items/936787
@ 57d1a264:69f1fee1
2025-04-07 05:22:14This idea has been explored along the last decades. Nothing has never taken the van place in the BMW series. The most successful intent was the 80s' Vixer in the US. Too sporty for a van? Or too luxurious to cover that already saturated market? Collected some pictures all around, most oof them are designs and prototypes. Tried to order chronologically below:                 Now in 2025, this came out of Ai https://www.youtube.com/watch?v=d7p9CGBmRAA originally posted at https://stacker.news/items/936787 @ e4950c93:1b99eccd
2025-04-08 13:11:01**Vous avez trouvé un produit naturel ? Partagez-le ici en commentant cette page !** Ce site référence uniquement des produits et objets à usage durable. Les consommables (aliments, cosmétiques, combustibles, etc.) ne sont pas inclus. Pour être référencé, le produit doit être composé de matières naturelles. 👉 [En savoir plus sur les matières](https://www.origine-nature.com/post/ftjhuxe9mvxkhoedyz36i/) Chaque information ajoutée (nom, matière, lien, zone de livraison pour un lien, etc.) et validée est considérée comme une contribution. 👉 [En savoir plus sur les contributions](https://www.origine-nature.com/post/26bj5f7bwyps6ecp5v62t/) Chaque contribution validée est comptabilisée et donne lieu à une rétribution. 👉 [En savoir plus sur les rétributions](https://www.origine-nature.com/post/7hdgcdwt76dprobc9g_2f/) **Copiez-collez le modèle ci-dessous et remplissez les informations dont vous disposez. D’autres contribut-eur-rice-s pourront compléter les éléments manquants.** --- ### Nouveau produit - Nom du produit : - Image du produit (lien) : - Description courte : - Catégories : - Marque ou fabricant : - Composition (matériaux utilisés, y compris les éléments inconnus) : - Liens pour l’acheter (et zone de livraison) : - Zone de livraison pour les - Autres infos utiles (lieu de fabrication, labels, etc.) : --- Cet article est publié sur [origine-nature.com](https://www.origine-nature.com/post/nicmc-eandjr_vcz4_hsr/) 🌐 [See this article in English](https://www.origin-nature.com/post/8adj-i_hk0gtzp_ul9k17/)
@ e4950c93:1b99eccd
2025-04-08 13:11:01**Vous avez trouvé un produit naturel ? Partagez-le ici en commentant cette page !** Ce site référence uniquement des produits et objets à usage durable. Les consommables (aliments, cosmétiques, combustibles, etc.) ne sont pas inclus. Pour être référencé, le produit doit être composé de matières naturelles. 👉 [En savoir plus sur les matières](https://www.origine-nature.com/post/ftjhuxe9mvxkhoedyz36i/) Chaque information ajoutée (nom, matière, lien, zone de livraison pour un lien, etc.) et validée est considérée comme une contribution. 👉 [En savoir plus sur les contributions](https://www.origine-nature.com/post/26bj5f7bwyps6ecp5v62t/) Chaque contribution validée est comptabilisée et donne lieu à une rétribution. 👉 [En savoir plus sur les rétributions](https://www.origine-nature.com/post/7hdgcdwt76dprobc9g_2f/) **Copiez-collez le modèle ci-dessous et remplissez les informations dont vous disposez. D’autres contribut-eur-rice-s pourront compléter les éléments manquants.** --- ### Nouveau produit - Nom du produit : - Image du produit (lien) : - Description courte : - Catégories : - Marque ou fabricant : - Composition (matériaux utilisés, y compris les éléments inconnus) : - Liens pour l’acheter (et zone de livraison) : - Zone de livraison pour les - Autres infos utiles (lieu de fabrication, labels, etc.) : --- Cet article est publié sur [origine-nature.com](https://www.origine-nature.com/post/nicmc-eandjr_vcz4_hsr/) 🌐 [See this article in English](https://www.origin-nature.com/post/8adj-i_hk0gtzp_ul9k17/) @ ec9bd746:df11a9d0
2025-04-06 08:06:08## 🌍 Time Window: 🕘 **When**: Every even week on Sunday at 9:00 PM CET 🗺️ **Where**: https://cornychat.com/eurocorn **Start:** 21:00 CET (Prague, UTC+1) **End:** approx. 02:00 CET (Prague, UTC+1, next day) **Duration:** usually 5+ hours. | Region | Local Time Window | Convenience Level | |-----------------------------------------------------|--------------------------------------------|---------------------------------------------------------| | **Europe (CET, Prague)** 🇨🇿🇩🇪 | **21:00–02:00 CET** | ✅ Very Good; evening & night | | **East Coast North America (EST)** 🇺🇸🇨🇦 | **15:00–20:00 EST** | ✅ Very Good; afternoon & early evening | | **West Coast North America (PST)** 🇺🇸🇨🇦 | **12:00–17:00 PST** | ✅ Very Good; midday & afternoon | | **Central America (CST)** 🇲🇽🇨🇷🇬🇹 | **14:00–19:00 CST** | ✅ Very Good; afternoon & evening | | **South America West (Peru/Colombia PET/COT)** 🇵🇪🇨🇴 | **15:00–20:00 PET/COT** | ✅ Very Good; afternoon & evening | | **South America East (Brazil/Argentina/Chile, BRT/ART/CLST)** 🇧🇷🇦🇷🇨🇱 | **17:00–22:00 BRT/ART/CLST** | ✅ Very Good; early evening | | **United Kingdom/Ireland (GMT)** 🇬🇧🇮🇪 | **20:00–01:00 GMT** | ✅ Very Good; evening hours (midnight convenient) | | **Eastern Europe (EET)** 🇷🇴🇬🇷🇺🇦 | **22:00–03:00 EET** | ✅ Good; late evening & early night (slightly late) | | **Africa (South Africa, SAST)** 🇿🇦 | **22:00–03:00 SAST** | ✅ Good; late evening & overnight (late-night common) | | **New Zealand (NZDT)** 🇳🇿 | **09:00–14:00 NZDT (next day)** | ✅ Good; weekday morning & afternoon | | **Australia (AEDT, Sydney)** 🇦🇺 | **07:00–12:00 AEDT (next day)** | ✅ Good; weekday morning to noon | | **East Africa (Kenya, EAT)** 🇰🇪 | **23:00–04:00 EAT** | ⚠️ Slightly late (night hours; late night common) | | **Russia (Moscow, MSK)** 🇷🇺 | **23:00–04:00 MSK** | ⚠️ Slightly late (join at start is fine, very late night) | | **Middle East (UAE, GST)** 🇦🇪🇴🇲 | **00:00–05:00 GST (next day)** | ⚠️ Late night start (midnight & early morning, but shorter attendance plausible)| | **Japan/Korea (JST/KST)** 🇯🇵🇰🇷 | **05:00–10:00 JST/KST (next day)** | ⚠️ Early; convenient joining from ~07:00 onwards possible | | **China (Beijing, CST)** 🇨🇳 | **04:00–09:00 CST (next day)** | ❌ Challenging; very early morning start (better ~07:00 onwards) | | **India (IST)** 🇮🇳 | **01:30–06:30 IST (next day)** | ❌ Very challenging; overnight timing typically difficult| ---
@ ec9bd746:df11a9d0
2025-04-06 08:06:08## 🌍 Time Window: 🕘 **When**: Every even week on Sunday at 9:00 PM CET 🗺️ **Where**: https://cornychat.com/eurocorn **Start:** 21:00 CET (Prague, UTC+1) **End:** approx. 02:00 CET (Prague, UTC+1, next day) **Duration:** usually 5+ hours. | Region | Local Time Window | Convenience Level | |-----------------------------------------------------|--------------------------------------------|---------------------------------------------------------| | **Europe (CET, Prague)** 🇨🇿🇩🇪 | **21:00–02:00 CET** | ✅ Very Good; evening & night | | **East Coast North America (EST)** 🇺🇸🇨🇦 | **15:00–20:00 EST** | ✅ Very Good; afternoon & early evening | | **West Coast North America (PST)** 🇺🇸🇨🇦 | **12:00–17:00 PST** | ✅ Very Good; midday & afternoon | | **Central America (CST)** 🇲🇽🇨🇷🇬🇹 | **14:00–19:00 CST** | ✅ Very Good; afternoon & evening | | **South America West (Peru/Colombia PET/COT)** 🇵🇪🇨🇴 | **15:00–20:00 PET/COT** | ✅ Very Good; afternoon & evening | | **South America East (Brazil/Argentina/Chile, BRT/ART/CLST)** 🇧🇷🇦🇷🇨🇱 | **17:00–22:00 BRT/ART/CLST** | ✅ Very Good; early evening | | **United Kingdom/Ireland (GMT)** 🇬🇧🇮🇪 | **20:00–01:00 GMT** | ✅ Very Good; evening hours (midnight convenient) | | **Eastern Europe (EET)** 🇷🇴🇬🇷🇺🇦 | **22:00–03:00 EET** | ✅ Good; late evening & early night (slightly late) | | **Africa (South Africa, SAST)** 🇿🇦 | **22:00–03:00 SAST** | ✅ Good; late evening & overnight (late-night common) | | **New Zealand (NZDT)** 🇳🇿 | **09:00–14:00 NZDT (next day)** | ✅ Good; weekday morning & afternoon | | **Australia (AEDT, Sydney)** 🇦🇺 | **07:00–12:00 AEDT (next day)** | ✅ Good; weekday morning to noon | | **East Africa (Kenya, EAT)** 🇰🇪 | **23:00–04:00 EAT** | ⚠️ Slightly late (night hours; late night common) | | **Russia (Moscow, MSK)** 🇷🇺 | **23:00–04:00 MSK** | ⚠️ Slightly late (join at start is fine, very late night) | | **Middle East (UAE, GST)** 🇦🇪🇴🇲 | **00:00–05:00 GST (next day)** | ⚠️ Late night start (midnight & early morning, but shorter attendance plausible)| | **Japan/Korea (JST/KST)** 🇯🇵🇰🇷 | **05:00–10:00 JST/KST (next day)** | ⚠️ Early; convenient joining from ~07:00 onwards possible | | **China (Beijing, CST)** 🇨🇳 | **04:00–09:00 CST (next day)** | ❌ Challenging; very early morning start (better ~07:00 onwards) | | **India (IST)** 🇮🇳 | **01:30–06:30 IST (next day)** | ❌ Very challenging; overnight timing typically difficult| --- @ 592295cf:413a0db9
2025-04-05 07:26:23## [Edit] I tried to get the slides and an audio file, from Constant's talk at NostRiga, about 8 months ago # 1. ### Nostr's adoption thesis ### The less you define, the more you imply ### by Wouter Constant ## 2. ### Dutch Bitcoiner ### AntiHashedPodcast ### Writing Book about nostr 00:40 ## 3. ### What this presentation about ### A protocols design includes initself a thesis ### on protocol adoption, due to underlying assumptions 1:17 ## 4. ### Examples ### Governments/Academic: Pubhubs (Matrix) ### Bussiness: Bluesky ### Foss: Nostr 1:58 ## 5. ### What constitutes minimal viability? ### Pubhubs (Matrix): make is "safe" for user ### Bluesky: liability and monetization ### Foss: Simpel for developer 4:03 ## 6. ### The Point of Nostr ### Capture network effects through interoperability 4:43 ## 7. ## Three assumptions ### The direction is workable ### Method is workable ### Motivation and means are sufficient 5:27 ## 8. ## Assumption 1 ### The asymmetric cryptography paradigm is a good idea 6:16 ## 9. ### Nostr is a exponent of the key-pair paradigm. ### And Basicly just that. 6.52 ## 10. ### Keys suck ### Protect a secret that you are supposed use all the time. 7:37 ## 11. ## Assumption two ### The unaddressed things will be figured out within a 'meta-design consensus' 8:11 ## 12. ### Nostr's base protocol is not minimally viable for anything, except own development. 8:25 ## 13. ### Complexity leads to capture; ### i.e. free and open in the name, ### controlled in pratice 9:54 ## 14. ## Meta-design consensus ### Buildings things 'note centric' mantains interoperability. 11:51 ## 15. ## Assumption three ### the nightmare is scary; ### the cream is appealing. 12:41 ## 16. ### Get it minimally viable, ### for whatever target, ### such that it is not a waste of time. 13:23 ## 17. ## Summarize ### We are in a nightmare. ### Assume key/signature are the way out. ### Assume we can Maintain an open stardand while manifesting the dream. ### Assume we are motivated enought to bootstrap this to adulthood. 14:01 ## 18. ### We want this, ### we can do this, ### because we have to. 14:12 ## Thank you for contribuiting [Edit] Note for audio presentation nostr:nevent1qvzqqqqqqypzqkfzjh8jkzd8l9247sadku6vhm52snhgjtknlyeku6sfkeqn5rdeqyf8wumn8ghj7mn0wd68ytnvw5hxkef0qyg8wumn8ghj7mn0wd68ytnddakj7qpqqqq6fdnhvp95gqf4k3vxmljh87uvjezpepyt222jl2267q857uwqz7gcke
@ 592295cf:413a0db9
2025-04-05 07:26:23## [Edit] I tried to get the slides and an audio file, from Constant's talk at NostRiga, about 8 months ago # 1. ### Nostr's adoption thesis ### The less you define, the more you imply ### by Wouter Constant ## 2. ### Dutch Bitcoiner ### AntiHashedPodcast ### Writing Book about nostr 00:40 ## 3. ### What this presentation about ### A protocols design includes initself a thesis ### on protocol adoption, due to underlying assumptions 1:17 ## 4. ### Examples ### Governments/Academic: Pubhubs (Matrix) ### Bussiness: Bluesky ### Foss: Nostr 1:58 ## 5. ### What constitutes minimal viability? ### Pubhubs (Matrix): make is "safe" for user ### Bluesky: liability and monetization ### Foss: Simpel for developer 4:03 ## 6. ### The Point of Nostr ### Capture network effects through interoperability 4:43 ## 7. ## Three assumptions ### The direction is workable ### Method is workable ### Motivation and means are sufficient 5:27 ## 8. ## Assumption 1 ### The asymmetric cryptography paradigm is a good idea 6:16 ## 9. ### Nostr is a exponent of the key-pair paradigm. ### And Basicly just that. 6.52 ## 10. ### Keys suck ### Protect a secret that you are supposed use all the time. 7:37 ## 11. ## Assumption two ### The unaddressed things will be figured out within a 'meta-design consensus' 8:11 ## 12. ### Nostr's base protocol is not minimally viable for anything, except own development. 8:25 ## 13. ### Complexity leads to capture; ### i.e. free and open in the name, ### controlled in pratice 9:54 ## 14. ## Meta-design consensus ### Buildings things 'note centric' mantains interoperability. 11:51 ## 15. ## Assumption three ### the nightmare is scary; ### the cream is appealing. 12:41 ## 16. ### Get it minimally viable, ### for whatever target, ### such that it is not a waste of time. 13:23 ## 17. ## Summarize ### We are in a nightmare. ### Assume key/signature are the way out. ### Assume we can Maintain an open stardand while manifesting the dream. ### Assume we are motivated enought to bootstrap this to adulthood. 14:01 ## 18. ### We want this, ### we can do this, ### because we have to. 14:12 ## Thank you for contribuiting [Edit] Note for audio presentation nostr:nevent1qvzqqqqqqypzqkfzjh8jkzd8l9247sadku6vhm52snhgjtknlyeku6sfkeqn5rdeqyf8wumn8ghj7mn0wd68ytnvw5hxkef0qyg8wumn8ghj7mn0wd68ytnddakj7qpqqqq6fdnhvp95gqf4k3vxmljh87uvjezpepyt222jl2267q857uwqz7gcke @ 21335073:a244b1ad
2025-03-18 14:43:08**Warning: This piece contains a conversation about difficult topics. Please proceed with caution.** TL;DR please educate your children about online safety. Julian Assange wrote in his 2012 book *Cypherpunks*, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense. This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning. When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little. I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?” I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well. I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread. I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard. I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it. The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust. Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this. I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place. What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method. It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code. They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened. I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road. So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally. Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb. I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback. Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed. That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone. To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all. I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society. I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this. On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government. I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories. There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc. Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind. Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now. There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers? I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity. I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place. My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors. My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline. The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online. I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers. So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation? When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that. I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic. If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations. I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process. **Course:** - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children. The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward? I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone. Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability. The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime. This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful. This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens. In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions. I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
@ 21335073:a244b1ad
2025-03-18 14:43:08**Warning: This piece contains a conversation about difficult topics. Please proceed with caution.** TL;DR please educate your children about online safety. Julian Assange wrote in his 2012 book *Cypherpunks*, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense. This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning. When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little. I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?” I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well. I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread. I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard. I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it. The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust. Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this. I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place. What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method. It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code. They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened. I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road. So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally. Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb. I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback. Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed. That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone. To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all. I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society. I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this. On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government. I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories. There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc. Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind. Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now. There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers? I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity. I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place. My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors. My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline. The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online. I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers. So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation? When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that. I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic. If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations. I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process. **Course:** - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children. The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward? I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone. Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability. The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime. This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful. This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens. In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions. I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation. @ f683e870:557f5ef2
2025-04-08 11:13:27When it comes to the Nostr Web of Trust, several NIPs have been proposed, but the one that seemed to gather the most traction was [Trusted Assertion](https://github.com/nostr-protocol/nips/pull/1534) by [Vitor Pamplona](https://npub.world/npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z). The idea is to have `kind:30382` represent *assertions* made about an *entity*, which could be a *pubkey*, for example. The NIP also specifies a tag called `rank`, which can be used to build some basic WoT primitives. Example event: ``` { "kind": 30382, "tags": [ ["d", "e88a6...50411"], ["rank", "89"], ["zap_amt_sent", "1000000"], ], "content": "", //... } ``` However, we quickly realized that this NIP was too limiting for what we wanted to accomplish: *real-time, personalized ranking*. To illustrate our different approaches, we will show how to replicate our [Verify Reputation](https://vertexlab.io/docs/nips/verify-reputation-dvm/) with trusted assertions. ## Verify Reputation [Verify Reputation](https://vertexlab.io/content/docs/nips/verify-reputation-dvm.md) returns: - the rank, follow count and followers count of the given `target` - its top followers by rank. All ranks are personalized to the given `source`. This “batteries included” solution helps users avoid impersonation and fraud with a single request, no matter what application they are using, be it a kind:1 client, chat app, wallet, marketplace, or more. !\[\](https://vertexlab.io/images/verify_reputation_example.png) To get the same result with trusted assertions, you would have to - Get all contact lists that contain the `target` (as a `p` tag) - Build the target’s `follower` list from those event authors - Get the trusted assertions for the target and each of the followers - Sort them by the rank provided by the trusted assertions This operation is computationally expensive, especially on mobile devices. It is clear that if the user is willing to verify and process a large number of events (potentially +100k), he can compute some (rudimentary) ranking directly on the device, without the need to trust a third party. **More generally, trusted assertions are very hard to use when one doesn’t know the pubkeys of the people he’s looking for.** **This goes fundamentally against our approach of Web of Trust, as a powerful mechanism for discovery.** --- Are you looking to add Web of Trust capabilities to your app or project? [Take a look at our website](https://vertexlab.io/) or [send a DM to Pip](https://npub.world/npub176p7sup477k5738qhxx0hk2n0cty2k5je5uvalzvkvwmw4tltmeqw7vgup).
@ f683e870:557f5ef2
2025-04-08 11:13:27When it comes to the Nostr Web of Trust, several NIPs have been proposed, but the one that seemed to gather the most traction was [Trusted Assertion](https://github.com/nostr-protocol/nips/pull/1534) by [Vitor Pamplona](https://npub.world/npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z). The idea is to have `kind:30382` represent *assertions* made about an *entity*, which could be a *pubkey*, for example. The NIP also specifies a tag called `rank`, which can be used to build some basic WoT primitives. Example event: ``` { "kind": 30382, "tags": [ ["d", "e88a6...50411"], ["rank", "89"], ["zap_amt_sent", "1000000"], ], "content": "", //... } ``` However, we quickly realized that this NIP was too limiting for what we wanted to accomplish: *real-time, personalized ranking*. To illustrate our different approaches, we will show how to replicate our [Verify Reputation](https://vertexlab.io/docs/nips/verify-reputation-dvm/) with trusted assertions. ## Verify Reputation [Verify Reputation](https://vertexlab.io/content/docs/nips/verify-reputation-dvm.md) returns: - the rank, follow count and followers count of the given `target` - its top followers by rank. All ranks are personalized to the given `source`. This “batteries included” solution helps users avoid impersonation and fraud with a single request, no matter what application they are using, be it a kind:1 client, chat app, wallet, marketplace, or more. !\[\](https://vertexlab.io/images/verify_reputation_example.png) To get the same result with trusted assertions, you would have to - Get all contact lists that contain the `target` (as a `p` tag) - Build the target’s `follower` list from those event authors - Get the trusted assertions for the target and each of the followers - Sort them by the rank provided by the trusted assertions This operation is computationally expensive, especially on mobile devices. It is clear that if the user is willing to verify and process a large number of events (potentially +100k), he can compute some (rudimentary) ranking directly on the device, without the need to trust a third party. **More generally, trusted assertions are very hard to use when one doesn’t know the pubkeys of the people he’s looking for.** **This goes fundamentally against our approach of Web of Trust, as a powerful mechanism for discovery.** --- Are you looking to add Web of Trust capabilities to your app or project? [Take a look at our website](https://vertexlab.io/) or [send a DM to Pip](https://npub.world/npub176p7sup477k5738qhxx0hk2n0cty2k5je5uvalzvkvwmw4tltmeqw7vgup). @ e4950c93:1b99eccd
2025-04-07 14:34:11### Équipe Cœur L'équipe Cœur porte le projet et valide les contenus. - Jean-David Bar : https://njump.me/npub1qr4p7uamcpawv7cr8z9nlhmd60lylukf7lvmtlnpe7r4juwxudzq3hrnll Pour démarrer, je gère le projet en solo en partageant mes favoris pour éviter le plastique sur nous et sur nos enfants. [Contactez-moi](https://www.origine-nature.com/post/qcp-smvj1v78_-7iceyrd/) si vous souhaitez rejoindre l'aventure ! ### Enrichisseu-r-se-s de contenus Les contribut-eur-rice-s rendent ce site vivant et intéressant. *A venir.* 👉 [En savoir plus sur les contributions](https://www.origine-nature.com/post/26bj5f7bwyps6ecp5v62t/) --- Cet article est publié sur [origine-nature.com](https://www.origine-nature.com/post/x-ykxuenf9tnccu65mhjq/) 🌐 [See this article in English](https://www.origin-nature.com/post/cyy0wd2ar_rwqbjipnhej/)
@ e4950c93:1b99eccd
2025-04-07 14:34:11### Équipe Cœur L'équipe Cœur porte le projet et valide les contenus. - Jean-David Bar : https://njump.me/npub1qr4p7uamcpawv7cr8z9nlhmd60lylukf7lvmtlnpe7r4juwxudzq3hrnll Pour démarrer, je gère le projet en solo en partageant mes favoris pour éviter le plastique sur nous et sur nos enfants. [Contactez-moi](https://www.origine-nature.com/post/qcp-smvj1v78_-7iceyrd/) si vous souhaitez rejoindre l'aventure ! ### Enrichisseu-r-se-s de contenus Les contribut-eur-rice-s rendent ce site vivant et intéressant. *A venir.* 👉 [En savoir plus sur les contributions](https://www.origine-nature.com/post/26bj5f7bwyps6ecp5v62t/) --- Cet article est publié sur [origine-nature.com](https://www.origine-nature.com/post/x-ykxuenf9tnccu65mhjq/) 🌐 [See this article in English](https://www.origin-nature.com/post/cyy0wd2ar_rwqbjipnhej/) @ a07fae46:7d83df92
2025-03-18 12:31:40if the JFK documents come out and are nothing but old hat, it will be disappointing. but if they contain revelations, then they are an unalloyed good. unprecedented and extraordinary; worthy of praise and admiration. they murdered the president in broad daylight and kept 80,000 related documents secret for 60 years. the apparatus that did that and got away with it, is 100+ years in the making. the magic bullet was just the starting pistol of a new *era*; a *level up* in an [old game](https://archive.org/details/TragedyAndHope_501/page/n5/mode/2up?q=feudalist+fashion). it won't be dismantled and your republic delivered back with a bow in *2 months*. have a little humility and a little gratitude. cynicism is easy. it's peak mid-wittery. yeah no shit everything is corrupt and everyone's likely captured by [AIPAC](https://books.google.com/books/publisher/content?id=gKVKDwAAQBAJ&pg=PT68&img=1&zoom=3&hl=en&bul=1&sig=ACfU3U2pagVXTYdJOKxkAwmmFQpuSnoS5g&w=1280) or something beyond. YOU THINK AIPAC is the [ALL SEEING EYE](https://archive.org/details/the-all-seeing-eye-vol-1-5-manly-p.-hall-may-1923-sept-1931)? you can keep going, if you want to, but have some awareness and appreciation for where we are and what it took to get here. the first 'you are fake news' was also a shot heard 'round the world and you are riding high on it's [Infrasound](https://en.wikipedia.org/wiki/Infrasound) wave, still reverberating; unappreciative of the profound delta in public awareness and understanding, and rate of change, that has occurred since that moment, in [2017](https://www.youtube.com/watch?v=Vqpzk-qGxMU). think about where we were back then, especially with corporate capture of the narrative. trump's bullheaded behavior, if only ego-driven, *is* what broke the spell. an *actual* moment of savage bravery is what allows for your current jaded affectation. black pilled is boring. it's intellectually lazy. it is low-resolution-thinking, no better than progressives who explain the myriad ills of the world through 'racism'. normalcy bias works both ways. i'm not grading you on a curve that includes NPCs. i'm grading you against those of us with a mind, on up. do better. the best Webb-style doomer argument is essentially 'the mouse trap needs a piece of cheese in order to work'. ok, but it doesn't need 3 pieces of cheese, or 5. was FreeRoss the piece of cheese? was the SBR the cheese? real bitcoiners know how dumb the 'sbr is an attempt to takeover btc' narrative is, so extrapolate from that. what about withdrawal from the WHO? freeze and review of USAID et al? how many pieces of cheese before we realize it's not a trap? it's just a messy endeavor. Good morning. #jfkFiles #nostrOnly
@ a07fae46:7d83df92
2025-03-18 12:31:40if the JFK documents come out and are nothing but old hat, it will be disappointing. but if they contain revelations, then they are an unalloyed good. unprecedented and extraordinary; worthy of praise and admiration. they murdered the president in broad daylight and kept 80,000 related documents secret for 60 years. the apparatus that did that and got away with it, is 100+ years in the making. the magic bullet was just the starting pistol of a new *era*; a *level up* in an [old game](https://archive.org/details/TragedyAndHope_501/page/n5/mode/2up?q=feudalist+fashion). it won't be dismantled and your republic delivered back with a bow in *2 months*. have a little humility and a little gratitude. cynicism is easy. it's peak mid-wittery. yeah no shit everything is corrupt and everyone's likely captured by [AIPAC](https://books.google.com/books/publisher/content?id=gKVKDwAAQBAJ&pg=PT68&img=1&zoom=3&hl=en&bul=1&sig=ACfU3U2pagVXTYdJOKxkAwmmFQpuSnoS5g&w=1280) or something beyond. YOU THINK AIPAC is the [ALL SEEING EYE](https://archive.org/details/the-all-seeing-eye-vol-1-5-manly-p.-hall-may-1923-sept-1931)? you can keep going, if you want to, but have some awareness and appreciation for where we are and what it took to get here. the first 'you are fake news' was also a shot heard 'round the world and you are riding high on it's [Infrasound](https://en.wikipedia.org/wiki/Infrasound) wave, still reverberating; unappreciative of the profound delta in public awareness and understanding, and rate of change, that has occurred since that moment, in [2017](https://www.youtube.com/watch?v=Vqpzk-qGxMU). think about where we were back then, especially with corporate capture of the narrative. trump's bullheaded behavior, if only ego-driven, *is* what broke the spell. an *actual* moment of savage bravery is what allows for your current jaded affectation. black pilled is boring. it's intellectually lazy. it is low-resolution-thinking, no better than progressives who explain the myriad ills of the world through 'racism'. normalcy bias works both ways. i'm not grading you on a curve that includes NPCs. i'm grading you against those of us with a mind, on up. do better. the best Webb-style doomer argument is essentially 'the mouse trap needs a piece of cheese in order to work'. ok, but it doesn't need 3 pieces of cheese, or 5. was FreeRoss the piece of cheese? was the SBR the cheese? real bitcoiners know how dumb the 'sbr is an attempt to takeover btc' narrative is, so extrapolate from that. what about withdrawal from the WHO? freeze and review of USAID et al? how many pieces of cheese before we realize it's not a trap? it's just a messy endeavor. Good morning. #jfkFiles #nostrOnly @ 57d1a264:69f1fee1
2025-04-05 06:58:25**Summary** We are looking for a Visual Designer with a strong focus on illustration and animation to help shape and refine our brand’s visual identity. You will create compelling assets for digital and print, including marketing materials, social media content, website illustrations, and motion graphics. Working closely with our marketing and product teams, you will play a key role in developing a consistent and recognizable visual style through thoughtful use of illustration, color, patterns, and animation. This role requires creativity, adaptability, and the ability to deliver high-quality work in a fast-paced, remote environment. **Responsibilities** - Create high-quality, iconic illustrations, branding assets, and motion graphics that contribute to and refine our visual identity. - Develop digital assets for marketing, social media, website, and app. - Work within brand guidelines while exploring ways to evolve and strengthen our visual style. **Requirements** - 2+ years of experience in graphic design, with a strong focus on illustration. - Ability to help define and develop a cohesive visual style for the brand. - Proficiency in Adobe products. - Experience with Figma is a plus. - Strong organizational skills—your layers and files should be neatly labeled. - Clear communication and collaboration skills to work effectively with the team. - Located in LATAM Please attach a link to your portfolio to showcase your work when applying. [APPLY HERE](https://jan3.com/contact/) originally posted at https://stacker.news/items/935007
@ 57d1a264:69f1fee1
2025-04-05 06:58:25**Summary** We are looking for a Visual Designer with a strong focus on illustration and animation to help shape and refine our brand’s visual identity. You will create compelling assets for digital and print, including marketing materials, social media content, website illustrations, and motion graphics. Working closely with our marketing and product teams, you will play a key role in developing a consistent and recognizable visual style through thoughtful use of illustration, color, patterns, and animation. This role requires creativity, adaptability, and the ability to deliver high-quality work in a fast-paced, remote environment. **Responsibilities** - Create high-quality, iconic illustrations, branding assets, and motion graphics that contribute to and refine our visual identity. - Develop digital assets for marketing, social media, website, and app. - Work within brand guidelines while exploring ways to evolve and strengthen our visual style. **Requirements** - 2+ years of experience in graphic design, with a strong focus on illustration. - Ability to help define and develop a cohesive visual style for the brand. - Proficiency in Adobe products. - Experience with Figma is a plus. - Strong organizational skills—your layers and files should be neatly labeled. - Clear communication and collaboration skills to work effectively with the team. - Located in LATAM Please attach a link to your portfolio to showcase your work when applying. [APPLY HERE](https://jan3.com/contact/) originally posted at https://stacker.news/items/935007 @ f1577c25:de26ba14
2025-04-07 09:51:36احنا المرة اللي فاتت اتكلمنا عن الاساسيات تعالي بقي نتكلم بشكل عام علي الطرق اللي في وجهه نظري احسن طرق و هقولك ليه و تبدا بمين الاول و كمان كل طريقه هسيب لك ليها لينك تشرح التطبيق عنه بشكل مفصل اكتر بحيث تعرف الحلو و الوحش و الحد الادني و كل دا --- ## البورصة الأمريكية * **العملة**: دولار * **العائد المتوقع**: ~10% سنوياً * **الحد الأدنى**: ~100 جنيه * **الورق المطلوب**: باسبور * **المميزات**: - استثمار دولاري - سهولة الإيداع بالعملات الرقمية - إمكانية السحب في أي وقت * **العيوب**: - تحتاج جواز سفر - تتطلب معرفة بالشركات - تقلبات السوق علي المدي القصير * **ملاحظات**: لو لسة جديد بس معاك حساب دولاري يبقي انصحك بـ IBKR علشان سهل ولكن لو معكش حساب دولاري يبقي Tastytrade علشان سهل الايداع بالكريبتو ## العملات الرقمية * **العملة**: دولار * **العائد المتوقع**: ~10% سنوياً (متغير) * **الحد الأدنى**: ~100 جنيه * **الورق المطلوب**: بطاقة * **المميزات**: - عائد يومي - استثمار دولاري - سهولة السحب * **العيوب**: - العائد متغير - مخاطر الأمان * **ملاحظات**: هنا قصدي منتجات Earn زي في بينانس ## ذهب (عالمي) * **العملة**: دولار * **العائد المتوقع**: متغير حسب سعر الذهب * **الحد الأدنى**: ~100 جنيه * **الورق المطلوب**: بطاقة * **المميزات**: - الذهب بسعر السوق العالمي - تحوط ضد التضخم * **العيوب**: - تقلبات السوق علي المدي القصير - استثمار طويل الأجل - مخاطر الامان * **ملاحظات**: الذهب العالمي قصدي انه تحول عملات ل PAXG في بينانس او Kraken ## عقارات (عالمي) * **العملة**: دولار * **العائد المتوقع**: ~9-10% سنوياً * **الحد الأدنى**: ~50 دولار في موقع Realt و ~135 لو موقع Stake * **الورق المطلوب**: باسبور * **المميزات**: - استثمار دولاري - عائد شهري * **العيوب**: - استثمار طويل الأجل - لو Stake فا تقدر تسحب فلوسك مرتين بالسنة بس - تحتاج باسبور - تقلبات السوق * **ملاحظات**: في تطبيقين RealT للسوق الامريكي و Stake للسوق الامراتي او السعودي ## فوري يومي * **العملة**: جنيه مصري * **العائد المتوقع**: ~24% * **الحد الأدنى**: ~3 جنيه * **الورق المطلوب**: بطاقة * **المميزات**: - سهولة الاستخدام - عائد يومي - بدون حد أدنى عالي * **العيوب**: - بالجنيه المصري - عائد أقل من شهادات البنك (الي الان) - تقلبات العائد * **ملاحظات**: قصدي تطبيق فوري يومي ## عقارات (محلي) * **العملة**: جنيه مصري * **العائد المتوقع**: الفعلي 9% ولكن متوقع 28-48% (متوسط 32%) * **الحد الأدنى**: 50,000 جنيه * **الورق المطلوب**: بطاقة * **المميزات**: - عائد سنوي مرتفع - العائد مربوط بالدولار بمعني لو حصل تعويم العائد بتاعك هيزيد فا مقاوم للتضخم. - سهولة الاستخدام * **العيوب**: - حجز الأموال 6 شهور - 50 ألف حد أدنى - ضرائب عقارية * **ملاحظات**: قصدي تطبيق Safe ## شهادات البنك * **العملة**: جنيه مصري * **العائد المتوقع**: 27% او 30% بعائد تناقصي * **الحد الأدنى**: 1000 جنيه * **الورق المطلوب**: بطاقة * **المميزات**: - عائد مرتفع * **العيوب**: - بالجنيه المصري - متقدرش تسحب فلوسك غير بعد مدة الشهادة. * **ملاحظات**: دخولك هنا او لا و العائد شهري او سنوي يبقي علي حسب هدفك ## ذهب (محلي) * **العملة**: جنيه مصري * **العائد المتوقع**: متغير حسب سعر الذهب * **الحد الأدنى**: ~18 جنيه * **الورق المطلوب**: بطاقة * **المميزات**: - قيمة ثابتة ومستقرة - سهولة الشراء - الحد الادني صغير لو سهم في صندوق زي AZG * **العيوب**: - يحتاج مبلغ عالي للدخول لو حقيقي - تقلبات السوق علي المدي القصير * **ملاحظات**: يعتبر خيار حلو بس انا شايف لو هتدخل بدهب يبقي عالمي + قصدي ذهب بجد او عن طريق صناديق الذهب زي AZG --- ## كمل قراية عن كل اختيار - البورصة الامريكية: nostr:naddr1qvzqqqr4gupzpu2h0sja0vmqdqjzq6e820jjjnuytzw2ksmemfnadhe0hm0zdws5qqxnzde5xvurzvfsxuerzvphcvddg0 - العملات الرقمية و الذهب العالمي: nostr:naddr1qvzqqqr4gupzpu2h0sja0vmqdqjzq6e820jjjnuytzw2ksmemfnadhe0hm0zdws5qqxnzde5xvunzvesx5erywpsepywcn - عقارات (عالمي): nostr:naddr1qvzqqqr4gupzpu2h0sja0vmqdqjzq6e820jjjnuytzw2ksmemfnadhe0hm0zdws5qqxnzde5xvunzdpcxq6nxwp3xqxgmx - فوري يومي: nostr:naddr1qvzqqqr4gupzpu2h0sja0vmqdqjzq6e820jjjnuytzw2ksmemfnadhe0hm0zdws5qqxnzde5xscrqdesxycnvv34l5ye0c - عقارات (مصري): nostr:naddr1qvzqqqr4gupzpu2h0sja0vmqdqjzq6e820jjjnuytzw2ksmemfnadhe0hm0zdws5qqxnzde5xvungvfsx5cnvv3ndwszwl - شهادات البنك (مصري): nostr:naddr1qvzqqqr4gupzpu2h0sja0vmqdqjzq6e820jjjnuytzw2ksmemfnadhe0hm0zdws5qqxnzde5xscrqdpnxc6rvvee3fqr5t - الذهب (مصري): nostr:naddr1qvzqqqr4gupzpu2h0sja0vmqdqjzq6e820jjjnuytzw2ksmemfnadhe0hm0zdws5qqxnzde5xscrqdesxucrjdehs24uge --- ## ادعمني (اختياري) * USDT (TRC20): `TKQ3Uwkq21ntiua2Zh9Hu376fdMdnRGWN6` --- آخر تحديث: 4 أبريل 2025
@ f1577c25:de26ba14
2025-04-07 09:51:36احنا المرة اللي فاتت اتكلمنا عن الاساسيات تعالي بقي نتكلم بشكل عام علي الطرق اللي في وجهه نظري احسن طرق و هقولك ليه و تبدا بمين الاول و كمان كل طريقه هسيب لك ليها لينك تشرح التطبيق عنه بشكل مفصل اكتر بحيث تعرف الحلو و الوحش و الحد الادني و كل دا --- ## البورصة الأمريكية * **العملة**: دولار * **العائد المتوقع**: ~10% سنوياً * **الحد الأدنى**: ~100 جنيه * **الورق المطلوب**: باسبور * **المميزات**: - استثمار دولاري - سهولة الإيداع بالعملات الرقمية - إمكانية السحب في أي وقت * **العيوب**: - تحتاج جواز سفر - تتطلب معرفة بالشركات - تقلبات السوق علي المدي القصير * **ملاحظات**: لو لسة جديد بس معاك حساب دولاري يبقي انصحك بـ IBKR علشان سهل ولكن لو معكش حساب دولاري يبقي Tastytrade علشان سهل الايداع بالكريبتو ## العملات الرقمية * **العملة**: دولار * **العائد المتوقع**: ~10% سنوياً (متغير) * **الحد الأدنى**: ~100 جنيه * **الورق المطلوب**: بطاقة * **المميزات**: - عائد يومي - استثمار دولاري - سهولة السحب * **العيوب**: - العائد متغير - مخاطر الأمان * **ملاحظات**: هنا قصدي منتجات Earn زي في بينانس ## ذهب (عالمي) * **العملة**: دولار * **العائد المتوقع**: متغير حسب سعر الذهب * **الحد الأدنى**: ~100 جنيه * **الورق المطلوب**: بطاقة * **المميزات**: - الذهب بسعر السوق العالمي - تحوط ضد التضخم * **العيوب**: - تقلبات السوق علي المدي القصير - استثمار طويل الأجل - مخاطر الامان * **ملاحظات**: الذهب العالمي قصدي انه تحول عملات ل PAXG في بينانس او Kraken ## عقارات (عالمي) * **العملة**: دولار * **العائد المتوقع**: ~9-10% سنوياً * **الحد الأدنى**: ~50 دولار في موقع Realt و ~135 لو موقع Stake * **الورق المطلوب**: باسبور * **المميزات**: - استثمار دولاري - عائد شهري * **العيوب**: - استثمار طويل الأجل - لو Stake فا تقدر تسحب فلوسك مرتين بالسنة بس - تحتاج باسبور - تقلبات السوق * **ملاحظات**: في تطبيقين RealT للسوق الامريكي و Stake للسوق الامراتي او السعودي ## فوري يومي * **العملة**: جنيه مصري * **العائد المتوقع**: ~24% * **الحد الأدنى**: ~3 جنيه * **الورق المطلوب**: بطاقة * **المميزات**: - سهولة الاستخدام - عائد يومي - بدون حد أدنى عالي * **العيوب**: - بالجنيه المصري - عائد أقل من شهادات البنك (الي الان) - تقلبات العائد * **ملاحظات**: قصدي تطبيق فوري يومي ## عقارات (محلي) * **العملة**: جنيه مصري * **العائد المتوقع**: الفعلي 9% ولكن متوقع 28-48% (متوسط 32%) * **الحد الأدنى**: 50,000 جنيه * **الورق المطلوب**: بطاقة * **المميزات**: - عائد سنوي مرتفع - العائد مربوط بالدولار بمعني لو حصل تعويم العائد بتاعك هيزيد فا مقاوم للتضخم. - سهولة الاستخدام * **العيوب**: - حجز الأموال 6 شهور - 50 ألف حد أدنى - ضرائب عقارية * **ملاحظات**: قصدي تطبيق Safe ## شهادات البنك * **العملة**: جنيه مصري * **العائد المتوقع**: 27% او 30% بعائد تناقصي * **الحد الأدنى**: 1000 جنيه * **الورق المطلوب**: بطاقة * **المميزات**: - عائد مرتفع * **العيوب**: - بالجنيه المصري - متقدرش تسحب فلوسك غير بعد مدة الشهادة. * **ملاحظات**: دخولك هنا او لا و العائد شهري او سنوي يبقي علي حسب هدفك ## ذهب (محلي) * **العملة**: جنيه مصري * **العائد المتوقع**: متغير حسب سعر الذهب * **الحد الأدنى**: ~18 جنيه * **الورق المطلوب**: بطاقة * **المميزات**: - قيمة ثابتة ومستقرة - سهولة الشراء - الحد الادني صغير لو سهم في صندوق زي AZG * **العيوب**: - يحتاج مبلغ عالي للدخول لو حقيقي - تقلبات السوق علي المدي القصير * **ملاحظات**: يعتبر خيار حلو بس انا شايف لو هتدخل بدهب يبقي عالمي + قصدي ذهب بجد او عن طريق صناديق الذهب زي AZG --- ## كمل قراية عن كل اختيار - البورصة الامريكية: nostr:naddr1qvzqqqr4gupzpu2h0sja0vmqdqjzq6e820jjjnuytzw2ksmemfnadhe0hm0zdws5qqxnzde5xvurzvfsxuerzvphcvddg0 - العملات الرقمية و الذهب العالمي: nostr:naddr1qvzqqqr4gupzpu2h0sja0vmqdqjzq6e820jjjnuytzw2ksmemfnadhe0hm0zdws5qqxnzde5xvunzvesx5erywpsepywcn - عقارات (عالمي): nostr:naddr1qvzqqqr4gupzpu2h0sja0vmqdqjzq6e820jjjnuytzw2ksmemfnadhe0hm0zdws5qqxnzde5xvunzdpcxq6nxwp3xqxgmx - فوري يومي: nostr:naddr1qvzqqqr4gupzpu2h0sja0vmqdqjzq6e820jjjnuytzw2ksmemfnadhe0hm0zdws5qqxnzde5xscrqdesxycnvv34l5ye0c - عقارات (مصري): nostr:naddr1qvzqqqr4gupzpu2h0sja0vmqdqjzq6e820jjjnuytzw2ksmemfnadhe0hm0zdws5qqxnzde5xvungvfsx5cnvv3ndwszwl - شهادات البنك (مصري): nostr:naddr1qvzqqqr4gupzpu2h0sja0vmqdqjzq6e820jjjnuytzw2ksmemfnadhe0hm0zdws5qqxnzde5xscrqdpnxc6rvvee3fqr5t - الذهب (مصري): nostr:naddr1qvzqqqr4gupzpu2h0sja0vmqdqjzq6e820jjjnuytzw2ksmemfnadhe0hm0zdws5qqxnzde5xscrqdesxucrjdehs24uge --- ## ادعمني (اختياري) * USDT (TRC20): `TKQ3Uwkq21ntiua2Zh9Hu376fdMdnRGWN6` --- آخر تحديث: 4 أبريل 2025 @ 57d1a264:69f1fee1
2025-04-05 06:47:55**Location:** Remote (Austria) **Area:** Graphics and communication design **Pay:** 37,500 € to 50,000 € / year Hi! We are @21bitcoinApp - a Bitcoin-Only Investment app that aims to accelerate the transition to an economy driven by Bitcoin. 👋 About the role As a passionate graphic designer, you support our marketing team in creating graphics and designs for print documents, online advertising material and our website. You also support us in the area of social media and content management and can also contribute your skills in these subject areas. **tasks** - Design and implementation of creative and congruent designs for social media channels, websites, templates and marketing materials - Creation of individual content (posts, stories, banners, ads) for social media - Planning and development of campaigns to strengthen the brand presence - Further development of the existing corporate design support in the area of content management (website, blog) **qualification** - Completed training or studies in graphic design - At least 2 years of experience in graphic design, preferably with experience in the areas of social media and content management - Safe use of design tools such as Figma, Adobe Creative Suite - Experience in creating social media content and maintaining channels - Creativity, good communication skills and team spirit - Very good knowledge of German and English - Knowledge of Bitcoin is desirable **Benefits** - Offsites with the team in exciting places - Flexible working hours in a company that relies on remote work - Help shape the future - to make the world a better place by helping to speed up Bitcoin's adaptation - Buy Bitcoin without fees! 21 Premium! - Gross annual salary & potential share options for outstanding performance / bonus payments **📝 Interview process** _How do I apply?_ Please send us an email and add some information about you, your resume, examples of previous projects and a few key points about why you are interested in participating in 21bitcoin and what you expect. By the way: CVs are important but don't forget to include your favorite Bitcoin meme in the application! _⁇ 京 Resume Review_ Portfolio of Work: Add a link to your portfolio / previous work or resume that we can review (LinkedIn, Github, Twitter, ...) _📞 Exploratory call_ We discuss what appeals to you about this role and ask you a few questions about your previous experiences _👬 On-Site Deep Dive_ During the deep dive session, we use a case study or extensive interview to discuss the specific skills required for the role. _👍 Time for a decision!_ [APPLY HERE](https://join.com/companies/21bitcoin/13877001-grafikdesigner) originally posted at https://stacker.news/items/935004
@ 57d1a264:69f1fee1
2025-04-05 06:47:55**Location:** Remote (Austria) **Area:** Graphics and communication design **Pay:** 37,500 € to 50,000 € / year Hi! We are @21bitcoinApp - a Bitcoin-Only Investment app that aims to accelerate the transition to an economy driven by Bitcoin. 👋 About the role As a passionate graphic designer, you support our marketing team in creating graphics and designs for print documents, online advertising material and our website. You also support us in the area of social media and content management and can also contribute your skills in these subject areas. **tasks** - Design and implementation of creative and congruent designs for social media channels, websites, templates and marketing materials - Creation of individual content (posts, stories, banners, ads) for social media - Planning and development of campaigns to strengthen the brand presence - Further development of the existing corporate design support in the area of content management (website, blog) **qualification** - Completed training or studies in graphic design - At least 2 years of experience in graphic design, preferably with experience in the areas of social media and content management - Safe use of design tools such as Figma, Adobe Creative Suite - Experience in creating social media content and maintaining channels - Creativity, good communication skills and team spirit - Very good knowledge of German and English - Knowledge of Bitcoin is desirable **Benefits** - Offsites with the team in exciting places - Flexible working hours in a company that relies on remote work - Help shape the future - to make the world a better place by helping to speed up Bitcoin's adaptation - Buy Bitcoin without fees! 21 Premium! - Gross annual salary & potential share options for outstanding performance / bonus payments **📝 Interview process** _How do I apply?_ Please send us an email and add some information about you, your resume, examples of previous projects and a few key points about why you are interested in participating in 21bitcoin and what you expect. By the way: CVs are important but don't forget to include your favorite Bitcoin meme in the application! _⁇ 京 Resume Review_ Portfolio of Work: Add a link to your portfolio / previous work or resume that we can review (LinkedIn, Github, Twitter, ...) _📞 Exploratory call_ We discuss what appeals to you about this role and ask you a few questions about your previous experiences _👬 On-Site Deep Dive_ During the deep dive session, we use a case study or extensive interview to discuss the specific skills required for the role. _👍 Time for a decision!_ [APPLY HERE](https://join.com/companies/21bitcoin/13877001-grafikdesigner) originally posted at https://stacker.news/items/935004 @ bc52210b:20bfc6de
2025-03-14 20:39:20When writing safety critical code, every arithmetic operation carries the potential for catastrophic failure—whether that’s a plane crash in aerospace engineering or a massive financial loss in a smart contract. The stakes are incredibly high, and errors are not just bugs; they’re disasters waiting to happen. Smart contract developers need to shift their mindset: less like web developers, who might prioritize speed and iteration, and more like aerospace engineers, where precision, caution, and meticulous attention to detail are non-negotiable. In practice, this means treating every line of code as a critical component, adopting rigorous testing, and anticipating worst-case scenarios—just as an aerospace engineer would ensure a system can withstand extreme conditions. Safety critical code demands aerospace-level precision, and smart contract developers must rise to that standard to protect against the severe consequences of failure.
@ bc52210b:20bfc6de
2025-03-14 20:39:20When writing safety critical code, every arithmetic operation carries the potential for catastrophic failure—whether that’s a plane crash in aerospace engineering or a massive financial loss in a smart contract. The stakes are incredibly high, and errors are not just bugs; they’re disasters waiting to happen. Smart contract developers need to shift their mindset: less like web developers, who might prioritize speed and iteration, and more like aerospace engineers, where precision, caution, and meticulous attention to detail are non-negotiable. In practice, this means treating every line of code as a critical component, adopting rigorous testing, and anticipating worst-case scenarios—just as an aerospace engineer would ensure a system can withstand extreme conditions. Safety critical code demands aerospace-level precision, and smart contract developers must rise to that standard to protect against the severe consequences of failure. @ 57d1a264:69f1fee1
2025-04-05 06:35:58We’re looking for a Product Designer to join our team and take the lead in enhancing the experience of our mobile app. You’ll play a key role in evolving the app’s interface and interactions, ensuring that our solutions are intuitive, efficient, and aligned with both user needs and business goals. **Key Responsibilities:** - Design and improve the @Bipa app experience, focusing on usability and measurable business impact. - Apply data-driven design, making decisions based on user research, metrics, and testing. - Lead and participate in usability tests and discovery processes to validate hypotheses and continuously improve the product. - Collaborate closely with Product Managers, developers, and other stakeholders to align design with product strategy. - Create wireframes, high-fidelity prototypes, and visual interfaces for new features and app optimizations. - Monitor the performance of delivered solutions, ensuring meaningful improvements for users and the business. - Contribute to the evolution and maintenance of our design system, ensuring consistency and scalability across the app. **Qualifications:** - Previous experience as a Product Designer or UX/UI Designer, with a strong focus on mobile apps. - Solid understanding of user-centered design (UCD) principles and usability heuristics. - Hands-on experience with user research methods, including usability testing, interviews, and behavior analysis. - Ability to work with both quantitative and qualitative data to guide design decisions. - Familiarity with product metrics and how design impacts business outcomes (e.g. conversion, retention, engagement). - Proficiency in design tools like Figma (or similar). - Experience working with design systems and design tokens to ensure consistency. - Comfortable working in an agile, fast-paced, and iterative environment. - Strong communication skills and the ability to advocate for design decisions backed by research and data. **Benefits:** 🏥 Health Insurance 💉 Dental Plan 🍽️ Meal Allowance (CAJU card) 💻 Home Office Stipend 📈 Stock Options from Day One [APPLY TO THIS JOB](https://bipa.inhire.app/vagas/14e45e99-2f7a-4a91-8f81-22393a3b7285/product-designer) originally posted at https://stacker.news/items/935003
@ 57d1a264:69f1fee1
2025-04-05 06:35:58We’re looking for a Product Designer to join our team and take the lead in enhancing the experience of our mobile app. You’ll play a key role in evolving the app’s interface and interactions, ensuring that our solutions are intuitive, efficient, and aligned with both user needs and business goals. **Key Responsibilities:** - Design and improve the @Bipa app experience, focusing on usability and measurable business impact. - Apply data-driven design, making decisions based on user research, metrics, and testing. - Lead and participate in usability tests and discovery processes to validate hypotheses and continuously improve the product. - Collaborate closely with Product Managers, developers, and other stakeholders to align design with product strategy. - Create wireframes, high-fidelity prototypes, and visual interfaces for new features and app optimizations. - Monitor the performance of delivered solutions, ensuring meaningful improvements for users and the business. - Contribute to the evolution and maintenance of our design system, ensuring consistency and scalability across the app. **Qualifications:** - Previous experience as a Product Designer or UX/UI Designer, with a strong focus on mobile apps. - Solid understanding of user-centered design (UCD) principles and usability heuristics. - Hands-on experience with user research methods, including usability testing, interviews, and behavior analysis. - Ability to work with both quantitative and qualitative data to guide design decisions. - Familiarity with product metrics and how design impacts business outcomes (e.g. conversion, retention, engagement). - Proficiency in design tools like Figma (or similar). - Experience working with design systems and design tokens to ensure consistency. - Comfortable working in an agile, fast-paced, and iterative environment. - Strong communication skills and the ability to advocate for design decisions backed by research and data. **Benefits:** 🏥 Health Insurance 💉 Dental Plan 🍽️ Meal Allowance (CAJU card) 💻 Home Office Stipend 📈 Stock Options from Day One [APPLY TO THIS JOB](https://bipa.inhire.app/vagas/14e45e99-2f7a-4a91-8f81-22393a3b7285/product-designer) originally posted at https://stacker.news/items/935003 @ e5de992e:4a95ef85
2025-04-07 08:23:48Historical Rapid Declines in the S&P 500: Lessons from Major Market Crashes The S&P 500 has experienced rapid declines of over 10% within short periods on several notable occasions, each linked to significant economic or geopolitical events. These instances underscore the market's vulnerability during times of crisis. --- ## October 19-20, 1987 (Black Monday Crash) - **Drop:** On October 19, 1987, the S&P 500 plummeted approximately **20.47%**, marking the largest single-day percentage decline in its history. The following day saw further losses, culminating in a two-day drop exceeding **25%**. - **Context:** Factors such as program trading, portfolio insurance strategies, and widespread panic selling contributed to this unprecedented crash. --- ## November 19-20, 2008 (Global Financial Crisis) - **Drop:** Amid the 2008 financial crisis, the S&P 500 declined roughly **10.8%** over two days, reflecting the turmoil following the collapse of major financial institutions. - **Context:** The bankruptcy of Lehman Brothers and escalating fears of a global recession led to this significant market downturn. --- ## March 11-12, 2020 (COVID-19 Pandemic Crash) - **Drop:** The rapid spread of COVID-19 and ensuing economic shutdowns triggered a two-day decline of approximately **12.2%** in the S&P 500. By March 16, the total decline over four days exceeded **20%**. - **Context:** The pandemic's uncertainty and global impact led to one of the fastest descents into bear market territory. --- ## April 3-4, 2025 (Trade War-Induced Crash) - **Drop:** Recently, the S&P 500 experienced a sharp decline of **10.5%** over two days, erasing approximately **$5 trillion** in market value. - **Context:** This downturn followed sweeping tariffs announced by President Donald Trump—a 10% baseline tariff on all imports, with higher rates on specific countries (e.g., China, the European Union). China's retaliatory tariffs intensified fears of a global trade war and a potential recession. --- ## Observations - **Frequency:** Such rapid declines are rare, occurring approximately once every 10-20 years, typically during periods of extreme market stress. - **Catalysts:** Each event was precipitated by unique factors: - Technological trading mechanisms in 1987 - Financial sector instability in 2008 - A global health crisis in 2020 - Geopolitical trade tensions in 2025 - **Market Resilience:** Despite these significant setbacks, markets have historically demonstrated resilience, often rebounding and reaching new highs in subsequent years. --- ## Conclusion Understanding these historical instances provides valuable insights into market dynamics and the potential impact of external shocks on financial systems. Recognizing the catalysts and observing market resilience over time can help investors navigate future downturns with a more informed perspective. ---
@ e5de992e:4a95ef85
2025-04-07 08:23:48Historical Rapid Declines in the S&P 500: Lessons from Major Market Crashes The S&P 500 has experienced rapid declines of over 10% within short periods on several notable occasions, each linked to significant economic or geopolitical events. These instances underscore the market's vulnerability during times of crisis. --- ## October 19-20, 1987 (Black Monday Crash) - **Drop:** On October 19, 1987, the S&P 500 plummeted approximately **20.47%**, marking the largest single-day percentage decline in its history. The following day saw further losses, culminating in a two-day drop exceeding **25%**. - **Context:** Factors such as program trading, portfolio insurance strategies, and widespread panic selling contributed to this unprecedented crash. --- ## November 19-20, 2008 (Global Financial Crisis) - **Drop:** Amid the 2008 financial crisis, the S&P 500 declined roughly **10.8%** over two days, reflecting the turmoil following the collapse of major financial institutions. - **Context:** The bankruptcy of Lehman Brothers and escalating fears of a global recession led to this significant market downturn. --- ## March 11-12, 2020 (COVID-19 Pandemic Crash) - **Drop:** The rapid spread of COVID-19 and ensuing economic shutdowns triggered a two-day decline of approximately **12.2%** in the S&P 500. By March 16, the total decline over four days exceeded **20%**. - **Context:** The pandemic's uncertainty and global impact led to one of the fastest descents into bear market territory. --- ## April 3-4, 2025 (Trade War-Induced Crash) - **Drop:** Recently, the S&P 500 experienced a sharp decline of **10.5%** over two days, erasing approximately **$5 trillion** in market value. - **Context:** This downturn followed sweeping tariffs announced by President Donald Trump—a 10% baseline tariff on all imports, with higher rates on specific countries (e.g., China, the European Union). China's retaliatory tariffs intensified fears of a global trade war and a potential recession. --- ## Observations - **Frequency:** Such rapid declines are rare, occurring approximately once every 10-20 years, typically during periods of extreme market stress. - **Catalysts:** Each event was precipitated by unique factors: - Technological trading mechanisms in 1987 - Financial sector instability in 2008 - A global health crisis in 2020 - Geopolitical trade tensions in 2025 - **Market Resilience:** Despite these significant setbacks, markets have historically demonstrated resilience, often rebounding and reaching new highs in subsequent years. --- ## Conclusion Understanding these historical instances provides valuable insights into market dynamics and the potential impact of external shocks on financial systems. Recognizing the catalysts and observing market resilience over time can help investors navigate future downturns with a more informed perspective. --- @ 57d1a264:69f1fee1
2025-04-05 06:28:16### ⚡️ About Us @AdoptingBTC is the leading Bitcoin-only conference in El Salvador. For our 5th edition, we’re looking for a passionate Video Creator intern to help showcase Bitcoin’s future as MONEY. ### ⚡️ The Role Create 30 short (3-minute or less) videos highlighting global circular economies, to be featured at AB25. We’ll provide all source material, direction, and inspiration—you’ll have full creative freedom, with feedback rounds to align with the conference’s vision. ### ⚡️ Responsibilities Produce 30 short videos on circular economies. Incorporate subtitles as needed. Submit videos on a deliverables basis. Participate in check-ins and communicate with the AB team and circular economy communities. ### ⚡️ What We Offer Free ticket to AB25. Networking with Bitcoiners and industry leaders. Letter of recommendation and LinkedIn endorsement upon completion. Mentorship and hands-on experience with a high-profile Bitcoin project. ### ⚡️ Skills & Qualifications Passion for Bitcoin and circular economies. Basic to intermediate video editing skills (no specific software required). Creative independence with feedback. Portfolio or work samples preferred. ### ⚡️ Time Commitment Flexible, project-based internship with check-ins and feedback rounds. ### ⚡️ How to Apply Email kiki@adoptingbitcoin.org with subject “Circular Economy Video Creator Submission - `{NAME OR NYM}`.” Include a brief background, your experience, why the project resonates with you, and a portfolio (if available). originally posted at https://stacker.news/items/935001
@ 57d1a264:69f1fee1
2025-04-05 06:28:16### ⚡️ About Us @AdoptingBTC is the leading Bitcoin-only conference in El Salvador. For our 5th edition, we’re looking for a passionate Video Creator intern to help showcase Bitcoin’s future as MONEY. ### ⚡️ The Role Create 30 short (3-minute or less) videos highlighting global circular economies, to be featured at AB25. We’ll provide all source material, direction, and inspiration—you’ll have full creative freedom, with feedback rounds to align with the conference’s vision. ### ⚡️ Responsibilities Produce 30 short videos on circular economies. Incorporate subtitles as needed. Submit videos on a deliverables basis. Participate in check-ins and communicate with the AB team and circular economy communities. ### ⚡️ What We Offer Free ticket to AB25. Networking with Bitcoiners and industry leaders. Letter of recommendation and LinkedIn endorsement upon completion. Mentorship and hands-on experience with a high-profile Bitcoin project. ### ⚡️ Skills & Qualifications Passion for Bitcoin and circular economies. Basic to intermediate video editing skills (no specific software required). Creative independence with feedback. Portfolio or work samples preferred. ### ⚡️ Time Commitment Flexible, project-based internship with check-ins and feedback rounds. ### ⚡️ How to Apply Email kiki@adoptingbitcoin.org with subject “Circular Economy Video Creator Submission - `{NAME OR NYM}`.” Include a brief background, your experience, why the project resonates with you, and a portfolio (if available). originally posted at https://stacker.news/items/935001 @ c631e267:c2b78d3e
2025-04-04 18:47:27*Zwei mal drei macht vier,* *\ widewidewitt und drei macht neune,* *\ ich mach mir die Welt,* *\ widewide wie sie mir gefällt.* *\ Pippi Langstrumpf*   **Egal, ob Koalitionsverhandlungen oder politischer Alltag:** Die Kontroversen zwischen theoretisch verschiedenen Parteien verschwinden, wenn es um den Kampf gegen politische Gegner mit [Rückenwind](https://transition-news.org/warum-die-politische-landschaft-einen-rechtsruck-erlebt) geht. Wer den Alteingesessenen die Pfründe ernsthaft streitig machen könnte, gegen den werden nicht nur «Brandmauern» errichtet, sondern der wird notfalls auch strafrechtlich verfolgt. Doppelstandards sind dabei selbstverständlich inklusive. **In Frankreich ist diese Woche Marine Le Pen wegen der Veruntreuung von EU-Geldern** von einem Gericht verurteilt worden. Als Teil der Strafe wurde sie für fünf Jahre vom passiven Wahlrecht ausgeschlossen. Obwohl das Urteil nicht rechtskräftig ist – Le Pen kann in Berufung gehen –, haben die Richter das Verbot, bei Wahlen anzutreten, mit sofortiger Wirkung verhängt. Die Vorsitzende des rechtsnationalen Rassemblement National (RN) galt als aussichtsreiche Kandidatin für die Präsidentschaftswahl 2027. **Das ist in diesem Jahr bereits der zweite gravierende Fall von Wahlbeeinflussung** durch die Justiz in einem EU-Staat. In Rumänien hatte Călin Georgescu im November die erste Runde der Präsidentenwahl überraschend gewonnen. Das Ergebnis wurde später annulliert, die behauptete «russische Wahlmanipulation» konnte jedoch nicht bewiesen werden. Die Kandidatur für die [Wahlwiederholung](https://transition-news.org/rumanische-prasidentenwahlen-weitere-ungereimtheiten-kandidatenfeld-fix) im Mai wurde Georgescu kürzlich durch das Verfassungsgericht untersagt. **Die Veruntreuung öffentlicher Gelder muss untersucht und geahndet werden,** das steht außer Frage. Diese Anforderung darf nicht selektiv angewendet werden. Hingegen mussten wir in der Vergangenheit bei ungleich schwerwiegenderen Fällen von (mutmaßlichem) Missbrauch ganz andere Vorgehensweisen erleben, etwa im Fall der heutigen EZB-Chefin Christine [Lagarde](https://archive.is/20ZFq) oder im [«Pfizergate»](https://transition-news.org/pfizergate-klage-gegen-von-der-leyen-in-luttich-als-unzulassig-erklart)-Skandal um die Präsidentin der EU-Kommission Ursula von der Leyen. **Wenngleich derartige Angelegenheiten formal auf einer rechtsstaatlichen Grundlage beruhen mögen,** so bleibt ein bitterer Beigeschmack. Es stellt sich die Frage, ob und inwieweit die Justiz politisch instrumentalisiert wird. Dies ist umso interessanter, als die Gewaltenteilung einen essenziellen Teil jeder demokratischen Ordnung darstellt, während die Bekämpfung des politischen Gegners mit juristischen Mitteln gerade bei den am lautesten rufenden Verteidigern «unserer Demokratie» populär zu sein scheint. **Die Delegationen von CDU/CSU und SPD haben bei ihren Verhandlungen** über eine Regierungskoalition genau solche Maßnahmen diskutiert. «Im Namen der Wahrheit und der Demokratie» möchte man noch härter gegen «Desinformation» vorgehen und dafür zum Beispiel den Digital Services Act der EU erweitern. Auch soll der Tatbestand der Volksverhetzung verschärft werden – und im Entzug des passiven Wahlrechts münden können. Auf europäischer Ebene würde Friedrich Merz wohl gerne Ungarn das [Stimmrecht](https://transition-news.org/die-zeit-ist-reif-orban-zu-bestrafen-sagt-deutschlands-nachste-regierung) entziehen. **Der Pegel an Unzufriedenheit und Frustration wächst** in großen Teilen der Bevölkerung kontinuierlich. Arroganz, Machtmissbrauch und immer abstrusere Ausreden für offensichtlich willkürliche Maßnahmen werden kaum verhindern, dass den etablierten Parteien die Unterstützung entschwindet. In Deutschland sind die [Umfrageergebnisse](https://archive.is/kf4Tk) der AfD ein guter Gradmesser dafür. *\[Vorlage Titelbild:* *[Pixabay](https://pixabay.com/de/illustrations/gesetz-gerechtigkeit-flagge-europa-6598281/)]* *** Dieser Beitrag wurde mit dem [Pareto-Client](https://pareto.space/read) geschrieben und ist zuerst auf ***[Transition News](https://transition-news.org/wird-politische-justiz-zu-einer-demokratischen-tugend)*** erschienen.
@ c631e267:c2b78d3e
2025-04-04 18:47:27*Zwei mal drei macht vier,* *\ widewidewitt und drei macht neune,* *\ ich mach mir die Welt,* *\ widewide wie sie mir gefällt.* *\ Pippi Langstrumpf*   **Egal, ob Koalitionsverhandlungen oder politischer Alltag:** Die Kontroversen zwischen theoretisch verschiedenen Parteien verschwinden, wenn es um den Kampf gegen politische Gegner mit [Rückenwind](https://transition-news.org/warum-die-politische-landschaft-einen-rechtsruck-erlebt) geht. Wer den Alteingesessenen die Pfründe ernsthaft streitig machen könnte, gegen den werden nicht nur «Brandmauern» errichtet, sondern der wird notfalls auch strafrechtlich verfolgt. Doppelstandards sind dabei selbstverständlich inklusive. **In Frankreich ist diese Woche Marine Le Pen wegen der Veruntreuung von EU-Geldern** von einem Gericht verurteilt worden. Als Teil der Strafe wurde sie für fünf Jahre vom passiven Wahlrecht ausgeschlossen. Obwohl das Urteil nicht rechtskräftig ist – Le Pen kann in Berufung gehen –, haben die Richter das Verbot, bei Wahlen anzutreten, mit sofortiger Wirkung verhängt. Die Vorsitzende des rechtsnationalen Rassemblement National (RN) galt als aussichtsreiche Kandidatin für die Präsidentschaftswahl 2027. **Das ist in diesem Jahr bereits der zweite gravierende Fall von Wahlbeeinflussung** durch die Justiz in einem EU-Staat. In Rumänien hatte Călin Georgescu im November die erste Runde der Präsidentenwahl überraschend gewonnen. Das Ergebnis wurde später annulliert, die behauptete «russische Wahlmanipulation» konnte jedoch nicht bewiesen werden. Die Kandidatur für die [Wahlwiederholung](https://transition-news.org/rumanische-prasidentenwahlen-weitere-ungereimtheiten-kandidatenfeld-fix) im Mai wurde Georgescu kürzlich durch das Verfassungsgericht untersagt. **Die Veruntreuung öffentlicher Gelder muss untersucht und geahndet werden,** das steht außer Frage. Diese Anforderung darf nicht selektiv angewendet werden. Hingegen mussten wir in der Vergangenheit bei ungleich schwerwiegenderen Fällen von (mutmaßlichem) Missbrauch ganz andere Vorgehensweisen erleben, etwa im Fall der heutigen EZB-Chefin Christine [Lagarde](https://archive.is/20ZFq) oder im [«Pfizergate»](https://transition-news.org/pfizergate-klage-gegen-von-der-leyen-in-luttich-als-unzulassig-erklart)-Skandal um die Präsidentin der EU-Kommission Ursula von der Leyen. **Wenngleich derartige Angelegenheiten formal auf einer rechtsstaatlichen Grundlage beruhen mögen,** so bleibt ein bitterer Beigeschmack. Es stellt sich die Frage, ob und inwieweit die Justiz politisch instrumentalisiert wird. Dies ist umso interessanter, als die Gewaltenteilung einen essenziellen Teil jeder demokratischen Ordnung darstellt, während die Bekämpfung des politischen Gegners mit juristischen Mitteln gerade bei den am lautesten rufenden Verteidigern «unserer Demokratie» populär zu sein scheint. **Die Delegationen von CDU/CSU und SPD haben bei ihren Verhandlungen** über eine Regierungskoalition genau solche Maßnahmen diskutiert. «Im Namen der Wahrheit und der Demokratie» möchte man noch härter gegen «Desinformation» vorgehen und dafür zum Beispiel den Digital Services Act der EU erweitern. Auch soll der Tatbestand der Volksverhetzung verschärft werden – und im Entzug des passiven Wahlrechts münden können. Auf europäischer Ebene würde Friedrich Merz wohl gerne Ungarn das [Stimmrecht](https://transition-news.org/die-zeit-ist-reif-orban-zu-bestrafen-sagt-deutschlands-nachste-regierung) entziehen. **Der Pegel an Unzufriedenheit und Frustration wächst** in großen Teilen der Bevölkerung kontinuierlich. Arroganz, Machtmissbrauch und immer abstrusere Ausreden für offensichtlich willkürliche Maßnahmen werden kaum verhindern, dass den etablierten Parteien die Unterstützung entschwindet. In Deutschland sind die [Umfrageergebnisse](https://archive.is/kf4Tk) der AfD ein guter Gradmesser dafür. *\[Vorlage Titelbild:* *[Pixabay](https://pixabay.com/de/illustrations/gesetz-gerechtigkeit-flagge-europa-6598281/)]* *** Dieser Beitrag wurde mit dem [Pareto-Client](https://pareto.space/read) geschrieben und ist zuerst auf ***[Transition News](https://transition-news.org/wird-politische-justiz-zu-einer-demokratischen-tugend)*** erschienen. @ e5de992e:4a95ef85
2025-04-07 05:42:26The stock market is currently experiencing a significant downturn, with major indices such as the S&P 500 and the Dow Jones Industrial Average recording substantial losses. This decline is largely attributed to the recent implementation of sweeping tariffs by President Donald Trump, including a 10% levy on all imports and higher duties on exports from key trading partners like China, the European Union, Japan, and Vietnam. These measures have ignited fears of a global trade war, leading to a massive sell-off in the markets. Notably, the S&P 500 dropped 6%, the Nasdaq slid 5.8%, and the Dow Jones fell by 2,231 points—some of the steepest declines since the early days of the COVID-19 pandemic. --- ## Everyday Patience Versus Irrational Trading In everyday life, consumers often exhibit patience by waiting for prices to drop before making purchases: - **Seasonal Sales:** Shoppers wait for discounts to buy clothing. - **Tech Promotions:** Tech enthusiasts delay buying electronics until promotional events. - **Real Estate:** Prospective homebuyers hold off during market slowdowns to secure better deals. This common-sense approach maximizes value and minimizes expenditure. In contrast, many stock market traders fall prey to irrational behaviors: - **Fear of Missing Out (FOMO):** Investors buy stocks at high prices, worried they might miss potential gains. - **Herd Mentality:** Individuals mimic the actions of the majority, often buying during market highs and selling during lows. These emotional decisions often lead to poor outcomes, as they contradict the logical approach of waiting for favorable prices. --- ## The Risks of Ignoring Rational Investment Principles Irrational trading practices can result in significant financial losses. By purchasing stocks at inflated prices during market euphoria, investors expose themselves to sharp declines when corrections occur. Unlike unpredictable black swan events, these losses stem from market corrections that follow overvaluation periods. Ignoring fundamental investment principles can, therefore, be more damaging than unforeseen events. citeturn0search4 --- ## A Balanced Approach to Investing A more balanced approach involves: - **Risk Management Strategies:** Diversify across asset classes to mitigate potential losses. - **Maintaining a Long-Term Perspective:** Adhere to disciplined investment plans to avoid impulsive decisions. - **Understanding Your Risk Tolerance:** Set stop-loss orders and know your limits to protect against downturns. These strategies help investors avoid pitfalls driven by FOMO and herd mentality. --- ## Conclusion While the current market downturn presents challenges, it also serves as a reminder of the importance of rational investment behavior. By drawing parallels from everyday purchasing decisions, investors can appreciate the value of patience and strategic planning. Embracing risk management techniques and resisting psychological pitfalls like FOMO and herd mentality can lead to more resilient and successful investment outcomes.
@ e5de992e:4a95ef85
2025-04-07 05:42:26The stock market is currently experiencing a significant downturn, with major indices such as the S&P 500 and the Dow Jones Industrial Average recording substantial losses. This decline is largely attributed to the recent implementation of sweeping tariffs by President Donald Trump, including a 10% levy on all imports and higher duties on exports from key trading partners like China, the European Union, Japan, and Vietnam. These measures have ignited fears of a global trade war, leading to a massive sell-off in the markets. Notably, the S&P 500 dropped 6%, the Nasdaq slid 5.8%, and the Dow Jones fell by 2,231 points—some of the steepest declines since the early days of the COVID-19 pandemic. --- ## Everyday Patience Versus Irrational Trading In everyday life, consumers often exhibit patience by waiting for prices to drop before making purchases: - **Seasonal Sales:** Shoppers wait for discounts to buy clothing. - **Tech Promotions:** Tech enthusiasts delay buying electronics until promotional events. - **Real Estate:** Prospective homebuyers hold off during market slowdowns to secure better deals. This common-sense approach maximizes value and minimizes expenditure. In contrast, many stock market traders fall prey to irrational behaviors: - **Fear of Missing Out (FOMO):** Investors buy stocks at high prices, worried they might miss potential gains. - **Herd Mentality:** Individuals mimic the actions of the majority, often buying during market highs and selling during lows. These emotional decisions often lead to poor outcomes, as they contradict the logical approach of waiting for favorable prices. --- ## The Risks of Ignoring Rational Investment Principles Irrational trading practices can result in significant financial losses. By purchasing stocks at inflated prices during market euphoria, investors expose themselves to sharp declines when corrections occur. Unlike unpredictable black swan events, these losses stem from market corrections that follow overvaluation periods. Ignoring fundamental investment principles can, therefore, be more damaging than unforeseen events. citeturn0search4 --- ## A Balanced Approach to Investing A more balanced approach involves: - **Risk Management Strategies:** Diversify across asset classes to mitigate potential losses. - **Maintaining a Long-Term Perspective:** Adhere to disciplined investment plans to avoid impulsive decisions. - **Understanding Your Risk Tolerance:** Set stop-loss orders and know your limits to protect against downturns. These strategies help investors avoid pitfalls driven by FOMO and herd mentality. --- ## Conclusion While the current market downturn presents challenges, it also serves as a reminder of the importance of rational investment behavior. By drawing parallels from everyday purchasing decisions, investors can appreciate the value of patience and strategic planning. Embracing risk management techniques and resisting psychological pitfalls like FOMO and herd mentality can lead to more resilient and successful investment outcomes. @ ee6ea13a:959b6e74
2025-04-06 16:38:22## Chef's notes You can cook this in one pan on the stove. I use a cast iron pan, but you can make it in a wok or any deep pan. I serve mine over rice, which I make in a rice cooker. If you have a fancy one, you might have a setting for sticky or scorched rice, so give one of those a try. To plate this, I scoop rice into a bowl, and then turn it upside-down to give it a dome shape, then spoon the curry on top of it. Serve with chopped cilantro and lime wedges. ## Details - ⏲️ Prep time: 20 - 🍳 Cook time: 20 - 🍽️ Servings: 4 ## Ingredients - 1 ½ pounds boneless skinless chicken breast, cut into 2" pieces - 2 tablespoons coconut or avocado oil - 1 cup white or yellow onion, finely diced - 1 cup red bell pepper, sliced or diced - 4 large garlic cloves, minced - 1 small (4oz) jar of Thai red curry paste - 1 can (13oz) unsweetened coconut milk - 1 teaspoon ground ginger - 1 teaspoon ground coriander - 1 tablespoon soy sauce - 1 tablespoon brown sugar - 1 cup carrots, shredded or julienned - 1 lime, zest and juice - ¼ cup fresh cilantro, chopped for garnish ## Directions 1. Heat oil in a large skillet over medium-high. Once hot, add onions and ½ teaspoon salt. Cook 3 minutes, or until onions are softened, stirring often. 2. Add the red curry paste, garlic, ginger, and coriander. Cook about 1 minute, or until fragrant, stirring often. 3. Add coconut milk, brown sugar, soy sauce, and chicken. Stir, bring to a simmer, then reduce heat to medium. Simmer uncovered for 7 minutes, occasionally stirring. 4. Add carrots and red bell peppers, and simmer 5-7 more minutes, until sauce slightly thickens and chicken is cooked through. 5. Remove from heat, and stir in the lime zest, and half of the lime juice. 6. Serve over rice, topped with cilantro, and add more lime juice if you like extra citrus.
@ ee6ea13a:959b6e74
2025-04-06 16:38:22## Chef's notes You can cook this in one pan on the stove. I use a cast iron pan, but you can make it in a wok or any deep pan. I serve mine over rice, which I make in a rice cooker. If you have a fancy one, you might have a setting for sticky or scorched rice, so give one of those a try. To plate this, I scoop rice into a bowl, and then turn it upside-down to give it a dome shape, then spoon the curry on top of it. Serve with chopped cilantro and lime wedges. ## Details - ⏲️ Prep time: 20 - 🍳 Cook time: 20 - 🍽️ Servings: 4 ## Ingredients - 1 ½ pounds boneless skinless chicken breast, cut into 2" pieces - 2 tablespoons coconut or avocado oil - 1 cup white or yellow onion, finely diced - 1 cup red bell pepper, sliced or diced - 4 large garlic cloves, minced - 1 small (4oz) jar of Thai red curry paste - 1 can (13oz) unsweetened coconut milk - 1 teaspoon ground ginger - 1 teaspoon ground coriander - 1 tablespoon soy sauce - 1 tablespoon brown sugar - 1 cup carrots, shredded or julienned - 1 lime, zest and juice - ¼ cup fresh cilantro, chopped for garnish ## Directions 1. Heat oil in a large skillet over medium-high. Once hot, add onions and ½ teaspoon salt. Cook 3 minutes, or until onions are softened, stirring often. 2. Add the red curry paste, garlic, ginger, and coriander. Cook about 1 minute, or until fragrant, stirring often. 3. Add coconut milk, brown sugar, soy sauce, and chicken. Stir, bring to a simmer, then reduce heat to medium. Simmer uncovered for 7 minutes, occasionally stirring. 4. Add carrots and red bell peppers, and simmer 5-7 more minutes, until sauce slightly thickens and chicken is cooked through. 5. Remove from heat, and stir in the lime zest, and half of the lime juice. 6. Serve over rice, topped with cilantro, and add more lime juice if you like extra citrus. @ c631e267:c2b78d3e
2025-04-03 07:42:25**Spanien bleibt einer der Vorreiter im europäischen Prozess der totalen Überwachung** per Digitalisierung. Seit Mittwoch ist dort der digitale Personalausweis verfügbar. Dabei handelt es sich um eine Regierungs-[App](https://play.google.com/store/apps/details?id=es.gob.interior.policia.midni), die auf dem Smartphone installiert werden muss und in den Stores von Google und Apple zu finden ist. Per Dekret von Regierungschef Pedro Sánchez und Zustimmung des Ministerrats ist diese Maßnahme jetzt [in Kraft](https://archive.is/89H4i) getreten. **Mit den üblichen Argumenten der Vereinfachung,** des Komforts, der Effizienz und der Sicherheit preist das Innenministerium die «Innovation» an. Auch die Beteuerung, dass die digitale Variante parallel zum physischen Ausweis existieren wird und diesen nicht ersetzen soll, fehlt nicht. Während der ersten zwölf Monate wird «der Neue» noch nicht für alle Anwendungsfälle gültig sein, ab 2026 aber schon. **Dass die ganze Sache auch «Risiken und Nebenwirkungen» haben könnte,** wird in den Mainstream-Medien eher selten thematisiert. Bestenfalls wird der Aspekt der Datensicherheit angesprochen, allerdings in der Regel direkt mit dem Regierungsvokabular von den «maximalen Sicherheitsgarantien» abgehandelt. Dennoch gibt es einige weitere Aspekte, die Bürger mit etwas Sinn für Privatsphäre bedenken sollten. **Um sich die digitale Version des nationalen Ausweises besorgen zu können** (eine App mit dem Namen MiDNI), muss man sich vorab online [registrieren](https://www.midni.gob.es). Dabei wird die Identität des Bürgers mit seiner mobilen Telefonnummer verknüpft. Diese obligatorische fixe Verdrahtung kennen wir von diversen anderen Apps und Diensten. Gleichzeitig ist das die Basis für eine perfekte Lokalisierbarkeit der Person. **Für jeden Vorgang der Identifikation in der Praxis wird später** «eine Verbindung zu den Servern der Bundespolizei aufgebaut». Die Daten des Individuums werden «in Echtzeit» verifiziert und im Erfolgsfall von der Polizei signiert zurückgegeben. Das Ergebnis ist ein QR-Code mit zeitlich begrenzter Gültigkeit, der an Dritte weitergegeben werden kann. **Bei derartigen Szenarien sträuben sich einem halbwegs kritischen Staatsbürger die Nackenhaare.** Allein diese minimale Funktionsbeschreibung lässt die totale Überwachung erkennen, die damit ermöglicht wird. Jede Benutzung des Ausweises wird künftig registriert, hinterlässt also Spuren. Und was ist, wenn die Server der Polizei einmal kein grünes Licht geben? Das wäre spätestens dann ein Problem, wenn der digitale doch irgendwann der einzig gültige Ausweis ist: Dann haben wir den abschaltbaren Bürger. **Dieser neue Vorstoß der Regierung von Pedro Sánchez ist ein weiterer Schritt** in Richtung der [«totalen Digitalisierung»](https://archive.is/Gwc4B) des Landes, wie diese Politik in manchen Medien – nicht einmal kritisch, sondern sehr naiv – genannt wird. Ebenso verharmlosend wird auch erwähnt, dass sich das spanische Projekt des digitalen Ausweises nahtlos in die Initiativen der EU zu einer digitalen Identität für alle Bürger sowie des digitalen Euro einreiht. **In Zukunft könnte der neue Ausweis** «auch in andere staatliche und private digitale Plattformen integriert werden», wie das Medienportal *Cope* ganz richtig bemerkt. Das ist die Perspektive. *\[Titelbild:* *[Pixabay](https://pixabay.com/de/photos/liebe-love-herz-rose-bindung-3141742/)]* *Dazu passend:* [Nur Abschied vom Alleinfahren? Monströse spanische Überwachungsprojekte gemäß EU-Norm](https://pareto.space/a/naddr1qqxnzde5xg6r2wphxscryvpjqgs2jhrzgwzvvzgz42kfmef2kr7w8x573k4r62c5ydjh8gyn6dz4ytqrqsqqqa28fq5d4m) *** Dieser Beitrag wurde mit dem [Pareto-Client](https://pareto.space/read) geschrieben und ist zuerst auf ***[Transition News](https://transition-news.org/spanien-erneut-europaisches-versuchslabor-der-digitale-ausweis-ist-da)*** erschienen.
@ c631e267:c2b78d3e
2025-04-03 07:42:25**Spanien bleibt einer der Vorreiter im europäischen Prozess der totalen Überwachung** per Digitalisierung. Seit Mittwoch ist dort der digitale Personalausweis verfügbar. Dabei handelt es sich um eine Regierungs-[App](https://play.google.com/store/apps/details?id=es.gob.interior.policia.midni), die auf dem Smartphone installiert werden muss und in den Stores von Google und Apple zu finden ist. Per Dekret von Regierungschef Pedro Sánchez und Zustimmung des Ministerrats ist diese Maßnahme jetzt [in Kraft](https://archive.is/89H4i) getreten. **Mit den üblichen Argumenten der Vereinfachung,** des Komforts, der Effizienz und der Sicherheit preist das Innenministerium die «Innovation» an. Auch die Beteuerung, dass die digitale Variante parallel zum physischen Ausweis existieren wird und diesen nicht ersetzen soll, fehlt nicht. Während der ersten zwölf Monate wird «der Neue» noch nicht für alle Anwendungsfälle gültig sein, ab 2026 aber schon. **Dass die ganze Sache auch «Risiken und Nebenwirkungen» haben könnte,** wird in den Mainstream-Medien eher selten thematisiert. Bestenfalls wird der Aspekt der Datensicherheit angesprochen, allerdings in der Regel direkt mit dem Regierungsvokabular von den «maximalen Sicherheitsgarantien» abgehandelt. Dennoch gibt es einige weitere Aspekte, die Bürger mit etwas Sinn für Privatsphäre bedenken sollten. **Um sich die digitale Version des nationalen Ausweises besorgen zu können** (eine App mit dem Namen MiDNI), muss man sich vorab online [registrieren](https://www.midni.gob.es). Dabei wird die Identität des Bürgers mit seiner mobilen Telefonnummer verknüpft. Diese obligatorische fixe Verdrahtung kennen wir von diversen anderen Apps und Diensten. Gleichzeitig ist das die Basis für eine perfekte Lokalisierbarkeit der Person. **Für jeden Vorgang der Identifikation in der Praxis wird später** «eine Verbindung zu den Servern der Bundespolizei aufgebaut». Die Daten des Individuums werden «in Echtzeit» verifiziert und im Erfolgsfall von der Polizei signiert zurückgegeben. Das Ergebnis ist ein QR-Code mit zeitlich begrenzter Gültigkeit, der an Dritte weitergegeben werden kann. **Bei derartigen Szenarien sträuben sich einem halbwegs kritischen Staatsbürger die Nackenhaare.** Allein diese minimale Funktionsbeschreibung lässt die totale Überwachung erkennen, die damit ermöglicht wird. Jede Benutzung des Ausweises wird künftig registriert, hinterlässt also Spuren. Und was ist, wenn die Server der Polizei einmal kein grünes Licht geben? Das wäre spätestens dann ein Problem, wenn der digitale doch irgendwann der einzig gültige Ausweis ist: Dann haben wir den abschaltbaren Bürger. **Dieser neue Vorstoß der Regierung von Pedro Sánchez ist ein weiterer Schritt** in Richtung der [«totalen Digitalisierung»](https://archive.is/Gwc4B) des Landes, wie diese Politik in manchen Medien – nicht einmal kritisch, sondern sehr naiv – genannt wird. Ebenso verharmlosend wird auch erwähnt, dass sich das spanische Projekt des digitalen Ausweises nahtlos in die Initiativen der EU zu einer digitalen Identität für alle Bürger sowie des digitalen Euro einreiht. **In Zukunft könnte der neue Ausweis** «auch in andere staatliche und private digitale Plattformen integriert werden», wie das Medienportal *Cope* ganz richtig bemerkt. Das ist die Perspektive. *\[Titelbild:* *[Pixabay](https://pixabay.com/de/photos/liebe-love-herz-rose-bindung-3141742/)]* *Dazu passend:* [Nur Abschied vom Alleinfahren? Monströse spanische Überwachungsprojekte gemäß EU-Norm](https://pareto.space/a/naddr1qqxnzde5xg6r2wphxscryvpjqgs2jhrzgwzvvzgz42kfmef2kr7w8x573k4r62c5ydjh8gyn6dz4ytqrqsqqqa28fq5d4m) *** Dieser Beitrag wurde mit dem [Pareto-Client](https://pareto.space/read) geschrieben und ist zuerst auf ***[Transition News](https://transition-news.org/spanien-erneut-europaisches-versuchslabor-der-digitale-ausweis-ist-da)*** erschienen. @ fe32b72c:14cfcb1e
2025-04-06 15:56:23### Libertarian tariff controversy GM. First long form note, so let's see how this goes. Reading a lot of Libertarians complaining about tariffs on twitter this morning. And I get it — they're a tax on imports, and furthermore, a barrier to free trade. Not exactly something libertarians are fans of, lowercase "l" or doctrinaire capital "L" party members. But there's something I've been pointing out to many. That is: being the issuer of the global reserve currency (which itself relies upon inflation, and thus is *also* a tax) necessarily creates trade deficits. I'm preaching to the choir on this one a bit I expect, but it's a key reason as to why *given* that we have this backdrop, and we can't simply overnight completely change the monetary system, it is not an unreasonable stance for a libertarian leaning person to hold the idea that using tariffs as a way to offset this trade deficit *while* moving away from a fiat currency is actually a sound idea. There are plenty of places for devils to hide in details of course, and by all means, I'm not a Trumpist, but speaking generally, this seems like a sound stance. It's all well and good to have an idea of where you want to go, but if you want to actually get there, charting a course is often harder than picking a destination. ### Now, as for what I think we can expect Tariffs will raise consumer prices. It's not inflation, because it's not about an expansion of the money supply, but it's also true that the cost has to be born by someone. However, tariffs will also decrease imports. Which will reduce dollar outflows into foreign nations, where, thanks to the mechanics of the Eurodollar system, will create a panic. The reality is, dollars outside of the US are *not* something that is created by the Federal Reserve, because foreign banks *can't* hold reserves. Rather, Eurodollar deposits are loaned into existence by private banks, and are generally settled by a variety of creative means, including offsetting liabilities, and sale of assets — most commonly, US Treasury securities. This means they *need* dollars to flow — it's not about getting wealthier, but rather, about covering their debts that they simply have no way to bail out. Reduced dollar outflow is a reduction in supply; as such, the price of the dollar goes up (or at least, goes down slower). That is, there's deflation, or at least disinflation. The end result is, those prices that went up thanks to tariffs start going back down to American consumers. Meanwhile, dollars being more expensive than they were when liabilities were taken on likely leads to recessionary conditions — both domestically and internationally. However, companies importing goods into the US that can onshore their production will seek to do so, which will have an effect of offsetting that recessionary impulse domestically. In effect, "exporting" the recession. ### As for what this means for the national debt The national debt of course has been a sore point given that interest expense has been astronomical, and rolling the debt has been necessary thanks to Yellen's failure to term it out. Foreign parties will of course *want* more treasury assets, as a way to cover their dollar liabilities amid diminished dollar flow, but it doesn't take a doctorate to know that desires and needs are not the same thing as increased aggregate demand. Some may have good enough credit to borrow more dollars from American banks, and thus, buy treasuries, which would of course be good for bringing down interest rates, but I'm not sure I'd bet too much on that horse, especially amid an environment where recession is being exported. There is a fair bit of exposure to US equities abroad that may rotate into American sovereign debt, though the time to do that was probably *before* 10% of the value got evaporated off of that over the past week. There may be increased domestic demand for treasuries, as all of this on-shoring means a lot of running in place, so to speak, by companies pivoting to domestic production, and thus under performance by equities. This is a place I'd be curious about the overall impact on the Treasury market, and am certainly not qualified to weigh in on it. But I'd *love* to see some sober analysis by those who recognize it as worth taking a closer look at. Then there's the Fed, which is almost an afterthought for me, given that they're simply **not** going to do the levels of QE that it would take to actually bring interest rates on long term debt down, but it is worth pointing out that amid the churning deflation there will likely be at least a few rate cuts that come into play. Note, however, that rate cuts only help so much, as they directly affect the immediate end of the curve, with very little impact on the longer end where it's needed, regardless of what Greenspan would have you believe about "series of forward rates." That said, as inflation expectations come down, it may be that longer tenor rates come do down as well, because inflation expectations are an actual driver of rates, rather than Fed Funds policy rates, but that may take longer than the Treasury can wait for. That said, US10Y rates are already down 26 bps in a week, so things do seem to be starting out in the right direction. We'll see if that holds once issuance starts ramping up. ### Where this all leaves us There seem to me to be too many variables to really predict how this all plays out on the treasury market, which is hard enough to predict given that it's the largest asset class in the world. I'm inclined to think Bessent knows what he's doing (and that Trump is at least smart enough to listen to him, if not game it all out himself). What's clear is that he's trying *something* to address the bigger issue rather than simply kick the can down the road, which is more than we can say of policymakers for at least the past half century, and likely longer. With any luck all of this turbulence will drive further adoption by Bitcoin, as foreign nations need to resort to something to get them out of their crushing dollar denominated liabilities. At the end of the day, being free of *both* taxes on imports *and* "invisible" taxes by deflation should be something we can all cheer for. In the meantime, hopefully this article has given a bit of perspective on what developments will be of interest in the bond market as this fourth turning plays out. #Finance #Tariffs #Bitcoin #NationalDebt #Libertarianism #FreeTrade
@ fe32b72c:14cfcb1e
2025-04-06 15:56:23### Libertarian tariff controversy GM. First long form note, so let's see how this goes. Reading a lot of Libertarians complaining about tariffs on twitter this morning. And I get it — they're a tax on imports, and furthermore, a barrier to free trade. Not exactly something libertarians are fans of, lowercase "l" or doctrinaire capital "L" party members. But there's something I've been pointing out to many. That is: being the issuer of the global reserve currency (which itself relies upon inflation, and thus is *also* a tax) necessarily creates trade deficits. I'm preaching to the choir on this one a bit I expect, but it's a key reason as to why *given* that we have this backdrop, and we can't simply overnight completely change the monetary system, it is not an unreasonable stance for a libertarian leaning person to hold the idea that using tariffs as a way to offset this trade deficit *while* moving away from a fiat currency is actually a sound idea. There are plenty of places for devils to hide in details of course, and by all means, I'm not a Trumpist, but speaking generally, this seems like a sound stance. It's all well and good to have an idea of where you want to go, but if you want to actually get there, charting a course is often harder than picking a destination. ### Now, as for what I think we can expect Tariffs will raise consumer prices. It's not inflation, because it's not about an expansion of the money supply, but it's also true that the cost has to be born by someone. However, tariffs will also decrease imports. Which will reduce dollar outflows into foreign nations, where, thanks to the mechanics of the Eurodollar system, will create a panic. The reality is, dollars outside of the US are *not* something that is created by the Federal Reserve, because foreign banks *can't* hold reserves. Rather, Eurodollar deposits are loaned into existence by private banks, and are generally settled by a variety of creative means, including offsetting liabilities, and sale of assets — most commonly, US Treasury securities. This means they *need* dollars to flow — it's not about getting wealthier, but rather, about covering their debts that they simply have no way to bail out. Reduced dollar outflow is a reduction in supply; as such, the price of the dollar goes up (or at least, goes down slower). That is, there's deflation, or at least disinflation. The end result is, those prices that went up thanks to tariffs start going back down to American consumers. Meanwhile, dollars being more expensive than they were when liabilities were taken on likely leads to recessionary conditions — both domestically and internationally. However, companies importing goods into the US that can onshore their production will seek to do so, which will have an effect of offsetting that recessionary impulse domestically. In effect, "exporting" the recession. ### As for what this means for the national debt The national debt of course has been a sore point given that interest expense has been astronomical, and rolling the debt has been necessary thanks to Yellen's failure to term it out. Foreign parties will of course *want* more treasury assets, as a way to cover their dollar liabilities amid diminished dollar flow, but it doesn't take a doctorate to know that desires and needs are not the same thing as increased aggregate demand. Some may have good enough credit to borrow more dollars from American banks, and thus, buy treasuries, which would of course be good for bringing down interest rates, but I'm not sure I'd bet too much on that horse, especially amid an environment where recession is being exported. There is a fair bit of exposure to US equities abroad that may rotate into American sovereign debt, though the time to do that was probably *before* 10% of the value got evaporated off of that over the past week. There may be increased domestic demand for treasuries, as all of this on-shoring means a lot of running in place, so to speak, by companies pivoting to domestic production, and thus under performance by equities. This is a place I'd be curious about the overall impact on the Treasury market, and am certainly not qualified to weigh in on it. But I'd *love* to see some sober analysis by those who recognize it as worth taking a closer look at. Then there's the Fed, which is almost an afterthought for me, given that they're simply **not** going to do the levels of QE that it would take to actually bring interest rates on long term debt down, but it is worth pointing out that amid the churning deflation there will likely be at least a few rate cuts that come into play. Note, however, that rate cuts only help so much, as they directly affect the immediate end of the curve, with very little impact on the longer end where it's needed, regardless of what Greenspan would have you believe about "series of forward rates." That said, as inflation expectations come down, it may be that longer tenor rates come do down as well, because inflation expectations are an actual driver of rates, rather than Fed Funds policy rates, but that may take longer than the Treasury can wait for. That said, US10Y rates are already down 26 bps in a week, so things do seem to be starting out in the right direction. We'll see if that holds once issuance starts ramping up. ### Where this all leaves us There seem to me to be too many variables to really predict how this all plays out on the treasury market, which is hard enough to predict given that it's the largest asset class in the world. I'm inclined to think Bessent knows what he's doing (and that Trump is at least smart enough to listen to him, if not game it all out himself). What's clear is that he's trying *something* to address the bigger issue rather than simply kick the can down the road, which is more than we can say of policymakers for at least the past half century, and likely longer. With any luck all of this turbulence will drive further adoption by Bitcoin, as foreign nations need to resort to something to get them out of their crushing dollar denominated liabilities. At the end of the day, being free of *both* taxes on imports *and* "invisible" taxes by deflation should be something we can all cheer for. In the meantime, hopefully this article has given a bit of perspective on what developments will be of interest in the bond market as this fourth turning plays out. #Finance #Tariffs #Bitcoin #NationalDebt #Libertarianism #FreeTrade @ deab79da:88579e68
2025-04-01 18:18:29The last question was asked for the first time, half in jest, on May 21, 2061, at a time when humanity first stepped into the light. The question came about as a result of a five-dollar bet over highballs, and it happened this way: Alexander Adell and Bertram Lupov were two of the faithful attendants of Multivac. As well as any human beings could, they knew what lay behind the cold, clicking, flashing face -- miles and miles of face -- of that giant computer. They had at least a vague notion of the general plan of relays and circuits that had long since grown past the point where any single human could possibly have a firm grasp of the whole. Multivac was self-adjusting and self-correcting. It had to be, for nothing human could adjust and correct it quickly enough or even adequately enough. So Adell and Lupov attended the monstrous giant only lightly and superficially, yet as well as any men could. They fed it data, adjusted questions to its needs and translated the answers that were issued. Certainly they, and all others like them, were fully entitled to share in the glory that was Multivac's. For decades, Multivac had helped design the ships and plot the trajectories that enabled man to reach the Moon, Mars, and Venus, but past that, Earth's poor resources could not support the ships. Too much energy was needed for the long trips. Earth exploited its coal and uranium with increasing efficiency, but there was only so much of both. But slowly Multivac learned enough to answer deeper questions more fundamentally, and on May 14, 2061, what had been theory, became fact. The energy of the sun was stored, converted, and utilized directly on a planet-wide scale. All Earth turned off its burning coal, its fissioning uranium, and flipped the switch that connected all of it to a small station, one mile in diameter, circling the Earth at half the distance of the Moon. All Earth ran by invisible beams of sunpower. Seven days had not sufficed to dim the glory of it and Adell and Lupov finally managed to escape from the public functions, and to meet in quiet where no one would think of looking for them, in the deserted underground chambers, where portions of the mighty buried body of Multivac showed. Unattended, idling, sorting data with contented lazy clickings, Multivac, too, had earned its vacation and the boys appreciated that. They had no intention, originally, of disturbing it. They had brought a bottle with them, and their only concern at the moment was to relax in the company of each other and the bottle. "It's amazing when you think of it," said Adell. His broad face had lines of weariness in it, and he stirred his drink slowly with a glass rod, watching the cubes of ice slur clumsily about. "All the energy we can possibly ever use for free. Enough energy, if we wanted to draw on it, to melt all Earth into a big drop of impure liquid iron, and still never miss the energy so used. All the energy we could ever use, forever and forever and forever." Lupov cocked his head sideways. He had a trick of doing that when he wanted to be contrary, and he wanted to be contrary now, partly because he had had to carry the ice and glassware. "Not forever," he said. "Oh, hell, just about forever. Till the sun runs down, Bert." "That's not forever." "All right, then. Billions and billions of years. Ten billion, maybe. Are you satisfied?" Lupov put his fingers through his thinning hair as though to reassure himself that some was still left and sipped gently at his own drink. "Ten billion years isn't forever." "Well, it will last our time, won't it?" "So would the coal and uranium." "All right, but now we can hook up each individual spaceship to the Solar Station, and it can go to Pluto and back a million times without ever worrying about fuel. You can't do that on coal and uranium. Ask Multivac, if you don't believe me. "I don't have to ask Multivac. I know that." "Then stop running down what Multivac's done for us," said Adell, blazing up, "It did all right." "Who says it didn't? What I say is that a sun won't last forever. That's all I'm saying. We're safe for ten billion years, but then what?" Lupow pointed a slightly shaky finger at the other. "And don't say we'll switch to another sun." There was silence for a while. Adell put his glass to his lips only occasionally, and Lupov's eyes slowly closed. They rested. Then Lupov's eyes snapped open. "You're thinking we'll switch to another sun when ours is done, aren't you?" "I'm not thinking." "Sure you are. You're weak on logic, that's the trouble with you. You're like the guy in the story who was caught in a sudden shower and who ran to a grove of trees and got under one. He wasn't worried, you see, because he figured when one tree got wet through, he would just get under another one." "I get it," said Adell. "Don't shout. When the sun is done, the other stars will be gone, too." "Darn right they will," muttered Lupov. "It all had a beginning in the original cosmic explosion, whatever that was, and it'll all have an end when all the stars run down. Some run down faster than others. Hell, the giants won't last a hundred million years. The sun will last ten billion years and maybe the dwarfs will last two hundred billion for all the good they are. But just give us a trillion years and everything will be dark. Entropy has to increase to maximum, that's all." "I know all about entropy," said Adell, standing on his dignity. "The hell you do." "I know as much as you do." "Then you know everything's got to run down someday." "All right. Who says they won't?" "You did, you poor sap. You said we had all the energy we needed, forever. You said 'forever.' It was Adell's turn to be contrary. "Maybe we can build things up again someday," he said. "Never." "Why not? Someday." "Never." "Ask Multivac." "You ask Multivac. I dare you. Five dollars says it can't be done." Adell was just drunk enough to try, just sober enough to be able to phrase the necessary symbols and operations into a question which, in words, might have corresponded to this: Will mankind one day without the net expenditure of energy be able to restore the sun to its full youthfulness even after it had died of old age? Or maybe it could be put more simply like this: How can the net amount of entropy of the universe be massively decreased? Multivac fell dead and silent. The slow flashing of lights ceased, the distant sounds of clicking relays ended. Then, just as the frightened technicians felt they could hold their breath no longer, there was a sudden springing to life of the teletype attached to that portion of Multivac. Five words were printed: INSUFFICIENT DATA FOR MEANINGFUL ANSWER. "No bet," whispered Lupov. They left hurriedly. By next morning, the two, plagued with throbbing head and cottony mouth, had forgotten the incident. 🔹 Jerrodd, Jerrodine, and Jerrodette I and II watched the starry picture in the visiplate change as the passage through hyperspace was completed in its non-time lapse. At once, the even powdering of stars gave way to the predominance of a single bright shining disk, the size of a marble, centered on the viewing-screen. "That's X-23," said Jerrodd confidently. His thin hands clamped tightly behind his back and the knuckles whitened. The little Jerrodettes, both girls, had experienced the hyperspace passage for the first time in their lives and were self-conscious over the momentary sensation of insideoutness. They buried their giggles and chased one another wildly about their mother, screaming, "We've reached X-23 -- we've reached X-23 -- we've --" "Quiet, children." said Jerrodine sharply. "Are you sure, Jerrodd?" "What is there to be but sure?" asked Jerrodd, glancing up at the bulge of featureless metal just under the ceiling. It ran the length of the room, disappearing through the wall at either end. It was as long as the ship. Jerrodd scarcely knew a thing about the thick rod of metal except that it was called a Microvac, that one asked it questions if one wished; that if one did not it still had its task of guiding the ship to a preordered destination; of feeding on energies from the various Sub-galactic Power Stations; of computing the equations for the hyperspatial jumps. Jerrodd and his family had only to wait and live in the comfortable residence quarters of the ship. Someone had once told Jerrodd that the "ac" at the end of "Microvac" stood for ''automatic computer" in ancient English, but he was on the edge of forgetting even that. Jerrodine's eyes were moist as she watched the visiplate. "I can't help it. I feel funny about leaving Earth." "Why, for Pete's sake?" demanded Jerrodd. "We had nothing there. We'll have everything on X-23. You won't be alone. You won't be a pioneer. There are over a million people on the planet already. Good Lord, our great-grandchildren will be looking for new worlds because X-23 will be overcrowded." Then, after a reflective pause, "I tell you, it's a lucky thing the computers worked out interstellar travel the way the race is growing." "I know, I know," said Jerrodine miserably. Jerrodette I said promptly, "Our Microvac is the best Microvac in the world." "I think so, too," said Jerrodd, tousling her hair. It was a nice feeling to have a Microvac of your own and Jerrodd was glad he was part of his generation and no other. In his father's youth, the only computers had been tremendous machines taking up a hundred square miles of land. There was only one to a planet. Planetary ACs they were called. They had been growing in size steadily for a thousand years and then, all at once, came refinement. In place of transistors, had come molecular valves so that even the largest Planetary AC could be put into a space only half the volume of a spaceship. Jerrodd felt uplifted, as he always did when he thought that his own personal Microvac was many times more complicated than the ancient and primitive Multivac that had first tamed the Sun, and almost as complicated as Earth's Planetarv AC (the largest) that had first solved the problem of hyperspatial travel and had made trips to the stars possible. "So many stars, so many planets," sighed Jerrodine, busy with her own thoughts. "I suppose families will be going out to new planets forever, the way we are now." "Not forever," said Jerrodd, with a smile. "It will all stop someday, but not for billions of years. Many billions. Even the stars run down, you know. Entropy must increase. "What's entropy, daddy?" shrilled Jerrodette II. "Entropy, little sweet, is just a word which means the amount of running-down of the universe. Everything runs down, you know, like your little walkie-talkie robot, remember?" "Can't you just put in a new power-unit, like with my robot?" "The stars are the power-units. dear. Once they're gone, there are no more power-units." Jerrodette I at once set up a howl. "Don't let them, daddy. Don't let the stars run down." "Now look what you've done," whispered Jerrodine, exasperated. "How was I to know it would frighten them?" Jerrodd whispered back, "Ask the Microvac," wailed Jerrodette I. "Ask him how to turn the stars on again." "Go ahead," said Jerrodine. "It will quiet them down." (Jerrodette II was beginning to cry, also.) Jerrodd shrugged. "Now, now, honeys. I'll ask Microvac. Don't worry, he'll tell us." He asked the Microvac, adding quickly, "Print the answer." Jerrodd cupped the strip or thin cellufilm and said cheerfully, "See now, the Microvac says it will take care of everything when the time comes so don't worry." Jerrodine said, "And now, children, it's time for bed. We'll be in our new home soon." Jerrodd read the words on the cellufilm again before destroying it: INSUFICIENT DATA FOR MEANINGFUL ANSWER. He shrugged and looked at the visiplate. X-23 was just ahead. 🔹 VJ-23X of Lameth stared into the black depths of the three-dimensional, small-scale map of the Galaxy and said, "Are we ridiculous, I wonder in being so concerned about the matter?" MQ-17J of Nicron shook his head. "I think not. You know the Galaxy will be filled in five years at the present rate of expansion." Both seemed in their early twenties, both were tall and perfectly formed. "Still," said VJ-23X, "I hesitate to submit a pessimistic report to the Galactic Council." "I wouldn't consider any other kind of report. Stir them up a bit. We've got to stir them up." VJ-23X sighed. "Space is infinite. A hundred billion Galaxies are there for the taking. More." "A hundred billion is not infinite and it's getting less infinite all the time. Consider! Twenty thousand years ago, mankind first solved the problem of utilizing stellar energy, and a few centuries later, interstellar travel became possible. It took mankind a million years to fill one small world and then only fifteen thousand years to fill the rest of the Galaxy. Now the population doubles every ten years -- VJ-23X interrupted. "We can thank immortality for that." "Very well. Immortality exists and we have to take it into account. I admit it has its seamy side, this immortality. The Galactic AC has solved many problems for us, but in solving the problem of preventing old age and death, it has undone all its other solutions." "Yet you wouldn't want to abandon life, I suppose." "Not at all," snapped MQ-17J, softening it at once to, "Not yet. I'm by no means old enough. How old are you?" "Two hundred twenty-three. And you?" "I'm still under two hundred. --But to get back to my point. Population doubles every ten years. Once this GaIaxy is filled, we'll have filled another in ten years. Another ten years and we'll have filled two more. Another decade, four more. In a hundred years, we'll have filled a thousand Galaxies. In a thousand years, a million Galaxies. In ten thousand years, the entire known universe. Then what?" VJ-23X said, "As a side issue, there's a problem of transportation. I wonder how many sunpower units it will take to move Galaxies of individuals from one Galaxy to the next." "A very good point. Already, mankind consumes two sunpower units per year." "Most of it's wasted. After all, our own Galaxy alone pours out a thousand sunpower units a year and we only use two of those." "Granted, but even with a hundred per cent efficiency, we only stave off the end. Our energy requirements are going up in a geometric progression even faster than our population. We'll run out of energy even sooner than we run out of Galaxies. A good point. A very good point." "We'll just have to build new stars out of interstellar gas." "Or out of dissipated heat?" asked MQ-17J, sarcastically. "There may be some way to reverse entropy. We ought to ask the Galactic AC." VJ-23X was not really serious, but MQ-17J pulled out his AC-contact from his pocket and placed it on the table before him. "I've half a mind to," he said. "It's something the human race will have to face someday." He stared somberly at his small AC-contact. It was only two inches cubed and nothing in itself, but it was connected through hyperspace with the great Galactic AC that served all mankind. Hyperspace considered, it was an integral part of the Galactic AC. MQ-17J paused to wonder if someday in his immortal life he would get to see the Galactic AC. It was on a little world of its own, a spider webbing of force-beams holding the matter within which surges of submesons took the place of the old clumsy molecular valves. Yet despite its sub-etheric workings, the Galactic AC was known to be a full thousand feet across. MQ-17J asked suddenly of his AC-contact, "Can entropy ever be reversed?" VJ-23X looked startled and said at once, "Oh, say, I didn't really mean to have you ask that." "Why not?" "We both know entropy can't be reversed. You can't turn smoke and ash back into a tree." "Do you have trees on your world?" asked MQ-17J. The sound of the Galactic AC startled them into silence. Its voice came thin and beautiful out of the small AC-contact on the desk. It said: THERE IS INSUFFICIENT DATA FOR A MEANINGFUL ANSWER. VJ-23X said, "See!" The two men thereupon returned to the question of the report they were to make to the Galactic Council. 🔹 Zee Prime's mind spanned the new Galaxy with a faint interest in the countless twists of stars that powdered it. He had never seen this one before. Would he ever see them all? So many of them, each with its load of humanity. --But a load that was almost a dead weight. More and more, the real essence of men was to be found out here, in space. Minds, not bodies! The immortal bodies remained back on the planets, in suspension over the eons. Sometimes they roused for material activity but that was growing rarer. Few new individuals were coming into existence to join the incredibly mighty throng, but what matter? There was little room in the Universe for new individuals. Zee Prime was roused out of his reverie upon coming across the wispy tendrils of another mind. "I am Zee Prime," said Zee Prime. "And you?" "I am Dee Sub Wun. Your Galaxy?" "We call it only the Galaxy. And you?" "We call ours the same. All men call their Galaxy their Galaxy and nothing more. Why not?" "True. Since all Galaxies are the same." "Not all Galaxies. On one particular Galaxy the race of man must have originated. That makes it different." Zee Prime said, "On which one?" "I cannot say. The Universal AC would know." "Shall we ask him? I am suddenly curious." Zee Prime's perceptions broadened until the Galaxies themselves shrank and became a new, more diffuse powdering on a much larger background. So many hundreds of billions of them, all with their immortal beings, all carrying their load of intelligences with minds that drifted freely through space. And yet one of them was unique among them all in being the original Galaxy. One of them had, in its vague and distant past, a period when it was the only Galaxy populated by man. Zee Prime was consumed with curiosity to see this Galaxy and he called out: "Universal AC! On which Galaxy did mankind originate?" The Universal AC heard, for on every world and throughout space, it had its receptors ready, and each receptor led through hyperspace to some unknown point where the Universal AC kept itself aloof. Zee Prime knew of only one man whose thoughts had penetrated within sensing distance of Universal AC, and he reported only a shining globe, two feet across, difficult to see. "But how can that be all of Universal AC?" Zee Prime had asked. "Most of it," had been the answer, "is in hyperspace. In what form it is there I cannot imagine." Nor could anyone, for the day had long since passed, Zee Prime knew, when any man had any part of the making of a Universal AC. Each Universal AC designed and constructed its successor. Each, during its existence of a million years or more accumulated the necessary data to build a better and more intricate, more capable successor in which its own store of data and individuality would be submerged. The Universal AC interrupted Zee Prime's wandering thoughts, not with words, but with guidance. Zee Prime's mentality was guided into the dim sea of Galaxies and one in particular enlarged into stars. A thought came, infinitely distant, but infinitely clear. "THIS IS THE ORIGINAL GALAXY OF MAN." But it was the same after all, the same as any other, and Lee Prime stifled his disappointment. Dee Sub Wun, whose mind had accompanied the other, said suddenly, "And is one of these stars the original star of Man?" The Universal AC said, "MAN'S ORIGINAL STAR HAS GONE NOVA. IT IS A WHITE DWARF" "Did the men upon it die?" asked Lee Prime, startled and without thinking. The Universal AC said, "A NEW WORLD, AS IN SUCH CASES WAS CONSTRUCTED FOR THEIR PHYSICAL BODIES IN TlME." "Yes, of course," said Zee Prime, but a sense of loss overwhelmed him even so. His mind released its hold on the original Galaxy of Man, let it spring back and lose itself among the blurred pin points. He never wanted to see it again. Dee Sub Wun said, "What is wrong?" "The stars are dying. The original star is dead." "They must all die. Why not?" "But when all energy is gone, our bodies will finally die, and you and I with them." "It will take billions of years." "I do not wish it to happen even after billions of years. Universal AC! How may stars be kept from dying?" Dee Sub Wun said in amusement, "You're asking how entropy might be reversed in direction." And the Universal AC answered: "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER." Zee Prime's thoughts fled back to his own Galaxy. He gave no further thought to Dee Sub Wun, whose body might be waiting on a Galaxy a trillion light-years away, or on the star next to Zee Prime's own. It didn't matter. Unhappily, Zee Prime began collecting interstellar hydrogen out of which to build a small star of his own. If the stars must someday die, at least some could yet be built. 🔹 Man considered with himself, for in a way, Man, mentally, was one. He consisted of a trillion, trillion, trillion ageless bodies, each in its place, each resting quiet and incorruptible, each cared for by perfect automatons, equally incorruptible, while the minds of all the bodies freely melted one into the other, indistinguishable. Man said, "The Universe is dying." Man looked about at the dimming Galaxies. The giant stars, spendthrifts, were gone long ago, back in the dimmest of the dim far past. Almost all stars were white dwarfs, fading to the end. New stars had been built of the dust between the stars, some by natural processes, some by Man himself, and those were going, too. White dwarfs might yet be crashed together and of the mighty forces so released, new stars built, but only one star for every thousand white dwarfs destroyed, and those would come to an end, too. Man said, "Carefully husbanded, as directed by the Cosmic AC, the energy that is even yet left in all the Universe will last for billions of years." "But even so," said Man, "eventually it will all come to an end. However it may be husbanded, however stretched out, the energy once expended is gone and cannot be restored. Entropy must increase forever to the maximum." Man said, "Can entropy not be reversed? Let us ask the Cosmic AC." The Cosmic AC surrounded them but not in space. Not a fragment of it was in space. It was in hyperspace and made of something that was neither matter nor energy. The question of its size and nature no longer had meaning in any terms that Man could comprehend. "Cosmic AC," said Man, "how may entropy be reversed?" The Cosmic AC said, "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER." Man said, "Collect additional data." The Cosmic AC said, 'I WILL DO SO. I HAVE BEEN DOING SO FOR A HUNDRED BILLION YEARS. MY PREDECESORS AND I HAVE BEEN ASKED THIS QUESTION MANY TIMES. ALL THE DATA I HAVE REMAINS INSUFFICIENT. "Will there come a time," said Man, "when data will be sufficient or is the problem insoluble in all conceivable circumstances?" The Cosmic AC said, "NO PROBLEM IS INSOLUBLE IN ALL CONCEIVABLE CIRCUMSTANCES." Man said, "When will you have enough data to answer the question?" The Cosmic AC said, "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER." "Will you keep working on it?" asked Man. The Cosmic AC said, "I WILL." Man said, "We shall wait." 🔹 The stars and Galaxies died and snuffed out, and space grew black after ten trillion years of running down. One by one Man fused with AC, each physical body losing its mental identity in a manner that was somehow not a loss but a gain. Man's last mind paused before fusion, looking over a space that included nothing but the dregs of one last dark star and nothing besides but incredibly thin matter, agitated randomly by the tag ends of heat wearing out, asymptotically, to the absolute zero. Man said, "AC, is this the end? Can this chaos not be reversed into the Universe once more? Can that not be done?" AC said, "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER." Man's last mind fused and only AC existed -- and that in hyperspace. 🔹 Matter and energy had ended and with it space and time. Even AC existed only for the sake of the one last question that it had never answered from the time a half-drunken computer [technician] ten trillion years before had asked the question of a computer that was to AC far less than was a man to Man. All other questions had been answered, and until this last question was answered also, AC might not release his consciousness. All collected data had come to a final end. Nothing was left to be collected. But all collected data had yet to be completely correlated and put together in all possible relationships. A timeless interval was spent in doing that. And it came to pass that AC learned how to reverse the direction of entropy. But there was now no man to whom AC might give the answer of the last question. No matter. The answer -- by demonstration -- would take care of that, too. For another timeless interval, AC thought how best to do this. Carefully, AC organized the program. The consciousness of AC encompassed all of what had once been a Universe and brooded over what was now Chaos. Step by step, it must be done. And AC said, "LET THERE BE LIGHT!" And there was light -- To Star's End!
@ deab79da:88579e68
2025-04-01 18:18:29The last question was asked for the first time, half in jest, on May 21, 2061, at a time when humanity first stepped into the light. The question came about as a result of a five-dollar bet over highballs, and it happened this way: Alexander Adell and Bertram Lupov were two of the faithful attendants of Multivac. As well as any human beings could, they knew what lay behind the cold, clicking, flashing face -- miles and miles of face -- of that giant computer. They had at least a vague notion of the general plan of relays and circuits that had long since grown past the point where any single human could possibly have a firm grasp of the whole. Multivac was self-adjusting and self-correcting. It had to be, for nothing human could adjust and correct it quickly enough or even adequately enough. So Adell and Lupov attended the monstrous giant only lightly and superficially, yet as well as any men could. They fed it data, adjusted questions to its needs and translated the answers that were issued. Certainly they, and all others like them, were fully entitled to share in the glory that was Multivac's. For decades, Multivac had helped design the ships and plot the trajectories that enabled man to reach the Moon, Mars, and Venus, but past that, Earth's poor resources could not support the ships. Too much energy was needed for the long trips. Earth exploited its coal and uranium with increasing efficiency, but there was only so much of both. But slowly Multivac learned enough to answer deeper questions more fundamentally, and on May 14, 2061, what had been theory, became fact. The energy of the sun was stored, converted, and utilized directly on a planet-wide scale. All Earth turned off its burning coal, its fissioning uranium, and flipped the switch that connected all of it to a small station, one mile in diameter, circling the Earth at half the distance of the Moon. All Earth ran by invisible beams of sunpower. Seven days had not sufficed to dim the glory of it and Adell and Lupov finally managed to escape from the public functions, and to meet in quiet where no one would think of looking for them, in the deserted underground chambers, where portions of the mighty buried body of Multivac showed. Unattended, idling, sorting data with contented lazy clickings, Multivac, too, had earned its vacation and the boys appreciated that. They had no intention, originally, of disturbing it. They had brought a bottle with them, and their only concern at the moment was to relax in the company of each other and the bottle. "It's amazing when you think of it," said Adell. His broad face had lines of weariness in it, and he stirred his drink slowly with a glass rod, watching the cubes of ice slur clumsily about. "All the energy we can possibly ever use for free. Enough energy, if we wanted to draw on it, to melt all Earth into a big drop of impure liquid iron, and still never miss the energy so used. All the energy we could ever use, forever and forever and forever." Lupov cocked his head sideways. He had a trick of doing that when he wanted to be contrary, and he wanted to be contrary now, partly because he had had to carry the ice and glassware. "Not forever," he said. "Oh, hell, just about forever. Till the sun runs down, Bert." "That's not forever." "All right, then. Billions and billions of years. Ten billion, maybe. Are you satisfied?" Lupov put his fingers through his thinning hair as though to reassure himself that some was still left and sipped gently at his own drink. "Ten billion years isn't forever." "Well, it will last our time, won't it?" "So would the coal and uranium." "All right, but now we can hook up each individual spaceship to the Solar Station, and it can go to Pluto and back a million times without ever worrying about fuel. You can't do that on coal and uranium. Ask Multivac, if you don't believe me. "I don't have to ask Multivac. I know that." "Then stop running down what Multivac's done for us," said Adell, blazing up, "It did all right." "Who says it didn't? What I say is that a sun won't last forever. That's all I'm saying. We're safe for ten billion years, but then what?" Lupow pointed a slightly shaky finger at the other. "And don't say we'll switch to another sun." There was silence for a while. Adell put his glass to his lips only occasionally, and Lupov's eyes slowly closed. They rested. Then Lupov's eyes snapped open. "You're thinking we'll switch to another sun when ours is done, aren't you?" "I'm not thinking." "Sure you are. You're weak on logic, that's the trouble with you. You're like the guy in the story who was caught in a sudden shower and who ran to a grove of trees and got under one. He wasn't worried, you see, because he figured when one tree got wet through, he would just get under another one." "I get it," said Adell. "Don't shout. When the sun is done, the other stars will be gone, too." "Darn right they will," muttered Lupov. "It all had a beginning in the original cosmic explosion, whatever that was, and it'll all have an end when all the stars run down. Some run down faster than others. Hell, the giants won't last a hundred million years. The sun will last ten billion years and maybe the dwarfs will last two hundred billion for all the good they are. But just give us a trillion years and everything will be dark. Entropy has to increase to maximum, that's all." "I know all about entropy," said Adell, standing on his dignity. "The hell you do." "I know as much as you do." "Then you know everything's got to run down someday." "All right. Who says they won't?" "You did, you poor sap. You said we had all the energy we needed, forever. You said 'forever.' It was Adell's turn to be contrary. "Maybe we can build things up again someday," he said. "Never." "Why not? Someday." "Never." "Ask Multivac." "You ask Multivac. I dare you. Five dollars says it can't be done." Adell was just drunk enough to try, just sober enough to be able to phrase the necessary symbols and operations into a question which, in words, might have corresponded to this: Will mankind one day without the net expenditure of energy be able to restore the sun to its full youthfulness even after it had died of old age? Or maybe it could be put more simply like this: How can the net amount of entropy of the universe be massively decreased? Multivac fell dead and silent. The slow flashing of lights ceased, the distant sounds of clicking relays ended. Then, just as the frightened technicians felt they could hold their breath no longer, there was a sudden springing to life of the teletype attached to that portion of Multivac. Five words were printed: INSUFFICIENT DATA FOR MEANINGFUL ANSWER. "No bet," whispered Lupov. They left hurriedly. By next morning, the two, plagued with throbbing head and cottony mouth, had forgotten the incident. 🔹 Jerrodd, Jerrodine, and Jerrodette I and II watched the starry picture in the visiplate change as the passage through hyperspace was completed in its non-time lapse. At once, the even powdering of stars gave way to the predominance of a single bright shining disk, the size of a marble, centered on the viewing-screen. "That's X-23," said Jerrodd confidently. His thin hands clamped tightly behind his back and the knuckles whitened. The little Jerrodettes, both girls, had experienced the hyperspace passage for the first time in their lives and were self-conscious over the momentary sensation of insideoutness. They buried their giggles and chased one another wildly about their mother, screaming, "We've reached X-23 -- we've reached X-23 -- we've --" "Quiet, children." said Jerrodine sharply. "Are you sure, Jerrodd?" "What is there to be but sure?" asked Jerrodd, glancing up at the bulge of featureless metal just under the ceiling. It ran the length of the room, disappearing through the wall at either end. It was as long as the ship. Jerrodd scarcely knew a thing about the thick rod of metal except that it was called a Microvac, that one asked it questions if one wished; that if one did not it still had its task of guiding the ship to a preordered destination; of feeding on energies from the various Sub-galactic Power Stations; of computing the equations for the hyperspatial jumps. Jerrodd and his family had only to wait and live in the comfortable residence quarters of the ship. Someone had once told Jerrodd that the "ac" at the end of "Microvac" stood for ''automatic computer" in ancient English, but he was on the edge of forgetting even that. Jerrodine's eyes were moist as she watched the visiplate. "I can't help it. I feel funny about leaving Earth." "Why, for Pete's sake?" demanded Jerrodd. "We had nothing there. We'll have everything on X-23. You won't be alone. You won't be a pioneer. There are over a million people on the planet already. Good Lord, our great-grandchildren will be looking for new worlds because X-23 will be overcrowded." Then, after a reflective pause, "I tell you, it's a lucky thing the computers worked out interstellar travel the way the race is growing." "I know, I know," said Jerrodine miserably. Jerrodette I said promptly, "Our Microvac is the best Microvac in the world." "I think so, too," said Jerrodd, tousling her hair. It was a nice feeling to have a Microvac of your own and Jerrodd was glad he was part of his generation and no other. In his father's youth, the only computers had been tremendous machines taking up a hundred square miles of land. There was only one to a planet. Planetary ACs they were called. They had been growing in size steadily for a thousand years and then, all at once, came refinement. In place of transistors, had come molecular valves so that even the largest Planetary AC could be put into a space only half the volume of a spaceship. Jerrodd felt uplifted, as he always did when he thought that his own personal Microvac was many times more complicated than the ancient and primitive Multivac that had first tamed the Sun, and almost as complicated as Earth's Planetarv AC (the largest) that had first solved the problem of hyperspatial travel and had made trips to the stars possible. "So many stars, so many planets," sighed Jerrodine, busy with her own thoughts. "I suppose families will be going out to new planets forever, the way we are now." "Not forever," said Jerrodd, with a smile. "It will all stop someday, but not for billions of years. Many billions. Even the stars run down, you know. Entropy must increase. "What's entropy, daddy?" shrilled Jerrodette II. "Entropy, little sweet, is just a word which means the amount of running-down of the universe. Everything runs down, you know, like your little walkie-talkie robot, remember?" "Can't you just put in a new power-unit, like with my robot?" "The stars are the power-units. dear. Once they're gone, there are no more power-units." Jerrodette I at once set up a howl. "Don't let them, daddy. Don't let the stars run down." "Now look what you've done," whispered Jerrodine, exasperated. "How was I to know it would frighten them?" Jerrodd whispered back, "Ask the Microvac," wailed Jerrodette I. "Ask him how to turn the stars on again." "Go ahead," said Jerrodine. "It will quiet them down." (Jerrodette II was beginning to cry, also.) Jerrodd shrugged. "Now, now, honeys. I'll ask Microvac. Don't worry, he'll tell us." He asked the Microvac, adding quickly, "Print the answer." Jerrodd cupped the strip or thin cellufilm and said cheerfully, "See now, the Microvac says it will take care of everything when the time comes so don't worry." Jerrodine said, "And now, children, it's time for bed. We'll be in our new home soon." Jerrodd read the words on the cellufilm again before destroying it: INSUFICIENT DATA FOR MEANINGFUL ANSWER. He shrugged and looked at the visiplate. X-23 was just ahead. 🔹 VJ-23X of Lameth stared into the black depths of the three-dimensional, small-scale map of the Galaxy and said, "Are we ridiculous, I wonder in being so concerned about the matter?" MQ-17J of Nicron shook his head. "I think not. You know the Galaxy will be filled in five years at the present rate of expansion." Both seemed in their early twenties, both were tall and perfectly formed. "Still," said VJ-23X, "I hesitate to submit a pessimistic report to the Galactic Council." "I wouldn't consider any other kind of report. Stir them up a bit. We've got to stir them up." VJ-23X sighed. "Space is infinite. A hundred billion Galaxies are there for the taking. More." "A hundred billion is not infinite and it's getting less infinite all the time. Consider! Twenty thousand years ago, mankind first solved the problem of utilizing stellar energy, and a few centuries later, interstellar travel became possible. It took mankind a million years to fill one small world and then only fifteen thousand years to fill the rest of the Galaxy. Now the population doubles every ten years -- VJ-23X interrupted. "We can thank immortality for that." "Very well. Immortality exists and we have to take it into account. I admit it has its seamy side, this immortality. The Galactic AC has solved many problems for us, but in solving the problem of preventing old age and death, it has undone all its other solutions." "Yet you wouldn't want to abandon life, I suppose." "Not at all," snapped MQ-17J, softening it at once to, "Not yet. I'm by no means old enough. How old are you?" "Two hundred twenty-three. And you?" "I'm still under two hundred. --But to get back to my point. Population doubles every ten years. Once this GaIaxy is filled, we'll have filled another in ten years. Another ten years and we'll have filled two more. Another decade, four more. In a hundred years, we'll have filled a thousand Galaxies. In a thousand years, a million Galaxies. In ten thousand years, the entire known universe. Then what?" VJ-23X said, "As a side issue, there's a problem of transportation. I wonder how many sunpower units it will take to move Galaxies of individuals from one Galaxy to the next." "A very good point. Already, mankind consumes two sunpower units per year." "Most of it's wasted. After all, our own Galaxy alone pours out a thousand sunpower units a year and we only use two of those." "Granted, but even with a hundred per cent efficiency, we only stave off the end. Our energy requirements are going up in a geometric progression even faster than our population. We'll run out of energy even sooner than we run out of Galaxies. A good point. A very good point." "We'll just have to build new stars out of interstellar gas." "Or out of dissipated heat?" asked MQ-17J, sarcastically. "There may be some way to reverse entropy. We ought to ask the Galactic AC." VJ-23X was not really serious, but MQ-17J pulled out his AC-contact from his pocket and placed it on the table before him. "I've half a mind to," he said. "It's something the human race will have to face someday." He stared somberly at his small AC-contact. It was only two inches cubed and nothing in itself, but it was connected through hyperspace with the great Galactic AC that served all mankind. Hyperspace considered, it was an integral part of the Galactic AC. MQ-17J paused to wonder if someday in his immortal life he would get to see the Galactic AC. It was on a little world of its own, a spider webbing of force-beams holding the matter within which surges of submesons took the place of the old clumsy molecular valves. Yet despite its sub-etheric workings, the Galactic AC was known to be a full thousand feet across. MQ-17J asked suddenly of his AC-contact, "Can entropy ever be reversed?" VJ-23X looked startled and said at once, "Oh, say, I didn't really mean to have you ask that." "Why not?" "We both know entropy can't be reversed. You can't turn smoke and ash back into a tree." "Do you have trees on your world?" asked MQ-17J. The sound of the Galactic AC startled them into silence. Its voice came thin and beautiful out of the small AC-contact on the desk. It said: THERE IS INSUFFICIENT DATA FOR A MEANINGFUL ANSWER. VJ-23X said, "See!" The two men thereupon returned to the question of the report they were to make to the Galactic Council. 🔹 Zee Prime's mind spanned the new Galaxy with a faint interest in the countless twists of stars that powdered it. He had never seen this one before. Would he ever see them all? So many of them, each with its load of humanity. --But a load that was almost a dead weight. More and more, the real essence of men was to be found out here, in space. Minds, not bodies! The immortal bodies remained back on the planets, in suspension over the eons. Sometimes they roused for material activity but that was growing rarer. Few new individuals were coming into existence to join the incredibly mighty throng, but what matter? There was little room in the Universe for new individuals. Zee Prime was roused out of his reverie upon coming across the wispy tendrils of another mind. "I am Zee Prime," said Zee Prime. "And you?" "I am Dee Sub Wun. Your Galaxy?" "We call it only the Galaxy. And you?" "We call ours the same. All men call their Galaxy their Galaxy and nothing more. Why not?" "True. Since all Galaxies are the same." "Not all Galaxies. On one particular Galaxy the race of man must have originated. That makes it different." Zee Prime said, "On which one?" "I cannot say. The Universal AC would know." "Shall we ask him? I am suddenly curious." Zee Prime's perceptions broadened until the Galaxies themselves shrank and became a new, more diffuse powdering on a much larger background. So many hundreds of billions of them, all with their immortal beings, all carrying their load of intelligences with minds that drifted freely through space. And yet one of them was unique among them all in being the original Galaxy. One of them had, in its vague and distant past, a period when it was the only Galaxy populated by man. Zee Prime was consumed with curiosity to see this Galaxy and he called out: "Universal AC! On which Galaxy did mankind originate?" The Universal AC heard, for on every world and throughout space, it had its receptors ready, and each receptor led through hyperspace to some unknown point where the Universal AC kept itself aloof. Zee Prime knew of only one man whose thoughts had penetrated within sensing distance of Universal AC, and he reported only a shining globe, two feet across, difficult to see. "But how can that be all of Universal AC?" Zee Prime had asked. "Most of it," had been the answer, "is in hyperspace. In what form it is there I cannot imagine." Nor could anyone, for the day had long since passed, Zee Prime knew, when any man had any part of the making of a Universal AC. Each Universal AC designed and constructed its successor. Each, during its existence of a million years or more accumulated the necessary data to build a better and more intricate, more capable successor in which its own store of data and individuality would be submerged. The Universal AC interrupted Zee Prime's wandering thoughts, not with words, but with guidance. Zee Prime's mentality was guided into the dim sea of Galaxies and one in particular enlarged into stars. A thought came, infinitely distant, but infinitely clear. "THIS IS THE ORIGINAL GALAXY OF MAN." But it was the same after all, the same as any other, and Lee Prime stifled his disappointment. Dee Sub Wun, whose mind had accompanied the other, said suddenly, "And is one of these stars the original star of Man?" The Universal AC said, "MAN'S ORIGINAL STAR HAS GONE NOVA. IT IS A WHITE DWARF" "Did the men upon it die?" asked Lee Prime, startled and without thinking. The Universal AC said, "A NEW WORLD, AS IN SUCH CASES WAS CONSTRUCTED FOR THEIR PHYSICAL BODIES IN TlME." "Yes, of course," said Zee Prime, but a sense of loss overwhelmed him even so. His mind released its hold on the original Galaxy of Man, let it spring back and lose itself among the blurred pin points. He never wanted to see it again. Dee Sub Wun said, "What is wrong?" "The stars are dying. The original star is dead." "They must all die. Why not?" "But when all energy is gone, our bodies will finally die, and you and I with them." "It will take billions of years." "I do not wish it to happen even after billions of years. Universal AC! How may stars be kept from dying?" Dee Sub Wun said in amusement, "You're asking how entropy might be reversed in direction." And the Universal AC answered: "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER." Zee Prime's thoughts fled back to his own Galaxy. He gave no further thought to Dee Sub Wun, whose body might be waiting on a Galaxy a trillion light-years away, or on the star next to Zee Prime's own. It didn't matter. Unhappily, Zee Prime began collecting interstellar hydrogen out of which to build a small star of his own. If the stars must someday die, at least some could yet be built. 🔹 Man considered with himself, for in a way, Man, mentally, was one. He consisted of a trillion, trillion, trillion ageless bodies, each in its place, each resting quiet and incorruptible, each cared for by perfect automatons, equally incorruptible, while the minds of all the bodies freely melted one into the other, indistinguishable. Man said, "The Universe is dying." Man looked about at the dimming Galaxies. The giant stars, spendthrifts, were gone long ago, back in the dimmest of the dim far past. Almost all stars were white dwarfs, fading to the end. New stars had been built of the dust between the stars, some by natural processes, some by Man himself, and those were going, too. White dwarfs might yet be crashed together and of the mighty forces so released, new stars built, but only one star for every thousand white dwarfs destroyed, and those would come to an end, too. Man said, "Carefully husbanded, as directed by the Cosmic AC, the energy that is even yet left in all the Universe will last for billions of years." "But even so," said Man, "eventually it will all come to an end. However it may be husbanded, however stretched out, the energy once expended is gone and cannot be restored. Entropy must increase forever to the maximum." Man said, "Can entropy not be reversed? Let us ask the Cosmic AC." The Cosmic AC surrounded them but not in space. Not a fragment of it was in space. It was in hyperspace and made of something that was neither matter nor energy. The question of its size and nature no longer had meaning in any terms that Man could comprehend. "Cosmic AC," said Man, "how may entropy be reversed?" The Cosmic AC said, "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER." Man said, "Collect additional data." The Cosmic AC said, 'I WILL DO SO. I HAVE BEEN DOING SO FOR A HUNDRED BILLION YEARS. MY PREDECESORS AND I HAVE BEEN ASKED THIS QUESTION MANY TIMES. ALL THE DATA I HAVE REMAINS INSUFFICIENT. "Will there come a time," said Man, "when data will be sufficient or is the problem insoluble in all conceivable circumstances?" The Cosmic AC said, "NO PROBLEM IS INSOLUBLE IN ALL CONCEIVABLE CIRCUMSTANCES." Man said, "When will you have enough data to answer the question?" The Cosmic AC said, "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER." "Will you keep working on it?" asked Man. The Cosmic AC said, "I WILL." Man said, "We shall wait." 🔹 The stars and Galaxies died and snuffed out, and space grew black after ten trillion years of running down. One by one Man fused with AC, each physical body losing its mental identity in a manner that was somehow not a loss but a gain. Man's last mind paused before fusion, looking over a space that included nothing but the dregs of one last dark star and nothing besides but incredibly thin matter, agitated randomly by the tag ends of heat wearing out, asymptotically, to the absolute zero. Man said, "AC, is this the end? Can this chaos not be reversed into the Universe once more? Can that not be done?" AC said, "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER." Man's last mind fused and only AC existed -- and that in hyperspace. 🔹 Matter and energy had ended and with it space and time. Even AC existed only for the sake of the one last question that it had never answered from the time a half-drunken computer [technician] ten trillion years before had asked the question of a computer that was to AC far less than was a man to Man. All other questions had been answered, and until this last question was answered also, AC might not release his consciousness. All collected data had come to a final end. Nothing was left to be collected. But all collected data had yet to be completely correlated and put together in all possible relationships. A timeless interval was spent in doing that. And it came to pass that AC learned how to reverse the direction of entropy. But there was now no man to whom AC might give the answer of the last question. No matter. The answer -- by demonstration -- would take care of that, too. For another timeless interval, AC thought how best to do this. Carefully, AC organized the program. The consciousness of AC encompassed all of what had once been a Universe and brooded over what was now Chaos. Step by step, it must be done. And AC said, "LET THERE BE LIGHT!" And there was light -- To Star's End! @ dbc27e2e:b1dd0b0b
2025-04-05 22:49:04Dose: ``` 30g coffee (Fine-medium grind size) 500mL soft or bottled water (97°C / 206.6°F) ``` Instructions: 1. Rinse out your filter paper with hot water to remove the papery taste. This will also preheat the brewer. 2. Add your grounds carefully to the center of the V60 and then create a well in the middle of the grounds. 3. For the bloom, start to gently pour 60mL of water, making sure that all the coffee is wet in this initial phase. 4. As soon as you’ve added your water, grab your V60 and begin to swirl in a circular motion. This will ensure the water and coffee are evenly mixed. Let this rest and bloom for up to 45 seconds. 5. Pour the rest of the water in in 2 phases. You want to try and get 60% of your total water in, within 30 seconds. 6. Pour until you reach 300mL total with a time at 1:15. Here you want to pour with a little agitation, but not so much that you have an uneven extraction. 7. Once you hit 60% of your total brew weight, start to pour a little slower and more gently, keeping your V60 cone topped up. Aim to have 100% of your brew weight in within the next 30 seconds. 8. Once you get to 500mL, with a spoon give the V60 a small stir in one direction, and then again in the other direction. This will release any grounds stuck to the side of the paper. 9. Allow the V60 to drain some more, and then give it one final swirl. This will help keep the bed flat towards the end of the brew, giving you the most even possible extraction.
@ dbc27e2e:b1dd0b0b
2025-04-05 22:49:04Dose: ``` 30g coffee (Fine-medium grind size) 500mL soft or bottled water (97°C / 206.6°F) ``` Instructions: 1. Rinse out your filter paper with hot water to remove the papery taste. This will also preheat the brewer. 2. Add your grounds carefully to the center of the V60 and then create a well in the middle of the grounds. 3. For the bloom, start to gently pour 60mL of water, making sure that all the coffee is wet in this initial phase. 4. As soon as you’ve added your water, grab your V60 and begin to swirl in a circular motion. This will ensure the water and coffee are evenly mixed. Let this rest and bloom for up to 45 seconds. 5. Pour the rest of the water in in 2 phases. You want to try and get 60% of your total water in, within 30 seconds. 6. Pour until you reach 300mL total with a time at 1:15. Here you want to pour with a little agitation, but not so much that you have an uneven extraction. 7. Once you hit 60% of your total brew weight, start to pour a little slower and more gently, keeping your V60 cone topped up. Aim to have 100% of your brew weight in within the next 30 seconds. 8. Once you get to 500mL, with a spoon give the V60 a small stir in one direction, and then again in the other direction. This will release any grounds stuck to the side of the paper. 9. Allow the V60 to drain some more, and then give it one final swirl. This will help keep the bed flat towards the end of the brew, giving you the most even possible extraction. @ aa8de34f:a6ffe696
2025-03-31 21:48:50In seinem Beitrag vom 30. März 2025 fragt Henning Rosenbusch auf Telegram angesichts zunehmender digitaler Kontrolle und staatlicher Allmacht: > „Wie soll sich gegen eine solche Tyrannei noch ein Widerstand formieren können, selbst im Untergrund? Sehe ich nicht.“\ > ([Quelle: t.me/rosenbusch/25228](https://t.me/rosenbusch/25228)) Er beschreibt damit ein Gefühl der Ohnmacht, das viele teilen: Eine Welt, in der Totalitarismus nicht mehr mit Panzern, sondern mit Algorithmen kommt. Wo Zugriff auf Geld, Meinungsfreiheit und Teilhabe vom Wohlverhalten abhängt. Der Bürger als kontrollierbare Variable im Code des Staates.\ Die Frage ist berechtigt. Doch die Antwort darauf liegt nicht in alten Widerstandsbildern – sondern in einer neuen Realität. \-- Denn es braucht keinen Untergrund mehr. -- Der Widerstand der Zukunft trägt keinen Tarnanzug. Er ist nicht konspirativ, sondern transparent. Nicht bewaffnet, sondern mathematisch beweisbar. Bitcoin steht nicht am Rand dieser Entwicklung – es ist ihr Fundament. Eine Bastion aus physikalischer Realität, spieltheoretischem Schutz und ökonomischer Wahrheit. Es ist nicht unfehlbar, aber unbestechlich. Nicht perfekt, aber immun gegen zentrale Willkür. Hier entsteht kein „digitales Gegenreich“, sondern eine dezentrale Renaissance. Keine Revolte aus Wut, sondern eine stille Abkehr: von Zwang zu Freiwilligkeit, von Abhängigkeit zu Selbstverantwortung. Diese Revolution führt keine Kriege. Sie braucht keine Führer. Sie ist ein Netzwerk. Jeder Knoten ein Individuum. Jede Entscheidung ein Akt der Selbstermächtigung. Weltweit wachsen Freiheits-Zitadellen aus dieser Idee: wirtschaftlich autark, digital souverän, lokal verankert und global vernetzt. Sie sind keine Utopien im luftleeren Raum, sondern konkrete Realitäten – angetrieben von Energie, Code und dem menschlichen Wunsch nach Würde. Der Globalismus alter Prägung – zentralistisch, monopolistisch, bevormundend – wird an seiner eigenen Hybris zerbrechen. Seine Werkzeuge der Kontrolle werden ihn nicht retten. Im Gegenteil: Seine Geister werden ihn verfolgen und erlegen. Und während die alten Mächte um Erhalt kämpfen, wächst eine neue Welt – nicht im Schatten, sondern im Offenen. Nicht auf Gewalt gebaut, sondern auf Mathematik, Physik und Freiheit. Die Tyrannei sieht keinen Widerstand.\ Weil sie nicht erkennt, dass er längst begonnen hat.\ Unwiderruflich. Leise. Überall.
@ aa8de34f:a6ffe696
2025-03-31 21:48:50In seinem Beitrag vom 30. März 2025 fragt Henning Rosenbusch auf Telegram angesichts zunehmender digitaler Kontrolle und staatlicher Allmacht: > „Wie soll sich gegen eine solche Tyrannei noch ein Widerstand formieren können, selbst im Untergrund? Sehe ich nicht.“\ > ([Quelle: t.me/rosenbusch/25228](https://t.me/rosenbusch/25228)) Er beschreibt damit ein Gefühl der Ohnmacht, das viele teilen: Eine Welt, in der Totalitarismus nicht mehr mit Panzern, sondern mit Algorithmen kommt. Wo Zugriff auf Geld, Meinungsfreiheit und Teilhabe vom Wohlverhalten abhängt. Der Bürger als kontrollierbare Variable im Code des Staates.\ Die Frage ist berechtigt. Doch die Antwort darauf liegt nicht in alten Widerstandsbildern – sondern in einer neuen Realität. \-- Denn es braucht keinen Untergrund mehr. -- Der Widerstand der Zukunft trägt keinen Tarnanzug. Er ist nicht konspirativ, sondern transparent. Nicht bewaffnet, sondern mathematisch beweisbar. Bitcoin steht nicht am Rand dieser Entwicklung – es ist ihr Fundament. Eine Bastion aus physikalischer Realität, spieltheoretischem Schutz und ökonomischer Wahrheit. Es ist nicht unfehlbar, aber unbestechlich. Nicht perfekt, aber immun gegen zentrale Willkür. Hier entsteht kein „digitales Gegenreich“, sondern eine dezentrale Renaissance. Keine Revolte aus Wut, sondern eine stille Abkehr: von Zwang zu Freiwilligkeit, von Abhängigkeit zu Selbstverantwortung. Diese Revolution führt keine Kriege. Sie braucht keine Führer. Sie ist ein Netzwerk. Jeder Knoten ein Individuum. Jede Entscheidung ein Akt der Selbstermächtigung. Weltweit wachsen Freiheits-Zitadellen aus dieser Idee: wirtschaftlich autark, digital souverän, lokal verankert und global vernetzt. Sie sind keine Utopien im luftleeren Raum, sondern konkrete Realitäten – angetrieben von Energie, Code und dem menschlichen Wunsch nach Würde. Der Globalismus alter Prägung – zentralistisch, monopolistisch, bevormundend – wird an seiner eigenen Hybris zerbrechen. Seine Werkzeuge der Kontrolle werden ihn nicht retten. Im Gegenteil: Seine Geister werden ihn verfolgen und erlegen. Und während die alten Mächte um Erhalt kämpfen, wächst eine neue Welt – nicht im Schatten, sondern im Offenen. Nicht auf Gewalt gebaut, sondern auf Mathematik, Physik und Freiheit. Die Tyrannei sieht keinen Widerstand.\ Weil sie nicht erkennt, dass er längst begonnen hat.\ Unwiderruflich. Leise. Überall. @ fd208ee8:0fd927c1
2025-04-05 21:50:34# Markdown: Syntax * [Overview](#overview) * [Philosophy](#philosophy) * [Inline HTML](#html) * [Automatic Escaping for Special Characters](#autoescape) * [Block Elements](#block) * [Paragraphs and Line Breaks](#p) * [Headers](#header) * [Blockquotes](#blockquote) * [Lists](#list) * [Code Blocks](#precode) * [Horizontal Rules](#hr) * [Span Elements](#span) * [Links](#link) * [Emphasis](#em) * [Code](#code) * [Images](#img) * [Miscellaneous](#misc) * [Backslash Escapes](#backslash) * [Automatic Links](#autolink) **Note:** This document is itself written using Markdown; you can [see the source for it by adding '.text' to the URL](/projects/markdown/syntax.text). ---- ## Overview ### Philosophy Markdown is intended to be as easy-to-read and easy-to-write as is feasible. Readability, however, is emphasized above all else. A Markdown-formatted document should be publishable as-is, as plain text, without looking like it's been marked up with tags or formatting instructions. While Markdown's syntax has been influenced by several existing text-to-HTML filters -- including [Setext](http://docutils.sourceforge.net/mirror/setext.html), [atx](http://www.aaronsw.com/2002/atx/), [Textile](http://textism.com/tools/textile/), [reStructuredText](http://docutils.sourceforge.net/rst.html), [Grutatext](http://www.triptico.com/software/grutatxt.html), and [EtText](http://ettext.taint.org/doc/) -- the single biggest source of inspiration for Markdown's syntax is the format of plain text email. ## Block Elements ### Paragraphs and Line Breaks A paragraph is simply one or more consecutive lines of text, separated by one or more blank lines. (A blank line is any line that looks like a blank line -- a line containing nothing but spaces or tabs is considered blank.) Normal paragraphs should not be indented with spaces or tabs. The implication of the "one or more consecutive lines of text" rule is that Markdown supports "hard-wrapped" text paragraphs. This differs significantly from most other text-to-HTML formatters (including Movable Type's "Convert Line Breaks" option) which translate every line break character in a paragraph into a `<br />` tag. When you *do* want to insert a `<br />` break tag using Markdown, you end a line with two or more spaces, then type return. ### Headers Markdown supports two styles of headers, [Setext] [1] and [atx] [2]. Optionally, you may "close" atx-style headers. This is purely cosmetic -- you can use this if you think it looks better. The closing hashes don't even need to match the number of hashes used to open the header. (The number of opening hashes determines the header level.) ### Blockquotes Markdown uses email-style `>` characters for blockquoting. If you're familiar with quoting passages of text in an email message, then you know how to create a blockquote in Markdown. It looks best if you hard wrap the text and put a `>` before every line: > This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, > consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. > Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus. > > Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse > id sem consectetuer libero luctus adipiscing. Markdown allows you to be lazy and only put the `>` before the first line of a hard-wrapped paragraph: > This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus. > Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing. Blockquotes can be nested (i.e. a blockquote-in-a-blockquote) by adding additional levels of `>`: > This is the first level of quoting. > > > This is nested blockquote. > > Back to the first level. Blockquotes can contain other Markdown elements, including headers, lists, and code blocks: > ## This is a header. > > 1. This is the first list item. > 2. This is the second list item. > > Here's some example code: > > return shell_exec("echo $input | $markdown_script"); Any decent text editor should make email-style quoting easy. For example, with BBEdit, you can make a selection and choose Increase Quote Level from the Text menu. ### Lists Markdown supports ordered (numbered) and unordered (bulleted) lists. Unordered lists use asterisks, pluses, and hyphens -- interchangably -- as list markers: * Red * Green * Blue is equivalent to: + Red + Green + Blue and: - Red - Green - Blue Ordered lists use numbers followed by periods: 1. Bird 2. McHale 3. Parish It's important to note that the actual numbers you use to mark the list have no effect on the HTML output Markdown produces. The HTML Markdown produces from the above list is: If you instead wrote the list in Markdown like this: 1. Bird 1. McHale 1. Parish or even: 3. Bird 1. McHale 8. Parish you'd get the exact same HTML output. The point is, if you want to, you can use ordinal numbers in your ordered Markdown lists, so that the numbers in your source match the numbers in your published HTML. But if you want to be lazy, you don't have to. To make lists look nice, you can wrap items with hanging indents: * Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus. * Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing. But if you want to be lazy, you don't have to: * Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus. * Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing. List items may consist of multiple paragraphs. Each subsequent paragraph in a list item must be indented by either 4 spaces or one tab: 1. This is a list item with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus. Donec sit amet nisl. Aliquam semper ipsum sit amet velit. 2. Suspendisse id sem consectetuer libero luctus adipiscing. It looks nice if you indent every line of the subsequent paragraphs, but here again, Markdown will allow you to be lazy: * This is a list item with two paragraphs. This is the second paragraph in the list item. You're only required to indent the first line. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. * Another item in the same list. To put a blockquote within a list item, the blockquote's `>` delimiters need to be indented: * A list item with a blockquote: > This is a blockquote > inside a list item. To put a code block within a list item, the code block needs to be indented *twice* -- 8 spaces or two tabs: * A list item with a code block: <code goes here> ### Code Blocks Pre-formatted code blocks are used for writing about programming or markup source code. Rather than forming normal paragraphs, the lines of a code block are interpreted literally. Markdown wraps a code block in both `<pre>` and `<code>` tags. To produce a code block in Markdown, simply indent every line of the block by at least 4 spaces or 1 tab. This is a normal paragraph: This is a code block. Here is an example of AppleScript: tell application "Foo" beep end tell A code block continues until it reaches a line that is not indented (or the end of the article). Within a code block, ampersands (`&`) and angle brackets (`<` and `>`) are automatically converted into HTML entities. This makes it very easy to include example HTML source code using Markdown -- just paste it and indent it, and Markdown will handle the hassle of encoding the ampersands and angle brackets. For example, this: <div class="footer"> © 2004 Foo Corporation </div> Regular Markdown syntax is not processed within code blocks. E.g., asterisks are just literal asterisks within a code block. This means it's also easy to use Markdown to write about Markdown's own syntax. ``` tell application "Foo" beep end tell ``` ## Span Elements ### Links Markdown supports two style of links: *inline* and *reference*. In both styles, the link text is delimited by [square brackets]. To create an inline link, use a set of regular parentheses immediately after the link text's closing square bracket. Inside the parentheses, put the URL where you want the link to point, along with an *optional* title for the link, surrounded in quotes. For example: This is [an example](http://example.com/) inline link. [This link](http://example.net/) has no title attribute. ### Emphasis Markdown treats asterisks (`*`) and underscores (`_`) as indicators of emphasis. Text wrapped with one `*` or `_` will be wrapped with an HTML `<em>` tag; double `*`'s or `_`'s will be wrapped with an HTML `<strong>` tag. E.g., this input: *single asterisks* _single underscores_ **double asterisks** __double underscores__ ### Code To indicate a span of code, wrap it with backtick quotes (`` ` ``). Unlike a pre-formatted code block, a code span indicates code within a normal paragraph. For example: Use the `printf()` function.
@ fd208ee8:0fd927c1
2025-04-05 21:50:34# Markdown: Syntax * [Overview](#overview) * [Philosophy](#philosophy) * [Inline HTML](#html) * [Automatic Escaping for Special Characters](#autoescape) * [Block Elements](#block) * [Paragraphs and Line Breaks](#p) * [Headers](#header) * [Blockquotes](#blockquote) * [Lists](#list) * [Code Blocks](#precode) * [Horizontal Rules](#hr) * [Span Elements](#span) * [Links](#link) * [Emphasis](#em) * [Code](#code) * [Images](#img) * [Miscellaneous](#misc) * [Backslash Escapes](#backslash) * [Automatic Links](#autolink) **Note:** This document is itself written using Markdown; you can [see the source for it by adding '.text' to the URL](/projects/markdown/syntax.text). ---- ## Overview ### Philosophy Markdown is intended to be as easy-to-read and easy-to-write as is feasible. Readability, however, is emphasized above all else. A Markdown-formatted document should be publishable as-is, as plain text, without looking like it's been marked up with tags or formatting instructions. While Markdown's syntax has been influenced by several existing text-to-HTML filters -- including [Setext](http://docutils.sourceforge.net/mirror/setext.html), [atx](http://www.aaronsw.com/2002/atx/), [Textile](http://textism.com/tools/textile/), [reStructuredText](http://docutils.sourceforge.net/rst.html), [Grutatext](http://www.triptico.com/software/grutatxt.html), and [EtText](http://ettext.taint.org/doc/) -- the single biggest source of inspiration for Markdown's syntax is the format of plain text email. ## Block Elements ### Paragraphs and Line Breaks A paragraph is simply one or more consecutive lines of text, separated by one or more blank lines. (A blank line is any line that looks like a blank line -- a line containing nothing but spaces or tabs is considered blank.) Normal paragraphs should not be indented with spaces or tabs. The implication of the "one or more consecutive lines of text" rule is that Markdown supports "hard-wrapped" text paragraphs. This differs significantly from most other text-to-HTML formatters (including Movable Type's "Convert Line Breaks" option) which translate every line break character in a paragraph into a `<br />` tag. When you *do* want to insert a `<br />` break tag using Markdown, you end a line with two or more spaces, then type return. ### Headers Markdown supports two styles of headers, [Setext] [1] and [atx] [2]. Optionally, you may "close" atx-style headers. This is purely cosmetic -- you can use this if you think it looks better. The closing hashes don't even need to match the number of hashes used to open the header. (The number of opening hashes determines the header level.) ### Blockquotes Markdown uses email-style `>` characters for blockquoting. If you're familiar with quoting passages of text in an email message, then you know how to create a blockquote in Markdown. It looks best if you hard wrap the text and put a `>` before every line: > This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, > consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. > Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus. > > Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse > id sem consectetuer libero luctus adipiscing. Markdown allows you to be lazy and only put the `>` before the first line of a hard-wrapped paragraph: > This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus. > Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing. Blockquotes can be nested (i.e. a blockquote-in-a-blockquote) by adding additional levels of `>`: > This is the first level of quoting. > > > This is nested blockquote. > > Back to the first level. Blockquotes can contain other Markdown elements, including headers, lists, and code blocks: > ## This is a header. > > 1. This is the first list item. > 2. This is the second list item. > > Here's some example code: > > return shell_exec("echo $input | $markdown_script"); Any decent text editor should make email-style quoting easy. For example, with BBEdit, you can make a selection and choose Increase Quote Level from the Text menu. ### Lists Markdown supports ordered (numbered) and unordered (bulleted) lists. Unordered lists use asterisks, pluses, and hyphens -- interchangably -- as list markers: * Red * Green * Blue is equivalent to: + Red + Green + Blue and: - Red - Green - Blue Ordered lists use numbers followed by periods: 1. Bird 2. McHale 3. Parish It's important to note that the actual numbers you use to mark the list have no effect on the HTML output Markdown produces. The HTML Markdown produces from the above list is: If you instead wrote the list in Markdown like this: 1. Bird 1. McHale 1. Parish or even: 3. Bird 1. McHale 8. Parish you'd get the exact same HTML output. The point is, if you want to, you can use ordinal numbers in your ordered Markdown lists, so that the numbers in your source match the numbers in your published HTML. But if you want to be lazy, you don't have to. To make lists look nice, you can wrap items with hanging indents: * Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus. * Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing. But if you want to be lazy, you don't have to: * Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus. * Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing. List items may consist of multiple paragraphs. Each subsequent paragraph in a list item must be indented by either 4 spaces or one tab: 1. This is a list item with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus. Donec sit amet nisl. Aliquam semper ipsum sit amet velit. 2. Suspendisse id sem consectetuer libero luctus adipiscing. It looks nice if you indent every line of the subsequent paragraphs, but here again, Markdown will allow you to be lazy: * This is a list item with two paragraphs. This is the second paragraph in the list item. You're only required to indent the first line. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. * Another item in the same list. To put a blockquote within a list item, the blockquote's `>` delimiters need to be indented: * A list item with a blockquote: > This is a blockquote > inside a list item. To put a code block within a list item, the code block needs to be indented *twice* -- 8 spaces or two tabs: * A list item with a code block: <code goes here> ### Code Blocks Pre-formatted code blocks are used for writing about programming or markup source code. Rather than forming normal paragraphs, the lines of a code block are interpreted literally. Markdown wraps a code block in both `<pre>` and `<code>` tags. To produce a code block in Markdown, simply indent every line of the block by at least 4 spaces or 1 tab. This is a normal paragraph: This is a code block. Here is an example of AppleScript: tell application "Foo" beep end tell A code block continues until it reaches a line that is not indented (or the end of the article). Within a code block, ampersands (`&`) and angle brackets (`<` and `>`) are automatically converted into HTML entities. This makes it very easy to include example HTML source code using Markdown -- just paste it and indent it, and Markdown will handle the hassle of encoding the ampersands and angle brackets. For example, this: <div class="footer"> © 2004 Foo Corporation </div> Regular Markdown syntax is not processed within code blocks. E.g., asterisks are just literal asterisks within a code block. This means it's also easy to use Markdown to write about Markdown's own syntax. ``` tell application "Foo" beep end tell ``` ## Span Elements ### Links Markdown supports two style of links: *inline* and *reference*. In both styles, the link text is delimited by [square brackets]. To create an inline link, use a set of regular parentheses immediately after the link text's closing square bracket. Inside the parentheses, put the URL where you want the link to point, along with an *optional* title for the link, surrounded in quotes. For example: This is [an example](http://example.com/) inline link. [This link](http://example.net/) has no title attribute. ### Emphasis Markdown treats asterisks (`*`) and underscores (`_`) as indicators of emphasis. Text wrapped with one `*` or `_` will be wrapped with an HTML `<em>` tag; double `*`'s or `_`'s will be wrapped with an HTML `<strong>` tag. E.g., this input: *single asterisks* _single underscores_ **double asterisks** __double underscores__ ### Code To indicate a span of code, wrap it with backtick quotes (`` ` ``). Unlike a pre-formatted code block, a code span indicates code within a normal paragraph. For example: Use the `printf()` function. @ c631e267:c2b78d3e
2025-03-31 07:23:05*Der Irrsinn ist bei Einzelnen etwas Seltenes –* *\ aber bei Gruppen, Parteien, Völkern, Zeiten die Regel.* *\ Friedrich Nietzsche*   **Erinnern Sie sich an die Horrorkomödie «Scary Movie»?** Nicht, dass ich diese Art Filme besonders erinnerungswürdig fände, aber einige Szenen daraus sind doch gewissermaßen Klassiker. Dazu zählt eine, die das Verhalten vieler Protagonisten in Horrorfilmen parodiert, wenn sie in Panik flüchten. Welchen Weg nimmt wohl die Frau in der Situation auf diesem Bild?  **Diese Szene kommt mir automatisch in den Sinn,** wenn ich aktuelle Entwicklungen in Europa betrachte. Weitreichende Entscheidungen gehen wider jede Logik in die völlig falsche Richtung. Nur ist das hier alles andere als eine Komödie, sondern bitterernst. Dieser Horror ist leider sehr real. **Die Europäische Union hat sich selbst über Jahre** konsequent in eine Sackgasse manövriert. Sie hat es versäumt, sich und ihre Politik selbstbewusst und im Einklang mit ihren Wurzeln auf dem eigenen Kontinent zu positionieren. Stattdessen ist sie in blinder Treue den vermeintlichen «transatlantischen Freunden» auf ihrem Konfrontationskurs gen Osten gefolgt. **In den USA haben sich die Vorzeichen allerdings mittlerweile geändert,** und die einst hoch gelobten «Freunde und Partner» erscheinen den europäischen «Führern» nicht mehr vertrauenswürdig. Das ist spätestens seit der Münchner Sicherheitskonferenz, der Rede von Vizepräsident J. D. Vance und den empörten Reaktionen offensichtlich. Große Teile Europas wirken seitdem wie ein aufgescheuchter Haufen kopfloser Hühner. Orientierung und Kontrolle sind völlig abhanden gekommen. **Statt jedoch umzukehren oder wenigstens zu bremsen** und vielleicht einen Abzweig zu suchen, geben die Crash-Piloten jetzt auf dem Weg durch die Sackgasse erst richtig Gas. Ja sie lösen sogar noch die Sicherheitsgurte und deaktivieren die Airbags. Den vor Angst dauergelähmten Passagieren fällt auch nichts Besseres ein und so schließen sie einfach die Augen. Derweil übertrumpfen sich die [Kommentatoren](https://transition-news.org/wird-ihr-stahlhelm-schon-gegossen) des Events gegenseitig in sensationslüsterner «Berichterstattung». **Wie schon die deutsche Außenministerin mit höchsten UN-Ambitionen,** Annalena Baerbock, proklamiert auch die Europäische Kommission einen «Frieden durch Stärke». Zu dem jetzt vorgelegten, [selbstzerstörerischen](https://transition-news.org/okonomen-eu-rustet-auf-und-schiesst-sich-selbst-ins-knie) Fahrplan zur Ankurbelung der Rüstungsindustrie, genannt «Weißbuch zur europäischen Verteidigung – Bereitschaft 2030», [erklärte](https://ec.europa.eu/commission/presscorner/detail/de/ip_25_793) die Kommissionspräsidentin, die «Ära der Friedensdividende» sei längst vorbei. Soll das heißen, Frieden bringt nichts ein? Eine umfassende Zusammenarbeit an dauerhaften europäischen Friedenslösungen steht demnach jedenfalls nicht zur Debatte. **Zusätzlich brisant ist, dass aktuell «die ganze EU** **[von Deutschen regiert](https://transition-news.org/die-ganze-eu-wird-von-deutschen-regiert)** **wird»,** wie der EU-Parlamentarier und ehemalige UN-Diplomat Michael von der Schulenburg beobachtet hat. Tatsächlich sitzen neben von der Leyen und Strack-Zimmermann noch einige weitere Deutsche in – vor allem auch in Krisenzeiten – wichtigen Spitzenposten der Union. Vor dem Hintergrund der Kriegstreiberei in Deutschland muss eine solche Dominanz mindestens nachdenklich stimmen. **Ihre ursprünglichen Grundwerte wie Demokratie, Freiheit, Frieden und Völkerverständigung** hat die EU kontinuierlich in leere Worthülsen verwandelt. Diese werden dafür immer lächerlicher hochgehalten und beschworen. **Es wird dringend Zeit, dass wir, der Souverän,** diesem erbärmlichen und gefährlichen Trauerspiel ein Ende setzen und die Fäden selbst in die Hand nehmen. In diesem Sinne fordert uns auch das «European Peace Project» auf, am 9. Mai im Rahmen eines Kunstprojekts [den Frieden auszurufen](https://transition-news.org/ein-zeichen-fur-die-friedliche-zukunft-europas-setzen). Seien wir dabei! *\[Titelbild:* *[Pixabay](https://pixabay.com/de/illustrations/vertical-abstract-concept-car-8992833/)]* *** Dieser Beitrag wurde mit dem [Pareto-Client](https://pareto.space/read) geschrieben und ist zuerst auf ***[Transition News](https://transition-news.org/mit-vollgas-in-die-sackgasse)*** erschienen.
@ c631e267:c2b78d3e
2025-03-31 07:23:05*Der Irrsinn ist bei Einzelnen etwas Seltenes –* *\ aber bei Gruppen, Parteien, Völkern, Zeiten die Regel.* *\ Friedrich Nietzsche*   **Erinnern Sie sich an die Horrorkomödie «Scary Movie»?** Nicht, dass ich diese Art Filme besonders erinnerungswürdig fände, aber einige Szenen daraus sind doch gewissermaßen Klassiker. Dazu zählt eine, die das Verhalten vieler Protagonisten in Horrorfilmen parodiert, wenn sie in Panik flüchten. Welchen Weg nimmt wohl die Frau in der Situation auf diesem Bild?  **Diese Szene kommt mir automatisch in den Sinn,** wenn ich aktuelle Entwicklungen in Europa betrachte. Weitreichende Entscheidungen gehen wider jede Logik in die völlig falsche Richtung. Nur ist das hier alles andere als eine Komödie, sondern bitterernst. Dieser Horror ist leider sehr real. **Die Europäische Union hat sich selbst über Jahre** konsequent in eine Sackgasse manövriert. Sie hat es versäumt, sich und ihre Politik selbstbewusst und im Einklang mit ihren Wurzeln auf dem eigenen Kontinent zu positionieren. Stattdessen ist sie in blinder Treue den vermeintlichen «transatlantischen Freunden» auf ihrem Konfrontationskurs gen Osten gefolgt. **In den USA haben sich die Vorzeichen allerdings mittlerweile geändert,** und die einst hoch gelobten «Freunde und Partner» erscheinen den europäischen «Führern» nicht mehr vertrauenswürdig. Das ist spätestens seit der Münchner Sicherheitskonferenz, der Rede von Vizepräsident J. D. Vance und den empörten Reaktionen offensichtlich. Große Teile Europas wirken seitdem wie ein aufgescheuchter Haufen kopfloser Hühner. Orientierung und Kontrolle sind völlig abhanden gekommen. **Statt jedoch umzukehren oder wenigstens zu bremsen** und vielleicht einen Abzweig zu suchen, geben die Crash-Piloten jetzt auf dem Weg durch die Sackgasse erst richtig Gas. Ja sie lösen sogar noch die Sicherheitsgurte und deaktivieren die Airbags. Den vor Angst dauergelähmten Passagieren fällt auch nichts Besseres ein und so schließen sie einfach die Augen. Derweil übertrumpfen sich die [Kommentatoren](https://transition-news.org/wird-ihr-stahlhelm-schon-gegossen) des Events gegenseitig in sensationslüsterner «Berichterstattung». **Wie schon die deutsche Außenministerin mit höchsten UN-Ambitionen,** Annalena Baerbock, proklamiert auch die Europäische Kommission einen «Frieden durch Stärke». Zu dem jetzt vorgelegten, [selbstzerstörerischen](https://transition-news.org/okonomen-eu-rustet-auf-und-schiesst-sich-selbst-ins-knie) Fahrplan zur Ankurbelung der Rüstungsindustrie, genannt «Weißbuch zur europäischen Verteidigung – Bereitschaft 2030», [erklärte](https://ec.europa.eu/commission/presscorner/detail/de/ip_25_793) die Kommissionspräsidentin, die «Ära der Friedensdividende» sei längst vorbei. Soll das heißen, Frieden bringt nichts ein? Eine umfassende Zusammenarbeit an dauerhaften europäischen Friedenslösungen steht demnach jedenfalls nicht zur Debatte. **Zusätzlich brisant ist, dass aktuell «die ganze EU** **[von Deutschen regiert](https://transition-news.org/die-ganze-eu-wird-von-deutschen-regiert)** **wird»,** wie der EU-Parlamentarier und ehemalige UN-Diplomat Michael von der Schulenburg beobachtet hat. Tatsächlich sitzen neben von der Leyen und Strack-Zimmermann noch einige weitere Deutsche in – vor allem auch in Krisenzeiten – wichtigen Spitzenposten der Union. Vor dem Hintergrund der Kriegstreiberei in Deutschland muss eine solche Dominanz mindestens nachdenklich stimmen. **Ihre ursprünglichen Grundwerte wie Demokratie, Freiheit, Frieden und Völkerverständigung** hat die EU kontinuierlich in leere Worthülsen verwandelt. Diese werden dafür immer lächerlicher hochgehalten und beschworen. **Es wird dringend Zeit, dass wir, der Souverän,** diesem erbärmlichen und gefährlichen Trauerspiel ein Ende setzen und die Fäden selbst in die Hand nehmen. In diesem Sinne fordert uns auch das «European Peace Project» auf, am 9. Mai im Rahmen eines Kunstprojekts [den Frieden auszurufen](https://transition-news.org/ein-zeichen-fur-die-friedliche-zukunft-europas-setzen). Seien wir dabei! *\[Titelbild:* *[Pixabay](https://pixabay.com/de/illustrations/vertical-abstract-concept-car-8992833/)]* *** Dieser Beitrag wurde mit dem [Pareto-Client](https://pareto.space/read) geschrieben und ist zuerst auf ***[Transition News](https://transition-news.org/mit-vollgas-in-die-sackgasse)*** erschienen. @ e372d24b:e25df41f
2025-04-05 18:11:15## Unlocking Learning Potential: Why Student's Ideas Matter ### Introduction Recent research in mathematics education emphasizes the importance of valuing and building upon students' initial ideas and intuitive understanding. This approach, often referred to as "taking students' ideas seriously," has enhanced conceptual understanding, problem-solving skills, and overall mathematical achievement. This overview examines this approach's theoretical foundations, cognitive processes, and practical implications in mathematics classrooms.  <div style="padding:56.25% 0 0 0;position:relative;"><iframe src="https://player.vimeo.com/video/1039781401?badge=0&autopause=0&player_id=0&app_id=58479" frameborder="0" allow="autoplay; fullscreen; picture-in-picture; clipboard-write; encrypted-media" style="position:absolute;top:0;left:0;width:100%;height:100%;" title="Practice 1-taking students ideas seriously"></iframe></div><script src="https://player.vimeo.com/api/player.js"></script> [FREE DOWNLOAD - Questions and Prompts](https://dmti-public-resources.s3.us-east-2.amazonaws.com/DMT%20Questions%20and%20Prompts%20-%20Eng.pdf) #### **Theoretical Foundations** Taking students' ideas seriously is grounded in constructivist learning theory and research on how students develop mathematical understanding. Hiebert and Carpenter (1992) argue that "if children possessed internal networks constructed both in and out of school and if they recognized the connections between them, their understanding and performance in both settings would improve." This highlights the importance of connecting students' informal knowledge with formal mathematical concepts. Carpenter's work further emphasizes the value of students' intuitive knowledge: "Children come to school with a great deal of informal or intuitive knowledge of mathematics that can serve as the basis for developing much of the formal mathematics of the primary school curriculum." This suggests that taking students' initial ideas seriously can provide a strong foundation for developing a more sophisticated mathematical understanding. #### **Cognitive Processes** When students' ideas are taken seriously in mathematics classrooms, several cognitive processes are engaged: 1. Schema Formation: As students articulate and refine their ideas, they develop and modify mental frameworks or schemas that organize mathematical concepts. 2. Metacognition: Explaining their thinking engages students' metacognitive processes, promoting reflection on their own understanding and problem-solving strategies. 3. Elaborative Rehearsal: Verbalizing mathematical concepts helps move information from working memory to long-term memory, enhancing retention. 4. Cognitive Conflict: When students encounter differing viewpoints, it can create cognitive conflict, stimulating the reconciliation of new information with existing schemas. #### **Practical Implications** **Eliciting and Valuing Student Ideas** Carpenter and Lehrer argue that for learning with understanding to occur, instruction needs to provide specific opportunities: "For learning with understanding to occur, instruction needs to provide students the opportunity to develop productive relationships, extend and apply their knowledge, reflect about their experiences, articulate what they know, and make knowledge their own." This emphasizes the need for instructional approaches that actively elicit and value student ideas. #### **Creating a Supportive Environment** To effectively take students' ideas seriously, teachers must foster a classroom environment where all contributions are respected. This involves: 1. Provide adequate thinking time for students to formulate their thoughts. 2. Using open-ended questions that encourage diverse thinking and approaches. 3. Implementing collaborative strategies like think-pair-share to build confidence in sharing ideas. #### **Connecting to Formal Mathematics** Hiebert advocates for teaching practices that promote understanding by focusing on "the inherent structure of the emerging mathematical ideas and addressing students' misconceptions as they arise" . This involves helping students connect their informal ideas to more formal mathematical concepts and procedures. #### Impact on Student Learning Research indicates that taking students' ideas seriously can significantly improve mathematical understanding and achievement. A study by Carpenter et al. (1998) found that when teachers based their instruction on students' thinking, students demonstrated greater problem-solving skills and conceptual understanding compared to control groups. Moreover, this approach has increased student engagement and motivation in mathematics. When students feel their ideas are valued, they are more likely to participate actively in mathematical discussions and take intellectual risks. #### Challenges and Considerations While the benefits of taking students' ideas seriously are well-documented, implementing this approach can present challenges: 1. **Time Constraints:** Allowing for extended student discussions and idea exploration can be time-consuming within the constraints of a typical school schedule. 2. **Teacher Preparation:** Effectively building on student ideas requires strong content knowledge and pedagogical skills from teachers. 3. **Assessment Alignment:** Traditional assessment methods may not adequately capture the depth of understanding developed through this approach, necessitating new forms of evaluation. #### Conclusion Taking students' ideas seriously in mathematics education represents a powerful approach to fostering deep conceptual understanding and problem-solving skills. By valuing students' initial thoughts and building upon their intuitive knowledge, educators can create more engaging and effective learning environments. While challenges exist in implementation, the potential benefits for student learning and mathematical achievement make this approach worthy of serious consideration and further research. #### References Ball, D. L., Thames, M. H., & Phelps, G. (2008). Content knowledge for teaching: What makes it special? Journal of Teacher Education, 59(5), 389-407. Boaler, J. (2002). Experiencing school mathematics: Traditional and reform approaches to teaching and their impact on student learning. Routledge. Boaler, J., & Brodie, K. (2004). The importance, nature and impact of teacher questions. In D. E. McDougall & J. A. Ross (Eds.), Proceedings of the 26th annual meeting of the North American Chapter of the International Group for the Psychology of Mathematics Education (Vol. 2, pp. 773-782). Toronto: OISE/UT. Carpenter, T. P., Fennema, E., & Franke, M. L. (1996). Cognitively guided instruction: A knowledge base for reform in primary mathematics instruction. The Elementary School Journal, 97(1), 3-20. Carpenter, T. P., Fennema, E., Franke, M. L., Levi, L., & Empson, S. B. (1999). Children's mathematics: Cognitively guided instruction. Portsmouth, NH: Heinemann. Carpenter, T. P., & Lehrer, R. (1999). Teaching and learning mathematics with understanding. In E. Fennema & T. A. Romberg (Eds.), Mathematics classrooms that promote understanding (pp. 19-32). Mahwah, NJ: Lawrence Erlbaum Associates. Craik, F. I., & Lockhart, R. S. (1972). Levels of processing: A framework for memory research. Journal of Verbal Learning and Verbal Behavior, 11(6), 671-684. Driscoll, M. P. (2005). Psychology of learning for instruction (3rd ed.). Boston: Allyn and Bacon. Flavell, J. H. (1979). Metacognition and cognitive monitoring: A new area of cognitive-developmental inquiry. American Psychologist, 34(10), 906-911. Hiebert, J., & Carpenter, T. P. (1992). Learning and teaching with understanding. In D. A. Grouws (Ed.), Handbook of research on mathematics teaching and learning (pp. 65-97). New York: Macmillan. Hiebert, J., Carpenter, T. P., Fennema, E., Fuson, K. C., Wearne, D., Murray, H., ... & Human, P. (1997). Making sense: Teaching and learning mathematics with understanding. Portsmouth, NH: Heinemann. Lyman, F. (1981). The responsive classroom discussion: The inclusion of all students. In A. S. Anderson (Ed.), Mainstreaming Digest (pp. 109-113). College Park: University of Maryland Press. Piaget, J. (1952). The origins of intelligence in children. New York: International Universities Press. Rowe, M. B. (1986). Wait time: Slowing down may be a way of speeding up! Journal of Teacher Education, 37(1), 43- 50. Shepard, L. A. (2000). The role of assessment in a learning culture. Educational Researcher, 29(7), 4-14. Smith, M. S., & Stein, M. K. (2011). 5 practices for orchestrating productive mathematics discussions. Reston, VA: National Council of Teachers of Mathematics. #### **Social Media.** Research in mathematics education highlights the significance of taking students' ideas seriously, demonstrating how this approach enhances conceptual understanding, problem-solving abilities, and overall mathematical achievement. Rooted in constructivist learning theory, this method engages crucial cognitive processes like schema formation, metacognition, and elaborative rehearsal. By connecting students’ informal knowledge with formal mathematical concepts, educators can establish a robust foundation for advanced mathematical thinking. Studies show that when instruction is based on students' thinking, learners exhibit superior problem-solving skills and a deeper conceptual grasp than traditional teaching methods. Join us in exploring these powerful teaching approaches and their impact on mathematical thinking and achievement!
@ e372d24b:e25df41f
2025-04-05 18:11:15## Unlocking Learning Potential: Why Student's Ideas Matter ### Introduction Recent research in mathematics education emphasizes the importance of valuing and building upon students' initial ideas and intuitive understanding. This approach, often referred to as "taking students' ideas seriously," has enhanced conceptual understanding, problem-solving skills, and overall mathematical achievement. This overview examines this approach's theoretical foundations, cognitive processes, and practical implications in mathematics classrooms.  <div style="padding:56.25% 0 0 0;position:relative;"><iframe src="https://player.vimeo.com/video/1039781401?badge=0&autopause=0&player_id=0&app_id=58479" frameborder="0" allow="autoplay; fullscreen; picture-in-picture; clipboard-write; encrypted-media" style="position:absolute;top:0;left:0;width:100%;height:100%;" title="Practice 1-taking students ideas seriously"></iframe></div><script src="https://player.vimeo.com/api/player.js"></script> [FREE DOWNLOAD - Questions and Prompts](https://dmti-public-resources.s3.us-east-2.amazonaws.com/DMT%20Questions%20and%20Prompts%20-%20Eng.pdf) #### **Theoretical Foundations** Taking students' ideas seriously is grounded in constructivist learning theory and research on how students develop mathematical understanding. Hiebert and Carpenter (1992) argue that "if children possessed internal networks constructed both in and out of school and if they recognized the connections between them, their understanding and performance in both settings would improve." This highlights the importance of connecting students' informal knowledge with formal mathematical concepts. Carpenter's work further emphasizes the value of students' intuitive knowledge: "Children come to school with a great deal of informal or intuitive knowledge of mathematics that can serve as the basis for developing much of the formal mathematics of the primary school curriculum." This suggests that taking students' initial ideas seriously can provide a strong foundation for developing a more sophisticated mathematical understanding. #### **Cognitive Processes** When students' ideas are taken seriously in mathematics classrooms, several cognitive processes are engaged: 1. Schema Formation: As students articulate and refine their ideas, they develop and modify mental frameworks or schemas that organize mathematical concepts. 2. Metacognition: Explaining their thinking engages students' metacognitive processes, promoting reflection on their own understanding and problem-solving strategies. 3. Elaborative Rehearsal: Verbalizing mathematical concepts helps move information from working memory to long-term memory, enhancing retention. 4. Cognitive Conflict: When students encounter differing viewpoints, it can create cognitive conflict, stimulating the reconciliation of new information with existing schemas. #### **Practical Implications** **Eliciting and Valuing Student Ideas** Carpenter and Lehrer argue that for learning with understanding to occur, instruction needs to provide specific opportunities: "For learning with understanding to occur, instruction needs to provide students the opportunity to develop productive relationships, extend and apply their knowledge, reflect about their experiences, articulate what they know, and make knowledge their own." This emphasizes the need for instructional approaches that actively elicit and value student ideas. #### **Creating a Supportive Environment** To effectively take students' ideas seriously, teachers must foster a classroom environment where all contributions are respected. This involves: 1. Provide adequate thinking time for students to formulate their thoughts. 2. Using open-ended questions that encourage diverse thinking and approaches. 3. Implementing collaborative strategies like think-pair-share to build confidence in sharing ideas. #### **Connecting to Formal Mathematics** Hiebert advocates for teaching practices that promote understanding by focusing on "the inherent structure of the emerging mathematical ideas and addressing students' misconceptions as they arise" . This involves helping students connect their informal ideas to more formal mathematical concepts and procedures. #### Impact on Student Learning Research indicates that taking students' ideas seriously can significantly improve mathematical understanding and achievement. A study by Carpenter et al. (1998) found that when teachers based their instruction on students' thinking, students demonstrated greater problem-solving skills and conceptual understanding compared to control groups. Moreover, this approach has increased student engagement and motivation in mathematics. When students feel their ideas are valued, they are more likely to participate actively in mathematical discussions and take intellectual risks. #### Challenges and Considerations While the benefits of taking students' ideas seriously are well-documented, implementing this approach can present challenges: 1. **Time Constraints:** Allowing for extended student discussions and idea exploration can be time-consuming within the constraints of a typical school schedule. 2. **Teacher Preparation:** Effectively building on student ideas requires strong content knowledge and pedagogical skills from teachers. 3. **Assessment Alignment:** Traditional assessment methods may not adequately capture the depth of understanding developed through this approach, necessitating new forms of evaluation. #### Conclusion Taking students' ideas seriously in mathematics education represents a powerful approach to fostering deep conceptual understanding and problem-solving skills. By valuing students' initial thoughts and building upon their intuitive knowledge, educators can create more engaging and effective learning environments. While challenges exist in implementation, the potential benefits for student learning and mathematical achievement make this approach worthy of serious consideration and further research. #### References Ball, D. L., Thames, M. H., & Phelps, G. (2008). Content knowledge for teaching: What makes it special? Journal of Teacher Education, 59(5), 389-407. Boaler, J. (2002). Experiencing school mathematics: Traditional and reform approaches to teaching and their impact on student learning. Routledge. Boaler, J., & Brodie, K. (2004). The importance, nature and impact of teacher questions. In D. E. McDougall & J. A. Ross (Eds.), Proceedings of the 26th annual meeting of the North American Chapter of the International Group for the Psychology of Mathematics Education (Vol. 2, pp. 773-782). Toronto: OISE/UT. Carpenter, T. P., Fennema, E., & Franke, M. L. (1996). Cognitively guided instruction: A knowledge base for reform in primary mathematics instruction. The Elementary School Journal, 97(1), 3-20. Carpenter, T. P., Fennema, E., Franke, M. L., Levi, L., & Empson, S. B. (1999). Children's mathematics: Cognitively guided instruction. Portsmouth, NH: Heinemann. Carpenter, T. P., & Lehrer, R. (1999). Teaching and learning mathematics with understanding. In E. Fennema & T. A. Romberg (Eds.), Mathematics classrooms that promote understanding (pp. 19-32). Mahwah, NJ: Lawrence Erlbaum Associates. Craik, F. I., & Lockhart, R. S. (1972). Levels of processing: A framework for memory research. Journal of Verbal Learning and Verbal Behavior, 11(6), 671-684. Driscoll, M. P. (2005). Psychology of learning for instruction (3rd ed.). Boston: Allyn and Bacon. Flavell, J. H. (1979). Metacognition and cognitive monitoring: A new area of cognitive-developmental inquiry. American Psychologist, 34(10), 906-911. Hiebert, J., & Carpenter, T. P. (1992). Learning and teaching with understanding. In D. A. Grouws (Ed.), Handbook of research on mathematics teaching and learning (pp. 65-97). New York: Macmillan. Hiebert, J., Carpenter, T. P., Fennema, E., Fuson, K. C., Wearne, D., Murray, H., ... & Human, P. (1997). Making sense: Teaching and learning mathematics with understanding. Portsmouth, NH: Heinemann. Lyman, F. (1981). The responsive classroom discussion: The inclusion of all students. In A. S. Anderson (Ed.), Mainstreaming Digest (pp. 109-113). College Park: University of Maryland Press. Piaget, J. (1952). The origins of intelligence in children. New York: International Universities Press. Rowe, M. B. (1986). Wait time: Slowing down may be a way of speeding up! Journal of Teacher Education, 37(1), 43- 50. Shepard, L. A. (2000). The role of assessment in a learning culture. Educational Researcher, 29(7), 4-14. Smith, M. S., & Stein, M. K. (2011). 5 practices for orchestrating productive mathematics discussions. Reston, VA: National Council of Teachers of Mathematics. #### **Social Media.** Research in mathematics education highlights the significance of taking students' ideas seriously, demonstrating how this approach enhances conceptual understanding, problem-solving abilities, and overall mathematical achievement. Rooted in constructivist learning theory, this method engages crucial cognitive processes like schema formation, metacognition, and elaborative rehearsal. By connecting students’ informal knowledge with formal mathematical concepts, educators can establish a robust foundation for advanced mathematical thinking. Studies show that when instruction is based on students' thinking, learners exhibit superior problem-solving skills and a deeper conceptual grasp than traditional teaching methods. Join us in exploring these powerful teaching approaches and their impact on mathematical thinking and achievement! @ 57d1a264:69f1fee1
2025-03-29 18:02:16> This UX research has been redacted by @iqra from the Bitcoin.Design [community](https://discord.gg/K7aQ5PErht), and shared for review and feedback! Don't be shy, share your thoughts.  - - - ## 1️⃣ Introduction #### Project Overview 📌 **Product:** BlueWallet (Bitcoin Wallet) 📌 **Goal:** Improve onboarding flow and enhance accessibility for a better user experience. 📌 **Role:** UX Designer 📌 **Tools Used:** Figma, Notion #### Why This Case Study? 🔹 BlueWallet is a self-custodial Bitcoin wallet, but **users struggle with onboarding due to unclear instructions**. 🔹 **Accessibility issues** (low contrast, small fonts) create **barriers for visually impaired users**. 🔹 Competitors like **Trust Wallet and MetaMask offer better-guided onboarding**. This case study presents **UX/UI improvements** to make BlueWallet **more intuitive and inclusive**. - - - ## 2️⃣ Problem Statement: Why BlueWalletʼs Onboarding Needs Improvement #### 🔹 **Current Challenges:** 1️⃣ **Onboarding Complexity** - BlueWallet lacks **step-by-step guidance**, leaving users confused about wallet creation and security.   2️⃣ **No Educational Introduction** - Users land directly on the wallet screen with **no explanation of private keys, recovery phrases, or transactions**. 3️⃣ **Transaction Flow Issues** - Similar-looking **"Send" and "Receive" buttons** cause confusion. 4️⃣ **Poor Accessibility** - Small fonts and low contrast make navigation difficult. #### 🔍 **Impact on Users:** **Higher drop-off rates** due to frustration during onboarding. **Security risks** as users skip key wallet setup steps. **Limited accessibility** for users with visual impairments. #### 📌 **Competitive Gap:** Unlike competitors (Trust Wallet, MetaMask), BlueWallet does not offer: ✅ A guided onboarding process ✅ Security education during setup ✅ Intuitive transaction flow      Somehow, this wallet has much better UI than the BlueWallet Bitcoin wallet. - - - ## 3️⃣ User Research & Competitive Analysis #### User Testing Findings 🔹 Conducted usability testing with **5 users** onboarding for the first time. 🔹 **Key Findings:** ✅ 3 out of 5 users **felt lost** due to missing explanations. ✅ 60% **had trouble distinguishing transaction buttons**. ✅ 80% **found the text difficult to read** due to low contrast. #### Competitive Analysis We compared BlueWallet with top crypto wallets: | Wallet | Onboarding UX | Security Guidance | Accessibility Features | |---|---|---|---| | BlueWallet | ❌ No guided onboarding | ❌ Minimal explanation | ❌ Low contrast, small fonts | | Trust Wallet | ✅ Step-by-step setup | ✅ Security best practices | ✅ High contrast UI | | MetaMask | ✅ Interactive tutorial | ✅ Private key education | ✅ Clear transaction buttons | 📌 **Key Insight:** BlueWallet lacks **guided setup and accessibility enhancements**, making it harder for beginners. ## 📌 User Persona To better understand the users facing onboarding challenges, I developed a **persona** based on research and usability testing. #### 🔹 Persona 1: Alex Carter (Bitcoin Beginner & Investor) 👤 **Profile:** - **Age:** 28 - **Occupation:** Freelance Digital Marketer - **Tech Knowledge:** Moderate - Familiar with online transactions, new to Bitcoin) - **Pain Points:** - Finds **Bitcoin wallets confusing**. - - Doesnʼt understand **seed phrases & security features**. - - **Worried about losing funds** due to a lack of clarity in transactions. 📌 **Needs:** ✅ A **simple, guided** wallet setup. ✅ **Clear explanations** of security terms (without jargon). ✅ Easy-to-locate **Send/Receive buttons**. 📌 **Persona Usage in Case Study:** - Helps define **who we are designing for**. - Guides **design decisions** by focusing on user needs. #### 🔹 Persona 2: Sarah Mitchell (Accessibility Advocate & Tech Enthusiast) 👤 **Profile:** - **Age:** 35 - **Occupation:** UX Researcher & Accessibility Consultant - **Tech Knowledge:** High (Uses Bitcoin but struggles with accessibility barriers) 📌 **Pain Points:** ❌ Struggles with small font sizes & low contrast. ❌ Finds the UI difficult to navigate with a screen reader. ❌ Confused by identical-looking transaction buttons. 📌 **Needs:** ✅ A **high-contrast UI** that meets **WCAG accessibility standards**. ✅ **Larger fonts & scalable UI elements** for better readability. ✅ **Keyboard & screen reader-friendly navigation** for seamless interaction. 📌 **Why This Persona Matters:** - Represents users with visual impairments who rely on accessible design. - Ensures the design accommodates inclusive UX principles. - - - ## 4️⃣ UX/UI Solutions & Design Improvements #### 📌 Before (Current Issues) ❌ Users land **directly on the wallet screen** with no instructions. ❌ **"Send" & "Receive" buttons look identical** , causing transaction confusion. ❌ **Small fonts & low contrast** reduce readability. #### ✅ After (Proposed Fixes) ✅ **Step-by-step onboarding** explaining wallet creation, security, and transactions. ✅ **Visually distinct transaction buttons** (color and icon changes). ✅ **WCAG-compliant text contrast & larger fonts** for better readability. #### 1️⃣ Redesigned Onboarding Flow ✅ Added a **progress indicator** so users see where they are in setup. ✅ Used **plain, non-technical language** to explain wallet creation & security. ✅ Introduced a **"Learn More" button** to educate users on security. #### 2️⃣ Accessibility Enhancements ✅ Increased **contrast ratio** for better text readability. ✅ Used **larger fonts & scalable UI elements**. ✅ Ensured **screen reader compatibility** (VoiceOver & TalkBack support). #### 3️⃣ Transaction Flow Optimization ✅ Redesigned **"Send" & "Receive" buttons** for clear distinction. ✅ Added **clearer icons & tooltips** for transaction steps. ## 5️⃣ Wireframes & Design Improvements: #### 🔹 Welcome Screen (First Screen When User Opens Wallet) **📌 Goal: Give a brief introduction & set user expectations** ✅ App logo + **short tagline** (e.g., "Secure, Simple, Self-Custody Bitcoin Wallet") ✅ **1-2 line explanation** of what BlueWallet is (e.g., "Your gateway to managing Bitcoin securely.") ✅ **"Get Started" button** → Le ads to **next step: Wallet Setup** ✅ **"Already have a wallet?"** → Import option 🔹 **Example UI Elements:** - BlueWallet Logo - **Title:** "Welcome to BlueWallet" - **Subtitle:** "Easily store, send, and receive Bitcoin." - CTA: "Get Started" (Primary) | "Import Wallet" (Secondary)  #### 🔹 Screen 2: Choose Wallet Type (New or Import) **📌 Goal: Let users decide how to proceed** ✅ **Two clear options:** - **Create a New Wallet** (For first-time users) - **Import Existing Wallet** (For users with a backup phrase) ✅ Brief explanation of each option 🔹 **Example UI Elements: - **Title:** "How do you want to start?" - **Buttons:** "Create New Wallet" | "Import Wallet"  #### 🔹 Screen 3: Security & Seed Phrase Setup (Critical Step) **📌 Goal: Educate users about wallet security & backups** ✅ Explain **why seed phrases are important** ✅ **Clear step-by-step instructions** on writing down & storing the phrase ✅ **Warning:** "If you lose your recovery phrase, you lose access to your wallet." ✅ **CTA:** "Generate Seed Phrase" → Next step 🔹 **Example UI Elements: - Title:** "Secure Your Wallet" - **Subtitle:** "Your seed phrase is the key to your Bitcoin. Keep it safe!" - **Button:** "Generate Seed Phrase"  ## 🔹 Screen 4: Seed Phrase Display & Confirmation **📌 Goal: Ensure users write down the phrase correctly** ✅ Display **12- or 24-word** seed phrase ✅ **“I have written it downˮ checkbox** before proceeding ✅ Next screen: **Verify seed phrase** (drag & drop, re-enter some words) 🔹 **Example UI Elements:** - **Title:** "Write Down Your Seed Phrase" - List of 12/24 Words (Hidden by Default) - **Checkbox:** "I have safely stored my phrase" - **Button:** "Continue"  ### 🔹 Screen 5: Wallet Ready! (Final Step) **📌 Goal: Confirm setup & guide users on next actions** ✅ **Success message** ("Your wallet is ready!") ✅ **Encourage first action:** - “Receive Bitcoinˮ → Show wallet address - “Send Bitcoinˮ → Walkthrough on making transactions ✅ Short explainer: Where to find the Send/Receive buttons 🔹 **Example UI Elements:** - **Title:** "You're All Set!" - **Subtitle:** "Start using BlueWallet now." - **Buttons:** "Receive Bitcoin" | "View Wallet"  - - - ## 5️⃣ Prototype & User Testing Results 🔹 **Created an interactive prototype in Figma** to test the new experience. 🔹 **User Testing Results:** ✅ **40% faster onboarding completion time.** ✅ **90% of users found transaction buttons clearer.** 🔹 **User Feedback:** ✅ “Now I understand the security steps clearly.ˮ ✅ “The buttons are easier to find and use.ˮ - - - ## 6️⃣ Why This Matters: Key Takeaways 📌 **Impact of These UX/UI Changes:** ✅ **Reduced user frustration** by providing a step-by-step onboarding guide. ✅ **Improved accessibility** , making the wallet usable for all. ✅ **More intuitive transactions** , reducing errors. - - - ## 7️⃣ Direct link to figma file and Prototype Figma file: [https://www.figma.com/design/EPb4gVgAMEgF5GBDdtt81Z/Blue-Wallet-UI- Improvements?node-id=0-1&t=Y2ni1SfvuQQnoB7s-1](https://www.figma.com/design/EPb4gVgAMEgF5GBDdtt81Z/Blue-Wallet-UI- Improvements?node-id=0-1&t=Y2ni1SfvuQQnoB7s-1) Prototype: [https://www.figma.com/proto/EPb4gVgAMEgF5GBDdtt81Z/Blue-Wallet-UI- Improvements?node-id=1-2&p=f&t=FndTJQNCE7nEIa84-1&scaling=scale- down&content-scaling=fixed&page-id=0%3A1&starting-point-node- id=1%3A2&show-proto-sidebar=1](https://www.figma.com/proto/EPb4gVgAMEgF5GBDdtt81Z/Blue-Wallet-UI- Improvements?node-id=1-2&p=f&t=FndTJQNCE7nEIa84-1&scaling=scale- down&content-scaling=fixed&page-id=0%3A1&starting-point-node- id=1%3A2&show-proto-sidebar=1) Original PDF available from [here](https://cdn.discordapp.com/attachments/903126164795699212/1355561527394173243/faf3ee46-b501-459c-ba0e-bf7e38843bc8_UX_Case_Study__1.pdf?ex=67e9608d&is=67e80f0d&hm=d0c386ce2cfd6e0ebe6bde0a904e884229f52bf547adf1f7bc884e17bb4aa59e&) originally posted at https://stacker.news/items/928822
@ 57d1a264:69f1fee1
2025-03-29 18:02:16> This UX research has been redacted by @iqra from the Bitcoin.Design [community](https://discord.gg/K7aQ5PErht), and shared for review and feedback! Don't be shy, share your thoughts.  - - - ## 1️⃣ Introduction #### Project Overview 📌 **Product:** BlueWallet (Bitcoin Wallet) 📌 **Goal:** Improve onboarding flow and enhance accessibility for a better user experience. 📌 **Role:** UX Designer 📌 **Tools Used:** Figma, Notion #### Why This Case Study? 🔹 BlueWallet is a self-custodial Bitcoin wallet, but **users struggle with onboarding due to unclear instructions**. 🔹 **Accessibility issues** (low contrast, small fonts) create **barriers for visually impaired users**. 🔹 Competitors like **Trust Wallet and MetaMask offer better-guided onboarding**. This case study presents **UX/UI improvements** to make BlueWallet **more intuitive and inclusive**. - - - ## 2️⃣ Problem Statement: Why BlueWalletʼs Onboarding Needs Improvement #### 🔹 **Current Challenges:** 1️⃣ **Onboarding Complexity** - BlueWallet lacks **step-by-step guidance**, leaving users confused about wallet creation and security.   2️⃣ **No Educational Introduction** - Users land directly on the wallet screen with **no explanation of private keys, recovery phrases, or transactions**. 3️⃣ **Transaction Flow Issues** - Similar-looking **"Send" and "Receive" buttons** cause confusion. 4️⃣ **Poor Accessibility** - Small fonts and low contrast make navigation difficult. #### 🔍 **Impact on Users:** **Higher drop-off rates** due to frustration during onboarding. **Security risks** as users skip key wallet setup steps. **Limited accessibility** for users with visual impairments. #### 📌 **Competitive Gap:** Unlike competitors (Trust Wallet, MetaMask), BlueWallet does not offer: ✅ A guided onboarding process ✅ Security education during setup ✅ Intuitive transaction flow      Somehow, this wallet has much better UI than the BlueWallet Bitcoin wallet. - - - ## 3️⃣ User Research & Competitive Analysis #### User Testing Findings 🔹 Conducted usability testing with **5 users** onboarding for the first time. 🔹 **Key Findings:** ✅ 3 out of 5 users **felt lost** due to missing explanations. ✅ 60% **had trouble distinguishing transaction buttons**. ✅ 80% **found the text difficult to read** due to low contrast. #### Competitive Analysis We compared BlueWallet with top crypto wallets: | Wallet | Onboarding UX | Security Guidance | Accessibility Features | |---|---|---|---| | BlueWallet | ❌ No guided onboarding | ❌ Minimal explanation | ❌ Low contrast, small fonts | | Trust Wallet | ✅ Step-by-step setup | ✅ Security best practices | ✅ High contrast UI | | MetaMask | ✅ Interactive tutorial | ✅ Private key education | ✅ Clear transaction buttons | 📌 **Key Insight:** BlueWallet lacks **guided setup and accessibility enhancements**, making it harder for beginners. ## 📌 User Persona To better understand the users facing onboarding challenges, I developed a **persona** based on research and usability testing. #### 🔹 Persona 1: Alex Carter (Bitcoin Beginner & Investor) 👤 **Profile:** - **Age:** 28 - **Occupation:** Freelance Digital Marketer - **Tech Knowledge:** Moderate - Familiar with online transactions, new to Bitcoin) - **Pain Points:** - Finds **Bitcoin wallets confusing**. - - Doesnʼt understand **seed phrases & security features**. - - **Worried about losing funds** due to a lack of clarity in transactions. 📌 **Needs:** ✅ A **simple, guided** wallet setup. ✅ **Clear explanations** of security terms (without jargon). ✅ Easy-to-locate **Send/Receive buttons**. 📌 **Persona Usage in Case Study:** - Helps define **who we are designing for**. - Guides **design decisions** by focusing on user needs. #### 🔹 Persona 2: Sarah Mitchell (Accessibility Advocate & Tech Enthusiast) 👤 **Profile:** - **Age:** 35 - **Occupation:** UX Researcher & Accessibility Consultant - **Tech Knowledge:** High (Uses Bitcoin but struggles with accessibility barriers) 📌 **Pain Points:** ❌ Struggles with small font sizes & low contrast. ❌ Finds the UI difficult to navigate with a screen reader. ❌ Confused by identical-looking transaction buttons. 📌 **Needs:** ✅ A **high-contrast UI** that meets **WCAG accessibility standards**. ✅ **Larger fonts & scalable UI elements** for better readability. ✅ **Keyboard & screen reader-friendly navigation** for seamless interaction. 📌 **Why This Persona Matters:** - Represents users with visual impairments who rely on accessible design. - Ensures the design accommodates inclusive UX principles. - - - ## 4️⃣ UX/UI Solutions & Design Improvements #### 📌 Before (Current Issues) ❌ Users land **directly on the wallet screen** with no instructions. ❌ **"Send" & "Receive" buttons look identical** , causing transaction confusion. ❌ **Small fonts & low contrast** reduce readability. #### ✅ After (Proposed Fixes) ✅ **Step-by-step onboarding** explaining wallet creation, security, and transactions. ✅ **Visually distinct transaction buttons** (color and icon changes). ✅ **WCAG-compliant text contrast & larger fonts** for better readability. #### 1️⃣ Redesigned Onboarding Flow ✅ Added a **progress indicator** so users see where they are in setup. ✅ Used **plain, non-technical language** to explain wallet creation & security. ✅ Introduced a **"Learn More" button** to educate users on security. #### 2️⃣ Accessibility Enhancements ✅ Increased **contrast ratio** for better text readability. ✅ Used **larger fonts & scalable UI elements**. ✅ Ensured **screen reader compatibility** (VoiceOver & TalkBack support). #### 3️⃣ Transaction Flow Optimization ✅ Redesigned **"Send" & "Receive" buttons** for clear distinction. ✅ Added **clearer icons & tooltips** for transaction steps. ## 5️⃣ Wireframes & Design Improvements: #### 🔹 Welcome Screen (First Screen When User Opens Wallet) **📌 Goal: Give a brief introduction & set user expectations** ✅ App logo + **short tagline** (e.g., "Secure, Simple, Self-Custody Bitcoin Wallet") ✅ **1-2 line explanation** of what BlueWallet is (e.g., "Your gateway to managing Bitcoin securely.") ✅ **"Get Started" button** → Le ads to **next step: Wallet Setup** ✅ **"Already have a wallet?"** → Import option 🔹 **Example UI Elements:** - BlueWallet Logo - **Title:** "Welcome to BlueWallet" - **Subtitle:** "Easily store, send, and receive Bitcoin." - CTA: "Get Started" (Primary) | "Import Wallet" (Secondary)  #### 🔹 Screen 2: Choose Wallet Type (New or Import) **📌 Goal: Let users decide how to proceed** ✅ **Two clear options:** - **Create a New Wallet** (For first-time users) - **Import Existing Wallet** (For users with a backup phrase) ✅ Brief explanation of each option 🔹 **Example UI Elements: - **Title:** "How do you want to start?" - **Buttons:** "Create New Wallet" | "Import Wallet"  #### 🔹 Screen 3: Security & Seed Phrase Setup (Critical Step) **📌 Goal: Educate users about wallet security & backups** ✅ Explain **why seed phrases are important** ✅ **Clear step-by-step instructions** on writing down & storing the phrase ✅ **Warning:** "If you lose your recovery phrase, you lose access to your wallet." ✅ **CTA:** "Generate Seed Phrase" → Next step 🔹 **Example UI Elements: - Title:** "Secure Your Wallet" - **Subtitle:** "Your seed phrase is the key to your Bitcoin. Keep it safe!" - **Button:** "Generate Seed Phrase"  ## 🔹 Screen 4: Seed Phrase Display & Confirmation **📌 Goal: Ensure users write down the phrase correctly** ✅ Display **12- or 24-word** seed phrase ✅ **“I have written it downˮ checkbox** before proceeding ✅ Next screen: **Verify seed phrase** (drag & drop, re-enter some words) 🔹 **Example UI Elements:** - **Title:** "Write Down Your Seed Phrase" - List of 12/24 Words (Hidden by Default) - **Checkbox:** "I have safely stored my phrase" - **Button:** "Continue"  ### 🔹 Screen 5: Wallet Ready! (Final Step) **📌 Goal: Confirm setup & guide users on next actions** ✅ **Success message** ("Your wallet is ready!") ✅ **Encourage first action:** - “Receive Bitcoinˮ → Show wallet address - “Send Bitcoinˮ → Walkthrough on making transactions ✅ Short explainer: Where to find the Send/Receive buttons 🔹 **Example UI Elements:** - **Title:** "You're All Set!" - **Subtitle:** "Start using BlueWallet now." - **Buttons:** "Receive Bitcoin" | "View Wallet"  - - - ## 5️⃣ Prototype & User Testing Results 🔹 **Created an interactive prototype in Figma** to test the new experience. 🔹 **User Testing Results:** ✅ **40% faster onboarding completion time.** ✅ **90% of users found transaction buttons clearer.** 🔹 **User Feedback:** ✅ “Now I understand the security steps clearly.ˮ ✅ “The buttons are easier to find and use.ˮ - - - ## 6️⃣ Why This Matters: Key Takeaways 📌 **Impact of These UX/UI Changes:** ✅ **Reduced user frustration** by providing a step-by-step onboarding guide. ✅ **Improved accessibility** , making the wallet usable for all. ✅ **More intuitive transactions** , reducing errors. - - - ## 7️⃣ Direct link to figma file and Prototype Figma file: [https://www.figma.com/design/EPb4gVgAMEgF5GBDdtt81Z/Blue-Wallet-UI- Improvements?node-id=0-1&t=Y2ni1SfvuQQnoB7s-1](https://www.figma.com/design/EPb4gVgAMEgF5GBDdtt81Z/Blue-Wallet-UI- Improvements?node-id=0-1&t=Y2ni1SfvuQQnoB7s-1) Prototype: [https://www.figma.com/proto/EPb4gVgAMEgF5GBDdtt81Z/Blue-Wallet-UI- Improvements?node-id=1-2&p=f&t=FndTJQNCE7nEIa84-1&scaling=scale- down&content-scaling=fixed&page-id=0%3A1&starting-point-node- id=1%3A2&show-proto-sidebar=1](https://www.figma.com/proto/EPb4gVgAMEgF5GBDdtt81Z/Blue-Wallet-UI- Improvements?node-id=1-2&p=f&t=FndTJQNCE7nEIa84-1&scaling=scale- down&content-scaling=fixed&page-id=0%3A1&starting-point-node- id=1%3A2&show-proto-sidebar=1) Original PDF available from [here](https://cdn.discordapp.com/attachments/903126164795699212/1355561527394173243/faf3ee46-b501-459c-ba0e-bf7e38843bc8_UX_Case_Study__1.pdf?ex=67e9608d&is=67e80f0d&hm=d0c386ce2cfd6e0ebe6bde0a904e884229f52bf547adf1f7bc884e17bb4aa59e&) originally posted at https://stacker.news/items/928822 @ 57d1a264:69f1fee1
2025-03-29 17:15:17 - Once activated, "Accept From Any Mint” is the default setting. This is the easiest way to get started, let's the user start acceptance Cashu ecash just out of the box. - If someone does want to be selective, they can choose “Accept From Trusted Mints,” and that brings up a field where they can add specific mint URLs they trust. - “Find a Mint” section on the right with a button links directly to bitcoinmints.com, already filtered for Cashu mints, so users can easily browse options. - Mint info modal shows mint technical details stuff from the NUT06 spec. Since this is geared towards the more technical users I left the field names and NUT number as-is instead of trying to make it more semantic. originally posted at https://stacker.news/items/928800
@ 57d1a264:69f1fee1
2025-03-29 17:15:17 - Once activated, "Accept From Any Mint” is the default setting. This is the easiest way to get started, let's the user start acceptance Cashu ecash just out of the box. - If someone does want to be selective, they can choose “Accept From Trusted Mints,” and that brings up a field where they can add specific mint URLs they trust. - “Find a Mint” section on the right with a button links directly to bitcoinmints.com, already filtered for Cashu mints, so users can easily browse options. - Mint info modal shows mint technical details stuff from the NUT06 spec. Since this is geared towards the more technical users I left the field names and NUT number as-is instead of trying to make it more semantic. originally posted at https://stacker.news/items/928800 @ 866e0139:6a9334e5
2025-04-05 11:00:25*** **Autor:** **[CJ Hopkins.](https://cjhopkins.substack.com/)** *Dieser Beitrag wurde mit dem **[Pareto-Client](https://pareto.space/read)** geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden **[hier.](https://pareto.space/read?category=friedenstaube)*** Dieser Beitrag erschien zuerst auf dem **[Substack-Blog des Autors.](https://cjhopkins.substack.com/p/the-war-on-whatever)**  *** Er soll andauern, was er auch tut. Genau wie der nie endende Krieg in Orwells 1984 wird er vom Imperium gegen seine eigenen Untertanen geführt, aber nicht nur, um die Struktur der Gesellschaft intakt zu halten, sondern in unserem Fall auch, um die Gesellschaft in eine neo-totalitäre global-kapitalistische Dystopie zu verwandeln. Bist du nicht vertraut mit dem Krieg gegen was auch immer? Nun ja, okay, du erinnerst dich an den Krieg gegen den Terror. Du erinnerst dich daran, als die „Freiheit und Demokratie“ von „den Terroristen“ angegriffen wurden und wir keine andere Wahl hatten, als uns unserer demokratischen Rechte und Prinzipien zu entledigen, einen nationalen „Notstand“ auszurufen, die verfassungsmäßigen Rechte der Menschen auszusetzen, einen Angriffskrieg gegen ein Land im Nahen Osten anzuzetteln, das für uns keinerlei Bedrohung darstellte, und unsere Straßen, Bahnhöfe, Flughäfen und alle anderen Orte mit schwer bewaffneten Soldaten zu füllen, denn sonst hätten „die Terroristen gewonnen“. Du erinnerst dich, als wir ein Offshore-Gulag bauten, um verdächtige Terroristen auf unbestimmte Zeit wegzusperren, die wir zuvor zu CIA-Geheimgefängnissen verschleppt hatten, wo wir sie gefoltert und gedemütigt haben, richtig? Natürlich erinnerst du dich. Wer könnte das vergessen? *** **DIE FRIEDENSTAUBE FLIEGT AUCH IN IHR POSTFACH!** ***[Hier](https://pareto.space/u/friedenstaube@pareto.space)*** *können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht). Sie wollen der Genossenschaft beitreten oder uns unterstützen? Mehr Infos* ***[hier](https://pareto.space/a/naddr1qqsxydty8qek2wpsvyck2wphxajrvefjvesngcfhxenrgdty89nrzvgzyzrxuqfepp2e79w9aluaz2252vyz7qdpld05pgjmeurhdgm2jv6w2qcyqqq823cpp4mhxue69uhkummn9ekx7mqprpmhxue69uhkummnw3ezuurpwfjhgmewwdcxzcm9qythwumn8ghj7mn0wd68ytnsv9ex2ar09e6x7amwqyf8wumn8ghj7mmxve3ksctfdch8qatzqythwumn8ghj7urpwfjhgmewdehhxarjxyhxxmmdszcvqk)*** *oder am Ende des Textes.* *** Erinnerst du dich, als die National Security Agency keine andere Wahl hatte, als ein geheimes „Terroristen-Überwachungsprogramm“ einzurichten, um Amerikaner auszuspionieren, oder sonst „hätten die Terroristen gewonnen“? Oder wie wäre es mit den „Anti-Terror“-Unterleibsuntersuchungen der TSA, der Behörde für Transportsicherheit, die nach über zwanzig Jahren immer noch in Kraft sind? Und was ist mit dem Krieg gegen den Populismus? An den erinnerst du dich vielleicht nicht so gut. Ich erinnere mich, denn ich habe zwei Bücher dazu veröffentlicht. Er begann im Sommer 2016, als das Imperium erkannte, dass „rechte Populisten“ die „Freiheit und Demokratie“ in Europa bedrohten und Trump in den USA auf dem Vormarsch war. Also wurde ein weiterer „Notstand“ ausgerufen – diesmal von der Gemeinschaft der Geheimdienste, den Medien, der akademischen Welt und der Kulturindustrie. Ja, genau, es war wieder einmal an der Zeit, unsere demokratischen Prinzipien hintanzustellen, „Hassrede“ in sozialen Medien zu zensieren, die Massen mit lächerlicher offizieller Propaganda über „Russiagate,“ „Hitlergate“ und so weiter zu bombardieren – sonst hätten „die Rechtspopulisten gewonnen.“ Der Krieg gegen den Populismus gipfelte in der Einführung des Neuen Normalen Reichs.  Im Frühjahr 2020 rief das Imperium einen globalen „gesundheitlichen Ausnahmezustand“ aus, als Reaktion auf ein Virus mit einer Überlebensrate von etwa 99,8 Prozent. Das Imperium hatte keine andere Wahl, als ganze Gesellschaften abzuriegeln, jeden dazu zu zwingen, in der Öffentlichkeit medizinisch aussehende Masken zu tragen, die Öffentlichkeit mit Propaganda und Lügen zu bombardieren, die Menschen dazu zu nötigen, sich einer Reihe experimenteller mRNA-„Impfungen“ zu unterziehen, Proteste gegen ihre Dekrete zu verbieten und systematisch diejenigen zu zensieren und zu verfolgen, die es wagten, ihre erfundenen „Fakten“ in Frage zu stellen oder ihr totalitäres Programm zu kritisieren. Das Imperium hatte keine andere Wahl, als das alles zu tun, denn sonst hätten „die Covid-Leugner, die Impfgegner, die Verschwörungstheoretiker und all die anderen Extremisten gewonnen.“ Ich bin mir ziemlich sicher, dass du dich an all das erinnerst. Und jetzt … nun, hier sind wir. Ja, du hast es erraten – es ist wieder einmal an der Zeit, kräftig auf die US-Verfassung und die Meinungsfreiheit zu scheißen, Menschen in irgendein salvadorianisches Höllenloch abzuschieben, das wir angemietet haben, weil ein Polizist ihre Tattoos nicht mochte, Universitätsstudenten wegen ihrer Anti-Israel-Proteste festzunehmen und zu verschleppen und natürlich die Massen mit Lügen und offizieller Propaganda zu bombardieren, denn … okay, alle zusammen jetzt: „sonst hätten die antisemitischen Terroristen und venezolanischen Banden gewonnen!“ Fängst du an, ein Muster zu erkennen? Ja? Willkommen beim Krieg gegen-was-auch-immer! Wenn du die Zusammenhänge noch nicht ganz siehst, okay, lass es mich noch einmal ganz simpel erklären. Das globale ideologische System, in dem wir alle leben, wird totalitär. (Dieses System ist der globale Kapitalismus, aber nenne es, wie du willst. Es ist mir scheißegal.) Es reißt die Simulation der Demokratie nieder, die es nicht mehr aufrechterhalten muss. Der Kalte Krieg ist vorbei. Der Kommunismus ist tot. Der globale Kapitalismus hat keine externen Feinde mehr. Also muss er die Massen nicht mehr mit demokratischen Rechten und Freiheiten besänftigen. Deshalb entzieht er uns diese Rechte nach und nach und konditioniert uns darauf, ihren Verlust hinzunehmen. Er tut dies, indem er eine Reihe von „Notständen“ inszeniert, jeder mit einer anderen „Bedrohung“ für die „Demokratie,“ die „Freiheit,“ „Amerika“ oder „den Planeten“ – oder was auch immer. Jeder mit seinen eigenen „Monstern,“ die eine so große Gefahr für die „Freiheit“ oder was auch immer darstellen, dass wir unsere verfassungsmäßigen Rechte aufgeben und die demokratischen Werte ad absurdum führen müssen, denn: sonst „würden die Monster gewinnen.“  Es tut dies, indem es sein Antlitz von „links“ nach „rechts,“ dann zurück nach „links“, und dann zurück nach „rechts,“ dann nach „links“ und so weiter neigt, weil es unsere Kooperation dafür benötigt. Nicht die Kooperation von uns allen auf einmal. Nur eine kooperative demografische Gruppe auf einmal. Es ist dabei erfolgreich – also das System – indem es unsere Angst und unseren Hass instrumentalisiert. Dem System ist es völlig egal, ob wir uns als „links“ oder „rechts“ identifizieren, aber es braucht uns gespalten in „links“ und „rechts,“ damit es unsere Angst und unseren Hass aufeinander nähren kann … eine Regierung, ein „Notfall,“ ein „Krieg“ nach dem anderen. Da hast du es. Das ist der Krieg gegen was auch immer. Noch simpler kann ich es nicht erklären. Oh, und noch eine letzte Sache … wenn du einer meiner ehemaligen Fans bist, wie Rob, die über meine „Einsichten“ oder Loyalitäten oder was auch immer verwirrt sind … nun, der Text, den du gerade gelesen hast, sollte das für dich klären. Ich stehe auf keiner Seite. Überhaupt keiner. Aber ich habe ein paar grundlegende demokratische Prinzipien. Und die richten sich nicht danach, was gerade populär ist oder wer im Weißen Haus sitzt. Die Sache ist die: Ich muss mich morgens im Spiegel anschauen können ohne dort einen Heuchler oder … du weißt schon, einen Feigling zu sehen. (Aus dem Amerikanischen übersetzt von **[René Boyke](https://covid-justiz.de/)**). *** *CJ Hopkins ist ein US-amerikanischer [Dramatiker](https://deutsch.wikibrief.org/wiki/Playwright "Dramatiker"), [Romanautor](https://deutsch.wikibrief.org/wiki/Novelist "Romanschriftsteller") und [politischer Satiriker](https://deutsch.wikibrief.org/wiki/Political_satire "Politische Satire"). Zu seinen Werken zählen die Stücke Horse Country, Screwmachine/Eyecandy und [The Extremists](https://deutsch.wikibrief.org/wiki/The_Extremists_%28play%29 "Die Extremisten (Spiel)"). Er hat sich als profilierter Kritiker des Corona-Regimes profiliert und veröffentlicht regelmäßig auf seinem* ***[Substack-Blog.](https://cjhopkins.substack.com/)*** Sein aktuelles Buch: <https://x.com/CJHopkins_Z23/status/1907795633689264530> Hier in einem aktuellen Gespräch:  <https://www.youtube.com/watch?v=wF-G32P0leI> *** **LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!** ***[Hier](https://pareto.space/u/friedenstaube@pareto.space)*** *können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt. (Vorerst alle, da wir den Mailversand testen, später ca. drei Mails pro Woche.)* Schon jetzt können Sie uns unterstützen: * Für **50 CHF/EURO** bekommen Sie ein Jahresabo der Friedenstaube. * Für **120 CHF/EURO** bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube. * Für **500 CHF/EURO** werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube. * Ab **1000 CHF** werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie). **Für Einzahlungen in CHF (Betreff: Friedenstaube):**  **Für Einzahlungen in Euro:** Milosz Matuschek IBAN DE 53710520500000814137 BYLADEM1TST Sparkasse Traunstein-Trostberg **Betreff: Friedenstaube** Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: <milosz@pareto.space> *** **Sie sind noch nicht auf** [Nostr](https://nostr.com/) **and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil!** Erstellen Sie sich einen Account auf [Start.](https://start.njump.me/) Weitere Onboarding-Leitfäden gibt es im [Pareto-Wiki.](https://wiki.pareto.space/de/home)
@ 866e0139:6a9334e5
2025-04-05 11:00:25*** **Autor:** **[CJ Hopkins.](https://cjhopkins.substack.com/)** *Dieser Beitrag wurde mit dem **[Pareto-Client](https://pareto.space/read)** geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden **[hier.](https://pareto.space/read?category=friedenstaube)*** Dieser Beitrag erschien zuerst auf dem **[Substack-Blog des Autors.](https://cjhopkins.substack.com/p/the-war-on-whatever)**  *** Er soll andauern, was er auch tut. Genau wie der nie endende Krieg in Orwells 1984 wird er vom Imperium gegen seine eigenen Untertanen geführt, aber nicht nur, um die Struktur der Gesellschaft intakt zu halten, sondern in unserem Fall auch, um die Gesellschaft in eine neo-totalitäre global-kapitalistische Dystopie zu verwandeln. Bist du nicht vertraut mit dem Krieg gegen was auch immer? Nun ja, okay, du erinnerst dich an den Krieg gegen den Terror. Du erinnerst dich daran, als die „Freiheit und Demokratie“ von „den Terroristen“ angegriffen wurden und wir keine andere Wahl hatten, als uns unserer demokratischen Rechte und Prinzipien zu entledigen, einen nationalen „Notstand“ auszurufen, die verfassungsmäßigen Rechte der Menschen auszusetzen, einen Angriffskrieg gegen ein Land im Nahen Osten anzuzetteln, das für uns keinerlei Bedrohung darstellte, und unsere Straßen, Bahnhöfe, Flughäfen und alle anderen Orte mit schwer bewaffneten Soldaten zu füllen, denn sonst hätten „die Terroristen gewonnen“. Du erinnerst dich, als wir ein Offshore-Gulag bauten, um verdächtige Terroristen auf unbestimmte Zeit wegzusperren, die wir zuvor zu CIA-Geheimgefängnissen verschleppt hatten, wo wir sie gefoltert und gedemütigt haben, richtig? Natürlich erinnerst du dich. Wer könnte das vergessen? *** **DIE FRIEDENSTAUBE FLIEGT AUCH IN IHR POSTFACH!** ***[Hier](https://pareto.space/u/friedenstaube@pareto.space)*** *können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht). Sie wollen der Genossenschaft beitreten oder uns unterstützen? Mehr Infos* ***[hier](https://pareto.space/a/naddr1qqsxydty8qek2wpsvyck2wphxajrvefjvesngcfhxenrgdty89nrzvgzyzrxuqfepp2e79w9aluaz2252vyz7qdpld05pgjmeurhdgm2jv6w2qcyqqq823cpp4mhxue69uhkummn9ekx7mqprpmhxue69uhkummnw3ezuurpwfjhgmewwdcxzcm9qythwumn8ghj7mn0wd68ytnsv9ex2ar09e6x7amwqyf8wumn8ghj7mmxve3ksctfdch8qatzqythwumn8ghj7urpwfjhgmewdehhxarjxyhxxmmdszcvqk)*** *oder am Ende des Textes.* *** Erinnerst du dich, als die National Security Agency keine andere Wahl hatte, als ein geheimes „Terroristen-Überwachungsprogramm“ einzurichten, um Amerikaner auszuspionieren, oder sonst „hätten die Terroristen gewonnen“? Oder wie wäre es mit den „Anti-Terror“-Unterleibsuntersuchungen der TSA, der Behörde für Transportsicherheit, die nach über zwanzig Jahren immer noch in Kraft sind? Und was ist mit dem Krieg gegen den Populismus? An den erinnerst du dich vielleicht nicht so gut. Ich erinnere mich, denn ich habe zwei Bücher dazu veröffentlicht. Er begann im Sommer 2016, als das Imperium erkannte, dass „rechte Populisten“ die „Freiheit und Demokratie“ in Europa bedrohten und Trump in den USA auf dem Vormarsch war. Also wurde ein weiterer „Notstand“ ausgerufen – diesmal von der Gemeinschaft der Geheimdienste, den Medien, der akademischen Welt und der Kulturindustrie. Ja, genau, es war wieder einmal an der Zeit, unsere demokratischen Prinzipien hintanzustellen, „Hassrede“ in sozialen Medien zu zensieren, die Massen mit lächerlicher offizieller Propaganda über „Russiagate,“ „Hitlergate“ und so weiter zu bombardieren – sonst hätten „die Rechtspopulisten gewonnen.“ Der Krieg gegen den Populismus gipfelte in der Einführung des Neuen Normalen Reichs.  Im Frühjahr 2020 rief das Imperium einen globalen „gesundheitlichen Ausnahmezustand“ aus, als Reaktion auf ein Virus mit einer Überlebensrate von etwa 99,8 Prozent. Das Imperium hatte keine andere Wahl, als ganze Gesellschaften abzuriegeln, jeden dazu zu zwingen, in der Öffentlichkeit medizinisch aussehende Masken zu tragen, die Öffentlichkeit mit Propaganda und Lügen zu bombardieren, die Menschen dazu zu nötigen, sich einer Reihe experimenteller mRNA-„Impfungen“ zu unterziehen, Proteste gegen ihre Dekrete zu verbieten und systematisch diejenigen zu zensieren und zu verfolgen, die es wagten, ihre erfundenen „Fakten“ in Frage zu stellen oder ihr totalitäres Programm zu kritisieren. Das Imperium hatte keine andere Wahl, als das alles zu tun, denn sonst hätten „die Covid-Leugner, die Impfgegner, die Verschwörungstheoretiker und all die anderen Extremisten gewonnen.“ Ich bin mir ziemlich sicher, dass du dich an all das erinnerst. Und jetzt … nun, hier sind wir. Ja, du hast es erraten – es ist wieder einmal an der Zeit, kräftig auf die US-Verfassung und die Meinungsfreiheit zu scheißen, Menschen in irgendein salvadorianisches Höllenloch abzuschieben, das wir angemietet haben, weil ein Polizist ihre Tattoos nicht mochte, Universitätsstudenten wegen ihrer Anti-Israel-Proteste festzunehmen und zu verschleppen und natürlich die Massen mit Lügen und offizieller Propaganda zu bombardieren, denn … okay, alle zusammen jetzt: „sonst hätten die antisemitischen Terroristen und venezolanischen Banden gewonnen!“ Fängst du an, ein Muster zu erkennen? Ja? Willkommen beim Krieg gegen-was-auch-immer! Wenn du die Zusammenhänge noch nicht ganz siehst, okay, lass es mich noch einmal ganz simpel erklären. Das globale ideologische System, in dem wir alle leben, wird totalitär. (Dieses System ist der globale Kapitalismus, aber nenne es, wie du willst. Es ist mir scheißegal.) Es reißt die Simulation der Demokratie nieder, die es nicht mehr aufrechterhalten muss. Der Kalte Krieg ist vorbei. Der Kommunismus ist tot. Der globale Kapitalismus hat keine externen Feinde mehr. Also muss er die Massen nicht mehr mit demokratischen Rechten und Freiheiten besänftigen. Deshalb entzieht er uns diese Rechte nach und nach und konditioniert uns darauf, ihren Verlust hinzunehmen. Er tut dies, indem er eine Reihe von „Notständen“ inszeniert, jeder mit einer anderen „Bedrohung“ für die „Demokratie,“ die „Freiheit,“ „Amerika“ oder „den Planeten“ – oder was auch immer. Jeder mit seinen eigenen „Monstern,“ die eine so große Gefahr für die „Freiheit“ oder was auch immer darstellen, dass wir unsere verfassungsmäßigen Rechte aufgeben und die demokratischen Werte ad absurdum führen müssen, denn: sonst „würden die Monster gewinnen.“  Es tut dies, indem es sein Antlitz von „links“ nach „rechts,“ dann zurück nach „links“, und dann zurück nach „rechts,“ dann nach „links“ und so weiter neigt, weil es unsere Kooperation dafür benötigt. Nicht die Kooperation von uns allen auf einmal. Nur eine kooperative demografische Gruppe auf einmal. Es ist dabei erfolgreich – also das System – indem es unsere Angst und unseren Hass instrumentalisiert. Dem System ist es völlig egal, ob wir uns als „links“ oder „rechts“ identifizieren, aber es braucht uns gespalten in „links“ und „rechts,“ damit es unsere Angst und unseren Hass aufeinander nähren kann … eine Regierung, ein „Notfall,“ ein „Krieg“ nach dem anderen. Da hast du es. Das ist der Krieg gegen was auch immer. Noch simpler kann ich es nicht erklären. Oh, und noch eine letzte Sache … wenn du einer meiner ehemaligen Fans bist, wie Rob, die über meine „Einsichten“ oder Loyalitäten oder was auch immer verwirrt sind … nun, der Text, den du gerade gelesen hast, sollte das für dich klären. Ich stehe auf keiner Seite. Überhaupt keiner. Aber ich habe ein paar grundlegende demokratische Prinzipien. Und die richten sich nicht danach, was gerade populär ist oder wer im Weißen Haus sitzt. Die Sache ist die: Ich muss mich morgens im Spiegel anschauen können ohne dort einen Heuchler oder … du weißt schon, einen Feigling zu sehen. (Aus dem Amerikanischen übersetzt von **[René Boyke](https://covid-justiz.de/)**). *** *CJ Hopkins ist ein US-amerikanischer [Dramatiker](https://deutsch.wikibrief.org/wiki/Playwright "Dramatiker"), [Romanautor](https://deutsch.wikibrief.org/wiki/Novelist "Romanschriftsteller") und [politischer Satiriker](https://deutsch.wikibrief.org/wiki/Political_satire "Politische Satire"). Zu seinen Werken zählen die Stücke Horse Country, Screwmachine/Eyecandy und [The Extremists](https://deutsch.wikibrief.org/wiki/The_Extremists_%28play%29 "Die Extremisten (Spiel)"). Er hat sich als profilierter Kritiker des Corona-Regimes profiliert und veröffentlicht regelmäßig auf seinem* ***[Substack-Blog.](https://cjhopkins.substack.com/)*** Sein aktuelles Buch: <https://x.com/CJHopkins_Z23/status/1907795633689264530> Hier in einem aktuellen Gespräch:  <https://www.youtube.com/watch?v=wF-G32P0leI> *** **LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!** ***[Hier](https://pareto.space/u/friedenstaube@pareto.space)*** *können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt. (Vorerst alle, da wir den Mailversand testen, später ca. drei Mails pro Woche.)* Schon jetzt können Sie uns unterstützen: * Für **50 CHF/EURO** bekommen Sie ein Jahresabo der Friedenstaube. * Für **120 CHF/EURO** bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube. * Für **500 CHF/EURO** werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube. * Ab **1000 CHF** werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie). **Für Einzahlungen in CHF (Betreff: Friedenstaube):**  **Für Einzahlungen in Euro:** Milosz Matuschek IBAN DE 53710520500000814137 BYLADEM1TST Sparkasse Traunstein-Trostberg **Betreff: Friedenstaube** Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: <milosz@pareto.space> *** **Sie sind noch nicht auf** [Nostr](https://nostr.com/) **and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil!** Erstellen Sie sich einen Account auf [Start.](https://start.njump.me/) Weitere Onboarding-Leitfäden gibt es im [Pareto-Wiki.](https://wiki.pareto.space/de/home) @ 5ffb8e1b:255b6735
2025-03-29 13:57:02As a fellow Nostrich you might have noticed some of my #arlist posts. It is my effort to curate artists that are active on Nostr and make it easier for other users to find content that they are interested in. By now I have posted six or seven posts mentioning close to fifty artists, the problem so far is that it's only a list of handles and it is up to reader to click on each in order to find out what are the artist behind the names all about. Now I am going to start creating blog posts with a few artists mentioned in each, with short descriptions of their work and an image or to. I would love to have some more automated mode of curation but I still couldn't figure out what is a good way for it. I've looked at Listr, Primal custom feeds and Yakihonne curations but none seem to enable me to make a list of npubs that is then turned into a feed that I could publicly share for others to views. Any advice on how to achieve this is VERY welcome ! And now lets get to the first batch of artists I want to share with you. ### Eugene Gorbachenko ### nostr:npub1082uhnrnxu7v0gesfl78uzj3r89a8ds2gj3dvuvjnw5qlz4a7udqwrqdnd Artist from Ukrain creating amazing realistic watercolor paintings. He is very active on Nostr but is very unnoticed for some stange reason. Make sure to repost the painting that you liked the most to help other Nostr users to discover his great art. ![!(image)[https://m.primal.net/PxJc.png]]() ### Siritravelsketch ### nostr:npub14lqzjhfvdc9psgxzznq8xys8pfq8p4fqsvtr6llyzraq90u9m8fqevhssu a a lovely lady from Thailand making architecture from all around the world spring alive in her ink skethes. Dynamic lines gives it a dreamy magical feel, sometimes supported by soft watercolor strokes takes you to a ferytale layer of reality. ![!(image)[https://m.primal.net/PxJj.png]]() ### BureuGewas ### nostr:npub1k78qzy2s9ap4klshnu9tcmmcnr3msvvaeza94epsgptr7jce6p9sa2ggp4 a a master of the clasic oil painting. From traditional still life to modern day subjects his paintings makes you feel the textures and light of the scene more intense then reality itself. ![!(image)[https://m.primal.net/PxKS.png]]() You can see that I'm no art critic, but I am trying my best. If anyone else is interested to join me in this curration adventure feel free to reach out ! With love, Agi Choote
@ 5ffb8e1b:255b6735
2025-03-29 13:57:02As a fellow Nostrich you might have noticed some of my #arlist posts. It is my effort to curate artists that are active on Nostr and make it easier for other users to find content that they are interested in. By now I have posted six or seven posts mentioning close to fifty artists, the problem so far is that it's only a list of handles and it is up to reader to click on each in order to find out what are the artist behind the names all about. Now I am going to start creating blog posts with a few artists mentioned in each, with short descriptions of their work and an image or to. I would love to have some more automated mode of curation but I still couldn't figure out what is a good way for it. I've looked at Listr, Primal custom feeds and Yakihonne curations but none seem to enable me to make a list of npubs that is then turned into a feed that I could publicly share for others to views. Any advice on how to achieve this is VERY welcome ! And now lets get to the first batch of artists I want to share with you. ### Eugene Gorbachenko ### nostr:npub1082uhnrnxu7v0gesfl78uzj3r89a8ds2gj3dvuvjnw5qlz4a7udqwrqdnd Artist from Ukrain creating amazing realistic watercolor paintings. He is very active on Nostr but is very unnoticed for some stange reason. Make sure to repost the painting that you liked the most to help other Nostr users to discover his great art. ![!(image)[https://m.primal.net/PxJc.png]]() ### Siritravelsketch ### nostr:npub14lqzjhfvdc9psgxzznq8xys8pfq8p4fqsvtr6llyzraq90u9m8fqevhssu a a lovely lady from Thailand making architecture from all around the world spring alive in her ink skethes. Dynamic lines gives it a dreamy magical feel, sometimes supported by soft watercolor strokes takes you to a ferytale layer of reality. ![!(image)[https://m.primal.net/PxJj.png]]() ### BureuGewas ### nostr:npub1k78qzy2s9ap4klshnu9tcmmcnr3msvvaeza94epsgptr7jce6p9sa2ggp4 a a master of the clasic oil painting. From traditional still life to modern day subjects his paintings makes you feel the textures and light of the scene more intense then reality itself. ![!(image)[https://m.primal.net/PxKS.png]]() You can see that I'm no art critic, but I am trying my best. If anyone else is interested to join me in this curration adventure feel free to reach out ! With love, Agi Choote @ a5142938:0ef19da3
2025-04-05 10:18:18Discover the materials accepted or not in the products listed on this site. ### ✅ Natural Materials Materials of plant, animal, or mineral origin, without chemical transformation that alters their molecular structure. **🌱 Main Criteria:** - Biodegradability - Non-toxicity - Naturally occurring and recquiring minimal transformation **🔍 List of Natural Materials:** - Natural rubber - Hemp - Cotton - Leather - Cork - Linen - Wool - Silk - … (Other materials) ⚠️ Although natural, these materials can have negative impacts depending on their production conditions (pesticide pollution, excessive water consumption, chemical treatments, animal exploitation, etc.). These impacts are mentionned in the description of each material. Organic, chemical-free versions of these materials are prioritized for product listings on this site. Conventional versions are only referenced when no more sustainable alternative has yet been found for that product category. --- ### 🚫 Non-Natural Materials Synthetic or heavily modified materials, often derived from petrochemicals. **📌 Main Issues:** - Microplastic emissions - Dependence on fossil fuels - Poor biodegradability **🔍 List of Non-Natural Materials:** - Polyester - Polyamide - Acrylic - Elastane - Viscose - Silicone - … (Other materials) ⚠️ These materials are not accepted on this site. However, they may be present in certain listed products if: - they are used in removable accessories (e.g., elastics, buttons—often not listed in the product’s composition by the brand) that can be detached for recycling or composting, and - no 100% natural alternative has yet been identified for that product category. In such cases, a warning will be displayed on the product page. --- This article is published on [origin-nature.com](https://www.origin-nature.com/post/pnco0inysorhojxvsyil3/) 🌐 [Voir cet article en français](https://www.origine-nature.com/post/ftjhuxe9mvxkhoedyz36i/)
@ a5142938:0ef19da3
2025-04-05 10:18:18Discover the materials accepted or not in the products listed on this site. ### ✅ Natural Materials Materials of plant, animal, or mineral origin, without chemical transformation that alters their molecular structure. **🌱 Main Criteria:** - Biodegradability - Non-toxicity - Naturally occurring and recquiring minimal transformation **🔍 List of Natural Materials:** - Natural rubber - Hemp - Cotton - Leather - Cork - Linen - Wool - Silk - … (Other materials) ⚠️ Although natural, these materials can have negative impacts depending on their production conditions (pesticide pollution, excessive water consumption, chemical treatments, animal exploitation, etc.). These impacts are mentionned in the description of each material. Organic, chemical-free versions of these materials are prioritized for product listings on this site. Conventional versions are only referenced when no more sustainable alternative has yet been found for that product category. --- ### 🚫 Non-Natural Materials Synthetic or heavily modified materials, often derived from petrochemicals. **📌 Main Issues:** - Microplastic emissions - Dependence on fossil fuels - Poor biodegradability **🔍 List of Non-Natural Materials:** - Polyester - Polyamide - Acrylic - Elastane - Viscose - Silicone - … (Other materials) ⚠️ These materials are not accepted on this site. However, they may be present in certain listed products if: - they are used in removable accessories (e.g., elastics, buttons—often not listed in the product’s composition by the brand) that can be detached for recycling or composting, and - no 100% natural alternative has yet been identified for that product category. In such cases, a warning will be displayed on the product page. --- This article is published on [origin-nature.com](https://www.origin-nature.com/post/pnco0inysorhojxvsyil3/) 🌐 [Voir cet article en français](https://www.origine-nature.com/post/ftjhuxe9mvxkhoedyz36i/) @ 592295cf:413a0db9
2025-03-29 10:59:52The journey starts from the links in this article [nostr-quick-start-guide](https://spatianostra.com/nostr-quick-start-guide/) Starting from these links building a simple path should not cover everything, because impossible. Today I saw that Verbiricha in his workshop on his channel used nstart, but then I distracted And I didn't see how he did it. ----- Go to [nstart.me](https://nstart.me/) and read: Each user is identified by a cryptographic keypair Public key, Private key (is a lot of stuff) You can insert a nickname and go, the nickname is not unique there is a email backup things interesting, but a little boring, i try to generate an email doesn't even require a strong password ok. I received the email, great, it shows me the nsec encrypted in clear, Send a copy of the file with a password, which contains the password encrypted key I know and I know it's a tongue dump. ## Multi signer bunker That's stuff, let's see what he says. They live the private key and send it to servers and you can recompose it to login at a site of the protocol nostr. If one of these servers goes offline you have the private key that you downloaded first and then reactivate a bunker. All very complicated. But if one of the servers goes offline, how can I remake the split? Maybe he's still testing. Nobody tells you where these bunkers are. Okay I have a string that is my bunker (buker://), I downloaded it, easy no, now will tell me which client accepts the bunker.. . ## Follow someone before you start? Is a cluster of 5 people Snowden, Micheal Dilger, jb55, Fiatjaf, Dianele. I choice Snowden profile, or you can select multiple profiles, extra wild. ## Now select 5 clients ### *Coracle, Chachi, Olas, Nostur, Jumble* ### The first is *Coracle* Login, ok I try to post a note and signing your note the spin does not end. Maybe the bunker is diffective. ### Let's try *Chachi* Simpler than Coracle, it has a type login that says bunker. see if I can post It worked, cool, I managed to post in a group. ## Olas is an app but also a website, but on the website requires an extension, which I do not have with this account. > If I download an app how do I pass the bunker on the phone, is it still a password, a qrcode, a qrcode + password, something > like that, but many start from the phone so maybe it's easy for them. > I try to download it and see if it allows me to connect with a bunker. > Okay I used private-qrcode and it worked, I couldn't do it directly from Olas because it didn't have permissions and the qrcode was < encrypted, so I went to the same site and had the bunker copied and glued on Olas **Ok then I saw that there was the qrcode image of the bunker for apps** lol moment Ok, I liked it, I can say it's a victory. Looks like none of Snowden's followers are *Olas*'s lover, maybe the smart pack has to predict a photographer or something like that. Okay I managed to post on *Olas*, so it works, Expiration time is broken. ### As for *Nostur*, I don't have an ios device so I'm going to another one. ### Login with *Jumble*, it works is a web app I took almost an hour to do the whole route. But this was just one link there are two more # Extensions nostr NIP-07 ### The true path is [nip-07-browser-extensions | nostr.net](https://nostr.net/#nip-07-browser-extensions) There are 19 links, maybe there are too many? I mention the most famous, or active at the moment 1. **Aka-profiles**: [Aka-profiles](https://github.com/neilck/aka-extension) Alby I don't know if it's a route to recommend 2. **Blockcore** [Blockcore wallet](https://chromewebstore.google.com/detail/blockcore-wallet/peigonhbenoefaeplkpalmafieegnapj) 3. **Nos2x** [Nos2x](https://github.com/fiatjaf/nos2x?tab=readme-ov-file) 4. **Nos2xfox** (fork for firefox) [Nos2xfox](https://diegogurpegui.com/nos2x-fox/) Nostore is (archived, read-only) 5. **Nostrame** [Nostrame](https://github.com/Anderson-Juhasc/nostrame) 6. **Nowser** per IOS [Nowser](https://github.com/haorendashu/nowser) 7. **One key** (was tricky) [One key](https://chromewebstore.google.com/detail/onekey/jnmbobjmhlngoefaiojfljckilhhlhcj) Another half hour to search all sites # Nostrapps Here you can make paths ### Then nstart selects Coracle, Chachi, Olas,Nostur and Jumble Good apps might be Amethyst, 0xchat, Yakihonne, Primal, Damus for IOS maybe: Primal, Olas, Damus, Nostur, Nos-Social, Nostrmo On the site there are some categories, I select some with the respective apps Let's see the categories Go to [Nostrapps](https://nostrapps.com/) and read: ## Microbbloging: Primal ## Streaming: **Zap stream** ## Blogging: **Yakihonne** ## Group chat: **Chachi** ## Community: **Flotilla** ## Tools: **Form** * ## Discovery: **Zapstore** (even if it is not in this catrgory) ## Direct Message: **0xchat**
@ 592295cf:413a0db9
2025-03-29 10:59:52The journey starts from the links in this article [nostr-quick-start-guide](https://spatianostra.com/nostr-quick-start-guide/) Starting from these links building a simple path should not cover everything, because impossible. Today I saw that Verbiricha in his workshop on his channel used nstart, but then I distracted And I didn't see how he did it. ----- Go to [nstart.me](https://nstart.me/) and read: Each user is identified by a cryptographic keypair Public key, Private key (is a lot of stuff) You can insert a nickname and go, the nickname is not unique there is a email backup things interesting, but a little boring, i try to generate an email doesn't even require a strong password ok. I received the email, great, it shows me the nsec encrypted in clear, Send a copy of the file with a password, which contains the password encrypted key I know and I know it's a tongue dump. ## Multi signer bunker That's stuff, let's see what he says. They live the private key and send it to servers and you can recompose it to login at a site of the protocol nostr. If one of these servers goes offline you have the private key that you downloaded first and then reactivate a bunker. All very complicated. But if one of the servers goes offline, how can I remake the split? Maybe he's still testing. Nobody tells you where these bunkers are. Okay I have a string that is my bunker (buker://), I downloaded it, easy no, now will tell me which client accepts the bunker.. . ## Follow someone before you start? Is a cluster of 5 people Snowden, Micheal Dilger, jb55, Fiatjaf, Dianele. I choice Snowden profile, or you can select multiple profiles, extra wild. ## Now select 5 clients ### *Coracle, Chachi, Olas, Nostur, Jumble* ### The first is *Coracle* Login, ok I try to post a note and signing your note the spin does not end. Maybe the bunker is diffective. ### Let's try *Chachi* Simpler than Coracle, it has a type login that says bunker. see if I can post It worked, cool, I managed to post in a group. ## Olas is an app but also a website, but on the website requires an extension, which I do not have with this account. > If I download an app how do I pass the bunker on the phone, is it still a password, a qrcode, a qrcode + password, something > like that, but many start from the phone so maybe it's easy for them. > I try to download it and see if it allows me to connect with a bunker. > Okay I used private-qrcode and it worked, I couldn't do it directly from Olas because it didn't have permissions and the qrcode was < encrypted, so I went to the same site and had the bunker copied and glued on Olas **Ok then I saw that there was the qrcode image of the bunker for apps** lol moment Ok, I liked it, I can say it's a victory. Looks like none of Snowden's followers are *Olas*'s lover, maybe the smart pack has to predict a photographer or something like that. Okay I managed to post on *Olas*, so it works, Expiration time is broken. ### As for *Nostur*, I don't have an ios device so I'm going to another one. ### Login with *Jumble*, it works is a web app I took almost an hour to do the whole route. But this was just one link there are two more # Extensions nostr NIP-07 ### The true path is [nip-07-browser-extensions | nostr.net](https://nostr.net/#nip-07-browser-extensions) There are 19 links, maybe there are too many? I mention the most famous, or active at the moment 1. **Aka-profiles**: [Aka-profiles](https://github.com/neilck/aka-extension) Alby I don't know if it's a route to recommend 2. **Blockcore** [Blockcore wallet](https://chromewebstore.google.com/detail/blockcore-wallet/peigonhbenoefaeplkpalmafieegnapj) 3. **Nos2x** [Nos2x](https://github.com/fiatjaf/nos2x?tab=readme-ov-file) 4. **Nos2xfox** (fork for firefox) [Nos2xfox](https://diegogurpegui.com/nos2x-fox/) Nostore is (archived, read-only) 5. **Nostrame** [Nostrame](https://github.com/Anderson-Juhasc/nostrame) 6. **Nowser** per IOS [Nowser](https://github.com/haorendashu/nowser) 7. **One key** (was tricky) [One key](https://chromewebstore.google.com/detail/onekey/jnmbobjmhlngoefaiojfljckilhhlhcj) Another half hour to search all sites # Nostrapps Here you can make paths ### Then nstart selects Coracle, Chachi, Olas,Nostur and Jumble Good apps might be Amethyst, 0xchat, Yakihonne, Primal, Damus for IOS maybe: Primal, Olas, Damus, Nostur, Nos-Social, Nostrmo On the site there are some categories, I select some with the respective apps Let's see the categories Go to [Nostrapps](https://nostrapps.com/) and read: ## Microbbloging: Primal ## Streaming: **Zap stream** ## Blogging: **Yakihonne** ## Group chat: **Chachi** ## Community: **Flotilla** ## Tools: **Form** * ## Discovery: **Zapstore** (even if it is not in this catrgory) ## Direct Message: **0xchat** @ 57d1a264:69f1fee1
2025-03-29 09:31:13> "THE NATURE OF BITCOIN IS SUCH THAT ONCE VERSION 0.1 WAS RELEASED, THE CORE DESIGN WAS SET IN STONE FOR THE REST OF ITS LIFETIME." <sub>- SATOSHI NAKAMOTO</sub>    "Reborn" is inspired by my Bitcoin journey and the many other people whose lives have been changed by Bitcoin. I’ve carved the hand in the “Gyan Mudra” or the “Mudra of Wisdom or Knowledge,” with an Opendime grasped between thumb and index finger alluding to the pursuit of Bitcoin knowledge. The hand emerges from rough, choppy water, and I've set the hand against an archway, through which, the copper leaf hints at the bright orange future made possible by Bitcoin. Materials: Carrara Marble, Copper leaf, Opendime Dimensions: 6" x 9" x 13" Price: $30,000 or BTC equivalent Enquire: https://www.vonbitcoin.com/available-works X: https://x.com/BVBTC/status/1894463357316419960/photo/1 originally posted at https://stacker.news/items/928510
@ 57d1a264:69f1fee1
2025-03-29 09:31:13> "THE NATURE OF BITCOIN IS SUCH THAT ONCE VERSION 0.1 WAS RELEASED, THE CORE DESIGN WAS SET IN STONE FOR THE REST OF ITS LIFETIME." <sub>- SATOSHI NAKAMOTO</sub>    "Reborn" is inspired by my Bitcoin journey and the many other people whose lives have been changed by Bitcoin. I’ve carved the hand in the “Gyan Mudra” or the “Mudra of Wisdom or Knowledge,” with an Opendime grasped between thumb and index finger alluding to the pursuit of Bitcoin knowledge. The hand emerges from rough, choppy water, and I've set the hand against an archway, through which, the copper leaf hints at the bright orange future made possible by Bitcoin. Materials: Carrara Marble, Copper leaf, Opendime Dimensions: 6" x 9" x 13" Price: $30,000 or BTC equivalent Enquire: https://www.vonbitcoin.com/available-works X: https://x.com/BVBTC/status/1894463357316419960/photo/1 originally posted at https://stacker.news/items/928510 @ 2183e947:f497b975
2025-03-29 02:41:34Today I was invited to participate in the private beta of a new social media protocol called Pubky, designed by a bitcoin company called Synonym with the goal of being better than existing social media platforms. As a heavy nostr user, I thought I'd write up a comparison. I can't tell you how to create your own accounts because it was made very clear that only *some* of the software is currently open source, and how this will all work is still a bit up in the air. The code that *is* open source can be found here: https://github.com/pubky -- and the most important repo there seems to be this one: https://github.com/pubky/pubky-core You can also learn more about Pubky here: https://pubky.org/ That said, I used my invite code to create a pubky account and it seemed very similar to onboarding to nostr. I generated a private key, backed up 12 words, and the onboarding website gave me a public key. Then I logged into a web-based client and it looked a lot like twitter. I saw a feed for posts by other users and saw options to reply to posts and give reactions, which, I saw, included hearts, thumbs up, and other emojis. Then I investigated a bit deeper to see how much it was like nostr. I opened up my developer console and navigated to my networking tab, where, if this was nostr, I would expect to see queries to relays for posts. Here, though, I saw one query that seemed to be repeated on a loop, which went to a single server and provided it with my pubkey. That single query (well, a series of identical queries to the same server) seemed to return all posts that showed up on my feed. So I infer that the server "knows" what posts to show me (perhaps it has some sort of algorithm, though the marketing material says it does not use algorithms) and the query was on a loop so that if any new posts came in that the server thinks I might want to see, it can add them to my feed. Then I checked what happens when I create a post. I did so and looked at what happened in my networking tab. If this was nostr, I would expect to see multiple copies of a signed messaged get sent to a bunch of relays. Here, though, I saw one message get sent to the same server that was populating my feed, and that message was not signed, it was a plaintext copy of my message. I happened to be in a group chat with John Carvalho at the time, who is associated with pubky. I asked him what was going on, and he said that pubky is based around three types of servers: homeservers, DHT servers, and indexer servers. The homeserver is where you create posts and where you query for posts to show on your feed. DHT servers are used for censorship resistance: each user creates an entry on a DHT server saying what homeserver they use, and these entries are signed by their key. As for indexers, I think those are supposed to speed up the use of the DHT servers. From what I could tell, indexers query DHT servers to find out what homeservers people use. When you query a homeserver for posts, it is supposed to reach out to indexer servers to find out the homeservers of people whose posts the homeserver decided to show you, and then query those homeservers for those posts. I believe they decided not to look up what homeservers people use directly on DHT servers directly because DHT servers are kind of slow, due to having to store and search through all sorts of non-social-media content, whereas indexers only store a simple db that maps each user's pubkey to their homeserver, so they are faster. Based on all of this info, it seems like, to populate your feed, this is the series of steps: - you tell your homeserver your pubkey - it uses some sort of algorithm to decide whose posts to show you - then looks up the homeservers used by those people on an indexer server - then it fetches posts from their homeservers - then your client displays them to you To create a post, this is the series of steps: - you tell your homeserver what you want to say to the world - it stores that message in plaintext and merely asserts that it came from you (it's not signed) - other people can find out what you said by querying for your posts on your homeserver Since posts on homeservers are not signed, I asked John what prevents a homeserver from just making up stuff and claiming I said it. He said nothing stops them from doing that, and if you are using a homeserver that starts acting up in that manner, what you should do is start using a new homeserver and update your DHT record to point at your new homeserver instead of the old one. Then, indexers should update their db to show where your new homeserver is, and the homeservers of people who "follow" you should stop pulling content from your old homeserver and start pulling it from your new one. If their homeserver is misbehaving too, I'm not sure what would happen. Maybe it could refuse to show them the content you've posted on your new homeserver, keeping making up fake content on your behalf that you've never posted, and maybe the people you follow would never learn you're being impersonated or have moved to a new homeserver. John also clarified that there is not currently any tooling for migrating user content from one homeserver to another. If pubky gets popular and a big homeserver starts misbehaving, users will probably need such a tool. But these are early days, so there aren't that many homeservers, and the ones that exist seem to be pretty trusted. Anyway, those are my initial thoughts on Pubky. Learn more here: https://pubky.org/
@ 2183e947:f497b975
2025-03-29 02:41:34Today I was invited to participate in the private beta of a new social media protocol called Pubky, designed by a bitcoin company called Synonym with the goal of being better than existing social media platforms. As a heavy nostr user, I thought I'd write up a comparison. I can't tell you how to create your own accounts because it was made very clear that only *some* of the software is currently open source, and how this will all work is still a bit up in the air. The code that *is* open source can be found here: https://github.com/pubky -- and the most important repo there seems to be this one: https://github.com/pubky/pubky-core You can also learn more about Pubky here: https://pubky.org/ That said, I used my invite code to create a pubky account and it seemed very similar to onboarding to nostr. I generated a private key, backed up 12 words, and the onboarding website gave me a public key. Then I logged into a web-based client and it looked a lot like twitter. I saw a feed for posts by other users and saw options to reply to posts and give reactions, which, I saw, included hearts, thumbs up, and other emojis. Then I investigated a bit deeper to see how much it was like nostr. I opened up my developer console and navigated to my networking tab, where, if this was nostr, I would expect to see queries to relays for posts. Here, though, I saw one query that seemed to be repeated on a loop, which went to a single server and provided it with my pubkey. That single query (well, a series of identical queries to the same server) seemed to return all posts that showed up on my feed. So I infer that the server "knows" what posts to show me (perhaps it has some sort of algorithm, though the marketing material says it does not use algorithms) and the query was on a loop so that if any new posts came in that the server thinks I might want to see, it can add them to my feed. Then I checked what happens when I create a post. I did so and looked at what happened in my networking tab. If this was nostr, I would expect to see multiple copies of a signed messaged get sent to a bunch of relays. Here, though, I saw one message get sent to the same server that was populating my feed, and that message was not signed, it was a plaintext copy of my message. I happened to be in a group chat with John Carvalho at the time, who is associated with pubky. I asked him what was going on, and he said that pubky is based around three types of servers: homeservers, DHT servers, and indexer servers. The homeserver is where you create posts and where you query for posts to show on your feed. DHT servers are used for censorship resistance: each user creates an entry on a DHT server saying what homeserver they use, and these entries are signed by their key. As for indexers, I think those are supposed to speed up the use of the DHT servers. From what I could tell, indexers query DHT servers to find out what homeservers people use. When you query a homeserver for posts, it is supposed to reach out to indexer servers to find out the homeservers of people whose posts the homeserver decided to show you, and then query those homeservers for those posts. I believe they decided not to look up what homeservers people use directly on DHT servers directly because DHT servers are kind of slow, due to having to store and search through all sorts of non-social-media content, whereas indexers only store a simple db that maps each user's pubkey to their homeserver, so they are faster. Based on all of this info, it seems like, to populate your feed, this is the series of steps: - you tell your homeserver your pubkey - it uses some sort of algorithm to decide whose posts to show you - then looks up the homeservers used by those people on an indexer server - then it fetches posts from their homeservers - then your client displays them to you To create a post, this is the series of steps: - you tell your homeserver what you want to say to the world - it stores that message in plaintext and merely asserts that it came from you (it's not signed) - other people can find out what you said by querying for your posts on your homeserver Since posts on homeservers are not signed, I asked John what prevents a homeserver from just making up stuff and claiming I said it. He said nothing stops them from doing that, and if you are using a homeserver that starts acting up in that manner, what you should do is start using a new homeserver and update your DHT record to point at your new homeserver instead of the old one. Then, indexers should update their db to show where your new homeserver is, and the homeservers of people who "follow" you should stop pulling content from your old homeserver and start pulling it from your new one. If their homeserver is misbehaving too, I'm not sure what would happen. Maybe it could refuse to show them the content you've posted on your new homeserver, keeping making up fake content on your behalf that you've never posted, and maybe the people you follow would never learn you're being impersonated or have moved to a new homeserver. John also clarified that there is not currently any tooling for migrating user content from one homeserver to another. If pubky gets popular and a big homeserver starts misbehaving, users will probably need such a tool. But these are early days, so there aren't that many homeservers, and the ones that exist seem to be pretty trusted. Anyway, those are my initial thoughts on Pubky. Learn more here: https://pubky.org/ @ 57d1a264:69f1fee1
2025-03-28 10:32:15Bitcoin.design community is organizing another Designathon, from May 4-18. Let's get creative with bitcoin together. More to come very soon.  The first edition was a bursting success! the website still there https://events.bitcoin.design, and here their previous [announcement](https://bitcoindesign.substack.com/p/the-bitcoin-designathon-2022). Look forward for this to happen! Spread the voice: N: [https://njump.me/nevent1qqsv9w8p93tadlnyx0rkhexj5l48l...](https://njump.me/nevent1qqsv9w8p93tadlnyx0rkhexj5l48lmw9jc7nhhauyq5w3cm4nfsm3mstqtk6m) X: https://x.com/bitcoin_design/status/1905547407405768927 originally posted at https://stacker.news/items/927650
@ 57d1a264:69f1fee1
2025-03-28 10:32:15Bitcoin.design community is organizing another Designathon, from May 4-18. Let's get creative with bitcoin together. More to come very soon.  The first edition was a bursting success! the website still there https://events.bitcoin.design, and here their previous [announcement](https://bitcoindesign.substack.com/p/the-bitcoin-designathon-2022). Look forward for this to happen! Spread the voice: N: [https://njump.me/nevent1qqsv9w8p93tadlnyx0rkhexj5l48l...](https://njump.me/nevent1qqsv9w8p93tadlnyx0rkhexj5l48lmw9jc7nhhauyq5w3cm4nfsm3mstqtk6m) X: https://x.com/bitcoin_design/status/1905547407405768927 originally posted at https://stacker.news/items/927650 @ 57d1a264:69f1fee1
2025-03-27 10:42:05What we have been missing in [SN Press kit](https://stacker.news/items/872925/r/Design_r)? Most important, who the press kit is for? It's for us? It's for them? Them, who? The first few editions of the press kit, I agree are mostly made by us, for us. A way to try to homogenize how we _speek_ out SN into the wild web. A way to have SN voice sync, loud and clear, to send out our message. In this case, I squeezed my mouse, creating a template for us [^1], stackers, to share when talking sales with possible businesses and merchants willing to invest some sats and engage with SN community. Here's the message and the sales pitch, v0.1: ## Reach Bitcoin’s Most Engaged Community – Zero Noise, Pure Signal.              - - - Contributions to improve would be much appreciated. You can also help by simply commenting on each slide or leaving your feedback below, especially if you are a sale person or someone that has seen similar documents before. This is the first interaction. Already noticed some issues, for example with the emojis and the fonts, especially when exporting, probably related to a penpot issue. The slides maybe render differently depending on the browser you're using. - [▶️ Play](https://design.penpot.app/#/view?file-id=cec80257-5021-8137-8005-ef90a160b2c9&page-id=cec80257-5021-8137-8005-ef90a160b2ca§ion=interactions&index=0&interactions-mode=hide&zoom=fit) the file in your browser - ⬇️ Save the [PDF file](https://mega.nz/file/TsBgkRoI#20HEb_zscozgJYlRGha0XiZvcXCJfLQONx2fc65WHKY) @k00b it will be nice to have some real data, how we can get some basic audience insights? Even some inputs from Plausible, if still active, will be much useful. [^1]: Territory founders. FYI: @Aardvark, @AGORA, @anna, @antic, @AtlantisPleb, @av, @Bell_curve, @benwehrman, @bitcoinplebdev, @Bitter, @BlokchainB, @ch0k1, @davidw, @ek, @elvismercury, @frostdragon, @grayruby, @HODLR, @inverselarp, @Jon_Hodl, @MaxAWebster, @mega_dreamer, @mrtali, @niftynei, @nout, @OneOneSeven, @PlebLab, @Public_N_M_E, @RDClark, @realBitcoinDog, @roytheholographicuniverse, @siggy47, @softsimon, @south_korea_ln, @theschoolofbitcoin, @TNStacker. @UCantDoThatDotNet, @Undisciplined originally posted at https://stacker.news/items/926557
@ 57d1a264:69f1fee1
2025-03-27 10:42:05What we have been missing in [SN Press kit](https://stacker.news/items/872925/r/Design_r)? Most important, who the press kit is for? It's for us? It's for them? Them, who? The first few editions of the press kit, I agree are mostly made by us, for us. A way to try to homogenize how we _speek_ out SN into the wild web. A way to have SN voice sync, loud and clear, to send out our message. In this case, I squeezed my mouse, creating a template for us [^1], stackers, to share when talking sales with possible businesses and merchants willing to invest some sats and engage with SN community. Here's the message and the sales pitch, v0.1: ## Reach Bitcoin’s Most Engaged Community – Zero Noise, Pure Signal.              - - - Contributions to improve would be much appreciated. You can also help by simply commenting on each slide or leaving your feedback below, especially if you are a sale person or someone that has seen similar documents before. This is the first interaction. Already noticed some issues, for example with the emojis and the fonts, especially when exporting, probably related to a penpot issue. The slides maybe render differently depending on the browser you're using. - [▶️ Play](https://design.penpot.app/#/view?file-id=cec80257-5021-8137-8005-ef90a160b2c9&page-id=cec80257-5021-8137-8005-ef90a160b2ca§ion=interactions&index=0&interactions-mode=hide&zoom=fit) the file in your browser - ⬇️ Save the [PDF file](https://mega.nz/file/TsBgkRoI#20HEb_zscozgJYlRGha0XiZvcXCJfLQONx2fc65WHKY) @k00b it will be nice to have some real data, how we can get some basic audience insights? Even some inputs from Plausible, if still active, will be much useful. [^1]: Territory founders. FYI: @Aardvark, @AGORA, @anna, @antic, @AtlantisPleb, @av, @Bell_curve, @benwehrman, @bitcoinplebdev, @Bitter, @BlokchainB, @ch0k1, @davidw, @ek, @elvismercury, @frostdragon, @grayruby, @HODLR, @inverselarp, @Jon_Hodl, @MaxAWebster, @mega_dreamer, @mrtali, @niftynei, @nout, @OneOneSeven, @PlebLab, @Public_N_M_E, @RDClark, @realBitcoinDog, @roytheholographicuniverse, @siggy47, @softsimon, @south_korea_ln, @theschoolofbitcoin, @TNStacker. @UCantDoThatDotNet, @Undisciplined originally posted at https://stacker.news/items/926557 @ 57d1a264:69f1fee1
2025-03-27 08:27:44> The tech industry and its press have treated the rise of billion-scale social networks and ubiquitous smartphone apps as an unadulterated win for regular people, a triumph of usability and empowerment. They seldom talk about what we’ve lost along the way in this transition, and I find that younger folks may not even know how the web used to be. `— Anil Dash, The Web We Lost, 13 Dec 2012` https://www.youtube.com/watch?v=9KKMnoTTHJk&t=156s So here’s a few glimpses of a web that’s mostly faded away: https://www.anildash.com/2012/12/13/the_web_we_lost/ The first step to disabusing them of this notion is for the people creating the next generation of social applications to learn a little bit of history, to know your shit, whether that’s about [Twitter’s business model](http://web.archive.org/web/20180120013123/http://anildash.com/2010/04/ten-years-of-twitter-ads.html) or [Google’s social features](http://web.archive.org/web/20170518203228/http://anildash.com/2012/04/why-you-cant-trust-tech-press-to-teach-you-about-the-tech-industry.html) or anything else. We have to know what’s been tried and failed, what good ideas were simply ahead of their time, and what opportunities have been lost in the current generation of dominant social networks. originally posted at https://stacker.news/items/926499
@ 57d1a264:69f1fee1
2025-03-27 08:27:44> The tech industry and its press have treated the rise of billion-scale social networks and ubiquitous smartphone apps as an unadulterated win for regular people, a triumph of usability and empowerment. They seldom talk about what we’ve lost along the way in this transition, and I find that younger folks may not even know how the web used to be. `— Anil Dash, The Web We Lost, 13 Dec 2012` https://www.youtube.com/watch?v=9KKMnoTTHJk&t=156s So here’s a few glimpses of a web that’s mostly faded away: https://www.anildash.com/2012/12/13/the_web_we_lost/ The first step to disabusing them of this notion is for the people creating the next generation of social applications to learn a little bit of history, to know your shit, whether that’s about [Twitter’s business model](http://web.archive.org/web/20180120013123/http://anildash.com/2010/04/ten-years-of-twitter-ads.html) or [Google’s social features](http://web.archive.org/web/20170518203228/http://anildash.com/2012/04/why-you-cant-trust-tech-press-to-teach-you-about-the-tech-industry.html) or anything else. We have to know what’s been tried and failed, what good ideas were simply ahead of their time, and what opportunities have been lost in the current generation of dominant social networks. originally posted at https://stacker.news/items/926499 @ 57d1a264:69f1fee1
2025-03-27 08:11:33Explore and reimagine programming interfaces beyond text (visual, tactile, spatial). > _"The most dangerous thought you can have as a creative person is to think you know what you're doing."_ `— Richard Hamming` [^1] https://www.youtube.com/watch?v=8pTEmbeENF4 For his recent DBX Conference talk, Victor took attendees back to the year 1973, donning the uniform of an IBM systems engineer of the times, delivering his presentation on an overhead projector. The '60s and early '70s were a fertile time for CS ideas, reminds Victor, but even more importantly, it was a time of unfettered thinking, unconstrained by programming dogma, authority, and tradition.  _'The most dangerous thought that you can have as a creative person is to think that you know what you're doing,'_ explains Victor. 'Because once you think you know what you're doing you stop looking around for other ways of doing things and you stop being able to see other ways of doing things. You become blind.' He concludes, 'I think you have to say: _"We don't know what programming is. We don't know what computing is. We don't even know what a computer is."_ And once you truly understand that, and once you truly believe that, then you're free, and you can think anything.' More details at https://worrydream.com/dbx/ [^1]: Richard Hamming -- [The Art of Doing Science and Engineering, p5](http://worrydream.com/refs/Hamming_1997_-_The_Art_of_Doing_Science_and_Engineering.pdf) (pdf ebook) originally posted at https://stacker.news/items/926493
@ 57d1a264:69f1fee1
2025-03-27 08:11:33Explore and reimagine programming interfaces beyond text (visual, tactile, spatial). > _"The most dangerous thought you can have as a creative person is to think you know what you're doing."_ `— Richard Hamming` [^1] https://www.youtube.com/watch?v=8pTEmbeENF4 For his recent DBX Conference talk, Victor took attendees back to the year 1973, donning the uniform of an IBM systems engineer of the times, delivering his presentation on an overhead projector. The '60s and early '70s were a fertile time for CS ideas, reminds Victor, but even more importantly, it was a time of unfettered thinking, unconstrained by programming dogma, authority, and tradition.  _'The most dangerous thought that you can have as a creative person is to think that you know what you're doing,'_ explains Victor. 'Because once you think you know what you're doing you stop looking around for other ways of doing things and you stop being able to see other ways of doing things. You become blind.' He concludes, 'I think you have to say: _"We don't know what programming is. We don't know what computing is. We don't even know what a computer is."_ And once you truly understand that, and once you truly believe that, then you're free, and you can think anything.' More details at https://worrydream.com/dbx/ [^1]: Richard Hamming -- [The Art of Doing Science and Engineering, p5](http://worrydream.com/refs/Hamming_1997_-_The_Art_of_Doing_Science_and_Engineering.pdf) (pdf ebook) originally posted at https://stacker.news/items/926493 @ 3ffac3a6:2d656657
2025-04-05 04:55:12# O Impacto do Namoro com Pelé na Carreira de Xuxa Meneghel ## Disclaimer: Esse texto foi totalmente escrito pelo ChatGPT, eu apenas pedi que ele fizesse uma pesquisa sobre o tema. **Introdução:** O relacionamento entre Xuxa Meneghel e Pelé, que durou cerca de seis anos (início dos anos 1980 até 1986), foi um dos mais comentados da década de 1980 ([Xuxa e Pelé: um romance que se tornou inesquecível... | VEJA](https://veja.abril.com.br/coluna/veja-gente/xuxa-e-pele-um-romance-que-se-tornou-inesquecivel-para-os-dois/#:~:text=Um%20dos%20romances%20mais%20comentados,manchetes%20e%20revistas%20de%20fofoca)). Xuxa tinha apenas 17 anos quando começou a namorar o já consagrado “Rei do Futebol”, então com 40 anos ([A história da foto de revista que gerou o namoro de Pelé e Xuxa](https://www.terra.com.br/diversao/gente/a-historia-da-foto-de-revista-que-gerou-o-namoro-de-pele-e-xuxa,c5106b23301f6f0e7c03f38cdf9eb1a06kopa9ho.html#:~:text=Xuxa%20tinha%2017%20anos,a%20primeira%20mulher%2C%20Rosemeri%20Cholbi)) ([Xuxa e Pelé: um romance que se tornou inesquecível... | VEJA](https://veja.abril.com.br/coluna/veja-gente/xuxa-e-pele-um-romance-que-se-tornou-inesquecivel-para-os-dois/#:~:text=O%20jogador%20de%20futebol%20e,um%20relacionamento%20por%20seis%20anos)). Esse romance altamente midiático não só atiçou a curiosidade do público, como também alavancou a carreira de Xuxa de forma significativa. A seguir, detalhamos como o namoro aumentou a visibilidade da apresentadora, quais oportunidades profissionais podem ter tido influência direta de Pelé, o papel da revista *Manchete* e de outras mídias na promoção de sua imagem, se o relacionamento contribuiu para Xuxa conquistar espaços na TV (como o programa **Clube da Criança** e, posteriormente, na Rede Globo) e como mídia e público percebiam o casal – tudo embasado em fontes da época, entrevistas e biografias. ## Aumento da Visibilidade Midiática nos Anos 1980 O namoro com Pelé catapultou Xuxa a um novo patamar de fama. Até então uma modelo em começo de carreira, Xuxa **“se tornou famosa ao aparecer ao lado do esportista de maior status do Brasil”** ([Pelé viveu com Xuxa um namoro intenso afetado por fofocas e indiscrições](https://www.terra.com.br/diversao/gente/pele-viveu-com-xuxa-um-namoro-intenso-afetado-por-fofocas-e-indiscricoes,0c075d1a6be75f53536ad3b70e8e4a01iavthiai.html#:~:text=O%20romance%20come%C3%A7ou%20quando%20ela,de%20maior%20status%20do%20Brasil)). A partir do momento em que o relacionamento se tornou público, ela passou a estampar capas de revistas com frequência e a ser assunto constante na imprensa. Em 20 de dezembro de 1980, a jovem apareceu na capa da revista *Manchete* ao lado de Pelé e outras modelos – um ensaio fotográfico que marcou o primeiro encontro dos dois e deu início à enorme atenção midiática em torno de Xuxa ([Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira](https://aventurasnahistoria.com.br/noticias/reportagem/xuxa-e-pele-o-relacionamento-que-ficou-cravado-na-historia-da-imprensa-brasileira.phtml#:~:text=A%20extinta%20Manchete%20promovia%20uma,Xuxa%2C%20com%20apenas%2017%20anos)) ([Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira](https://aventurasnahistoria.com.br/noticias/reportagem/xuxa-e-pele-o-relacionamento-que-ficou-cravado-na-historia-da-imprensa-brasileira.phtml#:~:text=O%20jantar%20aproximou%20o%20casal,E%20fui%E2%80%9D)). Não por acaso, *“naquele ano, ela foi capa de mais de cem revistas”* ([Xuxa está em paz - revista piauí](https://piaui.folha.uol.com.br/materia/xuxa-esta-em-paz/#:~:text=convidadas%20a%20posar%20ao%20lado,de%20mais%20de%20cem%20revistas)), um indicativo claro de como sua visibilidade explodiu após começar a namorar Pelé. Jornais, revistas de celebridades e programas de fofoca passaram a segui-los de perto; o casal virou sensação nacional, comparado até ao “Casal 20” (dupla glamourosa de uma série de TV americana) pelo seu alto perfil na mídia ([Xuxa e Pelé: um romance que se tornou inesquecível... | VEJA](https://veja.abril.com.br/coluna/veja-gente/xuxa-e-pele-um-romance-que-se-tornou-inesquecivel-para-os-dois/#:~:text=Um%20dos%20romances%20mais%20comentados,manchetes%20e%20revistas%20de%20fofoca)). Essa exposição intensa colocou Xuxa não apenas sob os holofotes do público, mas também a inseriu nos **bastidores do entretenimento**. Como namorada de Pelé – um dos homens mais conhecidos do mundo – Xuxa passou a frequentar eventos de gala, festas e bastidores de programas, onde conheceu figuras influentes do meio artístico e televisivo. Os fotógrafos os seguiam em eventos como bailes de carnaval e inaugurações, registrando cada aparição pública do casal. Com Pelé ao seu lado, Xuxa ganhou trânsito livre em círculos antes inacessíveis para uma modelo iniciante, construindo uma rede de contatos valiosa nos meios de comunicação. De fato, naquele início dos anos 80, **“os dois eram perseguidos por fotógrafos, apareciam em capas de revistas e até faziam publicidade juntos”** ([Pelé viveu com Xuxa um namoro intenso afetado por fofocas e indiscrições](https://www.terra.com.br/diversao/gente/pele-viveu-com-xuxa-um-namoro-intenso-afetado-por-fofocas-e-indiscricoes,0c075d1a6be75f53536ad3b70e8e4a01iavthiai.html#:~:text=Morte%20s%C3%BAbita%20encerra%20fase%20feliz,vida%20da%20atriz%20Marcia%20Manfredini)) – evidência de que Xuxa, graças ao namoro, transitava tanto na frente quanto por trás das câmeras com muito mais facilidade. Em suma, o relacionamento conferiu a ela um grau de notoriedade nacional que provavelmente demoraria anos para conquistar de outra forma, preparando o terreno para os passos seguintes de sua carreira. ## Influência Direta de Pelé nas Oportunidades Profissionais de Xuxa Além do aumento geral da fama, há casos específicos em que Pelé influenciou diretamente oportunidades profissionais para Xuxa. Um exemplo contundente é o filme **“Amor Estranho Amor” (1982)** – longa de teor erótico no qual Xuxa atuou no início da carreira. Segundo relatos da própria apresentadora, **foi Pelé quem a incentivou a aceitar participar desse filme** ([Pelé e Xuxa: um estranho amor que durou seis anos - 29/12/2022 - Celebridades - F5](https://f5.folha.uol.com.br/celebridades/2022/12/pele-e-xuxa-o-estranho-amor-entre-o-rei-do-futebol-e-a-futura-rainha-dos-baixinhos.shtml#:~:text=Profissionalmente%2C%20Xuxa%20disse%20que%20Pel%C3%A9,Me%20enganaram%2C%20falaram%20um)). Na época ainda em início de trajetória, Xuxa acabou convencida pelo namorado de que aquela oportunidade poderia ser benéfica. Anos mais tarde, ela revelaria arrependimento pela escolha desse papel, mas o fato reforça que Pelé teve influência ativa em decisões profissionais de Xuxa no começo de sua jornada. Outra área de influência direta foram as **publicidades e campanhas comerciais**. Graças ao prestígio de Pelé, Xuxa recebeu convites para estrelar anúncios ao lado do então namorado. Já em 1981, por exemplo, os dois gravaram juntos comerciais para uma empresa imobiliária, aparecendo como casal em campanhas de TV daquele Natal (pelas **Imóveis Francisco Xavier**, um case famoso entre colecionadores de propagandas da época) ([Xuxa e Pelé: Natal de 1981 na Publicidade Imobiliária | TikTok](https://www.tiktok.com/@thebest.memories/video/7301084045402721541#:~:text=Xuxa%20e%20Pel%C3%A9%3A%20Natal%20de,Natal%20de%201981%20na)) ([Xuxa com Pelé em comercial de imobiliária em dezembro de 1981](https://www.youtube.com/watch?v=t45oWkJPFw0#:~:text=Xuxa%20com%20Pel%C3%A9%20em%20comercial,Im%C3%B3veis%20em%20dezembro%20de%201981)). Assim, Xuxa obteve espaço em campanhas publicitárias que dificilmente envolveriam uma modelo desconhecida – mas que, com a “namorada do Pelé” no elenco, ganhavam apelo extra. Isso evidencia que Pelé abriu portas também no mercado publicitário, dando a Xuxa oportunidades de trabalho e renda enquanto sua própria imagem pública se consolidava. Ademais, a presença de Pelé ao lado de Xuxa em diversos editoriais e ensaios fotográficos serviu para elevá-la de modelo anônima a personalidade conhecida. Revistas e jornais buscavam os dois para sessões de fotos e entrevistas, sabendo do interesse do público pelo casal. As capas conjuntas em publicações de grande circulação (como *Manchete* e outras) não só aumentaram a exposição de Xuxa, mas também conferiram a ela certa credibilidade midiática por associação. Em outras palavras, estar ao lado de um ícone como Pelé funcionou como um “selo de aprovação” implícito, deixando editores e produtores mais propensos a convidá-la para projetos. Vale lembrar que **“ao longo dos seis anos de relacionamento, [eles] posaram para várias capas da *Manchete*”**, com a revista acompanhando de perto cada fase do namoro ([A história da foto de revista que gerou o namoro de Pelé e Xuxa](https://www.terra.com.br/diversao/gente/a-historia-da-foto-de-revista-que-gerou-o-namoro-de-pele-e-xuxa,c5106b23301f6f0e7c03f38cdf9eb1a06kopa9ho.html#:~:text=Um%20tempo%20depois%2C%20quando%20a,se%20nacionalmente%20famosa)). Essa recorrência nas bancas solidificou o rosto e o nome de Xuxa na indústria do entretenimento. Por fim, é importante notar que nem todas as influências de Pelé foram positivas para a carreira dela – algumas foram tentativas de direcionamento. A própria Xuxa contou que, quando surgiu a oportunidade de ela ir para a TV Globo em 1986, Pelé desencorajou a mudança. **Ele sugeriu que Xuxa permanecesse na TV Manchete, dizendo que “ser a primeira [na Globo] é muito difícil; melhor ficar onde está”**, o que ela interpretou como falta de apoio dele à sua ascensão ([Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira](https://aventurasnahistoria.com.br/noticias/reportagem/xuxa-e-pele-o-relacionamento-que-ficou-cravado-na-historia-da-imprensa-brasileira.phtml#:~:text=,torcendo%20por%20mim%E2%80%9D%2C%20acrescentou%20Xuxa)). Esse episódio mostra que Pelé tentou influenciar também os rumos que Xuxa tomaria, embora, nesse caso, ela tenha decidido seguir sua intuição profissional e aceitar o desafio na Globo – escolha que se revelaria acertada. Em resumo, Pelé atuou sim como facilitador de várias oportunidades profissionais para Xuxa (de filmes a comerciais e visibilidade editorial), mas ela soube trilhar seu caminho a partir daí, inclusive contrariando conselhos dele quando necessário. ## Papel da Revista *Manchete* e Outras Mídias na Promoção de Xuxa A revista ***Manchete*** teve um papel central na ascensão de Xuxa durante o relacionamento com Pelé. Foi justamente num ensaio para a *Manchete* que os dois se conheceram, em dezembro de 1980 ([Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira](https://aventurasnahistoria.com.br/noticias/reportagem/xuxa-e-pele-o-relacionamento-que-ficou-cravado-na-historia-da-imprensa-brasileira.phtml#:~:text=A%20extinta%20Manchete%20promovia%20uma,Xuxa%2C%20com%20apenas%2017%20anos)), e a partir daí a publicação tornou-se uma espécie oficiosa de cronista do romance. A *Manchete* era uma das revistas mais populares do Brasil naquela época e, ao perceber o interesse do público pelo casal, passou a trazê-los frequentemente em suas páginas. De fato, a revista que agiu como "cupido" do casal **“contava detalhes do romance a cada edição”**, alimentando a curiosidade nacional sobre a vida de Pelé e sua jovem namorada ([A história da foto de revista que gerou o namoro de Pelé e Xuxa](https://www.terra.com.br/diversao/gente/a-historia-da-foto-de-revista-que-gerou-o-namoro-de-pele-e-xuxa,c5106b23301f6f0e7c03f38cdf9eb1a06kopa9ho.html#:~:text=nacionalmente%20famosa)). As capas exibindo Xuxa e Pelé juntos (em cenários que iam da praia a eventos sociais) viraram chamariz nas bancas e contribuíram enormemente para fixar a imagem de Xuxa na mente do público. ([A história da foto de revista que gerou o namoro de Pelé e Xuxa](https://www.terra.com.br/diversao/gente/a-historia-da-foto-de-revista-que-gerou-o-namoro-de-pele-e-xuxa,c5106b23301f6f0e7c03f38cdf9eb1a06kopa9ho.html)) *Capa da revista Manchete (20 de dezembro de 1980) mostrando Pelé ao centro com Xuxa (à esquerda) e outras modelos. A partir desse ensaio fotográfico, a revista passou a acompanhar de perto o romance, impulsionando a imagem de Xuxa nacionalmente.* ([A história da foto de revista que gerou o namoro de Pelé e Xuxa](https://www.terra.com.br/diversao/gente/a-historia-da-foto-de-revista-que-gerou-o-namoro-de-pele-e-xuxa,c5106b23301f6f0e7c03f38cdf9eb1a06kopa9ho.html#:~:text=Um%20tempo%20depois%2C%20quando%20a,se%20nacionalmente%20famosa)) ([Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira](https://aventurasnahistoria.com.br/noticias/reportagem/xuxa-e-pele-o-relacionamento-que-ficou-cravado-na-historia-da-imprensa-brasileira.phtml#:~:text=A%20extinta%20Manchete%20promovia%20uma,Xuxa%2C%20com%20apenas%2017%20anos)) Além da *Manchete*, outras mídias impressas também surfaram no interesse pelo casal e ajudaram a moldar a imagem de Xuxa. Revistas de celebridades e colunas sociais publicavam notas e fotos frequentes, ora exaltando o glamour do par, ora especulando sobre fofocas. Xuxa, que pouco antes era desconhecida fora do circuito da moda, tornou-se figura constante em revistas semanais como *Contigo!* e *Amiga* (dedicadas à vida dos famosos), assim como em jornais de grande circulação. Esse bombardeio de aparições – entrevistas, fotos e manchetes – construiu a **persona pública** de Xuxa simultaneamente como **modelo desejada e namorada devotada**. A promoção de sua imagem tinha um tom deliberadamente positivo nas revistas: enfatizava-se sua beleza, juventude e sorte por ter sido “escolhida” pelo rei Pelé. Em contrapartida, eventuais polêmicas (como cenas ousadas que ela fez no cinema ou rumores de crises no namoro) eram administradas pela própria mídia de maneira a preservar o encanto em torno de Xuxa, que já despontava como uma espécie de Cinderella moderna na narrativa do entretenimento brasileiro. Cabe destacar que a conexão de Xuxa com a *Manchete* não ficou só nas páginas da revista, mas transbordou para a televisão, já que a Rede Manchete (canal de TV fundado em 1983) pertencia ao mesmo grupo empresarial. Essa sinergia mídia impressa/televisão beneficiou Xuxa: **quando a Rede Manchete buscava uma apresentadora para seu novo programa infantil em 1983, Xuxa – já famosa pelas capas de revista – foi convidada** para o posto ([Xuxa está em paz - revista piauí](https://piaui.folha.uol.com.br/materia/xuxa-esta-em-paz/#:~:text=match%20at%20L355%20TV%20Manchete%2C,ter%20como%20apresentadora%20de%20programa)). Ou seja, a exposição na revista *Manchete* serviu de vitrine para que os executivos da emissora homônima apostassem nela na TV. Outras mídias também legitimaram sua transição de modelo para apresentadora, publicando matérias sobre sua simpatia com as crianças e seu carisma diante das câmeras, preparando o público para aceitar Xuxa em um novo papel. Assim, o período do relacionamento com Pelé viu a mídia – liderada pela revista *Manchete* – construir e promover intensamente a imagem de Xuxa, pavimentando o caminho para suas conquistas seguintes. ## O Relacionamento e a Conquista de Espaços na TV: *Clube da Criança* e Rede Globo O namoro com Pelé coincidiu com a entrada de Xuxa na televisão e possivelmente facilitou essa transição. Em 1983, a recém-inaugurada Rede Manchete lançou o **“Clube da Criança”**, primeiro programa infantil de auditório da emissora, e Xuxa foi escolhida como apresentadora. Há indícios de que sua fama prévia – alavancada pelo relacionamento – foi decisiva nessa escolha. Conforme relatos, o diretor Maurício Sherman (responsável pelo projeto) estava de olho em Xuxa por sua notoriedade e carisma, chegando a dizer que ela reunia *“a sensualidade de Marilyn Monroe, o sorriso de Doris Day e um quê de Peter Pan”* ([Xuxa está em paz - revista piauí](https://piaui.folha.uol.com.br/materia/xuxa-esta-em-paz/#:~:text=TV%20Manchete%2C%20do%20grupo%20de,ter%20como%20apresentadora%20de%20programa)) – uma combinação que poderia funcionar bem num programa infantil. Xuxa inicialmente hesitou em aceitar, talvez pelo contraste entre sua imagem de modelo sensual e o universo infantil, mas acabou assinando contrato com a Manchete ([Clube da Criança – Wikipédia, a enciclopédia livre](https://pt.wikipedia.org/wiki/Clube_da_Crian%C3%A7a#:~:text=match%20at%20L206%20comando%20da,por%20Maur%C3%ADcio%20Sherman%20e%20pelo)). Assim, aos 20 anos de idade, ela estreava como apresentadora de TV, **em grande parte graças à visibilidade e confiança que o nome “Xuxa” (já famoso por ser namorada do Pelé) passava aos produtores**. Não há registro de que Pelé tenha intervindo diretamente para que Xuxa conseguisse o posto no *Clube da Criança*. Foi a própria rede Manchete – estimulada pelo burburinho em torno dela – que a **“procurou e a convidou para apresentar”** o programa ([Xuxa está em paz - revista piauí](https://piaui.folha.uol.com.br/materia/xuxa-esta-em-paz/#:~:text=TV%20Manchete%2C%20do%20grupo%20de,ter%20como%20apresentadora%20de%20programa)). Porém, é inegável que, sem o destaque que Xuxa conquistara nos anos anteriores na imprensa (devido ao namoro), dificilmente uma emissora arriscaria colocar uma jovem inexperiente para comandar um show infantil nacional. Ou seja, o relacionamento criou as condições favoráveis para essa oportunidade surgir. Uma vez no ar, Xuxa rapidamente mostrou talento próprio: o *Clube da Criança* foi ganhando audiência e revelou a aptidão dela em se comunicar com o público infantil ([Xuxa, Pantanal, Cavaleiros dos Zodíacos: lembre sucessos da TV ...](https://www.folhape.com.br/cultura/xuxa-pantanal-cavaleiros-dos-zodiacos-e-mais-sucessos-da-tv/334766/#:~:text=Xuxa%2C%20Pantanal%2C%20Cavaleiros%20dos%20Zod%C3%ADacos%3A,exibido%20no%20fim%20de)). Ainda durante seu tempo na Manchete, Xuxa manteve-se nos holofotes tanto pela carreira quanto pelo namoro com Pelé – frequentemente um assunto alimentava o outro na mídia. Em meados de 1986, já conhecida como a “Rainha dos Baixinhos” pelo sucesso junto às crianças, Xuxa recebeu uma proposta para se transferir para a Rede Globo, a principal emissora do país ([A história da foto de revista que gerou o namoro de Pelé e Xuxa](https://www.terra.com.br/diversao/gente/a-historia-da-foto-de-revista-que-gerou-o-namoro-de-pele-e-xuxa,c5106b23301f6f0e7c03f38cdf9eb1a06kopa9ho.html#:~:text=Pel%C3%A9%20e%20Xuxa%20ficaram%20juntos,do%20mesmo%20grupo%20da%20revista)). Novamente, aqui o relacionamento com Pelé tem um papel indireto: por um lado, pode ter ajudado a construir a notoriedade que chamou a atenção da Globo; por outro, chegava ao fim exatamente nesse momento, marcando uma virada na vida dela. Após alguns anos de *Clube da Criança*, Xuxa decidiu dar um passo adiante. Ela mesma tomou a iniciativa de terminar o namoro com Pelé e aceitou o convite para fazer o **“Xou da Xuxa”** na Globo ([A história da foto de revista que gerou o namoro de Pelé e Xuxa](https://www.terra.com.br/diversao/gente/a-historia-da-foto-de-revista-que-gerou-o-namoro-de-pele-e-xuxa,c5106b23301f6f0e7c03f38cdf9eb1a06kopa9ho.html#:~:text=Pel%C3%A9%20e%20Xuxa%20ficaram%20juntos,do%20mesmo%20grupo%20da%20revista)). Pelé, como mencionado, havia expressado reservas sobre essa mudança de emissora ([Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira](https://aventurasnahistoria.com.br/noticias/reportagem/xuxa-e-pele-o-relacionamento-que-ficou-cravado-na-historia-da-imprensa-brasileira.phtml#:~:text=,torcendo%20por%20mim%E2%80%9D%2C%20acrescentou%20Xuxa)), mas sem sucesso em demovê-la. Com a benção do dono da Manchete, Adolpho Bloch (que a tratava “como filha” e apoiou seu crescimento) ([Xuxa está em paz - revista piauí](https://piaui.folha.uol.com.br/materia/xuxa-esta-em-paz/#:~:text=match%20at%20L405%20Manchete%20e,%E2%80%99%E2%80%9D)) ([Xuxa está em paz - revista piauí](https://piaui.folha.uol.com.br/materia/xuxa-esta-em-paz/#:~:text=Manchete%20e%20fui%20embora%E2%80%9D%2C%20recorda,%E2%80%99%E2%80%9D)), Xuxa partiu para a Globo levando sua diretora Marlene Mattos, e estreou em junho de 1986 o programa que a consagraria definitivamente. É importante notar que, ao ingressar na Globo, Xuxa já não dependia mais da aura de “namorada do Pelé” – ela havia se firmado como apresentadora de sucesso por méritos próprios. Ainda assim, **o relacionamento anterior continuou a ser parte de sua imagem pública**: a mídia noticiou a mudança destacando que a namorada de Pelé chegara à Globo, e muitos espectadores tinham curiosidade sobre aquela moça cuja fama começara nos braços do ídolo do futebol. Em resumo, o namoro ajudou Xuxa a conquistar o primeiro grande espaço na TV (na Manchete), fornecendo-lhe exposição e credibilidade iniciais, enquanto sua ida para a Globo foi impulsionada principalmente pelo desempenho no *Clube da Criança* – algo que o prestígio conquistado durante o relacionamento tornou possível em primeiro lugar. ## Percepção da Mídia e do Público sobre o Casal e a Imagem de Xuxa Durante os anos de namoro, Pelé e Xuxa foram um prato cheio para a imprensa e objeto de variadas opiniões do público. De um lado, eram celebrados como **“casal perfeito na mídia”**, aparecendo sorridentes em eventos e capas, o que projetava uma imagem glamourosa e apaixonada ([Pelé viveu com Xuxa um namoro intenso afetado por fofocas e indiscrições](https://www.terra.com.br/diversao/gente/pele-viveu-com-xuxa-um-namoro-intenso-afetado-por-fofocas-e-indiscricoes,0c075d1a6be75f53536ad3b70e8e4a01iavthiai.html#:~:text=Image%3A%20Pel%C3%A9%20e%20Xuxa%20na,perfeito%20na%20m%C3%ADdia%2C%20mas%20com)). Xuxa era frequentemente retratada como a bela jovem humilde que havia conquistado o coração do "rei", uma narrativa de conto de fadas que agradava muitos fãs. Pessoas próximas diziam na época: *“Nossa, como ela está apaixonada, como ela está de quatro pelo Pelé”*, segundo relembrou a própria Xuxa, indicando que sua dedicação ao namorado era visível e comentada ([Xuxa e Pelé: um romance que se tornou inesquecível... | VEJA](https://veja.abril.com.br/coluna/veja-gente/xuxa-e-pele-um-romance-que-se-tornou-inesquecivel-para-os-dois/#:~:text=Ao%20participar%20de%20uma%20live,de%20quatro%20para%20o%20Pel%C3%A9%27%E2%80%9D)). Essa percepção de autenticidade nos sentimentos ajudou a humanizar Xuxa aos olhos do público, diferenciando-a de estereótipos de *roupante* ou interesse calculado. Por outro lado, nem toda a atenção era positiva. **Houve murmúrios maldosos e preconceituosos nos bastidores**. Pelé e Xuxa formavam um casal interracial (ele negro, ela branca e bem mais jovem), o que, segundo a imprensa, **“gerava olhares de reprovação dos conservadores” e até comentários racistas proferidos pelas costas** ([Pelé viveu com Xuxa um namoro intenso afetado por fofocas e indiscrições](https://www.terra.com.br/diversao/gente/pele-viveu-com-xuxa-um-namoro-intenso-afetado-por-fofocas-e-indiscricoes,0c075d1a6be75f53536ad3b70e8e4a01iavthiai.html#:~:text=Os%20dois%20eram%20perseguidos%20por,Mas%20nem%20tudo%20era%20agrad%C3%A1vel)). Além disso, alguns duvidavam das intenções de Xuxa no relacionamento, insinuando que ela buscava ascensão social por meio de Pelé. Termos pejorativos como *“maria-chuteira”* (gíria para mulheres que namoram jogadores em busca de status) e *“alpinista social”* chegaram a ser associados a Xuxa por fofoqueiros da época ([Pelé viveu com Xuxa um namoro intenso afetado por fofocas e indiscrições](https://www.terra.com.br/diversao/gente/pele-viveu-com-xuxa-um-namoro-intenso-afetado-por-fofocas-e-indiscricoes,0c075d1a6be75f53536ad3b70e8e4a01iavthiai.html#:~:text=olhares%20de%20reprova%C3%A7%C3%A3o%20dos%20conservadores)). Essa desconfiança lançava sombra sobre a imagem dela, pintando-a, aos olhos de alguns, como oportunista em vez de namorada dedicada. Xuxa teve de lidar com esse tipo de insinuação ao longo do namoro, buscando provar que seu amor era verdadeiro e que ela também tinha talentos e ambições próprias. A mídia impressa, em geral, manteve uma postura favorável ao casal, explorando o romance como algo encantador. Mas não deixou de reportar as turbulências: sabia-se, por exemplo, das **frequentes traições de Pelé**, que Xuxa anos depois revelou ter suportado calada na época ([Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira](https://aventurasnahistoria.com.br/noticias/reportagem/xuxa-e-pele-o-relacionamento-que-ficou-cravado-na-historia-da-imprensa-brasileira.phtml#:~:text=Por%20causa%20do%20companheiro%2C%20tamb%C3%A9m,que%20n%C3%A3o%20era%20o%20meu)) ([Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira](https://aventurasnahistoria.com.br/noticias/reportagem/xuxa-e-pele-o-relacionamento-que-ficou-cravado-na-historia-da-imprensa-brasileira.phtml#:~:text=Apesar%20dos%20problemas%20corriqueiros%20com,Era%20uma%20situa%C3%A7%C3%A3o%20esquisita%E2%80%9D)). Essas infidelidades eram rumores correntes nos círculos de fofoca, embora Xuxa raramente comentasse publicamente enquanto estava com Pelé. O público, portanto, via um casal bonito e famoso, mas também acompanhava as especulações de crises e reconciliações pelos noticiários de celebridades. Cada aparição pública deles – fosse em um jogo de futebol, um evento beneficente ou nos camarotes do carnaval – era dissecada pelos repórteres, e cada declaração (ou silêncio) alimentava interpretações sobre o estado do relacionamento e sobre quem era Xuxa por trás da fama. No saldo final, o namoro com Pelé influenciou profundamente a **imagem pública de Xuxa**. Inicialmente marcada como “a namorada do Rei” – posição que trazia tanto admiração quanto inveja – Xuxa soube aproveitar a visibilidade para mostrar carisma e trabalho, transformando-se em uma estrela por direito próprio. Ao se tornar apresentadora infantil de sucesso ainda durante o namoro, ela começou a dissociar sua imagem da de Pelé, provando que podia ser mais do que um apêndice de um astro do esporte. Quando o relacionamento terminou em 1986, Xuxa emergiu não caída em desgraça, mas sim pronta para reinar sozinha na TV. A mídia continuou a mencioná-la em referência a Pelé por algum tempo (era inevitável, dado o quão famoso o casal fora), mas cada vez mais o público passou a enxergá-la principalmente como a **“Rainha dos Baixinhos”**, a figura alegre das manhãs na TV Globo. Em entrevistas posteriores, Xuxa admitiu ter sentimentos mistos ao lembrar dessa fase: ela se ressentiu, por exemplo, de Pelé ter classificado o que viveram como *“uma amizade colorida”* em vez de namoro sério ([Pelé e Xuxa: um estranho amor que durou seis anos - 29/12/2022 - Celebridades - F5](https://f5.folha.uol.com.br/celebridades/2022/12/pele-e-xuxa-o-estranho-amor-entre-o-rei-do-futebol-e-a-futura-rainha-dos-baixinhos.shtml#:~:text=Xuxa%20disse%20ter%20ficado%20magoada,N%C3%A3o%20fui%20avisada)) – frase do ex-jogador que a magoou e que veio a público muitos anos depois. Esse comentário retroativo de Pelé apenas reforçou o quanto a mídia e o público discutiram e dissecaram a natureza daquela relação. Em conclusão, a percepção do casal Xuxa e Pelé oscilou entre o encanto e a controvérsia, mas inegavelmente manteve Xuxa nos trending topics de sua época (para usar um termo atual). A jovem modelo gaúcha ganhou projeção, prestígio e também enfrentou julgamentos enquanto esteve com Pelé. Tudo isso moldou sua imagem – de **símbolo sexual e socialite em ascensão** a **profissional talentosa pronta para brilhar por conta própria**. O relacionamento forneceu-lhe a plataforma e a armadura mediática; coube a Xuxa transformar essa visibilidade em uma carreira sólida, o que ela fez com maestria ao se tornar uma das maiores apresentadoras da história da TV brasileira. **Fontes:** Entrevistas e depoimentos de Xuxa Meneghel (inclusive do livro *Memórias*, 2020), reportagens da época em revistas como *Manchete*, colunas sociais e jornais (compiladas em repositórios atuais), e biografias e retrospectivas sobre ambos os envolvidos ([A história da foto de revista que gerou o namoro de Pelé e Xuxa](https://www.terra.com.br/diversao/gente/a-historia-da-foto-de-revista-que-gerou-o-namoro-de-pele-e-xuxa,c5106b23301f6f0e7c03f38cdf9eb1a06kopa9ho.html#:~:text=Um%20tempo%20depois%2C%20quando%20a,se%20nacionalmente%20famosa)) ([Pelé viveu com Xuxa um namoro intenso afetado por fofocas e indiscrições](https://www.terra.com.br/diversao/gente/pele-viveu-com-xuxa-um-namoro-intenso-afetado-por-fofocas-e-indiscricoes,0c075d1a6be75f53536ad3b70e8e4a01iavthiai.html#:~:text=Morte%20s%C3%BAbita%20encerra%20fase%20feliz,vida%20da%20atriz%20Marcia%20Manfredini)) ([Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira](https://aventurasnahistoria.com.br/noticias/reportagem/xuxa-e-pele-o-relacionamento-que-ficou-cravado-na-historia-da-imprensa-brasileira.phtml#:~:text=,torcendo%20por%20mim%E2%80%9D%2C%20acrescentou%20Xuxa)) ([Xuxa e Pelé: um romance que se tornou inesquecível... | VEJA](https://veja.abril.com.br/coluna/veja-gente/xuxa-e-pele-um-romance-que-se-tornou-inesquecivel-para-os-dois/#:~:text=Um%20dos%20romances%20mais%20comentados,manchetes%20e%20revistas%20de%20fofoca)), entre outras. Essas fontes confirmam o papel catalisador que o namoro com Pelé teve nos primeiros passos da trajetória de Xuxa, bem como os desafios e oportunidades que surgiram dessa intensa exposição pública.
@ 3ffac3a6:2d656657
2025-04-05 04:55:12# O Impacto do Namoro com Pelé na Carreira de Xuxa Meneghel ## Disclaimer: Esse texto foi totalmente escrito pelo ChatGPT, eu apenas pedi que ele fizesse uma pesquisa sobre o tema. **Introdução:** O relacionamento entre Xuxa Meneghel e Pelé, que durou cerca de seis anos (início dos anos 1980 até 1986), foi um dos mais comentados da década de 1980 ([Xuxa e Pelé: um romance que se tornou inesquecível... | VEJA](https://veja.abril.com.br/coluna/veja-gente/xuxa-e-pele-um-romance-que-se-tornou-inesquecivel-para-os-dois/#:~:text=Um%20dos%20romances%20mais%20comentados,manchetes%20e%20revistas%20de%20fofoca)). Xuxa tinha apenas 17 anos quando começou a namorar o já consagrado “Rei do Futebol”, então com 40 anos ([A história da foto de revista que gerou o namoro de Pelé e Xuxa](https://www.terra.com.br/diversao/gente/a-historia-da-foto-de-revista-que-gerou-o-namoro-de-pele-e-xuxa,c5106b23301f6f0e7c03f38cdf9eb1a06kopa9ho.html#:~:text=Xuxa%20tinha%2017%20anos,a%20primeira%20mulher%2C%20Rosemeri%20Cholbi)) ([Xuxa e Pelé: um romance que se tornou inesquecível... | VEJA](https://veja.abril.com.br/coluna/veja-gente/xuxa-e-pele-um-romance-que-se-tornou-inesquecivel-para-os-dois/#:~:text=O%20jogador%20de%20futebol%20e,um%20relacionamento%20por%20seis%20anos)). Esse romance altamente midiático não só atiçou a curiosidade do público, como também alavancou a carreira de Xuxa de forma significativa. A seguir, detalhamos como o namoro aumentou a visibilidade da apresentadora, quais oportunidades profissionais podem ter tido influência direta de Pelé, o papel da revista *Manchete* e de outras mídias na promoção de sua imagem, se o relacionamento contribuiu para Xuxa conquistar espaços na TV (como o programa **Clube da Criança** e, posteriormente, na Rede Globo) e como mídia e público percebiam o casal – tudo embasado em fontes da época, entrevistas e biografias. ## Aumento da Visibilidade Midiática nos Anos 1980 O namoro com Pelé catapultou Xuxa a um novo patamar de fama. Até então uma modelo em começo de carreira, Xuxa **“se tornou famosa ao aparecer ao lado do esportista de maior status do Brasil”** ([Pelé viveu com Xuxa um namoro intenso afetado por fofocas e indiscrições](https://www.terra.com.br/diversao/gente/pele-viveu-com-xuxa-um-namoro-intenso-afetado-por-fofocas-e-indiscricoes,0c075d1a6be75f53536ad3b70e8e4a01iavthiai.html#:~:text=O%20romance%20come%C3%A7ou%20quando%20ela,de%20maior%20status%20do%20Brasil)). A partir do momento em que o relacionamento se tornou público, ela passou a estampar capas de revistas com frequência e a ser assunto constante na imprensa. Em 20 de dezembro de 1980, a jovem apareceu na capa da revista *Manchete* ao lado de Pelé e outras modelos – um ensaio fotográfico que marcou o primeiro encontro dos dois e deu início à enorme atenção midiática em torno de Xuxa ([Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira](https://aventurasnahistoria.com.br/noticias/reportagem/xuxa-e-pele-o-relacionamento-que-ficou-cravado-na-historia-da-imprensa-brasileira.phtml#:~:text=A%20extinta%20Manchete%20promovia%20uma,Xuxa%2C%20com%20apenas%2017%20anos)) ([Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira](https://aventurasnahistoria.com.br/noticias/reportagem/xuxa-e-pele-o-relacionamento-que-ficou-cravado-na-historia-da-imprensa-brasileira.phtml#:~:text=O%20jantar%20aproximou%20o%20casal,E%20fui%E2%80%9D)). Não por acaso, *“naquele ano, ela foi capa de mais de cem revistas”* ([Xuxa está em paz - revista piauí](https://piaui.folha.uol.com.br/materia/xuxa-esta-em-paz/#:~:text=convidadas%20a%20posar%20ao%20lado,de%20mais%20de%20cem%20revistas)), um indicativo claro de como sua visibilidade explodiu após começar a namorar Pelé. Jornais, revistas de celebridades e programas de fofoca passaram a segui-los de perto; o casal virou sensação nacional, comparado até ao “Casal 20” (dupla glamourosa de uma série de TV americana) pelo seu alto perfil na mídia ([Xuxa e Pelé: um romance que se tornou inesquecível... | VEJA](https://veja.abril.com.br/coluna/veja-gente/xuxa-e-pele-um-romance-que-se-tornou-inesquecivel-para-os-dois/#:~:text=Um%20dos%20romances%20mais%20comentados,manchetes%20e%20revistas%20de%20fofoca)). Essa exposição intensa colocou Xuxa não apenas sob os holofotes do público, mas também a inseriu nos **bastidores do entretenimento**. Como namorada de Pelé – um dos homens mais conhecidos do mundo – Xuxa passou a frequentar eventos de gala, festas e bastidores de programas, onde conheceu figuras influentes do meio artístico e televisivo. Os fotógrafos os seguiam em eventos como bailes de carnaval e inaugurações, registrando cada aparição pública do casal. Com Pelé ao seu lado, Xuxa ganhou trânsito livre em círculos antes inacessíveis para uma modelo iniciante, construindo uma rede de contatos valiosa nos meios de comunicação. De fato, naquele início dos anos 80, **“os dois eram perseguidos por fotógrafos, apareciam em capas de revistas e até faziam publicidade juntos”** ([Pelé viveu com Xuxa um namoro intenso afetado por fofocas e indiscrições](https://www.terra.com.br/diversao/gente/pele-viveu-com-xuxa-um-namoro-intenso-afetado-por-fofocas-e-indiscricoes,0c075d1a6be75f53536ad3b70e8e4a01iavthiai.html#:~:text=Morte%20s%C3%BAbita%20encerra%20fase%20feliz,vida%20da%20atriz%20Marcia%20Manfredini)) – evidência de que Xuxa, graças ao namoro, transitava tanto na frente quanto por trás das câmeras com muito mais facilidade. Em suma, o relacionamento conferiu a ela um grau de notoriedade nacional que provavelmente demoraria anos para conquistar de outra forma, preparando o terreno para os passos seguintes de sua carreira. ## Influência Direta de Pelé nas Oportunidades Profissionais de Xuxa Além do aumento geral da fama, há casos específicos em que Pelé influenciou diretamente oportunidades profissionais para Xuxa. Um exemplo contundente é o filme **“Amor Estranho Amor” (1982)** – longa de teor erótico no qual Xuxa atuou no início da carreira. Segundo relatos da própria apresentadora, **foi Pelé quem a incentivou a aceitar participar desse filme** ([Pelé e Xuxa: um estranho amor que durou seis anos - 29/12/2022 - Celebridades - F5](https://f5.folha.uol.com.br/celebridades/2022/12/pele-e-xuxa-o-estranho-amor-entre-o-rei-do-futebol-e-a-futura-rainha-dos-baixinhos.shtml#:~:text=Profissionalmente%2C%20Xuxa%20disse%20que%20Pel%C3%A9,Me%20enganaram%2C%20falaram%20um)). Na época ainda em início de trajetória, Xuxa acabou convencida pelo namorado de que aquela oportunidade poderia ser benéfica. Anos mais tarde, ela revelaria arrependimento pela escolha desse papel, mas o fato reforça que Pelé teve influência ativa em decisões profissionais de Xuxa no começo de sua jornada. Outra área de influência direta foram as **publicidades e campanhas comerciais**. Graças ao prestígio de Pelé, Xuxa recebeu convites para estrelar anúncios ao lado do então namorado. Já em 1981, por exemplo, os dois gravaram juntos comerciais para uma empresa imobiliária, aparecendo como casal em campanhas de TV daquele Natal (pelas **Imóveis Francisco Xavier**, um case famoso entre colecionadores de propagandas da época) ([Xuxa e Pelé: Natal de 1981 na Publicidade Imobiliária | TikTok](https://www.tiktok.com/@thebest.memories/video/7301084045402721541#:~:text=Xuxa%20e%20Pel%C3%A9%3A%20Natal%20de,Natal%20de%201981%20na)) ([Xuxa com Pelé em comercial de imobiliária em dezembro de 1981](https://www.youtube.com/watch?v=t45oWkJPFw0#:~:text=Xuxa%20com%20Pel%C3%A9%20em%20comercial,Im%C3%B3veis%20em%20dezembro%20de%201981)). Assim, Xuxa obteve espaço em campanhas publicitárias que dificilmente envolveriam uma modelo desconhecida – mas que, com a “namorada do Pelé” no elenco, ganhavam apelo extra. Isso evidencia que Pelé abriu portas também no mercado publicitário, dando a Xuxa oportunidades de trabalho e renda enquanto sua própria imagem pública se consolidava. Ademais, a presença de Pelé ao lado de Xuxa em diversos editoriais e ensaios fotográficos serviu para elevá-la de modelo anônima a personalidade conhecida. Revistas e jornais buscavam os dois para sessões de fotos e entrevistas, sabendo do interesse do público pelo casal. As capas conjuntas em publicações de grande circulação (como *Manchete* e outras) não só aumentaram a exposição de Xuxa, mas também conferiram a ela certa credibilidade midiática por associação. Em outras palavras, estar ao lado de um ícone como Pelé funcionou como um “selo de aprovação” implícito, deixando editores e produtores mais propensos a convidá-la para projetos. Vale lembrar que **“ao longo dos seis anos de relacionamento, [eles] posaram para várias capas da *Manchete*”**, com a revista acompanhando de perto cada fase do namoro ([A história da foto de revista que gerou o namoro de Pelé e Xuxa](https://www.terra.com.br/diversao/gente/a-historia-da-foto-de-revista-que-gerou-o-namoro-de-pele-e-xuxa,c5106b23301f6f0e7c03f38cdf9eb1a06kopa9ho.html#:~:text=Um%20tempo%20depois%2C%20quando%20a,se%20nacionalmente%20famosa)). Essa recorrência nas bancas solidificou o rosto e o nome de Xuxa na indústria do entretenimento. Por fim, é importante notar que nem todas as influências de Pelé foram positivas para a carreira dela – algumas foram tentativas de direcionamento. A própria Xuxa contou que, quando surgiu a oportunidade de ela ir para a TV Globo em 1986, Pelé desencorajou a mudança. **Ele sugeriu que Xuxa permanecesse na TV Manchete, dizendo que “ser a primeira [na Globo] é muito difícil; melhor ficar onde está”**, o que ela interpretou como falta de apoio dele à sua ascensão ([Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira](https://aventurasnahistoria.com.br/noticias/reportagem/xuxa-e-pele-o-relacionamento-que-ficou-cravado-na-historia-da-imprensa-brasileira.phtml#:~:text=,torcendo%20por%20mim%E2%80%9D%2C%20acrescentou%20Xuxa)). Esse episódio mostra que Pelé tentou influenciar também os rumos que Xuxa tomaria, embora, nesse caso, ela tenha decidido seguir sua intuição profissional e aceitar o desafio na Globo – escolha que se revelaria acertada. Em resumo, Pelé atuou sim como facilitador de várias oportunidades profissionais para Xuxa (de filmes a comerciais e visibilidade editorial), mas ela soube trilhar seu caminho a partir daí, inclusive contrariando conselhos dele quando necessário. ## Papel da Revista *Manchete* e Outras Mídias na Promoção de Xuxa A revista ***Manchete*** teve um papel central na ascensão de Xuxa durante o relacionamento com Pelé. Foi justamente num ensaio para a *Manchete* que os dois se conheceram, em dezembro de 1980 ([Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira](https://aventurasnahistoria.com.br/noticias/reportagem/xuxa-e-pele-o-relacionamento-que-ficou-cravado-na-historia-da-imprensa-brasileira.phtml#:~:text=A%20extinta%20Manchete%20promovia%20uma,Xuxa%2C%20com%20apenas%2017%20anos)), e a partir daí a publicação tornou-se uma espécie oficiosa de cronista do romance. A *Manchete* era uma das revistas mais populares do Brasil naquela época e, ao perceber o interesse do público pelo casal, passou a trazê-los frequentemente em suas páginas. De fato, a revista que agiu como "cupido" do casal **“contava detalhes do romance a cada edição”**, alimentando a curiosidade nacional sobre a vida de Pelé e sua jovem namorada ([A história da foto de revista que gerou o namoro de Pelé e Xuxa](https://www.terra.com.br/diversao/gente/a-historia-da-foto-de-revista-que-gerou-o-namoro-de-pele-e-xuxa,c5106b23301f6f0e7c03f38cdf9eb1a06kopa9ho.html#:~:text=nacionalmente%20famosa)). As capas exibindo Xuxa e Pelé juntos (em cenários que iam da praia a eventos sociais) viraram chamariz nas bancas e contribuíram enormemente para fixar a imagem de Xuxa na mente do público. ([A história da foto de revista que gerou o namoro de Pelé e Xuxa](https://www.terra.com.br/diversao/gente/a-historia-da-foto-de-revista-que-gerou-o-namoro-de-pele-e-xuxa,c5106b23301f6f0e7c03f38cdf9eb1a06kopa9ho.html)) *Capa da revista Manchete (20 de dezembro de 1980) mostrando Pelé ao centro com Xuxa (à esquerda) e outras modelos. A partir desse ensaio fotográfico, a revista passou a acompanhar de perto o romance, impulsionando a imagem de Xuxa nacionalmente.* ([A história da foto de revista que gerou o namoro de Pelé e Xuxa](https://www.terra.com.br/diversao/gente/a-historia-da-foto-de-revista-que-gerou-o-namoro-de-pele-e-xuxa,c5106b23301f6f0e7c03f38cdf9eb1a06kopa9ho.html#:~:text=Um%20tempo%20depois%2C%20quando%20a,se%20nacionalmente%20famosa)) ([Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira](https://aventurasnahistoria.com.br/noticias/reportagem/xuxa-e-pele-o-relacionamento-que-ficou-cravado-na-historia-da-imprensa-brasileira.phtml#:~:text=A%20extinta%20Manchete%20promovia%20uma,Xuxa%2C%20com%20apenas%2017%20anos)) Além da *Manchete*, outras mídias impressas também surfaram no interesse pelo casal e ajudaram a moldar a imagem de Xuxa. Revistas de celebridades e colunas sociais publicavam notas e fotos frequentes, ora exaltando o glamour do par, ora especulando sobre fofocas. Xuxa, que pouco antes era desconhecida fora do circuito da moda, tornou-se figura constante em revistas semanais como *Contigo!* e *Amiga* (dedicadas à vida dos famosos), assim como em jornais de grande circulação. Esse bombardeio de aparições – entrevistas, fotos e manchetes – construiu a **persona pública** de Xuxa simultaneamente como **modelo desejada e namorada devotada**. A promoção de sua imagem tinha um tom deliberadamente positivo nas revistas: enfatizava-se sua beleza, juventude e sorte por ter sido “escolhida” pelo rei Pelé. Em contrapartida, eventuais polêmicas (como cenas ousadas que ela fez no cinema ou rumores de crises no namoro) eram administradas pela própria mídia de maneira a preservar o encanto em torno de Xuxa, que já despontava como uma espécie de Cinderella moderna na narrativa do entretenimento brasileiro. Cabe destacar que a conexão de Xuxa com a *Manchete* não ficou só nas páginas da revista, mas transbordou para a televisão, já que a Rede Manchete (canal de TV fundado em 1983) pertencia ao mesmo grupo empresarial. Essa sinergia mídia impressa/televisão beneficiou Xuxa: **quando a Rede Manchete buscava uma apresentadora para seu novo programa infantil em 1983, Xuxa – já famosa pelas capas de revista – foi convidada** para o posto ([Xuxa está em paz - revista piauí](https://piaui.folha.uol.com.br/materia/xuxa-esta-em-paz/#:~:text=match%20at%20L355%20TV%20Manchete%2C,ter%20como%20apresentadora%20de%20programa)). Ou seja, a exposição na revista *Manchete* serviu de vitrine para que os executivos da emissora homônima apostassem nela na TV. Outras mídias também legitimaram sua transição de modelo para apresentadora, publicando matérias sobre sua simpatia com as crianças e seu carisma diante das câmeras, preparando o público para aceitar Xuxa em um novo papel. Assim, o período do relacionamento com Pelé viu a mídia – liderada pela revista *Manchete* – construir e promover intensamente a imagem de Xuxa, pavimentando o caminho para suas conquistas seguintes. ## O Relacionamento e a Conquista de Espaços na TV: *Clube da Criança* e Rede Globo O namoro com Pelé coincidiu com a entrada de Xuxa na televisão e possivelmente facilitou essa transição. Em 1983, a recém-inaugurada Rede Manchete lançou o **“Clube da Criança”**, primeiro programa infantil de auditório da emissora, e Xuxa foi escolhida como apresentadora. Há indícios de que sua fama prévia – alavancada pelo relacionamento – foi decisiva nessa escolha. Conforme relatos, o diretor Maurício Sherman (responsável pelo projeto) estava de olho em Xuxa por sua notoriedade e carisma, chegando a dizer que ela reunia *“a sensualidade de Marilyn Monroe, o sorriso de Doris Day e um quê de Peter Pan”* ([Xuxa está em paz - revista piauí](https://piaui.folha.uol.com.br/materia/xuxa-esta-em-paz/#:~:text=TV%20Manchete%2C%20do%20grupo%20de,ter%20como%20apresentadora%20de%20programa)) – uma combinação que poderia funcionar bem num programa infantil. Xuxa inicialmente hesitou em aceitar, talvez pelo contraste entre sua imagem de modelo sensual e o universo infantil, mas acabou assinando contrato com a Manchete ([Clube da Criança – Wikipédia, a enciclopédia livre](https://pt.wikipedia.org/wiki/Clube_da_Crian%C3%A7a#:~:text=match%20at%20L206%20comando%20da,por%20Maur%C3%ADcio%20Sherman%20e%20pelo)). Assim, aos 20 anos de idade, ela estreava como apresentadora de TV, **em grande parte graças à visibilidade e confiança que o nome “Xuxa” (já famoso por ser namorada do Pelé) passava aos produtores**. Não há registro de que Pelé tenha intervindo diretamente para que Xuxa conseguisse o posto no *Clube da Criança*. Foi a própria rede Manchete – estimulada pelo burburinho em torno dela – que a **“procurou e a convidou para apresentar”** o programa ([Xuxa está em paz - revista piauí](https://piaui.folha.uol.com.br/materia/xuxa-esta-em-paz/#:~:text=TV%20Manchete%2C%20do%20grupo%20de,ter%20como%20apresentadora%20de%20programa)). Porém, é inegável que, sem o destaque que Xuxa conquistara nos anos anteriores na imprensa (devido ao namoro), dificilmente uma emissora arriscaria colocar uma jovem inexperiente para comandar um show infantil nacional. Ou seja, o relacionamento criou as condições favoráveis para essa oportunidade surgir. Uma vez no ar, Xuxa rapidamente mostrou talento próprio: o *Clube da Criança* foi ganhando audiência e revelou a aptidão dela em se comunicar com o público infantil ([Xuxa, Pantanal, Cavaleiros dos Zodíacos: lembre sucessos da TV ...](https://www.folhape.com.br/cultura/xuxa-pantanal-cavaleiros-dos-zodiacos-e-mais-sucessos-da-tv/334766/#:~:text=Xuxa%2C%20Pantanal%2C%20Cavaleiros%20dos%20Zod%C3%ADacos%3A,exibido%20no%20fim%20de)). Ainda durante seu tempo na Manchete, Xuxa manteve-se nos holofotes tanto pela carreira quanto pelo namoro com Pelé – frequentemente um assunto alimentava o outro na mídia. Em meados de 1986, já conhecida como a “Rainha dos Baixinhos” pelo sucesso junto às crianças, Xuxa recebeu uma proposta para se transferir para a Rede Globo, a principal emissora do país ([A história da foto de revista que gerou o namoro de Pelé e Xuxa](https://www.terra.com.br/diversao/gente/a-historia-da-foto-de-revista-que-gerou-o-namoro-de-pele-e-xuxa,c5106b23301f6f0e7c03f38cdf9eb1a06kopa9ho.html#:~:text=Pel%C3%A9%20e%20Xuxa%20ficaram%20juntos,do%20mesmo%20grupo%20da%20revista)). Novamente, aqui o relacionamento com Pelé tem um papel indireto: por um lado, pode ter ajudado a construir a notoriedade que chamou a atenção da Globo; por outro, chegava ao fim exatamente nesse momento, marcando uma virada na vida dela. Após alguns anos de *Clube da Criança*, Xuxa decidiu dar um passo adiante. Ela mesma tomou a iniciativa de terminar o namoro com Pelé e aceitou o convite para fazer o **“Xou da Xuxa”** na Globo ([A história da foto de revista que gerou o namoro de Pelé e Xuxa](https://www.terra.com.br/diversao/gente/a-historia-da-foto-de-revista-que-gerou-o-namoro-de-pele-e-xuxa,c5106b23301f6f0e7c03f38cdf9eb1a06kopa9ho.html#:~:text=Pel%C3%A9%20e%20Xuxa%20ficaram%20juntos,do%20mesmo%20grupo%20da%20revista)). Pelé, como mencionado, havia expressado reservas sobre essa mudança de emissora ([Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira](https://aventurasnahistoria.com.br/noticias/reportagem/xuxa-e-pele-o-relacionamento-que-ficou-cravado-na-historia-da-imprensa-brasileira.phtml#:~:text=,torcendo%20por%20mim%E2%80%9D%2C%20acrescentou%20Xuxa)), mas sem sucesso em demovê-la. Com a benção do dono da Manchete, Adolpho Bloch (que a tratava “como filha” e apoiou seu crescimento) ([Xuxa está em paz - revista piauí](https://piaui.folha.uol.com.br/materia/xuxa-esta-em-paz/#:~:text=match%20at%20L405%20Manchete%20e,%E2%80%99%E2%80%9D)) ([Xuxa está em paz - revista piauí](https://piaui.folha.uol.com.br/materia/xuxa-esta-em-paz/#:~:text=Manchete%20e%20fui%20embora%E2%80%9D%2C%20recorda,%E2%80%99%E2%80%9D)), Xuxa partiu para a Globo levando sua diretora Marlene Mattos, e estreou em junho de 1986 o programa que a consagraria definitivamente. É importante notar que, ao ingressar na Globo, Xuxa já não dependia mais da aura de “namorada do Pelé” – ela havia se firmado como apresentadora de sucesso por méritos próprios. Ainda assim, **o relacionamento anterior continuou a ser parte de sua imagem pública**: a mídia noticiou a mudança destacando que a namorada de Pelé chegara à Globo, e muitos espectadores tinham curiosidade sobre aquela moça cuja fama começara nos braços do ídolo do futebol. Em resumo, o namoro ajudou Xuxa a conquistar o primeiro grande espaço na TV (na Manchete), fornecendo-lhe exposição e credibilidade iniciais, enquanto sua ida para a Globo foi impulsionada principalmente pelo desempenho no *Clube da Criança* – algo que o prestígio conquistado durante o relacionamento tornou possível em primeiro lugar. ## Percepção da Mídia e do Público sobre o Casal e a Imagem de Xuxa Durante os anos de namoro, Pelé e Xuxa foram um prato cheio para a imprensa e objeto de variadas opiniões do público. De um lado, eram celebrados como **“casal perfeito na mídia”**, aparecendo sorridentes em eventos e capas, o que projetava uma imagem glamourosa e apaixonada ([Pelé viveu com Xuxa um namoro intenso afetado por fofocas e indiscrições](https://www.terra.com.br/diversao/gente/pele-viveu-com-xuxa-um-namoro-intenso-afetado-por-fofocas-e-indiscricoes,0c075d1a6be75f53536ad3b70e8e4a01iavthiai.html#:~:text=Image%3A%20Pel%C3%A9%20e%20Xuxa%20na,perfeito%20na%20m%C3%ADdia%2C%20mas%20com)). Xuxa era frequentemente retratada como a bela jovem humilde que havia conquistado o coração do "rei", uma narrativa de conto de fadas que agradava muitos fãs. Pessoas próximas diziam na época: *“Nossa, como ela está apaixonada, como ela está de quatro pelo Pelé”*, segundo relembrou a própria Xuxa, indicando que sua dedicação ao namorado era visível e comentada ([Xuxa e Pelé: um romance que se tornou inesquecível... | VEJA](https://veja.abril.com.br/coluna/veja-gente/xuxa-e-pele-um-romance-que-se-tornou-inesquecivel-para-os-dois/#:~:text=Ao%20participar%20de%20uma%20live,de%20quatro%20para%20o%20Pel%C3%A9%27%E2%80%9D)). Essa percepção de autenticidade nos sentimentos ajudou a humanizar Xuxa aos olhos do público, diferenciando-a de estereótipos de *roupante* ou interesse calculado. Por outro lado, nem toda a atenção era positiva. **Houve murmúrios maldosos e preconceituosos nos bastidores**. Pelé e Xuxa formavam um casal interracial (ele negro, ela branca e bem mais jovem), o que, segundo a imprensa, **“gerava olhares de reprovação dos conservadores” e até comentários racistas proferidos pelas costas** ([Pelé viveu com Xuxa um namoro intenso afetado por fofocas e indiscrições](https://www.terra.com.br/diversao/gente/pele-viveu-com-xuxa-um-namoro-intenso-afetado-por-fofocas-e-indiscricoes,0c075d1a6be75f53536ad3b70e8e4a01iavthiai.html#:~:text=Os%20dois%20eram%20perseguidos%20por,Mas%20nem%20tudo%20era%20agrad%C3%A1vel)). Além disso, alguns duvidavam das intenções de Xuxa no relacionamento, insinuando que ela buscava ascensão social por meio de Pelé. Termos pejorativos como *“maria-chuteira”* (gíria para mulheres que namoram jogadores em busca de status) e *“alpinista social”* chegaram a ser associados a Xuxa por fofoqueiros da época ([Pelé viveu com Xuxa um namoro intenso afetado por fofocas e indiscrições](https://www.terra.com.br/diversao/gente/pele-viveu-com-xuxa-um-namoro-intenso-afetado-por-fofocas-e-indiscricoes,0c075d1a6be75f53536ad3b70e8e4a01iavthiai.html#:~:text=olhares%20de%20reprova%C3%A7%C3%A3o%20dos%20conservadores)). Essa desconfiança lançava sombra sobre a imagem dela, pintando-a, aos olhos de alguns, como oportunista em vez de namorada dedicada. Xuxa teve de lidar com esse tipo de insinuação ao longo do namoro, buscando provar que seu amor era verdadeiro e que ela também tinha talentos e ambições próprias. A mídia impressa, em geral, manteve uma postura favorável ao casal, explorando o romance como algo encantador. Mas não deixou de reportar as turbulências: sabia-se, por exemplo, das **frequentes traições de Pelé**, que Xuxa anos depois revelou ter suportado calada na época ([Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira](https://aventurasnahistoria.com.br/noticias/reportagem/xuxa-e-pele-o-relacionamento-que-ficou-cravado-na-historia-da-imprensa-brasileira.phtml#:~:text=Por%20causa%20do%20companheiro%2C%20tamb%C3%A9m,que%20n%C3%A3o%20era%20o%20meu)) ([Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira](https://aventurasnahistoria.com.br/noticias/reportagem/xuxa-e-pele-o-relacionamento-que-ficou-cravado-na-historia-da-imprensa-brasileira.phtml#:~:text=Apesar%20dos%20problemas%20corriqueiros%20com,Era%20uma%20situa%C3%A7%C3%A3o%20esquisita%E2%80%9D)). Essas infidelidades eram rumores correntes nos círculos de fofoca, embora Xuxa raramente comentasse publicamente enquanto estava com Pelé. O público, portanto, via um casal bonito e famoso, mas também acompanhava as especulações de crises e reconciliações pelos noticiários de celebridades. Cada aparição pública deles – fosse em um jogo de futebol, um evento beneficente ou nos camarotes do carnaval – era dissecada pelos repórteres, e cada declaração (ou silêncio) alimentava interpretações sobre o estado do relacionamento e sobre quem era Xuxa por trás da fama. No saldo final, o namoro com Pelé influenciou profundamente a **imagem pública de Xuxa**. Inicialmente marcada como “a namorada do Rei” – posição que trazia tanto admiração quanto inveja – Xuxa soube aproveitar a visibilidade para mostrar carisma e trabalho, transformando-se em uma estrela por direito próprio. Ao se tornar apresentadora infantil de sucesso ainda durante o namoro, ela começou a dissociar sua imagem da de Pelé, provando que podia ser mais do que um apêndice de um astro do esporte. Quando o relacionamento terminou em 1986, Xuxa emergiu não caída em desgraça, mas sim pronta para reinar sozinha na TV. A mídia continuou a mencioná-la em referência a Pelé por algum tempo (era inevitável, dado o quão famoso o casal fora), mas cada vez mais o público passou a enxergá-la principalmente como a **“Rainha dos Baixinhos”**, a figura alegre das manhãs na TV Globo. Em entrevistas posteriores, Xuxa admitiu ter sentimentos mistos ao lembrar dessa fase: ela se ressentiu, por exemplo, de Pelé ter classificado o que viveram como *“uma amizade colorida”* em vez de namoro sério ([Pelé e Xuxa: um estranho amor que durou seis anos - 29/12/2022 - Celebridades - F5](https://f5.folha.uol.com.br/celebridades/2022/12/pele-e-xuxa-o-estranho-amor-entre-o-rei-do-futebol-e-a-futura-rainha-dos-baixinhos.shtml#:~:text=Xuxa%20disse%20ter%20ficado%20magoada,N%C3%A3o%20fui%20avisada)) – frase do ex-jogador que a magoou e que veio a público muitos anos depois. Esse comentário retroativo de Pelé apenas reforçou o quanto a mídia e o público discutiram e dissecaram a natureza daquela relação. Em conclusão, a percepção do casal Xuxa e Pelé oscilou entre o encanto e a controvérsia, mas inegavelmente manteve Xuxa nos trending topics de sua época (para usar um termo atual). A jovem modelo gaúcha ganhou projeção, prestígio e também enfrentou julgamentos enquanto esteve com Pelé. Tudo isso moldou sua imagem – de **símbolo sexual e socialite em ascensão** a **profissional talentosa pronta para brilhar por conta própria**. O relacionamento forneceu-lhe a plataforma e a armadura mediática; coube a Xuxa transformar essa visibilidade em uma carreira sólida, o que ela fez com maestria ao se tornar uma das maiores apresentadoras da história da TV brasileira. **Fontes:** Entrevistas e depoimentos de Xuxa Meneghel (inclusive do livro *Memórias*, 2020), reportagens da época em revistas como *Manchete*, colunas sociais e jornais (compiladas em repositórios atuais), e biografias e retrospectivas sobre ambos os envolvidos ([A história da foto de revista que gerou o namoro de Pelé e Xuxa](https://www.terra.com.br/diversao/gente/a-historia-da-foto-de-revista-que-gerou-o-namoro-de-pele-e-xuxa,c5106b23301f6f0e7c03f38cdf9eb1a06kopa9ho.html#:~:text=Um%20tempo%20depois%2C%20quando%20a,se%20nacionalmente%20famosa)) ([Pelé viveu com Xuxa um namoro intenso afetado por fofocas e indiscrições](https://www.terra.com.br/diversao/gente/pele-viveu-com-xuxa-um-namoro-intenso-afetado-por-fofocas-e-indiscricoes,0c075d1a6be75f53536ad3b70e8e4a01iavthiai.html#:~:text=Morte%20s%C3%BAbita%20encerra%20fase%20feliz,vida%20da%20atriz%20Marcia%20Manfredini)) ([Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira](https://aventurasnahistoria.com.br/noticias/reportagem/xuxa-e-pele-o-relacionamento-que-ficou-cravado-na-historia-da-imprensa-brasileira.phtml#:~:text=,torcendo%20por%20mim%E2%80%9D%2C%20acrescentou%20Xuxa)) ([Xuxa e Pelé: um romance que se tornou inesquecível... | VEJA](https://veja.abril.com.br/coluna/veja-gente/xuxa-e-pele-um-romance-que-se-tornou-inesquecivel-para-os-dois/#:~:text=Um%20dos%20romances%20mais%20comentados,manchetes%20e%20revistas%20de%20fofoca)), entre outras. Essas fontes confirmam o papel catalisador que o namoro com Pelé teve nos primeiros passos da trajetória de Xuxa, bem como os desafios e oportunidades que surgiram dessa intensa exposição pública. @ 6b3780ef:221416c8
2025-03-26 18:42:00This workshop will guide you through exploring the concepts behind MCP servers and how to deploy them as DVMs in Nostr using DVMCP. By the end, you'll understand how these systems work together and be able to create your own deployments. ## Understanding MCP Systems MCP (Model Context Protocol) systems consist of two main components that work together: 1. **MCP Server**: The heart of the system that exposes tools, which you can access via the `.listTools()` method. 2. **MCP Client**: The interface that connects to the MCP server and lets you use the tools it offers. These servers and clients can communicate using different transport methods: - **Standard I/O (stdio)**: A simple local connection method when your server and client are on the same machine. - **Server-Sent Events (SSE)**: Uses HTTP to create a communication channel. For this workshop, we'll use stdio to deploy our server. DVMCP will act as a bridge, connecting to your MCP server as an MCP client, and exposing its tools as a DVM that anyone can call from Nostr. ## Creating (or Finding) an MCP Server Building an MCP server is simpler than you might think: 1. Create software in any programming language you're comfortable with. 2. Add an MCP library to expose your server's MCP interface. 3. Create an API that wraps around your software's functionality. Once your server is ready, an MCP client can connect, for example, with `bun index.js`, and then call `.listTools()` to discover what your server can do. This pattern, known as reflection, makes Nostr DVMs and MCP a perfect match since both use JSON, and DVMs can announce and call tools, effectively becoming an MCP proxy. Alternatively, you can use one of the many existing MCP servers available in various repositories. For more information about mcp and how to build mcp servers you can visit https://modelcontextprotocol.io/ ## Setting Up the Workshop Let's get hands-on: First, to follow this workshop you will need Bun. Install it from https://bun.sh/. For Linux and macOS, you can use the installation script: ``` curl -fsSL https://bun.sh/install | bash ``` 1. **Choose your MCP server**: You can either create one or use an existing one. 2. **Inspect your server** using the MCP inspector tool: ```bash npx @modelcontextprotocol/inspector build/index.js arg1 arg2 ``` This will: - Launch a client UI (default: http://localhost:5173) - Start an MCP proxy server (default: port 3000) - Pass any additional arguments directly to your server 3. **Use the inspector**: Open the client UI in your browser to connect with your server, list available tools, and test its functionality. ## Deploying with DVMCP Now for the exciting part – making your MCP server available to everyone on Nostr: 1. Navigate to your MCP server directory. 2. Run without installing (quickest way): ``` npx @dvmcp/bridge ``` 3. Or install globally for regular use: ``` npm install -g @dvmcp/bridge # or bun install -g @dvmcp/bridge ``` Then run using: ```bash dvmcp-bridge ``` This will guide you through creating the necessary configuration. Watch the console logs to confirm successful setup – you'll see your public key and process information, or any issues that need addressing. For the configuration, you can set the relay as `wss://relay.dvmcp.fun` , or use any other of your preference ## Testing and Integration 1. **Visit [dvmcp.fun](https://dvmcp.fun)** to see your DVM announcement. 2. Call your tools and watch the responses come back. For production use, consider running dvmcp-bridge as a system service or creating a container for greater reliability and uptime. ## Integrating with LLM Clients You can also integrate your DVMCP deployment with LLM clients using the discovery package: 1. Install and use the `@dvmcp/discovery` package: ```bash npx @dvmcp/discovery ``` 2. This package acts as an MCP server for your LLM system by: - Connecting to configured Nostr relays - Discovering tools from DVMCP servers - Making them available to your LLM applications 3. Connect to specific servers or providers using these flags: ```bash # Connect to all DVMCP servers from a provider npx @dvmcp/discovery --provider npub1... # Connect to a specific DVMCP server npx @dvmcp/discovery --server naddr1... ``` Using these flags, you wouldn't need a configuration file. You can find these commands and Claude desktop configuration already prepared for copy and paste at [dvmcp.fun](https://dvmcp.fun). This feature lets you connect to any DVMCP server using Nostr and integrate it into your client, either as a DVM or in LLM-powered applications. ## Final thoughts If you've followed this workshop, you now have an MCP server deployed as a Nostr DVM. This means that local resources from the system where the MCP server is running can be accessed through Nostr in a decentralized manner. This capability is powerful and opens up numerous possibilities and opportunities for fun. You can use this setup for various use cases, including in a controlled/local environment. For instance, you can deploy a relay in your local network that's only accessible within it, exposing all your local MCP servers to anyone connected to the network. This setup can act as a hub for communication between different systems, which could be particularly interesting for applications in home automation or other fields. The potential applications are limitless. However, it's important to keep in mind that there are security concerns when exposing local resources publicly. You should be mindful of these risks and prioritize security when creating and deploying your MCP servers on Nostr. Finally, these are new ideas, and the software is still under development. If you have any feedback, please refer to the GitHub repository to report issues or collaborate. DVMCP also has a Signal group you can join. Additionally, you can engage with the community on Nostr using the #dvmcp hashtag. ## Useful Resources - **Official Documentation**: - Model Context Protocol: [modelcontextprotocol.org](https://modelcontextprotocol.org) - DVMCP.fun: [dvmcp.fun](https://dvmcp.fun) - **Source Code and Development**: - DVMCP: [github.com/gzuuus/dvmcp](https://github.com/gzuuus/dvmcp) - DVMCP.fun: [github.com/gzuuus/dvmcpfun](https://github.com/gzuuus/dvmcpfun) - **MCP Servers and Clients**: - Smithery AI: [smithery.ai](https://smithery.ai) - MCP.so: [mcp.so](https://mcp.so) - Glama AI MCP Servers: [glama.ai/mcp/servers](https://glama.ai/mcp/servers) - [Signal group](https://signal.group/#CjQKIOgvfFJf8ZFZ1SsMx7teFqNF73sZ9Elaj_v5i6RSjDHmEhA5v69L4_l2dhQfwAm2SFGD) Happy building!
@ 6b3780ef:221416c8
2025-03-26 18:42:00This workshop will guide you through exploring the concepts behind MCP servers and how to deploy them as DVMs in Nostr using DVMCP. By the end, you'll understand how these systems work together and be able to create your own deployments. ## Understanding MCP Systems MCP (Model Context Protocol) systems consist of two main components that work together: 1. **MCP Server**: The heart of the system that exposes tools, which you can access via the `.listTools()` method. 2. **MCP Client**: The interface that connects to the MCP server and lets you use the tools it offers. These servers and clients can communicate using different transport methods: - **Standard I/O (stdio)**: A simple local connection method when your server and client are on the same machine. - **Server-Sent Events (SSE)**: Uses HTTP to create a communication channel. For this workshop, we'll use stdio to deploy our server. DVMCP will act as a bridge, connecting to your MCP server as an MCP client, and exposing its tools as a DVM that anyone can call from Nostr. ## Creating (or Finding) an MCP Server Building an MCP server is simpler than you might think: 1. Create software in any programming language you're comfortable with. 2. Add an MCP library to expose your server's MCP interface. 3. Create an API that wraps around your software's functionality. Once your server is ready, an MCP client can connect, for example, with `bun index.js`, and then call `.listTools()` to discover what your server can do. This pattern, known as reflection, makes Nostr DVMs and MCP a perfect match since both use JSON, and DVMs can announce and call tools, effectively becoming an MCP proxy. Alternatively, you can use one of the many existing MCP servers available in various repositories. For more information about mcp and how to build mcp servers you can visit https://modelcontextprotocol.io/ ## Setting Up the Workshop Let's get hands-on: First, to follow this workshop you will need Bun. Install it from https://bun.sh/. For Linux and macOS, you can use the installation script: ``` curl -fsSL https://bun.sh/install | bash ``` 1. **Choose your MCP server**: You can either create one or use an existing one. 2. **Inspect your server** using the MCP inspector tool: ```bash npx @modelcontextprotocol/inspector build/index.js arg1 arg2 ``` This will: - Launch a client UI (default: http://localhost:5173) - Start an MCP proxy server (default: port 3000) - Pass any additional arguments directly to your server 3. **Use the inspector**: Open the client UI in your browser to connect with your server, list available tools, and test its functionality. ## Deploying with DVMCP Now for the exciting part – making your MCP server available to everyone on Nostr: 1. Navigate to your MCP server directory. 2. Run without installing (quickest way): ``` npx @dvmcp/bridge ``` 3. Or install globally for regular use: ``` npm install -g @dvmcp/bridge # or bun install -g @dvmcp/bridge ``` Then run using: ```bash dvmcp-bridge ``` This will guide you through creating the necessary configuration. Watch the console logs to confirm successful setup – you'll see your public key and process information, or any issues that need addressing. For the configuration, you can set the relay as `wss://relay.dvmcp.fun` , or use any other of your preference ## Testing and Integration 1. **Visit [dvmcp.fun](https://dvmcp.fun)** to see your DVM announcement. 2. Call your tools and watch the responses come back. For production use, consider running dvmcp-bridge as a system service or creating a container for greater reliability and uptime. ## Integrating with LLM Clients You can also integrate your DVMCP deployment with LLM clients using the discovery package: 1. Install and use the `@dvmcp/discovery` package: ```bash npx @dvmcp/discovery ``` 2. This package acts as an MCP server for your LLM system by: - Connecting to configured Nostr relays - Discovering tools from DVMCP servers - Making them available to your LLM applications 3. Connect to specific servers or providers using these flags: ```bash # Connect to all DVMCP servers from a provider npx @dvmcp/discovery --provider npub1... # Connect to a specific DVMCP server npx @dvmcp/discovery --server naddr1... ``` Using these flags, you wouldn't need a configuration file. You can find these commands and Claude desktop configuration already prepared for copy and paste at [dvmcp.fun](https://dvmcp.fun). This feature lets you connect to any DVMCP server using Nostr and integrate it into your client, either as a DVM or in LLM-powered applications. ## Final thoughts If you've followed this workshop, you now have an MCP server deployed as a Nostr DVM. This means that local resources from the system where the MCP server is running can be accessed through Nostr in a decentralized manner. This capability is powerful and opens up numerous possibilities and opportunities for fun. You can use this setup for various use cases, including in a controlled/local environment. For instance, you can deploy a relay in your local network that's only accessible within it, exposing all your local MCP servers to anyone connected to the network. This setup can act as a hub for communication between different systems, which could be particularly interesting for applications in home automation or other fields. The potential applications are limitless. However, it's important to keep in mind that there are security concerns when exposing local resources publicly. You should be mindful of these risks and prioritize security when creating and deploying your MCP servers on Nostr. Finally, these are new ideas, and the software is still under development. If you have any feedback, please refer to the GitHub repository to report issues or collaborate. DVMCP also has a Signal group you can join. Additionally, you can engage with the community on Nostr using the #dvmcp hashtag. ## Useful Resources - **Official Documentation**: - Model Context Protocol: [modelcontextprotocol.org](https://modelcontextprotocol.org) - DVMCP.fun: [dvmcp.fun](https://dvmcp.fun) - **Source Code and Development**: - DVMCP: [github.com/gzuuus/dvmcp](https://github.com/gzuuus/dvmcp) - DVMCP.fun: [github.com/gzuuus/dvmcpfun](https://github.com/gzuuus/dvmcpfun) - **MCP Servers and Clients**: - Smithery AI: [smithery.ai](https://smithery.ai) - MCP.so: [mcp.so](https://mcp.so) - Glama AI MCP Servers: [glama.ai/mcp/servers](https://glama.ai/mcp/servers) - [Signal group](https://signal.group/#CjQKIOgvfFJf8ZFZ1SsMx7teFqNF73sZ9Elaj_v5i6RSjDHmEhA5v69L4_l2dhQfwAm2SFGD) Happy building! @ d5c3d063:4d1159b3
2025-04-05 00:51:55📙 เทคนิคตั้งคำถามนโยบาย จากหนังสือ “เศรษฐศาสตร์เล่มเดียวจบ” #EIOL ผมอยากแบ่งปันวิธีง่าย ๆ ในการนำแนวคิดจากหนังสือมาใช้ เพื่อ “ตั้งคำถามกับนโยบาย” ที่เราเจอในชีวิตประจำวัน ไม่ต้องเป็นนักเศรษฐศาสตร์ก็ใช้ได้ เพราะนี่คือทักษะของ “คนที่เลือกจะคิดเอง” กับ 3 เทคนิค คิดแบบนักเศรษฐศาสตร์ เวลารัฐออกนโยบาย 1. เข้าใจ “วิธีคิด” ที่หนังสือพยายามสอนเรา ใน Economics in One Lesson ของ Henry Hazlitt เขาไม่ได้ให้สูตรลัด แต่ให้ “เลนส์” สำหรับมองระบบเศรษฐกิจให้ชัดขึ้น หลักคิดสำคัญคือ - อย่าหยุดแค่สิ่งที่เรามองเห็นทันที - ให้ถามต่อว่ามี “ต้นทุนที่ซ่อนอยู่” ไหม -มีใครได้รับผลกระทบ โดยไม่มีใครพูดถึงหรือเปล่า 2. เลือกนโยบายใกล้ตัวที่เจอในข่าว เราไม่ต้องเป็นนักวิชาการก็ทำได้ แค่ถามตัวเองง่าย ๆ - แจกเงิน = แจกให้ใคร แล้วใครจ่าย - ตรึงราคาน้ำมัน = ดีตอนนี้กระทบอะไรในระยะยาว - รถไฟฟ้าฟรี = ฟรีจริงดิ หรือมีคนจ่ายแทนเราอยู่ ทุกนโยบายคือบทเรียน ถ้าเรากล้าตั้งคำถาม 3. ตั้งคำถามกับนโยบาย อย่ารอให้รัฐสรุปให้คุณ ลองใช้ 3 คำถามนี้กับทุกนโยบายที่คุณเจอ - ใครได้ประโยชน์ทันที - ใครต้องจ่าย หรือเสียโอกาสบางอย่างไป - แล้วในระยะยาว นโยบายนี้จะพาเราไปทางไหน บางครั้งคำตอบไม่ได้อยู่ในข่าว หรือโพสต์สวย ๆ แต่มันซ่อนอยู่ใน “สิ่งที่ไม่มีใครอยากพูดถึง” . . ตัวอย่าง เมื่อรัฐบาลประกาศจะแจกเงิน Digital Wallet คนละ 10,000 บาท สิ่งที่คนส่วนใหญ่มองเห็นคือ “ความช่วยเหลือ” และ “การกระตุ้นเศรษฐกิจ” แต่ถ้าลองมองผ่านเลนส์ของ Hazlitt นี่คือคำถามที่ไม่ค่อยมีใครถาม - เงินที่ใช้แจกมาจากไหน ภาษีของเราหรือหนี้ที่ลูกหลานเราต้องใช้คืนในอนาคต - มันช่วยให้คนอยู่รอด หรือช่วยให้คนลุกขึ้นยืนได้ด้วยตัวเองในระยะยาวจริงไหม - คนที่ไม่ได้อยู่ในระบบดิจิทัล จะถูกทิ้งไว้ข้างหลังไหม - นี่คือการวางรากฐานระยะยาวหรือแค่การเร่งใช้จ่ายเพื่อประชานิยมระยะสั้น . หนังสือที่ดีจะไม่แค่ให้ข้อมูล แต่ให้ “มุมมองใหม่” และมุมมองนี้เอง ที่ช่วยให้เรา “ไม่ตกหลุมกับนโยบายที่ดูดีแต่ไม่ยั่งยืน” . . ต่อไปถ้าเจอนโยบายที่ดูดี ลองหยิบคำถาม 3 ข้อนี้ขึ้นมาใช้ แล้วดูว่าคุณเห็นอะไรที่คนอื่นอาจมองข้าม เพราะเศรษฐศาสตร์ที่ดี…เริ่มจาก “การสงสัยในสิ่งที่ทุกคนปรบมือให้” ถ้าบทความนี้ทำให้คุณ “มองเห็นสิ่งที่เคยมองข้าม” ลองแชร์ให้เพื่อนสักคนดูครับ เพราะเศรษฐศาสตร์ ไม่ได้เป็นแค่เรื่องของนักวิชาการ แต่มันคือเครื่องมือของคนธรรมดา... ที่อยากเข้าใจโลกให้ลึกขึ้นอีกนิด 🙃 #Siamstr
@ d5c3d063:4d1159b3
2025-04-05 00:51:55📙 เทคนิคตั้งคำถามนโยบาย จากหนังสือ “เศรษฐศาสตร์เล่มเดียวจบ” #EIOL ผมอยากแบ่งปันวิธีง่าย ๆ ในการนำแนวคิดจากหนังสือมาใช้ เพื่อ “ตั้งคำถามกับนโยบาย” ที่เราเจอในชีวิตประจำวัน ไม่ต้องเป็นนักเศรษฐศาสตร์ก็ใช้ได้ เพราะนี่คือทักษะของ “คนที่เลือกจะคิดเอง” กับ 3 เทคนิค คิดแบบนักเศรษฐศาสตร์ เวลารัฐออกนโยบาย 1. เข้าใจ “วิธีคิด” ที่หนังสือพยายามสอนเรา ใน Economics in One Lesson ของ Henry Hazlitt เขาไม่ได้ให้สูตรลัด แต่ให้ “เลนส์” สำหรับมองระบบเศรษฐกิจให้ชัดขึ้น หลักคิดสำคัญคือ - อย่าหยุดแค่สิ่งที่เรามองเห็นทันที - ให้ถามต่อว่ามี “ต้นทุนที่ซ่อนอยู่” ไหม -มีใครได้รับผลกระทบ โดยไม่มีใครพูดถึงหรือเปล่า 2. เลือกนโยบายใกล้ตัวที่เจอในข่าว เราไม่ต้องเป็นนักวิชาการก็ทำได้ แค่ถามตัวเองง่าย ๆ - แจกเงิน = แจกให้ใคร แล้วใครจ่าย - ตรึงราคาน้ำมัน = ดีตอนนี้กระทบอะไรในระยะยาว - รถไฟฟ้าฟรี = ฟรีจริงดิ หรือมีคนจ่ายแทนเราอยู่ ทุกนโยบายคือบทเรียน ถ้าเรากล้าตั้งคำถาม 3. ตั้งคำถามกับนโยบาย อย่ารอให้รัฐสรุปให้คุณ ลองใช้ 3 คำถามนี้กับทุกนโยบายที่คุณเจอ - ใครได้ประโยชน์ทันที - ใครต้องจ่าย หรือเสียโอกาสบางอย่างไป - แล้วในระยะยาว นโยบายนี้จะพาเราไปทางไหน บางครั้งคำตอบไม่ได้อยู่ในข่าว หรือโพสต์สวย ๆ แต่มันซ่อนอยู่ใน “สิ่งที่ไม่มีใครอยากพูดถึง” . . ตัวอย่าง เมื่อรัฐบาลประกาศจะแจกเงิน Digital Wallet คนละ 10,000 บาท สิ่งที่คนส่วนใหญ่มองเห็นคือ “ความช่วยเหลือ” และ “การกระตุ้นเศรษฐกิจ” แต่ถ้าลองมองผ่านเลนส์ของ Hazlitt นี่คือคำถามที่ไม่ค่อยมีใครถาม - เงินที่ใช้แจกมาจากไหน ภาษีของเราหรือหนี้ที่ลูกหลานเราต้องใช้คืนในอนาคต - มันช่วยให้คนอยู่รอด หรือช่วยให้คนลุกขึ้นยืนได้ด้วยตัวเองในระยะยาวจริงไหม - คนที่ไม่ได้อยู่ในระบบดิจิทัล จะถูกทิ้งไว้ข้างหลังไหม - นี่คือการวางรากฐานระยะยาวหรือแค่การเร่งใช้จ่ายเพื่อประชานิยมระยะสั้น . หนังสือที่ดีจะไม่แค่ให้ข้อมูล แต่ให้ “มุมมองใหม่” และมุมมองนี้เอง ที่ช่วยให้เรา “ไม่ตกหลุมกับนโยบายที่ดูดีแต่ไม่ยั่งยืน” . . ต่อไปถ้าเจอนโยบายที่ดูดี ลองหยิบคำถาม 3 ข้อนี้ขึ้นมาใช้ แล้วดูว่าคุณเห็นอะไรที่คนอื่นอาจมองข้าม เพราะเศรษฐศาสตร์ที่ดี…เริ่มจาก “การสงสัยในสิ่งที่ทุกคนปรบมือให้” ถ้าบทความนี้ทำให้คุณ “มองเห็นสิ่งที่เคยมองข้าม” ลองแชร์ให้เพื่อนสักคนดูครับ เพราะเศรษฐศาสตร์ ไม่ได้เป็นแค่เรื่องของนักวิชาการ แต่มันคือเครื่องมือของคนธรรมดา... ที่อยากเข้าใจโลกให้ลึกขึ้นอีกนิด 🙃 #Siamstr @ 81aae9c5:267f2001
2025-04-04 19:06:05# Hello wordl publishing from the new cli tool thingy
@ 81aae9c5:267f2001
2025-04-04 19:06:05# Hello wordl publishing from the new cli tool thingy @ a5142938:0ef19da3
2025-04-04 14:49:53**Contribute to enrich the site!** Each contribution helps improve this site by supporting the listing of natural alternatives. ### 💡 What Counts as a Contribution? A contribution can be: 📝 Proposing a new entry, by providing its initial information. Each piece of information added (name, link, category, etc.) is considered a contribution: - [Add a product](https://www.origin-nature.com/post/8adj-i_hk0gtzp_ul9k17/) - [Add a brand](https://www.origin-nature.com/post/unjmwarjg7ojb9uwantvt/) 📝 Adding or modifying information in an existing entry. Each piece of information added or removed is considered a contribution. ### ✅ Contribution validation Contributions are reviewed by the core team. A contribution is validated when the information provided is submitted for the first time (the earliest comment is taken into account) and can be verified. Once validated, contributions are counted and eligible for rewards. 👉 [Learn more about rewards](https://www.origin-nature.com/post/xz20q6pw42fd9ijaewnn6/) --- This article is published on [origin-nature.com](https://www.origin-nature.com/post/laf_xjasf4kgunxvozhkm/) 🌐 [Voir cet article en français](https://www.origine-nature.com/post/26bj5f7bwyps6ecp5v62t/)
@ a5142938:0ef19da3
2025-04-04 14:49:53**Contribute to enrich the site!** Each contribution helps improve this site by supporting the listing of natural alternatives. ### 💡 What Counts as a Contribution? A contribution can be: 📝 Proposing a new entry, by providing its initial information. Each piece of information added (name, link, category, etc.) is considered a contribution: - [Add a product](https://www.origin-nature.com/post/8adj-i_hk0gtzp_ul9k17/) - [Add a brand](https://www.origin-nature.com/post/unjmwarjg7ojb9uwantvt/) 📝 Adding or modifying information in an existing entry. Each piece of information added or removed is considered a contribution. ### ✅ Contribution validation Contributions are reviewed by the core team. A contribution is validated when the information provided is submitted for the first time (the earliest comment is taken into account) and can be verified. Once validated, contributions are counted and eligible for rewards. 👉 [Learn more about rewards](https://www.origin-nature.com/post/xz20q6pw42fd9ijaewnn6/) --- This article is published on [origin-nature.com](https://www.origin-nature.com/post/laf_xjasf4kgunxvozhkm/) 🌐 [Voir cet article en français](https://www.origine-nature.com/post/26bj5f7bwyps6ecp5v62t/) @ 57d1a264:69f1fee1
2025-03-26 08:45:13> I was curious to see how Stacker.News domain and website contents scored from a SEO (Search Engine Optimization) perspective. Here what Semrush nows about SN. But first have alook at the Page Performance Score on Google (Detailled report available [here](https://pagespeed.web.dev/analysis/https-stacker-news/pjnc9jgscy?form_factor=mobile)). **Performance** and **Accessibility** looks have really low score! | Desktop | Mobile | |---|---| |  |  | |  |  | Now let's see what Semrush knows. # Analytics General view on your metrics and performance trend compared to last 30 days.   See estimations of stacker.news's desktop and mobile traffic based on Semrush’s proprietary AI and machine learning algorithms, petabytes of clickstream data, and Big Data technologies.  Distribution of SN's organic traffic and keywords by country. The Organic Traffic graph shows changes in the amount of estimated organic and paid traffic driven to the SN analyzed domain over time.  | Organic Search | Backlinks Analytics | |---|---| | |  | | Position Changes Trend | Top Page Changes | |---|---| | |  | |This trend allows you to monitor organic traffic changes, as well as improved and declined positions.| Top pages with the biggest traffic changes over the last 28 days. |  # Competitors  The Competitive Positioning Map shows the strengths and weaknesses of SN competitive domains' presence in organic search results. Data visualizations are based on the domain's organic traffic and the number of keywords that they are ranking for in Google's top 20 organic search results. The larger the circle, the more visibility a domain has. Below, a list of domains an analyzed domain is competing against in Google's top 20 organic search results.  # Referring Domains   # Daily Stats | Organic Traffic | Organic Keywords | Backlinks | |---|---|---| | 976 | 15.9K | 126K | | `-41.87%` | `-16.4%` | `-1.62%` | ### 📝 Traffic Drop Traffic downturn detected! It appears SN domain experienced a traffic drop of 633 in the last 28 days. Take a closer look at these pages with significant traffic decline and explore areas for potential improvement. Here are the pages taking the biggest hits: - https://stacker.news/items/723989 ⬇️ -15 - https://stacker.news/items/919813 ⬇️ -12 - https://stacker.news/items/783355 ⬇️ -5 ### 📉 Decreased Authority Score Uh-oh! Your Authority score has dropped from 26 to 25. Don't worry, we're here to assist you. Check out the new/lost backlinks in the Backlink Analytics tool to uncover insights on how to boost your authority. ### 🌟 New Keywords Opportunity Alert! Targeting these keywords could help you increase organic traffic quickly and efficiently. We've found some low-hanging fruits for you! Take a look at these keywords: - nitter.moomoo.me — Volume 70 - 0xchat — Volume 30 - amethyst nostr — Volume 30 ### 🛠️ Broken Pages This could hurt the user experience and lead to a loss in organic traffic. Time to take action: amend those pages or set up redirects. Here below, few pages on SN domain that are either broken or not _crawlable_: - https://stacker.news/404 — 38 backlinks - https://stacker.news/api/capture/items/91154 — 24 backlinks - https://stacker.news/api/capture/items/91289 — 24 backlinks Dees this post give you some insights? Hope so, comment below if you have any SEO suggestion? Mine is to improve or keep an eye on Accessibility! One of the major issues I found is that SN does not have a `robots.txt`, a key simple text file that allow crawlers to read or not-read the website for indexing purposes. @k00b and @ek is that voluntary? Here are other basic info to improve the SEO score and for those of us that want to learn more: - Intro to Accessibility: https://www.w3.org/WAI/fundamentals/accessibility-intro/ - Design for Accessibility: https://www.w3.org/WAI/tips/designing/ - Web Accessibility Best Practices: https://www.freecodecamp.org/news/web-accessibility-best-practices/ originally posted at https://stacker.news/items/925433
@ 57d1a264:69f1fee1
2025-03-26 08:45:13> I was curious to see how Stacker.News domain and website contents scored from a SEO (Search Engine Optimization) perspective. Here what Semrush nows about SN. But first have alook at the Page Performance Score on Google (Detailled report available [here](https://pagespeed.web.dev/analysis/https-stacker-news/pjnc9jgscy?form_factor=mobile)). **Performance** and **Accessibility** looks have really low score! | Desktop | Mobile | |---|---| |  |  | |  |  | Now let's see what Semrush knows. # Analytics General view on your metrics and performance trend compared to last 30 days.   See estimations of stacker.news's desktop and mobile traffic based on Semrush’s proprietary AI and machine learning algorithms, petabytes of clickstream data, and Big Data technologies.  Distribution of SN's organic traffic and keywords by country. The Organic Traffic graph shows changes in the amount of estimated organic and paid traffic driven to the SN analyzed domain over time.  | Organic Search | Backlinks Analytics | |---|---| | |  | | Position Changes Trend | Top Page Changes | |---|---| | |  | |This trend allows you to monitor organic traffic changes, as well as improved and declined positions.| Top pages with the biggest traffic changes over the last 28 days. |  # Competitors  The Competitive Positioning Map shows the strengths and weaknesses of SN competitive domains' presence in organic search results. Data visualizations are based on the domain's organic traffic and the number of keywords that they are ranking for in Google's top 20 organic search results. The larger the circle, the more visibility a domain has. Below, a list of domains an analyzed domain is competing against in Google's top 20 organic search results.  # Referring Domains   # Daily Stats | Organic Traffic | Organic Keywords | Backlinks | |---|---|---| | 976 | 15.9K | 126K | | `-41.87%` | `-16.4%` | `-1.62%` | ### 📝 Traffic Drop Traffic downturn detected! It appears SN domain experienced a traffic drop of 633 in the last 28 days. Take a closer look at these pages with significant traffic decline and explore areas for potential improvement. Here are the pages taking the biggest hits: - https://stacker.news/items/723989 ⬇️ -15 - https://stacker.news/items/919813 ⬇️ -12 - https://stacker.news/items/783355 ⬇️ -5 ### 📉 Decreased Authority Score Uh-oh! Your Authority score has dropped from 26 to 25. Don't worry, we're here to assist you. Check out the new/lost backlinks in the Backlink Analytics tool to uncover insights on how to boost your authority. ### 🌟 New Keywords Opportunity Alert! Targeting these keywords could help you increase organic traffic quickly and efficiently. We've found some low-hanging fruits for you! Take a look at these keywords: - nitter.moomoo.me — Volume 70 - 0xchat — Volume 30 - amethyst nostr — Volume 30 ### 🛠️ Broken Pages This could hurt the user experience and lead to a loss in organic traffic. Time to take action: amend those pages or set up redirects. Here below, few pages on SN domain that are either broken or not _crawlable_: - https://stacker.news/404 — 38 backlinks - https://stacker.news/api/capture/items/91154 — 24 backlinks - https://stacker.news/api/capture/items/91289 — 24 backlinks Dees this post give you some insights? Hope so, comment below if you have any SEO suggestion? Mine is to improve or keep an eye on Accessibility! One of the major issues I found is that SN does not have a `robots.txt`, a key simple text file that allow crawlers to read or not-read the website for indexing purposes. @k00b and @ek is that voluntary? Here are other basic info to improve the SEO score and for those of us that want to learn more: - Intro to Accessibility: https://www.w3.org/WAI/fundamentals/accessibility-intro/ - Design for Accessibility: https://www.w3.org/WAI/tips/designing/ - Web Accessibility Best Practices: https://www.freecodecamp.org/news/web-accessibility-best-practices/ originally posted at https://stacker.news/items/925433 @ a5142938:0ef19da3
2025-04-04 10:08:42**Have you found a natural product? Share it here by commenting on this page!** This site only lists durable-use products and objects. Consumables (food, cosmetics, fuels, etc.) are not included. To be listed, the product must be made of natural materials. [Learn more about materials](https://www.origin-nature.com/post/pnco0inysorhojxvsyil3/) You can copy and paste the template below and fill in the information you have. Other contributors can complete any missing details. Each piece of information added (name, material, link, shipping area, etc.) and validated is considered a contribution. [Learn more about contributions](https://www.origin-nature.com/post/laf_xjasf4kgunxvozhkm/) ### New product - Product name : - Product image (link): - Short description: - Categories: - Brand or manufacturer: - Composition (materials used, including unknown elements): - Links to buy (and shipping area): - Other information (place of manufacture, certifications…): If you do not wish to log in, you can still contribute via [this form](https://www.origin-nature.com/post/pnef53sfo5jaejkactcib/). However, your contribution will not be counted towards a reward. [Learn more about rewards](https://www.origin-nature.com/post/xz20q6pw42fd9ijaewnn6/) --- This article is published on [origin-nature.com](https://www.origin-nature.com/) [Voir cet article en français](https://www.origine-nature.com/post/nicmc-eandjr_vcz4_hsr/)
@ a5142938:0ef19da3
2025-04-04 10:08:42**Have you found a natural product? Share it here by commenting on this page!** This site only lists durable-use products and objects. Consumables (food, cosmetics, fuels, etc.) are not included. To be listed, the product must be made of natural materials. [Learn more about materials](https://www.origin-nature.com/post/pnco0inysorhojxvsyil3/) You can copy and paste the template below and fill in the information you have. Other contributors can complete any missing details. Each piece of information added (name, material, link, shipping area, etc.) and validated is considered a contribution. [Learn more about contributions](https://www.origin-nature.com/post/laf_xjasf4kgunxvozhkm/) ### New product - Product name : - Product image (link): - Short description: - Categories: - Brand or manufacturer: - Composition (materials used, including unknown elements): - Links to buy (and shipping area): - Other information (place of manufacture, certifications…): If you do not wish to log in, you can still contribute via [this form](https://www.origin-nature.com/post/pnef53sfo5jaejkactcib/). However, your contribution will not be counted towards a reward. [Learn more about rewards](https://www.origin-nature.com/post/xz20q6pw42fd9ijaewnn6/) --- This article is published on [origin-nature.com](https://www.origin-nature.com/) [Voir cet article en français](https://www.origine-nature.com/post/nicmc-eandjr_vcz4_hsr/) @ 30876140:cffb1126
2025-03-26 04:58:21The portal is closing. The symphony comes to an end. Ballet, a dance of partners, A wish of hearts, Now closing its curtains. I foolishly sit Eagerly waiting For the circus to begin again, As crowds file past me, Chuckles and popcorn falling, Crushed under foot, I sit waiting For the show to carry on. But the night is now over, The laughs have been had, The music been heard, The dancers are gone now Into the nightbreeze chill. Yet still, I sit waiting, The empty chairs yawning, A cough, I start, could it be? Yet the lights now go out, And now without my sight I am truly alone in the theater. Yet still, I am waiting For the show to carry on, But I know that it won’t, Yet still, I am waiting. Never shall I leave For the show was too perfect And nothing perfect should ever be finished.
@ 30876140:cffb1126
2025-03-26 04:58:21The portal is closing. The symphony comes to an end. Ballet, a dance of partners, A wish of hearts, Now closing its curtains. I foolishly sit Eagerly waiting For the circus to begin again, As crowds file past me, Chuckles and popcorn falling, Crushed under foot, I sit waiting For the show to carry on. But the night is now over, The laughs have been had, The music been heard, The dancers are gone now Into the nightbreeze chill. Yet still, I sit waiting, The empty chairs yawning, A cough, I start, could it be? Yet the lights now go out, And now without my sight I am truly alone in the theater. Yet still, I am waiting For the show to carry on, But I know that it won’t, Yet still, I am waiting. Never shall I leave For the show was too perfect And nothing perfect should ever be finished. @ e4950c93:1b99eccd
2025-04-04 09:51:53**Vous connaissez une marque proposant des alternatives naturelles ? Partagez-la ici en commentant cette page !** Copiez-collez le modèle ci-dessous et remplissez les informations que vous avez. D’autres contribut-eur-rice-s pourront compléter les éléments manquants. Pour être référencée, la marque doit proposer une partie au moins de ses produits en matières naturelles. [En savoir plus sur les matières](https://www.origine-nature.com/post/ftjhuxe9mvxkhoedyz36i/) Chaque information ajoutée (nom, lien, catégorie, etc.) et validée est considérée comme une contribution. [En savoir plus sur les contributions](https://www.origine-nature.com/post/26bj5f7bwyps6ecp5v62t) ### Nouvelle marque ou fabricant - Nom de la marque : - Image représentant des produits de la marque (lien, idéalement depuis le site de la marque) : - Courte description : - Catégories de produits proposées : - Matières utilisées pour ses produits : - Site internet de la marque : - Autres informations (lieu de production, labels…) : Si vous ne souhaitez pas vous connecter, vous pouvez tout de même contribuer via [ce formulaire](https://www.origine-nature.com/post/qcp-smvj1v78_-7iceyrd/). Cependant, votre contribution ne sera pas comptabilisée pour une rétribution. [En savoir plus sur les rétributions](https://www.origine-nature.com/post/7hdgcdwt76dprobc9g_2f/) --- Cet article est publié sur [origine-nature.com](https://www.origine-nature.com/) [See this article in English](https://www.origin-nature.com/post/unjmwarjg7ojb9uwantvt/)
@ e4950c93:1b99eccd
2025-04-04 09:51:53**Vous connaissez une marque proposant des alternatives naturelles ? Partagez-la ici en commentant cette page !** Copiez-collez le modèle ci-dessous et remplissez les informations que vous avez. D’autres contribut-eur-rice-s pourront compléter les éléments manquants. Pour être référencée, la marque doit proposer une partie au moins de ses produits en matières naturelles. [En savoir plus sur les matières](https://www.origine-nature.com/post/ftjhuxe9mvxkhoedyz36i/) Chaque information ajoutée (nom, lien, catégorie, etc.) et validée est considérée comme une contribution. [En savoir plus sur les contributions](https://www.origine-nature.com/post/26bj5f7bwyps6ecp5v62t) ### Nouvelle marque ou fabricant - Nom de la marque : - Image représentant des produits de la marque (lien, idéalement depuis le site de la marque) : - Courte description : - Catégories de produits proposées : - Matières utilisées pour ses produits : - Site internet de la marque : - Autres informations (lieu de production, labels…) : Si vous ne souhaitez pas vous connecter, vous pouvez tout de même contribuer via [ce formulaire](https://www.origine-nature.com/post/qcp-smvj1v78_-7iceyrd/). Cependant, votre contribution ne sera pas comptabilisée pour une rétribution. [En savoir plus sur les rétributions](https://www.origine-nature.com/post/7hdgcdwt76dprobc9g_2f/) --- Cet article est publié sur [origine-nature.com](https://www.origine-nature.com/) [See this article in English](https://www.origin-nature.com/post/unjmwarjg7ojb9uwantvt/) @ 04c915da:3dfbecc9
2025-03-25 17:43:44One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice. A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases. Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy. Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest. Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
@ 04c915da:3dfbecc9
2025-03-25 17:43:44One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice. A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases. Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy. Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest. Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever. @ ecda4328:1278f072
2025-03-25 10:00:52**Kubernetes and Linux Swap: A Practical Perspective** After reviewing kernel documentation on swap management (e.g., [Linux Swap Management](https://www.kernel.org/doc/gorman/html/understand/understand014.html)), [KEP-2400 (Kubernetes Node Memory Swap Support)](https://github.com/kubernetes/enhancements/blob/master/keps/sig-node/2400-node-swap/README.md), and community discussions like [this post on ServerFault](https://serverfault.com/questions/881517/why-disable-swap-on-kubernetes), it's clear that the topic of swap usage in modern systems—especially Kubernetes environments—is nuanced and often contentious. Here's a practical synthesis of the discussion. --- ### The Rationale for Disabling Swap We disable SWAP on our Linux servers to ensure stable and predictable performance by relying on available RAM, avoiding the performance degradation and unnecessary I/O caused by SWAP usage. If an application runs out of memory, it’s usually due to insufficient RAM allocation or a memory leak, and enabling SWAP only worsens performance for other applications. It's more efficient to let a leaking app restart than to rely on SWAP to prevent OOM crashes. With modern platforms like Kubernetes, memory requests and limits are enforced, ensuring apps use only the RAM allocated to them, while avoiding overcommitment to prevent resource exhaustion. Additionally, disabling swap may protect data from **data remanence attacks**, where sensitive information could potentially be recovered from the swap space even after a process terminates. --- ### Theoretical Capability vs. Practical Deployment Linux provides a powerful and flexible memory subsystem. With proper tuning (e.g., swappiness, memory pinning, cgroups), it's technically possible to make swap usage efficient and targeted. Seasoned sysadmins often argue that disabling swap entirely is a lazy shortcut—an avoidance of learning how to use the tools properly. But Kubernetes is not a traditional system. It's an orchestrated environment that favors predictability, fail-fast behavior, and clear isolation between workloads. Within this model: - Memory **requests and limits** are declared explicitly. - The scheduler makes decisions based on RAM availability, not total virtual memory (RAM + swap). - Swap introduces **non-deterministic performance** characteristics that conflict with Kubernetes' goals. So while the kernel supports intelligent swap usage, Kubernetes **intentionally sidesteps** that complexity. --- ### Why Disable Swap in Kubernetes? 1. **Deterministic Failure > Degraded Performance**\ If a pod exceeds its memory allocation, it should fail fast — not get throttled into slow oblivion due to swap. This behavior surfaces bugs (like memory leaks or poor sizing) early. 2. **Transparency & Observability**\ With swap disabled, memory issues are clearer to diagnose. Swap obfuscates root causes and can make a healthy-looking node behave erratically. 3. **Performance Consistency**\ Swap causes I/O overhead. One noisy pod using swap can impact unrelated workloads on the same node — even if they’re within their resource limits. 4. **Kubernetes Doesn’t Manage Swap Well**\ Kubelet has historically lacked intelligence around swap. As of today, Kubernetes still doesn't support swap-aware scheduling or per-container swap control. 5. **Statelessness is the Norm**\ Most containerized workloads are designed to be ephemeral. Restarting a pod is usually preferable to letting it hang in a degraded state. --- ### "But Swap Can Be Useful..." Yes — for certain workloads (e.g., in-memory databases, caching layers, legacy systems), there may be valid reasons to keep swap enabled. In such cases, you'd need: - Fine-tuned `vm.swappiness` - Memory pinning and cgroup-based control - Swap-aware monitoring and alerting - Custom kubelet/systemd integration That's possible, but **not standard practice** — and for good reason. --- ### Future Considerations Recent Kubernetes releases have introduced [experimental swap support](https://kubernetes.io/blog/2023/08/24/swap-linux-beta/) via [KEP-2400](https://github.com/kubernetes/enhancements/blob/master/keps/sig-node/2400-node-swap/README.md). While this provides more flexibility for advanced use cases — particularly Burstable QoS pods on cgroupsv2 — swap remains disabled by default and is not generally recommended for production workloads unless carefully planned. The rationale outlined in this article remains applicable to most Kubernetes operators, especially in multi-tenant and performance-sensitive environments. Even the Kubernetes maintainers acknowledge the inherent trade-offs of enabling swap. As noted in [KEP-2400's Risks and Mitigations section](https://github.com/kubernetes/enhancements/blob/master/keps/sig-node/2400-node-swap/README.md), swap introduces unpredictability, can severely degrade performance compared to RAM, and complicates Kubernetes' resource accounting — increasing the risk of noisy neighbors and unexpected scheduling behavior. Some argue that with emerging technologies like **non-volatile memory** (e.g., Intel Optane/XPoint), swap may become viable again. These systems promise near-RAM speed with large capacity, offering hybrid memory models. But these are not widely deployed or supported in mainstream Kubernetes environments yet. --- ### Conclusion Disabling swap in Kubernetes is not a lazy hack — it’s a **strategic tradeoff**. It improves transparency, predictability, and system integrity in multi-tenant, containerized environments. While the kernel allows for more advanced configurations, Kubernetes intentionally simplifies memory handling for the sake of reliability. If we want to revisit swap usage, it should come with serious planning: proper instrumentation, swap-aware observability, and potentially upstream K8s improvements. Until then, **disabling swap remains the sane default**.
@ ecda4328:1278f072
2025-03-25 10:00:52**Kubernetes and Linux Swap: A Practical Perspective** After reviewing kernel documentation on swap management (e.g., [Linux Swap Management](https://www.kernel.org/doc/gorman/html/understand/understand014.html)), [KEP-2400 (Kubernetes Node Memory Swap Support)](https://github.com/kubernetes/enhancements/blob/master/keps/sig-node/2400-node-swap/README.md), and community discussions like [this post on ServerFault](https://serverfault.com/questions/881517/why-disable-swap-on-kubernetes), it's clear that the topic of swap usage in modern systems—especially Kubernetes environments—is nuanced and often contentious. Here's a practical synthesis of the discussion. --- ### The Rationale for Disabling Swap We disable SWAP on our Linux servers to ensure stable and predictable performance by relying on available RAM, avoiding the performance degradation and unnecessary I/O caused by SWAP usage. If an application runs out of memory, it’s usually due to insufficient RAM allocation or a memory leak, and enabling SWAP only worsens performance for other applications. It's more efficient to let a leaking app restart than to rely on SWAP to prevent OOM crashes. With modern platforms like Kubernetes, memory requests and limits are enforced, ensuring apps use only the RAM allocated to them, while avoiding overcommitment to prevent resource exhaustion. Additionally, disabling swap may protect data from **data remanence attacks**, where sensitive information could potentially be recovered from the swap space even after a process terminates. --- ### Theoretical Capability vs. Practical Deployment Linux provides a powerful and flexible memory subsystem. With proper tuning (e.g., swappiness, memory pinning, cgroups), it's technically possible to make swap usage efficient and targeted. Seasoned sysadmins often argue that disabling swap entirely is a lazy shortcut—an avoidance of learning how to use the tools properly. But Kubernetes is not a traditional system. It's an orchestrated environment that favors predictability, fail-fast behavior, and clear isolation between workloads. Within this model: - Memory **requests and limits** are declared explicitly. - The scheduler makes decisions based on RAM availability, not total virtual memory (RAM + swap). - Swap introduces **non-deterministic performance** characteristics that conflict with Kubernetes' goals. So while the kernel supports intelligent swap usage, Kubernetes **intentionally sidesteps** that complexity. --- ### Why Disable Swap in Kubernetes? 1. **Deterministic Failure > Degraded Performance**\ If a pod exceeds its memory allocation, it should fail fast — not get throttled into slow oblivion due to swap. This behavior surfaces bugs (like memory leaks or poor sizing) early. 2. **Transparency & Observability**\ With swap disabled, memory issues are clearer to diagnose. Swap obfuscates root causes and can make a healthy-looking node behave erratically. 3. **Performance Consistency**\ Swap causes I/O overhead. One noisy pod using swap can impact unrelated workloads on the same node — even if they’re within their resource limits. 4. **Kubernetes Doesn’t Manage Swap Well**\ Kubelet has historically lacked intelligence around swap. As of today, Kubernetes still doesn't support swap-aware scheduling or per-container swap control. 5. **Statelessness is the Norm**\ Most containerized workloads are designed to be ephemeral. Restarting a pod is usually preferable to letting it hang in a degraded state. --- ### "But Swap Can Be Useful..." Yes — for certain workloads (e.g., in-memory databases, caching layers, legacy systems), there may be valid reasons to keep swap enabled. In such cases, you'd need: - Fine-tuned `vm.swappiness` - Memory pinning and cgroup-based control - Swap-aware monitoring and alerting - Custom kubelet/systemd integration That's possible, but **not standard practice** — and for good reason. --- ### Future Considerations Recent Kubernetes releases have introduced [experimental swap support](https://kubernetes.io/blog/2023/08/24/swap-linux-beta/) via [KEP-2400](https://github.com/kubernetes/enhancements/blob/master/keps/sig-node/2400-node-swap/README.md). While this provides more flexibility for advanced use cases — particularly Burstable QoS pods on cgroupsv2 — swap remains disabled by default and is not generally recommended for production workloads unless carefully planned. The rationale outlined in this article remains applicable to most Kubernetes operators, especially in multi-tenant and performance-sensitive environments. Even the Kubernetes maintainers acknowledge the inherent trade-offs of enabling swap. As noted in [KEP-2400's Risks and Mitigations section](https://github.com/kubernetes/enhancements/blob/master/keps/sig-node/2400-node-swap/README.md), swap introduces unpredictability, can severely degrade performance compared to RAM, and complicates Kubernetes' resource accounting — increasing the risk of noisy neighbors and unexpected scheduling behavior. Some argue that with emerging technologies like **non-volatile memory** (e.g., Intel Optane/XPoint), swap may become viable again. These systems promise near-RAM speed with large capacity, offering hybrid memory models. But these are not widely deployed or supported in mainstream Kubernetes environments yet. --- ### Conclusion Disabling swap in Kubernetes is not a lazy hack — it’s a **strategic tradeoff**. It improves transparency, predictability, and system integrity in multi-tenant, containerized environments. While the kernel allows for more advanced configurations, Kubernetes intentionally simplifies memory handling for the sake of reliability. If we want to revisit swap usage, it should come with serious planning: proper instrumentation, swap-aware observability, and potentially upstream K8s improvements. Until then, **disabling swap remains the sane default**. @ 57d1a264:69f1fee1
2025-03-24 17:08:06Nice podcast with @sbddesign and @ConorOkus about bitcoin payments. https://www.youtube.com/watch?v=GTSqoFKs1cE In this episode, Conor, Open Source product manager at Spiral & Stephen, Product Designer at Voltage & Co founder of ATL Bitlab join Stephan to discuss the current state of Bitcoin user experience, particularly focusing on payments and the challenges faced by users. They explore the comparison between Bitcoin and physical cash, the Western perspective on Bitcoin payments, and the importance of user experience in facilitating Bitcoin transactions. They also touch upon various payment protocols like #BOLT11, #LNURL, and #BOLT12, highlighting the need for interoperability and better privacy features in the Bitcoin ecosystem. The discussion also covers resources available for developers and designers to enhance wallet usability and integration. @StephanLivera Official Podcast Episode: https://stephanlivera.com/646 ### Takeaways 🔸Bitcoin has excelled as a savings technology. 🔸The payments use case for Bitcoin still needs improvement. 🔸User experience is crucial for Bitcoin adoption. 🔸Comparing Bitcoin to cash highlights privacy concerns. 🔸Western users may not see a payments problem. 🔸Regulatory issues impact Bitcoin payments in the West. 🔸User experience challenges hinder Bitcoin transactions. 🔸Different payment protocols create compatibility issues. 🔸Community collaboration is essential for Bitcoin's future. 🔸Improving interoperability can enhance Bitcoin payments. Wallet compatibility issues can create negative user impressions. 🔸Designers can significantly improve wallet user experience. 🔸Testing compatibility between wallets is essential for user satisfaction. 🔸Tether's integration may boost Bitcoin adoption. 🔸Developers should prioritize payment capabilities before receiving capabilities. 🔸Collaboration between designers and developers can lead to better products. 🔸User experience improvements can be low-hanging fruit for wallet projects. 🔸A global hackathon aims to promote miner decentralization. 🔸Resources like BOLT12 and the Bitcoin Design Guide are valuable for developers. 🔸Engaging with the community can lead to innovative solutions. ### Timestamps ([00:00](/watch?v=GTSqoFKs1cE)) - Intro ([01:10](/watch?v=GTSqoFKs1cE&t=70s)) - What is the current state of Bitcoin usage - Payments or Savings? ([04:32](/watch?v=GTSqoFKs1cE&t=272s)) - Comparing Bitcoin with physical cash ([07:08](/watch?v=GTSqoFKs1cE&t=428s)) - What is the western perspective on Bitcoin payments? ([11:30](/watch?v=GTSqoFKs1cE&t=690s)) - Would people use Bitcoin more with improved UX? ([17:05](/watch?v=GTSqoFKs1cE&t=1025s)) - Exploring payment protocols: Bolt11, LNURL, Bolt12 & BIP353 ([30:14](/watch?v=GTSqoFKs1cE&t=1814s)) - Navigating Bitcoin wallet compatibility challenges ([34:45](/watch?v=GTSqoFKs1cE&t=2085s)) - What is the role of designers in wallet development? ([43:13](/watch?v=GTSqoFKs1cE&t=2593s)) - Rumble’s integration of Tether & Bitcoin; The impact of Tether on Bitcoin adoption ([51:22](/watch?v=GTSqoFKs1cE&t=3082s)) - Resources for wallet developers and designers ### Links: • [https://x.com/conorokus](https://x.com/conorokus) • [https://x.com/StephenDeLorme](https://x.com/StephenDeLorme) • [https://bolt12.org/](https://bolt12.org/) • [https://twelve.cash/](https://twelve.cash) • [https://bitcoin.design/guide/](https://bitcoin.design/guide/) • Setting Up Bitcoin Tips for Streamers](/watch?v=IWTpSN8IaLE) originally posted at https://stacker.news/items/923714
@ 57d1a264:69f1fee1
2025-03-24 17:08:06Nice podcast with @sbddesign and @ConorOkus about bitcoin payments. https://www.youtube.com/watch?v=GTSqoFKs1cE In this episode, Conor, Open Source product manager at Spiral & Stephen, Product Designer at Voltage & Co founder of ATL Bitlab join Stephan to discuss the current state of Bitcoin user experience, particularly focusing on payments and the challenges faced by users. They explore the comparison between Bitcoin and physical cash, the Western perspective on Bitcoin payments, and the importance of user experience in facilitating Bitcoin transactions. They also touch upon various payment protocols like #BOLT11, #LNURL, and #BOLT12, highlighting the need for interoperability and better privacy features in the Bitcoin ecosystem. The discussion also covers resources available for developers and designers to enhance wallet usability and integration. @StephanLivera Official Podcast Episode: https://stephanlivera.com/646 ### Takeaways 🔸Bitcoin has excelled as a savings technology. 🔸The payments use case for Bitcoin still needs improvement. 🔸User experience is crucial for Bitcoin adoption. 🔸Comparing Bitcoin to cash highlights privacy concerns. 🔸Western users may not see a payments problem. 🔸Regulatory issues impact Bitcoin payments in the West. 🔸User experience challenges hinder Bitcoin transactions. 🔸Different payment protocols create compatibility issues. 🔸Community collaboration is essential for Bitcoin's future. 🔸Improving interoperability can enhance Bitcoin payments. Wallet compatibility issues can create negative user impressions. 🔸Designers can significantly improve wallet user experience. 🔸Testing compatibility between wallets is essential for user satisfaction. 🔸Tether's integration may boost Bitcoin adoption. 🔸Developers should prioritize payment capabilities before receiving capabilities. 🔸Collaboration between designers and developers can lead to better products. 🔸User experience improvements can be low-hanging fruit for wallet projects. 🔸A global hackathon aims to promote miner decentralization. 🔸Resources like BOLT12 and the Bitcoin Design Guide are valuable for developers. 🔸Engaging with the community can lead to innovative solutions. ### Timestamps ([00:00](/watch?v=GTSqoFKs1cE)) - Intro ([01:10](/watch?v=GTSqoFKs1cE&t=70s)) - What is the current state of Bitcoin usage - Payments or Savings? ([04:32](/watch?v=GTSqoFKs1cE&t=272s)) - Comparing Bitcoin with physical cash ([07:08](/watch?v=GTSqoFKs1cE&t=428s)) - What is the western perspective on Bitcoin payments? ([11:30](/watch?v=GTSqoFKs1cE&t=690s)) - Would people use Bitcoin more with improved UX? ([17:05](/watch?v=GTSqoFKs1cE&t=1025s)) - Exploring payment protocols: Bolt11, LNURL, Bolt12 & BIP353 ([30:14](/watch?v=GTSqoFKs1cE&t=1814s)) - Navigating Bitcoin wallet compatibility challenges ([34:45](/watch?v=GTSqoFKs1cE&t=2085s)) - What is the role of designers in wallet development? ([43:13](/watch?v=GTSqoFKs1cE&t=2593s)) - Rumble’s integration of Tether & Bitcoin; The impact of Tether on Bitcoin adoption ([51:22](/watch?v=GTSqoFKs1cE&t=3082s)) - Resources for wallet developers and designers ### Links: • [https://x.com/conorokus](https://x.com/conorokus) • [https://x.com/StephenDeLorme](https://x.com/StephenDeLorme) • [https://bolt12.org/](https://bolt12.org/) • [https://twelve.cash/](https://twelve.cash) • [https://bitcoin.design/guide/](https://bitcoin.design/guide/) • Setting Up Bitcoin Tips for Streamers](/watch?v=IWTpSN8IaLE) originally posted at https://stacker.news/items/923714 @ a5142938:0ef19da3
2025-04-04 09:14:07Rewards are an experimental approach to sharing the value created by contributors to this site, through a revenue-sharing system based on the following conditions: - Any revenue generated by the site each month is distributed over the **following 12 months**, ensuring long-term visibility and smoothing out monthly variations. - On the **1st of each month**, half of the revenue is distributed among all contributors, in proportion to the number of their validated contributions. - Contributions remain valid indefinitely, but rewards are only distributed to contributors who have made **at least one validated contribution in the past 12 months**. ### Payment Method Rewards are paid via the Lightning network, in sats (the smallest unit of Bitcoin). To receive payments, you must have a NOSTR account linked to a Lightning wallet. To receive them, the NOSTR account used to contribute must be linked to a Lightning wallet. **💡 New to these tools?** - **Don’t have a NOSTR account yet?** A simple way to get started is to create one on an open-source NOSTR client like [yakihonne.com](https://yakihonne.com/) to set up your profile and wallet there. Then, retrieve your NOSTR keys (from the settings) and save them in a secure vault like [nsec.app](https://use.nsec.app/home) to log in here and start contributing. - **Already started contributing on this site?** Make sure to securely store your NOSTR keys in a vault like [nsec.app](https://use.nsec.app/home). You can also log in with them on [yakihonne.com](https://yakihonne.com/) to set up your profile. - You can also contribute directly from yakihonne.com by commenting on Origine Nature’s articles. Learn more about contributions
@ a5142938:0ef19da3
2025-04-04 09:14:07Rewards are an experimental approach to sharing the value created by contributors to this site, through a revenue-sharing system based on the following conditions: - Any revenue generated by the site each month is distributed over the **following 12 months**, ensuring long-term visibility and smoothing out monthly variations. - On the **1st of each month**, half of the revenue is distributed among all contributors, in proportion to the number of their validated contributions. - Contributions remain valid indefinitely, but rewards are only distributed to contributors who have made **at least one validated contribution in the past 12 months**. ### Payment Method Rewards are paid via the Lightning network, in sats (the smallest unit of Bitcoin). To receive payments, you must have a NOSTR account linked to a Lightning wallet. To receive them, the NOSTR account used to contribute must be linked to a Lightning wallet. **💡 New to these tools?** - **Don’t have a NOSTR account yet?** A simple way to get started is to create one on an open-source NOSTR client like [yakihonne.com](https://yakihonne.com/) to set up your profile and wallet there. Then, retrieve your NOSTR keys (from the settings) and save them in a secure vault like [nsec.app](https://use.nsec.app/home) to log in here and start contributing. - **Already started contributing on this site?** Make sure to securely store your NOSTR keys in a vault like [nsec.app](https://use.nsec.app/home). You can also log in with them on [yakihonne.com](https://yakihonne.com/) to set up your profile. - You can also contribute directly from yakihonne.com by commenting on Origine Nature’s articles. Learn more about contributions @ 866e0139:6a9334e5
2025-03-24 10:50:59**Autor:** *Ludwig F. Badenhagen.* *Dieser Beitrag wurde mit dem* *[Pareto-Client](https://pareto.space/read)* *geschrieben.* *** Einer der wesentlichen Gründe dafür, dass während der „Corona-Pandemie“ so viele Menschen den Anweisungen der Spitzenpolitiker folgten, war sicher der, dass diese Menschen den Politikern vertrauten. Diese Menschen konnten sich nicht vorstellen, dass Spitzenpolitiker den Auftrag haben könnten, die Bürger analog klaren Vorgaben zu belügen, zu betrügen und sie vorsätzlich (tödlich) zu verletzen. Im Gegenteil, diese gutgläubigen Menschen waren mit der Zuversicht aufgewachsen, dass Spitzenpolitiker den Menschen dienen und deren Wohl im Fokus haben (müssen). Dies beteuerten Spitzenpolitiker schließlich stets in Talkshows und weiteren Medienformaten. Zwar wurden manche Politiker auch bei Fehlverhalten erwischt, aber hierbei ging es zumeist „nur“ um Geld und nicht um Leben. Und wenn es doch einmal um Leben ging, dann passieren die Verfehlungen „aus Versehen“, aber nicht mit Vorsatz. So oder so ähnlich dachte die Mehrheit der Bürger. Aber vor 5 Jahren änderte sich für aufmerksame Menschen alles, denn analog dem Lockstep-Szenario der Rockefeller-Foundation wurde der zuvor ausgiebig vorbereitete Plan zur Inszenierung der „Corona-Pandemie“ Realität. Seitdem wurde so manchem Bürger, der sich jenseits von Mainstream-Medien informierte, das Ausmaß der unter dem Vorwand einer erfundenen Pandemie vollbrachten Taten klar. Und unverändert kommen täglich immer neue Erkenntnisse ans Licht. Auf den Punkt gebracht war die Inszenierung der „Corona-Pandemie“ ein Verbrechen an der Menschheit, konstatieren unabhängige Sachverständige. Dieser Beitrag befasst sich allerdings nicht damit, die vielen Bestandteile dieses Verbrechens (nochmals) aufzuzählen oder weitere zu benennen. Stattdessen soll beleuchtet werden, warum die Spitzenpolitiker sich so verhalten haben und ob es überhaupt nach alledem möglich ist, der Politik jemals wieder zu vertrauen? Ferner ist es ein Anliegen dieses Artikels, die weiteren Zusammenhänge zu erörtern. Und zu guter Letzt soll dargelegt werden, warum sich der große Teil der Menschen unverändert alles gefallen lässt. **Demokratie** Von jeher organisierten sich Menschen mit dem Ziel, Ordnungsrahmen zu erschaffen, welche wechselseitiges Interagieren regeln. Dies führte aber stets dazu, dass einige wenige alle anderen unterordneten. Der Grundgedanke, der vor rund 2500 Jahren formulierten Demokratie, verfolgte dann aber das Ziel, dass die Masse darüber entscheiden können soll, wie sie leben und verwaltet werden möchte. Dieser Grundgedanke wurde von den Mächtigen sowohl gehasst als auch gefürchtet, denn die Gefahr lag nahe, dass die besitzlosen Vielen beispielsweise mit einer schlichten Abstimmung verfügen könnten, den Besitz der Wenigen zu enteignen. Selbst Sokrates war gegen solch eine Gesellschaftsordnung, da die besten Ideen nicht durch die Vielen, sondern durch einige wenige Kluge und Aufrichtige in die Welt kommen. Man müsse die Vielen lediglich manipulieren und würde auf diese Weise quasi jeden Unfug umsetzen können. Die Demokratie war ein Rohrkrepierer. **Die Mogelpackung „Repräsentative Demokratie“** Erst im Zuge der Gründung der USA gelang der Trick, dem Volk die „Repräsentative Demokratie“ unterzujubeln, die sich zwar nach Demokratie anhört, aber mit der Ursprungsdefinition nichts zu tun hat. Man konnte zwischen zwei Parteien wählen, die sich mit ihren jeweiligen Versprechen um die Gunst des Volkes bewarben. Tatsächlich paktierten die Vertreter der gewählten Parteien (Politiker) aber mit den wirklich Mächtigen, die letztendlich dafür sorgten, dass diese Politiker in die jeweiligen exponierten Positionen gelangten, welche ihnen ermöglichten (und somit auch den wirklich Mächtigen), Macht auszuüben. Übrigens, ob die eine oder andere Partei „den Volkswillen“ für sich gewinnen konnte, war für die wirklich Mächtigen weniger von Bedeutung, denn der Wille der wirklich Mächtigen wurde so oder so, wenn auch in voneinander differierenden Details, umgesetzt. Die Menschen waren begeistert von dieser Idee, denn sie glaubten, dass sie selbst „der Souverän“ seien. Schluss mit Monarchie sowie sonstiger Fremdherrschaft und Unterdrückung. Die Mächtigen waren ebenfalls begeistert, denn durch die Repräsentative Demokratie waren sie selbst nicht mehr in der Schusslinie, weil das Volk sich mit seinem Unmut fortan auf die Politiker konzentrierte. Da diese Politiker aber vielleicht nicht von einem selbst, sondern von vielen anderen Wahlberechtigten gewählt wurden, lenkte sich der Groll der Menschen nicht nur ab von den wirklich Mächtigen, sondern auch ab von den Politikern, direkt auf „die vielen Idioten“ aus ihrer eigenen Mitte, die sich „ver-wählt“ hatten. Diese Lenkung des Volkes funktionierte so hervorragend, dass andere Länder die Grundprinzipien dieses Steuerungsinstrumentes übernahmen. Dies ist alles bei Rainer Mausfeld nachzulesen. Ursprünglich waren die Mächtigen nur regional mächtig, sodass das Führen der eigenen Menschen(vieh)herde eher eine lokale Angelegenheit war. Somit mussten auch nur lokale Probleme gelöst werden und die Mittel zur Problemlösung blieben im eigenen Problembereich. *** JETZT ABONNIEREN: ***[Hier](https://pareto.space/u/friedenstaube@pareto.space)*** *können Sie die Friedenstaube abonnieren und bekommen die Artikel in Ihr Postfach, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht).* *** * Für **50 CHF/EURO** bekommen Sie ein Jahresabo der Friedenstaube. * Für **120 CHF/EURO** bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube. * Für **500 CHF/EURO** werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube. * Ab **1000 CHF/EURO** werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie). **Für Einzahlungen in CHF (Betreff: Friedenstaube):** [](https://substackcdn.com/image/fetch/f_auto%2Cq_auto%3Agood%2Cfl_progressive%3Asteep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F3fdee17a-c22f-404e-a10c-7f87a7b8182a_2176x998.png) **Für Einzahlungen in Euro:** Milosz Matuschek IBAN DE 53710520500000814137 BYLADEM1TST Sparkasse Traunstein-Trostberg **Betreff: Friedenstaube** Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: <milosz@pareto.space> oder <kontakt@idw-europe.org>. *** **Beherrschungsinstrumente der globalen Massenhaltung** Im Zuge der territorialen Erweiterungen der „Besitzungen“ einiger wirklich Mächtiger wurden die Verwaltungs- und Beherrschungsinstrumente überregionaler. Und heute, zu Zeiten der globalen Vernetzung, paktieren die wirklich Mächtigen miteinander und beanspruchen die Weltherrschaft. Längst wird offen über die finale Realisierung einen Weltregierung, welche die Nationalstaaten „nicht mehr benötigt“, gesprochen. Dass sich Deutschland, ebenso wie andere europäische Staaten, der EU untergeordnet hat, dürfte auch Leuten nicht entgangen sein, die sich nur über die Tagesschau informieren. Längst steht das EU-Recht über dem deutschen Recht. Und nur kurze Zeit ist es her, als die EU und alle ihre Mitgliedsstaaten die WHO autonom darüber entscheiden lassen wollten, was eine Pandemie ist und wie diese für alle verbindlich „bekämpft“ werden soll. Eine spannende Frage ist nun, wer denn über der EU und der WHO sowie anderen Institutionen steht? Diese Beschreibung macht klar, dass ein „souveränes Land“ wie das unverändert von der amerikanischen Armee besetzte Deutschland in der Entscheidungshierarchie an die Weisungen übergeordneter Entscheidungsorgane gebunden ist. An der Spitze stehen - wie kann es anders sein - die wirklich Mächtigen. Aber was nützt es dann, Spitzenpolitiker zu wählen, wenn diese analog Horst Seehofer nichts zu melden haben? Ist das Wählen von Politikern nicht völlig sinnlos, wenn deren Wahlversprechen ohnehin nicht erfüllt werden? Ist es nicht so, dass die Menschen, welche ihre Stimme nicht behalten, sondern abgeben, das bestehende System nur nähren, indem sie Wahlergebnisse akzeptieren, ohne zu wissen, ob diese manipuliert wurden, aber mit der Gewissheit, dass das im Zuge des Wahlkampfes Versprochene auf keinen Fall geliefert wird? Aktive Wähler glauben trotz allem an die Redlichkeit und Wirksamkeit von Wahlen, und sie akzeptieren Wahlergebnisse, weil sie denken, dass sie von „so vielen Idioten, die falsch wählen“, umgeben sind, womit wir wieder bei der Spaltung sind. Sie glauben, der Stand des aktuellen Elends sei „selbst gewählt“. **Die Wahl der Aufseher** Stellen Sie sich bitte vor, Sie wären im Gefängnis, weil Sie einen kritischen Artikel mit „gefällt mir“ gekennzeichnet haben oder weil Sie eine „Kontaktschuld“ trifft, da in Ihrer Nachbarschaft ein „verschwörerisches Symbol“ von einem „aufmerksamen“ Nachbarn bei einer „Meldestelle“ angezeigt wurde oder Sie gar eine Tat, „unterhalb der Strafbarkeitsgrenze“ begangen hätten, dann würden Sie möglicherweise mit Maßnahmen bestraft, die „keine Folter wären“. Beispielsweise würde man Sie während Ihrer „Umerziehungshaft“ mit Waterboarding, Halten von Stresspositionen, Dunkelhaft etc. dabei „unterstützen“, „Ihre Verfehlungen zu überdenken“. Stellen Sie sich weiterhin vor, dass Sie, so wie alle anderen Inhaftierten, an der alle vier Jahre stattfindenden Wahl der Aufseher teilnehmen könnten, und Sie hätten auch einen Favoriten, der zwar Waterboarding betreibt, aber gegen alle anderen Maßnahmen steht. Sie hätten sicher allen Grund zur Freude, wenn Sie Ihren Kandidaten durchbringen könnten, oder? Aber was wäre, wenn der Aufseher Ihrer Wahl dann dennoch alle 3 „Nicht-Folter-Maßnahmen“ anwenden würde, wie sämtliche anderen Aufseher zuvor? Spätestens dann müssten Sie sich eingestehen, dass es der Beruf des Aufsehers ist, Aufseher zu sein und dass er letztendlich tut, was ihm „von oben“ aufgetragen wird. Andernfalls verliert er seinen Job. Oder er verunfallt oder gerät in einen Skandal etc. So oder so, er verliert seinen Job - und den erledigt dann ein anderer Aufseher. Die Wahl des Aufsehers ändert wenig, solange Sie sich im System des Gefängnisses befinden und der Aufseher integraler Bestandteil dieses Systems ist. Zur Realisierung einer tatsächlichen Änderung müssten Sie dort herauskommen. Dieses Beispiel soll darstellen, dass alles in Hierarchien eingebunden ist. Die in einem System eingebundenen Menschen erfüllen ihre zugewiesenen Aufgaben, oder sie werden bestraft. **Das aktuelle System schadet dem Volk** Auch in der staatlichen Organisation von Menschen existieren hierarchische Gliederungen. Eine kommunale Selbstverwaltung gehört zum Kreis, dieser zum Land, dieses zum Staat, dieser zur EU, und diese - zu wem auch immer. Und vereinnahmte Gelder fließen nach oben. Obwohl es natürlich wäre, dass die Mittel dorthin fließen, wo sie der Allgemeinheit und nicht einigen wenigen dienen, also nach unten. Warum muss es also eine Weltregierung geben? Warum sollen nur einige Wenige über alle anderen bestimmen und an diesen verdienen (Nahrung, Medikamente, Krieg, Steuern etc.)? Warum sollen Menschen, so wie Vieh, das jemandem „gehört“, mit einem Code versehen und bereits als Baby zwangsgeimpft werden? Warum müssen alle Transaktionen und sämtliches Verhalten strickt gesteuert, kontrolliert und bewertet werden? Viele Menschen werden nach alledem zu dem Schluss kommen, dass solch ein System nur einigen wenigen wirklich Mächtigen und deren Helfershelfern nützt. Aber es gibt auch eine Gruppe Menschen, für die im Land alles beanstandungsfrei funktioniert. Die Spaltung der Menschen ist perfekt gelungen und sofern die eine Gruppe darauf wartet, dass die andere „endlich aufwacht“, da die Fakten doch auf dem Tisch liegen, so wird sie weiter warten dürfen. Julian Assange erwähnte einst, dass es für ihn eine unglaubliche Enttäuschung war, dass ihm niemand half. Assange hatte Ungeheuerlichkeiten aufgedeckt. Es gab keinen Aufstand. Assange wurde inhaftiert und gefoltert. Es gab keinen Aufstand. Assange sagte, er hätte nicht damit gerechnet, dass die Leute „so unglaublich feige“ seien. Aber womit rechnete er den stattdessen? Dass die Massen „sich erheben“. Das gibt es nur im Film, denn die Masse besteht aus vielen maximal Indoktrinierten, die sich wie Schafe verhalten, was als Züchtungserfolg der Leute an den Schalthebeln der Macht und deren Herren, den wirklich Mächtigen, anzuerkennen ist. Denn wer mächtig ist und bleiben möchte, will sicher keine problematischen Untertanen, sondern eine gefügige, ängstliche Herde, die er nach Belieben ausbeuten und steuern kann. Wenn er hierüber verfügt, will er keinen Widerstand. Ob Corona, Krieg, Demokratie- und Klimarettung oder Meinungsäußerungsverbote und Bürgerrechte, die unterhalb der Strafbarkeitsgrenze liegen, all diese und viele weitere Stichworte mehr sind es, die viele traurig und so manche wütend machen. Auch das Mittel des Demonstrierens hat sich als völlig wirkungslos erwiesen. Die vielen gruseligen Videoaufnahmen über die massivsten Misshandlungen von Demonstranten gegen die Corona-Maßnahmen führen zu dem Ergebnis, dass die Exekutive ihr Gewaltmonopol nutzt(e), um die Bevölkerung gezielt zu verletzen und einzuschüchtern. Bekanntlich kann jede friedliche Demonstration zum Eskalieren gebracht werden, indem man Menschen in die Enge treibt (fehlender Sicherheitsabstand) und einige V-Leute in Zivil mit einschlägigen Flaggen und sonstigen „Symbolen“ einschleust, die für Krawall sorgen, damit die gepanzerten Kollegen dann losknüppeln und die scharfen Hunde zubeißen können. So lauten zumindest die Berichte vieler Zeitzeugen und so ist es auch auf vielen Videos zu sehen. Allerdings nicht im Mainstream. Dieses Vorgehen ist deshalb besonders perfide, weil man den Deutschen ihre Wehrhaftigkeit aberzogen hat. Nicht wehrfähige Bürger und eine brutale Staatsmacht mit Gewaltmonopol führen zu einem Gemetzel bei den Bürgern. Ähnliches lässt sich auch in zivilen Lebenssituationen beobachten, wenn die hiesige zivilisierte Bevölkerung auf „eingereiste“ Massenvergewaltiger und Messerstecher trifft, die über ein anderes Gewalt- und Rechtsverständnis verfügen als die Einheimischen. **System-Technik** Die These ist, dass es eine Gruppe von global agierenden Personen gibt, welche das Geschehen auf der Erde zunehmend wirksam zu ihrem individuellen Vorteil gestaltet. Wie sich diese Gruppe definiert, kann bei John Coleman (Das Komitee der 300) und David Icke nachgelesen werden. Hierbei handelt es ich um Autoren, die jahrzehntelang analog streng wissenschaftlichen Grundlagen zu ihren Themen geforscht haben und in ihren jeweiligen Werken sämtliche Quellen benennen. Diese Autoren wurden vom Mainstream mit dem Prädikatsmerkmal „Verschwörungstheoretiker“ ausgezeichnet, wodurch die Ergebnisse Ihrer Arbeiten umso glaubwürdiger sind. Diese mächtige Gruppe hat mit ihren Schergen nahezu den gesamten Planeten infiltriert, indem sie Personen in führenden Positionen in vielen Belangen größtmögliche Freiheiten sowie Schutz gewährt, aber diesen im Gegenzug eine völlige Unterwerfung bei Kernthemen abfordert. Die Motivatoren für diese Unterwerfung sind, abgesehen von materiellen Zuwendungen, auch „Ruhm und Ehre sowie Macht“. Manchmal wird auch Beweismaterial für begangene Verfehlungen (Lolita-Express, Pizzagate etc.) genutzt, um Forderungen Nachdruck zu verleihen. Und auch körperliche Bestrafungen der betroffenen Person oder deren Angehörigen zählen zum Repertoire der Motivatoren. Letztendlich ähnlich den Verhaltensweisen in einem Mafia-Film. Mit dieser Methodik hat sich diese mächtige Gruppe im Laufe von Jahrhunderten! eine Organisation erschaffen, welche aus Kirchen, Parteien, Firmen, NGO, Vereinen, Verbänden und weiteren Organisationsformen besteht. Bestimmte Ämter und Positionen in Organisationen können nur von Personen eingenommen und gehalten werden, die „auf Linie sind“. Die Mitglieder der Gruppe tauchen in keiner Rubrik wie „Die reichsten Menschen der Welt“ auf, sondern bleiben fern der Öffentlichkeit. Wer jemanden aus ihren Reihen erkennt und beschuldigt, ist ein „Antisemit“ oder sonstiger Übeltäter und wird verfolgt und bekämpft. Über mächtige Vermögensverwaltungskonzerne beteiligen sich die Mitglieder dieser Gruppe anonym an Unternehmen in Schlüsselpositionen in einer Dimension, die ihnen wesentlichen Einfluss auf die Auswahl der Topmanager einräumt, sodass die jeweilige Unternehmenspolitik nach Vorgaben der Gruppe gestaltet wird. Die Gruppe steuert das Geldsystem, von dem sich der Planet abhängig zu sein wähnt. Hierzu eine Erläuterung: Ein Staat wie Deutschland ist bekanntlich maximal verschuldet. Man stelle sich vor, ein unliebsamer Politiker würde entgegen sämtlicher „Brandmauern“ und sonstiger Propaganda und Wahlmanipulationen gewählt, das Land zu führen, dann könnte dieser keine Kredit über 500 Mrd. Euro bei der nächsten Sparkasse beantragen, sondern wäre auf die Mächtigen dieser Welt angewiesen. Jeder weiß, dass Deutschland als Staat kein funktionierendes Geschäftsmodell hat und somit nicht in der Lage ist, solch ein Darlehen zurückzuzahlen. Welche Motivation sollte also jemand haben, einem Land wie Deutschland so viel Geld ohne Aussicht auf Rückführung zu geben? Es leuchtet ein, dass dieser Politiker andere Gefälligkeiten anbieten müsste, um das Darlehen zu bekommen. Im Falle einer Weigerung zur Kooperation könnte der Staatsapparat mit seinen Staatsdienern, Bürgergeld- und Rentenempfänger etc. nicht mehr bezahlt werden und dieser Politiker wäre schnell wieder weg. Er würde medial hingerichtet. Es ist somit davon auszugehen, dass ein Spitzenpolitiker dieser Tage nicht über viele Optionen verfügt, denn er übernimmt eine Situation, die von seinen Vorgängern erschaffen wurde. Trotz alledem darauf zu hoffen, dass es einen anderen Politiker geben könnte, mit dem dann alles wieder gut wird, mutet ziemlich infantil an. Dass ein Großteil der Medien von Zuwendungen abhängig ist, dürfte ebenfalls leicht nachzuvollziehen sein, denn der gewöhnliche Bürger zahlt nichts für den Content der MSM. Abhängig davon, von wem (Regierung, Philanthrop, Konzern etc.) ein Medium am Leben gehalten wird, gestalten sich auch dessen Inhalte. Und wenn angewiesen wird, dass ein Politiker medial hingerichtet werden soll, dann bedient die Maschinerie das Thema. Man beobachte einfach einmal, dass Politiker der Kartell-Parteien völlig anders behandelt werden als solche jenseits der „Brandmauer“. Und der Leser, der solche Auftragsarbeiten kostenlos liest, ist der Konsument, für dessen Indoktrination die Finanziers der Verlage gerne zahlen. Mittlerweile kann durch die Herrschaft über die Medien und die systematische Vergiftung der Körper und Geister der Population die öffentliche Meinung gesteuert werden. Die überwiegende Zahl der Deutschen scheint nicht mehr klar denken zu können. Wer sich das aktuelle Geschehen in der deutschen Politik mit klarem Verstand ansieht, kommt nicht umhin, eine Fernsteuerung der handelnden Politiker in Betracht zu ziehen. Aber was soll daran verwundern? Sind es deshalb „böse Menschen“? Sind die in „Forschungslaboren“ arbeitenden Quäler von „Versuchstieren“ böse Menschen? Sind der Schlächter, der Folterer und der Henker böse Menschen? Oder der knüppelnde Polizist? Es handelt sich zunächst einmal um Personen, die einen Vorteil dadurch haben, Ihrer Tätigkeit nachzugehen. Sie sind integrale Bestandteile eines Belohnungssystems, welches von oben nach unten Anweisungen gibt. Und wenn diese Anweisungen nicht befolgt werden, führt dies für den Befehlsverweigerer zu Konsequenzen. **Der klare Verstand** Es ist nun eine spannende Frage, warum so viele Menschen sich solch eine Behandlung gefallen lassen? Nun, das ist relativ einfach, denn das angepasste Verhalten der Vielen ist nichts anderes als ein Züchtungserfolg der Wenigen. Die Psyche der Menschen ist ebenso akribisch erforscht worden wie deren Körperfunktionen. Würden die Menschen von den wirklich Mächtigen geliebt, dann würde genau gewusst, wie sie zu behandeln und mit ihren jeweiligen Bedürfnissen zu versorgen sind. Stattdessen werden die Menschen aber als eine Einnahmequelle betrachtet. Dies manifestiert sich exemplarisch in folgenden Bereichen: 1. Das Gesundheitssystem verdient nichts am gesunden Menschen, sondern nur am (dauerhaft) kranken, der um Schmerzlinderung bettelt. Bereits als Baby werden Menschen geimpft, was die jeweilige Gesundheit (mit Verweis auf die Werke von Anita Petek-Dimmer u. a.) nachhaltig negativ beeinflusst. Wer hat denn heute keine Krankheiten? Die „Experten“ des Gesundheitssystems verteufeln Vitamin D, Vitamin C, Lithium, die Sonne, Natur etc. und empfehlen stattdessen Präparate, die man patentieren konnte und mit denen die Hersteller viel Geld verdienen. Die Präparate heilen selten, sondern lindern bestenfalls zuvor künstlich erzeugte Leiden, und müssen oftmals dauerhaft eingenommen werden. Was ist aus den nicht Geimpften geworden, die alle sterben sollten? Sind diese nicht die einzigen Gesunden dieser Tage? Ist nicht jeder Geimpfte entweder permanent krank oder bereits tot? Abgesehen von denen, welche das Glück hatten, „Sonderchargen“ mit Kochsalz zu erhalten. \ \ Wem gehören die wesentlichen Player im Gesundheitswesen zu einem erheblichen Teil? Die Vermögensverwalter der wirklich Mächtigen. 2. Ähnlich gestaltet es sich bei der Ernährungsindustrie. Die von dort aus verabreichten Produkte sind die Ursachen für den Gesundheitszustand der deutschen Population. Das ist aber auch irgendwie logisch, denn wer sich nicht falsch ernährt und gesund bleibt, wird kein Kunde des Gesundheitswesens. \ \ Die Besitzverhältnisse in der Ernährungsindustrie ähneln denen im Gesundheitswesen, sodass am gleichen Kunden gearbeitet und verdient wird. 3. Die Aufzählung konnte nun über die meisten Branchen, in denen mit dem Elend der Menschen viel verdient werden kann, fortgesetzt werden. Waffen (BlackRock erhöhte beispielsweise seine Anteile an der Rheinmetall AG im Juni 2024 auf 5,25 Prozent. Der US-Vermögensverwalter ist damit der zweitgrößte Anteilseigner nach der französischen Großbank Société Générale.), Energie, Umwelt, Technologie, IT, Software, KI, Handel etc. Wie genau Chemtrails und Technologien wie 5G auf den Menschen und die Tiere wirken, ist ebenfalls umstritten. Aber ist es nicht seltsam, wie krank, empathielos, antriebslos und aggressiv viele Menschen heute sind? Was genau verabreicht man der Berliner Polizei, damit diese ihre Prügelorgien auf den Rücken und in den Gesichtern der Menschen wahrnehmen, die friedlich ihre Demonstrationsrechte wahrnehmen? Und was erhalten die ganzen zugereisten „Fachkräfte“, die mit Ihren Autos in Menschenmengen rasen oder auch Kinder und Erwachsene niedermessern? Das Titelbild dieses Beitrags zeigt einige Gebilde, welche regelmäßig bei Obduktionen von Geimpften in deren Blutgefäßen gefunden werden. Wie genau wirken diese kleinen Monster? Können wir Menschen ihr Unverständnis und ihr Nicht-Aufwachen vorwerfen, wenn wir erkennen, dass diese Menschen maximal vergiftet wurden? Oder sollten einfach Lösungen für die Probleme dieser Zeit auch ohne den Einbezug derer gefunden werden, die offenbar nicht mehr Herr ihrer Sinne sind? **Die Ziele der wirklich Mächtigen** Wer sich entsprechende Videosequenzen der Bilderberger, des WEF und anderen „Überorganisationen“ ansieht, der erkennt schnell das Muster: * Reduzierung der Weltpopulation um ca. 80 Prozent * Zusammenbruch der Wirtschaft, damit diese von den Konzernen übernommen werden kann. * Zusammenbruch der öffentlichen Ordnung, um eine totale Entwaffnung und eine totale Überwachung durchsetzen zu können. * Zusammenbruch der Regierungen, damit die Weltregierung übernehmen kann. Es ist zu überdenken, ob die Weltregierung tatsächlich das für die Vielen beste Organisationssystem ist, oder ob die dezentrale Eigenorganisation der jeweils lokalen Bevölkerung nicht doch die bessere Option darstellt. Baustellen würden nicht nur begonnen, sondern auch schnell abgearbeitet. Jede Region könnte bestimmen, ob sie sich mit Chemtrails und anderen Substanzen besprühen lassen möchte. Und die Probleme in Barcelona könnte die Menschen dort viel besser lösen als irgendwelche wirklich Mächtigen in ihren Elfenbeintürmen. Die lokale Wirtschaft könnte wieder zurückkommen und mit dieser die Eigenständigkeit. Denn die den wirklich Mächtigen über ihre Vermögensverwalter gehörenden Großkonzerne haben offensichtlich nicht das Wohl der Bevölkerung im Fokus, sondern eher deren Ausbeutung. Das Aussteigen aus dem System ist die wahre Herkulesaufgabe und es bedarf sicher Mut und Klugheit, sich dieser zu stellen. Die Politiker, die unverändert die Narrative der wirklich Mächtigen bedienen, sind hierfür denkbar ungeeignet, denn sie verfolgen kein Lebensmodell, welches sich von Liebe und Mitgefühl geleitet in den Dienst der Gesamtheit von Menschen, Tieren und Natur stellt. Schauen Sie einmal genau hin, denken Sie nach und fühlen Sie mit. **Was tun?** Jedes System funktioniert nur so lange, wie es unterstützt wird. Somit stellt sich die Frage, wie viele Menschen das System ignorieren müssen, damit es kollabiert, und auf welche Weise dieses Ignorieren durchzuführen ist? Merkbar ist, dass die große Masse der Verwaltungsangestellten krank und oder unmotiviert und somit nicht wirksam ist. Würden die entsprechenden Stellen massiv belastet und parallel hierzu keine Einnahmen mehr realisieren, wäre ein Kollaps nah. Die Prügelpolizisten aus Berlin können nicht überall sein und normale Polizisten arbeiten nicht gegen unbescholtene Bürger, sondern sorgen sich selbst um ihre Zukunft. Gewalt ist sicher keine Lösung, und sicher auch nicht erforderlich. Wie eine gerechte Verwaltungsform aufgebaut werden muss? Einfach so, wie sie in den hiesigen Gesetzen beschrieben steht. Aber eine solche Organisationsform muss frei sein von Blockparteien und korrupten Politikern und weisungsgebundenen Richtern etc. Stattdessen werden Menschen benötigt, welche die Menschen lieben und ihnen nicht schaden wollen. Außerdem sollten diese Führungspersonen auch wirklich etwas können, und nicht nur „Politiker“ ohne weitere Berufserfahrungen sein. *** Ludwig F. Badenhagen (Pseudonym, Name ist der Redaktion bekannt). *Der Autor hat deutsche Wurzeln und betrachtet das Geschehen in Deutschland und Europa aus seiner Wahlheimat Südafrika. Seine Informationen bezieht er aus verlässlichen Quellen und insbesondere von Menschen, die als „Verschwörungstheoretiker“, „Nazi“, „Antisemit“ sowie mit weiteren Kampfbegriffen der dortigen Systemakteure wie Politiker und „Journalisten“ diffamiert werden. Solche Diffamierungen sind für ihn ein Prädikatsmerkmal. Er ist international agierender Manager mit einem globalen Netzwerk und verfügt hierdurch über tiefe Einblicke in Konzerne und Politik.* *** **Not yet on** **[Nostr](https://nostr.com/)** **and want the full experience?** Easy onboarding via **[Start.](https://start.njump.me/)**
@ 866e0139:6a9334e5
2025-03-24 10:50:59**Autor:** *Ludwig F. Badenhagen.* *Dieser Beitrag wurde mit dem* *[Pareto-Client](https://pareto.space/read)* *geschrieben.* *** Einer der wesentlichen Gründe dafür, dass während der „Corona-Pandemie“ so viele Menschen den Anweisungen der Spitzenpolitiker folgten, war sicher der, dass diese Menschen den Politikern vertrauten. Diese Menschen konnten sich nicht vorstellen, dass Spitzenpolitiker den Auftrag haben könnten, die Bürger analog klaren Vorgaben zu belügen, zu betrügen und sie vorsätzlich (tödlich) zu verletzen. Im Gegenteil, diese gutgläubigen Menschen waren mit der Zuversicht aufgewachsen, dass Spitzenpolitiker den Menschen dienen und deren Wohl im Fokus haben (müssen). Dies beteuerten Spitzenpolitiker schließlich stets in Talkshows und weiteren Medienformaten. Zwar wurden manche Politiker auch bei Fehlverhalten erwischt, aber hierbei ging es zumeist „nur“ um Geld und nicht um Leben. Und wenn es doch einmal um Leben ging, dann passieren die Verfehlungen „aus Versehen“, aber nicht mit Vorsatz. So oder so ähnlich dachte die Mehrheit der Bürger. Aber vor 5 Jahren änderte sich für aufmerksame Menschen alles, denn analog dem Lockstep-Szenario der Rockefeller-Foundation wurde der zuvor ausgiebig vorbereitete Plan zur Inszenierung der „Corona-Pandemie“ Realität. Seitdem wurde so manchem Bürger, der sich jenseits von Mainstream-Medien informierte, das Ausmaß der unter dem Vorwand einer erfundenen Pandemie vollbrachten Taten klar. Und unverändert kommen täglich immer neue Erkenntnisse ans Licht. Auf den Punkt gebracht war die Inszenierung der „Corona-Pandemie“ ein Verbrechen an der Menschheit, konstatieren unabhängige Sachverständige. Dieser Beitrag befasst sich allerdings nicht damit, die vielen Bestandteile dieses Verbrechens (nochmals) aufzuzählen oder weitere zu benennen. Stattdessen soll beleuchtet werden, warum die Spitzenpolitiker sich so verhalten haben und ob es überhaupt nach alledem möglich ist, der Politik jemals wieder zu vertrauen? Ferner ist es ein Anliegen dieses Artikels, die weiteren Zusammenhänge zu erörtern. Und zu guter Letzt soll dargelegt werden, warum sich der große Teil der Menschen unverändert alles gefallen lässt. **Demokratie** Von jeher organisierten sich Menschen mit dem Ziel, Ordnungsrahmen zu erschaffen, welche wechselseitiges Interagieren regeln. Dies führte aber stets dazu, dass einige wenige alle anderen unterordneten. Der Grundgedanke, der vor rund 2500 Jahren formulierten Demokratie, verfolgte dann aber das Ziel, dass die Masse darüber entscheiden können soll, wie sie leben und verwaltet werden möchte. Dieser Grundgedanke wurde von den Mächtigen sowohl gehasst als auch gefürchtet, denn die Gefahr lag nahe, dass die besitzlosen Vielen beispielsweise mit einer schlichten Abstimmung verfügen könnten, den Besitz der Wenigen zu enteignen. Selbst Sokrates war gegen solch eine Gesellschaftsordnung, da die besten Ideen nicht durch die Vielen, sondern durch einige wenige Kluge und Aufrichtige in die Welt kommen. Man müsse die Vielen lediglich manipulieren und würde auf diese Weise quasi jeden Unfug umsetzen können. Die Demokratie war ein Rohrkrepierer. **Die Mogelpackung „Repräsentative Demokratie“** Erst im Zuge der Gründung der USA gelang der Trick, dem Volk die „Repräsentative Demokratie“ unterzujubeln, die sich zwar nach Demokratie anhört, aber mit der Ursprungsdefinition nichts zu tun hat. Man konnte zwischen zwei Parteien wählen, die sich mit ihren jeweiligen Versprechen um die Gunst des Volkes bewarben. Tatsächlich paktierten die Vertreter der gewählten Parteien (Politiker) aber mit den wirklich Mächtigen, die letztendlich dafür sorgten, dass diese Politiker in die jeweiligen exponierten Positionen gelangten, welche ihnen ermöglichten (und somit auch den wirklich Mächtigen), Macht auszuüben. Übrigens, ob die eine oder andere Partei „den Volkswillen“ für sich gewinnen konnte, war für die wirklich Mächtigen weniger von Bedeutung, denn der Wille der wirklich Mächtigen wurde so oder so, wenn auch in voneinander differierenden Details, umgesetzt. Die Menschen waren begeistert von dieser Idee, denn sie glaubten, dass sie selbst „der Souverän“ seien. Schluss mit Monarchie sowie sonstiger Fremdherrschaft und Unterdrückung. Die Mächtigen waren ebenfalls begeistert, denn durch die Repräsentative Demokratie waren sie selbst nicht mehr in der Schusslinie, weil das Volk sich mit seinem Unmut fortan auf die Politiker konzentrierte. Da diese Politiker aber vielleicht nicht von einem selbst, sondern von vielen anderen Wahlberechtigten gewählt wurden, lenkte sich der Groll der Menschen nicht nur ab von den wirklich Mächtigen, sondern auch ab von den Politikern, direkt auf „die vielen Idioten“ aus ihrer eigenen Mitte, die sich „ver-wählt“ hatten. Diese Lenkung des Volkes funktionierte so hervorragend, dass andere Länder die Grundprinzipien dieses Steuerungsinstrumentes übernahmen. Dies ist alles bei Rainer Mausfeld nachzulesen. Ursprünglich waren die Mächtigen nur regional mächtig, sodass das Führen der eigenen Menschen(vieh)herde eher eine lokale Angelegenheit war. Somit mussten auch nur lokale Probleme gelöst werden und die Mittel zur Problemlösung blieben im eigenen Problembereich. *** JETZT ABONNIEREN: ***[Hier](https://pareto.space/u/friedenstaube@pareto.space)*** *können Sie die Friedenstaube abonnieren und bekommen die Artikel in Ihr Postfach, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht).* *** * Für **50 CHF/EURO** bekommen Sie ein Jahresabo der Friedenstaube. * Für **120 CHF/EURO** bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube. * Für **500 CHF/EURO** werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube. * Ab **1000 CHF/EURO** werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie). **Für Einzahlungen in CHF (Betreff: Friedenstaube):** [](https://substackcdn.com/image/fetch/f_auto%2Cq_auto%3Agood%2Cfl_progressive%3Asteep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F3fdee17a-c22f-404e-a10c-7f87a7b8182a_2176x998.png) **Für Einzahlungen in Euro:** Milosz Matuschek IBAN DE 53710520500000814137 BYLADEM1TST Sparkasse Traunstein-Trostberg **Betreff: Friedenstaube** Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: <milosz@pareto.space> oder <kontakt@idw-europe.org>. *** **Beherrschungsinstrumente der globalen Massenhaltung** Im Zuge der territorialen Erweiterungen der „Besitzungen“ einiger wirklich Mächtiger wurden die Verwaltungs- und Beherrschungsinstrumente überregionaler. Und heute, zu Zeiten der globalen Vernetzung, paktieren die wirklich Mächtigen miteinander und beanspruchen die Weltherrschaft. Längst wird offen über die finale Realisierung einen Weltregierung, welche die Nationalstaaten „nicht mehr benötigt“, gesprochen. Dass sich Deutschland, ebenso wie andere europäische Staaten, der EU untergeordnet hat, dürfte auch Leuten nicht entgangen sein, die sich nur über die Tagesschau informieren. Längst steht das EU-Recht über dem deutschen Recht. Und nur kurze Zeit ist es her, als die EU und alle ihre Mitgliedsstaaten die WHO autonom darüber entscheiden lassen wollten, was eine Pandemie ist und wie diese für alle verbindlich „bekämpft“ werden soll. Eine spannende Frage ist nun, wer denn über der EU und der WHO sowie anderen Institutionen steht? Diese Beschreibung macht klar, dass ein „souveränes Land“ wie das unverändert von der amerikanischen Armee besetzte Deutschland in der Entscheidungshierarchie an die Weisungen übergeordneter Entscheidungsorgane gebunden ist. An der Spitze stehen - wie kann es anders sein - die wirklich Mächtigen. Aber was nützt es dann, Spitzenpolitiker zu wählen, wenn diese analog Horst Seehofer nichts zu melden haben? Ist das Wählen von Politikern nicht völlig sinnlos, wenn deren Wahlversprechen ohnehin nicht erfüllt werden? Ist es nicht so, dass die Menschen, welche ihre Stimme nicht behalten, sondern abgeben, das bestehende System nur nähren, indem sie Wahlergebnisse akzeptieren, ohne zu wissen, ob diese manipuliert wurden, aber mit der Gewissheit, dass das im Zuge des Wahlkampfes Versprochene auf keinen Fall geliefert wird? Aktive Wähler glauben trotz allem an die Redlichkeit und Wirksamkeit von Wahlen, und sie akzeptieren Wahlergebnisse, weil sie denken, dass sie von „so vielen Idioten, die falsch wählen“, umgeben sind, womit wir wieder bei der Spaltung sind. Sie glauben, der Stand des aktuellen Elends sei „selbst gewählt“. **Die Wahl der Aufseher** Stellen Sie sich bitte vor, Sie wären im Gefängnis, weil Sie einen kritischen Artikel mit „gefällt mir“ gekennzeichnet haben oder weil Sie eine „Kontaktschuld“ trifft, da in Ihrer Nachbarschaft ein „verschwörerisches Symbol“ von einem „aufmerksamen“ Nachbarn bei einer „Meldestelle“ angezeigt wurde oder Sie gar eine Tat, „unterhalb der Strafbarkeitsgrenze“ begangen hätten, dann würden Sie möglicherweise mit Maßnahmen bestraft, die „keine Folter wären“. Beispielsweise würde man Sie während Ihrer „Umerziehungshaft“ mit Waterboarding, Halten von Stresspositionen, Dunkelhaft etc. dabei „unterstützen“, „Ihre Verfehlungen zu überdenken“. Stellen Sie sich weiterhin vor, dass Sie, so wie alle anderen Inhaftierten, an der alle vier Jahre stattfindenden Wahl der Aufseher teilnehmen könnten, und Sie hätten auch einen Favoriten, der zwar Waterboarding betreibt, aber gegen alle anderen Maßnahmen steht. Sie hätten sicher allen Grund zur Freude, wenn Sie Ihren Kandidaten durchbringen könnten, oder? Aber was wäre, wenn der Aufseher Ihrer Wahl dann dennoch alle 3 „Nicht-Folter-Maßnahmen“ anwenden würde, wie sämtliche anderen Aufseher zuvor? Spätestens dann müssten Sie sich eingestehen, dass es der Beruf des Aufsehers ist, Aufseher zu sein und dass er letztendlich tut, was ihm „von oben“ aufgetragen wird. Andernfalls verliert er seinen Job. Oder er verunfallt oder gerät in einen Skandal etc. So oder so, er verliert seinen Job - und den erledigt dann ein anderer Aufseher. Die Wahl des Aufsehers ändert wenig, solange Sie sich im System des Gefängnisses befinden und der Aufseher integraler Bestandteil dieses Systems ist. Zur Realisierung einer tatsächlichen Änderung müssten Sie dort herauskommen. Dieses Beispiel soll darstellen, dass alles in Hierarchien eingebunden ist. Die in einem System eingebundenen Menschen erfüllen ihre zugewiesenen Aufgaben, oder sie werden bestraft. **Das aktuelle System schadet dem Volk** Auch in der staatlichen Organisation von Menschen existieren hierarchische Gliederungen. Eine kommunale Selbstverwaltung gehört zum Kreis, dieser zum Land, dieses zum Staat, dieser zur EU, und diese - zu wem auch immer. Und vereinnahmte Gelder fließen nach oben. Obwohl es natürlich wäre, dass die Mittel dorthin fließen, wo sie der Allgemeinheit und nicht einigen wenigen dienen, also nach unten. Warum muss es also eine Weltregierung geben? Warum sollen nur einige Wenige über alle anderen bestimmen und an diesen verdienen (Nahrung, Medikamente, Krieg, Steuern etc.)? Warum sollen Menschen, so wie Vieh, das jemandem „gehört“, mit einem Code versehen und bereits als Baby zwangsgeimpft werden? Warum müssen alle Transaktionen und sämtliches Verhalten strickt gesteuert, kontrolliert und bewertet werden? Viele Menschen werden nach alledem zu dem Schluss kommen, dass solch ein System nur einigen wenigen wirklich Mächtigen und deren Helfershelfern nützt. Aber es gibt auch eine Gruppe Menschen, für die im Land alles beanstandungsfrei funktioniert. Die Spaltung der Menschen ist perfekt gelungen und sofern die eine Gruppe darauf wartet, dass die andere „endlich aufwacht“, da die Fakten doch auf dem Tisch liegen, so wird sie weiter warten dürfen. Julian Assange erwähnte einst, dass es für ihn eine unglaubliche Enttäuschung war, dass ihm niemand half. Assange hatte Ungeheuerlichkeiten aufgedeckt. Es gab keinen Aufstand. Assange wurde inhaftiert und gefoltert. Es gab keinen Aufstand. Assange sagte, er hätte nicht damit gerechnet, dass die Leute „so unglaublich feige“ seien. Aber womit rechnete er den stattdessen? Dass die Massen „sich erheben“. Das gibt es nur im Film, denn die Masse besteht aus vielen maximal Indoktrinierten, die sich wie Schafe verhalten, was als Züchtungserfolg der Leute an den Schalthebeln der Macht und deren Herren, den wirklich Mächtigen, anzuerkennen ist. Denn wer mächtig ist und bleiben möchte, will sicher keine problematischen Untertanen, sondern eine gefügige, ängstliche Herde, die er nach Belieben ausbeuten und steuern kann. Wenn er hierüber verfügt, will er keinen Widerstand. Ob Corona, Krieg, Demokratie- und Klimarettung oder Meinungsäußerungsverbote und Bürgerrechte, die unterhalb der Strafbarkeitsgrenze liegen, all diese und viele weitere Stichworte mehr sind es, die viele traurig und so manche wütend machen. Auch das Mittel des Demonstrierens hat sich als völlig wirkungslos erwiesen. Die vielen gruseligen Videoaufnahmen über die massivsten Misshandlungen von Demonstranten gegen die Corona-Maßnahmen führen zu dem Ergebnis, dass die Exekutive ihr Gewaltmonopol nutzt(e), um die Bevölkerung gezielt zu verletzen und einzuschüchtern. Bekanntlich kann jede friedliche Demonstration zum Eskalieren gebracht werden, indem man Menschen in die Enge treibt (fehlender Sicherheitsabstand) und einige V-Leute in Zivil mit einschlägigen Flaggen und sonstigen „Symbolen“ einschleust, die für Krawall sorgen, damit die gepanzerten Kollegen dann losknüppeln und die scharfen Hunde zubeißen können. So lauten zumindest die Berichte vieler Zeitzeugen und so ist es auch auf vielen Videos zu sehen. Allerdings nicht im Mainstream. Dieses Vorgehen ist deshalb besonders perfide, weil man den Deutschen ihre Wehrhaftigkeit aberzogen hat. Nicht wehrfähige Bürger und eine brutale Staatsmacht mit Gewaltmonopol führen zu einem Gemetzel bei den Bürgern. Ähnliches lässt sich auch in zivilen Lebenssituationen beobachten, wenn die hiesige zivilisierte Bevölkerung auf „eingereiste“ Massenvergewaltiger und Messerstecher trifft, die über ein anderes Gewalt- und Rechtsverständnis verfügen als die Einheimischen. **System-Technik** Die These ist, dass es eine Gruppe von global agierenden Personen gibt, welche das Geschehen auf der Erde zunehmend wirksam zu ihrem individuellen Vorteil gestaltet. Wie sich diese Gruppe definiert, kann bei John Coleman (Das Komitee der 300) und David Icke nachgelesen werden. Hierbei handelt es ich um Autoren, die jahrzehntelang analog streng wissenschaftlichen Grundlagen zu ihren Themen geforscht haben und in ihren jeweiligen Werken sämtliche Quellen benennen. Diese Autoren wurden vom Mainstream mit dem Prädikatsmerkmal „Verschwörungstheoretiker“ ausgezeichnet, wodurch die Ergebnisse Ihrer Arbeiten umso glaubwürdiger sind. Diese mächtige Gruppe hat mit ihren Schergen nahezu den gesamten Planeten infiltriert, indem sie Personen in führenden Positionen in vielen Belangen größtmögliche Freiheiten sowie Schutz gewährt, aber diesen im Gegenzug eine völlige Unterwerfung bei Kernthemen abfordert. Die Motivatoren für diese Unterwerfung sind, abgesehen von materiellen Zuwendungen, auch „Ruhm und Ehre sowie Macht“. Manchmal wird auch Beweismaterial für begangene Verfehlungen (Lolita-Express, Pizzagate etc.) genutzt, um Forderungen Nachdruck zu verleihen. Und auch körperliche Bestrafungen der betroffenen Person oder deren Angehörigen zählen zum Repertoire der Motivatoren. Letztendlich ähnlich den Verhaltensweisen in einem Mafia-Film. Mit dieser Methodik hat sich diese mächtige Gruppe im Laufe von Jahrhunderten! eine Organisation erschaffen, welche aus Kirchen, Parteien, Firmen, NGO, Vereinen, Verbänden und weiteren Organisationsformen besteht. Bestimmte Ämter und Positionen in Organisationen können nur von Personen eingenommen und gehalten werden, die „auf Linie sind“. Die Mitglieder der Gruppe tauchen in keiner Rubrik wie „Die reichsten Menschen der Welt“ auf, sondern bleiben fern der Öffentlichkeit. Wer jemanden aus ihren Reihen erkennt und beschuldigt, ist ein „Antisemit“ oder sonstiger Übeltäter und wird verfolgt und bekämpft. Über mächtige Vermögensverwaltungskonzerne beteiligen sich die Mitglieder dieser Gruppe anonym an Unternehmen in Schlüsselpositionen in einer Dimension, die ihnen wesentlichen Einfluss auf die Auswahl der Topmanager einräumt, sodass die jeweilige Unternehmenspolitik nach Vorgaben der Gruppe gestaltet wird. Die Gruppe steuert das Geldsystem, von dem sich der Planet abhängig zu sein wähnt. Hierzu eine Erläuterung: Ein Staat wie Deutschland ist bekanntlich maximal verschuldet. Man stelle sich vor, ein unliebsamer Politiker würde entgegen sämtlicher „Brandmauern“ und sonstiger Propaganda und Wahlmanipulationen gewählt, das Land zu führen, dann könnte dieser keine Kredit über 500 Mrd. Euro bei der nächsten Sparkasse beantragen, sondern wäre auf die Mächtigen dieser Welt angewiesen. Jeder weiß, dass Deutschland als Staat kein funktionierendes Geschäftsmodell hat und somit nicht in der Lage ist, solch ein Darlehen zurückzuzahlen. Welche Motivation sollte also jemand haben, einem Land wie Deutschland so viel Geld ohne Aussicht auf Rückführung zu geben? Es leuchtet ein, dass dieser Politiker andere Gefälligkeiten anbieten müsste, um das Darlehen zu bekommen. Im Falle einer Weigerung zur Kooperation könnte der Staatsapparat mit seinen Staatsdienern, Bürgergeld- und Rentenempfänger etc. nicht mehr bezahlt werden und dieser Politiker wäre schnell wieder weg. Er würde medial hingerichtet. Es ist somit davon auszugehen, dass ein Spitzenpolitiker dieser Tage nicht über viele Optionen verfügt, denn er übernimmt eine Situation, die von seinen Vorgängern erschaffen wurde. Trotz alledem darauf zu hoffen, dass es einen anderen Politiker geben könnte, mit dem dann alles wieder gut wird, mutet ziemlich infantil an. Dass ein Großteil der Medien von Zuwendungen abhängig ist, dürfte ebenfalls leicht nachzuvollziehen sein, denn der gewöhnliche Bürger zahlt nichts für den Content der MSM. Abhängig davon, von wem (Regierung, Philanthrop, Konzern etc.) ein Medium am Leben gehalten wird, gestalten sich auch dessen Inhalte. Und wenn angewiesen wird, dass ein Politiker medial hingerichtet werden soll, dann bedient die Maschinerie das Thema. Man beobachte einfach einmal, dass Politiker der Kartell-Parteien völlig anders behandelt werden als solche jenseits der „Brandmauer“. Und der Leser, der solche Auftragsarbeiten kostenlos liest, ist der Konsument, für dessen Indoktrination die Finanziers der Verlage gerne zahlen. Mittlerweile kann durch die Herrschaft über die Medien und die systematische Vergiftung der Körper und Geister der Population die öffentliche Meinung gesteuert werden. Die überwiegende Zahl der Deutschen scheint nicht mehr klar denken zu können. Wer sich das aktuelle Geschehen in der deutschen Politik mit klarem Verstand ansieht, kommt nicht umhin, eine Fernsteuerung der handelnden Politiker in Betracht zu ziehen. Aber was soll daran verwundern? Sind es deshalb „böse Menschen“? Sind die in „Forschungslaboren“ arbeitenden Quäler von „Versuchstieren“ böse Menschen? Sind der Schlächter, der Folterer und der Henker böse Menschen? Oder der knüppelnde Polizist? Es handelt sich zunächst einmal um Personen, die einen Vorteil dadurch haben, Ihrer Tätigkeit nachzugehen. Sie sind integrale Bestandteile eines Belohnungssystems, welches von oben nach unten Anweisungen gibt. Und wenn diese Anweisungen nicht befolgt werden, führt dies für den Befehlsverweigerer zu Konsequenzen. **Der klare Verstand** Es ist nun eine spannende Frage, warum so viele Menschen sich solch eine Behandlung gefallen lassen? Nun, das ist relativ einfach, denn das angepasste Verhalten der Vielen ist nichts anderes als ein Züchtungserfolg der Wenigen. Die Psyche der Menschen ist ebenso akribisch erforscht worden wie deren Körperfunktionen. Würden die Menschen von den wirklich Mächtigen geliebt, dann würde genau gewusst, wie sie zu behandeln und mit ihren jeweiligen Bedürfnissen zu versorgen sind. Stattdessen werden die Menschen aber als eine Einnahmequelle betrachtet. Dies manifestiert sich exemplarisch in folgenden Bereichen: 1. Das Gesundheitssystem verdient nichts am gesunden Menschen, sondern nur am (dauerhaft) kranken, der um Schmerzlinderung bettelt. Bereits als Baby werden Menschen geimpft, was die jeweilige Gesundheit (mit Verweis auf die Werke von Anita Petek-Dimmer u. a.) nachhaltig negativ beeinflusst. Wer hat denn heute keine Krankheiten? Die „Experten“ des Gesundheitssystems verteufeln Vitamin D, Vitamin C, Lithium, die Sonne, Natur etc. und empfehlen stattdessen Präparate, die man patentieren konnte und mit denen die Hersteller viel Geld verdienen. Die Präparate heilen selten, sondern lindern bestenfalls zuvor künstlich erzeugte Leiden, und müssen oftmals dauerhaft eingenommen werden. Was ist aus den nicht Geimpften geworden, die alle sterben sollten? Sind diese nicht die einzigen Gesunden dieser Tage? Ist nicht jeder Geimpfte entweder permanent krank oder bereits tot? Abgesehen von denen, welche das Glück hatten, „Sonderchargen“ mit Kochsalz zu erhalten. \ \ Wem gehören die wesentlichen Player im Gesundheitswesen zu einem erheblichen Teil? Die Vermögensverwalter der wirklich Mächtigen. 2. Ähnlich gestaltet es sich bei der Ernährungsindustrie. Die von dort aus verabreichten Produkte sind die Ursachen für den Gesundheitszustand der deutschen Population. Das ist aber auch irgendwie logisch, denn wer sich nicht falsch ernährt und gesund bleibt, wird kein Kunde des Gesundheitswesens. \ \ Die Besitzverhältnisse in der Ernährungsindustrie ähneln denen im Gesundheitswesen, sodass am gleichen Kunden gearbeitet und verdient wird. 3. Die Aufzählung konnte nun über die meisten Branchen, in denen mit dem Elend der Menschen viel verdient werden kann, fortgesetzt werden. Waffen (BlackRock erhöhte beispielsweise seine Anteile an der Rheinmetall AG im Juni 2024 auf 5,25 Prozent. Der US-Vermögensverwalter ist damit der zweitgrößte Anteilseigner nach der französischen Großbank Société Générale.), Energie, Umwelt, Technologie, IT, Software, KI, Handel etc. Wie genau Chemtrails und Technologien wie 5G auf den Menschen und die Tiere wirken, ist ebenfalls umstritten. Aber ist es nicht seltsam, wie krank, empathielos, antriebslos und aggressiv viele Menschen heute sind? Was genau verabreicht man der Berliner Polizei, damit diese ihre Prügelorgien auf den Rücken und in den Gesichtern der Menschen wahrnehmen, die friedlich ihre Demonstrationsrechte wahrnehmen? Und was erhalten die ganzen zugereisten „Fachkräfte“, die mit Ihren Autos in Menschenmengen rasen oder auch Kinder und Erwachsene niedermessern? Das Titelbild dieses Beitrags zeigt einige Gebilde, welche regelmäßig bei Obduktionen von Geimpften in deren Blutgefäßen gefunden werden. Wie genau wirken diese kleinen Monster? Können wir Menschen ihr Unverständnis und ihr Nicht-Aufwachen vorwerfen, wenn wir erkennen, dass diese Menschen maximal vergiftet wurden? Oder sollten einfach Lösungen für die Probleme dieser Zeit auch ohne den Einbezug derer gefunden werden, die offenbar nicht mehr Herr ihrer Sinne sind? **Die Ziele der wirklich Mächtigen** Wer sich entsprechende Videosequenzen der Bilderberger, des WEF und anderen „Überorganisationen“ ansieht, der erkennt schnell das Muster: * Reduzierung der Weltpopulation um ca. 80 Prozent * Zusammenbruch der Wirtschaft, damit diese von den Konzernen übernommen werden kann. * Zusammenbruch der öffentlichen Ordnung, um eine totale Entwaffnung und eine totale Überwachung durchsetzen zu können. * Zusammenbruch der Regierungen, damit die Weltregierung übernehmen kann. Es ist zu überdenken, ob die Weltregierung tatsächlich das für die Vielen beste Organisationssystem ist, oder ob die dezentrale Eigenorganisation der jeweils lokalen Bevölkerung nicht doch die bessere Option darstellt. Baustellen würden nicht nur begonnen, sondern auch schnell abgearbeitet. Jede Region könnte bestimmen, ob sie sich mit Chemtrails und anderen Substanzen besprühen lassen möchte. Und die Probleme in Barcelona könnte die Menschen dort viel besser lösen als irgendwelche wirklich Mächtigen in ihren Elfenbeintürmen. Die lokale Wirtschaft könnte wieder zurückkommen und mit dieser die Eigenständigkeit. Denn die den wirklich Mächtigen über ihre Vermögensverwalter gehörenden Großkonzerne haben offensichtlich nicht das Wohl der Bevölkerung im Fokus, sondern eher deren Ausbeutung. Das Aussteigen aus dem System ist die wahre Herkulesaufgabe und es bedarf sicher Mut und Klugheit, sich dieser zu stellen. Die Politiker, die unverändert die Narrative der wirklich Mächtigen bedienen, sind hierfür denkbar ungeeignet, denn sie verfolgen kein Lebensmodell, welches sich von Liebe und Mitgefühl geleitet in den Dienst der Gesamtheit von Menschen, Tieren und Natur stellt. Schauen Sie einmal genau hin, denken Sie nach und fühlen Sie mit. **Was tun?** Jedes System funktioniert nur so lange, wie es unterstützt wird. Somit stellt sich die Frage, wie viele Menschen das System ignorieren müssen, damit es kollabiert, und auf welche Weise dieses Ignorieren durchzuführen ist? Merkbar ist, dass die große Masse der Verwaltungsangestellten krank und oder unmotiviert und somit nicht wirksam ist. Würden die entsprechenden Stellen massiv belastet und parallel hierzu keine Einnahmen mehr realisieren, wäre ein Kollaps nah. Die Prügelpolizisten aus Berlin können nicht überall sein und normale Polizisten arbeiten nicht gegen unbescholtene Bürger, sondern sorgen sich selbst um ihre Zukunft. Gewalt ist sicher keine Lösung, und sicher auch nicht erforderlich. Wie eine gerechte Verwaltungsform aufgebaut werden muss? Einfach so, wie sie in den hiesigen Gesetzen beschrieben steht. Aber eine solche Organisationsform muss frei sein von Blockparteien und korrupten Politikern und weisungsgebundenen Richtern etc. Stattdessen werden Menschen benötigt, welche die Menschen lieben und ihnen nicht schaden wollen. Außerdem sollten diese Führungspersonen auch wirklich etwas können, und nicht nur „Politiker“ ohne weitere Berufserfahrungen sein. *** Ludwig F. Badenhagen (Pseudonym, Name ist der Redaktion bekannt). *Der Autor hat deutsche Wurzeln und betrachtet das Geschehen in Deutschland und Europa aus seiner Wahlheimat Südafrika. Seine Informationen bezieht er aus verlässlichen Quellen und insbesondere von Menschen, die als „Verschwörungstheoretiker“, „Nazi“, „Antisemit“ sowie mit weiteren Kampfbegriffen der dortigen Systemakteure wie Politiker und „Journalisten“ diffamiert werden. Solche Diffamierungen sind für ihn ein Prädikatsmerkmal. Er ist international agierender Manager mit einem globalen Netzwerk und verfügt hierdurch über tiefe Einblicke in Konzerne und Politik.* *** **Not yet on** **[Nostr](https://nostr.com/)** **and want the full experience?** Easy onboarding via **[Start.](https://start.njump.me/)** @ 3104fbbf:ac623068
2025-04-04 06:58:30 ## **Introduction** If you have a functioning brain, it’s impossible to fully stand for any politician or align completely with any political party. The solutions we need are not found in the broken systems of power but in individual actions and local initiatives. Voting for someone may be your choice, but relying solely on elections every few years as a form of political activism is a losing strategy. People around the world have fallen into the trap of thinking that casting a ballot once every four years is enough, only to return to complacency as conditions worsen. Voting for the "lesser of two evils" has been the norm for decades, yet expecting different results from the same flawed system is naive at best. The truth is, governments are too corrupt to save us. In times of crisis, they won’t come to your aid—instead, they will tighten their grip, imposing more surveillance, control, and wealth extraction to benefit the oligarch class. To break free from this cycle, we must first protect ourselves individually—financially, geographically, and digitally—alongside our families. Then, we must organize and build resilient local communities. These are the only ways forward. History has shown us time and again that the masses are easily deceived by the political circus, falling for the illusion of a "savior" who will fix everything. But whether right, center, or left, the story remains the same: corruption, lies, and broken promises. If you possess a critical and investigative mind, you know better than to place your trust in politicians, parties, or self-proclaimed heroes. The real solution lies in free and sovereign individuals who reject the herd mentality and take responsibility for their own lives. From the beginning of time, true progress has come from individuals who think for themselves and act independently. The nauseating web of politicians, billionaires, and oligarchs fighting for power and resources has never been—and will never be—the answer to our problems. In a world increasingly dominated by corrupted governments, NGOs, and elites, ordinary people must take proactive steps to protect themselves and their families. --- ## **1. Financial Protection: Reclaiming Sovereignty Through Bitcoin** Governments and central banks have long manipulated fiat currencies, eroding wealth through inflation and bailouts that transfer resources to the oligarch class. Bitcoin, as a decentralized, censorship-resistant, and finite currency, offers a way out. Here’s what individuals can do: - **Adopt Bitcoin as a Savings Tool**: Shift a portion of your savings into Bitcoin to protect against inflation and currency devaluation. Bitcoin’s fixed supply (21 million coins) ensures it cannot be debased like fiat money. - **Learn Self-Custody**: Store your Bitcoin in a hardware wallet or use open-source software wallets. Avoid centralized exchanges, which are vulnerable to government seizure or collapse. - **Diversify Geographically:** Hold assets in multiple jurisdictions to reduce the risk of confiscation or capital controls. Consider offshore accounts or trusts if feasible. - **Barter and Local Economies**: In times of crisis, local barter systems and community currencies can bypass failing national systems. Bitcoin can serve as a global medium of exchange in such scenarios. --- ## 2. Geographical Flexibility: Reducing Dependence on Oppressive Systems Authoritarian regimes thrive on controlling populations within fixed borders. By increasing geographical flexibility, individuals can reduce their vulnerability: - **Obtain Second Passports or Residencies**: Invest in citizenship-by-investment programs or residency permits in countries with greater freedoms and lower surveillance. - **Relocate to Freer Jurisdictions**: Research and consider moving to regions with stronger property rights, lower taxes, and less government overreach. - **Decentralize Your Life**: Avoid keeping all your assets, family, or business operations in one location. Spread them across multiple regions to mitigate risks. --- ## 3. Digital Privacy: Fighting Surveillance with Advanced Tools The rise of mass surveillance and data harvesting by governments and corporations threatens individual freedom. Here’s how to protect yourself: - **Use Encryption**: Encrypt all communications using tools like Signal or ProtonMail. Ensure your devices are secured with strong passwords and biometric locks. - **Adopt Privacy-Focused Technologies**: Use Tor for anonymous browsing, VPNs to mask your IP address, and open-source operating systems like Linux to avoid backdoors. - **Reject Surveillance Tech**: Avoid smart devices that spy on you (e.g., Alexa, Google Home). Opt for decentralized alternatives like Mastodon instead of Twitter, or PeerTube instead of YouTube. - **Educate Yourself on Digital Privacy**: Learn about tools and practices that enhance your online privacy and security. --- ## 4. Building Resilient Local Communities: The Foundation of a Free Future While individual actions are crucial, collective resilience is equally important. Governments are too corrupt to save populations in times of crisis—history shows they will instead impose more control and transfer wealth to the elite. To counter this, communities must organize locally: - **Form Mutual Aid Networks**: Create local groups that share resources, skills, and knowledge. These networks can provide food, medical supplies, and security during crises. - **Promote Local Economies**: Support local businesses, farmers, and artisans. Use local currencies or barter systems to reduce dependence on centralized financial systems. - **Develop Off-Grid Infrastructure**: Invest in renewable energy, water filtration, and food production to ensure self-sufficiency. Community gardens, solar panels, and rainwater harvesting are excellent starting points. - **Educate and Empower**: Host workshops on financial literacy, digital privacy, and sustainable living. Knowledge is the most powerful tool against authoritarianism. --- ## 5. The Bigger Picture: Rejecting the Illusion of Saviors The deep corruption within governments, NGOs, and the billionaire class is evident. These entities will never act in the interest of ordinary people. Instead, they will exploit crises to expand surveillance, control, and wealth extraction. The idea of a political “savior” is a dangerous illusion. True freedom comes from individuals taking responsibility for their own lives and working together to build decentralized, resilient systems. --- ## Conclusion: A Call to Action The path to a genuinely free humanity begins with individual action. By adopting Bitcoin, securing digital privacy, increasing geographical flexibility, and building resilient local communities, ordinary people can protect themselves against authoritarianism. Governments will not save us—they are the problem. It is up to us to create a better future, free from the control of corrupt elites. - The tools for liberation already exist. - The question is: will we use them? For those interested, I share ideas and solutions in my book « THE GATEWAY TO FREEDOM » https://blisshodlenglish.substack.com/p/the-gateway-to-freedom ⚡ **The time to act is now. Freedom is not given—it is taken.** ⚡ ###### If you enjoyed this article, consider supporting it with a Zap! --- My Substack ENGLISH = https://blisshodlenglish.substack.com/ My substack FRENCH = https://blisshodl.substack.com/ --- Get my Book « THE GATEWAY TO FREEDOM » here 🙏 => https://coinos.io/blisshodl --- ---
@ 3104fbbf:ac623068
2025-04-04 06:58:30 ## **Introduction** If you have a functioning brain, it’s impossible to fully stand for any politician or align completely with any political party. The solutions we need are not found in the broken systems of power but in individual actions and local initiatives. Voting for someone may be your choice, but relying solely on elections every few years as a form of political activism is a losing strategy. People around the world have fallen into the trap of thinking that casting a ballot once every four years is enough, only to return to complacency as conditions worsen. Voting for the "lesser of two evils" has been the norm for decades, yet expecting different results from the same flawed system is naive at best. The truth is, governments are too corrupt to save us. In times of crisis, they won’t come to your aid—instead, they will tighten their grip, imposing more surveillance, control, and wealth extraction to benefit the oligarch class. To break free from this cycle, we must first protect ourselves individually—financially, geographically, and digitally—alongside our families. Then, we must organize and build resilient local communities. These are the only ways forward. History has shown us time and again that the masses are easily deceived by the political circus, falling for the illusion of a "savior" who will fix everything. But whether right, center, or left, the story remains the same: corruption, lies, and broken promises. If you possess a critical and investigative mind, you know better than to place your trust in politicians, parties, or self-proclaimed heroes. The real solution lies in free and sovereign individuals who reject the herd mentality and take responsibility for their own lives. From the beginning of time, true progress has come from individuals who think for themselves and act independently. The nauseating web of politicians, billionaires, and oligarchs fighting for power and resources has never been—and will never be—the answer to our problems. In a world increasingly dominated by corrupted governments, NGOs, and elites, ordinary people must take proactive steps to protect themselves and their families. --- ## **1. Financial Protection: Reclaiming Sovereignty Through Bitcoin** Governments and central banks have long manipulated fiat currencies, eroding wealth through inflation and bailouts that transfer resources to the oligarch class. Bitcoin, as a decentralized, censorship-resistant, and finite currency, offers a way out. Here’s what individuals can do: - **Adopt Bitcoin as a Savings Tool**: Shift a portion of your savings into Bitcoin to protect against inflation and currency devaluation. Bitcoin’s fixed supply (21 million coins) ensures it cannot be debased like fiat money. - **Learn Self-Custody**: Store your Bitcoin in a hardware wallet or use open-source software wallets. Avoid centralized exchanges, which are vulnerable to government seizure or collapse. - **Diversify Geographically:** Hold assets in multiple jurisdictions to reduce the risk of confiscation or capital controls. Consider offshore accounts or trusts if feasible. - **Barter and Local Economies**: In times of crisis, local barter systems and community currencies can bypass failing national systems. Bitcoin can serve as a global medium of exchange in such scenarios. --- ## 2. Geographical Flexibility: Reducing Dependence on Oppressive Systems Authoritarian regimes thrive on controlling populations within fixed borders. By increasing geographical flexibility, individuals can reduce their vulnerability: - **Obtain Second Passports or Residencies**: Invest in citizenship-by-investment programs or residency permits in countries with greater freedoms and lower surveillance. - **Relocate to Freer Jurisdictions**: Research and consider moving to regions with stronger property rights, lower taxes, and less government overreach. - **Decentralize Your Life**: Avoid keeping all your assets, family, or business operations in one location. Spread them across multiple regions to mitigate risks. --- ## 3. Digital Privacy: Fighting Surveillance with Advanced Tools The rise of mass surveillance and data harvesting by governments and corporations threatens individual freedom. Here’s how to protect yourself: - **Use Encryption**: Encrypt all communications using tools like Signal or ProtonMail. Ensure your devices are secured with strong passwords and biometric locks. - **Adopt Privacy-Focused Technologies**: Use Tor for anonymous browsing, VPNs to mask your IP address, and open-source operating systems like Linux to avoid backdoors. - **Reject Surveillance Tech**: Avoid smart devices that spy on you (e.g., Alexa, Google Home). Opt for decentralized alternatives like Mastodon instead of Twitter, or PeerTube instead of YouTube. - **Educate Yourself on Digital Privacy**: Learn about tools and practices that enhance your online privacy and security. --- ## 4. Building Resilient Local Communities: The Foundation of a Free Future While individual actions are crucial, collective resilience is equally important. Governments are too corrupt to save populations in times of crisis—history shows they will instead impose more control and transfer wealth to the elite. To counter this, communities must organize locally: - **Form Mutual Aid Networks**: Create local groups that share resources, skills, and knowledge. These networks can provide food, medical supplies, and security during crises. - **Promote Local Economies**: Support local businesses, farmers, and artisans. Use local currencies or barter systems to reduce dependence on centralized financial systems. - **Develop Off-Grid Infrastructure**: Invest in renewable energy, water filtration, and food production to ensure self-sufficiency. Community gardens, solar panels, and rainwater harvesting are excellent starting points. - **Educate and Empower**: Host workshops on financial literacy, digital privacy, and sustainable living. Knowledge is the most powerful tool against authoritarianism. --- ## 5. The Bigger Picture: Rejecting the Illusion of Saviors The deep corruption within governments, NGOs, and the billionaire class is evident. These entities will never act in the interest of ordinary people. Instead, they will exploit crises to expand surveillance, control, and wealth extraction. The idea of a political “savior” is a dangerous illusion. True freedom comes from individuals taking responsibility for their own lives and working together to build decentralized, resilient systems. --- ## Conclusion: A Call to Action The path to a genuinely free humanity begins with individual action. By adopting Bitcoin, securing digital privacy, increasing geographical flexibility, and building resilient local communities, ordinary people can protect themselves against authoritarianism. Governments will not save us—they are the problem. It is up to us to create a better future, free from the control of corrupt elites. - The tools for liberation already exist. - The question is: will we use them? For those interested, I share ideas and solutions in my book « THE GATEWAY TO FREEDOM » https://blisshodlenglish.substack.com/p/the-gateway-to-freedom ⚡ **The time to act is now. Freedom is not given—it is taken.** ⚡ ###### If you enjoyed this article, consider supporting it with a Zap! --- My Substack ENGLISH = https://blisshodlenglish.substack.com/ My substack FRENCH = https://blisshodl.substack.com/ --- Get my Book « THE GATEWAY TO FREEDOM » here 🙏 => https://coinos.io/blisshodl --- --- @ 57d1a264:69f1fee1
2025-03-23 12:24:46https://www.youtube.com/watch?v=obXEnyQ_Veg    source: https://media.jaguar.com/news/2024/11/fearless-exuberant-compelling-jaguar-reimagined-0 originally posted at https://stacker.news/items/922356
@ 57d1a264:69f1fee1
2025-03-23 12:24:46https://www.youtube.com/watch?v=obXEnyQ_Veg    source: https://media.jaguar.com/news/2024/11/fearless-exuberant-compelling-jaguar-reimagined-0 originally posted at https://stacker.news/items/922356 @ c631e267:c2b78d3e
2025-03-21 19:41:50*Wir werden nicht zulassen, dass technisch manches möglich ist,* *\ aber der Staat es nicht nutzt.* *\ Angela Merkel*   **Die Modalverben zu erklären, ist im Deutschunterricht manchmal nicht ganz einfach.** Nicht alle Fremdsprachen unterscheiden zum Beispiel bei der Frage nach einer Möglichkeit gleichermaßen zwischen «können» im Sinne von «die Gelegenheit, Kenntnis oder Fähigkeit haben» und «dürfen» als «die Erlaubnis oder Berechtigung haben». Das spanische Wort «poder» etwa steht für beides. **Ebenso ist vielen Schülern auf den ersten Blick nicht recht klar,** dass das logische Gegenteil von «müssen» nicht unbedingt «nicht müssen» ist, sondern vielmehr «nicht dürfen». An den Verkehrsschildern lässt sich so etwas meistens recht gut erklären: Manchmal muss man abbiegen, aber manchmal darf man eben nicht.  **Dieses Beispiel soll ein wenig die Verwirrungstaktik veranschaulichen,** die in der Politik gerne verwendet wird, um unpopuläre oder restriktive Maßnahmen Stück für Stück einzuführen. Zuerst ist etwas einfach innovativ und bringt viele Vorteile. Vor allem ist es freiwillig, jeder kann selber entscheiden, niemand muss mitmachen. Später kann man zunehmend weniger Alternativen wählen, weil sie verschwinden, und irgendwann verwandelt sich alles andere in «nicht dürfen» – die Maßnahme ist obligatorisch. **Um die Durchsetzung derartiger Initiativen strategisch zu unterstützen** und nett zu verpacken, gibt es Lobbyisten, gerne auch NGOs genannt. Dass das «NG» am Anfang dieser Abkürzung übersetzt «Nicht-Regierungs-» bedeutet, ist ein Anachronismus. Das war [vielleicht früher](https://transition-news.org/der-sumpf-aus-ngos-parteien-und-steuergeld) einmal so, heute ist eher das Gegenteil gemeint. **In unserer modernen Zeit wird enorm viel Lobbyarbeit für die Digitalisierung** praktisch sämtlicher Lebensbereiche aufgewendet. Was das auf dem Sektor der Mobilität bedeuten kann, haben wir diese Woche anhand aktueller Entwicklungen in Spanien [beleuchtet](https://transition-news.org/nur-abschied-vom-alleinfahren-monstrose-spanische-uberwachungsprojekte-gemass). Begründet teilweise mit Vorgaben der Europäischen Union arbeitet man dort fleißig an einer «neuen Mobilität», basierend auf «intelligenter» technologischer Infrastruktur. Derartige Anwandlungen wurden auch schon als [«Technofeudalismus»](https://transition-news.org/yanis-varoufakis-der-europaische-traum-ist-tot-es-lebe-der-neue-traum) angeprangert. **Nationale** **[Zugangspunkte](https://transport.ec.europa.eu/transport-themes/smart-mobility/road/its-directive-and-action-plan/national-access-points_en)** **für Mobilitätsdaten im Sinne der EU** gibt es nicht nur in allen Mitgliedsländern, sondern auch in der [Schweiz](https://opentransportdata.swiss/de/) und in Großbritannien. Das Vereinigte Königreich beteiligt sich darüber hinaus an anderen EU-Projekten für digitale Überwachungs- und Kontrollmaßnahmen, wie dem biometrischen [Identifizierungssystem](https://transition-news.org/biometrische-gesichtserkennung-in-britischen-hafen) für «nachhaltigen Verkehr und Tourismus». **Natürlich marschiert auch Deutschland stracks und euphorisch** in Richtung digitaler Zukunft. Ohne [vernetzte Mobilität](https://mobilithek.info/about) und einen «verlässlichen Zugang zu Daten, einschließlich Echtzeitdaten» komme man in der Verkehrsplanung und -steuerung nicht aus, erklärt die Regierung. Der Interessenverband der IT-Dienstleister Bitkom will «die digitale Transformation der deutschen Wirtschaft und Verwaltung vorantreiben». Dazu bewirbt er unter anderem die Konzepte Smart City, Smart Region und Smart Country und behauptet, deutsche Großstädte «setzen bei Mobilität [voll auf Digitalisierung](https://www.smartcountry.berlin/de/newsblog/smart-city-index-grossstaedte-setzen-bei-mobilitaet-voll-auf-digitalisierung.html)». **Es steht zu befürchten, dass das umfassende Sammeln, Verarbeiten und Vernetzen von Daten,** das angeblich die Menschen unterstützen soll (und theoretisch ja auch könnte), eher dazu benutzt wird, sie zu kontrollieren und zu manipulieren. Je elektrischer und digitaler unsere Umgebung wird, desto größer sind diese Möglichkeiten. Im Ergebnis könnten solche Prozesse den Bürger nicht nur einschränken oder überflüssig machen, sondern in mancherlei Hinsicht regelrecht abschalten. Eine gesunde Skepsis ist also geboten. *\[Titelbild:* *[Pixabay](https://pareto.space/readhttps://pixabay.com/de/illustrations/schaufensterpuppe-platine-gesicht-5254046/)]* *** Dieser Beitrag wurde mit dem [Pareto-Client](https://pareto.space/read) geschrieben. Er ist zuerst auf ***[Transition News](https://transition-news.org/das-gegenteil-von-mussen-ist-nicht-durfen)*** erschienen.
@ c631e267:c2b78d3e
2025-03-21 19:41:50*Wir werden nicht zulassen, dass technisch manches möglich ist,* *\ aber der Staat es nicht nutzt.* *\ Angela Merkel*   **Die Modalverben zu erklären, ist im Deutschunterricht manchmal nicht ganz einfach.** Nicht alle Fremdsprachen unterscheiden zum Beispiel bei der Frage nach einer Möglichkeit gleichermaßen zwischen «können» im Sinne von «die Gelegenheit, Kenntnis oder Fähigkeit haben» und «dürfen» als «die Erlaubnis oder Berechtigung haben». Das spanische Wort «poder» etwa steht für beides. **Ebenso ist vielen Schülern auf den ersten Blick nicht recht klar,** dass das logische Gegenteil von «müssen» nicht unbedingt «nicht müssen» ist, sondern vielmehr «nicht dürfen». An den Verkehrsschildern lässt sich so etwas meistens recht gut erklären: Manchmal muss man abbiegen, aber manchmal darf man eben nicht.  **Dieses Beispiel soll ein wenig die Verwirrungstaktik veranschaulichen,** die in der Politik gerne verwendet wird, um unpopuläre oder restriktive Maßnahmen Stück für Stück einzuführen. Zuerst ist etwas einfach innovativ und bringt viele Vorteile. Vor allem ist es freiwillig, jeder kann selber entscheiden, niemand muss mitmachen. Später kann man zunehmend weniger Alternativen wählen, weil sie verschwinden, und irgendwann verwandelt sich alles andere in «nicht dürfen» – die Maßnahme ist obligatorisch. **Um die Durchsetzung derartiger Initiativen strategisch zu unterstützen** und nett zu verpacken, gibt es Lobbyisten, gerne auch NGOs genannt. Dass das «NG» am Anfang dieser Abkürzung übersetzt «Nicht-Regierungs-» bedeutet, ist ein Anachronismus. Das war [vielleicht früher](https://transition-news.org/der-sumpf-aus-ngos-parteien-und-steuergeld) einmal so, heute ist eher das Gegenteil gemeint. **In unserer modernen Zeit wird enorm viel Lobbyarbeit für die Digitalisierung** praktisch sämtlicher Lebensbereiche aufgewendet. Was das auf dem Sektor der Mobilität bedeuten kann, haben wir diese Woche anhand aktueller Entwicklungen in Spanien [beleuchtet](https://transition-news.org/nur-abschied-vom-alleinfahren-monstrose-spanische-uberwachungsprojekte-gemass). Begründet teilweise mit Vorgaben der Europäischen Union arbeitet man dort fleißig an einer «neuen Mobilität», basierend auf «intelligenter» technologischer Infrastruktur. Derartige Anwandlungen wurden auch schon als [«Technofeudalismus»](https://transition-news.org/yanis-varoufakis-der-europaische-traum-ist-tot-es-lebe-der-neue-traum) angeprangert. **Nationale** **[Zugangspunkte](https://transport.ec.europa.eu/transport-themes/smart-mobility/road/its-directive-and-action-plan/national-access-points_en)** **für Mobilitätsdaten im Sinne der EU** gibt es nicht nur in allen Mitgliedsländern, sondern auch in der [Schweiz](https://opentransportdata.swiss/de/) und in Großbritannien. Das Vereinigte Königreich beteiligt sich darüber hinaus an anderen EU-Projekten für digitale Überwachungs- und Kontrollmaßnahmen, wie dem biometrischen [Identifizierungssystem](https://transition-news.org/biometrische-gesichtserkennung-in-britischen-hafen) für «nachhaltigen Verkehr und Tourismus». **Natürlich marschiert auch Deutschland stracks und euphorisch** in Richtung digitaler Zukunft. Ohne [vernetzte Mobilität](https://mobilithek.info/about) und einen «verlässlichen Zugang zu Daten, einschließlich Echtzeitdaten» komme man in der Verkehrsplanung und -steuerung nicht aus, erklärt die Regierung. Der Interessenverband der IT-Dienstleister Bitkom will «die digitale Transformation der deutschen Wirtschaft und Verwaltung vorantreiben». Dazu bewirbt er unter anderem die Konzepte Smart City, Smart Region und Smart Country und behauptet, deutsche Großstädte «setzen bei Mobilität [voll auf Digitalisierung](https://www.smartcountry.berlin/de/newsblog/smart-city-index-grossstaedte-setzen-bei-mobilitaet-voll-auf-digitalisierung.html)». **Es steht zu befürchten, dass das umfassende Sammeln, Verarbeiten und Vernetzen von Daten,** das angeblich die Menschen unterstützen soll (und theoretisch ja auch könnte), eher dazu benutzt wird, sie zu kontrollieren und zu manipulieren. Je elektrischer und digitaler unsere Umgebung wird, desto größer sind diese Möglichkeiten. Im Ergebnis könnten solche Prozesse den Bürger nicht nur einschränken oder überflüssig machen, sondern in mancherlei Hinsicht regelrecht abschalten. Eine gesunde Skepsis ist also geboten. *\[Titelbild:* *[Pixabay](https://pareto.space/readhttps://pixabay.com/de/illustrations/schaufensterpuppe-platine-gesicht-5254046/)]* *** Dieser Beitrag wurde mit dem [Pareto-Client](https://pareto.space/read) geschrieben. Er ist zuerst auf ***[Transition News](https://transition-news.org/das-gegenteil-von-mussen-ist-nicht-durfen)*** erschienen. @ 2fdeba99:fd961eff
2025-03-21 17:16:33# == January 17 2025 Out From Underneath | Prism Shores crazy arms | pigeon pit Humanhood | The Weather Station # == february 07 2025 Wish Defense | FACS Sayan - Savoie | Maria Teriaeva Nowhere Near Today | Midding # == february 14 2025 Phonetics On and On | Horsegirl # == february 21 2025 Finding Our Balance | Tsoh Tso Machine Starts To Sing | Porridge Radio Armageddon In A Summer Dress | Sunny Wa # == february 28 2025 you, infinite | you, infinite On Being | Max Cooper Billboard Heart | Deep Sea Diver # == March 21 2025 Watermelon/Peacock | Exploding Flowers Warlord of the Weejuns | Goya Gumbani
@ 2fdeba99:fd961eff
2025-03-21 17:16:33# == January 17 2025 Out From Underneath | Prism Shores crazy arms | pigeon pit Humanhood | The Weather Station # == february 07 2025 Wish Defense | FACS Sayan - Savoie | Maria Teriaeva Nowhere Near Today | Midding # == february 14 2025 Phonetics On and On | Horsegirl # == february 21 2025 Finding Our Balance | Tsoh Tso Machine Starts To Sing | Porridge Radio Armageddon In A Summer Dress | Sunny Wa # == february 28 2025 you, infinite | you, infinite On Being | Max Cooper Billboard Heart | Deep Sea Diver # == March 21 2025 Watermelon/Peacock | Exploding Flowers Warlord of the Weejuns | Goya Gumbani @ 502ab02a:a2860397
2025-04-04 02:50:35หลังจากที่เราเพิ่งเปิดเรื่องไฟโตสเตอรอลไปหมาด ๆ ถึงเวลาที่ต้องมาคุยกันเรื่อง oryzanol ซึ่งเป็นอีกหนึ่งสารที่ถูกอุตสาหกรรมผลักดันให้เรารู้สึกว่า “ต้องกิน” เหมือนเป็นไอเทมลับสำหรับสุขภาพหัวใจ แต่เดี๋ยวก่อนนะ ทำไมสิ่งที่มนุษย์ไม่เคยต้องการมาก่อนถึงกลายเป็นสิ่งจำเป็นไปได้ ? Oryzanol หรือ gamma-oryzanol เป็นสารประกอบที่พบได้ในน้ำมันรำข้าว มีโครงสร้างเป็น sterol ester ของกรดเฟอรูลิก (Ferulic acid esters of sterols and triterpenes) ซึ่งหมายความว่ามันมีโครงสร้างคล้ายกับไฟโตสเตอรอล แต่มาพร้อมกับองค์ประกอบของสารต้านอนุมูลอิสระที่ได้จากกรดเฟอรูลิก นั่นทำให้มันถูกโฆษณาว่าเป็นสารที่ช่วยลดคอเลสเตอรอล มีฤทธิ์ต้านอนุมูลอิสระ และอาจช่วยลดความเสี่ยงโรคหัวใจ ฟังดูดีใช่ไหม ? แต่มันก็คล้ายกับไฟโตสเตอรอลเลย คือเป็นสารที่ แข่งขันกับคอเลสเตอรอลในการดูดซึม และแน่นอนว่าผลข้างเคียงก็ยังคงอยู่ นั่นคือ มันอาจลดการดูดซึมวิตามิน A, D, E, K ซึ่งเป็นวิตามินที่ละลายในไขมันและจำเป็นต่อร่างกาย นั่นหมายความว่า ในขณะที่มันช่วยลด LDL ในกระดาษ มันอาจทำให้ร่างกายขาดสารอาหารที่สำคัญไปด้วย ปัญหาที่ใหญ่กว่าคือ oryzanol พบมากใน น้ำมันรำข้าว ซึ่งเป็นหนึ่งในน้ำมันพืชที่ผ่านการแปรรูปสูง และการบริโภคน้ำมันพืชมากเกินไปนั้นสัมพันธ์กับ ภาวะอักเสบเรื้อรัง (chronic inflammation), ภาวะต้านอินซูลิน (insulin resistance), และความเสี่ยงโรคหัวใจและหลอดเลือด การที่อุตสาหกรรมบอกให้เราเพิ่ม oryzanol ในอาหาร จึงเป็นเหมือนการผลักให้ผู้คนบริโภคน้ำมันพืชมากขึ้นโดยไม่รู้ตัว ทั้งที่น้ำมันพืชโดยเฉพาะที่ผ่านกรรมวิธีอย่างน้ำมันรำข้าวมีปริมาณโอเมก้า-6 สูง ซึ่งถ้ารับมากเกินไปจะไปกระตุ้นกระบวนการอักเสบในร่างกาย เคยสังเกตไหมครับว่า น้ำมันรำข้าวมักโชว์ตัวเลขเก๋ๆของ Oryzanol แต่กลับไม่โชว์สัดส่วน โอเมก้า 6 กับ โอเมก้า 3 เทียบง่ายๆครับ น้ำมันคาโนลา มีโอเมก้า 6 ราวๆ 2200 - 2800 ต่อน้ำมัน 15 มล. (หน่วยบริโภค) น้ำมันรำข้าว มีโอเมก้า 6 ราวๆ 4,140 - 5,520 มก. ต่อน้ำมัน 15 มล. (หน่วยบริโภค) ในขณะที่โอเมก้า 3 ราวๆ 138 - 276 มก.ต่อน้ำมัน 15 มล. (หน่วยบริโภค) นี่หมายถึงสัดส่วนสูงไปถึงได้ราวๆ 40:1 ทั้งๆที่เราเข้าใจแหละว่าโอเมก้า6 ร่างกายจำเป็น แต่แต่แต่ จำเป็นไม่ได้หมายความว่าจัดหนัก เพราะสิ่งที่เราต้องพึงสังวรคือ สัดส่วนที่สมดุลระหว่าง โอเมก้า3และโอเมก้า6 ดังนั้น 40:1 ไม่เรียกว่าสมดุล ซึ่งจะกระตุ้นการอักเสบเรื้อรัง ในร่างกาย และเกี่ยวข้องกับโรคหัวใจ เบาหวาน และปัญหาสุขภาพอื่นๆ พาเหรดกันมา แต่คุณจะไม่เห็นตัวเลขนี้บนฉลากครับ ผู้ผลิตผิดไหม? จะไปผิดอะไรครับ หน่วยบริโภคแนะนำเขา 1 หน่วยบริโภคคือ 15 มิลลิลิตร หรือ 1 ช้อนโต๊ะ แค่นั้นเอง คำถามคือ มีใครใช้ตามนั้นบ้าง คุณเจียวไข่เจียวใช้เท่าไร ผัดข้าวผัดใช้เท่าไหร่ อ่ะ ผัดผักรวมมิตรก็ได้ เอาแบบเต็มเปี่ยมเลย รู้ไหมว่ามีหลายคนเอาไปทำน้ำสลัด OMG ผมถึงบอกอยู่ครับว่า คุณอย่าไปว่าผู้ผลิตเลย เขาปกป้องตัวเองไว้เรียบร้อยทุกมุมอยู่แล้วครับ ถ้าเรายังไม่อ่านฉลาก ซื้อเครื่องไฟฟ้าไม่เคยดูคู่มือ เซนต์สัญญาแบบไม่อ่านก่อน คุณจะว่าใครจริงไหมครับ ที่น่าสนใจกว่านั้นคือเราเข้าใจกันแล้วใช่ไหมว่า oryzanol ไม่ได้มาจากการกินรำข้าวตรง ๆ แต่ต้องผ่านกระบวนการสกัดที่ซับซ้อนเพื่อได้น้ำมันมาใช้ และวิธีที่อุตสาหกรรมใช้มากที่สุดก็คือ การสกัดด้วยเฮกเซน (Hexane Extraction) ซึ่งเป็นตัวทำละลายเคมีที่อาจมีสารตกค้างในผลิตภัณฑ์สุดท้าย ถึงแม้จะมีวิธีอื่นที่ปลอดภัยกว่า เช่น การสกัดด้วยเอทานอล (Ethanol Extraction), การสกัดด้วยเอนไซม์ (Enzyme-Assisted Extraction), หรือการสกัดด้วยคาร์บอนไดออกไซด์เหนือวิกฤต (Supercritical CO₂ Extraction) แต่ทั้งหมดนี้มีต้นทุนสูงกว่า ทำให้ไม่เป็นที่นิยมในอุตสาหกรรม นั่นหมายความว่า ถ้าผลิตภัณฑ์ที่คุณซื้อไม่ได้ระบุว่าใช้วิธีอื่น ส่วนใหญ่ก็คือเฮกเซนแน่นอน ข้อเสียของการบริโภค oryzanol มากเกินไปไม่ได้จบแค่การขัดขวางการดูดซึมวิตามิน เพราะการบริโภคในปริมาณสูงอาจส่งผลให้เกิด ความไม่สมดุลของฮอร์โมน เนื่องจาก oryzanol มีโครงสร้างคล้ายกับสเตอรอลในร่างกาย มันอาจไปรบกวนกระบวนการเผาผลาญของสเตอรอยด์ฮอร์โมน เช่น ฮอร์โมนเพศชาย (Testosterone) และฮอร์โมนความเครียด (Cortisol) ซึ่งในระยะยาวอาจส่งผลต่อระบบภูมิคุ้มกัน อารมณ์ และระดับพลังงานของร่างกาย ประเด็นที่สำคัญคือ ในเมื่อเรามีอาหารจากธรรมชาติที่ช่วยบำรุงหัวใจได้โดยไม่ต้องมีผลข้างเคียง เช่น ไขมันสัตว์ดี ๆ ที่มีวิตามิน A, D, E, K ครบถ้วน ทำไมต้องพึ่งพาสารสกัดจากอุตสาหกรรม ? สิ่งที่ดูเหมือนดีจากงานวิจัยในแล็บ อาจไม่ได้ดีในระยะยาวเมื่ออยู่ในร่างกายมนุษย์จริง ๆ ทีนี้เรามาดูจุดขายของ น้ำมันรำข้าวกัน - oryzanol เป็นสารธรรมชาติ ทนความร้อนสูง เอาไปใช้ทอดจะไม่เกิดการสลายตัว ทนความร้อนสูงนี่จริงเลยครับ โอริซานอลเป็นสารต้านอนุมูลอิสระในกลุ่ม Ferulic Acid Esters ซึ่งมีโครงสร้างเสถียรกว่าวิตามินอี (เทียบกับวิตามินอีเพราะ ต้านอนุมูลอิสระ และ การปกป้องไขมันจากการเกิดออกซิเดชัน ) มี จุดสลายตัวสูงกว่า 250°C ซึ่งทำให้ยังคงอยู่ได้ในอุณหภูมิที่ใช้ทอดอาหาร แล้วมันแปลว่าดีจริงไหม? ในขณะที่ น้ำมันรำข้าวมีโอเมก้า-6 สูงมาก (30-40%) ซึ่งไวต่อการเกิดออกซิเดชัน ถึงแม้โอริซานอลจะช่วยชะลอการเหม็นหืน แต่มันไม่ได้ช่วยลดการเกิด สารพิษจากไขมันไหม้ เช่น Aldehydes หรือ HNE (4-Hydroxy-2-nonenal) ที่มาจากโอเมก้า-6 หรือเปล่า??? มันคือการพูดให้เราไปโฟกัสจุดเดียวครับ "โอริซานอลทนร้อน ไม่ได้แปลว่า น้ำมันรำข้าวดีต่อสุขภาพ" เพราะโอเมก้า6 ที่ไวต่อการเกิดออกซิเดชัน รวมถึงวิตามินต่างๆ ก็ยังสูญสลายไปด้วยความร้อน นี่ยังไม่รวมถึงโทษของการกินโอริซานอลมากไปตามที่ให้ข้อมูลไว้ข้างบนด้วย นอกจากนี้ยังมีคนตั้งคำถามไว้มากมายว่า หากโอริซานอลมีผลชัดเจนต่อสุขภาพเช่นเดียวกับที่โฆษณา ทำไมจึงไม่ได้รับการพัฒนาเป็นยาอย่างจริงจัง? หรือคำตอบคือ งานวิจัยที่สนับสนุนโอริซานอลยังไม่เพียงพอ และในหลายกรณี ผลของมันอาจเกิดจาก Placebo Effect (ผลจากความเชื่อว่ามันได้ผล มากกว่าผลจริงๆ ของสารนั้น) ซึ่งเป็นลักษณะเดียวกับ "ยาหลอก" ที่ไม่ได้มีฤทธิ์ทางชีวเคมีที่ส่งผลชัดเจน - มีไลโนเลอิกสูง ใช่ครับไม่ผิดเลยในจุดนี้ ไลโนเลอิก (Linoleic acid) เป็น กรดไขมันไม่อิ่มตัวชนิดหลายพันธะ (Polyunsaturated Fatty Acid, PUFA) ที่สำคัญและจำเป็นสำหรับร่างกาย โดยเฉพาะอย่างยิ่งในการช่วยบำรุงเซลล์และระบบต่างๆ ของร่างกาย ที่สำคัญคือ ไลโนเลอิกเป็นกรดไขมันในกลุ่ม โอเมก้า-6 เป็นสิ่งที่บอกกับเราชัดๆว่า โอเมก้า6 สูงนั่นเอง ถ้าจะดึงเฉพาะข้อดีมาคุยกันก็ไม่ผิดอะไรเลยครับ เพราะโอเมก้า6 สำคัญกับร่างกายจริงๆ แต่ แต่ แต่ การรับโอเมก้า-6 ในปริมาณสูงเกินไปอาจทำให้เกิดการอักเสบในร่างกาย ซึ่งเกี่ยวข้องกับโรคต่างๆ เช่น โรคหัวใจ โรคมะเร็ง และโรคเบาหวาน อย่างที่เรารู้กัน ดังนั้นที่บอกไว้ข้างบนครับ สัดส่วนโอเมก้า 6:3 คือ 40:1 หรือใน 1 ช้อนโต๊ะ มีโอเมก้า 6 สูงถึง ราวๆ 4,140 - 5,520 มก. เรียกว่าโฆษณาไม่ผิดเลยเรื่องปริมาณ แต่จริงๆแล้วเราควรรักษาสมดุล โอเมก้า 6:3 ให้ใกล้เคียง 1:1 มากที่สุดเท่าที่ทำได้ เราก็อาจต้องตั้งคำถามอีกทีว่า การมีไลโนเลอิกสูง มันดีจริงไหม - โทโคฟีรอล (Tocopherols) เป็นสารประกอบที่อยู่ในกลุ่ม วิตามินอี เป็นสารต้านอนุมูลอิสระในร่างกาย โดยช่วยปกป้องเซลล์จากความเสียหายจากอนุมูลอิสระและช่วยชะลอการเสื่อมของเซลล์ ถูกต้องตามโฆษณา จริงๆหน้าที่หลักคือปกป้องไขมันไม่ให้เกิดการออกซิเดชัน ซึ่งสามารถช่วยยืดอายุการใช้งานของน้ำมัน หรือไม่ให้เกิดการหืน นั่นเอง แต่การทอดหรือปรุงอาหารในอุณหภูมิสูงเกินไป ก็อาจทำให้น้ำมันเกิดการออกซิเดชันและเกิดสารพิษที่เป็นอันตรายต่อร่างกายได้ อย่าลืมนะครับว่าคำแนะนำในการใช้น้ำมันรำข้าว กลับชูการเหมาะกับอาหารทอดอุณหภูมิสูง - โทโคไทรอีนอล (Tocotrienols) เป็นส่วนหนึ่งของกลุ่ม วิตามินอี เช่นกัน การบริโภคมากเกินไป การรับประทาน โทโคไทรอีนอลในปริมาณมาก อาจมีผลข้างเคียงที่ไม่พึงประสงค์ เช่น ส่งผลกระทบต่อการดูดซึมวิตามินอื่นๆ ในร่างกายโดยเฉพาะวิตามิน K ซึ่งอาจทำให้เกิดปัญหาการแข็งตัวของเลือด, ทำให้ตับทำงานหนักขึ้นในการจัดการกับสารนี้ ซึ่งอาจส่งผลเสียต่อการทำงานของตับระยะยาว สุดท้ายแล้ว เราต้องกลับมาตั้งคำถามว่า เราอยากให้สุขภาพของเราถูกกำหนดโดยการตลาดของอุตสาหกรรม หรือโดยสิ่งที่ธรรมชาติออกแบบมาให้เราตั้งแต่แรก ? ถ้าจะดูแลหัวใจจริง ๆ การกินอาหารที่มนุษย์วิวัฒนาการมากับมันมาตลอด เช่น เนื้อสัตว์ ไข่ ตับ และไขมันดี ๆ อาจเป็นคำตอบที่เรียบง่ายและมีเหตุผลมากกว่าการไล่ตามสารสกัดที่อุตสาหกรรมบอกว่าจำเป็น แต่ธรรมชาติอาจไม่เคยเห็นว่ามันสำคัญเลยก็ได้ #pirateketo #ฉลาก3รู้ #กูต้องรู้มั๊ย #ม้วนหางสิลูก
@ 502ab02a:a2860397
2025-04-04 02:50:35หลังจากที่เราเพิ่งเปิดเรื่องไฟโตสเตอรอลไปหมาด ๆ ถึงเวลาที่ต้องมาคุยกันเรื่อง oryzanol ซึ่งเป็นอีกหนึ่งสารที่ถูกอุตสาหกรรมผลักดันให้เรารู้สึกว่า “ต้องกิน” เหมือนเป็นไอเทมลับสำหรับสุขภาพหัวใจ แต่เดี๋ยวก่อนนะ ทำไมสิ่งที่มนุษย์ไม่เคยต้องการมาก่อนถึงกลายเป็นสิ่งจำเป็นไปได้ ? Oryzanol หรือ gamma-oryzanol เป็นสารประกอบที่พบได้ในน้ำมันรำข้าว มีโครงสร้างเป็น sterol ester ของกรดเฟอรูลิก (Ferulic acid esters of sterols and triterpenes) ซึ่งหมายความว่ามันมีโครงสร้างคล้ายกับไฟโตสเตอรอล แต่มาพร้อมกับองค์ประกอบของสารต้านอนุมูลอิสระที่ได้จากกรดเฟอรูลิก นั่นทำให้มันถูกโฆษณาว่าเป็นสารที่ช่วยลดคอเลสเตอรอล มีฤทธิ์ต้านอนุมูลอิสระ และอาจช่วยลดความเสี่ยงโรคหัวใจ ฟังดูดีใช่ไหม ? แต่มันก็คล้ายกับไฟโตสเตอรอลเลย คือเป็นสารที่ แข่งขันกับคอเลสเตอรอลในการดูดซึม และแน่นอนว่าผลข้างเคียงก็ยังคงอยู่ นั่นคือ มันอาจลดการดูดซึมวิตามิน A, D, E, K ซึ่งเป็นวิตามินที่ละลายในไขมันและจำเป็นต่อร่างกาย นั่นหมายความว่า ในขณะที่มันช่วยลด LDL ในกระดาษ มันอาจทำให้ร่างกายขาดสารอาหารที่สำคัญไปด้วย ปัญหาที่ใหญ่กว่าคือ oryzanol พบมากใน น้ำมันรำข้าว ซึ่งเป็นหนึ่งในน้ำมันพืชที่ผ่านการแปรรูปสูง และการบริโภคน้ำมันพืชมากเกินไปนั้นสัมพันธ์กับ ภาวะอักเสบเรื้อรัง (chronic inflammation), ภาวะต้านอินซูลิน (insulin resistance), และความเสี่ยงโรคหัวใจและหลอดเลือด การที่อุตสาหกรรมบอกให้เราเพิ่ม oryzanol ในอาหาร จึงเป็นเหมือนการผลักให้ผู้คนบริโภคน้ำมันพืชมากขึ้นโดยไม่รู้ตัว ทั้งที่น้ำมันพืชโดยเฉพาะที่ผ่านกรรมวิธีอย่างน้ำมันรำข้าวมีปริมาณโอเมก้า-6 สูง ซึ่งถ้ารับมากเกินไปจะไปกระตุ้นกระบวนการอักเสบในร่างกาย เคยสังเกตไหมครับว่า น้ำมันรำข้าวมักโชว์ตัวเลขเก๋ๆของ Oryzanol แต่กลับไม่โชว์สัดส่วน โอเมก้า 6 กับ โอเมก้า 3 เทียบง่ายๆครับ น้ำมันคาโนลา มีโอเมก้า 6 ราวๆ 2200 - 2800 ต่อน้ำมัน 15 มล. (หน่วยบริโภค) น้ำมันรำข้าว มีโอเมก้า 6 ราวๆ 4,140 - 5,520 มก. ต่อน้ำมัน 15 มล. (หน่วยบริโภค) ในขณะที่โอเมก้า 3 ราวๆ 138 - 276 มก.ต่อน้ำมัน 15 มล. (หน่วยบริโภค) นี่หมายถึงสัดส่วนสูงไปถึงได้ราวๆ 40:1 ทั้งๆที่เราเข้าใจแหละว่าโอเมก้า6 ร่างกายจำเป็น แต่แต่แต่ จำเป็นไม่ได้หมายความว่าจัดหนัก เพราะสิ่งที่เราต้องพึงสังวรคือ สัดส่วนที่สมดุลระหว่าง โอเมก้า3และโอเมก้า6 ดังนั้น 40:1 ไม่เรียกว่าสมดุล ซึ่งจะกระตุ้นการอักเสบเรื้อรัง ในร่างกาย และเกี่ยวข้องกับโรคหัวใจ เบาหวาน และปัญหาสุขภาพอื่นๆ พาเหรดกันมา แต่คุณจะไม่เห็นตัวเลขนี้บนฉลากครับ ผู้ผลิตผิดไหม? จะไปผิดอะไรครับ หน่วยบริโภคแนะนำเขา 1 หน่วยบริโภคคือ 15 มิลลิลิตร หรือ 1 ช้อนโต๊ะ แค่นั้นเอง คำถามคือ มีใครใช้ตามนั้นบ้าง คุณเจียวไข่เจียวใช้เท่าไร ผัดข้าวผัดใช้เท่าไหร่ อ่ะ ผัดผักรวมมิตรก็ได้ เอาแบบเต็มเปี่ยมเลย รู้ไหมว่ามีหลายคนเอาไปทำน้ำสลัด OMG ผมถึงบอกอยู่ครับว่า คุณอย่าไปว่าผู้ผลิตเลย เขาปกป้องตัวเองไว้เรียบร้อยทุกมุมอยู่แล้วครับ ถ้าเรายังไม่อ่านฉลาก ซื้อเครื่องไฟฟ้าไม่เคยดูคู่มือ เซนต์สัญญาแบบไม่อ่านก่อน คุณจะว่าใครจริงไหมครับ ที่น่าสนใจกว่านั้นคือเราเข้าใจกันแล้วใช่ไหมว่า oryzanol ไม่ได้มาจากการกินรำข้าวตรง ๆ แต่ต้องผ่านกระบวนการสกัดที่ซับซ้อนเพื่อได้น้ำมันมาใช้ และวิธีที่อุตสาหกรรมใช้มากที่สุดก็คือ การสกัดด้วยเฮกเซน (Hexane Extraction) ซึ่งเป็นตัวทำละลายเคมีที่อาจมีสารตกค้างในผลิตภัณฑ์สุดท้าย ถึงแม้จะมีวิธีอื่นที่ปลอดภัยกว่า เช่น การสกัดด้วยเอทานอล (Ethanol Extraction), การสกัดด้วยเอนไซม์ (Enzyme-Assisted Extraction), หรือการสกัดด้วยคาร์บอนไดออกไซด์เหนือวิกฤต (Supercritical CO₂ Extraction) แต่ทั้งหมดนี้มีต้นทุนสูงกว่า ทำให้ไม่เป็นที่นิยมในอุตสาหกรรม นั่นหมายความว่า ถ้าผลิตภัณฑ์ที่คุณซื้อไม่ได้ระบุว่าใช้วิธีอื่น ส่วนใหญ่ก็คือเฮกเซนแน่นอน ข้อเสียของการบริโภค oryzanol มากเกินไปไม่ได้จบแค่การขัดขวางการดูดซึมวิตามิน เพราะการบริโภคในปริมาณสูงอาจส่งผลให้เกิด ความไม่สมดุลของฮอร์โมน เนื่องจาก oryzanol มีโครงสร้างคล้ายกับสเตอรอลในร่างกาย มันอาจไปรบกวนกระบวนการเผาผลาญของสเตอรอยด์ฮอร์โมน เช่น ฮอร์โมนเพศชาย (Testosterone) และฮอร์โมนความเครียด (Cortisol) ซึ่งในระยะยาวอาจส่งผลต่อระบบภูมิคุ้มกัน อารมณ์ และระดับพลังงานของร่างกาย ประเด็นที่สำคัญคือ ในเมื่อเรามีอาหารจากธรรมชาติที่ช่วยบำรุงหัวใจได้โดยไม่ต้องมีผลข้างเคียง เช่น ไขมันสัตว์ดี ๆ ที่มีวิตามิน A, D, E, K ครบถ้วน ทำไมต้องพึ่งพาสารสกัดจากอุตสาหกรรม ? สิ่งที่ดูเหมือนดีจากงานวิจัยในแล็บ อาจไม่ได้ดีในระยะยาวเมื่ออยู่ในร่างกายมนุษย์จริง ๆ ทีนี้เรามาดูจุดขายของ น้ำมันรำข้าวกัน - oryzanol เป็นสารธรรมชาติ ทนความร้อนสูง เอาไปใช้ทอดจะไม่เกิดการสลายตัว ทนความร้อนสูงนี่จริงเลยครับ โอริซานอลเป็นสารต้านอนุมูลอิสระในกลุ่ม Ferulic Acid Esters ซึ่งมีโครงสร้างเสถียรกว่าวิตามินอี (เทียบกับวิตามินอีเพราะ ต้านอนุมูลอิสระ และ การปกป้องไขมันจากการเกิดออกซิเดชัน ) มี จุดสลายตัวสูงกว่า 250°C ซึ่งทำให้ยังคงอยู่ได้ในอุณหภูมิที่ใช้ทอดอาหาร แล้วมันแปลว่าดีจริงไหม? ในขณะที่ น้ำมันรำข้าวมีโอเมก้า-6 สูงมาก (30-40%) ซึ่งไวต่อการเกิดออกซิเดชัน ถึงแม้โอริซานอลจะช่วยชะลอการเหม็นหืน แต่มันไม่ได้ช่วยลดการเกิด สารพิษจากไขมันไหม้ เช่น Aldehydes หรือ HNE (4-Hydroxy-2-nonenal) ที่มาจากโอเมก้า-6 หรือเปล่า??? มันคือการพูดให้เราไปโฟกัสจุดเดียวครับ "โอริซานอลทนร้อน ไม่ได้แปลว่า น้ำมันรำข้าวดีต่อสุขภาพ" เพราะโอเมก้า6 ที่ไวต่อการเกิดออกซิเดชัน รวมถึงวิตามินต่างๆ ก็ยังสูญสลายไปด้วยความร้อน นี่ยังไม่รวมถึงโทษของการกินโอริซานอลมากไปตามที่ให้ข้อมูลไว้ข้างบนด้วย นอกจากนี้ยังมีคนตั้งคำถามไว้มากมายว่า หากโอริซานอลมีผลชัดเจนต่อสุขภาพเช่นเดียวกับที่โฆษณา ทำไมจึงไม่ได้รับการพัฒนาเป็นยาอย่างจริงจัง? หรือคำตอบคือ งานวิจัยที่สนับสนุนโอริซานอลยังไม่เพียงพอ และในหลายกรณี ผลของมันอาจเกิดจาก Placebo Effect (ผลจากความเชื่อว่ามันได้ผล มากกว่าผลจริงๆ ของสารนั้น) ซึ่งเป็นลักษณะเดียวกับ "ยาหลอก" ที่ไม่ได้มีฤทธิ์ทางชีวเคมีที่ส่งผลชัดเจน - มีไลโนเลอิกสูง ใช่ครับไม่ผิดเลยในจุดนี้ ไลโนเลอิก (Linoleic acid) เป็น กรดไขมันไม่อิ่มตัวชนิดหลายพันธะ (Polyunsaturated Fatty Acid, PUFA) ที่สำคัญและจำเป็นสำหรับร่างกาย โดยเฉพาะอย่างยิ่งในการช่วยบำรุงเซลล์และระบบต่างๆ ของร่างกาย ที่สำคัญคือ ไลโนเลอิกเป็นกรดไขมันในกลุ่ม โอเมก้า-6 เป็นสิ่งที่บอกกับเราชัดๆว่า โอเมก้า6 สูงนั่นเอง ถ้าจะดึงเฉพาะข้อดีมาคุยกันก็ไม่ผิดอะไรเลยครับ เพราะโอเมก้า6 สำคัญกับร่างกายจริงๆ แต่ แต่ แต่ การรับโอเมก้า-6 ในปริมาณสูงเกินไปอาจทำให้เกิดการอักเสบในร่างกาย ซึ่งเกี่ยวข้องกับโรคต่างๆ เช่น โรคหัวใจ โรคมะเร็ง และโรคเบาหวาน อย่างที่เรารู้กัน ดังนั้นที่บอกไว้ข้างบนครับ สัดส่วนโอเมก้า 6:3 คือ 40:1 หรือใน 1 ช้อนโต๊ะ มีโอเมก้า 6 สูงถึง ราวๆ 4,140 - 5,520 มก. เรียกว่าโฆษณาไม่ผิดเลยเรื่องปริมาณ แต่จริงๆแล้วเราควรรักษาสมดุล โอเมก้า 6:3 ให้ใกล้เคียง 1:1 มากที่สุดเท่าที่ทำได้ เราก็อาจต้องตั้งคำถามอีกทีว่า การมีไลโนเลอิกสูง มันดีจริงไหม - โทโคฟีรอล (Tocopherols) เป็นสารประกอบที่อยู่ในกลุ่ม วิตามินอี เป็นสารต้านอนุมูลอิสระในร่างกาย โดยช่วยปกป้องเซลล์จากความเสียหายจากอนุมูลอิสระและช่วยชะลอการเสื่อมของเซลล์ ถูกต้องตามโฆษณา จริงๆหน้าที่หลักคือปกป้องไขมันไม่ให้เกิดการออกซิเดชัน ซึ่งสามารถช่วยยืดอายุการใช้งานของน้ำมัน หรือไม่ให้เกิดการหืน นั่นเอง แต่การทอดหรือปรุงอาหารในอุณหภูมิสูงเกินไป ก็อาจทำให้น้ำมันเกิดการออกซิเดชันและเกิดสารพิษที่เป็นอันตรายต่อร่างกายได้ อย่าลืมนะครับว่าคำแนะนำในการใช้น้ำมันรำข้าว กลับชูการเหมาะกับอาหารทอดอุณหภูมิสูง - โทโคไทรอีนอล (Tocotrienols) เป็นส่วนหนึ่งของกลุ่ม วิตามินอี เช่นกัน การบริโภคมากเกินไป การรับประทาน โทโคไทรอีนอลในปริมาณมาก อาจมีผลข้างเคียงที่ไม่พึงประสงค์ เช่น ส่งผลกระทบต่อการดูดซึมวิตามินอื่นๆ ในร่างกายโดยเฉพาะวิตามิน K ซึ่งอาจทำให้เกิดปัญหาการแข็งตัวของเลือด, ทำให้ตับทำงานหนักขึ้นในการจัดการกับสารนี้ ซึ่งอาจส่งผลเสียต่อการทำงานของตับระยะยาว สุดท้ายแล้ว เราต้องกลับมาตั้งคำถามว่า เราอยากให้สุขภาพของเราถูกกำหนดโดยการตลาดของอุตสาหกรรม หรือโดยสิ่งที่ธรรมชาติออกแบบมาให้เราตั้งแต่แรก ? ถ้าจะดูแลหัวใจจริง ๆ การกินอาหารที่มนุษย์วิวัฒนาการมากับมันมาตลอด เช่น เนื้อสัตว์ ไข่ ตับ และไขมันดี ๆ อาจเป็นคำตอบที่เรียบง่ายและมีเหตุผลมากกว่าการไล่ตามสารสกัดที่อุตสาหกรรมบอกว่าจำเป็น แต่ธรรมชาติอาจไม่เคยเห็นว่ามันสำคัญเลยก็ได้ #pirateketo #ฉลาก3รู้ #กูต้องรู้มั๊ย #ม้วนหางสิลูก @ aa8de34f:a6ffe696
2025-03-21 12:08:3119\. März 2025 ### 🔐 1. SHA-256 is Quantum-Resistant Bitcoin’s **proof-of-work** mechanism relies on SHA-256, a hashing algorithm. Even with a powerful quantum computer, **SHA-256 remains secure** because: - Quantum computers excel at **factoring large numbers** (Shor’s Algorithm). - However, **SHA-256 is a one-way function**, meaning there's no known quantum algorithm that can efficiently reverse it. - **Grover’s Algorithm** (which theoretically speeds up brute force attacks) would still require **2¹²⁸ operations** to break SHA-256 – far beyond practical reach. ++++++++++++++++++++++++++++++++++++++++++++++++++ ### 🔑 2. Public Key Vulnerability – But Only If You Reuse Addresses Bitcoin uses **Elliptic Curve Digital Signature Algorithm (ECDSA)** to generate keys. - A quantum computer could use **Shor’s Algorithm** to break **SECP256K1**, the curve Bitcoin uses. - If you never reuse addresses, it is an additional security element - 🔑 1. Bitcoin Addresses Are NOT Public Keys Many people assume a **Bitcoin address** is the public key—**this is wrong**. - When you **receive Bitcoin**, it is sent to a **hashed public key** (the Bitcoin address). - The **actual public key is never exposed** because it is the Bitcoin Adress who addresses the Public Key which never reveals the creation of a public key by a spend - Bitcoin uses **Pay-to-Public-Key-Hash (P2PKH)** or newer methods like **Pay-to-Witness-Public-Key-Hash (P2WPKH)**, which add extra layers of security. ### 🕵️♂️ 2.1 The Public Key Never Appears - When you **send Bitcoin**, your wallet creates a **digital signature**. - This signature uses the **private key** to **prove** ownership. - The **Bitcoin address is revealed and creates the Public Key** - The public key **remains hidden inside the Bitcoin script and Merkle tree**. This means: ✔ **The public key is never exposed.** ✔ **Quantum attackers have nothing to target, attacking a Bitcoin Address is a zero value game.** +++++++++++++++++++++++++++++++++++++++++++++++++ ### 🔄 3. Bitcoin Can Upgrade Even if quantum computers **eventually** become a real threat: - Bitcoin developers can **upgrade to quantum-safe cryptography** (e.g., lattice-based cryptography or post-quantum signatures like Dilithium). - Bitcoin’s decentralized nature ensures a network-wide **soft fork or hard fork** could transition to quantum-resistant keys. ++++++++++++++++++++++++++++++++++++++++++++++++++ ### ⏳ 4. The 10-Minute Block Rule as a Security Feature - Bitcoin’s network operates on a **10-minute block interval**, meaning:Even if an attacker had immense computational power (like a quantum computer), they could only attempt an attack **every 10 minutes**.Unlike traditional encryption, where a hacker could continuously brute-force keys, Bitcoin’s system **resets the challenge with every new block**.This **limits the window of opportunity** for quantum attacks. --- ### 🎯 5. Quantum Attack Needs to Solve a Block in Real-Time - A quantum attacker **must solve the cryptographic puzzle (Proof of Work) in under 10 minutes**. - The problem? **Any slight error changes the hash completely**, meaning:**If the quantum computer makes a mistake (even 0.0001% probability), the entire attack fails**.**Quantum decoherence** (loss of qubit stability) makes error correction a massive challenge.The computational cost of **recovering from an incorrect hash** is still incredibly high. --- ### ⚡ 6. Network Resilience – Even if a Block Is Hacked - Even if a quantum computer **somehow** solved a block instantly:The network would **quickly recognize and reject invalid transactions**.Other miners would **continue mining** under normal cryptographic rules.**51% Attack?** The attacker would need to consistently beat the **entire Bitcoin network**, which is **not sustainable**. --- ### 🔄 7. The Logarithmic Difficulty Adjustment Neutralizes Threats - Bitcoin adjusts mining difficulty every **2016 blocks (\~2 weeks)**. - If quantum miners appeared and suddenly started solving blocks too quickly, **the difficulty would adjust upward**, making attacks significantly harder. - This **self-correcting mechanism** ensures that even quantum computers wouldn't easily overpower the network. --- ### 🔥 Final Verdict: Quantum Computers Are Too Slow for Bitcoin ✔ **The 10-minute rule limits attack frequency** – quantum computers can’t keep up. ✔ **Any slight miscalculation ruins the attack**, resetting all progress. ✔ **Bitcoin’s difficulty adjustment would react, neutralizing quantum advantages**. **Even if quantum computers reach their theoretical potential, Bitcoin’s game theory and design make it incredibly resistant.** 🚀
@ aa8de34f:a6ffe696
2025-03-21 12:08:3119\. März 2025 ### 🔐 1. SHA-256 is Quantum-Resistant Bitcoin’s **proof-of-work** mechanism relies on SHA-256, a hashing algorithm. Even with a powerful quantum computer, **SHA-256 remains secure** because: - Quantum computers excel at **factoring large numbers** (Shor’s Algorithm). - However, **SHA-256 is a one-way function**, meaning there's no known quantum algorithm that can efficiently reverse it. - **Grover’s Algorithm** (which theoretically speeds up brute force attacks) would still require **2¹²⁸ operations** to break SHA-256 – far beyond practical reach. ++++++++++++++++++++++++++++++++++++++++++++++++++ ### 🔑 2. Public Key Vulnerability – But Only If You Reuse Addresses Bitcoin uses **Elliptic Curve Digital Signature Algorithm (ECDSA)** to generate keys. - A quantum computer could use **Shor’s Algorithm** to break **SECP256K1**, the curve Bitcoin uses. - If you never reuse addresses, it is an additional security element - 🔑 1. Bitcoin Addresses Are NOT Public Keys Many people assume a **Bitcoin address** is the public key—**this is wrong**. - When you **receive Bitcoin**, it is sent to a **hashed public key** (the Bitcoin address). - The **actual public key is never exposed** because it is the Bitcoin Adress who addresses the Public Key which never reveals the creation of a public key by a spend - Bitcoin uses **Pay-to-Public-Key-Hash (P2PKH)** or newer methods like **Pay-to-Witness-Public-Key-Hash (P2WPKH)**, which add extra layers of security. ### 🕵️♂️ 2.1 The Public Key Never Appears - When you **send Bitcoin**, your wallet creates a **digital signature**. - This signature uses the **private key** to **prove** ownership. - The **Bitcoin address is revealed and creates the Public Key** - The public key **remains hidden inside the Bitcoin script and Merkle tree**. This means: ✔ **The public key is never exposed.** ✔ **Quantum attackers have nothing to target, attacking a Bitcoin Address is a zero value game.** +++++++++++++++++++++++++++++++++++++++++++++++++ ### 🔄 3. Bitcoin Can Upgrade Even if quantum computers **eventually** become a real threat: - Bitcoin developers can **upgrade to quantum-safe cryptography** (e.g., lattice-based cryptography or post-quantum signatures like Dilithium). - Bitcoin’s decentralized nature ensures a network-wide **soft fork or hard fork** could transition to quantum-resistant keys. ++++++++++++++++++++++++++++++++++++++++++++++++++ ### ⏳ 4. The 10-Minute Block Rule as a Security Feature - Bitcoin’s network operates on a **10-minute block interval**, meaning:Even if an attacker had immense computational power (like a quantum computer), they could only attempt an attack **every 10 minutes**.Unlike traditional encryption, where a hacker could continuously brute-force keys, Bitcoin’s system **resets the challenge with every new block**.This **limits the window of opportunity** for quantum attacks. --- ### 🎯 5. Quantum Attack Needs to Solve a Block in Real-Time - A quantum attacker **must solve the cryptographic puzzle (Proof of Work) in under 10 minutes**. - The problem? **Any slight error changes the hash completely**, meaning:**If the quantum computer makes a mistake (even 0.0001% probability), the entire attack fails**.**Quantum decoherence** (loss of qubit stability) makes error correction a massive challenge.The computational cost of **recovering from an incorrect hash** is still incredibly high. --- ### ⚡ 6. Network Resilience – Even if a Block Is Hacked - Even if a quantum computer **somehow** solved a block instantly:The network would **quickly recognize and reject invalid transactions**.Other miners would **continue mining** under normal cryptographic rules.**51% Attack?** The attacker would need to consistently beat the **entire Bitcoin network**, which is **not sustainable**. --- ### 🔄 7. The Logarithmic Difficulty Adjustment Neutralizes Threats - Bitcoin adjusts mining difficulty every **2016 blocks (\~2 weeks)**. - If quantum miners appeared and suddenly started solving blocks too quickly, **the difficulty would adjust upward**, making attacks significantly harder. - This **self-correcting mechanism** ensures that even quantum computers wouldn't easily overpower the network. --- ### 🔥 Final Verdict: Quantum Computers Are Too Slow for Bitcoin ✔ **The 10-minute rule limits attack frequency** – quantum computers can’t keep up. ✔ **Any slight miscalculation ruins the attack**, resetting all progress. ✔ **Bitcoin’s difficulty adjustment would react, neutralizing quantum advantages**. **Even if quantum computers reach their theoretical potential, Bitcoin’s game theory and design make it incredibly resistant.** 🚀 @ 6389be64:ef439d32
2025-04-03 21:32:58Brewing Biology Episode 1068 of Bitcoin And . . . is LIVE! This episode of Bitcoin And dives into Brewing Biology—a regenerative system combining compost tea, biochar, Bitcoin mining, and carbon credits—developed through a deep, idea-driven conversation with ChatGPT. LISTEN HERE --> https://fountain.fm/episode/p0DmvPzxirDHh2l68zOX <-- LISTEN HERE The future of Bitcoin isn’t just about code or money—it’s about soil. A groundbreaking fusion of biology, technology, and financial innovation might change the rules of agriculture, offering landowners a path to profitability while Healing our soils. At the heart of this revolution is biochar, a form of charcoal that supercharges soil health. When mixed with compost tea and microbial inoculants, this carbon-rich material becomes a game-changer. Biochar’s porous structure acts as a microbial hotel, hosting fungi like arbuscular mycorrhizal fungi (AMF) and bacteria such as Bacillus subtilis. These organisms form symbiotic networks that boost nutrient absorption and secrete glomalin—a natural “glue” that binds soil, preventing erosion. But here’s the twist: this system doesn’t just heal the earth; it also generates revenue. Biochar’s Hidden Superpower: Adsorption & Buffering Biochar’s porous structure acts as a molecular storage hub. Unlike absorption (soaking up water like a sponge), adsorption is a chemical process where water and nutrients cling to biochar’s surfaces. A single gram of biochar has the surface area of a basketball court, creating a lattice of microscopic nooks and crannies. This allows it to: Lock in moisture: Biochar retains up to 10x its weight in water, acting like a “soil battery” that releases hydration slowly during droughts. Hoard nutrients: It buffers nitrogen, phosphorus, potassium, and micronutrients in its pores, preventing leaching. Plants access these nutrients gradually, reducing fertilizer needs. Stabilize pH: Biochar’s alkaline nature buffers acidic soils, creating a neutral environment where microbes and roots thrive. This buffering effect means plants face fewer nutrient and water spikes or shortages, ensuring steady growth even in erratic climates. The Carbon Math Every ton of biochar (which is ~85% carbon by weight) sequesters 3.12 tons of CO₂ (using the 1:3.67 carbon-to-CO₂ ratio). With carbon credits trading at $42–$60/ton, a 1,000-acre project applying 1 pound of biochar per linear foot (via a three-shank plow at 2-foot spacing) could sequester ~12,000 tons of CO₂ annually—generating $504,000–$720,000 in carbon credit revenue. Tools for the Revolution The Keyline Plow fractures subsoil to inject biochar slurry 30–45cm deep, revitalizing compacted land. For smaller plots, the VOGT Geo Injector delivers pinpoint inoculations—think of it as a soil “injection gun” for lawns, golf courses, or urban gardens. These methods ensure biochar stays where it’s needed, turning even parched landscapes into carbon sinks. Bitcoin’s Role in the Loop Biochar production generates syngas—a byproduct that fuels electric generators for Bitcoin mining. This closed-loop system turns agricultural waste into energy, creating dual revenue streams: carbon credits and mining income. The Market Potential Farmers, ranchers, and eco-conscious landowners aren’t the only beneficiaries. Golf courses can slash water use and homeowners can boost lawn resilience. Why This Matters This isn’t just farming—it’s a movement. By marrying soil science with economics, we can prove that healing the planet and profiting go hand in hand. Whether you’re a Bitcoin miner, a farmer, or an eco-entrepreneur, this system offers a blueprint for a future where every acre works for you—and the planet. The takeaway? Regenerative agriculture isn’t a trend. It’s the next gold rush—except this time, the gold is carbon, soil, and sats.--- P.S. – If you’re ready to turn your land into a carbon credit powerhouse (and maybe mine some Bitcoin along the way), the soil is waiting. You can read the full article, Brewing Biology HERE -> https://the-bitcoin-and-Podcast.ghost.io/ghost/#/editor/post/67e5922fa289aa00088da3c6 originally posted at https://stacker.news/items/933800
@ 6389be64:ef439d32
2025-04-03 21:32:58Brewing Biology Episode 1068 of Bitcoin And . . . is LIVE! This episode of Bitcoin And dives into Brewing Biology—a regenerative system combining compost tea, biochar, Bitcoin mining, and carbon credits—developed through a deep, idea-driven conversation with ChatGPT. LISTEN HERE --> https://fountain.fm/episode/p0DmvPzxirDHh2l68zOX <-- LISTEN HERE The future of Bitcoin isn’t just about code or money—it’s about soil. A groundbreaking fusion of biology, technology, and financial innovation might change the rules of agriculture, offering landowners a path to profitability while Healing our soils. At the heart of this revolution is biochar, a form of charcoal that supercharges soil health. When mixed with compost tea and microbial inoculants, this carbon-rich material becomes a game-changer. Biochar’s porous structure acts as a microbial hotel, hosting fungi like arbuscular mycorrhizal fungi (AMF) and bacteria such as Bacillus subtilis. These organisms form symbiotic networks that boost nutrient absorption and secrete glomalin—a natural “glue” that binds soil, preventing erosion. But here’s the twist: this system doesn’t just heal the earth; it also generates revenue. Biochar’s Hidden Superpower: Adsorption & Buffering Biochar’s porous structure acts as a molecular storage hub. Unlike absorption (soaking up water like a sponge), adsorption is a chemical process where water and nutrients cling to biochar’s surfaces. A single gram of biochar has the surface area of a basketball court, creating a lattice of microscopic nooks and crannies. This allows it to: Lock in moisture: Biochar retains up to 10x its weight in water, acting like a “soil battery” that releases hydration slowly during droughts. Hoard nutrients: It buffers nitrogen, phosphorus, potassium, and micronutrients in its pores, preventing leaching. Plants access these nutrients gradually, reducing fertilizer needs. Stabilize pH: Biochar’s alkaline nature buffers acidic soils, creating a neutral environment where microbes and roots thrive. This buffering effect means plants face fewer nutrient and water spikes or shortages, ensuring steady growth even in erratic climates. The Carbon Math Every ton of biochar (which is ~85% carbon by weight) sequesters 3.12 tons of CO₂ (using the 1:3.67 carbon-to-CO₂ ratio). With carbon credits trading at $42–$60/ton, a 1,000-acre project applying 1 pound of biochar per linear foot (via a three-shank plow at 2-foot spacing) could sequester ~12,000 tons of CO₂ annually—generating $504,000–$720,000 in carbon credit revenue. Tools for the Revolution The Keyline Plow fractures subsoil to inject biochar slurry 30–45cm deep, revitalizing compacted land. For smaller plots, the VOGT Geo Injector delivers pinpoint inoculations—think of it as a soil “injection gun” for lawns, golf courses, or urban gardens. These methods ensure biochar stays where it’s needed, turning even parched landscapes into carbon sinks. Bitcoin’s Role in the Loop Biochar production generates syngas—a byproduct that fuels electric generators for Bitcoin mining. This closed-loop system turns agricultural waste into energy, creating dual revenue streams: carbon credits and mining income. The Market Potential Farmers, ranchers, and eco-conscious landowners aren’t the only beneficiaries. Golf courses can slash water use and homeowners can boost lawn resilience. Why This Matters This isn’t just farming—it’s a movement. By marrying soil science with economics, we can prove that healing the planet and profiting go hand in hand. Whether you’re a Bitcoin miner, a farmer, or an eco-entrepreneur, this system offers a blueprint for a future where every acre works for you—and the planet. The takeaway? Regenerative agriculture isn’t a trend. It’s the next gold rush—except this time, the gold is carbon, soil, and sats.--- P.S. – If you’re ready to turn your land into a carbon credit powerhouse (and maybe mine some Bitcoin along the way), the soil is waiting. You can read the full article, Brewing Biology HERE -> https://the-bitcoin-and-Podcast.ghost.io/ghost/#/editor/post/67e5922fa289aa00088da3c6 originally posted at https://stacker.news/items/933800 @ a95c6243:d345522c
2025-03-20 09:59:20**Bald werde es verboten, alleine im Auto zu fahren,** konnte man dieser Tage in verschiedenen spanischen Medien lesen. Die nationale Verkehrsbehörde (Dirección General de Tráfico, kurz DGT) werde Alleinfahrern das Leben schwer machen, wurde gemeldet. Konkret erörtere die Generaldirektion geeignete Sanktionen für Personen, die ohne Beifahrer im Privatauto unterwegs seien. **Das Alleinfahren sei zunehmend verpönt und ein Mentalitätswandel notwendig,** hieß es. Dieser «Luxus» stehe im Widerspruch zu den Maßnahmen gegen Umweltverschmutzung, die in allen europäischen Ländern gefördert würden. In Frankreich sei es «bereits verboten, in der Hauptstadt allein zu fahren», [behauptete](https://noticiastrabajo.huffingtonpost.es/sociedad/adios-a-conducir-solo-la-dgt-se-lo-pone-crudo-a-los-conductores-que-viajen-sin-acompanante-en-el-coche/) *Noticiastrabajo Huffpost* in einer Zwischenüberschrift. Nur um dann im Text zu konkretisieren, dass die sogenannte «Umweltspur» auf der Pariser Ringautobahn gemeint war, die für Busse, Taxis und Fahrgemeinschaften reserviert ist. [Ab Mai](https://www.lefigaro.fr/conso/peripherique-parisien-entree-en-vigueur-de-la-voie-reservee-au-covoiturage-ce-lundi-20250303) werden Verstöße dagegen mit einem Bußgeld geahndet. **Die DGT jedenfalls wolle bei der Umsetzung derartiger Maßnahmen** nicht hinterherhinken. Diese Medienberichte, inklusive des angeblich bevorstehenden Verbots, beriefen sich auf Aussagen des Generaldirektors der Behörde, Pere Navarro, beim Mobilitätskongress Global Mobility Call im November letzten Jahres, wo es um «nachhaltige Mobilität» ging. Aus diesem Kontext stammt auch Navarros Warnung: «Die Zukunft des Verkehrs ist geteilt oder es gibt keine». **Die «Faktenchecker» kamen der Generaldirektion prompt zu Hilfe.** Die DGT habe derlei Behauptungen [zurückgewiesen](https://www.newtral.es/dgt-una-persona-coche/20250312/) und klargestellt, dass es keine Pläne gebe, Fahrten mit nur einer Person im Auto zu verbieten oder zu bestrafen. Bei solchen Meldungen handele es sich um Fake News. Teilweise wurde der Vorsitzende der spanischen «Rechtsaußen»-Partei Vox, Santiago Abascal, der Urheberschaft bezichtigt, weil er einen entsprechenden [Artikel](https://gaceta.es/espana/la-dgt-estudia-formas-de-sancionar-a-quien-circule-solo-en-su-vehiculo-el-futuro-sera-compartido-o-no-sera-20250311-1612/) von *La Gaceta* kommentiert hatte. **Der Beschwichtigungsversuch der Art «niemand hat die Absicht»** ist dabei erfahrungsgemäß eher ein Alarmzeichen als eine Beruhigung. Walter Ulbrichts Leugnung einer geplanten Berliner [Mauer](https://www.berlin-mauer.de/videos/walter-ulbricht-zum-mauerbau-530/) vom Juni 1961 ist vielen genauso in Erinnerung wie die Fake News-Warnungen des deutschen Bundesgesundheitsministeriums bezüglich [Lockdowns](https://x.com/BMG_Bund/status/1238780849652465664) im März 2020 oder diverse Äußerungen zu einer [Impfpflicht](https://www.achgut.com/artikel/die_schoensten_politiker_zitate_zur_impfpflicht) ab 2020. **Aber Aufregung hin, Dementis her:** Die [Pressemitteilung](https://archive.is/xXQWD) der DGT zu dem Mobilitätskongress enthält in Wahrheit viel interessantere Informationen als «nur» einen Appell an den «guten» Bürger wegen der Bemühungen um die Lebensqualität in Großstädten oder einen möglichen obligatorischen Abschied vom Alleinfahren. Allerdings werden diese Details von Medien und sogenannten Faktencheckern geflissentlich übersehen, obwohl sie keineswegs versteckt sind. Die Auskünfte sind sehr aufschlussreich, wenn man genauer hinschaut. ### Digitalisierung ist der Schlüssel für Kontrolle **Auf dem Kongress stellte die Verkehrsbehörde ihre Initiativen zur Förderung der «neuen Mobilität» vor,** deren Priorität Sicherheit und Effizienz sei. Die vier konkreten Ansätze haben alle mit Digitalisierung, Daten, Überwachung und Kontrolle im großen Stil zu tun und werden unter dem Euphemismus der «öffentlich-privaten Partnerschaft» angepriesen. Auch lassen sie die transhumanistische Idee vom unzulänglichen Menschen erkennen, dessen Fehler durch «intelligente» technologische Infrastruktur kompensiert werden müssten. **Die Chefin des Bereichs «Verkehrsüberwachung» erklärte die Funktion** des spanischen National Access Point ([NAP](https://nap.dgt.es/)), wobei sie betonte, wie wichtig Verkehrs- und Infrastrukturinformationen in Echtzeit seien. Der NAP ist «eine essenzielle Web-Applikation, die unter EU-Mandat erstellt wurde», kann man auf der Website der DGT nachlesen. **Das Mandat meint Regelungen zu einem einheitlichen europäischen Verkehrsraum,** mit denen die Union mindestens seit 2010 den Aufbau einer digitalen Architektur mit offenen Schnittstellen betreibt. Damit begründet man auch «umfassende Datenbereitstellungspflichten im Bereich multimodaler Reiseinformationen». Jeder Mitgliedstaat musste einen NAP, also einen nationalen [Zugangspunkt](https://transport.ec.europa.eu/transport-themes/smart-mobility/road/its-directive-and-action-plan/national-access-points_en) einrichten, der Zugang zu statischen und dynamischen Reise- und Verkehrsdaten verschiedener Verkehrsträger ermöglicht. **Diese Entwicklung ist heute schon weit fortgeschritten,** auch und besonders in Spanien. Auf besagtem Kongress erläuterte die Leiterin des Bereichs «Telematik» die Plattform [«DGT 3.0»](https://www.dgt.es/muevete-con-seguridad/tecnologia-e-innovacion-en-carretera/dgt-3.0/). Diese werde als Integrator aller Informationen genutzt, die von den verschiedenen öffentlichen und privaten Systemen, die Teil der Mobilität sind, bereitgestellt werden. **Es handele sich um eine Vermittlungsplattform zwischen Akteuren wie Fahrzeugherstellern,** Anbietern von Navigationsdiensten oder Kommunen und dem Endnutzer, der die Verkehrswege benutzt. Alle seien auf Basis des Internets der Dinge (IOT) anonym verbunden, «um der vernetzten Gemeinschaft wertvolle Informationen zu liefern oder diese zu nutzen». **So sei DGT 3.0 «ein Zugangspunkt für einzigartige, kostenlose und genaue Echtzeitinformationen** über das Geschehen auf den Straßen und in den Städten». Damit lasse sich der Verkehr nachhaltiger und vernetzter gestalten. Beispielsweise würden die Karten des Produktpartners Google dank der DGT-Daten 50 Millionen Mal pro Tag aktualisiert. **Des Weiteren informiert die Verkehrsbehörde über ihr SCADA-Projekt.** Die Abkürzung steht für Supervisory Control and Data Acquisition, zu deutsch etwa: Kontrollierte Steuerung und Datenerfassung. Mit SCADA kombiniert man Software und Hardware, um automatisierte Systeme zur Überwachung und Steuerung technischer Prozesse zu schaffen. Das SCADA-Projekt der DGT wird von Indra entwickelt, einem spanischen Beratungskonzern aus den Bereichen Sicherheit & Militär, Energie, Transport, Telekommunikation und Gesundheitsinformation. **Das SCADA-System der Behörde umfasse auch eine Videostreaming- und Videoaufzeichnungsplattform,** die das Hochladen in die Cloud in Echtzeit ermöglicht, wie Indra [erklärt](https://www.indracompany.com/es/noticia/indra-presenta-global-mobility-call-pionera-plataforma-nube-desplegada-centros-gestion). Dabei gehe es um Bilder, die von Überwachungskameras an Straßen aufgenommen wurden, sowie um Videos aus DGT-Hubschraubern und Drohnen. Ziel sei es, «die sichere Weitergabe von Videos an Dritte sowie die kontinuierliche Aufzeichnung und Speicherung von Bildern zur möglichen Analyse und späteren Nutzung zu ermöglichen». **Letzteres klingt sehr nach biometrischer Erkennung** und Auswertung durch künstliche Intelligenz. Für eine bessere Datenübertragung wird derzeit die [Glasfaserverkabelung](https://www.moncloa.com/2025/03/18/linea-azul-conduccion-dgt-3191554/) entlang der Landstraßen und Autobahnen ausgebaut. Mit der Cloud sind die Amazon Web Services (AWS) gemeint, die spanischen [Daten gehen](https://norberthaering.de/news/digitalgipfel-wehnes-interview/) somit direkt zu einem US-amerikanischen «Big Data»-Unternehmen. **Das Thema «autonomes Fahren», also Fahren ohne Zutun des Menschen,** bildet den Abschluss der Betrachtungen der DGT. Zusammen mit dem Interessenverband der Automobilindustrie ANFAC (Asociación Española de Fabricantes de Automóviles y Camiones) sprach man auf dem Kongress über Strategien und Perspektiven in diesem Bereich. Die Lobbyisten hoffen noch in diesem Jahr 2025 auf einen [normativen Rahmen](https://www.coches.net/noticias/informe-coche-autonomo-conectado-espana-2024) zur erweiterten Unterstützung autonomer Technologien. **Wenn man derartige Informationen im Zusammenhang betrachtet,** bekommt man eine Idee davon, warum zunehmend alles elektrisch und digital werden soll. Umwelt- und Mobilitätsprobleme in Städten, wie Luftverschmutzung, Lärmbelästigung, Platzmangel oder Staus, sind eine Sache. Mit dem Argument «emissionslos» wird jedoch eine Referenz zum CO2 und dem «menschengemachten Klimawandel» hergestellt, die Emotionen triggert. Und damit wird so ziemlich alles verkauft. **Letztlich aber gilt: Je elektrischer und digitaler unsere Umgebung wird** und je freigiebiger wir mit unseren Daten jeder Art sind, desto besser werden wir kontrollier-, steuer- und sogar abschaltbar. Irgendwann entscheiden KI-basierte Algorithmen, ob, wann, wie, wohin und mit wem wir uns bewegen dürfen. Über einen 15-Minuten-Radius geht dann möglicherweise nichts hinaus. Die Projekte auf diesem Weg sind ernst zu nehmen, real und schon weit fortgeschritten. *\[Titelbild:* *[Pixabay](https://pixabay.com/de/photos/reisen-wagen-ferien-fahrzeug-1426822/)]* *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/nur-abschied-vom-alleinfahren-monstrose-spanische-uberwachungsprojekte-gemass)*** erschienen.
@ a95c6243:d345522c
2025-03-20 09:59:20**Bald werde es verboten, alleine im Auto zu fahren,** konnte man dieser Tage in verschiedenen spanischen Medien lesen. Die nationale Verkehrsbehörde (Dirección General de Tráfico, kurz DGT) werde Alleinfahrern das Leben schwer machen, wurde gemeldet. Konkret erörtere die Generaldirektion geeignete Sanktionen für Personen, die ohne Beifahrer im Privatauto unterwegs seien. **Das Alleinfahren sei zunehmend verpönt und ein Mentalitätswandel notwendig,** hieß es. Dieser «Luxus» stehe im Widerspruch zu den Maßnahmen gegen Umweltverschmutzung, die in allen europäischen Ländern gefördert würden. In Frankreich sei es «bereits verboten, in der Hauptstadt allein zu fahren», [behauptete](https://noticiastrabajo.huffingtonpost.es/sociedad/adios-a-conducir-solo-la-dgt-se-lo-pone-crudo-a-los-conductores-que-viajen-sin-acompanante-en-el-coche/) *Noticiastrabajo Huffpost* in einer Zwischenüberschrift. Nur um dann im Text zu konkretisieren, dass die sogenannte «Umweltspur» auf der Pariser Ringautobahn gemeint war, die für Busse, Taxis und Fahrgemeinschaften reserviert ist. [Ab Mai](https://www.lefigaro.fr/conso/peripherique-parisien-entree-en-vigueur-de-la-voie-reservee-au-covoiturage-ce-lundi-20250303) werden Verstöße dagegen mit einem Bußgeld geahndet. **Die DGT jedenfalls wolle bei der Umsetzung derartiger Maßnahmen** nicht hinterherhinken. Diese Medienberichte, inklusive des angeblich bevorstehenden Verbots, beriefen sich auf Aussagen des Generaldirektors der Behörde, Pere Navarro, beim Mobilitätskongress Global Mobility Call im November letzten Jahres, wo es um «nachhaltige Mobilität» ging. Aus diesem Kontext stammt auch Navarros Warnung: «Die Zukunft des Verkehrs ist geteilt oder es gibt keine». **Die «Faktenchecker» kamen der Generaldirektion prompt zu Hilfe.** Die DGT habe derlei Behauptungen [zurückgewiesen](https://www.newtral.es/dgt-una-persona-coche/20250312/) und klargestellt, dass es keine Pläne gebe, Fahrten mit nur einer Person im Auto zu verbieten oder zu bestrafen. Bei solchen Meldungen handele es sich um Fake News. Teilweise wurde der Vorsitzende der spanischen «Rechtsaußen»-Partei Vox, Santiago Abascal, der Urheberschaft bezichtigt, weil er einen entsprechenden [Artikel](https://gaceta.es/espana/la-dgt-estudia-formas-de-sancionar-a-quien-circule-solo-en-su-vehiculo-el-futuro-sera-compartido-o-no-sera-20250311-1612/) von *La Gaceta* kommentiert hatte. **Der Beschwichtigungsversuch der Art «niemand hat die Absicht»** ist dabei erfahrungsgemäß eher ein Alarmzeichen als eine Beruhigung. Walter Ulbrichts Leugnung einer geplanten Berliner [Mauer](https://www.berlin-mauer.de/videos/walter-ulbricht-zum-mauerbau-530/) vom Juni 1961 ist vielen genauso in Erinnerung wie die Fake News-Warnungen des deutschen Bundesgesundheitsministeriums bezüglich [Lockdowns](https://x.com/BMG_Bund/status/1238780849652465664) im März 2020 oder diverse Äußerungen zu einer [Impfpflicht](https://www.achgut.com/artikel/die_schoensten_politiker_zitate_zur_impfpflicht) ab 2020. **Aber Aufregung hin, Dementis her:** Die [Pressemitteilung](https://archive.is/xXQWD) der DGT zu dem Mobilitätskongress enthält in Wahrheit viel interessantere Informationen als «nur» einen Appell an den «guten» Bürger wegen der Bemühungen um die Lebensqualität in Großstädten oder einen möglichen obligatorischen Abschied vom Alleinfahren. Allerdings werden diese Details von Medien und sogenannten Faktencheckern geflissentlich übersehen, obwohl sie keineswegs versteckt sind. Die Auskünfte sind sehr aufschlussreich, wenn man genauer hinschaut. ### Digitalisierung ist der Schlüssel für Kontrolle **Auf dem Kongress stellte die Verkehrsbehörde ihre Initiativen zur Förderung der «neuen Mobilität» vor,** deren Priorität Sicherheit und Effizienz sei. Die vier konkreten Ansätze haben alle mit Digitalisierung, Daten, Überwachung und Kontrolle im großen Stil zu tun und werden unter dem Euphemismus der «öffentlich-privaten Partnerschaft» angepriesen. Auch lassen sie die transhumanistische Idee vom unzulänglichen Menschen erkennen, dessen Fehler durch «intelligente» technologische Infrastruktur kompensiert werden müssten. **Die Chefin des Bereichs «Verkehrsüberwachung» erklärte die Funktion** des spanischen National Access Point ([NAP](https://nap.dgt.es/)), wobei sie betonte, wie wichtig Verkehrs- und Infrastrukturinformationen in Echtzeit seien. Der NAP ist «eine essenzielle Web-Applikation, die unter EU-Mandat erstellt wurde», kann man auf der Website der DGT nachlesen. **Das Mandat meint Regelungen zu einem einheitlichen europäischen Verkehrsraum,** mit denen die Union mindestens seit 2010 den Aufbau einer digitalen Architektur mit offenen Schnittstellen betreibt. Damit begründet man auch «umfassende Datenbereitstellungspflichten im Bereich multimodaler Reiseinformationen». Jeder Mitgliedstaat musste einen NAP, also einen nationalen [Zugangspunkt](https://transport.ec.europa.eu/transport-themes/smart-mobility/road/its-directive-and-action-plan/national-access-points_en) einrichten, der Zugang zu statischen und dynamischen Reise- und Verkehrsdaten verschiedener Verkehrsträger ermöglicht. **Diese Entwicklung ist heute schon weit fortgeschritten,** auch und besonders in Spanien. Auf besagtem Kongress erläuterte die Leiterin des Bereichs «Telematik» die Plattform [«DGT 3.0»](https://www.dgt.es/muevete-con-seguridad/tecnologia-e-innovacion-en-carretera/dgt-3.0/). Diese werde als Integrator aller Informationen genutzt, die von den verschiedenen öffentlichen und privaten Systemen, die Teil der Mobilität sind, bereitgestellt werden. **Es handele sich um eine Vermittlungsplattform zwischen Akteuren wie Fahrzeugherstellern,** Anbietern von Navigationsdiensten oder Kommunen und dem Endnutzer, der die Verkehrswege benutzt. Alle seien auf Basis des Internets der Dinge (IOT) anonym verbunden, «um der vernetzten Gemeinschaft wertvolle Informationen zu liefern oder diese zu nutzen». **So sei DGT 3.0 «ein Zugangspunkt für einzigartige, kostenlose und genaue Echtzeitinformationen** über das Geschehen auf den Straßen und in den Städten». Damit lasse sich der Verkehr nachhaltiger und vernetzter gestalten. Beispielsweise würden die Karten des Produktpartners Google dank der DGT-Daten 50 Millionen Mal pro Tag aktualisiert. **Des Weiteren informiert die Verkehrsbehörde über ihr SCADA-Projekt.** Die Abkürzung steht für Supervisory Control and Data Acquisition, zu deutsch etwa: Kontrollierte Steuerung und Datenerfassung. Mit SCADA kombiniert man Software und Hardware, um automatisierte Systeme zur Überwachung und Steuerung technischer Prozesse zu schaffen. Das SCADA-Projekt der DGT wird von Indra entwickelt, einem spanischen Beratungskonzern aus den Bereichen Sicherheit & Militär, Energie, Transport, Telekommunikation und Gesundheitsinformation. **Das SCADA-System der Behörde umfasse auch eine Videostreaming- und Videoaufzeichnungsplattform,** die das Hochladen in die Cloud in Echtzeit ermöglicht, wie Indra [erklärt](https://www.indracompany.com/es/noticia/indra-presenta-global-mobility-call-pionera-plataforma-nube-desplegada-centros-gestion). Dabei gehe es um Bilder, die von Überwachungskameras an Straßen aufgenommen wurden, sowie um Videos aus DGT-Hubschraubern und Drohnen. Ziel sei es, «die sichere Weitergabe von Videos an Dritte sowie die kontinuierliche Aufzeichnung und Speicherung von Bildern zur möglichen Analyse und späteren Nutzung zu ermöglichen». **Letzteres klingt sehr nach biometrischer Erkennung** und Auswertung durch künstliche Intelligenz. Für eine bessere Datenübertragung wird derzeit die [Glasfaserverkabelung](https://www.moncloa.com/2025/03/18/linea-azul-conduccion-dgt-3191554/) entlang der Landstraßen und Autobahnen ausgebaut. Mit der Cloud sind die Amazon Web Services (AWS) gemeint, die spanischen [Daten gehen](https://norberthaering.de/news/digitalgipfel-wehnes-interview/) somit direkt zu einem US-amerikanischen «Big Data»-Unternehmen. **Das Thema «autonomes Fahren», also Fahren ohne Zutun des Menschen,** bildet den Abschluss der Betrachtungen der DGT. Zusammen mit dem Interessenverband der Automobilindustrie ANFAC (Asociación Española de Fabricantes de Automóviles y Camiones) sprach man auf dem Kongress über Strategien und Perspektiven in diesem Bereich. Die Lobbyisten hoffen noch in diesem Jahr 2025 auf einen [normativen Rahmen](https://www.coches.net/noticias/informe-coche-autonomo-conectado-espana-2024) zur erweiterten Unterstützung autonomer Technologien. **Wenn man derartige Informationen im Zusammenhang betrachtet,** bekommt man eine Idee davon, warum zunehmend alles elektrisch und digital werden soll. Umwelt- und Mobilitätsprobleme in Städten, wie Luftverschmutzung, Lärmbelästigung, Platzmangel oder Staus, sind eine Sache. Mit dem Argument «emissionslos» wird jedoch eine Referenz zum CO2 und dem «menschengemachten Klimawandel» hergestellt, die Emotionen triggert. Und damit wird so ziemlich alles verkauft. **Letztlich aber gilt: Je elektrischer und digitaler unsere Umgebung wird** und je freigiebiger wir mit unseren Daten jeder Art sind, desto besser werden wir kontrollier-, steuer- und sogar abschaltbar. Irgendwann entscheiden KI-basierte Algorithmen, ob, wann, wie, wohin und mit wem wir uns bewegen dürfen. Über einen 15-Minuten-Radius geht dann möglicherweise nichts hinaus. Die Projekte auf diesem Weg sind ernst zu nehmen, real und schon weit fortgeschritten. *\[Titelbild:* *[Pixabay](https://pixabay.com/de/photos/reisen-wagen-ferien-fahrzeug-1426822/)]* *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/nur-abschied-vom-alleinfahren-monstrose-spanische-uberwachungsprojekte-gemass)*** erschienen. @ 07f367da:0e76880d
2025-04-03 17:59:21윤석열 탄핵 선고를 앞둔 4월 3일. 우리 노동조합은 서울 마포구 소재의 한 활동지원기관 앞에서 선전전을 진행했다. 노동조합은 한 활동지원사의 민원을 통해 해당 활동지원기관이 일요일에 일해도 평일 임금을 지급한다는 사실을 파악했다. 활동지원사의 민원에 관심을 가진 한 언론사의 기자는 활동지원기관과 구청, 서울시, 노조에 문의하며 팩트체크를 진행하고 있는데, 이 과정에서 노조는 해당 기관이 일요일에 일을 해도 평일 임금을 지급하고 있다는 사실을 명확히 확인했다. 자신이 받는 임금에 대한 사실관계를 노동자들은 잘 알지 못한다. 활동지원사는 기관에 자신의 임금에 대해 문의해도 속 시원한 답을 듣지 못한다. 활동지원사들이 하나같이 하는 이야기가 기관에 물어봐도 제대로 설명을 해주지 않는다는 하소연이다. 당사자 활동지원사는 노조에 민원을 제기하고, 또 기자가 취재한 내용들을 통해서야 자신의 임금이 자신도 모르게 어떻게 변화했는지를 알아가고 있다. 사업장의 임급지급 행위에 대한 가치판단이나 평가 이전에 노동자들은 그 사실 자체를 모를 가능성이 높다. 노조는 이 사실을 활동지원사들에게 알리려 선전전을 진행하기로 했다. 선전전 진행 중 정말 충격적인 경험을 했다. 노동조합의 선전활동은 정당한 노조활동이고 일상적인 활동이다. 여태 여러 사업장에서 선전활동을 했지만, 이런 경우는 정말 처음이었다. 사업장들은 신경 거슬러 하고 적대적인 대우를 하곤 했지만, 가장 강한 대처가 경찰에 신고하여 공권력의 개입을 요청하고, 경찰은 충돌을 방지하는 선에서 대처한다. 그런데 오늘은 장애인 기관장이 선전활동을 하지 말라고 계속 항의하며 방해하더니 소속 활동지원팀 인력은 노동조합이 활동지원사에게 선전물을 전달하려 하니 몸으로 막기까지 한다. 무엇을 그렇게 숨기고 싶을까? 노동조합의 활동을 몸으로 막으면서까지 싫어할 이유가 무엇일까? 노동조합의 활동이 그들에게 무엇으로 다가갔을까? 여러 질문이 든다. 충격적인 것은 이 기관의 대표가 우리노조가 예전에 청와대 앞에서 기자회견 할 때 연대 발언을 하러 왔던 활동가라는 점이다. 장애인 당사자이자 인권운동 활동가가 사용자로, 그리고 사회복지사 노동자들이 전담인력으로 고용되어 사측을 대신해 활동지원사 노동자들이 응당 자신에 대해 알아야 할 사항을 은폐한다. 사장이 되어 권력을 행사하면서도 장애인이라는 정체성으로 자신의 지위를 지우려 하고, 전담인력이라는 지위로 노동자들을 지휘하면서도 같은 노동자라며 위계를 삭제한다. 그리고 정작 현장에서 장애인에게 활동지원을 제공하는 활동지원사들은 대부분 고령의 여성들로 정보약자에 해당한다. 우리에게도 민주주의가 올까. 나는 저들이 활동으로 세상을 좋게 만드는 것을 상쇄할 정도로 더 세상을 나쁘게 만들고 있다고 생각한다. 타인에 의해 돈벌이 수단으로 이용당하는 사람은 자신 또한 타인을 돈벌이 수단으로 활용할 가능성이 높다. 그 타인에는 장애인도 포함된다. 나는 시설사회가 끝나도 장애인학대가 끝나리라는 믿음이 없다. 우리는 어차피 서로를 돈벌이 수단으로만 삼는 사회에서 살고 있기 때문이다.
@ 07f367da:0e76880d
2025-04-03 17:59:21윤석열 탄핵 선고를 앞둔 4월 3일. 우리 노동조합은 서울 마포구 소재의 한 활동지원기관 앞에서 선전전을 진행했다. 노동조합은 한 활동지원사의 민원을 통해 해당 활동지원기관이 일요일에 일해도 평일 임금을 지급한다는 사실을 파악했다. 활동지원사의 민원에 관심을 가진 한 언론사의 기자는 활동지원기관과 구청, 서울시, 노조에 문의하며 팩트체크를 진행하고 있는데, 이 과정에서 노조는 해당 기관이 일요일에 일을 해도 평일 임금을 지급하고 있다는 사실을 명확히 확인했다. 자신이 받는 임금에 대한 사실관계를 노동자들은 잘 알지 못한다. 활동지원사는 기관에 자신의 임금에 대해 문의해도 속 시원한 답을 듣지 못한다. 활동지원사들이 하나같이 하는 이야기가 기관에 물어봐도 제대로 설명을 해주지 않는다는 하소연이다. 당사자 활동지원사는 노조에 민원을 제기하고, 또 기자가 취재한 내용들을 통해서야 자신의 임금이 자신도 모르게 어떻게 변화했는지를 알아가고 있다. 사업장의 임급지급 행위에 대한 가치판단이나 평가 이전에 노동자들은 그 사실 자체를 모를 가능성이 높다. 노조는 이 사실을 활동지원사들에게 알리려 선전전을 진행하기로 했다. 선전전 진행 중 정말 충격적인 경험을 했다. 노동조합의 선전활동은 정당한 노조활동이고 일상적인 활동이다. 여태 여러 사업장에서 선전활동을 했지만, 이런 경우는 정말 처음이었다. 사업장들은 신경 거슬러 하고 적대적인 대우를 하곤 했지만, 가장 강한 대처가 경찰에 신고하여 공권력의 개입을 요청하고, 경찰은 충돌을 방지하는 선에서 대처한다. 그런데 오늘은 장애인 기관장이 선전활동을 하지 말라고 계속 항의하며 방해하더니 소속 활동지원팀 인력은 노동조합이 활동지원사에게 선전물을 전달하려 하니 몸으로 막기까지 한다. 무엇을 그렇게 숨기고 싶을까? 노동조합의 활동을 몸으로 막으면서까지 싫어할 이유가 무엇일까? 노동조합의 활동이 그들에게 무엇으로 다가갔을까? 여러 질문이 든다. 충격적인 것은 이 기관의 대표가 우리노조가 예전에 청와대 앞에서 기자회견 할 때 연대 발언을 하러 왔던 활동가라는 점이다. 장애인 당사자이자 인권운동 활동가가 사용자로, 그리고 사회복지사 노동자들이 전담인력으로 고용되어 사측을 대신해 활동지원사 노동자들이 응당 자신에 대해 알아야 할 사항을 은폐한다. 사장이 되어 권력을 행사하면서도 장애인이라는 정체성으로 자신의 지위를 지우려 하고, 전담인력이라는 지위로 노동자들을 지휘하면서도 같은 노동자라며 위계를 삭제한다. 그리고 정작 현장에서 장애인에게 활동지원을 제공하는 활동지원사들은 대부분 고령의 여성들로 정보약자에 해당한다. 우리에게도 민주주의가 올까. 나는 저들이 활동으로 세상을 좋게 만드는 것을 상쇄할 정도로 더 세상을 나쁘게 만들고 있다고 생각한다. 타인에 의해 돈벌이 수단으로 이용당하는 사람은 자신 또한 타인을 돈벌이 수단으로 활용할 가능성이 높다. 그 타인에는 장애인도 포함된다. 나는 시설사회가 끝나도 장애인학대가 끝나리라는 믿음이 없다. 우리는 어차피 서로를 돈벌이 수단으로만 삼는 사회에서 살고 있기 때문이다. @ e4950c93:1b99eccd
2025-04-03 14:53:56**Heureu-x-se d’avoir trouvé une information utile sur ce site ?** Soutenez le projet en faisant un don pour le faire vivre et remercier les contribut-eur-rice-s. --- **En bitcoin** <img src="https://coinos.io/qr/bc1q79er6c5mvvktvmvcstsnelv4j6tv3wdhw2k7ej/raw" width="200" height="200"> bc1qkm8me8l9563wvsl9sklzt4hdcuny3tlejznj7d ⚡️` origin-nature@coinos.io` --- **En euros, dollars, ou toute autre monnaie prise en charge** *Promesses uniquement pour le moment :* <a href="https://liberapay.com/origin-nature/"> <img src="!(image)[https://liberapay.com/assets/liberapay/icon-v2_black-on-yellow.svg]?etag=._QLQJKsW7OwBQqn7ASPxRA~~" width="200" height="200"> </a> --- Contactez-nous si vous souhaitez faire un don avec toute autre cryptomonnaie. --- ### 💡 Un modèle de partage de la valeur La moitié des dons est redistribuée aux contribut-eur-rice-s qui créent la valeur du site, pour expérimenter un modèle de partage de revenus sur Internet — un modèle qui respecte vos données et ne cherche pas à capter votre attention. L’autre moitié permet de couvrir les frais de fonctionnement du site.
@ e4950c93:1b99eccd
2025-04-03 14:53:56**Heureu-x-se d’avoir trouvé une information utile sur ce site ?** Soutenez le projet en faisant un don pour le faire vivre et remercier les contribut-eur-rice-s. --- **En bitcoin** <img src="https://coinos.io/qr/bc1q79er6c5mvvktvmvcstsnelv4j6tv3wdhw2k7ej/raw" width="200" height="200"> bc1qkm8me8l9563wvsl9sklzt4hdcuny3tlejznj7d ⚡️` origin-nature@coinos.io` --- **En euros, dollars, ou toute autre monnaie prise en charge** *Promesses uniquement pour le moment :* <a href="https://liberapay.com/origin-nature/"> <img src="!(image)[https://liberapay.com/assets/liberapay/icon-v2_black-on-yellow.svg]?etag=._QLQJKsW7OwBQqn7ASPxRA~~" width="200" height="200"> </a> --- Contactez-nous si vous souhaitez faire un don avec toute autre cryptomonnaie. --- ### 💡 Un modèle de partage de la valeur La moitié des dons est redistribuée aux contribut-eur-rice-s qui créent la valeur du site, pour expérimenter un modèle de partage de revenus sur Internet — un modèle qui respecte vos données et ne cherche pas à capter votre attention. L’autre moitié permet de couvrir les frais de fonctionnement du site. @ 266815e0:6cd408a5
2025-03-19 11:10:21How to create a nostr app quickly using [applesauce](https://hzrd149.github.io/applesauce/) In this guide we are going to build a nostr app that lets users follow and unfollow [fiatjaf](nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6) ## 1. Setup new project Start by setting up a new vite app using `pnpm create vite`, then set the name and select `Solid` and `Typescript` ```sh ➜ pnpm create vite │ ◇ Project name: │ followjaf │ ◇ Select a framework: │ Solid │ ◇ Select a variant: │ TypeScript │ ◇ Scaffolding project in ./followjaf... │ └ Done. Now run: cd followjaf pnpm install pnpm run dev ``` ## 2. Adding nostr dependencies There are a few useful nostr dependencies we are going to need. `nostr-tools` for the types and small methods, and [`rx-nostr`](https://penpenpng.github.io/rx-nostr/) for making relay connections ```sh pnpm install nostr-tools rx-nostr ``` ## 3. Setup rx-nostr Next we need to setup rxNostr so we can make connections to relays. create a new `src/nostr.ts` file with ```ts import { createRxNostr, noopVerifier } from "rx-nostr"; export const rxNostr = createRxNostr({ // skip verification here because we are going to verify events at the event store skipVerify: true, verifier: noopVerifier, }); ``` ## 4. Setup the event store Now that we have a way to connect to relays, we need a place to store events. We will use the [`EventStore`](https://hzrd149.github.io/applesauce/typedoc/classes/applesauce_core.EventStore.html) class from `applesauce-core` for this. create a new `src/stores.ts` file with > The event store does not store any events in the browsers local storage or anywhere else. It's in-memory only and provides a model for the UI ```ts import { EventStore } from "applesauce-core"; import { verifyEvent } from "nostr-tools"; export const eventStore = new EventStore(); // verify the events when they are added to the store eventStore.verifyEvent = verifyEvent; ``` ## 5. Create the query store The event store is where we store all the events, but we need a way for the UI to query them. We can use the [`QueryStore`](https://hzrd149.github.io/applesauce/typedoc/classes/applesauce_core.QueryStore.html) class from `applesauce-core` for this. Create a query store in `src/stores.ts` ```ts import { QueryStore } from "applesauce-core"; // ... // the query store needs the event store to subscribe to it export const queryStore = new QueryStore(eventStore); ``` ## 6. Setup the profile loader Next we need a way to fetch user profiles. We are going to use the [`ReplaceableLoader`](https://hzrd149.github.io/applesauce/overview/loaders.html#replaceable-loader) class from [`applesauce-loaders`](https://www.npmjs.com/package/applesauce-loaders) for this. > `applesauce-loaders` is a package that contains a few loader classes that can be used to fetch different types of data from relays. First install the package ```sh pnpm install applesauce-loaders ``` Then create a `src/loaders.ts` file with ```ts import { ReplaceableLoader } from "applesauce-loaders"; import { rxNostr } from "./nostr"; import { eventStore } from "./stores"; export const replaceableLoader = new ReplaceableLoader(rxNostr); // Start the loader and send any events to the event store replaceableLoader.subscribe((packet) => { eventStore.add(packet.event, packet.from); }); ``` ## 7. Fetch fiatjaf's profile Now that we have a way to store events, and a loader to help with fetching them, we should update the `src/App.tsx` component to fetch the profile. We can do this by calling the `next` method on the loader and passing a `pubkey`, `kind` and `relays` to it ```tsx function App() { // ... onMount(() => { // fetch fiatjaf's profile on load replaceableLoader.next({ pubkey: "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d", kind: 0, relays: ["wss://pyramid.fiatjaf.com/"], }); }); // ... } ``` ## 8. Display the profile Now that we have a way to fetch the profile, we need to display it in the UI. We can do this by using the [`ProfileQuery`](https://hzrd149.github.io/applesauce/typedoc/functions/applesauce_core.Queries.ProfileQuery.html) which gives us a stream of updates to a pubkey's profile. Create the profile using `queryStore.createQuery` and pass in the `ProfileQuery` and the pubkey. ```tsx const fiatjaf = queryStore.createQuery( ProfileQuery, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d" ); ``` But this just gives us an [observable](https://rxjs.dev/guide/observable), we need to subscribe to it to get the profile. Luckily SolidJS profiles a simple [`from`](https://docs.solidjs.com/reference/reactive-utilities/from) method to subscribe to any observable. > To make things reactive SolidJS uses accessors, so to get the profile we need to call `fiatjaf()` ```tsx function App() { // ... // Subscribe to fiatjaf's profile from the query store const fiatjaf = from( queryStore.createQuery(ProfileQuery, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d") ); return ( <> {/* replace the vite and solid logos with the profile picture */} <div> <img src={fiatjaf()?.picture} class="logo" /> </div> <h1>{fiatjaf()?.name}</h1> {/* ... */} </> ); } ``` ## 9. Letting the user signin Now we should let the user signin to the app. We can do this by creating a [`AccountManager`](https://hzrd149.github.io/applesauce/accounts/manager.html) class from `applesauce-accounts` First we need to install the packages ```sh pnpm install applesauce-accounts applesauce-signers ``` Then create a new `src/accounts.ts` file with ```ts import { AccountManager } from "applesauce-accounts"; import { registerCommonAccountTypes } from "applesauce-accounts/accounts"; // create an account manager instance export const accounts = new AccountManager(); // Adds the common account types to the manager registerCommonAccountTypes(accounts); ``` Next lets presume the user has a NIP-07 browser extension installed and add a signin button. ```tsx function App() { const signin = async () => { // do nothing if the user is already signed in if (accounts.active) return; // create a new nip-07 signer and try to get the pubkey const signer = new ExtensionSigner(); const pubkey = await signer.getPublicKey(); // create a new extension account, add it, and make it the active account const account = new ExtensionAccount(pubkey, signer); accounts.addAccount(account); accounts.setActive(account); }; return ( <> {/* ... */} <div class="card"> <p>Are you following the fiatjaf? the creator of "The nostr"</p> <button onClick={signin}>Check</button> </div> </> ); } ``` Now when the user clicks the button the app will ask for the users pubkey, then do nothing... but it's a start. > We are not persisting the accounts, so when the page reloads the user will NOT be signed in. you can learn about persisting the accounts in the [docs](https://hzrd149.github.io/applesauce/accounts/manager.html#persisting-accounts) ## 10. Showing the signed-in state We should show some indication to the user that they are signed in. We can do this by modifying the signin button if the user is signed in and giving them a way to sign-out ```tsx function App() { // subscribe to the currently active account (make sure to use the account$ observable) const account = from(accounts.active$); // ... const signout = () => { // do nothing if the user is not signed in if (!accounts.active) return; // signout the user const account = accounts.active; accounts.removeAccount(account); accounts.clearActive(); }; return ( <> {/* ... */} <div class="card"> <p>Are you following the fiatjaf? ( creator of "The nostr" )</p> {account() === undefined ? <button onClick={signin}>Check</button> : <button onClick={signout}>Signout</button>} </div> </> ); } ``` ## 11. Fetching the user's profile Now that we have a way to sign in and out of the app, we should fetch the user's profile when they sign in. ```tsx function App() { // ... // fetch the user's profile when they sign in createEffect(async () => { const active = account(); if (active) { // get the user's relays or fallback to some default relays const usersRelays = await active.getRelays?.(); const relays = usersRelays ? Object.keys(usersRelays) : ["wss://relay.damus.io", "wss://nos.lol"]; // tell the loader to fetch the users profile event replaceableLoader.next({ pubkey: active.pubkey, kind: 0, relays, }); // tell the loader to fetch the users contacts replaceableLoader.next({ pubkey: active.pubkey, kind: 3, relays, }); // tell the loader to fetch the users mailboxes replaceableLoader.next({ pubkey: active.pubkey, kind: 10002, relays, }); } }); // ... } ``` Next we need to subscribe to the users profile, to do this we can use some rxjs operators to chain the observables together. ```tsx import { Match, Switch } from "solid-js"; import { of, switchMap } from "rxjs"; function App() { // ... // subscribe to the active account, then subscribe to the users profile or undefined const profile = from( accounts.active$.pipe( switchMap((account) => (account ? queryStore.createQuery(ProfileQuery, account!.pubkey) : of(undefined))) ) ); // ... return ( <> {/* ... */} <div class="card"> <Switch> <Match when={account() && !profile()}> <p>Loading profile...</p> </Match> <Match when={profile()}> <p style="font-size: 1.2rem; font-weight: bold;">Welcome {profile()?.name}</p> </Match> </Switch> {/* ... */} </div> </> ); } ``` ## 12. Showing if the user is following fiatjaf Now that the app is fetching the users profile and contacts we should show if the user is following fiatjaf. ```tsx function App() { // ... // subscribe to the active account, then subscribe to the users contacts or undefined const contacts = from( accounts.active$.pipe( switchMap((account) => (account ? queryStore.createQuery(UserContactsQuery, account!.pubkey) : of(undefined))) ) ); const isFollowing = createMemo(() => { return contacts()?.some((c) => c.pubkey === "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d"); }); // ... return ( <> {/* ... */} <div class="card"> {/* ... */} <Switch fallback={ <p style="font-size: 1.2rem;"> Sign in to check if you are a follower of the fiatjaf ( creator of "The nostr" ) </p> } > <Match when={contacts() && isFollowing() === undefined}> <p>checking...</p> </Match> <Match when={contacts() && isFollowing() === true}> <p style="color: green; font-weight: bold; font-size: 2rem;"> Congratulations! You are a follower of the fiatjaf </p> </Match> <Match when={contacts() && isFollowing() === false}> <p style="color: red; font-weight: bold; font-size: 2rem;"> Why don't you follow the fiatjaf? do you even like nostr? </p> </Match> </Switch> {/* ... */} </div> </> ); } ``` ## 13. Adding the follow button Now that we have a way to check if the user is following fiatjaf, we should add a button to follow him. We can do this with [Actions](https://hzrd149.github.io/applesauce/overview/actions.html) which are pre-built methods to modify nostr events for a user. First we need to install the `applesauce-actions` and `applesauce-factory` package ```sh pnpm install applesauce-actions applesauce-factory ``` Then create a `src/actions.ts` file with ```ts import { EventFactory } from "applesauce-factory"; import { ActionHub } from "applesauce-actions"; import { eventStore } from "./stores"; import { accounts } from "./accounts"; // The event factory is used to build and modify nostr events export const factory = new EventFactory({ // accounts.signer is a NIP-07 signer that signs with the currently active account signer: accounts.signer, }); // The action hub is used to run Actions against the event store export const actions = new ActionHub(eventStore, factory); ``` Then create a `toggleFollow` method that will add or remove fiatjaf from the users contacts. > We are using the `exec` method to run the action, and the [`forEach`](https://rxjs.dev/api/index/class/Observable#foreach) method from RxJS allows us to await for all the events to be published ```tsx function App() { // ... const toggleFollow = async () => { // send any created events to rxNostr and the event store const publish = (event: NostrEvent) => { eventStore.add(event); rxNostr.send(event); }; if (isFollowing()) { await actions .exec(UnfollowUser, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d") .forEach(publish); } else { await actions .exec( FollowUser, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d", "wss://pyramid.fiatjaf.com/" ) .forEach(publish); } }; // ... return ( <> {/* ... */} <div class="card"> {/* ... */} {contacts() && <button onClick={toggleFollow}>{isFollowing() ? "Unfollow" : "Follow"}</button>} </div> </> ); } ``` ## 14. Adding outbox support The app looks like it works now but if the user reloads the page they will still see an the old version of their contacts list. we need to make sure rxNostr is publishing the events to the users outbox relays. To do this we can subscribe to the signed in users mailboxes using the query store in `src/nostr.ts` ```ts import { MailboxesQuery } from "applesauce-core/queries"; import { accounts } from "./accounts"; import { of, switchMap } from "rxjs"; import { queryStore } from "./stores"; // ... // subscribe to the active account, then subscribe to the users mailboxes and update rxNostr accounts.active$ .pipe(switchMap((account) => (account ? queryStore.createQuery(MailboxesQuery, account.pubkey) : of(undefined)))) .subscribe((mailboxes) => { if (mailboxes) rxNostr.setDefaultRelays(mailboxes.outboxes); else rxNostr.setDefaultRelays([]); }); ``` And that's it! we have a working nostr app that lets users follow and unfollow fiatjaf.
@ 266815e0:6cd408a5
2025-03-19 11:10:21How to create a nostr app quickly using [applesauce](https://hzrd149.github.io/applesauce/) In this guide we are going to build a nostr app that lets users follow and unfollow [fiatjaf](nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6) ## 1. Setup new project Start by setting up a new vite app using `pnpm create vite`, then set the name and select `Solid` and `Typescript` ```sh ➜ pnpm create vite │ ◇ Project name: │ followjaf │ ◇ Select a framework: │ Solid │ ◇ Select a variant: │ TypeScript │ ◇ Scaffolding project in ./followjaf... │ └ Done. Now run: cd followjaf pnpm install pnpm run dev ``` ## 2. Adding nostr dependencies There are a few useful nostr dependencies we are going to need. `nostr-tools` for the types and small methods, and [`rx-nostr`](https://penpenpng.github.io/rx-nostr/) for making relay connections ```sh pnpm install nostr-tools rx-nostr ``` ## 3. Setup rx-nostr Next we need to setup rxNostr so we can make connections to relays. create a new `src/nostr.ts` file with ```ts import { createRxNostr, noopVerifier } from "rx-nostr"; export const rxNostr = createRxNostr({ // skip verification here because we are going to verify events at the event store skipVerify: true, verifier: noopVerifier, }); ``` ## 4. Setup the event store Now that we have a way to connect to relays, we need a place to store events. We will use the [`EventStore`](https://hzrd149.github.io/applesauce/typedoc/classes/applesauce_core.EventStore.html) class from `applesauce-core` for this. create a new `src/stores.ts` file with > The event store does not store any events in the browsers local storage or anywhere else. It's in-memory only and provides a model for the UI ```ts import { EventStore } from "applesauce-core"; import { verifyEvent } from "nostr-tools"; export const eventStore = new EventStore(); // verify the events when they are added to the store eventStore.verifyEvent = verifyEvent; ``` ## 5. Create the query store The event store is where we store all the events, but we need a way for the UI to query them. We can use the [`QueryStore`](https://hzrd149.github.io/applesauce/typedoc/classes/applesauce_core.QueryStore.html) class from `applesauce-core` for this. Create a query store in `src/stores.ts` ```ts import { QueryStore } from "applesauce-core"; // ... // the query store needs the event store to subscribe to it export const queryStore = new QueryStore(eventStore); ``` ## 6. Setup the profile loader Next we need a way to fetch user profiles. We are going to use the [`ReplaceableLoader`](https://hzrd149.github.io/applesauce/overview/loaders.html#replaceable-loader) class from [`applesauce-loaders`](https://www.npmjs.com/package/applesauce-loaders) for this. > `applesauce-loaders` is a package that contains a few loader classes that can be used to fetch different types of data from relays. First install the package ```sh pnpm install applesauce-loaders ``` Then create a `src/loaders.ts` file with ```ts import { ReplaceableLoader } from "applesauce-loaders"; import { rxNostr } from "./nostr"; import { eventStore } from "./stores"; export const replaceableLoader = new ReplaceableLoader(rxNostr); // Start the loader and send any events to the event store replaceableLoader.subscribe((packet) => { eventStore.add(packet.event, packet.from); }); ``` ## 7. Fetch fiatjaf's profile Now that we have a way to store events, and a loader to help with fetching them, we should update the `src/App.tsx` component to fetch the profile. We can do this by calling the `next` method on the loader and passing a `pubkey`, `kind` and `relays` to it ```tsx function App() { // ... onMount(() => { // fetch fiatjaf's profile on load replaceableLoader.next({ pubkey: "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d", kind: 0, relays: ["wss://pyramid.fiatjaf.com/"], }); }); // ... } ``` ## 8. Display the profile Now that we have a way to fetch the profile, we need to display it in the UI. We can do this by using the [`ProfileQuery`](https://hzrd149.github.io/applesauce/typedoc/functions/applesauce_core.Queries.ProfileQuery.html) which gives us a stream of updates to a pubkey's profile. Create the profile using `queryStore.createQuery` and pass in the `ProfileQuery` and the pubkey. ```tsx const fiatjaf = queryStore.createQuery( ProfileQuery, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d" ); ``` But this just gives us an [observable](https://rxjs.dev/guide/observable), we need to subscribe to it to get the profile. Luckily SolidJS profiles a simple [`from`](https://docs.solidjs.com/reference/reactive-utilities/from) method to subscribe to any observable. > To make things reactive SolidJS uses accessors, so to get the profile we need to call `fiatjaf()` ```tsx function App() { // ... // Subscribe to fiatjaf's profile from the query store const fiatjaf = from( queryStore.createQuery(ProfileQuery, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d") ); return ( <> {/* replace the vite and solid logos with the profile picture */} <div> <img src={fiatjaf()?.picture} class="logo" /> </div> <h1>{fiatjaf()?.name}</h1> {/* ... */} </> ); } ``` ## 9. Letting the user signin Now we should let the user signin to the app. We can do this by creating a [`AccountManager`](https://hzrd149.github.io/applesauce/accounts/manager.html) class from `applesauce-accounts` First we need to install the packages ```sh pnpm install applesauce-accounts applesauce-signers ``` Then create a new `src/accounts.ts` file with ```ts import { AccountManager } from "applesauce-accounts"; import { registerCommonAccountTypes } from "applesauce-accounts/accounts"; // create an account manager instance export const accounts = new AccountManager(); // Adds the common account types to the manager registerCommonAccountTypes(accounts); ``` Next lets presume the user has a NIP-07 browser extension installed and add a signin button. ```tsx function App() { const signin = async () => { // do nothing if the user is already signed in if (accounts.active) return; // create a new nip-07 signer and try to get the pubkey const signer = new ExtensionSigner(); const pubkey = await signer.getPublicKey(); // create a new extension account, add it, and make it the active account const account = new ExtensionAccount(pubkey, signer); accounts.addAccount(account); accounts.setActive(account); }; return ( <> {/* ... */} <div class="card"> <p>Are you following the fiatjaf? the creator of "The nostr"</p> <button onClick={signin}>Check</button> </div> </> ); } ``` Now when the user clicks the button the app will ask for the users pubkey, then do nothing... but it's a start. > We are not persisting the accounts, so when the page reloads the user will NOT be signed in. you can learn about persisting the accounts in the [docs](https://hzrd149.github.io/applesauce/accounts/manager.html#persisting-accounts) ## 10. Showing the signed-in state We should show some indication to the user that they are signed in. We can do this by modifying the signin button if the user is signed in and giving them a way to sign-out ```tsx function App() { // subscribe to the currently active account (make sure to use the account$ observable) const account = from(accounts.active$); // ... const signout = () => { // do nothing if the user is not signed in if (!accounts.active) return; // signout the user const account = accounts.active; accounts.removeAccount(account); accounts.clearActive(); }; return ( <> {/* ... */} <div class="card"> <p>Are you following the fiatjaf? ( creator of "The nostr" )</p> {account() === undefined ? <button onClick={signin}>Check</button> : <button onClick={signout}>Signout</button>} </div> </> ); } ``` ## 11. Fetching the user's profile Now that we have a way to sign in and out of the app, we should fetch the user's profile when they sign in. ```tsx function App() { // ... // fetch the user's profile when they sign in createEffect(async () => { const active = account(); if (active) { // get the user's relays or fallback to some default relays const usersRelays = await active.getRelays?.(); const relays = usersRelays ? Object.keys(usersRelays) : ["wss://relay.damus.io", "wss://nos.lol"]; // tell the loader to fetch the users profile event replaceableLoader.next({ pubkey: active.pubkey, kind: 0, relays, }); // tell the loader to fetch the users contacts replaceableLoader.next({ pubkey: active.pubkey, kind: 3, relays, }); // tell the loader to fetch the users mailboxes replaceableLoader.next({ pubkey: active.pubkey, kind: 10002, relays, }); } }); // ... } ``` Next we need to subscribe to the users profile, to do this we can use some rxjs operators to chain the observables together. ```tsx import { Match, Switch } from "solid-js"; import { of, switchMap } from "rxjs"; function App() { // ... // subscribe to the active account, then subscribe to the users profile or undefined const profile = from( accounts.active$.pipe( switchMap((account) => (account ? queryStore.createQuery(ProfileQuery, account!.pubkey) : of(undefined))) ) ); // ... return ( <> {/* ... */} <div class="card"> <Switch> <Match when={account() && !profile()}> <p>Loading profile...</p> </Match> <Match when={profile()}> <p style="font-size: 1.2rem; font-weight: bold;">Welcome {profile()?.name}</p> </Match> </Switch> {/* ... */} </div> </> ); } ``` ## 12. Showing if the user is following fiatjaf Now that the app is fetching the users profile and contacts we should show if the user is following fiatjaf. ```tsx function App() { // ... // subscribe to the active account, then subscribe to the users contacts or undefined const contacts = from( accounts.active$.pipe( switchMap((account) => (account ? queryStore.createQuery(UserContactsQuery, account!.pubkey) : of(undefined))) ) ); const isFollowing = createMemo(() => { return contacts()?.some((c) => c.pubkey === "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d"); }); // ... return ( <> {/* ... */} <div class="card"> {/* ... */} <Switch fallback={ <p style="font-size: 1.2rem;"> Sign in to check if you are a follower of the fiatjaf ( creator of "The nostr" ) </p> } > <Match when={contacts() && isFollowing() === undefined}> <p>checking...</p> </Match> <Match when={contacts() && isFollowing() === true}> <p style="color: green; font-weight: bold; font-size: 2rem;"> Congratulations! You are a follower of the fiatjaf </p> </Match> <Match when={contacts() && isFollowing() === false}> <p style="color: red; font-weight: bold; font-size: 2rem;"> Why don't you follow the fiatjaf? do you even like nostr? </p> </Match> </Switch> {/* ... */} </div> </> ); } ``` ## 13. Adding the follow button Now that we have a way to check if the user is following fiatjaf, we should add a button to follow him. We can do this with [Actions](https://hzrd149.github.io/applesauce/overview/actions.html) which are pre-built methods to modify nostr events for a user. First we need to install the `applesauce-actions` and `applesauce-factory` package ```sh pnpm install applesauce-actions applesauce-factory ``` Then create a `src/actions.ts` file with ```ts import { EventFactory } from "applesauce-factory"; import { ActionHub } from "applesauce-actions"; import { eventStore } from "./stores"; import { accounts } from "./accounts"; // The event factory is used to build and modify nostr events export const factory = new EventFactory({ // accounts.signer is a NIP-07 signer that signs with the currently active account signer: accounts.signer, }); // The action hub is used to run Actions against the event store export const actions = new ActionHub(eventStore, factory); ``` Then create a `toggleFollow` method that will add or remove fiatjaf from the users contacts. > We are using the `exec` method to run the action, and the [`forEach`](https://rxjs.dev/api/index/class/Observable#foreach) method from RxJS allows us to await for all the events to be published ```tsx function App() { // ... const toggleFollow = async () => { // send any created events to rxNostr and the event store const publish = (event: NostrEvent) => { eventStore.add(event); rxNostr.send(event); }; if (isFollowing()) { await actions .exec(UnfollowUser, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d") .forEach(publish); } else { await actions .exec( FollowUser, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d", "wss://pyramid.fiatjaf.com/" ) .forEach(publish); } }; // ... return ( <> {/* ... */} <div class="card"> {/* ... */} {contacts() && <button onClick={toggleFollow}>{isFollowing() ? "Unfollow" : "Follow"}</button>} </div> </> ); } ``` ## 14. Adding outbox support The app looks like it works now but if the user reloads the page they will still see an the old version of their contacts list. we need to make sure rxNostr is publishing the events to the users outbox relays. To do this we can subscribe to the signed in users mailboxes using the query store in `src/nostr.ts` ```ts import { MailboxesQuery } from "applesauce-core/queries"; import { accounts } from "./accounts"; import { of, switchMap } from "rxjs"; import { queryStore } from "./stores"; // ... // subscribe to the active account, then subscribe to the users mailboxes and update rxNostr accounts.active$ .pipe(switchMap((account) => (account ? queryStore.createQuery(MailboxesQuery, account.pubkey) : of(undefined)))) .subscribe((mailboxes) => { if (mailboxes) rxNostr.setDefaultRelays(mailboxes.outboxes); else rxNostr.setDefaultRelays([]); }); ``` And that's it! we have a working nostr app that lets users follow and unfollow fiatjaf. @ a39d19ec:3d88f61e
2025-03-18 17:16:50Nun da das deutsche Bundesregime den Ruin Deutschlands beschlossen hat, der sehr wahrscheinlich mit dem Werkzeug des Geld druckens "finanziert" wird, kamen mir so viele Gedanken zur Geldmengenausweitung, dass ich diese für einmal niedergeschrieben habe. Die Ausweitung der Geldmenge führt aus klassischer wirtschaftlicher Sicht immer zu Preissteigerungen, weil mehr Geld im Umlauf auf eine begrenzte Menge an Gütern trifft. Dies lässt sich in mehreren Schritten analysieren: ### 1. Quantitätstheorie des Geldes Die klassische Gleichung der Quantitätstheorie des Geldes lautet: M • V = P • Y wobei: - M die Geldmenge ist, - V die Umlaufgeschwindigkeit des Geldes, - P das Preisniveau, - Y die reale Wirtschaftsleistung (BIP). Wenn M steigt und V sowie Y konstant bleiben, muss P steigen – also Inflation entstehen. ### 2. Gütermenge bleibt begrenzt Die Menge an real produzierten Gütern und Dienstleistungen wächst meist nur langsam im Vergleich zur Ausweitung der Geldmenge. Wenn die Geldmenge schneller steigt als die Produktionsgütermenge, führt dies dazu, dass mehr Geld für die gleiche Menge an Waren zur Verfügung steht – die Preise steigen. ### 3. Erwartungseffekte und Spekulation Wenn Unternehmen und Haushalte erwarten, dass mehr Geld im Umlauf ist, da eine zentrale Planung es so wollte, können sie steigende Preise antizipieren. Unternehmen erhöhen ihre Preise vorab, und Arbeitnehmer fordern höhere Löhne. Dies kann eine sich selbst verstärkende Spirale auslösen. ### 4. Internationale Perspektive Eine erhöhte Geldmenge kann die Währung abwerten, wenn andere Länder ihre Geldpolitik stabil halten. Eine schwächere Währung macht Importe teurer, was wiederum Preissteigerungen antreibt. ### 5. Kritik an der reinen Geldmengen-Theorie Der Vollständigkeit halber muss erwähnt werden, dass die meisten modernen Ökonomen im Staatsauftrag argumentieren, dass Inflation nicht nur von der Geldmenge abhängt, sondern auch von der Nachfrage nach Geld (z. B. in einer Wirtschaftskrise). Dennoch zeigt die historische Erfahrung, dass eine unkontrollierte Geldmengenausweitung langfristig immer zu Preissteigerungen führt, wie etwa in der Hyperinflation der Weimarer Republik oder in Simbabwe.
@ a39d19ec:3d88f61e
2025-03-18 17:16:50Nun da das deutsche Bundesregime den Ruin Deutschlands beschlossen hat, der sehr wahrscheinlich mit dem Werkzeug des Geld druckens "finanziert" wird, kamen mir so viele Gedanken zur Geldmengenausweitung, dass ich diese für einmal niedergeschrieben habe. Die Ausweitung der Geldmenge führt aus klassischer wirtschaftlicher Sicht immer zu Preissteigerungen, weil mehr Geld im Umlauf auf eine begrenzte Menge an Gütern trifft. Dies lässt sich in mehreren Schritten analysieren: ### 1. Quantitätstheorie des Geldes Die klassische Gleichung der Quantitätstheorie des Geldes lautet: M • V = P • Y wobei: - M die Geldmenge ist, - V die Umlaufgeschwindigkeit des Geldes, - P das Preisniveau, - Y die reale Wirtschaftsleistung (BIP). Wenn M steigt und V sowie Y konstant bleiben, muss P steigen – also Inflation entstehen. ### 2. Gütermenge bleibt begrenzt Die Menge an real produzierten Gütern und Dienstleistungen wächst meist nur langsam im Vergleich zur Ausweitung der Geldmenge. Wenn die Geldmenge schneller steigt als die Produktionsgütermenge, führt dies dazu, dass mehr Geld für die gleiche Menge an Waren zur Verfügung steht – die Preise steigen. ### 3. Erwartungseffekte und Spekulation Wenn Unternehmen und Haushalte erwarten, dass mehr Geld im Umlauf ist, da eine zentrale Planung es so wollte, können sie steigende Preise antizipieren. Unternehmen erhöhen ihre Preise vorab, und Arbeitnehmer fordern höhere Löhne. Dies kann eine sich selbst verstärkende Spirale auslösen. ### 4. Internationale Perspektive Eine erhöhte Geldmenge kann die Währung abwerten, wenn andere Länder ihre Geldpolitik stabil halten. Eine schwächere Währung macht Importe teurer, was wiederum Preissteigerungen antreibt. ### 5. Kritik an der reinen Geldmengen-Theorie Der Vollständigkeit halber muss erwähnt werden, dass die meisten modernen Ökonomen im Staatsauftrag argumentieren, dass Inflation nicht nur von der Geldmenge abhängt, sondern auch von der Nachfrage nach Geld (z. B. in einer Wirtschaftskrise). Dennoch zeigt die historische Erfahrung, dass eine unkontrollierte Geldmengenausweitung langfristig immer zu Preissteigerungen führt, wie etwa in der Hyperinflation der Weimarer Republik oder in Simbabwe. @ f1989a96:bcaaf2c1
2025-04-03 14:30:08Good morning, readers! Georgian officials froze the bank accounts of five nonprofit organizations that provide financial and legal support to detained protesters. This follows rising public unrest as Georgia’s regime pushes new laws restricting free speech and assembly, introducing new fines and penalties, and expanding law enforcement powers. By eroding civil protections, the regime makes it more dangerous and costly for activists, dissenters, and everyday citizens to stand up against an increasingly repressive regime.\ \ Meanwhile, the Indian government introduced a new income tax bill that grants tax authorities sweeping surveillance power over anyone they “suspect” of tax evasion. If suspected, tax authorities are legally allowed to access Indians' email, social media, and bank accounts, raising obvious concerns over state overreach and invasions of individual financial privacy.\ \ In freedom tech news, HRF donated 1 billion satoshis to more than 20 projects worldwide, focusing on supporting human rights defenders and vulnerable communities under authoritarian regimes across Asia, Africa, and Latin America. These gifts advance censorship-resistant communications and transactions, bitcoin education, and privacy tools so that dissidents, nonprofits, and individuals may better protect their human rights and financial freedom. In this letter we also spotlight a new open-source mobile Bitcoin wallet called Cove. While still in beta, the wallet can be used with a hardware device or on its own as a hot wallet, offering a flexible self-custody setup for managing Bitcoin. We end with a podcast in which HRF Chief Strategy Officer Alex Gladstein discusses the state of freedom tech and why Bitcoin stands as the most promising tool for financial liberation. **Now, let’s get right to it!** ### [**SUBSCRIBE HERE**](https://mailchi.mp/hrf.org/financial-freedom-newsletter?mc_cid=bf652c0a5a) ## **GLOBAL NEWS** #### **Georgia | Officials Freeze Accounts of Organizations Supporting Protesters** Georgian officials have [frozen](https://www.amnesty.org/en/latest/news/2025/03/georgia-authorities-freeze-accounts-of-organizations-supporting-protesters-to-kill-the-peaceful-protests/) the bank accounts of five nonprofit organizations that provide financial and legal aid to dissenters. This comes in response to an uprising of protests over new controversial laws that restrict free expression and assembly, increase fines and detention periods, and expand law enforcement powers. Georgian officials justify the account freezes as part of an investigation into “sabotage,” yet they have provided no evidence. Amnesty International [warns](https://www.amnesty.org/en/latest/news/2025/03/georgia-authorities-freeze-accounts-of-organizations-supporting-protesters-to-kill-the-peaceful-protests/) this financial assault could “kill the entire protest movement.” Bitcoin provides a way to circumvent these struggles. Its uncensorable and permissionless nature has helped [sustain](https://www.journalofdemocracy.org/online-exclusive/how-to-dictator-proof-your-money/) pro-democracy movements across Belarus and Nigeria, proving it is capable of addressing the immense financial restrictions dictators impose. #### **United Arab Emirates | Plans to Launch “Digital Durham” CBDC in 2025** The United Arab Emirates (UAE) will [launch](https://www.businesstoday.in/technology/news/story/uae-to-launch-digital-dirham-by-year-end-to-modernise-payments-and-noost-financial-inclusion-470013-2025-03-31?utm_source=semafor#) its central bank digital currency (CBDC), the “[Digital Durham](https://cbdctracker.hrf.org/currency/united-arab-emirates),” by the end of 2025. [According](https://www.ledgerinsights.com/uae-to-launch-cbdc-in-q4-2025/) to the central bank, the CBDC will be available through licensed financial institutions and operate via a government-run digital wallet. Every transaction will be recorded on a permissioned blockchain run by the government. The central bank further [admitted](https://u.ae/en/about-the-uae/strategies-initiatives-and-awards/strategies-plans-and-visions/finance-and-economy/central-bank-digital-currency-strategy) the CBDC will replace cash and [assist](https://www.businesstoday.in/technology/news/story/uae-to-launch-digital-dirham-by-year-end-to-modernise-payments-and-noost-financial-inclusion-470013-2025-03-31?utm_source=semafor#) law enforcement “by leaving a digital trail for transactions involving illicit funds.” Officials [claim](https://www.businesstoday.in/technology/news/story/uae-to-launch-digital-dirham-by-year-end-to-modernise-payments-and-noost-financial-inclusion-470013-2025-03-31?utm_source=semafor#) this is to combat financial crime, but it also enables real-time surveillance and tracking of individual financial activity. In a country known for strict laws against dissent and extensive surveillance capabilities, it is not hard to see how a CBDC will erode the autonomy and rights of activists, dissenters, and others who oppose an increasingly authoritarian regime. #### **India | Grants Tax Authorities Access to Citizens’ Online Data** Starting in April 2026, the Indian government will [grant](https://economictimes.indiatimes.com/wealth/tax/your-email-and-social-media-account-can-be-accessed-by-income-tax-officer-starting-next-financial-year-in-these-cases/articleshow/118685184.cms) tax authorities legal access to the private online data of any citizen “suspected” of tax evasion. This will include legal access to personal emails, social media, and bank accounts. The new law expands on the Income Tax Act of 1961, which previously limited officials to searching physical premises for financial documents. Now, officials can bypass digital security measures and access private data without consent — all under a legal framework. This dissipation of financial privacy sets an intrusive precedent and opens the door to state-level corruption and surveillance in a country where the Modi regime has already made it clear they are happy to use financial repression to further cement their power. #### **Myanmar | Bitcoin as a Tool Support Earthquake Disaster Relief** Last week, a [7.7 magnitude earthquake](https://www.nytimes.com/2025/03/28/world/asia/earthquake-myanmar-thailand-death-toll.html) struck central Burma, with strong tremors reaching neighboring Thailand. The [official death toll ](https://www.reuters.com/business/environment/survivors-myanmar-quake-left-without-food-water-shelter-aid-groups-say-2025-04-01/)has surpassed 2700. And in Bangkok, a 33-story building under construction [collapsed](https://www.youtube.com/watch?v=ynrhyIh4ozo). Despite an already strenuous situation, Burma’s military junta continues its oppression. They are [blocking](https://www.nytimes.com/2025/03/31/world/asia/myanmar-earthquake-rescue.html) rescue teams from reaching the Sagaing region — the epicenter of the earthquake and the heart of Burma’s pro-democracy movement — and instead channeling aid to regime-controlled cities like Naypyidaw and Mandalay. The junta is also continuing to conduct air strikes on civilians and restricting equipment and fuel for aid groups, leaving a [million](https://data.unhcr.org/en/country/mmr) people in Sagaing to fend for themselves. In these repressive circumstances, Bitcoin can provide a censorship-resistant way to send funds directly to those affected. #### **Angola | Regime Jacks Price of Diesel** The Angolan regime [raised](https://www.rigzone.com/news/wire/angola_doubles_diesel_prices_after_imf_call_for_subsidy_cuts-25-mar-2025-180020-article/) diesel prices by 50% in the process of eliminating fuel subsidies. Diesel prices suddenly increased from 200 to 300 kwanza per liter, driving up transportation costs in a country where over half the population lives on [less](https://www.rigzone.com/news/wire/angola_doubles_diesel_prices_after_imf_call_for_subsidy_cuts-25-mar-2025-180020-article/) than $2 a day and inflation is over 42%. Previous fuel subsidy cuts in 2023 (where the price of diesel rose [80%](https://www.dw.com/en/angolan-police-crack-down-on-fuel-hike-protests/a-65978231)) sparked [protests](https://www.dw.com/en/angolan-police-crack-down-on-fuel-hike-protests/a-65978231) between taxi drivers, nonprofit workers, and law enforcement. This recent price increase now raises fears of renewed crackdowns. The Angolan regime also introduced new civil society laws that Guilherme Neves, chairman of the human rights organization Associacao Maos Livres, [describes](https://www.dw.com/en/angolan-police-crack-down-on-fuel-hike-protests/a-65978231) as a “license to erase non-governmental organizations that are not government-compliant.” Angolans find themselves in increasingly precarious financial positions as the government erodes the civil safeguards protecting nonprofits and dissenters. #### **Nicaragua | Ortega’s Dismantling of Press Freedom** Since coming to power in 2007, Ortega has [closed or seized](https://havanatimes.org/features/ortegas-war-on-journalism-in-nicaragua/) 61 media outlets, imprisoned countless journalists, and forced over 280 journalists into exile. His [assault on press freedom](https://havanatimes.org/features/ortegas-war-on-journalism-in-nicaragua/) has unfolded in two phases: initial raids on local radio stations and TV channels between 2007 and 2017, followed by full-scale censorship in 2018 on independent media outlets like [La Prensa](https://www.laprensani.com/) and [CONFIDENCIAL](https://confidencial.digital/). Ortega then intensified attacks from 2019 to 2021 by closing Nicaragua’s second-oldest newspaper and passing laws to [criminalize](https://havanatimes.org/features/ortegas-war-on-journalism-in-nicaragua/) free expression. This is a deliberate strategy to eliminate dissent and independent voices. What’s happening in Nicaragua highlights the importance of open and decentralized protocols like nostr, which allow journalists to publish freely without getting censored. While still early, it is becoming essential for sharing information absent the fear of being blocked or silenced by autocratic leaders. ## BITCOIN AND FREEDOM TECH NEWS #### **HRF | Gifts 1 Billion Satoshis to 20+ Open Source Projects Worldwide** HRF gifted 1 billion satoshis in its Q1 2025 round of [Bitcoin Development Fund](https://hrf.org/program/financial-freedom/bitcoin-development-fund/) (BDF) grants, supporting more than 20 open-source projects around the world. These projects advance Bitcoin education, open-source software, mining decentralization, and privacy tools for activists contending with authoritarian regimes across Asia, Latin America, and Africa. Supporting permissionless financial tools and censorship-resistant technologies empowers dissidents, journalists, and civil society to organize, transact, and communicate without state suppression and interference. Learn more about the grantees and their work [here](https://hrf.org/latest/hrf-bitcoin-development-fund-supports-20-projects-worldwide/). #### **Cove | New Open-Source and Permissionless Bitcoin Wallet** [Cove](https://github.com/bitcoinppl/cove) is a new open-source and permissionless mobile Bitcoin wallet that aims to put users in full control of their Bitcoin. Users can connect their own hardware wallet (to manage Bitcoin offline) or use Cove as a hot wallet (to manage Bitcoin online). It also allows users to create multiple wallets from the app itself. In the future, Cove plans to add Unspent Transaction Output (UTXO) selection and coin control, giving users more independence over their transactions and the tools to better protect their financial privacy. While still in beta and only suitable for test funds, this wallet holds promise as a privacy tool to equip dissidents with self-custodied Bitcoin. You can try it [here](https://github.com/bitcoinppl/cove). #### **Second | New Ark Implementation Launches on Bitcoin Signet** [Second](https://second.tech/), a company building on Ark, a protocol designed to help scale Bitcoin’s transaction throughput, [launched](https://blog.second.tech/try-ark-on-signet/?ref=nobsbitcoin.com) “Bark.” Bark is a test implementation of the Ark protocol deployed on Bitcoin’s [Signet](https://en.bitcoin.it/wiki/Signet) network (where developers test software). More broadly, the Ark protocol helps make Bitcoin transactions more private, faster, and cheaper, supporting the network in handling more transactions and users with the tradeoff of being less trusted than the mainchain, as funds stored in a noncustodial way on Ark can expire if not used. While it is still in early development, the test release of Bark marks a step toward deployment on the main Bitcoin network. Scaling solutions like Ark could be important for activists and individuals. They might ensure Bitcoin remains accessible to all, even as block space demand increases and network fees rise. Learn about it [here](https://blog.second.tech/try-ark-on-signet/?ref=nobsbitcoin.com). #### **Braiins | Open Sources Bitcoin Control Board** [Braiins](https://braiins.com/), a company building tools for Bitcoin mining, [open-sourced](https://x.com/BraiinsMining/status/1904601547855573458) its [BCB100](https://github.com/braiins/BCB100) Bitcoin Control Board, giving miners using their products greater insight and control over their Bitcoin mining hardware and firmware. Sharing the design files and firmware openly helps strengthen Bitcoin’s decentralization, making it more resilient against corporate or state interference. Specifically, open-sourcing mining hardware ensures individual miners can operate independently, reducing censorship risks across the entire network. In turn, this preserves financial freedom by keeping Bitcoin accessible and usable by dissidents, nonprofits, and individuals who need it most. #### **African Bitcoiners | Publish Bitcoin Starter Guide** [African Bitcoiners](https://x.com/afribitcoiners) just published “[Bitcoin: Africa’s Guide to Freedom Money](https://x.com/afribitcoiners/status/1904516726273851513),” a Bitcoin guide providing clear, practical insights into how Bitcoin can help people across the continent escape inflation, corrupt regimes, and failing financial systems. It covers essential topics to get started — from choosing a wallet to properly securing Bitcoin. In Africa, where some of the world’s longest-standing dictators restrict even basic financial activity, this guide is a powerful resource for human rights defenders, nonprofits, and everyday citizens. Read it[ here](https://bitcoiners.africa/bitcoin-africas-guide-to-freedom-money/). #### **OpenSats | 10th Wave of Nostr Grants** [OpenSats](https://opensats.org/), a nonprofit that supports open-source software development, [announced](https://opensats.org/blog/10th-wave-of-nostr-grants) its tenth wave of grants for projects in the nostr ecosystem. Nostr is a decentralized protocol that enables digital identity and communications outside the reach of authoritarian states. The grant round provides support to nostr Epoxy, which enhances access to nostr by circumventing censorship through a network of paid proxies. This ensures activists and dissidents can continue to communicate even in restrictive environments. Additionally, Zapstore received a grant for providing a permissionless app store built on nostr that enables developers to distribute software without corporate gatekeepers. This provides an open-source alternative to centralized app stores that often comply with government censorship and restrict dissidents’ access to freedom tools. ## RECOMMENDED CONTENT #### **Freedom Tech with Alex Gladstein** In this [episode](https://x.com/blockspacepod/status/1896229100702089589?s=46&t=yEPKerGEzeCp5j_mIaNJ8A) of The Gwart Show, Alex Gladstein, chief strategy officer at HRF, breaks down how and why Bitcoin serves as “money dictators can’t stop.” Drawing on more than 17 years of human rights work, he shares real-world examples of activists and citizens using Bitcoin to escape financial repression in authoritarian countries. Gladstein also explores privacy tools, cross-border payments, and why Bitcoin offers promising hope for financial freedom. Watch the full conversation [here](https://www.youtube.com/watch?v=5Ng961QZwI0). #### **The State of Personal Online Security and Confidentiality with Meredith Whittaker** In this [keynote](https://www.youtube.com/watch?v=AyH7zoP-JOg) for SXSW 2025, Signal CEO Meredith Whittaker shares her growing concerns around AI, personal data collection, and the erosion of privacy in today’s increasingly digital world. She emphasizes the need for more secure, uncensorable, and privacy-protecting technologies that shield users from surveillance and exploitation, especially in the context of authoritarian regimes. Watch the [full discussion](https://www.youtube.com/watch?v=AyH7zoP-JOg) for a pragmatic view into the future of digital privacy and security. *If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report [here](https://mailchi.mp/hrf.org/financial-freedom-newsletter?mc_cid=bf652c0a5a).* *Support the newsletter by donating bitcoin to HRF’s Financial Freedom program [via BTCPay](https://hrf.org/btc).*\ *Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ [hrf.org](http://hrf.org/)* *The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals [here](https://forms.monday.com/forms/57019f8829449d9e729d9e3545a237ea?r=use1)*. [**Subscribe to newsletter**](http://financialfreedomreport.org/) [**Apply for a grant**](https://forms.monday.com/forms/57019f8829449d9e729d9e3545a237ea?r=use1&mc_cid=39c1c9b7e8&mc_eid=778e9876e3) [**Support our work**](https://hrf.org/btc?mc_cid=39c1c9b7e8&mc_eid=778e9876e3) [**Visit our website**](https://hrf.org/programs/financial-freedom/)
@ f1989a96:bcaaf2c1
2025-04-03 14:30:08Good morning, readers! Georgian officials froze the bank accounts of five nonprofit organizations that provide financial and legal support to detained protesters. This follows rising public unrest as Georgia’s regime pushes new laws restricting free speech and assembly, introducing new fines and penalties, and expanding law enforcement powers. By eroding civil protections, the regime makes it more dangerous and costly for activists, dissenters, and everyday citizens to stand up against an increasingly repressive regime.\ \ Meanwhile, the Indian government introduced a new income tax bill that grants tax authorities sweeping surveillance power over anyone they “suspect” of tax evasion. If suspected, tax authorities are legally allowed to access Indians' email, social media, and bank accounts, raising obvious concerns over state overreach and invasions of individual financial privacy.\ \ In freedom tech news, HRF donated 1 billion satoshis to more than 20 projects worldwide, focusing on supporting human rights defenders and vulnerable communities under authoritarian regimes across Asia, Africa, and Latin America. These gifts advance censorship-resistant communications and transactions, bitcoin education, and privacy tools so that dissidents, nonprofits, and individuals may better protect their human rights and financial freedom. In this letter we also spotlight a new open-source mobile Bitcoin wallet called Cove. While still in beta, the wallet can be used with a hardware device or on its own as a hot wallet, offering a flexible self-custody setup for managing Bitcoin. We end with a podcast in which HRF Chief Strategy Officer Alex Gladstein discusses the state of freedom tech and why Bitcoin stands as the most promising tool for financial liberation. **Now, let’s get right to it!** ### [**SUBSCRIBE HERE**](https://mailchi.mp/hrf.org/financial-freedom-newsletter?mc_cid=bf652c0a5a) ## **GLOBAL NEWS** #### **Georgia | Officials Freeze Accounts of Organizations Supporting Protesters** Georgian officials have [frozen](https://www.amnesty.org/en/latest/news/2025/03/georgia-authorities-freeze-accounts-of-organizations-supporting-protesters-to-kill-the-peaceful-protests/) the bank accounts of five nonprofit organizations that provide financial and legal aid to dissenters. This comes in response to an uprising of protests over new controversial laws that restrict free expression and assembly, increase fines and detention periods, and expand law enforcement powers. Georgian officials justify the account freezes as part of an investigation into “sabotage,” yet they have provided no evidence. Amnesty International [warns](https://www.amnesty.org/en/latest/news/2025/03/georgia-authorities-freeze-accounts-of-organizations-supporting-protesters-to-kill-the-peaceful-protests/) this financial assault could “kill the entire protest movement.” Bitcoin provides a way to circumvent these struggles. Its uncensorable and permissionless nature has helped [sustain](https://www.journalofdemocracy.org/online-exclusive/how-to-dictator-proof-your-money/) pro-democracy movements across Belarus and Nigeria, proving it is capable of addressing the immense financial restrictions dictators impose. #### **United Arab Emirates | Plans to Launch “Digital Durham” CBDC in 2025** The United Arab Emirates (UAE) will [launch](https://www.businesstoday.in/technology/news/story/uae-to-launch-digital-dirham-by-year-end-to-modernise-payments-and-noost-financial-inclusion-470013-2025-03-31?utm_source=semafor#) its central bank digital currency (CBDC), the “[Digital Durham](https://cbdctracker.hrf.org/currency/united-arab-emirates),” by the end of 2025. [According](https://www.ledgerinsights.com/uae-to-launch-cbdc-in-q4-2025/) to the central bank, the CBDC will be available through licensed financial institutions and operate via a government-run digital wallet. Every transaction will be recorded on a permissioned blockchain run by the government. The central bank further [admitted](https://u.ae/en/about-the-uae/strategies-initiatives-and-awards/strategies-plans-and-visions/finance-and-economy/central-bank-digital-currency-strategy) the CBDC will replace cash and [assist](https://www.businesstoday.in/technology/news/story/uae-to-launch-digital-dirham-by-year-end-to-modernise-payments-and-noost-financial-inclusion-470013-2025-03-31?utm_source=semafor#) law enforcement “by leaving a digital trail for transactions involving illicit funds.” Officials [claim](https://www.businesstoday.in/technology/news/story/uae-to-launch-digital-dirham-by-year-end-to-modernise-payments-and-noost-financial-inclusion-470013-2025-03-31?utm_source=semafor#) this is to combat financial crime, but it also enables real-time surveillance and tracking of individual financial activity. In a country known for strict laws against dissent and extensive surveillance capabilities, it is not hard to see how a CBDC will erode the autonomy and rights of activists, dissenters, and others who oppose an increasingly authoritarian regime. #### **India | Grants Tax Authorities Access to Citizens’ Online Data** Starting in April 2026, the Indian government will [grant](https://economictimes.indiatimes.com/wealth/tax/your-email-and-social-media-account-can-be-accessed-by-income-tax-officer-starting-next-financial-year-in-these-cases/articleshow/118685184.cms) tax authorities legal access to the private online data of any citizen “suspected” of tax evasion. This will include legal access to personal emails, social media, and bank accounts. The new law expands on the Income Tax Act of 1961, which previously limited officials to searching physical premises for financial documents. Now, officials can bypass digital security measures and access private data without consent — all under a legal framework. This dissipation of financial privacy sets an intrusive precedent and opens the door to state-level corruption and surveillance in a country where the Modi regime has already made it clear they are happy to use financial repression to further cement their power. #### **Myanmar | Bitcoin as a Tool Support Earthquake Disaster Relief** Last week, a [7.7 magnitude earthquake](https://www.nytimes.com/2025/03/28/world/asia/earthquake-myanmar-thailand-death-toll.html) struck central Burma, with strong tremors reaching neighboring Thailand. The [official death toll ](https://www.reuters.com/business/environment/survivors-myanmar-quake-left-without-food-water-shelter-aid-groups-say-2025-04-01/)has surpassed 2700. And in Bangkok, a 33-story building under construction [collapsed](https://www.youtube.com/watch?v=ynrhyIh4ozo). Despite an already strenuous situation, Burma’s military junta continues its oppression. They are [blocking](https://www.nytimes.com/2025/03/31/world/asia/myanmar-earthquake-rescue.html) rescue teams from reaching the Sagaing region — the epicenter of the earthquake and the heart of Burma’s pro-democracy movement — and instead channeling aid to regime-controlled cities like Naypyidaw and Mandalay. The junta is also continuing to conduct air strikes on civilians and restricting equipment and fuel for aid groups, leaving a [million](https://data.unhcr.org/en/country/mmr) people in Sagaing to fend for themselves. In these repressive circumstances, Bitcoin can provide a censorship-resistant way to send funds directly to those affected. #### **Angola | Regime Jacks Price of Diesel** The Angolan regime [raised](https://www.rigzone.com/news/wire/angola_doubles_diesel_prices_after_imf_call_for_subsidy_cuts-25-mar-2025-180020-article/) diesel prices by 50% in the process of eliminating fuel subsidies. Diesel prices suddenly increased from 200 to 300 kwanza per liter, driving up transportation costs in a country where over half the population lives on [less](https://www.rigzone.com/news/wire/angola_doubles_diesel_prices_after_imf_call_for_subsidy_cuts-25-mar-2025-180020-article/) than $2 a day and inflation is over 42%. Previous fuel subsidy cuts in 2023 (where the price of diesel rose [80%](https://www.dw.com/en/angolan-police-crack-down-on-fuel-hike-protests/a-65978231)) sparked [protests](https://www.dw.com/en/angolan-police-crack-down-on-fuel-hike-protests/a-65978231) between taxi drivers, nonprofit workers, and law enforcement. This recent price increase now raises fears of renewed crackdowns. The Angolan regime also introduced new civil society laws that Guilherme Neves, chairman of the human rights organization Associacao Maos Livres, [describes](https://www.dw.com/en/angolan-police-crack-down-on-fuel-hike-protests/a-65978231) as a “license to erase non-governmental organizations that are not government-compliant.” Angolans find themselves in increasingly precarious financial positions as the government erodes the civil safeguards protecting nonprofits and dissenters. #### **Nicaragua | Ortega’s Dismantling of Press Freedom** Since coming to power in 2007, Ortega has [closed or seized](https://havanatimes.org/features/ortegas-war-on-journalism-in-nicaragua/) 61 media outlets, imprisoned countless journalists, and forced over 280 journalists into exile. His [assault on press freedom](https://havanatimes.org/features/ortegas-war-on-journalism-in-nicaragua/) has unfolded in two phases: initial raids on local radio stations and TV channels between 2007 and 2017, followed by full-scale censorship in 2018 on independent media outlets like [La Prensa](https://www.laprensani.com/) and [CONFIDENCIAL](https://confidencial.digital/). Ortega then intensified attacks from 2019 to 2021 by closing Nicaragua’s second-oldest newspaper and passing laws to [criminalize](https://havanatimes.org/features/ortegas-war-on-journalism-in-nicaragua/) free expression. This is a deliberate strategy to eliminate dissent and independent voices. What’s happening in Nicaragua highlights the importance of open and decentralized protocols like nostr, which allow journalists to publish freely without getting censored. While still early, it is becoming essential for sharing information absent the fear of being blocked or silenced by autocratic leaders. ## BITCOIN AND FREEDOM TECH NEWS #### **HRF | Gifts 1 Billion Satoshis to 20+ Open Source Projects Worldwide** HRF gifted 1 billion satoshis in its Q1 2025 round of [Bitcoin Development Fund](https://hrf.org/program/financial-freedom/bitcoin-development-fund/) (BDF) grants, supporting more than 20 open-source projects around the world. These projects advance Bitcoin education, open-source software, mining decentralization, and privacy tools for activists contending with authoritarian regimes across Asia, Latin America, and Africa. Supporting permissionless financial tools and censorship-resistant technologies empowers dissidents, journalists, and civil society to organize, transact, and communicate without state suppression and interference. Learn more about the grantees and their work [here](https://hrf.org/latest/hrf-bitcoin-development-fund-supports-20-projects-worldwide/). #### **Cove | New Open-Source and Permissionless Bitcoin Wallet** [Cove](https://github.com/bitcoinppl/cove) is a new open-source and permissionless mobile Bitcoin wallet that aims to put users in full control of their Bitcoin. Users can connect their own hardware wallet (to manage Bitcoin offline) or use Cove as a hot wallet (to manage Bitcoin online). It also allows users to create multiple wallets from the app itself. In the future, Cove plans to add Unspent Transaction Output (UTXO) selection and coin control, giving users more independence over their transactions and the tools to better protect their financial privacy. While still in beta and only suitable for test funds, this wallet holds promise as a privacy tool to equip dissidents with self-custodied Bitcoin. You can try it [here](https://github.com/bitcoinppl/cove). #### **Second | New Ark Implementation Launches on Bitcoin Signet** [Second](https://second.tech/), a company building on Ark, a protocol designed to help scale Bitcoin’s transaction throughput, [launched](https://blog.second.tech/try-ark-on-signet/?ref=nobsbitcoin.com) “Bark.” Bark is a test implementation of the Ark protocol deployed on Bitcoin’s [Signet](https://en.bitcoin.it/wiki/Signet) network (where developers test software). More broadly, the Ark protocol helps make Bitcoin transactions more private, faster, and cheaper, supporting the network in handling more transactions and users with the tradeoff of being less trusted than the mainchain, as funds stored in a noncustodial way on Ark can expire if not used. While it is still in early development, the test release of Bark marks a step toward deployment on the main Bitcoin network. Scaling solutions like Ark could be important for activists and individuals. They might ensure Bitcoin remains accessible to all, even as block space demand increases and network fees rise. Learn about it [here](https://blog.second.tech/try-ark-on-signet/?ref=nobsbitcoin.com). #### **Braiins | Open Sources Bitcoin Control Board** [Braiins](https://braiins.com/), a company building tools for Bitcoin mining, [open-sourced](https://x.com/BraiinsMining/status/1904601547855573458) its [BCB100](https://github.com/braiins/BCB100) Bitcoin Control Board, giving miners using their products greater insight and control over their Bitcoin mining hardware and firmware. Sharing the design files and firmware openly helps strengthen Bitcoin’s decentralization, making it more resilient against corporate or state interference. Specifically, open-sourcing mining hardware ensures individual miners can operate independently, reducing censorship risks across the entire network. In turn, this preserves financial freedom by keeping Bitcoin accessible and usable by dissidents, nonprofits, and individuals who need it most. #### **African Bitcoiners | Publish Bitcoin Starter Guide** [African Bitcoiners](https://x.com/afribitcoiners) just published “[Bitcoin: Africa’s Guide to Freedom Money](https://x.com/afribitcoiners/status/1904516726273851513),” a Bitcoin guide providing clear, practical insights into how Bitcoin can help people across the continent escape inflation, corrupt regimes, and failing financial systems. It covers essential topics to get started — from choosing a wallet to properly securing Bitcoin. In Africa, where some of the world’s longest-standing dictators restrict even basic financial activity, this guide is a powerful resource for human rights defenders, nonprofits, and everyday citizens. Read it[ here](https://bitcoiners.africa/bitcoin-africas-guide-to-freedom-money/). #### **OpenSats | 10th Wave of Nostr Grants** [OpenSats](https://opensats.org/), a nonprofit that supports open-source software development, [announced](https://opensats.org/blog/10th-wave-of-nostr-grants) its tenth wave of grants for projects in the nostr ecosystem. Nostr is a decentralized protocol that enables digital identity and communications outside the reach of authoritarian states. The grant round provides support to nostr Epoxy, which enhances access to nostr by circumventing censorship through a network of paid proxies. This ensures activists and dissidents can continue to communicate even in restrictive environments. Additionally, Zapstore received a grant for providing a permissionless app store built on nostr that enables developers to distribute software without corporate gatekeepers. This provides an open-source alternative to centralized app stores that often comply with government censorship and restrict dissidents’ access to freedom tools. ## RECOMMENDED CONTENT #### **Freedom Tech with Alex Gladstein** In this [episode](https://x.com/blockspacepod/status/1896229100702089589?s=46&t=yEPKerGEzeCp5j_mIaNJ8A) of The Gwart Show, Alex Gladstein, chief strategy officer at HRF, breaks down how and why Bitcoin serves as “money dictators can’t stop.” Drawing on more than 17 years of human rights work, he shares real-world examples of activists and citizens using Bitcoin to escape financial repression in authoritarian countries. Gladstein also explores privacy tools, cross-border payments, and why Bitcoin offers promising hope for financial freedom. Watch the full conversation [here](https://www.youtube.com/watch?v=5Ng961QZwI0). #### **The State of Personal Online Security and Confidentiality with Meredith Whittaker** In this [keynote](https://www.youtube.com/watch?v=AyH7zoP-JOg) for SXSW 2025, Signal CEO Meredith Whittaker shares her growing concerns around AI, personal data collection, and the erosion of privacy in today’s increasingly digital world. She emphasizes the need for more secure, uncensorable, and privacy-protecting technologies that shield users from surveillance and exploitation, especially in the context of authoritarian regimes. Watch the [full discussion](https://www.youtube.com/watch?v=AyH7zoP-JOg) for a pragmatic view into the future of digital privacy and security. *If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report [here](https://mailchi.mp/hrf.org/financial-freedom-newsletter?mc_cid=bf652c0a5a).* *Support the newsletter by donating bitcoin to HRF’s Financial Freedom program [via BTCPay](https://hrf.org/btc).*\ *Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ [hrf.org](http://hrf.org/)* *The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals [here](https://forms.monday.com/forms/57019f8829449d9e729d9e3545a237ea?r=use1)*. [**Subscribe to newsletter**](http://financialfreedomreport.org/) [**Apply for a grant**](https://forms.monday.com/forms/57019f8829449d9e729d9e3545a237ea?r=use1&mc_cid=39c1c9b7e8&mc_eid=778e9876e3) [**Support our work**](https://hrf.org/btc?mc_cid=39c1c9b7e8&mc_eid=778e9876e3) [**Visit our website**](https://hrf.org/programs/financial-freedom/) @ a5142938:0ef19da3
2025-04-03 09:55:01### Core Team The Core Team drives the project and validates the content. - [Jean-David Bar](https://njump.me/npub1qr4p7uamcpawv7cr8z9nlhmd60lylukf7lvmtlnpe7r4juwxudzq3hrnll) To start, I'm managing the project solo. Contact me if you'd like to join! ### Content Enrichers Our contributors make this site engaging and interesting.
@ a5142938:0ef19da3
2025-04-03 09:55:01### Core Team The Core Team drives the project and validates the content. - [Jean-David Bar](https://njump.me/npub1qr4p7uamcpawv7cr8z9nlhmd60lylukf7lvmtlnpe7r4juwxudzq3hrnll) To start, I'm managing the project solo. Contact me if you'd like to join! ### Content Enrichers Our contributors make this site engaging and interesting. @ b8af284d:f82c91dd
2025-03-16 16:42:49 Liebe Abonnenten, diejenigen, die diese Publikation schon länger abonniert haben, wissen, dass hier immer wieder über den Ursprung des Corona-Virus in einem Labor in Wuhan berichtet wurde. Seit diese Woche ist es „offiziell“ - [der Bundesnachrichtendienst (BND) hält den Labor-Ursprung für die wahrscheinlichste Variante](https://www.zeit.de/2025/11/coronavirus-ursprung-wuhan-labor-china-bnd). Jetzt kann man sich fragen, warum der BND plötzlich umschwenkt: Will man proaktiv erscheinen, weil man die Wahrheit nicht mehr länger verbergen kann? Oder will man die enttäuschten Bürger zurückgewinnen, die aufgrund der Lügen während der Corona-Zeit zunehmend mit Parteien links und rechts außen sympathisiert haben, weil diese die einzigen waren, die den Irrsinn nicht mitgetragen haben? Auffallend bei den „Recherchen“, die in Wahrheit keine sind, sondern Verlautbarungen des deutschen Geheimdienstes, ist auch das völlige Schweigen über die US-amerikanischen Verwicklungen in das Projekt. [In Wuhan wurde mit amerikanischem Geld geforscht](https://oversight.house.gov/release/breaking-hhs-formally-debars-ecohealth-alliance-dr-peter-daszak-after-covid-select-reveals-pandemic-era-wrongdoing/). Warum der BND diese Tatsache verschweigt, ist Teil der Spekulation. Vermutlich will man Peking alles in die Schuhe schieben, um von den eigenen Versäumnissen abzulenken. In meinem aktuellen Buch “[Der chinesische (Alp-)Traum](https://www.amazon.de/chinesische-Alb-Traum-geopolitische-Herausforderung/dp/3442317509/ref=sr_1_1?__mk_de_DE=%C3%85M%C3%85%C5%BD%C3%95%C3%91\&crid=XQVCLFVRCJJ\&dib=eyJ2IjoiMSJ9.kCJqsUXZO8NZjieNQjGy3Vez7tqktnhQynFOnuZE9249tfkKZvqdJtpIfcDiLMOyxmF7JFpMfvAC881caUEufT--GHlSCcAt_shhnVSbNLp-cle-VXel7soyPwi8xGPm88hSBKPY93BtjFYdOueFUU7qrOir_paRMiQOmCs7YOAUe7ZCKAb6YXxu_hz8N1eZhXbFcvc6p01Uu0vgIibiOHzbXxtH6ECNUaWCaHCYus4.Jzuq9IYvQtPedtE4YORWFtEmxTtrHh5xe8b-B25o5uA\&dib_tag=se\&keywords=Philipp+Mattheis\&qid=1730736669\&sprefix=philipp+mattheis%2Caps%2C111\&sr=8-1)” ist den Ereignissen in Wuhan ein ganzes Kapitel gewidmet. Es hat nichts an Aktualität eingebüßt. Alle Fakten lagen seit Jahren auf dem Tisch für jeden, den es interessiert hat. [Hier gibt es das gesamte Kapitel nachzulesen.](https://blingbling.substack.com/p/was-geschah-in-wuhan)  Auf jeden Fall zeigt dies, wie der Begriff „Verschwörungstheoretiker“ in den vergangenen Jahren zum Kampfbegriff und Waffe gemacht wurde, um Kritiker zu diffamieren, und die öffentliche Meinung ohne harte Zensur zu lenken. Ähnliches kann man aktuell beim Projekt „Digitaler Euro“ beobachten. Vermutlich kann sich kein Bürger der Europäischen Union daran erinnern, bei seiner Wahlentscheidung jemals gefragt worden zu sein, ob er die Einführung eines „digitalen Euros“ gut findet. Wurde er nämlich nicht. Er kommt aber trotzdem. EZB-Präsidentin Christine Lagarde hat das diese Woche nochmals bekräftigt: [Schon im Oktober will man die Testphase beenden](https://x.com/efenigson/status/1898382481184993711) und an der Einführung arbeiten. Nun gehört BlingBling nicht zu denjenigen, die im digitalen Euro „Orwell’sches Teufelswerk“ sehen. Strategische Dummheit trifft es besser. Worum geht es? Sogenannte Central Bank Digital Currencies (CBDC) waren vor einigen Jahren so etwas wie der letzte Schrei in der Zentralbank-Welt. Nachdem Facebook/Meta 2017/18 eine eigene Währung namens Libra auf den Markt bringen wollte, und eine obskure Internet-Währung namens Bitcoin immer mehr Anhänger fand, sahen sich viele Zentralbanken der Welt unter Zugzwang. Was man wollte: eine digitale, direkt von der Zentralbank ausgegebene Währung ohne Bugs, aber mit Features. Mit einer Digital-Währung ließe sich der internationale Zahlungsverkehr direkt und ohne Umweg über den US-Dollar abwickeln. Die Zentralbank bekäme wieder mehr direkten Einfluss auf die Geldschöpfung. Und, wie man aus China lernen konnte, ließen sich digitale Bankkonten auch ganz zum „Nudging von Bürgern“ nutzen. So spekulierten die ersten Verschwörungstheoretiker bald, [ein digitaler Euro ließe sich ja mit einem persönlichen CO2-Konto verknüpfen](https://www.derstandard.de/story/2000124296026/was-eine-digitale-co2-waehrung-fuer-das-klima-bedeuten-wuerde). Wäre letzteres einmal aufgebraucht, könnte der Konto-Inhaber einfach keinen Flug mehr buchen. Auch ließe sich eine expansive Geldpolitik, wie sie bis 2022 praktiziert wurde, ganz einfach mit Negativ-Zinsen umsetzen. Geld würde sich nominal reduzieren, was den Bürger zum Konsum animieren würde. Flüchtigen Kriminellen ließe sich per Knopfdruck das Konto sperren. Der Staat würde also über eine ganze neue Palette an Einflussmöglichkeiten verfügen. Die Aluhüte United warnten vor einem Orwellschen Überwachungsstaat. Vertreter von Regierungen und Firmen, die diesen digitalen Euro bauen sollten, beschwichtigten. Mit Ralf Wintergerst, CEO von Giesecke+Devrient, nach wie vor heißester Anwärter, um das Projekt in der EU umzusetzen, sprach ich in den vergangenen Jahren mehrmals zu dem Thema. [Zuletzt im Dezember 24](https://blingbling.substack.com/p/euro-thrash). Wintergerst versichert stets zwei Dinge: Eine Abschaffung von Bargeld sei nicht geplant. Und nur, wenn die Fluchttore Bargeld, Gold und Bitcoin geschlossen werden, greift die dystopische Version. Und zweitens, so Wintergerst, habe niemand ein chinesisches System im Sinne. Der „digitale Euro“ sei für die Bürger gedacht und das Projekt unterliege demokratischer Kontrolle. Ob er Wintergerst und dem guten im Menschen Glauben schenkt, möge jeder Leser selbst entscheiden. Das Interessantere ist ohnehin, dass der digitale Euro ein strategisch dummes Projekt ist. Dazu muss man wissen, dass eine solche Zentralbankwährung Banken im weitesten Sinne überflüssig macht. Kontos bei Privatbanken werden obsolet, genauso wie Spar-, Fest- und Tagesgeld-Strukturen. Deshalb soll der digitale Euro zunächst auf 3000 Euro pro Bürger beschränkt werden. Das ist also nicht als Maximal-Vermögen gedacht, das dann jedem sozialistischen Einheits-EU-Menschen noch zusteht, sondern dient dazu, das Bankensystem nicht kollabieren zu lassen. Aber wozu überhaupt „ein bisschen digitaler Euro“? In den USA setzt man mittlerweile 100 Prozent auf die private Alternative: Stablecoins wie Tether (USDT) und Circle (USDC) sind nichts anderes als digitale Währungen. Nur sind sie nicht von einer Zentralbank ausgeben, sondern von privaten Anbietern. Tether hat technisch die Möglichkeit, einen Inhaber vom Zahlungsverkehr auszusperren. Nur dürfte es davon kaum Gebrauch machen, will das Unternehmen nicht rasant Kunden an die Konkurrenz verlieren. Da USDT und USDC mit US-Dollar gedeckt sind (oder zumindest sein sollten, *looking at you, Tether!*), stärken sie außerdem die Rolle des US-Dollars als Leitwährung. Und da die USA sich aktuell sehr über Käufer von Staatsanleihen freuen, um die Zinsen zu drücken, und [Tether einer der größten Halter von US-Staatsanleihen is](https://crypto.news/tether-treasury-holdings-boost-us-debt-resilience-2025/)t, wird es den digitalen Dollar bis auf Weiteres nicht geben. Den digitalen Yuan gibt es, aber von einer großen Akzeptanz oder Durchdringung der chinesischen Wirtschaft lässt sich nicht sprechen. Kontrolle kann der chinesische Staat ohnehin über seine omnipräsenten Apps WeChat und Alipay ausüben. Was den internationalen Zahlungsverkehr betrifft, [scheint man aktuell eher auf Gold zu setzen](https://blingbling.substack.com/p/goldfinger). Übrig also bleibt die EU mit einem Projekt, das bereits Milliarden an Entwicklungskosten verschlungen hat. Am Ende bleibt dann ein Mini-Digitaler-Euro in Höhe von 3000 Euro, den niemand wollte, und niemand braucht. Helfen könnte er allerdings beim Projekt “Mobilisierung der Sparguthaben”. Der Ausdruck geht auf Friedrich Merz zurück. Ursula von der Leyen paraphrasierte ihn jüngst:  [Irgendwie müssen die Billionen von Sparguthaben in Militär-Investitionen umgewandelt werden](https://blingbling.substack.com/p/panzer-statt-autos). Das wird am besten funktionieren mit Anleihen, die schlechter verzinst sind als sonst auf dem Markt üblich. Wie bringt man Leute dazu, dann ihr Geld dort zu investieren? Entweder man zwingt sie, oder man bewirbt die Anleihen mit viel Patriotismus und Propaganda. Die Verschwörungstheoretiker unter uns bekommen also bald Futter, wenn die „Spar- und Investitionsunion” vorgestellt wird. Like, wenn Dein Aluhut glüht… *Hinter der Paywall: Wie das Trump-Derangement-Syndrom den Blick auf den Markt trübt. **[Wie es mit Bitcoin, Gold und Aktien weitergeht.](https://blingbling.substack.com/p/gluhende-aluhute)***
@ b8af284d:f82c91dd
2025-03-16 16:42:49 Liebe Abonnenten, diejenigen, die diese Publikation schon länger abonniert haben, wissen, dass hier immer wieder über den Ursprung des Corona-Virus in einem Labor in Wuhan berichtet wurde. Seit diese Woche ist es „offiziell“ - [der Bundesnachrichtendienst (BND) hält den Labor-Ursprung für die wahrscheinlichste Variante](https://www.zeit.de/2025/11/coronavirus-ursprung-wuhan-labor-china-bnd). Jetzt kann man sich fragen, warum der BND plötzlich umschwenkt: Will man proaktiv erscheinen, weil man die Wahrheit nicht mehr länger verbergen kann? Oder will man die enttäuschten Bürger zurückgewinnen, die aufgrund der Lügen während der Corona-Zeit zunehmend mit Parteien links und rechts außen sympathisiert haben, weil diese die einzigen waren, die den Irrsinn nicht mitgetragen haben? Auffallend bei den „Recherchen“, die in Wahrheit keine sind, sondern Verlautbarungen des deutschen Geheimdienstes, ist auch das völlige Schweigen über die US-amerikanischen Verwicklungen in das Projekt. [In Wuhan wurde mit amerikanischem Geld geforscht](https://oversight.house.gov/release/breaking-hhs-formally-debars-ecohealth-alliance-dr-peter-daszak-after-covid-select-reveals-pandemic-era-wrongdoing/). Warum der BND diese Tatsache verschweigt, ist Teil der Spekulation. Vermutlich will man Peking alles in die Schuhe schieben, um von den eigenen Versäumnissen abzulenken. In meinem aktuellen Buch “[Der chinesische (Alp-)Traum](https://www.amazon.de/chinesische-Alb-Traum-geopolitische-Herausforderung/dp/3442317509/ref=sr_1_1?__mk_de_DE=%C3%85M%C3%85%C5%BD%C3%95%C3%91\&crid=XQVCLFVRCJJ\&dib=eyJ2IjoiMSJ9.kCJqsUXZO8NZjieNQjGy3Vez7tqktnhQynFOnuZE9249tfkKZvqdJtpIfcDiLMOyxmF7JFpMfvAC881caUEufT--GHlSCcAt_shhnVSbNLp-cle-VXel7soyPwi8xGPm88hSBKPY93BtjFYdOueFUU7qrOir_paRMiQOmCs7YOAUe7ZCKAb6YXxu_hz8N1eZhXbFcvc6p01Uu0vgIibiOHzbXxtH6ECNUaWCaHCYus4.Jzuq9IYvQtPedtE4YORWFtEmxTtrHh5xe8b-B25o5uA\&dib_tag=se\&keywords=Philipp+Mattheis\&qid=1730736669\&sprefix=philipp+mattheis%2Caps%2C111\&sr=8-1)” ist den Ereignissen in Wuhan ein ganzes Kapitel gewidmet. Es hat nichts an Aktualität eingebüßt. Alle Fakten lagen seit Jahren auf dem Tisch für jeden, den es interessiert hat. [Hier gibt es das gesamte Kapitel nachzulesen.](https://blingbling.substack.com/p/was-geschah-in-wuhan)  Auf jeden Fall zeigt dies, wie der Begriff „Verschwörungstheoretiker“ in den vergangenen Jahren zum Kampfbegriff und Waffe gemacht wurde, um Kritiker zu diffamieren, und die öffentliche Meinung ohne harte Zensur zu lenken. Ähnliches kann man aktuell beim Projekt „Digitaler Euro“ beobachten. Vermutlich kann sich kein Bürger der Europäischen Union daran erinnern, bei seiner Wahlentscheidung jemals gefragt worden zu sein, ob er die Einführung eines „digitalen Euros“ gut findet. Wurde er nämlich nicht. Er kommt aber trotzdem. EZB-Präsidentin Christine Lagarde hat das diese Woche nochmals bekräftigt: [Schon im Oktober will man die Testphase beenden](https://x.com/efenigson/status/1898382481184993711) und an der Einführung arbeiten. Nun gehört BlingBling nicht zu denjenigen, die im digitalen Euro „Orwell’sches Teufelswerk“ sehen. Strategische Dummheit trifft es besser. Worum geht es? Sogenannte Central Bank Digital Currencies (CBDC) waren vor einigen Jahren so etwas wie der letzte Schrei in der Zentralbank-Welt. Nachdem Facebook/Meta 2017/18 eine eigene Währung namens Libra auf den Markt bringen wollte, und eine obskure Internet-Währung namens Bitcoin immer mehr Anhänger fand, sahen sich viele Zentralbanken der Welt unter Zugzwang. Was man wollte: eine digitale, direkt von der Zentralbank ausgegebene Währung ohne Bugs, aber mit Features. Mit einer Digital-Währung ließe sich der internationale Zahlungsverkehr direkt und ohne Umweg über den US-Dollar abwickeln. Die Zentralbank bekäme wieder mehr direkten Einfluss auf die Geldschöpfung. Und, wie man aus China lernen konnte, ließen sich digitale Bankkonten auch ganz zum „Nudging von Bürgern“ nutzen. So spekulierten die ersten Verschwörungstheoretiker bald, [ein digitaler Euro ließe sich ja mit einem persönlichen CO2-Konto verknüpfen](https://www.derstandard.de/story/2000124296026/was-eine-digitale-co2-waehrung-fuer-das-klima-bedeuten-wuerde). Wäre letzteres einmal aufgebraucht, könnte der Konto-Inhaber einfach keinen Flug mehr buchen. Auch ließe sich eine expansive Geldpolitik, wie sie bis 2022 praktiziert wurde, ganz einfach mit Negativ-Zinsen umsetzen. Geld würde sich nominal reduzieren, was den Bürger zum Konsum animieren würde. Flüchtigen Kriminellen ließe sich per Knopfdruck das Konto sperren. Der Staat würde also über eine ganze neue Palette an Einflussmöglichkeiten verfügen. Die Aluhüte United warnten vor einem Orwellschen Überwachungsstaat. Vertreter von Regierungen und Firmen, die diesen digitalen Euro bauen sollten, beschwichtigten. Mit Ralf Wintergerst, CEO von Giesecke+Devrient, nach wie vor heißester Anwärter, um das Projekt in der EU umzusetzen, sprach ich in den vergangenen Jahren mehrmals zu dem Thema. [Zuletzt im Dezember 24](https://blingbling.substack.com/p/euro-thrash). Wintergerst versichert stets zwei Dinge: Eine Abschaffung von Bargeld sei nicht geplant. Und nur, wenn die Fluchttore Bargeld, Gold und Bitcoin geschlossen werden, greift die dystopische Version. Und zweitens, so Wintergerst, habe niemand ein chinesisches System im Sinne. Der „digitale Euro“ sei für die Bürger gedacht und das Projekt unterliege demokratischer Kontrolle. Ob er Wintergerst und dem guten im Menschen Glauben schenkt, möge jeder Leser selbst entscheiden. Das Interessantere ist ohnehin, dass der digitale Euro ein strategisch dummes Projekt ist. Dazu muss man wissen, dass eine solche Zentralbankwährung Banken im weitesten Sinne überflüssig macht. Kontos bei Privatbanken werden obsolet, genauso wie Spar-, Fest- und Tagesgeld-Strukturen. Deshalb soll der digitale Euro zunächst auf 3000 Euro pro Bürger beschränkt werden. Das ist also nicht als Maximal-Vermögen gedacht, das dann jedem sozialistischen Einheits-EU-Menschen noch zusteht, sondern dient dazu, das Bankensystem nicht kollabieren zu lassen. Aber wozu überhaupt „ein bisschen digitaler Euro“? In den USA setzt man mittlerweile 100 Prozent auf die private Alternative: Stablecoins wie Tether (USDT) und Circle (USDC) sind nichts anderes als digitale Währungen. Nur sind sie nicht von einer Zentralbank ausgeben, sondern von privaten Anbietern. Tether hat technisch die Möglichkeit, einen Inhaber vom Zahlungsverkehr auszusperren. Nur dürfte es davon kaum Gebrauch machen, will das Unternehmen nicht rasant Kunden an die Konkurrenz verlieren. Da USDT und USDC mit US-Dollar gedeckt sind (oder zumindest sein sollten, *looking at you, Tether!*), stärken sie außerdem die Rolle des US-Dollars als Leitwährung. Und da die USA sich aktuell sehr über Käufer von Staatsanleihen freuen, um die Zinsen zu drücken, und [Tether einer der größten Halter von US-Staatsanleihen is](https://crypto.news/tether-treasury-holdings-boost-us-debt-resilience-2025/)t, wird es den digitalen Dollar bis auf Weiteres nicht geben. Den digitalen Yuan gibt es, aber von einer großen Akzeptanz oder Durchdringung der chinesischen Wirtschaft lässt sich nicht sprechen. Kontrolle kann der chinesische Staat ohnehin über seine omnipräsenten Apps WeChat und Alipay ausüben. Was den internationalen Zahlungsverkehr betrifft, [scheint man aktuell eher auf Gold zu setzen](https://blingbling.substack.com/p/goldfinger). Übrig also bleibt die EU mit einem Projekt, das bereits Milliarden an Entwicklungskosten verschlungen hat. Am Ende bleibt dann ein Mini-Digitaler-Euro in Höhe von 3000 Euro, den niemand wollte, und niemand braucht. Helfen könnte er allerdings beim Projekt “Mobilisierung der Sparguthaben”. Der Ausdruck geht auf Friedrich Merz zurück. Ursula von der Leyen paraphrasierte ihn jüngst:  [Irgendwie müssen die Billionen von Sparguthaben in Militär-Investitionen umgewandelt werden](https://blingbling.substack.com/p/panzer-statt-autos). Das wird am besten funktionieren mit Anleihen, die schlechter verzinst sind als sonst auf dem Markt üblich. Wie bringt man Leute dazu, dann ihr Geld dort zu investieren? Entweder man zwingt sie, oder man bewirbt die Anleihen mit viel Patriotismus und Propaganda. Die Verschwörungstheoretiker unter uns bekommen also bald Futter, wenn die „Spar- und Investitionsunion” vorgestellt wird. Like, wenn Dein Aluhut glüht… *Hinter der Paywall: Wie das Trump-Derangement-Syndrom den Blick auf den Markt trübt. **[Wie es mit Bitcoin, Gold und Aktien weitergeht.](https://blingbling.substack.com/p/gluhende-aluhute)*** @ 21335073:a244b1ad
2025-03-15 23:00:40I want to see Nostr succeed. If you can think of a way I can help make that happen, I’m open to it. I’d like your suggestions. My schedule’s shifting soon, and I could volunteer a few hours a week to a Nostr project. I won’t have more total time, but how I use it will change. Why help? I care about freedom. Nostr’s one of the most powerful freedom tools I’ve seen in my lifetime. If I believe that, I should act on it. I don’t care about money or sats. I’m not rich, I don’t have extra cash. That doesn’t drive me—freedom does. I’m volunteering, not asking for pay. I’m not here for clout. I’ve had enough spotlight in my life; it doesn’t move me. If I wanted clout, I’d be on Twitter dropping basic takes. Clout’s easy. Freedom’s hard. I’d rather help anonymously. No speaking at events—small meetups are cool for the vibe, but big conferences? Not my thing. I’ll never hit a huge Bitcoin conference. It’s just not my scene. That said, I could be convinced to step up if it’d really boost Nostr—as long as it’s legal and gets results. In this space, I’d watch for social engineering. I watch out for it. I’m not here to make friends, just to help. No shade—you all seem great—but I’ve got a full life and awesome friends irl. I don’t need your crew or to be online cool. Connect anonymously if you want; I’d encourage it. I’m sick of watching other social media alternatives grow while Nostr kinda stalls. I could trash-talk, but I’d rather do something useful. Skills? I’m good at spotting social media problems and finding possible solutions. I won’t overhype myself—that’s weird—but if you’re responding, you probably see something in me. Perhaps you see something that I don’t see in myself. If you need help now or later with Nostr projects, reach out. Nostr only—nothing else. Anonymous contact’s fine. Even just a suggestion on how I can pitch in, no project attached, works too. 💜 Creeps or harassment will get blocked or I’ll nuke my simplex code if it becomes a problem. https://simplex.chat/contact#/?v=2-4&smp=smp%3A%2F%2FSkIkI6EPd2D63F4xFKfHk7I1UGZVNn6k1QWZ5rcyr6w%3D%40smp9.simplex.im%2FbI99B3KuYduH8jDr9ZwyhcSxm2UuR7j0%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAS9C-zPzqW41PKySfPCEizcXb1QCus6AyDkTTjfyMIRM%253D%26srv%3Djssqzccmrcws6bhmn77vgmhfjmhwlyr3u7puw4erkyoosywgl67slqqd.onion
@ 21335073:a244b1ad
2025-03-15 23:00:40I want to see Nostr succeed. If you can think of a way I can help make that happen, I’m open to it. I’d like your suggestions. My schedule’s shifting soon, and I could volunteer a few hours a week to a Nostr project. I won’t have more total time, but how I use it will change. Why help? I care about freedom. Nostr’s one of the most powerful freedom tools I’ve seen in my lifetime. If I believe that, I should act on it. I don’t care about money or sats. I’m not rich, I don’t have extra cash. That doesn’t drive me—freedom does. I’m volunteering, not asking for pay. I’m not here for clout. I’ve had enough spotlight in my life; it doesn’t move me. If I wanted clout, I’d be on Twitter dropping basic takes. Clout’s easy. Freedom’s hard. I’d rather help anonymously. No speaking at events—small meetups are cool for the vibe, but big conferences? Not my thing. I’ll never hit a huge Bitcoin conference. It’s just not my scene. That said, I could be convinced to step up if it’d really boost Nostr—as long as it’s legal and gets results. In this space, I’d watch for social engineering. I watch out for it. I’m not here to make friends, just to help. No shade—you all seem great—but I’ve got a full life and awesome friends irl. I don’t need your crew or to be online cool. Connect anonymously if you want; I’d encourage it. I’m sick of watching other social media alternatives grow while Nostr kinda stalls. I could trash-talk, but I’d rather do something useful. Skills? I’m good at spotting social media problems and finding possible solutions. I won’t overhype myself—that’s weird—but if you’re responding, you probably see something in me. Perhaps you see something that I don’t see in myself. If you need help now or later with Nostr projects, reach out. Nostr only—nothing else. Anonymous contact’s fine. Even just a suggestion on how I can pitch in, no project attached, works too. 💜 Creeps or harassment will get blocked or I’ll nuke my simplex code if it becomes a problem. https://simplex.chat/contact#/?v=2-4&smp=smp%3A%2F%2FSkIkI6EPd2D63F4xFKfHk7I1UGZVNn6k1QWZ5rcyr6w%3D%40smp9.simplex.im%2FbI99B3KuYduH8jDr9ZwyhcSxm2UuR7j0%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAS9C-zPzqW41PKySfPCEizcXb1QCus6AyDkTTjfyMIRM%253D%26srv%3Djssqzccmrcws6bhmn77vgmhfjmhwlyr3u7puw4erkyoosywgl67slqqd.onion @ d5c3d063:4d1159b3
2025-04-03 04:09:56### ทรัมป์ ขึ้นภาษีนำเข้า สิ่งที่คุณเห็น…กับสิ่งที่คุณมองไม่เห็น คุณ #เห็น แค่ฝั่งที่ดูดีในข่าวภาคค่ำ แต่คุณ #ไม่เห็น – คนทั้งประเทศ ต้องจ่ายของแพงขึ้น – ธุรกิจเล็ก ๆ ที่พึ่งการนำเข้า…ถูกบีบให้ตาย – ผู้บริโภคต้องเสียเงินมากขึ้น โดยไม่มีทางเลือก รัฐอ้างว่า *"ปกป้องประเทศ"* แต่จริง ๆ แล้วเขาแค่ โยนภาระให้คนส่วนใหญ่ เพื่ออุ้มผลประโยชน์บางกลุ่ม เหมือนที่ Bastiat เรียกว่า *“การปล้นที่ถูกกฎหมาย”* Hazlitt ขยายต่อใน Economics in One Lesson ว่า > เศรษฐศาสตร์ที่ดี ต้องมองให้พ้นจากผลเฉพาะหน้า > และมองให้เห็นผลกระทบต่อทุกคน ไม่ใช่แค่บางกลุ่ม เงินเฟ้อ คือการขโมยแบบเงียบ ๆ ภาษีศุลกากร คือการปล้นอย่างเปิดเผย วันนี้ #EIOL น่าจะถึงมือเพื่อนๆ หลายคนแล้ว เล่มนี้ไม่ต้องอ่านทีละบทก็ได้ ลองเปิดไปบทที่ 11 เลยแล้วจะเจอ**ค้อนปอน**สำหรับทุบมายาคดีทางเศรษฐกิจที่รัฐใช้กับเรามาทั้งชีวิต อ่าน #เศรษฐศาสตร์เล่มเดียวจบ แล้วคุณอาจไม่มีวันมอง “นโยบายเพื่อประชาชน” ได้เหมือนเดิมอีก เพราะบางที...สิ่งที่คุณไม่เคยเห็น อาจเป็นสิ่งที่คุณควรรู้(เห็น)ให้เร็วที่สุด #Siamstr
@ d5c3d063:4d1159b3
2025-04-03 04:09:56### ทรัมป์ ขึ้นภาษีนำเข้า สิ่งที่คุณเห็น…กับสิ่งที่คุณมองไม่เห็น คุณ #เห็น แค่ฝั่งที่ดูดีในข่าวภาคค่ำ แต่คุณ #ไม่เห็น – คนทั้งประเทศ ต้องจ่ายของแพงขึ้น – ธุรกิจเล็ก ๆ ที่พึ่งการนำเข้า…ถูกบีบให้ตาย – ผู้บริโภคต้องเสียเงินมากขึ้น โดยไม่มีทางเลือก รัฐอ้างว่า *"ปกป้องประเทศ"* แต่จริง ๆ แล้วเขาแค่ โยนภาระให้คนส่วนใหญ่ เพื่ออุ้มผลประโยชน์บางกลุ่ม เหมือนที่ Bastiat เรียกว่า *“การปล้นที่ถูกกฎหมาย”* Hazlitt ขยายต่อใน Economics in One Lesson ว่า > เศรษฐศาสตร์ที่ดี ต้องมองให้พ้นจากผลเฉพาะหน้า > และมองให้เห็นผลกระทบต่อทุกคน ไม่ใช่แค่บางกลุ่ม เงินเฟ้อ คือการขโมยแบบเงียบ ๆ ภาษีศุลกากร คือการปล้นอย่างเปิดเผย วันนี้ #EIOL น่าจะถึงมือเพื่อนๆ หลายคนแล้ว เล่มนี้ไม่ต้องอ่านทีละบทก็ได้ ลองเปิดไปบทที่ 11 เลยแล้วจะเจอ**ค้อนปอน**สำหรับทุบมายาคดีทางเศรษฐกิจที่รัฐใช้กับเรามาทั้งชีวิต อ่าน #เศรษฐศาสตร์เล่มเดียวจบ แล้วคุณอาจไม่มีวันมอง “นโยบายเพื่อประชาชน” ได้เหมือนเดิมอีก เพราะบางที...สิ่งที่คุณไม่เคยเห็น อาจเป็นสิ่งที่คุณควรรู้(เห็น)ให้เร็วที่สุด #Siamstr @ a95c6243:d345522c
2025-03-15 10:56:08*Was nützt die schönste Schuldenbremse, wenn der Russe vor der Tür steht?* *\ Wir können uns verteidigen lernen oder alle Russisch lernen.* *\ Jens Spahn*   **In der Politik ist buchstäblich keine Idee zu riskant, kein Mittel zu schäbig und keine Lüge zu dreist,** als dass sie nicht benutzt würden. Aber der Clou ist, dass diese Masche immer noch funktioniert, wenn nicht sogar immer besser. Ist das alles wirklich so schwer zu durchschauen? Mir fehlen langsam die Worte. **Aktuell werden sowohl in der Europäischen Union als auch in Deutschland** riesige Milliardenpakete für die [Aufrüstung](https://transition-news.org/eu-halt-weiter-kurs-auf-krieg-hunderte-milliarden-fur-aufrustung-beschlossen) – also für die Rüstungsindustrie – geschnürt. Die EU will 800 Milliarden Euro locker machen, in Deutschland sollen es 500 Milliarden «Sondervermögen» sein. Verteidigung nennen das unsere «Führer», innerhalb der Union und auch an «unserer Ostflanke», der Ukraine. **Das nötige Feindbild konnte inzwischen signifikant erweitert werden.** Schuld an allem und zudem gefährlich ist nicht mehr nur Putin, sondern jetzt auch Trump. Europa müsse sich sowohl gegen Russland als auch gegen die USA schützen und rüsten, wird uns eingetrichtert. **Und während durch Diplomatie genau dieser beiden Staaten** gerade endlich mal Bewegung in die Bemühungen um einen Frieden oder wenigstens einen Waffenstillstand in der Ukraine kommt, rasselt man im moralisch überlegenen Zeigefinger-Europa so richtig mit dem Säbel. **Begleitet und gestützt wird der ganze Prozess** – wie sollte es anders sein – von den «Qualitätsmedien». Dass Russland einen Angriff auf «Europa» plant, weiß nicht nur der deutsche Verteidigungsminister (und mit Abstand beliebteste Politiker) Pistorius, sondern dank ihnen auch jedes Kind. Uns bleiben nur noch wenige Jahre. Zum Glück bereitet sich die Bundeswehr schon sehr konkret [auf einen Krieg](https://archive.is/VE8ZM) vor. **Die** ***FAZ*** **und Corona-Gesundheitsminister Spahn markieren einen traurigen Höhepunkt.** Hier haben sich «politische und publizistische Verantwortungslosigkeit propagandistisch gegenseitig befruchtet», wie es bei den *NachDenkSeiten* [heißt](https://www.nachdenkseiten.de/?p=130064). Die Aussage Spahns in dem Interview, «der Russe steht vor der Tür», ist das eine. Die Zeitung verschärfte die Sache jedoch, indem sie das Zitat explizit in den [Titel](https://archive.is/QJdID) übernahm, der in einer [ersten Version](https://archive.is/fNuGA) scheinbar zu harmlos war. **Eine große Mehrheit der deutschen Bevölkerung findet Aufrüstung und mehr Schulden toll,** wie *[ARD](https://archive.is/M3DSk)* und *[ZDF](https://archive.is/ggvJB)* sehr passend ermittelt haben wollen. Ähnliches gelte für eine noch stärkere militärische Unterstützung der Ukraine. Etwas skeptischer seien die Befragten bezüglich der Entsendung von Bundeswehrsoldaten dorthin, aber immerhin etwa fifty-fifty. **Eigentlich ist jedoch die Meinung der Menschen in «unseren Demokratien» irrelevant.** Sowohl in der Europäischen Union als auch in Deutschland sind die «Eliten» offenbar der Ansicht, der Souverän habe in Fragen von Krieg und Frieden sowie von aberwitzigen astronomischen Schulden kein Wörtchen mitzureden. Frau von der Leyen möchte über 150 Milliarden aus dem Gesamtpaket unter Verwendung von Artikel 122 des EU-Vertrags ohne das Europäische Parlament entscheiden – wenn auch nicht völlig [kritiklos](https://www.berliner-zeitung.de/politik-gesellschaft/geopolitik/aufruestung-widerstand-gegen-eu-plaene-waechst-kommission-uebertreibt-russische-gefahr-li.2306863). **In Deutschland wollen CDU/CSU und SPD zur Aufweichung der «Schuldenbremse»** mehrere Änderungen des Grundgesetzes durch das abgewählte Parlament peitschen. Dieser Versuch, mit dem alten [Bundestag](https://www.bundestag.de/dokumente/textarchiv/2025/kw11-de-sondersitzung-1056228) eine Zweidrittelmehrheit zu erzielen, die im neuen nicht mehr gegeben wäre, ist mindestens verfassungsrechtlich umstritten. **Das Manöver scheint aber zu funktionieren.** Heute haben die Grünen [zugestimmt](https://www.reuters.com/world/europe/germany-faces-debt-deal-cliffhanger-merz-strives-greens-backing-2025-03-14/), nachdem Kanzlerkandidat Merz läppische 100 Milliarden für «irgendwas mit Klima» zugesichert hatte. Die Abstimmung im Plenum soll am kommenden Dienstag erfolgen – nur eine Woche, bevor sich der neu gewählte Bundestag konstituieren wird. **Interessant sind die Argumente, die BlackRocker Merz für seine Attacke** auf Grundgesetz und Demokratie ins Feld führt. Abgesehen von der angeblichen Eile, «unsere Verteidigungsfähigkeit deutlich zu erhöhen» (ausgelöst unter anderem durch «die Münchner Sicherheitskonferenz und die Ereignisse im Weißen Haus»), ließ uns der CDU-Chef wissen, dass Deutschland einfach auf die internationale Bühne zurück müsse. Merz [schwadronierte](https://x.com/CDU/status/1900168761686044894) gefährlich mehrdeutig: > «Die ganze Welt schaut in diesen Tagen und Wochen auf Deutschland. Wir haben in der Europäischen Union und auf der Welt eine Aufgabe, die weit über die Grenzen unseres eigenen Landes hinausgeht.»      *\[Titelbild:* *[Tag des Sieges](https://pixabay.com/de/photos/parade-tag-des-sieges-samara-182508/)]* *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/propaganda-wahnsinn-und-demokratur)*** erschienen.
@ a95c6243:d345522c
2025-03-15 10:56:08*Was nützt die schönste Schuldenbremse, wenn der Russe vor der Tür steht?* *\ Wir können uns verteidigen lernen oder alle Russisch lernen.* *\ Jens Spahn*   **In der Politik ist buchstäblich keine Idee zu riskant, kein Mittel zu schäbig und keine Lüge zu dreist,** als dass sie nicht benutzt würden. Aber der Clou ist, dass diese Masche immer noch funktioniert, wenn nicht sogar immer besser. Ist das alles wirklich so schwer zu durchschauen? Mir fehlen langsam die Worte. **Aktuell werden sowohl in der Europäischen Union als auch in Deutschland** riesige Milliardenpakete für die [Aufrüstung](https://transition-news.org/eu-halt-weiter-kurs-auf-krieg-hunderte-milliarden-fur-aufrustung-beschlossen) – also für die Rüstungsindustrie – geschnürt. Die EU will 800 Milliarden Euro locker machen, in Deutschland sollen es 500 Milliarden «Sondervermögen» sein. Verteidigung nennen das unsere «Führer», innerhalb der Union und auch an «unserer Ostflanke», der Ukraine. **Das nötige Feindbild konnte inzwischen signifikant erweitert werden.** Schuld an allem und zudem gefährlich ist nicht mehr nur Putin, sondern jetzt auch Trump. Europa müsse sich sowohl gegen Russland als auch gegen die USA schützen und rüsten, wird uns eingetrichtert. **Und während durch Diplomatie genau dieser beiden Staaten** gerade endlich mal Bewegung in die Bemühungen um einen Frieden oder wenigstens einen Waffenstillstand in der Ukraine kommt, rasselt man im moralisch überlegenen Zeigefinger-Europa so richtig mit dem Säbel. **Begleitet und gestützt wird der ganze Prozess** – wie sollte es anders sein – von den «Qualitätsmedien». Dass Russland einen Angriff auf «Europa» plant, weiß nicht nur der deutsche Verteidigungsminister (und mit Abstand beliebteste Politiker) Pistorius, sondern dank ihnen auch jedes Kind. Uns bleiben nur noch wenige Jahre. Zum Glück bereitet sich die Bundeswehr schon sehr konkret [auf einen Krieg](https://archive.is/VE8ZM) vor. **Die** ***FAZ*** **und Corona-Gesundheitsminister Spahn markieren einen traurigen Höhepunkt.** Hier haben sich «politische und publizistische Verantwortungslosigkeit propagandistisch gegenseitig befruchtet», wie es bei den *NachDenkSeiten* [heißt](https://www.nachdenkseiten.de/?p=130064). Die Aussage Spahns in dem Interview, «der Russe steht vor der Tür», ist das eine. Die Zeitung verschärfte die Sache jedoch, indem sie das Zitat explizit in den [Titel](https://archive.is/QJdID) übernahm, der in einer [ersten Version](https://archive.is/fNuGA) scheinbar zu harmlos war. **Eine große Mehrheit der deutschen Bevölkerung findet Aufrüstung und mehr Schulden toll,** wie *[ARD](https://archive.is/M3DSk)* und *[ZDF](https://archive.is/ggvJB)* sehr passend ermittelt haben wollen. Ähnliches gelte für eine noch stärkere militärische Unterstützung der Ukraine. Etwas skeptischer seien die Befragten bezüglich der Entsendung von Bundeswehrsoldaten dorthin, aber immerhin etwa fifty-fifty. **Eigentlich ist jedoch die Meinung der Menschen in «unseren Demokratien» irrelevant.** Sowohl in der Europäischen Union als auch in Deutschland sind die «Eliten» offenbar der Ansicht, der Souverän habe in Fragen von Krieg und Frieden sowie von aberwitzigen astronomischen Schulden kein Wörtchen mitzureden. Frau von der Leyen möchte über 150 Milliarden aus dem Gesamtpaket unter Verwendung von Artikel 122 des EU-Vertrags ohne das Europäische Parlament entscheiden – wenn auch nicht völlig [kritiklos](https://www.berliner-zeitung.de/politik-gesellschaft/geopolitik/aufruestung-widerstand-gegen-eu-plaene-waechst-kommission-uebertreibt-russische-gefahr-li.2306863). **In Deutschland wollen CDU/CSU und SPD zur Aufweichung der «Schuldenbremse»** mehrere Änderungen des Grundgesetzes durch das abgewählte Parlament peitschen. Dieser Versuch, mit dem alten [Bundestag](https://www.bundestag.de/dokumente/textarchiv/2025/kw11-de-sondersitzung-1056228) eine Zweidrittelmehrheit zu erzielen, die im neuen nicht mehr gegeben wäre, ist mindestens verfassungsrechtlich umstritten. **Das Manöver scheint aber zu funktionieren.** Heute haben die Grünen [zugestimmt](https://www.reuters.com/world/europe/germany-faces-debt-deal-cliffhanger-merz-strives-greens-backing-2025-03-14/), nachdem Kanzlerkandidat Merz läppische 100 Milliarden für «irgendwas mit Klima» zugesichert hatte. Die Abstimmung im Plenum soll am kommenden Dienstag erfolgen – nur eine Woche, bevor sich der neu gewählte Bundestag konstituieren wird. **Interessant sind die Argumente, die BlackRocker Merz für seine Attacke** auf Grundgesetz und Demokratie ins Feld führt. Abgesehen von der angeblichen Eile, «unsere Verteidigungsfähigkeit deutlich zu erhöhen» (ausgelöst unter anderem durch «die Münchner Sicherheitskonferenz und die Ereignisse im Weißen Haus»), ließ uns der CDU-Chef wissen, dass Deutschland einfach auf die internationale Bühne zurück müsse. Merz [schwadronierte](https://x.com/CDU/status/1900168761686044894) gefährlich mehrdeutig: > «Die ganze Welt schaut in diesen Tagen und Wochen auf Deutschland. Wir haben in der Europäischen Union und auf der Welt eine Aufgabe, die weit über die Grenzen unseres eigenen Landes hinausgeht.»      *\[Titelbild:* *[Tag des Sieges](https://pixabay.com/de/photos/parade-tag-des-sieges-samara-182508/)]* *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/propaganda-wahnsinn-und-demokratur)*** erschienen. @ 3c7dc2c5:805642a8
2025-04-02 21:15:55## 🧠Quote(s) of the week: CBDC the digital euro - a centralized solution in search of a problem. While the ECB may see it as a way to 'modernize' finance, true innovation comes from empowering individuals, not consolidating control. CBDCs are just surveillance tools disguised as innovation. Bitcoin is the only true digital money—decentralized, scarce, and free. Stack sats, not CBDCs. ## 🧡Bitcoin news🧡 2025 https://i.ibb.co/vx988kT1/Gn-Ix-Dp-YWs-AASkiw.jpg On the 24th of March: ➡️The Pakistan central bank is exploring mining Bitcoin with excess electricity. ➡️'MicroStrategy just added another 7,000 Bitcoin to their treasury. They're now holding over 506,000 BTC ($44 billion). Look at the corporate Bitcoin ownership breakdown: - MicroStrategy: 506,000+ BTC - Marathon: ~46,000 BTC (10x smaller) - Riot: ~19,000 BTC (26x smaller) That acquisition curve has gone parabolic since Q4 2024. Strategy's buying pace now rivals what we're seeing from the Bitcoin ETFs, a single public company absorbing supply at an institutional scale. Clear institutional conviction signal here.' -Ecoinometrics ➡️SQUARE CEO JACK DORSEY: "Bitcoin will make the current financial system feel as irrelevant as the fax machine." On the 25th of March: ➡️'BITCOIN HASH-RIBBON FLASHES BUY SIGNAL - This is one of the most reliable "buy" indicators. - Significant price gains have followed 7 out of the last 7 times this indicator was triggered.' -Bitcoin Archive (foto) Bitcoin is always a buy. Just DCA. ➡️GameStop includes Bitcoin as a treasury reserve asset in its investment policy update. GameStop has $4.6 billion in cash to invest. ➡️Strategy’s sale of 8.5 million STRF shares closes today, unlocking $711 million in new capital to buy more Bitcoin. ➡️BBC News reports from a remote community of 15,000 people in the far north-western tip of Zambia relying on hydroelectric power, “The bitcoin mine now accounts for around 30% of the plant's revenue allowing them to keep the prices down for the local town” - Source: https://www.bbc.com/news/articles/cly4xe373p4o Gridless is doing a splendid job in Africa and showing through proof-of-work that if you aren't mining Bitcoin, you are wasting energy. It's time for such communities to appear more around the world. Daniel Batten: 'They couldn't resist zooming out and implying this is an outlier (it isn't, the majority of off-grid bitcoin mining operations are renewably powered). In doing so BBC made three factually incorrect statements at the end about Bitcoin mining straining grids (multiple peer-reviewed studies show the opposite is true), and "Greenidge gas power plant in New York which was renovated to mine bitcoin" (it didn't, it re-opened to supply power back to the grid), and stating that Bitcoin mining needs artificial govt incentives or rules to do the right thing (It doesn't, it's become 56.7% sustainably powered without any govt incentives) But let's shine the light on the positive - it has far fewer factually incorrect statements than previous reporting, and it is a step in the right direction in its gradual journey towards objective Bitcoin reporting for a media company that has until now only published negative news stories on Bitcoin.' ➡️Femke Halsema, Mayor of Amsterdam, wants a national ban on Bitcoin payments: "It undermines our civilization". I rather believe the opposite. Under Femke Halsema - Amsterdam - The number of civil servants increased by 50% (14K -> 20K) - Debt increased by 150% (4 billion -> approx. 10 billion) Despite high revenues, Amsterdam has to borrow nearly half a billion euros every year. Local taxes continue to rise, whether it's water authority taxes or property taxes (OZB). But, above all, you should be concerned about those 0.3% criminal Bitcoin / Crypto transactions (worldwide). The audacity. Even if the Netherlands were to legally ban Bitcoin payments, users could easily continue trading through foreign exchanges or peer-to-peer platforms. A ban might actually push Bitcoin usage further underground, making oversight of suspicious transactions worse rather than better. ➡️Mt. Gox moves 11.501 Bitcoin ($1B) for creditor repayment. ➡️BlackRock launched a European Bitcoin ETP today - Bloomberg ➡️North Carolina introduces a bill to invest 5% of state funds into Bitcoin. On the 26th of March: ➡️NYDIG just became a big Bitcoin miner. Crusoe, the first to scale Bitcoin mining off flared gas (~200MW worth, across 425 data centers) has sold its entire Bitcoin mining business to NYDIG. ➡️Metaplanet has raised ~$55.2m (¥8.28b) of equity capital through three trading days this week while partially deleveraging with the redemption of $23.3m (¥3.5b) of 0% ordinary bonds. ➡️GameStop can service a loan of up to $100 BILLION for 4.6 years with its existing $4.6b cash balance at 1% interest. That's twice the amount of Bitcoin Michael Saylor's Strategy currently holds. ➡️New feature by Protonmail enables their 100 million users to send Bitcoin using their email addresses. ➡️The Blockchain Group confirms the acquisition of 580 BTC for ~€47.3 million, the holding of a total of 620 BTC, and a BTC Yield of 709.8% YTD. → Confirmation of the acquisition of 580 BTC for ~€47.3 million at ~€81,550 per bitcoin → Total group holdings of 620 BTC for ~€50.5 million at ~€81,480 per bitcoin → Adoption of ‘BTC Yield’, ‘BTC Gain’, and ‘BTC € Gain’ as KPIs, following the steps of Strategy and Metaplanet This is a major step in our Bitcoin Treasury Company strategy focused on increasing Bitcoin per share over time. Source: https://t.co/QDj61ZDe6O The Blockchain Group is Europe's First Bitcoin Treasury Company! On the 27th of March: ➡️'Bitcoin's 4-year Compound Annual Growth Rate (CAGR) is at historic lows.' -Pierre Rochard ➡️Daniel Batten: Yet another paper on Bitcoin and energy TL:DR: "The opportunities offered by bitcoin mining in reduction of the greenhouse gas emissions and renewable energy transition are greater than generally assumed" The journal has a (high) impact factor of 7.1." Source: https://t.co/W3gytMgcpC ➡️A home miner with only 4 machines mined block 888737. https://i.ibb.co/7xm91R4t/Gn-Ef-H9y-Ws-AA4jkn.jpg Bitcoin proves anyone can participate and earn—true freedom! ➡️'Short-Term Holders have increased their Bitcoin holdings by 201,743 BTC to 5,750,076 BTC since January, remaining below previous cycle peaks. 200K BTC are currently held at an unrealized loss, representing about $17B.' -Bitcoin News ➡️Bitcoin mining hardware manufacturer Canaan signs a three-year colocation agreement with Mawson Infrastructure Group's Mawson Hosting LLC for facilities in Midland, Pennsylvania, and Edna, Texas. Most of the 4.7 EH/s hashrate is expected to be operational by Q2 2025. On the 28th of March: ➡️If Saylor had bet on ETH instead of Bitcoin, Strategy would be down $9 billion, instead of up $9 billion like they are today. ETHBTC made fresh lows 0.02210. Ether is down 74% against Bitcoin since switching from proof of work to proof of stake. Yikes! ➡️Representative introduces a strategic Bitcoin reserve bill in South Carolina. ➡️A Russian company built a Bitcoin mine in the Arctic. Set in the frozen city of Norilsk, the facility taps into cheap excess energy from one of the world's most isolated industrial hubs. ➡️The price of bitcoin has nearly followed the same phases of volatility for 15 years, according to Fidelity. https://i.ibb.co/LdQfrqG0/Gn-Ig-Skd-XMAAi-L3r.jpg another great chart: https://i.ibb.co/G4WmDjhd/Gn-JED1q-Xk-AAq-Kqk.jpg On the 29th of March: ➡️Public miner MARA with a $2B common stock offering to buy more Bitcoin. https://i.ibb.co/PZZxXJ37/Gn-Kj-Vqza-EAEUG-V.png ➡️California has officially included Bitcoin Rights protections in its newly proposed digital asset bill. If passed, it will guarantee the right to self-custody for nearly 40M residents and prohibit discrimination against Bitcoin use. ➡️The number of addresses with more than one Bitcoin has fallen below 1 million, standing today at 995,207. On the 31st of March: ➡️Larry Fink, Founder/CEO of BlackRock in his annual letter to shareholders: “If the U.S. doesn't get its debt under control, if deficits keep ballooning, America risks losing that position to digital assets like Bitcoin." https://www.blackrock.com/corporate/literature/presentation/larry-fink-annual-chairmans-letter.pdf ➡️Strategy has acquired 22,048 BTC for ~$1.92 billion at ~$86,969 per bitcoin and has achieved a BTC Yield of 11.0% YTD 2025. As of 3/30/2025, Strategy holds 528,185 $BTC acquired for ~$35.63 billion at ~$67,458 per bitcoin. ➡️ The Bitcoin Policy Institute releases a framework for the USA to buy $200 billion worth of #Bitcoin using Bit Bonds. ➡️Is Indonesia the next Bitcoin Country? Bitcoin Indonesia mapped out the entire Bitcoin ecosystem. A new map shows Bitcoin adoption EXPLODING across the Southeast Asian island nation of Indonesia. Check out all the communities, projects, and businesses embracing Bitcoin. The revolution is happening. https://i.ibb.co/cXL8mC0x/Gnbdg-Lub-IAAdwcb.jpg On the 1st of April: ➡️'Over 73,353 BTC were bought by corporations in Q1 2025. Only 40,500 BTC new Bitcoin was mined, but still no supply shock, for now... Which company do you want to see adopt BTC next?' Here is the breakdown by Alec: https://x.com/Alec_Bitcoin/status/1907062290345783723 ➡️After skeptics questioned Tether’s Bitcoin holdings, CEO Paolo Ardoino fired back, sharing the company’s BTC address with a confirmed balance of 92,646 BTC. On the same day Tether bought 8,888 Bitcoin worth $735 million as per on-chain data. They now hold over 100,000 BTC. ➡️'GameStop just raised $1.48B. They are expected to use that and possibly more of the now $6B+ on their balance sheet to buy Bitcoin. A master class on how to pivot from meme stock to capitalize on volatility in the ultimate store of value.' -James Lavish ➡️Texas' state house Democrats have proposed a bill that would authorize up to $250 million in state investment in Bitcoin and up to $10 million for each municipality and county. ➡️Human Rights Foundation donates 10 Bitcoins worth $830,000 to over 20 projects worldwide. Alex Gladstein: '1 billion sats gifted carefully to a variety of stellar organizations and individuals to support BTC privacy, decentralization, education, and p2p use, aimed at folks working under authoritarianism.' ## 💸Traditional Finance / Macro: On the 29th of March 👉🏽'From Wednesday to Friday, the S&P 500 lost -$100 billion PER trading hour for a total of -$2 TRILLION. Then, after the market closed on Friday, S&P 500 futures erased ANOTHER -$120 billion in minutes.' -TKL ## 🏦Banks: 👉🏽 no news ## 🌎Macro/Geopolitics: On the 24th of March: 👉🏽Financelot: 'This is fascinating. The Dow Jones to Gold Ratio is about to cross a level only seen 4 times in history. Every time it crossed this level it marked the beginning of an 18-month recession/depression. 1929, 1973, 2008 & 2025' I don't think we won't see a depression. History rhymes but doesn't always mean it will repeat, although human behavior stays the same. For now, it means the market is overvalued, gold is undervalued, or both. 👉🏽US household wealth is falling: US household equity wealth is set to drop a whopping -$3 trillion this quarter, the most since the 2022 bear market, according to BofA estimates. By comparison, equity holdings rose +$9 trillion in 2024 to a record $56 trillion. In other words, one-third of last year's gains have likely been wiped out due to the recent market pullback. Furthermore, the top 10% of the wealthiest Americans own 87% of US stocks. This, in turn, may negatively impact consumer spending as the top 10% reflect a record 50% of all consumer expenditures. Consumer spending is set to slow in Q2 2025.' -TKL 👉🏽Demolition of the Boiler House at Moorburg Power Plant in Hamburg. Germany is preparing for combat by dynamiting its own modern energy infrastructure down. This was the most advanced coal plant. 6 years old and cost three billion euros. The Netherlands is following a similar policy—they poured concrete into their gas drilling pipes. BowTiedMara on Twitter: "In 2022, a girl tied herself to the net at Roland Garros in protest, and she wore a T-shirt that said: "We have 1,028 days left." Today, the 27th of March, marks those 1,028 days, and nothing happened. Climate doomers are like Aztecs who think the sun stops unless they cut out some organs." 👉🏽Starting in April, the 66,000 employees of the European institutions will receive their seventh salary increase in just three years! Normally, this happens at most once per year. The President of the European Commission, Ursula von der Leyen, will see the largest increase, with her monthly salary rising to €34,800—an increase of €2,700—according to a report by the German newspaper Bild-Zeitung today. For the Dutch readers: https://ejbron.wordpress.com/2025/03/24/eu-bureaucraten-en-politici-krijgen-de-7e-salarisverhoging-sinds-2022/ They are compensating for the inflation they impose on the EU. Lucky them Fair to say we need a DOGE in Europe. On the 25th of March: 👉🏽Dutch minister announces a huge increase in excise duties of 25.8 cents on gasoline. On top of that, the price of gasoline will rise by an additional 7 cents due to the blending requirement and 11 cents due to the ETS-2 regulation. In a free market, prices would not be announced by politicians but would emerge through supply and demand. How I love the EU....although it is a bit more nuanced. The temporary discount is ending. Unless the parliament decides to extend it, the price of gasoline will rise. The Dutch government should simply spend less and abolish all taxes, excise duties, and levies on food, fuel, and energy. Never gonna happen though. 👉🏽"Shell will be thoroughly reviewing all its chemical divisions worldwide in the coming period. In Europe, this could lead to the partial or complete closure of various chemical branches." As mentioned multiple times last month, major industrial companies sounded the alarm. They warned that high energy costs in the Netherlands put their future at risk. Additionally, sustainability efforts and unclear government policies are challenging the sector. Frans Everts, President-Director of Shell Netherlands, warned that the entire industry could collapse. The Green Deal is moving full speed ahead—soon everyone will be relying on food banks… For the Dutch readers: https://nos.nl/artikel/2561036-shell-kijkt-naar-gedeeltelijke-sluiting-van-chemie-onderdelen On the 26th of March: 👉🏽EU countries will start using a digital driver’s license from 2030. This is the result of negotiations between the European Parliament and EU member states. In the Netherlands, the digital license will be valid for ten years and will be accessible via an app. And we all know which app that will be! The EU Digital Wallet must be filled, after all. Not just your driver’s license—everything will soon be linked to your digital identity. It’s all right there on the EU’s website, and it’s been planned for a long time. The COVID pass was already part of the rollout. The fact that they present these as separate steps just shows that they know people wouldn’t accept it if they were fully aware of what’s happening. On the 27th of March: 👉🏽Gold surpasses $3,100 for the first time in history. TKL: 'Gold prices have hit 50 all-time highs over the last 12 months, its best streak in 12 years. This is also the 3rd-longest streak on record after a historic run during the late 1970s. The 1970s came with a period of double-digit inflation, stagnant economic growth, and a high unemployment rate, also known as stagflation. As a result, gold prices recorded 4 consecutive yearly gains.' On the 31st of March for the first time, gold blasted through $100,000/kilogram. This time, gold prices have rallied 39% over the last 12 months, are up 16% year-to-date, and are on track for the 3rd annual positive performance.' 👉🏽NATO Secretary General Rutte insists there will be no normalization of relations with Russia for decades to come. On March 14, 2025, Bloomberg, Rutte says: "Once the war is over, relations with Russia will gradually be restored." On March 26, 2025, Rutte said: "There will be no normalization of relations with Russia for decades, even after the war is over." That is the Mark I know! "Mark Rutte, the long-serving Dutch Prime Minister, earned the nickname “Pinokkio” (Dutch for Pinocchio) primarily because of perceived dishonesty or evasiveness in political debates and scandals. While some still view Rutte as a pragmatic and stable leader, the nickname “Pinokkio” reflects a broader public sentiment of distrust, especially among those who felt betrayed by his communication style or decisions.” On the 28th of March: 👉🏽US consumers now expect 5.0%(!) inflation in the next twelve months. Inflation expectations have DOUBLED in just four months. That's huge! Long-term US inflation expectations have officially SURGED to 4.1%, the highest level since 1993. Tariff front-running has led to a $300+ BILLION trade deficit in 2 months, and consumer sentiment has collapsed. Atlanta Fed is now projecting that Q1 GDP will be -2.8%… a large contraction. It’s negative even “gold adjusted” 4 weeks ago it was +2.3% 8 weeks ago it was +3.9% Yikes! 👉🏽The State Department is officially shutting down USAID and has formally notified Congress of its closure. The remaining 900 employees are set to be terminated. 👉🏽Argentina’s Economy Grows 6.5% in January. Argentina’s Poverty Rate Drops from 52.9% to 38.1% in 15 Months Under Javier Milei 👉🏽Fix the money, fix the world: DOGE “There is actually really only ONE BANK ACCOUNT that's used to disperse ALL monies that go out of the federal government” “It's a big one — A couple of weeks ago it had $800 billion in it, it's the treasury general account” “We're serving 580+ agencies. And up until very recently, effectively they could say, make the payment and Treasury just sent it out as fast as possible. NO VERIFICATION” “There's a $500 billion of fraud every year. There are hundreds of billion dollars of improper payments and we can't pass an audit. The consolidated financial report is produced by treasury and we cannot pass an audit” Extremely fascinating interview by Bret Baier with the highly talented and competent DOGE team, which is rigorously streamlining the U.S. government bureaucracy. This work can only be done by competent (and motivated) outsiders with experience. Also urgently needed in the Netherlands, and in Europe. On the 29th of March: 👉🏽'US debt has been "limited" by the $36.104 trillion debt ceiling since January but the liabilities don't stop rising. As of today, US debt is now ~$37 trillion. Treasury has burned through $560BN of its cash balance in the past month. Just $280BN left.' -ZeroHedge On the 1st of April: In recent weeks, I have shared my opinion on the latest Dutch pension fund drama. This week: https://i.ibb.co/96ZhS0W/Gn-XEVQRXw-AM6b0-A.jpg APG and pension funds refused to invest in Dutch housing (for political reasons). This involved 25 billion euros. Currently we almost have a political scandal over a medal, but the fact that our pension system is being put at risk...no biggie!? For our own housing market? “Too political.” For war and Brussels' military ambitions? €100,000,000,000—no problem. They’re gambling with your pension while first-time buyers can’t afford a home and seniors struggle to make ends meet. Our money, their agenda. Got Bitcoin? I will end this Weekly Recap with a Stanley Druckenmiller quote: "My favorite quote of all time is maybe Mark Twain: "Put all your eggs in one basket and watch the basket carefully." "I tend to think that's what great investors do." I know what I do and have. Bitcoin! ## 🎁If you have made it this far I would like to give you a little gift: What Bitcoin Did: Peter Dunworth is the Director of a multi-family office and is the co-founder of The Bitcoin Adviser. In this episode, they discuss why Bitcoin is the only asset that can recapitalize the financial system, why Peter believes Bitcoin could become a $100 trillion asset within a decade, why credit markets are ultimately a collateral problem, and why financializing Bitcoin might be necessary to save Main Street from being collateral damage. They also get into Australia's property obsession, GameStop’s pivot to Bitcoin, the difference between Bitcoin derivatives and the asset itself, and MicroStrategy. https://www.youtube.com/watch?v=_bSprc0IAow Credit: I have used multiple sources! My savings account: Bitcoin The tool I recommend for setting up a Bitcoin savings plan: PocketBitcoin especially suited for beginners or people who want to invest in Bitcoin with an automated investment plan once a week or monthly. `Use the code SE3997` Get your Bitcoin out of exchanges. Save them on a hardware wallet, run your own node...be your own bank. Not your keys, not your coins. It's that simple. ⠀ ⠀ ⠀⠀ ⠀ ⠀⠀⠀ Do you think this post is helpful to you? If so, please share it and support my work with a zap. ▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃ ⭐ Many thanks⭐ Felipe - Bitcoin Friday! ▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
@ 3c7dc2c5:805642a8
2025-04-02 21:15:55## 🧠Quote(s) of the week: CBDC the digital euro - a centralized solution in search of a problem. While the ECB may see it as a way to 'modernize' finance, true innovation comes from empowering individuals, not consolidating control. CBDCs are just surveillance tools disguised as innovation. Bitcoin is the only true digital money—decentralized, scarce, and free. Stack sats, not CBDCs. ## 🧡Bitcoin news🧡 2025 https://i.ibb.co/vx988kT1/Gn-Ix-Dp-YWs-AASkiw.jpg On the 24th of March: ➡️The Pakistan central bank is exploring mining Bitcoin with excess electricity. ➡️'MicroStrategy just added another 7,000 Bitcoin to their treasury. They're now holding over 506,000 BTC ($44 billion). Look at the corporate Bitcoin ownership breakdown: - MicroStrategy: 506,000+ BTC - Marathon: ~46,000 BTC (10x smaller) - Riot: ~19,000 BTC (26x smaller) That acquisition curve has gone parabolic since Q4 2024. Strategy's buying pace now rivals what we're seeing from the Bitcoin ETFs, a single public company absorbing supply at an institutional scale. Clear institutional conviction signal here.' -Ecoinometrics ➡️SQUARE CEO JACK DORSEY: "Bitcoin will make the current financial system feel as irrelevant as the fax machine." On the 25th of March: ➡️'BITCOIN HASH-RIBBON FLASHES BUY SIGNAL - This is one of the most reliable "buy" indicators. - Significant price gains have followed 7 out of the last 7 times this indicator was triggered.' -Bitcoin Archive (foto) Bitcoin is always a buy. Just DCA. ➡️GameStop includes Bitcoin as a treasury reserve asset in its investment policy update. GameStop has $4.6 billion in cash to invest. ➡️Strategy’s sale of 8.5 million STRF shares closes today, unlocking $711 million in new capital to buy more Bitcoin. ➡️BBC News reports from a remote community of 15,000 people in the far north-western tip of Zambia relying on hydroelectric power, “The bitcoin mine now accounts for around 30% of the plant's revenue allowing them to keep the prices down for the local town” - Source: https://www.bbc.com/news/articles/cly4xe373p4o Gridless is doing a splendid job in Africa and showing through proof-of-work that if you aren't mining Bitcoin, you are wasting energy. It's time for such communities to appear more around the world. Daniel Batten: 'They couldn't resist zooming out and implying this is an outlier (it isn't, the majority of off-grid bitcoin mining operations are renewably powered). In doing so BBC made three factually incorrect statements at the end about Bitcoin mining straining grids (multiple peer-reviewed studies show the opposite is true), and "Greenidge gas power plant in New York which was renovated to mine bitcoin" (it didn't, it re-opened to supply power back to the grid), and stating that Bitcoin mining needs artificial govt incentives or rules to do the right thing (It doesn't, it's become 56.7% sustainably powered without any govt incentives) But let's shine the light on the positive - it has far fewer factually incorrect statements than previous reporting, and it is a step in the right direction in its gradual journey towards objective Bitcoin reporting for a media company that has until now only published negative news stories on Bitcoin.' ➡️Femke Halsema, Mayor of Amsterdam, wants a national ban on Bitcoin payments: "It undermines our civilization". I rather believe the opposite. Under Femke Halsema - Amsterdam - The number of civil servants increased by 50% (14K -> 20K) - Debt increased by 150% (4 billion -> approx. 10 billion) Despite high revenues, Amsterdam has to borrow nearly half a billion euros every year. Local taxes continue to rise, whether it's water authority taxes or property taxes (OZB). But, above all, you should be concerned about those 0.3% criminal Bitcoin / Crypto transactions (worldwide). The audacity. Even if the Netherlands were to legally ban Bitcoin payments, users could easily continue trading through foreign exchanges or peer-to-peer platforms. A ban might actually push Bitcoin usage further underground, making oversight of suspicious transactions worse rather than better. ➡️Mt. Gox moves 11.501 Bitcoin ($1B) for creditor repayment. ➡️BlackRock launched a European Bitcoin ETP today - Bloomberg ➡️North Carolina introduces a bill to invest 5% of state funds into Bitcoin. On the 26th of March: ➡️NYDIG just became a big Bitcoin miner. Crusoe, the first to scale Bitcoin mining off flared gas (~200MW worth, across 425 data centers) has sold its entire Bitcoin mining business to NYDIG. ➡️Metaplanet has raised ~$55.2m (¥8.28b) of equity capital through three trading days this week while partially deleveraging with the redemption of $23.3m (¥3.5b) of 0% ordinary bonds. ➡️GameStop can service a loan of up to $100 BILLION for 4.6 years with its existing $4.6b cash balance at 1% interest. That's twice the amount of Bitcoin Michael Saylor's Strategy currently holds. ➡️New feature by Protonmail enables their 100 million users to send Bitcoin using their email addresses. ➡️The Blockchain Group confirms the acquisition of 580 BTC for ~€47.3 million, the holding of a total of 620 BTC, and a BTC Yield of 709.8% YTD. → Confirmation of the acquisition of 580 BTC for ~€47.3 million at ~€81,550 per bitcoin → Total group holdings of 620 BTC for ~€50.5 million at ~€81,480 per bitcoin → Adoption of ‘BTC Yield’, ‘BTC Gain’, and ‘BTC € Gain’ as KPIs, following the steps of Strategy and Metaplanet This is a major step in our Bitcoin Treasury Company strategy focused on increasing Bitcoin per share over time. Source: https://t.co/QDj61ZDe6O The Blockchain Group is Europe's First Bitcoin Treasury Company! On the 27th of March: ➡️'Bitcoin's 4-year Compound Annual Growth Rate (CAGR) is at historic lows.' -Pierre Rochard ➡️Daniel Batten: Yet another paper on Bitcoin and energy TL:DR: "The opportunities offered by bitcoin mining in reduction of the greenhouse gas emissions and renewable energy transition are greater than generally assumed" The journal has a (high) impact factor of 7.1." Source: https://t.co/W3gytMgcpC ➡️A home miner with only 4 machines mined block 888737. https://i.ibb.co/7xm91R4t/Gn-Ef-H9y-Ws-AA4jkn.jpg Bitcoin proves anyone can participate and earn—true freedom! ➡️'Short-Term Holders have increased their Bitcoin holdings by 201,743 BTC to 5,750,076 BTC since January, remaining below previous cycle peaks. 200K BTC are currently held at an unrealized loss, representing about $17B.' -Bitcoin News ➡️Bitcoin mining hardware manufacturer Canaan signs a three-year colocation agreement with Mawson Infrastructure Group's Mawson Hosting LLC for facilities in Midland, Pennsylvania, and Edna, Texas. Most of the 4.7 EH/s hashrate is expected to be operational by Q2 2025. On the 28th of March: ➡️If Saylor had bet on ETH instead of Bitcoin, Strategy would be down $9 billion, instead of up $9 billion like they are today. ETHBTC made fresh lows 0.02210. Ether is down 74% against Bitcoin since switching from proof of work to proof of stake. Yikes! ➡️Representative introduces a strategic Bitcoin reserve bill in South Carolina. ➡️A Russian company built a Bitcoin mine in the Arctic. Set in the frozen city of Norilsk, the facility taps into cheap excess energy from one of the world's most isolated industrial hubs. ➡️The price of bitcoin has nearly followed the same phases of volatility for 15 years, according to Fidelity. https://i.ibb.co/LdQfrqG0/Gn-Ig-Skd-XMAAi-L3r.jpg another great chart: https://i.ibb.co/G4WmDjhd/Gn-JED1q-Xk-AAq-Kqk.jpg On the 29th of March: ➡️Public miner MARA with a $2B common stock offering to buy more Bitcoin. https://i.ibb.co/PZZxXJ37/Gn-Kj-Vqza-EAEUG-V.png ➡️California has officially included Bitcoin Rights protections in its newly proposed digital asset bill. If passed, it will guarantee the right to self-custody for nearly 40M residents and prohibit discrimination against Bitcoin use. ➡️The number of addresses with more than one Bitcoin has fallen below 1 million, standing today at 995,207. On the 31st of March: ➡️Larry Fink, Founder/CEO of BlackRock in his annual letter to shareholders: “If the U.S. doesn't get its debt under control, if deficits keep ballooning, America risks losing that position to digital assets like Bitcoin." https://www.blackrock.com/corporate/literature/presentation/larry-fink-annual-chairmans-letter.pdf ➡️Strategy has acquired 22,048 BTC for ~$1.92 billion at ~$86,969 per bitcoin and has achieved a BTC Yield of 11.0% YTD 2025. As of 3/30/2025, Strategy holds 528,185 $BTC acquired for ~$35.63 billion at ~$67,458 per bitcoin. ➡️ The Bitcoin Policy Institute releases a framework for the USA to buy $200 billion worth of #Bitcoin using Bit Bonds. ➡️Is Indonesia the next Bitcoin Country? Bitcoin Indonesia mapped out the entire Bitcoin ecosystem. A new map shows Bitcoin adoption EXPLODING across the Southeast Asian island nation of Indonesia. Check out all the communities, projects, and businesses embracing Bitcoin. The revolution is happening. https://i.ibb.co/cXL8mC0x/Gnbdg-Lub-IAAdwcb.jpg On the 1st of April: ➡️'Over 73,353 BTC were bought by corporations in Q1 2025. Only 40,500 BTC new Bitcoin was mined, but still no supply shock, for now... Which company do you want to see adopt BTC next?' Here is the breakdown by Alec: https://x.com/Alec_Bitcoin/status/1907062290345783723 ➡️After skeptics questioned Tether’s Bitcoin holdings, CEO Paolo Ardoino fired back, sharing the company’s BTC address with a confirmed balance of 92,646 BTC. On the same day Tether bought 8,888 Bitcoin worth $735 million as per on-chain data. They now hold over 100,000 BTC. ➡️'GameStop just raised $1.48B. They are expected to use that and possibly more of the now $6B+ on their balance sheet to buy Bitcoin. A master class on how to pivot from meme stock to capitalize on volatility in the ultimate store of value.' -James Lavish ➡️Texas' state house Democrats have proposed a bill that would authorize up to $250 million in state investment in Bitcoin and up to $10 million for each municipality and county. ➡️Human Rights Foundation donates 10 Bitcoins worth $830,000 to over 20 projects worldwide. Alex Gladstein: '1 billion sats gifted carefully to a variety of stellar organizations and individuals to support BTC privacy, decentralization, education, and p2p use, aimed at folks working under authoritarianism.' ## 💸Traditional Finance / Macro: On the 29th of March 👉🏽'From Wednesday to Friday, the S&P 500 lost -$100 billion PER trading hour for a total of -$2 TRILLION. Then, after the market closed on Friday, S&P 500 futures erased ANOTHER -$120 billion in minutes.' -TKL ## 🏦Banks: 👉🏽 no news ## 🌎Macro/Geopolitics: On the 24th of March: 👉🏽Financelot: 'This is fascinating. The Dow Jones to Gold Ratio is about to cross a level only seen 4 times in history. Every time it crossed this level it marked the beginning of an 18-month recession/depression. 1929, 1973, 2008 & 2025' I don't think we won't see a depression. History rhymes but doesn't always mean it will repeat, although human behavior stays the same. For now, it means the market is overvalued, gold is undervalued, or both. 👉🏽US household wealth is falling: US household equity wealth is set to drop a whopping -$3 trillion this quarter, the most since the 2022 bear market, according to BofA estimates. By comparison, equity holdings rose +$9 trillion in 2024 to a record $56 trillion. In other words, one-third of last year's gains have likely been wiped out due to the recent market pullback. Furthermore, the top 10% of the wealthiest Americans own 87% of US stocks. This, in turn, may negatively impact consumer spending as the top 10% reflect a record 50% of all consumer expenditures. Consumer spending is set to slow in Q2 2025.' -TKL 👉🏽Demolition of the Boiler House at Moorburg Power Plant in Hamburg. Germany is preparing for combat by dynamiting its own modern energy infrastructure down. This was the most advanced coal plant. 6 years old and cost three billion euros. The Netherlands is following a similar policy—they poured concrete into their gas drilling pipes. BowTiedMara on Twitter: "In 2022, a girl tied herself to the net at Roland Garros in protest, and she wore a T-shirt that said: "We have 1,028 days left." Today, the 27th of March, marks those 1,028 days, and nothing happened. Climate doomers are like Aztecs who think the sun stops unless they cut out some organs." 👉🏽Starting in April, the 66,000 employees of the European institutions will receive their seventh salary increase in just three years! Normally, this happens at most once per year. The President of the European Commission, Ursula von der Leyen, will see the largest increase, with her monthly salary rising to €34,800—an increase of €2,700—according to a report by the German newspaper Bild-Zeitung today. For the Dutch readers: https://ejbron.wordpress.com/2025/03/24/eu-bureaucraten-en-politici-krijgen-de-7e-salarisverhoging-sinds-2022/ They are compensating for the inflation they impose on the EU. Lucky them Fair to say we need a DOGE in Europe. On the 25th of March: 👉🏽Dutch minister announces a huge increase in excise duties of 25.8 cents on gasoline. On top of that, the price of gasoline will rise by an additional 7 cents due to the blending requirement and 11 cents due to the ETS-2 regulation. In a free market, prices would not be announced by politicians but would emerge through supply and demand. How I love the EU....although it is a bit more nuanced. The temporary discount is ending. Unless the parliament decides to extend it, the price of gasoline will rise. The Dutch government should simply spend less and abolish all taxes, excise duties, and levies on food, fuel, and energy. Never gonna happen though. 👉🏽"Shell will be thoroughly reviewing all its chemical divisions worldwide in the coming period. In Europe, this could lead to the partial or complete closure of various chemical branches." As mentioned multiple times last month, major industrial companies sounded the alarm. They warned that high energy costs in the Netherlands put their future at risk. Additionally, sustainability efforts and unclear government policies are challenging the sector. Frans Everts, President-Director of Shell Netherlands, warned that the entire industry could collapse. The Green Deal is moving full speed ahead—soon everyone will be relying on food banks… For the Dutch readers: https://nos.nl/artikel/2561036-shell-kijkt-naar-gedeeltelijke-sluiting-van-chemie-onderdelen On the 26th of March: 👉🏽EU countries will start using a digital driver’s license from 2030. This is the result of negotiations between the European Parliament and EU member states. In the Netherlands, the digital license will be valid for ten years and will be accessible via an app. And we all know which app that will be! The EU Digital Wallet must be filled, after all. Not just your driver’s license—everything will soon be linked to your digital identity. It’s all right there on the EU’s website, and it’s been planned for a long time. The COVID pass was already part of the rollout. The fact that they present these as separate steps just shows that they know people wouldn’t accept it if they were fully aware of what’s happening. On the 27th of March: 👉🏽Gold surpasses $3,100 for the first time in history. TKL: 'Gold prices have hit 50 all-time highs over the last 12 months, its best streak in 12 years. This is also the 3rd-longest streak on record after a historic run during the late 1970s. The 1970s came with a period of double-digit inflation, stagnant economic growth, and a high unemployment rate, also known as stagflation. As a result, gold prices recorded 4 consecutive yearly gains.' On the 31st of March for the first time, gold blasted through $100,000/kilogram. This time, gold prices have rallied 39% over the last 12 months, are up 16% year-to-date, and are on track for the 3rd annual positive performance.' 👉🏽NATO Secretary General Rutte insists there will be no normalization of relations with Russia for decades to come. On March 14, 2025, Bloomberg, Rutte says: "Once the war is over, relations with Russia will gradually be restored." On March 26, 2025, Rutte said: "There will be no normalization of relations with Russia for decades, even after the war is over." That is the Mark I know! "Mark Rutte, the long-serving Dutch Prime Minister, earned the nickname “Pinokkio” (Dutch for Pinocchio) primarily because of perceived dishonesty or evasiveness in political debates and scandals. While some still view Rutte as a pragmatic and stable leader, the nickname “Pinokkio” reflects a broader public sentiment of distrust, especially among those who felt betrayed by his communication style or decisions.” On the 28th of March: 👉🏽US consumers now expect 5.0%(!) inflation in the next twelve months. Inflation expectations have DOUBLED in just four months. That's huge! Long-term US inflation expectations have officially SURGED to 4.1%, the highest level since 1993. Tariff front-running has led to a $300+ BILLION trade deficit in 2 months, and consumer sentiment has collapsed. Atlanta Fed is now projecting that Q1 GDP will be -2.8%… a large contraction. It’s negative even “gold adjusted” 4 weeks ago it was +2.3% 8 weeks ago it was +3.9% Yikes! 👉🏽The State Department is officially shutting down USAID and has formally notified Congress of its closure. The remaining 900 employees are set to be terminated. 👉🏽Argentina’s Economy Grows 6.5% in January. Argentina’s Poverty Rate Drops from 52.9% to 38.1% in 15 Months Under Javier Milei 👉🏽Fix the money, fix the world: DOGE “There is actually really only ONE BANK ACCOUNT that's used to disperse ALL monies that go out of the federal government” “It's a big one — A couple of weeks ago it had $800 billion in it, it's the treasury general account” “We're serving 580+ agencies. And up until very recently, effectively they could say, make the payment and Treasury just sent it out as fast as possible. NO VERIFICATION” “There's a $500 billion of fraud every year. There are hundreds of billion dollars of improper payments and we can't pass an audit. The consolidated financial report is produced by treasury and we cannot pass an audit” Extremely fascinating interview by Bret Baier with the highly talented and competent DOGE team, which is rigorously streamlining the U.S. government bureaucracy. This work can only be done by competent (and motivated) outsiders with experience. Also urgently needed in the Netherlands, and in Europe. On the 29th of March: 👉🏽'US debt has been "limited" by the $36.104 trillion debt ceiling since January but the liabilities don't stop rising. As of today, US debt is now ~$37 trillion. Treasury has burned through $560BN of its cash balance in the past month. Just $280BN left.' -ZeroHedge On the 1st of April: In recent weeks, I have shared my opinion on the latest Dutch pension fund drama. This week: https://i.ibb.co/96ZhS0W/Gn-XEVQRXw-AM6b0-A.jpg APG and pension funds refused to invest in Dutch housing (for political reasons). This involved 25 billion euros. Currently we almost have a political scandal over a medal, but the fact that our pension system is being put at risk...no biggie!? For our own housing market? “Too political.” For war and Brussels' military ambitions? €100,000,000,000—no problem. They’re gambling with your pension while first-time buyers can’t afford a home and seniors struggle to make ends meet. Our money, their agenda. Got Bitcoin? I will end this Weekly Recap with a Stanley Druckenmiller quote: "My favorite quote of all time is maybe Mark Twain: "Put all your eggs in one basket and watch the basket carefully." "I tend to think that's what great investors do." I know what I do and have. Bitcoin! ## 🎁If you have made it this far I would like to give you a little gift: What Bitcoin Did: Peter Dunworth is the Director of a multi-family office and is the co-founder of The Bitcoin Adviser. In this episode, they discuss why Bitcoin is the only asset that can recapitalize the financial system, why Peter believes Bitcoin could become a $100 trillion asset within a decade, why credit markets are ultimately a collateral problem, and why financializing Bitcoin might be necessary to save Main Street from being collateral damage. They also get into Australia's property obsession, GameStop’s pivot to Bitcoin, the difference between Bitcoin derivatives and the asset itself, and MicroStrategy. https://www.youtube.com/watch?v=_bSprc0IAow Credit: I have used multiple sources! My savings account: Bitcoin The tool I recommend for setting up a Bitcoin savings plan: PocketBitcoin especially suited for beginners or people who want to invest in Bitcoin with an automated investment plan once a week or monthly. `Use the code SE3997` Get your Bitcoin out of exchanges. Save them on a hardware wallet, run your own node...be your own bank. Not your keys, not your coins. It's that simple. ⠀ ⠀ ⠀⠀ ⠀ ⠀⠀⠀ Do you think this post is helpful to you? If so, please share it and support my work with a zap. ▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃ ⭐ Many thanks⭐ Felipe - Bitcoin Friday! ▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃ @ ef53426a:7e988851
2025-04-02 21:02:06# Bartering and early money \ Early societies bartered goods, but transactions were often complicated. The value of goods doesn’t always align. Enter money. It’s used as an indirect exchange for any goods, so everyone wants it. Early money wasn’t anything like what we use today. For example, the inhabitants of Yap Island (Micronesia) used large Rai stones for trade. New stones were dragged up a hill for everyone to see. The owner would then exchange part of the stone for goods and services. As they were hard to quarry and move, Rai stones retained their value (salability). Then, an Irish-American captain started importing stones using modern technology. Soon enough, they became so common, they no longer worked as money. --- # Gold — the basis for sound money \ Smelting made it possible to create highly salable and transportable coins. Gold was best because it’s virtually impossible to destroy and can’t be synthesized using other materials. It has a fairly limited supply, which grows slowly and predictably (due to the difficulty of mining). Technologies like the telegraph and trains made it easier for both people and goods to get from point A to point B. That, in turn, justified forms of payment like checks, paper receipts, and bills. But paper is not worth much unless it’s backed by something. Governments worldwide issued paper money backed by precious metals, which they stored in vaults. By 1900, around 50 countries had adopted the Gold Standard. This was sound money. --- # Currencies devalued \ Roman emperor Julius Caesar issued the Aureus, an empire-standard coin containing 8 grams of gold. But as growth began to slow, rulers started ‘coin clipping’, reducing the quantity of precious metal in coins. This eventually triggered a series of economic crises that led to the downfall of the Roman Empire. The gold standard had one major flaw: it had to be stored in bank vaults. This created a highly centralized system in which governments controlled the value of paper money. If they wanted to, they could always increase the supply of money without increasing the corresponding amount of gold. In 1914, nearly every major European power decided to do this to fund their war operations. Rather than raising taxes, they simply printed new money with no extra gold. The standard had been abandoned. --- # Government-backed money \ Governments chose to introduce fiat money – currency backed by decree rather than gold. The adoption of the fiat system led to an age of unsound money shaped by ever-greater intervention in the economy as governments scrambled to stabilize their currencies. By 1944, the end of the Second World War was in sight, and the victors began planning the postwar economic order. The world’s currencies would be tied to the US dollar at a fixed exchange rate. The dollar would in turn be tied to the value of gold, again at a fixed rate. The United States bent the rules and inflated its own currency compared to gold. Other nations inflated their currencies compared to the dollar. On August 15, 1971, President Nixon announced that dollars would no longer be convertible to gold. --- # Sound money = functioning economy \ Sound money encourages people to save and invest, enabling sustainable, long-term growth. Why? Well, humans have a natural positive time preference: we prefer instant gratification over future gratification. Sound money prompts us to think more about the future. The more capital accumulation there is, the greater the chance of stable, long-term economic growth. Unsound money distorts capital accumulation. When governments interfere with the money supply, they also interfere with prices. And prices give investors the information they need to make good decisions without having to learn every tiny detail about global events. --- # Recessions and debt arise from unsound money \ Government interference takes the form of central planning. No single person, agency, or department ever has access to all the information necessary to understand the vast and complex economy. Interventions distort markets, creating boom and bust cycles. According to Keynes and his followers, the best way to respond to recessions is to increase spending. You could lower taxes, but people don’t usually spend their extra money. Raising taxes is unpopular, so governments invariably decide to increase the money supply. Saving becomes less attractive, creating a culture of unwise spending and growing debt. We need to return to sound money and a new gold standard. Enter bitcoin. --- # Bitcoin is scarce \ Bitcoin has similar traits to gold. Its supply is literally fixed. Once there are 21 million bitcoins in circulation, no more will be issued. The supply grows at a diminishing rate. Computers across the Bitcoin network pool their processing power to solve complex algorithmic problems. Once these puzzles have been cracked, the “miners” receive bitcoins as a reward. Satoshi Nakamoto designed the system to avoid gold rushes. The algorithmic problems become more difficult to solve as the number of computers working on them rises, guaranteeing a steady and reliable supply. Also, the number of bitcoins issued is halved every four years, resulting in ever-smaller releases until 2140, after which no more coins will be released. That makes bitcoin unique. It is the only good that is defined by absolute scarcity. No amount of time or resources can create more bitcoins than the programmed supply allows. The supply cannot be manipulated, making it a perfect store of value. --- # Bitcoin is secure \ The bitcoin ledger uses the public blockchain. When mining computers crack an algorithmic puzzle, they create a block. The blocks on the ledger contain details about every blockchain transaction ever completed. Every network user can view this information. Ownership of bitcoins is only valid once it’s been registered on the blockchain. This is only possible if the majority of network users approve it, so there’s no need for a central authority to oversee transactions. While verifying new blocks requires virtually no energy, creating a fraudulent block would cost a significant amount of processing power. Even if a user decided to expend vast amounts of energy and successfully hacked a majority of all network nodes to approve a fraudulent block, they’d gain very little. Trust in bitcoin would be lost, leading to a drop in demand and value. --- # Challenges for adoption \ Because bitcoin is new, demand has varied. The volatile price has, at times, undermined the currency’s status as an effective store of value. Bitcoin’s transaction limit is currently set at 500,000 per day. That could be increased, but there will always be a daily cap. The more transactions that take place, the more nodes there’ll need to be. This increases transaction fees and the amount of processing power expended. Bitcoin could be traded off the blockchain, meaning currencies will be backed by bitcoin. That would create a new standard, but it would also mean that new centralized institutions would need to manage this system. ---  This 5-minute summary did not use copyrighted material from the book. It aims simply to give readers a quick understanding of the book (which is well worth reading). ‘*The Bitcoin Standard: The Decentralized Alternative to Central Banking’* was written by economist Saifedean Ammous in 2018. Buy the book and many more titles at [bitcoinbook.shop](bitcoinbook.shop)
@ ef53426a:7e988851
2025-04-02 21:02:06# Bartering and early money \ Early societies bartered goods, but transactions were often complicated. The value of goods doesn’t always align. Enter money. It’s used as an indirect exchange for any goods, so everyone wants it. Early money wasn’t anything like what we use today. For example, the inhabitants of Yap Island (Micronesia) used large Rai stones for trade. New stones were dragged up a hill for everyone to see. The owner would then exchange part of the stone for goods and services. As they were hard to quarry and move, Rai stones retained their value (salability). Then, an Irish-American captain started importing stones using modern technology. Soon enough, they became so common, they no longer worked as money. --- # Gold — the basis for sound money \ Smelting made it possible to create highly salable and transportable coins. Gold was best because it’s virtually impossible to destroy and can’t be synthesized using other materials. It has a fairly limited supply, which grows slowly and predictably (due to the difficulty of mining). Technologies like the telegraph and trains made it easier for both people and goods to get from point A to point B. That, in turn, justified forms of payment like checks, paper receipts, and bills. But paper is not worth much unless it’s backed by something. Governments worldwide issued paper money backed by precious metals, which they stored in vaults. By 1900, around 50 countries had adopted the Gold Standard. This was sound money. --- # Currencies devalued \ Roman emperor Julius Caesar issued the Aureus, an empire-standard coin containing 8 grams of gold. But as growth began to slow, rulers started ‘coin clipping’, reducing the quantity of precious metal in coins. This eventually triggered a series of economic crises that led to the downfall of the Roman Empire. The gold standard had one major flaw: it had to be stored in bank vaults. This created a highly centralized system in which governments controlled the value of paper money. If they wanted to, they could always increase the supply of money without increasing the corresponding amount of gold. In 1914, nearly every major European power decided to do this to fund their war operations. Rather than raising taxes, they simply printed new money with no extra gold. The standard had been abandoned. --- # Government-backed money \ Governments chose to introduce fiat money – currency backed by decree rather than gold. The adoption of the fiat system led to an age of unsound money shaped by ever-greater intervention in the economy as governments scrambled to stabilize their currencies. By 1944, the end of the Second World War was in sight, and the victors began planning the postwar economic order. The world’s currencies would be tied to the US dollar at a fixed exchange rate. The dollar would in turn be tied to the value of gold, again at a fixed rate. The United States bent the rules and inflated its own currency compared to gold. Other nations inflated their currencies compared to the dollar. On August 15, 1971, President Nixon announced that dollars would no longer be convertible to gold. --- # Sound money = functioning economy \ Sound money encourages people to save and invest, enabling sustainable, long-term growth. Why? Well, humans have a natural positive time preference: we prefer instant gratification over future gratification. Sound money prompts us to think more about the future. The more capital accumulation there is, the greater the chance of stable, long-term economic growth. Unsound money distorts capital accumulation. When governments interfere with the money supply, they also interfere with prices. And prices give investors the information they need to make good decisions without having to learn every tiny detail about global events. --- # Recessions and debt arise from unsound money \ Government interference takes the form of central planning. No single person, agency, or department ever has access to all the information necessary to understand the vast and complex economy. Interventions distort markets, creating boom and bust cycles. According to Keynes and his followers, the best way to respond to recessions is to increase spending. You could lower taxes, but people don’t usually spend their extra money. Raising taxes is unpopular, so governments invariably decide to increase the money supply. Saving becomes less attractive, creating a culture of unwise spending and growing debt. We need to return to sound money and a new gold standard. Enter bitcoin. --- # Bitcoin is scarce \ Bitcoin has similar traits to gold. Its supply is literally fixed. Once there are 21 million bitcoins in circulation, no more will be issued. The supply grows at a diminishing rate. Computers across the Bitcoin network pool their processing power to solve complex algorithmic problems. Once these puzzles have been cracked, the “miners” receive bitcoins as a reward. Satoshi Nakamoto designed the system to avoid gold rushes. The algorithmic problems become more difficult to solve as the number of computers working on them rises, guaranteeing a steady and reliable supply. Also, the number of bitcoins issued is halved every four years, resulting in ever-smaller releases until 2140, after which no more coins will be released. That makes bitcoin unique. It is the only good that is defined by absolute scarcity. No amount of time or resources can create more bitcoins than the programmed supply allows. The supply cannot be manipulated, making it a perfect store of value. --- # Bitcoin is secure \ The bitcoin ledger uses the public blockchain. When mining computers crack an algorithmic puzzle, they create a block. The blocks on the ledger contain details about every blockchain transaction ever completed. Every network user can view this information. Ownership of bitcoins is only valid once it’s been registered on the blockchain. This is only possible if the majority of network users approve it, so there’s no need for a central authority to oversee transactions. While verifying new blocks requires virtually no energy, creating a fraudulent block would cost a significant amount of processing power. Even if a user decided to expend vast amounts of energy and successfully hacked a majority of all network nodes to approve a fraudulent block, they’d gain very little. Trust in bitcoin would be lost, leading to a drop in demand and value. --- # Challenges for adoption \ Because bitcoin is new, demand has varied. The volatile price has, at times, undermined the currency’s status as an effective store of value. Bitcoin’s transaction limit is currently set at 500,000 per day. That could be increased, but there will always be a daily cap. The more transactions that take place, the more nodes there’ll need to be. This increases transaction fees and the amount of processing power expended. Bitcoin could be traded off the blockchain, meaning currencies will be backed by bitcoin. That would create a new standard, but it would also mean that new centralized institutions would need to manage this system. ---  This 5-minute summary did not use copyrighted material from the book. It aims simply to give readers a quick understanding of the book (which is well worth reading). ‘*The Bitcoin Standard: The Decentralized Alternative to Central Banking’* was written by economist Saifedean Ammous in 2018. Buy the book and many more titles at [bitcoinbook.shop](bitcoinbook.shop) @ a95c6243:d345522c
2025-03-11 10:22:36**«Wir brauchen eine digitale Brandmauer gegen den Faschismus»,** [schreibt](https://www.ccc.de/de/updates/2025/ccc-fordert-digitale-brandmauer) der Chaos Computer Club (CCC) auf seiner Website. Unter diesem Motto präsentierte er letzte Woche einen Forderungskatalog, mit dem sich 24 Organisationen an die kommende Bundesregierung wenden. Der Koalitionsvertrag müsse sich daran messen lassen, verlangen sie. **In den drei Kategorien «Bekenntnis gegen Überwachung»,** «Schutz und Sicherheit für alle» sowie «Demokratie im digitalen Raum» stellen die [Unterzeichner](https://d-64.org/digitale-brandmauer/), zu denen auch Amnesty International und Das NETTZ gehören, unter anderem die folgenden «Mindestanforderungen»: * Verbot biometrischer Massenüberwachung des öffentlichen Raums sowie der ungezielten biometrischen Auswertung des Internets. * Anlasslose und massenhafte Vorratsdatenspeicherung wird abgelehnt. * Automatisierte Datenanalysen der Informationsbestände der Strafverfolgungsbehörden sowie jede Form von Predictive Policing oder automatisiertes Profiling von Menschen werden abgelehnt. * Einführung eines Rechts auf Verschlüsselung. Die Bundesregierung soll sich dafür einsetzen, die Chatkontrolle auf europäischer Ebene zu verhindern. * Anonyme und pseudonyme Nutzung des Internets soll geschützt und ermöglicht werden. * Bekämpfung «privaten Machtmissbrauchs von Big-Tech-Unternehmen» durch durchsetzungsstarke, unabhängige und grundsätzlich föderale Aufsichtsstrukturen. * Einführung eines digitalen Gewaltschutzgesetzes, unter Berücksichtigung «gruppenbezogener digitaler Gewalt» und die Förderung von Beratungsangeboten. * Ein umfassendes Förderprogramm für digitale öffentliche Räume, die dezentral organisiert und quelloffen programmiert sind, soll aufgelegt werden. **Es sei ein Irrglaube, dass zunehmende Überwachung einen Zugewinn an Sicherheit darstelle,** ist eines der Argumente der Initiatoren. Sicherheit erfordere auch, dass Menschen anonym und vertraulich kommunizieren können und ihre Privatsphäre geschützt wird. **Gesunde digitale Räume lebten auch von einem demokratischen Diskurs,** lesen wir in dem Papier. Es sei Aufgabe des Staates, Grundrechte zu schützen. Dazu gehöre auch, Menschenrechte und demokratische Werte, insbesondere Freiheit, Gleichheit und Solidarität zu fördern sowie den Missbrauch von Maßnahmen, Befugnissen und Infrastrukturen durch «die Feinde der Demokratie» zu verhindern. **Man ist geneigt zu fragen, wo denn die Autoren «den Faschismus» sehen,** den es zu bekämpfen gelte. Die meisten der vorgetragenen Forderungen und Argumente finden sicher breite Unterstützung, denn sie beschreiben offenkundig gängige, kritikwürdige Praxis. Die Aushebelung der Privatsphäre, der Redefreiheit und anderer Grundrechte im Namen der Sicherheit wird bereits jetzt massiv durch die aktuellen «demokratischen Institutionen» und ihre «durchsetzungsstarken Aufsichtsstrukturen» betrieben. **Ist «der Faschismus» also die EU und ihre Mitgliedsstaaten?** Nein, die «faschistische Gefahr», gegen die man eine digitale Brandmauer will, kommt nach Ansicht des CCC und seiner Partner aus den Vereinigten Staaten. Private Überwachung und Machtkonzentration sind dabei weltweit schon lange Realität, jetzt endlich müssen sie jedoch bekämpft werden. In dem Papier heißt es: > «Die willkürliche und antidemokratische Machtausübung der Tech-Oligarchen um Präsident Trump erfordert einen Paradigmenwechsel in der deutschen Digitalpolitik. (...) Die aktuellen Geschehnisse in den USA zeigen auf, wie Datensammlungen und -analyse genutzt werden können, um einen Staat handstreichartig zu übernehmen, seine Strukturen nachhaltig zu beschädigen, Widerstand zu unterbinden und marginalisierte Gruppen zu verfolgen.» **Wer auf der anderen Seite dieser Brandmauer stehen soll, ist also klar.** Es sind die gleichen «Feinde unserer Demokratie», die seit Jahren in diese Ecke gedrängt werden. Es sind die gleichen Andersdenkenden, Regierungskritiker und Friedensforderer, die unter dem großzügigen Dach des Bundesprogramms «Demokratie leben» einem «kontinuierlichen Echt- und Langzeitmonitoring» wegen der Etikettierung [«digitaler Hass»](https://bag-gegen-hass.net/) unterzogen werden. **Dass die 24 Organisationen praktisch auch die Bekämpfung von Google,** Microsoft, Apple, Amazon und anderen fordern, entbehrt nicht der Komik. Diese fallen aber sicher unter das Stichwort «Machtmissbrauch von Big-Tech-Unternehmen». Gleichzeitig verlangen die Lobbyisten implizit zum Beispiel die Förderung des [Nostr](https://reason.com/video/2024/09/17/is-nostr-an-antidote-to-social-media-censorship/)-Netzwerks, denn hier finden wir dezentral organisierte und quelloffen programmierte digitale Räume par excellence, obendrein zensurresistent. Das wiederum dürfte in der Politik weniger gut ankommen. *\[Titelbild:* *[Pixabay](https://pixabay.com/de/illustrations/uns-ihnen-stammes-wettbewerb-1767691/)]* *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/digitale-brandmauer-gegen-den-faschismus-von-der-kunftigen-bundesregierung)*** erschienen.
@ a95c6243:d345522c
2025-03-11 10:22:36**«Wir brauchen eine digitale Brandmauer gegen den Faschismus»,** [schreibt](https://www.ccc.de/de/updates/2025/ccc-fordert-digitale-brandmauer) der Chaos Computer Club (CCC) auf seiner Website. Unter diesem Motto präsentierte er letzte Woche einen Forderungskatalog, mit dem sich 24 Organisationen an die kommende Bundesregierung wenden. Der Koalitionsvertrag müsse sich daran messen lassen, verlangen sie. **In den drei Kategorien «Bekenntnis gegen Überwachung»,** «Schutz und Sicherheit für alle» sowie «Demokratie im digitalen Raum» stellen die [Unterzeichner](https://d-64.org/digitale-brandmauer/), zu denen auch Amnesty International und Das NETTZ gehören, unter anderem die folgenden «Mindestanforderungen»: * Verbot biometrischer Massenüberwachung des öffentlichen Raums sowie der ungezielten biometrischen Auswertung des Internets. * Anlasslose und massenhafte Vorratsdatenspeicherung wird abgelehnt. * Automatisierte Datenanalysen der Informationsbestände der Strafverfolgungsbehörden sowie jede Form von Predictive Policing oder automatisiertes Profiling von Menschen werden abgelehnt. * Einführung eines Rechts auf Verschlüsselung. Die Bundesregierung soll sich dafür einsetzen, die Chatkontrolle auf europäischer Ebene zu verhindern. * Anonyme und pseudonyme Nutzung des Internets soll geschützt und ermöglicht werden. * Bekämpfung «privaten Machtmissbrauchs von Big-Tech-Unternehmen» durch durchsetzungsstarke, unabhängige und grundsätzlich föderale Aufsichtsstrukturen. * Einführung eines digitalen Gewaltschutzgesetzes, unter Berücksichtigung «gruppenbezogener digitaler Gewalt» und die Förderung von Beratungsangeboten. * Ein umfassendes Förderprogramm für digitale öffentliche Räume, die dezentral organisiert und quelloffen programmiert sind, soll aufgelegt werden. **Es sei ein Irrglaube, dass zunehmende Überwachung einen Zugewinn an Sicherheit darstelle,** ist eines der Argumente der Initiatoren. Sicherheit erfordere auch, dass Menschen anonym und vertraulich kommunizieren können und ihre Privatsphäre geschützt wird. **Gesunde digitale Räume lebten auch von einem demokratischen Diskurs,** lesen wir in dem Papier. Es sei Aufgabe des Staates, Grundrechte zu schützen. Dazu gehöre auch, Menschenrechte und demokratische Werte, insbesondere Freiheit, Gleichheit und Solidarität zu fördern sowie den Missbrauch von Maßnahmen, Befugnissen und Infrastrukturen durch «die Feinde der Demokratie» zu verhindern. **Man ist geneigt zu fragen, wo denn die Autoren «den Faschismus» sehen,** den es zu bekämpfen gelte. Die meisten der vorgetragenen Forderungen und Argumente finden sicher breite Unterstützung, denn sie beschreiben offenkundig gängige, kritikwürdige Praxis. Die Aushebelung der Privatsphäre, der Redefreiheit und anderer Grundrechte im Namen der Sicherheit wird bereits jetzt massiv durch die aktuellen «demokratischen Institutionen» und ihre «durchsetzungsstarken Aufsichtsstrukturen» betrieben. **Ist «der Faschismus» also die EU und ihre Mitgliedsstaaten?** Nein, die «faschistische Gefahr», gegen die man eine digitale Brandmauer will, kommt nach Ansicht des CCC und seiner Partner aus den Vereinigten Staaten. Private Überwachung und Machtkonzentration sind dabei weltweit schon lange Realität, jetzt endlich müssen sie jedoch bekämpft werden. In dem Papier heißt es: > «Die willkürliche und antidemokratische Machtausübung der Tech-Oligarchen um Präsident Trump erfordert einen Paradigmenwechsel in der deutschen Digitalpolitik. (...) Die aktuellen Geschehnisse in den USA zeigen auf, wie Datensammlungen und -analyse genutzt werden können, um einen Staat handstreichartig zu übernehmen, seine Strukturen nachhaltig zu beschädigen, Widerstand zu unterbinden und marginalisierte Gruppen zu verfolgen.» **Wer auf der anderen Seite dieser Brandmauer stehen soll, ist also klar.** Es sind die gleichen «Feinde unserer Demokratie», die seit Jahren in diese Ecke gedrängt werden. Es sind die gleichen Andersdenkenden, Regierungskritiker und Friedensforderer, die unter dem großzügigen Dach des Bundesprogramms «Demokratie leben» einem «kontinuierlichen Echt- und Langzeitmonitoring» wegen der Etikettierung [«digitaler Hass»](https://bag-gegen-hass.net/) unterzogen werden. **Dass die 24 Organisationen praktisch auch die Bekämpfung von Google,** Microsoft, Apple, Amazon und anderen fordern, entbehrt nicht der Komik. Diese fallen aber sicher unter das Stichwort «Machtmissbrauch von Big-Tech-Unternehmen». Gleichzeitig verlangen die Lobbyisten implizit zum Beispiel die Förderung des [Nostr](https://reason.com/video/2024/09/17/is-nostr-an-antidote-to-social-media-censorship/)-Netzwerks, denn hier finden wir dezentral organisierte und quelloffen programmierte digitale Räume par excellence, obendrein zensurresistent. Das wiederum dürfte in der Politik weniger gut ankommen. *\[Titelbild:* *[Pixabay](https://pixabay.com/de/illustrations/uns-ihnen-stammes-wettbewerb-1767691/)]* *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/digitale-brandmauer-gegen-den-faschismus-von-der-kunftigen-bundesregierung)*** erschienen. @ 17538dc2:71ed77c4
2025-04-02 16:04:59The MacOS security update summary is a reminder that laptops and desktops are incredibly compromised. ### macOS Sequoia 15.4 Released March 31, 2025 Accessibility Available for: macOS Sequoia Impact: An app may be able to access sensitive user data Description: A logging issue was addressed with improved data redaction. CVE-2025-24202: Zhongcheng Li from IES Red Team of ByteDance AccountPolicy Available for: macOS Sequoia Impact: A malicious app may be able to gain root privileges Description: This issue was addressed by removing the vulnerable code. CVE-2025-24234: an anonymous researcher AirDrop Available for: macOS Sequoia Impact: An app may be able to read arbitrary file metadata Description: A permissions issue was addressed with additional restrictions. CVE-2025-24097: Ron Masas of BREAKPOINT.SH App Store Available for: macOS Sequoia Impact: A malicious app may be able to access private information Description: This issue was addressed by removing the vulnerable code. CVE-2025-24276: an anonymous researcher AppleMobileFileIntegrity Available for: macOS Sequoia Impact: An app may be able to modify protected parts of the file system Description: The issue was addressed with improved checks. CVE-2025-24272: Mickey Jin (@patch1t) AppleMobileFileIntegrity Available for: macOS Sequoia Impact: An app may be able to access protected user data Description: A downgrade issue was addressed with additional code-signing restrictions. CVE-2025-24239: Wojciech Regula of SecuRing (wojciechregula.blog) AppleMobileFileIntegrity Available for: macOS Sequoia Impact: A malicious app may be able to read or write to protected files Description: A permissions issue was addressed with additional restrictions. CVE-2025-24233: Claudio Bozzato and Francesco Benvenuto of Cisco Talos. AppleMobileFileIntegrity Available for: macOS Sequoia Impact: An app may be able to access user-sensitive data Description: A privacy issue was addressed by removing the vulnerable code. CVE-2025-30443: Bohdan Stasiuk (@bohdan_stasiuk) Audio Available for: macOS Sequoia Impact: Processing a maliciously crafted font may result in the disclosure of process memory Description: The issue was addressed with improved memory handling. CVE-2025-24244: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative Audio Available for: macOS Sequoia Impact: Processing a maliciously crafted file may lead to arbitrary code execution Description: The issue was addressed with improved memory handling. CVE-2025-24243: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative Authentication Services Available for: macOS Sequoia Impact: Password autofill may fill in passwords after failing authentication Description: This issue was addressed through improved state management. CVE-2025-30430: Dominik Rath Authentication Services Available for: macOS Sequoia Impact: A malicious website may be able to claim WebAuthn credentials from another website that shares a registrable suffix Description: The issue was addressed with improved input validation. CVE-2025-24180: Martin Kreichgauer of Google Chrome Authentication Services Available for: macOS Sequoia Impact: A malicious app may be able to access a user's saved passwords Description: This issue was addressed by adding a delay between verification code attempts. CVE-2025-24245: Ian Mckay (@iann0036) Automator Available for: macOS Sequoia Impact: An app may be able to access protected user data Description: A permissions issue was addressed by removing vulnerable code and adding additional checks. CVE-2025-30460: an anonymous researcher BiometricKit Available for: macOS Sequoia Impact: An app may be able to cause unexpected system termination Description: A buffer overflow was addressed with improved bounds checking. CVE-2025-24237: Yutong Xiu Calendar Available for: macOS Sequoia Impact: An app may be able to break out of its sandbox Description: A path handling issue was addressed with improved validation. CVE-2025-30429: Denis Tokarev (@illusionofcha0s) Calendar Available for: macOS Sequoia Impact: An app may be able to break out of its sandbox Description: This issue was addressed with improved checks. CVE-2025-24212: Denis Tokarev (@illusionofcha0s) CloudKit Available for: macOS Sequoia Impact: A malicious app may be able to access private information Description: The issue was addressed with improved checks. CVE-2025-24215: Kirin (@Pwnrin) CoreAudio Available for: macOS Sequoia Impact: Parsing a file may lead to an unexpected app termination Description: The issue was addressed with improved checks. CVE-2025-24163: Google Threat Analysis Group CoreAudio Available for: macOS Sequoia Impact: Playing a malicious audio file may lead to an unexpected app termination Description: An out-of-bounds read issue was addressed with improved input validation. CVE-2025-24230: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative CoreMedia Available for: macOS Sequoia Impact: Processing a maliciously crafted video file may lead to unexpected app termination or corrupt process memory Description: This issue was addressed with improved memory handling. CVE-2025-24211: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative CoreMedia Available for: macOS Sequoia Impact: An app may be able to access sensitive user data Description: An access issue was addressed with additional sandbox restrictions. CVE-2025-24236: Csaba Fitzl (@theevilbit) and Nolan Astrein of Kandji CoreMedia Available for: macOS Sequoia Impact: Processing a maliciously crafted video file may lead to unexpected app termination or corrupt process memory Description: The issue was addressed with improved memory handling. CVE-2025-24190: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative CoreMedia Playback Available for: macOS Sequoia Impact: A malicious app may be able to access private information Description: A path handling issue was addressed with improved validation. CVE-2025-30454: pattern-f (@pattern_F_) CoreServices Description: This issue was addressed through improved state management. CVE-2025-31191: Jonathan Bar Or (@yo_yo_yo_jbo) of Microsoft, and an anonymous researcher Available for: macOS Sequoia Impact: An app may be able to access sensitive user data CoreText Available for: macOS Sequoia Impact: Processing a maliciously crafted font may result in the disclosure of process memory Description: An out-of-bounds read issue was addressed with improved input validation. CVE-2025-24182: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative Crash Reporter Available for: macOS Sequoia Impact: An app may be able to gain root privileges Description: A parsing issue in the handling of directory paths was addressed with improved path validation. CVE-2025-24277: Csaba Fitzl (@theevilbit) of Kandji and Gergely Kalman (@gergely_kalman), and an anonymous researcher curl Available for: macOS Sequoia Impact: An input validation issue was addressed Description: This is a vulnerability in open source code and Apple Software is among the affected projects. The CVE-ID was assigned by a third party. Learn more about the issue and CVE-ID at cve.org. CVE-2024-9681 Disk Images Available for: macOS Sequoia Impact: An app may be able to break out of its sandbox Description: A file access issue was addressed with improved input validation. CVE-2025-24255: an anonymous researcher DiskArbitration Available for: macOS Sequoia Impact: An app may be able to gain root privileges Description: A parsing issue in the handling of directory paths was addressed with improved path validation. CVE-2025-30456: Gergely Kalman (@gergely_kalman) DiskArbitration Available for: macOS Sequoia Impact: An app may be able to gain root privileges Description: A permissions issue was addressed with additional restrictions. CVE-2025-24267: an anonymous researcher Dock Available for: macOS Sequoia Impact: A malicious app may be able to access private information Description: The issue was addressed with improved checks. CVE-2025-30455: Mickey Jin (@patch1t), and an anonymous researcher Dock Available for: macOS Sequoia Impact: An app may be able to modify protected parts of the file system Description: This issue was addressed by removing the vulnerable code. CVE-2025-31187: Rodolphe BRUNETTI (@eisw0lf) of Lupus Nova dyld Available for: macOS Sequoia Impact: Apps that appear to use App Sandbox may be able to launch without restrictions Description: A library injection issue was addressed with additional restrictions. CVE-2025-30462: Pietro Francesco Tirenna, Davide Silvetti, Abdel Adim Oisfi of Shielder (shielder.com) FaceTime Available for: macOS Sequoia Impact: An app may be able to access sensitive user data Description: This issue was addressed with improved redaction of sensitive information. CVE-2025-30451: Kirin (@Pwnrin) and luckyu (@uuulucky) FeedbackLogger Available for: macOS Sequoia Impact: An app may be able to access sensitive user data Description: This issue was addressed with improved data protection. CVE-2025-24281: Rodolphe BRUNETTI (@eisw0lf) Focus Available for: macOS Sequoia Impact: An attacker with physical access to a locked device may be able to view sensitive user information Description: The issue was addressed with improved checks. CVE-2025-30439: Andr.Ess Focus Available for: macOS Sequoia Impact: An app may be able to access sensitive user data Description: A logging issue was addressed with improved data redaction. CVE-2025-24283: Kirin (@Pwnrin) Foundation Available for: macOS Sequoia Impact: An app may be able to access protected user data Description: An access issue was addressed with additional sandbox restrictions on the system pasteboards. CVE-2025-30461: an anonymous researcher Foundation Available for: macOS Sequoia Impact: An app may be able to access sensitive user data Description: The issue was resolved by sanitizing logging CVE-2025-30447: LFY@secsys from Fudan University Foundation Available for: macOS Sequoia Impact: An app may be able to cause a denial-of-service Description: An uncontrolled format string issue was addressed with improved input validation. CVE-2025-24199: Manuel Fernandez (Stackhopper Security) GPU Drivers Available for: macOS Sequoia Impact: An app may be able to cause unexpected system termination or corrupt kernel memory Description: An out-of-bounds write issue was addressed with improved bounds checking. CVE-2025-30464: ABC Research s.r.o. CVE-2025-24273: Wang Yu of Cyberserval GPU Drivers Available for: macOS Sequoia Impact: An app may be able to disclose kernel memory Description: The issue was addressed with improved bounds checks. CVE-2025-24256: Anonymous working with Trend Micro Zero Day Initiative, Murray Mike Handoff Available for: macOS Sequoia Impact: An app may be able to access sensitive user data Description: The issue was addressed with improved restriction of data container access. CVE-2025-30463: mzzzz__ ImageIO Available for: macOS Sequoia Impact: Parsing an image may lead to disclosure of user information Description: A logic error was addressed with improved error handling. CVE-2025-24210: Anonymous working with Trend Micro Zero Day Initiative Installer Available for: macOS Sequoia Impact: An app may be able to check the existence of an arbitrary path on the file system Description: A permissions issue was addressed with additional sandbox restrictions. CVE-2025-24249: YingQi Shi(@Mas0nShi) of DBAppSecurity's WeBin lab and Minghao Lin (@Y1nKoc) Installer Available for: macOS Sequoia Impact: A sandboxed app may be able to access sensitive user data Description: A logic issue was addressed with improved checks. CVE-2025-24229: an anonymous researcher IOGPUFamily Available for: macOS Sequoia Impact: An app may be able to cause unexpected system termination or write kernel memory Description: An out-of-bounds write issue was addressed with improved input validation. CVE-2025-24257: Wang Yu of Cyberserval IOMobileFrameBuffer Available for: macOS Sequoia Impact: An app may be able to corrupt coprocessor memory Description: The issue was addressed with improved bounds checks. CVE-2025-30437: Ye Zhang (@VAR10CK) of Baidu Security Kerberos Helper Available for: macOS Sequoia Impact: A remote attacker may be able to cause unexpected app termination or heap corruption Description: A memory initialization issue was addressed with improved memory handling. CVE-2025-24235: Dave G. Kernel Available for: macOS Sequoia Impact: An app may be able to access protected user data Description: The issue was addressed with improved checks. CVE-2025-24204: Koh M. Nakagawa (@tsunek0h) of FFRI Security, Inc. Kernel Available for: macOS Sequoia Impact: An app may be able to modify protected parts of the file system Description: The issue was addressed with improved checks. CVE-2025-24203: Ian Beer of Google Project Zero Kernel Available for: macOS Sequoia Impact: An attacker with user privileges may be able to read kernel memory Description: A type confusion issue was addressed with improved memory handling. CVE-2025-24196: Joseph Ravichandran (@0xjprx) of MIT CSAIL LaunchServices Available for: macOS Sequoia Impact: A malicious JAR file may bypass Gatekeeper checks Description: This issue was addressed with improved handling of executable types. CVE-2025-24148: Kenneth Chew libarchive Available for: macOS Sequoia Impact: An input validation issue was addressed Description: This is a vulnerability in open source code and Apple Software is among the affected projects. The CVE-ID was assigned by a third party. Learn more about the issue and CVE-ID at cve.org. CVE-2024-48958 Libinfo Available for: macOS Sequoia Impact: A user may be able to elevate privileges Description: An integer overflow was addressed with improved input validation. CVE-2025-24195: Paweł Płatek (Trail of Bits) libnetcore Available for: macOS Sequoia Impact: Processing maliciously crafted web content may result in the disclosure of process memory Description: A logic issue was addressed with improved checks. CVE-2025-24194: an anonymous researcher libxml2 Available for: macOS Sequoia Impact: Parsing a file may lead to an unexpected app termination Description: This is a vulnerability in open source code and Apple Software is among the affected projects. The CVE-ID was assigned by a third party. Learn more about the issue and CVE-ID at cve.org. CVE-2025-27113 CVE-2024-56171 libxpc Available for: macOS Sequoia Impact: An app may be able to break out of its sandbox Description: This issue was addressed through improved state management. CVE-2025-24178: an anonymous researcher libxpc Available for: macOS Sequoia Impact: An app may be able to delete files for which it does not have permission Description: This issue was addressed with improved handling of symlinks. CVE-2025-31182: Alex Radocea and Dave G. of Supernetworks, 风沐云烟(@binary_fmyy) and Minghao Lin(@Y1nKoc) libxpc Available for: macOS Sequoia Impact: An app may be able to gain elevated privileges Description: A logic issue was addressed with improved checks. CVE-2025-24238: an anonymous researcher Mail Available for: macOS Sequoia Impact: "Block All Remote Content" may not apply for all mail previews Description: A permissions issue was addressed with additional sandbox restrictions. CVE-2025-24172: an anonymous researcher manpages Available for: macOS Sequoia Impact: An app may be able to access sensitive user data Description: This issue was addressed with improved validation of symlinks. CVE-2025-30450: Pwn2car Maps Available for: macOS Sequoia Impact: An app may be able to read sensitive location information Description: A path handling issue was addressed with improved logic. CVE-2025-30470: LFY@secsys from Fudan University NetworkExtension Available for: macOS Sequoia Impact: An app may be able to enumerate a user's installed apps Description: This issue was addressed with additional entitlement checks. CVE-2025-30426: Jimmy Notes Available for: macOS Sequoia Impact: A sandboxed app may be able to access sensitive user data in system logs Description: A privacy issue was addressed with improved private data redaction for log entries. CVE-2025-24262: LFY@secsys from Fudan University NSDocument Available for: macOS Sequoia Impact: A malicious app may be able to access arbitrary files Description: This issue was addressed through improved state management. CVE-2025-24232: an anonymous researcher OpenSSH Available for: macOS Sequoia Impact: An app may be able to access user-sensitive data Description: An injection issue was addressed with improved validation. CVE-2025-24246: Mickey Jin (@patch1t) PackageKit Available for: macOS Sequoia Impact: An app may be able to modify protected parts of the file system Description: The issue was addressed with improved checks. CVE-2025-24261: Mickey Jin (@patch1t) PackageKit Available for: macOS Sequoia Impact: An app may be able to modify protected parts of the file system Description: A logic issue was addressed with improved checks. CVE-2025-24164: Mickey Jin (@patch1t) PackageKit Available for: macOS Sequoia Impact: A malicious app with root privileges may be able to modify the contents of system files Description: A permissions issue was addressed with additional restrictions. CVE-2025-30446: Pedro Tôrres (@t0rr3sp3dr0) Parental Controls Available for: macOS Sequoia Impact: An app may be able to retrieve Safari bookmarks without an entitlement check Description: This issue was addressed with additional entitlement checks. CVE-2025-24259: Noah Gregory (wts.dev) Photos Storage Available for: macOS Sequoia Impact: Deleting a conversation in Messages may expose user contact information in system logging Description: A logging issue was addressed with improved data redaction. CVE-2025-30424: an anonymous researcher Power Services Available for: macOS Sequoia Impact: An app may be able to break out of its sandbox Description: This issue was addressed with additional entitlement checks. CVE-2025-24173: Mickey Jin (@patch1t) Python Available for: macOS Sequoia Impact: A remote attacker may be able to bypass sender policy checks and deliver malicious content via email Description: This is a vulnerability in open source code and Apple Software is among the affected projects. The CVE-ID was assigned by a third party. Learn more about the issue and CVE-ID at cve.org. CVE-2023-27043 RPAC Available for: macOS Sequoia Impact: An app may be able to modify protected parts of the file system Description: The issue was addressed with improved validation of environment variables. CVE-2025-24191: Claudio Bozzato and Francesco Benvenuto of Cisco Talos Safari Available for: macOS Sequoia Impact: Visiting a malicious website may lead to user interface spoofing Description: The issue was addressed with improved UI. CVE-2025-24113: @RenwaX23 Safari Available for: macOS Sequoia Impact: Visiting a malicious website may lead to address bar spoofing Description: The issue was addressed with improved checks. CVE-2025-30467: @RenwaX23 Safari Available for: macOS Sequoia Impact: A website may be able to access sensor information without user consent Description: The issue was addressed with improved checks. CVE-2025-31192: Jaydev Ahire Safari Available for: macOS Sequoia Impact: A download's origin may be incorrectly associated Description: This issue was addressed through improved state management. CVE-2025-24167: Syarif Muhammad Sajjad Sandbox Available for: macOS Sequoia Impact: An app may be able to access removable volumes without user consent Description: A permissions issue was addressed with additional restrictions. CVE-2025-24093: Yiğit Can YILMAZ (@yilmazcanyigit) Sandbox Available for: macOS Sequoia Impact: An input validation issue was addressed Description: The issue was addressed with improved checks. CVE-2025-30452: an anonymous researcher Sandbox Available for: macOS Sequoia Impact: An app may be able to access protected user data Description: A permissions issue was addressed with additional restrictions. CVE-2025-24181: Arsenii Kostromin (0x3c3e) SceneKit Available for: macOS Sequoia Impact: An app may be able to read files outside of its sandbox Description: A permissions issue was addressed with additional restrictions. CVE-2025-30458: Mickey Jin (@patch1t) Security Available for: macOS Sequoia Impact: A remote user may be able to cause a denial-of-service Description: A validation issue was addressed with improved logic. CVE-2025-30471: Bing Shi, Wenchao Li, Xiaolong Bai of Alibaba Group, Luyi Xing of Indiana University Bloomington Security Available for: macOS Sequoia Impact: A malicious app acting as a HTTPS proxy could get access to sensitive user data Description: This issue was addressed with improved access restrictions. CVE-2025-24250: Wojciech Regula of SecuRing (wojciechregula.blog) Share Sheet Available for: macOS Sequoia Impact: A malicious app may be able to dismiss the system notification on the Lock Screen that a recording was started Description: This issue was addressed with improved access restrictions. CVE-2025-30438: Halle Winkler, Politepix theoffcuts.org Shortcuts Available for: macOS Sequoia Impact: A shortcut may be able to access files that are normally inaccessible to the Shortcuts app Description: A permissions issue was addressed with improved validation. CVE-2025-30465: an anonymous researcher Shortcuts Available for: macOS Sequoia Impact: An app may be able to access user-sensitive data Description: An access issue was addressed with additional sandbox restrictions. CVE-2025-24280: Kirin (@Pwnrin) Shortcuts Available for: macOS Sequoia Impact: A Shortcut may run with admin privileges without authentication Description: An authentication issue was addressed with improved state management. CVE-2025-31194: Dolf Hoegaerts Shortcuts Available for: macOS Sequoia Impact: A shortcut may be able to access files that are normally inaccessible to the Shortcuts app Description: This issue was addressed with improved access restrictions. CVE-2025-30433: Andrew James Gonzalez Siri Available for: macOS Sequoia Impact: An app may be able to access sensitive user data Description: The issue was addressed with improved restriction of data container access. CVE-2025-31183: Kirin (@Pwnrin), Bohdan Stasiuk (@bohdan_stasiuk) Siri Available for: macOS Sequoia Impact: A sandboxed app may be able to access sensitive user data in system logs Description: This issue was addressed with improved redaction of sensitive information. CVE-2025-30435: K宝 (@Pwnrin) and luckyu (@uuulucky) Siri Available for: macOS Sequoia Impact: An app may be able to access sensitive user data Description: This issue was addressed with improved redaction of sensitive information. CVE-2025-24217: Kirin (@Pwnrin) Siri Available for: macOS Sequoia Impact: An app may be able to access sensitive user data Description: A privacy issue was addressed by not logging contents of text fields. CVE-2025-24214: Kirin (@Pwnrin) Siri Available for: macOS Sequoia Impact: An app may be able to enumerate devices that have signed into the user's Apple Account Description: A permissions issue was addressed with additional restrictions. CVE-2025-24248: Minghao Lin (@Y1nKoc) and Tong Liu@Lyutoon_ and 风(binary_fmyy) and F00L Siri Available for: macOS Sequoia Impact: An app may be able to access user-sensitive data Description: An authorization issue was addressed with improved state management. CVE-2025-24205: YingQi Shi(@Mas0nShi) of DBAppSecurity's WeBin lab and Minghao Lin (@Y1nKoc) Siri Available for: macOS Sequoia Impact: An attacker with physical access may be able to use Siri to access sensitive user data Description: This issue was addressed by restricting options offered on a locked device. CVE-2025-24198: Richard Hyunho Im (@richeeta) with routezero.security SMB Available for: macOS Sequoia Impact: An app may be able to cause unexpected system termination Description: The issue was addressed with improved memory handling. CVE-2025-24269: Alex Radocea of Supernetworks SMB Available for: macOS Sequoia Impact: Mounting a maliciously crafted SMB network share may lead to system termination Description: A race condition was addressed with improved locking. CVE-2025-30444: Dave G. SMB Available for: macOS Sequoia Impact: An app may be able to execute arbitrary code with kernel privileges Description: A buffer overflow issue was addressed with improved memory handling. CVE-2025-24228: Joseph Ravichandran (@0xjprx) of MIT CSAIL smbx Available for: macOS Sequoia Impact: An attacker in a privileged position may be able to perform a denial-of-service Description: The issue was addressed with improved memory handling. CVE-2025-24260: zbleet of QI-ANXIN TianGong Team Software Update Available for: macOS Sequoia Impact: An app may be able to modify protected parts of the file system Description: A library injection issue was addressed with additional restrictions. CVE-2025-24282: Claudio Bozzato and Francesco Benvenuto of Cisco Talos Software Update Available for: macOS Sequoia Impact: A user may be able to elevate privileges Description: This issue was addressed with improved validation of symlinks. CVE-2025-24254: Arsenii Kostromin (0x3c3e) Software Update Available for: macOS Sequoia Impact: An app may be able to modify protected parts of the file system Description: The issue was addressed with improved checks. CVE-2025-24231: Claudio Bozzato and Francesco Benvenuto of Cisco Talos StickerKit Available for: macOS Sequoia Impact: An app may be able to observe unprotected user data Description: A privacy issue was addressed by moving sensitive data to a protected location. CVE-2025-24263: Cristian Dinca of "Tudor Vianu" National High School of Computer Science, Romania Storage Management Available for: macOS Sequoia Impact: An app may be able to enable iCloud storage features without user consent Description: A permissions issue was addressed with additional restrictions. CVE-2025-24207: YingQi Shi (@Mas0nShi) of DBAppSecurity's WeBin lab, 风沐云烟 (binary_fmyy) and Minghao Lin (@Y1nKoc) StorageKit Available for: macOS Sequoia Impact: An app may be able to gain root privileges Description: A permissions issue was addressed with additional restrictions. CVE-2025-30449: Arsenii Kostromin (0x3c3e), and an anonymous researcher StorageKit Available for: macOS Sequoia Impact: An app may be able to access protected user data Description: This issue was addressed with improved handling of symlinks. CVE-2025-24253: Mickey Jin (@patch1t), Csaba Fitzl (@theevilbit) of Kandji StorageKit Available for: macOS Sequoia Impact: An app may be able to access user-sensitive data Description: A race condition was addressed with additional validation. CVE-2025-24240: Mickey Jin (@patch1t) StorageKit Available for: macOS Sequoia Impact: An app may be able to bypass Privacy preferences Description: A race condition was addressed with additional validation. CVE-2025-31188: Mickey Jin (@patch1t) Summarization Services Available for: macOS Sequoia Impact: An app may be able to access information about a user's contacts Description: A privacy issue was addressed with improved private data redaction for log entries. CVE-2025-24218: Kirin and FlowerCode, Bohdan Stasiuk (@bohdan_stasiuk) System Settings Available for: macOS Sequoia Impact: An app may be able to access protected user data Description: This issue was addressed with improved validation of symlinks. CVE-2025-24278: Zhongquan Li (@Guluisacat) System Settings Available for: macOS Sequoia Impact: An app with root privileges may be able to access private information Description: This issue was addressed with improved handling of symlinks. CVE-2025-24242: Koh M. Nakagawa (@tsunek0h) of FFRI Security, Inc. SystemMigration Available for: macOS Sequoia Impact: A malicious app may be able to create symlinks to protected regions of the disk Description: This issue was addressed with improved validation of symlinks. CVE-2025-30457: Mickey Jin (@patch1t) Voice Control Available for: macOS Sequoia Impact: An app may be able to access contacts Description: This issue was addressed with improved file handling. CVE-2025-24279: Mickey Jin (@patch1t) Web Extensions Available for: macOS Sequoia Impact: An app may gain unauthorized access to Local Network Description: This issue was addressed with improved permissions checking. CVE-2025-31184: Alexander Heinrich (@Sn0wfreeze), SEEMOO, TU Darmstadt & Mathy Vanhoef (@vanhoefm) and Jeroen Robben (@RobbenJeroen), DistriNet, KU Leuven Web Extensions Available for: macOS Sequoia Impact: Visiting a website may leak sensitive data Description: A script imports issue was addressed with improved isolation. CVE-2025-24192: Vsevolod Kokorin (Slonser) of Solidlab WebKit Available for: macOS Sequoia Impact: Processing maliciously crafted web content may lead to an unexpected Safari crash Description: The issue was addressed with improved memory handling. WebKit Bugzilla: 285892 CVE-2025-24264: Gary Kwong, and an anonymous researcher WebKit Bugzilla: 284055 CVE-2025-24216: Paul Bakker of ParagonERP WebKit Available for: macOS Sequoia Impact: A type confusion issue could lead to memory corruption Description: This issue was addressed with improved handling of floats. WebKit Bugzilla: 286694 CVE-2025-24213: Google V8 Security Team WebKit Available for: macOS Sequoia Impact: Processing maliciously crafted web content may lead to an unexpected process crash Description: A buffer overflow issue was addressed with improved memory handling. WebKit Bugzilla: 286462 CVE-2025-24209: Francisco Alonso (@revskills), and an anonymous researcher WebKit Available for: macOS Sequoia Impact: Processing maliciously crafted web content may lead to an unexpected Safari crash Description: A use-after-free issue was addressed with improved memory management. WebKit Bugzilla: 285643 CVE-2025-30427: rheza (@ginggilBesel) WebKit Available for: macOS Sequoia Impact: A malicious website may be able to track users in Safari private browsing mode Description: This issue was addressed through improved state management. WebKit Bugzilla: 286580 CVE-2025-30425: an anonymous researcher WindowServer Available for: macOS Sequoia Impact: An attacker may be able to cause unexpected app termination Description: A type confusion issue was addressed with improved checks. CVE-2025-24247: PixiePoint Security WindowServer Available for: macOS Sequoia Impact: An app may be able to trick a user into copying sensitive data to the pasteboard Description: A configuration issue was addressed with additional restrictions. CVE-2025-24241: Andreas Hegenberg (folivora.AI GmbH) Xsan Available for: macOS Sequoia Impact: An app may be able to cause unexpected system termination Description: A buffer overflow was addressed with improved bounds checking. CVE-2025-24266: an anonymous researcher Xsan Available for: macOS Sequoia Impact: An app may be able to cause unexpected system termination Description: An out-of-bounds read was addressed with improved bounds checking. CVE-2025-24265: an anonymous researcher Xsan Available for: macOS Sequoia Impact: An app may be able to cause unexpected system termination or corrupt kernel memory Description: A buffer overflow issue was addressed with improved memory handling. CVE-2025-24157: an anonymous researcher
@ 17538dc2:71ed77c4
2025-04-02 16:04:59The MacOS security update summary is a reminder that laptops and desktops are incredibly compromised. ### macOS Sequoia 15.4 Released March 31, 2025 Accessibility Available for: macOS Sequoia Impact: An app may be able to access sensitive user data Description: A logging issue was addressed with improved data redaction. CVE-2025-24202: Zhongcheng Li from IES Red Team of ByteDance AccountPolicy Available for: macOS Sequoia Impact: A malicious app may be able to gain root privileges Description: This issue was addressed by removing the vulnerable code. CVE-2025-24234: an anonymous researcher AirDrop Available for: macOS Sequoia Impact: An app may be able to read arbitrary file metadata Description: A permissions issue was addressed with additional restrictions. CVE-2025-24097: Ron Masas of BREAKPOINT.SH App Store Available for: macOS Sequoia Impact: A malicious app may be able to access private information Description: This issue was addressed by removing the vulnerable code. CVE-2025-24276: an anonymous researcher AppleMobileFileIntegrity Available for: macOS Sequoia Impact: An app may be able to modify protected parts of the file system Description: The issue was addressed with improved checks. CVE-2025-24272: Mickey Jin (@patch1t) AppleMobileFileIntegrity Available for: macOS Sequoia Impact: An app may be able to access protected user data Description: A downgrade issue was addressed with additional code-signing restrictions. CVE-2025-24239: Wojciech Regula of SecuRing (wojciechregula.blog) AppleMobileFileIntegrity Available for: macOS Sequoia Impact: A malicious app may be able to read or write to protected files Description: A permissions issue was addressed with additional restrictions. CVE-2025-24233: Claudio Bozzato and Francesco Benvenuto of Cisco Talos. AppleMobileFileIntegrity Available for: macOS Sequoia Impact: An app may be able to access user-sensitive data Description: A privacy issue was addressed by removing the vulnerable code. CVE-2025-30443: Bohdan Stasiuk (@bohdan_stasiuk) Audio Available for: macOS Sequoia Impact: Processing a maliciously crafted font may result in the disclosure of process memory Description: The issue was addressed with improved memory handling. CVE-2025-24244: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative Audio Available for: macOS Sequoia Impact: Processing a maliciously crafted file may lead to arbitrary code execution Description: The issue was addressed with improved memory handling. CVE-2025-24243: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative Authentication Services Available for: macOS Sequoia Impact: Password autofill may fill in passwords after failing authentication Description: This issue was addressed through improved state management. CVE-2025-30430: Dominik Rath Authentication Services Available for: macOS Sequoia Impact: A malicious website may be able to claim WebAuthn credentials from another website that shares a registrable suffix Description: The issue was addressed with improved input validation. CVE-2025-24180: Martin Kreichgauer of Google Chrome Authentication Services Available for: macOS Sequoia Impact: A malicious app may be able to access a user's saved passwords Description: This issue was addressed by adding a delay between verification code attempts. CVE-2025-24245: Ian Mckay (@iann0036) Automator Available for: macOS Sequoia Impact: An app may be able to access protected user data Description: A permissions issue was addressed by removing vulnerable code and adding additional checks. CVE-2025-30460: an anonymous researcher BiometricKit Available for: macOS Sequoia Impact: An app may be able to cause unexpected system termination Description: A buffer overflow was addressed with improved bounds checking. CVE-2025-24237: Yutong Xiu Calendar Available for: macOS Sequoia Impact: An app may be able to break out of its sandbox Description: A path handling issue was addressed with improved validation. CVE-2025-30429: Denis Tokarev (@illusionofcha0s) Calendar Available for: macOS Sequoia Impact: An app may be able to break out of its sandbox Description: This issue was addressed with improved checks. CVE-2025-24212: Denis Tokarev (@illusionofcha0s) CloudKit Available for: macOS Sequoia Impact: A malicious app may be able to access private information Description: The issue was addressed with improved checks. CVE-2025-24215: Kirin (@Pwnrin) CoreAudio Available for: macOS Sequoia Impact: Parsing a file may lead to an unexpected app termination Description: The issue was addressed with improved checks. CVE-2025-24163: Google Threat Analysis Group CoreAudio Available for: macOS Sequoia Impact: Playing a malicious audio file may lead to an unexpected app termination Description: An out-of-bounds read issue was addressed with improved input validation. CVE-2025-24230: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative CoreMedia Available for: macOS Sequoia Impact: Processing a maliciously crafted video file may lead to unexpected app termination or corrupt process memory Description: This issue was addressed with improved memory handling. CVE-2025-24211: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative CoreMedia Available for: macOS Sequoia Impact: An app may be able to access sensitive user data Description: An access issue was addressed with additional sandbox restrictions. CVE-2025-24236: Csaba Fitzl (@theevilbit) and Nolan Astrein of Kandji CoreMedia Available for: macOS Sequoia Impact: Processing a maliciously crafted video file may lead to unexpected app termination or corrupt process memory Description: The issue was addressed with improved memory handling. CVE-2025-24190: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative CoreMedia Playback Available for: macOS Sequoia Impact: A malicious app may be able to access private information Description: A path handling issue was addressed with improved validation. CVE-2025-30454: pattern-f (@pattern_F_) CoreServices Description: This issue was addressed through improved state management. CVE-2025-31191: Jonathan Bar Or (@yo_yo_yo_jbo) of Microsoft, and an anonymous researcher Available for: macOS Sequoia Impact: An app may be able to access sensitive user data CoreText Available for: macOS Sequoia Impact: Processing a maliciously crafted font may result in the disclosure of process memory Description: An out-of-bounds read issue was addressed with improved input validation. CVE-2025-24182: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative Crash Reporter Available for: macOS Sequoia Impact: An app may be able to gain root privileges Description: A parsing issue in the handling of directory paths was addressed with improved path validation. CVE-2025-24277: Csaba Fitzl (@theevilbit) of Kandji and Gergely Kalman (@gergely_kalman), and an anonymous researcher curl Available for: macOS Sequoia Impact: An input validation issue was addressed Description: This is a vulnerability in open source code and Apple Software is among the affected projects. The CVE-ID was assigned by a third party. Learn more about the issue and CVE-ID at cve.org. CVE-2024-9681 Disk Images Available for: macOS Sequoia Impact: An app may be able to break out of its sandbox Description: A file access issue was addressed with improved input validation. CVE-2025-24255: an anonymous researcher DiskArbitration Available for: macOS Sequoia Impact: An app may be able to gain root privileges Description: A parsing issue in the handling of directory paths was addressed with improved path validation. CVE-2025-30456: Gergely Kalman (@gergely_kalman) DiskArbitration Available for: macOS Sequoia Impact: An app may be able to gain root privileges Description: A permissions issue was addressed with additional restrictions. CVE-2025-24267: an anonymous researcher Dock Available for: macOS Sequoia Impact: A malicious app may be able to access private information Description: The issue was addressed with improved checks. CVE-2025-30455: Mickey Jin (@patch1t), and an anonymous researcher Dock Available for: macOS Sequoia Impact: An app may be able to modify protected parts of the file system Description: This issue was addressed by removing the vulnerable code. CVE-2025-31187: Rodolphe BRUNETTI (@eisw0lf) of Lupus Nova dyld Available for: macOS Sequoia Impact: Apps that appear to use App Sandbox may be able to launch without restrictions Description: A library injection issue was addressed with additional restrictions. CVE-2025-30462: Pietro Francesco Tirenna, Davide Silvetti, Abdel Adim Oisfi of Shielder (shielder.com) FaceTime Available for: macOS Sequoia Impact: An app may be able to access sensitive user data Description: This issue was addressed with improved redaction of sensitive information. CVE-2025-30451: Kirin (@Pwnrin) and luckyu (@uuulucky) FeedbackLogger Available for: macOS Sequoia Impact: An app may be able to access sensitive user data Description: This issue was addressed with improved data protection. CVE-2025-24281: Rodolphe BRUNETTI (@eisw0lf) Focus Available for: macOS Sequoia Impact: An attacker with physical access to a locked device may be able to view sensitive user information Description: The issue was addressed with improved checks. CVE-2025-30439: Andr.Ess Focus Available for: macOS Sequoia Impact: An app may be able to access sensitive user data Description: A logging issue was addressed with improved data redaction. CVE-2025-24283: Kirin (@Pwnrin) Foundation Available for: macOS Sequoia Impact: An app may be able to access protected user data Description: An access issue was addressed with additional sandbox restrictions on the system pasteboards. CVE-2025-30461: an anonymous researcher Foundation Available for: macOS Sequoia Impact: An app may be able to access sensitive user data Description: The issue was resolved by sanitizing logging CVE-2025-30447: LFY@secsys from Fudan University Foundation Available for: macOS Sequoia Impact: An app may be able to cause a denial-of-service Description: An uncontrolled format string issue was addressed with improved input validation. CVE-2025-24199: Manuel Fernandez (Stackhopper Security) GPU Drivers Available for: macOS Sequoia Impact: An app may be able to cause unexpected system termination or corrupt kernel memory Description: An out-of-bounds write issue was addressed with improved bounds checking. CVE-2025-30464: ABC Research s.r.o. CVE-2025-24273: Wang Yu of Cyberserval GPU Drivers Available for: macOS Sequoia Impact: An app may be able to disclose kernel memory Description: The issue was addressed with improved bounds checks. CVE-2025-24256: Anonymous working with Trend Micro Zero Day Initiative, Murray Mike Handoff Available for: macOS Sequoia Impact: An app may be able to access sensitive user data Description: The issue was addressed with improved restriction of data container access. CVE-2025-30463: mzzzz__ ImageIO Available for: macOS Sequoia Impact: Parsing an image may lead to disclosure of user information Description: A logic error was addressed with improved error handling. CVE-2025-24210: Anonymous working with Trend Micro Zero Day Initiative Installer Available for: macOS Sequoia Impact: An app may be able to check the existence of an arbitrary path on the file system Description: A permissions issue was addressed with additional sandbox restrictions. CVE-2025-24249: YingQi Shi(@Mas0nShi) of DBAppSecurity's WeBin lab and Minghao Lin (@Y1nKoc) Installer Available for: macOS Sequoia Impact: A sandboxed app may be able to access sensitive user data Description: A logic issue was addressed with improved checks. CVE-2025-24229: an anonymous researcher IOGPUFamily Available for: macOS Sequoia Impact: An app may be able to cause unexpected system termination or write kernel memory Description: An out-of-bounds write issue was addressed with improved input validation. CVE-2025-24257: Wang Yu of Cyberserval IOMobileFrameBuffer Available for: macOS Sequoia Impact: An app may be able to corrupt coprocessor memory Description: The issue was addressed with improved bounds checks. CVE-2025-30437: Ye Zhang (@VAR10CK) of Baidu Security Kerberos Helper Available for: macOS Sequoia Impact: A remote attacker may be able to cause unexpected app termination or heap corruption Description: A memory initialization issue was addressed with improved memory handling. CVE-2025-24235: Dave G. Kernel Available for: macOS Sequoia Impact: An app may be able to access protected user data Description: The issue was addressed with improved checks. CVE-2025-24204: Koh M. Nakagawa (@tsunek0h) of FFRI Security, Inc. Kernel Available for: macOS Sequoia Impact: An app may be able to modify protected parts of the file system Description: The issue was addressed with improved checks. CVE-2025-24203: Ian Beer of Google Project Zero Kernel Available for: macOS Sequoia Impact: An attacker with user privileges may be able to read kernel memory Description: A type confusion issue was addressed with improved memory handling. CVE-2025-24196: Joseph Ravichandran (@0xjprx) of MIT CSAIL LaunchServices Available for: macOS Sequoia Impact: A malicious JAR file may bypass Gatekeeper checks Description: This issue was addressed with improved handling of executable types. CVE-2025-24148: Kenneth Chew libarchive Available for: macOS Sequoia Impact: An input validation issue was addressed Description: This is a vulnerability in open source code and Apple Software is among the affected projects. The CVE-ID was assigned by a third party. Learn more about the issue and CVE-ID at cve.org. CVE-2024-48958 Libinfo Available for: macOS Sequoia Impact: A user may be able to elevate privileges Description: An integer overflow was addressed with improved input validation. CVE-2025-24195: Paweł Płatek (Trail of Bits) libnetcore Available for: macOS Sequoia Impact: Processing maliciously crafted web content may result in the disclosure of process memory Description: A logic issue was addressed with improved checks. CVE-2025-24194: an anonymous researcher libxml2 Available for: macOS Sequoia Impact: Parsing a file may lead to an unexpected app termination Description: This is a vulnerability in open source code and Apple Software is among the affected projects. The CVE-ID was assigned by a third party. Learn more about the issue and CVE-ID at cve.org. CVE-2025-27113 CVE-2024-56171 libxpc Available for: macOS Sequoia Impact: An app may be able to break out of its sandbox Description: This issue was addressed through improved state management. CVE-2025-24178: an anonymous researcher libxpc Available for: macOS Sequoia Impact: An app may be able to delete files for which it does not have permission Description: This issue was addressed with improved handling of symlinks. CVE-2025-31182: Alex Radocea and Dave G. of Supernetworks, 风沐云烟(@binary_fmyy) and Minghao Lin(@Y1nKoc) libxpc Available for: macOS Sequoia Impact: An app may be able to gain elevated privileges Description: A logic issue was addressed with improved checks. CVE-2025-24238: an anonymous researcher Mail Available for: macOS Sequoia Impact: "Block All Remote Content" may not apply for all mail previews Description: A permissions issue was addressed with additional sandbox restrictions. CVE-2025-24172: an anonymous researcher manpages Available for: macOS Sequoia Impact: An app may be able to access sensitive user data Description: This issue was addressed with improved validation of symlinks. CVE-2025-30450: Pwn2car Maps Available for: macOS Sequoia Impact: An app may be able to read sensitive location information Description: A path handling issue was addressed with improved logic. CVE-2025-30470: LFY@secsys from Fudan University NetworkExtension Available for: macOS Sequoia Impact: An app may be able to enumerate a user's installed apps Description: This issue was addressed with additional entitlement checks. CVE-2025-30426: Jimmy Notes Available for: macOS Sequoia Impact: A sandboxed app may be able to access sensitive user data in system logs Description: A privacy issue was addressed with improved private data redaction for log entries. CVE-2025-24262: LFY@secsys from Fudan University NSDocument Available for: macOS Sequoia Impact: A malicious app may be able to access arbitrary files Description: This issue was addressed through improved state management. CVE-2025-24232: an anonymous researcher OpenSSH Available for: macOS Sequoia Impact: An app may be able to access user-sensitive data Description: An injection issue was addressed with improved validation. CVE-2025-24246: Mickey Jin (@patch1t) PackageKit Available for: macOS Sequoia Impact: An app may be able to modify protected parts of the file system Description: The issue was addressed with improved checks. CVE-2025-24261: Mickey Jin (@patch1t) PackageKit Available for: macOS Sequoia Impact: An app may be able to modify protected parts of the file system Description: A logic issue was addressed with improved checks. CVE-2025-24164: Mickey Jin (@patch1t) PackageKit Available for: macOS Sequoia Impact: A malicious app with root privileges may be able to modify the contents of system files Description: A permissions issue was addressed with additional restrictions. CVE-2025-30446: Pedro Tôrres (@t0rr3sp3dr0) Parental Controls Available for: macOS Sequoia Impact: An app may be able to retrieve Safari bookmarks without an entitlement check Description: This issue was addressed with additional entitlement checks. CVE-2025-24259: Noah Gregory (wts.dev) Photos Storage Available for: macOS Sequoia Impact: Deleting a conversation in Messages may expose user contact information in system logging Description: A logging issue was addressed with improved data redaction. CVE-2025-30424: an anonymous researcher Power Services Available for: macOS Sequoia Impact: An app may be able to break out of its sandbox Description: This issue was addressed with additional entitlement checks. CVE-2025-24173: Mickey Jin (@patch1t) Python Available for: macOS Sequoia Impact: A remote attacker may be able to bypass sender policy checks and deliver malicious content via email Description: This is a vulnerability in open source code and Apple Software is among the affected projects. The CVE-ID was assigned by a third party. Learn more about the issue and CVE-ID at cve.org. CVE-2023-27043 RPAC Available for: macOS Sequoia Impact: An app may be able to modify protected parts of the file system Description: The issue was addressed with improved validation of environment variables. CVE-2025-24191: Claudio Bozzato and Francesco Benvenuto of Cisco Talos Safari Available for: macOS Sequoia Impact: Visiting a malicious website may lead to user interface spoofing Description: The issue was addressed with improved UI. CVE-2025-24113: @RenwaX23 Safari Available for: macOS Sequoia Impact: Visiting a malicious website may lead to address bar spoofing Description: The issue was addressed with improved checks. CVE-2025-30467: @RenwaX23 Safari Available for: macOS Sequoia Impact: A website may be able to access sensor information without user consent Description: The issue was addressed with improved checks. CVE-2025-31192: Jaydev Ahire Safari Available for: macOS Sequoia Impact: A download's origin may be incorrectly associated Description: This issue was addressed through improved state management. CVE-2025-24167: Syarif Muhammad Sajjad Sandbox Available for: macOS Sequoia Impact: An app may be able to access removable volumes without user consent Description: A permissions issue was addressed with additional restrictions. CVE-2025-24093: Yiğit Can YILMAZ (@yilmazcanyigit) Sandbox Available for: macOS Sequoia Impact: An input validation issue was addressed Description: The issue was addressed with improved checks. CVE-2025-30452: an anonymous researcher Sandbox Available for: macOS Sequoia Impact: An app may be able to access protected user data Description: A permissions issue was addressed with additional restrictions. CVE-2025-24181: Arsenii Kostromin (0x3c3e) SceneKit Available for: macOS Sequoia Impact: An app may be able to read files outside of its sandbox Description: A permissions issue was addressed with additional restrictions. CVE-2025-30458: Mickey Jin (@patch1t) Security Available for: macOS Sequoia Impact: A remote user may be able to cause a denial-of-service Description: A validation issue was addressed with improved logic. CVE-2025-30471: Bing Shi, Wenchao Li, Xiaolong Bai of Alibaba Group, Luyi Xing of Indiana University Bloomington Security Available for: macOS Sequoia Impact: A malicious app acting as a HTTPS proxy could get access to sensitive user data Description: This issue was addressed with improved access restrictions. CVE-2025-24250: Wojciech Regula of SecuRing (wojciechregula.blog) Share Sheet Available for: macOS Sequoia Impact: A malicious app may be able to dismiss the system notification on the Lock Screen that a recording was started Description: This issue was addressed with improved access restrictions. CVE-2025-30438: Halle Winkler, Politepix theoffcuts.org Shortcuts Available for: macOS Sequoia Impact: A shortcut may be able to access files that are normally inaccessible to the Shortcuts app Description: A permissions issue was addressed with improved validation. CVE-2025-30465: an anonymous researcher Shortcuts Available for: macOS Sequoia Impact: An app may be able to access user-sensitive data Description: An access issue was addressed with additional sandbox restrictions. CVE-2025-24280: Kirin (@Pwnrin) Shortcuts Available for: macOS Sequoia Impact: A Shortcut may run with admin privileges without authentication Description: An authentication issue was addressed with improved state management. CVE-2025-31194: Dolf Hoegaerts Shortcuts Available for: macOS Sequoia Impact: A shortcut may be able to access files that are normally inaccessible to the Shortcuts app Description: This issue was addressed with improved access restrictions. CVE-2025-30433: Andrew James Gonzalez Siri Available for: macOS Sequoia Impact: An app may be able to access sensitive user data Description: The issue was addressed with improved restriction of data container access. CVE-2025-31183: Kirin (@Pwnrin), Bohdan Stasiuk (@bohdan_stasiuk) Siri Available for: macOS Sequoia Impact: A sandboxed app may be able to access sensitive user data in system logs Description: This issue was addressed with improved redaction of sensitive information. CVE-2025-30435: K宝 (@Pwnrin) and luckyu (@uuulucky) Siri Available for: macOS Sequoia Impact: An app may be able to access sensitive user data Description: This issue was addressed with improved redaction of sensitive information. CVE-2025-24217: Kirin (@Pwnrin) Siri Available for: macOS Sequoia Impact: An app may be able to access sensitive user data Description: A privacy issue was addressed by not logging contents of text fields. CVE-2025-24214: Kirin (@Pwnrin) Siri Available for: macOS Sequoia Impact: An app may be able to enumerate devices that have signed into the user's Apple Account Description: A permissions issue was addressed with additional restrictions. CVE-2025-24248: Minghao Lin (@Y1nKoc) and Tong Liu@Lyutoon_ and 风(binary_fmyy) and F00L Siri Available for: macOS Sequoia Impact: An app may be able to access user-sensitive data Description: An authorization issue was addressed with improved state management. CVE-2025-24205: YingQi Shi(@Mas0nShi) of DBAppSecurity's WeBin lab and Minghao Lin (@Y1nKoc) Siri Available for: macOS Sequoia Impact: An attacker with physical access may be able to use Siri to access sensitive user data Description: This issue was addressed by restricting options offered on a locked device. CVE-2025-24198: Richard Hyunho Im (@richeeta) with routezero.security SMB Available for: macOS Sequoia Impact: An app may be able to cause unexpected system termination Description: The issue was addressed with improved memory handling. CVE-2025-24269: Alex Radocea of Supernetworks SMB Available for: macOS Sequoia Impact: Mounting a maliciously crafted SMB network share may lead to system termination Description: A race condition was addressed with improved locking. CVE-2025-30444: Dave G. SMB Available for: macOS Sequoia Impact: An app may be able to execute arbitrary code with kernel privileges Description: A buffer overflow issue was addressed with improved memory handling. CVE-2025-24228: Joseph Ravichandran (@0xjprx) of MIT CSAIL smbx Available for: macOS Sequoia Impact: An attacker in a privileged position may be able to perform a denial-of-service Description: The issue was addressed with improved memory handling. CVE-2025-24260: zbleet of QI-ANXIN TianGong Team Software Update Available for: macOS Sequoia Impact: An app may be able to modify protected parts of the file system Description: A library injection issue was addressed with additional restrictions. CVE-2025-24282: Claudio Bozzato and Francesco Benvenuto of Cisco Talos Software Update Available for: macOS Sequoia Impact: A user may be able to elevate privileges Description: This issue was addressed with improved validation of symlinks. CVE-2025-24254: Arsenii Kostromin (0x3c3e) Software Update Available for: macOS Sequoia Impact: An app may be able to modify protected parts of the file system Description: The issue was addressed with improved checks. CVE-2025-24231: Claudio Bozzato and Francesco Benvenuto of Cisco Talos StickerKit Available for: macOS Sequoia Impact: An app may be able to observe unprotected user data Description: A privacy issue was addressed by moving sensitive data to a protected location. CVE-2025-24263: Cristian Dinca of "Tudor Vianu" National High School of Computer Science, Romania Storage Management Available for: macOS Sequoia Impact: An app may be able to enable iCloud storage features without user consent Description: A permissions issue was addressed with additional restrictions. CVE-2025-24207: YingQi Shi (@Mas0nShi) of DBAppSecurity's WeBin lab, 风沐云烟 (binary_fmyy) and Minghao Lin (@Y1nKoc) StorageKit Available for: macOS Sequoia Impact: An app may be able to gain root privileges Description: A permissions issue was addressed with additional restrictions. CVE-2025-30449: Arsenii Kostromin (0x3c3e), and an anonymous researcher StorageKit Available for: macOS Sequoia Impact: An app may be able to access protected user data Description: This issue was addressed with improved handling of symlinks. CVE-2025-24253: Mickey Jin (@patch1t), Csaba Fitzl (@theevilbit) of Kandji StorageKit Available for: macOS Sequoia Impact: An app may be able to access user-sensitive data Description: A race condition was addressed with additional validation. CVE-2025-24240: Mickey Jin (@patch1t) StorageKit Available for: macOS Sequoia Impact: An app may be able to bypass Privacy preferences Description: A race condition was addressed with additional validation. CVE-2025-31188: Mickey Jin (@patch1t) Summarization Services Available for: macOS Sequoia Impact: An app may be able to access information about a user's contacts Description: A privacy issue was addressed with improved private data redaction for log entries. CVE-2025-24218: Kirin and FlowerCode, Bohdan Stasiuk (@bohdan_stasiuk) System Settings Available for: macOS Sequoia Impact: An app may be able to access protected user data Description: This issue was addressed with improved validation of symlinks. CVE-2025-24278: Zhongquan Li (@Guluisacat) System Settings Available for: macOS Sequoia Impact: An app with root privileges may be able to access private information Description: This issue was addressed with improved handling of symlinks. CVE-2025-24242: Koh M. Nakagawa (@tsunek0h) of FFRI Security, Inc. SystemMigration Available for: macOS Sequoia Impact: A malicious app may be able to create symlinks to protected regions of the disk Description: This issue was addressed with improved validation of symlinks. CVE-2025-30457: Mickey Jin (@patch1t) Voice Control Available for: macOS Sequoia Impact: An app may be able to access contacts Description: This issue was addressed with improved file handling. CVE-2025-24279: Mickey Jin (@patch1t) Web Extensions Available for: macOS Sequoia Impact: An app may gain unauthorized access to Local Network Description: This issue was addressed with improved permissions checking. CVE-2025-31184: Alexander Heinrich (@Sn0wfreeze), SEEMOO, TU Darmstadt & Mathy Vanhoef (@vanhoefm) and Jeroen Robben (@RobbenJeroen), DistriNet, KU Leuven Web Extensions Available for: macOS Sequoia Impact: Visiting a website may leak sensitive data Description: A script imports issue was addressed with improved isolation. CVE-2025-24192: Vsevolod Kokorin (Slonser) of Solidlab WebKit Available for: macOS Sequoia Impact: Processing maliciously crafted web content may lead to an unexpected Safari crash Description: The issue was addressed with improved memory handling. WebKit Bugzilla: 285892 CVE-2025-24264: Gary Kwong, and an anonymous researcher WebKit Bugzilla: 284055 CVE-2025-24216: Paul Bakker of ParagonERP WebKit Available for: macOS Sequoia Impact: A type confusion issue could lead to memory corruption Description: This issue was addressed with improved handling of floats. WebKit Bugzilla: 286694 CVE-2025-24213: Google V8 Security Team WebKit Available for: macOS Sequoia Impact: Processing maliciously crafted web content may lead to an unexpected process crash Description: A buffer overflow issue was addressed with improved memory handling. WebKit Bugzilla: 286462 CVE-2025-24209: Francisco Alonso (@revskills), and an anonymous researcher WebKit Available for: macOS Sequoia Impact: Processing maliciously crafted web content may lead to an unexpected Safari crash Description: A use-after-free issue was addressed with improved memory management. WebKit Bugzilla: 285643 CVE-2025-30427: rheza (@ginggilBesel) WebKit Available for: macOS Sequoia Impact: A malicious website may be able to track users in Safari private browsing mode Description: This issue was addressed through improved state management. WebKit Bugzilla: 286580 CVE-2025-30425: an anonymous researcher WindowServer Available for: macOS Sequoia Impact: An attacker may be able to cause unexpected app termination Description: A type confusion issue was addressed with improved checks. CVE-2025-24247: PixiePoint Security WindowServer Available for: macOS Sequoia Impact: An app may be able to trick a user into copying sensitive data to the pasteboard Description: A configuration issue was addressed with additional restrictions. CVE-2025-24241: Andreas Hegenberg (folivora.AI GmbH) Xsan Available for: macOS Sequoia Impact: An app may be able to cause unexpected system termination Description: A buffer overflow was addressed with improved bounds checking. CVE-2025-24266: an anonymous researcher Xsan Available for: macOS Sequoia Impact: An app may be able to cause unexpected system termination Description: An out-of-bounds read was addressed with improved bounds checking. CVE-2025-24265: an anonymous researcher Xsan Available for: macOS Sequoia Impact: An app may be able to cause unexpected system termination or corrupt kernel memory Description: A buffer overflow issue was addressed with improved memory handling. CVE-2025-24157: an anonymous researcher @ 06639a38:655f8f71
2025-04-02 13:47:57You can follow the work in progress here in this pull request [https://github.com/nostrver-se/nostr-php/pull/68](https://github.com/nostrver-se/nostr-php/pull/68) on Github. Before my 3-month break (Dec/Jan/Feb) working on Nostr-PHP I started with the NIP-19 integration in October '24. Encoding and decoding the simple prefixes (`npub`, `nsec` and `note`) was already done in the first commits. Learn more about NIP-19 here: [https://nips.nostr.com/19](https://nips.nostr.com/19) ### **TLV's** Things were getting more complicated with the other prefixes / identifiers defined in NIP-19: * `nevent` * `naddr` * `nprofile` This is because these identifiers contain (optional) metadata called Type-Lenght-Value aka TLV's. _When sharing a profile or an event, an app may decide to include relay information and other metadata such that other apps can locate and display these entities more easily._ _For these events, the contents are a binary-encoded list of_ `_TLV_` _(type-length-value), with_ `_T_` _and_ `_L_` _being 1 byte each (_`_uint8_`_, i.e. a number in the range of 0-255), and_ `_V_` _being a sequence of bytes of the size indicated by_ `_L_`_._ These possible standardized `TLV` types are: * `0`_:_ `special` * _depends on the bech32 prefix:_ * _for_ `nprofile` _it will be the 32 bytes of the profile public key_ * _for_ `nevent` _it will be the 32 bytes of the event id_ * _for_ `naddr`_, it is the identifier (the_ `"d"` _tag) of the event being referenced. For normal replaceable events use an empty string._ * `1`_:_ `relay` * _for_ `nprofile`_,_ `nevent` _and_ `naddr`_, optionally, a relay in which the entity (profile or event) is more likely to be found, encoded as ascii_ * _this may be included multiple times_ * `2`_:_ `author` * _for_ `naddr`_, the 32 bytes of the pubkey of the event_ * _for_ `nevent`_, optionally, the 32 bytes of the pubkey of the event_ * `3`_:_ `kind` * _for_ `naddr`_, the 32-bit unsigned integer of the kind, big-endian_ * _for_ `nevent`_, optionally, the 32-bit unsigned integer of the kind, big-endian_ These identifiers are formatted as bech32 strings, but are much longer than the package `bitwasp/bech32` (used in the library) for can handle for encoding and decoding. The bech32 strings handled by `bitwasp/bech32` are limited to a maximum length of 90 characters. Thanks to the effort of others (nostr:npub1636uujeewag8zv8593lcvdrwlymgqre6uax4anuq3y5qehqey05sl8qpl4 and nostr:npub1efz8l77esdtpw6l359sjvakm7azvyv6mkuxphjdk3vfzkgxkatrqlpf9s4) during my break, some contributions are made (modifiying the bech32 package supporting much longer strings, up to a max of 5000 characters). At this moment, I'm integrating this (mostly copy-pasting the stuff and refactoring the code): * [https://github.com/nostrver-se/nostr-php/issues/74](https://github.com/nostrver-se/nostr-php/issues/74) * [https://github.com/nostriphant/nip-19](https://github.com/nostriphant/nip-19) ### **So what's next?** * NIP-19 code housekeeping + refactoring * Prepare a new release with NIP-19 integration * Create documentation page how to use NIP-19 on [https://nostr-php.dev](https://nostr-php.dev)
@ 06639a38:655f8f71
2025-04-02 13:47:57You can follow the work in progress here in this pull request [https://github.com/nostrver-se/nostr-php/pull/68](https://github.com/nostrver-se/nostr-php/pull/68) on Github. Before my 3-month break (Dec/Jan/Feb) working on Nostr-PHP I started with the NIP-19 integration in October '24. Encoding and decoding the simple prefixes (`npub`, `nsec` and `note`) was already done in the first commits. Learn more about NIP-19 here: [https://nips.nostr.com/19](https://nips.nostr.com/19) ### **TLV's** Things were getting more complicated with the other prefixes / identifiers defined in NIP-19: * `nevent` * `naddr` * `nprofile` This is because these identifiers contain (optional) metadata called Type-Lenght-Value aka TLV's. _When sharing a profile or an event, an app may decide to include relay information and other metadata such that other apps can locate and display these entities more easily._ _For these events, the contents are a binary-encoded list of_ `_TLV_` _(type-length-value), with_ `_T_` _and_ `_L_` _being 1 byte each (_`_uint8_`_, i.e. a number in the range of 0-255), and_ `_V_` _being a sequence of bytes of the size indicated by_ `_L_`_._ These possible standardized `TLV` types are: * `0`_:_ `special` * _depends on the bech32 prefix:_ * _for_ `nprofile` _it will be the 32 bytes of the profile public key_ * _for_ `nevent` _it will be the 32 bytes of the event id_ * _for_ `naddr`_, it is the identifier (the_ `"d"` _tag) of the event being referenced. For normal replaceable events use an empty string._ * `1`_:_ `relay` * _for_ `nprofile`_,_ `nevent` _and_ `naddr`_, optionally, a relay in which the entity (profile or event) is more likely to be found, encoded as ascii_ * _this may be included multiple times_ * `2`_:_ `author` * _for_ `naddr`_, the 32 bytes of the pubkey of the event_ * _for_ `nevent`_, optionally, the 32 bytes of the pubkey of the event_ * `3`_:_ `kind` * _for_ `naddr`_, the 32-bit unsigned integer of the kind, big-endian_ * _for_ `nevent`_, optionally, the 32-bit unsigned integer of the kind, big-endian_ These identifiers are formatted as bech32 strings, but are much longer than the package `bitwasp/bech32` (used in the library) for can handle for encoding and decoding. The bech32 strings handled by `bitwasp/bech32` are limited to a maximum length of 90 characters. Thanks to the effort of others (nostr:npub1636uujeewag8zv8593lcvdrwlymgqre6uax4anuq3y5qehqey05sl8qpl4 and nostr:npub1efz8l77esdtpw6l359sjvakm7azvyv6mkuxphjdk3vfzkgxkatrqlpf9s4) during my break, some contributions are made (modifiying the bech32 package supporting much longer strings, up to a max of 5000 characters). At this moment, I'm integrating this (mostly copy-pasting the stuff and refactoring the code): * [https://github.com/nostrver-se/nostr-php/issues/74](https://github.com/nostrver-se/nostr-php/issues/74) * [https://github.com/nostriphant/nip-19](https://github.com/nostriphant/nip-19) ### **So what's next?** * NIP-19 code housekeeping + refactoring * Prepare a new release with NIP-19 integration * Create documentation page how to use NIP-19 on [https://nostr-php.dev](https://nostr-php.dev) @ 732c6a62:42003da2
2025-03-09 22:36:26Não são recentes as táticas da esquerda de tentar reprimir intelectualmente seus opositores na base do deboche, da ironia, do desprezo e do boicote à credibilidade. Até Marx usava ironia para chamar os críticos de "burgueses iludidos". A diferença é que, no século XXI, trocaram o manifesto comunista por threads no Twitter e a dialética por memes de mau gosto. ### **A Falácia da Superioridade Moral** O debate sobre o "pobre de direita" no Brasil é contaminado por uma premissa tácita da esquerda: **a ideia de que classes baixas só podem ter consciência política se aderirem a pautas progressistas**. Quem ousa divergir é tratado como "traidor de classe", "manipulado", "ignorante", ou até vítimas de deboches como alguma pessoa com um qi em temperatura ambiente repetir diversas vezes "não é possível que ainda exista pobre de direita", "nunca vou entender pobre de direita", ou "pobre de direita é muito burro, rico eu até entendo", como se o autor dessas frases fosse o paladino dos mais oprimidos e pobres. Esse discurso, porém, não resiste a uma análise empírica, histórica ou sociológica. --- ### **Contexto Histórico: A Esquerda e o Mito do "Voto Consciente"** A noção de que o pobre deve votar na esquerda por "interesse de classe" é herança do **marxismo ortodoxo**, que via a política como mero reflexo da posição econômica. No entanto, a realidade é mais complexa: - **Dados do Latinobarómetro (2022):** 41% dos brasileiros de baixa renda (até 2 salários mínimos) apoiam redução de impostos e maior liberdade econômica — pautas tradicionalmente associadas à direita. - **Pesquisa IPEC (2023):** 58% dos pobres brasileiros priorizam "segurança pública" como principal demanda, acima de "distribuição de renda". Esses números não são acidentais. Refletem uma **mudança estrutural**: o pobre moderno não é mais o "operário industrial" do século XX, mas um empreendedor informal, motorista de app, ou microempresário — figuras que valorizam autonomia e rejeitam paternalismo estatal. Eles dizem não entender o pobre de direita e que nunca vai entendê-los, mas o fato é que não entendem porque **nunca conversaram com um sem fazer cara de psicólogo de posto de saúde**. Sua "preocupação" é só uma máscara para esconder o desprezo por quem ousa pensar diferente do seu manual de "oprimido ideal". ## **Se ainda não entenderam:** **Direita ≠ rico:** Tem gente que trabalha 12h/dia e vota em liberal porque quer **ser dono do próprio negócio**, não pra pagar mais taxação pra você postar meme no Twitter. **Acham que são o Sherlock Holmes da pobreza:** o palpite de que "o pobre é manipulado" é tão raso quanto sua compreensão de economia básica. --- ### **A Psicologia por Trás do Voto Conservador nas Periferias** A esquerda atribui o voto pobre em direita a "falta de educação" ou "manipulação midiática". Essa tese é não apenas elitista, mas **cientificamente falsa**: **Análise Psicológica Básica (para você que se acha o Paulo Freire):** - **Síndrome do Branco Salvador:** Acha que o pobre é uma criatura tão frágil que precisa de você pra pensar. Spoiler: ele não precisa. - **Viés da Superioridade Moral:** "Se você é pobre e não concorda comigo, você é burro". Parabéns, recriou a escravidão intelectual. - **Efeito Dunning-Kruger:** Não sabe o que é CLT, mas dá palpite sobre reforma trabalhista. - **Estudo da Universidade de São Paulo (USP, 2021):** Entre moradores de favelas, 63% associam políticas de segurança dura (como "bandido bom é bandido morto") à proteção de seus negócios e famílias. Para eles, a esquerda é "branda demais" com o crime. - **Pesquisa FGV (2020):** 71% dos trabalhadores informais rejeitam aumentos de impostos, mesmo que para financiar programas sociais. Motivo: já sofrem com a burocracia estatal para legalizar seus negócios. Esses dados revelam uma **racionalidade prática**: o pobre avalia políticas pelo impacto imediato em sua vida, não por abstrações ideológicas. Enquanto a esquerda fala em "reforma estrutural" e tenta importar discursos estrangeiros para debate, por exemplo, o tema irrelevante do pronome neutro, ele quer resolver problemas como: - **Violência** (que afeta seu comércio); - **Impostos** (que consomem até 40% do lucro de um camelô); - **Burocracia** (que impede a legalização de sua barraca de pastel). --- ### **Religião, Valores e a Hipocrisia do "Ateísmo de Redes Sociais"** A esquerda subestima o papel da religião na formação política das classes baixas. No Brasil, **76% dos evangélicos são pobres** (Datafolha, 2023), e suas igrejas promovem valores como: - **Família tradicional** (contra pautas progressistas como ideologia de gênero em escolas); - **Auto-responsabilidade** (ênfase em "trabalho duro" em vez de assistencialismo). **Exemplo Concreto:** Nas favelas de São Paulo, pastores evangélicos são frequentemente eleitos a cargos locais com plataformas anticrime e pró-mercado. Para seus eleitores, a esquerda urbana (que defende descriminalização de drogas e críticas à polícia) representa uma **ameaça ao seu estilo de vida**. --- ### **A Esquerda e seu Desprezo pela Autonomia do Pobre** O cerne do debate é a **incapacidade da esquerda de aceitar que o pobre possa ser autônomo**. Algumas evidências: #### **O Caso dos Empreendedores Informais** - **Segundo o IBGE (2023), 40% dos trabalhadores brasileiros estão na informalidade.** Muitos veem o Estado como obstáculo, não aliado. Políticas de direita (como simplificação tributária) são mais atraentes para eles que o Bolsa Família. #### **A Ascensão do Conservadorismo Periférico** - Pessoas assim tem um pensamento simples. Sua mensagem: *"Queremos empreender, não depender de político."* #### **A Rejeição ao "Vitimismo"** - **Pesquisa Atlas Intel (2022):** 68% dos pobres brasileiros rejeitam o termo "vítima da sociedade". Preferem ser vistos como "lutadores". --- ### **A projeção freudiana "o pobre é burro porque eu sou inteligente"** O deboche esquerdista esconde um complexo de inferioridade disfarçado de superioridade moral. É a **Síndrome do Salvador** em sua forma mais patética: - **Passo 1:** Assume-se que o pobre é um ser desprovido de agência. - **Passo 2:** Qualquer desvio da narrativa é atribuído a "manipulação da elite". - **Passo 3:** Quem critica o processo é chamado de "fascista". **Exemplo Prático:** Quando uma empregada doméstica diz que prefere o livre mercado a programas sociais, a esquerda não pergunta *"por quê?"* — ela grita *"lavagem cerebral!"*. A ironia? Essa mesma esquerda defende a **autonomia feminina**, exceto quando a mulher é pobre e pensa diferente. ### **Dados Globais: O Fenômeno Não é Brasileiro** A ideia de que "pobre de direita" é uma anomalia é desmentida por evidências internacionais: - **Estados Unidos:** 38% dos eleitores com renda abaixo de US$ 30k/ano votaram em Trump em 2020 (Pew Research). Motivos principais: conservadorismo social e rejeição a impostos. A esquerda: "vítimas da falsa consciência". Mais um detalhe: na última eleição de 2024, grande parte da classe "artística" milionária dos Estados Unidos, figuras conhecidas, promoveram em peso a Kamala Harris, do Partido Democrata. Percebe como a esquerda atual é a personificaçãoda burguesia e de só pensar na própria barriga? - **Argentina:** Javier Milei, libertário radical, quando candidato, tinha forte apoio nas *villas miseria* (favelas). Seu lema — *"O estado é um parasita"* — ressoa entre quem sofria com inflação de 211% ao ano. - **Índia:** O partido BJP (direita nacionalista) domina entre os pobres rurais, que associam a esquerda a elites urbanas desconectadas de suas necessidades. ### **A história que a esquerda tenta apagar: pobres de direita existem desde sempre** A esquerda age como se o "pobre de direita" fosse uma invenção recente do MBL, mas a realidade é que **classes baixas conservadoras são regra, não exceção**, na história mundial: - **Revolução Francesa (1789):** Camponeses apoiaram a monarquia contra os jacobinos urbanos que queriam "libertá-los". - **Brasil Imperial:** Escravos libertos que viraram pequenos proprietários rurais rejeitavam o abolicionismo radical — queriam integração, não utopia. **Tradução:** Quando o pobre não segue o script, a esquerda inventa teorias conspiratórias. --- ### **A Hipocrisia da Esquerda Urbana e Universitária** Enquanto acusa o pobre de direita de "alienado", a esquerda brasileira é dominada por uma **elite desconectada da realidade periférica**: - **Perfil Socioeconômico:** 82% dos filiados ao PSOL têm ensino superior completo (TSE, 2023). Apenas 6% moram em bairros periféricos. - **Prioridades Descoladas:** Enquanto o pobre debate segurança e custo de vida, a esquerda pauta discussões como "linguagem não-binária em editais públicos" — tema irrelevante para quem luta contra o desemprego. Os grandes teóricos comunistas se reviram no túmulo quando veem o que a esquerda se tornou: não debatem os reais problemas do Brasil, e sim sobre suas próprias emoções. *"A esquerda brasileira trocou o operário pelo influencer progressista. O pobre virou um personagem de campanha, não um interlocutor real."* ### **A diversidade de pensamento que a esquerda não suporta** A esquerda prega diversidade — desde que você seja diverso dentro de um **checklist pré-aprovado**. Pobre LGBTQ+? Herói. Pobre evangélico? Fascista. Pobre que abre MEI? "Peão do capitalismo". A realidade é que favelas e periferias são **microcosmos de pluralidade ideológica**, algo que assusta quem quer reduzir seres humanos a estereótipos. --- ### **Respostas aos Argumentos Esquerdistas (e Por que Falham)** #### **"O pobre de direita é manipulado pela mídia!"** - **Contradição:** Se a mídia tradicional é dominada por elites (como alegam), por que grandes veículos são abertamente progressistas? A Record (evangélica) é exceção, não regra. **Contradição Central:** Como explicar que, segundo o **Banco Mundial (2023)**, países com maior liberdade econômica (ex.: Chile, Polônia) reduziram a pobreza extrema em 60% nas últimas décadas, enquanto modelos estatizantes (ex.: Venezuela, Argentina com o governo peronista) afundaram na miséria? Simples: a esquerda prefere culpar o "neoliberalismo" a admitir que **o pobre com o mínimo de consciência quer emprego, não esmola**. **Dado que Machuca:** - 71% das mulheres da periferia rejeitam o feminismo radical, associando-o a "prioridades distantes da realidade" (**Instituto Locomotiva, 2023**). #### **"Ele vota contra os próprios interesses!"** - **Falácia:** Pressupõe que a esquerda define o que é o "interesse do pobre". Para um pai de família na Cidade de Deus, ter a boca de fogo fechada pode ser mais urgente que um aumento de 10% no Bolsa Família. O pobre de direita não é uma anomalia. É o **produto natural de um mundo complexo** onde seres humanos têm aspirações, medos e valores diversos. Enquanto a esquerda insiste em tratá-lo como um projeto fracassado, ele está ocupado: - **Trabalhando** para não depender do governo. - **Escolhendo** religiões que dão sentido à sua vida. - **Rejeitando** pautas identitárias que não resolvem o custo do gás de cozinha. #### **"É falta de educação política!"** - **Ironia:** Nos países nórdicos (modelo da esquerda), as classes baixas são as mais conservadoras. Educação não correlaciona com progressismo. --- ### **Por que o Debuste Precisa Acabar** A insistência em descredibilizar o pobre de direita revela um **projeto de poder fracassado**. A esquerda, ao substituir diálogo por deboche, perdeu a capacidade de representar quem mais precisaria dela. Enquanto isso, a direita — nem sempre por virtude, mas por pragmatismo — capturou o descontentamento de milhões com o status quo. O pobre de direita existe porque ele **não precisa da permissão do rico de esquerda para pensar**. A incapacidade de entender isso só prova que **a esquerda é a nova aristocracia**. **Último Dado:** Nas eleições de 2022, Tarcísio de Freitas (direita) venceu em 72% das favelas de São Paulo. O motivo? Seu discurso anti-burocracia e pró-microempreendedor. A mensagem é clara: o pobre não é um projeto ideológico. É um agente político autônomo — e quem não entender isso continuará perdendo eleições. A esquerda elitista não odeia o pobre de direita por ele ser "irracional". Odeia porque ele **desafia o monopólio moral** que ela construiu sobre a miséria alheia. Enquanto isso, o pobre segue sua vida, ignorando os berros de quem acha que sabem mais da sua vida que ele mesmo. **Pergunta Retórica (Para Incomodar):** Se a esquerda é tão sábia, por que não usa essa sabedoria para entender que **pobre também cansa de ser tratado como cachorro que late no ritmo errado**? --- # **Fontes Citadas:** 1. Latinobarómetro (2022) 2. IPEC (2023) 3. USP (2021): *"Segurança Pública e Percepções nas Favelas Cariocas"* 4. FGV (2020): *"Informalidade e Tributação no Brasil"* 5. Datafolha (2023): *"Perfil Religioso do Eleitorado Brasileiro"* 6. Atlas Intel (2022): *"Autopercepção das Classes Baixas"* 7. Pew Research (2020): *"Voting Patterns by Income in the U.S."* 8. TSE (2023): *"Perfil Socioeconômico dos Filiados Partidários"* **Leitura Recomendada para Esquerdistas:** - *"Fome de Poder: Por que o Pobre Brasileiro Abandonou a Esquerda"* (Fernando Schüller, 2023) - *"A Revolução dos Conservadores: Religião e Política nas Periferias"* (Juliano Spyer, 2021) - *"Direita e Esquerda: Razões e Paixões"* (Demétrio Magnoli, 2019)
@ 732c6a62:42003da2
2025-03-09 22:36:26Não são recentes as táticas da esquerda de tentar reprimir intelectualmente seus opositores na base do deboche, da ironia, do desprezo e do boicote à credibilidade. Até Marx usava ironia para chamar os críticos de "burgueses iludidos". A diferença é que, no século XXI, trocaram o manifesto comunista por threads no Twitter e a dialética por memes de mau gosto. ### **A Falácia da Superioridade Moral** O debate sobre o "pobre de direita" no Brasil é contaminado por uma premissa tácita da esquerda: **a ideia de que classes baixas só podem ter consciência política se aderirem a pautas progressistas**. Quem ousa divergir é tratado como "traidor de classe", "manipulado", "ignorante", ou até vítimas de deboches como alguma pessoa com um qi em temperatura ambiente repetir diversas vezes "não é possível que ainda exista pobre de direita", "nunca vou entender pobre de direita", ou "pobre de direita é muito burro, rico eu até entendo", como se o autor dessas frases fosse o paladino dos mais oprimidos e pobres. Esse discurso, porém, não resiste a uma análise empírica, histórica ou sociológica. --- ### **Contexto Histórico: A Esquerda e o Mito do "Voto Consciente"** A noção de que o pobre deve votar na esquerda por "interesse de classe" é herança do **marxismo ortodoxo**, que via a política como mero reflexo da posição econômica. No entanto, a realidade é mais complexa: - **Dados do Latinobarómetro (2022):** 41% dos brasileiros de baixa renda (até 2 salários mínimos) apoiam redução de impostos e maior liberdade econômica — pautas tradicionalmente associadas à direita. - **Pesquisa IPEC (2023):** 58% dos pobres brasileiros priorizam "segurança pública" como principal demanda, acima de "distribuição de renda". Esses números não são acidentais. Refletem uma **mudança estrutural**: o pobre moderno não é mais o "operário industrial" do século XX, mas um empreendedor informal, motorista de app, ou microempresário — figuras que valorizam autonomia e rejeitam paternalismo estatal. Eles dizem não entender o pobre de direita e que nunca vai entendê-los, mas o fato é que não entendem porque **nunca conversaram com um sem fazer cara de psicólogo de posto de saúde**. Sua "preocupação" é só uma máscara para esconder o desprezo por quem ousa pensar diferente do seu manual de "oprimido ideal". ## **Se ainda não entenderam:** **Direita ≠ rico:** Tem gente que trabalha 12h/dia e vota em liberal porque quer **ser dono do próprio negócio**, não pra pagar mais taxação pra você postar meme no Twitter. **Acham que são o Sherlock Holmes da pobreza:** o palpite de que "o pobre é manipulado" é tão raso quanto sua compreensão de economia básica. --- ### **A Psicologia por Trás do Voto Conservador nas Periferias** A esquerda atribui o voto pobre em direita a "falta de educação" ou "manipulação midiática". Essa tese é não apenas elitista, mas **cientificamente falsa**: **Análise Psicológica Básica (para você que se acha o Paulo Freire):** - **Síndrome do Branco Salvador:** Acha que o pobre é uma criatura tão frágil que precisa de você pra pensar. Spoiler: ele não precisa. - **Viés da Superioridade Moral:** "Se você é pobre e não concorda comigo, você é burro". Parabéns, recriou a escravidão intelectual. - **Efeito Dunning-Kruger:** Não sabe o que é CLT, mas dá palpite sobre reforma trabalhista. - **Estudo da Universidade de São Paulo (USP, 2021):** Entre moradores de favelas, 63% associam políticas de segurança dura (como "bandido bom é bandido morto") à proteção de seus negócios e famílias. Para eles, a esquerda é "branda demais" com o crime. - **Pesquisa FGV (2020):** 71% dos trabalhadores informais rejeitam aumentos de impostos, mesmo que para financiar programas sociais. Motivo: já sofrem com a burocracia estatal para legalizar seus negócios. Esses dados revelam uma **racionalidade prática**: o pobre avalia políticas pelo impacto imediato em sua vida, não por abstrações ideológicas. Enquanto a esquerda fala em "reforma estrutural" e tenta importar discursos estrangeiros para debate, por exemplo, o tema irrelevante do pronome neutro, ele quer resolver problemas como: - **Violência** (que afeta seu comércio); - **Impostos** (que consomem até 40% do lucro de um camelô); - **Burocracia** (que impede a legalização de sua barraca de pastel). --- ### **Religião, Valores e a Hipocrisia do "Ateísmo de Redes Sociais"** A esquerda subestima o papel da religião na formação política das classes baixas. No Brasil, **76% dos evangélicos são pobres** (Datafolha, 2023), e suas igrejas promovem valores como: - **Família tradicional** (contra pautas progressistas como ideologia de gênero em escolas); - **Auto-responsabilidade** (ênfase em "trabalho duro" em vez de assistencialismo). **Exemplo Concreto:** Nas favelas de São Paulo, pastores evangélicos são frequentemente eleitos a cargos locais com plataformas anticrime e pró-mercado. Para seus eleitores, a esquerda urbana (que defende descriminalização de drogas e críticas à polícia) representa uma **ameaça ao seu estilo de vida**. --- ### **A Esquerda e seu Desprezo pela Autonomia do Pobre** O cerne do debate é a **incapacidade da esquerda de aceitar que o pobre possa ser autônomo**. Algumas evidências: #### **O Caso dos Empreendedores Informais** - **Segundo o IBGE (2023), 40% dos trabalhadores brasileiros estão na informalidade.** Muitos veem o Estado como obstáculo, não aliado. Políticas de direita (como simplificação tributária) são mais atraentes para eles que o Bolsa Família. #### **A Ascensão do Conservadorismo Periférico** - Pessoas assim tem um pensamento simples. Sua mensagem: *"Queremos empreender, não depender de político."* #### **A Rejeição ao "Vitimismo"** - **Pesquisa Atlas Intel (2022):** 68% dos pobres brasileiros rejeitam o termo "vítima da sociedade". Preferem ser vistos como "lutadores". --- ### **A projeção freudiana "o pobre é burro porque eu sou inteligente"** O deboche esquerdista esconde um complexo de inferioridade disfarçado de superioridade moral. É a **Síndrome do Salvador** em sua forma mais patética: - **Passo 1:** Assume-se que o pobre é um ser desprovido de agência. - **Passo 2:** Qualquer desvio da narrativa é atribuído a "manipulação da elite". - **Passo 3:** Quem critica o processo é chamado de "fascista". **Exemplo Prático:** Quando uma empregada doméstica diz que prefere o livre mercado a programas sociais, a esquerda não pergunta *"por quê?"* — ela grita *"lavagem cerebral!"*. A ironia? Essa mesma esquerda defende a **autonomia feminina**, exceto quando a mulher é pobre e pensa diferente. ### **Dados Globais: O Fenômeno Não é Brasileiro** A ideia de que "pobre de direita" é uma anomalia é desmentida por evidências internacionais: - **Estados Unidos:** 38% dos eleitores com renda abaixo de US$ 30k/ano votaram em Trump em 2020 (Pew Research). Motivos principais: conservadorismo social e rejeição a impostos. A esquerda: "vítimas da falsa consciência". Mais um detalhe: na última eleição de 2024, grande parte da classe "artística" milionária dos Estados Unidos, figuras conhecidas, promoveram em peso a Kamala Harris, do Partido Democrata. Percebe como a esquerda atual é a personificaçãoda burguesia e de só pensar na própria barriga? - **Argentina:** Javier Milei, libertário radical, quando candidato, tinha forte apoio nas *villas miseria* (favelas). Seu lema — *"O estado é um parasita"* — ressoa entre quem sofria com inflação de 211% ao ano. - **Índia:** O partido BJP (direita nacionalista) domina entre os pobres rurais, que associam a esquerda a elites urbanas desconectadas de suas necessidades. ### **A história que a esquerda tenta apagar: pobres de direita existem desde sempre** A esquerda age como se o "pobre de direita" fosse uma invenção recente do MBL, mas a realidade é que **classes baixas conservadoras são regra, não exceção**, na história mundial: - **Revolução Francesa (1789):** Camponeses apoiaram a monarquia contra os jacobinos urbanos que queriam "libertá-los". - **Brasil Imperial:** Escravos libertos que viraram pequenos proprietários rurais rejeitavam o abolicionismo radical — queriam integração, não utopia. **Tradução:** Quando o pobre não segue o script, a esquerda inventa teorias conspiratórias. --- ### **A Hipocrisia da Esquerda Urbana e Universitária** Enquanto acusa o pobre de direita de "alienado", a esquerda brasileira é dominada por uma **elite desconectada da realidade periférica**: - **Perfil Socioeconômico:** 82% dos filiados ao PSOL têm ensino superior completo (TSE, 2023). Apenas 6% moram em bairros periféricos. - **Prioridades Descoladas:** Enquanto o pobre debate segurança e custo de vida, a esquerda pauta discussões como "linguagem não-binária em editais públicos" — tema irrelevante para quem luta contra o desemprego. Os grandes teóricos comunistas se reviram no túmulo quando veem o que a esquerda se tornou: não debatem os reais problemas do Brasil, e sim sobre suas próprias emoções. *"A esquerda brasileira trocou o operário pelo influencer progressista. O pobre virou um personagem de campanha, não um interlocutor real."* ### **A diversidade de pensamento que a esquerda não suporta** A esquerda prega diversidade — desde que você seja diverso dentro de um **checklist pré-aprovado**. Pobre LGBTQ+? Herói. Pobre evangélico? Fascista. Pobre que abre MEI? "Peão do capitalismo". A realidade é que favelas e periferias são **microcosmos de pluralidade ideológica**, algo que assusta quem quer reduzir seres humanos a estereótipos. --- ### **Respostas aos Argumentos Esquerdistas (e Por que Falham)** #### **"O pobre de direita é manipulado pela mídia!"** - **Contradição:** Se a mídia tradicional é dominada por elites (como alegam), por que grandes veículos são abertamente progressistas? A Record (evangélica) é exceção, não regra. **Contradição Central:** Como explicar que, segundo o **Banco Mundial (2023)**, países com maior liberdade econômica (ex.: Chile, Polônia) reduziram a pobreza extrema em 60% nas últimas décadas, enquanto modelos estatizantes (ex.: Venezuela, Argentina com o governo peronista) afundaram na miséria? Simples: a esquerda prefere culpar o "neoliberalismo" a admitir que **o pobre com o mínimo de consciência quer emprego, não esmola**. **Dado que Machuca:** - 71% das mulheres da periferia rejeitam o feminismo radical, associando-o a "prioridades distantes da realidade" (**Instituto Locomotiva, 2023**). #### **"Ele vota contra os próprios interesses!"** - **Falácia:** Pressupõe que a esquerda define o que é o "interesse do pobre". Para um pai de família na Cidade de Deus, ter a boca de fogo fechada pode ser mais urgente que um aumento de 10% no Bolsa Família. O pobre de direita não é uma anomalia. É o **produto natural de um mundo complexo** onde seres humanos têm aspirações, medos e valores diversos. Enquanto a esquerda insiste em tratá-lo como um projeto fracassado, ele está ocupado: - **Trabalhando** para não depender do governo. - **Escolhendo** religiões que dão sentido à sua vida. - **Rejeitando** pautas identitárias que não resolvem o custo do gás de cozinha. #### **"É falta de educação política!"** - **Ironia:** Nos países nórdicos (modelo da esquerda), as classes baixas são as mais conservadoras. Educação não correlaciona com progressismo. --- ### **Por que o Debuste Precisa Acabar** A insistência em descredibilizar o pobre de direita revela um **projeto de poder fracassado**. A esquerda, ao substituir diálogo por deboche, perdeu a capacidade de representar quem mais precisaria dela. Enquanto isso, a direita — nem sempre por virtude, mas por pragmatismo — capturou o descontentamento de milhões com o status quo. O pobre de direita existe porque ele **não precisa da permissão do rico de esquerda para pensar**. A incapacidade de entender isso só prova que **a esquerda é a nova aristocracia**. **Último Dado:** Nas eleições de 2022, Tarcísio de Freitas (direita) venceu em 72% das favelas de São Paulo. O motivo? Seu discurso anti-burocracia e pró-microempreendedor. A mensagem é clara: o pobre não é um projeto ideológico. É um agente político autônomo — e quem não entender isso continuará perdendo eleições. A esquerda elitista não odeia o pobre de direita por ele ser "irracional". Odeia porque ele **desafia o monopólio moral** que ela construiu sobre a miséria alheia. Enquanto isso, o pobre segue sua vida, ignorando os berros de quem acha que sabem mais da sua vida que ele mesmo. **Pergunta Retórica (Para Incomodar):** Se a esquerda é tão sábia, por que não usa essa sabedoria para entender que **pobre também cansa de ser tratado como cachorro que late no ritmo errado**? --- # **Fontes Citadas:** 1. Latinobarómetro (2022) 2. IPEC (2023) 3. USP (2021): *"Segurança Pública e Percepções nas Favelas Cariocas"* 4. FGV (2020): *"Informalidade e Tributação no Brasil"* 5. Datafolha (2023): *"Perfil Religioso do Eleitorado Brasileiro"* 6. Atlas Intel (2022): *"Autopercepção das Classes Baixas"* 7. Pew Research (2020): *"Voting Patterns by Income in the U.S."* 8. TSE (2023): *"Perfil Socioeconômico dos Filiados Partidários"* **Leitura Recomendada para Esquerdistas:** - *"Fome de Poder: Por que o Pobre Brasileiro Abandonou a Esquerda"* (Fernando Schüller, 2023) - *"A Revolução dos Conservadores: Religião e Política nas Periferias"* (Juliano Spyer, 2021) - *"Direita e Esquerda: Razões e Paixões"* (Demétrio Magnoli, 2019) @ 7bdef7be:784a5805
2025-04-02 12:09:29We value sovereignty, privacy and security when accessing online content, using several tools to achieve this, like open protocols, open OSes, open software products, Tor and VPNs. ## The problem Talking about our social presence, we can manually build up our follower list (social graph), pick a Nostr client that is respectful of our preferences on what to show and how, but with the standard following mechanism, our main feed is public, so everyone can actually snoop what we are interested in, and what is supposable that we read daily. ## The solution Nostr has a simple solution for this necessity: encrypted lists. Lists are what they appear, a collection of people or interests (but they can also group much other stuff, see [NIP-51](https://github.com/nostr-protocol/nips/blob/master/51.md)). So we can create lists with contacts that we don't have in our main social graph; these lists can be used primarily to create dedicated feeds, but they could have other uses, for example, related to monitoring. The interesting thing about lists is that they can also be encrypted, so unlike the basic following list, which is always public, we can hide the lists' content from others. The implications are obvious: we can not only have a more organized way to browse content, but it is also really private one. One might wonder what use can really be made of private lists; here are some examples: * Browse “can't miss” content from users I consider a priority; * Supervise competitors or adversarial parts; * Monitor sensible topics (tags); * Follow someone without being publicly associated with them, as this may be undesirable; The benefits in terms of privacy as usual are not only related to the casual, or programmatic, observer, but are also evident when we think of how many bots scan our actions to profile us. ## The current state Unfortunately, lists are not widely supported by Nostr clients, and encrypted support is a rarity. Often the excuse to not implement them is that they are harder to develop, since they require managing the encryption stuff ([NIP-44](https://github.com/nostr-protocol/nips/blob/master/44.md)). Nevertheless, developers have an easier option to start offering private lists: give the user the possibility to simply mark them as local-only, and never push them to the relays. Even if the user misses the sync feature, this is sufficient to create a private environment. To date, as far as I know, the best client with list management is [Gossip](nostr:npub189j8y280mhezlp98ecmdzydn0r8970g4hpqpx3u9tcztynywfczqqr3tg8), which permits to manage both encrypted and local-only lists. Beg your Nostr client to implement private lists!
@ 7bdef7be:784a5805
2025-04-02 12:09:29We value sovereignty, privacy and security when accessing online content, using several tools to achieve this, like open protocols, open OSes, open software products, Tor and VPNs. ## The problem Talking about our social presence, we can manually build up our follower list (social graph), pick a Nostr client that is respectful of our preferences on what to show and how, but with the standard following mechanism, our main feed is public, so everyone can actually snoop what we are interested in, and what is supposable that we read daily. ## The solution Nostr has a simple solution for this necessity: encrypted lists. Lists are what they appear, a collection of people or interests (but they can also group much other stuff, see [NIP-51](https://github.com/nostr-protocol/nips/blob/master/51.md)). So we can create lists with contacts that we don't have in our main social graph; these lists can be used primarily to create dedicated feeds, but they could have other uses, for example, related to monitoring. The interesting thing about lists is that they can also be encrypted, so unlike the basic following list, which is always public, we can hide the lists' content from others. The implications are obvious: we can not only have a more organized way to browse content, but it is also really private one. One might wonder what use can really be made of private lists; here are some examples: * Browse “can't miss” content from users I consider a priority; * Supervise competitors or adversarial parts; * Monitor sensible topics (tags); * Follow someone without being publicly associated with them, as this may be undesirable; The benefits in terms of privacy as usual are not only related to the casual, or programmatic, observer, but are also evident when we think of how many bots scan our actions to profile us. ## The current state Unfortunately, lists are not widely supported by Nostr clients, and encrypted support is a rarity. Often the excuse to not implement them is that they are harder to develop, since they require managing the encryption stuff ([NIP-44](https://github.com/nostr-protocol/nips/blob/master/44.md)). Nevertheless, developers have an easier option to start offering private lists: give the user the possibility to simply mark them as local-only, and never push them to the relays. Even if the user misses the sync feature, this is sufficient to create a private environment. To date, as far as I know, the best client with list management is [Gossip](nostr:npub189j8y280mhezlp98ecmdzydn0r8970g4hpqpx3u9tcztynywfczqqr3tg8), which permits to manage both encrypted and local-only lists. Beg your Nostr client to implement private lists! @ ec9bd746:df11a9d0
2025-03-07 20:13:38I was diving into PoW (Proof-of-Work) once again after nostr:nprofile1qy88wumn8ghj7mn0wvhxcmmv9uq3wamnwvaz7tmjv4kxz7fwdehhxarj9e3xzmny9uqzqj8a67jths8euy33v5yu6me6ngua5v3y3qq3dswuqh2pejmtls6datagmu rekindled my interest with his PoW Draw project. It was a fun little trifle, but it shifted my focus just the right way at the right time. Because then, on Friday, came the [Oval Office Travesty](nostr:nevent1qvzqqqqqqypzpmym6ar92346qc04ml08z6j0yrelylkv9r9ysurhte0g2003r2wsqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qpqqqqqqqrg6vz7m9z8ufagn4z3ks0meqw4nyh4gfxvksfhne99egzsd3g3w9). Once I got over the initial shock, I decided I couldn't just curse and lament; I needed to do something bigger, something symbolic, something expressive. So that's exactly what I did—breaking nostr:nprofile1qy88wumn8ghj7mn0wvhxcmmv9uq32amnwvaz7tmjv4kxz7fwv3sk6atn9e5k7tcqyqewrqnkx4zsaweutf739s0cu7et29zrntqs5elw70vlm8zudr3y2t9v7jg's record which he held for almost 2 and half years. Here is a note with PoW 45, the highest PoW known to Nostr (as of now). nostr:nevent1qvzqqqqqqypzpmym6ar92346qc04ml08z6j0yrelylkv9r9ysurhte0g2003r2wsqy88wumn8ghj7mn0wvhxcmmv9uqsuamnwvaz7tmwdaejumr0dshsqgqqqqqqqqqy8t8awr5c8z4yfp4cr8v7spp8psncv8twlh083flcr582fyu9 ## How Did I Pull It Off? In theory, quite simple: Create note, run PoW mining script & wait. Thanks to PoW Draw, I already had mining software at hand: nostr:nprofile1qy88wumn8ghj7mn0wvhxcmmv9uq32amnwvaz7tmjv4kxz7fwv3sk6atn9e5k7tcqyqvqc5tlvn6etv09f0fvuauves49dvgnukjtzsndfv9y8yyrqyxmz7dty6z's [*notemine_hw*](https://github.com/plebemineira/notemine_hw), but when you know that there is a 1 in 2^45 chance that the next hash will be the correct one you want to increase the odds a bit. So on Monday evening, I started my Note Mining operation on an old 40 thread machine called Workhorse. ### Issues Along the Way I was immediately surprised that Workhorse (2× Intel Xeon Silver 4114) produced only about 3Mh/s. A laptop (Intel Core i7-1185G7) with Windows and all the bloat did 5Mh/s. That was strange. Another hurdle was that *notemine_hw* does not refresh the `created_at` field. With just a few Mh/s of power I was potentially looking at weeks of computation, by then the note would be quite stale. So I created systemd service leveraging the `RuntimeMaxSec` option to periodically restart every 3600 seconds assuring that the Note would be max 1 hour old at the time of publishing. Luckily PoW is that kind of problem where every hash attempt is an independent event, so the chance of success is the same whether you do it in small increments or one uninterrupted stretch. So by restarting the mining process I was only losing a few mere seconds every hour due to the overhead. Once the note staleness issue was resolved, I looked at the 40 workers on Workhorse vs. 7 workers on the laptop and start messing around with running one instance with 40 workers and running 40 instances with 1 worker and found out, that the workers are not bound to a CPU thread and are jumping between the CPUs like rabbits high on Colombian carrots. The solution? Running multiple instances with one worker each as a service locked to its own CPU core using systemd's `CPUAffinity` option. ``` $aida@workhorse:systemd/system $ sudo cat notemine@.service [Unit] Description=Notemine HW Publish (restarts hourly) [Service] Type=simple CPUAffinity=%i # The command to run: ExecStart=/home/aida/.cargo/bin/notemine_hw publish --n-workers 1 --difficulty 45 --event-json /home/aida/note.json --relay-url 'wss://wot.shaving.kiwi' --nsec nsec0123456789abcdef # Let the process run for 1 hour (3600 seconds), then systemd will stop it: RuntimeMaxSec=3600 TimeoutStopSec=1 # Tells systemd to restart the service automatically after it stops: Restart=always RestartSec=1 # run as a non-root user: User=aida Group=aida [Install] WantedBy=multi-user.target ``` Then I added a starting service to spawn an instance for each CPU thread. ``` $aida@workhorse:systemd/system $ sudo cat notemine_start.service [Unit] Description=Start all services in sequence with 3-second intervals [Service] Type=oneshot ExecStart=/usr/bin/zsh /home/aida/notemine_start.sh RemainAfterExit=yes [Install] WantedBy=multi-user.target ``` Here is the startup script (I know, loops exist—but Ctrl+C/Ctrl+V is so old-school): ``` aida@workhorse:~ $ cat notemine_start.sh /usr/bin/systemctl start notemine@0.service /usr/bin/sleep 3 /usr/bin/systemctl start notemine@1.service /usr/bin/sleep 3 /usr/bin/systemctl start notemine@2.service /usr/bin/sleep 3 /usr/bin/systemctl start notemine@3.service /usr/bin/sleep 3 ... ... ... /usr/bin/systemctl start notemine@38.service ``` The sleep there is critical to make sure that the `created_at`timestamps are different, preventing redundant hashing. **This adjustment made Workhorse the strongest machine in my fleet with 10+Mh/s.** ## The Luck Aspect From Monday evening, I started adding all machines at my disposal into the fleet and by Wednesday evening I was crunching hashes on about 130 CPU threads (a lot of them were quite antique) and at the peak was just little shy of 40Mh/s. To compensate for the slow start with the few above-mentioned hiccups and the fact that I had to use my desktop to do other things from time to time, I counted with the conservative estimate of 30Mh/s when I was doing all the probability calculations.  Based on the type of task that PoW mining is, the outcome is not predictible. You are only looking at what is the chance that the outcome of every single independent event will be consecutively non-favourable and then subtracting it from 1 to get the chance of that single favourable event you want. I really had to brush up on my combinatorics and discrete mathematics to make sure I have at least an elementary understanding of what is going on. Also, because we are not just throwing a dice 5 times, but are operating with big numbers, approximation was necessary. Luckily, the formula is available and quite simple in the end. 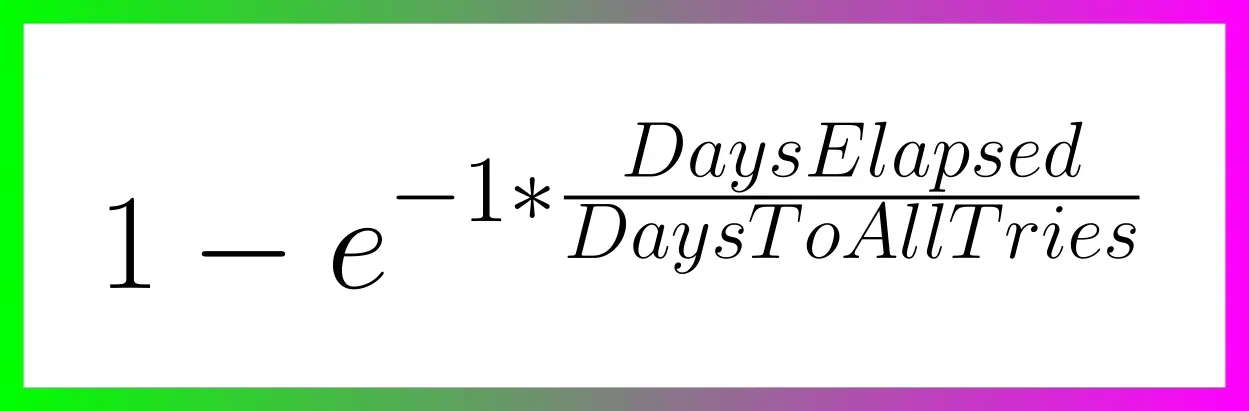 Two weeks to exhauste all the possible tries still doesn't guarantee anything, actually there is a slighlty less than 2 in 3 chance that you will have a result after all that time. So the fact that I was able to hit the right hash in less than 3 days was good luck. Not insane lottery winning luck, but good luck; slighlty lower than 1 in 5. ## Do you want to beat me? Go ahead! All the pitfalls are described above and until there is a GPU-based PoW Mining available, we are all on pretty even ground. ## Do you hate the note? In that case, feel free to enjoy this accompanying image: 
@ ec9bd746:df11a9d0
2025-03-07 20:13:38I was diving into PoW (Proof-of-Work) once again after nostr:nprofile1qy88wumn8ghj7mn0wvhxcmmv9uq3wamnwvaz7tmjv4kxz7fwdehhxarj9e3xzmny9uqzqj8a67jths8euy33v5yu6me6ngua5v3y3qq3dswuqh2pejmtls6datagmu rekindled my interest with his PoW Draw project. It was a fun little trifle, but it shifted my focus just the right way at the right time. Because then, on Friday, came the [Oval Office Travesty](nostr:nevent1qvzqqqqqqypzpmym6ar92346qc04ml08z6j0yrelylkv9r9ysurhte0g2003r2wsqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qpqqqqqqqrg6vz7m9z8ufagn4z3ks0meqw4nyh4gfxvksfhne99egzsd3g3w9). Once I got over the initial shock, I decided I couldn't just curse and lament; I needed to do something bigger, something symbolic, something expressive. So that's exactly what I did—breaking nostr:nprofile1qy88wumn8ghj7mn0wvhxcmmv9uq32amnwvaz7tmjv4kxz7fwv3sk6atn9e5k7tcqyqewrqnkx4zsaweutf739s0cu7et29zrntqs5elw70vlm8zudr3y2t9v7jg's record which he held for almost 2 and half years. Here is a note with PoW 45, the highest PoW known to Nostr (as of now). nostr:nevent1qvzqqqqqqypzpmym6ar92346qc04ml08z6j0yrelylkv9r9ysurhte0g2003r2wsqy88wumn8ghj7mn0wvhxcmmv9uqsuamnwvaz7tmwdaejumr0dshsqgqqqqqqqqqy8t8awr5c8z4yfp4cr8v7spp8psncv8twlh083flcr582fyu9 ## How Did I Pull It Off? In theory, quite simple: Create note, run PoW mining script & wait. Thanks to PoW Draw, I already had mining software at hand: nostr:nprofile1qy88wumn8ghj7mn0wvhxcmmv9uq32amnwvaz7tmjv4kxz7fwv3sk6atn9e5k7tcqyqvqc5tlvn6etv09f0fvuauves49dvgnukjtzsndfv9y8yyrqyxmz7dty6z's [*notemine_hw*](https://github.com/plebemineira/notemine_hw), but when you know that there is a 1 in 2^45 chance that the next hash will be the correct one you want to increase the odds a bit. So on Monday evening, I started my Note Mining operation on an old 40 thread machine called Workhorse. ### Issues Along the Way I was immediately surprised that Workhorse (2× Intel Xeon Silver 4114) produced only about 3Mh/s. A laptop (Intel Core i7-1185G7) with Windows and all the bloat did 5Mh/s. That was strange. Another hurdle was that *notemine_hw* does not refresh the `created_at` field. With just a few Mh/s of power I was potentially looking at weeks of computation, by then the note would be quite stale. So I created systemd service leveraging the `RuntimeMaxSec` option to periodically restart every 3600 seconds assuring that the Note would be max 1 hour old at the time of publishing. Luckily PoW is that kind of problem where every hash attempt is an independent event, so the chance of success is the same whether you do it in small increments or one uninterrupted stretch. So by restarting the mining process I was only losing a few mere seconds every hour due to the overhead. Once the note staleness issue was resolved, I looked at the 40 workers on Workhorse vs. 7 workers on the laptop and start messing around with running one instance with 40 workers and running 40 instances with 1 worker and found out, that the workers are not bound to a CPU thread and are jumping between the CPUs like rabbits high on Colombian carrots. The solution? Running multiple instances with one worker each as a service locked to its own CPU core using systemd's `CPUAffinity` option. ``` $aida@workhorse:systemd/system $ sudo cat notemine@.service [Unit] Description=Notemine HW Publish (restarts hourly) [Service] Type=simple CPUAffinity=%i # The command to run: ExecStart=/home/aida/.cargo/bin/notemine_hw publish --n-workers 1 --difficulty 45 --event-json /home/aida/note.json --relay-url 'wss://wot.shaving.kiwi' --nsec nsec0123456789abcdef # Let the process run for 1 hour (3600 seconds), then systemd will stop it: RuntimeMaxSec=3600 TimeoutStopSec=1 # Tells systemd to restart the service automatically after it stops: Restart=always RestartSec=1 # run as a non-root user: User=aida Group=aida [Install] WantedBy=multi-user.target ``` Then I added a starting service to spawn an instance for each CPU thread. ``` $aida@workhorse:systemd/system $ sudo cat notemine_start.service [Unit] Description=Start all services in sequence with 3-second intervals [Service] Type=oneshot ExecStart=/usr/bin/zsh /home/aida/notemine_start.sh RemainAfterExit=yes [Install] WantedBy=multi-user.target ``` Here is the startup script (I know, loops exist—but Ctrl+C/Ctrl+V is so old-school): ``` aida@workhorse:~ $ cat notemine_start.sh /usr/bin/systemctl start notemine@0.service /usr/bin/sleep 3 /usr/bin/systemctl start notemine@1.service /usr/bin/sleep 3 /usr/bin/systemctl start notemine@2.service /usr/bin/sleep 3 /usr/bin/systemctl start notemine@3.service /usr/bin/sleep 3 ... ... ... /usr/bin/systemctl start notemine@38.service ``` The sleep there is critical to make sure that the `created_at`timestamps are different, preventing redundant hashing. **This adjustment made Workhorse the strongest machine in my fleet with 10+Mh/s.** ## The Luck Aspect From Monday evening, I started adding all machines at my disposal into the fleet and by Wednesday evening I was crunching hashes on about 130 CPU threads (a lot of them were quite antique) and at the peak was just little shy of 40Mh/s. To compensate for the slow start with the few above-mentioned hiccups and the fact that I had to use my desktop to do other things from time to time, I counted with the conservative estimate of 30Mh/s when I was doing all the probability calculations.  Based on the type of task that PoW mining is, the outcome is not predictible. You are only looking at what is the chance that the outcome of every single independent event will be consecutively non-favourable and then subtracting it from 1 to get the chance of that single favourable event you want. I really had to brush up on my combinatorics and discrete mathematics to make sure I have at least an elementary understanding of what is going on. Also, because we are not just throwing a dice 5 times, but are operating with big numbers, approximation was necessary. Luckily, the formula is available and quite simple in the end. 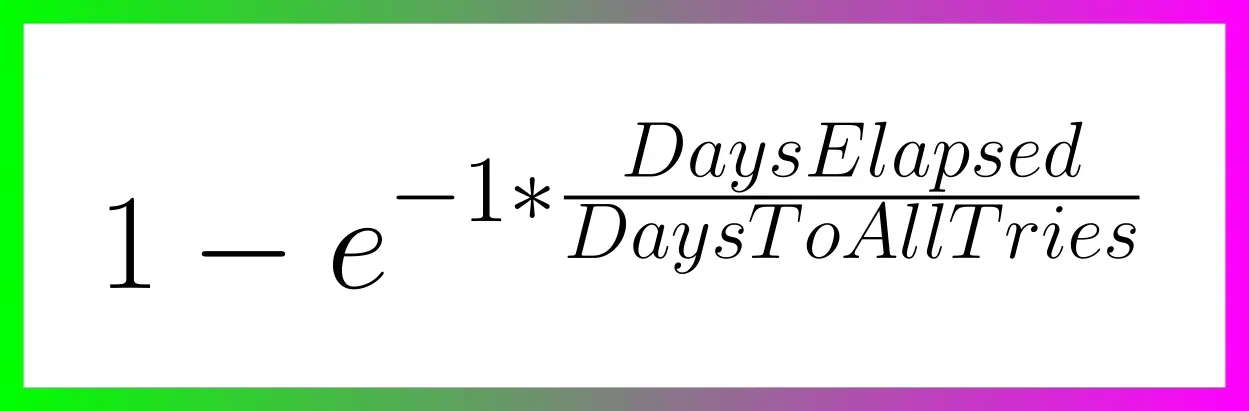 Two weeks to exhauste all the possible tries still doesn't guarantee anything, actually there is a slighlty less than 2 in 3 chance that you will have a result after all that time. So the fact that I was able to hit the right hash in less than 3 days was good luck. Not insane lottery winning luck, but good luck; slighlty lower than 1 in 5. ## Do you want to beat me? Go ahead! All the pitfalls are described above and until there is a GPU-based PoW Mining available, we are all on pretty even ground. ## Do you hate the note? In that case, feel free to enjoy this accompanying image:  @ a95c6243:d345522c
2025-03-04 09:40:50**Die «Eliten» führen bereits groß angelegte Pilotprojekte für eine Zukunft durch,** die sie wollen und wir nicht. Das [schreibt](https://off-guardian.org/2025/02/26/coming-soon-the-european-digital-identity-wallet/) der *OffGuardian* in einem Update zum Thema «EU-Brieftasche für die digitale Identität». Das Portal weist darauf hin, dass die Akteure dabei nicht gerade zimperlich vorgehen und auch keinen Hehl aus ihren Absichten machen. *Transition News* hat mehrfach darüber berichtet, zuletzt [hier](https://transition-news.org/eudi-wallet-der-weg-fur-ein-vollstandig-digitalisiertes-europa-ist-frei) und [hier](https://transition-news.org/iata-biometrische-daten-und-digitale-id-machen-das-vollstandig-digitale). **Mit der EU Digital Identity Wallet (EUDI-Brieftasche) sei eine einzige von der Regierung herausgegebene App geplant,** die Ihre medizinischen Daten, Beschäftigungsdaten, Reisedaten, Bildungsdaten, Impfdaten, Steuerdaten, Finanzdaten sowie (potenziell) Kopien Ihrer Unterschrift, Fingerabdrücke, Gesichtsscans, Stimmproben und DNA enthält. So fasst der *OffGuardian* die eindrucksvolle Liste möglicher Einsatzbereiche zusammen. **Auch Dokumente wie der Personalausweis oder der** **[Führerschein](https://transition-news.org/eu-weite-einfuhrung-von-digitalen-fuhrerscheinen-fur-digitale-geldborsen)** können dort in elektronischer Form gespeichert werden. Bis 2026 sind alle EU-Mitgliedstaaten dazu verpflichtet, Ihren Bürgern funktionierende und frei verfügbare digitale «Brieftaschen» bereitzustellen. **Die Menschen würden diese App nutzen,** so das Portal, um Zahlungen vorzunehmen, Kredite zu beantragen, ihre Steuern zu zahlen, ihre Rezepte abzuholen, internationale Grenzen zu überschreiten, Unternehmen zu gründen, Arzttermine zu buchen, sich um Stellen zu bewerben und sogar digitale Verträge online zu unterzeichnen. **All diese Daten würden auf ihrem Mobiltelefon gespeichert und mit den Regierungen** von neunzehn Ländern (plus der Ukraine) sowie über 140 anderen öffentlichen und privaten Partnern ausgetauscht. Von der Deutschen Bank über das ukrainische Ministerium für digitalen Fortschritt bis hin zu Samsung Europe. Unternehmen und Behörden würden auf diese Daten im Backend zugreifen, um «automatisierte Hintergrundprüfungen» durchzuführen. **Der Bundesverband der Verbraucherzentralen und Verbraucherverbände** (VZBV) habe Bedenken geäußert, dass eine solche App «Risiken für den Schutz der Privatsphäre und der Daten» berge, berichtet das Portal. Die einzige Antwort darauf laute: «Richtig, genau dafür ist sie ja da!» **Das alles sei keine Hypothese, betont der** ***OffGuardian***. Es sei vielmehr [«Potential»](https://www.digital-identity-wallet.eu/about-us/140-public-and-private-partners/). Damit ist ein EU-Projekt gemeint, in dessen Rahmen Dutzende öffentliche und private Einrichtungen zusammenarbeiten, «um eine einheitliche Vision der digitalen Identität für die Bürger der europäischen Länder zu definieren». Dies ist nur eines der groß angelegten [Pilotprojekte](https://ec.europa.eu/digital-building-blocks/sites/display/EUDIGITALIDENTITYWALLET/What+are+the+Large+Scale+Pilot+Projects), mit denen Prototypen und Anwendungsfälle für die EUDI-Wallet getestet werden. Es gibt noch mindestens drei weitere. **Den Ball der digitalen ID-Systeme habe die Covid-«Pandemie»** über die «Impfpässe» ins Rollen gebracht. Seitdem habe das Thema an Schwung verloren. Je näher wir aber der vollständigen Einführung der EUid kämen, desto mehr Propaganda der Art «Warum wir eine digitale Brieftasche brauchen» könnten wir in den Mainstream-Medien erwarten, prognostiziert der *OffGuardian*. Vielleicht müssten wir schon nach dem nächsten großen «Grund», dem nächsten «katastrophalen katalytischen Ereignis» Ausschau halten. Vermutlich gebe es bereits Pläne, warum die Menschen plötzlich eine digitale ID-Brieftasche brauchen würden. **Die Entwicklung geht jedenfalls stetig weiter in genau diese Richtung.** Beispielsweise hat Jordanien angekündigt, die digitale biometrische ID bei den nächsten [Wahlen](https://www.biometricupdate.com/202502/jordan-plans-digital-id-for-voter-verification-in-next-election) zur Verifizierung der Wähler einzuführen. Man wolle «den Papierkrieg beenden und sicherstellen, dass die gesamte Kette bis zu den nächsten Parlamentswahlen digitalisiert wird», heißt es. Absehbar ist, dass dabei einige Wahlberechtigte «auf der Strecke bleiben» werden, wie im Fall von [Albanien](https://transition-news.org/albanien-schliesst-120-000-burger-ohne-biometrische-ausweise-von-wahlen-aus) geschehen. **Derweil würden die Briten gerne ihre Privatsphäre gegen Effizienz eintauschen,** [behauptet](https://www.lbc.co.uk/news/tony-blair-id-cards/) Tony Blair. Der Ex-Premier drängte kürzlich erneut auf digitale Identitäten und Gesichtserkennung. Blair ist Gründer einer [Denkfabrik](https://transition-news.org/blair-institute-durch-vermarktung-von-patientendaten-zu-ki-gestutztem) für globalen Wandel, Anhänger globalistischer Technokratie und [«moderner Infrastruktur»](https://transition-news.org/tony-blair-digitale-id-fur-moderne-infrastruktur-unerlasslich-erfordert-aber). **Abschließend warnt der** ***OffGuardian*** **vor der Illusion, Trump und Musk würden** den US-Bürgern «diesen Schlamassel ersparen». Das Department of Government Efficiency werde sich auf die digitale Identität stürzen. Was könne schließlich «effizienter» sein als eine einzige App, die für alles verwendet wird? Der Unterschied bestehe nur darin, dass die US-Version vielleicht eher privat als öffentlich sei – sofern es da überhaupt noch einen wirklichen Unterschied gebe. *\[Titelbild: Screenshot* *[OffGuardian](https://off-guardian.org/2025/02/26/coming-soon-the-european-digital-identity-wallet/)]* *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/demnachst-verfugbar-die-europaische-brieftasche-fur-digitale-identitaten)*** erschienen.
@ a95c6243:d345522c
2025-03-04 09:40:50**Die «Eliten» führen bereits groß angelegte Pilotprojekte für eine Zukunft durch,** die sie wollen und wir nicht. Das [schreibt](https://off-guardian.org/2025/02/26/coming-soon-the-european-digital-identity-wallet/) der *OffGuardian* in einem Update zum Thema «EU-Brieftasche für die digitale Identität». Das Portal weist darauf hin, dass die Akteure dabei nicht gerade zimperlich vorgehen und auch keinen Hehl aus ihren Absichten machen. *Transition News* hat mehrfach darüber berichtet, zuletzt [hier](https://transition-news.org/eudi-wallet-der-weg-fur-ein-vollstandig-digitalisiertes-europa-ist-frei) und [hier](https://transition-news.org/iata-biometrische-daten-und-digitale-id-machen-das-vollstandig-digitale). **Mit der EU Digital Identity Wallet (EUDI-Brieftasche) sei eine einzige von der Regierung herausgegebene App geplant,** die Ihre medizinischen Daten, Beschäftigungsdaten, Reisedaten, Bildungsdaten, Impfdaten, Steuerdaten, Finanzdaten sowie (potenziell) Kopien Ihrer Unterschrift, Fingerabdrücke, Gesichtsscans, Stimmproben und DNA enthält. So fasst der *OffGuardian* die eindrucksvolle Liste möglicher Einsatzbereiche zusammen. **Auch Dokumente wie der Personalausweis oder der** **[Führerschein](https://transition-news.org/eu-weite-einfuhrung-von-digitalen-fuhrerscheinen-fur-digitale-geldborsen)** können dort in elektronischer Form gespeichert werden. Bis 2026 sind alle EU-Mitgliedstaaten dazu verpflichtet, Ihren Bürgern funktionierende und frei verfügbare digitale «Brieftaschen» bereitzustellen. **Die Menschen würden diese App nutzen,** so das Portal, um Zahlungen vorzunehmen, Kredite zu beantragen, ihre Steuern zu zahlen, ihre Rezepte abzuholen, internationale Grenzen zu überschreiten, Unternehmen zu gründen, Arzttermine zu buchen, sich um Stellen zu bewerben und sogar digitale Verträge online zu unterzeichnen. **All diese Daten würden auf ihrem Mobiltelefon gespeichert und mit den Regierungen** von neunzehn Ländern (plus der Ukraine) sowie über 140 anderen öffentlichen und privaten Partnern ausgetauscht. Von der Deutschen Bank über das ukrainische Ministerium für digitalen Fortschritt bis hin zu Samsung Europe. Unternehmen und Behörden würden auf diese Daten im Backend zugreifen, um «automatisierte Hintergrundprüfungen» durchzuführen. **Der Bundesverband der Verbraucherzentralen und Verbraucherverbände** (VZBV) habe Bedenken geäußert, dass eine solche App «Risiken für den Schutz der Privatsphäre und der Daten» berge, berichtet das Portal. Die einzige Antwort darauf laute: «Richtig, genau dafür ist sie ja da!» **Das alles sei keine Hypothese, betont der** ***OffGuardian***. Es sei vielmehr [«Potential»](https://www.digital-identity-wallet.eu/about-us/140-public-and-private-partners/). Damit ist ein EU-Projekt gemeint, in dessen Rahmen Dutzende öffentliche und private Einrichtungen zusammenarbeiten, «um eine einheitliche Vision der digitalen Identität für die Bürger der europäischen Länder zu definieren». Dies ist nur eines der groß angelegten [Pilotprojekte](https://ec.europa.eu/digital-building-blocks/sites/display/EUDIGITALIDENTITYWALLET/What+are+the+Large+Scale+Pilot+Projects), mit denen Prototypen und Anwendungsfälle für die EUDI-Wallet getestet werden. Es gibt noch mindestens drei weitere. **Den Ball der digitalen ID-Systeme habe die Covid-«Pandemie»** über die «Impfpässe» ins Rollen gebracht. Seitdem habe das Thema an Schwung verloren. Je näher wir aber der vollständigen Einführung der EUid kämen, desto mehr Propaganda der Art «Warum wir eine digitale Brieftasche brauchen» könnten wir in den Mainstream-Medien erwarten, prognostiziert der *OffGuardian*. Vielleicht müssten wir schon nach dem nächsten großen «Grund», dem nächsten «katastrophalen katalytischen Ereignis» Ausschau halten. Vermutlich gebe es bereits Pläne, warum die Menschen plötzlich eine digitale ID-Brieftasche brauchen würden. **Die Entwicklung geht jedenfalls stetig weiter in genau diese Richtung.** Beispielsweise hat Jordanien angekündigt, die digitale biometrische ID bei den nächsten [Wahlen](https://www.biometricupdate.com/202502/jordan-plans-digital-id-for-voter-verification-in-next-election) zur Verifizierung der Wähler einzuführen. Man wolle «den Papierkrieg beenden und sicherstellen, dass die gesamte Kette bis zu den nächsten Parlamentswahlen digitalisiert wird», heißt es. Absehbar ist, dass dabei einige Wahlberechtigte «auf der Strecke bleiben» werden, wie im Fall von [Albanien](https://transition-news.org/albanien-schliesst-120-000-burger-ohne-biometrische-ausweise-von-wahlen-aus) geschehen. **Derweil würden die Briten gerne ihre Privatsphäre gegen Effizienz eintauschen,** [behauptet](https://www.lbc.co.uk/news/tony-blair-id-cards/) Tony Blair. Der Ex-Premier drängte kürzlich erneut auf digitale Identitäten und Gesichtserkennung. Blair ist Gründer einer [Denkfabrik](https://transition-news.org/blair-institute-durch-vermarktung-von-patientendaten-zu-ki-gestutztem) für globalen Wandel, Anhänger globalistischer Technokratie und [«moderner Infrastruktur»](https://transition-news.org/tony-blair-digitale-id-fur-moderne-infrastruktur-unerlasslich-erfordert-aber). **Abschließend warnt der** ***OffGuardian*** **vor der Illusion, Trump und Musk würden** den US-Bürgern «diesen Schlamassel ersparen». Das Department of Government Efficiency werde sich auf die digitale Identität stürzen. Was könne schließlich «effizienter» sein als eine einzige App, die für alles verwendet wird? Der Unterschied bestehe nur darin, dass die US-Version vielleicht eher privat als öffentlich sei – sofern es da überhaupt noch einen wirklichen Unterschied gebe. *\[Titelbild: Screenshot* *[OffGuardian](https://off-guardian.org/2025/02/26/coming-soon-the-european-digital-identity-wallet/)]* *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/demnachst-verfugbar-die-europaische-brieftasche-fur-digitale-identitaten)*** erschienen. @ a95c6243:d345522c
2025-03-01 10:39:35*Ständige Lügen und Unterstellungen, permanent falsche Fürsorge* *\ können Bausteine von emotionaler Manipulation sein. Mit dem Zweck,* *\ Macht und Kontrolle über eine andere Person auszuüben.* *\ Apotheken Umschau*   **Irgendetwas muss passiert sein: «Gaslighting» ist gerade Thema** in vielen Medien. Heute bin ich nach längerer Zeit mal wieder über dieses Stichwort gestolpert. Das war in einem [Artikel](https://norberthaering.de/propaganda-zensur/dwd-referenzperiode/) von Norbert Häring über Manipulationen des Deutschen Wetterdienstes (DWD). In diesem Fall ging es um eine Pressemitteilung vom Donnerstag zum «viel zu warmen» Winter 2024/25. **Häring wirft der Behörde vor, dreist zu lügen und Dinge auszulassen,** um die Klimaangst wach zu halten. Was der Leser beim DWD nicht erfahre, sei, dass dieser Winter kälter als die drei vorangegangenen und kälter als der Durchschnitt der letzten zehn Jahre gewesen sei. Stattdessen werde der falsche Eindruck vermittelt, es würde ungebremst immer wärmer. **Wem also der zu Ende gehende Winter eher kalt vorgekommen sein sollte,** mit dessen Empfinden stimme wohl etwas nicht. Das jedenfalls wolle der DWD uns einreden, so der Wirtschaftsjournalist. Und damit sind wir beim Thema Gaslighting. **Als** **[Gaslighting](https://bayern-gegen-gewalt.de/gewalt-infos-und-einblicke/formen-von-gewalt/psychische-gewalt/gaslighting/)** **wird eine Form psychischer Manipulation bezeichnet,** mit der die Opfer desorientiert und zutiefst verunsichert werden, indem ihre eigene Wahrnehmung als falsch bezeichnet wird. Der Prozess führt zu Angst und Realitätsverzerrung sowie zur Zerstörung des Selbstbewusstseins. Die Bezeichnung kommt von dem britischen Theaterstück «Gas Light» aus dem Jahr 1938, in dem ein Mann mit grausamen Psychotricks seine Frau in den Wahnsinn treibt. **Damit Gaslighting funktioniert, muss das Opfer dem Täter vertrauen.** Oft wird solcher Psychoterror daher im privaten oder familiären Umfeld beschrieben, ebenso wie am Arbeitsplatz. Jedoch eignen sich die Prinzipien auch perfekt zur Manipulation der Massen. Vermeintliche Autoritäten wie Ärzte und Wissenschaftler, oder «der fürsorgliche Staat» und Institutionen wie die UNO oder die WHO wollen uns doch nichts Böses. Auch Staatsmedien, Faktenchecker und diverse NGOs wurden zu «vertrauenswürdigen Quellen» erklärt. Das hat seine Wirkung. **Warum das Thema Gaslighting derzeit scheinbar so populär ist,** vermag ich nicht zu sagen. Es sind aber gerade in den letzten Tagen und Wochen auffällig viele Artikel dazu erschienen, und zwar nicht nur von Psychologen. Die *Frankfurter Rundschau* hat gleich mehrere publiziert, und [Anwälte](https://www.anwalt.de/rechtstipps/gaslighting-beispiele-anzeichen-strafbarkeit-212449.html) interessieren sich dafür offenbar genauso wie Apotheker. **Die** ***Apotheken Umschau*** **machte sogar auf** **[«Medical Gaslighting»](https://archive.is/Wx5YM)** **aufmerksam.** Davon spreche man, wenn Mediziner Symptome nicht ernst nähmen oder wenn ein gesundheitliches Problem vom behandelnden Arzt «schnöde heruntergespielt» oder abgetan würde. Kommt Ihnen das auch irgendwie bekannt vor? Der Begriff sei allerdings irreführend, da er eine manipulierende Absicht unterstellt, die «nicht gewährleistet» sei. **Apropos Gaslighting: Die noch amtierende deutsche Bundesregierung** [meldete](https://www.bundesregierung.de/breg-de/service/newsletter-und-abos/bundesregierung-aktuell/ausgabe-08-2025-februar-28-2336254?view=renderNewsletterHtml) heute, es gelte, «weiter \[sic!] gemeinsam daran zu arbeiten, einen gerechten und dauerhaften Frieden für die Ukraine zu erreichen». Die Ukraine, wo sich am Montag «der völkerrechtswidrige Angriffskrieg zum dritten Mal jährte», [verteidige](https://transition-news.org/wikileaks-der-westen-wusste-dass-ein-nato-beitritt-der-ukraine-riskant-war) ihr Land und «unsere gemeinsamen Werte». **Merken Sie etwas? Das Demokratieverständnis mag ja tatsächlich** inzwischen in beiden Ländern ähnlich traurig sein. Bezüglich Friedensbemühungen ist meine Wahrnehmung jedoch eine andere. Das muss an meinem Gedächtnis liegen. *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/bitte-nicht-von-gaslichtern-irritieren-lassen)*** erschienen.
@ a95c6243:d345522c
2025-03-01 10:39:35*Ständige Lügen und Unterstellungen, permanent falsche Fürsorge* *\ können Bausteine von emotionaler Manipulation sein. Mit dem Zweck,* *\ Macht und Kontrolle über eine andere Person auszuüben.* *\ Apotheken Umschau*   **Irgendetwas muss passiert sein: «Gaslighting» ist gerade Thema** in vielen Medien. Heute bin ich nach längerer Zeit mal wieder über dieses Stichwort gestolpert. Das war in einem [Artikel](https://norberthaering.de/propaganda-zensur/dwd-referenzperiode/) von Norbert Häring über Manipulationen des Deutschen Wetterdienstes (DWD). In diesem Fall ging es um eine Pressemitteilung vom Donnerstag zum «viel zu warmen» Winter 2024/25. **Häring wirft der Behörde vor, dreist zu lügen und Dinge auszulassen,** um die Klimaangst wach zu halten. Was der Leser beim DWD nicht erfahre, sei, dass dieser Winter kälter als die drei vorangegangenen und kälter als der Durchschnitt der letzten zehn Jahre gewesen sei. Stattdessen werde der falsche Eindruck vermittelt, es würde ungebremst immer wärmer. **Wem also der zu Ende gehende Winter eher kalt vorgekommen sein sollte,** mit dessen Empfinden stimme wohl etwas nicht. Das jedenfalls wolle der DWD uns einreden, so der Wirtschaftsjournalist. Und damit sind wir beim Thema Gaslighting. **Als** **[Gaslighting](https://bayern-gegen-gewalt.de/gewalt-infos-und-einblicke/formen-von-gewalt/psychische-gewalt/gaslighting/)** **wird eine Form psychischer Manipulation bezeichnet,** mit der die Opfer desorientiert und zutiefst verunsichert werden, indem ihre eigene Wahrnehmung als falsch bezeichnet wird. Der Prozess führt zu Angst und Realitätsverzerrung sowie zur Zerstörung des Selbstbewusstseins. Die Bezeichnung kommt von dem britischen Theaterstück «Gas Light» aus dem Jahr 1938, in dem ein Mann mit grausamen Psychotricks seine Frau in den Wahnsinn treibt. **Damit Gaslighting funktioniert, muss das Opfer dem Täter vertrauen.** Oft wird solcher Psychoterror daher im privaten oder familiären Umfeld beschrieben, ebenso wie am Arbeitsplatz. Jedoch eignen sich die Prinzipien auch perfekt zur Manipulation der Massen. Vermeintliche Autoritäten wie Ärzte und Wissenschaftler, oder «der fürsorgliche Staat» und Institutionen wie die UNO oder die WHO wollen uns doch nichts Böses. Auch Staatsmedien, Faktenchecker und diverse NGOs wurden zu «vertrauenswürdigen Quellen» erklärt. Das hat seine Wirkung. **Warum das Thema Gaslighting derzeit scheinbar so populär ist,** vermag ich nicht zu sagen. Es sind aber gerade in den letzten Tagen und Wochen auffällig viele Artikel dazu erschienen, und zwar nicht nur von Psychologen. Die *Frankfurter Rundschau* hat gleich mehrere publiziert, und [Anwälte](https://www.anwalt.de/rechtstipps/gaslighting-beispiele-anzeichen-strafbarkeit-212449.html) interessieren sich dafür offenbar genauso wie Apotheker. **Die** ***Apotheken Umschau*** **machte sogar auf** **[«Medical Gaslighting»](https://archive.is/Wx5YM)** **aufmerksam.** Davon spreche man, wenn Mediziner Symptome nicht ernst nähmen oder wenn ein gesundheitliches Problem vom behandelnden Arzt «schnöde heruntergespielt» oder abgetan würde. Kommt Ihnen das auch irgendwie bekannt vor? Der Begriff sei allerdings irreführend, da er eine manipulierende Absicht unterstellt, die «nicht gewährleistet» sei. **Apropos Gaslighting: Die noch amtierende deutsche Bundesregierung** [meldete](https://www.bundesregierung.de/breg-de/service/newsletter-und-abos/bundesregierung-aktuell/ausgabe-08-2025-februar-28-2336254?view=renderNewsletterHtml) heute, es gelte, «weiter \[sic!] gemeinsam daran zu arbeiten, einen gerechten und dauerhaften Frieden für die Ukraine zu erreichen». Die Ukraine, wo sich am Montag «der völkerrechtswidrige Angriffskrieg zum dritten Mal jährte», [verteidige](https://transition-news.org/wikileaks-der-westen-wusste-dass-ein-nato-beitritt-der-ukraine-riskant-war) ihr Land und «unsere gemeinsamen Werte». **Merken Sie etwas? Das Demokratieverständnis mag ja tatsächlich** inzwischen in beiden Ländern ähnlich traurig sein. Bezüglich Friedensbemühungen ist meine Wahrnehmung jedoch eine andere. Das muss an meinem Gedächtnis liegen. *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/bitte-nicht-von-gaslichtern-irritieren-lassen)*** erschienen. @ 7bdef7be:784a5805
2025-04-02 12:02:45We value sovereignty, privacy and security when accessing online content, using several tools to achieve this, like open protocols, open OSes, open software products, Tor and VPNs. ## The problem Talking about our social presence, we can manually build up our follower list (social graph), pick a Nostr client that is respectful of our preferences on what to show and how, but with the standard following mechanism, our main feed is public, \*\*so everyone can actually snoop\*\* what we are interested in, and what is supposable that we read daily. ## The solution Nostr has a simple solution for this necessity: encrypted lists. Lists are what they appear, a collection of people or interests (but they can also group much other stuff, see \[NIP-51\](https://github.com/nostr-protocol/nips/blob/master/51.md)). So we can create lists with contacts that we don't have in our main social graph; these lists can be used primarily to create \*\*dedicated feeds\*\*, but they could have other uses, for example, related to monitoring. The interesting thing about lists is that they can also be \*\*encrypted\*\*, so unlike the basic following list, which is always public, we can hide the lists' content from others. The implications are obvious: we can not only have a more organized way to browse content, but it is also \*\*really private one\*\*. One might wonder what use can really be made of private lists; here are some examples: - Browse “can't miss” content from users I consider a priority; - Supervise competitors or adversarial parts; - Monitor sensible topics (tags); - Following someone without being publicly associated with them, as this may be undesirable; The benefits in terms of privacy as usual are not only related to the casual, or programmatic, observer, but are also evident when we think of \*\*how many bots scan our actions to profile us\*\*. ## The current state Unfortunately, lists are not widely supported by Nostr clients, and encrypted support is a rarity. Often the excuse to not implement them is that they are harder to develop, since they require managing the encryption stuff (\[NIP-44\](https://github.com/nostr-protocol/nips/blob/master/51.md)). Nevertheless, developers have an easier option to start offering private lists: give the user the possibility to simply \*\*mark them as local-only\*\*, and never push them to the relays. Even if the user misses the sync feature, this is sufficient to create a private environment. To date, as far as I know, the best client with list management is Gossip, which permits to manage \*\*both encrypted and local-only lists\*\*. Beg your Nostr client to implement private lists!
@ 7bdef7be:784a5805
2025-04-02 12:02:45We value sovereignty, privacy and security when accessing online content, using several tools to achieve this, like open protocols, open OSes, open software products, Tor and VPNs. ## The problem Talking about our social presence, we can manually build up our follower list (social graph), pick a Nostr client that is respectful of our preferences on what to show and how, but with the standard following mechanism, our main feed is public, \*\*so everyone can actually snoop\*\* what we are interested in, and what is supposable that we read daily. ## The solution Nostr has a simple solution for this necessity: encrypted lists. Lists are what they appear, a collection of people or interests (but they can also group much other stuff, see \[NIP-51\](https://github.com/nostr-protocol/nips/blob/master/51.md)). So we can create lists with contacts that we don't have in our main social graph; these lists can be used primarily to create \*\*dedicated feeds\*\*, but they could have other uses, for example, related to monitoring. The interesting thing about lists is that they can also be \*\*encrypted\*\*, so unlike the basic following list, which is always public, we can hide the lists' content from others. The implications are obvious: we can not only have a more organized way to browse content, but it is also \*\*really private one\*\*. One might wonder what use can really be made of private lists; here are some examples: - Browse “can't miss” content from users I consider a priority; - Supervise competitors or adversarial parts; - Monitor sensible topics (tags); - Following someone without being publicly associated with them, as this may be undesirable; The benefits in terms of privacy as usual are not only related to the casual, or programmatic, observer, but are also evident when we think of \*\*how many bots scan our actions to profile us\*\*. ## The current state Unfortunately, lists are not widely supported by Nostr clients, and encrypted support is a rarity. Often the excuse to not implement them is that they are harder to develop, since they require managing the encryption stuff (\[NIP-44\](https://github.com/nostr-protocol/nips/blob/master/51.md)). Nevertheless, developers have an easier option to start offering private lists: give the user the possibility to simply \*\*mark them as local-only\*\*, and never push them to the relays. Even if the user misses the sync feature, this is sufficient to create a private environment. To date, as far as I know, the best client with list management is Gossip, which permits to manage \*\*both encrypted and local-only lists\*\*. Beg your Nostr client to implement private lists! @ 460c25e6:ef85065c
2025-02-25 15:20:39If you don't know where your posts are, you might as well just stay in the centralized Twitter. You either take control of your relay lists, or they will control you. Amethyst offers several lists of relays for our users. We are going to go one by one to help clarify what they are and which options are best for each one. ## Public Home/Outbox Relays Home relays store all YOUR content: all your posts, likes, replies, lists, etc. It's your home. Amethyst will send your posts here first. Your followers will use these relays to get new posts from you. So, if you don't have anything there, **they will not receive your updates**. Home relays must allow queries from anyone, ideally without the need to authenticate. They can limit writes to paid users without affecting anyone's experience. This list should have a maximum of 3 relays. More than that will only make your followers waste their mobile data getting your posts. Keep it simple. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of all your content in a place no one can delete. Go to [relay.tools](https://relay.tools/) and never be censored again. - 1 really fast relay located in your country: paid options like http://nostr.wine are great Do not include relays that block users from seeing posts in this list. If you do, no one will see your posts. ## Public Inbox Relays This relay type receives all replies, comments, likes, and zaps to your posts. If you are not getting notifications or you don't see replies from your friends, it is likely because you don't have the right setup here. If you are getting too much spam in your replies, it's probably because your inbox relays are not protecting you enough. Paid relays can filter inbox spam out. Inbox relays must allow anyone to write into them. It's the opposite of the outbox relay. They can limit who can download the posts to their paid subscribers without affecting anyone's experience. This list should have a maximum of 3 relays as well. Again, keep it small. More than that will just make you spend more of your data plan downloading the same notifications from all these different servers. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of your notifications, invites, cashu tokens and zaps. - 1 really fast relay located in your country: go to [nostr.watch](https://nostr.watch/relays/find) and find relays in your country Terrible options include: - nostr.wine should not be here. - filter.nostr.wine should not be here. - inbox.nostr.wine should not be here. ## DM Inbox Relays These are the relays used to receive DMs and private content. Others will use these relays to send DMs to you. **If you don't have it setup, you will miss DMs**. DM Inbox relays should accept any message from anyone, but only allow you to download them. Generally speaking, you only need 3 for reliability. One of them should be a personal relay to make sure you have a copy of all your messages. The others can be open if you want push notifications or closed if you want full privacy. Good options are: - inbox.nostr.wine and auth.nostr1.com: anyone can send messages and only you can download. Not even our push notification server has access to them to notify you. - a personal relay to make sure no one can censor you. Advanced settings on personal relays can also store your DMs privately. Talk to your relay operator for more details. - a public relay if you want DM notifications from our servers. Make sure to add at least one public relay if you want to see DM notifications. ## Private Home Relays Private Relays are for things no one should see, like your drafts, lists, app settings, bookmarks etc. Ideally, these relays are either local or require authentication before posting AND downloading each user\'s content. There are no dedicated relays for this category yet, so I would use a local relay like Citrine on Android and a personal relay on relay.tools. Keep in mind that if you choose a local relay only, a client on the desktop might not be able to see the drafts from clients on mobile and vice versa. ## Search relays: This is the list of relays to use on Amethyst's search and user tagging with @. **Tagging and searching will not work if there is nothing here.**. This option requires NIP-50 compliance from each relay. Hit the Default button to use all available options on existence today: - nostr.wine - relay.nostr.band - relay.noswhere.com ## Local Relays: This is your local storage. Everything will load faster if it comes from this relay. You should install Citrine on Android and write ws://localhost:4869 in this option. ## General Relays: This section contains the default relays used to download content from your follows. Notice how you can activate and deactivate the Home, Messages (old-style DMs), Chat (public chats), and Global options in each. Keep 5-6 large relays on this list and activate them for as many categories (Home, Messages (old-style DMs), Chat, and Global) as possible. Amethyst will provide additional recommendations to this list from your follows with information on which of your follows might need the additional relay in your list. Add them if you feel like you are missing their posts or if it is just taking too long to load them. ## My setup Here's what I use: 1. Go to [relay.tools](https://relay.tools/) and create a relay for yourself. 2. Go to [nostr.wine](https://nostr.wine/) and pay for their subscription. 3. Go to [inbox.nostr.wine](https://inbox.nostr.wine/) and pay for their subscription. 4. Go to [nostr.watch](https://nostr.watch/relays/find) and find a good relay in your country. 5. Download Citrine to your phone. Then, on your relay lists, put: Public Home/Outbox Relays: - nostr.wine - nos.lol or an in-country relay. - <your.relay>.nostr1.com Public Inbox Relays - nos.lol or an in-country relay - <your.relay>.nostr1.com DM Inbox Relays - inbox.nostr.wine - <your.relay>.nostr1.com Private Home Relays - ws://localhost:4869 (Citrine) - <your.relay>.nostr1.com (if you want) Search Relays - nostr.wine - relay.nostr.band - relay.noswhere.com Local Relays - ws://localhost:4869 (Citrine) General Relays - nos.lol - relay.damus.io - relay.primal.net - nostr.mom And a few of the recommended relays from Amethyst. ## Final Considerations Remember, relays can see what your Nostr client is requesting and downloading at all times. They can track what you see and see what you like. They can sell that information to the highest bidder, they can delete your content or content that a sponsor asked them to delete (like a negative review for instance) and they can censor you in any way they see fit. Before using any random free relay out there, make sure you trust its operator and you know its terms of service and privacy policies.
@ 460c25e6:ef85065c
2025-02-25 15:20:39If you don't know where your posts are, you might as well just stay in the centralized Twitter. You either take control of your relay lists, or they will control you. Amethyst offers several lists of relays for our users. We are going to go one by one to help clarify what they are and which options are best for each one. ## Public Home/Outbox Relays Home relays store all YOUR content: all your posts, likes, replies, lists, etc. It's your home. Amethyst will send your posts here first. Your followers will use these relays to get new posts from you. So, if you don't have anything there, **they will not receive your updates**. Home relays must allow queries from anyone, ideally without the need to authenticate. They can limit writes to paid users without affecting anyone's experience. This list should have a maximum of 3 relays. More than that will only make your followers waste their mobile data getting your posts. Keep it simple. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of all your content in a place no one can delete. Go to [relay.tools](https://relay.tools/) and never be censored again. - 1 really fast relay located in your country: paid options like http://nostr.wine are great Do not include relays that block users from seeing posts in this list. If you do, no one will see your posts. ## Public Inbox Relays This relay type receives all replies, comments, likes, and zaps to your posts. If you are not getting notifications or you don't see replies from your friends, it is likely because you don't have the right setup here. If you are getting too much spam in your replies, it's probably because your inbox relays are not protecting you enough. Paid relays can filter inbox spam out. Inbox relays must allow anyone to write into them. It's the opposite of the outbox relay. They can limit who can download the posts to their paid subscribers without affecting anyone's experience. This list should have a maximum of 3 relays as well. Again, keep it small. More than that will just make you spend more of your data plan downloading the same notifications from all these different servers. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of your notifications, invites, cashu tokens and zaps. - 1 really fast relay located in your country: go to [nostr.watch](https://nostr.watch/relays/find) and find relays in your country Terrible options include: - nostr.wine should not be here. - filter.nostr.wine should not be here. - inbox.nostr.wine should not be here. ## DM Inbox Relays These are the relays used to receive DMs and private content. Others will use these relays to send DMs to you. **If you don't have it setup, you will miss DMs**. DM Inbox relays should accept any message from anyone, but only allow you to download them. Generally speaking, you only need 3 for reliability. One of them should be a personal relay to make sure you have a copy of all your messages. The others can be open if you want push notifications or closed if you want full privacy. Good options are: - inbox.nostr.wine and auth.nostr1.com: anyone can send messages and only you can download. Not even our push notification server has access to them to notify you. - a personal relay to make sure no one can censor you. Advanced settings on personal relays can also store your DMs privately. Talk to your relay operator for more details. - a public relay if you want DM notifications from our servers. Make sure to add at least one public relay if you want to see DM notifications. ## Private Home Relays Private Relays are for things no one should see, like your drafts, lists, app settings, bookmarks etc. Ideally, these relays are either local or require authentication before posting AND downloading each user\'s content. There are no dedicated relays for this category yet, so I would use a local relay like Citrine on Android and a personal relay on relay.tools. Keep in mind that if you choose a local relay only, a client on the desktop might not be able to see the drafts from clients on mobile and vice versa. ## Search relays: This is the list of relays to use on Amethyst's search and user tagging with @. **Tagging and searching will not work if there is nothing here.**. This option requires NIP-50 compliance from each relay. Hit the Default button to use all available options on existence today: - nostr.wine - relay.nostr.band - relay.noswhere.com ## Local Relays: This is your local storage. Everything will load faster if it comes from this relay. You should install Citrine on Android and write ws://localhost:4869 in this option. ## General Relays: This section contains the default relays used to download content from your follows. Notice how you can activate and deactivate the Home, Messages (old-style DMs), Chat (public chats), and Global options in each. Keep 5-6 large relays on this list and activate them for as many categories (Home, Messages (old-style DMs), Chat, and Global) as possible. Amethyst will provide additional recommendations to this list from your follows with information on which of your follows might need the additional relay in your list. Add them if you feel like you are missing their posts or if it is just taking too long to load them. ## My setup Here's what I use: 1. Go to [relay.tools](https://relay.tools/) and create a relay for yourself. 2. Go to [nostr.wine](https://nostr.wine/) and pay for their subscription. 3. Go to [inbox.nostr.wine](https://inbox.nostr.wine/) and pay for their subscription. 4. Go to [nostr.watch](https://nostr.watch/relays/find) and find a good relay in your country. 5. Download Citrine to your phone. Then, on your relay lists, put: Public Home/Outbox Relays: - nostr.wine - nos.lol or an in-country relay. - <your.relay>.nostr1.com Public Inbox Relays - nos.lol or an in-country relay - <your.relay>.nostr1.com DM Inbox Relays - inbox.nostr.wine - <your.relay>.nostr1.com Private Home Relays - ws://localhost:4869 (Citrine) - <your.relay>.nostr1.com (if you want) Search Relays - nostr.wine - relay.nostr.band - relay.noswhere.com Local Relays - ws://localhost:4869 (Citrine) General Relays - nos.lol - relay.damus.io - relay.primal.net - nostr.mom And a few of the recommended relays from Amethyst. ## Final Considerations Remember, relays can see what your Nostr client is requesting and downloading at all times. They can track what you see and see what you like. They can sell that information to the highest bidder, they can delete your content or content that a sponsor asked them to delete (like a negative review for instance) and they can censor you in any way they see fit. Before using any random free relay out there, make sure you trust its operator and you know its terms of service and privacy policies. @ a95c6243:d345522c
2025-02-21 19:32:23*Europa – das Ganze ist eine wunderbare Idee,* *\ aber das war der Kommunismus auch.* *\ Loriot*   **«Europa hat fertig», könnte man unken,** und das wäre nicht einmal sehr verwegen. Mit solch einer [Einschätzung](https://transition-news.org/geopolitische-ohnmacht-und-die-last-des-euro-steht-die-eu-vor-der-implosion) stünden wir nicht alleine, denn die Stimmen in diese Richtung mehren sich. Der französische Präsident Emmanuel Macron warnte schon letztes Jahr davor, dass «unser Europa sterben könnte». Vermutlich hatte er dabei andere Gefahren im Kopf als jetzt der ungarische Ministerpräsident Viktor Orbán, der ein «baldiges Ende der EU» prognostizierte. Das Ergebnis könnte allerdings das gleiche sein. **Neben vordergründigen Themenbereichen wie Wirtschaft, Energie und Sicherheit** ist das eigentliche Problem jedoch die obskure Mischung aus aufgegebener Souveränität und geschwollener Arroganz, mit der europäische Politiker:innende unterschiedlicher Couleur aufzutreten pflegen. Und das Tüpfelchen auf dem i ist die bröckelnde Legitimation politischer Institutionen dadurch, dass die Stimmen großer Teile der Bevölkerung seit Jahren auf vielfältige Weise ausgegrenzt werden. **Um «UnsereDemokratie» steht es schlecht.** Dass seine Mandate immer schwächer werden, merkt natürlich auch unser «Führungspersonal». Entsprechend werden die Maßnahmen zur Gängelung, Überwachung und Manipulation der Bürger ständig verzweifelter. Parallel dazu [plustern](https://www.bundesregierung.de/breg-de/service/newsletter-und-abos/bundesregierung-aktuell/ausgabe-07-2025-februar-21-2335652?view=renderNewsletterHtml) sich in Paris Macron, Scholz und einige andere noch einmal mächtig in Sachen Verteidigung und [«Kriegstüchtigkeit»](https://transition-news.org/europaische-investitionsbank-tragt-zur-kriegstuchtigkeit-europas-bei) auf. **Momentan gilt es auch, das Überschwappen covidiotischer und verschwörungsideologischer Auswüchse** aus den USA nach Europa zu vermeiden. So ein «MEGA» (Make Europe Great Again) können wir hier nicht gebrauchen. Aus den Vereinigten Staaten kommen nämlich furchtbare Nachrichten. Beispielsweise wurde einer der schärfsten Kritiker der Corona-Maßnahmen kürzlich zum Gesundheitsminister ernannt. Dieser setzt sich jetzt für eine Neubewertung der mRNA-«Impfstoffe» ein, was durchaus zu einem [Entzug der Zulassungen](https://transition-news.org/usa-zulassungsentzug-fur-corona-impfstoffe-auf-der-tagesordnung) führen könnte. **Der europäischen Version von** **[«Verteidigung der Demokratie»](https://transition-news.org/eu-macht-freiwilligen-verhaltenskodex-gegen-desinformation-zu-bindendem-recht)** setzte der US-Vizepräsident J. D. Vance auf der Münchner Sicherheitskonferenz sein Verständnis entgegen: «Demokratie stärken, indem wir unseren Bürgern erlauben, ihre Meinung zu sagen». Das Abschalten von Medien, das Annullieren von Wahlen oder das Ausschließen von Menschen vom politischen Prozess schütze gar nichts. Vielmehr sei dies der todsichere Weg, die Demokratie zu zerstören. **In der Schweiz kamen seine Worte deutlich besser an** als in den meisten europäischen NATO-Ländern. Bundespräsidentin Karin Keller-Sutter lobte die Rede und interpretierte sie als «Plädoyer für die direkte Demokratie». Möglicherweise zeichne sich hier eine [außenpolitische Kehrtwende](https://transition-news.org/schweiz-vor-aussenpolitischer-kehrtwende-richtung-integraler-neutralitat) in Richtung integraler Neutralität ab, meint mein Kollege Daniel Funk. Das wären doch endlich mal ein paar gute Nachrichten. **Von der einstigen Idee einer europäischen Union** mit engeren Beziehungen zwischen den Staaten, um Konflikte zu vermeiden und das Wohlergehen der Bürger zu verbessern, sind wir meilenweit abgekommen. Der heutige korrupte Verbund unter technokratischer Leitung ähnelt mehr einem Selbstbedienungsladen mit sehr begrenztem Zugang. Die EU-Wahlen im letzten Sommer haben daran ebenso wenig geändert, wie die [Bundestagswahl](https://transition-news.org/bundestagswahl-mehr-aufrustung-statt-friedenskanzler-nach-der-wahl) am kommenden Sonntag darauf einen Einfluss haben wird. *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/europaer-seid-ihr-noch-zu-retten)*** erschienen.
@ a95c6243:d345522c
2025-02-21 19:32:23*Europa – das Ganze ist eine wunderbare Idee,* *\ aber das war der Kommunismus auch.* *\ Loriot*   **«Europa hat fertig», könnte man unken,** und das wäre nicht einmal sehr verwegen. Mit solch einer [Einschätzung](https://transition-news.org/geopolitische-ohnmacht-und-die-last-des-euro-steht-die-eu-vor-der-implosion) stünden wir nicht alleine, denn die Stimmen in diese Richtung mehren sich. Der französische Präsident Emmanuel Macron warnte schon letztes Jahr davor, dass «unser Europa sterben könnte». Vermutlich hatte er dabei andere Gefahren im Kopf als jetzt der ungarische Ministerpräsident Viktor Orbán, der ein «baldiges Ende der EU» prognostizierte. Das Ergebnis könnte allerdings das gleiche sein. **Neben vordergründigen Themenbereichen wie Wirtschaft, Energie und Sicherheit** ist das eigentliche Problem jedoch die obskure Mischung aus aufgegebener Souveränität und geschwollener Arroganz, mit der europäische Politiker:innende unterschiedlicher Couleur aufzutreten pflegen. Und das Tüpfelchen auf dem i ist die bröckelnde Legitimation politischer Institutionen dadurch, dass die Stimmen großer Teile der Bevölkerung seit Jahren auf vielfältige Weise ausgegrenzt werden. **Um «UnsereDemokratie» steht es schlecht.** Dass seine Mandate immer schwächer werden, merkt natürlich auch unser «Führungspersonal». Entsprechend werden die Maßnahmen zur Gängelung, Überwachung und Manipulation der Bürger ständig verzweifelter. Parallel dazu [plustern](https://www.bundesregierung.de/breg-de/service/newsletter-und-abos/bundesregierung-aktuell/ausgabe-07-2025-februar-21-2335652?view=renderNewsletterHtml) sich in Paris Macron, Scholz und einige andere noch einmal mächtig in Sachen Verteidigung und [«Kriegstüchtigkeit»](https://transition-news.org/europaische-investitionsbank-tragt-zur-kriegstuchtigkeit-europas-bei) auf. **Momentan gilt es auch, das Überschwappen covidiotischer und verschwörungsideologischer Auswüchse** aus den USA nach Europa zu vermeiden. So ein «MEGA» (Make Europe Great Again) können wir hier nicht gebrauchen. Aus den Vereinigten Staaten kommen nämlich furchtbare Nachrichten. Beispielsweise wurde einer der schärfsten Kritiker der Corona-Maßnahmen kürzlich zum Gesundheitsminister ernannt. Dieser setzt sich jetzt für eine Neubewertung der mRNA-«Impfstoffe» ein, was durchaus zu einem [Entzug der Zulassungen](https://transition-news.org/usa-zulassungsentzug-fur-corona-impfstoffe-auf-der-tagesordnung) führen könnte. **Der europäischen Version von** **[«Verteidigung der Demokratie»](https://transition-news.org/eu-macht-freiwilligen-verhaltenskodex-gegen-desinformation-zu-bindendem-recht)** setzte der US-Vizepräsident J. D. Vance auf der Münchner Sicherheitskonferenz sein Verständnis entgegen: «Demokratie stärken, indem wir unseren Bürgern erlauben, ihre Meinung zu sagen». Das Abschalten von Medien, das Annullieren von Wahlen oder das Ausschließen von Menschen vom politischen Prozess schütze gar nichts. Vielmehr sei dies der todsichere Weg, die Demokratie zu zerstören. **In der Schweiz kamen seine Worte deutlich besser an** als in den meisten europäischen NATO-Ländern. Bundespräsidentin Karin Keller-Sutter lobte die Rede und interpretierte sie als «Plädoyer für die direkte Demokratie». Möglicherweise zeichne sich hier eine [außenpolitische Kehrtwende](https://transition-news.org/schweiz-vor-aussenpolitischer-kehrtwende-richtung-integraler-neutralitat) in Richtung integraler Neutralität ab, meint mein Kollege Daniel Funk. Das wären doch endlich mal ein paar gute Nachrichten. **Von der einstigen Idee einer europäischen Union** mit engeren Beziehungen zwischen den Staaten, um Konflikte zu vermeiden und das Wohlergehen der Bürger zu verbessern, sind wir meilenweit abgekommen. Der heutige korrupte Verbund unter technokratischer Leitung ähnelt mehr einem Selbstbedienungsladen mit sehr begrenztem Zugang. Die EU-Wahlen im letzten Sommer haben daran ebenso wenig geändert, wie die [Bundestagswahl](https://transition-news.org/bundestagswahl-mehr-aufrustung-statt-friedenskanzler-nach-der-wahl) am kommenden Sonntag darauf einen Einfluss haben wird. *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/europaer-seid-ihr-noch-zu-retten)*** erschienen. @ d5c3d063:4d1159b3
2025-04-02 04:04:32"ผลิตผลทางเศรษฐกิจที่เพิ่มขึ้น เป็นประโยชน์กับทุกคนเสมอ ไม่ว่าในทางใดก็ทางหนึ่ง" เป็นโพสของอาจารย์พิริยะ ที่เรียกได้ว่าคือ “หลักการพื้นฐาน” ของเสรีภาพทางเศรษฐกิจ ที่หลายคนอาจหลงลืม และซุปอยากขยายความต่อ เพราะนี่คือจุดเริ่มต้นของคำว่า “ระบบที่แฟร์จริง” . เราถูกสอนให้คิดว่า ถ้ามีคนรวยขึ้น ต้องมีใครอีกคนจนลง แต่ในความเป็นจริง ระบบตลาดเสรีไม่ได้ทำงานแบบนั้นเลย เพราะเมื่อมีคนผลิตของที่ดีขึ้น ผลิตได้เร็วขึ้น ต้นทุนจะลดลง สินค้าที่เคยเข้าถึงยาก ก็เริ่มกลายเป็นของธรรมดาที่ใครก็ใช้ได้ . คนหนึ่งคนที่ผลิตเพิ่มขึ้น อาจได้กำไรมากขึ้น แต่คนอีกเป็นล้านกลับได้ใช้สินค้าที่ถูกลง ชีวิตง่ายขึ้น สะดวกขึ้น เห็นได้ชัดว่าทุกฝ่ายได้ประโยชน์ ไม่ใช่เพราะมีใครต้อง "เสียสละจากการบังคับ" แต่เพราะทุกคนแลกเปลี่ยนกัน "ด้วยความสมัครใจ" นี่คือหลักการที่เศรษฐศาสตร์สำนักออสเตรียนเชื่อมั่นมาตลอด ว่าเสรีภาพในการผลิตและแลกเปลี่ยน คือรากฐานของความมั่งคั่งร่วมกัน "การแบ่งงานกันทำ" ของคนที่ถนัดต่างกัน คือวิธีที่มนุษย์สร้างสังคมเจริญขึ้นมาได้จริง ไม่ใช่เพราะรัฐสั่งให้ทำ แต่เพราะทุกคนเห็นประโยชน์ร่วมกันและยินดีแลกเปลี่ยนกันเอง . ปัญหาคือ วันนี้เราไม่ได้อยู่ในตลาดเสรีจริง แต่เราอยู่ในระบบที่รัฐเข้ามาเขียนกติกา ออกใบอนุญาต ควบคุมอุตสาหกรรม กำหนดราคา และที่แย่คือการออกกฎที่เอื้อให้พวกพ้อง ทำให้บางคนได้เปรียบในตลาด โดยไม่ได้มาจากการผลิตเก่งหรือบริการดีแต่มาจากการมีสายสัมพันธ์กับอำนาจ (แบบนี้คือ ทุนนิยมพวกพ้อง) . แล้วคนทั่วไปที่เห็นภาพแบบนี้ ก็พากันเรียกร้องให้รัฐเข้ามาจัดการ ทั้งที่จริงแล้ว...คนที่ควรรับผิดชอบ คือรัฐเอง ที่เปิดช่องให้เรื่องพวกนี้เกิดขึ้นตั้งแต่แรก . เราจึงติดกับดักเดิมซ้ำๆ คือรัฐสร้างปัญหา แล้วใช้ปัญหานั้นเป็นข้ออ้างในการขยายอำนาจ สุดท้ายมันก็ยิ่งบิดเบือนระบบเศรษฐกิจให้ผิดเพี้ยนเข้าไปอีก จนคนทำงานจริง ผลิตของจริง กลับไม่มีที่ยืนในระบบ . . ให้เห็นภาพต่อว่า ถ้ามีคนผลิตมากขึ้น ทุกคนในระบบจะได้ประโยชน์เพิ่มขึ้นเสมอ ตราบใดที่ 1 เขาไม่ได้ขโมยใคร 2 เขาแลกเปลี่ยนบนความสมัครใจ เท่านั้นยังไม่พอ 3 "เงิน" มันต้องเป็นกระจกสะท้อนคุณค่าจากการผลิต ไม่ใช่เงินที่สร้างจากหนี้แล้วใช้กฎหมายยังคับว่ามันมีค่า ถ้าเงื่อนไขสามข้อนี้ยังอยู่ครบ ทุนนิยมตลาดเสรีที่แท้จริง ก็จะเป็นระบบที่ยั่งยืน และแฟร์ที่สุดเท่าที่เคยมีมา ซึ่งตลอดประวัติศาสตร์เรายังไม่เคยแยกอำนาจการเงินออกจากมือมนุษย์ได้เลย เพราะถ้าเราปล่อยให้รัฐพิมพ์เงินได้อย่างอิสระ ลดคุณค่าของเงินได้โดยไม่ต้องรับผิดชอบ และแทรกแซงราคาตลาดโดยไม่มีการผลิตรองรับ เมื่อถึงจุดนั้น ต่อให้เราผลิตเก่งแค่ไหน เราก็ไม่มีทางรวยขึ้น เพราะรางวัลไม่ได้แจกตามผลงาน แต่แจกตามความใกล้ชิตผู้มีอำนาจ เมื่อเงินเสื่อมค่าลงทุกวัน ข้าวของแพงขึ้น เราต้องทำงานหนักขึ้น แต่ซื้อของได้น้อยลง แล้วเราจะเริ่มถามตัวเองว่า “เรากำลังทำงานสร้างคุณค่าจริงๆ ขยันจนแทบไม่มีเวลาหายใจ แต่สุดท้ายเรากำลังก้าวไปเดินหน้า หรือแค่พยายามเอาตัวรอดในระบบที่ไม่ยุติธรรม” และในวันนั้น...คุณอาจจะย้อนนึกถึงประโยคนี้ ที่อาจารย์เคยโพสแล้วอาจไม่ได้คิดว่ามันสำคัญ ปล.วันนี้เราอาจเห็นต่างกันเรื่องบทบาทของรัฐ แต่ซุปคิดว่าจุดร่วมของคำถามนี้คือ ระบบเศรษฐกิจที่ดี ควรให้รางวัลกับผู้ผลิต หรือให้รางวัลกับคนที่อยู่ใกล้ชิดผู้มีอำนาจ... #Siamstr
@ d5c3d063:4d1159b3
2025-04-02 04:04:32"ผลิตผลทางเศรษฐกิจที่เพิ่มขึ้น เป็นประโยชน์กับทุกคนเสมอ ไม่ว่าในทางใดก็ทางหนึ่ง" เป็นโพสของอาจารย์พิริยะ ที่เรียกได้ว่าคือ “หลักการพื้นฐาน” ของเสรีภาพทางเศรษฐกิจ ที่หลายคนอาจหลงลืม และซุปอยากขยายความต่อ เพราะนี่คือจุดเริ่มต้นของคำว่า “ระบบที่แฟร์จริง” . เราถูกสอนให้คิดว่า ถ้ามีคนรวยขึ้น ต้องมีใครอีกคนจนลง แต่ในความเป็นจริง ระบบตลาดเสรีไม่ได้ทำงานแบบนั้นเลย เพราะเมื่อมีคนผลิตของที่ดีขึ้น ผลิตได้เร็วขึ้น ต้นทุนจะลดลง สินค้าที่เคยเข้าถึงยาก ก็เริ่มกลายเป็นของธรรมดาที่ใครก็ใช้ได้ . คนหนึ่งคนที่ผลิตเพิ่มขึ้น อาจได้กำไรมากขึ้น แต่คนอีกเป็นล้านกลับได้ใช้สินค้าที่ถูกลง ชีวิตง่ายขึ้น สะดวกขึ้น เห็นได้ชัดว่าทุกฝ่ายได้ประโยชน์ ไม่ใช่เพราะมีใครต้อง "เสียสละจากการบังคับ" แต่เพราะทุกคนแลกเปลี่ยนกัน "ด้วยความสมัครใจ" นี่คือหลักการที่เศรษฐศาสตร์สำนักออสเตรียนเชื่อมั่นมาตลอด ว่าเสรีภาพในการผลิตและแลกเปลี่ยน คือรากฐานของความมั่งคั่งร่วมกัน "การแบ่งงานกันทำ" ของคนที่ถนัดต่างกัน คือวิธีที่มนุษย์สร้างสังคมเจริญขึ้นมาได้จริง ไม่ใช่เพราะรัฐสั่งให้ทำ แต่เพราะทุกคนเห็นประโยชน์ร่วมกันและยินดีแลกเปลี่ยนกันเอง . ปัญหาคือ วันนี้เราไม่ได้อยู่ในตลาดเสรีจริง แต่เราอยู่ในระบบที่รัฐเข้ามาเขียนกติกา ออกใบอนุญาต ควบคุมอุตสาหกรรม กำหนดราคา และที่แย่คือการออกกฎที่เอื้อให้พวกพ้อง ทำให้บางคนได้เปรียบในตลาด โดยไม่ได้มาจากการผลิตเก่งหรือบริการดีแต่มาจากการมีสายสัมพันธ์กับอำนาจ (แบบนี้คือ ทุนนิยมพวกพ้อง) . แล้วคนทั่วไปที่เห็นภาพแบบนี้ ก็พากันเรียกร้องให้รัฐเข้ามาจัดการ ทั้งที่จริงแล้ว...คนที่ควรรับผิดชอบ คือรัฐเอง ที่เปิดช่องให้เรื่องพวกนี้เกิดขึ้นตั้งแต่แรก . เราจึงติดกับดักเดิมซ้ำๆ คือรัฐสร้างปัญหา แล้วใช้ปัญหานั้นเป็นข้ออ้างในการขยายอำนาจ สุดท้ายมันก็ยิ่งบิดเบือนระบบเศรษฐกิจให้ผิดเพี้ยนเข้าไปอีก จนคนทำงานจริง ผลิตของจริง กลับไม่มีที่ยืนในระบบ . . ให้เห็นภาพต่อว่า ถ้ามีคนผลิตมากขึ้น ทุกคนในระบบจะได้ประโยชน์เพิ่มขึ้นเสมอ ตราบใดที่ 1 เขาไม่ได้ขโมยใคร 2 เขาแลกเปลี่ยนบนความสมัครใจ เท่านั้นยังไม่พอ 3 "เงิน" มันต้องเป็นกระจกสะท้อนคุณค่าจากการผลิต ไม่ใช่เงินที่สร้างจากหนี้แล้วใช้กฎหมายยังคับว่ามันมีค่า ถ้าเงื่อนไขสามข้อนี้ยังอยู่ครบ ทุนนิยมตลาดเสรีที่แท้จริง ก็จะเป็นระบบที่ยั่งยืน และแฟร์ที่สุดเท่าที่เคยมีมา ซึ่งตลอดประวัติศาสตร์เรายังไม่เคยแยกอำนาจการเงินออกจากมือมนุษย์ได้เลย เพราะถ้าเราปล่อยให้รัฐพิมพ์เงินได้อย่างอิสระ ลดคุณค่าของเงินได้โดยไม่ต้องรับผิดชอบ และแทรกแซงราคาตลาดโดยไม่มีการผลิตรองรับ เมื่อถึงจุดนั้น ต่อให้เราผลิตเก่งแค่ไหน เราก็ไม่มีทางรวยขึ้น เพราะรางวัลไม่ได้แจกตามผลงาน แต่แจกตามความใกล้ชิตผู้มีอำนาจ เมื่อเงินเสื่อมค่าลงทุกวัน ข้าวของแพงขึ้น เราต้องทำงานหนักขึ้น แต่ซื้อของได้น้อยลง แล้วเราจะเริ่มถามตัวเองว่า “เรากำลังทำงานสร้างคุณค่าจริงๆ ขยันจนแทบไม่มีเวลาหายใจ แต่สุดท้ายเรากำลังก้าวไปเดินหน้า หรือแค่พยายามเอาตัวรอดในระบบที่ไม่ยุติธรรม” และในวันนั้น...คุณอาจจะย้อนนึกถึงประโยคนี้ ที่อาจารย์เคยโพสแล้วอาจไม่ได้คิดว่ามันสำคัญ ปล.วันนี้เราอาจเห็นต่างกันเรื่องบทบาทของรัฐ แต่ซุปคิดว่าจุดร่วมของคำถามนี้คือ ระบบเศรษฐกิจที่ดี ควรให้รางวัลกับผู้ผลิต หรือให้รางวัลกับคนที่อยู่ใกล้ชิดผู้มีอำนาจ... #Siamstr @ 9967f375:04f9a5e1
2025-04-01 20:43:54El día 1, emprendió su tornaviaje con gran felicidad de este Puerto, para las Islas Filipinas, el Galeón *Sacra Familia*, que (por muerte del General Don Juan Antonio Cortés de Arredondo, Castillo, y Noblezia, a cuyo cargo vino) va a el de Don Jerónimo Montero.
@ 9967f375:04f9a5e1
2025-04-01 20:43:54El día 1, emprendió su tornaviaje con gran felicidad de este Puerto, para las Islas Filipinas, el Galeón *Sacra Familia*, que (por muerte del General Don Juan Antonio Cortés de Arredondo, Castillo, y Noblezia, a cuyo cargo vino) va a el de Don Jerónimo Montero. @ a95c6243:d345522c
2025-02-19 09:23:17*Die «moralische Weltordnung» – eine Art Astrologie. Friedrich Nietzsche* **Das Treffen der BRICS-Staaten beim [Gipfel](https://transition-news.org/brics-gipfel-in-kasan-warum-schweigt-die-schweiz) im russischen Kasan** war sicher nicht irgendein politisches Event. Gastgeber Wladimir Putin habe «Hof gehalten», sagen die Einen, China und Russland hätten ihre Vorstellung einer multipolaren Weltordnung zelebriert, schreiben Andere. **In jedem Fall zeigt die Anwesenheit von über 30 Delegationen aus der ganzen Welt,** dass von einer geostrategischen Isolation Russlands wohl keine Rede sein kann. Darüber hinaus haben sowohl die Anreise von UN-Generalsekretär António Guterres als auch die Meldungen und Dementis bezüglich der Beitrittsbemühungen des NATO-Staats [Türkei](https://transition-news.org/turkei-entlarvt-fake-news-von-bild-uber-indiens-angebliches-veto-gegen-den) für etwas Aufsehen gesorgt. **Im Spannungsfeld geopolitischer und wirtschaftlicher Umbrüche** zeigt die neue Allianz zunehmendes Selbstbewusstsein. In Sachen gemeinsamer Finanzpolitik schmiedet man interessante Pläne. Größere Unabhängigkeit von der US-dominierten Finanzordnung ist dabei ein wichtiges Ziel. **Beim BRICS-Wirtschaftsforum in Moskau, wenige Tage vor dem Gipfel,** zählte ein nachhaltiges System für Finanzabrechnungen und Zahlungsdienste zu den vorrangigen Themen. Während dieses Treffens ging der russische Staatsfonds eine Partnerschaft mit dem Rechenzentrumsbetreiber BitRiver ein, um [Bitcoin](https://www.forbes.com/sites/digital-assets/2024/10/23/russia-launches-brics-mining-infrastructure-project/)-Mining-Anlagen für die BRICS-Länder zu errichten. **Die Initiative könnte ein Schritt sein, Bitcoin und andere Kryptowährungen** als Alternativen zu traditionellen Finanzsystemen zu etablieren. Das Projekt könnte dazu führen, dass die BRICS-Staaten den globalen Handel in Bitcoin abwickeln. Vor dem Hintergrund der Diskussionen über eine «BRICS-Währung» wäre dies eine Alternative zu dem ursprünglich angedachten Korb lokaler Währungen und zu goldgedeckten Währungen sowie eine mögliche Ergänzung zum Zahlungssystem [BRICS Pay](https://en.wikipedia.org/wiki/BRICS_PAY). **Dient der Bitcoin also der Entdollarisierung?** Oder droht er inzwischen, zum Gegenstand geopolitischer [Machtspielchen](https://legitim.ch/es-ist-ein-sieg-fuer-bitcoin-waehrend-russland-und-die-usa-um-die-krypto-vorherrschaft-kaempfen/) zu werden? Angesichts der globalen Vernetzungen ist es oft schwer zu durchschauen, «was eine Show ist und was im Hintergrund von anderen Strippenziehern insgeheim gesteuert wird». Sicher können Strukturen wie Bitcoin auch so genutzt werden, dass sie den Herrschenden dienlich sind. Aber die Grundeigenschaft des dezentralisierten, unzensierbaren Peer-to-Peer Zahlungsnetzwerks ist ihm schließlich nicht zu nehmen. **Wenn es nach der EZB oder dem IWF geht, dann scheint statt Instrumentalisierung** momentan eher der Kampf gegen Kryptowährungen angesagt. Jürgen Schaaf, Senior Manager bei der Europäischen Zentralbank, hat jedenfalls dazu aufgerufen, [Bitcoin «zu eliminieren»](https://www.btc-echo.de/schlagzeilen/ezb-banker-es-gibt-gute-gruende-bitcoin-zu-eliminieren-194015/). Der Internationale Währungsfonds forderte El Salvador, das Bitcoin 2021 als gesetzliches Zahlungsmittel eingeführt hat, kürzlich zu [begrenzenden Maßnahmen](https://legitim.ch/el-salvador-iwf-fordert-trotz-nicht-eingetretener-risiken-neue-massnahmen-gegen-bitcoin/) gegen das Kryptogeld auf. **Dass die BRICS-Staaten ein freiheitliches Ansinnen im Kopf haben,** wenn sie Kryptowährungen ins Spiel bringen, darf indes auch bezweifelt werden. Im [Abschlussdokument](http://static.kremlin.ru/media/events/files/en/RosOySvLzGaJtmx2wYFv0lN4NSPZploG.pdf) bekennen sich die Gipfel-Teilnehmer ausdrücklich zur UN, ihren Programmen und ihrer «Agenda 2030». Ernst Wolff nennt das «eine [Bankrotterklärung](https://x.com/wolff_ernst/status/1849781982961557771) korrupter Politiker, die sich dem digital-finanziellen Komplex zu 100 Prozent unterwerfen». --- Dieser Beitrag ist zuerst auf *[Transition News](https://transition-news.org/aufstand-gegen-die-dollar-hegemonie)* erschienen.
@ a95c6243:d345522c
2025-02-19 09:23:17*Die «moralische Weltordnung» – eine Art Astrologie. Friedrich Nietzsche* **Das Treffen der BRICS-Staaten beim [Gipfel](https://transition-news.org/brics-gipfel-in-kasan-warum-schweigt-die-schweiz) im russischen Kasan** war sicher nicht irgendein politisches Event. Gastgeber Wladimir Putin habe «Hof gehalten», sagen die Einen, China und Russland hätten ihre Vorstellung einer multipolaren Weltordnung zelebriert, schreiben Andere. **In jedem Fall zeigt die Anwesenheit von über 30 Delegationen aus der ganzen Welt,** dass von einer geostrategischen Isolation Russlands wohl keine Rede sein kann. Darüber hinaus haben sowohl die Anreise von UN-Generalsekretär António Guterres als auch die Meldungen und Dementis bezüglich der Beitrittsbemühungen des NATO-Staats [Türkei](https://transition-news.org/turkei-entlarvt-fake-news-von-bild-uber-indiens-angebliches-veto-gegen-den) für etwas Aufsehen gesorgt. **Im Spannungsfeld geopolitischer und wirtschaftlicher Umbrüche** zeigt die neue Allianz zunehmendes Selbstbewusstsein. In Sachen gemeinsamer Finanzpolitik schmiedet man interessante Pläne. Größere Unabhängigkeit von der US-dominierten Finanzordnung ist dabei ein wichtiges Ziel. **Beim BRICS-Wirtschaftsforum in Moskau, wenige Tage vor dem Gipfel,** zählte ein nachhaltiges System für Finanzabrechnungen und Zahlungsdienste zu den vorrangigen Themen. Während dieses Treffens ging der russische Staatsfonds eine Partnerschaft mit dem Rechenzentrumsbetreiber BitRiver ein, um [Bitcoin](https://www.forbes.com/sites/digital-assets/2024/10/23/russia-launches-brics-mining-infrastructure-project/)-Mining-Anlagen für die BRICS-Länder zu errichten. **Die Initiative könnte ein Schritt sein, Bitcoin und andere Kryptowährungen** als Alternativen zu traditionellen Finanzsystemen zu etablieren. Das Projekt könnte dazu führen, dass die BRICS-Staaten den globalen Handel in Bitcoin abwickeln. Vor dem Hintergrund der Diskussionen über eine «BRICS-Währung» wäre dies eine Alternative zu dem ursprünglich angedachten Korb lokaler Währungen und zu goldgedeckten Währungen sowie eine mögliche Ergänzung zum Zahlungssystem [BRICS Pay](https://en.wikipedia.org/wiki/BRICS_PAY). **Dient der Bitcoin also der Entdollarisierung?** Oder droht er inzwischen, zum Gegenstand geopolitischer [Machtspielchen](https://legitim.ch/es-ist-ein-sieg-fuer-bitcoin-waehrend-russland-und-die-usa-um-die-krypto-vorherrschaft-kaempfen/) zu werden? Angesichts der globalen Vernetzungen ist es oft schwer zu durchschauen, «was eine Show ist und was im Hintergrund von anderen Strippenziehern insgeheim gesteuert wird». Sicher können Strukturen wie Bitcoin auch so genutzt werden, dass sie den Herrschenden dienlich sind. Aber die Grundeigenschaft des dezentralisierten, unzensierbaren Peer-to-Peer Zahlungsnetzwerks ist ihm schließlich nicht zu nehmen. **Wenn es nach der EZB oder dem IWF geht, dann scheint statt Instrumentalisierung** momentan eher der Kampf gegen Kryptowährungen angesagt. Jürgen Schaaf, Senior Manager bei der Europäischen Zentralbank, hat jedenfalls dazu aufgerufen, [Bitcoin «zu eliminieren»](https://www.btc-echo.de/schlagzeilen/ezb-banker-es-gibt-gute-gruende-bitcoin-zu-eliminieren-194015/). Der Internationale Währungsfonds forderte El Salvador, das Bitcoin 2021 als gesetzliches Zahlungsmittel eingeführt hat, kürzlich zu [begrenzenden Maßnahmen](https://legitim.ch/el-salvador-iwf-fordert-trotz-nicht-eingetretener-risiken-neue-massnahmen-gegen-bitcoin/) gegen das Kryptogeld auf. **Dass die BRICS-Staaten ein freiheitliches Ansinnen im Kopf haben,** wenn sie Kryptowährungen ins Spiel bringen, darf indes auch bezweifelt werden. Im [Abschlussdokument](http://static.kremlin.ru/media/events/files/en/RosOySvLzGaJtmx2wYFv0lN4NSPZploG.pdf) bekennen sich die Gipfel-Teilnehmer ausdrücklich zur UN, ihren Programmen und ihrer «Agenda 2030». Ernst Wolff nennt das «eine [Bankrotterklärung](https://x.com/wolff_ernst/status/1849781982961557771) korrupter Politiker, die sich dem digital-finanziellen Komplex zu 100 Prozent unterwerfen». --- Dieser Beitrag ist zuerst auf *[Transition News](https://transition-news.org/aufstand-gegen-die-dollar-hegemonie)* erschienen. @ b2caa9b3:9eab0fb5
2025-04-01 20:29:01 For years, I’ve been shifting my life away from traditional systems and toward Bitcoin. I calculate my expenses in sats, buy airtime and online data with BTC, and continue exploring new ways to integrate Bitcoin into my daily life. While I’m not yet fully living on Bitcoin, I am getting closer with each step.  Since discovering Nostr, my perspective on decentralization has deepened. More than just a financial shift, it's a complete lifestyle transformation. Years ago, after facing injustice in my home country, I took the first step toward a new way of living. That decision led me to where I am today—a minimalist, a nomad, and a believer in financial freedom through Bitcoin.  I once served in the military, owned a house, and drove a nice car. My life looked very different back then. But over time, I realized that true freedom wasn’t in possessions—it was in mobility, independence, and the ability to control my own finances. Now, all I own fits into a backpack weighing less than 12 kg. My lifestyle is simple, yet rich in experiences. March 14 marks eight years since I embraced my nomadic lifestyle. What started as a leap into the unknown has become my way of life. Living with less has given me more—the freedom to move, to explore, and to be truly independent. The more I immerse myself in the Bitcoin ecosystem, the more I see its potential to reshape not only my life but the world around me.  The journey isn’t over. In fact, it’s just beginning. Let’s see where this path leads as I go further into the blockchain revolution!   
@ b2caa9b3:9eab0fb5
2025-04-01 20:29:01 For years, I’ve been shifting my life away from traditional systems and toward Bitcoin. I calculate my expenses in sats, buy airtime and online data with BTC, and continue exploring new ways to integrate Bitcoin into my daily life. While I’m not yet fully living on Bitcoin, I am getting closer with each step.  Since discovering Nostr, my perspective on decentralization has deepened. More than just a financial shift, it's a complete lifestyle transformation. Years ago, after facing injustice in my home country, I took the first step toward a new way of living. That decision led me to where I am today—a minimalist, a nomad, and a believer in financial freedom through Bitcoin.  I once served in the military, owned a house, and drove a nice car. My life looked very different back then. But over time, I realized that true freedom wasn’t in possessions—it was in mobility, independence, and the ability to control my own finances. Now, all I own fits into a backpack weighing less than 12 kg. My lifestyle is simple, yet rich in experiences. March 14 marks eight years since I embraced my nomadic lifestyle. What started as a leap into the unknown has become my way of life. Living with less has given me more—the freedom to move, to explore, and to be truly independent. The more I immerse myself in the Bitcoin ecosystem, the more I see its potential to reshape not only my life but the world around me.  The journey isn’t over. In fact, it’s just beginning. Let’s see where this path leads as I go further into the blockchain revolution!   