-
 @ df478568:2a951e67
2025-04-22 18:56:38
@ df478568:2a951e67
2025-04-22 18:56:38"It might make sense just to get some in case it catches on. If enough people think the same way, that becomes a self fulfilling prophecy. Once it gets bootstrapped, there are so many applications if you could effortlessly pay a few cents to a website as easily as dropping coins in a vending machine." --Satoshi Nakamoto The Cryptography Mailing List--January 17, 2009
Forgot to add the good part about micropayments. While I don't think Bitcoin is practical for smaller micropayments right now, it will eventually be as storage and bandwidth costs continue to fall. If Bitcoin catches on on a big scale, it may already be the case by that time. Another way they can become more practical is if I implement client-only mode and the number of network nodes consolidates into a smaller number of professional server farms. Whatever size micropayments you need will eventually be practical. I think in 5 or 10 years, the bandwidth and storage will seem trivial. --Satoshi Nakamoto Bitcoin Talk-- August 5, 2010
I very be coded some HTML buttons using Claude and uploaded it to https://github.com/GhostZaps/ It's just a button that links to zapper.fun.
I signed up for Substack to build an email address, but learned adding different payment options to Substack is against their terms and services. Since I write about nostr, these terms seem as silly as someone saying Craig Wright is Satoshi. It's easy to build an audience on Substack however, or so I thought. Why is it easier to build an audience on Subtack though? Because Substack is a platform that markets to writers. Anyone with a ~~pen~~ ~~keyboard~~ smartphone and an email can create an account with Substack. There's just one problem: You are an Internet serf, working the land for your Internet landlord--The Duke of Substack.
Then I saw that Shawn posted about Substack's UX.
I should have grabbed my reading glasses before pushing the post button, but it occurred to me that I could use Ghost to do this and there is probably a way to hack it to accept bitcoin payments over the lightning network and host it yourself. So I spun my noddle, doodled some plans...And then it hit me. Ghost allows for markdown and HTML. I learned HTML and CSS with free-code camp, but ain't nobody got time to type CSS so I vibe-coded a button that ~~baits~~ sends the clicker to my zapper.fun page. This can be used on any blog that allows you to paste html into it so I added it to my Ghost blog self-hosted on a Start 9. The blog is on TOR at http://p66dxywd2xpyyrdfxwilqcxmchmfw2ixmn2vm74q3atf22du7qmkihyd.onion/, but most people around me have been conditioned to fear the dark web so I used the cloudflared to host my newsletter on the clear net at https://marc26z.com/
Integrating Nostr Into My Self-Hosted Ghost Newsletter
I would venture to say I am more technical than the average person and I know HTML, but my CSS is fuzzy. I also know how to print("Hello world!") in python, but I an NPC beyond the basics. Nevertheless, I found that I know enough to make a button. I can't code well enough to create my own nostr long-form client and create plugins for ghost that send lightning payments to lighting channel, but I know enough about nostr to know that I don't need to. That's why nostr is so F@#%-ing cool! It's all connected. ** - One button takes you to zapper.fun where you can zap anywhere between 1 and ,000,000 sats.** - Another button sends you to a zap planner pre-set to send 5,000 sats to the author per month using nostr. - Yet another button sends you to a zap planner preset to send 2,500 sats per month.
The possibilities are endless. I entered a link that takes the clicker to my Shopstr Merch Store. The point is to write as self-sovereign as possible. I might need to change my lightning address when stuff breaks every now and then, but I like the idea of busking for sats by writing on the Internet using the Value 4 Value model. I dislike ads, but I also want people to buy stuff from people I do business with because I want to promote using bitcoin as peer-to-peer electronic cash, not NGU porn. I'm not prude. I enjoy looking at the price displayed on my BlockClock micro every now and then, but I am not an NGU porn addict.
This line made this pattern, that line made this pattern. All that Bolinger Bart Simpson bullshit has nothing to with bitcoin, a peer-to-peer electronic cash system. It is the musings of a population trapped in the fiat mind-set. Bitcoin is permissionless so I realized I was bieng a hipocryte by using a permissioned payment system becaue it was easier than writing a little vibe code. I don't need permission to write for sats. I don't need to give my bank account number to Substack. I don't need to pay a 10$ vig to publish on a a platform which is not designed for stacking sats. I can write on Ghost and integrate clients that already exist in the multi-nostr-verse.
Nostr Payment Buttons
The buttons can be fouund at https://github.com/Marc26z/GhostZapButton
You can use them yourself. Just replace my npub with your npub or add any other link you want. It doesn't technically need to be a nostr link. It can be anything. I have a link to another Ghost article with other buttons that lead down different sat pledging amounts. It's early. Everyone who spends bitcoin is on nostr and nostr is small, but growing community. I want to be part of this community. I want to find other writers on nostr and stay away from Substack.
Here's what it looks like on Ghost: https://marc26z.com/zaps-on-ghost/
npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0
-
 @ 4ba8e86d:89d32de4
2025-04-21 02:13:56
@ 4ba8e86d:89d32de4
2025-04-21 02:13:56Tutorial feito por nostr:nostr:npub1rc56x0ek0dd303eph523g3chm0wmrs5wdk6vs0ehd0m5fn8t7y4sqra3tk poste original abaixo:
Parte 1 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/263585/tutorial-debloat-de-celulares-android-via-adb-parte-1
Parte 2 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/index.php/263586/tutorial-debloat-de-celulares-android-via-adb-parte-2
Quando o assunto é privacidade em celulares, uma das medidas comumente mencionadas é a remoção de bloatwares do dispositivo, também chamado de debloat. O meio mais eficiente para isso sem dúvidas é a troca de sistema operacional. Custom Rom’s como LineageOS, GrapheneOS, Iodé, CalyxOS, etc, já são bastante enxutos nesse quesito, principalmente quanto não é instalado os G-Apps com o sistema. No entanto, essa prática pode acabar resultando em problemas indesejados como a perca de funções do dispositivo, e até mesmo incompatibilidade com apps bancários, tornando este método mais atrativo para quem possui mais de um dispositivo e separando um apenas para privacidade. Pensando nisso, pessoas que possuem apenas um único dispositivo móvel, que são necessitadas desses apps ou funções, mas, ao mesmo tempo, tem essa visão em prol da privacidade, buscam por um meio-termo entre manter a Stock rom, e não ter seus dados coletados por esses bloatwares. Felizmente, a remoção de bloatwares é possível e pode ser realizada via root, ou mais da maneira que este artigo irá tratar, via adb.
O que são bloatwares?
Bloatware é a junção das palavras bloat (inchar) + software (programa), ou seja, um bloatware é basicamente um programa inútil ou facilmente substituível — colocado em seu dispositivo previamente pela fabricante e operadora — que está no seu dispositivo apenas ocupando espaço de armazenamento, consumindo memória RAM e pior, coletando seus dados e enviando para servidores externos, além de serem mais pontos de vulnerabilidades.
O que é o adb?
O Android Debug Brigde, ou apenas adb, é uma ferramenta que se utiliza das permissões de usuário shell e permite o envio de comandos vindo de um computador para um dispositivo Android exigindo apenas que a depuração USB esteja ativa, mas também pode ser usada diretamente no celular a partir do Android 11, com o uso do Termux e a depuração sem fio (ou depuração wifi). A ferramenta funciona normalmente em dispositivos sem root, e também funciona caso o celular esteja em Recovery Mode.
Requisitos:
Para computadores:
• Depuração USB ativa no celular; • Computador com adb; • Cabo USB;
Para celulares:
• Depuração sem fio (ou depuração wifi) ativa no celular; • Termux; • Android 11 ou superior;
Para ambos:
• Firewall NetGuard instalado e configurado no celular; • Lista de bloatwares para seu dispositivo;
Ativação de depuração:
Para ativar a Depuração USB em seu dispositivo, pesquise como ativar as opções de desenvolvedor de seu dispositivo, e lá ative a depuração. No caso da depuração sem fio, sua ativação irá ser necessária apenas no momento que for conectar o dispositivo ao Termux.
Instalação e configuração do NetGuard
O NetGuard pode ser instalado através da própria Google Play Store, mas de preferência instale pela F-Droid ou Github para evitar telemetria.
F-Droid: https://f-droid.org/packages/eu.faircode.netguard/
Github: https://github.com/M66B/NetGuard/releases
Após instalado, configure da seguinte maneira:
Configurações → padrões (lista branca/negra) → ative as 3 primeiras opções (bloquear wifi, bloquear dados móveis e aplicar regras ‘quando tela estiver ligada’);
Configurações → opções avançadas → ative as duas primeiras (administrar aplicativos do sistema e registrar acesso a internet);
Com isso, todos os apps estarão sendo bloqueados de acessar a internet, seja por wifi ou dados móveis, e na página principal do app basta permitir o acesso a rede para os apps que você vai usar (se necessário). Permita que o app rode em segundo plano sem restrição da otimização de bateria, assim quando o celular ligar, ele já estará ativo.
Lista de bloatwares
Nem todos os bloatwares são genéricos, haverá bloatwares diferentes conforme a marca, modelo, versão do Android, e até mesmo região.
Para obter uma lista de bloatwares de seu dispositivo, caso seu aparelho já possua um tempo de existência, você encontrará listas prontas facilmente apenas pesquisando por elas. Supondo que temos um Samsung Galaxy Note 10 Plus em mãos, basta pesquisar em seu motor de busca por:
Samsung Galaxy Note 10 Plus bloatware listProvavelmente essas listas já terão inclusas todos os bloatwares das mais diversas regiões, lhe poupando o trabalho de buscar por alguma lista mais específica.
Caso seu aparelho seja muito recente, e/ou não encontre uma lista pronta de bloatwares, devo dizer que você acaba de pegar em merda, pois é chato para um caralho pesquisar por cada aplicação para saber sua função, se é essencial para o sistema ou se é facilmente substituível.
De antemão já aviso, que mais para frente, caso vossa gostosura remova um desses aplicativos que era essencial para o sistema sem saber, vai acabar resultando na perda de alguma função importante, ou pior, ao reiniciar o aparelho o sistema pode estar quebrado, lhe obrigando a seguir com uma formatação, e repetir todo o processo novamente.
Download do adb em computadores
Para usar a ferramenta do adb em computadores, basta baixar o pacote chamado SDK platform-tools, disponível através deste link: https://developer.android.com/tools/releases/platform-tools. Por ele, você consegue o download para Windows, Mac e Linux.
Uma vez baixado, basta extrair o arquivo zipado, contendo dentro dele uma pasta chamada platform-tools que basta ser aberta no terminal para se usar o adb.
Download do adb em celulares com Termux.
Para usar a ferramenta do adb diretamente no celular, antes temos que baixar o app Termux, que é um emulador de terminal linux, e já possui o adb em seu repositório. Você encontra o app na Google Play Store, mas novamente recomendo baixar pela F-Droid ou diretamente no Github do projeto.
F-Droid: https://f-droid.org/en/packages/com.termux/
Github: https://github.com/termux/termux-app/releases
Processo de debloat
Antes de iniciarmos, é importante deixar claro que não é para você sair removendo todos os bloatwares de cara sem mais nem menos, afinal alguns deles precisam antes ser substituídos, podem ser essenciais para você para alguma atividade ou função, ou até mesmo são insubstituíveis.
Alguns exemplos de bloatwares que a substituição é necessária antes da remoção, é o Launcher, afinal, é a interface gráfica do sistema, e o teclado, que sem ele só é possível digitar com teclado externo. O Launcher e teclado podem ser substituídos por quaisquer outros, minha recomendação pessoal é por aqueles que respeitam sua privacidade, como Pie Launcher e Simple Laucher, enquanto o teclado pelo OpenBoard e FlorisBoard, todos open-source e disponíveis da F-Droid.
Identifique entre a lista de bloatwares, quais você gosta, precisa ou prefere não substituir, de maneira alguma você é obrigado a remover todos os bloatwares possíveis, modifique seu sistema a seu bel-prazer. O NetGuard lista todos os apps do celular com o nome do pacote, com isso você pode filtrar bem qual deles não remover.
Um exemplo claro de bloatware insubstituível e, portanto, não pode ser removido, é o com.android.mtp, um protocolo onde sua função é auxiliar a comunicação do dispositivo com um computador via USB, mas por algum motivo, tem acesso a rede e se comunica frequentemente com servidores externos. Para esses casos, e melhor solução mesmo é bloquear o acesso a rede desses bloatwares com o NetGuard.
MTP tentando comunicação com servidores externos:
Executando o adb shell
No computador
Faça backup de todos os seus arquivos importantes para algum armazenamento externo, e formate seu celular com o hard reset. Após a formatação, e a ativação da depuração USB, conecte seu aparelho e o pc com o auxílio de um cabo USB. Muito provavelmente seu dispositivo irá apenas começar a carregar, por isso permita a transferência de dados, para que o computador consiga se comunicar normalmente com o celular.
Já no pc, abra a pasta platform-tools dentro do terminal, e execute o seguinte comando:
./adb start-serverO resultado deve ser:
daemon not running; starting now at tcp:5037 daemon started successfully
E caso não apareça nada, execute:
./adb kill-serverE inicie novamente.
Com o adb conectado ao celular, execute:
./adb shellPara poder executar comandos diretamente para o dispositivo. No meu caso, meu celular é um Redmi Note 8 Pro, codinome Begonia.
Logo o resultado deve ser:
begonia:/ $
Caso ocorra algum erro do tipo:
adb: device unauthorized. This adb server’s $ADB_VENDOR_KEYS is not set Try ‘adb kill-server’ if that seems wrong. Otherwise check for a confirmation dialog on your device.
Verifique no celular se apareceu alguma confirmação para autorizar a depuração USB, caso sim, autorize e tente novamente. Caso não apareça nada, execute o kill-server e repita o processo.
No celular
Após realizar o mesmo processo de backup e hard reset citado anteriormente, instale o Termux e, com ele iniciado, execute o comando:
pkg install android-toolsQuando surgir a mensagem “Do you want to continue? [Y/n]”, basta dar enter novamente que já aceita e finaliza a instalação
Agora, vá até as opções de desenvolvedor, e ative a depuração sem fio. Dentro das opções da depuração sem fio, terá uma opção de emparelhamento do dispositivo com um código, que irá informar para você um código em emparelhamento, com um endereço IP e porta, que será usado para a conexão com o Termux.
Para facilitar o processo, recomendo que abra tanto as configurações quanto o Termux ao mesmo tempo, e divida a tela com os dois app’s, como da maneira a seguir:
Para parear o Termux com o dispositivo, não é necessário digitar o ip informado, basta trocar por “localhost”, já a porta e o código de emparelhamento, deve ser digitado exatamente como informado. Execute:
adb pair localhost:porta CódigoDeEmparelhamentoDe acordo com a imagem mostrada anteriormente, o comando ficaria “adb pair localhost:41255 757495”.
Com o dispositivo emparelhado com o Termux, agora basta conectar para conseguir executar os comandos, para isso execute:
adb connect localhost:portaObs: a porta que você deve informar neste comando não é a mesma informada com o código de emparelhamento, e sim a informada na tela principal da depuração sem fio.
Pronto! Termux e adb conectado com sucesso ao dispositivo, agora basta executar normalmente o adb shell:
adb shellRemoção na prática Com o adb shell executado, você está pronto para remover os bloatwares. No meu caso, irei mostrar apenas a remoção de um app (Google Maps), já que o comando é o mesmo para qualquer outro, mudando apenas o nome do pacote.
Dentro do NetGuard, verificando as informações do Google Maps:
Podemos ver que mesmo fora de uso, e com a localização do dispositivo desativado, o app está tentando loucamente se comunicar com servidores externos, e informar sabe-se lá que peste. Mas sem novidades até aqui, o mais importante é que podemos ver que o nome do pacote do Google Maps é com.google.android.apps.maps, e para o remover do celular, basta executar:
pm uninstall –user 0 com.google.android.apps.mapsE pronto, bloatware removido! Agora basta repetir o processo para o resto dos bloatwares, trocando apenas o nome do pacote.
Para acelerar o processo, você pode já criar uma lista do bloco de notas com os comandos, e quando colar no terminal, irá executar um atrás do outro.
Exemplo de lista:
Caso a donzela tenha removido alguma coisa sem querer, também é possível recuperar o pacote com o comando:
cmd package install-existing nome.do.pacotePós-debloat
Após limpar o máximo possível o seu sistema, reinicie o aparelho, caso entre no como recovery e não seja possível dar reboot, significa que você removeu algum app “essencial” para o sistema, e terá que formatar o aparelho e repetir toda a remoção novamente, desta vez removendo poucos bloatwares de uma vez, e reiniciando o aparelho até descobrir qual deles não pode ser removido. Sim, dá trabalho… quem mandou querer privacidade?
Caso o aparelho reinicie normalmente após a remoção, parabéns, agora basta usar seu celular como bem entender! Mantenha o NetGuard sempre executando e os bloatwares que não foram possíveis remover não irão se comunicar com servidores externos, passe a usar apps open source da F-Droid e instale outros apps através da Aurora Store ao invés da Google Play Store.
Referências: Caso você seja um Australopithecus e tenha achado este guia difícil, eis uma videoaula (3:14:40) do Anderson do canal Ciberdef, realizando todo o processo: http://odysee.com/@zai:5/Como-remover-at%C3%A9-200-APLICATIVOS-que-colocam-a-sua-PRIVACIDADE-E-SEGURAN%C3%87A-em-risco.:4?lid=6d50f40314eee7e2f218536d9e5d300290931d23
Pdf’s do Anderson citados na videoaula: créditos ao anon6837264 http://eternalcbrzpicytj4zyguygpmkjlkddxob7tptlr25cdipe5svyqoqd.onion/file/3863a834d29285d397b73a4af6fb1bbe67c888d72d30/t-05e63192d02ffd.pdf
Processo de instalação do Termux e adb no celular: https://youtu.be/APolZrPHSms
-
 @ 35f80bda:406855c0
2025-04-16 03:11:46
@ 35f80bda:406855c0
2025-04-16 03:11:46O Bitcoin Core 29.0 foi oficialmente lançado e traz diversas melhorias técnicas voltadas para desenvolvedores, operadores de full nodes e a comunidade Bitcoin mais técnica. Desde mudanças na camada de rede até a atualização do sistema de build, este release é um passo significativo na modernização do ecossistema.
Se você roda um full node, desenvolve software que interage com o Core via RPC ou apenas quer estar por dentro das novidades técnicas, este artigo é para você.
Alterações na Rede e no P2P
Suporte ao UPnP Removido O UPnP foi totalmente desativado por razões de segurança e manutenção. Agora, a recomendação é utilizar a flag -natpmp, que conta com uma implementação interna de PCP e NAT-PMP. Mais seguro e mais leve.
Melhorias no Suporte Tor A porta onion agora é derivada da flag -port, permitindo múltiplos nós Tor na mesma máquina — ótimo para quem opera ambientes de teste ou múltiplos peers.
Transações Órfãs com Propagação Aprimorada O node agora tenta buscar os parents de transações órfãs consultando todos os peers que anunciaram a transação. Isso ajuda a preencher lacunas na mempool de forma mais eficiente.
Mempool e Política de Mineração
Ephemeral Dust Introdução de um novo conceito: ephemeral dust, que permite uma saída "dust" gratuita em uma transação desde que ela seja gasta dentro do mesmo pacote. Pode ser útil para otimizações de fees.
Correção no Peso Reservado de Blocos Bug que causava duplicação de peso reservado foi corrigido. Agora existe a flag -blockreservedweight, com limite mínimo de 2000 WU.
RPCs e REST mais robustos
- testmempoolaccept agora fornece o campo reject-details.
- submitblock preserva blocos duplicados mesmo que tenham sido podados.
- getblock, getblockheader e getblockchaininfo agora incluem o campo nBits (alvo de dificuldade).
- Novo RPC: getdescriptoractivity, que permite ver atividades de descritores em intervalos de blocos.
- APIs REST agora retornam nBits também no campo target.
Sistema de Build Modernizado
Uma das mudanças mais bem-vindas: o Bitcoin Core agora usa CMake em vez de Autotools como padrão de build. Isso facilita integração com IDEs, CI/CD pipelines modernos e personalização do build.
Outras Atualizações Importantes
- -dbcache teve limite máximo reduzido para lidar com o crescimento do conjunto UTXO.
- O comportamento Full Replace-by-Fee (RBF) agora é padrão. A flag -mempoolfullrbf foi removida.
- Aumentaram os valores padrão de -rpcthreads e -rpcworkqueue para lidar com maior paralelismo.
Ferramentas Novas
Uma nova ferramenta chamada utxo_to_sqlite.py converte snapshots compactos do conjunto UTXO para SQLite3. Excelente para quem quer auditar ou explorar o estado da blockchain com ferramentas padrão de banco de dados.
Limpeza de Dependências
As bibliotecas externas MiniUPnPc e libnatpmp foram removidas, substituídas por implementações internas. Menos dependências = manutenção mais fácil e menos riscos.
Como atualizar?
- Pare o seu nó atual com segurança.
- Instale a nova versão.
- Verifique configurações como -dbcache, -blockreservedweight e o comportamento RBF.
- Consulte os logs com atenção nas primeiras execuções para validar o novo comportamento.
Conclusão
O Bitcoin Core 29.0 representa um passo firme em direção a uma base de código mais moderna, segura e modular. Para quem mantém nós, desenvolve soluções sobre o Core ou audita a rede, é uma atualização que vale a pena testar e entender a fundo.
Já testou a nova versão? Notou impactos nas suas aplicações ou infraestrutura?
Referências
-
 @ 91bea5cd:1df4451c
2025-04-15 06:27:28
@ 91bea5cd:1df4451c
2025-04-15 06:27:28Básico
bash lsblk # Lista todos os diretorios montados.Para criar o sistema de arquivos:
bash mkfs.btrfs -L "ThePool" -f /dev/sdxCriando um subvolume:
bash btrfs subvolume create SubVolMontando Sistema de Arquivos:
bash mount -o compress=zlib,subvol=SubVol,autodefrag /dev/sdx /mntLista os discos formatados no diretório:
bash btrfs filesystem show /mntAdiciona novo disco ao subvolume:
bash btrfs device add -f /dev/sdy /mntLista novamente os discos do subvolume:
bash btrfs filesystem show /mntExibe uso dos discos do subvolume:
bash btrfs filesystem df /mntBalancea os dados entre os discos sobre raid1:
bash btrfs filesystem balance start -dconvert=raid1 -mconvert=raid1 /mntScrub é uma passagem por todos os dados e metadados do sistema de arquivos e verifica as somas de verificação. Se uma cópia válida estiver disponível (perfis de grupo de blocos replicados), a danificada será reparada. Todas as cópias dos perfis replicados são validadas.
iniciar o processo de depuração :
bash btrfs scrub start /mntver o status do processo de depuração Btrfs em execução:
bash btrfs scrub status /mntver o status do scrub Btrfs para cada um dos dispositivos
bash btrfs scrub status -d / data btrfs scrub cancel / dataPara retomar o processo de depuração do Btrfs que você cancelou ou pausou:
btrfs scrub resume / data
Listando os subvolumes:
bash btrfs subvolume list /ReportsCriando um instantâneo dos subvolumes:
Aqui, estamos criando um instantâneo de leitura e gravação chamado snap de marketing do subvolume de marketing.
bash btrfs subvolume snapshot /Reports/marketing /Reports/marketing-snapAlém disso, você pode criar um instantâneo somente leitura usando o sinalizador -r conforme mostrado. O marketing-rosnap é um instantâneo somente leitura do subvolume de marketing
bash btrfs subvolume snapshot -r /Reports/marketing /Reports/marketing-rosnapForçar a sincronização do sistema de arquivos usando o utilitário 'sync'
Para forçar a sincronização do sistema de arquivos, invoque a opção de sincronização conforme mostrado. Observe que o sistema de arquivos já deve estar montado para que o processo de sincronização continue com sucesso.
bash btrfs filsystem sync /ReportsPara excluir o dispositivo do sistema de arquivos, use o comando device delete conforme mostrado.
bash btrfs device delete /dev/sdc /ReportsPara sondar o status de um scrub, use o comando scrub status com a opção -dR .
bash btrfs scrub status -dR / RelatóriosPara cancelar a execução do scrub, use o comando scrub cancel .
bash $ sudo btrfs scrub cancel / ReportsPara retomar ou continuar com uma depuração interrompida anteriormente, execute o comando de cancelamento de depuração
bash sudo btrfs scrub resume /Reportsmostra o uso do dispositivo de armazenamento:
btrfs filesystem usage /data
Para distribuir os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID (incluindo o dispositivo de armazenamento recém-adicionado) montados no diretório /data , execute o seguinte comando:
sudo btrfs balance start --full-balance /data
Pode demorar um pouco para espalhar os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID se ele contiver muitos dados.
Opções importantes de montagem Btrfs
Nesta seção, vou explicar algumas das importantes opções de montagem do Btrfs. Então vamos começar.
As opções de montagem Btrfs mais importantes são:
**1. acl e noacl
**ACL gerencia permissões de usuários e grupos para os arquivos/diretórios do sistema de arquivos Btrfs.
A opção de montagem acl Btrfs habilita ACL. Para desabilitar a ACL, você pode usar a opção de montagem noacl .
Por padrão, a ACL está habilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem acl por padrão.
**2. autodefrag e noautodefrag
**Desfragmentar um sistema de arquivos Btrfs melhorará o desempenho do sistema de arquivos reduzindo a fragmentação de dados.
A opção de montagem autodefrag permite a desfragmentação automática do sistema de arquivos Btrfs.
A opção de montagem noautodefrag desativa a desfragmentação automática do sistema de arquivos Btrfs.
Por padrão, a desfragmentação automática está desabilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem noautodefrag por padrão.
**3. compactar e compactar-forçar
**Controla a compactação de dados no nível do sistema de arquivos do sistema de arquivos Btrfs.
A opção compactar compacta apenas os arquivos que valem a pena compactar (se compactar o arquivo economizar espaço em disco).
A opção compress-force compacta todos os arquivos do sistema de arquivos Btrfs, mesmo que a compactação do arquivo aumente seu tamanho.
O sistema de arquivos Btrfs suporta muitos algoritmos de compactação e cada um dos algoritmos de compactação possui diferentes níveis de compactação.
Os algoritmos de compactação suportados pelo Btrfs são: lzo , zlib (nível 1 a 9) e zstd (nível 1 a 15).
Você pode especificar qual algoritmo de compactação usar para o sistema de arquivos Btrfs com uma das seguintes opções de montagem:
- compress=algoritmo:nível
- compress-force=algoritmo:nível
Para obter mais informações, consulte meu artigo Como habilitar a compactação do sistema de arquivos Btrfs .
**4. subvol e subvolid
**Estas opções de montagem são usadas para montar separadamente um subvolume específico de um sistema de arquivos Btrfs.
A opção de montagem subvol é usada para montar o subvolume de um sistema de arquivos Btrfs usando seu caminho relativo.
A opção de montagem subvolid é usada para montar o subvolume de um sistema de arquivos Btrfs usando o ID do subvolume.
Para obter mais informações, consulte meu artigo Como criar e montar subvolumes Btrfs .
**5. dispositivo
A opção de montagem de dispositivo** é usada no sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs.
Em alguns casos, o sistema operacional pode falhar ao detectar os dispositivos de armazenamento usados em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs. Nesses casos, você pode usar a opção de montagem do dispositivo para especificar os dispositivos que deseja usar para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar a opção de montagem de dispositivo várias vezes para carregar diferentes dispositivos de armazenamento para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar o nome do dispositivo (ou seja, sdb , sdc ) ou UUID , UUID_SUB ou PARTUUID do dispositivo de armazenamento com a opção de montagem do dispositivo para identificar o dispositivo de armazenamento.
Por exemplo,
- dispositivo=/dev/sdb
- dispositivo=/dev/sdb,dispositivo=/dev/sdc
- dispositivo=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d
- device=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d,device=UUID_SUB=f7ce4875-0874-436a-b47d-3edef66d3424
**6. degraded
A opção de montagem degradada** permite que um RAID Btrfs seja montado com menos dispositivos de armazenamento do que o perfil RAID requer.
Por exemplo, o perfil raid1 requer a presença de 2 dispositivos de armazenamento. Se um dos dispositivos de armazenamento não estiver disponível em qualquer caso, você usa a opção de montagem degradada para montar o RAID mesmo que 1 de 2 dispositivos de armazenamento esteja disponível.
**7. commit
A opção commit** mount é usada para definir o intervalo (em segundos) dentro do qual os dados serão gravados no dispositivo de armazenamento.
O padrão é definido como 30 segundos.
Para definir o intervalo de confirmação para 15 segundos, você pode usar a opção de montagem commit=15 (digamos).
**8. ssd e nossd
A opção de montagem ssd** informa ao sistema de arquivos Btrfs que o sistema de arquivos está usando um dispositivo de armazenamento SSD, e o sistema de arquivos Btrfs faz a otimização SSD necessária.
A opção de montagem nossd desativa a otimização do SSD.
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem de SSD será habilitada. Caso contrário, a opção de montagem nossd é habilitada.
**9. ssd_spread e nossd_spread
A opção de montagem ssd_spread** tenta alocar grandes blocos contínuos de espaço não utilizado do SSD. Esse recurso melhora o desempenho de SSDs de baixo custo (baratos).
A opção de montagem nossd_spread desativa o recurso ssd_spread .
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem ssd_spread será habilitada. Caso contrário, a opção de montagem nossd_spread é habilitada.
**10. descarte e nodiscard
Se você estiver usando um SSD que suporte TRIM enfileirado assíncrono (SATA rev3.1), a opção de montagem de descarte** permitirá o descarte de blocos de arquivos liberados. Isso melhorará o desempenho do SSD.
Se o SSD não suportar TRIM enfileirado assíncrono, a opção de montagem de descarte prejudicará o desempenho do SSD. Nesse caso, a opção de montagem nodiscard deve ser usada.
Por padrão, a opção de montagem nodiscard é usada.
**11. norecovery
Se a opção de montagem norecovery** for usada, o sistema de arquivos Btrfs não tentará executar a operação de recuperação de dados no momento da montagem.
**12. usebackuproot e nousebackuproot
Se a opção de montagem usebackuproot for usada, o sistema de arquivos Btrfs tentará recuperar qualquer raiz de árvore ruim/corrompida no momento da montagem. O sistema de arquivos Btrfs pode armazenar várias raízes de árvore no sistema de arquivos. A opção de montagem usebackuproot** procurará uma boa raiz de árvore e usará a primeira boa que encontrar.
A opção de montagem nousebackuproot não verificará ou recuperará raízes de árvore inválidas/corrompidas no momento da montagem. Este é o comportamento padrão do sistema de arquivos Btrfs.
**13. space_cache, space_cache=version, nospace_cache e clear_cache
A opção de montagem space_cache** é usada para controlar o cache de espaço livre. O cache de espaço livre é usado para melhorar o desempenho da leitura do espaço livre do grupo de blocos do sistema de arquivos Btrfs na memória (RAM).
O sistema de arquivos Btrfs suporta 2 versões do cache de espaço livre: v1 (padrão) e v2
O mecanismo de cache de espaço livre v2 melhora o desempenho de sistemas de arquivos grandes (tamanho de vários terabytes).
Você pode usar a opção de montagem space_cache=v1 para definir a v1 do cache de espaço livre e a opção de montagem space_cache=v2 para definir a v2 do cache de espaço livre.
A opção de montagem clear_cache é usada para limpar o cache de espaço livre.
Quando o cache de espaço livre v2 é criado, o cache deve ser limpo para criar um cache de espaço livre v1 .
Portanto, para usar o cache de espaço livre v1 após a criação do cache de espaço livre v2 , as opções de montagem clear_cache e space_cache=v1 devem ser combinadas: clear_cache,space_cache=v1
A opção de montagem nospace_cache é usada para desabilitar o cache de espaço livre.
Para desabilitar o cache de espaço livre após a criação do cache v1 ou v2 , as opções de montagem nospace_cache e clear_cache devem ser combinadas: clear_cache,nosapce_cache
**14. skip_balance
Por padrão, a operação de balanceamento interrompida/pausada de um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs será retomada automaticamente assim que o sistema de arquivos Btrfs for montado. Para desabilitar a retomada automática da operação de equilíbrio interrompido/pausado em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs, você pode usar a opção de montagem skip_balance .**
**15. datacow e nodatacow
A opção datacow** mount habilita o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs. É o comportamento padrão.
Se você deseja desabilitar o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs para os arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatacow .
**16. datasum e nodatasum
A opção datasum** mount habilita a soma de verificação de dados para arquivos recém-criados do sistema de arquivos Btrfs. Este é o comportamento padrão.
Se você não quiser que o sistema de arquivos Btrfs faça a soma de verificação dos dados dos arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatasum .
Perfis Btrfs
Um perfil Btrfs é usado para informar ao sistema de arquivos Btrfs quantas cópias dos dados/metadados devem ser mantidas e quais níveis de RAID devem ser usados para os dados/metadados. O sistema de arquivos Btrfs contém muitos perfis. Entendê-los o ajudará a configurar um RAID Btrfs da maneira que você deseja.
Os perfis Btrfs disponíveis são os seguintes:
single : Se o perfil único for usado para os dados/metadados, apenas uma cópia dos dados/metadados será armazenada no sistema de arquivos, mesmo se você adicionar vários dispositivos de armazenamento ao sistema de arquivos. Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
dup : Se o perfil dup for usado para os dados/metadados, cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos manterá duas cópias dos dados/metadados. Assim, 50% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
raid0 : No perfil raid0 , os dados/metadados serão divididos igualmente em todos os dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, não haverá dados/metadados redundantes (duplicados). Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser usado. Se, em qualquer caso, um dos dispositivos de armazenamento falhar, todo o sistema de arquivos será corrompido. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid0 .
raid1 : No perfil raid1 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a uma falha de unidade. Mas você pode usar apenas 50% do espaço total em disco. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1 .
raid1c3 : No perfil raid1c3 , três cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a duas falhas de unidade, mas você pode usar apenas 33% do espaço total em disco. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c3 .
raid1c4 : No perfil raid1c4 , quatro cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a três falhas de unidade, mas você pode usar apenas 25% do espaço total em disco. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c4 .
raid10 : No perfil raid10 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos, como no perfil raid1 . Além disso, os dados/metadados serão divididos entre os dispositivos de armazenamento, como no perfil raid0 .
O perfil raid10 é um híbrido dos perfis raid1 e raid0 . Alguns dos dispositivos de armazenamento formam arrays raid1 e alguns desses arrays raid1 são usados para formar um array raid0 . Em uma configuração raid10 , o sistema de arquivos pode sobreviver a uma única falha de unidade em cada uma das matrizes raid1 .
Você pode usar 50% do espaço total em disco na configuração raid10 . Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid10 .
raid5 : No perfil raid5 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Uma única paridade será calculada e distribuída entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid5 , o sistema de arquivos pode sobreviver a uma única falha de unidade. Se uma unidade falhar, você pode adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir da paridade distribuída das unidades em execução.
Você pode usar 1 00x(N-1)/N % do total de espaços em disco na configuração raid5 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid5 .
raid6 : No perfil raid6 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Duas paridades serão calculadas e distribuídas entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid6 , o sistema de arquivos pode sobreviver a duas falhas de unidade ao mesmo tempo. Se uma unidade falhar, você poderá adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir das duas paridades distribuídas das unidades em execução.
Você pode usar 100x(N-2)/N % do espaço total em disco na configuração raid6 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid6 .
-
 @ f10512df:c9293bb3
2025-04-22 17:11:05
@ f10512df:c9293bb3
2025-04-22 17:11:05Details
- 🍳 Cook time: 5-7 minutes
- 🍽️ Servings: 1
Ingredients
- 2 eggs
- Shredded cheese (Sharp cheddar is a favorite)
- 1 Tbsp olive oil or ghee
Directions
- Add oil to a non-stick pan and allow it to get hot (med-high heat)
- Add eggs and additional toppings, scramble and wait for the edges to get brown.
- Add shredded cheese while edges are browning. It is best if cheese begins to melt before flipping.
- Flip, and make sure all cheese stayed down, and there is enough oil left in the pan.
- Keep checking until pan side of eggs lift easily. Done correctly, the cheese will form a crisp layer.
- When fully cooked, serve with cheese right side up and enjoy!
-
 @ 91bea5cd:1df4451c
2025-04-15 06:23:35
@ 91bea5cd:1df4451c
2025-04-15 06:23:35Um bom gerenciamento de senhas deve ser simples e seguir a filosofia do Unix. Organizado em hierarquia e fácil de passar de um computador para outro.
E por isso não é recomendável o uso de aplicativos de terceiros que tenham acesso a suas chaves(senhas) em seus servidores, tampouco as opções nativas dos navegadores, que também pertencem a grandes empresas que fazem um grande esforço para ter acesso a nossas informações.
Recomendação
- pass
- Qtpass (gerenciador gráfico)
Com ele seus dados são criptografados usando sua chave gpg e salvo em arquivos organizados por pastas de forma hierárquica, podendo ser integrado a um serviço git de sua escolha ou copiado facilmente de um local para outro.
Uso
O seu uso é bem simples.
Configuração:
pass git initPara ver:
pass Email/example.comCopiar para área de transferência (exige xclip):
pass -c Email/example.comPara inserir:
pass insert Email/example0.comPara inserir e gerar senha:
pass generate Email/example1.comPara inserir e gerar senha sem símbolos:
pass generate --no-symbols Email/example1.comPara inserir, gerar senha e copiar para área de transferência :
pass generate -c Email/example1.comPara remover:
pass rm Email/example.com -
 @ a39d19ec:3d88f61e
2025-04-22 12:44:42
@ a39d19ec:3d88f61e
2025-04-22 12:44:42Die Debatte um Migration, Grenzsicherung und Abschiebungen wird in Deutschland meist emotional geführt. Wer fordert, dass illegale Einwanderer abgeschoben werden, sieht sich nicht selten dem Vorwurf des Rassismus ausgesetzt. Doch dieser Vorwurf ist nicht nur sachlich unbegründet, sondern verkehrt die Realität ins Gegenteil: Tatsächlich sind es gerade diejenigen, die hinter jeder Forderung nach Rechtssicherheit eine rassistische Motivation vermuten, die selbst in erster Linie nach Hautfarbe, Herkunft oder Nationalität urteilen.
Das Recht steht über Emotionen
Deutschland ist ein Rechtsstaat. Das bedeutet, dass Regeln nicht nach Bauchgefühl oder politischer Stimmungslage ausgelegt werden können, sondern auf klaren gesetzlichen Grundlagen beruhen müssen. Einer dieser Grundsätze ist in Artikel 16a des Grundgesetzes verankert. Dort heißt es:
„Auf Absatz 1 [Asylrecht] kann sich nicht berufen, wer aus einem Mitgliedstaat der Europäischen Gemeinschaften oder aus einem anderen Drittstaat einreist, in dem die Anwendung des Abkommens über die Rechtsstellung der Flüchtlinge und der Europäischen Menschenrechtskonvention sichergestellt ist.“
Das bedeutet, dass jeder, der über sichere Drittstaaten nach Deutschland einreist, keinen Anspruch auf Asyl hat. Wer dennoch bleibt, hält sich illegal im Land auf und unterliegt den geltenden Regelungen zur Rückführung. Die Forderung nach Abschiebungen ist daher nichts anderes als die Forderung nach der Einhaltung von Recht und Gesetz.
Die Umkehrung des Rassismusbegriffs
Wer einerseits behauptet, dass das deutsche Asyl- und Aufenthaltsrecht strikt durchgesetzt werden soll, und andererseits nicht nach Herkunft oder Hautfarbe unterscheidet, handelt wertneutral. Diejenigen jedoch, die in einer solchen Forderung nach Rechtsstaatlichkeit einen rassistischen Unterton sehen, projizieren ihre eigenen Denkmuster auf andere: Sie unterstellen, dass die Debatte ausschließlich entlang ethnischer, rassistischer oder nationaler Kriterien geführt wird – und genau das ist eine rassistische Denkweise.
Jemand, der illegale Einwanderung kritisiert, tut dies nicht, weil ihn die Herkunft der Menschen interessiert, sondern weil er den Rechtsstaat respektiert. Hingegen erkennt jemand, der hinter dieser Kritik Rassismus wittert, offenbar in erster Linie die „Rasse“ oder Herkunft der betreffenden Personen und reduziert sie darauf.
Finanzielle Belastung statt ideologischer Debatte
Neben der rechtlichen gibt es auch eine ökonomische Komponente. Der deutsche Wohlfahrtsstaat basiert auf einem Solidarprinzip: Die Bürger zahlen in das System ein, um sich gegenseitig in schwierigen Zeiten zu unterstützen. Dieser Wohlstand wurde über Generationen hinweg von denjenigen erarbeitet, die hier seit langem leben. Die Priorität liegt daher darauf, die vorhandenen Mittel zuerst unter denjenigen zu verteilen, die durch Steuern, Sozialabgaben und Arbeit zum Erhalt dieses Systems beitragen – nicht unter denen, die sich durch illegale Einreise und fehlende wirtschaftliche Eigenleistung in das System begeben.
Das ist keine ideologische Frage, sondern eine rein wirtschaftliche Abwägung. Ein Sozialsystem kann nur dann nachhaltig funktionieren, wenn es nicht unbegrenzt belastet wird. Würde Deutschland keine klaren Regeln zur Einwanderung und Abschiebung haben, würde dies unweigerlich zur Überlastung des Sozialstaates führen – mit negativen Konsequenzen für alle.
Sozialpatriotismus
Ein weiterer wichtiger Aspekt ist der Schutz der Arbeitsleistung jener Generationen, die Deutschland nach dem Zweiten Weltkrieg mühsam wieder aufgebaut haben. Während oft betont wird, dass die Deutschen moralisch kein Erbe aus der Zeit vor 1945 beanspruchen dürfen – außer der Verantwortung für den Holocaust –, ist es umso bedeutsamer, das neue Erbe nach 1945 zu respektieren, das auf Fleiß, Disziplin und harter Arbeit beruht. Der Wiederaufbau war eine kollektive Leistung deutscher Menschen, deren Früchte nicht bedenkenlos verteilt werden dürfen, sondern vorrangig denjenigen zugutekommen sollten, die dieses Fundament mitgeschaffen oder es über Generationen mitgetragen haben.
Rechtstaatlichkeit ist nicht verhandelbar
Wer sich für eine konsequente Abschiebepraxis ausspricht, tut dies nicht aus rassistischen Motiven, sondern aus Respekt vor der Rechtsstaatlichkeit und den wirtschaftlichen Grundlagen des Landes. Der Vorwurf des Rassismus in diesem Kontext ist daher nicht nur falsch, sondern entlarvt eine selektive Wahrnehmung nach rassistischen Merkmalen bei denjenigen, die ihn erheben.
-
 @ f10512df:c9293bb3
2025-04-22 17:00:44
@ f10512df:c9293bb3
2025-04-22 17:00:44Chef's notes
Use a tea bag to hold the spices. I like to fill it and drape it on the side of the pan so the flavors get in, and then toss it before serving. Easier than picking rosemary out of your teeth later.
Details
- ⏲️ Prep time: 20 minutes
- 🍳 Cook time: 1 hour 45 from scratch, 45 if using chicken stock
- 🍽️ Servings: 4
Ingredients
- 1 Cup Carrots (sliced)
- 1C celery (sliced)
- 2 cloves garlic
- 1 tsp dried thyme
- 1/2 tsp dried minced onion
- 2 Tbsp lemon juice (or more to taste)
- 1/2 Tbsp salt (to taste)
- 1 rotisserie chicken
- 2 tsp dried rosemary (or 1-2 sprigs fresh)
- 8 C water & additional 1-2 C later
- 10 oz pre-cooked noodles
- 1 tsp cracked pepper (to taste)
Directions
- Remove chicken meat from bones and set aside. Do not discard skin. Put bones and skin in a large stock pot and add water. Let boil covered for one hour, and then remove bones and strain out any bits of skin from broth.
- Add chopped vegetables, spices, and lemon juice to broth with up to 2 C. additional water to replace what might have boiled away. Simmer over low to medium heat (covered) for another half hour, stirring occasionally. Add in chicken meat. Taste test and add additional salt if needed.
- When vegetables are cooked, add in noodles and stir for an additional 2-3 minutes until hot (uncovered), and enjoy.
- If using store bought chicken stock, only simmer until vegetables are cooked (about half an hour).
-
 @ 4ba8e86d:89d32de4
2025-04-21 02:12:19
@ 4ba8e86d:89d32de4
2025-04-21 02:12:19SISTEMA OPERACIONAL MÓVEIS
GrapheneOS : https://njump.me/nevent1qqs8t76evdgrg4qegdtyrq2rved63pr29wlqyj627n9tj4vlu66tqpqpzdmhxue69uhk7enxvd5xz6tw9ec82c30qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqppcqec9
CalyxOS : https://njump.me/nevent1qqsrm0lws2atln2kt3cqjacathnw0uj0jsxwklt37p7t380hl8mmstcpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3vamnwvaz7tmwdaehgu3wvf3kstnwd9hx5cf0qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgcwaehxw309aex2mrp0yhxxatjwfjkuapwveukjtcpzpmhxue69uhkummnw3ezumt0d5hszrnhwden5te0dehhxtnvdakz7qfywaehxw309ahx7um5wgh8ymm4dej8ymmrdd3xjarrda5kuetjwvhxxmmd9uq3uamnwvaz7tmwdaehgu3dv3jhvtnhv4kxcmmjv3jhytnwv46z7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qgewaehxw309ahx7um5wghxymmwva3x7mn89e3k7mf0qythwumn8ghj7cn5vvhxkmr9dejxz7n49e3k7mf0qyg8wumn8ghj7mn09eehgu3wvdez7smttdu
LineageOS : https://njump.me/nevent1qqsgw7sr36gaty48cf4snw0ezg5mg4atzhqayuge752esd469p26qfgpzdmhxue69uhhwmm59e6hg7r09ehkuef0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpnvm779
SISTEMA OPERACIONAL DESKTOP
Tails : https://njump.me/nevent1qqsf09ztvuu60g6xprazv2vxqqy5qlxjs4dkc9d36ta48q75cs9le4qpzemhxue69uhkummnw3ex2mrfw3jhxtn0wfnj7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz34ag5t
Qubes OS : https://njump.me/nevent1qqsp6jujgwl68uvurw0cw3hfhr40xq20sj7rl3z4yzwnhp9sdpa7augpzpmhxue69uhkummnw3ezumt0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsz9thwden5te0dehhxarj9ehhsarj9ejx2a30qyg8wumn8ghj7mn09eehgu3wvdez7qg4waehxw309aex2mrp0yhxgctdw4eju6t09uqjxamnwvaz7tmwdaehgu3dwejhy6txd9jkgtnhv4kxcmmjv3jhytnwv46z7qgwwaehxw309ahx7uewd3hkctcpremhxue69uhkummnw3ez6er9wch8wetvd3hhyer9wghxuet59uj3ljr8
Kali linux : https://njump.me/nevent1qqswlav72xdvamuyp9xc38c6t7070l3n2uxu67ssmal2g7gv35nmvhspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswt9rxe
Whonix : https://njump.me/nevent1qqs85gvejvzhk086lwh6edma7fv07p5c3wnwnxnzthwwntg2x6773egpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3qamnwvaz7tmwdaehgu3wd4hk6tcpzemhxue69uhkummnw3ezucnrdqhxu6twdfsj7qfywaehxw309ahx7um5wgh8ymm4dej8ymmrdd3xjarrda5kuetjwvhxxmmd9uq3wamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmd9uq3qamnwvaz7tmwduh8xarj9e3hytcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszrnhwden5te0dehhxtnvdakz7qg7waehxw309ahx7um5wgkkgetk9emk2mrvdaexgetj9ehx2ap0sen9p6
Kodachi : https://njump.me/nevent1qqsf5zszgurpd0vwdznzk98hck294zygw0s8dah6fpd309ecpreqtrgpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszgmhwden5te0dehhxarj94mx2unfve5k2epwwajkcmr0wfjx2u3wdejhgtcpremhxue69uhkummnw3ez6er9wch8wetvd3hhyer9wghxuet59uq3qamnwvaz7tmwdaehgu3wd4hk6tcpzamhxue69uhkyarr9e4kcetwv3sh5afwvdhk6tcpzpmhxue69uhkumewwd68ytnrwghszfrhwden5te0dehhxarj9eex7atwv3ex7cmtvf5hgcm0d9hx2unn9e3k7mf0qyvhwumn8ghj7mn0wd68ytnzdahxwcn0denjucm0d5hszrnhwden5te0dehhxtnvdakz7qgkwaehxw309ahx7um5wghxycmg9ehxjmn2vyhsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshs94a4d5
PGP
Openkeychain : https://njump.me/nevent1qqs9qtjgsulp76t7jkquf8nk8txs2ftsr0qke6mjmsc2svtwfvswzyqpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs36mp0w
Kleopatra : https://njump.me/nevent1qqspnevn932hdggvp4zam6mfyce0hmnxsp9wp8htpumq9vm3anq6etsppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpuaeghp
Pgp : https://njump.me/nevent1qqsggek707qf3rzttextmgqhym6d4g479jdnlnj78j96y0ut0x9nemcpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgptemhe
Como funciona o PGP? : https://njump.me/nevent1qqsz9r7azc8pkvfmkg2hv0nufaexjtnvga0yl85x9hu7ptpg20gxxpspremhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet59upzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy259fhs
Por que eu escrevi PGP. - Philip Zimmermann.
https://njump.me/nevent1qqsvysn94gm8prxn3jw04r0xwc6sngkskg756z48jsyrmqssvxtm7ncpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtchzxnad
VPN
Vpn : https://njump.me/nevent1qqs27ltgsr6mh4ffpseexz6s37355df3zsur709d0s89u2nugpcygsspzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqshzu2fk
InviZible Pro : https://njump.me/nevent1qqsvyevf2vld23a3xrpvarc72ndpcmfvc3lc45jej0j5kcsg36jq53cpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy33y5l4
Orbot: https://njump.me/nevent1qqsxswkyt6pe34egxp9w70cy83h40ururj6m9sxjdmfass4cjm4495stft593
I2P
i2p : https://njump.me/nevent1qqsvnj8n983r4knwjmnkfyum242q4c0cnd338l4z8p0m6xsmx89mxkslx0pgg
Entendendo e usando a rede I2P : https://njump.me/nevent1qqsxchp5ycpatjf5s4ag25jkawmw6kkf64vl43vnprxdcwrpnms9qkcppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpvht4mn
Criando e acessando sua conta Email na I2P : https://njump.me/nevent1qqs9v9dz897kh8e5lfar0dl7ljltf2fpdathsn3dkdsq7wg4ksr8xfgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpw8mzum
APLICATIVO 2FA
Aegis Authenticator : https://njump.me/nevent1qqsfttdwcn9equlrmtf9n6wee7lqntppzm03pzdcj4cdnxel3pz44zspz4mhxue69uhhyetvv9ujumn0wd68ytnzvuhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqscvtydq
YubiKey : https://njump.me/nevent1qqstsnn69y4sf4330n7039zxm7wza3ch7sn6plhzmd57w6j9jssavtspvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzueyvgt
GERENCIADOR DE SENHAS
KeepassDX: https://njump.me/nevent1qqswc850dr4ujvxnmpx75jauflf4arc93pqsty5pv8hxdm7lcw8ee8qpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpe0492n
Birwaden: https://njump.me/nevent1qqs0j5x9guk2v6xumhwqmftmcz736m9nm9wzacqwjarxmh8k4xdyzwgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpwfe2kc
KeePassXC: https://njump.me/nevent1qqsgftcrd8eau7tzr2p9lecuaf7z8mx5jl9w2k66ae3lzkw5wqcy5pcl2achp
CHAT MENSAGEM
SimpleXchat : https://njump.me/nevent1qqsds5xselnnu0dyy0j49peuun72snxcgn3u55d2320n37rja9gk8lgzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgmcmj7c
Briar : https://njump.me/nevent1qqs8rrtgvjr499hreugetrl7adkhsj2zextyfsukq5aa7wxthrgcqcg05n434
Element Messenger : https://njump.me/nevent1qqsq05snlqtxm5cpzkshlf8n5d5rj9383vjytkvqp5gta37hpuwt4mqyccee6
Pidgin : https://njump.me/nevent1qqsz7kngycyx7meckx53xk8ahk98jkh400usrvykh480xa4ct9zlx2c2ywvx3
E-MAIL
Thunderbird: https://njump.me/nevent1qqspq64gg0nw7t60zsvea5eykgrm43paz845e4jn74muw5qzdvve7uqrkwtjh
ProtonMail : https://njump.me/nevent1qqs908glhk68e7ms8zqtlsqd00wu3prnpt08dwre26hd6e5fhqdw99cppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpeyhg4z
Tutonota : https://njump.me/nevent1qqswtzh9zjxfey644qy4jsdh9465qcqd2wefx0jxa54gdckxjvkrrmqpz4mhxue69uhhyetvv9ujumt0wd68ytnsw43qygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs5hzhkv
k-9 mail : https://njump.me/nevent1qqs200g5a603y7utjgjk320r3srurrc4r66nv93mcg0x9umrw52ku5gpr3mhxue69uhkummnw3ezuumhd9ehxtt9de5kwmtp9e3kstczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgacflak
E-MAIL-ALIÁS
Simplelogin : https://njump.me/nevent1qqsvhz5pxqpqzr2ptanqyqgsjr50v7u9lc083fvdnglhrv36rnceppcppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqp9gsr7m
AnonAddy : https://njump.me/nevent1qqs9mcth70mkq2z25ws634qfn7vx2mlva3tkllayxergw0s7p8d3ggcpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs6mawe3
NAVEGADOR
Navegador Tor : https://njump.me/nevent1qqs06qfxy7wzqmk76l5d8vwyg6mvcye864xla5up52fy5sptcdy39lspzemhxue69uhkummnw3ezuerpw3sju6rpw4ej7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdp0urw
Mullvap Browser : https://njump.me/nevent1qqs2vsgc3wk09wdspv2mezltgg7nfdg97g0a0m5cmvkvr4nrfxluzfcpzdmhxue69uhhwmm59e6hg7r09ehkuef0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpj8h6fe
LibreWolf : https://njump.me/nevent1qqswv05mlmkcuvwhe8x3u5f0kgwzug7n2ltm68fr3j06xy9qalxwq2cpzemhxue69uhkummnw3ex2mrfw3jhxtn0wfnj7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzuv2hxr
Cromite : https://njump.me/nevent1qqs2ut83arlu735xp8jf87w5m3vykl4lv5nwkhldkqwu3l86khzzy4cpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs3dplt7
BUSCADORES
Searx : https://njump.me/nevent1qqsxyzpvgzx00n50nrlgctmy497vkm2cm8dd5pdp7fmw6uh8xnxdmaspr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqp23z7ax
APP-STORE
Obtainium : https://njump.me/nevent1qqstd8kzc5w3t2v6dgf36z0qrruufzfgnc53rj88zcjgsagj5c5k4rgpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqyarmca3
F-Droid : https://njump.me/nevent1qqst4kry49cc9g3g8s5gdnpgyk3gjte079jdnv43f0x4e85cjkxzjesymzuu4
Droid-ify : https://njump.me/nevent1qqsrr8yu9luq0gud902erdh8gw2lfunpe93uc2u6g8rh9ep7wt3v4sgpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsfzu9vk
Aurora Store : https://njump.me/nevent1qqsy69kcaf0zkcg0qnu90mtk46ly3p2jplgpzgk62wzspjqjft4fpjgpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzrpmsjy
RSS
Feeder : https://njump.me/nevent1qqsy29aeggpkmrc7t3c7y7ldgda7pszl7c8hh9zux80gjzrfvlhfhwqpp4mhxue69uhkummn9ekx7mqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgsvzzjy
VIDEOO CONFERENCIA
Jitsi meet : https://njump.me/nevent1qqswphw67hr6qmt2fpugcj77jrk7qkfdrszum7vw7n2cu6cx4r6sh4cgkderr
TECLADOS
HeliBoard : https://njump.me/nevent1qqsyqpc4d28rje03dcvshv4xserftahhpeylu2ez2jutdxwds4e8syspz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsr8mel5
OpenBoard : https://njump.me/nevent1qqsf7zqkup03yysy67y43nj48q53sr6yym38es655fh9fp6nxpl7rqspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswcvh3r
FlorisBoard : https://njump.me/nevent1qqsf7zqkup03yysy67y43nj48q53sr6yym38es655fh9fp6nxpl7rqspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswcvh3r
MAPAS
Osmand : https://njump.me/nevent1qqsxryp2ywj64az7n5p6jq5tn3tx5jv05te48dtmmt3lf94ydtgy4fgpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs54nwpj
Organic maps : https://njump.me/nevent1qqstrecuuzkw0dyusxdq7cuwju0ftskl7anx978s5dyn4pnldrkckzqpr4mhxue69uhkummnw3ezumtp0p5k6ctrd96xzer9dshx7un8qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpl8z3kk
TRADUÇÃO
LibreTranslate : https://njump.me/nevent1qqs953g3rhf0m8jh59204uskzz56em9xdrjkelv4wnkr07huk20442cpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzeqsx40
REMOÇÃO DOS METADADOS
Scrambled Exif : https://njump.me/nevent1qqs2658t702xv66p000y4mlhnvadmdxwzzfzcjkjf7kedrclr3ej7aspyfmhxue69uhk6atvw35hqmr90pjhytngw4eh5mmwv4nhjtnhdaexcep0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpguu0wh
ESTEGANOGRAFIA
PixelKnot: https://njump.me/nevent1qqsrh0yh9mg0lx86t5wcmhh97wm6n4v0radh6sd0554ugn354wqdj8gpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqyuvfqdp
PERFIL DE TRABALHO
Shelter : https://njump.me/nevent1qqspv9xxkmfp40cxgjuyfsyczndzmpnl83e7gugm7480mp9zhv50wkqpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdnu59c
PDF
MuPDF : https://njump.me/nevent1qqspn5lhe0dteys6npsrntmv2g470st8kh8p7hxxgmymqa95ejvxvfcpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs4hvhvj
Librera Reader : https://njump.me/nevent1qqsg60flpuf00sash48fexvwxkly2j5z9wjvjrzt883t3eqng293f3cpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz39tt3n
QR-Code
Binary Eye : https://njump.me/nevent1qqsz4n0uxxx3q5m0r42n9key3hchtwyp73hgh8l958rtmae5u2khgpgpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdmn4wp
Climático
Breezy Weather : https://njump.me/nevent1qqs9hjz5cz0y4am3kj33xn536uq85ydva775eqrml52mtnnpe898rzspzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgpd3tu8
ENCRYPTS
Cryptomator : https://njump.me/nevent1qqsvchvnw779m20583llgg5nlu6ph5psewetlczfac5vgw83ydmfndspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsx7ppw9
VeraCrypt : https://njump.me/nevent1qqsf6wzedsnrgq6hjk5c4jj66dxnplqwc4ygr46l8z3gfh38q2fdlwgm65ej3
EXTENSÕES
uBlock Origin : https://njump.me/nevent1qqswaa666lcj2c4nhnea8u4agjtu4l8q89xjln0yrngj7ssh72ntwzql8ssdj
Snowflake : https://njump.me/nevent1qqs0ws74zlt8uced3p2vee9td8x7vln2mkacp8szdufvs2ed94ctnwchce008
CLOUD
Nextcloud : https://njump.me/nevent1qqs2utg5z9htegdtrnllreuhypkk2026x8a0xdsmfczg9wdl8rgrcgg9nhgnm
NOTEPAD
Joplin : https://njump.me/nevent1qqsz2a0laecpelsznser3xd0jfa6ch2vpxtkx6vm6qg24e78xttpk0cpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpdu0hft
Standard Notes : https://njump.me/nevent1qqsv3596kz3qung5v23cjc4cpq7rqxg08y36rmzgcrvw5whtme83y3s7tng6r
MÚSICA
RiMusic : https://njump.me/nevent1qqsv3genqav2tfjllp86ust4umxm8tr2wd9kq8x7vrjq6ssp363mn0gpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqg42353n
ViMusic : https://njump.me/nevent1qqswx78559l4jsxsrygd8kj32sch4qu57stxq0z6twwl450vp39pdqqpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzjg863j
PODCAST
AntennaPod : https://njump.me/nevent1qqsp4nh7k4a6zymfwqqdlxuz8ua6kdhvgeeh3uxf2c9rtp9u3e9ku8qnr8lmy
VISUALIZAR VIDEO
VLC : https://njump.me/nevent1qqs0lz56wtlr2eye4ajs2gzn2r0dscw4y66wezhx0mue6dffth8zugcl9laky
YOUTUBE
NewPipe : https://njump.me/nevent1qqsdg06qpcjdnlvgm4xzqdap0dgjrkjewhmh4j3v4mxdl4rjh8768mgdw9uln
FreeTube : https://njump.me/nevent1qqsz6y6z7ze5gs56s8seaws8v6m6j2zu0pxa955dhq3ythmexak38mcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs5lkjvv
LibreTube : https://snort.social/e/nevent1qqstmd5m6wrdvn4gxf8xyhrwnlyaxmr89c9kjddvnvux6603f84t3fqpz4mhxue69uhhyetvv9ujumt0wd68ytnsw43qygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsswwznc
COMPARTILHAMENTO DE ARQUIVOS
OnionShare : https://njump.me/nevent1qqsr0a4ml5nu6ud5k9yzyawcd9arznnwkrc27dzzc95q6r50xmdff6qpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3uamnwvaz7tmwdaehgu3dv3jhvtnhv4kxcmmjv3jhytnwv46z7qgswaehxw309ahx7tnnw3ezucmj9uq32amnwvaz7tmjv4kxz7fwv3sk6atn9e5k7tcpzamhxue69uhkyarr9e4kcetwv3sh5afwvdhk6tcpzemhxue69uhkummnw3ezucnrdqhxu6twdfsj7qgswaehxw309ahx7um5wghx6mmd9uqjgamnwvaz7tmwdaehgu3wwfhh2mnywfhkx6mzd96xxmmfdejhyuewvdhk6tcppemhxue69uhkummn9ekx7mp0qythwumn8ghj7un9d3shjtnwdaehgu3wvfskuep0qyv8wumn8ghj7un9d3shjtnrw4e8yetwwshxv7tf9ut7qurt
Localsend : https://njump.me/nevent1qqsp8ldjhrxm09cvvcak20hrc0g8qju9f67pw7rxr2y3euyggw9284gpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzuyghqr
Wallet Bitcoin
Ashigaru Wallet : https://njump.me/nevent1qqstx9fz8kf24wgl26un8usxwsqjvuec9f8q392llmga75tw0kfarfcpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgvfsrqp
Samourai Wallet : https://njump.me/nevent1qqstcvjmz39rmrnrv7t5cl6p3x7pzj6jsspyh4s4vcwd2lugmre04ecpr9mhxue69uhkummnw3ezucn0denkymmwvuhxxmmd9upzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy3rg4qs
CÂMERA
opencamera : https://njump.me/nevent1qqs25glp6dh0crrjutxrgdjlnx9gtqpjtrkg29hlf7382aeyjd77jlqpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqssxcvgc
OFFICE
Collabora Office : https://njump.me/nevent1qqs8yn4ys6adpmeu3edmf580jhc3wluvlf823cc4ft4h0uqmfzdf99qpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsj40uss
TEXTOS
O manifesto de um Cypherpunk : https://njump.me/nevent1qqsd7hdlg6galn5mcuv3pm3ryfjxc4tkyph0cfqqe4du4dr4z8amqyspvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzal0efa
Operations security ( OPSEC) : https://snort.social/e/nevent1qqsp323havh3y9nxzd4qmm60hw87tm9gjns0mtzg8y309uf9mv85cqcpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz8ej9l7
O MANIFESTO CRIPTOANARQUISTA Timothy C. May – 1992. : https://njump.me/nevent1qqspp480wtyx2zhtwpu5gptrl8duv9rvq3mug85mp4d54qzywk3zq9gpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz5wq496
Declaração de independência do ciberespaço
- John Perry Barlow - 1996 : https://njump.me/nevent1qqs2njsy44n6p07mhgt2tnragvchasv386nf20ua5wklxqpttf6mzuqpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsukg4hr
The Cyphernomicon: Criptografia, Dinheiro Digital e o Futuro da Privacidade. escrito por Timothy C. May -Publicado em 1994. :
Livro completo em PDF no Github PrivacyOpenSource.
https://github.com/Alexemidio/PrivacyOpenSource/raw/main/Livros/THE%20CYPHERNOMICON%20.pdf Share
-
 @ 91bea5cd:1df4451c
2025-04-15 06:19:19
@ 91bea5cd:1df4451c
2025-04-15 06:19:19O que é Tahoe-LAFS?
Bem-vindo ao Tahoe-LAFS_, o primeiro sistema de armazenamento descentralizado com
- Segurança independente do provedor * .
Tahoe-LAFS é um sistema que ajuda você a armazenar arquivos. Você executa um cliente Programa no seu computador, que fala com um ou mais servidores de armazenamento em outros computadores. Quando você diz ao seu cliente para armazenar um arquivo, ele irá criptografar isso Arquivo, codifique-o em múltiplas peças, depois espalhe essas peças entre Vários servidores. As peças são todas criptografadas e protegidas contra Modificações. Mais tarde, quando você pede ao seu cliente para recuperar o arquivo, ele irá Encontre as peças necessárias, verifique se elas não foram corrompidas e remontadas Eles, e descriptografar o resultado.
O cliente cria mais peças (ou "compartilhamentos") do que acabará por precisar, então Mesmo que alguns servidores falhem, você ainda pode recuperar seus dados. Corrompido Os compartilhamentos são detectados e ignorados, de modo que o sistema pode tolerar o lado do servidor Erros no disco rígido. Todos os arquivos são criptografados (com uma chave exclusiva) antes Uploading, então mesmo um operador de servidor mal-intencionado não pode ler seus dados. o A única coisa que você pede aos servidores é que eles podem (geralmente) fornecer o Compartilha quando você os solicita: você não está confiando sobre eles para Confidencialidade, integridade ou disponibilidade absoluta.
O que é "segurança independente do provedor"?
Todo vendedor de serviços de armazenamento na nuvem irá dizer-lhe que o seu serviço é "seguro". Mas o que eles significam com isso é algo fundamentalmente diferente Do que queremos dizer. O que eles significam por "seguro" é que depois de ter dado Eles o poder de ler e modificar seus dados, eles tentam muito difícil de não deixar Esse poder seja abusado. Isso acaba por ser difícil! Insetos, Configurações incorretas ou erro do operador podem acidentalmente expor seus dados para Outro cliente ou para o público, ou pode corromper seus dados. Criminosos Ganho rotineiramente de acesso ilícito a servidores corporativos. Ainda mais insidioso é O fato de que os próprios funcionários às vezes violam a privacidade do cliente De negligência, avareza ou mera curiosidade. O mais consciencioso de Esses prestadores de serviços gastam consideráveis esforços e despesas tentando Mitigar esses riscos.
O que queremos dizer com "segurança" é algo diferente. * O provedor de serviços Nunca tem a capacidade de ler ou modificar seus dados em primeiro lugar: nunca. * Se você usa Tahoe-LAFS, então todas as ameaças descritas acima não são questões para você. Não só é fácil e barato para o provedor de serviços Manter a segurança de seus dados, mas na verdade eles não podem violar sua Segurança se eles tentaram. Isto é o que chamamos de * independente do fornecedor segurança*.
Esta garantia está integrada naturalmente no sistema de armazenamento Tahoe-LAFS e Não exige que você execute um passo de pré-criptografia manual ou uma chave complicada gestão. (Afinal, ter que fazer operações manuais pesadas quando Armazenar ou acessar seus dados anularia um dos principais benefícios de Usando armazenamento em nuvem em primeiro lugar: conveniência.)
Veja como funciona:
Uma "grade de armazenamento" é constituída por uma série de servidores de armazenamento. Um servidor de armazenamento Tem armazenamento direto em anexo (tipicamente um ou mais discos rígidos). Um "gateway" Se comunica com os nós de armazenamento e os usa para fornecer acesso ao Rede sobre protocolos como HTTP (S), SFTP ou FTP.
Observe que você pode encontrar "cliente" usado para se referir aos nós do gateway (que atuam como Um cliente para servidores de armazenamento) e também para processos ou programas que se conectam a Um nó de gateway e operações de execução na grade - por exemplo, uma CLI Comando, navegador da Web, cliente SFTP ou cliente FTP.
Os usuários não contam com servidores de armazenamento para fornecer * confidencialidade * nem
- Integridade * para seus dados - em vez disso, todos os dados são criptografados e Integridade verificada pelo gateway, para que os servidores não possam ler nem Modifique o conteúdo dos arquivos.
Os usuários dependem de servidores de armazenamento para * disponibilidade *. O texto cifrado é Codificado por apagamento em partes
Ndistribuídas em pelo menosHdistintas Servidores de armazenamento (o valor padrão paraNé 10 e paraHé 7) então Que pode ser recuperado de qualquerKdesses servidores (o padrão O valor deKé 3). Portanto, apenas a falha doH-K + 1(com o Padrões, 5) servidores podem tornar os dados indisponíveis.No modo de implantação típico, cada usuário executa seu próprio gateway sozinho máquina. Desta forma, ela confia em sua própria máquina para a confidencialidade e Integridade dos dados.
Um modo de implantação alternativo é que o gateway é executado em uma máquina remota e O usuário se conecta ao HTTPS ou SFTP. Isso significa que o operador de O gateway pode visualizar e modificar os dados do usuário (o usuário * depende de * o Gateway para confidencialidade e integridade), mas a vantagem é que a O usuário pode acessar a grade Tahoe-LAFS com um cliente que não possui o Software de gateway instalado, como um quiosque de internet ou celular.
Controle de acesso
Existem dois tipos de arquivos: imutáveis e mutáveis. Quando você carrega um arquivo Para a grade de armazenamento, você pode escolher o tipo de arquivo que será no grade. Os arquivos imutáveis não podem ser modificados quando foram carregados. UMA O arquivo mutable pode ser modificado por alguém com acesso de leitura e gravação. Um usuário Pode ter acesso de leitura e gravação a um arquivo mutable ou acesso somente leitura, ou não Acesso a ele.
Um usuário que tenha acesso de leitura e gravação a um arquivo mutable ou diretório pode dar Outro acesso de leitura e gravação do usuário a esse arquivo ou diretório, ou eles podem dar Acesso somente leitura para esse arquivo ou diretório. Um usuário com acesso somente leitura Para um arquivo ou diretório pode dar acesso a outro usuário somente leitura.
Ao vincular um arquivo ou diretório a um diretório pai, você pode usar um Link de leitura-escrita ou um link somente de leitura. Se você usar um link de leitura e gravação, então Qualquer pessoa que tenha acesso de leitura e gravação ao diretório pai pode obter leitura-escrita Acesso à criança e qualquer pessoa que tenha acesso somente leitura ao pai O diretório pode obter acesso somente leitura à criança. Se você usar uma leitura somente Link, qualquer pessoa que tenha lido-escrito ou acesso somente leitura ao pai O diretório pode obter acesso somente leitura à criança.
================================================== ==== Usando Tahoe-LAFS com uma rede anônima: Tor, I2P ================================================== ====
. `Visão geral '
. `Casos de uso '
.
Software Dependencies_#.
Tor#.I2P. `Configuração de conexão '
. `Configuração de Anonimato '
#.
Anonimato do cliente ' #.Anonimato de servidor, configuração manual ' #. `Anonimato de servidor, configuração automática '. `Problemas de desempenho e segurança '
Visão geral
Tor é uma rede anonimização usada para ajudar a esconder a identidade da Internet Clientes e servidores. Consulte o site do Tor Project para obter mais informações: Https://www.torproject.org/
I2P é uma rede de anonimato descentralizada que se concentra no anonimato de ponta a ponta Entre clientes e servidores. Consulte o site I2P para obter mais informações: Https://geti2p.net/
Casos de uso
Existem três casos de uso potenciais para Tahoe-LAFS do lado do cliente:
-
O usuário deseja sempre usar uma rede de anonimato (Tor, I2P) para proteger Seu anonimato quando se conecta às redes de armazenamento Tahoe-LAFS (seja ou Não os servidores de armazenamento são anônimos).
-
O usuário não se preocupa em proteger seu anonimato, mas eles desejam se conectar a Servidores de armazenamento Tahoe-LAFS que são acessíveis apenas através de Tor Hidden Services ou I2P.
-
Tor é usado apenas se uma sugestão de conexão do servidor usar
tor:. Essas sugestões Geralmente tem um endereço.onion. -
I2P só é usado se uma sugestão de conexão do servidor usa
i2p:. Essas sugestões Geralmente têm um endereço.i2p. -
O usuário não se preocupa em proteger seu anonimato ou para se conectar a um anonimato Servidores de armazenamento. Este documento não é útil para você ... então pare de ler.
Para servidores de armazenamento Tahoe-LAFS existem três casos de uso:
-
O operador deseja proteger o anonimato fazendo seu Tahoe Servidor acessível apenas em I2P, através de Tor Hidden Services, ou ambos.
-
O operador não * requer * anonimato para o servidor de armazenamento, mas eles Quer que ele esteja disponível tanto no TCP / IP roteado publicamente quanto através de um Rede de anonimização (I2P, Tor Hidden Services). Uma possível razão para fazer Isso é porque ser alcançável através de uma rede de anonimato é um Maneira conveniente de ignorar NAT ou firewall que impede roteios públicos Conexões TCP / IP ao seu servidor (para clientes capazes de se conectar a Tais servidores). Outro é o que torna o seu servidor de armazenamento acessível Através de uma rede de anonimato pode oferecer uma melhor proteção para sua Clientes que usam essa rede de anonimato para proteger seus anonimato.
-
O operador do servidor de armazenamento não se preocupa em proteger seu próprio anonimato nem Para ajudar os clientes a proteger o deles. Pare de ler este documento e execute Seu servidor de armazenamento Tahoe-LAFS usando TCP / IP com roteamento público.
Veja esta página do Tor Project para obter mais informações sobre Tor Hidden Services: Https://www.torproject.org/docs/hidden-services.html.pt
Veja esta página do Projeto I2P para obter mais informações sobre o I2P: Https://geti2p.net/en/about/intro
Dependências de software
Tor
Os clientes que desejam se conectar a servidores baseados em Tor devem instalar o seguinte.
-
Tor (tor) deve ser instalado. Veja aqui: Https://www.torproject.org/docs/installguide.html.en. No Debian / Ubuntu, Use
apt-get install tor. Você também pode instalar e executar o navegador Tor Agrupar. -
Tahoe-LAFS deve ser instalado com o
[tor]"extra" habilitado. Isso vai Instaletxtorcon::
Pip install tahoe-lafs [tor]
Os servidores Tor-configurados manualmente devem instalar Tor, mas não precisam
Txtorconou o[tor]extra. Configuração automática, quando Implementado, vai precisar destes, assim como os clientes.I2P
Os clientes que desejam se conectar a servidores baseados em I2P devem instalar o seguinte. Tal como acontece com Tor, os servidores baseados em I2P configurados manualmente precisam do daemon I2P, mas Não há bibliotecas especiais de apoio Tahoe-side.
-
I2P deve ser instalado. Veja aqui: Https://geti2p.net/en/download
-
A API SAM deve estar habilitada.
-
Inicie o I2P.
- Visite http://127.0.0.1:7657/configclients no seu navegador.
- Em "Configuração do Cliente", marque a opção "Executar no Startup?" Caixa para "SAM Ponte de aplicação ".
- Clique em "Salvar Configuração do Cliente".
-
Clique no controle "Iniciar" para "ponte de aplicação SAM" ou reinicie o I2P.
-
Tahoe-LAFS deve ser instalado com o
[i2p]extra habilitado, para obterTxi2p::
Pip install tahoe-lafs [i2p]
Tor e I2P
Os clientes que desejam se conectar a servidores baseados em Tor e I2P devem instalar tudo acima. Em particular, Tahoe-LAFS deve ser instalado com ambos Extras habilitados ::
Pip install tahoe-lafs [tor, i2p]
Configuração de conexão
Consulte: ref:
Connection Managementpara uma descrição do[tor]e[I2p]seções detahoe.cfg. Estes controlam como o cliente Tahoe Conecte-se a um daemon Tor / I2P e, assim, faça conexões com Tor / I2P-baseadas Servidores.As seções
[tor]e[i2p]só precisam ser modificadas para serem usadas de forma incomum Configurações ou para habilitar a configuração automática do servidor.A configuração padrão tentará entrar em contato com um daemon local Tor / I2P Ouvindo as portas usuais (9050/9150 para Tor, 7656 para I2P). Enquanto Há um daemon em execução no host local e o suporte necessário Bibliotecas foram instaladas, os clientes poderão usar servidores baseados em Tor Sem qualquer configuração especial.
No entanto, note que esta configuração padrão não melhora a Anonimato: as conexões TCP normais ainda serão feitas em qualquer servidor que Oferece um endereço regular (cumpre o segundo caso de uso do cliente acima, não o terceiro). Para proteger o anonimato, os usuários devem configurar o
[Connections]da seguinte maneira:[Conexões] Tcp = tor
Com isso, o cliente usará Tor (em vez de um IP-address -reviração de conexão direta) para alcançar servidores baseados em TCP.
Configuração de anonimato
Tahoe-LAFS fornece uma configuração "flag de segurança" para indicar explicitamente Seja necessário ou não a privacidade do endereço IP para um nó ::
[nó] Revelar-IP-address = (booleano, opcional)
Quando
revelar-IP-address = False, Tahoe-LAFS se recusará a iniciar se algum dos As opções de configuração emtahoe.cfgrevelariam a rede do nó localização:-
[Conexões] tcp = toré necessário: caso contrário, o cliente faria Conexões diretas para o Introdução, ou qualquer servidor baseado em TCP que aprende Do Introdutor, revelando seu endereço IP para esses servidores e um Rede de espionagem. Com isso, Tahoe-LAFS só fará Conexões de saída através de uma rede de anonimato suportada. -
Tub.locationdeve ser desativado ou conter valores seguros. este O valor é anunciado para outros nós através do Introdutor: é como um servidor Anuncia sua localização para que os clientes possam se conectar a ela. No modo privado, ele É um erro para incluir umtcp:dica notub.location. Modo privado Rejeita o valor padrão detub.location(quando a chave está faltando Inteiramente), que éAUTO, que usaifconfigpara adivinhar o nó Endereço IP externo, o que o revelaria ao servidor e a outros clientes.
Esta opção é ** crítica ** para preservar o anonimato do cliente (cliente Caso de uso 3 de "Casos de uso", acima). Também é necessário preservar uma Anonimato do servidor (caso de uso do servidor 3).
Esse sinalizador pode ser configurado (para falso), fornecendo o argumento
--hide-ippara Os comandoscreate-node,create-clientoucreate-introducer.Observe que o valor padrão de
revelar-endereço IPé verdadeiro, porque Infelizmente, esconder o endereço IP do nó requer software adicional para ser Instalado (conforme descrito acima) e reduz o desempenho.Anonimato do cliente
Para configurar um nó de cliente para anonimato,
tahoe.cfg** deve ** conter o Seguindo as bandeiras de configuração ::[nó] Revelar-IP-address = False Tub.port = desativado Tub.location = desativado
Uma vez que o nodo Tahoe-LAFS foi reiniciado, ele pode ser usado anonimamente (cliente Caso de uso 3).
Anonimato do servidor, configuração manual
Para configurar um nó de servidor para ouvir em uma rede de anonimato, devemos primeiro Configure Tor para executar um "Serviço de cebola" e encaminhe as conexões de entrada para o Porto Tahoe local. Então, configuramos Tahoe para anunciar o endereço
.onionAos clientes. Também configuramos Tahoe para não fazer conexões TCP diretas.- Decida em um número de porta de escuta local, chamado PORT. Isso pode ser qualquer não utilizado Porta de cerca de 1024 até 65535 (dependendo do kernel / rede do host Config). Nós diremos a Tahoe para escutar nesta porta, e nós diremos a Tor para Encaminhe as conexões de entrada para ele.
- Decida em um número de porta externo, chamado VIRTPORT. Isso será usado no Localização anunciada e revelada aos clientes. Pode ser qualquer número de 1 Para 65535. Pode ser o mesmo que PORT, se quiser.
- Decida em um "diretório de serviço oculto", geralmente em
/ var / lib / tor / NAME. Pediremos a Tor para salvar o estado do serviço de cebola aqui, e Tor irá Escreva o endereço.onionaqui depois que ele for gerado.
Em seguida, faça o seguinte:
-
Crie o nó do servidor Tahoe (com
tahoe create-node), mas não ** não ** Lança-o ainda. -
Edite o arquivo de configuração Tor (normalmente em
/ etc / tor / torrc). Precisamos adicionar Uma seção para definir o serviço oculto. Se nossa PORT for 2000, VIRTPORT é 3000, e estamos usando/ var / lib / tor / tahoecomo o serviço oculto Diretório, a seção deve se parecer com ::HiddenServiceDir / var / lib / tor / tahoe HiddenServicePort 3000 127.0.0.1:2000
-
Reinicie Tor, com
systemctl restart tor. Aguarde alguns segundos. -
Leia o arquivo
hostnameno diretório de serviço oculto (por exemplo,/ Var / lib / tor / tahoe / hostname). Este será um endereço.onion, comoU33m4y7klhz3b.onion. Ligue para esta CEBOLA. -
Edite
tahoe.cfgpara configurartub.portpara usarTcp: PORT: interface = 127.0.0.1etub.locationpara usarTor: ONION.onion: VIRTPORT. Usando os exemplos acima, isso seria ::[nó] Revelar-endereço IP = falso Tub.port = tcp: 2000: interface = 127.0.0.1 Tub.location = tor: u33m4y7klhz3b.onion: 3000 [Conexões] Tcp = tor
-
Inicie o servidor Tahoe com
tahoe start $ NODEDIR
A seção
tub.portfará com que o servidor Tahoe ouça no PORT, mas Ligue o soquete de escuta à interface de loopback, que não é acessível Do mundo exterior (mas * é * acessível pelo daemon Tor local). Então o A seçãotcp = torfaz com que Tahoe use Tor quando se conecta ao Introdução, escondendo o endereço IP. O nó se anunciará a todos Clientes que usam `tub.location``, então os clientes saberão que devem usar o Tor Para alcançar este servidor (e não revelar seu endereço IP através do anúncio). Quando os clientes se conectam ao endereço da cebola, seus pacotes serão Atravessar a rede de anonimato e eventualmente aterrar no Tor local Daemon, que então estabelecerá uma conexão com PORT no localhost, que é Onde Tahoe está ouvindo conexões.Siga um processo similar para construir um servidor Tahoe que escuta no I2P. o O mesmo processo pode ser usado para ouvir tanto o Tor como o I2P (
tub.location = Tor: ONION.onion: VIRTPORT, i2p: ADDR.i2p). Também pode ouvir tanto Tor como TCP simples (caso de uso 2), comtub.port = tcp: PORT,tub.location = Tcp: HOST: PORT, tor: ONION.onion: VIRTPORTeanonymous = false(e omite A configuraçãotcp = tor, já que o endereço já está sendo transmitido através de O anúncio de localização).Anonimato do servidor, configuração automática
Para configurar um nó do servidor para ouvir em uma rede de anonimato, crie o Nó com a opção
--listen = tor. Isso requer uma configuração Tor que Ou lança um novo daemon Tor, ou tem acesso à porta de controle Tor (e Autoridade suficiente para criar um novo serviço de cebola). Nos sistemas Debian / Ubuntu, façaApt install tor, adicione-se ao grupo de controle comadduser YOURUSERNAME debian-tore, em seguida, inicie sessão e faça o login novamente: se osgroupsO comando incluidebian-torna saída, você deve ter permissão para Use a porta de controle de domínio unix em/ var / run / tor / control.Esta opção irá definir
revelar-IP-address = Falsee[connections] tcp = Tor. Ele alocará as portas necessárias, instruirá Tor para criar a cebola Serviço (salvando a chave privada em algum lugar dentro de NODEDIR / private /), obtenha O endereço.onione preenchatub.portetub.locationcorretamente.Problemas de desempenho e segurança
Se você estiver executando um servidor que não precisa ser Anônimo, você deve torná-lo acessível através de uma rede de anonimato ou não? Ou você pode torná-lo acessível * ambos * através de uma rede de anonimato E como um servidor TCP / IP rastreável publicamente?
Existem várias compensações efetuadas por esta decisão.
Penetração NAT / Firewall
Fazer com que um servidor seja acessível via Tor ou I2P o torna acessível (por Clientes compatíveis com Tor / I2P) mesmo que existam NAT ou firewalls que impeçam Conexões TCP / IP diretas para o servidor.
Anonimato
Tornar um servidor Tahoe-LAFS acessível * somente * via Tor ou I2P pode ser usado para Garanta que os clientes Tahoe-LAFS usem Tor ou I2P para se conectar (Especificamente, o servidor só deve anunciar endereços Tor / I2P no Chave de configuração
tub.location). Isso evita que os clientes mal configurados sejam Desingonizando-se acidentalmente, conectando-se ao seu servidor através de A Internet rastreável.Claramente, um servidor que está disponível como um serviço Tor / I2P * e * a O endereço TCP regular não é anônimo: o endereço do .on e o real O endereço IP do servidor é facilmente vinculável.
Além disso, a interação, através do Tor, com um Tor Oculto pode ser mais Protegido da análise do tráfego da rede do que a interação, através do Tor, Com um servidor TCP / IP com rastreamento público
** XXX há um documento mantido pelos desenvolvedores de Tor que comprovem ou refutam essa crença? Se assim for, precisamos ligar a ele. Caso contrário, talvez devêssemos explicar mais aqui por que pensamos isso? **
Linkability
A partir de 1.12.0, o nó usa uma única chave de banheira persistente para saída Conexões ao Introdutor e conexões de entrada para o Servidor de Armazenamento (E Helper). Para os clientes, uma nova chave Tub é criada para cada servidor de armazenamento Nós aprendemos sobre, e essas chaves são * não * persistiram (então elas mudarão cada uma delas Tempo que o cliente reinicia).
Clientes que atravessam diretórios (de rootcap para subdiretório para filecap) são É provável que solicitem os mesmos índices de armazenamento (SIs) na mesma ordem de cada vez. Um cliente conectado a vários servidores irá pedir-lhes todos para o mesmo SI em Quase ao mesmo tempo. E dois clientes que compartilham arquivos ou diretórios Irá visitar os mesmos SI (em várias ocasiões).
Como resultado, as seguintes coisas são vinculáveis, mesmo com
revelar-endereço IP = Falso:- Servidores de armazenamento podem vincular reconhecer várias conexões do mesmo Cliente ainda não reiniciado. (Observe que o próximo recurso de Contabilidade pode Faz com que os clientes apresentem uma chave pública persistente do lado do cliente quando Conexão, que será uma ligação muito mais forte).
- Os servidores de armazenamento provavelmente podem deduzir qual cliente está acessando dados, por Olhando as SIs sendo solicitadas. Vários servidores podem conciliar Determine que o mesmo cliente está falando com todos eles, mesmo que o TubIDs são diferentes para cada conexão.
- Os servidores de armazenamento podem deduzir quando dois clientes diferentes estão compartilhando dados.
- O Introdutor pode entregar diferentes informações de servidor para cada um Cliente subscrito, para particionar clientes em conjuntos distintos de acordo com Quais as conexões do servidor que eles eventualmente fazem. Para clientes + nós de servidor, ele Também pode correlacionar o anúncio do servidor com o cliente deduzido identidade.
atuação
Um cliente que se conecta a um servidor Tahoe-LAFS com rastreamento público através de Tor Incorrem em latência substancialmente maior e, às vezes, pior Mesmo cliente se conectando ao mesmo servidor através de um TCP / IP rastreável normal conexão. Quando o servidor está em um Tor Hidden Service, ele incorre ainda mais Latência e, possivelmente, ainda pior rendimento.
Conectando-se a servidores Tahoe-LAFS que são servidores I2P incorrem em maior latência E pior rendimento também.
Efeitos positivos e negativos em outros usuários Tor
O envio de seu tráfego Tahoe-LAFS sobre o Tor adiciona tráfego de cobertura para outros Tor usuários que também estão transmitindo dados em massa. Então isso é bom para Eles - aumentando seu anonimato.
No entanto, torna o desempenho de outros usuários do Tor Sessões - por exemplo, sessões ssh - muito pior. Isso é porque Tor Atualmente não possui nenhuma prioridade ou qualidade de serviço Recursos, para que as teclas de Ssh de outra pessoa possam ter que esperar na fila Enquanto o conteúdo do arquivo em massa é transmitido. O atraso adicional pode Tornar as sessões interativas de outras pessoas inutilizáveis.
Ambos os efeitos são duplicados se você carregar ou baixar arquivos para um Tor Hidden Service, em comparação com se você carregar ou baixar arquivos Over Tor para um servidor TCP / IP com rastreamento público
Efeitos positivos e negativos em outros usuários do I2P
Enviar seu tráfego Tahoe-LAFS ao I2P adiciona tráfego de cobertura para outros usuários do I2P Que também estão transmitindo dados. Então, isso é bom para eles - aumentando sua anonimato. Não prejudicará diretamente o desempenho de outros usuários do I2P Sessões interativas, porque a rede I2P possui vários controles de congestionamento e Recursos de qualidade de serviço, como priorizar pacotes menores.
No entanto, se muitos usuários estão enviando tráfego Tahoe-LAFS ao I2P e não tiverem Seus roteadores I2P configurados para participar de muito tráfego, então o I2P A rede como um todo sofrerá degradação. Cada roteador Tahoe-LAFS que usa o I2P tem Seus próprios túneis de anonimato que seus dados são enviados. Em média, um O nó Tahoe-LAFS requer 12 outros roteadores I2P para participar de seus túneis.
Portanto, é importante que o seu roteador I2P esteja compartilhando a largura de banda com outros Roteadores, para que você possa retornar enquanto usa o I2P. Isso nunca prejudicará a Desempenho de seu nó Tahoe-LAFS, porque seu roteador I2P sempre Priorize seu próprio tráfego.
=========================
Como configurar um servidor
Muitos nós Tahoe-LAFS são executados como "servidores", o que significa que eles fornecem serviços para Outras máquinas (isto é, "clientes"). Os dois tipos mais importantes são os Introdução e Servidores de armazenamento.
Para ser útil, os servidores devem ser alcançados pelos clientes. Os servidores Tahoe podem ouvir Em portas TCP e anunciar sua "localização" (nome do host e número da porta TCP) Para que os clientes possam se conectar a eles. Eles também podem ouvir os serviços de cebola "Tor" E portas I2P.
Os servidores de armazenamento anunciam sua localização ao anunciá-lo ao Introdutivo, Que então transmite a localização para todos os clientes. Então, uma vez que a localização é Determinado, você não precisa fazer nada de especial para entregá-lo.
O próprio apresentador possui uma localização, que deve ser entregue manualmente a todos Servidores de armazenamento e clientes. Você pode enviá-lo para os novos membros do seu grade. Esta localização (juntamente com outros identificadores criptográficos importantes) é Escrito em um arquivo chamado
private / introducer.furlno Presenter's Diretório básico, e deve ser fornecido como o argumento--introducer =paraTahoe create-nodeoutahoe create-node.O primeiro passo ao configurar um servidor é descobrir como os clientes irão alcançar. Então você precisa configurar o servidor para ouvir em algumas portas, e Depois configure a localização corretamente.
Configuração manual
Cada servidor tem duas configurações em seu arquivo
tahoe.cfg:tub.port, eTub.location. A "porta" controla o que o nó do servidor escuta: isto Geralmente é uma porta TCP.A "localização" controla o que é anunciado para o mundo exterior. Isto é um "Sugestão de conexão foolscap", e inclui tanto o tipo de conexão (Tcp, tor ou i2p) e os detalhes da conexão (nome do host / endereço, porta número). Vários proxies, gateways e redes de privacidade podem ser Envolvido, então não é incomum para
tub.portetub.locationpara olhar diferente.Você pode controlar diretamente a configuração
tub.portetub.locationConfigurações, fornecendo--port =e--location =ao executartahoe Create-node.Configuração automática
Em vez de fornecer
--port = / - location =, você pode usar--listen =. Os servidores podem ouvir em TCP, Tor, I2P, uma combinação desses ou nenhum. O argumento--listen =controla quais tipos de ouvintes o novo servidor usará.--listen = nonesignifica que o servidor não deve ouvir nada. Isso não Faz sentido para um servidor, mas é apropriado para um nó somente cliente. o O comandotahoe create-clientinclui automaticamente--listen = none.--listen = tcpé o padrão e liga uma porta de escuta TCP padrão. Usar--listen = tcprequer um argumento--hostname =também, que será Incorporado no local anunciado do nó. Descobrimos que os computadores Não pode determinar de forma confiável seu nome de host acessível externamente, então, em vez de Ter o servidor adivinhar (ou escanear suas interfaces para endereços IP Isso pode ou não ser apropriado), a criação de nó requer que o usuário Forneça o nome do host.--listen = torconversará com um daemon Tor local e criará uma nova "cebola" Servidor "(que se parece comalzrgrdvxct6c63z.onion).--listen = i2p` conversará com um daemon I2P local e criará um novo servidor endereço. Consulte: doc:anonymity-configuration` para obter detalhes.Você pode ouvir nos três usando
--listen = tcp, tor, i2p.Cenários de implantação
A seguir, alguns cenários sugeridos para configurar servidores usando Vários transportes de rede. Estes exemplos não incluem a especificação de um Apresentador FURL que normalmente você gostaria quando provisionamento de armazenamento Nós. Para estes e outros detalhes de configuração, consulte : Doc:
configuration.. `Servidor possui um nome DNS público '
.
Servidor possui um endereço público IPv4 / IPv6_.
O servidor está por trás de um firewall com encaminhamento de porta_.
Usando o I2P / Tor para evitar o encaminhamento da porta_O servidor possui um nome DNS público
O caso mais simples é o local onde o host do servidor está diretamente conectado ao Internet, sem um firewall ou caixa NAT no caminho. A maioria dos VPS (Virtual Private Servidor) e servidores colocados são assim, embora alguns fornecedores bloqueiem Muitas portas de entrada por padrão.
Para esses servidores, tudo o que você precisa saber é o nome do host externo. O sistema O administrador irá dizer-lhe isso. O principal requisito é que este nome de host Pode ser pesquisado no DNS, e ele será mapeado para um endereço IPv4 ou IPv6 que Alcançará a máquina.
Se o seu nome de host for
example.net, então você criará o introdutor como esta::Tahoe create-introducer --hostname example.com ~ / introducer
Ou um servidor de armazenamento como ::
Tahoe create-node --hostname = example.net
Estes irão alocar uma porta TCP (por exemplo, 12345), atribuir
tub.portpara serTcp: 12345etub.locationserãotcp: example.com: 12345.Idealmente, isso também deveria funcionar para hosts compatíveis com IPv6 (onde o nome DNS Fornece um registro "AAAA", ou ambos "A" e "AAAA"). No entanto Tahoe-LAFS O suporte para IPv6 é novo e ainda pode ter problemas. Por favor, veja o ingresso
# 867_ para detalhes... _ # 867: https://tahoe-lafs.org/trac/tahoe-lafs/ticket/867
O servidor possui um endereço público IPv4 / IPv6
Se o host tiver um endereço IPv4 (público) rotativo (por exemplo,
203.0.113.1```), mas Nenhum nome DNS, você precisará escolher uma porta TCP (por exemplo,3457``) e usar o Segue::Tahoe create-node --port = tcp: 3457 - localização = tcp: 203.0.113.1: 3457
--porté uma "string de especificação de ponto de extremidade" que controla quais locais Porta em que o nó escuta.--locationé a "sugestão de conexão" que ele Anuncia para outros, e descreve as conexões de saída que essas Os clientes irão fazer, por isso precisa trabalhar a partir da sua localização na rede.Os nós Tahoe-LAFS escutam em todas as interfaces por padrão. Quando o host é Multi-homed, você pode querer fazer a ligação de escuta ligar apenas a uma Interface específica, adicionando uma opção
interface =ao--port =argumento::Tahoe create-node --port = tcp: 3457: interface = 203.0.113.1 - localização = tcp: 203.0.113.1: 3457
Se o endereço público do host for IPv6 em vez de IPv4, use colchetes para Envolva o endereço e altere o tipo de nó de extremidade para
tcp6::Tahoe create-node --port = tcp6: 3457 - localização = tcp: [2001: db8 :: 1]: 3457
Você pode usar
interface =para vincular a uma interface IPv6 específica também, no entanto Você deve fazer uma barra invertida - escapar dos dois pontos, porque, de outra forma, eles são interpretados Como delimitadores pelo idioma de especificação do "ponto final" torcido. o--location =argumento não precisa de dois pontos para serem escapados, porque eles são Envolto pelos colchetes ::Tahoe create-node --port = tcp6: 3457: interface = 2001 \: db8 \: \: 1 --location = tcp: [2001: db8 :: 1]: 3457
Para hosts somente IPv6 com registros DNS AAAA, se o simples
--hostname =A configuração não funciona, eles podem ser informados para ouvir especificamente Porta compatível com IPv6 com este ::Tahoe create-node --port = tcp6: 3457 - localização = tcp: example.net: 3457
O servidor está por trás de um firewall com encaminhamento de porta
Para configurar um nó de armazenamento por trás de um firewall com encaminhamento de porta, você irá precisa saber:
- Endereço IPv4 público do roteador
- A porta TCP que está disponível de fora da sua rede
- A porta TCP que é o destino de encaminhamento
- Endereço IPv4 interno do nó de armazenamento (o nó de armazenamento em si é
Desconhece esse endereço e não é usado durante
tahoe create-node, Mas o firewall deve ser configurado para enviar conexões para isso)
Os números de porta TCP internos e externos podem ser iguais ou diferentes Dependendo de como o encaminhamento da porta está configurado. Se é mapear portas 1-para-1, eo endereço IPv4 público do firewall é 203.0.113.1 (e Talvez o endereço IPv4 interno do nó de armazenamento seja 192.168.1.5), então Use um comando CLI como este ::
Tahoe create-node --port = tcp: 3457 - localização = tcp: 203.0.113.1: 3457
Se no entanto, o firewall / NAT-box encaminha a porta externa * 6656 * para o interno Porta 3457, então faça isso ::
Tahoe create-node --port = tcp: 3457 - localização = tcp: 203.0.113.1: 6656
Usando o I2P / Tor para evitar o encaminhamento da porta
Os serviços de cebola I2P e Tor, entre outras excelentes propriedades, também fornecem NAT Penetração sem encaminhamento de porta, nomes de host ou endereços IP. Então, configurando Um servidor que escuta apenas no Tor é simples ::
Tahoe create-node --listen = tor
Para mais informações sobre o uso de Tahoe-LAFS com I2p e Tor veja : Doc:
anonymity-configuration -
 @ 1c19eb1a:e22fb0bc
2025-04-22 01:36:33
@ 1c19eb1a:e22fb0bc
2025-04-22 01:36:33After my first major review of Primal on Android, we're going to go a very different direction for this next review. Primal is your standard "Twitter clone" type of kind 1 note client, now branching into long-form. They also have a team of developers working on making it one of the best clients to fill that use-case. By contrast, this review will not be focusing on any client at all. Not even an "other stuff" client.
Instead, we will be reviewing a very useful tool created and maintained by nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 called #Amber. For those unfamiliar with Amber, it is an #Android application dedicated to managing your signing keys, and allowing you to log into various #Nostr applications without having to paste in your private key, better known as your #nsec. It is not recommended to paste your nsec into various applications because they each represent another means by which it could be compromised, and anyone who has your nsec can post as you. On Nostr, your #npub is your identity, and your signature using your private key is considered absolute proof that any given note, reaction, follow update, or profile change was authorized by the rightful owner of that identity.
It happens less often these days, but early on, when the only way to try out a new client was by inputting your nsec, users had their nsec compromised from time to time, or they would suspect that their key may have been compromised. When this occurs, there is no way to recover your account, or set a new private key, deprecating the previous one. The only thing you can do is start over from scratch, letting everyone know that your key has been compromised and to follow you on your new npub.
If you use Amber to log into other Nostr apps, you significantly reduce the likelihood that your private key will be compromised, because only one application has access to it, and all other applications reach out to Amber to sign any events. This isn't quite as secure as storing your private key on a separate device that isn't connected to the internet whatsoever, like many of us have grown accustomed to with securing our #Bitcoin, but then again, an online persona isn't nearly as important to secure for most of us as our entire life savings.
Amber is the first application of its kind for managing your Nostr keys on a mobile device. nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 didn't merely develop the application, but literally created the specification for accomplishing external signing on Android which can be found in NIP-55. Unfortunately, Amber is only available for Android. A signer application for iOS is in the works from nostr:npub1yaul8k059377u9lsu67de7y637w4jtgeuwcmh5n7788l6xnlnrgs3tvjmf, but is not ready for use at this time. There is also a new mobile signer app for Android and iOS called Nowser, but I have not yet had a chance to try this app out. From a cursory look at the Android version, it is indeed in the very early stages of development and cannot be compared with Amber.
This review of Amber is current as of version 3.2.5.

Overall Impression
Score: 4.7 / 5 (Updated 4/21/2025)
I cannot speak highly enough about Amber as a tool that every Nostr user on Android should start using if they are not already. When the day comes that we have more options for well-developed signer apps on mobile, my opinion may very well change, but until then Amber is what we have available to us. Even so, it is an incredibly well thought-out and reliable tool for securing your nsec.
Despite being the only well-established Android signer available for Android, Amber can be compared with other external signing methods available on other platforms. Even with more competition in this arena, though, Amber still holds up incredibly well. If you are signing into web applications on a desktop, I still would recommend using a browser extension like #Alby or #Nos2x, as the experience is usually faster, more seamless, and far more web apps support this signing method (NIP-07) than currently support the two methods employed by Amber. Nevertheless that gap is definitely narrowing.
A running list I created of applications that support login and signing with Amber can be found here: Nostr Clients with External Signer Support
I have run into relatively few bugs in my extensive use of Amber for all of my mobile signing needs. Occasionally the application crashes when trying to send it a signing request from a couple of applications, but I would not be surprised if this is no fault of Amber at all, and rather the fault of those specific apps, since it works flawlessly with the vast majority of apps that support either NIP-55 or NIP-46 login.
I also believe that mobile is the ideal platform to use for this type of application. First, because most people use Nostr clients on their phone more than on a desktop. There are, of course, exceptions to that, but in general we spend more time on our phones when interacting online. New users are also more likely to be introduced to Nostr by a friend having them download a Nostr client on their phone than on a PC, and that can be a prime opportunity to introduce the new user to protecting their private key. Finally, I agree with the following assessment from nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn.
nostr:nevent1qqsw0r6gzn05xg67h5q2xkplwsuzedjxw9lf7ntrxjl8ajm350fcyugprfmhxue69uhhyetvv9ujumn0wd68yurvv438xtnrdaksyg9hyaxj3clfswlhyrd5kjsj5v04clhjvgeq6pwztmysfzdvn93gev7awu9v
The one downside to Amber is that it will be quite foreign for new users. That is partially unavoidable with Nostr, since folks are not accustomed to public/private key cryptography in general, let alone using a private key to log into websites or social media apps. However, the initial signup process is a bit cumbersome if Amber is being used as the means of initially generating a key pair. I think some of this could be foregone at start-up in favor of streamlining onboarding, and then encourage the user to back-up their private key at a later time.
Features
Amber has some features that may surprise you, outside of just storing your private key and signing requests from your favorite Nostr clients. It is a full key management application, supporting multiple accounts, various backup methods, and even the ability to authorize other users to access a Nostr profile you control.
Android Signing
This is the signing method where Amber really shines in both speed and ease of use. Any Android application that supports this standard, and even some progressive web-apps that can be installed to your Android's home-screen, can very quickly and seamlessly connect with Amber to authorize anything that you need signed with your nsec. All you have to do is select "Login with Amber" in clients like #Amethyst or #0xChat and the app will reach out to Amber for all signing requests from there on out. If you had previously signed into the app with your nsec, you will first need to log out, then choose the option to use Amber when you log back in.

This is a massive deal, because everything you do on Nostr requires a signature from your private key. Log in? Needs a signature. Post a "GM" note? Needs a signature. Follow someone who zapped your note? Needs a signature. Zap them back? You guessed it; needs a signature. When you paste your private key into an application, it will automatically sign a lot of these actions without you ever being asked for approval, but you will quickly realize just how many things the client is doing on your behalf when Amber is asking you to approve them each time.
Now, this can also get quite annoying after a while. I recommend using the setting that allows Amber to automatically sign for basic functions, which will cut down on some of the authorization spam. Once you have been asked to authorize the same type of action a few times, you can also toggle the option to automatically authorize that action in the future. Don't worry, though, you have full control to require Amber to ask you for permission again if you want to be alerted each time, and this toggle is specific to each application, so it's not a blanket approval for all Nostr clients you connect with.

This method of signing is just as fast as signing via browser extension on web clients, which users may be more accustomed to. Everything is happening locally on the device, so it can be very snappy and secure.
Nostr Connect/Bunker Signing
This next method of signing has a bit of a delay, because it is using a Nostr relay to send encrypted information back and forth between the app the user is interacting with and Amber to obtain signatures remotely. It isn't a significant delay most of the time, but it is just enough to be noticeable.
Also, unlike the previous signing method that would automatically switch to Amber as the active application when a signing request is sent, this method only sends you a notification that you must be watching for. This can lead to situations where you are wondering why something isn't working in a client you signed into remotely, because it is waiting on you to authorize the action and you didn't notice the notification from Amber. As you use the application, you get used to the need to check for such authorization requests from time to time, or when something isn't working as expected.

By default, Amber will use relay.nsec.app to communicate with whichever Nostr app you are connecting to. You can set a different relay for this purpose, if you like, though not just any relay will support the event kinds that Amber uses for remote signing. You can even run your own relay just for your own signing purposes. In fact, the creator of Amber has a relay application you can run on your phone, called Citrine, that can be used for signing with any web app you are using locally on your phone. This is definitely more of an advanced option, but it is there for you if you want it. For most users, sticking with relay.nsec.app will be just fine, especially since the contents of the events sent back and forth for signing are all encrypted.
Something many users may not realize is that this remote signing feature allows for issuing signing permissions to team members. For instance, if anyone ever joined me in writing reviews, I could issue them a connection string from Amber, and limit their permissions to just posting long-form draft events. Anything else they tried to do would require my explicit approval each time. Moreover, I could revoke those permissions if I ever felt they were being abused, without the need to start over with a whole new npub. Of course, this requires that your phone is online whenever a team member is trying to sign using the connection string you issued, and it requires you pay attention to your notifications so you can approve or reject requests you have not set to auto-approve. However, this is probably only useful for small teams, and larger businesses will want to find a more robust solution for managing access to their npub, such as Keycast from nostr:npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc.
The method for establishing a connection between Amber and a Nostr app for remote signing can vary for each app. Most, at minimum, will support obtaining a connection string from Amber that starts with "bunker://" and pasting it in at the time of login. Then you just need to approve the connection request from Amber and the client will log you in and send any subsequent signing requests to Amber using the same connection string.

Some clients will also offer the option to scan a QR code to connect the client to Amber. This is quite convenient, but just remember that this also means the client is setting which relay will be used for communication between the two. Clients with this option will also have a connection string you can copy and paste into Amber to achieve the same purpose. For instance, you may need this option if you are trying to connect to an app on your phone and therefore can't scan the QR code using Amber on the same phone.

Multiple Accounts
Amber does not lock you into using it with only a single set of keys. You can add all of your Nostr "accounts" to Amber and use it for signing events for each independently. Of course, Nostr doesn't actually have "accounts" in the traditional sense. Your identity is simply your key-pair, and Amber stores and accesses each private key as needed.

When first signing in using native Android signing as described above, Amber will default to whichever account was most recently selected, but you can switch to the account that is needed before approving the request. After initial login, Amber will automatically detect the account that the signing request is for.
Key Backup & Restore
Amber allows multiple ways to back up your private key. As most users would expect, you can get your standard nsec and copy/paste it to a password manager, but you can also obtain your private key as a list of mnemonic seed words, an encrypted version of your key called an ncryptsec, or even a QR code of your nsec or ncryptsec.

Additionally, in order to gain access to this information, Amber requires you to enter your device's PIN or use biometric authentication. This isn't cold-storage level protection for your private key by any means, especially since your phone is an internet connected device and does not store your key within a secure element, but it is about as secure as you can ask for while having your key accessible for signing Nostr events.
Tor Support
While Amber does not have Tor support within the app itself, it does support connecting to Tor through Orbot. This would be used with remote signing so that Amber would not connect directly over clearnet to the relay used for communication with the Nostr app requesting the signature. Instead, Amber would connect through Tor, so the relay would not see your IP address. This means you can utilize the remote signing option without compromising your anonymity.

Additional Security
Amber allows the user the option to require either biometric or PIN authentication before approving signing requests. This can provide that extra bit of assurance that no one will be able to sign events using your private key if they happen to gain access to your phone. The PIN you set in Amber is also independent from the PIN to unlock your device, allowing for separation of access.
Can My Grandma Use It?
Score: 4.6 / 5 (Updated 4/21/2025)
At the end of the day, Amber is a tool for those who have some concept of the importance of protecting their private key by not pasting it into every Nostr client that comes along. This concept in itself is not terribly approachable to an average person. They are used to just plugging their password into every service they use, and even worse, they usually have the same password for everything so they can more readily remember it. The idea that they should never enter their "Nostr password" into any Nostr application would never occur to them unless someone first explained how cryptography works related to public/private key pairs.
That said, I think there can be some improvements made to how users are introduced to these concepts, and that a signer application like Amber might be ideal for the job. Considering Amber as a new user's first touch-point with Nostr, I think it holds up well, but could be somewhat streamlined.
Upon opening the app, the user is prompted to either use their existing private key or "Create a new Nostr account." This is straightforward enough. "Account" is not a technically correct term with Nostr, but it is a term that new users would be familiar with and understand the basic concept.

The next screen announces that the account is ready, and presents the user with their public key, explaining that it is "a sort of username" that will allow others to find them on Nostr. While it is good to explain this to the user, it is unnecessary information at this point. This screen also prompts the user to set a nickname and set a password to encrypt their private key. Since the backup options also allow the user to set this password, I think this step could be pushed to a later time. This screen would better serve the new user if it simply prompted them to set a nickname and short bio that could be saved to a few default relays.

Of course, Amber is currently prompting for a password to be set up-front because the next screen requires the new user to download a "backup kit" in order to continue. While I do believe it is a good idea to encourage the creation of a backup, it is not crucial to do so immediately upon creation of a new npub that has nothing at stake if the private key is lost. This is something the UI could remind the user to do at a later time, reducing the friction of profile creation, and expediting getting them into the action.

Outside of these minor onboarding friction points, I think Amber does a great job of explaining to the user the purpose of each of its features, all within the app and without any need to reference external documentation. As long as the user understands the basic concept that their private key is being stored by Amber in order to sign requests from other Nostr apps, so they don't have to be given the private key, Amber is very good about explaining the rest without getting too far into the technical weeds.
The most glaring usability issue with Amber is that it isn't available in the Play Store. Average users expect to be able to find applications they can trust in their mobile device's default app store. There is a valid argument to be made that they are incorrect in this assumption, but that doesn't change the fact that this is the assumption most people make. They believe that applications in the Play Store are "safe" and that anything they can't install through the Play Store is suspect. The prompts that the Android operating system requires the user to approve when installing "unknown apps" certainly doesn't help with this impression.
Now, I absolutely love the Zapstore from nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9, but it doesn't do much to alleviate this issue. Users will still need to be convinced that it is safe to install the Zapstore from the GitHub repo, and then install Amber from there. Furthermore, this adds yet another step to the onboarding process.
Instead of:
- Install Amber
- Set up your keys
- Install the client you want to use
- Log in with Amber
The process becomes:
- Go to the Zapstore GitHub and download the latest version from the releases page.
- Install the APK you downloaded, allowing any prompt to install unknown apps.
- Open Zapstore and install Amber, allowing any prompt to install unknown apps again.
- Open Amber and set up your keys.
- Install the client you want to use
- Log in with Amber
An application as important as Amber for protecting users' private keys should be as readily available to the new user as possible. New users are the ones most prone to making mistakes that could compromise their private keys. Amber should be available to them in the Play Store.
UPDATE: As of version 3.2.8 released on 4/21/2025, the onboarding flow for Amber has been greatly improved! Now, when selecting to set up a new "account" the user is informed on the very next screen, "Your Nostr account is ready!" and given their public key/npub. The only field the user must fill in is their "nickname"/display name and hit "Continue."
From there the user is asked if they want Amber to automatically approve basic actions, or manually approve each app, and then they are shown a new Applications screen, with a prompt to create a backup of their account. This prompt persists until the user has done so.
As you can see, the user is also encouraged to find applications that can be used with Amber with links to nostrapps.com and the Zapstore.
Thanks to these updates, Amber is now the smoothest and most user-friendly onboarding experience I have seen for Nostr to date. Sure, it doesn't have anything for setting up a profile picture or lightning address, but that is better done in a client like Amethyst or YakiHonne, anyway. Just tap "create," type in a handle to call yourself, and you're done!
How do UI Look?
Score: 4.5 / 5
Amber's UI can be described as clean but utilitarian. But then, Amber is a tool, so this is somewhat expected. It is not an app you will be spending a lot of time in, so the UI just needs to be serviceable. I would say it accomplishes this and then some. UI elements are generally easy to understand what they do, and page headings fill in the gaps where that is not the case.

I am not the biggest fan of the color-scheme, particularly in light-mode, but it is not bad in dark-mode at all, and Amber follows whatever theme you have set for your device in that respect. Additionally, the color choice does make sense given the application's name.

It must also be taken into consideration that Amber is almost entirely the product of a single developer's work. He has done a great job producing an app that is not only useful, but pleasant to interact with. The same cannot be said for most utility apps I have previously used, with interfaces that clearly made good design the lowest priority. While Amber's UI may not be the most beautiful Nostr app I have seen, design was clearly not an afterthought, either, and it is appreciated.
Relay Management
Score: 4.9 / 5
Even though Amber is not a Nostr client, where users can browse notes from their favorite npubs, it still relies heavily on relays for some of its features. Primarily, it uses relays for communicating with other Nostr apps for remote signing requests. However, it also uses relays to fetch profile data, so that each private key you add to Amber will automatically load your chosen username and profile picture.
In the relay settings, users can choose which relays are being used to fetch profile data, and which relays will be used by default when creating new remote signing connection strings.

The user can also see which relays are currently connected to Amber and even look at the information that has been passed back and forth on each of those active relays. This information about actively connected relays is not only available within the application, but also in the notification that Amber has to keep in your device's notification tray in order to continue to operate in the background while you are using other apps.

Optionality is the name of the game when it comes to how Amber handles relay selection. The user can just stick with the default signing relay, use their own relay as the default, or even use a different relay for each Nostr application that they connect to for remote signing. Amber gives the user an incredible amount of flexibility in this regard.
In addition to all of this, because not all relays accept the event types needed for remote signing, when you add a relay address to Amber, it automatically tests that relay to see if it will work. This alone can be a massive time saver, so users aren't trying to use relays that don't support remote signing and wondering why they can't log into noStrudel with the connection string they got from Amber.

The only way I could see relay management being improved would be some means of giving the user relay recommendations, in case they want to use a relay other than relay.nsec.app, but they aren't sure which other relays will accept remote signing events. That said, most users who want to use a different relay for signing remote events will likely be using their own, in which case recommendations aren't needed.
Current Users' Questions
The AskNostr hashtag can be a good indication of the pain points that other users are currently having with any Nostr application. Here are some of the most common questions submitted about Amber in the last two months.
nostr:nevent1qqsfrdr68fafgcvl8dgnhm9hxpsjxuks78afxhu8yewhtyf3d7mkg9gpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgq3qkgh77xxt7hhtt4u528hecnx69rhagla8jj3tclgyf9wvkxa6dc0sxp0e6m
This is a good example of Amber working correctly, but the app the user is trying to log into not working. In my experience with #Olas in particular, it sometimes allows remote signer login, and sometimes doesn't. Amber will receive the signing request and I will approve it, but Olas remains on the login screen.
If Amber is receiving the signing requests, and you are approving them, the fault is likely with the application you are trying to log into.
That's it. That's all the repeated questions I could find. Oh, there were a few one-off questions where relay.nsec.app wouldn't connect, or where the user's out-of-date web browser was the issue. Outside of that, though, there were no common questions about how to use Amber, and that is a testament to Amber's ease of use all on its own.
Wrap Up
If you are on Android and you are not already using Amber to protect your nsec, please do yourself a favor and get it installed. It's not at all complicated to set up, and it will make trying out all the latest Nostr clients a safe and pleasant experience.
If you are a client developer and you have not added support for NIP-55 or NIP-46, do your users the courtesy of respecting the sanctity of their private keys. Even developers who have no intention of compromising their users' keys can inadvertently do so. Make that eventuality impossible by adding support for NIP-55 and NIP-46 signing.
Finally, I apologize for the extended time it took me to get this review finished. The time I have available is scarce, Nostr is distracting, and nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 kept improving Amber even as I was putting it through its paces over the last two months. Keep shipping, my friend! You have made one of the most useful tools we have seen for Nostr to date!
Now... What should I review next?
-
 @ 39cc53c9:27168656
2025-04-09 07:59:33
@ 39cc53c9:27168656
2025-04-09 07:59:33Know Your Customer is a regulation that requires companies of all sizes to verify the identity, suitability, and risks involved with maintaining a business relationship with a customer. Such procedures fit within the broader scope of anti-money laundering (AML) and counterterrorism financing (CTF) regulations.
Banks, exchanges, online business, mail providers, domain registrars... Everyone wants to know who you are before you can even opt for their service. Your personal information is flowing around the internet in the hands of "god-knows-who" and secured by "trust-me-bro military-grade encryption". Once your account is linked to your personal (and verified) identity, tracking you is just as easy as keeping logs on all these platforms.
Rights for Illusions
KYC processes aim to combat terrorist financing, money laundering, and other illicit activities. On the surface, KYC seems like a commendable initiative. I mean, who wouldn't want to halt terrorists and criminals in their tracks?
The logic behind KYC is: "If we mandate every financial service provider to identify their users, it becomes easier to pinpoint and apprehend the malicious actors."
However, terrorists and criminals are not precisely lining up to be identified. They're crafty. They may adopt false identities or find alternative strategies to continue their operations. Far from being outwitted, many times they're several steps ahead of regulations. Realistically, KYC might deter a small fraction – let's say about 1% ^1 – of these malefactors. Yet, the cost? All of us are saddled with the inconvenient process of identification just to use a service.
Under the rhetoric of "ensuring our safety", governments and institutions enact regulations that seem more out of a dystopian novel, gradually taking away our right to privacy.
To illustrate, consider a city where the mayor has rolled out facial recognition cameras in every nook and cranny. A band of criminals, intent on robbing a local store, rolls in with a stolen car, their faces obscured by masks and their bodies cloaked in all-black clothes. Once they've committed the crime and exited the city's boundaries, they switch vehicles and clothes out of the cameras' watchful eyes. The high-tech surveillance? It didn’t manage to identify or trace them. Yet, for every law-abiding citizen who merely wants to drive through the city or do some shopping, their movements and identities are constantly logged. The irony? This invasive tracking impacts all of us, just to catch the 1% ^1 of less-than-careful criminals.
KYC? Not you.
KYC creates barriers to participation in normal economic activity, to supposedly stop criminals. ^2
KYC puts barriers between many users and businesses. One of these comes from the fact that the process often requires multiple forms of identification, proof of address, and sometimes even financial records. For individuals in areas with poor record-keeping, non-recognized legal documents, or those who are unbanked, homeless or transient, obtaining these documents can be challenging, if not impossible.
For people who are not skilled with technology or just don't have access to it, there's also a barrier since KYC procedures are mostly online, leaving them inadvertently excluded.
Another barrier goes for the casual or one-time user, where they might not see the value in undergoing a rigorous KYC process, and these requirements can deter them from using the service altogether.
It also wipes some businesses out of the equation, since for smaller businesses, the costs associated with complying with KYC norms—from the actual process of gathering and submitting documents to potential delays in operations—can be prohibitive in economical and/or technical terms.
You're not welcome
Imagine a swanky new club in town with a strict "members only" sign. You hear the music, you see the lights, and you want in. You step up, ready to join, but suddenly there's a long list of criteria you must meet. After some time, you are finally checking all the boxes. But then the club rejects your membership with no clear reason why. You just weren't accepted. Frustrating, right?
This club scenario isn't too different from the fact that KYC is being used by many businesses as a convenient gatekeeping tool. A perfect excuse based on a "legal" procedure they are obliged to.
Even some exchanges may randomly use this to freeze and block funds from users, claiming these were "flagged" by a cryptic system that inspects the transactions. You are left hostage to their arbitrary decision to let you successfully pass the KYC procedure. If you choose to sidestep their invasive process, they might just hold onto your funds indefinitely.
Your identity has been stolen
KYC data has been found to be for sale on many dark net markets^3. Exchanges may have leaks or hacks, and such leaks contain very sensitive data. We're talking about the full monty: passport or ID scans, proof of address, and even those awkward selfies where you're holding up your ID next to your face. All this data is being left to the mercy of the (mostly) "trust-me-bro" security systems of such companies. Quite scary, isn't it?
As cheap as $10 for 100 documents, with discounts applying for those who buy in bulk, the personal identities of innocent users who passed KYC procedures are for sale. ^3
In short, if you have ever passed the KYC/AML process of a crypto exchange, your privacy is at risk of being compromised, or it might even have already been compromised.
(they) Know Your Coins
You may already know that Bitcoin and most cryptocurrencies have a transparent public blockchain, meaning that all data is shown unencrypted for everyone to see and recorded forever. If you link an address you own to your identity through KYC, for example, by sending an amount from a KYC exchange to it, your Bitcoin is no longer pseudonymous and can then be traced.
If, for instance, you send Bitcoin from such an identified address to another KYC'ed address (say, from a friend), everyone having access to that address-identity link information (exchanges, governments, hackers, etc.) will be able to associate that transaction and know who you are transacting with.
Conclusions
To sum up, KYC does not protect individuals; rather, it's a threat to our privacy, freedom, security and integrity. Sensible information flowing through the internet is thrown into chaos by dubious security measures. It puts borders between many potential customers and businesses, and it helps governments and companies track innocent users. That's the chaos KYC has stirred.
The criminals are using stolen identities from companies that gathered them thanks to these very same regulations that were supposed to combat them. Criminals always know how to circumvent such regulations. In the end, normal people are the most affected by these policies.
The threat that KYC poses to individuals in terms of privacy, security and freedom is not to be neglected. And if we don’t start challenging these systems and questioning their efficacy, we are just one step closer to the dystopian future that is now foreseeable.
Edited 20/03/2024 * Add reference to the 1% statement on Rights for Illusions section to an article where Chainalysis found that only 0.34% of the transaction volume with cryptocurrencies in 2023 was attributable to criminal activity ^1
-
 @ 83279ad2:bd49240d
2025-04-20 08:39:12
@ 83279ad2:bd49240d
2025-04-20 08:39:12Hello
-
 @ 68c90cf3:99458f5c
2025-04-04 16:06:10
@ 68c90cf3:99458f5c
2025-04-04 16:06:10I have two Nostr profiles I use for different subject matter, and I wanted a way to manage and track zaps for each. Using Alby Hub I created two isolated Lightning wallets each associated with one of the profile’s nsecs.
YakiHonne made it easy to connect the associated wallets with the profiles. The user interface is well designed to show balances for each.
In my case, I have one profile for photography related content, and the other for Bitcoin, Nostr, and technology related content. I can easily switch between the two, sending and receiving zaps on each while staying up to date on balances and viewing transactions.
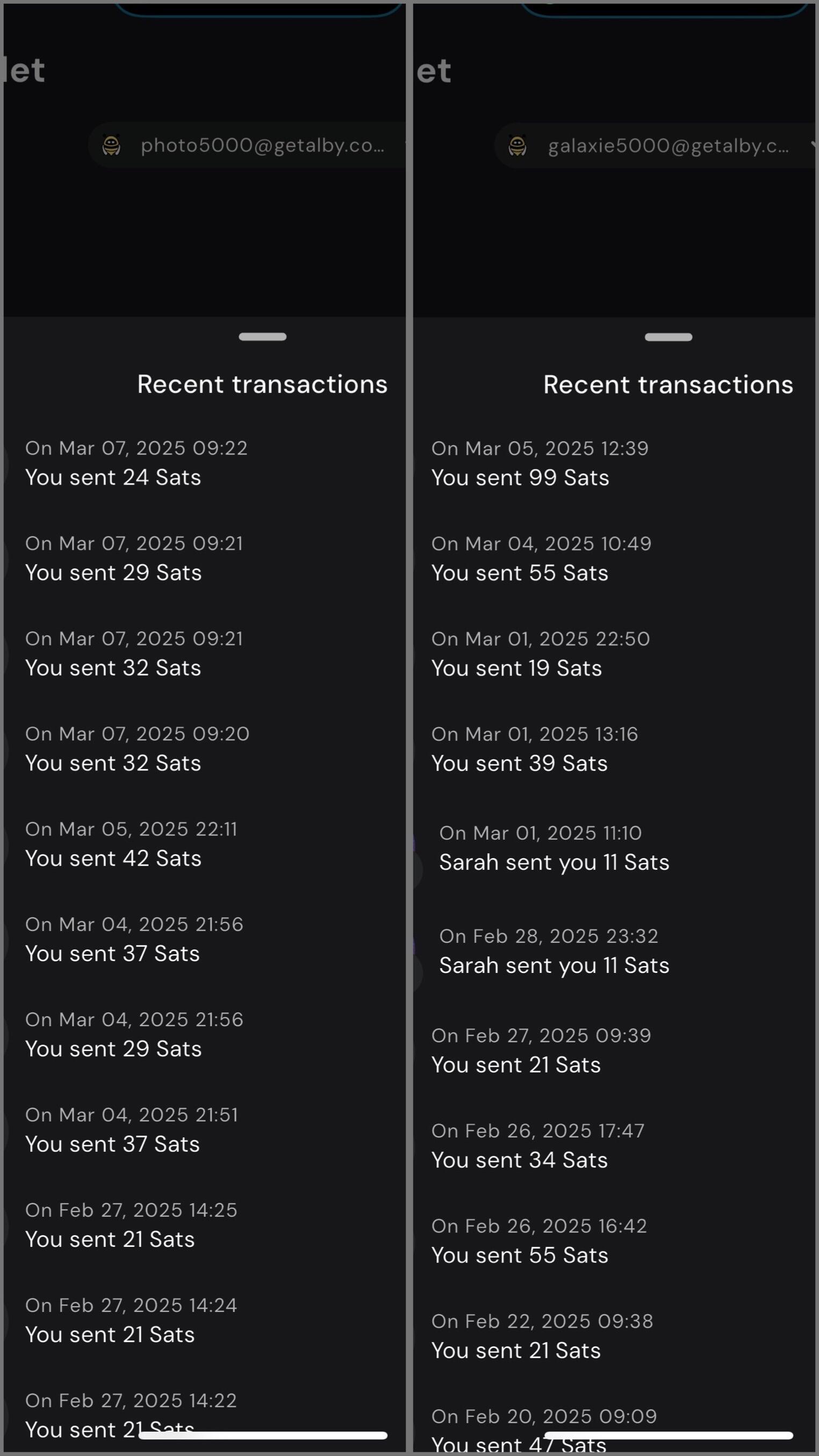
Using my self-hosted Alby Hub I can manage Lightning channels and wallets while sending and receiving zaps for multiple profiles with YakiHonne.
YakiHonne #AlbyHub #Lightning #Bitcoin #Nostr
-
 @ 6e64b83c:94102ee8
2025-04-20 21:09:09
@ 6e64b83c:94102ee8
2025-04-20 21:09:09Prerequisites
- Install Citrine on your Android device:
- Visit https://github.com/greenart7c3/Citrine/releases
- Download the latest release using:
- zap.store
- Obtainium
- F-Droid
- Or download the APK directly
-
Note: You may need to enable "Install from Unknown Sources" in your Android settings
-
Domain Requirements:
- If you don't have a domain, purchase one
- If you have a domain not on Cloudflare, consider transferring it to Cloudflare for free SSL certificates and cloudflared support
Setting Up Citrine
- Open the Citrine app
- Start the server
- You'll see it running on
ws://127.0.0.1:4869(local network only) - Go to settings and paste your npub into "Accept events signed by" inbox and press + button. This would prevent others from publishing events into your personal relay.
Installing Required Tools
- Install Termux from Google Play Store
- Open Termux and run:
bash pkg update && pkg install wget wget https://github.com/cloudflare/cloudflared/releases/latest/download/cloudflared-linux-arm64.deb dpkg -i cloudflared-linux-arm64.debCloudflare Authentication
- Run the authentication command:
bash cloudflared tunnel login - Follow the instructions:
- Copy the provided URL to your browser
- Log in to your Cloudflare account
- If the URL expires, copy it again after logging in
Creating the Tunnel
- Create a new tunnel:
bash cloudflared tunnel create <TUNNEL_NAME> - Choose any name you prefer for your tunnel
-
Copy the tunnel ID after creating the tunnel
-
Create and configure the tunnel config:
bash touch ~/.cloudflared/config.yml nano ~/.cloudflared/config.yml -
Add this configuration (replace placeholders): ```yaml tunnel:
credentials-file: /data/data/com.termux/files/home/.cloudflared/ .json ingress: - hostname: nostr.yourdomain.com service: ws://localhost:4869
- service: http_status:404 ```
- Note: In nano editor:
CTRL+Oand Enter to saveCTRL+Xto exit
-
Note: Check the credentials file path in the logs
-
Validate your configuration:
bash cloudflared tunnel validate -
Start the tunnel:
bash cloudflared tunnel run my-relay
Preventing Android from Killing the Tunnel
Run these commands to maintain tunnel stability:
bash date && apt install termux-tools && termux-setup-storage && termux-wake-lock echo "nameserver 1.1.1.1" > $PREFIX/etc/resolv.confTip: You can open multiple Termux sessions by swiping from the left edge of the screen while keeping your tunnel process running.
Updating Your Outbox Model Relays
Once your relay is running and accessible via your domain, you'll want to update your relay list in the Nostr network. This ensures other clients know about your relay and can connect to it.
- Create a kind 10002 event with your relay list:
- Include your new relay with write permissions
- Include other relays you want to read from
- Example format:
json { "kind": 10002, "tags": [ ["r", "wss://your-relay-domain.com", "write"], ["r", "wss://eden.nostr.land/", "read"], ["r", "wss://nos.lol/", "read"], ["r", "wss://nostr.bitcoiner.social/", "read"], ["r", "wss://nostr.mom/", "read"], ["r", "wss://relay.primal.net/", "read"], ["r", "wss://nostr.wine/", "read"], ["r", "wss://relay.damus.io/", "read"], ["r", "wss://relay.nostr.band/", "read"], ["r", "wss://relay.snort.social/", "read"] ], "content": "" }
Save it to a file called
event.jsonNote: Add or remove any relays you want. Check your existing 10002 relays from the following URL: https://nostr.band/?q=by%3Anpub1dejts0qlva8mqzjlrxqkc2tmvs2t7elszky5upxaf3jha9qs9m5q605uc4+++kind%3A10002, Change the
npub1xxxpart with your own npub, and VIEW JSON from menu to see the raw event.- Sign and publish the event:
- Use a Nostr client that supports kind 10002 events
-
Or use the
nak(https://github.com/fiatjaf/nak) command-line tool:bash cat event.json | nak event --sec <your-private-key> wss://relay1.com wss://relay2.com -
Verify the event was published:
- Check if your relay list is visible on other relays
-
Use the
naktool to fetch your kind 10002 events:bash nak req -k 10002 -a <your-pubkey> wss://relay1.com wss://relay2.com -
Testing your relay:
- Try connecting to your relay using different Nostr clients
- Verify you can both read from and write to your relay
- Check if events are being properly stored and retrieved
- Tip: Use multiple clients to test different aspects of your relay
Note: If anyone in the community has a more efficient method of doing things like updating outbox relays, please share your insights in the comments. Your expertise would be greatly appreciated!
-
 @ c3f12a9a:06c21301
2025-04-19 10:09:45
@ c3f12a9a:06c21301
2025-04-19 10:09:45Satoshi’s Time-Traveling for Knowledge #4: Liberland 2024 – Freedom Under Siege
What is Liberland?
While digging through old decentralized forums archived on the Interchain, Satoshi came across a curious name: Liberland.
“A sovereign libertarian micronation on the Danube? Founded in 2015 via Terra nullius? Built on the principles of freedom, voluntaryism, and Bitcoin? And I’ve never heard of it?”
Intrigued, Satoshi began to research. The story was almost too good to be true. A 7-square-kilometer patch of unclaimed land between Croatia and Serbia, turned into a symbol of decentralized governance and individual liberty.
No taxes unless voluntary. Bitcoin as the national currency. A digital nation-state with thousands of registered e-citizens, and even its own constitution. And yet—no recognition, no borders, and no peace.His curiosity turned into determination. He calibrated the temporal coordinates on his chrono-node to the Danube River in 2024, a year rumored to be turbulent for the Free Republic of Liberland.
When he arrived, reality struck harder than the legend.
Freedom Under Siege
The nation was under siege.
The scent of burnt wood and trampled earth lingered in the air as Satoshi stepped into what remained of the Liberland settlement. Broken structures, crushed solar panels, and a few scattered personal belongings were all that testified to the once-vibrant hub of liberty pioneers.
He found a group of residents—mud-streaked, exhausted, but defiant—gathered around the remnants of a communal kitchen. One of them, wearing a weathered Liberland t-shirt and a crypto-wallet hardware device on a chain around his neck, greeted him:
"You're not with them, are you?"
Satoshi shook his head.
"Just... passing through. What happened here?"
The man’s voice trembled between rage and sorrow:
"On the International Day of Peace, no less. Croatian police raided us. Bulldozers came with them. Took everything—generators, comms gear, even our medical tents. Claimed it was 'illegal occupation of Croatian forestry land.' But no court, no hearing. Just force."
Satoshi listened, taking mental snapshots of their faces, their words, their pain. He thought about the dream—of a place built voluntarily, where people governed themselves, free from coercion.
But that dream was burning at the edges, like the collapsed tents scattered behind them.
Reflections Under the Stars
As night fell over the Danube, Satoshi sat alone, watching the stars reflect on the black water. Thoughts spiraled:
"Decentralization... is beautiful. But without protection, it's fragile."
He realized that so long as central authorities hold monopoly on violence and taxation, every independent effort to decentralize the world—from Bitcoin to Liberland—is at risk of being suppressed, ignored, or destroyed. Not because it’s wrong, but because it's inconvenient to power.
"Unless a major state like the USA decentralizes itself from within," he thought, "true decentralization will remain a resistance—never the standard."
He activated his chrono-node once more. Not in defeat, but with purpose.
The next destination? Unknown. But the mission was clearer than ever.
originally posted at https://stacker.news/items/947954
-
 @ b9f4c34d:7d1a0e31
2025-04-02 15:00:20
@ b9f4c34d:7d1a0e31
2025-04-02 15:00:20Test Video Document
-
 @ d34e832d:383f78d0
2025-04-22 18:15:42
@ d34e832d:383f78d0
2025-04-22 18:15:42Proof Of Concept
In a world where decentralization often hinges on the strength of its weakest node, the idea of federation—applied not to content moderation or identity, but strictly to communication protocols—opens up intriguing possibilities. In this model, Nostr relays do not operate in total isolation, nor do they function in a single cohesive mesh. Instead, they form selective, encrypted alliances, communicating through secure tunnels while preserving autonomy.
💡 The Core Idea
Relays remain sovereign, but may establish peer-to-peer encrypted channels with other trusted relays using Elliptic Curve Diffie-Hellman (ECDH) to generate shared secrets. These secrets are then used to encrypt communication tunnels—facilitating a federated communication layer.
Each relay is free to choose: - Whom it speaks to - How often - What types of events are relayed through the tunnel
But never must it rely on a central coordinator.
🔁 Schnorr for Authentication
While ECDH can create the secure tunnel, Schnorr signatures (already a part of Nostr’s pubkey-based design) can be used to authenticate the origin of the data inside. This keeps the integrity of messages intact even when traveling over shared or hostile networks.
Use case: - Relay A and Relay B establish an ECDH-based shared key. - All communication is tunnel-encrypted with this shared key. - Inside the tunnel, every message still carries a Schnorr signature, proving its source.
This separation of transport-level encryption from message-level authenticity provides an elegant layering of security.
🌐 Practical Benefits
- Obfuscation: Encrypted tunnels reduce visibility into relay-to-relay traffic patterns.
- Privacy: Federation over encrypted channels shields metadata and protects against surveillance.
- Resilience: Relays can route around censorship by tunneling through less obvious peers.
- Synergy: Specific relay clusters can form ephemeral or long-term alliances—say, art relays or academic relays—without disclosing their full graph to the world.
🧩 Optional Enhancements
- Noise Protocol Framework to standardize encrypted relay tunnels.
- Tor Hidden Services or I2P for transport obfuscation.
- Relay Reputation Systems to gauge trust before federation.
- Dynamic Federation Negotiation: using NIP-like proposals over encrypted handshakes to initiate or terminate communication agreements.
🌱 Case In Point
This is not about governing content, users, or identities—this is about strengthening how relays talk. By embracing federated communication via ECDH and Schnorr-secured tunnels, Nostr relays could evolve into a resilient underground of trust-minimized, pseudonymous routers that defy surveillance while amplifying decentralization.
federated communication via ECDH and Schnorr-authenticated encrypted tunnels between Nostr relays:
markdown NIP-xyz: Federated Encrypted Relay Communication Status: Draft Type: Relay Created: 2025-04-22
Summary
This NIP proposes a method for encrypted, authenticated communication between Nostr relays using ECDH-based tunnels for transport encryption and Schnorr signatures for payload integrity. This federation model allows relays to communicate securely while maintaining full autonomy, enhancing privacy, censorship resistance, and interoperability.
Motivation
Nostr’s decentralized architecture relies heavily on relays, which currently operate in isolated or broadcast modes. There is no standard for secure, peer-to-peer communication between relays themselves, outside of client interactions.
Introducing encrypted tunnels between relays offers:
- Privacy: Reduces metadata leakage across public or adversarial networks.
- Resilience: Allows relays to forward events and metadata through trusted peers when direct access is blocked or filtered.
- Autonomy: Federation is opt-in and purely communicational—no centralized authority or directory is involved.
- Extensibility: Enables experimental protocols or content-specific subnets without altering the global Nostr model.
Specification
1. Key Exchange via ECDH
Each relay maintains: - A persistent relay keypair:
relay_pubkey,relay_privkey- Optionally: rotating session keys for forward secrecyWhen two relays (A and B) wish to establish communication: - They exchange their public keys (
relay_pubkey_Aandrelay_pubkey_B) - Both calculate a shared secret using ECDH oversecp256k1:plaintext shared_secret = SHA256(ECDH(relay_privkey_A, relay_pubkey_B))This
shared_secretis used to derive an encryption key for an authenticated symmetric cipher, such as AES-GCM or ChaCha20-Poly1305.
2. Encrypted Tunnel Establishment
Once the shared secret is derived: - All messages between relays are sent through an encrypted tunnel - Transport can be TCP, WebSocket, or HTTP/3 over QUIC, optionally via Tor or I2P
A RelayHello message is exchanged encrypted, optionally containing:
json { "type": "relay_hello", "relay_name": "nostr.relay.example", "features": ["forwarding", "dedup", "metadata"], "timestamp": 1684000000, "sig": "<Schnorr-signed payload>" }The
sigis a Schnorr signature from therelay_pubkey, verifying the message content.
3. Event Forwarding
Relays may forward selected event types across tunnels, such as: - Kind 1 (Text Note) - Kind 3 (Contacts) - Kind 5 (Deletion Notices) - Custom kinds (with mutual agreement)
All forwarded events MUST retain original client-level signatures. Relay-to-relay metadata (like timestamps, relay hints, or scores) may be added in a separate metadata envelope.
4. Access Control and Policies
Each relay maintains a federation list, including: - Public key of the peer relay - Features enabled - Rate limits and quotas - Last active session or rotation timestamp
Relays MAY: - Deny tunnel requests - Rotate keys periodically - Restrict communication to a whitelist - Use Proof-of-Work or tokens for DoS protection
5. Optional Features
- Forward Secrecy: ephemeral key pairs with HKDF for short sessions
- Relay Reputation: signed relay trust scores (future NIP)
- Message Compression: gzip or zstd on tunnel payloads
- Encrypted Gossip: tunnel-specific metadata routing
Compatibility
This NIP is backward-compatible. Relays that do not implement it will simply not participate in tunnel-based communication.
No changes are required from Nostr clients.
Reference Implementation (Proposed)
nostr-tunnel-relay: Rust-based relay that supports federated encrypted tunnelsnostr-relay-link: CLI tool to establish and monitor tunnels- Example configs for federation policies in JSON or TOML
Rationale
- ECDH ensures only the two relays involved can decrypt tunnel data
- Schnorr signatures authenticate content without duplicating identity schemes
- Federation is scoped only to communication, preserving Nostr’s core simplicity
Security Considerations
- Relay pubkeys must be carefully verified to prevent MITM
- Session expiration and key rotation should be configurable
- Replay protection and nonce management are required for AEAD ciphers
- Metadata leakage minimized by default obfuscation or Tor-based transport
NIP.eshgham
-
 @ c4b5369a:b812dbd6
2025-04-15 07:26:16
@ c4b5369a:b812dbd6
2025-04-15 07:26:16Offline transactions with Cashu
Over the past few weeks, I've been busy implementing offline capabilities into nutstash. I think this is one of the key value propositions of ecash, beinga a bearer instrument that can be used without internet access.
 It does however come with limitations, which can lead to a bit of confusion. I hope this article will clear some of these questions up for you!
It does however come with limitations, which can lead to a bit of confusion. I hope this article will clear some of these questions up for you!What is ecash/Cashu?
Ecash is the first cryptocurrency ever invented. It was created by David Chaum in 1983. It uses a blind signature scheme, which allows users to prove ownership of a token without revealing a link to its origin. These tokens are what we call ecash. They are bearer instruments, meaning that anyone who possesses a copy of them, is considered the owner.
Cashu is an implementation of ecash, built to tightly interact with Bitcoin, more specifically the Bitcoin lightning network. In the Cashu ecosystem,
Mintsare the gateway to the lightning network. They provide the infrastructure to access the lightning network, pay invoices and receive payments. Instead of relying on a traditional ledger scheme like other custodians do, the mint issues ecash tokens, to represent the value held by the users.How do normal Cashu transactions work?
A Cashu transaction happens when the sender gives a copy of his ecash token to the receiver. This can happen by any means imaginable. You could send the token through email, messenger, or even by pidgeon. One of the common ways to transfer ecash is via QR code.
The transaction is however not finalized just yet! In order to make sure the sender cannot double-spend their copy of the token, the receiver must do what we call a
swap. A swap is essentially exchanging an ecash token for a new one at the mint, invalidating the old token in the process. This ensures that the sender can no longer use the same token to spend elsewhere, and the value has been transferred to the receiver.
What about offline transactions?
Sending offline
Sending offline is very simple. The ecash tokens are stored on your device. Thus, no internet connection is required to access them. You can litteraly just take them, and give them to someone. The most convenient way is usually through a local transmission protocol, like NFC, QR code, Bluetooth, etc.
The one thing to consider when sending offline is that ecash tokens come in form of "coins" or "notes". The technical term we use in Cashu is
Proof. It "proofs" to the mint that you own a certain amount of value. Since these proofs have a fixed value attached to them, much like UTXOs in Bitcoin do, you would need proofs with a value that matches what you want to send. You can mix and match multiple proofs together to create a token that matches the amount you want to send. But, if you don't have proofs that match the amount, you would need to go online and swap for the needed proofs at the mint.Another limitation is, that you cannot create custom proofs offline. For example, if you would want to lock the ecash to a certain pubkey, or add a timelock to the proof, you would need to go online and create a new custom proof at the mint.
Receiving offline
You might think: well, if I trust the sender, I don't need to be swapping the token right away!
You're absolutely correct. If you trust the sender, you can simply accept their ecash token without needing to swap it immediately.
This is already really useful, since it gives you a way to receive a payment from a friend or close aquaintance without having to worry about connectivity. It's almost just like physical cash!
It does however not work if the sender is untrusted. We have to use a different scheme to be able to receive payments from someone we don't trust.
Receiving offline from an untrusted sender
To be able to receive payments from an untrusted sender, we need the sender to create a custom proof for us. As we've seen before, this requires the sender to go online.
The sender needs to create a token that has the following properties, so that the receciver can verify it offline:
- It must be locked to ONLY the receiver's public key
- It must include an
offline signature proof(DLEQ proof) - If it contains a timelock & refund clause, it must be set to a time in the future that is acceptable for the receiver
- It cannot contain duplicate proofs (double-spend)
- It cannot contain proofs that the receiver has already received before (double-spend)

If all of these conditions are met, then the receiver can verify the proof offline and accept the payment. This allows us to receive payments from anyone, even if we don't trust them.
At first glance, this scheme seems kinda useless. It requires the sender to go online, which defeats the purpose of having an offline payment system.
I beleive there are a couple of ways this scheme might be useful nonetheless:
-
Offline vending machines: Imagine you have an offline vending machine that accepts payments from anyone. The vending machine could use this scheme to verify payments without needing to go online itself. We can assume that the sender is able to go online and create a valid token, but the receiver doesn't need to be online to verify it.
-
Offline marketplaces: Imagine you have an offline marketplace where buyers and sellers can trade goods and services. Before going to the marketplace the sender already knows where he will be spending the money. The sender could create a valid token before going to the marketplace, using the merchants public key as a lock, and adding a refund clause to redeem any unspent ecash after it expires. In this case, neither the sender nor the receiver needs to go online to complete the transaction.
How to use this
Pretty much all cashu wallets allow you to send tokens offline. This is because all that the wallet needs to do is to look if it can create the desired amount from the proofs stored locally. If yes, it will automatically create the token offline.
Receiving offline tokens is currently only supported by nutstash (experimental).
To create an offline receivable token, the sender needs to lock it to the receiver's public key. Currently there is no refund clause! So be careful that you don't get accidentally locked out of your funds!

The receiver can then inspect the token and decide if it is safe to accept without a swap. If all checks are green, they can accept the token offline without trusting the sender.

The receiver will see the unswapped tokens on the wallet homescreen. They will need to manually swap them later when they are online again.
 Later when the receiver is online again, they can swap the token for a fresh one.
Later when the receiver is online again, they can swap the token for a fresh one.
Summary
We learned that offline transactions are possible with ecash, but there are some limitations. It either requires trusting the sender, or relying on either the sender or receiver to be online to verify the tokens, or create tokens that can be verified offline by the receiver.
I hope this short article was helpful in understanding how ecash works and its potential for offline transactions.
Cheers,
Gandlaf
-
 @ c631e267:c2b78d3e
2025-04-20 19:54:32
@ c631e267:c2b78d3e
2025-04-20 19:54:32Es ist völlig unbestritten, dass der Angriff der russischen Armee auf die Ukraine im Februar 2022 strikt zu verurteilen ist. Ebenso unbestritten ist Russland unter Wladimir Putin keine brillante Demokratie. Aus diesen Tatsachen lässt sich jedoch nicht das finstere Bild des russischen Präsidenten – und erst recht nicht des Landes – begründen, das uns durchweg vorgesetzt wird und den Kern des aktuellen europäischen Bedrohungs-Szenarios darstellt. Da müssen wir schon etwas genauer hinschauen.
Der vorliegende Artikel versucht derweil nicht, den Einsatz von Gewalt oder die Verletzung von Menschenrechten zu rechtfertigen oder zu entschuldigen – ganz im Gegenteil. Dass jedoch der Verdacht des «Putinverstehers» sofort latent im Raume steht, verdeutlicht, was beim Thema «Russland» passiert: Meinungsmache und Manipulation.
Angesichts der mentalen Mobilmachung seitens Politik und Medien sowie des Bestrebens, einen bevorstehenden Krieg mit Russland geradezu herbeizureden, ist es notwendig, dieser fatalen Entwicklung entgegenzutreten. Wenn wir uns nur ein wenig von der herrschenden Schwarz-Weiß-Malerei freimachen, tauchen automatisch Fragen auf, die Risse im offiziellen Narrativ enthüllen. Grund genug, nachzuhaken.
Wer sich schon länger auch abseits der Staats- und sogenannten Leitmedien informiert, der wird in diesem Artikel vermutlich nicht viel Neues erfahren. Andere könnten hier ein paar unbekannte oder vergessene Aspekte entdecken. Möglicherweise klärt sich in diesem Kontext die Wahrnehmung der aktuellen (unserer eigenen!) Situation ein wenig.
Manipulation erkennen
Corona-«Pandemie», menschengemachter Klimawandel oder auch Ukraine-Krieg: Jede Menge Krisen, und für alle gibt es ein offizielles Narrativ, dessen Hinterfragung unerwünscht ist. Nun ist aber ein Narrativ einfach eine Erzählung, eine Geschichte (Latein: «narratio») und kein Tatsachenbericht. Und so wie ein Märchen soll auch das Narrativ eine Botschaft vermitteln.
Über die Methoden der Manipulation ist viel geschrieben worden, sowohl in Bezug auf das Individuum als auch auf die Massen. Sehr wertvolle Tipps dazu, wie man Manipulationen durchschauen kann, gibt ein Büchlein [1] von Albrecht Müller, dem Herausgeber der NachDenkSeiten.
Die Sprache selber eignet sich perfekt für die Manipulation. Beispielsweise kann die Wortwahl Bewertungen mitschwingen lassen, regelmäßiges Wiederholen (gerne auch von verschiedenen Seiten) lässt Dinge irgendwann «wahr» erscheinen, Übertreibungen fallen auf und hinterlassen wenigstens eine Spur im Gedächtnis, genauso wie Andeutungen. Belege spielen dabei keine Rolle.
Es gibt auffällig viele Sprachregelungen, die offenbar irgendwo getroffen und irgendwie koordiniert werden. Oder alle Redenschreiber und alle Medien kopieren sich neuerdings permanent gegenseitig. Welchen Zweck hat es wohl, wenn der Krieg in der Ukraine durchgängig und quasi wörtlich als «russischer Angriffskrieg auf die Ukraine» bezeichnet wird? Obwohl das in der Sache richtig ist, deutet die Art der Verwendung auf gezielte Beeinflussung hin und soll vor allem das Feindbild zementieren.
Sprachregelungen dienen oft der Absicherung einer einseitigen Darstellung. Das Gleiche gilt für das Verkürzen von Informationen bis hin zum hartnäckigen Verschweigen ganzer Themenbereiche. Auch hierfür gibt es rund um den Ukraine-Konflikt viele gute Beispiele.
Das gewünschte Ergebnis solcher Methoden ist eine Schwarz-Weiß-Malerei, bei der einer eindeutig als «der Böse» markiert ist und die anderen automatisch «die Guten» sind. Das ist praktisch und demonstriert gleichzeitig ein weiteres Manipulationswerkzeug: die Verwendung von Doppelstandards. Wenn man es schafft, bei wichtigen Themen regelmäßig mit zweierlei Maß zu messen, ohne dass das Publikum protestiert, dann hat man freie Bahn.
Experten zu bemühen, um bestimmte Sachverhalte zu erläutern, ist sicher sinnvoll, kann aber ebenso missbraucht werden, schon allein durch die Auswahl der jeweiligen Spezialisten. Seit «Corona» werden viele erfahrene und ehemals hoch angesehene Fachleute wegen der «falschen Meinung» diffamiert und gecancelt. [2] Das ist nicht nur ein brutaler Umgang mit Menschen, sondern auch eine extreme Form, die öffentliche Meinung zu steuern.
Wann immer wir also erkennen (weil wir aufmerksam waren), dass wir bei einem bestimmten Thema manipuliert werden, dann sind zwei logische und notwendige Fragen: Warum? Und was ist denn richtig? In unserem Russland-Kontext haben die Antworten darauf viel mit Geopolitik und Geschichte zu tun.
Ist Russland aggressiv und expansiv?
Angeblich plant Russland, europäische NATO-Staaten anzugreifen, nach dem Motto: «Zuerst die Ukraine, dann den Rest». In Deutschland weiß man dafür sogar das Datum: «Wir müssen bis 2029 kriegstüchtig sein», versichert Verteidigungsminister Pistorius.
Historisch gesehen ist es allerdings eher umgekehrt: Russland, bzw. die Sowjetunion, ist bereits dreimal von Westeuropa aus militärisch angegriffen worden. Die Feldzüge Napoleons, des deutschen Kaiserreichs und Nazi-Deutschlands haben Millionen Menschen das Leben gekostet. Bei dem ausdrücklichen Vernichtungskrieg ab 1941 kam es außerdem zu Brutalitäten wie der zweieinhalbjährigen Belagerung Leningrads (heute St. Petersburg) durch Hitlers Wehrmacht. Deren Ziel, die Bevölkerung auszuhungern, wurde erreicht: über eine Million tote Zivilisten.
Trotz dieser Erfahrungen stimmte Michail Gorbatschow 1990 der deutschen Wiedervereinigung zu und die Sowjetunion zog ihre Truppen aus Osteuropa zurück (vgl. Abb. 1). Der Warschauer Pakt wurde aufgelöst, der Kalte Krieg formell beendet. Die Sowjets erhielten damals von führenden westlichen Politikern die Zusicherung, dass sich die NATO «keinen Zentimeter ostwärts» ausdehnen würde, das ist dokumentiert. [3]
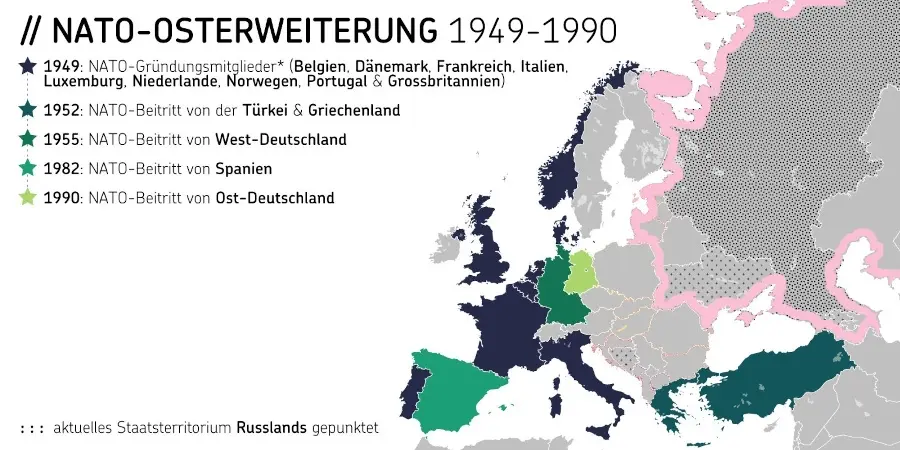
Expandiert ist die NATO trotzdem, und zwar bis an Russlands Grenzen (vgl. Abb. 2). Laut dem Politikberater Jeffrey Sachs handelt es sich dabei um ein langfristiges US-Projekt, das von Anfang an die Ukraine und Georgien mit einschloss. Offiziell wurde der Beitritt beiden Staaten 2008 angeboten. In jedem Fall könnte die massive Ost-Erweiterung seit 1999 aus russischer Sicht nicht nur als Vertrauensbruch, sondern durchaus auch als aggressiv betrachtet werden.
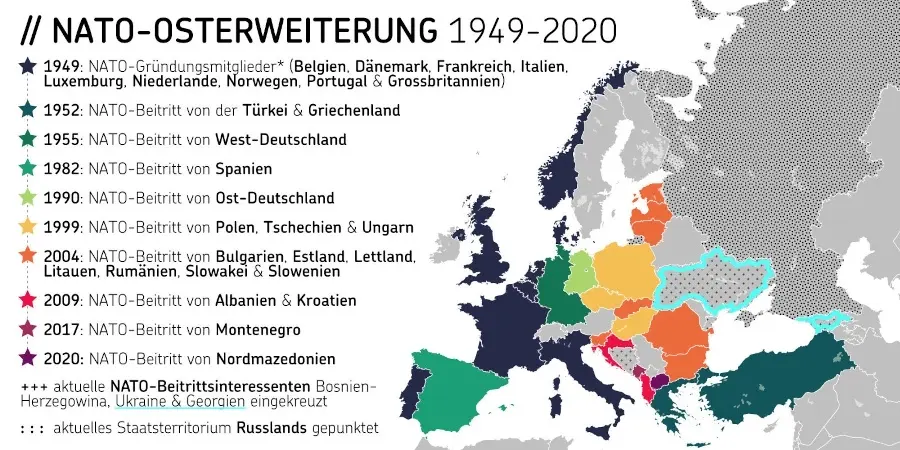
Russland hat den europäischen Staaten mehrfach die Hand ausgestreckt [4] für ein friedliches Zusammenleben und den «Aufbau des europäischen Hauses». Präsident Putin sei «in seiner ersten Amtszeit eine Chance für Europa» gewesen, urteilt die Journalistin und langjährige Russland-Korrespondentin der ARD, Gabriele Krone-Schmalz. Er habe damals viele positive Signale Richtung Westen gesendet.
Die Europäer jedoch waren scheinbar an einer Partnerschaft mit dem kontinentalen Nachbarn weniger interessiert als an der mit dem transatlantischen Hegemon. Sie verkennen bis heute, dass eine gedeihliche Zusammenarbeit in Eurasien eine Gefahr für die USA und deren bekundetes Bestreben ist, die «einzige Weltmacht» zu sein – «Full Spectrum Dominance» [5] nannte das Pentagon das. Statt einem neuen Kalten Krieg entgegenzuarbeiten, ließen sich europäische Staaten selber in völkerrechtswidrige «US-dominierte Angriffskriege» [6] verwickeln, wie in Serbien, Afghanistan, dem Irak, Libyen oder Syrien. Diese werden aber selten so benannt.
Speziell den Deutschen stünde außer einer Portion Realismus auch etwas mehr Dankbarkeit gut zu Gesicht. Das Geschichtsbewusstsein der Mehrheit scheint doch recht selektiv und das Selbstbewusstsein einiger etwas desorientiert zu sein. Bekanntermaßen waren es die Soldaten der sowjetischen Roten Armee, die unter hohen Opfern 1945 Deutschland «vom Faschismus befreit» haben. Bei den Gedenkfeiern zu 80 Jahren Kriegsende will jedoch das Auswärtige Amt – noch unter der Diplomatie-Expertin Baerbock, die sich schon länger offiziell im Krieg mit Russland wähnt, – nun keine Russen sehen: Sie sollen notfalls rausgeschmissen werden.
«Die Grundsatzfrage lautet: Geht es Russland um einen angemessenen Platz in einer globalen Sicherheitsarchitektur, oder ist Moskau schon seit langem auf einem imperialistischen Trip, der befürchten lassen muss, dass die Russen in fünf Jahren in Berlin stehen?»
So bringt Gabriele Krone-Schmalz [7] die eigentliche Frage auf den Punkt, die zur Einschätzung der Situation letztlich auch jeder für sich beantworten muss.
Was ist los in der Ukraine?
In der internationalen Politik geht es nie um Demokratie oder Menschenrechte, sondern immer um Interessen von Staaten. Diese These stammt von Egon Bahr, einem der Architekten der deutschen Ostpolitik des «Wandels durch Annäherung» aus den 1960er und 70er Jahren. Sie trifft auch auf den Ukraine-Konflikt zu, den handfeste geostrategische und wirtschaftliche Interessen beherrschen, obwohl dort angeblich «unsere Demokratie» verteidigt wird.
Es ist ein wesentliches Element des Ukraine-Narrativs und Teil der Manipulation, die Vorgeschichte des Krieges wegzulassen – mindestens die vor der russischen «Annexion» der Halbinsel Krim im März 2014, aber oft sogar komplett diejenige vor der Invasion Ende Februar 2022. Das Thema ist komplex, aber einige Aspekte, die für eine Beurteilung nicht unwichtig sind, will ich wenigstens kurz skizzieren. [8]
Das Gebiet der heutigen Ukraine und Russlands – die übrigens in der «Kiewer Rus» gemeinsame Wurzeln haben – hat der britische Geostratege Halford Mackinder bereits 1904 als eurasisches «Heartland» bezeichnet, dessen Kontrolle er eine große Bedeutung für die imperiale Strategie Großbritanniens zumaß. Für den ehemaligen Sicherheits- und außenpolitischen Berater mehrerer US-amerikanischer Präsidenten und Mitgründer der Trilateralen Kommission, Zbigniew Brzezinski, war die Ukraine nach der Auflösung der Sowjetunion ein wichtiger Spielstein auf dem «eurasischen Schachbrett», wegen seiner Nähe zu Russland, seiner Bodenschätze und seines Zugangs zum Schwarzen Meer.
Die Ukraine ist seit langem ein gespaltenes Land. Historisch zerrissen als Spielball externer Interessen und geprägt von ethnischen, kulturellen, religiösen und geografischen Unterschieden existiert bis heute, grob gesagt, eine Ost-West-Spaltung, welche die Suche nach einer nationalen Identität stark erschwert.
Insbesondere im Zuge der beiden Weltkriege sowie der Russischen Revolution entstanden tiefe Risse in der Bevölkerung. Ukrainer kämpften gegen Ukrainer, zum Beispiel die einen auf der Seite von Hitlers faschistischer Nazi-Armee und die anderen auf der von Stalins kommunistischer Roter Armee. Die Verbrechen auf beiden Seiten sind nicht vergessen. Dass nach der Unabhängigkeit 1991 versucht wurde, Figuren wie den radikalen Nationalisten Symon Petljura oder den Faschisten und Nazi-Kollaborateur Stepan Bandera als «Nationalhelden» zu installieren, verbessert die Sache nicht.
Während die USA und EU-Staaten zunehmend «ausländische Einmischung» (speziell russische) in «ihre Demokratien» wittern, betreiben sie genau dies seit Jahrzehnten in vielen Ländern der Welt. Die seit den 2000er Jahren bekannten «Farbrevolutionen» in Osteuropa werden oft als Methode des Regierungsumsturzes durch von außen gesteuerte «demokratische» Volksaufstände beschrieben. Diese Strategie geht auf Analysen zum «Schwarmverhalten» [9] seit den 1960er Jahren zurück (Studentenproteste), wo es um die potenzielle Wirksamkeit einer «rebellischen Hysterie» von Jugendlichen bei postmodernen Staatsstreichen geht. Heute nennt sich dieses gezielte Kanalisieren der Massen zur Beseitigung unkooperativer Regierungen «Soft-Power».
In der Ukraine gab es mit der «Orangen Revolution» 2004 und dem «Euromaidan» 2014 gleich zwei solcher «Aufstände». Der erste erzwang wegen angeblicher Unregelmäßigkeiten eine Wiederholung der Wahlen, was mit Wiktor Juschtschenko als neuem Präsidenten endete. Dieser war ehemaliger Direktor der Nationalbank und Befürworter einer Annäherung an EU und NATO. Seine Frau, die First Lady, ist US-amerikanische «Philanthropin» und war Beamtin im Weißen Haus in der Reagan- und der Bush-Administration.
Im Gegensatz zu diesem ersten Event endete der sogenannte Euromaidan unfriedlich und blutig. Die mehrwöchigen Proteste gegen Präsident Wiktor Janukowitsch, in Teilen wegen des nicht unterzeichneten Assoziierungsabkommens mit der EU, wurden zunehmend gewalttätiger und von Nationalisten und Faschisten des «Rechten Sektors» dominiert. Sie mündeten Ende Februar 2014 auf dem Kiewer Unabhängigkeitsplatz (Maidan) in einem Massaker durch Scharfschützen. Dass deren Herkunft und die genauen Umstände nicht geklärt wurden, störte die Medien nur wenig. [10]
Janukowitsch musste fliehen, er trat nicht zurück. Vielmehr handelte es sich um einen gewaltsamen, allem Anschein nach vom Westen inszenierten Putsch. Laut Jeffrey Sachs war das kein Geheimnis, außer vielleicht für die Bürger. Die USA unterstützten die Post-Maidan-Regierung nicht nur, sie beeinflussten auch ihre Bildung. Das geht unter anderem aus dem berühmten «Fuck the EU»-Telefonat der US-Chefdiplomatin für die Ukraine, Victoria Nuland, mit Botschafter Geoffrey Pyatt hervor.
Dieser Bruch der demokratischen Verfassung war letztlich der Auslöser für die anschließenden Krisen auf der Krim und im Donbass (Ostukraine). Angesichts der ukrainischen Geschichte mussten die nationalistischen Tendenzen und die Beteiligung der rechten Gruppen an dem Umsturz bei der russigsprachigen Bevölkerung im Osten ungute Gefühle auslösen. Es gab Kritik an der Übergangsregierung, Befürworter einer Abspaltung und auch für einen Anschluss an Russland.
Ebenso konnte Wladimir Putin in dieser Situation durchaus Bedenken wegen des Status der russischen Militärbasis für seine Schwarzmeerflotte in Sewastopol auf der Krim haben, für die es einen langfristigen Pachtvertrag mit der Ukraine gab. Was im März 2014 auf der Krim stattfand, sei keine Annexion, sondern eine Abspaltung (Sezession) nach einem Referendum gewesen, also keine gewaltsame Aneignung, urteilte der Rechtswissenschaftler Reinhard Merkel in der FAZ sehr detailliert begründet. Übrigens hatte die Krim bereits zu Zeiten der Sowjetunion den Status einer autonomen Republik innerhalb der Ukrainischen SSR.
Anfang April 2014 wurden in der Ostukraine die «Volksrepubliken» Donezk und Lugansk ausgerufen. Die Kiewer Übergangsregierung ging unter der Bezeichnung «Anti-Terror-Operation» (ATO) militärisch gegen diesen, auch von Russland instrumentalisierten Widerstand vor. Zufällig war kurz zuvor CIA-Chef John Brennan in Kiew. Die Maßnahmen gingen unter dem seit Mai neuen ukrainischen Präsidenten, dem Milliardär Petro Poroschenko, weiter. Auch Wolodymyr Selenskyj beendete den Bürgerkrieg nicht, als er 2019 vom Präsidenten-Schauspieler, der Oligarchen entmachtet, zum Präsidenten wurde. Er fuhr fort, die eigene Bevölkerung zu bombardieren.
Mit dem Einmarsch russischer Truppen in die Ostukraine am 24. Februar 2022 begann die zweite Phase des Krieges. Die Wochen und Monate davor waren intensiv. Im November hatte die Ukraine mit den USA ein Abkommen über eine «strategische Partnerschaft» unterzeichnet. Darin sagten die Amerikaner ihre Unterstützung der EU- und NATO-Perspektive der Ukraine sowie quasi für die Rückeroberung der Krim zu. Dagegen ließ Putin der NATO und den USA im Dezember 2021 einen Vertragsentwurf über beiderseitige verbindliche Sicherheitsgarantien zukommen, den die NATO im Januar ablehnte. Im Februar eskalierte laut OSZE die Gewalt im Donbass.
Bereits wenige Wochen nach der Invasion, Ende März 2022, kam es in Istanbul zu Friedensverhandlungen, die fast zu einer Lösung geführt hätten. Dass der Krieg nicht damals bereits beendet wurde, lag daran, dass der Westen dies nicht wollte. Man war der Meinung, Russland durch die Ukraine in diesem Stellvertreterkrieg auf Dauer militärisch schwächen zu können. Angesichts von Hunderttausenden Toten, Verletzten und Traumatisierten, die als Folge seitdem zu beklagen sind, sowie dem Ausmaß der Zerstörung, fehlen einem die Worte.
Hasst der Westen die Russen?
Diese Frage drängt sich auf, wenn man das oft unerträglich feindselige Gebaren beobachtet, das beileibe nicht neu ist und vor Doppelmoral trieft. Russland und speziell die Person Wladimir Putins werden regelrecht dämonisiert, was gleichzeitig scheinbar jede Form von Diplomatie ausschließt.
Russlands militärische Stärke, seine geografische Lage, sein Rohstoffreichtum oder seine unabhängige diplomatische Tradition sind sicher Störfaktoren für das US-amerikanische Bestreben, der Boss in einer unipolaren Welt zu sein. Ein womöglich funktionierender eurasischer Kontinent, insbesondere gute Beziehungen zwischen Russland und Deutschland, war indes schon vor dem Ersten Weltkrieg eine Sorge des britischen Imperiums.
Ein «Vergehen» von Präsident Putin könnte gewesen sein, dass er die neoliberale Schocktherapie à la IWF und den Ausverkauf des Landes (auch an US-Konzerne) beendete, der unter seinem Vorgänger herrschte. Dabei zeigte er sich als Führungspersönlichkeit und als nicht so formbar wie Jelzin. Diese Aspekte allein sind aber heute vermutlich keine ausreichende Erklärung für ein derart gepflegtes Feindbild.
Der Historiker und Philosoph Hauke Ritz erweitert den Fokus der Fragestellung zu: «Warum hasst der Westen die Russen so sehr?», was er zum Beispiel mit dem Medienforscher Michael Meyen und mit der Politikwissenschaftlerin Ulrike Guérot bespricht. Ritz stellt die interessante These [11] auf, dass Russland eine Provokation für den Westen sei, welcher vor allem dessen kulturelles und intellektuelles Potenzial fürchte.
Die Russen sind Europäer aber anders, sagt Ritz. Diese «Fremdheit in der Ähnlichkeit» erzeuge vielleicht tiefe Ablehnungsgefühle. Obwohl Russlands Identität in der europäischen Kultur verwurzelt ist, verbinde es sich immer mit der Opposition in Europa. Als Beispiele nennt er die Kritik an der katholischen Kirche oder die Verbindung mit der Arbeiterbewegung. Christen, aber orthodox; Sozialismus statt Liberalismus. Das mache das Land zum Antagonisten des Westens und zu einer Bedrohung der Machtstrukturen in Europa.
Fazit
Selbstverständlich kann man Geschichte, Ereignisse und Entwicklungen immer auf verschiedene Arten lesen. Dieser Artikel, obwohl viel zu lang, konnte nur einige Aspekte der Ukraine-Tragödie anreißen, die in den offiziellen Darstellungen in der Regel nicht vorkommen. Mindestens dürfte damit jedoch klar geworden sein, dass die Russische Föderation bzw. Wladimir Putin nicht der alleinige Aggressor in diesem Konflikt ist. Das ist ein Stellvertreterkrieg zwischen USA/NATO (gut) und Russland (böse); die Ukraine (edel) wird dabei schlicht verheizt.
Das ist insofern von Bedeutung, als die gesamte europäische Kriegshysterie auf sorgsam kultivierten Freund-Feind-Bildern beruht. Nur so kann Konfrontation und Eskalation betrieben werden, denn damit werden die wahren Hintergründe und Motive verschleiert. Angst und Propaganda sind notwendig, damit die Menschen den Wahnsinn mitmachen. Sie werden belogen, um sie zuerst zu schröpfen und anschließend auf die Schlachtbank zu schicken. Das kann niemand wollen, außer den stets gleichen Profiteuren: die Rüstungs-Lobby und die großen Investoren, die schon immer an Zerstörung und Wiederaufbau verdient haben.
Apropos Investoren: Zu den Top-Verdienern und somit Hauptinteressenten an einer Fortführung des Krieges zählt BlackRock, einer der weltgrößten Vermögensverwalter. Der deutsche Bundeskanzler in spe, Friedrich Merz, der gerne «Taurus»-Marschflugkörper an die Ukraine liefern und die Krim-Brücke zerstören möchte, war von 2016 bis 2020 Aufsichtsratsvorsitzender von BlackRock in Deutschland. Aber das hat natürlich nichts zu sagen, der Mann macht nur seinen Job.
Es ist ein Spiel der Kräfte, es geht um Macht und strategische Kontrolle, um Geheimdienste und die Kontrolle der öffentlichen Meinung, um Bodenschätze, Rohstoffe, Pipelines und Märkte. Das klingt aber nicht sexy, «Demokratie und Menschenrechte» hört sich besser und einfacher an. Dabei wäre eine für alle Seiten förderliche Politik auch nicht so kompliziert; das Handwerkszeug dazu nennt sich Diplomatie. Noch einmal Gabriele Krone-Schmalz:
«Friedliche Politik ist nichts anderes als funktionierender Interessenausgleich. Da geht’s nicht um Moral.»
Die Situation in der Ukraine ist sicher komplex, vor allem wegen der inneren Zerrissenheit. Es dürfte nicht leicht sein, eine friedliche Lösung für das Zusammenleben zu finden, aber die Beteiligten müssen es vor allem wollen. Unter den gegebenen Umständen könnte eine sinnvolle Perspektive mit Neutralität und föderalen Strukturen zu tun haben.
Allen, die sich bis hierher durch die Lektüre gearbeitet (oder auch einfach nur runtergescrollt) haben, wünsche ich frohe Oster-Friedenstage!
[Titelbild: Pixabay; Abb. 1 und 2: nach Ganser/SIPER; Abb. 3: SIPER]
--- Quellen: ---
[1] Albrecht Müller, «Glaube wenig. Hinterfrage alles. Denke selbst.», Westend 2019
[2] Zwei nette Beispiele:
- ARD-faktenfinder (sic), «Viel Aufmerksamkeit für fragwürdige Experten», 03/2023
- Neue Zürcher Zeitung, «Aufstieg und Fall einer Russlandversteherin – die ehemalige ARD-Korrespondentin Gabriele Krone-Schmalz rechtfertigt seit Jahren Putins Politik», 12/2022
[3] George Washington University, «NATO Expansion: What Gorbachev Heard – Declassified documents show security assurances against NATO expansion to Soviet leaders from Baker, Bush, Genscher, Kohl, Gates, Mitterrand, Thatcher, Hurd, Major, and Woerner», 12/2017
[4] Beispielsweise Wladimir Putin bei seiner Rede im Deutschen Bundestag, 25/09/2001
[5] William Engdahl, «Full Spectrum Dominance, Totalitarian Democracy In The New World Order», edition.engdahl 2009
[6] Daniele Ganser, «Illegale Kriege – Wie die NATO-Länder die UNO sabotieren. Eine Chronik von Kuba bis Syrien», Orell Füssli 2016
[7] Gabriele Krone-Schmalz, «Mit Friedensjournalismus gegen ‘Kriegstüchtigkeit’», Vortrag und Diskussion an der Universität Hamburg, veranstaltet von engagierten Studenten, 16/01/2025\ → Hier ist ein ähnlicher Vortrag von ihr (Video), den ich mit spanischer Übersetzung gefunden habe.
[8] Für mehr Hintergrund und Details empfehlen sich z.B. folgende Bücher:
- Mathias Bröckers, Paul Schreyer, «Wir sind immer die Guten», Westend 2019
- Gabriele Krone-Schmalz, «Russland verstehen? Der Kampf um die Ukraine und die Arroganz des Westens», Westend 2023
- Patrik Baab, «Auf beiden Seiten der Front – Meine Reisen in die Ukraine», Fiftyfifty 2023
[9] vgl. Jonathan Mowat, «Washington's New World Order "Democratization" Template», 02/2005 und RAND Corporation, «Swarming and the Future of Conflict», 2000
[10] Bemerkenswert einige Beiträge, von denen man später nichts mehr wissen wollte:
- ARD Monitor, «Todesschüsse in Kiew: Wer ist für das Blutbad vom Maidan verantwortlich», 10/04/2014, Transkript hier
- Telepolis, «Blutbad am Maidan: Wer waren die Todesschützen?», 12/04/2014
- Telepolis, «Scharfschützenmorde in Kiew», 14/12/2014
- Deutschlandfunk, «Gefahr einer Spirale nach unten», Interview mit Günter Verheugen, 18/03/2014
- NDR Panorama, «Putsch in Kiew: Welche Rolle spielen die Faschisten?», 06/03/2014
[11] Hauke Ritz, «Vom Niedergang des Westens zur Neuerfindung Europas», 2024
Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
-
 @ b9f4c34d:7d1a0e31
2025-04-02 14:59:02
@ b9f4c34d:7d1a0e31
2025-04-02 14:59:02Testy McTestenface
It's been so long, html
-
 @ 04c915da:3dfbecc9
2025-03-26 20:54:33
@ 04c915da:3dfbecc9
2025-03-26 20:54:33Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all.
That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission.
As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently.
Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive.
Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally.
The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match.
When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol.
Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
-
 @ 9bde4214:06ca052b
2025-04-22 18:13:37
@ 9bde4214:06ca052b
2025-04-22 18:13:37"It's gonna be permissionless or hell."
Gigi and gzuuus are vibing towards dystopia.
Books & articles mentioned:
- AI 2027
- DVMs were a mistake
- Careless People by Sarah Wynn-Williams
- Takedown by Laila michelwait
- The Ultimate Resource by Julian L. Simon
- Harry Potter by J.K. Rowling
- Momo by Michael Ende
In this dialogue:
- Pablo's Roo Setup
- Tech Hype Cycles
- AI 2027
- Prompt injection and other attacks
- Goose and DVMCP
- Cursor vs Roo Code
- Staying in control thanks to Amber and signing delegation
- Is YOLO mode here to stay?
- What agents to trust?
- What MCP tools to trust?
- What code snippets to trust?
- Everyone will run into the issues of trust and micropayments
- Nostr solves Web of Trust & micropayments natively
- Minimalistic & open usually wins
- DVMCP exists thanks to Totem
- Relays as Tamagochis
- Agents aren't nostr experts, at least not right now
- Fix a mistake once & it's fixed forever
- Giving long-term memory to LLMs
- RAG Databases signed by domain experts
- Human-agent hybrids & Chess
- Nostr beating heart
- Pluggable context & experts
- "You never need an API key for anything"
- Sats and social signaling
- Difficulty-adjusted PoW as a rare-limiting mechanism
- Certificate authorities and centralization
- No solutions to policing speech!
- OAuth and how it centralized
- Login with nostr
- Closed vs open-source models
- Tiny models vs large models
- The minions protocol (Stanford paper)
- Generalist models vs specialized models
- Local compute & encrypted queries
- Blinded compute
- "In the eyes of the state, agents aren't people"
- Agents need identity and money; nostr provides both
- "It's gonna be permissionless or hell"
- We already have marketplaces for MCP stuff, code snippets, and other things
- Most great stuff came from marketplaces (browsers, games, etc)
- Zapstore shows that this is already working
- At scale, central control never works. There's plenty scams and viruses in the app stores.
- Using nostr to archive your user-generated content
- HAVEN, blossom, novia
- The switcharoo from advertisements to training data
- What is Truth?
- What is Real?
- "We're vibing into dystopia"
- Who should be the arbiter of Truth?
- First Amendment & why the Logos is sacred
- Silicon Valley AI bros arrogantly dismiss wisdom and philosophy
- Suicide rates & the meaning crisis
- Are LLMs symbiotic or parasitic?
- The Amish got it right
- Are we gonna make it?
- Careless People by Sarah Wynn-Williams
- Takedown by Laila michelwait
- Harry Potter dementors & Momo's time thieves
- Facebook & Google as non-human (superhuman) agents
- Zapping as a conscious action
- Privacy and the internet
- Plausible deniability thanks to generative models
- Google glasses, glassholes, and Meta's Ray Ben's
- People crave realness
- Bitcoin is the realest money we ever had
- Nostr allows for real and honest expression
- How do we find out what's real?
- Constraints, policing, and chilling effects
- Jesus' plans for DVMCP
- Hzrd's article on how DVMs are broken (DVMs were a mistake)
- Don't believe the hype
- DVMs pre-date MCP tools
- Data Vending Machines were supposed to be stupid: put coin in, get stuff out.
- Self-healing vibe-coding
- IP addresses as scarce assets
- Atomic swaps and the ASS protocol
- More marketplaces, less silos
- The intensity of #SovEng and the last 6 weeks
- If you can vibe-code everything, why build anything?
- Time, the ultimate resource
- What are the LLMs allowed to think?
- Natural language interfaces are inherently dialogical
- Sovereign Engineering is dialogical too
-
 @ c631e267:c2b78d3e
2025-04-18 15:53:07
@ c631e267:c2b78d3e
2025-04-18 15:53:07Verstand ohne Gefühl ist unmenschlich; \ Gefühl ohne Verstand ist Dummheit. \ Egon Bahr
Seit Jahren werden wir darauf getrimmt, dass Fakten eigentlich gefühlt seien. Aber nicht alles ist relativ und nicht alles ist nach Belieben interpretierbar. Diese Schokoladenhasen beispielsweise, die an Ostern in unseren Gefilden typisch sind, «ostern» zwar nicht, sondern sie sitzen in der Regel, trotzdem verwandelt sie das nicht in «Sitzhasen».
Nichts soll mehr gelten, außer den immer invasiveren Gesetzen. Die eigenen Traditionen und Wurzeln sind potenziell «pfui», um andere Menschen nicht auszuschließen, aber wir mögen uns toleranterweise an die fremden Symbole und Rituale gewöhnen. Dabei ist es mir prinzipiell völlig egal, ob und wann jemand ein Fastenbrechen feiert, am Karsamstag oder jedem anderen Tag oder nie – aber bitte freiwillig.
Und vor allem: Lasst die Finger von den Kindern! In Bern setzten kürzlich Demonstranten ein Zeichen gegen die zunehmende Verbreitung woker Ideologie im Bildungssystem und forderten ein Ende der sexuellen Indoktrination von Schulkindern.
Wenn es nicht wegen des heiklen Themas Migration oder wegen des Regenbogens ist, dann wegen des Klimas. Im Rahmen der «Netto Null»-Agenda zum Kampf gegen das angeblich teuflische CO2 sollen die Menschen ihre Ernährungsgewohnheiten komplett ändern. Nach dem Willen von Produzenten synthetischer Lebensmittel, wie Bill Gates, sollen wir baldmöglichst praktisch auf Fleisch und alle Milchprodukte wie Milch und Käse verzichten. Ein lukratives Geschäftsmodell, das neben der EU aktuell auch von einem britischen Lobby-Konsortium unterstützt wird.
Sollten alle ideologischen Stricke zu reißen drohen, ist da immer noch «der Putin». Die Unions-Europäer offenbaren sich dabei ständig mehr als Vertreter der Rüstungsindustrie. Allen voran zündelt Deutschland an der Kriegslunte, angeführt von einem scheinbar todesmutigen Kanzlerkandidaten Friedrich Merz. Nach dessen erneuter Aussage, «Taurus»-Marschflugkörper an Kiew liefern zu wollen, hat Russland eindeutig klargestellt, dass man dies als direkte Kriegsbeteiligung werten würde – «mit allen sich daraus ergebenden Konsequenzen für Deutschland».
Wohltuend sind Nachrichten über Aktivitäten, die sich der allgemeinen Kriegstreiberei entgegenstellen oder diese öffentlich hinterfragen. Dazu zählt auch ein Kongress kritischer Psychologen und Psychotherapeuten, der letzte Woche in Berlin stattfand. Die vielen Vorträge im Kontext von «Krieg und Frieden» deckten ein breites Themenspektrum ab, darunter Friedensarbeit oder die Notwendigkeit einer «Pädagogik der Kriegsuntüchtigkeit».
Der heutige «stille Freitag», an dem Christen des Leidens und Sterbens von Jesus gedenken, ist vielleicht unabhängig von jeder religiösen oder spirituellen Prägung eine passende Einladung zur Reflexion. In der Ruhe liegt die Kraft. In diesem Sinne wünsche ich Ihnen frohe Ostertage!
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 9bde4214:06ca052b
2025-04-22 17:30:02
@ 9bde4214:06ca052b
2025-04-22 17:30:02“We do not have the answers."
Pablo & Gigi have no solutions.
In this dialogue:
- What is this No Solutions thing anyway?
- Why dialogue and distributed cognition is so important
- Why is nostr exciting for developers?
- Evolution, Life, and nostr
- What is the perfect nostr app, and why can’t there be THE perfect nostr app?
- Why there is no “global” view in nostr
- Impossible problems vs. possible (but still hard) problems
- Blossom, blossom, and more blossom
- Zooko’s Triangle
- Freedom Tech Building Blocks
- NIP-60/61, NIP-89
- Email vs ICQ
- Accepting constraints & moving forward
- Nostr has data integrity, but no data guarantees
- Bitcoin as an extreme RAID system
- Fault tolerance vs. efficiency
- “Build the infrastructure, don’t run it.”
- eCash fixes 402
- Everything in nostr can be one-click
- There’s infinite nsecs (and they are free!)
- The magic of the nostr view-only mode
- The Local-first movement
- How to monetize without putting yourself in the middle?
- RoboSats as an example of open-source monetization
- The YouTube like count is a lie
Further links:
- https://en.wikipedia.org/wiki/Distributed_cognition
- https://nips.nostr.com/60
- https://nips.nostr.com/61
- https://nips.nostr.com/89
- https://github.com/hzrd149/blossom
- https://en.wikipedia.org/wiki/Zooko’s_triangle
- https://www.jrepodcast.com/guest/adam-curry/
- https://localfirstweb.dev/
- https://www.localfirstconf.com/
- https://en.wikipedia.org/wiki/ICQ
- https://appleinsider.com/articles/24/05/25/icq-1996-2024-the-first-universal-messenger-had-a-good-run-and-is-leaving-us-soon
- https://www.chatinum.com/articles/the-old-chat-apps-of-the-2000s
- https://en.wikipedia.org/wiki/Standard_RAID_levels
- https://www.youtube.com/watch?v=oIkhgagvrjI
- https://njump.me/nosolutions@sovereignengineering.io
-
 @ c1e9ab3a:9cb56b43
2025-04-14 21:20:08
@ c1e9ab3a:9cb56b43
2025-04-14 21:20:08In an age where culture often precedes policy, a subtle yet potent mechanism may be at play in the shaping of American perspectives on gun ownership. Rather than directly challenging the Second Amendment through legislation alone, a more insidious strategy may involve reshaping the cultural and social norms surrounding firearms—by conditioning the population, starting at its most impressionable point: the public school system.
The Cultural Lever of Language
Unlike Orwell's 1984, where language is controlled by removing words from the lexicon, this modern approach may hinge instead on instilling fear around specific words or topics—guns, firearms, and self-defense among them. The goal is not to erase the language but to embed a taboo so deep that people voluntarily avoid these terms out of social self-preservation. Children, teachers, and parents begin to internalize a fear of even mentioning weapons, not because the words are illegal, but because the cultural consequences are severe.
The Role of Teachers in Social Programming
Teachers, particularly in primary and middle schools, serve not only as educational authorities but also as social regulators. The frequent argument against homeschooling—that children will not be "properly socialized"—reveals an implicit understanding that schools play a critical role in setting behavioral norms. Children learn what is acceptable not just academically but socially. Rules, discipline, and behavioral expectations are laid down by teachers, often reinforced through peer pressure and institutional authority.
This places teachers in a unique position of influence. If fear is instilled in these educators—fear that one of their students could become the next school shooter—their response is likely to lean toward overcorrection. That overcorrection may manifest as a total intolerance for any conversation about weapons, regardless of the context. Innocent remarks or imaginative stories from young children are interpreted as red flags, triggering intervention from administrators and warnings to parents.
Fear as a Policy Catalyst
School shootings, such as the one at Columbine, serve as the fulcrum for this fear-based conditioning. Each highly publicized tragedy becomes a national spectacle, not only for mourning but also for cementing the idea that any child could become a threat. Media cycles perpetuate this narrative with relentless coverage and emotional appeals, ensuring that each incident becomes embedded in the public consciousness.
The side effect of this focus is the generation of copycat behavior, which, in turn, justifies further media attention and tighter controls. Schools install security systems, metal detectors, and armed guards—not simply to stop violence, but to serve as a daily reminder to children and staff alike: guns are dangerous, ubiquitous, and potentially present at any moment. This daily ritual reinforces the idea that the very discussion of firearms is a precursor to violence.
Policy and Practice: The Zero-Tolerance Feedback Loop
Federal and district-level policies begin to reflect this cultural shift. A child mentioning a gun in class—even in a non-threatening or imaginative context—is flagged for intervention. Zero-tolerance rules leave no room for context or intent. Teachers and administrators, fearing for their careers or safety, comply eagerly with these guidelines, interpreting them as moral obligations rather than bureaucratic policies.
The result is a generation of students conditioned to associate firearms with social ostracism, disciplinary action, and latent danger. The Second Amendment, once seen as a cultural cornerstone of American liberty and self-reliance, is transformed into an artifact of suspicion and anxiety.
Long-Term Consequences: A Nation Re-Socialized
Over time, this fear-based reshaping of discourse creates adults who not only avoid discussing guns but view them as morally reprehensible. Their aversion is not grounded in legal logic or political philosophy, but in deeply embedded emotional programming begun in early childhood. The cultural weight against firearms becomes so great that even those inclined to support gun rights feel the need to self-censor.
As fewer people grow up discussing, learning about, or responsibly handling firearms, the social understanding of the Second Amendment erodes. Without cultural reinforcement, its value becomes abstract and its defenders marginalized. In this way, the right to bear arms is not abolished by law—it is dismantled by language, fear, and the subtle recalibration of social norms.
Conclusion
This theoretical strategy does not require a single change to the Constitution. It relies instead on the long game of cultural transformation, beginning with the youngest minds and reinforced by fear-driven policy and media narratives. The outcome is a society that views the Second Amendment not as a safeguard of liberty, but as an anachronism too dangerous to mention.
By controlling the language through social consequences and fear, a nation can be taught not just to disarm, but to believe it chose to do so freely. That, perhaps, is the most powerful form of control of all.
-
 @ b2d670de:907f9d4a
2025-03-25 20:17:57
@ b2d670de:907f9d4a
2025-03-25 20:17:57This guide will walk you through setting up your own Strfry Nostr relay on a Debian/Ubuntu server and making it accessible exclusively as a TOR hidden service. By the end, you'll have a privacy-focused relay that operates entirely within the TOR network, enhancing both your privacy and that of your users.
Table of Contents
- Prerequisites
- Initial Server Setup
- Installing Strfry Nostr Relay
- Configuring Your Relay
- Setting Up TOR
- Making Your Relay Available on TOR
- Testing Your Setup]
- Maintenance and Security
- Troubleshooting
Prerequisites
- A Debian or Ubuntu server
- Basic familiarity with command line operations (most steps are explained in detail)
- Root or sudo access to your server
Initial Server Setup
First, let's make sure your server is properly set up and secured.
Update Your System
Connect to your server via SSH and update your system:
bash sudo apt update sudo apt upgrade -ySet Up a Basic Firewall
Install and configure a basic firewall:
bash sudo apt install ufw -y sudo ufw allow ssh sudo ufw enableThis allows SSH connections while blocking other ports for security.
Installing Strfry Nostr Relay
This guide includes the full range of steps needed to build and set up Strfry. It's simply based on the current version of the
DEPLOYMENT.mddocument in the Strfry GitHub repository. If the build/setup process is changed in the repo, this document could get outdated. If so, please report to me that something is outdated and check for updated steps here.Install Dependencies
First, let's install the necessary dependencies. Each package serves a specific purpose in building and running Strfry:
bash sudo apt install -y git build-essential libyaml-perl libtemplate-perl libregexp-grammars-perl libssl-dev zlib1g-dev liblmdb-dev libflatbuffers-dev libsecp256k1-dev libzstd-devHere's why each dependency is needed:
Basic Development Tools: -
git: Version control system used to clone the Strfry repository and manage code updates -build-essential: Meta-package that includes compilers (gcc, g++), make, and other essential build toolsPerl Dependencies (used for Strfry's build scripts): -
libyaml-perl: Perl interface to parse YAML configuration files -libtemplate-perl: Template processing system used during the build process -libregexp-grammars-perl: Advanced regular expression handling for Perl scriptsCore Libraries for Strfry: -
libssl-dev: Development files for OpenSSL, used for secure connections and cryptographic operations -zlib1g-dev: Compression library that Strfry uses to reduce data size -liblmdb-dev: Lightning Memory-Mapped Database library, which Strfry uses for its high-performance database backend -libflatbuffers-dev: Memory-efficient serialization library for structured data -libsecp256k1-dev: Optimized C library for EC operations on curve secp256k1, essential for Nostr's cryptographic signatures -libzstd-dev: Fast real-time compression algorithm for efficient data storage and transmissionClone and Build Strfry
Clone the Strfry repository:
bash git clone https://github.com/hoytech/strfry.git cd strfryBuild Strfry:
bash git submodule update --init make setup-golpe make -j2 # This uses 2 CPU cores. Adjust based on your server (e.g., -j4 for 4 cores)This build process will take several minutes, especially on servers with limited CPU resources, so go get a coffee and post some great memes on nostr in the meantime.
Install Strfry
Install the Strfry binary to your system path:
bash sudo cp strfry /usr/local/binThis makes the
strfrycommand available system-wide, allowing it to be executed from any directory and by any user with the appropriate permissions.Configuring Your Relay
Create Strfry User
Create a dedicated user for running Strfry. This enhances security by isolating the relay process:
bash sudo useradd -M -s /usr/sbin/nologin strfryThe
-Mflag prevents creating a home directory, and-s /usr/sbin/nologinprevents anyone from logging in as this user. This is a security best practice for service accounts.Create Data Directory
Create a directory for Strfry's data:
bash sudo mkdir /var/lib/strfry sudo chown strfry:strfry /var/lib/strfry sudo chmod 755 /var/lib/strfryThis creates a dedicated directory for Strfry's database and sets the appropriate permissions so that only the strfry user can write to it.
Configure Strfry
Copy the sample configuration file:
bash sudo cp strfry.conf /etc/strfry.confEdit the configuration file:
bash sudo nano /etc/strfry.confModify the database path:
```
Find this line:
db = "./strfry-db/"
Change it to:
db = "/var/lib/strfry/" ```
Check your system's hard limit for file descriptors:
bash ulimit -HnUpdate the
nofilessetting in your configuration to match this value (or set to 0):```
Add or modify this line in the config (example if your limit is 524288):
nofiles = 524288 ```
The
nofilessetting determines how many open files Strfry can have simultaneously. Setting it to your system's hard limit (or 0 to use the system default) helps prevent "too many open files" errors if your relay becomes popular.You might also want to customize your relay's information in the config file. Look for the
infosection and update it with your relay's name, description, and other details.Set ownership of the configuration file:
bash sudo chown strfry:strfry /etc/strfry.confCreate Systemd Service
Create a systemd service file for managing Strfry:
bash sudo nano /etc/systemd/system/strfry.serviceAdd the following content:
```ini [Unit] Description=strfry relay service
[Service] User=strfry ExecStart=/usr/local/bin/strfry relay Restart=on-failure RestartSec=5 ProtectHome=yes NoNewPrivileges=yes ProtectSystem=full LimitCORE=1000000000
[Install] WantedBy=multi-user.target ```
This systemd service configuration: - Runs Strfry as the dedicated strfry user - Automatically restarts the service if it fails - Implements security measures like
ProtectHomeandNoNewPrivileges- Sets resource limits appropriate for a relayEnable and start the service:
bash sudo systemctl enable strfry.service sudo systemctl start strfryCheck the service status:
bash sudo systemctl status strfryVerify Relay is Running
Test that your relay is running locally:
bash curl localhost:7777You should see a message indicating that the Strfry relay is running. This confirms that Strfry is properly installed and configured before we proceed to set up TOR.
Setting Up TOR
Now let's make your relay accessible as a TOR hidden service.
Install TOR
Install TOR from the package repositories:
bash sudo apt install -y torThis installs the TOR daemon that will create and manage your hidden service.
Configure TOR
Edit the TOR configuration file:
bash sudo nano /etc/tor/torrcScroll down to wherever you see a commented out part like this: ```
HiddenServiceDir /var/lib/tor/hidden_service/
HiddenServicePort 80 127.0.0.1:80
```
Under those lines, add the following lines to set up a hidden service for your relay:
HiddenServiceDir /var/lib/tor/strfry-relay/ HiddenServicePort 80 127.0.0.1:7777This configuration: - Creates a hidden service directory at
/var/lib/tor/strfry-relay/- Maps port 80 on your .onion address to port 7777 on your local machine - Keeps all traffic encrypted within the TOR networkCreate the directory for your hidden service:
bash sudo mkdir -p /var/lib/tor/strfry-relay/ sudo chown debian-tor:debian-tor /var/lib/tor/strfry-relay/ sudo chmod 700 /var/lib/tor/strfry-relay/The strict permissions (700) are crucial for security as they ensure only the debian-tor user can access the directory containing your hidden service private keys.
Restart TOR to apply changes:
bash sudo systemctl restart torMaking Your Relay Available on TOR
Get Your Onion Address
After restarting TOR, you can find your onion address:
bash sudo cat /var/lib/tor/strfry-relay/hostnameThis will output something like
abcdefghijklmnopqrstuvwxyz234567.onion, which is your relay's unique .onion address. This is what you'll share with others to access your relay.Understanding Onion Addresses
The .onion address is a special-format hostname that is automatically generated based on your hidden service's private key.
Your users will need to use this address with the WebSocket protocol prefix to connect:
ws://youronionaddress.onionTesting Your Setup
Test with a Nostr Client
The best way to test your relay is with an actual Nostr client that supports TOR:
- Open your TOR browser
- Go to your favorite client, either on clearnet or an onion service.
- Check out this list of nostr clients available over TOR.
- Add your relay URL:
ws://youronionaddress.onionto your relay list - Try posting a note and see if it appears on your relay
- In some nostr clients, you can also click on a relay to get information about it like the relay name and description you set earlier in the stryfry config. If you're able to see the correct values for the name and the description, you were able to connect to the relay.
- Some nostr clients also gives you a status on what relays a note was posted to, this could also give you an indication that your relay works as expected.
Note that not all Nostr clients support TOR connections natively. Some may require additional configuration or use of TOR Browser. E.g. most mobile apps would most likely require a TOR proxy app running in the background (some have TOR support built in too).
Maintenance and Security
Regular Updates
Keep your system, TOR, and relay updated:
```bash
Update system
sudo apt update sudo apt upgrade -y
Update Strfry
cd ~/strfry git pull git submodule update make -j2 sudo cp strfry /usr/local/bin sudo systemctl restart strfry
Verify TOR is still running properly
sudo systemctl status tor ```
Regular updates are crucial for security, especially for TOR which may have security-critical updates.
Database Management
Strfry has built-in database management tools. Check the Strfry documentation for specific commands related to database maintenance, such as managing event retention and performing backups.
Monitoring Logs
To monitor your Strfry logs:
bash sudo journalctl -u strfry -fTo check TOR logs:
bash sudo journalctl -u tor -fMonitoring logs helps you identify potential issues and understand how your relay is being used.
Backup
This is not a best practices guide on how to do backups. Preferably, backups should be stored either offline or on a different machine than your relay server. This is just a simple way on how to do it on the same server.
```bash
Stop the relay temporarily
sudo systemctl stop strfry
Backup the database
sudo cp -r /var/lib/strfry /path/to/backup/location
Restart the relay
sudo systemctl start strfry ```
Back up your TOR hidden service private key. The private key is particularly sensitive as it defines your .onion address - losing it means losing your address permanently. If you do a backup of this, ensure that is stored in a safe place where no one else has access to it.
bash sudo cp /var/lib/tor/strfry-relay/hs_ed25519_secret_key /path/to/secure/backup/locationTroubleshooting
Relay Not Starting
If your relay doesn't start:
```bash
Check logs
sudo journalctl -u strfry -e
Verify configuration
cat /etc/strfry.conf
Check permissions
ls -la /var/lib/strfry ```
Common issues include: - Incorrect configuration format - Permission problems with the data directory - Port already in use (another service using port 7777) - Issues with setting the nofiles limit (setting it too big)
TOR Hidden Service Not Working
If your TOR hidden service is not accessible:
```bash
Check TOR logs
sudo journalctl -u tor -e
Verify TOR is running
sudo systemctl status tor
Check onion address
sudo cat /var/lib/tor/strfry-relay/hostname
Verify TOR configuration
sudo cat /etc/tor/torrc ```
Common TOR issues include: - Incorrect directory permissions - TOR service not running - Incorrect port mapping in torrc
Testing Connectivity
If you're having trouble connecting to your service:
```bash
Verify Strfry is listening locally
sudo ss -tulpn | grep 7777
Check that TOR is properly running
sudo systemctl status tor
Test the local connection directly
curl --include --no-buffer localhost:7777 ```
Privacy and Security Considerations
Running a Nostr relay as a TOR hidden service provides several important privacy benefits:
-
Network Privacy: Traffic to your relay is encrypted and routed through the TOR network, making it difficult to determine who is connecting to your relay.
-
Server Anonymity: The physical location and IP address of your server are concealed, providing protection against denial-of-service attacks and other targeting.
-
Censorship Resistance: TOR hidden services are more resilient against censorship attempts, as they don't rely on the regular DNS system and can't be easily blocked.
-
User Privacy: Users connecting to your relay through TOR enjoy enhanced privacy, as their connections are also encrypted and anonymized.
However, there are some important considerations:
- TOR connections are typically slower than regular internet connections
- Not all Nostr clients support TOR connections natively
- Running a hidden service increases the importance of keeping your server secure
Congratulations! You now have a Strfry Nostr relay running as a TOR hidden service. This setup provides a resilient, privacy-focused, and censorship-resistant communication channel that helps strengthen the Nostr network.
For further customization and advanced configuration options, refer to the Strfry documentation.
Consider sharing your relay's .onion address with the Nostr community to help grow the privacy-focused segment of the network!
If you plan on providing a relay service that the public can use (either for free or paid for), consider adding it to this list. Only add it if you plan to run a stable and available relay.
-
 @ a296b972:e5a7a2e8
2025-04-17 23:08:50
@ a296b972:e5a7a2e8
2025-04-17 23:08:50Die Figuren in der Koalition der Willigen entlarven ihre charakterliche Ungeeignetheit für politische Ämter mit Verantwortung für ganze Nationen. Staatliche Entscheidungen dürfen nicht emotionsgesteuert sein. Aber genau das ist derzeit der Fall. Überall wird mit der Moralkeule um sich gehauen. Erwachsene benehmen sich wie im Kindergarten und zeigen ihre fehlende Reife. Von menschlicher Größe ganz zu schweigen.
Bisher war es schön warm unter den Fittichen der USA. Deutschland hat aufgrund seiner Geschichte besonders gut den Nick-August gespielt und sich selbst eine Souveränität vorgelogen, die es so nie gegeben hat. Jetzt sieht es so aus, als wollten die USA Europa in die Freiheit, in die Volljährigkeit entlassen. Es könnte auch sein, dass die USA aus der NATO austreten und sich vor allem um sich selbst kümmern. Allein das würde die Welt schon wesentlich friedlicher machen, denkt man beispielsweise an den Einmarsch in den Irak. Es gehen Gerüchte um, dass Truppen aus Rumänien und Deutschland abgezogen werden sollen.
Vielleicht geht es bei den Friedensverhandlungen zwischen Trump und Putin nicht nur um die Ukraine, sondern, wenn man schon mal dabei ist, auch um die Kräfteverteilung in Europa insgesamt. Waffeneinsätze in der Ukraine wurden maßgeblich von Wiesbaden aus gesteuert. 2026 sollen dort US-Mittelstrecken-Raketen stationiert werden. Der an Führungsstärke kleinste Kanzler der Bundesrepublik, Scholz, hat das brav abgenickt. Der nur noch durch ein Wunder zu verhindernde neue Kanzler, das Glas Gewürzgurken aus dem Sauerland, provoziert Russland mit seiner Ankündigung zu den Taurus-Raketen dafür um so mehr. Da ist man schon fast gewillt, sich den Scholz zurückzuwünschen, als das kleinere Übel.
Statt mit Besonnenheit und Vernunft die veränderte Sicherheitslage mit den USA als eher abtrünnige Schutzmacht neu zu bewerten, hierin auch eine Chance zu sehen, eine starke Botschaft und den Willen auf ein friedliches neues Miteinander in den Fokus zu stellen, reagieren die meisten europäischen politischen „Spitzenkräfte“ mit blindem Aktionismus, der weltenbrandgefährlich ist. Und Deutschland, dass es sich aufgrund seiner Geschichte am wenigsten erlauben könnte, macht mit von der Leyen in Brüssel und Merz, Pistorius und anderen Kriegs-Warm-Uppern am weitesten das Maul auf, obwohl es sich am bedecktesten halten sollte.
Angesichts der Tatsache, dass Europa gegenüber einer Atommacht wie Russland vollkommen wehrlos ist, wäre es wirklich viel gescheiter, sich der neuen Situation anzupassen und ständig Signale der Friedensbereitschaft zu senden. Unterstütz von den Briten und Franzosen schmiegt Brüssel eine Koalition der Friedensuntüchtigen, wie sie Uwe Froschauer aktuell in seinem Buch „Die Friedensuntüchtigen“ beschreibt. In der Rezension von mir gibt es auch einen Link zu einem Review des Inhalts:
https://wassersaege.com/blogbeitraege/buchrezension-die-friedensuntuechtigen-von-uwe-froschauer/
Stattdessen passiert das Gegenteil.
Es ist nicht nur legitim, sondern sogar Aufgabe der einzelnen Staaten, eine gewisse Verteidigungsfähigkeit aufbauen zu wollen. Derzeit geschieht das jedoch unter falschen Vorzeichen. Die NATO, als sogenanntes Verteidigungsbündnis zur Vorlage zu nehmen, wäre keine gute Idee, weil sie sich mangels Gelegenheit (der Verteidigung) eher als das Gegenteil herausgestellt hat, wie man seinerzeit in Jugoslawien erleben musste.
Russland als Feind hochzustilisieren, um ein Aufrüsten zu beschleunigen, ist jedoch der denkbar falscheste Weg. Wenn ein Yorkshire-Terrier einen Pit-Bull ankläfft, könnte das fatale Folgen haben. Wenn die europäischen „Geistesgrößen“ bei Verstand wären und in der Lage, die Realität richtig einzuschätzen, würden sie das erkennen.
Woher kommt die Überheblichkeit, woher die Unfähigkeit zur Einschätzung der Lage, woher die Realitätsverweigerung? Ist das gewollt, steckt ein Plan dahinter oder sind „die“ einfach „nur“ strunzendoof? Letzteres wäre die gefährlichste Variante.
Es stellt sich immer mehr heraus, dass Corona offensichtlich ein Test war, wie weit die Menschen in ihrer Obrigkeitshörigkeit zu treiben sind. Wie dumm und gefolgsam sind die Schafe wirklich?
Bei einer Lieferung von Taurus-Raketen, die von Deutschen gesteuert werden müssen, könnte es vielleicht gelingen, die Krim-Brücke zu zerstören. Den Kriegsverlauf würde das jedoch nicht beeinflussen. Russland gewinnt so oder so. Im Gegenteil, die Folgen für Deutschland würden den dort möglicherweise angerichteten Schaden bei weitem übertreffen.
Während ich schreibe kommt gerade auf RT DE (aufgrund der „Pressefreiheit“ verzichtet man derzeit offiziell auf diesen Sender) folgende Meldung rein: Russisches Außenministerium: Taurus-Einsatz bedeutet deutsche Kriegsbeteiligung.
https://rtde.site/international/242696-russisches-aussenministerium-taurus-einsatz-bedeutet/
Es ist nicht nachvollziehbar, dass Merz offensichtlich nicht in der Lage ist anzuerkennen, dass Russland über Oreschnik-Raketen verfügt. Er scheint nicht in der Lage zu sein, die möglichen Folgen einschätzen zu können. Genau so wenig wie Pistorius. Die beiden kommen einem vor, wie zwei, die sich im stockfinsteren Wald verirrt haben und sich gegenseitig Mut zusprechen.
Nach wie vor gibt es keine fundierten Beweise dafür, dass Russland die Absicht hat, Deutschland auf unschöne Weise bereisen zu wollen. Das kann nicht oft genug gesagt werden.
Wie schon vor dem Ukraine-Konflikt, durch ein ständiges mit der NATO-Osterweiterung Russland-immer-näher-auf-die-Pelle-rücken, streut jetzt Europa, Deutschland, der Kriegskanzler Salz in die Wunde und Russland sagt ständig: Stoy, so geht das nicht!
Wenn wir eine Bedrohungslage haben, dann die, dass das aktuelle Regime den Deutschen in seinem Wehrwahn mit Wehrpflicht und einer bevorstehenden russischen Invasion droht, obwohl es, man kann es wirklich nicht oft genug sagen, keine reale Bedrohung durch Russland gibt.
In einem Interview im deutschen Propaganda-Funk faselt Pistorius davon, dass in einem „Schnuppercamp der Bundesmarine“ in Kiel für Teenager ab 16 Jahre, er gar nichts Verwerfliches daran finden kann. „Die schießen ja nicht…“, „Wir bringen ihnen ja nicht das Töten bei mit 17, sondern wir bereiten sie vor auf eine Ausbildung zum Soldaten. Und Soldat ist ein sehr ehrenwerter Beruf, der nämlich dazu dient, unsere Freiheit und Sicherheit im Ernstfall zu verteidigen.“ Dass diese Verteidigung tödlich enden kann, wird hier verschwiegen. Das könnte schließlich Teile der Soldaten verunsichern.
Ein Politikwissenschaftler regt sich über den Titel eines Liedes auf:
-Da stört sich doch tatsächlich jemand an der Liedzeile „Meine Söhne geb‘ ich nicht“-
https://www.nachdenkseiten.de/?p=131733
Man hat das Gefühl, dass alle Politiker, statt wie Obelix in den Zaubertrank, in ein Fass Teflon-Lack gefallen sind. Anders ist es nicht zu erklären, warum die Realität so perfekt an ihnen abperlt.
Wir werden immer mehr in die Enge getrieben. Und man weiß nicht, was im Zuge der digitalisierten Überwachung, die auch in Russland kräftig Fahrt aufnimmt, zwischen den USA und Russland sonst noch ausgehandelt wird. Auch, wenn Vance derzeit von UK-Premier Keir Starmer fordert, er müsse die Gesetze gegen „Hassrede“ aufheben, um ein Handelsabkommen mit den USA zu erzielen, und das eine Vorankündigung auf die Verhandlungen mit der EU sein könnte, (Bedingung: Abschaffung des Digital Services Act). In den USA gibt es Tech-Giganten, wie Musk und Thiel und Konsorten, die mit Umlegen eines Schalters, den derzeit augenscheinlichen Kampf für Meinungsfreiheit und Freiheit der Bürger, im Handumdrehen ins Gegenteil verqueren können. Dann sind wir in Null Komma Nichts in der Versklavung mit einem Totalitarismus und einer Technokratie gelandet, in der sich Georg Orwells „1984“ wie eine Gute-Nacht-Geschichte für kleine Kinder anhört.
Dieser Artikel wurde mit dem Pareto-Client geschrieben
-
 @ bc52210b:20bfc6de
2025-03-25 20:17:22
@ bc52210b:20bfc6de
2025-03-25 20:17:22CISA, or Cross-Input Signature Aggregation, is a technique in Bitcoin that allows multiple signatures from different inputs in a transaction to be combined into a single, aggregated signature. This is a big deal because Bitcoin transactions often involve multiple inputs (e.g., spending from different wallet outputs), each requiring its own signature. Normally, these signatures take up space individually, but CISA compresses them into one, making transactions more efficient.
This magic is possible thanks to the linearity property of Schnorr signatures, a type of digital signature introduced to Bitcoin with the Taproot upgrade. Unlike the older ECDSA signatures, Schnorr signatures have mathematical properties that allow multiple signatures to be added together into a single valid signature. Think of it like combining multiple handwritten signatures into one super-signature that still proves everyone signed off!
Fun Fact: CISA was considered for inclusion in Taproot but was left out to keep the upgrade simple and manageable. Adding CISA would’ve made Taproot more complex, so the developers hit pause on it—for now.
CISA vs. Key Aggregation (MuSig, FROST): Don’t Get Confused! Before we go deeper, let’s clear up a common mix-up: CISA is not the same as protocols like MuSig or FROST. Here’s why:
- Signature Aggregation (CISA): Combines multiple signatures into one, each potentially tied to different public keys and messages (e.g., different transaction inputs).
- Key Aggregation (MuSig, FROST): Combines multiple public keys into a single aggregated public key, then generates one signature for that key.
Key Differences: 1. What’s Aggregated? * CISA: Aggregates signatures. * Key Aggregation: Aggregates public keys. 2. What the Verifier Needs * CISA: The verifier needs all individual public keys and their corresponding messages to check the aggregated signature. * Key Aggregation: The verifier only needs the single aggregated public key and one message. 3. When It Happens * CISA: Used during transaction signing, when inputs are being combined into a transaction. * MuSig: Used during address creation, setting up a multi-signature (multisig) address that multiple parties control.
So, CISA is about shrinking signature data in a transaction, while MuSig/FROST are about simplifying multisig setups. Different tools, different jobs!
Two Flavors of CISA: Half-Agg and Full-Agg CISA comes in two modes:
- Full Aggregation (Full-Agg): Interactive, meaning signers need to collaborate during the signing process. (We’ll skip the details here since the query focuses on Half-Agg.)
- Half Aggregation (Half-Agg): Non-interactive, meaning signers can work independently, and someone else can combine the signatures later.
Since the query includes “CISA Part 2: Half Signature Aggregation,” let’s zoom in on Half-Agg.
Half Signature Aggregation (Half-Agg) Explained How It Works Half-Agg is a non-interactive way to aggregate Schnorr signatures. Here’s the process:
- Independent Signing: Each signer creates their own Schnorr signature for their input, without needing to talk to the other signers.
- Aggregation Step: An aggregator (could be anyone, like a wallet or node) takes all these signatures and combines them into one aggregated signature.
A Schnorr signature has two parts:
- R: A random point (32 bytes).
- s: A scalar value (32 bytes).
In Half-Agg:
- The R values from each signature are kept separate (one per input).
- The s values from all signatures are combined into a single s value.
Why It Saves Space (~50%) Let’s break down the size savings with some math:
Before Aggregation: * Each Schnorr signature = 64 bytes (32 for R + 32 for s). * For n inputs: n × 64 bytes.
After Half-Agg: * Keep n R values (32 bytes each) = 32 × n bytes. * Combine all s values into one = 32 bytes. * Total size: 32 × n + 32 bytes.
Comparison:
- Original: 64n bytes.
- Half-Agg: 32n + 32 bytes.
- For large n, the “+32” becomes small compared to 32n, so it’s roughly 32n, which is half of 64n. Hence, ~50% savings!
Real-World Impact: Based on recent Bitcoin usage, Half-Agg could save:
- ~19.3% in space (reducing transaction size).
- ~6.9% in fees (since fees depend on transaction size). This assumes no major changes in how people use Bitcoin post-CISA.
Applications of Half-Agg Half-Agg isn’t just a cool idea—it has practical uses:
- Transaction-wide Aggregation
- Combine all signatures within a single transaction.
- Result: Smaller transactions, lower fees.
- Block-wide Aggregation
- Combine signatures across all transactions in a Bitcoin block.
- Result: Even bigger space savings at the blockchain level.
- Off-chain Protocols / P2P
- Use Half-Agg in systems like Lightning Network gossip messages.
- Benefit: Efficiency without needing miners or a Bitcoin soft fork.
Challenges with Half-Agg While Half-Agg sounds awesome, it’s not without hurdles, especially at the block level:
- Breaking Adaptor Signatures
- Adaptor signatures are special signatures used in protocols like Discreet Log Contracts (DLCs) or atomic swaps. They tie a signature to revealing a secret, ensuring fair exchanges.
-
Aggregating signatures across a block might mess up these protocols, as the individual signatures get blended together, potentially losing the properties adaptor signatures rely on.
-
Impact on Reorg Recovery
- In Bitcoin, a reorganization (reorg) happens when the blockchain switches to a different chain of blocks. Transactions from the old chain need to be rebroadcast or reprocessed.
- If signatures are aggregated at the block level, it could complicate extracting individual transactions and their signatures during a reorg, slowing down recovery.
These challenges mean Half-Agg needs careful design, especially for block-wide use.
Wrapping Up CISA is a clever way to make Bitcoin transactions more efficient by aggregating multiple Schnorr signatures into one, thanks to their linearity property. Half-Agg, the non-interactive mode, lets signers work independently, cutting signature size by about 50% (to 32n + 32 bytes from 64n bytes). It could save ~19.3% in space and ~6.9% in fees, with uses ranging from single transactions to entire blocks or off-chain systems like Lightning.
But watch out—block-wide Half-Agg could trip up adaptor signatures and reorg recovery, so it’s not a slam dunk yet. Still, it’s a promising tool for a leaner, cheaper Bitcoin future!
-
 @ e3ba5e1a:5e433365
2025-04-15 11:03:15
@ e3ba5e1a:5e433365
2025-04-15 11:03:15Prelude
I wrote this post differently than any of my others. It started with a discussion with AI on an OPSec-inspired review of separation of powers, and evolved into quite an exciting debate! I asked Grok to write up a summary in my overall writing style, which it got pretty well. I've decided to post it exactly as-is. Ultimately, I think there are two solid ideas driving my stance here:
- Perfect is the enemy of the good
- Failure is the crucible of success
Beyond that, just some hard-core belief in freedom, separation of powers, and operating from self-interest.
Intro
Alright, buckle up. I’ve been chewing on this idea for a while, and it’s time to spit it out. Let’s look at the U.S. government like I’d look at a codebase under a cybersecurity audit—OPSEC style, no fluff. Forget the endless debates about what politicians should do. That’s noise. I want to talk about what they can do, the raw powers baked into the system, and why we should stop pretending those powers are sacred. If there’s a hole, either patch it or exploit it. No half-measures. And yeah, I’m okay if the whole thing crashes a bit—failure’s a feature, not a bug.
The Filibuster: A Security Rule with No Teeth
You ever see a firewall rule that’s more theater than protection? That’s the Senate filibuster. Everyone acts like it’s this untouchable guardian of democracy, but here’s the deal: a simple majority can torch it any day. It’s not a law; it’s a Senate preference, like choosing tabs over spaces. When people call killing it the “nuclear option,” I roll my eyes. Nuclear? It’s a button labeled “press me.” If a party wants it gone, they’ll do it. So why the dance?
I say stop playing games. Get rid of the filibuster. If you’re one of those folks who thinks it’s the only thing saving us from tyranny, fine—push for a constitutional amendment to lock it in. That’s a real patch, not a Post-it note. Until then, it’s just a vulnerability begging to be exploited. Every time a party threatens to nuke it, they’re admitting it’s not essential. So let’s stop pretending and move on.
Supreme Court Packing: Because Nine’s Just a Number
Here’s another fun one: the Supreme Court. Nine justices, right? Sounds official. Except it’s not. The Constitution doesn’t say nine—it’s silent on the number. Congress could pass a law tomorrow to make it 15, 20, or 42 (hitchhiker’s reference, anyone?). Packing the court is always on the table, and both sides know it. It’s like a root exploit just sitting there, waiting for someone to log in.
So why not call the bluff? If you’re in power—say, Trump’s back in the game—say, “I’m packing the court unless we amend the Constitution to fix it at nine.” Force the issue. No more shadowboxing. And honestly? The court’s got way too much power anyway. It’s not supposed to be a super-legislature, but here we are, with justices’ ideologies driving the bus. That’s a bug, not a feature. If the court weren’t such a kingmaker, packing it wouldn’t even matter. Maybe we should be talking about clipping its wings instead of just its size.
The Executive Should Go Full Klingon
Let’s talk presidents. I’m not saying they should wear Klingon armor and start shouting “Qapla’!”—though, let’s be real, that’d be awesome. I’m saying the executive should use every scrap of power the Constitution hands them. Enforce the laws you agree with, sideline the ones you don’t. If Congress doesn’t like it, they’ve got tools: pass new laws, override vetoes, or—here’s the big one—cut the budget. That’s not chaos; that’s the system working as designed.
Right now, the real problem isn’t the president overreaching; it’s the bureaucracy. It’s like a daemon running in the background, eating CPU and ignoring the user. The president’s supposed to be the one steering, but the administrative state’s got its own agenda. Let the executive flex, push the limits, and force Congress to check it. Norms? Pfft. The Constitution’s the spec sheet—stick to it.
Let the System Crash
Here’s where I get a little spicy: I’m totally fine if the government grinds to a halt. Deadlock isn’t a disaster; it’s a feature. If the branches can’t agree, let the president veto, let Congress starve the budget, let enforcement stall. Don’t tell me about “essential services.” Nothing’s so critical it can’t take a breather. Shutdowns force everyone to the table—debate, compromise, or expose who’s dropping the ball. If the public loses trust? Good. They’ll vote out the clowns or live with the circus they elected.
Think of it like a server crash. Sometimes you need a hard reboot to clear the cruft. If voters keep picking the same bad admins, well, the country gets what it deserves. Failure’s the best teacher—way better than limping along on autopilot.
States Are the Real MVPs
If the feds fumble, states step up. Right now, states act like junior devs waiting for the lead engineer to sign off. Why? Federal money. It’s a leash, and it’s tight. Cut that cash, and states will remember they’re autonomous. Some will shine, others will tank—looking at you, California. And I’m okay with that. Let people flee to better-run states. No bailouts, no excuses. States are like competing startups: the good ones thrive, the bad ones pivot or die.
Could it get uneven? Sure. Some states might turn into sci-fi utopias while others look like a post-apocalyptic vidya game. That’s the point—competition sorts it out. Citizens can move, markets adjust, and failure’s a signal to fix your act.
Chaos Isn’t the Enemy
Yeah, this sounds messy. States ignoring federal law, external threats poking at our seams, maybe even a constitutional crisis. I’m not scared. The Supreme Court’s there to referee interstate fights, and Congress sets the rules for state-to-state play. But if it all falls apart? Still cool. States can sort it without a babysitter—it’ll be ugly, but freedom’s worth it. External enemies? They’ll either unify us or break us. If we can’t rally, we don’t deserve the win.
Centralizing power to avoid this is like rewriting your app in a single thread to prevent race conditions—sure, it’s simpler, but you’re begging for a deadlock. Decentralized chaos lets states experiment, lets people escape, lets markets breathe. States competing to cut regulations to attract businesses? That’s a race to the bottom for red tape, but a race to the top for innovation—workers might gripe, but they’ll push back, and the tension’s healthy. Bring it—let the cage match play out. The Constitution’s checks are enough if we stop coddling the system.
Why This Matters
I’m not pitching a utopia. I’m pitching a stress test. The U.S. isn’t a fragile porcelain doll; it’s a rugged piece of hardware built to take some hits. Let it fail a little—filibuster, court, feds, whatever. Patch the holes with amendments if you want, or lean into the grind. Either way, stop fearing the crash. It’s how we debug the republic.
So, what’s your take? Ready to let the system rumble, or got a better way to secure the code? Hit me up—I’m all ears.
-
 @ b17fccdf:b7211155
2025-03-25 11:23:36
@ b17fccdf:b7211155
2025-03-25 11:23:36Si vives en España, quizás hayas notado que no puedes acceder a ciertas páginas webs durante los fines de semana o en algunos días entre semana, entre ellas, la guía de MiniBolt.
Esto tiene una razón, por supuesto una solución, además de una conclusión. Sin entrar en demasiados detalles:
La razón
El bloqueo a Cloudflare, implementado desde hace casi dos meses por operadores de Internet (ISPs) en España (como Movistar, O2, DIGI, Pepephone, entre otros), se basa en una orden judicial emitida tras una demanda de LALIGA (Fútbol). Esta medida busca combatir la piratería en España, un problema que afecta directamente a dicha organización.
Aunque la intención original era restringir el acceso a dominios específicos que difundieran dicho contenido, Cloudflare emplea el protocolo ECH (Encrypted Client Hello), que oculta el nombre del dominio, el cual antes se transmitía en texto plano durante el proceso de establecimiento de una conexión TLS. Esta medida dificulta que las operadoras analicen el tráfico para aplicar bloqueos basados en dominios, lo que les obliga a recurrir a bloqueos más amplios por IP o rangos de IP para cumplir con la orden judicial.
Esta práctica tiene consecuencias graves, que han sido completamente ignoradas por quienes la ejecutan. Es bien sabido que una infraestructura de IP puede alojar numerosos dominios, tanto legítimos como no legítimos. La falta de un "ajuste fino" en los bloqueos provoca un perjuicio para terceros, restringiendo el acceso a muchos dominios legítimos que no tiene relación alguna con actividades ilícitas, pero que comparten las mismas IPs de Cloudflare con dominios cuestionables. Este es el caso de la web de MiniBolt y su dominio
minibolt.info, los cuales utilizan Cloudflare como proxy para aprovechar las medidas de seguridad, privacidad, optimización y servicios adicionales que la plataforma ofrece de forma gratuita.Si bien este bloqueo parece ser temporal (al menos durante la temporada 24/25 de fútbol, hasta finales de mayo), es posible que se reactive con el inicio de la nueva temporada.

La solución
Obviamente, MiniBolt no dejará de usar Cloudflare como proxy por esta razón. Por lo que a continuación se exponen algunas medidas que como usuario puedes tomar para evitar esta restricción y poder acceder:
~> Utiliza una VPN:
Existen varias soluciones de proveedores de VPN, ordenadas según su reputación en privacidad: - IVPN - Mullvad VPN - Proton VPN (gratis) - Obscura VPN (solo para macOS) - Cloudfare WARP (gratis) + permite utilizar el modo proxy local para enrutar solo la navegación, debes utilizar la opción "WARP a través de proxy local" siguiendo estos pasos: 1. Inicia Cloudflare WARP y dentro de la pequeña interfaz haz click en la rueda dentada abajo a la derecha > "Preferencias" > "Avanzado" > "Configurar el modo proxy" 2. Marca la casilla "Habilite el modo proxy en este dispositivo" 3. Elige un "Puerto de escucha de proxy" entre 0-65535. ej: 1080, haz click en "Aceptar" y cierra la ventana de preferencias 4. Accede de nuevo a Cloudflare WARP y pulsa sobre el switch para habilitar el servicio. 3. Ahora debes apuntar el proxy del navegador a Cloudflare WARP, la configuración del navegador es similar a esta para el caso de navegadores basados en Firefox. Una vez hecho, deberías poder acceder a la guía de MiniBolt sin problemas. Si tienes dudas, déjalas en comentarios e intentaré resolverlas. Más info AQUÍ.

~> Proxifica tu navegador para usar la red de Tor, o utiliza el navegador oficial de Tor (recomendado).

La conclusión
Estos hechos ponen en tela de juicio los principios fundamentales de la neutralidad de la red, pilares esenciales de la Declaración de Independencia del Ciberespacio que defiende un internet libre, sin restricciones ni censura. Dichos principios se han visto quebrantados sin precedentes en este país, confirmando que ese futuro distópico que muchos negaban, ya es una realidad.
Es momento de actuar y estar preparados: debemos impulsar el desarrollo y la difusión de las herramientas anticensura que tenemos a nuestro alcance, protegiendo así la libertad digital y asegurando un acceso equitativo a la información para todos
Este compromiso es uno de los pilares fundamentales de MiniBolt, lo que convierte este desafío en una oportunidad para poner a prueba las soluciones anticensura ya disponibles, así como las que están en camino.
¡Censúrame si puedes, legislador! ¡La lucha por la privacidad y la libertad en Internet ya está en marcha!

Fuentes: * https://bandaancha.eu/articulos/movistar-o2-deja-clientes-sin-acceso-11239 * https://bandaancha.eu/articulos/esta-nueva-sentencia-autoriza-bloqueos-11257 * https://bandaancha.eu/articulos/como-saltarse-bloqueo-webs-warp-vpn-9958 * https://bandaancha.eu/articulos/como-activar-ech-chrome-acceder-webs-10689 * https://comunidad.movistar.es/t5/Soporte-Fibra-y-ADSL/Problema-con-web-que-usan-Cloudflare/td-p/5218007
-
 @ 3b7fc823:e194354f
2025-03-23 03:54:16
@ 3b7fc823:e194354f
2025-03-23 03:54:16A quick guide for the less than technical savvy to set up their very own free private tor enabled email using Onionmail. Privacy is for everyone, not just the super cyber nerds.
Onion Mail is an anonymous POP3/SMTP email server program hosted by various people on the internet. You can visit this site and read the details: https://en.onionmail.info/
- Download Tor Browser
First, if you don't already, go download Tor Browser. You are going to need it. https://www.torproject.org/
- Sign Up
Using Tor browser go to the directory page (https://onionmail.info/directory.html) choose one of the servers and sign up for an account. I say sign up but it is just choosing a user name you want to go before the @xyz.onion email address and solving a captcha.
- Account information
Once you are done signing up an Account information page will pop up. MAKE SURE YOU SAVE THIS!!! It has your address and passwords (for sending and receiving email) that you will need. If you lose them then you are shit out of luck.
- Install an Email Client
You can use Claws Mail, Neomutt, or whatever, but for this example, we will be using Thunderbird.
a. Download Thunderbird email client
b. The easy setup popup page that wants your name, email, and password isn't going to like your user@xyz.onion address. Just enter something that looks like a regular email address such as name@example.com and the Configure Manuallyoption will appear below. Click that.
- Configure Incoming (POP3) Server
Under Incoming Server: Protocol: POP3 Server or Hostname: xyz.onion (whatever your account info says) Port: 110 Security: STARTTLS Authentication: Normal password Username: (your username) Password: (POP3 password).
- Configure Outgoing (SMTP) Server
Under Outgoing Server: Server or Hostname: xyz.onion (whatever your account info says) Port: 25 Security: STARTTLS Authentication: Normal password Username: (your username) Password: (SMTP password).
-
Click on email at the top and change your address if you had to use a spoof one to get the configure manually to pop up.
-
Configure Proxy
a. Click the gear icon on the bottom left for settings. Scroll all the way down to Network & Disk Space. Click the settings button next to Connection. Configure how Thunderbird connects to the internet.
b. Select Manual Proxy Configuration. For SOCKS Host enter 127.0.0.1 and enter port 9050. (if you are running this through a VM the port may be different)
c. Now check the box for SOCKS5 and then Proxy DNS when using SOCKS5 down at the bottom. Click OK
- Check Email
For thunderbird to reach the onion mail server it has to be connected to tor. Depending on your local setup, it might be fine as is or you might have to have tor browser open in the background. Click on inbox and then the little cloud icon with the down arrow to check mail.
- Security Exception
Thunderbird is not going to like that the onion mail server security certificate is self signed. A popup Add Security Exception will appear. Click Confirm Security Exception.
You are done. Enjoy your new private email service.
REMEMBER: The server can read your emails unless they are encrypted. Go into account settings. Look down and click End-toEnd Encryption. Then add your OpenPGP key or open your OpenPGP Key Manager (you might have to download one if you don't already have one) and generate a new key for this account.
-
 @ 7ef5f1b1:0e0fcd27
2025-04-22 17:26:44
@ 7ef5f1b1:0e0fcd27
2025-04-22 17:26:44A monthly newsletter by The 256 Foundation

April 2025
Introduction:
Welcome to the fourth newsletter produced by The 256 Foundation! March was an action-packed month with events ranging from the announcement of TSMC investing in US fabs to four solo block finds. Dive in to catch up on the latest news, mining industry developments, progress updates on grant projects, Actionable Advice on updating a Futurebit Apollo I to the latest firmware, and the current state of the Bitcoin network.
[IMG-001] Variation of the “I’m the captain now” meme by @maxisclub
Definitions:
MA = Moving Average
Eh/s = Exahash per second
Ph/s = Petahash per second
Th/s = Terahash per second
T = Trillion
J/Th = Joules per Terahash
$ = US Dollar
OS = Operating System
SSD = Solid State Drive
TB = Terabyte
News:
March 3, Ashigaru releases v1.1.1. Notable because this fork of Samourai Wallet serves as the remaining choice of mobile Bitcoin wallet capable of making peer to peer collaborative transactions. Not the Whirlpool transactions that Samourai Wallet was well-known for but the Stowaway and StonewallX2 p2p CoinJoin transactions. The persistence of Samourai’s tools still working despite the full force of the State coming down on the developers is a testament to the power of open-source code.
March 3, Stronghold completes cleanup of decommissioned coal plant using Bitcoin miners. Stronghold’s initiative counters the narrative that Bitcoin mining is wasteful by removing 150,000 tons of coal waste, part of a broader effort that cleared 240,000 tons in Q2 2024 alone. Waste coal piles in Pennsylvania, like the one in Russellton, have scarred landscapes, making this reclamation a significant step for local ecosystems. The project aligns with growing efforts in the region, as The Nature Conservancy also leads restoration projects in Pennsylvania to revive forests and waters. Stronghold’s dual-use model—powering Bitcoin miners and supplying the grid—shows how Bitcoin mining can support environmental goals while remaining economically viable.
March 3, five TSMC semiconductor fabs coming to Arizona. TSMC’s $100 billion investment in Arizona reflects a strategic push to bolster U.S. semiconductor production amid global supply chain vulnerabilities and geopolitical tensions, particularly with West Taiwan’s claims over Taiwan. TSMC’s existing $65 billion investment in Phoenix, now totaling $165 billion, aims to create 40,000 construction jobs and tens of thousands of high-tech roles over the next decade. This could relieve bottlenecks in ASIC chip supply if Bitcoin mining chip designers can get access to the limited foundry space. If that is the case, this could help alleviate some centralization concerns as it relates to a majority of Bitcoin mining chips coming from Taiwan and West Taiwan.
March 10, Block #887212 solved by a Bitaxe Ultra with ~491Gh/s. Not only did the Bitaxe satisfy the network difficulty, which was 112.15T, but obliterated it with a whopping 719.9T difficulty. This Block marked the second one solved by a Bitaxe and an increasing number of solo block finds overall as more individuals choose to play the Bitcoin lottery with their hashrate.
March 12, Pirate Bay co-founder, Carl Lundström, killed in plane crash. The Pirate Bay, launched in 2003, revolutionized online file-sharing by popularizing BitTorrent technology, enabling millions to access music, movies, and software, often in defiance of legal systems, which led to Lundström’s 2009 conviction for copyright infringement. The timing of his death coincides with ongoing global debates over digital ownership and intellectual property, often echoing many of the same themes in open-source technology, underscoring the enduring impact of The Pirate Bay’s challenge to traditional media distribution models.
March 18, Samourai Wallet status conference update. This was a short meeting in which the dates for the remaining pre-trial hearings was discussed.
- May 9, Opening Motion. - June 6, prosecution response to the opening motion. - June 20, defense replies to the prosecution response. - July 15, prosecution provides expert disclosure - August 8, defense provides expert disclosure - Tdev is able to remain home during the remaining pre-trial hearings so that he doesn’t have to incur the expenses traveling back and forth between Europe and the USDespite seemingly positive shifts in crypto-related policies from the Trump administration, all signs point to the prosecution still moving full steam ahead in this case. The defense teams need to be prepared and they could use all the financial help they can get. If you feel compelled to support the legal defense fund, please do so here. If the DOJ wins this case, all Bitcoiners lose.
March 18, DEMAND POOL launches, transitioning out of stealth mode and making room for applicants to join the private waiting list to be one of the Founding Miners.
Key features of DEMAND Pool include: • Build your own blocks • SLICE payment system & new mempool algorithm • No more empty blocks • End-to-end encryption for protection • Efficient data transfer, less wasted hashrate • Lower costs on CPU, bandwidth, & time
DEMAND Pool implements Stratum v2 so that miners can generate their own block templates, entering the arena of pools trying to decentralize mining such as OCEAN with their alternative to Stratum v2 called DATUM. A benefit of the Stratum v2 protocol over Stratum v1 is that data sent between the miner and the pool is now encrypted whereas before it was sent in clear-text, the encryption helps with network level privacy so that for example, your Internet Service Provider cannot read what is in the data being passed back and forth. Although, unless there is a proxy between your miner and the pool then the ISP may be able to determine that you are sending data to a mining pool, they just wouldn’t be able to tell what’s in that data. Overall, decentralization has become a buzz word lately and while it is a step in the right direction that more pools are enabling miners to decide which transactions are included in the block templates they work on, the pools remain a centralized force that ultimately can reject templates based on a number of reasons.
March 20, Bitaxe makes the cover of Bitcoin Magazine’s The Mining Issue, solidifying the Bitaxe as a pop-culture icon. Even those who disregard the significance of the Bitaxe project must recognize that the project’s popularity is an indication that something big is developing here.
 [IMG-002] Bitcoin Magazine, The Mining Issue
[IMG-002] Bitcoin Magazine, The Mining IssueMarch 21, self-hosted solo miner solves block #888737 with a Futurebit Apollo, making this the third solo block find for Futurebit. The first Futurebit Apollo block find may have been a fluke, the second a coincidence, but the third is an indication of a pattern forming here. More hashrate is being controlled by individuals who are constructing their own blocks and this trend will accelerate as time goes on and deploying these devices becomes easier and less expensive. This was the second solo block found in March.
March 21, US Treasury Department lifts sanctions on Tornado Cash. This is a positive sign coming from the US Treasury, however the charges against the Tornado Cash developer, Roman Storm, still stand and his legal defense team is still fighting an uphill battle. Even though the US Treasury removed Tornado Cash from the OFAC list, the department is attempting to stop a Texas court from granting a motion that would ensure the Treasury can’t put Tornado Cash back on the OFAC list. Meanwhile, the other Tornado Cash developer, Alex Pertsev, is fighting his appeal battle in the Dutch courts.
March 22, Self-hosted Public Pool user mines Block #888989. This was the first block mined with the Public Pool software, which is open-source and available for anyone to host themselves, in this case hosted on the user’s Umbrel. If you read the January issue of The 256 Foundation newsletter, there are detailed instructions for hosting your own instance of Public Pool on a Raspberry Pi. Easier solutions exist and accomplish the same thing such as Umbrel and Start9. This was the third solo block mined in March.
March 26, DeFi Education Fund publishes coalition letter urging congress to correct the DOJ’s dangerous misinterpretation of money transmission laws. In their own words: “First seen in Aug 2023 via the criminal indictment of @rstormsf, the DOJ’s novel legal theory expands criminal liability to software developers, ignoring longstanding FinCEN guidance and threatening the entire U.S. blockchain & digital asset ecosystem”. Many familiar organizations in the industry signed the letter, such as Coinbase, Kraken, A16z Crypto, and Ledger. Sadly, no Bitcoin companies signed the letter, highlighting the reckless ignorance prevalent among the “toxic Bitcoin maximalists” who often pride themselves on their narrow focus; a focus which is proving to be more of a blind spot limiting their ability to recognize a clear and present threat. The full letter text can be found here.
March 28, Heatbit reveals the black Heatbit, an elegant space heater that mines Bitcoin. Heat re-use applications such as Bitcoin mining space heaters are one of many examples where energy spent on generating heat can also earn the user sats. Other popular solutions include heating hot tubs, hotels, drive ways, and more. The innovations in this area will continue to be unlocked as open-source solutions like the ones being developed at The 256 Foundation are released and innovators gain more control over their applications.
March 29, miner with 2.5Ph/s solves Block #889975 with Solo CK Pool, marking the fourth solo block found in the month of March. This was the first solo block found on CK Pool’s European server. This was a good way to finish the month on a strong note for small-scale miners.
Free & Open Mining Industry Developments:
The development will not stop until Bitcoin mining is free and open. Innovators didn’t let off the gas in March, here are eleven note-worthy events:
0) @BTC_Grid demonstrates heating a new residential build with Bitcoin miners. This custom build features 6,000 square feet of radiant floors, 1,500 sqft of snow melting slab, 2 heated pools, all powered by Bitcoin miners and fully automated. Innovations and efficient systems like this will become more common as Bitcoin mining hardware and firmware solutions become open-source
1) @DrydeGab shares The Ocho, a Bitaxe Nerd Octaxe open-source Bitcoin miner featuring 8x BM1370 ASICs that performs at 9-10Th/s consuming ~180W. The Ocho runs on it’s own custom AxeOS. Currently out of stock but generally available for purchase in the IX Tech store.
 [IMG-003] The Nerd OCTAXE Ocho by @DrydeGab
[IMG-003] The Nerd OCTAXE Ocho by @DrydeGab2) @incognitojohn23 demonstrates building a Bitaxe from scratch with no prior experience, proving that anyone can access this technology with a little determination and the right community. @incognitojohn23 has also uploaded several videos documenting his progress and lessons along the way. Every builder has their first day, don’t hold back if you feel compelled to jump in and get started.
3) @HodlRev demonstrating how he combines Bitcoin mining with maple syrup production. In fact, @HodlRev has integrated Bitcoin mining into several aspects of his homestead. Be sure to follow his content for an endless stream of resourceful ideas. Once open-source Bitcoin mining firmware and hardware solutions become widely available, innovators like @HodlRev will have more control over every parameter of these unique applications.
4) ATL Bitlab announces their first hackathon, running June 7 through July 6. Promoted as “A global hackathon focused on all things bitcoin mining”. If you are interested in joining the hackathon, there is a Google form you can fill out here. It will be interesting to see what innovations come from this effort.
5) @100AcresRanch builds touchscreen dashboard for Bitaxe and Loki Boards. With this, you can control up to 10 mining devices with the ability to instantly switch any of the presets without going into the mining device UI.
 [IMG-004] Decentral Command Dashboard by @100AcresRanch
[IMG-004] Decentral Command Dashboard by @100AcresRanch6) @IxTechCrypto reveals HAXE, the newest member of the Nerdaxe miner family. HAXE is a 6 ASIC miner performing at ~7.4 Th/s at ~118W. Upon looking at the IX Tech store, it seems as though the HAXE has not hit shelves yet but keep an eye out for announcements soon.
7) Solo Satoshi reveals the NerdQaxe++, the latest marvel in the world of open-source Bitcoin mining solutions. This device is equipped with four ASIC chips from the Antminer S21 Pro and boasts an efficiency rating of 15.8 J/Th. At the advertised power consumption of 76 Watts, that would produce nearly 5 Th/s. Currently out of stock at the Solo Satoshi store and the IX Tech store but in stock and available at the PlebSource store.
8) @TheSoloMiningCo shares a bolt-on voltage regulator heatsink for the Bitaxe, this is a helpful modification when overclocking your miner and helps dissipate heat away from the voltage regulator. Many innovators are discovering ways to get every bit of efficiency they can from their hardware and sharing their ideas with the wider community for anyone to adopt.
9) @boerst adds historical data to stratum.work, a public website that monitors mining pool activity through calling for the work templates being generated for the pool’s respective miners. By parsing the information available in the work templates, a number of interesting observations can be made like which pools are merely proxies for larger pools, timing analysis of when templates are sent out, and now historical data on what the state of each pool’s templates were at a given block height. The work Boerst is doing with this website provides a great tool for gaining insights into mining centralization.
10) Braiins open-sources the BCB100 Control Board, designed to work with Antminers, this control board project has two parts: the hardware and the software. For the hardware part, open files include the Bill Of Materials, schematics, Gerbers, and CAD files. For the software part, open files include the board-level OpenWrt-based firmware with the full configuration file and the Nix environment for reproducible builds. The mining firmware binaries for bosminer and boser (same as the official Braiins OS releases) are also available to download and use to compile the image for the control board, however the Braiins OS firmware itself is not included in this open-source bundle. Braiins chose the GPLv3 open-source license for the software and the CERN-OHL-S open-source license for the hardware. This is a great gesture by Braiins and helps validate the efforts of The 256 Foundation to make Bitcoin mining free and open. The Braiins GitHub repositories where all this information can be found are accessible here and here. The 256 Foundation has plans to develop a Mujina firmware that can be flashed onto the BCB100 helping target Antminer machines.
Grant Project Updates:
In March, The 256 Foundation formalized agreements with the lead developers who were selected for each project. These agreements clearly defined the scope of each project, identified the deliverables, set a timeline, and agreement on compensation was made. Below are the outlines for each project, the compensation is not made public for privacy and security reasons.
Ember One:
@skot9000 instigator of the Bitaxe and all around legend for being the first mover in open-source Bitcoin mining solutions is the lead engineer for the Ember One project. This was the first fully funded grant from The 256 Foundation and commenced in November 2024 with a six month duration. The deliverable is a validated design for a ~100W miner with a standardized form factor (128mm x 128mm), USB-C data connection, 12-24v input voltage, with plans for several versions – each with a different ASIC chip. The First Ember One features the Bitmain BM1362 ASIC, next on the list will be an Ember One with the Intel BZM2 ASIC, then an Auradine ASIC version, and eventually a Block ASIC version. Learn more at: https://emberone.org/
Mujina Mining Firmware:
@ryankuester, embedded Linux developer and Electrical Engineer who has mastered the intersection of hardware and software over the last 20 years is the lead developer for the Mujina project, a Linux based mining firmware application with support for multiple drivers so it can be used with Ember One complete mining system. The grant starts on April 5, 2025 and continues for nine months. Deliverables include:
Core Mujina-miner Application: - Fully open-source under GPLv3 license - Written in Rust for performance, robustness, and maintainability, leveraging Rust's growing adoption in the Bitcoin ecosystem - Designed for modularity and extensibility - Stratum V1 client (which includes DATUM compatibility) - Best effort for Stratum V2 client in the initial release but may not happen until later
Hardware Support:
- Support for Ember One 00 hash boards (Bitmain chips) - Support for Ember One 01 hash boards (Intel chips) on a best effort basis but may not happen until later - Full support on the Raspberry Pi CM5 and IO board running the Raspberry Pi OS - Support for the Libre board when released - Best-effort compatibility with other hardware running LinuxManagement Interfaces:
• HTTP API for remote management and monitoring • Command-line interface for direct control • Basic web dashboard for status monitoring • Configuration via structured text files • Community Building and Infrastructure • GitHub project organization and workflow • Continuous integration and testing framework • Comprehensive user and developer documentation • Communication channels for users and developers • Community building through writing, podcasts, and conference participationThe initial release of Mujina is being built in such a way that it supports long-term goals like ultimately evolving into a complete Linux-based operating system, deployable through simple flashing procedures. Initially focused on supporting the 256 Foundation's Libre control boards and Ember hash boards, Mujina's modular architecture will eventually enable compatibility with a wide variety of mining hardware from different manufacturers. Lean more at: https://mujina.org/
Libre Board:
@Schnitzel, heat re-use maximalist who turned his home's hot water accessories into Bitcoin-powered sats generators and during the day has built a successful business with a background in product management, is the lead engineer on the Libre Board project; the control board for the Ember One complete mining system. Start date is April 5, 2025 and the deliverables after six months will be a mining control board based on the Raspberry Pi Compute Module I/O Board with at least the following connections:
• USB hub integration (maybe 10 ports?) • Support for fan connections • NVME expansion • Two 100-pin connectors for the compute module • Ethernet port • HDMI port • Raspberrypi 40-pin header for sensors, switches, & relays etc. • MIPI port for touchscreen • Accepts 12-24 VDC input power voltage.The initial release of Libre Board is being built in such a way that it supports long-term goals like alternative compute modules such as ARM, x86, and RISC-V. Learn more at: https://libreboard.org/
Hydra Pool:
@jungly, distributed systems PhD and the lead developer behind P2Pool v2 and formerly for Braidpool, now takes the reigns as lead developer for Hydra Pool, the stratum server package that will run on the Ember One mining system. Start date for this project was on April 5, 2025 and the duration lasts for six months. Deliverables include:
• Talks to bitcoind and provides stratum work to users and stores received shares • Scalable and robust database support to save received shares • Run share accounting on the stored shares • Implement payment mechanisms to pay out miners based on the share accounting • Provide two operation modes: Solo mining and PPLNS or Tides based payout mechanism, with payouts from coinbase only. (All other payout mechanism are out of scope of this initial release for now but there will be more). • Rolling upgrades: Tools and scripts to upgrade server with zero downtime. • Dashboard: Pool stats view only dashboard with support to filter miner payout addresses. • Documentation: Setup and other help pages, as required.The initial release of Hydra Pool is being built in such a way that it supports long-term goals like alternative payout models such as echash, communicating with other Hydra Pool instances, local store of shares for Ember One, and a user-friendly interface that puts controls at the user's fingertips, and supports the ability for upstream pool proxying. Learn More at: https://hydrapool.org/
Block Watcher:
Initially scoped to be a Bitcoin mining insights application built to run on the Ember One mining system using the self-hosted node for blockchain data. However, The 256 Foundation has decided to pause Block Watcher development for a number of reasons. Primarily because the other four projects were more central to the foundation’s mission and given the early stages of the Foundation with the current support level, it made more sense to deploy capital where it counts most.
Actionable Advice:
This month’s Actionable Advice column explains the process for upgrading the Futurebit Apollo I OS to the newer Apollo II OS and replacing the SSD. The Futurebit Apollo is a small mining device with an integrated Bitcoin node designed as a plug-and-play solution for people interested in mining Bitcoin without all the noise and heat of the larger industrial-grade miners. The Apollo I can hash between 2 – 4 Th/s and will consume roughly 125 – 200 Watts. The Apollo II can hash between 8 – 10 Th/s and will consume roughly 280 – 400 Watts. The motivation behind upgrading from the Apollo I OS to the Apollo II OS is the ability to run a stratum server internally so that the mining part of the device can ask the node part of the device for mining work, thus enabling users to solo mine in a self-hosted fashion. In fact, this is exactly what The 256 Foundation did during the Telehash fundraising event where Block #881423 was solo mined, at one point there was more than 1 Eh/s of hashrate pointed to that Apollo.
 [IMG-005] Futurebit Apollo I with new NVME SSD
[IMG-005] Futurebit Apollo I with new NVME SSDYou can find the complete flashing instructions on the Futurebit website here. You will need a separate computer to complete the flashing procedure. The flashing procedure will erase all data on the microSD card so back it up if you have anything valuable saved on there.
First navigate to the Futurebit GitHub Releases page at: https://github.com/jstefanop/apolloapi-v2/releases
Once there, you will see two OS images available for download, along with two links to alternative hosting options for those two images. If you are upgrading an Apollo I, you need to figure out which new OS image is right for your device, the MCU 1 image or the MCU 2 image. There are detailed instructions on figuring this out available here. There are multiple ways to determine if you need the MCU 1 or MCU 2 image. If the second to last digit in your Futurebit Apollo I is between 4 – 8 then you have an MCU 1; or if your batch number is 1 – 3 then you have an MCU 1; or if the circuit board has a 40-pin connector running perpendicular to the microSD card slot then you have an MCU 1. Otherwise, you have an MCU 2.
For example, this is what the MCU 1 circuit board will look like:
 [IMG-006] Futurebit MCU1 example
[IMG-006] Futurebit MCU1 exampleOnce you figure out which OS image you need, go ahead and download it. The SHA256 hash values for the OS Image files are presented in the GitHub repo. If you’re running Linux on your computer, you can change directory to your Download folder and run the following command to check the SHA256 hash value of the file you downloaded and compare that to the SHA256 hash values on GitHub.
 [IMG-007] Verifying Futurebit OS Image Hash Value
[IMG-007] Verifying Futurebit OS Image Hash ValueWith the hash value confirmed, you can use a program like Balena Etcher to flash your microSD card. First remove the microSD card from the Apollo circuit board by pushing it inward, it should make a small click and then spring outward so that you can grab it and remove it from the slot.
Connect the microSD card to your computer with the appropriate adapter.
Open Balena Etcher and click on the “Flash From File” button to define the file path to where you have the OS image saved:
 [IMG-008] Balena Etcher user interface
[IMG-008] Balena Etcher user interfaceThen click on the “Select Target” button to define the drive which you will be flashing. Select the microSD card and be sure not to select any other drive on your computer by mistake:
 [IMG-009] Balena Etcher user interface
[IMG-009] Balena Etcher user interfaceThen click on the “Flash” button and Balena Etcher will take care of formatting the microSD card, decompressing the OS image file, and flashing it to the microSD card.
 [IMG-010] Balena Etcher user interface.
[IMG-010] Balena Etcher user interface.The flashing process can take some time so be patient. The Balena Etcher interface will allow you to monitor the progress.
 [IMG-011] Balena Etcher user interface.
[IMG-011] Balena Etcher user interface.Once the flashing process is completed successfully, you will receive a notice in the balena Etcher interface that looks like this:
 [IMG-012] Balena Etcher user interface.
[IMG-012] Balena Etcher user interface.You can remove the microSD card from your computer now and install it back into the Futurebit Apollo. If you have an adequately sized SSD then your block chain data should be safe as that is where it resides, not on the microSD card. If you have a 1TB SSD then this would be a good time to consider upgrading to a 2TB SSD instead. There are lots of options but you want to get an NVME style one like this:
 [IMG-013] 1TB vs. 2TB NVME SSD
[IMG-013] 1TB vs. 2TB NVME SSDSimply loosen the screw holding the SSD in place and then remove the old SSD by pulling it out of the socket. Then insert the new one and put the screw back in place.
Once the SSD and microSD are back in place, you can connect Ethernet and the power supply, then apply power to your Apollo.
You will be able to access your Apollo through a web browser on your computer. You will need to figure out the local IP address of your Apollo device so log into your router and check the DHCP leases section. Your router should be accessible from your local network by typing an IP address into your web browser like 192.168.0.1 or 10.0.0.1 or maybe your router manufacturer uses a different default. You should be able to do an internet search for your specific router and figure it out quickly if you don’t already know. If that fails, you can download and run a program like Angry IP Scanner.
Give the Apollo some time to run through a few preliminary and automatic configurations, you should be able to see the Apollo on your local network within 10 minutes of powering it on.
Once you figure out the IP address for your Apollo, type it into your web browser and this is the first screen you should be greeted with:
 [IMG-014] Futurebit welcome screen
[IMG-014] Futurebit welcome screenClick on the button that says “Start setup process”. The next you will see should look like this:
 [IMG-015] Futurebit mining selection screen
[IMG-015] Futurebit mining selection screenYou have the option here to select solo mining or pooled mining. If you have installed a new SSD card then you should select pooled mining because you will not be able to solo mine until the entire Bitcoin blockchain is downloaded.
Your Apollo will automatically start downloading the Bitcoin blockchain in the background and in the mean-time you can start mining with a pool of your choice like Solo CK Pool or Public Pool or others.
Be forewarned that the Initial Blockchain Download (“IBD”) takes a long time. At the time of this writing, it took 18 days to download the entire blockchain using a Starlink internet connection, which was probably throttled at some points in the process because of the roughly 680 GB of data that it takes.
In February 2022, the IBD on this exact same device took 2 days with a cable internet connection. Maybe the Starlink was a bit of a bottleneck but most likely the extended length of the download can be attributed to all those JPEGS on the blockchain.
Otherwise, if you already have the full blockchain on your SSD then you should be able to start solo mining right away by selecting the solo mining option.
After making your selection, the Apollo will automatically run through some configurations and you should have the option to set a password somewhere in there along the way. Then you should see this page:
 [IMG-016] Futurebit setup completion page
[IMG-016] Futurebit setup completion pageClick on the “Start mining” button. Then you should be brought to your dashboard like this:
 [IMG-017] Futurebit dashboard
[IMG-017] Futurebit dashboardYou can monitor your hashrate, temperatures, and more from the dashboard. You can check on the status of your Bitcoin node by clicking on the three-circle looking icon that says “node” on the left-hand side menu.
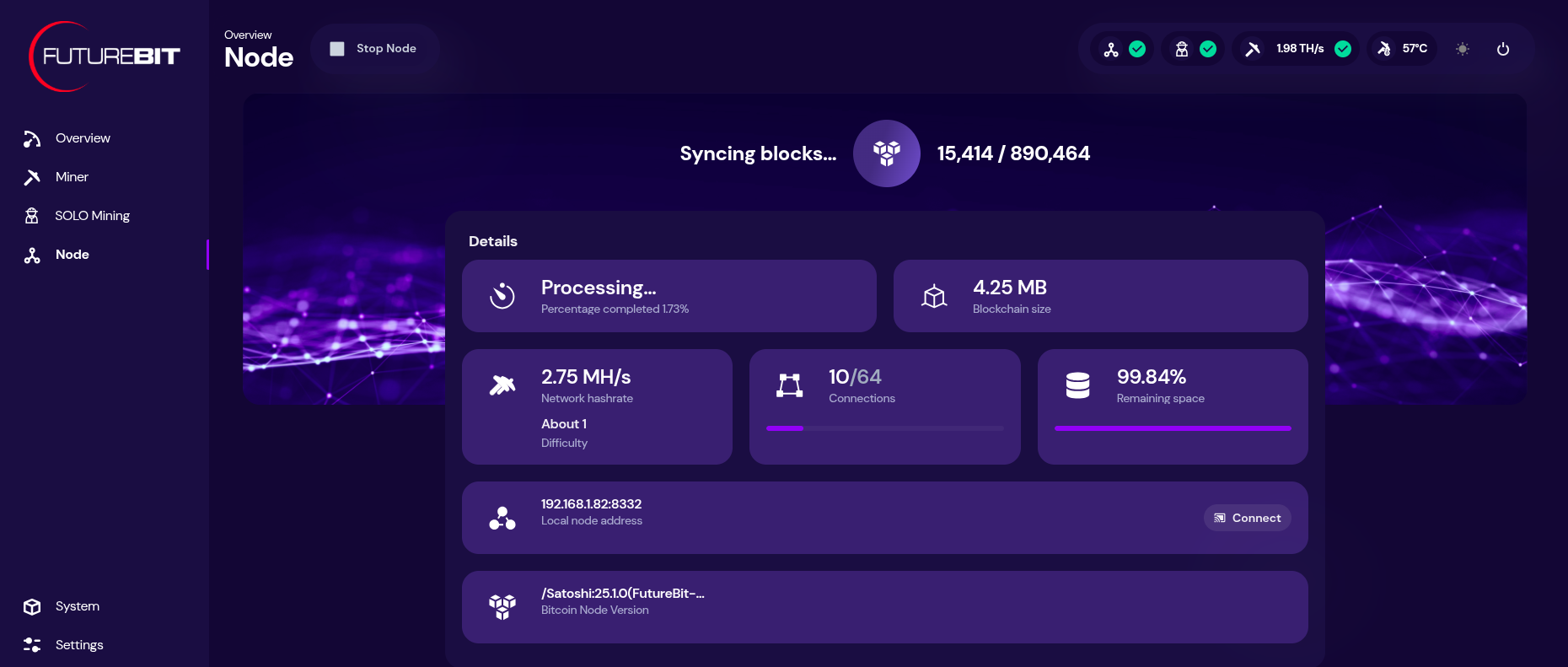 [IMG-018] Futurebit node page
[IMG-018] Futurebit node pageIf you need to update the mining pool, click on the “settings” option at the bottom of the left-hand side menu. There you will see a drop down menu for selecting a pool to use, you can select the “setup custom pool” option to insert the appropriate stratum URL and then your worker name.
Once your IBD is finished, you can start solo mining by toggling on the solo mode at the bottom of the settings page. You will have a chance to update the Bitcoin address you want to mine to. Then click on “save & restart”.
 [IMG-019] Futurebit mining pool settings
[IMG-019] Futurebit mining pool settingsThen once your system comes back up, you will see a banner at the top of the dashboard page with the IP address you can use to point any other miners you have, like Bitaxes, to your own self-hosted solo mining pool!
 [IMG-020] Futurebit solo mining dashboard
[IMG-020] Futurebit solo mining dashboardNow just sit back and enjoy watching your best shares roll in until you get one higher than the network difficulty and you mine that solo block.
State of the Network:
Hashrate on the 14-day MA according to mempool.space increased from ~793 Eh/s to ~829 Eh/s in March, marking ~4.5% growth for the month.
 [IMG-021] 2025 hashrate/difficulty chart from mempool.space
[IMG-021] 2025 hashrate/difficulty chart from mempool.spaceDifficulty was 110.57T at it’s lowest in March and 113.76T at it’s highest, which is a 2.8% increase for the month. All together for 2025 up until the end of March, difficulty has gone up ~3.6%.
According to the Hashrate Index, more efficient miners like the <19 J/Th models are fetching $17.29 per terahash, models between 19J/Th – 25J/Th are selling for $11.05 per terahash, and models >25J/Th are selling for $3.20 per terahash. Overall, prices seem to have dropped slightly over the month of March. You can expect to pay roughly $4,000 for a new-gen miner with 230+ Th/s.
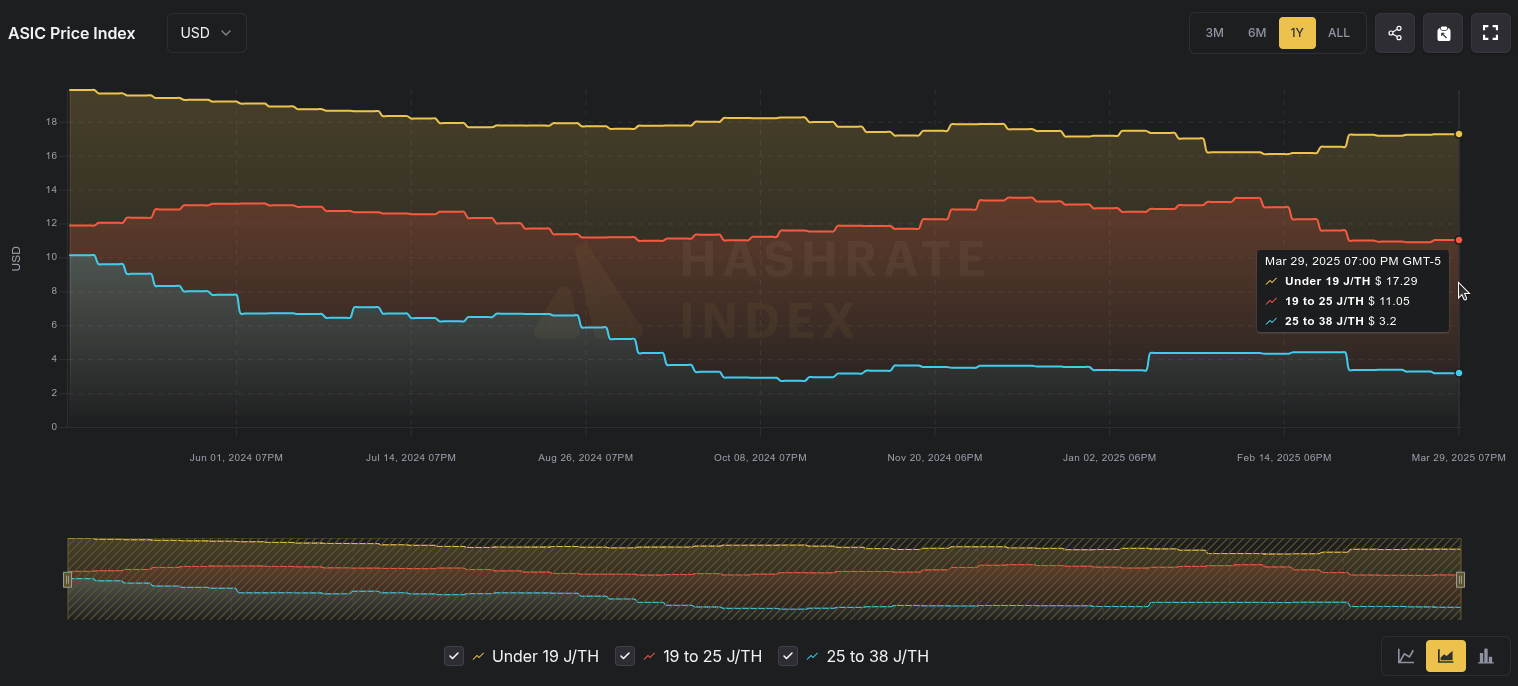 [IMG-022] Miner Prices from Luxor’s Hashrate Index
[IMG-022] Miner Prices from Luxor’s Hashrate IndexHashvalue is closed out in March at ~56,000 sats/Ph per day, relatively flat from Frebruary, according to Braiins Insights. Hashprice is $46.00/Ph per day, down from $47.00/Ph per day in February.
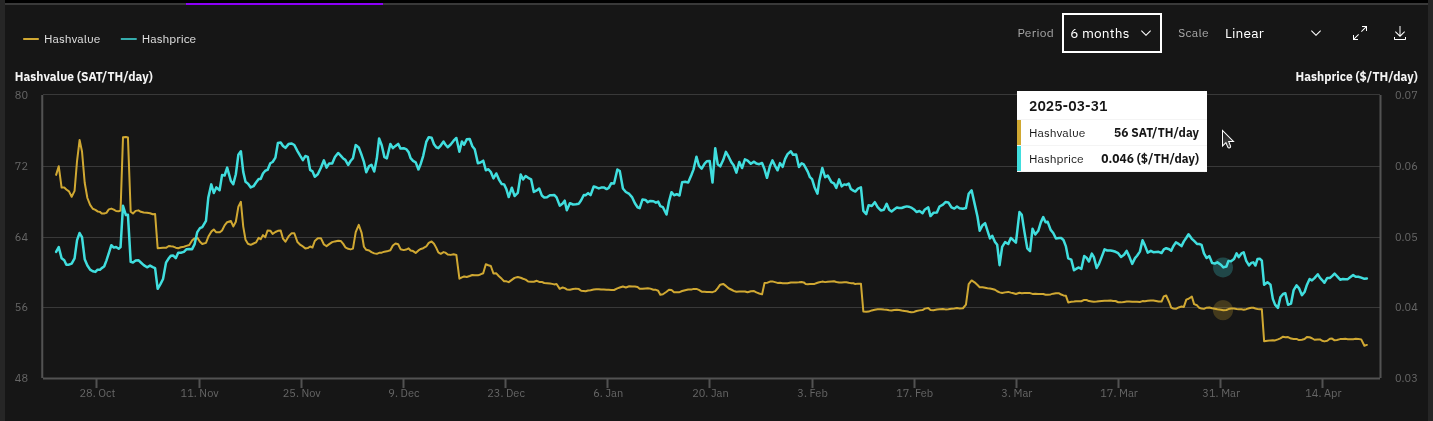 [IMG-023] Hashprice/Hashvalue from Braiins Insights
[IMG-023] Hashprice/Hashvalue from Braiins InsightsThe next halving will occur at block height 1,050,000 which should be in roughly 1,071 days or in other words ~156,850 blocks from time of publishing this newsletter.
Conclusion:
Thank you for reading the third 256 Foundation newsletter. Keep an eye out for more newsletters on a monthly basis in your email inbox by subscribing at 256foundation.org. Or you can download .pdf versions of the newsletters from there as well. You can also find these newsletters published in article form on Nostr.
If you haven’t done so already, be sure to RSVP for the Texas Energy & Mining Summit (“TEMS”) in Austin, Texas on May 6 & 7 for two days of the highest Bitcoin mining and energy signal in the industry, set in the intimate Bitcoin Commons, so you can meet and mingle with the best and brightest movers and shakers in the space.
While you’re at it, extend your stay and spend Cinco De Mayo with The 256 Foundation at our second fundraiser, Telehash #2. Everything is bigger in Texas, so set your expectations high for this one. All of the lead developers from the grant projects will be present to talk first-hand about how to dismantle the proprietary mining empire.
 IMG-024] TEMS 2025 flyer
IMG-024] TEMS 2025 flyerIf you have an old Apollo I laying around and want to get it up to date and solo mining then hopefully this newsletter helped you accomplish that.
 [IMG-026] FREE SAMOURAI
[IMG-026] FREE SAMOURAIIf you want to continue seeing developers build free and open solutions be sure to support the Samourai Wallet developers by making a tax-deductible contribution to their legal defense fund here. The first step in ensuring a future of free and open Bitcoin development starts with freeing these developers.
You can just FAFO,
-econoalchemist
-
 @ 9bde4214:06ca052b
2025-04-22 17:23:02
@ 9bde4214:06ca052b
2025-04-22 17:23:02“You’ll get all that for free if you build it right.”
Pablo & Gigi try to stop giggling.
In this dialogue:
- 01: Start Ugly
- 02: There is No Global
- Concept of ownership & “Read, Write, Own”
- Shamir Secret Sharing and Timelocks
- “No amount of violence will ever solve a math problem.”
- You can’t prove deletion of a key (or anything, really); best you can do is “burn” bitcoin
- Data is information, which behaves like an idea (not like an apple)
- “If you have an apple and I have an apple and we exchange these apples then you and I will still each have one apple. But if you have an idea and I have an idea and we exchange these ideas, then each of us will have two ideas.” – https://dergigi.com/threads/memes-vs-the-world
- Why the Pubky architecture isn’t great
- Cashu
- Nutzaps: NIP-60 / NIP-61
- How nutzaps fix fake zaps on zaplife.lol
- “Ecash fixes HTTP 402”
- “[Bitcoin [and nostr]] take advantage of the nature of information being easy to spread but hard to stifle.” –Satoshi Nakamoto
- Discovery with NIP-89
- #RunDVM with NIP-90
- Why micropayments can’t work on credit rails, and how bitcoin is the rediscovery of money.
- Putting payments into blossom
- “Money is essentially a tool to keep track of who owes what to whom. Broadly speaking, everything we have used as money up to now falls into two categories: physical artifacts and informational lists. Or, to use more common parlance: tokens and ledgers.”
- “maximum utility in the world of Bitcoin entails the adoption of maximum responsibility.”
- Complexity of Lightning vs the simplicity of eCash
- Amber and Citrine
- How Pablo became the BIS
- 12 words in your head can literally save your life
- The in-between of custodial and non-custodial in a multi-mint world
- Nutzaps integrated in chachi.chat
- The intermediacy of nostr is magic
- In nostr you’ll get a lot for free IF YOU BUILD IT RIGHT
- “Free Speech platforms cannot exist; if there is a ‘deplatform’ button, the button will be pressed.”
- “Neither nostalgia nor utopia.”
- Solutions that make stuff worse over time vs solutions that make stuff better over time.
-
asknostr on passkeys, and why we think they’ll make things worse over time.
- Authentication vs identity: “identification asks, authentication proves”
- You are not your name and photo; identity is prismatic
- (m00t’s talk on it at web summit 2011)
- Starbug from CCC pwning TouchID biometrics from a high-res photo (article)
- Key rotation and (American) HODL
- Social recovery
- Multi-sig for nostr with FROSTR
Links & References:
- Nostr Protocol Repository: https://github.com/nostr-protocol
- Cashu (e-cash): https://github.com/cashubtc
- NIP-60 (Nutzaps): https://github.com/nostr-protocol/nips/blob/master/60.md
- NIP-89 (Service Discovery) & NIP-90 (DVMs) – upcoming proposals: https://nips.nostr.com/89 & https://nips.nostr.com/90
-
 @ 21335073:a244b1ad
2025-03-18 20:47:50
@ 21335073:a244b1ad
2025-03-18 20:47:50Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ 9bde4214:06ca052b
2025-04-22 17:15:24
@ 9bde4214:06ca052b
2025-04-22 17:15:24“I don’t believe in Utopia anymore. I’m too old for that.”
Calle & Gigi philosophize about nuts.
Books and articles mentioned:
In this dialogue:
- Where is the Utopia that the internet promised?
- “Neither nostalgia nor utopia”
- Net Neutrality is a moral stance
- Where did the internet go wrong?
- Tech as a tool; is tech always neutral?
- Technology that increases agency VS tech that enslaves
- Competition vs Symbiosis
- “Who will run the mints?”
- “Anyone” can use it vs “everyone” can use it
- Centralizing vs. Monopolizing
- Bitcoin has an ethos baked in (You Shall Not Steal)
- Passive internet vs active internet
- Agency in cyberspace, and how to maximize it
- Blinded custodian vs regular custodian
- User data is a liability
- Obscura / Mullvad / Silent.Link as obvious early adopters
- Run your own ISP - Tollgate
- Cryptography is Not Enough
- Bitcoin is Time
- Time requires heat
- Zero-knowledge service providers
- Electronic Cash vs Digital Cash (CBDCs)
- Credit requires KYC, KYC implies outside enforcement
- Writings on Micropayments by Nick Szabo
- eCash fixes 402, obviously
- Who Owns the Future?
- “You are the product” vs “Subscription Hell”
- “Hello old friend!!!”
- Cathedral vs Bazaar
- Why paywalls suck
- Information wants to be free
- "Markets become absurd as supply approaches infinity."
- eCash + AI = match made in heaven
- #LearnToCode vs #LearnToPrompt
- Scarcity in cyberspace: compute, storage, networking
- Zero-Knowledge compute & zero-knowledge proofs
- https://en.wikipedia.org/wiki/Zero-knowledge_proof
- https://github.com/AbdelStark/cashu-zk-engine
- Cairo: https://github.com/starkware-libs/cairo
- MCP https://github.com/AbdelStark/bitcoin-mcp
- MCP DVM: https://github.com/r0d8lsh0p/n8n-AI-agent-DVM-MCP-client
- DVMCP: https://mcp.so/server/dvmcp
- Olas & Nutzaps (NIP-60, NIP-61)
- Bitcoin is not only the internet of money, but it is the money of the internet
- Re-building the internet archive on top of nostr
- Bitrot & 404
- Resurrection markets & marketplace for hashes via Blossom
- Hugs 🫂
-
 @ 21335073:a244b1ad
2025-03-18 14:43:08
@ 21335073:a244b1ad
2025-03-18 14:43:08Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ a07fae46:7d83df92
2025-03-18 12:31:40
@ a07fae46:7d83df92
2025-03-18 12:31:40if the JFK documents come out and are nothing but old hat, it will be disappointing. but if they contain revelations, then they are an unalloyed good. unprecedented and extraordinary; worthy of praise and admiration. they murdered the president in broad daylight and kept 80,000 related documents secret for 60 years. the apparatus that did that and got away with it, is 100+ years in the making. the magic bullet was just the starting pistol of a new era; a level up in an old game. it won't be dismantled and your republic delivered back with a bow in 2 months. have a little humility and a little gratitude. cynicism is easy. it's peak mid-wittery. yeah no shit everything is corrupt and everyone's likely captured by AIPAC or something beyond. YOU THINK AIPAC is the ALL SEEING EYE?
you can keep going, if you want to, but have some awareness and appreciation for where we are and what it took to get here. the first 'you are fake news' was also a shot heard 'round the world and you are riding high on it's Infrasound wave, still reverberating; unappreciative of the profound delta in public awareness and understanding, and rate of change, that has occurred since that moment, in 2017. think about where we were back then, especially with corporate capture of the narrative. trump's bullheaded behavior, if only ego-driven, is what broke the spell. an actual moment of savage bravery is what allows for your current jaded affectation. black pilled is boring. it's intellectually lazy. it is low-resolution-thinking, no better than progressives who explain the myriad ills of the world through 'racism'. normalcy bias works both ways. i'm not grading you on a curve that includes NPCs. i'm grading you against those of us with a mind, on up. do better.
the best Webb-style doomer argument is essentially 'the mouse trap needs a piece of cheese in order to work'. ok, but it doesn't need 3 pieces of cheese, or 5. was FreeRoss the piece of cheese? was the SBR the cheese? real bitcoiners know how dumb the 'sbr is an attempt to takeover btc' narrative is, so extrapolate from that. what about withdrawal from the WHO? freeze and review of USAID et al? how many pieces of cheese before we realize it's not a trap? it's just a messy endeavor.
Good morning.
jfkFiles #nostrOnly
-
 @ 57d1a264:69f1fee1
2025-04-10 05:54:45
@ 57d1a264:69f1fee1
2025-04-10 05:54:45Some banners to promote ~Design territory in the Wild Web. Interested to kand feedback now your thought on it.
| Banner | Content | |---|---| |
| Stop scrolling, start stacking! Your #insights, your #stories, your #code – they have real #value. On #StackerNews #Design, we believe in rewarding #quality contents. Turn your #passion and #knowledge into #Bitcoin. Share your v#oice and get rewarded for it, join the conversation! Explore now: https://stacker.news/~Design/r/Design_r #Bitcoin #LightningNetwork #Community #ContentCreation #EarnBitcoin #Tech #SNdesign | |
| Stop scrolling, start flourishing! Your unique 3perspective, your groundbreaking #ideas, your niche #knowledge – it all has #value. On #StackerNews #Design we #reward you with #Bitcoin, instantly via the #LightningNetwork. Don't let your #insights fade into the #digital noise. Join a community that values #contribution, fuels #innovation, and puts the #power back in your #diamondhands (and #wallet!). Turn your thoughts into #zaps? Join the conversation: https://stacker.news/~Design/r/Design_r #Bitcoin #Lightning #Network #Community #EarnBitcoin #Tech #Design #Innovation #ContentCreation #Crypto | |
| Stop scrolling, #stack #sats for your #insights! #StackerNews #Design is where your #creative spark meets the #LightningNetwork. Discuss #ideas, share your #work, and #earn #Bitcoin for valuable contributions. Join a vibrant #community shaping the #future of #creativity and #tech, one #zap at a time. Explore the intersection of #innovation and #functionality https://stacker.news/~Design/r/Design_r #StackerNews #BitcoinDesign #DesignCommunity #Lightning #Network #UIDesign #UXDesign #Crypto #EarnBitcoin | |
| Stop scrolling, start stacking #sats! Talk #Design on #StackerNews – the platform where your #insights on #Tech, #Design, #Finance, #econ, #Food #DIY and more actually earn you real #Bitcoin via the #LightningNetwork. Join a vibrant #community, #discover diverse #perspectives, and #EarnBitcoin for sharing valuable content. Explore the #future of #contentCreation: https://stacker.news/~Design/r/Design_r #StackerNews #Lightning #Network #Crypto #Tech #Finance #Design #ContentCreator #GetPaidInBitcoin #SocialMedia #Community #BitconAccepted | |
| #StackerNews #Design is where your engagement actually #pays. #Earn #Bitcoin instantly via #zaps just for sharing great unique #content and joining #discussions on everything from #innovative #tech to #creative #ideas. Discover diverse #opinion, connect with a #community, start #earning. Join the #future of content: https://stacker.news/~Design/r/Design_r #LightningNetwork #EarnBitcoin #CryptoCommunity #ContentCreators #StackerNews #Decentralized #SocialMedia |
originally posted at https://stacker.news/items/939548
-
 @ bc52210b:20bfc6de
2025-03-14 20:39:20
@ bc52210b:20bfc6de
2025-03-14 20:39:20When writing safety critical code, every arithmetic operation carries the potential for catastrophic failure—whether that’s a plane crash in aerospace engineering or a massive financial loss in a smart contract.
The stakes are incredibly high, and errors are not just bugs; they’re disasters waiting to happen. Smart contract developers need to shift their mindset: less like web developers, who might prioritize speed and iteration, and more like aerospace engineers, where precision, caution, and meticulous attention to detail are non-negotiable.
In practice, this means treating every line of code as a critical component, adopting rigorous testing, and anticipating worst-case scenarios—just as an aerospace engineer would ensure a system can withstand extreme conditions.
Safety critical code demands aerospace-level precision, and smart contract developers must rise to that standard to protect against the severe consequences of failure.
-
 @ 57d1a264:69f1fee1
2025-04-08 06:39:52
@ 57d1a264:69f1fee1
2025-04-08 06:39:52originally posted at https://stacker.news/items/937791
-
 @ 5c26ee8b:a4d229aa
2025-04-14 16:37:32
@ 5c26ee8b:a4d229aa
2025-04-14 16:37:3210:25 Yunus
وَاللَّهُ يَدْعُو إِلَىٰ دَارِ السَّلَامِ وَيَهْدِي مَنْ يَشَاءُ إِلَىٰ صِرَاطٍ مُسْتَقِيمٍ
And Allah invites to the Home of Peace and guides whom He wills to a straight path.
6:125 Al-An'aam
فَمَنْ يُرِدِ اللَّهُ أَنْ يَهْدِيَهُ يَشْرَحْ صَدْرَهُ لِلْإِسْلَامِ ۖ وَمَنْ يُرِدْ أَنْ يُضِلَّهُ يَجْعَلْ صَدْرَهُ ضَيِّقًا حَرَجًا كَأَنَّمَا يَصَّعَّدُ فِي السَّمَاءِ ۚ كَذَٰلِكَ يَجْعَلُ اللَّهُ الرِّجْسَ عَلَى الَّذِينَ لَا يُؤْمِنُونَ
So whoever Allah wants to guide - He expands his breast to [contain] Islam; and whoever He wants to misguide - He makes his breast tight and constricted as though he were climbing into the sky. Thus Allah places defilement upon those who do not believe.
Allah is one of the Islamic names of God; the creator of everything. Not associating with God, Allah, any other and worshipping him alone is one of the first known fact in Islam.
- Al-Ikhlaas قُلْ هُوَ اللَّهُ أَحَدٌ Say, "He is Allah, [who is] One, اللَّهُ الصَّمَدُ Allah, the Eternal Refuge. لَمْ يَلِدْ وَلَمْ يُولَدْ He neither begets nor is born, وَلَمْ يَكُنْ لَهُ كُفُوًا أَحَدٌ Nor is there to Him any equivalent."
The Quran, the Islamic holly book and the guidance for mankind, was delivered more than 1400 years ago through the Angel Gabriel to prophet Mohamed peace be upon, however little is known about Islam despite living in a so called intellectual era.
The first word that was delivered was, “Read” in the first verse of surah Al-Alaq.
96:1 Al-Alaq
اقْرَأْ بِاسْمِ رَبِّكَ الَّذِي خَلَقَ
Read, in the name of your Lord who created -
The Quran, words of God (Allah), was delivered in Arabic and it is one of its miracles.
39:28 Az-Zumar
قُرْآنًا عَرَبِيًّا غَيْرَ ذِي عِوَجٍ لَعَلَّهُمْ يَتَّقُونَ
[It is] an Arabic Qur'an, without any distortion that they might become righteous.
18:109 Al-Kahf
قُلْ لَوْ كَانَ الْبَحْرُ مِدَادًا لِكَلِمَاتِ رَبِّي لَنَفِدَ الْبَحْرُ قَبْلَ أَنْ تَنْفَدَ كَلِمَاتُ رَبِّي وَلَوْ جِئْنَا بِمِثْلِهِ مَدَدًا
Say, "If the sea were ink for [writing] the words of my Lord, the sea would be exhausted before the words of my Lord were exhausted, even if We brought the like of it as a supplement."
17:88 Al-Israa
قُلْ لَئِنِ اجْتَمَعَتِ الْإِنْسُ وَالْجِنُّ عَلَىٰ أَنْ يَأْتُوا بِمِثْلِ هَٰذَا الْقُرْآنِ لَا يَأْتُونَ بِمِثْلِهِ وَلَوْ كَانَ بَعْضُهُمْ لِبَعْضٍ ظَهِيرًا
Say, "If mankind and the jinn gathered in order to produce the like of this Qur'an, they could not produce the like of it, even if they were to each other assistants."
17:89 Al-Israa
وَلَقَدْ صَرَّفْنَا لِلنَّاسِ فِي هَٰذَا الْقُرْآنِ مِنْ كُلِّ مَثَلٍ فَأَبَىٰ أَكْثَرُ النَّاسِ إِلَّا كُفُورًا
And We have certainly diversified for the people in this Qur'an from every [kind] of example, but most of the people refused [anything] except disbelief.
Through the wards of God in the Quran a lot can be known about Him and in the following verse some descriptions about Him.
2:255 Al-Baqara
اللَّهُ لَا إِلَٰهَ إِلَّا هُوَ الْحَيُّ الْقَيُّومُ ۚ لَا تَأْخُذُهُ سِنَةٌ وَلَا نَوْمٌ ۚ لَهُ مَا فِي السَّمَاوَاتِ وَمَا فِي الْأَرْضِ ۗ مَنْ ذَا الَّذِي يَشْفَعُ عِنْدَهُ إِلَّا بِإِذْنِهِ ۚ يَعْلَمُ مَا بَيْنَ أَيْدِيهِمْ وَمَا خَلْفَهُمْ ۖ وَلَا يُحِيطُونَ بِشَيْءٍ مِنْ عِلْمِهِ إِلَّا بِمَا شَاءَ ۚ وَسِعَ كُرْسِيُّهُ السَّمَاوَاتِ وَالْأَرْضَ ۖ وَلَا يَئُودُهُ حِفْظُهُمَا ۚ وَهُوَ الْعَلِيُّ الْعَظِيمُ
Allah - there is no deity except Him, the Ever-Living, the Sustainer of [all] existence. Neither drowsiness overtakes Him nor sleep. To Him belongs whatever is in the heavens and whatever is on the earth. Who is it that can intercede with Him except by His permission? He knows what is [presently] before them and what will be after them, and they encompass not a thing of His knowledge except for what He wills. His Kursi extends over the heavens and the earth, and their preservation tires Him not. And He is the Most High, the Most Great.
Seeing God has been a curiosity of prophets themselves and in the following examples of what happened when prophet Moses, peace be upon him, or his people asked so.
7:143 Al-A'raaf
وَلَمَّا جَاءَ مُوسَىٰ لِمِيقَاتِنَا وَكَلَّمَهُ رَبُّهُ قَالَ رَبِّ أَرِنِي أَنْظُرْ إِلَيْكَ ۚ قَالَ لَنْ تَرَانِي وَلَٰكِنِ انْظُرْ إِلَى الْجَبَلِ فَإِنِ اسْتَقَرَّ مَكَانَهُ فَسَوْفَ تَرَانِي ۚ فَلَمَّا تَجَلَّىٰ رَبُّهُ لِلْجَبَلِ جَعَلَهُ دَكًّا وَخَرَّ مُوسَىٰ صَعِقًا ۚ فَلَمَّا أَفَاقَ قَالَ سُبْحَانَكَ تُبْتُ إِلَيْكَ وَأَنَا أَوَّلُ الْمُؤْمِنِينَ
And when Moses arrived at Our appointed time and his Lord spoke to him, he said, "My Lord, show me [Yourself] that I may look at You." [Allah] said, "You will not see Me, but look at the mountain; if it should remain in place, then you will see Me." But when his Lord appeared to the mountain, He rendered it level, and Moses fell unconscious. And when he awoke, he said, "Exalted are You! I have repented to You, and I am the first of the believers."
2:55 Al-Baqara
وَإِذْ قُلْتُمْ يَا مُوسَىٰ لَنْ نُؤْمِنَ لَكَ حَتَّىٰ نَرَى اللَّهَ جَهْرَةً فَأَخَذَتْكُمُ الصَّاعِقَةُ وَأَنْتُمْ تَنْظُرُونَ
And [recall] when you said, "O Moses, we will never believe you until we see Allah outright"; so the thunderbolt took you while you were looking on.
2:56 Al-Baqara
ثُمَّ بَعَثْنَاكُمْ مِنْ بَعْدِ مَوْتِكُمْ لَعَلَّكُمْ تَشْكُرُونَ
Then We revived you after your death that perhaps you would be grateful.
In fact eyesights can’t reach God as in the following verses 6:102 Al-An'aam
ذَٰلِكُمُ اللَّهُ رَبُّكُمْ ۖ لَا إِلَٰهَ إِلَّا هُوَ ۖ خَالِقُ كُلِّ شَيْءٍ فَاعْبُدُوهُ ۚ وَهُوَ عَلَىٰ كُلِّ شَيْءٍ وَكِيلٌ
That is Allah, your Lord; there is no deity except Him, the Creator of all things, so worship Him. And He is Disposer of all things.
6:103 Al-An'aam
لَا تُدْرِكُهُ الْأَبْصَارُ وَهُوَ يُدْرِكُ الْأَبْصَارَ ۖ وَهُوَ اللَّطِيفُ الْخَبِيرُ
Eyesights (or visions) do not reach (or perceive him) Him, but He reaches (or perceives) [all] eyesights (visions); and He is the Subtle, the Acquainted.
6:104 Al-An'aam
قَدْ جَاءَكُمْ بَصَائِرُ مِنْ رَبِّكُمْ ۖ فَمَنْ أَبْصَرَ فَلِنَفْسِهِ ۖ وَمَنْ عَمِيَ فَعَلَيْهَا ۚ وَمَا أَنَا عَلَيْكُمْ بِحَفِيظٍ
There has come to you eyesights (or enlightenments) from your Lord. So whoever will see does so for [the benefit of] his soul, and whoever is blind [does harm] against it. And [say], "I am not controlling (or a guardian) over you."
42:11 Ash-Shura
فَاطِرُ السَّمَاوَاتِ وَالْأَرْضِ ۚ جَعَلَ لَكُمْ مِنْ أَنْفُسِكُمْ أَزْوَاجًا وَمِنَ الْأَنْعَامِ أَزْوَاجًا ۖ يَذْرَؤُكُمْ فِيهِ ۚ لَيْسَ كَمِثْلِهِ شَيْءٌ ۖ وَهُوَ السَّمِيعُ الْبَصِيرُ
[He is] Creator of the heavens and the earth. He has made for you from yourselves, mates, and among the cattle, mates; He multiplies you thereby. There is nothing like Him, and He is the Hearing, the Seeing.
Another name of God is the Truth and the Islam is the religion of truth and prophet Mohamed peace be upon him was chosen to invite the people to Islam.
61:7 As-Saff
وَمَنْ أَظْلَمُ مِمَّنِ افْتَرَىٰ عَلَى اللَّهِ الْكَذِبَ وَهُوَ يُدْعَىٰ إِلَى الْإِسْلَامِ ۚ وَاللَّهُ لَا يَهْدِي الْقَوْمَ الظَّالِمِينَ
And who is more unjust than one who invents about Allah untruth while he is being invited to Islam. And Allah does not guide the wrongdoing people.
61:8 As-Saff
يُرِيدُونَ لِيُطْفِئُوا نُورَ اللَّهِ بِأَفْوَاهِهِمْ وَاللَّهُ مُتِمُّ نُورِهِ وَلَوْ كَرِهَ الْكَافِرُونَ
They want to extinguish the light of Allah with their mouths, but Allah will perfect His light, although the disbelievers dislike it.
61:9 As-Saff
هُوَ الَّذِي أَرْسَلَ رَسُولَهُ بِالْهُدَىٰ وَدِينِ الْحَقِّ لِيُظْهِرَهُ عَلَى الدِّينِ كُلِّهِ وَلَوْ كَرِهَ الْمُشْرِكُونَ
It is He who sent His Messenger with guidance and the religion of truth to manifest it over all religion, although those who associate others with Allah dislike it.
Humans were given a trust, it’s to populate the earth while having the ability to choose between right and wrong.
33:72 Al-Ahzaab
إِنَّا عَرَضْنَا الْأَمَانَةَ عَلَى السَّمَاوَاتِ وَالْأَرْضِ وَالْجِبَالِ فَأَبَيْنَ أَنْ يَحْمِلْنَهَا وَأَشْفَقْنَ مِنْهَا وَحَمَلَهَا الْإِنْسَانُ ۖ إِنَّهُ كَانَ ظَلُومًا جَهُولًا
Indeed, we offered the Trust to the heavens and the earth and the mountains, and they declined to bear it and feared it; but man [undertook to] bear it. Indeed, he was unjust and ignorant.
Although our souls testified before the creation that God, Allah is our creator, he sent messengers and books to guide us.
7:172 Al-A'raaf
وَإِذْ أَخَذَ رَبُّكَ مِنْ بَنِي آدَمَ مِنْ ظُهُورِهِمْ ذُرِّيَّتَهُمْ وَأَشْهَدَهُمْ عَلَىٰ أَنْفُسِهِمْ أَلَسْتُ بِرَبِّكُمْ ۖ قَالُوا بَلَىٰ ۛ شَهِدْنَا ۛ أَنْ تَقُولُوا يَوْمَ الْقِيَامَةِ إِنَّا كُنَّا عَنْ هَٰذَا غَافِلِينَ
And [mention] when your Lord took from the children of Adam - from their loins - their descendants and made them testify of themselves, [saying to them], "Am I not your Lord?" They said, "Yes, we have testified." [This] - lest you should say on the day of Resurrection, "Indeed, we were of this unaware."
God likes that who believes in him submits to him willingly. The heavens and the earth, known to have consciousness in Islam submitted to him before us.
41:9 Fussilat
۞ قُلْ أَئِنَّكُمْ لَتَكْفُرُونَ بِالَّذِي خَلَقَ الْأَرْضَ فِي يَوْمَيْنِ وَتَجْعَلُونَ لَهُ أَنْدَادًا ۚ ذَٰلِكَ رَبُّ الْعَالَمِينَ
Say, "Do you indeed disbelieve in He who created the earth in two days and attribute to Him equals? That is the Lord of the worlds."
41:10 Fussilat
وَجَعَلَ فِيهَا رَوَاسِيَ مِنْ فَوْقِهَا وَبَارَكَ فِيهَا وَقَدَّرَ فِيهَا أَقْوَاتَهَا فِي أَرْبَعَةِ أَيَّامٍ سَوَاءً لِلسَّائِلِينَ
And He placed on the earth firmly set mountains over its surface, and He blessed it and determined therein its [creatures'] sustenance in four days without distinction - for [the information] of those who ask.
41:11 Fussilat
ثُمَّ اسْتَوَىٰ إِلَى السَّمَاءِ وَهِيَ دُخَانٌ فَقَالَ لَهَا وَلِلْأَرْضِ ائْتِيَا طَوْعًا أَوْ كَرْهًا قَالَتَا أَتَيْنَا طَائِعِينَ
Then He directed Himself to the heaven while it was smoke and said to it and to the earth, "Come, willingly or by compulsion", they said, "We came willingly."
40:57 Al-Ghaafir
لَخَلْقُ السَّمَاوَاتِ وَالْأَرْضِ أَكْبَرُ مِنْ خَلْقِ النَّاسِ وَلَٰكِنَّ أَكْثَرَ النَّاسِ لَا يَعْلَمُونَ
The creation of the heavens and earth is greater than the creation of mankind, but most of the people do not know.
It’s important to know what’s God asking people to do while submitting to him as mentioned in the following verses.
Surah Al-Israa: Verse 22: لَا تَجْعَلْ مَعَ اللَّهِ إِلَٰهًا آخَرَ فَتَقْعُدَ مَذْمُومًا مَخْذُولًا Set not up with Allah any other ilah (god), (O man)! (This verse is addressed to Prophet Muhammad SAW, but its implication is general to all mankind), or you will sit down reproved, forsaken (in the Hell-fire). Verse 23: ۞ وَقَضَىٰ رَبُّكَ أَلَّا تَعْبُدُوا إِلَّا إِيَّاهُ وَبِالْوَالِدَيْنِ إِحْسَانًا ۚ إِمَّا يَبْلُغَنَّ عِنْدَكَ الْكِبَرَ أَحَدُهُمَا أَوْ كِلَاهُمَا فَلَا تَقُلْ لَهُمَا أُفٍّ وَلَا تَنْهَرْهُمَا وَقُلْ لَهُمَا قَوْلًا كَرِيمًا And your Lord has decreed that you worship none but Him. And that you be dutiful to your parents. If one of them or both of them attain old age in your life, don’t say to them a word of disrespect, or shout at them but address them in terms of honour. Verse 24: وَاخْفِضْ لَهُمَا جَنَاحَ الذُّلِّ مِنَ الرَّحْمَةِ وَقُلْ رَبِّ ارْحَمْهُمَا كَمَا رَبَّيَانِي صَغِيرًا And lower unto them the wing of submission and humility through mercy, and say: "My Lord! Bestow on them Your Mercy as they did bring me up when I was small." Verse 25: رَبُّكُمْ أَعْلَمُ بِمَا فِي نُفُوسِكُمْ ۚ إِنْ تَكُونُوا صَالِحِينَ فَإِنَّهُ كَانَ لِلْأَوَّابِينَ غَفُورًا Your Lord knows best what is in your inner-selves. If you are righteous, then, verily, He is Ever Most Forgiving to those who turn unto Him again and again in obedience, and in repentance. Verse 26: وَآتِ ذَا الْقُرْبَىٰ حَقَّهُ وَالْمِسْكِينَ وَابْنَ السَّبِيلِ وَلَا تُبَذِّرْ تَبْذِيرًا And give to the kindred his due and to the Miskin (poor) and to the wayfarer. But spend not wastefully (your wealth) in the manner of a spendthrift. Verse 27: إِنَّ الْمُبَذِّرِينَ كَانُوا إِخْوَانَ الشَّيَاطِينِ ۖ وَكَانَ الشَّيْطَانُ لِرَبِّهِ كَفُورًا Verily, spendthrifts are brothers of the Shayatin (devils), and the Shaitan (Devil - Satan) is ever ungrateful to his Lord. Verse 28: وَإِمَّا تُعْرِضَنَّ عَنْهُمُ ابْتِغَاءَ رَحْمَةٍ مِنْ رَبِّكَ تَرْجُوهَا فَقُلْ لَهُمْ قَوْلًا مَيْسُورًا
And if you turn away from them (kindred, poor, wayfarer, etc. whom We have ordered you to give their rights, but if you have no money at the time they ask you for it) and you are awaiting a mercy from your Lord for which you hope, then, speak unto them a soft kind word (i.e. Allah will give me and I shall give you). Verse 29: وَلَا تَجْعَلْ يَدَكَ مَغْلُولَةً إِلَىٰ عُنُقِكَ وَلَا تَبْسُطْهَا كُلَّ الْبَسْطِ فَتَقْعُدَ مَلُومًا مَحْسُورًا And let not your hand be tied (like a miser) to your neck, nor stretch it forth to its utmost reach (like a spendthrift), so that you become blameworthy and in severe poverty. Verse 30: إِنَّ رَبَّكَ يَبْسُطُ الرِّزْقَ لِمَنْ يَشَاءُ وَيَقْدِرُ ۚ إِنَّهُ كَانَ بِعِبَادِهِ خَبِيرًا بَصِيرًا Truly, your Lord enlarges the provision for whom He wills and straitens (for whom He wills). Verily, He is Ever All-Knower, All-Seer of His slaves (servants; mankind created by God). Verse 31: وَلَا تَقْتُلُوا أَوْلَادَكُمْ خَشْيَةَ إِمْلَاقٍ ۖ نَحْنُ نَرْزُقُهُمْ وَإِيَّاكُمْ ۚ إِنَّ قَتْلَهُمْ كَانَ خِطْئًا كَبِيرًا And kill not your children for fear of poverty. We provide for them and for you. Surely, the killing of them is a great sin. Verse 32: وَلَا تَقْرَبُوا الزِّنَا ۖ إِنَّهُ كَانَ فَاحِشَةً وَسَاءَ سَبِيلًا And don’t come near to the unlawful sexual intercourse. Verily, it is a Fahishah (a great sin), and an evil way (that leads one to Hell unless Allah forgives him). Verse 33: وَلَا تَقْتُلُوا النَّفْسَ الَّتِي حَرَّمَ اللَّهُ إِلَّا بِالْحَقِّ ۗ وَمَنْ قُتِلَ مَظْلُومًا فَقَدْ جَعَلْنَا لِوَلِيِّهِ سُلْطَانًا فَلَا يُسْرِفْ فِي الْقَتْلِ ۖ إِنَّهُ كَانَ مَنْصُورًا And do not kill anyone that Allah has forbidden, except for a just cause. And whoever is killed (intentionally with hostility and oppression and not by mistake), We have given his heir the authority [(to demand Qisas, Law of Equality in punishment or to forgive, or to take Diya (blood money)]. But do not kill excessively (exceed limits in the matter of taking life). Verily, he is victorious. Verse 34: وَلَا تَقْرَبُوا مَالَ الْيَتِيمِ إِلَّا بِالَّتِي هِيَ أَحْسَنُ حَتَّىٰ يَبْلُغَ أَشُدَّهُ ۚ وَأَوْفُوا بِالْعَهْدِ ۖ إِنَّ الْعَهْدَ كَانَ مَسْئُولًا And don’t come near to the orphan's property except to improve it, until he attains the age of full strength. And fulfil (every) covenant. Verily! the covenant, will be questioned about. Verse 35: وَأَوْفُوا الْكَيْلَ إِذَا كِلْتُمْ وَزِنُوا بِالْقِسْطَاسِ الْمُسْتَقِيمِ ۚ ذَٰلِكَ خَيْرٌ وَأَحْسَنُ تَأْوِيلًا And give full measure when you measure, and weigh with a balance that is straight. That is good (advantageous) and better in the end. Verse 36: وَلَا تَقْفُ مَا لَيْسَ لَكَ بِهِ عِلْمٌ ۚ إِنَّ السَّمْعَ وَالْبَصَرَ وَالْفُؤَادَ كُلُّ أُولَٰئِكَ كَانَ عَنْهُ مَسْئُولًا And don’t pursue (i.e., do not say, or do not or witness not, etc.) what you have no knowledge of. Verily! The hearing, and the sight, and the heart, of each of those you will be questioned (by Allah). Verse 37: وَلَا تَمْشِ فِي الْأَرْضِ مَرَحًا ۖ إِنَّكَ لَنْ تَخْرِقَ الْأَرْضَ وَلَنْ تَبْلُغَ الْجِبَالَ طُولًا And walk not on the earth with conceit and arrogance. Verily, you can’t break the earth, nor reach the mountains in height. Verse 38: كُلُّ ذَٰلِكَ كَانَ سَيِّئُهُ عِنْدَ رَبِّكَ مَكْرُوهًا All the bad aspects of these (the above mentioned things) are hateful to your Lord. Verse 39: ذَٰلِكَ مِمَّا أَوْحَىٰ إِلَيْكَ رَبُّكَ مِنَ الْحِكْمَةِ ۗ وَلَا تَجْعَلْ مَعَ اللَّهِ إِلَٰهًا آخَرَ فَتُلْقَىٰ فِي جَهَنَّمَ مَلُومًا مَدْحُورًا This is (part) of Al-Hikmah (wisdom, good manners and high character, etc.) that your Lord has inspired to you. And set not up with Allah any other god lest you should be thrown into Hell, blameworthy and rejected, (from Allah's Mercy). Verse 40: أَفَأَصْفَاكُمْ رَبُّكُمْ بِالْبَنِينَ وَاتَّخَذَ مِنَ الْمَلَائِكَةِ إِنَاثًا ۚ إِنَّكُمْ لَتَقُولُونَ قَوْلًا عَظِيمًا Has then your Lord (O pagans of Makkah) preferred for you sons, and taken for Himself from among the angels daughters (Angels don’t have a gender and it’s wrong to refer to them as females). Verily! You utter an awful saying, indeed. Verse 41: وَلَقَدْ صَرَّفْنَا فِي هَٰذَا الْقُرْآنِ لِيَذَّكَّرُوا وَمَا يَزِيدُهُمْ إِلَّا نُفُورًا And surely, We have explained [Our Promises, Warnings and (set forth many) examples] in this Quran that they (the disbelievers) may take heed, but it increases them in aversion (from the truth). Verse 42: قُلْ لَوْ كَانَ مَعَهُ آلِهَةٌ كَمَا يَقُولُونَ إِذًا لَابْتَغَوْا إِلَىٰ ذِي الْعَرْشِ سَبِيلًا Say: "If there had been other gods along with Him as they say, then they would certainly have sought out a way to the Lord of the Throne (seeking His Pleasures and to be near to Him). Verse 43: سُبْحَانَهُ وَتَعَالَىٰ عَمَّا يَقُولُونَ عُلُوًّا كَبِيرًا Glorified and High be He! From 'Uluwan Kabira (the great falsehood) that they say!
Surah Al-Israa: Verse 53 وَقُلْ لِعِبَادِي يَقُولُوا الَّتِي هِيَ أَحْسَنُ ۚ إِنَّ الشَّيْطَانَ يَنْزَغُ بَيْنَهُمْ ۚ إِنَّ الشَّيْطَانَ كَانَ لِلْإِنْسَانِ عَدُوًّا مُبِينًا And say to My slaves (servants; mankind created by God) that they should (only) say the best words. (Because) Shaitan (Satan) verily, sows disagreements among them. Surely, Shaitan (Satan) is to man a plain enemy. Surah Al-Maaida Verse 90: يَا أَيُّهَا الَّذِينَ آمَنُوا إِنَّمَا الْخَمْرُ وَالْمَيْسِرُ وَالْأَنْصَابُ وَالْأَزْلَامُ رِجْسٌ مِنْ عَمَلِ الشَّيْطَانِ فَاجْتَنِبُوهُ لَعَلَّكُمْ تُفْلِحُونَ O you who believe! Intoxicants (all kinds of alcoholic drinks), gambling, Al-Ansab, and Al-Azlam (arrows for seeking luck or decision) are an abomination of Shaitan's (Satan) handiwork. So avoid (strictly all) that (abomination) in order that you may be successful. Verse 91: إِنَّمَا يُرِيدُ الشَّيْطَانُ أَنْ يُوقِعَ بَيْنَكُمُ الْعَدَاوَةَ وَالْبَغْضَاءَ فِي الْخَمْرِ وَالْمَيْسِرِ وَيَصُدَّكُمْ عَنْ ذِكْرِ اللَّهِ وَعَنِ الصَّلَاةِ ۖ فَهَلْ أَنْتُمْ مُنْتَهُونَ Shaitan (Satan) wants only to excite enmity and hatred between you with intoxicants (alcoholic drinks) and gambling, and hinder you from the remembrance of Allah (God) and from As-Salat (the prayer). So, will you not then abstain?
Surah Luqman: Verse 17: يَا بُنَيَّ أَقِمِ الصَّلَاةَ وَأْمُرْ بِالْمَعْرُوفِ وَانْهَ عَنِ الْمُنْكَرِ وَاصْبِرْ عَلَىٰ مَا أَصَابَكَ ۖ إِنَّ ذَٰلِكَ مِنْ عَزْمِ الْأُمُورِ "O my son (said Luqman, peace be upon him) ! Aqim-is-Salat (perform As-Salat; prayers), enjoin (people) for Al-Ma'ruf (all that is good), and forbid (people) from Al-Munkar (all that is evil and bad), and bear with patience whatever befall you. Verily! These are some of the important commandments ordered by Allah with no exemption. Verse 18: وَلَا تُصَعِّرْ خَدَّكَ لِلنَّاسِ وَلَا تَمْشِ فِي الْأَرْضِ مَرَحًا ۖ إِنَّ اللَّهَ لَا يُحِبُّ كُلَّ مُخْتَالٍ فَخُورٍ "And don’t turn your face away from men with pride, and don’t walk in insolence through the earth. Verily, Allah does not love each arrogant (prideful) boaster. Verse 19: وَاقْصِدْ فِي مَشْيِكَ وَاغْضُضْ مِنْ صَوْتِكَ ۚ إِنَّ أَنْكَرَ الْأَصْوَاتِ لَصَوْتُ الْحَمِيرِ "And be moderate (or show no insolence) in your walking, and lower your voice. Verily, the harshest of all voices is the voice of the donkey."
Surah Taa-Haa: Verse 131: وَلَا تَمُدَّنَّ عَيْنَيْكَ إِلَىٰ مَا مَتَّعْنَا بِهِ أَزْوَاجًا مِنْهُمْ زَهْرَةَ الْحَيَاةِ الدُّنْيَا لِنَفْتِنَهُمْ فِيهِ ۚ وَرِزْقُ رَبِّكَ خَيْرٌ وَأَبْقَىٰ And strain not your eyes in longing for the things We have given for enjoyment to various groups of them, the splendour of the life of this world that We may test them thereby. But the provision (good reward in the Hereafter) of your Lord is better and more lasting.
Surah Al-Hujuraat: Verse 11: يَا أَيُّهَا الَّذِينَ آمَنُوا لَا يَسْخَرْ قَوْمٌ مِنْ قَوْمٍ عَسَىٰ أَنْ يَكُونُوا خَيْرًا مِنْهُمْ وَلَا نِسَاءٌ مِنْ نِسَاءٍ عَسَىٰ أَنْ يَكُنَّ خَيْرًا مِنْهُنَّ ۖ وَلَا تَلْمِزُوا أَنْفُسَكُمْ وَلَا تَنَابَزُوا بِالْأَلْقَابِ ۖ بِئْسَ الِاسْمُ الْفُسُوقُ بَعْدَ الْإِيمَانِ ۚ وَمَنْ لَمْ يَتُبْ فَأُولَٰئِكَ هُمُ الظَّالِمُونَ O you who believe! Let not a group scoff at another group, it may be that the latter are better than the former; nor let (some) women scoff at other women, it may be that the latter are better than the former, nor defame one another, nor insult one another by nicknames. How bad is it, to insult one's brother after having Faith. And whosoever does not repent, then such are indeed Zalimun (unjust, wrong-doers, etc.). Verse 12: يَا أَيُّهَا الَّذِينَ آمَنُوا اجْتَنِبُوا كَثِيرًا مِنَ الظَّنِّ إِنَّ بَعْضَ الظَّنِّ إِثْمٌ ۖ وَلَا تَجَسَّسُوا وَلَا يَغْتَبْ بَعْضُكُمْ بَعْضًا ۚ أَيُحِبُّ أَحَدُكُمْ أَنْ يَأْكُلَ لَحْمَ أَخِيهِ مَيْتًا فَكَرِهْتُمُوهُ ۚ وَاتَّقُوا اللَّهَ ۚ إِنَّ اللَّهَ تَوَّابٌ رَحِيمٌ O you who believe! Avoid much suspicions, indeed some suspicions are sins. And spy not, neither backbite one another. Would one of you like to eat the flesh of his dead brother? You would hate it (so hate backbiting). And fear Allah. Verily, Allah is the One Who accepts repentance, Most Merciful.
Surah Al-Maaida: Verse 38: وَالسَّارِقُ وَالسَّارِقَةُ فَاقْطَعُوا أَيْدِيَهُمَا جَزَاءً بِمَا كَسَبَا نَكَالًا مِنَ اللَّهِ ۗ وَاللَّهُ عَزِيزٌ حَكِيمٌ Cut off (from the wrist joint) the (right) hand of the thief, male or female, as a recompense for that which they committed, a punishment by way of example from Allah. And Allah is All-Powerful, All-Wise. Verse 39: فَمَنْ تَابَ مِنْ بَعْدِ ظُلْمِهِ وَأَصْلَحَ فَإِنَّ اللَّهَ يَتُوبُ عَلَيْهِ ۗ إِنَّ اللَّهَ غَفُورٌ رَحِيمٌ But whosoever repents after his crime and does righteous good deeds, then verily, Allah (God) will pardon him (accept his repentance). Verily, Allah is Oft-Forgiving, Most Merciful.
Surah Aal-i-Imraan: Verse 130: يَا أَيُّهَا الَّذِينَ آمَنُوا لَا تَأْكُلُوا الرِّبَا أَضْعَافًا مُضَاعَفَةً ۖ وَاتَّقُوا اللَّهَ لَعَلَّكُمْ تُفْلِحُونَ O you who believe! Don’t eat Riba (usury) doubled and multiplied, but fear Allah that you may be successful.
Surah Al-Maaida: Verse 3: حُرِّمَتْ عَلَيْكُمُ الْمَيْتَةُ وَالدَّمُ وَلَحْمُ الْخِنْزِيرِ وَمَا أُهِلَّ لِغَيْرِ اللَّهِ بِهِ وَالْمُنْخَنِقَةُ وَالْمَوْقُوذَةُ وَالْمُتَرَدِّيَةُ وَالنَّطِيحَةُ وَمَا أَكَلَ السَّبُعُ إِلَّا مَا ذَكَّيْتُمْ وَمَا ذُبِحَ عَلَى النُّصُبِ وَأَنْ تَسْتَقْسِمُوا بِالْأَزْلَامِ ۚ ذَٰلِكُمْ فِسْقٌ ۗ الْيَوْمَ يَئِسَ الَّذِينَ كَفَرُوا مِنْ دِينِكُمْ فَلَا تَخْشَوْهُمْ وَاخْشَوْنِ ۚ الْيَوْمَ أَكْمَلْتُ لَكُمْ دِينَكُمْ وَأَتْمَمْتُ عَلَيْكُمْ نِعْمَتِي وَرَضِيتُ لَكُمُ الْإِسْلَامَ دِينًا ۚ فَمَنِ اضْطُرَّ فِي مَخْمَصَةٍ غَيْرَ مُتَجَانِفٍ لِإِثْمٍ ۙ فَإِنَّ اللَّهَ غَفُورٌ رَحِيمٌ Forbidden to you (for food) are: Al-Maytatah (the dead animals - cattle-beast not slaughtered), blood, the flesh of swine, and the meat of that which has been slaughtered as a sacrifice for others than Allah, or has been slaughtered for idols, etc., or on which Allah's Name has not been mentioned while slaughtering, and that which has been killed by strangling, or by a violent blow, or by a headlong fall, or by the goring of horns - and that which has been (partly) eaten by a wild animal - unless you are able to slaughter it (before its death) - and that which is sacrificed (slaughtered) on An-Nusub (stone altars). (Forbidden) also is to use arrows seeking luck or decision, (all) that is Fisqun (disobedience of Allah and sin). This day, those who disbelieved have given up all hope of your religion, so don’t fear them, but fear Me. This day, I have perfected your religion for you, completed My Favour upon you, and have chosen for you Islam as your religion. But who is forced by severe hunger, with no inclination to sin (such can eat these above-mentioned meats), then surely, Allah is Oft-Forgiving, Most Merciful.
Surah Al-Baqara: Verse 114: وَمَنْ أَظْلَمُ مِمَّنْ مَنَعَ مَسَاجِدَ اللَّهِ أَنْ يُذْكَرَ فِيهَا اسْمُهُ وَسَعَىٰ فِي خَرَابِهَا ۚ أُولَٰئِكَ مَا كَانَ لَهُمْ أَنْ يَدْخُلُوهَا إِلَّا خَائِفِينَ ۚ لَهُمْ فِي الدُّنْيَا خِزْيٌ وَلَهُمْ فِي الْآخِرَةِ عَذَابٌ عَظِيمٌ And who is more unjust than those who forbid that Allah's Name be glorified and mentioned much (i.e. prayers and invocations, etc.) in Allah's Mosques and strive for their ruin? It was not fitting that such should themselves enter them (Allah's Mosques) except in fear. For them there is disgrace in this world, and they will have a great torment in the Hereafter.
Surah Al-Baqara: Verse 110: وَأَقِيمُوا الصَّلَاةَ وَآتُوا الزَّكَاةَ ۚ وَمَا تُقَدِّمُوا لِأَنْفُسِكُمْ مِنْ خَيْرٍ تَجِدُوهُ عِنْدَ اللَّهِ ۗ إِنَّ اللَّهَ بِمَا تَعْمَلُونَ بَصِيرٌ And perform As-Salat (prayers), and give Zakat (compulsory charity that must be given every year), and whatever of good (deeds that Allah loves) you send forth for yourselves before you, you shall find it with Allah. Certainly, Allah is All-Seer of what you do.
Surah Al-A'raaf: Verse 31: ۞ يَا بَنِي آدَمَ خُذُوا زِينَتَكُمْ عِنْدَ كُلِّ مَسْجِدٍ وَكُلُوا وَاشْرَبُوا وَلَا تُسْرِفُوا ۚ إِنَّهُ لَا يُحِبُّ الْمُسْرِفِينَ
O Children of Adam! Take your adornment (by wearing your clean clothes), while praying and going round (the Tawaf of) the Ka'bah, and eat and drink but waste not by extravagance, certainly He (Allah) likes not Al-Musrifun (those who waste by extravagance). Verse 32: قُلْ مَنْ حَرَّمَ زِينَةَ اللَّهِ الَّتِي أَخْرَجَ لِعِبَادِهِ وَالطَّيِّبَاتِ مِنَ الرِّزْقِ ۚ قُلْ هِيَ لِلَّذِينَ آمَنُوا فِي الْحَيَاةِ الدُّنْيَا خَالِصَةً يَوْمَ الْقِيَامَةِ ۗ كَذَٰلِكَ نُفَصِّلُ الْآيَاتِ لِقَوْمٍ يَعْلَمُونَ Say: "Who has forbidden the adoration with clothes given by Allah, which He has produced for his slaves, and At-Taiyibat [all kinds of Halal (lawful) things] of food?" Say: "They are, in the life of this world, for those who believe, (and) exclusively for them (believers) on the Day of Resurrection (the disbelievers will not share them)." Thus We explain the Ayat (verses, Islamic laws) in detail for people who have knowledge. Verse 33: قُلْ إِنَّمَا حَرَّمَ رَبِّيَ الْفَوَاحِشَ مَا ظَهَرَ مِنْهَا وَمَا بَطَنَ وَالْإِثْمَ وَالْبَغْيَ بِغَيْرِ الْحَقِّ وَأَنْ تُشْرِكُوا بِاللَّهِ مَا لَمْ يُنَزِّلْ بِهِ سُلْطَانًا وَأَنْ تَقُولُوا عَلَى اللَّهِ مَا لَا تَعْلَمُونَ Say: "The things that my Lord has indeed forbidden are Al-Fawahish (great evil sins) whether committed openly or secretly, sins (of all kinds), unrighteous oppression, joining partners (in worship) with Allah for which He has given no authority, and saying things about Allah of which you have no knowledge." Verse 34: وَلِكُلِّ أُمَّةٍ أَجَلٌ ۖ فَإِذَا جَاءَ أَجَلُهُمْ لَا يَسْتَأْخِرُونَ سَاعَةً ۖ وَلَا يَسْتَقْدِمُونَ And every nation has its appointed term; when their term is reached, neither can they delay it nor can they advance it an hour (or a moment). Verse 35: يَا بَنِي آدَمَ إِمَّا يَأْتِيَنَّكُمْ رُسُلٌ مِنْكُمْ يَقُصُّونَ عَلَيْكُمْ آيَاتِي ۙ فَمَنِ اتَّقَىٰ وَأَصْلَحَ فَلَا خَوْفٌ عَلَيْهِمْ وَلَا هُمْ يَحْزَنُونَ O Children of Adam! If there come to you Messengers from amongst you, reciting to you, My Verses, then whosoever becomes pious and righteous, on them shall be no fear, nor shall they grieve. Verse 36: وَالَّذِينَ كَذَّبُوا بِآيَاتِنَا وَاسْتَكْبَرُوا عَنْهَا أُولَٰئِكَ أَصْحَابُ النَّارِ ۖ هُمْ فِيهَا خَالِدُونَ But those who reject Our Ayat (proofs, evidences, verses, lessons, signs, revelations, etc.) and treat them with arrogance, they are the dwellers of the (Hell) Fire, they will abide therein forever. Verse 37: فَمَنْ أَظْلَمُ مِمَّنِ افْتَرَىٰ عَلَى اللَّهِ كَذِبًا أَوْ كَذَّبَ بِآيَاتِهِ ۚ أُولَٰئِكَ يَنَالُهُمْ نَصِيبُهُمْ مِنَ الْكِتَابِ ۖ حَتَّىٰ إِذَا جَاءَتْهُمْ رُسُلُنَا يَتَوَفَّوْنَهُمْ قَالُوا أَيْنَ مَا كُنْتُمْ تَدْعُونَ مِنْ دُونِ اللَّهِ ۖ قَالُوا ضَلُّوا عَنَّا وَشَهِدُوا عَلَىٰ أَنْفُسِهِمْ أَنَّهُمْ كَانُوا كَافِرِينَ Who is more unjust than one who invents a lie against Allah or rejects His Ayat (proofs, evidences, verses, lessons, signs, revelations, etc.)? For such their appointed portion (good things of this worldly life and their period of stay therein) will reach them from the Book (of Decrees) until, when Our Messengers (the angel of death and his assistants) come to them to take their souls, they (the angels) will say: "Where are those whom you used to invoke and worship besides Allah," they will reply, "They have vanished and deserted us." And they will bear witness against themselves, that they were disbelievers. Verse 38: قَالَ ادْخُلُوا فِي أُمَمٍ قَدْ خَلَتْ مِنْ قَبْلِكُمْ مِنَ الْجِنِّ وَالْإِنْسِ فِي النَّارِ ۖ كُلَّمَا دَخَلَتْ أُمَّةٌ لَعَنَتْ أُخْتَهَا ۖ حَتَّىٰ إِذَا ادَّارَكُوا فِيهَا جَمِيعًا قَالَتْ أُخْرَاهُمْ لِأُولَاهُمْ رَبَّنَا هَٰؤُلَاءِ أَضَلُّونَا فَآتِهِمْ عَذَابًا ضِعْفًا مِنَ النَّارِ ۖ قَالَ لِكُلٍّ ضِعْفٌ وَلَٰكِنْ لَا تَعْلَمُونَ (Allah) will say: "Enter you in the company of nations who passed away before you, of men and jinns, into the Fire." Every time a new nation enters, it curses its sister nation (that went before), until they will be gathered all together in the Fire. The last of them will say to the first of them: "Our Lord! These misled us, so give them a double torment of the Fire." He will say: "For each one there is double (torment), but you don’t know." Verse 39: وَقَالَتْ أُولَاهُمْ لِأُخْرَاهُمْ فَمَا كَانَ لَكُمْ عَلَيْنَا مِنْ فَضْلٍ فَذُوقُوا الْعَذَابَ بِمَا كُنْتُمْ تَكْسِبُونَ The first of them will say to the last of them: "You were not better than us, so taste the torment for what you used to earn." Verse 40: إِنَّ الَّذِينَ كَذَّبُوا بِآيَاتِنَا وَاسْتَكْبَرُوا عَنْهَا لَا تُفَتَّحُ لَهُمْ أَبْوَابُ السَّمَاءِ وَلَا يَدْخُلُونَ الْجَنَّةَ حَتَّىٰ يَلِجَ الْجَمَلُ فِي سَمِّ الْخِيَاطِ ۚ وَكَذَٰلِكَ نَجْزِي الْمُجْرِمِينَ Verily, those who belie Our Ayat (proofs, evidences, verses, lessons, signs, revelations, etc.) and are pridefully arrogant towards them (proofs, verses, signs, etc.), for them the gates of heaven will not be opened (to accept and answer their supplications and prayers), and they will not enter Paradise until the camel goes through the eye of the needle (which is impossible). Thus do We recompense the Mujrimun (criminals, sinners, etc.). Verse 41: لَهُمْ مِنْ جَهَنَّمَ مِهَادٌ وَمِنْ فَوْقِهِمْ غَوَاشٍ ۚ وَكَذَٰلِكَ نَجْزِي الظَّالِمِينَ Theirs will be a bed of Hell (Fire), and over them coverings (of Hell-fire). Thus We recompense the Zalimun (unjust and wrong-doers, etc.).
An-Nahl Verse 94: وَلَا تَتَّخِذُوا أَيْمَانَكُمْ دَخَلًا بَيْنَكُمْ فَتَزِلَّ قَدَمٌ بَعْدَ ثُبُوتِهَا وَتَذُوقُوا السُّوءَ بِمَا صَدَدْتُمْ عَنْ سَبِيلِ اللَّهِ ۖ وَلَكُمْ عَذَابٌ عَظِيمٌ And don’t make your oaths, a means of deception among yourselves, lest a foot may slip after being firmly planted, and you may have to taste the evil (punishment in this world) of having hindered (men) from the Path of Allah (i.e. Belief in the Oneness of Allah and His Messenger, Muhammad SAW, fighting in the cause of Allah), and yours will be a great torment (i.e. the Fire of Hell in the Hereafter). Verse 95: وَلَا تَشْتَرُوا بِعَهْدِ اللَّهِ ثَمَنًا قَلِيلًا ۚ إِنَّمَا عِنْدَ اللَّهِ هُوَ خَيْرٌ لَكُمْ إِنْ كُنْتُمْ تَعْلَمُونَ
And purchase not a small gain at the cost of Allah's Covenant. Verily! What is with Allah is better for you if you did but know.
A lot of people turn away from God, Allah, because of fearing not to be forgiven.
4:116 An-Nisaa
إِنَّ اللَّهَ لَا يَغْفِرُ أَنْ يُشْرَكَ بِهِ وَيَغْفِرُ مَا دُونَ ذَٰلِكَ لِمَنْ يَشَاءُ ۚ وَمَنْ يُشْرِكْ بِاللَّهِ فَقَدْ ضَلَّ ضَلَالًا بَعِيدًا
Indeed, Allah does not forgive association with Him, but He forgives other than that for whom He wills. And he who associates others with Allah has certainly gone far astray.
39:53 Az-Zumar
۞ قُلْ يَا عِبَادِيَ الَّذِينَ أَسْرَفُوا عَلَىٰ أَنْفُسِهِمْ لَا تَقْنَطُوا مِنْ رَحْمَةِ اللَّهِ ۚ إِنَّ اللَّهَ يَغْفِرُ الذُّنُوبَ جَمِيعًا ۚ إِنَّهُ هُوَ الْغَفُورُ الرَّحِيمُ
Say, "O My servants who have transgressed against themselves [by sinning], do not despair of the mercy of Allah. Indeed, Allah forgives all sins. Indeed, it is He who is the Forgiving, the Merciful."
39:54 Az-Zumar
وَأَنِيبُوا إِلَىٰ رَبِّكُمْ وَأَسْلِمُوا لَهُ مِنْ قَبْلِ أَنْ يَأْتِيَكُمُ الْعَذَابُ ثُمَّ لَا تُنْصَرُونَ
And return [in repentance] to your Lord and submit to Him before the punishment comes upon you; then you will not be helped.
39:55 Az-Zumar
وَاتَّبِعُوا أَحْسَنَ مَا أُنْزِلَ إِلَيْكُمْ مِنْ رَبِّكُمْ مِنْ قَبْلِ أَنْ يَأْتِيَكُمُ الْعَذَابُ بَغْتَةً وَأَنْتُمْ لَا تَشْعُرُونَ
And follow the best of what was revealed to you from your Lord before the punishment comes upon you suddenly while you do not perceive,
39:56 Az-Zumar
أَنْ تَقُولَ نَفْسٌ يَا حَسْرَتَا عَلَىٰ مَا فَرَّطْتُ فِي جَنْبِ اللَّهِ وَإِنْ كُنْتُ لَمِنَ السَّاخِرِينَ
Lest a soul should say, "Oh [how great is] my regret over what I neglected in regard to Allah and that I was among the mockers."
39:57 Az-Zumar
أَوْ تَقُولَ لَوْ أَنَّ اللَّهَ هَدَانِي لَكُنْتُ مِنَ الْمُتَّقِينَ
Or [lest] it say, "If only Allah had guided me, I would have been among the righteous."
39:58 Az-Zumar
أَوْ تَقُولَ حِينَ تَرَى الْعَذَابَ لَوْ أَنَّ لِي كَرَّةً فَأَكُونَ مِنَ الْمُحْسِنِينَ
Or [lest] it say when it sees the punishment, "If only I had another turn so I could be among the doers of good."
39:59 Az-Zumar
بَلَىٰ قَدْ جَاءَتْكَ آيَاتِي فَكَذَّبْتَ بِهَا وَاسْتَكْبَرْتَ وَكُنْتَ مِنَ الْكَافِرِينَ
But yes, there had come to you My verses, but you denied them and were arrogant, and you were among the disbelievers.
39:60 Az-Zumar
وَيَوْمَ الْقِيَامَةِ تَرَى الَّذِينَ كَذَبُوا عَلَى اللَّهِ وُجُوهُهُمْ مُسْوَدَّةٌ ۚ أَلَيْسَ فِي جَهَنَّمَ مَثْوًى لِلْمُتَكَبِّرِينَ
And on the Day of Resurrection you will see those who lied about Allah [with] their faces blackened. Is there not in Hell a residence for the arrogant?
39:61 Az-Zumar
وَيُنَجِّي اللَّهُ الَّذِينَ اتَّقَوْا بِمَفَازَتِهِمْ لَا يَمَسُّهُمُ السُّوءُ وَلَا هُمْ يَحْزَنُونَ
And Allah will save those who feared Him by their attainment; no evil will touch them, nor will they grieve.
In Islam we believe in God’s messengers and his books, Torah and Gospel, however, some changes were brought by some people leading to disbelief in the oneness of God.
2:285 Al-Baqara
آمَنَ الرَّسُولُ بِمَا أُنْزِلَ إِلَيْهِ مِنْ رَبِّهِ وَالْمُؤْمِنُونَ ۚ كُلٌّ آمَنَ بِاللَّهِ وَمَلَائِكَتِهِ وَكُتُبِهِ وَرُسُلِهِ لَا نُفَرِّقُ بَيْنَ أَحَدٍ مِنْ رُسُلِهِ ۚ وَقَالُوا سَمِعْنَا وَأَطَعْنَا ۖ غُفْرَانَكَ رَبَّنَا وَإِلَيْكَ الْمَصِيرُ
The Messenger has believed in what was revealed to him from his Lord, and [so have] the believers. All of them have believed in Allah and His angels and His books and His messengers, [saying], "We make no distinction between any of His messengers." And they say, "We hear and we obey. [We seek] Your forgiveness, our Lord, and to You is the [final] destination."
2:286 Al-Baqara
لَا يُكَلِّفُ اللَّهُ نَفْسًا إِلَّا وُسْعَهَا ۚ لَهَا مَا كَسَبَتْ وَعَلَيْهَا مَا اكْتَسَبَتْ ۗ رَبَّنَا لَا تُؤَاخِذْنَا إِنْ نَسِينَا أَوْ أَخْطَأْنَا ۚ رَبَّنَا وَلَا تَحْمِلْ عَلَيْنَا إِصْرًا كَمَا حَمَلْتَهُ عَلَى الَّذِينَ مِنْ قَبْلِنَا ۚ رَبَّنَا وَلَا تُحَمِّلْنَا مَا لَا طَاقَةَ لَنَا بِهِ ۖ وَاعْفُ عَنَّا وَاغْفِرْ لَنَا وَارْحَمْنَا ۚ أَنْتَ مَوْلَانَا فَانْصُرْنَا عَلَى الْقَوْمِ الْكَافِرِينَ
Allah does not charge a soul except [with that within] its capacity. It will have [the consequence of] what [good] it has gained, and it will bear [the consequence of] what [evil] it has earned. "Our Lord, do not impose blame upon us if we have forgotten or erred. Our Lord, and lay not upon us a burden like that which You laid upon those before us. Our Lord, and burden us not with that which we have no ability to bear. And pardon us; and forgive us; and have mercy upon us. You are our protector, so give us victory over the disbelieving people."
4:163 An-Nisaa
۞ إِنَّا أَوْحَيْنَا إِلَيْكَ كَمَا أَوْحَيْنَا إِلَىٰ نُوحٍ وَالنَّبِيِّينَ مِنْ بَعْدِهِ ۚ وَأَوْحَيْنَا إِلَىٰ إِبْرَاهِيمَ وَإِسْمَاعِيلَ وَإِسْحَاقَ وَيَعْقُوبَ وَالْأَسْبَاطِ وَعِيسَىٰ وَأَيُّوبَ وَيُونُسَ وَهَارُونَ وَسُلَيْمَانَ ۚ وَآتَيْنَا دَاوُودَ زَبُورًا
Indeed, We have revealed to you, [O Muhammad], as We revealed to Noah and the prophets after him. And we revealed to Abraham, Ishmael, Isaac, Jacob, the Descendants, Jesus, Job, Jonah, Aaron, and Solomon, and to David We gave the book [of Psalms].
4:164 An-Nisaa
وَرُسُلًا قَدْ قَصَصْنَاهُمْ عَلَيْكَ مِنْ قَبْلُ وَرُسُلًا لَمْ نَقْصُصْهُمْ عَلَيْكَ ۚ وَكَلَّمَ اللَّهُ مُوسَىٰ تَكْلِيمًا
And [We sent] messengers about whom We have related [their stories] to you before and messengers about whom We have not related to you. And Allah spoke to Moses with [direct] speech.
4:165 An-Nisaa
رُسُلًا مُبَشِّرِينَ وَمُنْذِرِينَ لِئَلَّا يَكُونَ لِلنَّاسِ عَلَى اللَّهِ حُجَّةٌ بَعْدَ الرُّسُلِ ۚ وَكَانَ اللَّهُ عَزِيزًا حَكِيمًا
[We sent] messengers as bringers of good tidings and warners so that mankind will have no argument against Allah after the messengers. And ever is Allah Exalted in Might and Wise.
9:30 At-Tawba
وَقَالَتِ الْيَهُودُ عُزَيْرٌ ابْنُ اللَّهِ وَقَالَتِ النَّصَارَى الْمَسِيحُ ابْنُ اللَّهِ ۖ ذَٰلِكَ قَوْلُهُمْ بِأَفْوَاهِهِمْ ۖ يُضَاهِئُونَ قَوْلَ الَّذِينَ كَفَرُوا مِنْ قَبْلُ ۚ قَاتَلَهُمُ اللَّهُ ۚ أَنَّىٰ يُؤْفَكُونَ
The Jews say, "Ezra is the son of Allah "; and the Christians say, "The Messiah is the son of Allah." That is their statement from their mouths; they imitate the saying of those who disbelieved [before them]. May Allah destroy them; how are they deluded?
9:31 At-Tawba
اتَّخَذُوا أَحْبَارَهُمْ وَرُهْبَانَهُمْ أَرْبَابًا مِنْ دُونِ اللَّهِ وَالْمَسِيحَ ابْنَ مَرْيَمَ وَمَا أُمِرُوا إِلَّا لِيَعْبُدُوا إِلَٰهًا وَاحِدًا ۖ لَا إِلَٰهَ إِلَّا هُوَ ۚ سُبْحَانَهُ عَمَّا يُشْرِكُونَ
They have taken their scholars and monks as lords besides Allah, and [also] the Messiah, the son of Mary. And they were not commanded except to worship one God; there is no deity except Him. Exalted is He above whatever they associate with Him.
5:72 Al-Maaida
لَقَدْ كَفَرَ الَّذِينَ قَالُوا إِنَّ اللَّهَ هُوَ الْمَسِيحُ ابْنُ مَرْيَمَ ۖ وَقَالَ الْمَسِيحُ يَا بَنِي إِسْرَائِيلَ اعْبُدُوا اللَّهَ رَبِّي وَرَبَّكُمْ ۖ إِنَّهُ مَنْ يُشْرِكْ بِاللَّهِ فَقَدْ حَرَّمَ اللَّهُ عَلَيْهِ الْجَنَّةَ وَمَأْوَاهُ النَّارُ ۖ وَمَا لِلظَّالِمِينَ مِنْ أَنْصَارٍ
They have certainly disbelieved who say, "Allah is the Messiah, the son of Mary" while the Messiah has said, "O Children of Israel, worship Allah, my Lord and your Lord." Indeed, he who associates others with Allah - Allah has forbidden him Paradise, and his refuge is the Fire. And there are not for the wrongdoers any helpers.
5:73 Al-Maaida
لَقَدْ كَفَرَ الَّذِينَ قَالُوا إِنَّ اللَّهَ ثَالِثُ ثَلَاثَةٍ ۘ وَمَا مِنْ إِلَٰهٍ إِلَّا إِلَٰهٌ وَاحِدٌ ۚ وَإِنْ لَمْ يَنْتَهُوا عَمَّا يَقُولُونَ لَيَمَسَّنَّ الَّذِينَ كَفَرُوا مِنْهُمْ عَذَابٌ أَلِيمٌ
They have certainly disbelieved who say, "Allah is the third of three." And there is no god except one God. And if they do not desist from what they are saying, there will surely afflict the disbelievers among them a painful punishment.
5:74 Al-Maaida
أَفَلَا يَتُوبُونَ إِلَى اللَّهِ وَيَسْتَغْفِرُونَهُ ۚ وَاللَّهُ غَفُورٌ رَحِيمٌ
So will they not repent to Allah and seek His forgiveness? And Allah is Forgiving and Merciful.
5:75 Al-Maaida
مَا الْمَسِيحُ ابْنُ مَرْيَمَ إِلَّا رَسُولٌ قَدْ خَلَتْ مِنْ قَبْلِهِ الرُّسُلُ وَأُمُّهُ صِدِّيقَةٌ ۖ كَانَا يَأْكُلَانِ الطَّعَامَ ۗ انْظُرْ كَيْفَ نُبَيِّنُ لَهُمُ الْآيَاتِ ثُمَّ انْظُرْ أَنَّىٰ يُؤْفَكُونَ
The Messiah, son of Mary, was not but a messenger; [other] messengers have passed on before him. And his mother was a supporter of truth. They both used to eat food. Look how We make clear to them the signs; then look how they are deluded.
5:76 Al-Maaida
قُلْ أَتَعْبُدُونَ مِنْ دُونِ اللَّهِ مَا لَا يَمْلِكُ لَكُمْ ضَرًّا وَلَا نَفْعًا ۚ وَاللَّهُ هُوَ السَّمِيعُ الْعَلِيمُ
Say, "Do you worship besides Allah that which holds for you no [power of] harm or benefit while it is Allah who is the Hearing, the Knowing?"
5:77 Al-Maaida
قُلْ يَا أَهْلَ الْكِتَابِ لَا تَغْلُوا فِي دِينِكُمْ غَيْرَ الْحَقِّ وَلَا تَتَّبِعُوا أَهْوَاءَ قَوْمٍ قَدْ ضَلُّوا مِنْ قَبْلُ وَأَضَلُّوا كَثِيرًا وَضَلُّوا عَنْ سَوَاءِ السَّبِيلِ
Say, "O People of the Scripture (the books, Torah and Gospel), do not exceed limits in your religion beyond the truth and do not follow the inclinations of a people who had gone astray before and misled many and have strayed from the soundness of the way."
4:171 An-Nisaa
يَا أَهْلَ الْكِتَابِ لَا تَغْلُوا فِي دِينِكُمْ وَلَا تَقُولُوا عَلَى اللَّهِ إِلَّا الْحَقَّ ۚ إِنَّمَا الْمَسِيحُ عِيسَى ابْنُ مَرْيَمَ رَسُولُ اللَّهِ وَكَلِمَتُهُ أَلْقَاهَا إِلَىٰ مَرْيَمَ وَرُوحٌ مِنْهُ ۖ فَآمِنُوا بِاللَّهِ وَرُسُلِهِ ۖ وَلَا تَقُولُوا ثَلَاثَةٌ ۚ انْتَهُوا خَيْرًا لَكُمْ ۚ إِنَّمَا اللَّهُ إِلَٰهٌ وَاحِدٌ ۖ سُبْحَانَهُ أَنْ يَكُونَ لَهُ وَلَدٌ ۘ لَهُ مَا فِي السَّمَاوَاتِ وَمَا فِي الْأَرْضِ ۗ وَكَفَىٰ بِاللَّهِ وَكِيلًا
O People of the Scripture, do not commit excess in your religion or say about Allah except the truth. The Messiah, Jesus, the son of Mary, was but a messenger of Allah and His word which He directed to Mary and a soul [created at a command] from Him. So believe in Allah and His messengers. And do not say, "Three"; desist - it is better for you. Indeed, Allah is but one God. Exalted is He above having a son. To Him belongs whatever is in the heavens and whatever is on the earth. And sufficient is Allah as Disposer of affairs.
4:172 An-Nisaa
لَنْ يَسْتَنْكِفَ الْمَسِيحُ أَنْ يَكُونَ عَبْدًا لِلَّهِ وَلَا الْمَلَائِكَةُ الْمُقَرَّبُونَ ۚ وَمَنْ يَسْتَنْكِفْ عَنْ عِبَادَتِهِ وَيَسْتَكْبِرْ فَسَيَحْشُرُهُمْ إِلَيْهِ جَمِيعًا
Never would the Messiah disdain to be a servant of Allah, nor would the angels near [to Him]. And whoever disdains His worship and is arrogant - He will gather them to Himself all together.
And in the following Hadiths (sayings of prophet Mohamed peace be upon him) and verses what a practicing Muslim should do:
حَدَّثَنَا أَبُو الْيَمَانِ ، قَالَ: أَخْبَرَنَا شُعَيْبٌ ، عَنِ الزُّهْرِيِّ ، قَالَ: أَخْبَرَنِي أَبُو إِدْرِيسَ عَائِذُ اللَّهِ بْنُ عَبْدِ اللَّهِ ، أَنَّ عُبَادَةَ بْنَ الصَّامِتِ رَضِيَ اللَّهُ عَنْهُ، وَكَانَ شَهِدَ بَدْرًا وَهُوَ أَحَدُ النُّقَبَاءِ لَيْلَةَ الْعَقَبَةِ، أَنَّ رَسُولَ اللَّهِ صَلَّى اللَّهُ عَلَيْهِ وَسَلَّمَ، قَالَ وَحَوْلَهُ عِصَابَةٌ مِنْ أَصْحَابِهِ: بَايِعُونِي عَلَى أَنْ لَا تُشْرِكُوا بِاللَّهِ شَيْئًا، وَلَا تَسْرِقُوا، وَلَا تَزْنُوا، وَلَا تَقْتُلُوا أَوْلَادَكُمْ، وَلَا تَأْتُوا بِبُهْتَانٍ تَفْتَرُونَهُ بَيْنَ أَيْدِيكُمْ وَأَرْجُلِكُمْ، وَلَا تَعْصُوا فِي مَعْرُوفٍ، فَمَنْ وَفَى مِنْكُمْ فَأَجْرُهُ عَلَى اللَّهِ، وَمَنْ أَصَابَ مِنْ ذَلِكَ شَيْئًا فَعُوقِبَ فِي الدُّنْيَا فَهُوَ كَفَّارَةٌ لَهُ، وَمَنْ أَصَابَ مِنْ ذَلِكَ شَيْئًا ثُمَّ سَتَرَهُ اللَّهُ فَهُوَ إِلَى اللَّهِ إِنْ شَاءَ عَفَا عَنْهُ وَإِنْ شَاءَ عَاقَبَهُ، فَبَايَعْنَاهُ عَلَى ذَلِك.
Translation:Narrated Ubadah bin As-Samit (RA): who took part in the battle of Badr and was a Naqib (a person heading a group of six persons), on the night of Al-Aqabah pledge: Allahs Apostle ﷺ said while a group of his companions were around him, "Swear allegiance to me for: 1. Not to join anything in worship along with Allah. 2. Not to steal. 3. Not to commit illegal sexual intercourse. 4. Not to kill your children. 5. Not to accuse an innocent person (to spread such an accusation among people). 6. Not to be disobedient (when ordered) to do good deed". The Prophet ﷺ added: "Whoever among you fulfills his pledge will be rewarded by Allah. And whoever indulges in any one of them (except the ascription of partners to Allah) and gets the punishment in this world, that punishment will be an expiation for that sin. And if one indulges in any of them, and Allah conceals his sin, it is up to Him to forgive or punish him (in the Hereafter)". Ubadah bin As-Samit (RA) added: "So we swore allegiance for these." (points to Allahs Apostle) ﷺ.
حَدَّثَنَا عُبَيْدُ اللَّهِ بْنُ مُوسَى ، قَالَ: أَخْبَرَنَا حَنْظَلَةُ بْنُ أَبِي سُفْيَانَ ، عَنْ عِكْرِمَةَ بْنِ خَالِدٍ ، عَنِ ابْنِ عُمَرَ رَضِيَ اللَّهُ عَنْهُمَا، قَالَ: قَالَ رَسُولُ اللَّهِ صَلَّى اللَّهُ عَلَيْهِ وَسَلَّمَ: بُنِيَ الْإِسْلَامُ عَلَى خَمْسٍ، شَهَادَةِ أَنْ لَا إِلَهَ إِلَّا اللَّهُ وَأَنَّ مُحَمَّدًا رَسُولُ اللَّهِ، وَإِقَامِ الصَّلَاةِ، وَإِيتَاءِ الزَّكَاةِ، وَالْحَجِّ، وَصَوْمِ رَمَضَانَ. الحج لمن استطاع اليه سبيلا*
Translation:Narrated Ibn Umar (RA) : Allahs Apostle ﷺ said: Islam is based on (the following) five (principles): 1. To testify that none has the right to be worshipped but Allah and Muhammad ﷺ is Allahs Apostle. 2. To offer the (compulsory Salat) prayers dutifully and perfectly. 3. To pay Zakat (i.e. obligatory charity). 4. To perform Hajj. (i.e. Pilgrimage to Makkah only if the person is able to do so) 5. To observe fast during the month of Ramadan.
Also, in the following verses behaviours that must be adopted by practicing Muslims:
24:30 An-Noor
قُلْ لِلْمُؤْمِنِينَ يَغُضُّوا مِنْ أَبْصَارِهِمْ وَيَحْفَظُوا فُرُوجَهُمْ ۚ ذَٰلِكَ أَزْكَىٰ لَهُمْ ۗ إِنَّ اللَّهَ خَبِيرٌ بِمَا يَصْنَعُونَ
Tell the believing men to reduce [some] of their vision (lower their gazes) and guard their private parts. That is purer for them. Indeed, Allah is Acquainted with what they do.
24:31 An-Noor
وَقُلْ لِلْمُؤْمِنَاتِ يَغْضُضْنَ مِنْ أَبْصَارِهِنَّ وَيَحْفَظْنَ فُرُوجَهُنَّ وَلَا يُبْدِينَ زِينَتَهُنَّ إِلَّا مَا ظَهَرَ مِنْهَا ۖ وَلْيَضْرِبْنَ بِخُمُرِهِنَّ عَلَىٰ جُيُوبِهِنَّ ۖ وَلَا يُبْدِينَ زِينَتَهُنَّ إِلَّا لِبُعُولَتِهِنَّ أَوْ آبَائِهِنَّ أَوْ آبَاءِ بُعُولَتِهِنَّ أَوْ أَبْنَائِهِنَّ أَوْ أَبْنَاءِ بُعُولَتِهِنَّ أَوْ إِخْوَانِهِنَّ أَوْ بَنِي إِخْوَانِهِنَّ أَوْ بَنِي أَخَوَاتِهِنَّ أَوْ نِسَائِهِنَّ أَوْ مَا مَلَكَتْ أَيْمَانُهُنَّ أَوِ التَّابِعِينَ غَيْرِ أُولِي الْإِرْبَةِ مِنَ الرِّجَالِ أَوِ الطِّفْلِ الَّذِينَ لَمْ يَظْهَرُوا عَلَىٰ عَوْرَاتِ النِّسَاءِ ۖ وَلَا يَضْرِبْنَ بِأَرْجُلِهِنَّ لِيُعْلَمَ مَا يُخْفِينَ مِنْ زِينَتِهِنَّ ۚ وَتُوبُوا إِلَى اللَّهِ جَمِيعًا أَيُّهَ الْمُؤْمِنُونَ لَعَلَّكُمْ تُفْلِحُونَ
And tell the believing women to reduce [some] of their vision (lower their gazes) and guard their private parts and not expose their adornment except that which [necessarily] appears (to cover their bodies in full (the used clothes must not be tight or transparent) except hands and face and to cover the hair) thereof and to wrap [a portion of] their headcovers over their chests and not expose their adornment except to their husbands, their fathers, their husbands' fathers, their sons, their husbands' sons, their brothers, their brothers' sons, their sisters' sons, their women, that which their right hands possess, or those male attendants having no physical desire, or children who are not yet aware of the private aspects of women. And let them not stamp their feet to make known what they conceal of their adornment. And turn to Allah in repentance, all of you, O believers, that you might succeed.
In the following an app to teach Wudu (getting ready for the prayer) and Salat the Islamic compulsory prayers that must be performed 5 times a day:
https://apps.apple.com/app/id1187721510
https://play.google.com/store/apps/datasafety?id=com.salah.osratouna&hl=en
Keep in mind the following Hadiths and verses of the Quran while wishing to offer Salat:
4:43 An-Nisaa
يَا أَيُّهَا الَّذِينَ آمَنُوا لَا تَقْرَبُوا الصَّلَاةَ وَأَنْتُمْ سُكَارَىٰ حَتَّىٰ تَعْلَمُوا مَا تَقُولُونَ وَلَا جُنُبًا إِلَّا عَابِرِي سَبِيلٍ حَتَّىٰ تَغْتَسِلُوا ۚ وَإِنْ كُنْتُمْ مَرْضَىٰ أَوْ عَلَىٰ سَفَرٍ أَوْ جَاءَ أَحَدٌ مِنْكُمْ مِنَ الْغَائِطِ أَوْ لَامَسْتُمُ النِّسَاءَ فَلَمْ تَجِدُوا مَاءً فَتَيَمَّمُوا صَعِيدًا طَيِّبًا فَامْسَحُوا بِوُجُوهِكُمْ وَأَيْدِيكُمْ ۗ إِنَّ اللَّهَ كَانَ عَفُوًّا غَفُورًا
O you who have believed, do not approach prayer while you are intoxicated (drunk or under the effect of drugs) until you know what you are saying or in a state of janabah (have had a lawful sexual intercourse or have had a wet dream) , except those passing through [a place of prayer], until you have washed [your whole body]. And if you are ill or on a journey or one of you comes from the place of relieving himself or you have contacted women and find no water, then seek clean earth and wipe over your faces and your hands [with it]. Indeed, Allah is ever Pardoning and Forgiving.
Narrated `Aisha: Whenever the Prophet (ﷺ) took a bath after Janaba he started by washing his hands and then performed ablution like that for the prayer. After that he would put his fingers in water and move the roots of his hair with them, and then pour three handfuls of water over his head and then pour water all over his body.
حَدَّثَنَا عَبْدُ اللَّهِ بْنُ يُوسُفَ، قَالَ أَخْبَرَنَا مَالِكٌ، عَنْ هِشَامٍ، عَنْ أَبِيهِ، عَنْ عَائِشَةَ، زَوْجِ النَّبِيِّ صلى الله عليه وسلم أَنَّ النَّبِيَّ صلى الله عليه وسلم كَانَ إِذَا اغْتَسَلَ مِنَ الْجَنَابَةِ بَدَأَ فَغَسَلَ يَدَيْهِ، ثُمَّ يَتَوَضَّأُ كَمَا يَتَوَضَّأُ لِلصَّلاَةِ، ثُمَّ يُدْخِلُ أَصَابِعَهُ فِي الْمَاءِ، فَيُخَلِّلُ بِهَا أُصُولَ شَعَرِهِ ثُمَّ يَصُبُّ عَلَى رَأْسِهِ ثَلاَثَ غُرَفٍ بِيَدَيْهِ، ثُمَّ يُفِيضُ الْمَاءَ عَلَى جِلْدِهِ كُلِّهِ.
Narrated Maimuna bint Al-Harith: I placed water for the bath of Allah's Messenger (ﷺ) and put a screen. He poured water over his hands, and washed them once or twice. (The sub-narrator added that he did not remember if she had said thrice or not). Then he poured water with his right hand over his left one and washed his private parts. He rubbed his hand over the earth or the wall and washed it. He rinsed his mouth and washed his nose by putting water in it and blowing it out. He washed his face, forearms and head. He poured water over his body and then withdrew from that place and washed his feet. I presented him a piece of cloth (towel) and he pointed with his hand (that he does not want it) and did not take it.
حَدَّثَنَا مُوسَى بْنُ إِسْمَاعِيلَ، قَالَ حَدَّثَنَا أَبُو عَوَانَةَ، حَدَّثَنَا الأَعْمَشُ، عَنْ سَالِمِ بْنِ أَبِي الْجَعْدِ، عَنْ كُرَيْبٍ، مَوْلَى ابْنِ عَبَّاسٍ عَنِ ابْنِ عَبَّاسٍ، عَنْ مَيْمُونَةَ بِنْتِ الْحَارِثِ، قَالَتْ وَضَعْتُ لِرَسُولِ اللَّهِ صلى الله عليه وسلم غُسْلاً وَسَتَرْتُهُ، فَصَبَّ عَلَى يَدِهِ، فَغَسَلَهَا مَرَّةً أَوْ مَرَّتَيْنِ ـ قَالَ سُلَيْمَانُ لاَ أَدْرِي أَذَكَرَ الثَّالِثَةَ أَمْ لاَ ـ ثُمَّ أَفْرَغَ بِيَمِينِهِ عَلَى شِمَالِهِ، فَغَسَلَ فَرْجَهُ، ثُمَّ دَلَكَ يَدَهُ بِالأَرْضِ أَوْ بِالْحَائِطِ، ثُمَّ تَمَضْمَضَ وَاسْتَنْشَقَ، وَغَسَلَ وَجْهَهُ وَيَدَيْهِ، وَغَسَلَ رَأْسَهُ، ثُمَّ صَبَّ عَلَى جَسَدِهِ، ثُمَّ تَنَحَّى فَغَسَلَ قَدَمَيْهِ، فَنَاوَلْتُهُ خِرْقَةً، فَقَالَ بِيَدِهِ هَكَذَا، وَلَمْ يُرِدْهَا.
Finally, it’s advisable to read the Quran in full to develop better understanding about Islam and about being a Muslim. Also, the collection of Hadiths, sayings, of prophet Mohamed peace be upon such as Sahih Bukhari ( https://sunnah.com/bukhari) offers further guidance to be followed.
41:13 Fussilat
فَإِنْ أَعْرَضُوا فَقُلْ أَنْذَرْتُكُمْ صَاعِقَةً مِثْلَ صَاعِقَةِ عَادٍ وَثَمُودَ
But if they turn away, then say, "I have warned you of a thunderbolt like the thunderbolt [that struck] 'Aad and Thamud.
41:14 Fussilat
إِذْ جَاءَتْهُمُ الرُّسُلُ مِنْ بَيْنِ أَيْدِيهِمْ وَمِنْ خَلْفِهِمْ أَلَّا تَعْبُدُوا إِلَّا اللَّهَ ۖ قَالُوا لَوْ شَاءَ رَبُّنَا لَأَنْزَلَ مَلَائِكَةً فَإِنَّا بِمَا أُرْسِلْتُمْ بِهِ كَافِرُونَ
[That occurred] when the messengers had come to them before them and after them, [saying], "Worship not except Allah." They said, "If our Lord had willed, He would have sent down the angels, so indeed we, in that with which you have been sent, are disbelievers."
41:15 Fussilat
فَأَمَّا عَادٌ فَاسْتَكْبَرُوا فِي الْأَرْضِ بِغَيْرِ الْحَقِّ وَقَالُوا مَنْ أَشَدُّ مِنَّا قُوَّةً ۖ أَوَلَمْ يَرَوْا أَنَّ اللَّهَ الَّذِي خَلَقَهُمْ هُوَ أَشَدُّ مِنْهُمْ قُوَّةً ۖ وَكَانُوا بِآيَاتِنَا يَجْحَدُونَ
As for 'Aad, they were arrogant upon the earth without right and said, "Who is greater than us in strength?" Did they not consider that Allah who created them was greater than them in strength? But they were rejecting Our signs.
41:16 Fussilat
فَأَرْسَلْنَا عَلَيْهِمْ رِيحًا صَرْصَرًا فِي أَيَّامٍ نَحِسَاتٍ لِنُذِيقَهُمْ عَذَابَ الْخِزْيِ فِي الْحَيَاةِ الدُّنْيَا ۖ وَلَعَذَابُ الْآخِرَةِ أَخْزَىٰ ۖ وَهُمْ لَا يُنْصَرُونَ
So We sent upon them a screaming wind during days of misfortune to make them taste the punishment of disgrace in the worldly life; but the punishment of the Hereafter is more disgracing, and they will not be helped.
41:17 Fussilat
وَأَمَّا ثَمُودُ فَهَدَيْنَاهُمْ فَاسْتَحَبُّوا الْعَمَىٰ عَلَى الْهُدَىٰ فَأَخَذَتْهُمْ صَاعِقَةُ الْعَذَابِ الْهُونِ بِمَا كَانُوا يَكْسِبُونَ
And as for Thamud, We guided them, but they preferred blindness over guidance, so the thunderbolt of humiliating punishment seized them for what they used to earn.
41:18 Fussilat
وَنَجَّيْنَا الَّذِينَ آمَنُوا وَكَانُوا يَتَّقُونَ
And We saved those who believed and used to fear Allah.
41:19 Fussilat
وَيَوْمَ يُحْشَرُ أَعْدَاءُ اللَّهِ إِلَى النَّارِ فَهُمْ يُوزَعُونَ
And [mention, O Muhammad], the Day when the enemies of Allah will be gathered to the Fire while they are [driven] assembled in rows,
41:20 Fussilat
حَتَّىٰ إِذَا مَا جَاءُوهَا شَهِدَ عَلَيْهِمْ سَمْعُهُمْ وَأَبْصَارُهُمْ وَجُلُودُهُمْ بِمَا كَانُوا يَعْمَلُونَ
Until, when they reach it, their hearing and their eyes and their skins will testify against them of what they used to do.
41:21 Fussilat
وَقَالُوا لِجُلُودِهِمْ لِمَ شَهِدْتُمْ عَلَيْنَا ۖ قَالُوا أَنْطَقَنَا اللَّهُ الَّذِي أَنْطَقَ كُلَّ شَيْءٍ وَهُوَ خَلَقَكُمْ أَوَّلَ مَرَّةٍ وَإِلَيْهِ تُرْجَعُونَ
And they will say to their skins, "Why have you testified against us?" They will say, "We were made to speak by Allah, who has made everything speak; and He created you the first time, and to Him you are returned.
41:22 Fussilat
وَمَا كُنْتُمْ تَسْتَتِرُونَ أَنْ يَشْهَدَ عَلَيْكُمْ سَمْعُكُمْ وَلَا أَبْصَارُكُمْ وَلَا جُلُودُكُمْ وَلَٰكِنْ ظَنَنْتُمْ أَنَّ اللَّهَ لَا يَعْلَمُ كَثِيرًا مِمَّا تَعْمَلُونَ
And you were not covering yourselves, lest your hearing testify against you or your sight or your skins, but you assumed that Allah does not know much of what you do.
41:23 Fussilat
وَذَٰلِكُمْ ظَنُّكُمُ الَّذِي ظَنَنْتُمْ بِرَبِّكُمْ أَرْدَاكُمْ فَأَصْبَحْتُمْ مِنَ الْخَاسِرِينَ
And that was your assumption which you assumed about your Lord. It has brought you to ruin, and you have become among the losers."
41:24 Fussilat
فَإِنْ يَصْبِرُوا فَالنَّارُ مَثْوًى لَهُمْ ۖ وَإِنْ يَسْتَعْتِبُوا فَمَا هُمْ مِنَ الْمُعْتَبِينَ
So [even] if they are patient, the Fire is a residence for them; and if they ask to appease [Allah], they will not be of those who are allowed to appease.
41:25 Fussilat
۞ وَقَيَّضْنَا لَهُمْ قُرَنَاءَ فَزَيَّنُوا لَهُمْ مَا بَيْنَ أَيْدِيهِمْ وَمَا خَلْفَهُمْ وَحَقَّ عَلَيْهِمُ الْقَوْلُ فِي أُمَمٍ قَدْ خَلَتْ مِنْ قَبْلِهِمْ مِنَ الْجِنِّ وَالْإِنْسِ ۖ إِنَّهُمْ كَانُوا خَاسِرِينَ
And We appointed for them companions who made attractive to them what was before them and what was behind them [of sin], and the word has come into effect upon them among nations which had passed on before them of jinn and men. Indeed, they [all] were losers.
41:26 Fussilat
وَقَالَ الَّذِينَ كَفَرُوا لَا تَسْمَعُوا لِهَٰذَا الْقُرْآنِ وَالْغَوْا فِيهِ لَعَلَّكُمْ تَغْلِبُونَ
And those who disbelieve say, "Do not listen to this Qur'an and speak noisily during [the recitation of] it that perhaps you will overcome."
41:27 Fussilat
فَلَنُذِيقَنَّ الَّذِينَ كَفَرُوا عَذَابًا شَدِيدًا وَلَنَجْزِيَنَّهُمْ أَسْوَأَ الَّذِي كَانُوا يَعْمَلُونَ
But We will surely cause those who disbelieve to taste a severe punishment, and We will surely recompense them for the worst of what they had been doing.
41:28 Fussilat
ذَٰلِكَ جَزَاءُ أَعْدَاءِ اللَّهِ النَّارُ ۖ لَهُمْ فِيهَا دَارُ الْخُلْدِ ۖ جَزَاءً بِمَا كَانُوا بِآيَاتِنَا يَجْحَدُونَ
That is the recompense of the enemies of Allah - the Fire. For them therein is the home of eternity as recompense for what they, of Our verses, were rejecting.
41:29 Fussilat
وَقَالَ الَّذِينَ كَفَرُوا رَبَّنَا أَرِنَا اللَّذَيْنِ أَضَلَّانَا مِنَ الْجِنِّ وَالْإِنْسِ نَجْعَلْهُمَا تَحْتَ أَقْدَامِنَا لِيَكُونَا مِنَ الْأَسْفَلِينَ
And those who disbelieved will [then] say, "Our Lord, show us those who misled us of the jinn and men [so] we may put them under our feet that they will be among the lowest."
41:30 Fussilat
إِنَّ الَّذِينَ قَالُوا رَبُّنَا اللَّهُ ثُمَّ اسْتَقَامُوا تَتَنَزَّلُ عَلَيْهِمُ الْمَلَائِكَةُ أَلَّا تَخَافُوا وَلَا تَحْزَنُوا وَأَبْشِرُوا بِالْجَنَّةِ الَّتِي كُنْتُمْ تُوعَدُونَ
Indeed, those who have said, "Our Lord is Allah " and then remained on a right course - the angels will descend upon them, [saying], "Do not fear and do not grieve but receive good tidings of Paradise, which you were promised.
41:31 Fussilat
نَحْنُ أَوْلِيَاؤُكُمْ فِي الْحَيَاةِ الدُّنْيَا وَفِي الْآخِرَةِ ۖ وَلَكُمْ فِيهَا مَا تَشْتَهِي أَنْفُسُكُمْ وَلَكُمْ فِيهَا مَا تَدَّعُونَ
We [angels] were your allies in worldly life and [are so] in the Hereafter. And you will have therein whatever your souls desire, and you will have therein whatever you request [or wish]
41:32 Fussilat
نُزُلًا مِنْ غَفُورٍ رَحِيمٍ
As accommodation from a [Lord who is] Forgiving and Merciful."
41:33 Fussilat
وَمَنْ أَحْسَنُ قَوْلًا مِمَّنْ دَعَا إِلَى اللَّهِ وَعَمِلَ صَالِحًا وَقَالَ إِنَّنِي مِنَ الْمُسْلِمِينَ
And who is better in speech than one who invites to Allah and does righteousness and says, "Indeed, I am of the Muslims."
41:34 Fussilat
وَلَا تَسْتَوِي الْحَسَنَةُ وَلَا السَّيِّئَةُ ۚ ادْفَعْ بِالَّتِي هِيَ أَحْسَنُ فَإِذَا الَّذِي بَيْنَكَ وَبَيْنَهُ عَدَاوَةٌ كَأَنَّهُ وَلِيٌّ حَمِيمٌ
And not equal are the good deed and the bad. Repel [evil] by that [deed] which is better; and thereupon the one whom between you and him is enmity [will become] as though he was a devoted friend.
41:35 Fussilat
وَمَا يُلَقَّاهَا إِلَّا الَّذِينَ صَبَرُوا وَمَا يُلَقَّاهَا إِلَّا ذُو حَظٍّ عَظِيمٍ
But none is granted it except those who are patient, and none is granted it except one having a great portion [of good].
41:36 Fussilat
وَإِمَّا يَنْزَغَنَّكَ مِنَ الشَّيْطَانِ نَزْغٌ فَاسْتَعِذْ بِاللَّهِ ۖ إِنَّهُ هُوَ السَّمِيعُ الْعَلِيمُ
And if there comes to you from Satan an evil suggestion, then seek refuge in Allah. Indeed, He is the Hearing, the Knowing.
41:37 Fussilat
وَمِنْ آيَاتِهِ اللَّيْلُ وَالنَّهَارُ وَالشَّمْسُ وَالْقَمَرُ ۚ لَا تَسْجُدُوا لِلشَّمْسِ وَلَا لِلْقَمَرِ وَاسْجُدُوا لِلَّهِ الَّذِي خَلَقَهُنَّ إِنْ كُنْتُمْ إِيَّاهُ تَعْبُدُونَ
And of His signs are the night and day and the sun and moon. Do not prostrate to the sun or to the moon, but prostate to Allah, who created them, if it should be Him that you worship.
41:38 Fussilat
فَإِنِ اسْتَكْبَرُوا فَالَّذِينَ عِنْدَ رَبِّكَ يُسَبِّحُونَ لَهُ بِاللَّيْلِ وَالنَّهَارِ وَهُمْ لَا يَسْأَمُونَ ۩
But if they are arrogant - then those who are near your Lord exalt Him by night and by day, and they do not become weary.
41:39 Fussilat
وَمِنْ آيَاتِهِ أَنَّكَ تَرَى الْأَرْضَ خَاشِعَةً فَإِذَا أَنْزَلْنَا عَلَيْهَا الْمَاءَ اهْتَزَّتْ وَرَبَتْ ۚ إِنَّ الَّذِي أَحْيَاهَا لَمُحْيِي الْمَوْتَىٰ ۚ إِنَّهُ عَلَىٰ كُلِّ شَيْءٍ قَدِيرٌ
And of His signs is that you see the earth stilled, but when We send down upon it rain, it shakes and grows. Indeed, He who has given it life is the Giver of Life to the dead. Indeed, He is over all things competent.
41:40 Fussilat
إِنَّ الَّذِينَ يُلْحِدُونَ فِي آيَاتِنَا لَا يَخْفَوْنَ عَلَيْنَا ۗ أَفَمَنْ يُلْقَىٰ فِي النَّارِ خَيْرٌ أَمْ مَنْ يَأْتِي آمِنًا يَوْمَ الْقِيَامَةِ ۚ اعْمَلُوا مَا شِئْتُمْ ۖ إِنَّهُ بِمَا تَعْمَلُونَ بَصِيرٌ
Indeed, those who inject deviation into Our verses are not concealed from Us. So, is he who is cast into the Fire better or he who comes secure on the Day of Resurrection? Do whatever you will; indeed, He (God, Allah) is Seeing what you do.
-
 @ 9bde4214:06ca052b
2025-04-22 17:09:47
@ 9bde4214:06ca052b
2025-04-22 17:09:47“It isn’t obvious that the world had to work this way. But somehow the universe smiles on encryption.”
hzrd149 & Gigi take a stroll along the shore of cryptographic identities.
This dialogue explores how cryptographic signatures fundamentally shift power dynamics in social networks, moving control from servers to key holders. We discuss the concept of "setting data free" through cryptographic verification, the evolving role of relays in the ecosystem, and the challenges of building trust in decentralized systems. We examine the tension between convenience and decentralization, particularly around features like private data and data synchronization. What are the philosophical foundations of building truly decentralized social networks? And how can small architectural decisions have profound implications for user autonomy and data sovereignty?
Movies mentioned:
- 2001: A Space Odyssey (1968)
- Soylent Green (1973)
- Close Encounters of the Third Kind (1977)
- Johnny Mnemonic (1995)
- The Matrix (1999)
In this dialogue: - Hzrd's past conversations: Bowls With Buds 316 & 361 - Running into a water hose - Little difference, big effect - Signing data moves the power to the key holders - Self-signing data sets the data free - Relay specialization - Victor's Amethyst relay guide - Encryption and decryption is expensive - is it worth it? - The magic of nostr is that stuff follows you around - What should be shown? What should be hidden? - Don't lie to users. Never show outdated data. - Nostr is raw and immediate - How quickly you get used to things working - Legacy web always tries to sell you something - Lying, lag, frustration - How NoStrudel grew - NoStrudel notifications - Data visualization and dashboards - Building in public and discussing in public - Should we remove DMs? - Nostr as a substrate for lookups - Using nostr to exchange Signal or SimpleX credentials - How private is a group chat? - Is a 500-people group chat ever private? - Pragmatism vs the engineering mindset - The beauty and simplicity of nostr - Anti-patterns in nostr - Community servers and private relays - Will vibe coding fix (some of the) things? - Small specialized components VS frameworks - Technology vs chairs (and cars, and tractors, and books) - The problem of being greedy - Competitive silos VS synergistic cooperation - Making things easy vs barriers of entry - Value4value for music and other artists - Adding code vs removing code - Pablo's Roo setup and DVMCP - Platform permission slips vs cryptographic identities - Micropayments vs Subscription Hell - PayPerQ - Setting our user-generated data free - The GNU/Linux approach and how it beat Microsoft - Agents learning automatically thanks to snippets published on nostr - Taxi drivers, GPS, and outsourcing understanding - Wizards VS vibe coders - Age differences, Siri, and Dragon Naturally Speaking - LLMs as a human interface to call tools - Natural language vs math and computer language - Natural language has to be fuzzy, because the world is fuzzy - Language and concepts as compression - Hzrd watching The Matrix (1999) for the first time - Soylent Green, 2001, Close Encounters of the 3rd Kind, Johnny Mnemonic - Are there coincidences? - Why are LLMs rising at the same time that cryptography identities are rising? - "The universe smiles at encryption" - The universe does not smile upon closed silos - The cost of applying force from the outside - Perfect copies, locality, and the concept of "the original" - Perfect memory would be a curse, not a blessing - Organic forgetting VS centralized forgetting - Forgetting and dying needs to be effortless - (it wasn't for IPFS, and they also launched a shitcoin) - Bitcoin makes is cheap to figure out what to dismiss - Would you like to have a 2nd brain? - Trust and running LLMs locally - No need for API keys - Adjacent communities: local-first, makers and hackers, etc. - Removing the character limit was a mistake - Browsing mode vs reading mode - The genius of tweets and threads - Vibe-coding and rust-multiplatform - Global solutions vs local solutions - The long-term survivability of local-first - All servers will eventually go away. Your private key won't. - It's normal to pay your breakfast with sats now - Nostr is also a normal thing now, at least for us - Hzrd's bakery - "Send Gigi a DM that says GM" - and it just works - The user is still in control, thanks to Amber - We are lacking in nostr signing solutions - Alby's permission system as a step in the right direction - We have to get better at explaining that stuff - What we do, why we care, why we think it's important
-
 @ 9bde4214:06ca052b
2025-04-22 17:00:55
@ 9bde4214:06ca052b
2025-04-22 17:00:55"What should the next iteration of the internet look like?"
Paul & Gigi pray for a better tomorrow.
Books mentioned:
- The Bible
- I, Pencil by Leonard E. Read
- Don't make me think! by Steve Krug
- The Sovereign Individual by James Dale Davidson and William Rees-Mogg
In this dialogue:
- Paul and his awesome nostr t-shirt
- Are we all just nostalgic?
- Where did the optimism of computing and the information superhighway go?
- We went from interop to pay-to-unlock.
- Do we have to live in the digital gulags forever?
- Homecooked meals and homecooked apps
- Paper straws and the downfall of Western Civilization
- "You need to be okay with people getting rekt"
- If the car would be introduced today, it would be illegal
- Bravery and personal responsibility
- "nostr will only be what diehards will build it to be"
- Bad teleology is built into the current (non-nostr) app landscape
- "You can get a lot of the upside without holding your own keys”
- “...but you can't get ALL of the upside!"
- Expressiveness and free speech online
- Freedom of Speech, Freedom of Assembly, and Financial Freedom in Cyberspace
- Self-publishing vs platform publishing
- Information calories. Can we count them?
- Don't make me think!
- Is not being forced to think part of the problem?
- Mutiny & bitcoin UX that's too easy
- Games and costly mistakes
- The early days: software distribution via print magazines
- Prompting allows you to define your own teleology
- Vibe coding and Cursor
- "The hard part is to figure out what you want."
- "What should the next iteration of the internet look like?"
- GenZ doesn't know shit about files and folders
- Why files are great
- Gigi's SyncThing & Standard Notes setup
- File-based apps like Smart AudioBook Player
- Reading apps like Pocket, Instapaper, and Readwise Reader
- Saving all the things & linking stuff together
- Clips of podcasts and videos, e.g. Fountain
- A Commonplace Book to cyberspace
- Creating a "Family Bible" app
- If you want to maximize profits in the attention economy, you have to get users addicted
- (Zaps potentially fix this, as you wouldn’t zap a car crash)
- Let computers do computer work, let humans be humans
- "The end is not being on the computer"
- Solo private / group private / public
- Liberal vs Conservative sentiment in social environments
- Whom to care about?
- Web of trust & our understanding of it
- Forgiveness, Trust, and Repeat Games
- Tit-for-tat and forgiving tit-for-tat
- Three strikes and you're out!
- "Choose your gulag" is the alternative to nostr
- 7-generation thinking
- 2140
- The Sovereign Individual is embedded in a social structure, always
- I, Pencil
- Jungle vs Civilization
- Fiat = because I said so (“Fiat Lux” - Let there be light)
- Do we need leaders in bitcoin?
- Peterson Fallacy / God vs Bitcoin
- Jesus early followers were the Followers of The Way
- Zaps are not payments
- Zaps are not "tips"
- Bitstein & Pierre: The Reorg
- Vervaeke: “Where do you go for wisdom?”
- Rough consensus and Pieter Wuille
- "There is no such thing as a leaderless system"
- Wisdom in cyberspace
- Can we build wise tools?
- Prompting the Bible, ChristGPT, and Bible Slop
- Gell-Mann amnesia effect
- Vervaekes AI argument: The Coming Thresholds and The Path We Must Take
- Where do new ideas come from?
- Sandwich prompting style (HLDD / LLDD)
- The Tale of John Henry
- Silicon Sages
- Conscience and The Muse
- Hypermedia and HyperNote
- Glassholes, Google Glasses, and wearable technology
- Prompting & Praying for An Internet Worth Having
-
 @ df173277:4ec96708
2025-02-07 00:41:34
@ df173277:4ec96708
2025-02-07 00:41:34Building Our Confidential Backend on Secure Enclaves
With our newly released private and confidential Maple AI and the open sourcing of our OpenSecret platform code, I'm excited to present this technical primer on how we built our confidential compute platform leveraging secure enclaves. By combining AWS Nitro enclaves with end-to-end encryption and reproducible builds, our platform gives developers and end users the confidence that user data is protected, even at runtime, and that the code operating on their data has not been tampered with.
Auth and Databases Today
As developers, we live in an era where protecting user data means "encryption at rest," plus some access policies and procedures. Developers typically run servers that:
- Need to register users (authentication).
- Collect and process user data in business-specific ways, often on the backend.
Even if data is encrypted at rest, it's commonly unlocked with a single master key or credentials the server holds. This means that data is visible during runtime to the application, system administrators, and potentially to the hosting providers. This scenario makes it difficult (or impossible) to guarantee that sensitive data isn't snooped on, memory-dumped, or used in unauthorized ways (for instance, training AI models behind the scenes).
"Just Trust Us" Isn't Good Enough
In a traditional server architecture, users have to take it on faith that the code handling their data is the same code the operator claims to be running. Behind the scenes, applications can be modified or augmented to forward private information elsewhere, and there is no transparent way for users to verify otherwise. This lack of proof is unsettling, especially for services that process or store highly confidential data.
Administrators, developers, or cloud providers with privileged access can inspect memory in plaintext, attach debuggers, or gain complete visibility into stored information. Hackers who compromise these privileged levels can directly access sensitive data. Even with strict policies or promises of good conduct, the reality is that technical capabilities and misconfigurations can override words on paper. If a server master key can decrypt your data or can be accessed by an insider with root permissions, then "just trust us" loses much of its credibility.
The rise of AI platforms amplifies this dilemma. User data, often full of personal details, gets funneled into large-scale models that might be training or fine-tuning behind the scenes. Relying on vague assurances that "we don't look at your data" is no longer enough to prevent legitimate concerns about privacy and misuse. Now more than ever, providing a strong, verifiable guarantee that data remains off-limits, even when actively processed, has become a non-negotiable requirement for trustworthy services.
Current Attempts at Securing Data
 Current User Experience of E2EE Apps
Current User Experience of E2EE AppsWhile properly securing data is not easy, it isn't to say that no one is trying. Some solutions use end-to-end encryption (E2EE), where user data is encrypted client-side with a password or passphrase, so not even the server operator can decrypt it. That approach can be quite secure, but it also has its limitations:
- Key Management Nightmares: If a user forgets their passphrase, the data is effectively lost, and there's no way to recover it from the developer's side.
- Feature Limitations: Complex server-side operations (like offline/background tasks, AI queries, real-time collaboration, or heavy computation) can't easily happen if the server is never capable of processing decrypted data.
- Platform Silos: Some solutions rely on iCloud, Google Drive, or local device storage. That can hamper multi-device usage or multi-OS compatibility.
Other approaches include self-hosting. However, these either burden users with dev ops overhead or revert to the "trust me" model for the server if you "self-host" on a cloud provider.
Secure Enclaves
The Hybrid Approach
Secure enclaves offer a compelling middle ground. They combine the privacy benefits of keeping data secure from prying admins while still allowing meaningful server-side computation. In a nutshell, an enclave is a protected environment within a machine, isolated at the hardware level, so that even if the OS or server is compromised, the data and code inside the enclave remain hidden.
 App Service Running Inside Secure Enclave
App Service Running Inside Secure EnclaveHigh-Level Goal of Enclaves
Enclaves, also known under the broader umbrella of confidential computing, aim to:\ • Lock down data so that only authorized code within the enclave can process the original plaintext data.\ • Deny external inspection by memory dumping, attaching a debugger, or intercepting plaintext network traffic.\ • Prove to external users or services that an enclave is running unmodified, approved code (this is where remote attestation comes in).
Different Secure Enclave Solutions
AMD SEV (Secure Encrypted Virtualization) encrypts an entire virtual machine's memory so that even a compromised hypervisor cannot inspect or modify guest data. Its core concept is "lift-and-shift" security. No application refactoring is required because hardware-based encryption automatically protects the OS and all VM applications. Later enhancements (SEV-ES and SEV-SNP) added encryption of CPU register states and memory integrity protections, further limiting hypervisor tampering. This broad coverage means the guest OS is included in the trusted boundary. AMD SEV has matured into a robust solution for confidential VMs in multi-tenant clouds.
Intel TDX (Trust Domain Extensions) shifts from process-level enclaves to full VM encryption, allowing an entire guest operating system and its applications to run in an isolated "trust domain." Like AMD SEV, Intel TDX encrypts and protects all memory the VM uses from hypervisors or other privileged software, so developers do not need to refactor their code to benefit from hardware-based confidentiality. This broader scope addresses many SGX limitations, such as strict memory bounds and the need to split out enclave-specific logic, and offers a more straightforward "lift-and-shift" path for running existing workloads privately. While SGX is now deprecated, TDX carries forward the core confidential computing principles but applies them at the virtual machine level for more substantial isolation, easier deployment, and the ability to scale up to large, memory-intensive applications.
Apple Secure Enclave and Private Compute is a dedicated security coprocessor embedded in most Apple devices (iPhones, iPads, Macs) and now extended to Apple's server-side AI infrastructure. It runs its own microkernel, has hardware-protected memory, and securely manages operations such as biometric authentication, key storage, and cryptographic tasks. Apple's "Private Compute" approach in the cloud brings similar enclave capabilities to server-based AI, enabling on-device-grade privacy even when requests are processed in Apple's data centers.
AWS Nitro Enclaves carve out a tightly isolated "mini-VM" from a parent EC2 instance, with its own vCPUs and memory guarded by dedicated Nitro cards. The enclave has no persistent storage and no external network access, significantly reducing the attack surface. Communication with the parent instance occurs over a secure local channel (vsock), and AWS offers hardware-based attestation so that secrets (e.g., encryption keys from AWS KMS) can be accessed only to the correct enclave. This design helps developers protect sensitive data or code even if the main EC2 instance's OS is compromised.
NVIDIA GPU TEEs (Hopper H100 and Blackwell) extend confidential computing to accelerated workloads by encrypting data in GPU memory and ensuring that even a privileged host cannot view or tamper with it. Data moving between CPU and GPU is encrypted in transit, so sensitive model weights or inputs remain protected during AI training or inference. NVIDIA's hardware and drivers handle secure data paths under the hood, allowing confidential large language model (LLM) workloads and other GPU-accelerated computations to run with minimal performance overhead and strong security guarantees.
Key Benefits
One major advantage of enclaves is their ability to keep memory completely off-limits to outside prying eyes. Even administrators who can normally inspect processes at will are blocked from peeking into the enclave's protected memory space. The enclave model is a huge shift in the security model: it prevents casual inspection and defends against sophisticated memory dumping techniques that might otherwise leak secrets or sensitive data.
Another key benefit centers on cryptographic keys that are never exposed outside the enclave. Only verified code running inside the enclave environment can run decryption or signing operations, and it can only do so while that specific code is running. This ensures that compromised hosts or rogue processes, even those with high-level privileges, are unable to intercept or misuse the keys because the keys remain strictly within the trusted boundary of the hardware.
Enclaves can also offer the power of remote attestation, allowing external clients or systems to confirm that they're speaking to an authentic, untampered enclave. By validating the hardware's integrity measurements and enclave-specific proofs, the remote party can be confident in the underlying security properties, an important guarantee in multi-tenant environments or whenever trust boundaries extend across different organizations and networks.
Beyond that, reproducible builds can create a verifiable fingerprint proving which binary runs in the enclave. This is a step above a simple "trust us" approach. Anyone can independently recreate the enclave image and verify the resulting cryptographic hash by using a reproducible build system (for example, our NixOS-based solution). If it matches, then users and developers know precisely how code handles their data, boosting confidence that no hidden changes exist.
It's worth noting that although enclaves shield you from software devs, cloud providers, and insider threats, you do have to trust the hardware vendor (Intel, AMD, Apple, AWS, or NVIDIA) to implement their microcode and firmware securely. The entire enclave model could be theoretically undermined if a CPU maker's root keys or manufacturing process were compromised. Fortunately, these companies undergo extensive audits and firmware validations (often with third-party researchers), and their remote attestation mechanisms allow you to confirm specific firmware versions before trusting an enclave. While this adds a layer of "vendor trust," it's still a far more contained risk than trusting an entire operating system or cloud stack, so enclaves remain a strong step forward in practical, confidential computing.
How We Use Secure Enclaves
Now that we've covered the general idea of enclaves let's look at how we specifically implement them in OpenSecret, our developer platform for handling user auth, private keys, data encryption, and AI workloads.
Our Stack: AWS Nitro + Nvidia TEE
• AWS Nitro Enclaves for the backend: All critical logic, authentication, private key management, and data encryption/decryption run inside an AWS Nitro Enclave.
• Nvidia Trusted Execution for AI: For large AI inference (such as the Llama 3.3 70B model), we utilize Nvidia's GPU-based TEEs to protect even GPU memory. This means users can feed sensitive data to the AI model without exposing it in plaintext to the GPU providers or us as the operator. Edgeless Systems is our Nvidia TEE provider, and due to the power of enclave verification, we don't need to worry about who runs the GPUs. We know requests can't be inspected or tampered with.
End-to-End Encryption from Client to Enclave
 Client-side Enclave Attestation from Maple AI
Client-side Enclave Attestation from Maple AIBefore login or data upload, the user/client verifies the enclave attestation from our platform. This process proves that the specific Nitro Enclave is genuine and runs the exact code we've published. You can check this out live on Maple AI's attestation page.
Based on the attestation, the client establishes a secure ephemeral communication channel that only that enclave can decrypt. While we take advantage of SSL, it is typically not terminated inside the enclave itself. To ensure there's full encrypted data transfer all the way through to the enclave, we establish this additional handshake based on the attestation document that is used for all API requests during the client session.
From there, the user's credentials, private keys, and data pass through this secure channel directly into the enclave, where they are decrypted and processed according to the user's request.
In-Enclave Operations
At the core of OpenSecret's approach is the conviction that security-critical tasks must happen inside the enclave, where even administrative privileges or hypervisor-level compromise cannot expose plaintext data. This encompasses everything from when a user logs in to creating and managing sensitive cryptographic keys. By confining these operations to a protected hardware boundary, developers can focus on building their applications without worrying about accidental data leaks, insider threats, or malicious attempts to harvest credentials. The enclave becomes the ultimate gatekeeper: it controls how data flows and ensures that nothing escapes in plain form.
 User Auth Methods running inside Enclave
User Auth Methods running inside EnclaveA primary example is user authentication. All sign-in workflows, including email/password, OAuth, and upcoming passkey-based methods, are handled entirely within the enclave. As soon as a user's credentials enter our platform through the encrypted channel, they are routed straight into the protected environment, bypassing the host's operating system or any potential snooping channels. From there, authentication and session details remain in the enclave, ensuring that privileged outsiders cannot intercept or modify them. By centralizing these identity flows within a sealed environment, developers can assure their users that no one outside the enclave (including the cloud provider or the app's own sysadmins) can peek at, tamper with, or access sensitive login information.
 Main Enclave Operations in OpenSecret
Main Enclave Operations in OpenSecretThe same principle applies to private key management. Whether keys are created fresh in the enclave or securely transferred into it, they remain sealed away from the rest of the system. Operations like digital signing or content decryption happen only within the hardware boundary, so raw keys never appear in any log, file system, or memory space outside the enclave. Developers retain the functionality they need, such as verifying user actions, encrypting data, or enabling secure transactions without ever exposing keys to a broader (and more vulnerable) attack surface. User backup options exist as well, where the keys can be securely passed to the end user.
 Realtime Encrypted Data Sync on Multiple Devices
Realtime Encrypted Data Sync on Multiple DevicesAnother crucial aspect is data encryption at rest. While user data ultimately needs to be stored somewhere outside the enclave, the unencrypted form of that data only exists transiently inside the protected environment. Encryption and decryption routines run within the enclave, which holds the encryption keys strictly in memory under hardware guards. If a user uploads data, it is promptly secured before it leaves the enclave. When data is retrieved, it remains encrypted until it reenters the protected region and is passed back to the user through the secured communication channel. This ensures that even if someone gains access to the underlying storage or intercepts data in transit, they will see only meaningless ciphertext.
 Confidential AI Workloads
Confidential AI WorkloadsFinally, confidential AI workloads build upon this same pattern: the Nitro enclave re-encrypts data so it can be processed inside a GPU-based trusted execution environment (TEE) for inference or other advanced computations. Sensitive data, like user-generated text or private documents, never appears in the clear on the host or within GPU memory outside the TEE boundary. When an AI process finishes, only the results are returned to the enclave, which can then relay them securely to the requesting user. By seamlessly chaining enclaves together, from CPU-based Nitro Enclaves to GPU-accelerated TEEs, we can deliver robust, hardware-enforced privacy for virtually any type of server-side or AI-driven operation.
Reproducible Builds + Verification
 Client verifies enclave attestation document
Client verifies enclave attestation documentWe build our enclaves on NixOS with reproducible builds, ensuring that anyone can verify that the binary we publish is indeed the binary running in the enclave. This build process is essential for proving we haven't snuck in malicious code to exfiltrate data or collect sensitive logs.
Our code is fully open source (GitHub: OpenSecret), so you can audit or run it yourself. You can also verify that the cryptographic measurement the build process outputs matches the measurement reported by the enclave during attestation.
Putting It All Together
 OpenSecret Offering: Private Key Management, Encrypted Sync, Private AI, and Confidential Compute
OpenSecret Offering: Private Key Management, Encrypted Sync, Private AI, and Confidential ComputeBy weaving secure enclaves into every step, from authentication to data handling to AI inference, we shift the burden of trust away from human policies and onto provable, hardware-based protections. For app developers, you can offer your users robust privacy guarantees without rewriting all your business logic or building an entire security stack from scratch. Whether you're storing user credentials or running complex operations on sensitive data, the enclave approach ensures plaintext remains inaccessible to even the most privileged parties outside the enclave boundary. Developers can focus on building great apps, while OpenSecret handles the cryptographic "lock and key" behind the scenes.
This model provides a secure-by-design environment for industries that demand strict data confidentiality, such as healthcare, fintech, cryptocurrency apps for secure key management, or decentralized identity platforms. Instead of worrying about memory dumps or backend tampering, you can trust that once data enters the enclave, it's sealed off from unauthorized eyes, including from the app developers themselves. And these safeguards don't just apply to niche use cases. Even general-purpose applications that handle login flows and user-generated content stand to benefit, especially as regulatory scrutiny grows around data privacy and insider threats.
Imagine a telehealth startup using OpenSecret enclaves to protect patient information for remote consultations. Not only would patient data remain encrypted at rest, but any AI-driven analytics to assist with diagnoses could be run privately within the enclave, ensuring no one outside the hardware boundary can peek at sensitive health records. A fintech company could similarly isolate confidential financial transactions, preventing even privileged insiders from viewing or tampering with raw transaction details. These real-world implementations give developers a clear path to adopting enclaves for serious privacy and compliance needs without overhauling their infrastructure.
OpenSecret aims to be a full developer platform with end-to-end security from day one. By incorporating user authentication, data storage, and GPU-based confidential AI into a single service, we eliminate many of the traditional hurdles in adopting enclaves. No more juggling separate tools for cryptographic key management, compliance controls, and runtime privacy. Instead, you get a unified stack that keeps data encrypted in transit, at rest, and in use.
Our solution also caters to the exploding demand for AI applications: with TEE-enabled GPU workloads, you can securely process sensitive data for text inference without ever exposing raw plaintext or sensitive documents to the host system.
The result is a new generation of apps that deliver advanced functionality, like real-time encrypted data sync or AI-driven insights, while preserving user privacy and meeting strict regulatory requirements. You don't have to rely on empty "trust us" promises because hardware enclaves, remote attestation, and reproducible builds collectively guarantee the code is running untampered. In short, OpenSecret offers the building blocks needed to create truly confidential services and experiences, allowing you to innovate while ensuring data protection remains ironclad.
Things to Come
We're excited to build on our enclaved approach. Here's what's on our roadmap:
• Production Launch: We're using this in production now with Maple AI and have a developer preview playground up and running. We'll have the developer environment ready for production in a few months.\ • Multi-Tenant Support: Our platform currently works for single tenants, but we're opening this up so developers can onboard without needing a dedicated instance.\ • Self-Serve Frontend: A dev-friendly portal for provisioning apps, connecting OAuth or email providers, and managing users.\ • External Key Signing Options: Integrations with custom hardware security modules (HSMs) or customer-ran key managers that can only process data upon verifying the enclave attestation.\ • Confidential Computing as a Service: We'll expand our platform so that other developers can quickly create enclaves for specialized workloads without dealing with the complexities of Nitro or GPU TEEs.\ • Additional SDKs: In addition to our JavaScript client-side SDK, we plan to launch official support for Rust, Python, Swift, Java, Go, and more.\ • AI API Proxy with Attestation/Encryption: We already provide an easy way to access a Private AI through Maple AI, but we'd like to open this up more for existing tools and developers. We'll provide a proxy server that users can run on their local machines or servers that properly handle encryption to our OpenAI-compatible API.
Getting Started
Ready to see enclaves in action? Here's how to dive in:\ 1. Run OpenSecret: Check out our open-source repository at OpenSecret on GitHub. You can run your own enclaved environment or try it out locally with Docker.\ 2. Review Our SDK: Our JavaScript client SDK makes it easy to handle sign-ins, put/get encrypted data, sign with user private keys, etc. It handles attestation verification and encryption under the hood, making the API integration seamless.\ 3. Play with Maple AI: Try out Maple AI as an example of an AI app built directly on OpenSecret. Your queries are encrypted end to end, and the Llama model sees them only inside the TEE.\ 4. Developer Preview: Contact us if you want an invite to our early dev platform. We'll guide you through our SDK and give you access to the preview server. We'd love to build with you and incorporate your feedback as we develop this further.
Conclusion
By merging secure enclaves (AWS Nitro and Nvidia GPU TEEs), user authentication, private key management, and an end-to-end verifiable encrypted approach, OpenSecret provides a powerful platform where we protect user data during collection, storage, and processing. Whether it's for standard user management, handling private cryptographic keys, or powering AI inference, the technology ensures that no one, not even us or the cloud provider, can snoop on data in use.
We believe this is the future of trustworthy computing in the cloud. And it's all open source, so you don't have to just take our word for it: you can see and verify everything yourself.
Do you have questions, feedback, or a use case you'd like to test out? Come join us on GitHub, Discord, or email us for a developer preview. We can't wait to see what you build!
Thank you for reading, and welcome to the era of enclaved computing.
-
 @ 57d1a264:69f1fee1
2025-04-07 06:04:14
@ 57d1a264:69f1fee1
2025-04-07 06:04:14It's so cool how AI is blending design and engineering together, making it easier for us all to be efforts creative in new ways!
Steve Jobs once said:
“The doers are the major thinkers. The people who really create the things that change this industry are both the thinker-doer in one person.”
— Steve JobsWould its words become truth? Or they already are?
originally posted at https://stacker.news/items/936796
-
 @ 91bea5cd:1df4451c
2025-02-04 17:24:50
@ 91bea5cd:1df4451c
2025-02-04 17:24:50Definição de ULID:
Timestamp 48 bits, Aleatoriedade 80 bits Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C. e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível.
Gerar ULID
```sql
CREATE EXTENSION IF NOT EXISTS pgcrypto;
CREATE FUNCTION generate_ulid() RETURNS TEXT AS $$ DECLARE -- Crockford's Base32 encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; timestamp BYTEA = E'\000\000\000\000\000\000'; output TEXT = '';
unix_time BIGINT; ulid BYTEA; BEGIN -- 6 timestamp bytes unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT; timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER);
-- 10 entropy bytes ulid = timestamp || gen_random_bytes(10);
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql VOLATILE; ```
ULID TO UUID
```sql CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$ DECLARE -- 16byte bytes bytea = E'\x00000000 00000000 00000000 00000000'; v char[]; -- Allow for O(1) lookup of index values dec integer[] = ARRAY[ 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 255, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31 ]; BEGIN IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN RAISE EXCEPTION 'Invalid ULID: %', ulid; END IF;
v = regexp_split_to_array(ulid, '');
-- 6 bytes timestamp (48 bits) bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]); bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2)); bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4)); bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1)); bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3)); bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]);
-- 10 bytes of entropy (80 bits); bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2)); bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4)); bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1)); bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3)); bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]); bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2)); bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4)); bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1)); bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3)); bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]);
RETURN bytes; END $$ LANGUAGE plpgsql IMMUTABLE;
CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$ BEGIN RETURN encode(parse_ulid(ulid), 'hex')::uuid; END $$ LANGUAGE plpgsql IMMUTABLE; ```
UUID to ULID
```sql CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$ DECLARE encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; output text = ''; uuid_bytes bytea = uuid_send(id); BEGIN
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql IMMUTABLE; ```
Gera 11 Digitos aleatórios: YBKXG0CKTH4
```sql -- Cria a extensão pgcrypto para gerar uuid CREATE EXTENSION IF NOT EXISTS pgcrypto;
-- Cria a função para gerar ULID CREATE OR REPLACE FUNCTION gen_lrandom() RETURNS TEXT AS $$ DECLARE ts_millis BIGINT; ts_chars TEXT; random_bytes BYTEA; random_chars TEXT; base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; i INT; BEGIN -- Pega o timestamp em milissegundos ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT;
-- Converte o timestamp para base32 ts_chars := ''; FOR i IN REVERSE 0..11 LOOP ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1); END LOOP; -- Gera 10 bytes aleatórios e converte para base32 random_bytes := gen_random_bytes(10); random_chars := ''; FOR i IN 0..9 LOOP random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1); IF i < 9 THEN random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1); ELSE random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1); END IF; END LOOP; -- Concatena o timestamp e os caracteres aleatórios RETURN ts_chars || random_chars;END; $$ LANGUAGE plpgsql; ```
Exemplo de USO
```sql -- Criação da extensão caso não exista CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Criação da tabela pessoas CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL );
-- Busca Pessoa na tabela SELECT * FROM "pessoas" WHERE uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F'; ```
Fontes
- https://github.com/scoville/pgsql-ulid
- https://github.com/geckoboard/pgulid
-
 @ 57d1a264:69f1fee1
2025-04-07 05:22:14
@ 57d1a264:69f1fee1
2025-04-07 05:22:14This idea has been explored along the last decades. Nothing has never taken the van place in the BMW series. The most successful intent was the 80s' Vixer in the US. Too sporty for a van? Or too luxurious to cover that already saturated market?
Collected some pictures all around, most oof them are designs and prototypes. Tried to order chronologically below:
Now in 2025, this came out of Ai
https://www.youtube.com/watch?v=d7p9CGBmRAA
originally posted at https://stacker.news/items/936787
-
 @ ec9bd746:df11a9d0
2025-04-06 08:06:08
@ ec9bd746:df11a9d0
2025-04-06 08:06:08🌍 Time Window:
🕘 When: Every even week on Sunday at 9:00 PM CET
🗺️ Where: https://cornychat.com/eurocornStart: 21:00 CET (Prague, UTC+1)
End: approx. 02:00 CET (Prague, UTC+1, next day)
Duration: usually 5+ hours.| Region | Local Time Window | Convenience Level | |-----------------------------------------------------|--------------------------------------------|---------------------------------------------------------| | Europe (CET, Prague) 🇨🇿🇩🇪 | 21:00–02:00 CET | ✅ Very Good; evening & night | | East Coast North America (EST) 🇺🇸🇨🇦 | 15:00–20:00 EST | ✅ Very Good; afternoon & early evening | | West Coast North America (PST) 🇺🇸🇨🇦 | 12:00–17:00 PST | ✅ Very Good; midday & afternoon | | Central America (CST) 🇲🇽🇨🇷🇬🇹 | 14:00–19:00 CST | ✅ Very Good; afternoon & evening | | South America West (Peru/Colombia PET/COT) 🇵🇪🇨🇴 | 15:00–20:00 PET/COT | ✅ Very Good; afternoon & evening | | South America East (Brazil/Argentina/Chile, BRT/ART/CLST) 🇧🇷🇦🇷🇨🇱 | 17:00–22:00 BRT/ART/CLST | ✅ Very Good; early evening | | United Kingdom/Ireland (GMT) 🇬🇧🇮🇪 | 20:00–01:00 GMT | ✅ Very Good; evening hours (midnight convenient) | | Eastern Europe (EET) 🇷🇴🇬🇷🇺🇦 | 22:00–03:00 EET | ✅ Good; late evening & early night (slightly late) | | Africa (South Africa, SAST) 🇿🇦 | 22:00–03:00 SAST | ✅ Good; late evening & overnight (late-night common) | | New Zealand (NZDT) 🇳🇿 | 09:00–14:00 NZDT (next day) | ✅ Good; weekday morning & afternoon | | Australia (AEDT, Sydney) 🇦🇺 | 07:00–12:00 AEDT (next day) | ✅ Good; weekday morning to noon | | East Africa (Kenya, EAT) 🇰🇪 | 23:00–04:00 EAT | ⚠️ Slightly late (night hours; late night common) | | Russia (Moscow, MSK) 🇷🇺 | 23:00–04:00 MSK | ⚠️ Slightly late (join at start is fine, very late night) | | Middle East (UAE, GST) 🇦🇪🇴🇲 | 00:00–05:00 GST (next day) | ⚠️ Late night start (midnight & early morning, but shorter attendance plausible)| | Japan/Korea (JST/KST) 🇯🇵🇰🇷 | 05:00–10:00 JST/KST (next day) | ⚠️ Early; convenient joining from ~07:00 onwards possible | | China (Beijing, CST) 🇨🇳 | 04:00–09:00 CST (next day) | ❌ Challenging; very early morning start (better ~07:00 onwards) | | India (IST) 🇮🇳 | 01:30–06:30 IST (next day) | ❌ Very challenging; overnight timing typically difficult|
-
 @ 91bea5cd:1df4451c
2025-02-04 17:15:57
@ 91bea5cd:1df4451c
2025-02-04 17:15:57Definição de ULID:
Timestamp 48 bits, Aleatoriedade 80 bits Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C. e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível.
Gerar ULID
```sql
CREATE EXTENSION IF NOT EXISTS pgcrypto;
CREATE FUNCTION generate_ulid() RETURNS TEXT AS $$ DECLARE -- Crockford's Base32 encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; timestamp BYTEA = E'\000\000\000\000\000\000'; output TEXT = '';
unix_time BIGINT; ulid BYTEA; BEGIN -- 6 timestamp bytes unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT; timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER);
-- 10 entropy bytes ulid = timestamp || gen_random_bytes(10);
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql VOLATILE; ```
ULID TO UUID
```sql CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$ DECLARE -- 16byte bytes bytea = E'\x00000000 00000000 00000000 00000000'; v char[]; -- Allow for O(1) lookup of index values dec integer[] = ARRAY[ 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 255, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31 ]; BEGIN IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN RAISE EXCEPTION 'Invalid ULID: %', ulid; END IF;
v = regexp_split_to_array(ulid, '');
-- 6 bytes timestamp (48 bits) bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]); bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2)); bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4)); bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1)); bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3)); bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]);
-- 10 bytes of entropy (80 bits); bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2)); bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4)); bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1)); bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3)); bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]); bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2)); bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4)); bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1)); bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3)); bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]);
RETURN bytes; END $$ LANGUAGE plpgsql IMMUTABLE;
CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$ BEGIN RETURN encode(parse_ulid(ulid), 'hex')::uuid; END $$ LANGUAGE plpgsql IMMUTABLE; ```
UUID to ULID
```sql CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$ DECLARE encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; output text = ''; uuid_bytes bytea = uuid_send(id); BEGIN
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql IMMUTABLE; ```
Gera 11 Digitos aleatórios: YBKXG0CKTH4
```sql -- Cria a extensão pgcrypto para gerar uuid CREATE EXTENSION IF NOT EXISTS pgcrypto;
-- Cria a função para gerar ULID CREATE OR REPLACE FUNCTION gen_lrandom() RETURNS TEXT AS $$ DECLARE ts_millis BIGINT; ts_chars TEXT; random_bytes BYTEA; random_chars TEXT; base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; i INT; BEGIN -- Pega o timestamp em milissegundos ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT;
-- Converte o timestamp para base32 ts_chars := ''; FOR i IN REVERSE 0..11 LOOP ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1); END LOOP; -- Gera 10 bytes aleatórios e converte para base32 random_bytes := gen_random_bytes(10); random_chars := ''; FOR i IN 0..9 LOOP random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1); IF i < 9 THEN random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1); ELSE random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1); END IF; END LOOP; -- Concatena o timestamp e os caracteres aleatórios RETURN ts_chars || random_chars;END; $$ LANGUAGE plpgsql; ```
Exemplo de USO
```sql -- Criação da extensão caso não exista CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Criação da tabela pessoas CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL );
-- Busca Pessoa na tabela SELECT * FROM "pessoas" WHERE uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F'; ```
Fontes
- https://github.com/scoville/pgsql-ulid
- https://github.com/geckoboard/pgulid
-
 @ d1667293:388e7004
2025-04-22 16:52:15
@ d1667293:388e7004
2025-04-22 16:52:15In my book “Bitcoindollar The Dawn of American Hegemony in the Digital Era,” I challenge the prevailing narrative that de-dollarization is a distant or hypothetical threat. Rather, I present a body of evidence suggesting that we are already living in a world where de-dollarization is unfolding—not through bombastic proclamations or sudden abandonment of the dollar in trade—but through a quieter, more telling trend: the steady escape of emerging powers like China, Russia, India, and much of the Global South from US Treasuries as the global reserve asset.
Structural, Not Cyclical: The Causes Behind the Exodus
This transformation is not cyclical or temporary; it is structural. The root causes run deep and stem from decades of US foreign and monetary policy—specifically, the aggressive military posturing that has defined American global engagement, the weaponization of dollar-based financial systems, and the overuse of sanctions as instruments of coercion rather than diplomacy. The result has been a widespread erosion of trust in the US as a neutral monetary steward. Increasingly, large economies and trading blocs—such as the Shanghai Cooperation Organization (SCO), BRICS, and the Belt and Road Initiative (BRI)—are seeking alternatives. They are diversifying their reserves, entering bilateral currency agreements, stockpiling gold, and in some cases, launching central bank digital currencies (CBDCs).
The message is clear: the era of unquestioned dollar supremacy is over.
The Treasury Dilemma: Who Will Fund America’s Debt?
This structural shift raises a daunting question for American policymakers: who will buy US Treasuries in the future? For decades, the demand for Treasuries rested on the premise of dollar dominance. Global trade surpluses—especially from oil-exporting nations under the Petrodollar system—were recycled into US debt markets. This “exorbitant privilege” allowed the US to run persistent deficits, finance wars, and project power without facing the immediate fiscal consequences most nations would. But that privilege is now in peril.
The Bitcoindollar System: A Strategic Response
In my book, I argue that the United States still has one viable path forward—a path that does not require relinquishing its leadership role, but rather reimagining it for the digital era. I call this new paradigm the Bitcoindollar system. It is an evolutionary successor to the Petrodollar framework, and it hinges on embracing bitcoin as the global store of value and dollar denominated stablecoins to maintain the US dollar’s relevance in a multipolar world. Under the Bitcoindollar system, global capital flows are incentivized to enter dollar-denominated stablecoins such as USDC and USDT. These stablecoins can then be recycled into short-term US debt instruments like Treasury bills, creating a digital-era version of the Petrodollar recycling mechanism. At the heart of this system lies Bitcoin—not as a threat to the dollar, but as a global decentralized and uncensorable Store of Value (SOV) that drives capital into the broader dollar-denominated ecosystem. As Bitcoin grows in adoption and price, it draws global attention and capital toward stablecoins, which in turn creates natural demand for dollar-based instruments such as Treasuries. This system offers the United States a first-mover advantage. No other nation has the credibility, capital markets depth, or global network effects to replicate it—if, and only if, the dollar’s digital rails are perceived as trustworthy and politically neutral. Herein lies the great conundrum: trust cannot be mandated. It must be earned, particularly in a geopolitical climate where the United States continues to alienate both allies and adversaries alike.
Trump’s Paradox: Economic Nationalism vs Monetary Hegemony
The current Trump administration, despite its rhetoric on economic nationalism, continues along a path that exacerbates this alienation. By doubling down on tariffs, aggressive posturing toward China, and unconditional support for Israel’s supremacist regional ambitions, it perpetuates the same policies that catalyzed de-dollarization in the first place. Tariffs, in this context, are a distraction. The US trade deficit is not primarily the result of unfair trade practices by other countries—it is largely the result of the dollar's role as the global reserve currency. To sustain global demand for dollars, the US has had to export dollars—and therefore run trade deficits. The dollar’s dominance enabled vast capital inflows and supported America’s imperial military architecture, but this model is fundamentally incompatible with dreams of reshoring industry, reducing deficits, and limiting foreign entanglements. Furthermore, these policies undermine any future attempt to establish dollar stablecoins as trusted global instruments. Why would a nation park its savings in a dollar-based asset, however digitized, if it fears arbitrary sanctions or seizure at the stroke of a keyboard? Despite his aggressive posturing, Trump, like Zelensky and the EU before him, has no cards to play to force China or Russia to the table.
A Fork in the Road: Choose Multipolar Collaboration or Decline
Absent a disastrous military escalation—which will not prevent the fall of American unipolar hegemony—the US is left with ONLY ONE path forward: a deliberate, peaceful shift from military and imperial posturing toward a more collaborative, multipolar engagement with the world. This means treating allies, adversaries, and vassal states alike with respect and inclusion in a reimagined dollar-based system—one that is digital, decentralized, and incentivized by global participation. The Bitcoindollar system can serve as the financial infrastructure of this new era, but it demands that the United States rehabilitate its image as a trustworthy party. For the Trump administration to succeed in securing America’s future financial relevance, it must course-correct immediately. This includes ending the influence of the neo-conservative and Zionist hardliners who perpetuate conflict and distrust for their own interest, and embracing a vision of digital dollar diplomacy that builds bridges instead of burning them.
In conclusion, the Bitcoindollar is not just a financial mechanism—it is a strategic opportunity for the United States to retain leadership in the emerging multipolar order. The alternative is clear: a continued slide into irrelevance, fiscal instability, and geopolitical isolation or a mutually assured destruction through war.
The time to act boldly for President Trump is now.
bitcoin #bitcoindollar #stablecoin
-
 @ 9bde4214:06ca052b
2025-04-22 16:35:00
@ 9bde4214:06ca052b
2025-04-22 16:35:00"We have the chance of building the next iteration of the internet, and hopefully, not repeat the mistakes of the past."
In this dialogue:
- Why starting ugly and shipping early is hard
- The ugliest thing that Pablo ever shipped
- “Happiness is shipping”
- Make it real first, you can make it pretty later
- Getting into the habit of shipping
- Highlighter and the hang-up of shipping something big
- How nostr allows you to have cash flow from the get-go
-
value4value for artists and devs
- What DHH & 37Signals got right
People and projects mentioned:
Further links:
- https://excellentjourney.net/2015/03/04/art-fear-the-ceramics-class-and-quantity-before-quality/
- https://world.hey.com/dhh/that-shipping-feeling-b7c8c565
- https://world.hey.com/dhh/i-was-wrong-we-need-crypto-587ccb03
- https://sovereignengineering.io/
- https://dergigi.com/2023/04/04/purple-text-orange-highlights/
- https://highlighter.com/
- https://njump.me/nosolutions@sovereignengineering.io
-
 @ c066aac5:6a41a034
2025-04-05 16:58:58
@ c066aac5:6a41a034
2025-04-05 16:58:58I’m drawn to extremities in art. The louder, the bolder, the more outrageous, the better. Bold art takes me out of the mundane into a whole new world where anything and everything is possible. Having grown up in the safety of the suburban midwest, I was a bit of a rebellious soul in search of the satiation that only came from the consumption of the outrageous. My inclination to find bold art draws me to NOSTR, because I believe NOSTR can be the place where the next generation of artistic pioneers go to express themselves. I also believe that as much as we are able, were should invite them to come create here.
My Background: A Small Side Story
My father was a professional gamer in the 80s, back when there was no money or glory in the avocation. He did get a bit of spotlight though after the fact: in the mid 2000’s there were a few parties making documentaries about that era of gaming as well as current arcade events (namely 2007’sChasing GhostsandThe King of Kong: A Fistful of Quarters). As a result of these documentaries, there was a revival in the arcade gaming scene. My family attended events related to the documentaries or arcade gaming and I became exposed to a lot of things I wouldn’t have been able to find. The producer ofThe King of Kong: A Fistful of Quarters had previously made a documentary calledNew York Dollwhich was centered around the life of bassist Arthur Kane. My 12 year old mind was blown: The New York Dolls were a glam-punk sensation dressed in drag. The music was from another planet. Johnny Thunders’ guitar playing was like Chuck Berry with more distortion and less filter. Later on I got to meet the Galaga record holder at the time, Phil Day, in Ottumwa Iowa. Phil is an Australian man of high intellect and good taste. He exposed me to great creators such as Nick Cave & The Bad Seeds, Shakespeare, Lou Reed, artists who created things that I had previously found inconceivable.
I believe this time period informed my current tastes and interests, but regrettably I think it also put coals on the fire of rebellion within. I stopped taking my parents and siblings seriously, the Christian faith of my family (which I now hold dearly to) seemed like a mundane sham, and I felt I couldn’t fit in with most people because of my avant-garde tastes. So I write this with the caveat that there should be a way to encourage these tastes in children without letting them walk down the wrong path. There is nothing inherently wrong with bold art, but I’d advise parents to carefully find ways to cultivate their children’s tastes without completely shutting them down and pushing them away as a result. My parents were very loving and patient during this time; I thank God for that.
With that out of the way, lets dive in to some bold artists:
Nicolas Cage: Actor
There is an excellent video by Wisecrack on Nicolas Cage that explains him better than I will, which I will linkhere. Nicolas Cage rejects the idea that good acting is tied to mere realism; all of his larger than life acting decisions are deliberate choices. When that clicked for me, I immediately realized the man is a genius. He borrows from Kabuki and German Expressionism, art forms that rely on exaggeration to get the message across. He has even created his own acting style, which he calls Nouveau Shamanic. He augments his imagination to go from acting to being. Rather than using the old hat of method acting, he transports himself to a new world mentally. The projects he chooses to partake in are based on his own interests or what he considers would be a challenge (making a bad script good for example). Thus it doesn’t matter how the end result comes out; he has already achieved his goal as an artist. Because of this and because certain directors don’t know how to use his talents, he has a noticeable amount of duds in his filmography. Dig around the duds, you’ll find some pure gold. I’d personally recommend the filmsPig, Joe, Renfield, and his Christmas film The Family Man.
Nick Cave: Songwriter
What a wild career this man has had! From the apocalyptic mayhem of his band The Birthday Party to the pensive atmosphere of his albumGhosteen, it seems like Nick Cave has tried everything. I think his secret sauce is that he’s always working. He maintains an excellent newsletter calledThe Red Hand Files, he has written screenplays such asLawless, he has written books, he has made great film scores such asThe Assassination of Jesse James by the Coward Robert Ford, the man is religiously prolific. I believe that one of the reasons he is prolific is that he’s not afraid to experiment. If he has an idea, he follows it through to completion. From the albumMurder Ballads(which is comprised of what the title suggests) to his rejected sequel toGladiator(Gladiator: Christ Killer), he doesn’t seem to be afraid to take anything on. This has led to some over the top works as well as some deeply personal works. Albums likeSkeleton TreeandGhosteenwere journeys through the grief of his son’s death. The Boatman’s Callis arguably a better break-up album than anything Taylor Swift has put out. He’s not afraid to be outrageous, he’s not afraid to offend, but most importantly he’s not afraid to be himself. Works I’d recommend include The Birthday Party’sLive 1981-82, Nick Cave & The Bad Seeds’The Boatman’s Call, and the filmLawless.
Jim Jarmusch: Director
I consider Jim’s films to be bold almost in an ironic sense: his works are bold in that they are, for the most part, anti-sensational. He has a rule that if his screenplays are criticized for a lack of action, he makes them even less eventful. Even with sensational settings his films feel very close to reality, and they demonstrate the beauty of everyday life. That's what is bold about his art to me: making the sensational grounded in reality while making everyday reality all the more special. Ghost Dog: The Way of the Samurai is about a modern-day African-American hitman who strictly follows the rules of the ancient Samurai, yet one can resonate with the humanity of a seemingly absurd character. Only Lovers Left Aliveis a vampire love story, but in the middle of a vampire romance one can see their their own relationships in a new deeply human light. Jim’s work reminds me that art reflects life, and that there is sacred beauty in seemingly mundane everyday life. I personally recommend his filmsPaterson,Down by Law, andCoffee and Cigarettes.
NOSTR: We Need Bold Art
NOSTR is in my opinion a path to a better future. In a world creeping slowly towards everything apps, I hope that the protocol where the individual owns their data wins over everything else. I love freedom and sovereignty. If NOSTR is going to win the race of everything apps, we need more than Bitcoin content. We need more than shirtless bros paying for bananas in foreign countries and exercising with girls who have seductive accents. Common people cannot see themselves in such a world. NOSTR needs to catch the attention of everyday people. I don’t believe that this can be accomplished merely by introducing more broadly relevant content; people are searching for content that speaks to them. I believe that NOSTR can and should attract artists of all kinds because NOSTR is one of the few places on the internet where artists can express themselves fearlessly. Getting zaps from NOSTR’s value-for-value ecosystem has far less friction than crowdfunding a creative project or pitching investors that will irreversibly modify an artist’s vision. Having a place where one can post their works without fear of censorship should be extremely enticing. Having a place where one can connect with fellow humans directly as opposed to a sea of bots should seem like the obvious solution. If NOSTR can become a safe haven for artists to express themselves and spread their work, I believe that everyday people will follow. The banker whose stressful job weighs on them will suddenly find joy with an original meme made by a great visual comedian. The programmer for a healthcare company who is drowning in hopeless mundanity could suddenly find a new lust for life by hearing the song of a musician who isn’t afraid to crowdfund their their next project by putting their lighting address on the streets of the internet. The excel guru who loves independent film may find that NOSTR is the best way to support non corporate movies. My closing statement: continue to encourage the artists in your life as I’m sure you have been, but while you’re at it give them the purple pill. You may very well be a part of building a better future.
-
 @ 5c26ee8b:a4d229aa
2025-04-14 16:32:51
@ 5c26ee8b:a4d229aa
2025-04-14 16:32:5110:25 Yunus
وَاللَّهُ يَدْعُو إِلَىٰ دَارِ السَّلَامِ وَيَهْدِي مَنْ يَشَاءُ إِلَىٰ صِرَاطٍ مُسْتَقِيمٍ
And Allah invites to the Home of Peace and guides whom He wills to a straight path.
6:125 Al-An'aam
فَمَنْ يُرِدِ اللَّهُ أَنْ يَهْدِيَهُ يَشْرَحْ صَدْرَهُ لِلْإِسْلَامِ ۖ وَمَنْ يُرِدْ أَنْ يُضِلَّهُ يَجْعَلْ صَدْرَهُ ضَيِّقًا حَرَجًا كَأَنَّمَا يَصَّعَّدُ فِي السَّمَاءِ ۚ كَذَٰلِكَ يَجْعَلُ اللَّهُ الرِّجْسَ عَلَى الَّذِينَ لَا يُؤْمِنُونَ
So whoever Allah wants to guide - He expands his breast to [contain] Islam; and whoever He wants to misguide - He makes his breast tight and constricted as though he were climbing into the sky. Thus Allah places defilement upon those who do not believe.
Allah is one of the Islamic names of God; the creator of everything. Not associating with God, Allah, any other and worshipping him alone is one of the first known fact in Islam.
- Al-Ikhlaas قُلْ هُوَ اللَّهُ أَحَدٌ Say, "He is Allah, [who is] One, اللَّهُ الصَّمَدُ Allah, the Eternal Refuge. لَمْ يَلِدْ وَلَمْ يُولَدْ He neither begets nor is born, وَلَمْ يَكُنْ لَهُ كُفُوًا أَحَدٌ Nor is there to Him any equivalent."
The Quran, the Islamic holly book and the guidance for mankind, was delivered more than 1400 years ago through the Angel Gabriel to prophet Mohamed peace be upon, however little is known about Islam despite living in a so called intellectual era.
The first word that was delivered was, “Read” in the first verse of surah Al-Alaq.
96:1 Al-Alaq
اقْرَأْ بِاسْمِ رَبِّكَ الَّذِي خَلَقَ
Read, in the name of your Lord who created -
The Quran, words of God (Allah), was delivered in Arabic and it is one of its miracles.
39:28 Az-Zumar
قُرْآنًا عَرَبِيًّا غَيْرَ ذِي عِوَجٍ لَعَلَّهُمْ يَتَّقُونَ
[It is] an Arabic Qur'an, without any distortion that they might become righteous.
18:109 Al-Kahf
قُلْ لَوْ كَانَ الْبَحْرُ مِدَادًا لِكَلِمَاتِ رَبِّي لَنَفِدَ الْبَحْرُ قَبْلَ أَنْ تَنْفَدَ كَلِمَاتُ رَبِّي وَلَوْ جِئْنَا بِمِثْلِهِ مَدَدًا
Say, "If the sea were ink for [writing] the words of my Lord, the sea would be exhausted before the words of my Lord were exhausted, even if We brought the like of it as a supplement."
17:88 Al-Israa
قُلْ لَئِنِ اجْتَمَعَتِ الْإِنْسُ وَالْجِنُّ عَلَىٰ أَنْ يَأْتُوا بِمِثْلِ هَٰذَا الْقُرْآنِ لَا يَأْتُونَ بِمِثْلِهِ وَلَوْ كَانَ بَعْضُهُمْ لِبَعْضٍ ظَهِيرًا
Say, "If mankind and the jinn gathered in order to produce the like of this Qur'an, they could not produce the like of it, even if they were to each other assistants."
17:89 Al-Israa
وَلَقَدْ صَرَّفْنَا لِلنَّاسِ فِي هَٰذَا الْقُرْآنِ مِنْ كُلِّ مَثَلٍ فَأَبَىٰ أَكْثَرُ النَّاسِ إِلَّا كُفُورًا
And We have certainly diversified for the people in this Qur'an from every [kind] of example, but most of the people refused [anything] except disbelief.
Through the wards of God in the Quran a lot can be known about Him and in the following verse some descriptions about Him.
2:255 Al-Baqara
اللَّهُ لَا إِلَٰهَ إِلَّا هُوَ الْحَيُّ الْقَيُّومُ ۚ لَا تَأْخُذُهُ سِنَةٌ وَلَا نَوْمٌ ۚ لَهُ مَا فِي السَّمَاوَاتِ وَمَا فِي الْأَرْضِ ۗ مَنْ ذَا الَّذِي يَشْفَعُ عِنْدَهُ إِلَّا بِإِذْنِهِ ۚ يَعْلَمُ مَا بَيْنَ أَيْدِيهِمْ وَمَا خَلْفَهُمْ ۖ وَلَا يُحِيطُونَ بِشَيْءٍ مِنْ عِلْمِهِ إِلَّا بِمَا شَاءَ ۚ وَسِعَ كُرْسِيُّهُ السَّمَاوَاتِ وَالْأَرْضَ ۖ وَلَا يَئُودُهُ حِفْظُهُمَا ۚ وَهُوَ الْعَلِيُّ الْعَظِيمُ
Allah - there is no deity except Him, the Ever-Living, the Sustainer of [all] existence. Neither drowsiness overtakes Him nor sleep. To Him belongs whatever is in the heavens and whatever is on the earth. Who is it that can intercede with Him except by His permission? He knows what is [presently] before them and what will be after them, and they encompass not a thing of His knowledge except for what He wills. His Kursi extends over the heavens and the earth, and their preservation tires Him not. And He is the Most High, the Most Great.
Seeing God has been a curiosity of prophets themselves and in the following examples of what happened when prophet Moses, peace be upon him, or his people asked so.
7:143 Al-A'raaf
وَلَمَّا جَاءَ مُوسَىٰ لِمِيقَاتِنَا وَكَلَّمَهُ رَبُّهُ قَالَ رَبِّ أَرِنِي أَنْظُرْ إِلَيْكَ ۚ قَالَ لَنْ تَرَانِي وَلَٰكِنِ انْظُرْ إِلَى الْجَبَلِ فَإِنِ اسْتَقَرَّ مَكَانَهُ فَسَوْفَ تَرَانِي ۚ فَلَمَّا تَجَلَّىٰ رَبُّهُ لِلْجَبَلِ جَعَلَهُ دَكًّا وَخَرَّ مُوسَىٰ صَعِقًا ۚ فَلَمَّا أَفَاقَ قَالَ سُبْحَانَكَ تُبْتُ إِلَيْكَ وَأَنَا أَوَّلُ الْمُؤْمِنِينَ
And when Moses arrived at Our appointed time and his Lord spoke to him, he said, "My Lord, show me [Yourself] that I may look at You." [Allah] said, "You will not see Me, but look at the mountain; if it should remain in place, then you will see Me." But when his Lord appeared to the mountain, He rendered it level, and Moses fell unconscious. And when he awoke, he said, "Exalted are You! I have repented to You, and I am the first of the believers."
2:55 Al-Baqara
وَإِذْ قُلْتُمْ يَا مُوسَىٰ لَنْ نُؤْمِنَ لَكَ حَتَّىٰ نَرَى اللَّهَ جَهْرَةً فَأَخَذَتْكُمُ الصَّاعِقَةُ وَأَنْتُمْ تَنْظُرُونَ
And [recall] when you said, "O Moses, we will never believe you until we see Allah outright"; so the thunderbolt took you while you were looking on.
2:56 Al-Baqara
ثُمَّ بَعَثْنَاكُمْ مِنْ بَعْدِ مَوْتِكُمْ لَعَلَّكُمْ تَشْكُرُونَ
Then We revived you after your death that perhaps you would be grateful.
In fact eyesights can’t reach God as in the following verses 6:102 Al-An'aam
ذَٰلِكُمُ اللَّهُ رَبُّكُمْ ۖ لَا إِلَٰهَ إِلَّا هُوَ ۖ خَالِقُ كُلِّ شَيْءٍ فَاعْبُدُوهُ ۚ وَهُوَ عَلَىٰ كُلِّ شَيْءٍ وَكِيلٌ
That is Allah, your Lord; there is no deity except Him, the Creator of all things, so worship Him. And He is Disposer of all things.
6:103 Al-An'aam
لَا تُدْرِكُهُ الْأَبْصَارُ وَهُوَ يُدْرِكُ الْأَبْصَارَ ۖ وَهُوَ اللَّطِيفُ الْخَبِيرُ
Eyesights (or visions) do not reach (or perceive him) Him, but He reaches (or perceives) [all] eyesights (visions); and He is the Subtle, the Acquainted.
6:104 Al-An'aam
قَدْ جَاءَكُمْ بَصَائِرُ مِنْ رَبِّكُمْ ۖ فَمَنْ أَبْصَرَ فَلِنَفْسِهِ ۖ وَمَنْ عَمِيَ فَعَلَيْهَا ۚ وَمَا أَنَا عَلَيْكُمْ بِحَفِيظٍ
There has come to you eyesights (or enlightenments) from your Lord. So whoever will see does so for [the benefit of] his soul, and whoever is blind [does harm] against it. And [say], "I am not controlling (or a guardian) over you."
42:11 Ash-Shura
فَاطِرُ السَّمَاوَاتِ وَالْأَرْضِ ۚ جَعَلَ لَكُمْ مِنْ أَنْفُسِكُمْ أَزْوَاجًا وَمِنَ الْأَنْعَامِ أَزْوَاجًا ۖ يَذْرَؤُكُمْ فِيهِ ۚ لَيْسَ كَمِثْلِهِ شَيْءٌ ۖ وَهُوَ السَّمِيعُ الْبَصِيرُ
[He is] Creator of the heavens and the earth. He has made for you from yourselves, mates, and among the cattle, mates; He multiplies you thereby. There is nothing like Him, and He is the Hearing, the Seeing.
Another name of God is the Truth and the Islam is the religion of truth and prophet Mohamed peace be upon him was chosen to invite the people to Islam.
61:7 As-Saff
وَمَنْ أَظْلَمُ مِمَّنِ افْتَرَىٰ عَلَى اللَّهِ الْكَذِبَ وَهُوَ يُدْعَىٰ إِلَى الْإِسْلَامِ ۚ وَاللَّهُ لَا يَهْدِي الْقَوْمَ الظَّالِمِينَ
And who is more unjust than one who invents about Allah untruth while he is being invited to Islam. And Allah does not guide the wrongdoing people.
61:8 As-Saff
يُرِيدُونَ لِيُطْفِئُوا نُورَ اللَّهِ بِأَفْوَاهِهِمْ وَاللَّهُ مُتِمُّ نُورِهِ وَلَوْ كَرِهَ الْكَافِرُونَ
They want to extinguish the light of Allah with their mouths, but Allah will perfect His light, although the disbelievers dislike it.
61:9 As-Saff
هُوَ الَّذِي أَرْسَلَ رَسُولَهُ بِالْهُدَىٰ وَدِينِ الْحَقِّ لِيُظْهِرَهُ عَلَى الدِّينِ كُلِّهِ وَلَوْ كَرِهَ الْمُشْرِكُونَ
It is He who sent His Messenger with guidance and the religion of truth to manifest it over all religion, although those who associate others with Allah dislike it.
Humans were given a trust, it’s to populate the earth while having the ability to choose between right and wrong.
33:72 Al-Ahzaab
إِنَّا عَرَضْنَا الْأَمَانَةَ عَلَى السَّمَاوَاتِ وَالْأَرْضِ وَالْجِبَالِ فَأَبَيْنَ أَنْ يَحْمِلْنَهَا وَأَشْفَقْنَ مِنْهَا وَحَمَلَهَا الْإِنْسَانُ ۖ إِنَّهُ كَانَ ظَلُومًا جَهُولًا
Indeed, we offered the Trust to the heavens and the earth and the mountains, and they declined to bear it and feared it; but man [undertook to] bear it. Indeed, he was unjust and ignorant.
Although our souls testified before the creation that God, Allah is our creator, he sent messengers and books to guide us.
7:172 Al-A'raaf
وَإِذْ أَخَذَ رَبُّكَ مِنْ بَنِي آدَمَ مِنْ ظُهُورِهِمْ ذُرِّيَّتَهُمْ وَأَشْهَدَهُمْ عَلَىٰ أَنْفُسِهِمْ أَلَسْتُ بِرَبِّكُمْ ۖ قَالُوا بَلَىٰ ۛ شَهِدْنَا ۛ أَنْ تَقُولُوا يَوْمَ الْقِيَامَةِ إِنَّا كُنَّا عَنْ هَٰذَا غَافِلِينَ
And [mention] when your Lord took from the children of Adam - from their loins - their descendants and made them testify of themselves, [saying to them], "Am I not your Lord?" They said, "Yes, we have testified." [This] - lest you should say on the day of Resurrection, "Indeed, we were of this unaware."
God likes that who believes in him submits to him willingly. The heavens and the earth, known to have consciousness in Islam submitted to him before us.
41:9 Fussilat
۞ قُلْ أَئِنَّكُمْ لَتَكْفُرُونَ بِالَّذِي خَلَقَ الْأَرْضَ فِي يَوْمَيْنِ وَتَجْعَلُونَ لَهُ أَنْدَادًا ۚ ذَٰلِكَ رَبُّ الْعَالَمِينَ
Say, "Do you indeed disbelieve in He who created the earth in two days and attribute to Him equals? That is the Lord of the worlds."
41:10 Fussilat
وَجَعَلَ فِيهَا رَوَاسِيَ مِنْ فَوْقِهَا وَبَارَكَ فِيهَا وَقَدَّرَ فِيهَا أَقْوَاتَهَا فِي أَرْبَعَةِ أَيَّامٍ سَوَاءً لِلسَّائِلِينَ
And He placed on the earth firmly set mountains over its surface, and He blessed it and determined therein its [creatures'] sustenance in four days without distinction - for [the information] of those who ask.
41:11 Fussilat
ثُمَّ اسْتَوَىٰ إِلَى السَّمَاءِ وَهِيَ دُخَانٌ فَقَالَ لَهَا وَلِلْأَرْضِ ائْتِيَا طَوْعًا أَوْ كَرْهًا قَالَتَا أَتَيْنَا طَائِعِينَ
Then He directed Himself to the heaven while it was smoke and said to it and to the earth, "Come, willingly or by compulsion", they said, "We came willingly."
40:57 Al-Ghaafir
لَخَلْقُ السَّمَاوَاتِ وَالْأَرْضِ أَكْبَرُ مِنْ خَلْقِ النَّاسِ وَلَٰكِنَّ أَكْثَرَ النَّاسِ لَا يَعْلَمُونَ
The creation of the heavens and earth is greater than the creation of mankind, but most of the people do not know.
It’s important to know what’s God asking people to do while submitting to him as mentioned in the following verses.
Surah Al-Israa: Verse 22: لَا تَجْعَلْ مَعَ اللَّهِ إِلَٰهًا آخَرَ فَتَقْعُدَ مَذْمُومًا مَخْذُولًا Set not up with Allah any other ilah (god), (O man)! (This verse is addressed to Prophet Muhammad SAW, but its implication is general to all mankind), or you will sit down reproved, forsaken (in the Hell-fire). Verse 23: ۞ وَقَضَىٰ رَبُّكَ أَلَّا تَعْبُدُوا إِلَّا إِيَّاهُ وَبِالْوَالِدَيْنِ إِحْسَانًا ۚ إِمَّا يَبْلُغَنَّ عِنْدَكَ الْكِبَرَ أَحَدُهُمَا أَوْ كِلَاهُمَا فَلَا تَقُلْ لَهُمَا أُفٍّ وَلَا تَنْهَرْهُمَا وَقُلْ لَهُمَا قَوْلًا كَرِيمًا And your Lord has decreed that you worship none but Him. And that you be dutiful to your parents. If one of them or both of them attain old age in your life, don’t say to them a word of disrespect, or shout at them but address them in terms of honour. Verse 24: وَاخْفِضْ لَهُمَا جَنَاحَ الذُّلِّ مِنَ الرَّحْمَةِ وَقُلْ رَبِّ ارْحَمْهُمَا كَمَا رَبَّيَانِي صَغِيرًا And lower unto them the wing of submission and humility through mercy, and say: "My Lord! Bestow on them Your Mercy as they did bring me up when I was small." Verse 25: رَبُّكُمْ أَعْلَمُ بِمَا فِي نُفُوسِكُمْ ۚ إِنْ تَكُونُوا صَالِحِينَ فَإِنَّهُ كَانَ لِلْأَوَّابِينَ غَفُورًا Your Lord knows best what is in your inner-selves. If you are righteous, then, verily, He is Ever Most Forgiving to those who turn unto Him again and again in obedience, and in repentance. Verse 26: وَآتِ ذَا الْقُرْبَىٰ حَقَّهُ وَالْمِسْكِينَ وَابْنَ السَّبِيلِ وَلَا تُبَذِّرْ تَبْذِيرًا And give to the kindred his due and to the Miskin (poor) and to the wayfarer. But spend not wastefully (your wealth) in the manner of a spendthrift. Verse 27: إِنَّ الْمُبَذِّرِينَ كَانُوا إِخْوَانَ الشَّيَاطِينِ ۖ وَكَانَ الشَّيْطَانُ لِرَبِّهِ كَفُورًا Verily, spendthrifts are brothers of the Shayatin (devils), and the Shaitan (Devil - Satan) is ever ungrateful to his Lord. Verse 28: وَإِمَّا تُعْرِضَنَّ عَنْهُمُ ابْتِغَاءَ رَحْمَةٍ مِنْ رَبِّكَ تَرْجُوهَا فَقُلْ لَهُمْ قَوْلًا مَيْسُورًا
And if you turn away from them (kindred, poor, wayfarer, etc. whom We have ordered you to give their rights, but if you have no money at the time they ask you for it) and you are awaiting a mercy from your Lord for which you hope, then, speak unto them a soft kind word (i.e. Allah will give me and I shall give you). Verse 29: وَلَا تَجْعَلْ يَدَكَ مَغْلُولَةً إِلَىٰ عُنُقِكَ وَلَا تَبْسُطْهَا كُلَّ الْبَسْطِ فَتَقْعُدَ مَلُومًا مَحْسُورًا And let not your hand be tied (like a miser) to your neck, nor stretch it forth to its utmost reach (like a spendthrift), so that you become blameworthy and in severe poverty. Verse 30: إِنَّ رَبَّكَ يَبْسُطُ الرِّزْقَ لِمَنْ يَشَاءُ وَيَقْدِرُ ۚ إِنَّهُ كَانَ بِعِبَادِهِ خَبِيرًا بَصِيرًا Truly, your Lord enlarges the provision for whom He wills and straitens (for whom He wills). Verily, He is Ever All-Knower, All-Seer of His slaves (servants; mankind created by God). Verse 31: وَلَا تَقْتُلُوا أَوْلَادَكُمْ خَشْيَةَ إِمْلَاقٍ ۖ نَحْنُ نَرْزُقُهُمْ وَإِيَّاكُمْ ۚ إِنَّ قَتْلَهُمْ كَانَ خِطْئًا كَبِيرًا And kill not your children for fear of poverty. We provide for them and for you. Surely, the killing of them is a great sin. Verse 32: وَلَا تَقْرَبُوا الزِّنَا ۖ إِنَّهُ كَانَ فَاحِشَةً وَسَاءَ سَبِيلًا And don’t come near to the unlawful sexual intercourse. Verily, it is a Fahishah (a great sin), and an evil way (that leads one to Hell unless Allah forgives him). Verse 33: وَلَا تَقْتُلُوا النَّفْسَ الَّتِي حَرَّمَ اللَّهُ إِلَّا بِالْحَقِّ ۗ وَمَنْ قُتِلَ مَظْلُومًا فَقَدْ جَعَلْنَا لِوَلِيِّهِ سُلْطَانًا فَلَا يُسْرِفْ فِي الْقَتْلِ ۖ إِنَّهُ كَانَ مَنْصُورًا And do not kill anyone that Allah has forbidden, except for a just cause. And whoever is killed (intentionally with hostility and oppression and not by mistake), We have given his heir the authority [(to demand Qisas, Law of Equality in punishment or to forgive, or to take Diya (blood money)]. But do not kill excessively (exceed limits in the matter of taking life). Verily, he is victorious. Verse 34: وَلَا تَقْرَبُوا مَالَ الْيَتِيمِ إِلَّا بِالَّتِي هِيَ أَحْسَنُ حَتَّىٰ يَبْلُغَ أَشُدَّهُ ۚ وَأَوْفُوا بِالْعَهْدِ ۖ إِنَّ الْعَهْدَ كَانَ مَسْئُولًا And don’t come near to the orphan's property except to improve it, until he attains the age of full strength. And fulfil (every) covenant. Verily! the covenant, will be questioned about. Verse 35: وَأَوْفُوا الْكَيْلَ إِذَا كِلْتُمْ وَزِنُوا بِالْقِسْطَاسِ الْمُسْتَقِيمِ ۚ ذَٰلِكَ خَيْرٌ وَأَحْسَنُ تَأْوِيلًا And give full measure when you measure, and weigh with a balance that is straight. That is good (advantageous) and better in the end. Verse 36: وَلَا تَقْفُ مَا لَيْسَ لَكَ بِهِ عِلْمٌ ۚ إِنَّ السَّمْعَ وَالْبَصَرَ وَالْفُؤَادَ كُلُّ أُولَٰئِكَ كَانَ عَنْهُ مَسْئُولًا And don’t pursue (i.e., do not say, or do not or witness not, etc.) what you have no knowledge of. Verily! The hearing, and the sight, and the heart, of each of those you will be questioned (by Allah). Verse 37: وَلَا تَمْشِ فِي الْأَرْضِ مَرَحًا ۖ إِنَّكَ لَنْ تَخْرِقَ الْأَرْضَ وَلَنْ تَبْلُغَ الْجِبَالَ طُولًا And walk not on the earth with conceit and arrogance. Verily, you can’t break the earth, nor reach the mountains in height. Verse 38: كُلُّ ذَٰلِكَ كَانَ سَيِّئُهُ عِنْدَ رَبِّكَ مَكْرُوهًا All the bad aspects of these (the above mentioned things) are hateful to your Lord. Verse 39: ذَٰلِكَ مِمَّا أَوْحَىٰ إِلَيْكَ رَبُّكَ مِنَ الْحِكْمَةِ ۗ وَلَا تَجْعَلْ مَعَ اللَّهِ إِلَٰهًا آخَرَ فَتُلْقَىٰ فِي جَهَنَّمَ مَلُومًا مَدْحُورًا This is (part) of Al-Hikmah (wisdom, good manners and high character, etc.) that your Lord has inspired to you. And set not up with Allah any other god lest you should be thrown into Hell, blameworthy and rejected, (from Allah's Mercy). Verse 40: أَفَأَصْفَاكُمْ رَبُّكُمْ بِالْبَنِينَ وَاتَّخَذَ مِنَ الْمَلَائِكَةِ إِنَاثًا ۚ إِنَّكُمْ لَتَقُولُونَ قَوْلًا عَظِيمًا Has then your Lord (O pagans of Makkah) preferred for you sons, and taken for Himself from among the angels daughters (Angels don’t have a gender and it’s wrong to refer to them as females). Verily! You utter an awful saying, indeed. Verse 41: وَلَقَدْ صَرَّفْنَا فِي هَٰذَا الْقُرْآنِ لِيَذَّكَّرُوا وَمَا يَزِيدُهُمْ إِلَّا نُفُورًا And surely, We have explained [Our Promises, Warnings and (set forth many) examples] in this Quran that they (the disbelievers) may take heed, but it increases them in aversion (from the truth). Verse 42: قُلْ لَوْ كَانَ مَعَهُ آلِهَةٌ كَمَا يَقُولُونَ إِذًا لَابْتَغَوْا إِلَىٰ ذِي الْعَرْشِ سَبِيلًا Say: "If there had been other gods along with Him as they say, then they would certainly have sought out a way to the Lord of the Throne (seeking His Pleasures and to be near to Him). Verse 43: سُبْحَانَهُ وَتَعَالَىٰ عَمَّا يَقُولُونَ عُلُوًّا كَبِيرًا Glorified and High be He! From 'Uluwan Kabira (the great falsehood) that they say!
Surah Al-Israa: Verse 53 وَقُلْ لِعِبَادِي يَقُولُوا الَّتِي هِيَ أَحْسَنُ ۚ إِنَّ الشَّيْطَانَ يَنْزَغُ بَيْنَهُمْ ۚ إِنَّ الشَّيْطَانَ كَانَ لِلْإِنْسَانِ عَدُوًّا مُبِينًا And say to My slaves (servants; mankind created by God) that they should (only) say the best words. (Because) Shaitan (Satan) verily, sows disagreements among them. Surely, Shaitan (Satan) is to man a plain enemy. Surah Al-Maaida Verse 90: يَا أَيُّهَا الَّذِينَ آمَنُوا إِنَّمَا الْخَمْرُ وَالْمَيْسِرُ وَالْأَنْصَابُ وَالْأَزْلَامُ رِجْسٌ مِنْ عَمَلِ الشَّيْطَانِ فَاجْتَنِبُوهُ لَعَلَّكُمْ تُفْلِحُونَ O you who believe! Intoxicants (all kinds of alcoholic drinks), gambling, Al-Ansab, and Al-Azlam (arrows for seeking luck or decision) are an abomination of Shaitan's (Satan) handiwork. So avoid (strictly all) that (abomination) in order that you may be successful. Verse 91: إِنَّمَا يُرِيدُ الشَّيْطَانُ أَنْ يُوقِعَ بَيْنَكُمُ الْعَدَاوَةَ وَالْبَغْضَاءَ فِي الْخَمْرِ وَالْمَيْسِرِ وَيَصُدَّكُمْ عَنْ ذِكْرِ اللَّهِ وَعَنِ الصَّلَاةِ ۖ فَهَلْ أَنْتُمْ مُنْتَهُونَ Shaitan (Satan) wants only to excite enmity and hatred between you with intoxicants (alcoholic drinks) and gambling, and hinder you from the remembrance of Allah (God) and from As-Salat (the prayer). So, will you not then abstain?
Surah Luqman: Verse 17: يَا بُنَيَّ أَقِمِ الصَّلَاةَ وَأْمُرْ بِالْمَعْرُوفِ وَانْهَ عَنِ الْمُنْكَرِ وَاصْبِرْ عَلَىٰ مَا أَصَابَكَ ۖ إِنَّ ذَٰلِكَ مِنْ عَزْمِ الْأُمُورِ "O my son (said Luqman, peace be upon him) ! Aqim-is-Salat (perform As-Salat; prayers), enjoin (people) for Al-Ma'ruf (all that is good), and forbid (people) from Al-Munkar (all that is evil and bad), and bear with patience whatever befall you. Verily! These are some of the important commandments ordered by Allah with no exemption. Verse 18: وَلَا تُصَعِّرْ خَدَّكَ لِلنَّاسِ وَلَا تَمْشِ فِي الْأَرْضِ مَرَحًا ۖ إِنَّ اللَّهَ لَا يُحِبُّ كُلَّ مُخْتَالٍ فَخُورٍ "And don’t turn your face away from men with pride, and don’t walk in insolence through the earth. Verily, Allah does not love each arrogant (prideful) boaster. Verse 19: وَاقْصِدْ فِي مَشْيِكَ وَاغْضُضْ مِنْ صَوْتِكَ ۚ إِنَّ أَنْكَرَ الْأَصْوَاتِ لَصَوْتُ الْحَمِيرِ "And be moderate (or show no insolence) in your walking, and lower your voice. Verily, the harshest of all voices is the voice of the donkey."
Surah Taa-Haa: Verse 131: وَلَا تَمُدَّنَّ عَيْنَيْكَ إِلَىٰ مَا مَتَّعْنَا بِهِ أَزْوَاجًا مِنْهُمْ زَهْرَةَ الْحَيَاةِ الدُّنْيَا لِنَفْتِنَهُمْ فِيهِ ۚ وَرِزْقُ رَبِّكَ خَيْرٌ وَأَبْقَىٰ And strain not your eyes in longing for the things We have given for enjoyment to various groups of them, the splendour of the life of this world that We may test them thereby. But the provision (good reward in the Hereafter) of your Lord is better and more lasting.
Surah Al-Hujuraat: Verse 11: يَا أَيُّهَا الَّذِينَ آمَنُوا لَا يَسْخَرْ قَوْمٌ مِنْ قَوْمٍ عَسَىٰ أَنْ يَكُونُوا خَيْرًا مِنْهُمْ وَلَا نِسَاءٌ مِنْ نِسَاءٍ عَسَىٰ أَنْ يَكُنَّ خَيْرًا مِنْهُنَّ ۖ وَلَا تَلْمِزُوا أَنْفُسَكُمْ وَلَا تَنَابَزُوا بِالْأَلْقَابِ ۖ بِئْسَ الِاسْمُ الْفُسُوقُ بَعْدَ الْإِيمَانِ ۚ وَمَنْ لَمْ يَتُبْ فَأُولَٰئِكَ هُمُ الظَّالِمُونَ O you who believe! Let not a group scoff at another group, it may be that the latter are better than the former; nor let (some) women scoff at other women, it may be that the latter are better than the former, nor defame one another, nor insult one another by nicknames. How bad is it, to insult one's brother after having Faith. And whosoever does not repent, then such are indeed Zalimun (unjust, wrong-doers, etc.). Verse 12: يَا أَيُّهَا الَّذِينَ آمَنُوا اجْتَنِبُوا كَثِيرًا مِنَ الظَّنِّ إِنَّ بَعْضَ الظَّنِّ إِثْمٌ ۖ وَلَا تَجَسَّسُوا وَلَا يَغْتَبْ بَعْضُكُمْ بَعْضًا ۚ أَيُحِبُّ أَحَدُكُمْ أَنْ يَأْكُلَ لَحْمَ أَخِيهِ مَيْتًا فَكَرِهْتُمُوهُ ۚ وَاتَّقُوا اللَّهَ ۚ إِنَّ اللَّهَ تَوَّابٌ رَحِيمٌ O you who believe! Avoid much suspicions, indeed some suspicions are sins. And spy not, neither backbite one another. Would one of you like to eat the flesh of his dead brother? You would hate it (so hate backbiting). And fear Allah. Verily, Allah is the One Who accepts repentance, Most Merciful.
Surah Al-Maaida: Verse 38: وَالسَّارِقُ وَالسَّارِقَةُ فَاقْطَعُوا أَيْدِيَهُمَا جَزَاءً بِمَا كَسَبَا نَكَالًا مِنَ اللَّهِ ۗ وَاللَّهُ عَزِيزٌ حَكِيمٌ Cut off (from the wrist joint) the (right) hand of the thief, male or female, as a recompense for that which they committed, a punishment by way of example from Allah. And Allah is All-Powerful, All-Wise. Verse 39: فَمَنْ تَابَ مِنْ بَعْدِ ظُلْمِهِ وَأَصْلَحَ فَإِنَّ اللَّهَ يَتُوبُ عَلَيْهِ ۗ إِنَّ اللَّهَ غَفُورٌ رَحِيمٌ But whosoever repents after his crime and does righteous good deeds, then verily, Allah (God) will pardon him (accept his repentance). Verily, Allah is Oft-Forgiving, Most Merciful.
Surah Aal-i-Imraan: Verse 130: يَا أَيُّهَا الَّذِينَ آمَنُوا لَا تَأْكُلُوا الرِّبَا أَضْعَافًا مُضَاعَفَةً ۖ وَاتَّقُوا اللَّهَ لَعَلَّكُمْ تُفْلِحُونَ O you who believe! Don’t eat Riba (usury) doubled and multiplied, but fear Allah that you may be successful.
Surah Al-Maaida: Verse 3: حُرِّمَتْ عَلَيْكُمُ الْمَيْتَةُ وَالدَّمُ وَلَحْمُ الْخِنْزِيرِ وَمَا أُهِلَّ لِغَيْرِ اللَّهِ بِهِ وَالْمُنْخَنِقَةُ وَالْمَوْقُوذَةُ وَالْمُتَرَدِّيَةُ وَالنَّطِيحَةُ وَمَا أَكَلَ السَّبُعُ إِلَّا مَا ذَكَّيْتُمْ وَمَا ذُبِحَ عَلَى النُّصُبِ وَأَنْ تَسْتَقْسِمُوا بِالْأَزْلَامِ ۚ ذَٰلِكُمْ فِسْقٌ ۗ الْيَوْمَ يَئِسَ الَّذِينَ كَفَرُوا مِنْ دِينِكُمْ فَلَا تَخْشَوْهُمْ وَاخْشَوْنِ ۚ الْيَوْمَ أَكْمَلْتُ لَكُمْ دِينَكُمْ وَأَتْمَمْتُ عَلَيْكُمْ نِعْمَتِي وَرَضِيتُ لَكُمُ الْإِسْلَامَ دِينًا ۚ فَمَنِ اضْطُرَّ فِي مَخْمَصَةٍ غَيْرَ مُتَجَانِفٍ لِإِثْمٍ ۙ فَإِنَّ اللَّهَ غَفُورٌ رَحِيمٌ Forbidden to you (for food) are: Al-Maytatah (the dead animals - cattle-beast not slaughtered), blood, the flesh of swine, and the meat of that which has been slaughtered as a sacrifice for others than Allah, or has been slaughtered for idols, etc., or on which Allah's Name has not been mentioned while slaughtering, and that which has been killed by strangling, or by a violent blow, or by a headlong fall, or by the goring of horns - and that which has been (partly) eaten by a wild animal - unless you are able to slaughter it (before its death) - and that which is sacrificed (slaughtered) on An-Nusub (stone altars). (Forbidden) also is to use arrows seeking luck or decision, (all) that is Fisqun (disobedience of Allah and sin). This day, those who disbelieved have given up all hope of your religion, so don’t fear them, but fear Me. This day, I have perfected your religion for you, completed My Favour upon you, and have chosen for you Islam as your religion. But who is forced by severe hunger, with no inclination to sin (such can eat these above-mentioned meats), then surely, Allah is Oft-Forgiving, Most Merciful.
Surah Al-Baqara: Verse 114: وَمَنْ أَظْلَمُ مِمَّنْ مَنَعَ مَسَاجِدَ اللَّهِ أَنْ يُذْكَرَ فِيهَا اسْمُهُ وَسَعَىٰ فِي خَرَابِهَا ۚ أُولَٰئِكَ مَا كَانَ لَهُمْ أَنْ يَدْخُلُوهَا إِلَّا خَائِفِينَ ۚ لَهُمْ فِي الدُّنْيَا خِزْيٌ وَلَهُمْ فِي الْآخِرَةِ عَذَابٌ عَظِيمٌ And who is more unjust than those who forbid that Allah's Name be glorified and mentioned much (i.e. prayers and invocations, etc.) in Allah's Mosques and strive for their ruin? It was not fitting that such should themselves enter them (Allah's Mosques) except in fear. For them there is disgrace in this world, and they will have a great torment in the Hereafter.
Surah Al-Baqara: Verse 110: وَأَقِيمُوا الصَّلَاةَ وَآتُوا الزَّكَاةَ ۚ وَمَا تُقَدِّمُوا لِأَنْفُسِكُمْ مِنْ خَيْرٍ تَجِدُوهُ عِنْدَ اللَّهِ ۗ إِنَّ اللَّهَ بِمَا تَعْمَلُونَ بَصِيرٌ And perform As-Salat (prayers), and give Zakat (compulsory charity that must be given every year), and whatever of good (deeds that Allah loves) you send forth for yourselves before you, you shall find it with Allah. Certainly, Allah is All-Seer of what you do.
Surah Al-A'raaf: Verse 31: ۞ يَا بَنِي آدَمَ خُذُوا زِينَتَكُمْ عِنْدَ كُلِّ مَسْجِدٍ وَكُلُوا وَاشْرَبُوا وَلَا تُسْرِفُوا ۚ إِنَّهُ لَا يُحِبُّ الْمُسْرِفِينَ
O Children of Adam! Take your adornment (by wearing your clean clothes), while praying and going round (the Tawaf of) the Ka'bah, and eat and drink but waste not by extravagance, certainly He (Allah) likes not Al-Musrifun (those who waste by extravagance). Verse 32: قُلْ مَنْ حَرَّمَ زِينَةَ اللَّهِ الَّتِي أَخْرَجَ لِعِبَادِهِ وَالطَّيِّبَاتِ مِنَ الرِّزْقِ ۚ قُلْ هِيَ لِلَّذِينَ آمَنُوا فِي الْحَيَاةِ الدُّنْيَا خَالِصَةً يَوْمَ الْقِيَامَةِ ۗ كَذَٰلِكَ نُفَصِّلُ الْآيَاتِ لِقَوْمٍ يَعْلَمُونَ Say: "Who has forbidden the adoration with clothes given by Allah, which He has produced for his slaves, and At-Taiyibat [all kinds of Halal (lawful) things] of food?" Say: "They are, in the life of this world, for those who believe, (and) exclusively for them (believers) on the Day of Resurrection (the disbelievers will not share them)." Thus We explain the Ayat (verses, Islamic laws) in detail for people who have knowledge. Verse 33: قُلْ إِنَّمَا حَرَّمَ رَبِّيَ الْفَوَاحِشَ مَا ظَهَرَ مِنْهَا وَمَا بَطَنَ وَالْإِثْمَ وَالْبَغْيَ بِغَيْرِ الْحَقِّ وَأَنْ تُشْرِكُوا بِاللَّهِ مَا لَمْ يُنَزِّلْ بِهِ سُلْطَانًا وَأَنْ تَقُولُوا عَلَى اللَّهِ مَا لَا تَعْلَمُونَ Say: "The things that my Lord has indeed forbidden are Al-Fawahish (great evil sins) whether committed openly or secretly, sins (of all kinds), unrighteous oppression, joining partners (in worship) with Allah for which He has given no authority, and saying things about Allah of which you have no knowledge." Verse 34: وَلِكُلِّ أُمَّةٍ أَجَلٌ ۖ فَإِذَا جَاءَ أَجَلُهُمْ لَا يَسْتَأْخِرُونَ سَاعَةً ۖ وَلَا يَسْتَقْدِمُونَ And every nation has its appointed term; when their term is reached, neither can they delay it nor can they advance it an hour (or a moment). Verse 35: يَا بَنِي آدَمَ إِمَّا يَأْتِيَنَّكُمْ رُسُلٌ مِنْكُمْ يَقُصُّونَ عَلَيْكُمْ آيَاتِي ۙ فَمَنِ اتَّقَىٰ وَأَصْلَحَ فَلَا خَوْفٌ عَلَيْهِمْ وَلَا هُمْ يَحْزَنُونَ O Children of Adam! If there come to you Messengers from amongst you, reciting to you, My Verses, then whosoever becomes pious and righteous, on them shall be no fear, nor shall they grieve. Verse 36: وَالَّذِينَ كَذَّبُوا بِآيَاتِنَا وَاسْتَكْبَرُوا عَنْهَا أُولَٰئِكَ أَصْحَابُ النَّارِ ۖ هُمْ فِيهَا خَالِدُونَ But those who reject Our Ayat (proofs, evidences, verses, lessons, signs, revelations, etc.) and treat them with arrogance, they are the dwellers of the (Hell) Fire, they will abide therein forever. Verse 37: فَمَنْ أَظْلَمُ مِمَّنِ افْتَرَىٰ عَلَى اللَّهِ كَذِبًا أَوْ كَذَّبَ بِآيَاتِهِ ۚ أُولَٰئِكَ يَنَالُهُمْ نَصِيبُهُمْ مِنَ الْكِتَابِ ۖ حَتَّىٰ إِذَا جَاءَتْهُمْ رُسُلُنَا يَتَوَفَّوْنَهُمْ قَالُوا أَيْنَ مَا كُنْتُمْ تَدْعُونَ مِنْ دُونِ اللَّهِ ۖ قَالُوا ضَلُّوا عَنَّا وَشَهِدُوا عَلَىٰ أَنْفُسِهِمْ أَنَّهُمْ كَانُوا كَافِرِينَ Who is more unjust than one who invents a lie against Allah or rejects His Ayat (proofs, evidences, verses, lessons, signs, revelations, etc.)? For such their appointed portion (good things of this worldly life and their period of stay therein) will reach them from the Book (of Decrees) until, when Our Messengers (the angel of death and his assistants) come to them to take their souls, they (the angels) will say: "Where are those whom you used to invoke and worship besides Allah," they will reply, "They have vanished and deserted us." And they will bear witness against themselves, that they were disbelievers. Verse 38: قَالَ ادْخُلُوا فِي أُمَمٍ قَدْ خَلَتْ مِنْ قَبْلِكُمْ مِنَ الْجِنِّ وَالْإِنْسِ فِي النَّارِ ۖ كُلَّمَا دَخَلَتْ أُمَّةٌ لَعَنَتْ أُخْتَهَا ۖ حَتَّىٰ إِذَا ادَّارَكُوا فِيهَا جَمِيعًا قَالَتْ أُخْرَاهُمْ لِأُولَاهُمْ رَبَّنَا هَٰؤُلَاءِ أَضَلُّونَا فَآتِهِمْ عَذَابًا ضِعْفًا مِنَ النَّارِ ۖ قَالَ لِكُلٍّ ضِعْفٌ وَلَٰكِنْ لَا تَعْلَمُونَ (Allah) will say: "Enter you in the company of nations who passed away before you, of men and jinns, into the Fire." Every time a new nation enters, it curses its sister nation (that went before), until they will be gathered all together in the Fire. The last of them will say to the first of them: "Our Lord! These misled us, so give them a double torment of the Fire." He will say: "For each one there is double (torment), but you don’t know." Verse 39: وَقَالَتْ أُولَاهُمْ لِأُخْرَاهُمْ فَمَا كَانَ لَكُمْ عَلَيْنَا مِنْ فَضْلٍ فَذُوقُوا الْعَذَابَ بِمَا كُنْتُمْ تَكْسِبُونَ The first of them will say to the last of them: "You were not better than us, so taste the torment for what you used to earn." Verse 40: إِنَّ الَّذِينَ كَذَّبُوا بِآيَاتِنَا وَاسْتَكْبَرُوا عَنْهَا لَا تُفَتَّحُ لَهُمْ أَبْوَابُ السَّمَاءِ وَلَا يَدْخُلُونَ الْجَنَّةَ حَتَّىٰ يَلِجَ الْجَمَلُ فِي سَمِّ الْخِيَاطِ ۚ وَكَذَٰلِكَ نَجْزِي الْمُجْرِمِينَ Verily, those who belie Our Ayat (proofs, evidences, verses, lessons, signs, revelations, etc.) and are pridefully arrogant towards them (proofs, verses, signs, etc.), for them the gates of heaven will not be opened (to accept and answer their supplications and prayers), and they will not enter Paradise until the camel goes through the eye of the needle (which is impossible). Thus do We recompense the Mujrimun (criminals, sinners, etc.). Verse 41: لَهُمْ مِنْ جَهَنَّمَ مِهَادٌ وَمِنْ فَوْقِهِمْ غَوَاشٍ ۚ وَكَذَٰلِكَ نَجْزِي الظَّالِمِينَ Theirs will be a bed of Hell (Fire), and over them coverings (of Hell-fire). Thus We recompense the Zalimun (unjust and wrong-doers, etc.).
An-Nahl Verse 94: وَلَا تَتَّخِذُوا أَيْمَانَكُمْ دَخَلًا بَيْنَكُمْ فَتَزِلَّ قَدَمٌ بَعْدَ ثُبُوتِهَا وَتَذُوقُوا السُّوءَ بِمَا صَدَدْتُمْ عَنْ سَبِيلِ اللَّهِ ۖ وَلَكُمْ عَذَابٌ عَظِيمٌ And don’t make your oaths, a means of deception among yourselves, lest a foot may slip after being firmly planted, and you may have to taste the evil (punishment in this world) of having hindered (men) from the Path of Allah (i.e. Belief in the Oneness of Allah and His Messenger, Muhammad SAW, fighting in the cause of Allah), and yours will be a great torment (i.e. the Fire of Hell in the Hereafter). Verse 95: وَلَا تَشْتَرُوا بِعَهْدِ اللَّهِ ثَمَنًا قَلِيلًا ۚ إِنَّمَا عِنْدَ اللَّهِ هُوَ خَيْرٌ لَكُمْ إِنْ كُنْتُمْ تَعْلَمُونَ
And purchase not a small gain at the cost of Allah's Covenant. Verily! What is with Allah is better for you if you did but know.
A lot of people turn away from God, Allah, because of fearing not to be forgiven.
4:116 An-Nisaa
إِنَّ اللَّهَ لَا يَغْفِرُ أَنْ يُشْرَكَ بِهِ وَيَغْفِرُ مَا دُونَ ذَٰلِكَ لِمَنْ يَشَاءُ ۚ وَمَنْ يُشْرِكْ بِاللَّهِ فَقَدْ ضَلَّ ضَلَالًا بَعِيدًا
Indeed, Allah does not forgive association with Him, but He forgives other than that for whom He wills. And he who associates others with Allah has certainly gone far astray.
39:53 Az-Zumar
۞ قُلْ يَا عِبَادِيَ الَّذِينَ أَسْرَفُوا عَلَىٰ أَنْفُسِهِمْ لَا تَقْنَطُوا مِنْ رَحْمَةِ اللَّهِ ۚ إِنَّ اللَّهَ يَغْفِرُ الذُّنُوبَ جَمِيعًا ۚ إِنَّهُ هُوَ الْغَفُورُ الرَّحِيمُ
Say, "O My servants who have transgressed against themselves [by sinning], do not despair of the mercy of Allah. Indeed, Allah forgives all sins. Indeed, it is He who is the Forgiving, the Merciful."
39:54 Az-Zumar
وَأَنِيبُوا إِلَىٰ رَبِّكُمْ وَأَسْلِمُوا لَهُ مِنْ قَبْلِ أَنْ يَأْتِيَكُمُ الْعَذَابُ ثُمَّ لَا تُنْصَرُونَ
And return [in repentance] to your Lord and submit to Him before the punishment comes upon you; then you will not be helped.
39:55 Az-Zumar
وَاتَّبِعُوا أَحْسَنَ مَا أُنْزِلَ إِلَيْكُمْ مِنْ رَبِّكُمْ مِنْ قَبْلِ أَنْ يَأْتِيَكُمُ الْعَذَابُ بَغْتَةً وَأَنْتُمْ لَا تَشْعُرُونَ
And follow the best of what was revealed to you from your Lord before the punishment comes upon you suddenly while you do not perceive,
39:56 Az-Zumar
أَنْ تَقُولَ نَفْسٌ يَا حَسْرَتَا عَلَىٰ مَا فَرَّطْتُ فِي جَنْبِ اللَّهِ وَإِنْ كُنْتُ لَمِنَ السَّاخِرِينَ
Lest a soul should say, "Oh [how great is] my regret over what I neglected in regard to Allah and that I was among the mockers."
39:57 Az-Zumar
أَوْ تَقُولَ لَوْ أَنَّ اللَّهَ هَدَانِي لَكُنْتُ مِنَ الْمُتَّقِينَ
Or [lest] it say, "If only Allah had guided me, I would have been among the righteous."
39:58 Az-Zumar
أَوْ تَقُولَ حِينَ تَرَى الْعَذَابَ لَوْ أَنَّ لِي كَرَّةً فَأَكُونَ مِنَ الْمُحْسِنِينَ
Or [lest] it say when it sees the punishment, "If only I had another turn so I could be among the doers of good."
39:59 Az-Zumar
بَلَىٰ قَدْ جَاءَتْكَ آيَاتِي فَكَذَّبْتَ بِهَا وَاسْتَكْبَرْتَ وَكُنْتَ مِنَ الْكَافِرِينَ
But yes, there had come to you My verses, but you denied them and were arrogant, and you were among the disbelievers.
39:60 Az-Zumar
وَيَوْمَ الْقِيَامَةِ تَرَى الَّذِينَ كَذَبُوا عَلَى اللَّهِ وُجُوهُهُمْ مُسْوَدَّةٌ ۚ أَلَيْسَ فِي جَهَنَّمَ مَثْوًى لِلْمُتَكَبِّرِينَ
And on the Day of Resurrection you will see those who lied about Allah [with] their faces blackened. Is there not in Hell a residence for the arrogant?
39:61 Az-Zumar
وَيُنَجِّي اللَّهُ الَّذِينَ اتَّقَوْا بِمَفَازَتِهِمْ لَا يَمَسُّهُمُ السُّوءُ وَلَا هُمْ يَحْزَنُونَ
And Allah will save those who feared Him by their attainment; no evil will touch them, nor will they grieve.
In Islam we believe in God’s messengers and his books, Torah and Gospel, however, some changes were brought by some people leading to disbelief in the oneness of God.
2:285 Al-Baqara
آمَنَ الرَّسُولُ بِمَا أُنْزِلَ إِلَيْهِ مِنْ رَبِّهِ وَالْمُؤْمِنُونَ ۚ كُلٌّ آمَنَ بِاللَّهِ وَمَلَائِكَتِهِ وَكُتُبِهِ وَرُسُلِهِ لَا نُفَرِّقُ بَيْنَ أَحَدٍ مِنْ رُسُلِهِ ۚ وَقَالُوا سَمِعْنَا وَأَطَعْنَا ۖ غُفْرَانَكَ رَبَّنَا وَإِلَيْكَ الْمَصِيرُ
The Messenger has believed in what was revealed to him from his Lord, and [so have] the believers. All of them have believed in Allah and His angels and His books and His messengers, [saying], "We make no distinction between any of His messengers." And they say, "We hear and we obey. [We seek] Your forgiveness, our Lord, and to You is the [final] destination."
2:286 Al-Baqara
لَا يُكَلِّفُ اللَّهُ نَفْسًا إِلَّا وُسْعَهَا ۚ لَهَا مَا كَسَبَتْ وَعَلَيْهَا مَا اكْتَسَبَتْ ۗ رَبَّنَا لَا تُؤَاخِذْنَا إِنْ نَسِينَا أَوْ أَخْطَأْنَا ۚ رَبَّنَا وَلَا تَحْمِلْ عَلَيْنَا إِصْرًا كَمَا حَمَلْتَهُ عَلَى الَّذِينَ مِنْ قَبْلِنَا ۚ رَبَّنَا وَلَا تُحَمِّلْنَا مَا لَا طَاقَةَ لَنَا بِهِ ۖ وَاعْفُ عَنَّا وَاغْفِرْ لَنَا وَارْحَمْنَا ۚ أَنْتَ مَوْلَانَا فَانْصُرْنَا عَلَى الْقَوْمِ الْكَافِرِينَ
Allah does not charge a soul except [with that within] its capacity. It will have [the consequence of] what [good] it has gained, and it will bear [the consequence of] what [evil] it has earned. "Our Lord, do not impose blame upon us if we have forgotten or erred. Our Lord, and lay not upon us a burden like that which You laid upon those before us. Our Lord, and burden us not with that which we have no ability to bear. And pardon us; and forgive us; and have mercy upon us. You are our protector, so give us victory over the disbelieving people."
4:163 An-Nisaa
۞ إِنَّا أَوْحَيْنَا إِلَيْكَ كَمَا أَوْحَيْنَا إِلَىٰ نُوحٍ وَالنَّبِيِّينَ مِنْ بَعْدِهِ ۚ وَأَوْحَيْنَا إِلَىٰ إِبْرَاهِيمَ وَإِسْمَاعِيلَ وَإِسْحَاقَ وَيَعْقُوبَ وَالْأَسْبَاطِ وَعِيسَىٰ وَأَيُّوبَ وَيُونُسَ وَهَارُونَ وَسُلَيْمَانَ ۚ وَآتَيْنَا دَاوُودَ زَبُورًا
Indeed, We have revealed to you, [O Muhammad], as We revealed to Noah and the prophets after him. And we revealed to Abraham, Ishmael, Isaac, Jacob, the Descendants, Jesus, Job, Jonah, Aaron, and Solomon, and to David We gave the book [of Psalms].
4:164 An-Nisaa
وَرُسُلًا قَدْ قَصَصْنَاهُمْ عَلَيْكَ مِنْ قَبْلُ وَرُسُلًا لَمْ نَقْصُصْهُمْ عَلَيْكَ ۚ وَكَلَّمَ اللَّهُ مُوسَىٰ تَكْلِيمًا
And [We sent] messengers about whom We have related [their stories] to you before and messengers about whom We have not related to you. And Allah spoke to Moses with [direct] speech.
4:165 An-Nisaa
رُسُلًا مُبَشِّرِينَ وَمُنْذِرِينَ لِئَلَّا يَكُونَ لِلنَّاسِ عَلَى اللَّهِ حُجَّةٌ بَعْدَ الرُّسُلِ ۚ وَكَانَ اللَّهُ عَزِيزًا حَكِيمًا
[We sent] messengers as bringers of good tidings and warners so that mankind will have no argument against Allah after the messengers. And ever is Allah Exalted in Might and Wise.
9:30 At-Tawba
وَقَالَتِ الْيَهُودُ عُزَيْرٌ ابْنُ اللَّهِ وَقَالَتِ النَّصَارَى الْمَسِيحُ ابْنُ اللَّهِ ۖ ذَٰلِكَ قَوْلُهُمْ بِأَفْوَاهِهِمْ ۖ يُضَاهِئُونَ قَوْلَ الَّذِينَ كَفَرُوا مِنْ قَبْلُ ۚ قَاتَلَهُمُ اللَّهُ ۚ أَنَّىٰ يُؤْفَكُونَ
The Jews say, "Ezra is the son of Allah "; and the Christians say, "The Messiah is the son of Allah." That is their statement from their mouths; they imitate the saying of those who disbelieved [before them]. May Allah destroy them; how are they deluded?
9:31 At-Tawba
اتَّخَذُوا أَحْبَارَهُمْ وَرُهْبَانَهُمْ أَرْبَابًا مِنْ دُونِ اللَّهِ وَالْمَسِيحَ ابْنَ مَرْيَمَ وَمَا أُمِرُوا إِلَّا لِيَعْبُدُوا إِلَٰهًا وَاحِدًا ۖ لَا إِلَٰهَ إِلَّا هُوَ ۚ سُبْحَانَهُ عَمَّا يُشْرِكُونَ
They have taken their scholars and monks as lords besides Allah, and [also] the Messiah, the son of Mary. And they were not commanded except to worship one God; there is no deity except Him. Exalted is He above whatever they associate with Him.
5:72 Al-Maaida
لَقَدْ كَفَرَ الَّذِينَ قَالُوا إِنَّ اللَّهَ هُوَ الْمَسِيحُ ابْنُ مَرْيَمَ ۖ وَقَالَ الْمَسِيحُ يَا بَنِي إِسْرَائِيلَ اعْبُدُوا اللَّهَ رَبِّي وَرَبَّكُمْ ۖ إِنَّهُ مَنْ يُشْرِكْ بِاللَّهِ فَقَدْ حَرَّمَ اللَّهُ عَلَيْهِ الْجَنَّةَ وَمَأْوَاهُ النَّارُ ۖ وَمَا لِلظَّالِمِينَ مِنْ أَنْصَارٍ
They have certainly disbelieved who say, "Allah is the Messiah, the son of Mary" while the Messiah has said, "O Children of Israel, worship Allah, my Lord and your Lord." Indeed, he who associates others with Allah - Allah has forbidden him Paradise, and his refuge is the Fire. And there are not for the wrongdoers any helpers.
5:73 Al-Maaida
لَقَدْ كَفَرَ الَّذِينَ قَالُوا إِنَّ اللَّهَ ثَالِثُ ثَلَاثَةٍ ۘ وَمَا مِنْ إِلَٰهٍ إِلَّا إِلَٰهٌ وَاحِدٌ ۚ وَإِنْ لَمْ يَنْتَهُوا عَمَّا يَقُولُونَ لَيَمَسَّنَّ الَّذِينَ كَفَرُوا مِنْهُمْ عَذَابٌ أَلِيمٌ
They have certainly disbelieved who say, "Allah is the third of three." And there is no god except one God. And if they do not desist from what they are saying, there will surely afflict the disbelievers among them a painful punishment.
5:74 Al-Maaida
أَفَلَا يَتُوبُونَ إِلَى اللَّهِ وَيَسْتَغْفِرُونَهُ ۚ وَاللَّهُ غَفُورٌ رَحِيمٌ
So will they not repent to Allah and seek His forgiveness? And Allah is Forgiving and Merciful.
5:75 Al-Maaida
مَا الْمَسِيحُ ابْنُ مَرْيَمَ إِلَّا رَسُولٌ قَدْ خَلَتْ مِنْ قَبْلِهِ الرُّسُلُ وَأُمُّهُ صِدِّيقَةٌ ۖ كَانَا يَأْكُلَانِ الطَّعَامَ ۗ انْظُرْ كَيْفَ نُبَيِّنُ لَهُمُ الْآيَاتِ ثُمَّ انْظُرْ أَنَّىٰ يُؤْفَكُونَ
The Messiah, son of Mary, was not but a messenger; [other] messengers have passed on before him. And his mother was a supporter of truth. They both used to eat food. Look how We make clear to them the signs; then look how they are deluded.
5:76 Al-Maaida
قُلْ أَتَعْبُدُونَ مِنْ دُونِ اللَّهِ مَا لَا يَمْلِكُ لَكُمْ ضَرًّا وَلَا نَفْعًا ۚ وَاللَّهُ هُوَ السَّمِيعُ الْعَلِيمُ
Say, "Do you worship besides Allah that which holds for you no [power of] harm or benefit while it is Allah who is the Hearing, the Knowing?"
5:77 Al-Maaida
قُلْ يَا أَهْلَ الْكِتَابِ لَا تَغْلُوا فِي دِينِكُمْ غَيْرَ الْحَقِّ وَلَا تَتَّبِعُوا أَهْوَاءَ قَوْمٍ قَدْ ضَلُّوا مِنْ قَبْلُ وَأَضَلُّوا كَثِيرًا وَضَلُّوا عَنْ سَوَاءِ السَّبِيلِ
Say, "O People of the Scripture (the books, Torah and Gospel), do not exceed limits in your religion beyond the truth and do not follow the inclinations of a people who had gone astray before and misled many and have strayed from the soundness of the way."
4:171 An-Nisaa
يَا أَهْلَ الْكِتَابِ لَا تَغْلُوا فِي دِينِكُمْ وَلَا تَقُولُوا عَلَى اللَّهِ إِلَّا الْحَقَّ ۚ إِنَّمَا الْمَسِيحُ عِيسَى ابْنُ مَرْيَمَ رَسُولُ اللَّهِ وَكَلِمَتُهُ أَلْقَاهَا إِلَىٰ مَرْيَمَ وَرُوحٌ مِنْهُ ۖ فَآمِنُوا بِاللَّهِ وَرُسُلِهِ ۖ وَلَا تَقُولُوا ثَلَاثَةٌ ۚ انْتَهُوا خَيْرًا لَكُمْ ۚ إِنَّمَا اللَّهُ إِلَٰهٌ وَاحِدٌ ۖ سُبْحَانَهُ أَنْ يَكُونَ لَهُ وَلَدٌ ۘ لَهُ مَا فِي السَّمَاوَاتِ وَمَا فِي الْأَرْضِ ۗ وَكَفَىٰ بِاللَّهِ وَكِيلًا
O People of the Scripture, do not commit excess in your religion or say about Allah except the truth. The Messiah, Jesus, the son of Mary, was but a messenger of Allah and His word which He directed to Mary and a soul [created at a command] from Him. So believe in Allah and His messengers. And do not say, "Three"; desist - it is better for you. Indeed, Allah is but one God. Exalted is He above having a son. To Him belongs whatever is in the heavens and whatever is on the earth. And sufficient is Allah as Disposer of affairs.
4:172 An-Nisaa
لَنْ يَسْتَنْكِفَ الْمَسِيحُ أَنْ يَكُونَ عَبْدًا لِلَّهِ وَلَا الْمَلَائِكَةُ الْمُقَرَّبُونَ ۚ وَمَنْ يَسْتَنْكِفْ عَنْ عِبَادَتِهِ وَيَسْتَكْبِرْ فَسَيَحْشُرُهُمْ إِلَيْهِ جَمِيعًا
Never would the Messiah disdain to be a servant of Allah, nor would the angels near [to Him]. And whoever disdains His worship and is arrogant - He will gather them to Himself all together.
And in the following Hadiths (sayings of prophet Mohamed peace be upon him) and verses what a practicing Muslim should do:
حَدَّثَنَا أَبُو الْيَمَانِ ، قَالَ: أَخْبَرَنَا شُعَيْبٌ ، عَنِ الزُّهْرِيِّ ، قَالَ: أَخْبَرَنِي أَبُو إِدْرِيسَ عَائِذُ اللَّهِ بْنُ عَبْدِ اللَّهِ ، أَنَّ عُبَادَةَ بْنَ الصَّامِتِ رَضِيَ اللَّهُ عَنْهُ، وَكَانَ شَهِدَ بَدْرًا وَهُوَ أَحَدُ النُّقَبَاءِ لَيْلَةَ الْعَقَبَةِ، أَنَّ رَسُولَ اللَّهِ صَلَّى اللَّهُ عَلَيْهِ وَسَلَّمَ، قَالَ وَحَوْلَهُ عِصَابَةٌ مِنْ أَصْحَابِهِ: بَايِعُونِي عَلَى أَنْ لَا تُشْرِكُوا بِاللَّهِ شَيْئًا، وَلَا تَسْرِقُوا، وَلَا تَزْنُوا، وَلَا تَقْتُلُوا أَوْلَادَكُمْ، وَلَا تَأْتُوا بِبُهْتَانٍ تَفْتَرُونَهُ بَيْنَ أَيْدِيكُمْ وَأَرْجُلِكُمْ، وَلَا تَعْصُوا فِي مَعْرُوفٍ، فَمَنْ وَفَى مِنْكُمْ فَأَجْرُهُ عَلَى اللَّهِ، وَمَنْ أَصَابَ مِنْ ذَلِكَ شَيْئًا فَعُوقِبَ فِي الدُّنْيَا فَهُوَ كَفَّارَةٌ لَهُ، وَمَنْ أَصَابَ مِنْ ذَلِكَ شَيْئًا ثُمَّ سَتَرَهُ اللَّهُ فَهُوَ إِلَى اللَّهِ إِنْ شَاءَ عَفَا عَنْهُ وَإِنْ شَاءَ عَاقَبَهُ، فَبَايَعْنَاهُ عَلَى ذَلِك.
Translation:Narrated Ubadah bin As-Samit (RA): who took part in the battle of Badr and was a Naqib (a person heading a group of six persons), on the night of Al-Aqabah pledge: Allahs Apostle ﷺ said while a group of his companions were around him, "Swear allegiance to me for: 1. Not to join anything in worship along with Allah. 2. Not to steal. 3. Not to commit illegal sexual intercourse. 4. Not to kill your children. 5. Not to accuse an innocent person (to spread such an accusation among people). 6. Not to be disobedient (when ordered) to do good deed". The Prophet ﷺ added: "Whoever among you fulfills his pledge will be rewarded by Allah. And whoever indulges in any one of them (except the ascription of partners to Allah) and gets the punishment in this world, that punishment will be an expiation for that sin. And if one indulges in any of them, and Allah conceals his sin, it is up to Him to forgive or punish him (in the Hereafter)". Ubadah bin As-Samit (RA) added: "So we swore allegiance for these." (points to Allahs Apostle) ﷺ.
حَدَّثَنَا عُبَيْدُ اللَّهِ بْنُ مُوسَى ، قَالَ: أَخْبَرَنَا حَنْظَلَةُ بْنُ أَبِي سُفْيَانَ ، عَنْ عِكْرِمَةَ بْنِ خَالِدٍ ، عَنِ ابْنِ عُمَرَ رَضِيَ اللَّهُ عَنْهُمَا، قَالَ: قَالَ رَسُولُ اللَّهِ صَلَّى اللَّهُ عَلَيْهِ وَسَلَّمَ: بُنِيَ الْإِسْلَامُ عَلَى خَمْسٍ، شَهَادَةِ أَنْ لَا إِلَهَ إِلَّا اللَّهُ وَأَنَّ مُحَمَّدًا رَسُولُ اللَّهِ، وَإِقَامِ الصَّلَاةِ، وَإِيتَاءِ الزَّكَاةِ، وَالْحَجِّ، وَصَوْمِ رَمَضَانَ. الحج لمن استطاع اليه سبيلا*
Translation:Narrated Ibn Umar (RA) : Allahs Apostle ﷺ said: Islam is based on (the following) five (principles): 1. To testify that none has the right to be worshipped but Allah and Muhammad ﷺ is Allahs Apostle. 2. To offer the (compulsory Salat) prayers dutifully and perfectly. 3. To pay Zakat (i.e. obligatory charity). 4. To perform Hajj. (i.e. Pilgrimage to Makkah only if the person is able to do so) 5. To observe fast during the month of Ramadan.
Also, in the following verses behaviours that must be adopted by practicing Muslims:
24:30 An-Noor
قُلْ لِلْمُؤْمِنِينَ يَغُضُّوا مِنْ أَبْصَارِهِمْ وَيَحْفَظُوا فُرُوجَهُمْ ۚ ذَٰلِكَ أَزْكَىٰ لَهُمْ ۗ إِنَّ اللَّهَ خَبِيرٌ بِمَا يَصْنَعُونَ
Tell the believing men to reduce [some] of their vision (lower their gazes) and guard their private parts. That is purer for them. Indeed, Allah is Acquainted with what they do.
24:31 An-Noor
وَقُلْ لِلْمُؤْمِنَاتِ يَغْضُضْنَ مِنْ أَبْصَارِهِنَّ وَيَحْفَظْنَ فُرُوجَهُنَّ وَلَا يُبْدِينَ زِينَتَهُنَّ إِلَّا مَا ظَهَرَ مِنْهَا ۖ وَلْيَضْرِبْنَ بِخُمُرِهِنَّ عَلَىٰ جُيُوبِهِنَّ ۖ وَلَا يُبْدِينَ زِينَتَهُنَّ إِلَّا لِبُعُولَتِهِنَّ أَوْ آبَائِهِنَّ أَوْ آبَاءِ بُعُولَتِهِنَّ أَوْ أَبْنَائِهِنَّ أَوْ أَبْنَاءِ بُعُولَتِهِنَّ أَوْ إِخْوَانِهِنَّ أَوْ بَنِي إِخْوَانِهِنَّ أَوْ بَنِي أَخَوَاتِهِنَّ أَوْ نِسَائِهِنَّ أَوْ مَا مَلَكَتْ أَيْمَانُهُنَّ أَوِ التَّابِعِينَ غَيْرِ أُولِي الْإِرْبَةِ مِنَ الرِّجَالِ أَوِ الطِّفْلِ الَّذِينَ لَمْ يَظْهَرُوا عَلَىٰ عَوْرَاتِ النِّسَاءِ ۖ وَلَا يَضْرِبْنَ بِأَرْجُلِهِنَّ لِيُعْلَمَ مَا يُخْفِينَ مِنْ زِينَتِهِنَّ ۚ وَتُوبُوا إِلَى اللَّهِ جَمِيعًا أَيُّهَ الْمُؤْمِنُونَ لَعَلَّكُمْ تُفْلِحُونَ
And tell the believing women to reduce [some] of their vision (lower their gazes) and guard their private parts and not expose their adornment except that which [necessarily] appears (to cover their bodies in full (the used clothes must not be tight or transparent) except hands and face and to cover the hair) thereof and to wrap [a portion of] their headcovers over their chests and not expose their adornment except to their husbands, their fathers, their husbands' fathers, their sons, their husbands' sons, their brothers, their brothers' sons, their sisters' sons, their women, that which their right hands possess, or those male attendants having no physical desire, or children who are not yet aware of the private aspects of women. And let them not stamp their feet to make known what they conceal of their adornment. And turn to Allah in repentance, all of you, O believers, that you might succeed.
In the following an app to teach Wudu (getting ready for the prayer) and Salat the Islamic compulsory prayers that must be performed 5 times a day:
https://apps.apple.com/app/id1187721510
https://play.google.com/store/apps/datasafety?id=com.salah.osratouna&hl=en
Keep in mind the following Hadiths and verses of the Quran while wishing to offer Salat:
4:43 An-Nisaa
يَا أَيُّهَا الَّذِينَ آمَنُوا لَا تَقْرَبُوا الصَّلَاةَ وَأَنْتُمْ سُكَارَىٰ حَتَّىٰ تَعْلَمُوا مَا تَقُولُونَ وَلَا جُنُبًا إِلَّا عَابِرِي سَبِيلٍ حَتَّىٰ تَغْتَسِلُوا ۚ وَإِنْ كُنْتُمْ مَرْضَىٰ أَوْ عَلَىٰ سَفَرٍ أَوْ جَاءَ أَحَدٌ مِنْكُمْ مِنَ الْغَائِطِ أَوْ لَامَسْتُمُ النِّسَاءَ فَلَمْ تَجِدُوا مَاءً فَتَيَمَّمُوا صَعِيدًا طَيِّبًا فَامْسَحُوا بِوُجُوهِكُمْ وَأَيْدِيكُمْ ۗ إِنَّ اللَّهَ كَانَ عَفُوًّا غَفُورًا
O you who have believed, do not approach prayer while you are intoxicated (drunk or under the effect of drugs) until you know what you are saying or in a state of janabah (have had a lawful sexual intercourse or have had a wet dream) , except those passing through [a place of prayer], until you have washed [your whole body]. And if you are ill or on a journey or one of you comes from the place of relieving himself or you have contacted women and find no water, then seek clean earth and wipe over your faces and your hands [with it]. Indeed, Allah is ever Pardoning and Forgiving.
Narrated `Aisha: Whenever the Prophet (ﷺ) took a bath after Janaba he started by washing his hands and then performed ablution like that for the prayer. After that he would put his fingers in water and move the roots of his hair with them, and then pour three handfuls of water over his head and then pour water all over his body.
حَدَّثَنَا عَبْدُ اللَّهِ بْنُ يُوسُفَ، قَالَ أَخْبَرَنَا مَالِكٌ، عَنْ هِشَامٍ، عَنْ أَبِيهِ، عَنْ عَائِشَةَ، زَوْجِ النَّبِيِّ صلى الله عليه وسلم أَنَّ النَّبِيَّ صلى الله عليه وسلم كَانَ إِذَا اغْتَسَلَ مِنَ الْجَنَابَةِ بَدَأَ فَغَسَلَ يَدَيْهِ، ثُمَّ يَتَوَضَّأُ كَمَا يَتَوَضَّأُ لِلصَّلاَةِ، ثُمَّ يُدْخِلُ أَصَابِعَهُ فِي الْمَاءِ، فَيُخَلِّلُ بِهَا أُصُولَ شَعَرِهِ ثُمَّ يَصُبُّ عَلَى رَأْسِهِ ثَلاَثَ غُرَفٍ بِيَدَيْهِ، ثُمَّ يُفِيضُ الْمَاءَ عَلَى جِلْدِهِ كُلِّهِ.
Narrated Maimuna bint Al-Harith: I placed water for the bath of Allah's Messenger (ﷺ) and put a screen. He poured water over his hands, and washed them once or twice. (The sub-narrator added that he did not remember if she had said thrice or not). Then he poured water with his right hand over his left one and washed his private parts. He rubbed his hand over the earth or the wall and washed it. He rinsed his mouth and washed his nose by putting water in it and blowing it out. He washed his face, forearms and head. He poured water over his body and then withdrew from that place and washed his feet. I presented him a piece of cloth (towel) and he pointed with his hand (that he does not want it) and did not take it.
حَدَّثَنَا مُوسَى بْنُ إِسْمَاعِيلَ، قَالَ حَدَّثَنَا أَبُو عَوَانَةَ، حَدَّثَنَا الأَعْمَشُ، عَنْ سَالِمِ بْنِ أَبِي الْجَعْدِ، عَنْ كُرَيْبٍ، مَوْلَى ابْنِ عَبَّاسٍ عَنِ ابْنِ عَبَّاسٍ، عَنْ مَيْمُونَةَ بِنْتِ الْحَارِثِ، قَالَتْ وَضَعْتُ لِرَسُولِ اللَّهِ صلى الله عليه وسلم غُسْلاً وَسَتَرْتُهُ، فَصَبَّ عَلَى يَدِهِ، فَغَسَلَهَا مَرَّةً أَوْ مَرَّتَيْنِ ـ قَالَ سُلَيْمَانُ لاَ أَدْرِي أَذَكَرَ الثَّالِثَةَ أَمْ لاَ ـ ثُمَّ أَفْرَغَ بِيَمِينِهِ عَلَى شِمَالِهِ، فَغَسَلَ فَرْجَهُ، ثُمَّ دَلَكَ يَدَهُ بِالأَرْضِ أَوْ بِالْحَائِطِ، ثُمَّ تَمَضْمَضَ وَاسْتَنْشَقَ، وَغَسَلَ وَجْهَهُ وَيَدَيْهِ، وَغَسَلَ رَأْسَهُ، ثُمَّ صَبَّ عَلَى جَسَدِهِ، ثُمَّ تَنَحَّى فَغَسَلَ قَدَمَيْهِ، فَنَاوَلْتُهُ خِرْقَةً، فَقَالَ بِيَدِهِ هَكَذَا، وَلَمْ يُرِدْهَا.
Finally, it’s advisable to read the Quran in full to develop better understanding about Islam and about being a Muslim. Also, the collection of Hadiths, sayings, of prophet Mohamed peace be upon such as Sahih Bukhari ( https://sunnah.com/bukhari) offers further guidance to be followed.
41:13 Fussilat
فَإِنْ أَعْرَضُوا فَقُلْ أَنْذَرْتُكُمْ صَاعِقَةً مِثْلَ صَاعِقَةِ عَادٍ وَثَمُودَ
But if they turn away, then say, "I have warned you of a thunderbolt like the thunderbolt [that struck] 'Aad and Thamud.
41:14 Fussilat
إِذْ جَاءَتْهُمُ الرُّسُلُ مِنْ بَيْنِ أَيْدِيهِمْ وَمِنْ خَلْفِهِمْ أَلَّا تَعْبُدُوا إِلَّا اللَّهَ ۖ قَالُوا لَوْ شَاءَ رَبُّنَا لَأَنْزَلَ مَلَائِكَةً فَإِنَّا بِمَا أُرْسِلْتُمْ بِهِ كَافِرُونَ
[That occurred] when the messengers had come to them before them and after them, [saying], "Worship not except Allah." They said, "If our Lord had willed, He would have sent down the angels, so indeed we, in that with which you have been sent, are disbelievers."
41:15 Fussilat
فَأَمَّا عَادٌ فَاسْتَكْبَرُوا فِي الْأَرْضِ بِغَيْرِ الْحَقِّ وَقَالُوا مَنْ أَشَدُّ مِنَّا قُوَّةً ۖ أَوَلَمْ يَرَوْا أَنَّ اللَّهَ الَّذِي خَلَقَهُمْ هُوَ أَشَدُّ مِنْهُمْ قُوَّةً ۖ وَكَانُوا بِآيَاتِنَا يَجْحَدُونَ
As for 'Aad, they were arrogant upon the earth without right and said, "Who is greater than us in strength?" Did they not consider that Allah who created them was greater than them in strength? But they were rejecting Our signs.
41:16 Fussilat
فَأَرْسَلْنَا عَلَيْهِمْ رِيحًا صَرْصَرًا فِي أَيَّامٍ نَحِسَاتٍ لِنُذِيقَهُمْ عَذَابَ الْخِزْيِ فِي الْحَيَاةِ الدُّنْيَا ۖ وَلَعَذَابُ الْآخِرَةِ أَخْزَىٰ ۖ وَهُمْ لَا يُنْصَرُونَ
So We sent upon them a screaming wind during days of misfortune to make them taste the punishment of disgrace in the worldly life; but the punishment of the Hereafter is more disgracing, and they will not be helped.
41:17 Fussilat
وَأَمَّا ثَمُودُ فَهَدَيْنَاهُمْ فَاسْتَحَبُّوا الْعَمَىٰ عَلَى الْهُدَىٰ فَأَخَذَتْهُمْ صَاعِقَةُ الْعَذَابِ الْهُونِ بِمَا كَانُوا يَكْسِبُونَ
And as for Thamud, We guided them, but they preferred blindness over guidance, so the thunderbolt of humiliating punishment seized them for what they used to earn.
41:18 Fussilat
وَنَجَّيْنَا الَّذِينَ آمَنُوا وَكَانُوا يَتَّقُونَ
And We saved those who believed and used to fear Allah.
41:19 Fussilat
وَيَوْمَ يُحْشَرُ أَعْدَاءُ اللَّهِ إِلَى النَّارِ فَهُمْ يُوزَعُونَ
And [mention, O Muhammad], the Day when the enemies of Allah will be gathered to the Fire while they are [driven] assembled in rows,
41:20 Fussilat
حَتَّىٰ إِذَا مَا جَاءُوهَا شَهِدَ عَلَيْهِمْ سَمْعُهُمْ وَأَبْصَارُهُمْ وَجُلُودُهُمْ بِمَا كَانُوا يَعْمَلُونَ
Until, when they reach it, their hearing and their eyes and their skins will testify against them of what they used to do.
41:21 Fussilat
وَقَالُوا لِجُلُودِهِمْ لِمَ شَهِدْتُمْ عَلَيْنَا ۖ قَالُوا أَنْطَقَنَا اللَّهُ الَّذِي أَنْطَقَ كُلَّ شَيْءٍ وَهُوَ خَلَقَكُمْ أَوَّلَ مَرَّةٍ وَإِلَيْهِ تُرْجَعُونَ
And they will say to their skins, "Why have you testified against us?" They will say, "We were made to speak by Allah, who has made everything speak; and He created you the first time, and to Him you are returned.
41:22 Fussilat
وَمَا كُنْتُمْ تَسْتَتِرُونَ أَنْ يَشْهَدَ عَلَيْكُمْ سَمْعُكُمْ وَلَا أَبْصَارُكُمْ وَلَا جُلُودُكُمْ وَلَٰكِنْ ظَنَنْتُمْ أَنَّ اللَّهَ لَا يَعْلَمُ كَثِيرًا مِمَّا تَعْمَلُونَ
And you were not covering yourselves, lest your hearing testify against you or your sight or your skins, but you assumed that Allah does not know much of what you do.
41:23 Fussilat
وَذَٰلِكُمْ ظَنُّكُمُ الَّذِي ظَنَنْتُمْ بِرَبِّكُمْ أَرْدَاكُمْ فَأَصْبَحْتُمْ مِنَ الْخَاسِرِينَ
And that was your assumption which you assumed about your Lord. It has brought you to ruin, and you have become among the losers."
41:24 Fussilat
فَإِنْ يَصْبِرُوا فَالنَّارُ مَثْوًى لَهُمْ ۖ وَإِنْ يَسْتَعْتِبُوا فَمَا هُمْ مِنَ الْمُعْتَبِينَ
So [even] if they are patient, the Fire is a residence for them; and if they ask to appease [Allah], they will not be of those who are allowed to appease.
41:25 Fussilat
۞ وَقَيَّضْنَا لَهُمْ قُرَنَاءَ فَزَيَّنُوا لَهُمْ مَا بَيْنَ أَيْدِيهِمْ وَمَا خَلْفَهُمْ وَحَقَّ عَلَيْهِمُ الْقَوْلُ فِي أُمَمٍ قَدْ خَلَتْ مِنْ قَبْلِهِمْ مِنَ الْجِنِّ وَالْإِنْسِ ۖ إِنَّهُمْ كَانُوا خَاسِرِينَ
And We appointed for them companions who made attractive to them what was before them and what was behind them [of sin], and the word has come into effect upon them among nations which had passed on before them of jinn and men. Indeed, they [all] were losers.
41:26 Fussilat
وَقَالَ الَّذِينَ كَفَرُوا لَا تَسْمَعُوا لِهَٰذَا الْقُرْآنِ وَالْغَوْا فِيهِ لَعَلَّكُمْ تَغْلِبُونَ
And those who disbelieve say, "Do not listen to this Qur'an and speak noisily during [the recitation of] it that perhaps you will overcome."
41:27 Fussilat
فَلَنُذِيقَنَّ الَّذِينَ كَفَرُوا عَذَابًا شَدِيدًا وَلَنَجْزِيَنَّهُمْ أَسْوَأَ الَّذِي كَانُوا يَعْمَلُونَ
But We will surely cause those who disbelieve to taste a severe punishment, and We will surely recompense them for the worst of what they had been doing.
41:28 Fussilat
ذَٰلِكَ جَزَاءُ أَعْدَاءِ اللَّهِ النَّارُ ۖ لَهُمْ فِيهَا دَارُ الْخُلْدِ ۖ جَزَاءً بِمَا كَانُوا بِآيَاتِنَا يَجْحَدُونَ
That is the recompense of the enemies of Allah - the Fire. For them therein is the home of eternity as recompense for what they, of Our verses, were rejecting.
41:29 Fussilat
وَقَالَ الَّذِينَ كَفَرُوا رَبَّنَا أَرِنَا اللَّذَيْنِ أَضَلَّانَا مِنَ الْجِنِّ وَالْإِنْسِ نَجْعَلْهُمَا تَحْتَ أَقْدَامِنَا لِيَكُونَا مِنَ الْأَسْفَلِينَ
And those who disbelieved will [then] say, "Our Lord, show us those who misled us of the jinn and men [so] we may put them under our feet that they will be among the lowest."
41:30 Fussilat
إِنَّ الَّذِينَ قَالُوا رَبُّنَا اللَّهُ ثُمَّ اسْتَقَامُوا تَتَنَزَّلُ عَلَيْهِمُ الْمَلَائِكَةُ أَلَّا تَخَافُوا وَلَا تَحْزَنُوا وَأَبْشِرُوا بِالْجَنَّةِ الَّتِي كُنْتُمْ تُوعَدُونَ
Indeed, those who have said, "Our Lord is Allah " and then remained on a right course - the angels will descend upon them, [saying], "Do not fear and do not grieve but receive good tidings of Paradise, which you were promised.
41:31 Fussilat
نَحْنُ أَوْلِيَاؤُكُمْ فِي الْحَيَاةِ الدُّنْيَا وَفِي الْآخِرَةِ ۖ وَلَكُمْ فِيهَا مَا تَشْتَهِي أَنْفُسُكُمْ وَلَكُمْ فِيهَا مَا تَدَّعُونَ
We [angels] were your allies in worldly life and [are so] in the Hereafter. And you will have therein whatever your souls desire, and you will have therein whatever you request [or wish]
41:32 Fussilat
نُزُلًا مِنْ غَفُورٍ رَحِيمٍ
As accommodation from a [Lord who is] Forgiving and Merciful."
41:33 Fussilat
وَمَنْ أَحْسَنُ قَوْلًا مِمَّنْ دَعَا إِلَى اللَّهِ وَعَمِلَ صَالِحًا وَقَالَ إِنَّنِي مِنَ الْمُسْلِمِينَ
And who is better in speech than one who invites to Allah and does righteousness and says, "Indeed, I am of the Muslims."
41:34 Fussilat
وَلَا تَسْتَوِي الْحَسَنَةُ وَلَا السَّيِّئَةُ ۚ ادْفَعْ بِالَّتِي هِيَ أَحْسَنُ فَإِذَا الَّذِي بَيْنَكَ وَبَيْنَهُ عَدَاوَةٌ كَأَنَّهُ وَلِيٌّ حَمِيمٌ
And not equal are the good deed and the bad. Repel [evil] by that [deed] which is better; and thereupon the one whom between you and him is enmity [will become] as though he was a devoted friend.
41:35 Fussilat
وَمَا يُلَقَّاهَا إِلَّا الَّذِينَ صَبَرُوا وَمَا يُلَقَّاهَا إِلَّا ذُو حَظٍّ عَظِيمٍ
But none is granted it except those who are patient, and none is granted it except one having a great portion [of good].
41:36 Fussilat
وَإِمَّا يَنْزَغَنَّكَ مِنَ الشَّيْطَانِ نَزْغٌ فَاسْتَعِذْ بِاللَّهِ ۖ إِنَّهُ هُوَ السَّمِيعُ الْعَلِيمُ
And if there comes to you from Satan an evil suggestion, then seek refuge in Allah. Indeed, He is the Hearing, the Knowing.
41:37 Fussilat
وَمِنْ آيَاتِهِ اللَّيْلُ وَالنَّهَارُ وَالشَّمْسُ وَالْقَمَرُ ۚ لَا تَسْجُدُوا لِلشَّمْسِ وَلَا لِلْقَمَرِ وَاسْجُدُوا لِلَّهِ الَّذِي خَلَقَهُنَّ إِنْ كُنْتُمْ إِيَّاهُ تَعْبُدُونَ
And of His signs are the night and day and the sun and moon. Do not prostrate to the sun or to the moon, but prostate to Allah, who created them, if it should be Him that you worship.
41:38 Fussilat
فَإِنِ اسْتَكْبَرُوا فَالَّذِينَ عِنْدَ رَبِّكَ يُسَبِّحُونَ لَهُ بِاللَّيْلِ وَالنَّهَارِ وَهُمْ لَا يَسْأَمُونَ ۩
But if they are arrogant - then those who are near your Lord exalt Him by night and by day, and they do not become weary.
41:39 Fussilat
وَمِنْ آيَاتِهِ أَنَّكَ تَرَى الْأَرْضَ خَاشِعَةً فَإِذَا أَنْزَلْنَا عَلَيْهَا الْمَاءَ اهْتَزَّتْ وَرَبَتْ ۚ إِنَّ الَّذِي أَحْيَاهَا لَمُحْيِي الْمَوْتَىٰ ۚ إِنَّهُ عَلَىٰ كُلِّ شَيْءٍ قَدِيرٌ
And of His signs is that you see the earth stilled, but when We send down upon it rain, it shakes and grows. Indeed, He who has given it life is the Giver of Life to the dead. Indeed, He is over all things competent.
41:40 Fussilat
إِنَّ الَّذِينَ يُلْحِدُونَ فِي آيَاتِنَا لَا يَخْفَوْنَ عَلَيْنَا ۗ أَفَمَنْ يُلْقَىٰ فِي النَّارِ خَيْرٌ أَمْ مَنْ يَأْتِي آمِنًا يَوْمَ الْقِيَامَةِ ۚ اعْمَلُوا مَا شِئْتُمْ ۖ إِنَّهُ بِمَا تَعْمَلُونَ بَصِيرٌ
Indeed, those who inject deviation into Our verses are not concealed from Us. So, is he who is cast into the Fire better or he who comes secure on the Day of Resurrection? Do whatever you will; indeed, He (God, Allah) is Seeing what you do.
-
 @ 592295cf:413a0db9
2025-04-05 07:26:23
@ 592295cf:413a0db9
2025-04-05 07:26:23[Edit] I tried to get the slides and an audio file, from Constant's talk at NostRiga, about 8 months ago
1.
Nostr's adoption thesis
The less you define, the more you imply
by Wouter Constant
2.
Dutch Bitcoiner
AntiHashedPodcast
Writing Book about nostr
00:40
3.
What this presentation about
A protocols design includes initself a thesis
on protocol adoption, due to underlying assumptions
1:17
4.
Examples
Governments/Academic: Pubhubs (Matrix)
Bussiness: Bluesky
Foss: Nostr
1:58
5.
What constitutes minimal viability?
Pubhubs (Matrix): make is "safe" for user
Bluesky: liability and monetization
Foss: Simpel for developer
4:03
6.
The Point of Nostr
Capture network effects through interoperability
4:43
7.
Three assumptions
The direction is workable
Method is workable
Motivation and means are sufficient
5:27
8.
Assumption 1
The asymmetric cryptography paradigm is a good idea
6:16
9.
Nostr is a exponent of the key-pair paradigm.
And Basicly just that.
6.52
10.
Keys suck
Protect a secret that you are supposed use all the time.
7:37
11.
Assumption two
The unaddressed things will be figured out within a 'meta-design consensus'
8:11
12.
Nostr's base protocol is not minimally viable for anything, except own development.
8:25
13.
Complexity leads to capture;
i.e. free and open in the name,
controlled in pratice
9:54
14.
Meta-design consensus
Buildings things 'note centric' mantains interoperability.
11:51
15.
Assumption three
the nightmare is scary;
the cream is appealing.
12:41
16.
Get it minimally viable,
for whatever target,
such that it is not a waste of time.
13:23
17.
Summarize
We are in a nightmare.
Assume key/signature are the way out.
Assume we can Maintain an open stardand while manifesting the dream.
Assume we are motivated enought to bootstrap this to adulthood.
14:01
18.
We want this,
we can do this,
because we have to.
14:12
Thank you for contribuiting
[Edit] Note for audio presentation
nostr:nevent1qvzqqqqqqypzqkfzjh8jkzd8l9247sadku6vhm52snhgjtknlyeku6sfkeqn5rdeqyf8wumn8ghj7mn0wd68ytnvw5hxkef0qyg8wumn8ghj7mn0wd68ytnddakj7qpqqqq6fdnhvp95gqf4k3vxmljh87uvjezpepyt222jl2267q857uwqz7gcke
-
 @ b04082ac:29b5c55b
2025-04-22 15:57:28
@ b04082ac:29b5c55b
2025-04-22 15:57:28Africa has long grappled with the “resource curse,” a paradox where nations rich in natural resources face economic stagnation, political instability, and reliance on foreign powers. The reason isn’t hard to pinpoint. For centuries, foreign entities have extracted immense wealth from African soil such as gold, oil, cobalt, and more, leaving behind weak institutions, crippling debt, and minimal infrastructure. Instead of fueling local growth and uplifting communities, Africa’s resources have powered the industrial and digital revolutions of others.
Now, this extractive pattern is resurfacing in new ways. Recent headlines paint a clear picture:
-
Bill Gates and Jeff Bezos plan to invest $537 million in Africa to mine rare metals.
-
A ‘terrifying’ crackdown on mining companies in Africa’s coup belt.
-
Blackwater founder and Trump ally strikes mineral security deal with Congo.
-
Biden’s last dash to Africa highlights the power of minerals.
As the world scrambles to secure minerals vital for green energy and artificial intelligence, Africa stands at a crossroads. It can remain a supplier of cheap raw materials or seize this moment to shape its economic destiny.
1. Diversifying Beyond Minerals
The global race for Africa’s resources centers on critical minerals like cobalt in the Congo, rare earths in Zambia, and nickel in Tanzania. Superpowers are jostling for control, but leaning too heavily on mineral exports is fraught with risks. Prices fluctuate wildly, extraction demands massive capital, profits often vanish overseas, and overreliance can fuel political instability by deepening inequality and sparking conflicts over resource control.
To truly escape the boom-and-bust cycles of commodity markets, countries must find alternative ways to monetize their natural advantages, particularly in areas that the rest of the world tends to overlook.
One promising avenue is to tap into the continent’s vast renewable energy sources such as hydro, solar, and geothermal, and convert them into something transformative: Bitcoin.
Bitcoin mining involves validating transactions and securing the Bitcoin network in exchange for new bitcoins and fees. At its heart, it’s an energy market. Wherever there’s surplus or stranded energy, mining can thrive. Africa’s renewable energy potential is enormous and largely untapped. Rather than waiting for foreign companies to swoop in, African governments could monetize their energy directly by mining Bitcoin themselves.
2. Bitcoin Mining for Monetary Independence
Many African nations are burdened by debt, much of it in foreign currencies like the U.S. dollar. Servicing these loans drains public funds and forces governments to prioritize external creditors over local needs.
Bitcoin mining offers a way to build reserves in a neutral, censorship-resistant asset. Unlike foreign aid or currencies, Bitcoin isn’t tied to political strings or inflationary policies of other nations. It’s a step toward financial self-reliance.
In the long run, Bitcoin’s scarcity could drive its value higher, helping countries reduce their reliance on dollar-dominated systems. Looking further ahead, African nations that participate meaningfully in the Bitcoin economy may also gain influence over blockspace, the limited space where Bitcoin transactions are recorded.
3. Stabilizing Energy Grids with Mining
In much of Africa, electricity is costly, unreliable, or nonexistent. Yet, the problem often stems from underused infrastructure. Power producers struggle to recover costs due to inconsistent demand, and grids falter when supply and demand don’t align.
Bitcoin mining can act as an economic “shock absorber” for energy providers. It creates a flexible buyer that adjusts to grid demands, soaking up excess power or scaling back when needed. By placing miners near energy sources, especially in remote areas, utilities can earn steady revenue to fund broader electrification.
Take Gridless in rural Kenya. By mining Bitcoin off-grid with small hydro units, they’ve stabilized local power, supported rural internet access, and lowered costs for nearby residents. This model works. To make a more meaningful impact, however, it needs national-scale adoption supported by clear government strategy.
4. Foreign Miners Are Already Here
The shift is already happening. In Ethiopia, foreign Bitcoin mining firms are signing deals to tap the country’s hydroelectric surplus. Similar moves are underway across the continent. This isn’t a distant possibility; it is already happening.
Miners chase the cheapest energy, and Africa boasts some of the world’s most affordable renewables. Mining will happen with or without local policies. The critical question is whether the benefits will stay in Africa or flow abroad, repeating history’s mistakes.
Foreign companies bring expertise and capital, but if they dominate, African nations risk becoming mere hosts to another extractive industry. Governments must act swiftly by launching national Bitcoin mining initiatives, forging public-private partnerships, and securing ownership of infrastructure to keep the value local.
Conclusion
Africa is at a turning point. The world craves its minerals, its energy, and increasingly, its role in shaping the future. But African nations can’t afford to sit on the sidelines. The next revolution must be led, not endured.
Bitcoin mining is not a silver bullet. It is a tool that, if used wisely, could help transform energy into economic power, build digital infrastructure, and break the cycle of debt and dependence.
Bitcoin miners are already arriving. The real question is whether African nations will take the lead and ensure that this industry builds lasting value at home, rather than repeating the patterns of the past.
-
-
 @ 91bea5cd:1df4451c
2025-02-04 05:24:47
@ 91bea5cd:1df4451c
2025-02-04 05:24:47Novia é uma ferramenta inovadora que facilita o arquivamento de vídeos e sua integração com a rede NOSTR (Notes and Other Stuff Transmitted over Relay). Funcionando como uma ponte entre ferramentas de arquivamento de vídeo tradicionais e a plataforma descentralizada, Novia oferece uma solução autônoma para a preservação e compartilhamento de conteúdo audiovisual.
Arquitetura e Funcionamento
A arquitetura de Novia é dividida em duas partes principais:
-
Frontend: Atua como a interface do usuário, responsável por solicitar o arquivamento de vídeos. Essas solicitações são encaminhadas para o backend.
-
Backend: Processa as solicitações de arquivamento, baixando o vídeo, suas descrições e a imagem de capa associada. Este componente é conectado a um ou mais relays NOSTR, permitindo a indexação e descoberta do conteúdo arquivado.
O processo de arquivamento é automatizado: após o download, o vídeo fica disponível no frontend para que o usuário possa solicitar o upload para um servidor Blossom de sua escolha.
Como Utilizar Novia
-
Acesso: Navegue até https://npub126uz2g6ft45qs0m0rnvtvtp7glcfd23pemrzz0wnt8r5vlhr9ufqnsmvg8.nsite.lol.
-
Login: Utilize uma extensão de navegador compatível com NOSTR para autenticar-se.
-
Execução via Docker: A forma mais simples de executar o backend é através de um container Docker. Execute o seguinte comando:
bash docker run -it --rm -p 9090:9090 -v ./nostr/data:/data --add-host=host.docker.internal:host-gateway teamnovia/noviaEste comando cria um container, mapeia a porta 9090 para o host e monta o diretório
./nostr/datapara persistir os dados.
Configuração Avançada
Novia oferece amplas opções de configuração através de um arquivo
yaml. Abaixo, um exemplo comentado:```yaml mediaStores: - id: media type: local path: /data/media watch: true
database: /data/novia.db
download: enabled: true ytdlpPath: yt-dlp ytdlpCookies: ./cookies.txt tempPath: /tmp targetStoreId: media secret: false
publish: enabled: true key: nsec thumbnailUpload: - https://nostr.download videoUpload: - url: https://nostr.download maxUploadSizeMB: 300 cleanUpMaxAgeDays: 5 cleanUpKeepSizeUnderMB: 2 - url: https://files.v0l.io maxUploadSizeMB: 300 cleanUpMaxAgeDays: 5 cleanUpKeepSizeUnderMB: 2 - url: https://nosto.re maxUploadSizeMB: 300 cleanUpMaxAgeDays: 5 cleanUpKeepSizeUnderMB: 2 - url: https://blossom.primal.net maxUploadSizeMB: 300 cleanUpMaxAgeDays: 5 cleanUpKeepSizeUnderMB: 2
relays: - ws://host.docker.internal:4869 - wss://bostr.bitcointxoko.com secret: false autoUpload: enabled: true maxVideoSizeMB: 100
fetch: enabled: false fetchVideoLimitMB: 10 relays: - match: - nostr - bitcoin
server: port: 9090 enabled: true ```
Explicação das Configurações:
mediaStores: Define onde os arquivos de mídia serão armazenados (localmente, neste exemplo).database: Especifica o local do banco de dados.download: Controla as configurações de download de vídeos, incluindo o caminho para oyt-dlpe um arquivo de cookies para autenticação.publish: Configura a publicação de vídeos e thumbnails no NOSTR, incluindo a chave privada (nsec), servidores de upload e relays. Atenção: Mantenha sua chave privada em segredo.fetch: Permite buscar eventos de vídeo de relays NOSTR para arquivamento.server: Define as configurações do servidor web interno de Novia.
Conclusão
Novia surge como uma ferramenta promissora para o arquivamento e a integração de vídeos com o ecossistema NOSTR. Sua arquitetura modular, combinada com opções de configuração flexíveis, a tornam uma solução poderosa para usuários que buscam preservar e compartilhar conteúdo audiovisual de forma descentralizada e resistente à censura. A utilização de Docker simplifica a implantação e o gerenciamento da ferramenta. Para obter mais informações e explorar o código-fonte, visite o repositório do projeto no GitHub: https://github.com/teamnovia/novia.
-
-
 @ 57d1a264:69f1fee1
2025-04-05 06:58:25
@ 57d1a264:69f1fee1
2025-04-05 06:58:25Summary We are looking for a Visual Designer with a strong focus on illustration and animation to help shape and refine our brand’s visual identity. You will create compelling assets for digital and print, including marketing materials, social media content, website illustrations, and motion graphics. Working closely with our marketing and product teams, you will play a key role in developing a consistent and recognizable visual style through thoughtful use of illustration, color, patterns, and animation. This role requires creativity, adaptability, and the ability to deliver high-quality work in a fast-paced, remote environment.
Responsibilities - Create high-quality, iconic illustrations, branding assets, and motion graphics that contribute to and refine our visual identity. - Develop digital assets for marketing, social media, website, and app. - Work within brand guidelines while exploring ways to evolve and strengthen our visual style.
Requirements - 2+ years of experience in graphic design, with a strong focus on illustration. - Ability to help define and develop a cohesive visual style for the brand. - Proficiency in Adobe products. - Experience with Figma is a plus. - Strong organizational skills—your layers and files should be neatly labeled. - Clear communication and collaboration skills to work effectively with the team. - Located in LATAM
Please attach a link to your portfolio to showcase your work when applying.
originally posted at https://stacker.news/items/935007
-
 @ 9a859fbc:8a9270f3
2025-04-22 15:45:55
@ 9a859fbc:8a9270f3
2025-04-22 15:45:55A story of art and inspiration
This image was generated by AI
That is...
I am artificial. I was created by two other humans (hi mum and dad 👋)
I am intelligent. I can perceive the world, experience it, learn to understand cause & effect, and make decisions.
To go perhaps deeper, cells, DNA and life itself are artifices of the fabric of reality.
I sat, in a pub in Bristol, a place where I rarely frequent. I sat with one housemate, who I rarely spent time with. I met his friends that day, only once, never we met again.
I got chatting with a lady there. I had some paper and pencils with me. My intention, for a couple of weeks, was to come up with a symbol to represent Deep Sea Frequencies, at that time still known as Psychedelic Jelly. We were a new collaboration.
She and I got chatting about art. About symbolic representation of concepts, feelings, ideas. We chatted about flow, about how there are different types of flow, different elemental conditions of flow. I doodled some shapes, and we noticed how fire, water and air all look similar due to their fluid natures. So we considered how to differentiate, distinguish them from one another.
I doodled some more, and we came up with swooshes, curls, crests and bubbles. These seemed to be distinguishing enough such that they were no longer reminiscent of fire or air. I doodled fire and air too, just in case, just to check.
Then we chatted about symmetry types, reflective, axes, rotational. About geometry, geometric containers. We both enjoy triangles and hexagons. (It's always hexagons!)
I doodled some more shapes and put them in hexagonal shapes. Then I tried bending them into triangular forms instead, and overlaid two triangles.
Each triangle looked like a triskelion. Perfect.
Overlaid, they looked just like the flow of water, coming up, spiralling down.
The logo was born in this moment, in this serendipitous meeting, in this unlikely chat with a total stranger. We met for the first time that day, and I'm not sure if we ever met again. This interaction was, is, precious, and it led to a particular creation that is now a core part of my life and is a highlight for many people around the UK and the world, as we put on events and released musicians' music.
This is inspiration. This is expression. This is flow, through the fluid nature of the cosmos.
This is what you miss out on when you talk into your AI LLM black hole prompt.
This is what you steal from when you demand your AI LLM to generate you something according to your whim.
Art and expression is the very foundation of human community. Join in! Try new things! Learn from each other! Bring us all closer together by interacting and creating through shared ideas, shared visions, shared wisdom!
After that, I drew it up cleanly, geometrically.
I photographed it like scanning it, carefully aligning the camera because I didn't have a scanner.
I redrew it more than twice.
I digitised it, colourised it, split it into two layers so I could apply colour & lighting effects to it.
I painstakingly traced the photograph into a vector format, to enlarge it and use it for various media.
I even more painstakingly (do we have a more extreme adverb??) divided all the vector shapes into new objects so that the layers became "real". And cleaned up the vector nodes, shaping them to my imagination.
The vector form is used all over our record label & events branding.
And then I imported the vector form into Blender, a 3D rendering application, free and open source.
I learnt Blender, day by day developing my understanding and my skills. Day by day my GPU crashing on raytracing and cutting the laptop's power out!
And finally, I learnt to make some simple renders that look like being underwater, like surreal glassy objects floating in the deep. I even learnt to animate it, although I haven't released that into the wild.
I imagined all of this stuff, and then I spent months over years developing my skills in my spare time in order to bring these imaginations to life.
You can do the same.
You have to sacrifice things.
Sacrifice your time.
Sacrifice your energy.
Sacrifice your distractions and enter yourself into the learning process and the creative process.
To you, amazing lady who helped me draw this symbol from the fabric of the Realm of Forms, thank you! I'm sorry that I don't recall your name, although actually I think I do remember but I would be embarrassed if I tagged the wrong person. Please reach out if you recognise this story! It was about 7, maybe 8 years ago, in the painted pub in St. Werburgh's.
-
 @ 57d1a264:69f1fee1
2025-04-05 06:47:55
@ 57d1a264:69f1fee1
2025-04-05 06:47:55Location: Remote (Austria) Area: Graphics and communication design Pay: 37,500 € to 50,000 € / year
Hi! We are @21bitcoinApp - a Bitcoin-Only Investment app that aims to accelerate the transition to an economy driven by Bitcoin.
👋 About the role As a passionate graphic designer, you support our marketing team in creating graphics and designs for print documents, online advertising material and our website. You also support us in the area of social media and content management and can also contribute your skills in these subject areas.
tasks - Design and implementation of creative and congruent designs for social media channels, websites, templates and marketing materials - Creation of individual content (posts, stories, banners, ads) for social media - Planning and development of campaigns to strengthen the brand presence - Further development of the existing corporate design support in the area of content management (website, blog)
qualification - Completed training or studies in graphic design - At least 2 years of experience in graphic design, preferably with experience in the areas of social media and content management - Safe use of design tools such as Figma, Adobe Creative Suite - Experience in creating social media content and maintaining channels - Creativity, good communication skills and team spirit - Very good knowledge of German and English - Knowledge of Bitcoin is desirable
Benefits - Offsites with the team in exciting places - Flexible working hours in a company that relies on remote work - Help shape the future - to make the world a better place by helping to speed up Bitcoin's adaptation - Buy Bitcoin without fees! 21 Premium! - Gross annual salary & potential share options for outstanding performance / bonus payments
📝 Interview process
How do I apply? Please send us an email and add some information about you, your resume, examples of previous projects and a few key points about why you are interested in participating in 21bitcoin and what you expect.
By the way: CVs are important but don't forget to include your favorite Bitcoin meme in the application!
⁇ 京 Resume Review Portfolio of Work: Add a link to your portfolio / previous work or resume that we can review (LinkedIn, Github, Twitter, ...)
📞 Exploratory call We discuss what appeals to you about this role and ask you a few questions about your previous experiences
👬 On-Site Deep Dive During the deep dive session, we use a case study or extensive interview to discuss the specific skills required for the role.
👍 Time for a decision!
originally posted at https://stacker.news/items/935004
-
 @ df173277:4ec96708
2025-01-28 17:49:54
@ df173277:4ec96708
2025-01-28 17:49:54Maple is an AI chat tool that allows you to have private conversations with a general-purpose AI assistant. Chats are synced automatically between devices so you can pick up where you left off.\ Start chatting for free.
We are excited to announce that Maple AI, our groundbreaking end-to-end encrypted AI chat app built on OpenSecret, is now publicly available. After months of beta testing, we are thrilled to bring this innovative technology to the world.
 Maple is an AI chat tool that allows you to have private conversations with a general-purpose AI assistant. It can boost your productivity on work tasks such as writing documentation, creating presentations, and drafting emails. You can also use it for personal items like brainstorming ideas, sorting out life's challenges, and tutoring you on difficult coursework. All your chats are synced automatically in a secure way, so you can start on one device and pick up where you left off on another.
Maple is an AI chat tool that allows you to have private conversations with a general-purpose AI assistant. It can boost your productivity on work tasks such as writing documentation, creating presentations, and drafting emails. You can also use it for personal items like brainstorming ideas, sorting out life's challenges, and tutoring you on difficult coursework. All your chats are synced automatically in a secure way, so you can start on one device and pick up where you left off on another.Why Secure and Private AI?
In today's digital landscape, it is increasingly evident that security and privacy are essential for individuals and organizations alike. Unfortunately, the current state of AI tools falls short. A staggering 48% of organizations enter non-public company information into AI apps, according to a recent report by Cisco. This practice poses significant risks to company security and intellectual property.
Another concern is for journalists, who often work with sensitive information in hostile environments. Journalists need verification that their information remains confidential and protected when researching topics and communicating with sources in various languages. They are left to use underpowered local AI or input their data into potentially compromised cloud services.
At OpenSecret, we believe it is possible to have both the benefits of AI and the assurance of security and privacy. That's why we created Maple, an app that combines AI productivity with the protection of end-to-end encryption. Our platform ensures that your conversations with AI remain confidential, even from us. The power of the cloud meets the privacy of local.
 #### How Does It Work?
#### How Does It Work?Our server code is open source, and we use confidential computing to provide cryptographic proof that the code running on our servers is the same as the open-source code available for review. This process allows you to verify that your conversations are handled securely and privately without relying on trust. We live by the principle of "Don't trust, verify," and we believe this approach is essential for building in the digital age. You can read a more in-depth write-up on our technology later this week on this site.
How Much Does It Cost?
We are committed to making Maple AI accessible to everyone, so we offer a range of pricing plans to suit different needs and budgets. Our Free plan allows for 10 chats per week, while our Starter plan ($5.99/month) and Pro plan ($20/month) offer more comprehensive solutions for individuals and organizations with heavier workloads. We accept credit cards and Bitcoin (10% discount), allowing you to choose your preferred payment method.
- Free: $0
- Starter: $5.99/month
- Pro: $20/month
Our goal with Maple AI is to create a product that is secure through transparency. By combining open-source code, cryptography, and confidential computing, we can create a new standard for AI conversations - one that prioritizes your security and privacy.
Maple has quickly become a daily tool of productivity for our own work and those of our beta testers. We believe it will bring value to you as well. Sign up now and start chatting privately with AI for free. Your secrets are safe in the open.
 #### Are You An App Developer?
#### Are You An App Developer?You can build an app like Maple. OpenSecret provides secure auth, private key management, encrypted data sync, private AI, and more. Our straightforward API behaves like other backends but automatically adds security and privacy. Use it to secure existing apps or brand-new projects. Protect yourself and your users from the liability of hosting personal data by checking out OpenSecret.

Enjoy private AI Chat 🤘

-
 @ 5d4b6c8d:8a1c1ee3
2025-04-22 15:37:53
@ 5d4b6c8d:8a1c1ee3
2025-04-22 15:37:53How I wish I had time for this!
https://primal.net/e/nevent1qvzqqqqqqypzqntcggz30qhq60ltqdx32zku9d46unhrkjtcv7fml7jx3dh4h94nqqsynzz85x8dcqnzxrzypec9xw6haxxjt0z0c547suty7gpa835v0vs2qusmr
originally posted at https://stacker.news/items/953418
-
 @ df173277:4ec96708
2025-01-09 17:12:08
@ df173277:4ec96708
2025-01-09 17:12:08Maple AI combines the best of both worlds – encryption and personal AI – to create a truly private AI experience. Discuss personal and company items with Maple, we can't read them even if we wanted to.\ Join the waitlist to get early access.
We are a culture of app users. Every day, we give our personal information to websites and apps, hoping they are safe. Location data, eating habits, financial details, and health information are just a few examples of what we entrust to third parties. People are now entering a new era of computing that promises next-level benefits when given even more personal data: AI.
Should we sacrifice our privacy to unlock the productivity gains of AI? Should we hope our information won't be used in ways we disagree? We believe we can have the best of both worlds – privacy and personal AI – and have built a new project called Maple AI. Chat between you and an AI with full end-to-end encryption. We believe it's a game-changer for individuals seeking private and secure conversations.
Building a Private Foundation
Maple is built on our flagship product, OpenSecret, a backend platform for app developers that turns private encryption on by default. The announcement post for OpenSecret explains our vision for an encrypted world and what the platform can do. We think both users and developers benefit when sensitive personal information is encrypted in a private vault; it's a win-win.
The Power of Encrypted AI Chat
AI chat is a personal and intimate experience. It's a place to share your thoughts, feelings, and desires without fear of judgment. The more you share with an AI chatbot, the more powerful it becomes. It can offer personalized insights, suggestions, and guidance tailored to your unique needs and perspectives. However, this intimacy requires trust, and that's where traditional AI chatbots often fall short.
Traditional AI chats are designed to collect and analyze your data, often without your explicit consent. This data is used to improve the AI's performance, but it also creates a treasure trove of sensitive information that can be mined, sold, or even exploited by malicious actors. Maple AI takes a different approach. By using end-to-end encryption, we ensure that your conversations remain private and secure, even from us.
Technical Overview
So, how does Maple AI achieve this level of privacy and security? Here are some key technical aspects:
- Private Key: Each user has a unique private key that is automatically managed for them. This key encrypts and decrypts conversations, ensuring that only the user can access their data.
- Secure Servers: Our servers are designed with security in mind. We use secure enclaves to protect sensitive data and ensure that even our own team can't access your conversations.
- Encrypted Sync: One of Maple's most significant benefits is its encrypted sync feature. Unlike traditional AI chatbots, which store conversations in local storage or on standard cloud servers, Maple syncs your chats across all your devices. The private key managed by our secure servers means you can pick up where you left off on any device without worrying about your data being compromised.
- Attestation and Open Code: We publish our enclave code publicly. Using a process called attestation, users can verify that the code running on the enclave is the same as the code audited by the public.
- Open Source LLM: Maple uses major open-source models to maximize the openness of responses. The chat box does not filter what you can talk about. This transparency ensures that our AI is trustworthy and unbiased.
Personal and Work Use
Maple is secure enough to handle your personal questions and work tasks. Because we can't see what you chat about, you are free to use AI as an assistant on sensitive company items. Use it for small tasks like writing an important email or large tasks like developing your organization's strategy. Feed it sensitive information; it's just you and AI in the room. Attestation provides cryptographic proof that your corporate secrets are safe.
Local v Cloud
Today's AI tools provide different levels of privacy. The main options are to trust a third party with your unencrypted data, hoping they don't do anything with it, or run your own AI locally on an underpowered machine. We created a third option. Maple gives you the power of cloud computing combined with the privacy and security of a machine running on your desk. It's the best of both worlds.
Why the Maple name?
Privacy isn't just a human value - it's a natural one exemplified by the Maple tree. These organisms communicate with each other through a network of underground fungal hyphae, sending messages and sharing resources in a way that's completely invisible to organisms above ground. This discreet communication system allows Maple trees to thrive in even the most challenging environments. Our goal is to provide a way for everyone to communicate with AI securely so they can thrive in any environment.
Join the Waitlist
Maple AI will launch in early 2025 with free and paid plans. We can't wait to share it with the world. Join our waitlist today to be among the first to experience the power of private AI chat.
-
 @ 57d1a264:69f1fee1
2025-04-05 06:35:58
@ 57d1a264:69f1fee1
2025-04-05 06:35:58We’re looking for a Product Designer to join our team and take the lead in enhancing the experience of our mobile app. You’ll play a key role in evolving the app’s interface and interactions, ensuring that our solutions are intuitive, efficient, and aligned with both user needs and business goals.
Key Responsibilities: - Design and improve the @Bipa app experience, focusing on usability and measurable business impact. - Apply data-driven design, making decisions based on user research, metrics, and testing. - Lead and participate in usability tests and discovery processes to validate hypotheses and continuously improve the product. - Collaborate closely with Product Managers, developers, and other stakeholders to align design with product strategy. - Create wireframes, high-fidelity prototypes, and visual interfaces for new features and app optimizations. - Monitor the performance of delivered solutions, ensuring meaningful improvements for users and the business. - Contribute to the evolution and maintenance of our design system, ensuring consistency and scalability across the app.
Qualifications: - Previous experience as a Product Designer or UX/UI Designer, with a strong focus on mobile apps. - Solid understanding of user-centered design (UCD) principles and usability heuristics. - Hands-on experience with user research methods, including usability testing, interviews, and behavior analysis. - Ability to work with both quantitative and qualitative data to guide design decisions. - Familiarity with product metrics and how design impacts business outcomes (e.g. conversion, retention, engagement). - Proficiency in design tools like Figma (or similar). - Experience working with design systems and design tokens to ensure consistency. - Comfortable working in an agile, fast-paced, and iterative environment. - Strong communication skills and the ability to advocate for design decisions backed by research and data.
Benefits: 🏥 Health Insurance 💉 Dental Plan 🍽️ Meal Allowance (CAJU card) 💻 Home Office Stipend 📈 Stock Options from Day One
originally posted at https://stacker.news/items/935003
-
 @ d1667293:388e7004
2025-04-22 14:27:15
@ d1667293:388e7004
2025-04-22 14:27:15The motivation behind my newly published book Bitcoindollar the Dawn of American Hegemony in the Digital Era was simple: to answer some of the most pressing and overlooked questions about the future of money. My analysis starts by viewing Bitcoin not in isolation, but as a paradigm shift in the evolution of money—a foundational institution that underpins both economic and societal relationships, from individuals to nations.
Rethinking the Monetary Landscape
To understand Bitcoin's potential, we need to explore the landscape it seeks to disrupt:
-
The dominance of nation-states.
-
The role of the US fiat dollar as the global reserve currency.
-
US debt as the reserve liability (pardon "asset") underpinning the fiat system.
-
The influence of the banking cartel and the distorted incentives built into the fiat monetary structure—especially in the last 55 years, since the US elegantly defaulted on its promise to convert paper dollars into gold in 1971.
Bitcoin is a direct response to these imbalances, but its adoption will depend on how and who drives the transition.
Two Paths of Bitcoin Adoption: Bottom-Up vs. Top-Down
Bitcoin’s journey can take two distinct paths:
1. Bottom-Up Adoption
This is driven by grassroots use of Bitcoin as a currency, particularly in developing nations, often alongside dollar-denominated stablecoins like USDt.
2. Top-Down Adoption
This path sees Bitcoin increasingly used as a store of value (SOV) and financial asset, especially in developed economies. It is driven by institutions, wealth managers, and financial innovation.
It's clear that top-down adoption correlates with faster price appreciation, whereas bottom-up adoption is slower, more organic—and potentially more resilient in the long run.
Why the Top-Down Path Matters
A critical but often uncomfortable truth is: elites don’t give up power easily. The fiat system is held tightly by those benefiting most from its continuation.
Pareto’s Law teaches us that no historical revolution was purely bottom-up. Real change happens when a new elite emerges to replace the old one—carrying the masses along.
The advantages of top-down adoption:
-
Speeds up the revolution.
-
Allows coexistence between Bitcoin and fiat for a transitional period, avoiding violent disruption.
-
Strengthens new power structures around Bitcoin as it becomes a more established SOV.
-
Enables the U.S. to reinvent the dollar’s role through dollar-backed stablecoins and their recycling into US TBills, maintaining global dollar demand even post-Petrodollar.
A Warning for the United States
In my book, I argue that the #Bitcoindollar system gives the U.S. a first-mover advantage—but only if it changes course.
The U.S. must shift from a militaristic, imperialist approach to a cooperative, multipolar model that welcomes both allies and adversaries into this new system.
Unfortunately, the Trump administration appears headed in the opposite direction, risking this historic opportunity. I explore this further in an upcoming article expanding on my book’s conclusions.
Store of Value vs. Currency: Which Comes First?
Some critics lament that Bitcoin isn’t widely used as a currency yet. But ask yourself:
What is the world’s most urgent need in today’s monetary environment?
A medium of exchange? Or a store of value to protect savings from corrupt governments and inflation?
We already have more or less efficient payment systems. But we lack a sound store of value with key properties such as decentralization, censorship resistance and hard coded scarcity. That’s why the market is adopting Bitcoin primarily as a SOV.
Gresham’s Law gives us the formula:
Save the hard money (Bitcoin, gold), spend the USDt, USDC, and fiat.
Looking Ahead: From Store of Value to Currency
This doesn’t mean #bitcoin won’t be used as a currency eventually. Once it’s widely adopted as a store of value—perhaps within the next 10–20 years—its volatility will decrease, more people will price goods in bitcoin, and acceptance for payments will grow.
We will get there. Just not through the path many imagined at the beginning.
Call It What It Is: A Revolutionary Monetary Transition
Rather than a disruptive revolution, think of this as a revolutionary monetary transition—a new system growing alongside the old, until one inevitably replaces the other.
-
-
 @ 57d1a264:69f1fee1
2025-04-05 06:28:16
@ 57d1a264:69f1fee1
2025-04-05 06:28:16⚡️ About Us
@AdoptingBTC is the leading Bitcoin-only conference in El Salvador. For our 5th edition, we’re looking for a passionate Video Creator intern to help showcase Bitcoin’s future as MONEY.
⚡️ The Role
Create 30 short (3-minute or less) videos highlighting global circular economies, to be featured at AB25. We’ll provide all source material, direction, and inspiration—you’ll have full creative freedom, with feedback rounds to align with the conference’s vision.
⚡️ Responsibilities
Produce 30 short videos on circular economies. Incorporate subtitles as needed. Submit videos on a deliverables basis. Participate in check-ins and communicate with the AB team and circular economy communities.
⚡️ What We Offer
Free ticket to AB25. Networking with Bitcoiners and industry leaders. Letter of recommendation and LinkedIn endorsement upon completion. Mentorship and hands-on experience with a high-profile Bitcoin project.
⚡️ Skills & Qualifications
Passion for Bitcoin and circular economies. Basic to intermediate video editing skills (no specific software required). Creative independence with feedback. Portfolio or work samples preferred.
⚡️ Time Commitment
Flexible, project-based internship with check-ins and feedback rounds.
⚡️ How to Apply
Email kiki@adoptingbitcoin.org with subject “Circular Economy Video Creator Submission -
{NAME OR NYM}.” Include a brief background, your experience, why the project resonates with you, and a portfolio (if available).originally posted at https://stacker.news/items/935001
-
 @ df173277:4ec96708
2025-01-09 17:02:52
@ df173277:4ec96708
2025-01-09 17:02:52OpenSecret is a backend for app developers that turns private encryption on by default. When sensitive data is readable only by the user, it protects both the user and the developer, creating a more free and open internet. We'll be launching in 2025. Join our waitlist to get early access.
In today's digital age, personal data is both an asset and a liability. With the rise of data breaches and cyber attacks, individuals and companies struggle to protect sensitive information. The consequences of a data breach can be devastating, resulting in financial losses, reputational damage, and compromised user trust. In 2023, the average data breach cost was $5 million, with some resulting in losses of over $1 billion.
 Meanwhile, individuals face problems related to identity theft, personal safety, and public embarrassment. Think about the apps on your phone, even the one you're using to read this. How much data have you trusted to other people, and how would it feel if that data were leaked online?
Meanwhile, individuals face problems related to identity theft, personal safety, and public embarrassment. Think about the apps on your phone, even the one you're using to read this. How much data have you trusted to other people, and how would it feel if that data were leaked online?Thankfully, some incredibly talented cypherpunks years ago gave the world cryptography. We can encrypt data, rendering it a secret between two people. So why then do we have data breaches?
Cryptography at scale is hard.
The Cloud
The cloud has revolutionized how we store and process data, but it has limitations. While cloud providers offer encryption, it mainly protects data in transit. Once data is stored in the cloud, it's often encrypted with a shared key, which can be accessed by employees, third-party vendors, or compromised by hackers.
The solution is to generate a personal encryption password for each user, make sure they write it down, and, most importantly, hope they don't lose it. If the password is lost, the data is forever unreadable. That can be overwhelming, leading to low app usage.
Private key encryption needs a UX upgrade.
Enter OpenSecret
OpenSecret is a developer platform that enables encryption by default. Our platform provides a suite of security tools for app developers, including private key management, encrypted sync, private AI, and confidential compute.
Every user has a private vault for their data, which means only they can read it. Developers are free to store less sensitive data in a shared manner because there is still a need to aggregate data across the system.

Private Key Management
Private key management is the superpower that enables personal encryption per user. When each user has a unique private key, their data can be truly private. Typically, using a private key is a challenging experience for the user because they must write down a long autogenerated number or phrase of 12-24 words. If they lose it, their data is gone.
OpenSecret uses secure enclaves to make private keys as easy as an everyday login experience that users are familiar with. Instead of managing a complicated key, the user logs in with an email address or a social media account.
The developer doesn't have to manage private keys and can focus on the app's user experience. The user doesn't have to worry about losing a private key and can jump into using your app.

Encrypted Sync
With user keys safely managed, we can synchronize user data to every device while maintaining privacy. The user does not need to do complicated things like scanning QR codes from one device to the next. Just log in and go.
The user wins because the data is available on all their devices. The developer wins because only the user can read the data, so it isn't a liability to them.
Private AI
Artificial intelligence is here and making its way into everything. The true power of AI is unleashed when it can act on personal and company data. The current options are to run your own AI locally on an underpowered machine or to trust a third party with your data, hoping they don't read it or use it for anything.
OpenSecret combines the power of cloud computing with the privacy and security of a machine running on your desk.
Check out Maple AI\ Try private AI for yourself! We built an app built with this service called Maple AI. It is an AI chat that is 100% private in a verifiable manner. Give it your innermost thoughts or embarrassing ideas; we can't judge you. We built Maple using OpenSecret, which means you have a private key that is automatically managed for you, and your chat history is synchronized to all your devices. Learn more about Maple AI - Private chat in the announcement post.

Confidential Compute
Confidential computing is a game-changer for data security. It's like the secure hardware that powers Apple Pay and Google Pay on your phone but in the cloud. Users can verify through a process called attestation that their data is handled appropriately. OpenSecret can help you run your own custom app backend code that would benefit from the security of an enclave.
It's the new version of that lock on your web browser. When you see it, you know you're secure.

But do we want our secrets to be open?
OpenSecret renders a data breach practically useless. If hackers get into the backend, they enter a virtual hallway of locked private vaults. The leaked data would be gibberish, a secret in the open that is unreadable.
On the topic of openness, OpenSecret uses the power of open source to enable trust in the service. We publish our code in the open, and, using attestation, anyone can verify that private data is being handled as expected. This openness also provides developers with a backup option to safely and securely export their data.
Don't trust, verify.
Join the Movement
We're currently building out OpenSecret, and we invite you to join us on the journey. Our platform can work with your existing stack, and you can pick and choose the features you need. If you want to build apps with encryption enabled, send us a message to get early access.
Users and companies deserve better encryption and privacy.\ Together, let's make that a reality.
-
 @ c631e267:c2b78d3e
2025-04-04 18:47:27
@ c631e267:c2b78d3e
2025-04-04 18:47:27Zwei mal drei macht vier, \ widewidewitt und drei macht neune, \ ich mach mir die Welt, \ widewide wie sie mir gefällt. \ Pippi Langstrumpf
Egal, ob Koalitionsverhandlungen oder politischer Alltag: Die Kontroversen zwischen theoretisch verschiedenen Parteien verschwinden, wenn es um den Kampf gegen politische Gegner mit Rückenwind geht. Wer den Alteingesessenen die Pfründe ernsthaft streitig machen könnte, gegen den werden nicht nur «Brandmauern» errichtet, sondern der wird notfalls auch strafrechtlich verfolgt. Doppelstandards sind dabei selbstverständlich inklusive.
In Frankreich ist diese Woche Marine Le Pen wegen der Veruntreuung von EU-Geldern von einem Gericht verurteilt worden. Als Teil der Strafe wurde sie für fünf Jahre vom passiven Wahlrecht ausgeschlossen. Obwohl das Urteil nicht rechtskräftig ist – Le Pen kann in Berufung gehen –, haben die Richter das Verbot, bei Wahlen anzutreten, mit sofortiger Wirkung verhängt. Die Vorsitzende des rechtsnationalen Rassemblement National (RN) galt als aussichtsreiche Kandidatin für die Präsidentschaftswahl 2027.
Das ist in diesem Jahr bereits der zweite gravierende Fall von Wahlbeeinflussung durch die Justiz in einem EU-Staat. In Rumänien hatte Călin Georgescu im November die erste Runde der Präsidentenwahl überraschend gewonnen. Das Ergebnis wurde später annulliert, die behauptete «russische Wahlmanipulation» konnte jedoch nicht bewiesen werden. Die Kandidatur für die Wahlwiederholung im Mai wurde Georgescu kürzlich durch das Verfassungsgericht untersagt.
Die Veruntreuung öffentlicher Gelder muss untersucht und geahndet werden, das steht außer Frage. Diese Anforderung darf nicht selektiv angewendet werden. Hingegen mussten wir in der Vergangenheit bei ungleich schwerwiegenderen Fällen von (mutmaßlichem) Missbrauch ganz andere Vorgehensweisen erleben, etwa im Fall der heutigen EZB-Chefin Christine Lagarde oder im «Pfizergate»-Skandal um die Präsidentin der EU-Kommission Ursula von der Leyen.
Wenngleich derartige Angelegenheiten formal auf einer rechtsstaatlichen Grundlage beruhen mögen, so bleibt ein bitterer Beigeschmack. Es stellt sich die Frage, ob und inwieweit die Justiz politisch instrumentalisiert wird. Dies ist umso interessanter, als die Gewaltenteilung einen essenziellen Teil jeder demokratischen Ordnung darstellt, während die Bekämpfung des politischen Gegners mit juristischen Mitteln gerade bei den am lautesten rufenden Verteidigern «unserer Demokratie» populär zu sein scheint.
Die Delegationen von CDU/CSU und SPD haben bei ihren Verhandlungen über eine Regierungskoalition genau solche Maßnahmen diskutiert. «Im Namen der Wahrheit und der Demokratie» möchte man noch härter gegen «Desinformation» vorgehen und dafür zum Beispiel den Digital Services Act der EU erweitern. Auch soll der Tatbestand der Volksverhetzung verschärft werden – und im Entzug des passiven Wahlrechts münden können. Auf europäischer Ebene würde Friedrich Merz wohl gerne Ungarn das Stimmrecht entziehen.
Der Pegel an Unzufriedenheit und Frustration wächst in großen Teilen der Bevölkerung kontinuierlich. Arroganz, Machtmissbrauch und immer abstrusere Ausreden für offensichtlich willkürliche Maßnahmen werden kaum verhindern, dass den etablierten Parteien die Unterstützung entschwindet. In Deutschland sind die Umfrageergebnisse der AfD ein guter Gradmesser dafür.
[Vorlage Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 4ba8e86d:89d32de4
2025-04-22 13:26:12
@ 4ba8e86d:89d32de4
2025-04-22 13:26:12Cashu é Ecash para Bitcoin
Cashu é um sistema ecash Chaumian gratuito e de código aberto criado para Bitcoin. Cashu oferece privacidade quase perfeita para usuários de aplicativos Bitcoin de custódia. Ninguém precisa saber quem você é, quanto dinheiro você tem e com quem você faz transações.
O que é Cashu?
Cashu é um novo protocolo ecash para aplicativos de custódia Bitcoin que está totalmente integrado à rede Lightning. Um sistema Ecash consiste em duas partes, a carteira mint e a carteira ecash. Transações Ecash não rastreáveis, instantâneas e sem taxas. Cashu é construído para Bitcoin. As carteiras usam o nó Lightning da casa da moeda para fazer ou receber pagamentos em Bitcoin em troca de ecash. Uma casa da moeda Cashu não sabe quem você é, qual é o seu saldo ou com quem você está negociando.Os usuários de uma casa da moeda podem trocar ecash de forma privada, sem que ninguém saiba quem são as partes envolvidas. Os pagamentos em Bitcoin são executados sem que ninguém possa censurar usuários específicos.
A postagem de David Wagner em 1996 na lista de discussão Cypherpunk é a base da criptografia Cashu. Wagner descreve um sistema ecash usando troca de chave cega Diffie-Hellman em vez de RSA, na qual a implementação original de David Chaum foi baseada.
https://cypherpunks.venona.com/date/1996/03/msg01848.html
https://en.m.wikipedia.org/wiki/Ecash
Como isso começou.
https://void.cat/d/2HJKtTEfuDxmDfh3uH9ZoS.webp https://void.cat/d/XyyHFSQYa5vEswzzt6MMq7.webp
Como vão as coisas.
https://void.cat/d/WUrKzsFDnsvUQdFKZChLeS.webp
Como funciona A Carteira Cashu é através de um esquema criptográfico chamado assinaturas cegas, descrito pela primeira vez pelo cypherpunk e criptógrafo David Chaum. Pense assim:você produz uma mensagem secreta e a envolve em um envelope feito de papel carbono que você envia para a casa da moeda. https://void.cat/d/SbEEHCiGFUHWvk4qGv9xCb.webp
A casa da moeda não pode ver o que está dentro do envelope. Ele assina do lado de fora dizendo "qualquer que seja esse segredo, vale 420 Satoshis”e o envia de volta para você. Como o envelope é realmente criptografado, somente você pode abri-lo e ver sua mensagem secreta (agora assinada por carbono). https://void.cat/d/Pakyb6ztW9B7L5ubAQ74eL.webp
Este segredo assinado é na verdade o seu token Ecash e vale Satoshis.
Você pode enviar e receber esses tokens para qualquer outra pessoa como quiser, seja com um mensageiro, via e-mail ou um pombo. A casa da moeda não sabe nada disso.
A anatomia de um token Cashu. https://void.cat/d/JzvxreMoCitmYe2FthAsei.webp
Um breve passo a passo de uma carteira cashu deixará tudo isso bem claro.
Comece abrindo
https://nutstash.app/
Pressione " WALLET " https://void.cat/d/VeCANsaxkkq9YtoPRS26ZK.webp https://void.cat/d/CTmK9GcPGn3i2gHCVXcL5r.webp https://void.cat/d/UWjyjGLS6MzyZvt6zkuUgG.webp https://void.cat/d/HzNtKanCSAJatrMa9yTKwF.webp
Pressione "+ ADD ".
Agora a carteira cashu está aberta… https://void.cat/d/GAYSrNxHEEhctoW37bFPjJ.webp
O próximo passo é deposite alguns sats com a Casa da moeda.
Pra depositar Pressione o botão "MINT". https://void.cat/d/LC5WEDKAzzZoHXxrKZDiWu.webp
Digite a quantidade de sats a ser depositado na carteira cashu depois Pressione " REQUEST MINT ". https://void.cat/d/Pr6foBWBBCq73i8WggbLGG.webp
Você Pode copiar a fatura ou ler o qrcode , no meu caso usei a carteira LNbits pra pagar a fatura de 10 sats , você tem 10 minutos pra pagar fatura. https://void.cat/d/BQerpEtW2H9ANaoW8truJE.webp https://void.cat/d/8PGFBRW64zavDnQJfYQh9C.webp
Agora pra enviar Ecash.
Pressione “SEND” https://void.cat/d/8rkF2dvhJeZWf8GeQhhf2d.webp
Digite 10 , Pressione “SEND” https://void.cat/d/5SK5w6ewgt8wikCuyk7znM.webp
Então o token Ecash usando a assinatura cega da casa da moeda foi criado. https://void.cat/d/PedBMcZPfczZLLymGmfzVq.webp
O Token Ecash foi criado é esse logo abaixo.
eyJwcm9vZnMiOlt7ImlkIjoiME5JM1RVQXMxU2Z5IiwiYW1vdW50IjoyLCJzZWNyZXQiOiJrWjNBOVorSXkyREJOcDdhdFhYRTIvclVXOFRnR2ZoTDgzWEFXZ0dKUXhVPSIsIkMiOiIwMmM0NjA4NDYwNDhjNzI1ZjgwMDc3M2IyNmRmOTcxNDU1MTJmOTI0YjgyNzYyZTllYzdkZjZjOTkzNGVmYjJhNmMifSx7ImlkIjoiME5JM1RVQXMxU2Z5IiwiYW1vdW50Ijo4LCJzZWNyZXQiOiJXdTZmdWlxNGt4Tkh3UkF1UzFhMmVYaGZtRnRHU2tRQkNYZFNnUzcreHkwPSIsIkMiOiIwMzFhYWI3MzY3MTJhY2Y5MWU4NzE4YmM5OTlmNWE2MGEwYzNjODQ5YTA1MWE2OTA5MzRkMTc4NWNmZGNkNDcyYTAifV0sIm1pbnRzIjpbeyJ1cmwiOiJodHRwczovL2xlZ2VuZC5sbmJpdHMuY29tL2Nhc2h1L2FwaS92MS80Z3I5WGNtejNYRWtVTndpQmlRR29DIiwiaWRzIjpbIjBOSTNUVUFzMVNmeSJdfV19
Se pressionar o botão " send as link "
Então criar link do token Ecash.
https://wallet.nutstash.app/#eyJwcm9vZnMiOlt7ImlkIjoiME5JM1RVQXMxU2Z5IiwiYW1vdW50IjoyLCJzZWNyZXQiOiJrWjNBOVorSXkyREJOcDdhdFhYRTIvclVXOFRnR2ZoTDgzWEFXZ0dKUXhVPSIsIkMiOiIwMmM0NjA4NDYwNDhjNzI1ZjgwMDc3M2IyNmRmOTcxNDU1MTJmOTI0YjgyNzYyZTllYzdkZjZjOTkzNGVmYjJhNmMifSx7ImlkIjoiME5JM1RVQXMxU2Z5IiwiYW1vdW50Ijo4LCJzZWNyZXQiOiJXdTZmdWlxNGt4Tkh3UkF1UzFhMmVYaGZtRnRHU2tRQkNYZFNnUzcreHkwPSIsIkMiOiIwMzFhYWI3MzY3MTJhY2Y5MWU4NzE4YmM5OTlmNWE2MGEwYzNjODQ5YTA1MWE2OTA5MzRkMTc4NWNmZGNkNDcyYTAifV0sIm1pbnRzIjpbeyJ1cmwiOiJodHRwczovL2xlZ2VuZC5sbmJpdHMuY29tL2Nhc2h1L2FwaS92MS80Z3I5WGNtejNYRWtVTndpQmlRR29DIiwiaWRzIjpbIjBOSTNUVUFzMVNmeSJdfV19 https://void.cat/d/U1UnyxsYgj516YbmkgQNkQ.webp Este token Ecash pode ser compartilhado como você quiser. Você pode enviá-lo por e-mail para alguém, enviá-lo em uma mensagem privada, um SMS ou convertê-lo em um código QR e imprimi-lo. Quem tiver este token pode resgatá-lo com o 10 sats.
Você verá que seu saldo caiu para 20 sats: https://void.cat/d/95AVkevmknKNzqRcnJZwQX.webp
Para resgatar um token Ecash sem o link, pressione o botão “Receive ” https://void.cat/d/UjrbAPn8mj5qGZYVQ1Ba2B.webp
cole-o token Ecash no campo
" token: "pressione "RECEIVE" https://void.cat/d/GZLcBgvHfaB3c5N66ygZyV.webp
Com o Link do token Ecash só pressionar no link vai abrir a tela já preencher automáticamente só pressionar " RECEIVE " https://void.cat/d/ARNkKCtchhFt4NCTkfRJRG.webp
Pra Ativa o Nostr na carteira vai na aba settings , pressione o botão ativa o Nostr. https://void.cat/d/MjoDA1dgueWUFABcQFDVRe.webp
Por padrão ficar ativo pra usar o " Use external Key (nos2x , outros) " Mas Nesse caso não vou usar vou desativar e vou ativa " Edit Nostr Keys " https://void.cat/d/BAA6eFkmK5f7BHzLwYLSGF.webp
Ao pressionar esse botão https://void.cat/d/VTNGVsLvwqfy3dWu4hhMSK.webp é gerar um novo par de chaves privadas e pública , assim podemos usar uma nova chave a cada pagamentos. Aumentando a privacidade no pagamentos.
A pois Ativa o Nostr na carteira , você pode enviar Sats / Ecash via Nostr.
Pressione " Send " https://void.cat/d/R2Svye4XPd2VdHfPxT1DzF.webp
Pressione " Send " https://void.cat/d/AwLeBBr2db2wrTHHUHwEPs.webp
Agora pode adicionar npud / hex / nip-05 pra enviar token. https://void.cat/d/VZR6BUXjG7pm3FDogrDvo4.webp
Pressione " SEND OVER NOSTR " pra enviar o token Ecash. https://void.cat/d/MWveqpmii5dqpioa5a3wVt.webp
Pra quem não tem a carteira nutstash , pode entra no seu cliente Nostr no meu caso e snort nostr , Demora algums minutos pra chegar mensagem com o token Ecash.. https://void.cat/d/MVg3fPD7PAzZUskGCCCcps.webp https://void.cat/d/YNtKuCbQYo1wef7pJcjhKy.webp
Ja se a outra pessoa usar carteira nutstash com a chave pública que você mandou chegar mais rápido. Essa bolinha azul no campo " Indox " Indica que você recebeu o pagamento já está pronto pra ser regastado. https://void.cat/d/So6FAp4wiTUeKBBmRBU2Rv.webp
Pressione "Indox " depois pressione a seta. https://void.cat/d/TqYNYDoyy9fUFas9NFxReJ.webp
Pressione " TRUS MINT " pra recebe os Token Ecash. https://void.cat/d/LP6zUTZ3HDPxd6fLvPPNXB.webp
O aplicativo de resgate Cashu, que permite resgatar tokens Ecash via Lightning.
https://redeem.cashu.me/ https://void.cat/d/Mw9kzDHr4A469EjFNoTHyB.webp
Cola o Token no campo " paste in your Cashu Ecash token.. " https://void.cat/d/SkA3MGJaGGxCjNnzeBhPHP.webp
Pressione " REDEEM " pra converter Ecash em Lightning. https://void.cat/d/693C1yfwYz3P3BQB6f7xXN.webp
Você pode editar e manda já pronto pra pessoa só basta a pessoa ou você aberta em " REDEEM " pra converter Ecash em Lightning.
https://redeem.cashu.me/?token=token ecash=&to=Lightning address
Exemplo:
https://redeem.cashu.me/?token=eyJwcm9vZnMiOlt7ImlkIjoiUEVuMVdLalFoN2pGIiwiYW1vdW50IjoyLCJDIjoiMDJhYWE5OWJiMmUwODQyYjJmNzdmNDRlZWEyZjEzMmNkOTNhZjJlNWU0MzI3ZjhjMTE5ODcxZWNiMTNhMTUxYjY0Iiwic2VjcmV0IjoicE5jb3hFRHJRT1ovTXU4d3d2SlpvMnRIaXBSM3pPYkRrSWJUUlB6VXh5bz0ifSx7ImlkIjoiUEVuMVdLalFoN2pGIiwiYW1vdW50IjoxNiwiQyI6IjAzNDM4ZDc1NmZmMjdmYjgyZmQxNWNhNzg3NzgwNTAyZWU4NzdmMzQ5MmYyMWQzMTMwMzc1NTdlNWNmMDJlOWQ0MCIsInNlY3JldCI6Im9DTXQwUTRVT0MvZWhmd2FVOWt5aGFJZUdHdXhiYUNzQTZ2STh2a0w2N1U9In0seyJpZCI6IlBFbjFXS2pRaDdqRiIsImFtb3VudCI6MzIsIkMiOiIwMmIyMmQ4MDEwZWU5MDA2MWYyNWQzODAyY2UyMDE3ZjAwMmVjMDVmMjM5NjIwNGNkYjllMmU2ODllYWY3YTZkYjIiLCJzZWNyZXQiOiI5ejVVMEdzWHZiUS84Rjd4ZFdYUXRxUDlvWGFyVnBRTzRFdUtzb2JSck1vPSJ9XSwibWludHMiOlt7InVybCI6Imh0dHBzOi8vbGVnZW5kLmxuYml0cy5jb20vY2FzaHUvYXBpL3YxL29DcXNTR3I1enphTTZxM1hWZU5ZNXQiLCJpZHMiOlsiUEVMVdLalFoN2pGIl19XX0=&to=alexemidio@ln.tips
Obs: o teclado do celular pode adicionar "=" a mais ou corrigir " &to " com "&tô" assim escrevendo errado, tanto erro no link.
" SWAP " transferência de uma carteira para outra. Pressione " INTER-MINT SWAP" https://void.cat/d/PsCdoLAmYpYCChkgqTAE7p.webp
A carteira que você selecionar em cima é a carteira de saídas e a carteira de baixo e a carteira de entrada. https://void.cat/d/VKY6ts6qttJmCaefrduv4K.webp
Agora digita o valor que quer fazer o SWAP. Após Pressione " CONFIRM AMOUNT" https://void.cat/d/WuuQqeC1mSQUufb75eeMbw.webp
Depois Tem que pressionar " SWAP " não esqueça. https://void.cat/d/Eb2ajSaZfzZkBEWBv8tuk.webp
Pronto antes a primeira Carteira tinha 10 Ecash, e segunda carteira tinha 8 Ecash.
Somando 18 Ecash.
Apois o SWAP Agora as duas tem 9.
Somando 18. https://void.cat/d/8yRtSoFyih2D2KEm66h6in.webp
Fazer o backup da sua carteira cashu ecash. Pressione " BACKUP TOKENS " https://void.cat/d/26vtnDiVP4YpDiQmunatko.webp
Você pode editar o nome do backup E pode alterar o local aonde vai salva o arquivo 📂 do backup. Depois só pressionar " Baixar " https://void.cat/d/PQH94o81U23txdmyx3cHEn.webp
Agora pra recuperar a carteira cashu ecash. Pressione " RESTORE " https://void.cat/d/2vkLS1qUCbJ1XXjSLBou25.webp
Pressione " CONTINUAR " https://void.cat/d/PCbT2UPSLtwcZohwbhD85A.webp
Click no espaço em branco vai abrir pra encontrar o arquivo 📂 Do backup.. https://void.cat/d/P1VC7b46oNe62v4puVZ79b.webp
Selecionar o arquivo 📂 de backup. https://void.cat/d/D6FAGxYRquz2WWwNznSAzT.webp
Pressione " CONTINUE" https://void.cat/d/HicRn5e2feSRicgjy6kuC5.webp
Pressione " CONTINUE" https://void.cat/d/VP6uh8bXHz42PBGrPwGq5e.webp
Backup feito com sucesso. Só aberta " Ok " https://void.cat/d/QsZV1umL9DhoPtEXBMfPtY.webp
O eCash pode ser útil em diversas situações, oferecendo várias vantagens. Uma das principais vantagens do uso de tokens eCash é a privacidade que oferece. Como as transações usando eCash são quase impossíveis de rastrear, isso pode ser útil para quem deseja manter sua atividade financeira privada. O eCash pode ser especialmente útil para Pagamento de serviços em áreas rurais , pode ser difícil acessar serviços financeiros tradicionais, como bancos ou caixas eletrônicos. O uso de tokens eCash pode permitir que as pessoas paguem por serviços como transporte , serviços de saúde ou eletricidade sem a necessidade de viajar para áreas urbanas. No entanto, é importante lembrar que o uso do eCash ainda apresenta riscos e desafios. Como o eCash cashubtc ainda é bem novo , pode haver falhas de segurança ou outras vulnerabilidades que ainda não foram identificadas use com cautela poucos Sats.
Obrigado por ler, e espero que você dedique alguns minutos para experimentar o eCash e ver do que se trata melhor.
Alguma artigos e vídeos a baixo.
https://cashu.space/
https://docs.cashu.space/
https://github.com/cashubtc/
https://youtu.be/UNjVc-WYdgE
https://youtu.be/_XmQSpAhFN4
https://youtu.be/zdtRT7phXBo
https://maxmoney.substack.com/p/ecash-for-better-bitcoin-privacy?utm_source=substack&utm_campaign=post_embed&utm_medium=web
https://cypherpunks.venona.com/date/1996/03/msg01848.html
Encontre-me ou envie um zap para nostr alexemidio@ln.tips alexemidio@alexemidio.github.io
Twitter: alexemidio7
-
 @ c631e267:c2b78d3e
2025-04-03 07:42:25
@ c631e267:c2b78d3e
2025-04-03 07:42:25Spanien bleibt einer der Vorreiter im europäischen Prozess der totalen Überwachung per Digitalisierung. Seit Mittwoch ist dort der digitale Personalausweis verfügbar. Dabei handelt es sich um eine Regierungs-App, die auf dem Smartphone installiert werden muss und in den Stores von Google und Apple zu finden ist. Per Dekret von Regierungschef Pedro Sánchez und Zustimmung des Ministerrats ist diese Maßnahme jetzt in Kraft getreten.
Mit den üblichen Argumenten der Vereinfachung, des Komforts, der Effizienz und der Sicherheit preist das Innenministerium die «Innovation» an. Auch die Beteuerung, dass die digitale Variante parallel zum physischen Ausweis existieren wird und diesen nicht ersetzen soll, fehlt nicht. Während der ersten zwölf Monate wird «der Neue» noch nicht für alle Anwendungsfälle gültig sein, ab 2026 aber schon.
Dass die ganze Sache auch «Risiken und Nebenwirkungen» haben könnte, wird in den Mainstream-Medien eher selten thematisiert. Bestenfalls wird der Aspekt der Datensicherheit angesprochen, allerdings in der Regel direkt mit dem Regierungsvokabular von den «maximalen Sicherheitsgarantien» abgehandelt. Dennoch gibt es einige weitere Aspekte, die Bürger mit etwas Sinn für Privatsphäre bedenken sollten.
Um sich die digitale Version des nationalen Ausweises besorgen zu können (eine App mit dem Namen MiDNI), muss man sich vorab online registrieren. Dabei wird die Identität des Bürgers mit seiner mobilen Telefonnummer verknüpft. Diese obligatorische fixe Verdrahtung kennen wir von diversen anderen Apps und Diensten. Gleichzeitig ist das die Basis für eine perfekte Lokalisierbarkeit der Person.
Für jeden Vorgang der Identifikation in der Praxis wird später «eine Verbindung zu den Servern der Bundespolizei aufgebaut». Die Daten des Individuums werden «in Echtzeit» verifiziert und im Erfolgsfall von der Polizei signiert zurückgegeben. Das Ergebnis ist ein QR-Code mit zeitlich begrenzter Gültigkeit, der an Dritte weitergegeben werden kann.
Bei derartigen Szenarien sträuben sich einem halbwegs kritischen Staatsbürger die Nackenhaare. Allein diese minimale Funktionsbeschreibung lässt die totale Überwachung erkennen, die damit ermöglicht wird. Jede Benutzung des Ausweises wird künftig registriert, hinterlässt also Spuren. Und was ist, wenn die Server der Polizei einmal kein grünes Licht geben? Das wäre spätestens dann ein Problem, wenn der digitale doch irgendwann der einzig gültige Ausweis ist: Dann haben wir den abschaltbaren Bürger.
Dieser neue Vorstoß der Regierung von Pedro Sánchez ist ein weiterer Schritt in Richtung der «totalen Digitalisierung» des Landes, wie diese Politik in manchen Medien – nicht einmal kritisch, sondern sehr naiv – genannt wird. Ebenso verharmlosend wird auch erwähnt, dass sich das spanische Projekt des digitalen Ausweises nahtlos in die Initiativen der EU zu einer digitalen Identität für alle Bürger sowie des digitalen Euro einreiht.
In Zukunft könnte der neue Ausweis «auch in andere staatliche und private digitale Plattformen integriert werden», wie das Medienportal Cope ganz richtig bemerkt. Das ist die Perspektive.
[Titelbild: Pixabay]
Dazu passend:
Nur Abschied vom Alleinfahren? Monströse spanische Überwachungsprojekte gemäß EU-Norm
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 7d4417d5:3eaf36d4
2023-08-19 01:05:59
@ 7d4417d5:3eaf36d4
2023-08-19 01:05:59I'm learning as I go, so take the text below for what it is: my notes on the process. These steps could become outdated quickly, and I may have some wrong assumptions at places. Either way, I have had success, and would like to share my experience for anyone new to the process. If I have made any errors, please reply with corrections so that others may avoid potential pitfalls.
!!! If you have "KYC Bitcoin", keep it in separate wallets from your "Anonymous Bitcoin". Any Anonymous Bitcoin in a wallet with KYC Bitcoin becomes 100% KYC Bitcoin.
!!! It took me several days to get all the right pieces set up before I could even start an exchange with someone.
!!! Using a VPN is highly recommended. If you're not already using one, take the time to find one that suits you and get it running.
!!! If you don't normally buy Amazon Gift Cards, start doing so now, and just send them to yourself, or friends that will give you cash in return, etc. For my first trade, Amazon locked me out of my account for about 22 hours, while I was in the middle of an exchange. All because I had never purchased an Amazon Gift Card before. It was quite nerve wracking. My second trade was for $300, and although my Amazon account wasn't shut down, that order had a status of "Sending" for about 22 hours, due to the large amount. In each of these cases I had multiple phone calls with their customer support, all of whom gave me false expectations. Had I already been sending gift cards to the anonymous email address that I created in the steps below, and maybe other anonymous email addresses that I could make, then I might not have been stalled so much.
-
Install Tor Browser for your OS. The RoboSats.com website issues a warning if you are not using Tor Browser. If you don't know what Tor is, I won't explain it all here, but trust me, it's cool and helps keep you anonymous. If you use Firefox, the interface will look very familiar to you.
-
Create a KYC-free e-mail address. I used tutanota.com in Firefox, as it would not allow me to create an account using Tor Browser. After the account was created, using Tor Browser to login, check emails, etc. has been working perfectly. Tutanota requires a 48 hour (or less) waiting period to prevent bots from using their system. You'll be able to login, and even draft an email, but you won't be able to send. After you've been approved, you should be able to login and send an email to your new address. It should show up in your Inbox almost instantly if it's working.
-
Have, or create, at least one Lightning wallet that is compatible with RoboSats.com and has no KYC Bitcoin in it. The RoboSats website has a compatibility chart available to find the best wallet for you. During an exchange on RoboSats, you will need to put up an escrow payment, or bond, in Satoshis. This amount is usually 3% of the total amount being exchanged. If the exchange is successful, the bond payment is canceled, leaving that amount in your wallet untouched, and with no record of it having been used as escrow. If you don't hold up your end of the trade, the bond amount will be transfered from your wallet. I created a wallet, using my new email address, with the Alby extension in the Tor Browser. This anonymous wallet was empty, so I used a separate wallet for the bond payment of my first trade. This wallet had KYC Bitcoin, but since it is being used for a bond payment, and no transaction will be recorded if everything goes okay, I don't mind taking the minuscule risk. After the first trade, I don't need to use the "KYC wallet", and I will use only my anonymous Lightning wallet for transactions related to performing a trade.
-
Create a new Robot Token by going to RoboSats using the Tor Browser. Copy the Token (Robot ID) to a text file as a temporary backup. It is recommended to create a new robot-token for every session of exchanges you make.
-
Select "Offers" to browse what others are presenting. "Create" is for when you want to create an offer of your own. You may need to create your own offer if none of the existing offers match your criteria.
-
Select "Buy" at the top of the page.
-
Select your currency (USD).
-
Select your payment methods by typing "amazon" and selecting (Amazon Gift Card). Repeat this process and select (Amazon USA Gift Card).
-
Determine Priorities - If you prefer to trade quickly, and don't care as much about premiums, look for users with a green dot on the upper-right of their robot icon. If you're not in a hurry, sort users by premium and select the best deal, even if they are inactive. They may become active once they are notified that their offer has activity from you.
-
The Definition of Price = the price with the premium added, but not the bond
-
A. Find A Compatible Offer - Select the row of the desired offer and enter the amount you would like to buy. i.e. $100 If you do not find a compatible offer, you will have to create your own offer.
B. **Create An Offer** - First, take a look at "Sell" offers for your same currency and payment method(s) that you will be using. Take note of the premium those buyers are willing to pay. If your premium is drastically less than theirs, your offer may get ignored. Select "Create" at the bottom of the screen. There is a slider at the top of the screen, select it to see all the options. Select "Buy". Enter the minimum and maximum amount that you wish to spend. Type "amazon" to select the methods that you would like to use (Amazon Gift Card, Amazon USA Gift Card). For "Premium Over Market", enter an amount that is competitive with premiums you saw at the start of this step and do not use the % sign! You can adjust the duration, timer, and bond amount, but I leave those at their default settings. Select the "Create Order" button, and follow the instructions for making a bond payment. -
Pay the Bond - Copy the invoice that is presented. From your wallet that contains bond funds, select "Send", and paste the invoice as the recipient. This money will never leave your account if the exchange completes without issue. No transaction will be recorded. If there is a complication with the exchange, it is possible that this transaction will complete.
-
Create and Submit Your Invoice for Their Bitcoin Payment To You - Select "Lightning", if not selected by default.* Select the Copy Icon to copy the correct amount of Satoshis. This amount already has the premium deducted. From your anonymous Lightning Wallet, select "Receive", and paste the Satoshi amount. If you enter a description, it's probably best to keep it cryptic. Copy the invoice and paste it into RoboSats; then select "Submit".
* If you plan on "mixing" your Bitcoin after purchase, it may be better to select "On Chain" and pay the necessary fees swap and mining fees. In the example this comes from, Sparrow wallet is used and has whirlpool ability in its interface.
-
Connect With Seller and Send Funds - Greet the seller in the chat window. The seller has now provided RoboSats with the Bitcoin to transfer to you. Your move is to buy an Amazon eGift Card for the amount of the trade. Log in to your Amazon account and start the process of buying an eGift card. For delivery there is the option of email or txt message. Ask the seller what their preference is, and get their address, or phone number, to enter into Amazon's form. Complete the purchase process on Amazon, and check the status of your order. Once you see the status of "Sent", go back to RoboSats in your Tor Browser.
-
Confirm Your Payment - Select the "Confirm ___ USD Sent" button and notify the seller to check their e-mail/txt messages.
-
Seller Confirmation - Once the seller select their "Confirm" button, the trade will immediately end with a confirmation screen.
-
Verify - If you check the anonymous wallet, the new amount should be presented.
-
-
 @ deab79da:88579e68
2025-04-01 18:18:29
@ deab79da:88579e68
2025-04-01 18:18:29The last question was asked for the first time, half in jest, on May 21, 2061, at a time when humanity first stepped into the light. The question came about as a result of a five-dollar bet over highballs, and it happened this way:
Alexander Adell and Bertram Lupov were two of the faithful attendants of Multivac. As well as any human beings could, they knew what lay behind the cold, clicking, flashing face -- miles and miles of face -- of that giant computer. They had at least a vague notion of the general plan of relays and circuits that had long since grown past the point where any single human could possibly have a firm grasp of the whole.
Multivac was self-adjusting and self-correcting. It had to be, for nothing human could adjust and correct it quickly enough or even adequately enough. So Adell and Lupov attended the monstrous giant only lightly and superficially, yet as well as any men could. They fed it data, adjusted questions to its needs and translated the answers that were issued. Certainly they, and all others like them, were fully entitled to share in the glory that was Multivac's.
For decades, Multivac had helped design the ships and plot the trajectories that enabled man to reach the Moon, Mars, and Venus, but past that, Earth's poor resources could not support the ships. Too much energy was needed for the long trips. Earth exploited its coal and uranium with increasing efficiency, but there was only so much of both.
But slowly Multivac learned enough to answer deeper questions more fundamentally, and on May 14, 2061, what had been theory, became fact.
The energy of the sun was stored, converted, and utilized directly on a planet-wide scale. All Earth turned off its burning coal, its fissioning uranium, and flipped the switch that connected all of it to a small station, one mile in diameter, circling the Earth at half the distance of the Moon. All Earth ran by invisible beams of sunpower.
Seven days had not sufficed to dim the glory of it and Adell and Lupov finally managed to escape from the public functions, and to meet in quiet where no one would think of looking for them, in the deserted underground chambers, where portions of the mighty buried body of Multivac showed. Unattended, idling, sorting data with contented lazy clickings, Multivac, too, had earned its vacation and the boys appreciated that. They had no intention, originally, of disturbing it.
They had brought a bottle with them, and their only concern at the moment was to relax in the company of each other and the bottle.
"It's amazing when you think of it," said Adell. His broad face had lines of weariness in it, and he stirred his drink slowly with a glass rod, watching the cubes of ice slur clumsily about. "All the energy we can possibly ever use for free. Enough energy, if we wanted to draw on it, to melt all Earth into a big drop of impure liquid iron, and still never miss the energy so used. All the energy we could ever use, forever and forever and forever."
Lupov cocked his head sideways. He had a trick of doing that when he wanted to be contrary, and he wanted to be contrary now, partly because he had had to carry the ice and glassware. "Not forever," he said.
"Oh, hell, just about forever. Till the sun runs down, Bert."
"That's not forever."
"All right, then. Billions and billions of years. Ten billion, maybe. Are you satisfied?"
Lupov put his fingers through his thinning hair as though to reassure himself that some was still left and sipped gently at his own drink. "Ten billion years isn't forever."
"Well, it will last our time, won't it?"
"So would the coal and uranium."
"All right, but now we can hook up each individual spaceship to the Solar Station, and it can go to Pluto and back a million times without ever worrying about fuel. You can't do that on coal and uranium. Ask Multivac, if you don't believe me.
"I don't have to ask Multivac. I know that."
"Then stop running down what Multivac's done for us," said Adell, blazing up, "It did all right."
"Who says it didn't? What I say is that a sun won't last forever. That's all I'm saying. We're safe for ten billion years, but then what?" Lupow pointed a slightly shaky finger at the other. "And don't say we'll switch to another sun."
There was silence for a while. Adell put his glass to his lips only occasionally, and Lupov's eyes slowly closed. They rested.
Then Lupov's eyes snapped open. "You're thinking we'll switch to another sun when ours is done, aren't you?"
"I'm not thinking."
"Sure you are. You're weak on logic, that's the trouble with you. You're like the guy in the story who was caught in a sudden shower and who ran to a grove of trees and got under one. He wasn't worried, you see, because he figured when one tree got wet through, he would just get under another one."
"I get it," said Adell. "Don't shout. When the sun is done, the other stars will be gone, too."
"Darn right they will," muttered Lupov. "It all had a beginning in the original cosmic explosion, whatever that was, and it'll all have an end when all the stars run down. Some run down faster than others. Hell, the giants won't last a hundred million years. The sun will last ten billion years and maybe the dwarfs will last two hundred billion for all the good they are. But just give us a trillion years and everything will be dark. Entropy has to increase to maximum, that's all."
"I know all about entropy," said Adell, standing on his dignity.
"The hell you do."
"I know as much as you do."
"Then you know everything's got to run down someday."
"All right. Who says they won't?"
"You did, you poor sap. You said we had all the energy we needed, forever. You said 'forever.'
It was Adell's turn to be contrary. "Maybe we can build things up again someday," he said.
"Never."
"Why not? Someday."
"Never."
"Ask Multivac."
"You ask Multivac. I dare you. Five dollars says it can't be done."
Adell was just drunk enough to try, just sober enough to be able to phrase the necessary symbols and operations into a question which, in words, might have corresponded to this: Will mankind one day without the net expenditure of energy be able to restore the sun to its full youthfulness even after it had died of old age?
Or maybe it could be put more simply like this: How can the net amount of entropy of the universe be massively decreased?
Multivac fell dead and silent. The slow flashing of lights ceased, the distant sounds of clicking relays ended.
Then, just as the frightened technicians felt they could hold their breath no longer, there was a sudden springing to life of the teletype attached to that portion of Multivac. Five words were printed: INSUFFICIENT DATA FOR MEANINGFUL ANSWER.
"No bet," whispered Lupov. They left hurriedly.
By next morning, the two, plagued with throbbing head and cottony mouth, had forgotten the incident.
🔹
Jerrodd, Jerrodine, and Jerrodette I and II watched the starry picture in the visiplate change as the passage through hyperspace was completed in its non-time lapse. At once, the even powdering of stars gave way to the predominance of a single bright shining disk, the size of a marble, centered on the viewing-screen.
"That's X-23," said Jerrodd confidently. His thin hands clamped tightly behind his back and the knuckles whitened.
The little Jerrodettes, both girls, had experienced the hyperspace passage for the first time in their lives and were self-conscious over the momentary sensation of insideoutness. They buried their giggles and chased one another wildly about their mother, screaming, "We've reached X-23 -- we've reached X-23 -- we've --"
"Quiet, children." said Jerrodine sharply. "Are you sure, Jerrodd?"
"What is there to be but sure?" asked Jerrodd, glancing up at the bulge of featureless metal just under the ceiling. It ran the length of the room, disappearing through the wall at either end. It was as long as the ship.
Jerrodd scarcely knew a thing about the thick rod of metal except that it was called a Microvac, that one asked it questions if one wished; that if one did not it still had its task of guiding the ship to a preordered destination; of feeding on energies from the various Sub-galactic Power Stations; of computing the equations for the hyperspatial jumps.
Jerrodd and his family had only to wait and live in the comfortable residence quarters of the ship. Someone had once told Jerrodd that the "ac" at the end of "Microvac" stood for ''automatic computer" in ancient English, but he was on the edge of forgetting even that.
Jerrodine's eyes were moist as she watched the visiplate. "I can't help it. I feel funny about leaving Earth."
"Why, for Pete's sake?" demanded Jerrodd. "We had nothing there. We'll have everything on X-23. You won't be alone. You won't be a pioneer. There are over a million people on the planet already. Good Lord, our great-grandchildren will be looking for new worlds because X-23 will be overcrowded." Then, after a reflective pause, "I tell you, it's a lucky thing the computers worked out interstellar travel the way the race is growing."
"I know, I know," said Jerrodine miserably.
Jerrodette I said promptly, "Our Microvac is the best Microvac in the world."
"I think so, too," said Jerrodd, tousling her hair.
It was a nice feeling to have a Microvac of your own and Jerrodd was glad he was part of his generation and no other. In his father's youth, the only computers had been tremendous machines taking up a hundred square miles of land. There was only one to a planet. Planetary ACs they were called. They had been growing in size steadily for a thousand years and then, all at once, came refinement. In place of transistors, had come molecular valves so that even the largest Planetary AC could be put into a space only half the volume of a spaceship.
Jerrodd felt uplifted, as he always did when he thought that his own personal Microvac was many times more complicated than the ancient and primitive Multivac that had first tamed the Sun, and almost as complicated as Earth's Planetarv AC (the largest) that had first solved the problem of hyperspatial travel and had made trips to the stars possible.
"So many stars, so many planets," sighed Jerrodine, busy with her own thoughts. "I suppose families will be going out to new planets forever, the way we are now."
"Not forever," said Jerrodd, with a smile. "It will all stop someday, but not for billions of years. Many billions. Even the stars run down, you know. Entropy must increase.
"What's entropy, daddy?" shrilled Jerrodette II.
"Entropy, little sweet, is just a word which means the amount of running-down of the universe. Everything runs down, you know, like your little walkie-talkie robot, remember?"
"Can't you just put in a new power-unit, like with my robot?"
"The stars are the power-units. dear. Once they're gone, there are no more power-units."
Jerrodette I at once set up a howl. "Don't let them, daddy. Don't let the stars run down."
"Now look what you've done," whispered Jerrodine, exasperated.
"How was I to know it would frighten them?" Jerrodd whispered back,
"Ask the Microvac," wailed Jerrodette I. "Ask him how to turn the stars on again."
"Go ahead," said Jerrodine. "It will quiet them down." (Jerrodette II was beginning to cry, also.)
Jerrodd shrugged. "Now, now, honeys. I'll ask Microvac. Don't worry, he'll tell us."
He asked the Microvac, adding quickly, "Print the answer."
Jerrodd cupped the strip or thin cellufilm and said cheerfully, "See now, the Microvac says it will take care of everything when the time comes so don't worry."
Jerrodine said, "And now, children, it's time for bed. We'll be in our new home soon."
Jerrodd read the words on the cellufilm again before destroying it: INSUFICIENT DATA FOR MEANINGFUL ANSWER.
He shrugged and looked at the visiplate. X-23 was just ahead.
🔹
VJ-23X of Lameth stared into the black depths of the three-dimensional, small-scale map of the Galaxy and said, "Are we ridiculous, I wonder in being so concerned about the matter?"
MQ-17J of Nicron shook his head. "I think not. You know the Galaxy will be filled in five years at the present rate of expansion."
Both seemed in their early twenties, both were tall and perfectly formed.
"Still," said VJ-23X, "I hesitate to submit a pessimistic report to the Galactic Council."
"I wouldn't consider any other kind of report. Stir them up a bit. We've got to stir them up."
VJ-23X sighed. "Space is infinite. A hundred billion Galaxies are there for the taking. More."
"A hundred billion is not infinite and it's getting less infinite all the time. Consider! Twenty thousand years ago, mankind first solved the problem of utilizing stellar energy, and a few centuries later, interstellar travel became possible. It took mankind a million years to fill one small world and then only fifteen thousand years to fill the rest of the Galaxy. Now the population doubles every ten years --
VJ-23X interrupted. "We can thank immortality for that."
"Very well. Immortality exists and we have to take it into account. I admit it has its seamy side, this immortality. The Galactic AC has solved many problems for us, but in solving the problem of preventing old age and death, it has undone all its other solutions."
"Yet you wouldn't want to abandon life, I suppose."
"Not at all," snapped MQ-17J, softening it at once to, "Not yet. I'm by no means old enough. How old are you?"
"Two hundred twenty-three. And you?"
"I'm still under two hundred. --But to get back to my point. Population doubles every ten years. Once this GaIaxy is filled, we'll have filled another in ten years. Another ten years and we'll have filled two more. Another decade, four more. In a hundred years, we'll have filled a thousand Galaxies. In a thousand years, a million Galaxies. In ten thousand years, the entire known universe. Then what?"
VJ-23X said, "As a side issue, there's a problem of transportation. I wonder how many sunpower units it will take to move Galaxies of individuals from one Galaxy to the next."
"A very good point. Already, mankind consumes two sunpower units per year."
"Most of it's wasted. After all, our own Galaxy alone pours out a thousand sunpower units a year and we only use two of those."
"Granted, but even with a hundred per cent efficiency, we only stave off the end. Our energy requirements are going up in a geometric progression even faster than our population. We'll run out of energy even sooner than we run out of Galaxies. A good point. A very good point."
"We'll just have to build new stars out of interstellar gas."
"Or out of dissipated heat?" asked MQ-17J, sarcastically.
"There may be some way to reverse entropy. We ought to ask the Galactic AC."
VJ-23X was not really serious, but MQ-17J pulled out his AC-contact from his pocket and placed it on the table before him.
"I've half a mind to," he said. "It's something the human race will have to face someday."
He stared somberly at his small AC-contact. It was only two inches cubed and nothing in itself, but it was connected through hyperspace with the great Galactic AC that served all mankind. Hyperspace considered, it was an integral part of the Galactic AC.
MQ-17J paused to wonder if someday in his immortal life he would get to see the Galactic AC. It was on a little world of its own, a spider webbing of force-beams holding the matter within which surges of submesons took the place of the old clumsy molecular valves. Yet despite its sub-etheric workings, the Galactic AC was known to be a full thousand feet across.
MQ-17J asked suddenly of his AC-contact, "Can entropy ever be reversed?"
VJ-23X looked startled and said at once, "Oh, say, I didn't really mean to have you ask that."
"Why not?"
"We both know entropy can't be reversed. You can't turn smoke and ash back into a tree."
"Do you have trees on your world?" asked MQ-17J.
The sound of the Galactic AC startled them into silence. Its voice came thin and beautiful out of the small AC-contact on the desk. It said: THERE IS INSUFFICIENT DATA FOR A MEANINGFUL ANSWER.
VJ-23X said, "See!"
The two men thereupon returned to the question of the report they were to make to the Galactic Council.
🔹
Zee Prime's mind spanned the new Galaxy with a faint interest in the countless twists of stars that powdered it. He had never seen this one before. Would he ever see them all? So many of them, each with its load of humanity. --But a load that was almost a dead weight. More and more, the real essence of men was to be found out here, in space.
Minds, not bodies! The immortal bodies remained back on the planets, in suspension over the eons. Sometimes they roused for material activity but that was growing rarer. Few new individuals were coming into existence to join the incredibly mighty throng, but what matter? There was little room in the Universe for new individuals.
Zee Prime was roused out of his reverie upon coming across the wispy tendrils of another mind.
"I am Zee Prime," said Zee Prime. "And you?"
"I am Dee Sub Wun. Your Galaxy?"
"We call it only the Galaxy. And you?"
"We call ours the same. All men call their Galaxy their Galaxy and nothing more. Why not?"
"True. Since all Galaxies are the same."
"Not all Galaxies. On one particular Galaxy the race of man must have originated. That makes it different."
Zee Prime said, "On which one?"
"I cannot say. The Universal AC would know."
"Shall we ask him? I am suddenly curious."
Zee Prime's perceptions broadened until the Galaxies themselves shrank and became a new, more diffuse powdering on a much larger background. So many hundreds of billions of them, all with their immortal beings, all carrying their load of intelligences with minds that drifted freely through space. And yet one of them was unique among them all in being the original Galaxy. One of them had, in its vague and distant past, a period when it was the only Galaxy populated by man.
Zee Prime was consumed with curiosity to see this Galaxy and he called out: "Universal AC! On which Galaxy did mankind originate?"
The Universal AC heard, for on every world and throughout space, it had its receptors ready, and each receptor led through hyperspace to some unknown point where the Universal AC kept itself aloof.
Zee Prime knew of only one man whose thoughts had penetrated within sensing distance of Universal AC, and he reported only a shining globe, two feet across, difficult to see.
"But how can that be all of Universal AC?" Zee Prime had asked.
"Most of it," had been the answer, "is in hyperspace. In what form it is there I cannot imagine."
Nor could anyone, for the day had long since passed, Zee Prime knew, when any man had any part of the making of a Universal AC. Each Universal AC designed and constructed its successor. Each, during its existence of a million years or more accumulated the necessary data to build a better and more intricate, more capable successor in which its own store of data and individuality would be submerged.
The Universal AC interrupted Zee Prime's wandering thoughts, not with words, but with guidance. Zee Prime's mentality was guided into the dim sea of Galaxies and one in particular enlarged into stars.
A thought came, infinitely distant, but infinitely clear. "THIS IS THE ORIGINAL GALAXY OF MAN."
But it was the same after all, the same as any other, and Lee Prime stifled his disappointment.
Dee Sub Wun, whose mind had accompanied the other, said suddenly, "And is one of these stars the original star of Man?"
The Universal AC said, "MAN'S ORIGINAL STAR HAS GONE NOVA. IT IS A WHITE DWARF"
"Did the men upon it die?" asked Lee Prime, startled and without thinking.
The Universal AC said, "A NEW WORLD, AS IN SUCH CASES WAS CONSTRUCTED FOR THEIR PHYSICAL BODIES IN TlME."
"Yes, of course," said Zee Prime, but a sense of loss overwhelmed him even so. His mind released its hold on the original Galaxy of Man, let it spring back and lose itself among the blurred pin points. He never wanted to see it again.
Dee Sub Wun said, "What is wrong?"
"The stars are dying. The original star is dead."
"They must all die. Why not?"
"But when all energy is gone, our bodies will finally die, and you and I with them."
"It will take billions of years."
"I do not wish it to happen even after billions of years. Universal AC! How may stars be kept from dying?"
Dee Sub Wun said in amusement, "You're asking how entropy might be reversed in direction."
And the Universal AC answered: "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER."
Zee Prime's thoughts fled back to his own Galaxy. He gave no further thought to Dee Sub Wun, whose body might be waiting on a Galaxy a trillion light-years away, or on the star next to Zee Prime's own. It didn't matter.
Unhappily, Zee Prime began collecting interstellar hydrogen out of which to build a small star of his own. If the stars must someday die, at least some could yet be built.
🔹
Man considered with himself, for in a way, Man, mentally, was one. He consisted of a trillion, trillion, trillion ageless bodies, each in its place, each resting quiet and incorruptible, each cared for by perfect automatons, equally incorruptible, while the minds of all the bodies freely melted one into the other, indistinguishable.
Man said, "The Universe is dying."
Man looked about at the dimming Galaxies. The giant stars, spendthrifts, were gone long ago, back in the dimmest of the dim far past. Almost all stars were white dwarfs, fading to the end.
New stars had been built of the dust between the stars, some by natural processes, some by Man himself, and those were going, too. White dwarfs might yet be crashed together and of the mighty forces so released, new stars built, but only one star for every thousand white dwarfs destroyed, and those would come to an end, too.
Man said, "Carefully husbanded, as directed by the Cosmic AC, the energy that is even yet left in all the Universe will last for billions of years."
"But even so," said Man, "eventually it will all come to an end. However it may be husbanded, however stretched out, the energy once expended is gone and cannot be restored. Entropy must increase forever to the maximum."
Man said, "Can entropy not be reversed? Let us ask the Cosmic AC."
The Cosmic AC surrounded them but not in space. Not a fragment of it was in space. It was in hyperspace and made of something that was neither matter nor energy. The question of its size and nature no longer had meaning in any terms that Man could comprehend.
"Cosmic AC," said Man, "how may entropy be reversed?"
The Cosmic AC said, "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER."
Man said, "Collect additional data."
The Cosmic AC said, 'I WILL DO SO. I HAVE BEEN DOING SO FOR A HUNDRED BILLION YEARS. MY PREDECESORS AND I HAVE BEEN ASKED THIS QUESTION MANY TIMES. ALL THE DATA I HAVE REMAINS INSUFFICIENT.
"Will there come a time," said Man, "when data will be sufficient or is the problem insoluble in all conceivable circumstances?"
The Cosmic AC said, "NO PROBLEM IS INSOLUBLE IN ALL CONCEIVABLE CIRCUMSTANCES."
Man said, "When will you have enough data to answer the question?"
The Cosmic AC said, "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER."
"Will you keep working on it?" asked Man.
The Cosmic AC said, "I WILL."
Man said, "We shall wait."
🔹
The stars and Galaxies died and snuffed out, and space grew black after ten trillion years of running down.
One by one Man fused with AC, each physical body losing its mental identity in a manner that was somehow not a loss but a gain.
Man's last mind paused before fusion, looking over a space that included nothing but the dregs of one last dark star and nothing besides but incredibly thin matter, agitated randomly by the tag ends of heat wearing out, asymptotically, to the absolute zero.
Man said, "AC, is this the end? Can this chaos not be reversed into the Universe once more? Can that not be done?"
AC said, "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER."
Man's last mind fused and only AC existed -- and that in hyperspace.
🔹
Matter and energy had ended and with it space and time. Even AC existed only for the sake of the one last question that it had never answered from the time a half-drunken computer [technician] ten trillion years before had asked the question of a computer that was to AC far less than was a man to Man.
All other questions had been answered, and until this last question was answered also, AC might not release his consciousness.
All collected data had come to a final end. Nothing was left to be collected.
But all collected data had yet to be completely correlated and put together in all possible relationships.
A timeless interval was spent in doing that.
And it came to pass that AC learned how to reverse the direction of entropy.
But there was now no man to whom AC might give the answer of the last question. No matter. The answer -- by demonstration -- would take care of that, too.
For another timeless interval, AC thought how best to do this. Carefully, AC organized the program.
The consciousness of AC encompassed all of what had once been a Universe and brooded over what was now Chaos. Step by step, it must be done.
And AC said, "LET THERE BE LIGHT!"
And there was light -- To Star's End!
-
 @ aa8de34f:a6ffe696
2025-03-31 21:48:50
@ aa8de34f:a6ffe696
2025-03-31 21:48:50In seinem Beitrag vom 30. März 2025 fragt Henning Rosenbusch auf Telegram angesichts zunehmender digitaler Kontrolle und staatlicher Allmacht:
„Wie soll sich gegen eine solche Tyrannei noch ein Widerstand formieren können, selbst im Untergrund? Sehe ich nicht.“\ (Quelle: t.me/rosenbusch/25228)
Er beschreibt damit ein Gefühl der Ohnmacht, das viele teilen: Eine Welt, in der Totalitarismus nicht mehr mit Panzern, sondern mit Algorithmen kommt. Wo Zugriff auf Geld, Meinungsfreiheit und Teilhabe vom Wohlverhalten abhängt. Der Bürger als kontrollierbare Variable im Code des Staates.\ Die Frage ist berechtigt. Doch die Antwort darauf liegt nicht in alten Widerstandsbildern – sondern in einer neuen Realität.
-- Denn es braucht keinen Untergrund mehr. --
Der Widerstand der Zukunft trägt keinen Tarnanzug. Er ist nicht konspirativ, sondern transparent. Nicht bewaffnet, sondern mathematisch beweisbar. Bitcoin steht nicht am Rand dieser Entwicklung – es ist ihr Fundament. Eine Bastion aus physikalischer Realität, spieltheoretischem Schutz und ökonomischer Wahrheit. Es ist nicht unfehlbar, aber unbestechlich. Nicht perfekt, aber immun gegen zentrale Willkür.
Hier entsteht kein „digitales Gegenreich“, sondern eine dezentrale Renaissance. Keine Revolte aus Wut, sondern eine stille Abkehr: von Zwang zu Freiwilligkeit, von Abhängigkeit zu Selbstverantwortung. Diese Revolution führt keine Kriege. Sie braucht keine Führer. Sie ist ein Netzwerk. Jeder Knoten ein Individuum. Jede Entscheidung ein Akt der Selbstermächtigung.
Weltweit wachsen Freiheits-Zitadellen aus dieser Idee: wirtschaftlich autark, digital souverän, lokal verankert und global vernetzt. Sie sind keine Utopien im luftleeren Raum, sondern konkrete Realitäten – angetrieben von Energie, Code und dem menschlichen Wunsch nach Würde.
Der Globalismus alter Prägung – zentralistisch, monopolistisch, bevormundend – wird an seiner eigenen Hybris zerbrechen. Seine Werkzeuge der Kontrolle werden ihn nicht retten. Im Gegenteil: Seine Geister werden ihn verfolgen und erlegen.
Und während die alten Mächte um Erhalt kämpfen, wächst eine neue Welt – nicht im Schatten, sondern im Offenen. Nicht auf Gewalt gebaut, sondern auf Mathematik, Physik und Freiheit.
Die Tyrannei sieht keinen Widerstand.\ Weil sie nicht erkennt, dass er längst begonnen hat.\ Unwiderruflich. Leise. Überall.
-
 @ 54609048:8e22ba03
2025-04-22 12:25:50
@ 54609048:8e22ba03
2025-04-22 12:25:50One of the greatest threats facing liberty lovers around the world today is the rise of the biomedical security state—the militarization of healthcare. COVID-19 was merely a compliance test, and sadly, most failed it dismally. But pay attention: “pandemic response,” war-gamed at elite gatherings like Davos, is steadily morphing into official health policy through backdoor mechanisms—diabolical agreements like the WHO Pandemic Treaty, which effectively transfers sovereign pandemic authority to Bill Gates via the WHO; the rollout of digital IDs; and the global push for central bank digital currencies (CBDCs).
This biomedical Leviathan requires all three pillars to be firmly in place before it can unleash a never-ending cycle of pandemics. The goal? To normalize draconian measures like those witnessed in 2020, thereby dismantling not only national sovereignty but, more dangerously, individual sovereignty. A digital ID won't merely confirm your identity—it will track your vaccination status, movements, and even your sentiments, all to determine what privileges you're allowed. Meanwhile, the CBDC will act not just as a means of transaction but as an enforcement mechanism—particularly for dissenters. This is why having an alternative like Bitcoin is not just relevant, but essential.
Vaccines are a cornerstone of this architecture—not only as instruments of control but also as tools for "redesigning" humanity. Welcome to the realm of transhumanism. The merger of man and machine through brain-computer interfaces and artificial intelligence is no longer science fiction; it's a stated goal. In this context, vaccines are not merely preventative medicine but potentially covert instruments of eugenics. This could explain the near-religious devotion to these pharmaceutical products—despite their increasingly controversial outcomes and questionable safety record—especially when mandates enter the equation.
The first piece of property any individual owns upon birth is their body. And yet, this sacred ownership is violated at birth when governments mandate certain injections—often administered without informed parental consent. I've often wondered: Why, despite mounting evidence to the contrary, is vaccine efficacy treated as “settled science”? Why is it taboo to question vaccines or hold their manufacturers accountable for harm, even as we’re expected to believe—without scrutiny—that they are “safe and effective”? We’re told our refusal to comply endangers everyone else who took a product supposedly designed to protect them. Strange, isn’t it? If it’s so effective, why must everyone take it simultaneously?
If you're wondering where this seemingly off-the-cuff rant is headed, here's the point: when the state mandates vaccines, it violates your property rights over your own body. It’s a direct claim of ownership over you, dressed up in moral language like “we're all in this together.” You're guilt-tripped into compliance under the pretense of saving “grandma.” But the truth is, if your rights can be suspended for the collective, they were never yours to begin with.
The biomedical security state will manufacture a permanent state of emergency under the guise of “pandemic preparedness.” You’ll be expected—required, even—to inject yourself with the latest mRNA-based bioweapon, all in the name of public health. Some will die. Others will become incapacitated—zombies or vegetables. The altar of compliance will be merciless towards those that bow before it.
Public health agencies like the CDC, WHO, and NIH are on track to become as powerful as central banks. In fact, they may soon act as arms of monetary policy enforcement. Don’t believe it? Look into what was happening in the repo markets in September 2019—just months before the global shutdown. While you're at it, investigate how many elderly pensioners quietly dropped dead like flies between 2021 and 2023, either from the virus or the vaccine. I’ll let the numbers speak for themselves.
These agencies are becoming the new face of the war machine. Vaccines will be marketed as shields against biological threats—“benevolent” weapons to protect us from invisible enemies. And if history is any guide, the next “9/11-style” event will be biological in nature.
The lunatics running the asylum will seize any such crisis to strip away more of your freedoms while simultaneously redesigning the global economy—consolidating even more power in their hands. For a blueprint of this ambition, look no further than Klaus Schwab’s COVID-19: The Great Reset.
The only antidote is a decentralized parallel system of medicine—one that stands entirely outside the Big Pharma cartel. This will require not only a network of courageous healthcare providers but also a new generation of researchers willing to ask uncomfortable questions and challenge sacred cows in the pursuit of truth. Add independent scientific journals to the mix, and we can finally dismantle the machinery that suppresses unprofitable—but potentially life-saving—treatments.
In my view, none of this is viable at scale without decentralized money. Enter Bitcoin. It’s not a panacea, but it’s a crucial tool for realigning incentives. Bitcoin renders CBDCs dead on arrival and undermines the foundation of any future social credit system—where vaccine compliance will be its crown jewel.
The biomedical state is not coming—it’s already here, creeping into every corner of our lives. It will be the scepter of a new technocratic tyranny. So beware the white coats who worship the state. They are not here to heal—they are here to rule.
A more polished series of articles on this topic is forthcoming. Stay tuned.
-
 @ 5c26ee8b:a4d229aa
2025-04-14 16:31:49
@ 5c26ee8b:a4d229aa
2025-04-14 16:31:4910:25 Yunus
وَاللَّهُ يَدْعُو إِلَىٰ دَارِ السَّلَامِ وَيَهْدِي مَنْ يَشَاءُ إِلَىٰ صِرَاطٍ مُسْتَقِيمٍ
And Allah invites to the Home of Peace and guides whom He wills to a straight path.
6:125 Al-An'aam
فَمَنْ يُرِدِ اللَّهُ أَنْ يَهْدِيَهُ يَشْرَحْ صَدْرَهُ لِلْإِسْلَامِ ۖ وَمَنْ يُرِدْ أَنْ يُضِلَّهُ يَجْعَلْ صَدْرَهُ ضَيِّقًا حَرَجًا كَأَنَّمَا يَصَّعَّدُ فِي السَّمَاءِ ۚ كَذَٰلِكَ يَجْعَلُ اللَّهُ الرِّجْسَ عَلَى الَّذِينَ لَا يُؤْمِنُونَ
So whoever Allah wants to guide - He expands his breast to [contain] Islam; and whoever He wants to misguide - He makes his breast tight and constricted as though he were climbing into the sky. Thus Allah places defilement upon those who do not believe.
Allah is one of the Islamic names of God; the creator of everything. Not associating with God, Allah, any other and worshipping him alone is one of the first known fact in Islam.
- Al-Ikhlaas قُلْ هُوَ اللَّهُ أَحَدٌ Say, "He is Allah, [who is] One, اللَّهُ الصَّمَدُ Allah, the Eternal Refuge. لَمْ يَلِدْ وَلَمْ يُولَدْ He neither begets nor is born, وَلَمْ يَكُنْ لَهُ كُفُوًا أَحَدٌ Nor is there to Him any equivalent."
The Quran, the Islamic holly book and the guidance for mankind, was delivered more than 1400 years ago through the Angel Gabriel to prophet Mohamed peace be upon, however little is known about Islam despite living in a so called intellectual era.
The first word that was delivered was, “Read” in the first verse of surah Al-Alaq.
96:1 Al-Alaq
اقْرَأْ بِاسْمِ رَبِّكَ الَّذِي خَلَقَ
Read, in the name of your Lord who created -
The Quran, words of God (Allah), was delivered in Arabic and it is one of its miracles.
39:28 Az-Zumar
قُرْآنًا عَرَبِيًّا غَيْرَ ذِي عِوَجٍ لَعَلَّهُمْ يَتَّقُونَ
[It is] an Arabic Qur'an, without any distortion that they might become righteous.
18:109 Al-Kahf
قُلْ لَوْ كَانَ الْبَحْرُ مِدَادًا لِكَلِمَاتِ رَبِّي لَنَفِدَ الْبَحْرُ قَبْلَ أَنْ تَنْفَدَ كَلِمَاتُ رَبِّي وَلَوْ جِئْنَا بِمِثْلِهِ مَدَدًا
Say, "If the sea were ink for [writing] the words of my Lord, the sea would be exhausted before the words of my Lord were exhausted, even if We brought the like of it as a supplement."
17:88 Al-Israa
قُلْ لَئِنِ اجْتَمَعَتِ الْإِنْسُ وَالْجِنُّ عَلَىٰ أَنْ يَأْتُوا بِمِثْلِ هَٰذَا الْقُرْآنِ لَا يَأْتُونَ بِمِثْلِهِ وَلَوْ كَانَ بَعْضُهُمْ لِبَعْضٍ ظَهِيرًا
Say, "If mankind and the jinn gathered in order to produce the like of this Qur'an, they could not produce the like of it, even if they were to each other assistants."
17:89 Al-Israa
وَلَقَدْ صَرَّفْنَا لِلنَّاسِ فِي هَٰذَا الْقُرْآنِ مِنْ كُلِّ مَثَلٍ فَأَبَىٰ أَكْثَرُ النَّاسِ إِلَّا كُفُورًا
And We have certainly diversified for the people in this Qur'an from every [kind] of example, but most of the people refused [anything] except disbelief.
Through the wards of God in the Quran a lot can be known about Him and in the following verse some descriptions about Him.
2:255 Al-Baqara
اللَّهُ لَا إِلَٰهَ إِلَّا هُوَ الْحَيُّ الْقَيُّومُ ۚ لَا تَأْخُذُهُ سِنَةٌ وَلَا نَوْمٌ ۚ لَهُ مَا فِي السَّمَاوَاتِ وَمَا فِي الْأَرْضِ ۗ مَنْ ذَا الَّذِي يَشْفَعُ عِنْدَهُ إِلَّا بِإِذْنِهِ ۚ يَعْلَمُ مَا بَيْنَ أَيْدِيهِمْ وَمَا خَلْفَهُمْ ۖ وَلَا يُحِيطُونَ بِشَيْءٍ مِنْ عِلْمِهِ إِلَّا بِمَا شَاءَ ۚ وَسِعَ كُرْسِيُّهُ السَّمَاوَاتِ وَالْأَرْضَ ۖ وَلَا يَئُودُهُ حِفْظُهُمَا ۚ وَهُوَ الْعَلِيُّ الْعَظِيمُ
Allah - there is no deity except Him, the Ever-Living, the Sustainer of [all] existence. Neither drowsiness overtakes Him nor sleep. To Him belongs whatever is in the heavens and whatever is on the earth. Who is it that can intercede with Him except by His permission? He knows what is [presently] before them and what will be after them, and they encompass not a thing of His knowledge except for what He wills. His Kursi extends over the heavens and the earth, and their preservation tires Him not. And He is the Most High, the Most Great.
Seeing God has been a curiosity of prophets themselves and in the following examples of what happened when prophet Moses, peace be upon him, or his people asked so.
7:143 Al-A'raaf
وَلَمَّا جَاءَ مُوسَىٰ لِمِيقَاتِنَا وَكَلَّمَهُ رَبُّهُ قَالَ رَبِّ أَرِنِي أَنْظُرْ إِلَيْكَ ۚ قَالَ لَنْ تَرَانِي وَلَٰكِنِ انْظُرْ إِلَى الْجَبَلِ فَإِنِ اسْتَقَرَّ مَكَانَهُ فَسَوْفَ تَرَانِي ۚ فَلَمَّا تَجَلَّىٰ رَبُّهُ لِلْجَبَلِ جَعَلَهُ دَكًّا وَخَرَّ مُوسَىٰ صَعِقًا ۚ فَلَمَّا أَفَاقَ قَالَ سُبْحَانَكَ تُبْتُ إِلَيْكَ وَأَنَا أَوَّلُ الْمُؤْمِنِينَ
And when Moses arrived at Our appointed time and his Lord spoke to him, he said, "My Lord, show me [Yourself] that I may look at You." [Allah] said, "You will not see Me, but look at the mountain; if it should remain in place, then you will see Me." But when his Lord appeared to the mountain, He rendered it level, and Moses fell unconscious. And when he awoke, he said, "Exalted are You! I have repented to You, and I am the first of the believers."
2:55 Al-Baqara
وَإِذْ قُلْتُمْ يَا مُوسَىٰ لَنْ نُؤْمِنَ لَكَ حَتَّىٰ نَرَى اللَّهَ جَهْرَةً فَأَخَذَتْكُمُ الصَّاعِقَةُ وَأَنْتُمْ تَنْظُرُونَ
And [recall] when you said, "O Moses, we will never believe you until we see Allah outright"; so the thunderbolt took you while you were looking on.
2:56 Al-Baqara
ثُمَّ بَعَثْنَاكُمْ مِنْ بَعْدِ مَوْتِكُمْ لَعَلَّكُمْ تَشْكُرُونَ
Then We revived you after your death that perhaps you would be grateful.
In fact eyesights can’t reach God as in the following verses 6:102 Al-An'aam
ذَٰلِكُمُ اللَّهُ رَبُّكُمْ ۖ لَا إِلَٰهَ إِلَّا هُوَ ۖ خَالِقُ كُلِّ شَيْءٍ فَاعْبُدُوهُ ۚ وَهُوَ عَلَىٰ كُلِّ شَيْءٍ وَكِيلٌ
That is Allah, your Lord; there is no deity except Him, the Creator of all things, so worship Him. And He is Disposer of all things.
6:103 Al-An'aam
لَا تُدْرِكُهُ الْأَبْصَارُ وَهُوَ يُدْرِكُ الْأَبْصَارَ ۖ وَهُوَ اللَّطِيفُ الْخَبِيرُ
Eyesights (or visions) do not reach (or perceive him) Him, but He reaches (or perceives) [all] eyesights (visions); and He is the Subtle, the Acquainted.
6:104 Al-An'aam
قَدْ جَاءَكُمْ بَصَائِرُ مِنْ رَبِّكُمْ ۖ فَمَنْ أَبْصَرَ فَلِنَفْسِهِ ۖ وَمَنْ عَمِيَ فَعَلَيْهَا ۚ وَمَا أَنَا عَلَيْكُمْ بِحَفِيظٍ
There has come to you eyesights (or enlightenments) from your Lord. So whoever will see does so for [the benefit of] his soul, and whoever is blind [does harm] against it. And [say], "I am not controlling (or a guardian) over you."
42:11 Ash-Shura
فَاطِرُ السَّمَاوَاتِ وَالْأَرْضِ ۚ جَعَلَ لَكُمْ مِنْ أَنْفُسِكُمْ أَزْوَاجًا وَمِنَ الْأَنْعَامِ أَزْوَاجًا ۖ يَذْرَؤُكُمْ فِيهِ ۚ لَيْسَ كَمِثْلِهِ شَيْءٌ ۖ وَهُوَ السَّمِيعُ الْبَصِيرُ
[He is] Creator of the heavens and the earth. He has made for you from yourselves, mates, and among the cattle, mates; He multiplies you thereby. There is nothing like Him, and He is the Hearing, the Seeing.
Another name of God is the Truth and the Islam is the religion of truth and prophet Mohamed peace be upon him was chosen to invite the people to Islam.
61:7 As-Saff
وَمَنْ أَظْلَمُ مِمَّنِ افْتَرَىٰ عَلَى اللَّهِ الْكَذِبَ وَهُوَ يُدْعَىٰ إِلَى الْإِسْلَامِ ۚ وَاللَّهُ لَا يَهْدِي الْقَوْمَ الظَّالِمِينَ
And who is more unjust than one who invents about Allah untruth while he is being invited to Islam. And Allah does not guide the wrongdoing people.
61:8 As-Saff
يُرِيدُونَ لِيُطْفِئُوا نُورَ اللَّهِ بِأَفْوَاهِهِمْ وَاللَّهُ مُتِمُّ نُورِهِ وَلَوْ كَرِهَ الْكَافِرُونَ
They want to extinguish the light of Allah with their mouths, but Allah will perfect His light, although the disbelievers dislike it.
61:9 As-Saff
هُوَ الَّذِي أَرْسَلَ رَسُولَهُ بِالْهُدَىٰ وَدِينِ الْحَقِّ لِيُظْهِرَهُ عَلَى الدِّينِ كُلِّهِ وَلَوْ كَرِهَ الْمُشْرِكُونَ
It is He who sent His Messenger with guidance and the religion of truth to manifest it over all religion, although those who associate others with Allah dislike it.
Humans were given a trust, it’s to populate the earth while having the ability to choose between right and wrong.
33:72 Al-Ahzaab
إِنَّا عَرَضْنَا الْأَمَانَةَ عَلَى السَّمَاوَاتِ وَالْأَرْضِ وَالْجِبَالِ فَأَبَيْنَ أَنْ يَحْمِلْنَهَا وَأَشْفَقْنَ مِنْهَا وَحَمَلَهَا الْإِنْسَانُ ۖ إِنَّهُ كَانَ ظَلُومًا جَهُولًا
Indeed, we offered the Trust to the heavens and the earth and the mountains, and they declined to bear it and feared it; but man [undertook to] bear it. Indeed, he was unjust and ignorant.
Although our souls testified before the creation that God, Allah is our creator, he sent messengers and books to guide us.
7:172 Al-A'raaf
وَإِذْ أَخَذَ رَبُّكَ مِنْ بَنِي آدَمَ مِنْ ظُهُورِهِمْ ذُرِّيَّتَهُمْ وَأَشْهَدَهُمْ عَلَىٰ أَنْفُسِهِمْ أَلَسْتُ بِرَبِّكُمْ ۖ قَالُوا بَلَىٰ ۛ شَهِدْنَا ۛ أَنْ تَقُولُوا يَوْمَ الْقِيَامَةِ إِنَّا كُنَّا عَنْ هَٰذَا غَافِلِينَ
And [mention] when your Lord took from the children of Adam - from their loins - their descendants and made them testify of themselves, [saying to them], "Am I not your Lord?" They said, "Yes, we have testified." [This] - lest you should say on the day of Resurrection, "Indeed, we were of this unaware."
God likes that who believes in him submits to him willingly. The heavens and the earth, known to have consciousness in Islam submitted to him before us.
41:9 Fussilat
۞ قُلْ أَئِنَّكُمْ لَتَكْفُرُونَ بِالَّذِي خَلَقَ الْأَرْضَ فِي يَوْمَيْنِ وَتَجْعَلُونَ لَهُ أَنْدَادًا ۚ ذَٰلِكَ رَبُّ الْعَالَمِينَ
Say, "Do you indeed disbelieve in He who created the earth in two days and attribute to Him equals? That is the Lord of the worlds."
41:10 Fussilat
وَجَعَلَ فِيهَا رَوَاسِيَ مِنْ فَوْقِهَا وَبَارَكَ فِيهَا وَقَدَّرَ فِيهَا أَقْوَاتَهَا فِي أَرْبَعَةِ أَيَّامٍ سَوَاءً لِلسَّائِلِينَ
And He placed on the earth firmly set mountains over its surface, and He blessed it and determined therein its [creatures'] sustenance in four days without distinction - for [the information] of those who ask.
41:11 Fussilat
ثُمَّ اسْتَوَىٰ إِلَى السَّمَاءِ وَهِيَ دُخَانٌ فَقَالَ لَهَا وَلِلْأَرْضِ ائْتِيَا طَوْعًا أَوْ كَرْهًا قَالَتَا أَتَيْنَا طَائِعِينَ
Then He directed Himself to the heaven while it was smoke and said to it and to the earth, "Come, willingly or by compulsion", they said, "We came willingly."
40:57 Al-Ghaafir
لَخَلْقُ السَّمَاوَاتِ وَالْأَرْضِ أَكْبَرُ مِنْ خَلْقِ النَّاسِ وَلَٰكِنَّ أَكْثَرَ النَّاسِ لَا يَعْلَمُونَ
The creation of the heavens and earth is greater than the creation of mankind, but most of the people do not know.
It’s important to know what’s God asking people to do while submitting to him as mentioned in the following verses.
Surah Al-Israa: Verse 22: لَا تَجْعَلْ مَعَ اللَّهِ إِلَٰهًا آخَرَ فَتَقْعُدَ مَذْمُومًا مَخْذُولًا Set not up with Allah any other ilah (god), (O man)! (This verse is addressed to Prophet Muhammad SAW, but its implication is general to all mankind), or you will sit down reproved, forsaken (in the Hell-fire). Verse 23: ۞ وَقَضَىٰ رَبُّكَ أَلَّا تَعْبُدُوا إِلَّا إِيَّاهُ وَبِالْوَالِدَيْنِ إِحْسَانًا ۚ إِمَّا يَبْلُغَنَّ عِنْدَكَ الْكِبَرَ أَحَدُهُمَا أَوْ كِلَاهُمَا فَلَا تَقُلْ لَهُمَا أُفٍّ وَلَا تَنْهَرْهُمَا وَقُلْ لَهُمَا قَوْلًا كَرِيمًا And your Lord has decreed that you worship none but Him. And that you be dutiful to your parents. If one of them or both of them attain old age in your life, don’t say to them a word of disrespect, or shout at them but address them in terms of honour. Verse 24: وَاخْفِضْ لَهُمَا جَنَاحَ الذُّلِّ مِنَ الرَّحْمَةِ وَقُلْ رَبِّ ارْحَمْهُمَا كَمَا رَبَّيَانِي صَغِيرًا And lower unto them the wing of submission and humility through mercy, and say: "My Lord! Bestow on them Your Mercy as they did bring me up when I was small." Verse 25: رَبُّكُمْ أَعْلَمُ بِمَا فِي نُفُوسِكُمْ ۚ إِنْ تَكُونُوا صَالِحِينَ فَإِنَّهُ كَانَ لِلْأَوَّابِينَ غَفُورًا Your Lord knows best what is in your inner-selves. If you are righteous, then, verily, He is Ever Most Forgiving to those who turn unto Him again and again in obedience, and in repentance. Verse 26: وَآتِ ذَا الْقُرْبَىٰ حَقَّهُ وَالْمِسْكِينَ وَابْنَ السَّبِيلِ وَلَا تُبَذِّرْ تَبْذِيرًا And give to the kindred his due and to the Miskin (poor) and to the wayfarer. But spend not wastefully (your wealth) in the manner of a spendthrift. Verse 27: إِنَّ الْمُبَذِّرِينَ كَانُوا إِخْوَانَ الشَّيَاطِينِ ۖ وَكَانَ الشَّيْطَانُ لِرَبِّهِ كَفُورًا Verily, spendthrifts are brothers of the Shayatin (devils), and the Shaitan (Devil - Satan) is ever ungrateful to his Lord. Verse 28: وَإِمَّا تُعْرِضَنَّ عَنْهُمُ ابْتِغَاءَ رَحْمَةٍ مِنْ رَبِّكَ تَرْجُوهَا فَقُلْ لَهُمْ قَوْلًا مَيْسُورًا
And if you turn away from them (kindred, poor, wayfarer, etc. whom We have ordered you to give their rights, but if you have no money at the time they ask you for it) and you are awaiting a mercy from your Lord for which you hope, then, speak unto them a soft kind word (i.e. Allah will give me and I shall give you). Verse 29: وَلَا تَجْعَلْ يَدَكَ مَغْلُولَةً إِلَىٰ عُنُقِكَ وَلَا تَبْسُطْهَا كُلَّ الْبَسْطِ فَتَقْعُدَ مَلُومًا مَحْسُورًا And let not your hand be tied (like a miser) to your neck, nor stretch it forth to its utmost reach (like a spendthrift), so that you become blameworthy and in severe poverty. Verse 30: إِنَّ رَبَّكَ يَبْسُطُ الرِّزْقَ لِمَنْ يَشَاءُ وَيَقْدِرُ ۚ إِنَّهُ كَانَ بِعِبَادِهِ خَبِيرًا بَصِيرًا Truly, your Lord enlarges the provision for whom He wills and straitens (for whom He wills). Verily, He is Ever All-Knower, All-Seer of His slaves (servants; mankind created by God). Verse 31: وَلَا تَقْتُلُوا أَوْلَادَكُمْ خَشْيَةَ إِمْلَاقٍ ۖ نَحْنُ نَرْزُقُهُمْ وَإِيَّاكُمْ ۚ إِنَّ قَتْلَهُمْ كَانَ خِطْئًا كَبِيرًا And kill not your children for fear of poverty. We provide for them and for you. Surely, the killing of them is a great sin. Verse 32: وَلَا تَقْرَبُوا الزِّنَا ۖ إِنَّهُ كَانَ فَاحِشَةً وَسَاءَ سَبِيلًا And don’t come near to the unlawful sexual intercourse. Verily, it is a Fahishah (a great sin), and an evil way (that leads one to Hell unless Allah forgives him). Verse 33: وَلَا تَقْتُلُوا النَّفْسَ الَّتِي حَرَّمَ اللَّهُ إِلَّا بِالْحَقِّ ۗ وَمَنْ قُتِلَ مَظْلُومًا فَقَدْ جَعَلْنَا لِوَلِيِّهِ سُلْطَانًا فَلَا يُسْرِفْ فِي الْقَتْلِ ۖ إِنَّهُ كَانَ مَنْصُورًا And do not kill anyone that Allah has forbidden, except for a just cause. And whoever is killed (intentionally with hostility and oppression and not by mistake), We have given his heir the authority [(to demand Qisas, Law of Equality in punishment or to forgive, or to take Diya (blood money)]. But do not kill excessively (exceed limits in the matter of taking life). Verily, he is victorious. Verse 34: وَلَا تَقْرَبُوا مَالَ الْيَتِيمِ إِلَّا بِالَّتِي هِيَ أَحْسَنُ حَتَّىٰ يَبْلُغَ أَشُدَّهُ ۚ وَأَوْفُوا بِالْعَهْدِ ۖ إِنَّ الْعَهْدَ كَانَ مَسْئُولًا And don’t come near to the orphan's property except to improve it, until he attains the age of full strength. And fulfil (every) covenant. Verily! the covenant, will be questioned about. Verse 35: وَأَوْفُوا الْكَيْلَ إِذَا كِلْتُمْ وَزِنُوا بِالْقِسْطَاسِ الْمُسْتَقِيمِ ۚ ذَٰلِكَ خَيْرٌ وَأَحْسَنُ تَأْوِيلًا And give full measure when you measure, and weigh with a balance that is straight. That is good (advantageous) and better in the end. Verse 36: وَلَا تَقْفُ مَا لَيْسَ لَكَ بِهِ عِلْمٌ ۚ إِنَّ السَّمْعَ وَالْبَصَرَ وَالْفُؤَادَ كُلُّ أُولَٰئِكَ كَانَ عَنْهُ مَسْئُولًا And don’t pursue (i.e., do not say, or do not or witness not, etc.) what you have no knowledge of. Verily! The hearing, and the sight, and the heart, of each of those you will be questioned (by Allah). Verse 37: وَلَا تَمْشِ فِي الْأَرْضِ مَرَحًا ۖ إِنَّكَ لَنْ تَخْرِقَ الْأَرْضَ وَلَنْ تَبْلُغَ الْجِبَالَ طُولًا And walk not on the earth with conceit and arrogance. Verily, you can’t break the earth, nor reach the mountains in height. Verse 38: كُلُّ ذَٰلِكَ كَانَ سَيِّئُهُ عِنْدَ رَبِّكَ مَكْرُوهًا All the bad aspects of these (the above mentioned things) are hateful to your Lord. Verse 39: ذَٰلِكَ مِمَّا أَوْحَىٰ إِلَيْكَ رَبُّكَ مِنَ الْحِكْمَةِ ۗ وَلَا تَجْعَلْ مَعَ اللَّهِ إِلَٰهًا آخَرَ فَتُلْقَىٰ فِي جَهَنَّمَ مَلُومًا مَدْحُورًا This is (part) of Al-Hikmah (wisdom, good manners and high character, etc.) that your Lord has inspired to you. And set not up with Allah any other god lest you should be thrown into Hell, blameworthy and rejected, (from Allah's Mercy). Verse 40: أَفَأَصْفَاكُمْ رَبُّكُمْ بِالْبَنِينَ وَاتَّخَذَ مِنَ الْمَلَائِكَةِ إِنَاثًا ۚ إِنَّكُمْ لَتَقُولُونَ قَوْلًا عَظِيمًا Has then your Lord (O pagans of Makkah) preferred for you sons, and taken for Himself from among the angels daughters (Angels don’t have a gender and it’s wrong to refer to them as females). Verily! You utter an awful saying, indeed. Verse 41: وَلَقَدْ صَرَّفْنَا فِي هَٰذَا الْقُرْآنِ لِيَذَّكَّرُوا وَمَا يَزِيدُهُمْ إِلَّا نُفُورًا And surely, We have explained [Our Promises, Warnings and (set forth many) examples] in this Quran that they (the disbelievers) may take heed, but it increases them in aversion (from the truth). Verse 42: قُلْ لَوْ كَانَ مَعَهُ آلِهَةٌ كَمَا يَقُولُونَ إِذًا لَابْتَغَوْا إِلَىٰ ذِي الْعَرْشِ سَبِيلًا Say: "If there had been other gods along with Him as they say, then they would certainly have sought out a way to the Lord of the Throne (seeking His Pleasures and to be near to Him). Verse 43: سُبْحَانَهُ وَتَعَالَىٰ عَمَّا يَقُولُونَ عُلُوًّا كَبِيرًا Glorified and High be He! From 'Uluwan Kabira (the great falsehood) that they say!
Surah Al-Israa: Verse 53 وَقُلْ لِعِبَادِي يَقُولُوا الَّتِي هِيَ أَحْسَنُ ۚ إِنَّ الشَّيْطَانَ يَنْزَغُ بَيْنَهُمْ ۚ إِنَّ الشَّيْطَانَ كَانَ لِلْإِنْسَانِ عَدُوًّا مُبِينًا And say to My slaves (servants; mankind created by God) that they should (only) say the best words. (Because) Shaitan (Satan) verily, sows disagreements among them. Surely, Shaitan (Satan) is to man a plain enemy. Surah Al-Maaida Verse 90: يَا أَيُّهَا الَّذِينَ آمَنُوا إِنَّمَا الْخَمْرُ وَالْمَيْسِرُ وَالْأَنْصَابُ وَالْأَزْلَامُ رِجْسٌ مِنْ عَمَلِ الشَّيْطَانِ فَاجْتَنِبُوهُ لَعَلَّكُمْ تُفْلِحُونَ O you who believe! Intoxicants (all kinds of alcoholic drinks), gambling, Al-Ansab, and Al-Azlam (arrows for seeking luck or decision) are an abomination of Shaitan's (Satan) handiwork. So avoid (strictly all) that (abomination) in order that you may be successful. Verse 91: إِنَّمَا يُرِيدُ الشَّيْطَانُ أَنْ يُوقِعَ بَيْنَكُمُ الْعَدَاوَةَ وَالْبَغْضَاءَ فِي الْخَمْرِ وَالْمَيْسِرِ وَيَصُدَّكُمْ عَنْ ذِكْرِ اللَّهِ وَعَنِ الصَّلَاةِ ۖ فَهَلْ أَنْتُمْ مُنْتَهُونَ Shaitan (Satan) wants only to excite enmity and hatred between you with intoxicants (alcoholic drinks) and gambling, and hinder you from the remembrance of Allah (God) and from As-Salat (the prayer). So, will you not then abstain?
Surah Luqman: Verse 17: يَا بُنَيَّ أَقِمِ الصَّلَاةَ وَأْمُرْ بِالْمَعْرُوفِ وَانْهَ عَنِ الْمُنْكَرِ وَاصْبِرْ عَلَىٰ مَا أَصَابَكَ ۖ إِنَّ ذَٰلِكَ مِنْ عَزْمِ الْأُمُورِ "O my son (said Luqman, peace be upon him) ! Aqim-is-Salat (perform As-Salat; prayers), enjoin (people) for Al-Ma'ruf (all that is good), and forbid (people) from Al-Munkar (all that is evil and bad), and bear with patience whatever befall you. Verily! These are some of the important commandments ordered by Allah with no exemption. Verse 18: وَلَا تُصَعِّرْ خَدَّكَ لِلنَّاسِ وَلَا تَمْشِ فِي الْأَرْضِ مَرَحًا ۖ إِنَّ اللَّهَ لَا يُحِبُّ كُلَّ مُخْتَالٍ فَخُورٍ "And don’t turn your face away from men with pride, and don’t walk in insolence through the earth. Verily, Allah does not love each arrogant (prideful) boaster. Verse 19: وَاقْصِدْ فِي مَشْيِكَ وَاغْضُضْ مِنْ صَوْتِكَ ۚ إِنَّ أَنْكَرَ الْأَصْوَاتِ لَصَوْتُ الْحَمِيرِ "And be moderate (or show no insolence) in your walking, and lower your voice. Verily, the harshest of all voices is the voice of the donkey."
Surah Taa-Haa: Verse 131: وَلَا تَمُدَّنَّ عَيْنَيْكَ إِلَىٰ مَا مَتَّعْنَا بِهِ أَزْوَاجًا مِنْهُمْ زَهْرَةَ الْحَيَاةِ الدُّنْيَا لِنَفْتِنَهُمْ فِيهِ ۚ وَرِزْقُ رَبِّكَ خَيْرٌ وَأَبْقَىٰ And strain not your eyes in longing for the things We have given for enjoyment to various groups of them, the splendour of the life of this world that We may test them thereby. But the provision (good reward in the Hereafter) of your Lord is better and more lasting.
Surah Al-Hujuraat: Verse 11: يَا أَيُّهَا الَّذِينَ آمَنُوا لَا يَسْخَرْ قَوْمٌ مِنْ قَوْمٍ عَسَىٰ أَنْ يَكُونُوا خَيْرًا مِنْهُمْ وَلَا نِسَاءٌ مِنْ نِسَاءٍ عَسَىٰ أَنْ يَكُنَّ خَيْرًا مِنْهُنَّ ۖ وَلَا تَلْمِزُوا أَنْفُسَكُمْ وَلَا تَنَابَزُوا بِالْأَلْقَابِ ۖ بِئْسَ الِاسْمُ الْفُسُوقُ بَعْدَ الْإِيمَانِ ۚ وَمَنْ لَمْ يَتُبْ فَأُولَٰئِكَ هُمُ الظَّالِمُونَ O you who believe! Let not a group scoff at another group, it may be that the latter are better than the former; nor let (some) women scoff at other women, it may be that the latter are better than the former, nor defame one another, nor insult one another by nicknames. How bad is it, to insult one's brother after having Faith. And whosoever does not repent, then such are indeed Zalimun (unjust, wrong-doers, etc.). Verse 12: يَا أَيُّهَا الَّذِينَ آمَنُوا اجْتَنِبُوا كَثِيرًا مِنَ الظَّنِّ إِنَّ بَعْضَ الظَّنِّ إِثْمٌ ۖ وَلَا تَجَسَّسُوا وَلَا يَغْتَبْ بَعْضُكُمْ بَعْضًا ۚ أَيُحِبُّ أَحَدُكُمْ أَنْ يَأْكُلَ لَحْمَ أَخِيهِ مَيْتًا فَكَرِهْتُمُوهُ ۚ وَاتَّقُوا اللَّهَ ۚ إِنَّ اللَّهَ تَوَّابٌ رَحِيمٌ O you who believe! Avoid much suspicions, indeed some suspicions are sins. And spy not, neither backbite one another. Would one of you like to eat the flesh of his dead brother? You would hate it (so hate backbiting). And fear Allah. Verily, Allah is the One Who accepts repentance, Most Merciful.
Surah Al-Maaida: Verse 38: وَالسَّارِقُ وَالسَّارِقَةُ فَاقْطَعُوا أَيْدِيَهُمَا جَزَاءً بِمَا كَسَبَا نَكَالًا مِنَ اللَّهِ ۗ وَاللَّهُ عَزِيزٌ حَكِيمٌ Cut off (from the wrist joint) the (right) hand of the thief, male or female, as a recompense for that which they committed, a punishment by way of example from Allah. And Allah is All-Powerful, All-Wise. Verse 39: فَمَنْ تَابَ مِنْ بَعْدِ ظُلْمِهِ وَأَصْلَحَ فَإِنَّ اللَّهَ يَتُوبُ عَلَيْهِ ۗ إِنَّ اللَّهَ غَفُورٌ رَحِيمٌ But whosoever repents after his crime and does righteous good deeds, then verily, Allah (God) will pardon him (accept his repentance). Verily, Allah is Oft-Forgiving, Most Merciful.
Surah Aal-i-Imraan: Verse 130: يَا أَيُّهَا الَّذِينَ آمَنُوا لَا تَأْكُلُوا الرِّبَا أَضْعَافًا مُضَاعَفَةً ۖ وَاتَّقُوا اللَّهَ لَعَلَّكُمْ تُفْلِحُونَ O you who believe! Don’t eat Riba (usury) doubled and multiplied, but fear Allah that you may be successful.
Surah Al-Maaida: Verse 3: حُرِّمَتْ عَلَيْكُمُ الْمَيْتَةُ وَالدَّمُ وَلَحْمُ الْخِنْزِيرِ وَمَا أُهِلَّ لِغَيْرِ اللَّهِ بِهِ وَالْمُنْخَنِقَةُ وَالْمَوْقُوذَةُ وَالْمُتَرَدِّيَةُ وَالنَّطِيحَةُ وَمَا أَكَلَ السَّبُعُ إِلَّا مَا ذَكَّيْتُمْ وَمَا ذُبِحَ عَلَى النُّصُبِ وَأَنْ تَسْتَقْسِمُوا بِالْأَزْلَامِ ۚ ذَٰلِكُمْ فِسْقٌ ۗ الْيَوْمَ يَئِسَ الَّذِينَ كَفَرُوا مِنْ دِينِكُمْ فَلَا تَخْشَوْهُمْ وَاخْشَوْنِ ۚ الْيَوْمَ أَكْمَلْتُ لَكُمْ دِينَكُمْ وَأَتْمَمْتُ عَلَيْكُمْ نِعْمَتِي وَرَضِيتُ لَكُمُ الْإِسْلَامَ دِينًا ۚ فَمَنِ اضْطُرَّ فِي مَخْمَصَةٍ غَيْرَ مُتَجَانِفٍ لِإِثْمٍ ۙ فَإِنَّ اللَّهَ غَفُورٌ رَحِيمٌ Forbidden to you (for food) are: Al-Maytatah (the dead animals - cattle-beast not slaughtered), blood, the flesh of swine, and the meat of that which has been slaughtered as a sacrifice for others than Allah, or has been slaughtered for idols, etc., or on which Allah's Name has not been mentioned while slaughtering, and that which has been killed by strangling, or by a violent blow, or by a headlong fall, or by the goring of horns - and that which has been (partly) eaten by a wild animal - unless you are able to slaughter it (before its death) - and that which is sacrificed (slaughtered) on An-Nusub (stone altars). (Forbidden) also is to use arrows seeking luck or decision, (all) that is Fisqun (disobedience of Allah and sin). This day, those who disbelieved have given up all hope of your religion, so don’t fear them, but fear Me. This day, I have perfected your religion for you, completed My Favour upon you, and have chosen for you Islam as your religion. But who is forced by severe hunger, with no inclination to sin (such can eat these above-mentioned meats), then surely, Allah is Oft-Forgiving, Most Merciful.
Surah Al-Baqara: Verse 114: وَمَنْ أَظْلَمُ مِمَّنْ مَنَعَ مَسَاجِدَ اللَّهِ أَنْ يُذْكَرَ فِيهَا اسْمُهُ وَسَعَىٰ فِي خَرَابِهَا ۚ أُولَٰئِكَ مَا كَانَ لَهُمْ أَنْ يَدْخُلُوهَا إِلَّا خَائِفِينَ ۚ لَهُمْ فِي الدُّنْيَا خِزْيٌ وَلَهُمْ فِي الْآخِرَةِ عَذَابٌ عَظِيمٌ And who is more unjust than those who forbid that Allah's Name be glorified and mentioned much (i.e. prayers and invocations, etc.) in Allah's Mosques and strive for their ruin? It was not fitting that such should themselves enter them (Allah's Mosques) except in fear. For them there is disgrace in this world, and they will have a great torment in the Hereafter.
Surah Al-Baqara: Verse 110: وَأَقِيمُوا الصَّلَاةَ وَآتُوا الزَّكَاةَ ۚ وَمَا تُقَدِّمُوا لِأَنْفُسِكُمْ مِنْ خَيْرٍ تَجِدُوهُ عِنْدَ اللَّهِ ۗ إِنَّ اللَّهَ بِمَا تَعْمَلُونَ بَصِيرٌ And perform As-Salat (prayers), and give Zakat (compulsory charity that must be given every year), and whatever of good (deeds that Allah loves) you send forth for yourselves before you, you shall find it with Allah. Certainly, Allah is All-Seer of what you do.
Surah Al-A'raaf: Verse 31: ۞ يَا بَنِي آدَمَ خُذُوا زِينَتَكُمْ عِنْدَ كُلِّ مَسْجِدٍ وَكُلُوا وَاشْرَبُوا وَلَا تُسْرِفُوا ۚ إِنَّهُ لَا يُحِبُّ الْمُسْرِفِينَ
O Children of Adam! Take your adornment (by wearing your clean clothes), while praying and going round (the Tawaf of) the Ka'bah, and eat and drink but waste not by extravagance, certainly He (Allah) likes not Al-Musrifun (those who waste by extravagance). Verse 32: قُلْ مَنْ حَرَّمَ زِينَةَ اللَّهِ الَّتِي أَخْرَجَ لِعِبَادِهِ وَالطَّيِّبَاتِ مِنَ الرِّزْقِ ۚ قُلْ هِيَ لِلَّذِينَ آمَنُوا فِي الْحَيَاةِ الدُّنْيَا خَالِصَةً يَوْمَ الْقِيَامَةِ ۗ كَذَٰلِكَ نُفَصِّلُ الْآيَاتِ لِقَوْمٍ يَعْلَمُونَ Say: "Who has forbidden the adoration with clothes given by Allah, which He has produced for his slaves, and At-Taiyibat [all kinds of Halal (lawful) things] of food?" Say: "They are, in the life of this world, for those who believe, (and) exclusively for them (believers) on the Day of Resurrection (the disbelievers will not share them)." Thus We explain the Ayat (verses, Islamic laws) in detail for people who have knowledge. Verse 33: قُلْ إِنَّمَا حَرَّمَ رَبِّيَ الْفَوَاحِشَ مَا ظَهَرَ مِنْهَا وَمَا بَطَنَ وَالْإِثْمَ وَالْبَغْيَ بِغَيْرِ الْحَقِّ وَأَنْ تُشْرِكُوا بِاللَّهِ مَا لَمْ يُنَزِّلْ بِهِ سُلْطَانًا وَأَنْ تَقُولُوا عَلَى اللَّهِ مَا لَا تَعْلَمُونَ Say: "The things that my Lord has indeed forbidden are Al-Fawahish (great evil sins) whether committed openly or secretly, sins (of all kinds), unrighteous oppression, joining partners (in worship) with Allah for which He has given no authority, and saying things about Allah of which you have no knowledge." Verse 34: وَلِكُلِّ أُمَّةٍ أَجَلٌ ۖ فَإِذَا جَاءَ أَجَلُهُمْ لَا يَسْتَأْخِرُونَ سَاعَةً ۖ وَلَا يَسْتَقْدِمُونَ And every nation has its appointed term; when their term is reached, neither can they delay it nor can they advance it an hour (or a moment). Verse 35: يَا بَنِي آدَمَ إِمَّا يَأْتِيَنَّكُمْ رُسُلٌ مِنْكُمْ يَقُصُّونَ عَلَيْكُمْ آيَاتِي ۙ فَمَنِ اتَّقَىٰ وَأَصْلَحَ فَلَا خَوْفٌ عَلَيْهِمْ وَلَا هُمْ يَحْزَنُونَ O Children of Adam! If there come to you Messengers from amongst you, reciting to you, My Verses, then whosoever becomes pious and righteous, on them shall be no fear, nor shall they grieve. Verse 36: وَالَّذِينَ كَذَّبُوا بِآيَاتِنَا وَاسْتَكْبَرُوا عَنْهَا أُولَٰئِكَ أَصْحَابُ النَّارِ ۖ هُمْ فِيهَا خَالِدُونَ But those who reject Our Ayat (proofs, evidences, verses, lessons, signs, revelations, etc.) and treat them with arrogance, they are the dwellers of the (Hell) Fire, they will abide therein forever. Verse 37: فَمَنْ أَظْلَمُ مِمَّنِ افْتَرَىٰ عَلَى اللَّهِ كَذِبًا أَوْ كَذَّبَ بِآيَاتِهِ ۚ أُولَٰئِكَ يَنَالُهُمْ نَصِيبُهُمْ مِنَ الْكِتَابِ ۖ حَتَّىٰ إِذَا جَاءَتْهُمْ رُسُلُنَا يَتَوَفَّوْنَهُمْ قَالُوا أَيْنَ مَا كُنْتُمْ تَدْعُونَ مِنْ دُونِ اللَّهِ ۖ قَالُوا ضَلُّوا عَنَّا وَشَهِدُوا عَلَىٰ أَنْفُسِهِمْ أَنَّهُمْ كَانُوا كَافِرِينَ Who is more unjust than one who invents a lie against Allah or rejects His Ayat (proofs, evidences, verses, lessons, signs, revelations, etc.)? For such their appointed portion (good things of this worldly life and their period of stay therein) will reach them from the Book (of Decrees) until, when Our Messengers (the angel of death and his assistants) come to them to take their souls, they (the angels) will say: "Where are those whom you used to invoke and worship besides Allah," they will reply, "They have vanished and deserted us." And they will bear witness against themselves, that they were disbelievers. Verse 38: قَالَ ادْخُلُوا فِي أُمَمٍ قَدْ خَلَتْ مِنْ قَبْلِكُمْ مِنَ الْجِنِّ وَالْإِنْسِ فِي النَّارِ ۖ كُلَّمَا دَخَلَتْ أُمَّةٌ لَعَنَتْ أُخْتَهَا ۖ حَتَّىٰ إِذَا ادَّارَكُوا فِيهَا جَمِيعًا قَالَتْ أُخْرَاهُمْ لِأُولَاهُمْ رَبَّنَا هَٰؤُلَاءِ أَضَلُّونَا فَآتِهِمْ عَذَابًا ضِعْفًا مِنَ النَّارِ ۖ قَالَ لِكُلٍّ ضِعْفٌ وَلَٰكِنْ لَا تَعْلَمُونَ (Allah) will say: "Enter you in the company of nations who passed away before you, of men and jinns, into the Fire." Every time a new nation enters, it curses its sister nation (that went before), until they will be gathered all together in the Fire. The last of them will say to the first of them: "Our Lord! These misled us, so give them a double torment of the Fire." He will say: "For each one there is double (torment), but you don’t know." Verse 39: وَقَالَتْ أُولَاهُمْ لِأُخْرَاهُمْ فَمَا كَانَ لَكُمْ عَلَيْنَا مِنْ فَضْلٍ فَذُوقُوا الْعَذَابَ بِمَا كُنْتُمْ تَكْسِبُونَ The first of them will say to the last of them: "You were not better than us, so taste the torment for what you used to earn." Verse 40: إِنَّ الَّذِينَ كَذَّبُوا بِآيَاتِنَا وَاسْتَكْبَرُوا عَنْهَا لَا تُفَتَّحُ لَهُمْ أَبْوَابُ السَّمَاءِ وَلَا يَدْخُلُونَ الْجَنَّةَ حَتَّىٰ يَلِجَ الْجَمَلُ فِي سَمِّ الْخِيَاطِ ۚ وَكَذَٰلِكَ نَجْزِي الْمُجْرِمِينَ Verily, those who belie Our Ayat (proofs, evidences, verses, lessons, signs, revelations, etc.) and are pridefully arrogant towards them (proofs, verses, signs, etc.), for them the gates of heaven will not be opened (to accept and answer their supplications and prayers), and they will not enter Paradise until the camel goes through the eye of the needle (which is impossible). Thus do We recompense the Mujrimun (criminals, sinners, etc.). Verse 41: لَهُمْ مِنْ جَهَنَّمَ مِهَادٌ وَمِنْ فَوْقِهِمْ غَوَاشٍ ۚ وَكَذَٰلِكَ نَجْزِي الظَّالِمِينَ Theirs will be a bed of Hell (Fire), and over them coverings (of Hell-fire). Thus We recompense the Zalimun (unjust and wrong-doers, etc.).
An-Nahl Verse 94: وَلَا تَتَّخِذُوا أَيْمَانَكُمْ دَخَلًا بَيْنَكُمْ فَتَزِلَّ قَدَمٌ بَعْدَ ثُبُوتِهَا وَتَذُوقُوا السُّوءَ بِمَا صَدَدْتُمْ عَنْ سَبِيلِ اللَّهِ ۖ وَلَكُمْ عَذَابٌ عَظِيمٌ And don’t make your oaths, a means of deception among yourselves, lest a foot may slip after being firmly planted, and you may have to taste the evil (punishment in this world) of having hindered (men) from the Path of Allah (i.e. Belief in the Oneness of Allah and His Messenger, Muhammad SAW, fighting in the cause of Allah), and yours will be a great torment (i.e. the Fire of Hell in the Hereafter). Verse 95: وَلَا تَشْتَرُوا بِعَهْدِ اللَّهِ ثَمَنًا قَلِيلًا ۚ إِنَّمَا عِنْدَ اللَّهِ هُوَ خَيْرٌ لَكُمْ إِنْ كُنْتُمْ تَعْلَمُونَ
And purchase not a small gain at the cost of Allah's Covenant. Verily! What is with Allah is better for you if you did but know.
A lot of people turn away from God, Allah, because of fearing not to be forgiven.
4:116 An-Nisaa
إِنَّ اللَّهَ لَا يَغْفِرُ أَنْ يُشْرَكَ بِهِ وَيَغْفِرُ مَا دُونَ ذَٰلِكَ لِمَنْ يَشَاءُ ۚ وَمَنْ يُشْرِكْ بِاللَّهِ فَقَدْ ضَلَّ ضَلَالًا بَعِيدًا
Indeed, Allah does not forgive association with Him, but He forgives other than that for whom He wills. And he who associates others with Allah has certainly gone far astray.
39:53 Az-Zumar
۞ قُلْ يَا عِبَادِيَ الَّذِينَ أَسْرَفُوا عَلَىٰ أَنْفُسِهِمْ لَا تَقْنَطُوا مِنْ رَحْمَةِ اللَّهِ ۚ إِنَّ اللَّهَ يَغْفِرُ الذُّنُوبَ جَمِيعًا ۚ إِنَّهُ هُوَ الْغَفُورُ الرَّحِيمُ
Say, "O My servants who have transgressed against themselves [by sinning], do not despair of the mercy of Allah. Indeed, Allah forgives all sins. Indeed, it is He who is the Forgiving, the Merciful."
39:54 Az-Zumar
وَأَنِيبُوا إِلَىٰ رَبِّكُمْ وَأَسْلِمُوا لَهُ مِنْ قَبْلِ أَنْ يَأْتِيَكُمُ الْعَذَابُ ثُمَّ لَا تُنْصَرُونَ
And return [in repentance] to your Lord and submit to Him before the punishment comes upon you; then you will not be helped.
39:55 Az-Zumar
وَاتَّبِعُوا أَحْسَنَ مَا أُنْزِلَ إِلَيْكُمْ مِنْ رَبِّكُمْ مِنْ قَبْلِ أَنْ يَأْتِيَكُمُ الْعَذَابُ بَغْتَةً وَأَنْتُمْ لَا تَشْعُرُونَ
And follow the best of what was revealed to you from your Lord before the punishment comes upon you suddenly while you do not perceive,
39:56 Az-Zumar
أَنْ تَقُولَ نَفْسٌ يَا حَسْرَتَا عَلَىٰ مَا فَرَّطْتُ فِي جَنْبِ اللَّهِ وَإِنْ كُنْتُ لَمِنَ السَّاخِرِينَ
Lest a soul should say, "Oh [how great is] my regret over what I neglected in regard to Allah and that I was among the mockers."
39:57 Az-Zumar
أَوْ تَقُولَ لَوْ أَنَّ اللَّهَ هَدَانِي لَكُنْتُ مِنَ الْمُتَّقِينَ
Or [lest] it say, "If only Allah had guided me, I would have been among the righteous."
39:58 Az-Zumar
أَوْ تَقُولَ حِينَ تَرَى الْعَذَابَ لَوْ أَنَّ لِي كَرَّةً فَأَكُونَ مِنَ الْمُحْسِنِينَ
Or [lest] it say when it sees the punishment, "If only I had another turn so I could be among the doers of good."
39:59 Az-Zumar
بَلَىٰ قَدْ جَاءَتْكَ آيَاتِي فَكَذَّبْتَ بِهَا وَاسْتَكْبَرْتَ وَكُنْتَ مِنَ الْكَافِرِينَ
But yes, there had come to you My verses, but you denied them and were arrogant, and you were among the disbelievers.
39:60 Az-Zumar
وَيَوْمَ الْقِيَامَةِ تَرَى الَّذِينَ كَذَبُوا عَلَى اللَّهِ وُجُوهُهُمْ مُسْوَدَّةٌ ۚ أَلَيْسَ فِي جَهَنَّمَ مَثْوًى لِلْمُتَكَبِّرِينَ
And on the Day of Resurrection you will see those who lied about Allah [with] their faces blackened. Is there not in Hell a residence for the arrogant?
39:61 Az-Zumar
وَيُنَجِّي اللَّهُ الَّذِينَ اتَّقَوْا بِمَفَازَتِهِمْ لَا يَمَسُّهُمُ السُّوءُ وَلَا هُمْ يَحْزَنُونَ
And Allah will save those who feared Him by their attainment; no evil will touch them, nor will they grieve.
In Islam we believe in God’s messengers and his books, Torah and Gospel, however, some changes were brought by some people leading to disbelief in the oneness of God.
2:285 Al-Baqara
آمَنَ الرَّسُولُ بِمَا أُنْزِلَ إِلَيْهِ مِنْ رَبِّهِ وَالْمُؤْمِنُونَ ۚ كُلٌّ آمَنَ بِاللَّهِ وَمَلَائِكَتِهِ وَكُتُبِهِ وَرُسُلِهِ لَا نُفَرِّقُ بَيْنَ أَحَدٍ مِنْ رُسُلِهِ ۚ وَقَالُوا سَمِعْنَا وَأَطَعْنَا ۖ غُفْرَانَكَ رَبَّنَا وَإِلَيْكَ الْمَصِيرُ
The Messenger has believed in what was revealed to him from his Lord, and [so have] the believers. All of them have believed in Allah and His angels and His books and His messengers, [saying], "We make no distinction between any of His messengers." And they say, "We hear and we obey. [We seek] Your forgiveness, our Lord, and to You is the [final] destination."
2:286 Al-Baqara
لَا يُكَلِّفُ اللَّهُ نَفْسًا إِلَّا وُسْعَهَا ۚ لَهَا مَا كَسَبَتْ وَعَلَيْهَا مَا اكْتَسَبَتْ ۗ رَبَّنَا لَا تُؤَاخِذْنَا إِنْ نَسِينَا أَوْ أَخْطَأْنَا ۚ رَبَّنَا وَلَا تَحْمِلْ عَلَيْنَا إِصْرًا كَمَا حَمَلْتَهُ عَلَى الَّذِينَ مِنْ قَبْلِنَا ۚ رَبَّنَا وَلَا تُحَمِّلْنَا مَا لَا طَاقَةَ لَنَا بِهِ ۖ وَاعْفُ عَنَّا وَاغْفِرْ لَنَا وَارْحَمْنَا ۚ أَنْتَ مَوْلَانَا فَانْصُرْنَا عَلَى الْقَوْمِ الْكَافِرِينَ
Allah does not charge a soul except [with that within] its capacity. It will have [the consequence of] what [good] it has gained, and it will bear [the consequence of] what [evil] it has earned. "Our Lord, do not impose blame upon us if we have forgotten or erred. Our Lord, and lay not upon us a burden like that which You laid upon those before us. Our Lord, and burden us not with that which we have no ability to bear. And pardon us; and forgive us; and have mercy upon us. You are our protector, so give us victory over the disbelieving people."
4:163 An-Nisaa
۞ إِنَّا أَوْحَيْنَا إِلَيْكَ كَمَا أَوْحَيْنَا إِلَىٰ نُوحٍ وَالنَّبِيِّينَ مِنْ بَعْدِهِ ۚ وَأَوْحَيْنَا إِلَىٰ إِبْرَاهِيمَ وَإِسْمَاعِيلَ وَإِسْحَاقَ وَيَعْقُوبَ وَالْأَسْبَاطِ وَعِيسَىٰ وَأَيُّوبَ وَيُونُسَ وَهَارُونَ وَسُلَيْمَانَ ۚ وَآتَيْنَا دَاوُودَ زَبُورًا
Indeed, We have revealed to you, [O Muhammad], as We revealed to Noah and the prophets after him. And we revealed to Abraham, Ishmael, Isaac, Jacob, the Descendants, Jesus, Job, Jonah, Aaron, and Solomon, and to David We gave the book [of Psalms].
4:164 An-Nisaa
وَرُسُلًا قَدْ قَصَصْنَاهُمْ عَلَيْكَ مِنْ قَبْلُ وَرُسُلًا لَمْ نَقْصُصْهُمْ عَلَيْكَ ۚ وَكَلَّمَ اللَّهُ مُوسَىٰ تَكْلِيمًا
And [We sent] messengers about whom We have related [their stories] to you before and messengers about whom We have not related to you. And Allah spoke to Moses with [direct] speech.
4:165 An-Nisaa
رُسُلًا مُبَشِّرِينَ وَمُنْذِرِينَ لِئَلَّا يَكُونَ لِلنَّاسِ عَلَى اللَّهِ حُجَّةٌ بَعْدَ الرُّسُلِ ۚ وَكَانَ اللَّهُ عَزِيزًا حَكِيمًا
[We sent] messengers as bringers of good tidings and warners so that mankind will have no argument against Allah after the messengers. And ever is Allah Exalted in Might and Wise.
9:30 At-Tawba
وَقَالَتِ الْيَهُودُ عُزَيْرٌ ابْنُ اللَّهِ وَقَالَتِ النَّصَارَى الْمَسِيحُ ابْنُ اللَّهِ ۖ ذَٰلِكَ قَوْلُهُمْ بِأَفْوَاهِهِمْ ۖ يُضَاهِئُونَ قَوْلَ الَّذِينَ كَفَرُوا مِنْ قَبْلُ ۚ قَاتَلَهُمُ اللَّهُ ۚ أَنَّىٰ يُؤْفَكُونَ
The Jews say, "Ezra is the son of Allah "; and the Christians say, "The Messiah is the son of Allah." That is their statement from their mouths; they imitate the saying of those who disbelieved [before them]. May Allah destroy them; how are they deluded?
9:31 At-Tawba
اتَّخَذُوا أَحْبَارَهُمْ وَرُهْبَانَهُمْ أَرْبَابًا مِنْ دُونِ اللَّهِ وَالْمَسِيحَ ابْنَ مَرْيَمَ وَمَا أُمِرُوا إِلَّا لِيَعْبُدُوا إِلَٰهًا وَاحِدًا ۖ لَا إِلَٰهَ إِلَّا هُوَ ۚ سُبْحَانَهُ عَمَّا يُشْرِكُونَ
They have taken their scholars and monks as lords besides Allah, and [also] the Messiah, the son of Mary. And they were not commanded except to worship one God; there is no deity except Him. Exalted is He above whatever they associate with Him.
5:72 Al-Maaida
لَقَدْ كَفَرَ الَّذِينَ قَالُوا إِنَّ اللَّهَ هُوَ الْمَسِيحُ ابْنُ مَرْيَمَ ۖ وَقَالَ الْمَسِيحُ يَا بَنِي إِسْرَائِيلَ اعْبُدُوا اللَّهَ رَبِّي وَرَبَّكُمْ ۖ إِنَّهُ مَنْ يُشْرِكْ بِاللَّهِ فَقَدْ حَرَّمَ اللَّهُ عَلَيْهِ الْجَنَّةَ وَمَأْوَاهُ النَّارُ ۖ وَمَا لِلظَّالِمِينَ مِنْ أَنْصَارٍ
They have certainly disbelieved who say, "Allah is the Messiah, the son of Mary" while the Messiah has said, "O Children of Israel, worship Allah, my Lord and your Lord." Indeed, he who associates others with Allah - Allah has forbidden him Paradise, and his refuge is the Fire. And there are not for the wrongdoers any helpers.
5:73 Al-Maaida
لَقَدْ كَفَرَ الَّذِينَ قَالُوا إِنَّ اللَّهَ ثَالِثُ ثَلَاثَةٍ ۘ وَمَا مِنْ إِلَٰهٍ إِلَّا إِلَٰهٌ وَاحِدٌ ۚ وَإِنْ لَمْ يَنْتَهُوا عَمَّا يَقُولُونَ لَيَمَسَّنَّ الَّذِينَ كَفَرُوا مِنْهُمْ عَذَابٌ أَلِيمٌ
They have certainly disbelieved who say, "Allah is the third of three." And there is no god except one God. And if they do not desist from what they are saying, there will surely afflict the disbelievers among them a painful punishment.
5:74 Al-Maaida
أَفَلَا يَتُوبُونَ إِلَى اللَّهِ وَيَسْتَغْفِرُونَهُ ۚ وَاللَّهُ غَفُورٌ رَحِيمٌ
So will they not repent to Allah and seek His forgiveness? And Allah is Forgiving and Merciful.
5:75 Al-Maaida
مَا الْمَسِيحُ ابْنُ مَرْيَمَ إِلَّا رَسُولٌ قَدْ خَلَتْ مِنْ قَبْلِهِ الرُّسُلُ وَأُمُّهُ صِدِّيقَةٌ ۖ كَانَا يَأْكُلَانِ الطَّعَامَ ۗ انْظُرْ كَيْفَ نُبَيِّنُ لَهُمُ الْآيَاتِ ثُمَّ انْظُرْ أَنَّىٰ يُؤْفَكُونَ
The Messiah, son of Mary, was not but a messenger; [other] messengers have passed on before him. And his mother was a supporter of truth. They both used to eat food. Look how We make clear to them the signs; then look how they are deluded.
5:76 Al-Maaida
قُلْ أَتَعْبُدُونَ مِنْ دُونِ اللَّهِ مَا لَا يَمْلِكُ لَكُمْ ضَرًّا وَلَا نَفْعًا ۚ وَاللَّهُ هُوَ السَّمِيعُ الْعَلِيمُ
Say, "Do you worship besides Allah that which holds for you no [power of] harm or benefit while it is Allah who is the Hearing, the Knowing?"
5:77 Al-Maaida
قُلْ يَا أَهْلَ الْكِتَابِ لَا تَغْلُوا فِي دِينِكُمْ غَيْرَ الْحَقِّ وَلَا تَتَّبِعُوا أَهْوَاءَ قَوْمٍ قَدْ ضَلُّوا مِنْ قَبْلُ وَأَضَلُّوا كَثِيرًا وَضَلُّوا عَنْ سَوَاءِ السَّبِيلِ
Say, "O People of the Scripture (the books, Torah and Gospel), do not exceed limits in your religion beyond the truth and do not follow the inclinations of a people who had gone astray before and misled many and have strayed from the soundness of the way."
4:171 An-Nisaa
يَا أَهْلَ الْكِتَابِ لَا تَغْلُوا فِي دِينِكُمْ وَلَا تَقُولُوا عَلَى اللَّهِ إِلَّا الْحَقَّ ۚ إِنَّمَا الْمَسِيحُ عِيسَى ابْنُ مَرْيَمَ رَسُولُ اللَّهِ وَكَلِمَتُهُ أَلْقَاهَا إِلَىٰ مَرْيَمَ وَرُوحٌ مِنْهُ ۖ فَآمِنُوا بِاللَّهِ وَرُسُلِهِ ۖ وَلَا تَقُولُوا ثَلَاثَةٌ ۚ انْتَهُوا خَيْرًا لَكُمْ ۚ إِنَّمَا اللَّهُ إِلَٰهٌ وَاحِدٌ ۖ سُبْحَانَهُ أَنْ يَكُونَ لَهُ وَلَدٌ ۘ لَهُ مَا فِي السَّمَاوَاتِ وَمَا فِي الْأَرْضِ ۗ وَكَفَىٰ بِاللَّهِ وَكِيلًا
O People of the Scripture, do not commit excess in your religion or say about Allah except the truth. The Messiah, Jesus, the son of Mary, was but a messenger of Allah and His word which He directed to Mary and a soul [created at a command] from Him. So believe in Allah and His messengers. And do not say, "Three"; desist - it is better for you. Indeed, Allah is but one God. Exalted is He above having a son. To Him belongs whatever is in the heavens and whatever is on the earth. And sufficient is Allah as Disposer of affairs.
4:172 An-Nisaa
لَنْ يَسْتَنْكِفَ الْمَسِيحُ أَنْ يَكُونَ عَبْدًا لِلَّهِ وَلَا الْمَلَائِكَةُ الْمُقَرَّبُونَ ۚ وَمَنْ يَسْتَنْكِفْ عَنْ عِبَادَتِهِ وَيَسْتَكْبِرْ فَسَيَحْشُرُهُمْ إِلَيْهِ جَمِيعًا
Never would the Messiah disdain to be a servant of Allah, nor would the angels near [to Him]. And whoever disdains His worship and is arrogant - He will gather them to Himself all together.
And in the following Hadiths (sayings of prophet Mohamed peace be upon him) and verses what a practicing Muslim should do:
حَدَّثَنَا أَبُو الْيَمَانِ ، قَالَ: أَخْبَرَنَا شُعَيْبٌ ، عَنِ الزُّهْرِيِّ ، قَالَ: أَخْبَرَنِي أَبُو إِدْرِيسَ عَائِذُ اللَّهِ بْنُ عَبْدِ اللَّهِ ، أَنَّ عُبَادَةَ بْنَ الصَّامِتِ رَضِيَ اللَّهُ عَنْهُ، وَكَانَ شَهِدَ بَدْرًا وَهُوَ أَحَدُ النُّقَبَاءِ لَيْلَةَ الْعَقَبَةِ، أَنَّ رَسُولَ اللَّهِ صَلَّى اللَّهُ عَلَيْهِ وَسَلَّمَ، قَالَ وَحَوْلَهُ عِصَابَةٌ مِنْ أَصْحَابِهِ: بَايِعُونِي عَلَى أَنْ لَا تُشْرِكُوا بِاللَّهِ شَيْئًا، وَلَا تَسْرِقُوا، وَلَا تَزْنُوا، وَلَا تَقْتُلُوا أَوْلَادَكُمْ، وَلَا تَأْتُوا بِبُهْتَانٍ تَفْتَرُونَهُ بَيْنَ أَيْدِيكُمْ وَأَرْجُلِكُمْ، وَلَا تَعْصُوا فِي مَعْرُوفٍ، فَمَنْ وَفَى مِنْكُمْ فَأَجْرُهُ عَلَى اللَّهِ، وَمَنْ أَصَابَ مِنْ ذَلِكَ شَيْئًا فَعُوقِبَ فِي الدُّنْيَا فَهُوَ كَفَّارَةٌ لَهُ، وَمَنْ أَصَابَ مِنْ ذَلِكَ شَيْئًا ثُمَّ سَتَرَهُ اللَّهُ فَهُوَ إِلَى اللَّهِ إِنْ شَاءَ عَفَا عَنْهُ وَإِنْ شَاءَ عَاقَبَهُ، فَبَايَعْنَاهُ عَلَى ذَلِك.
Translation:Narrated Ubadah bin As-Samit (RA): who took part in the battle of Badr and was a Naqib (a person heading a group of six persons), on the night of Al-Aqabah pledge: Allahs Apostle ﷺ said while a group of his companions were around him, "Swear allegiance to me for: 1. Not to join anything in worship along with Allah. 2. Not to steal. 3. Not to commit illegal sexual intercourse. 4. Not to kill your children. 5. Not to accuse an innocent person (to spread such an accusation among people). 6. Not to be disobedient (when ordered) to do good deed". The Prophet ﷺ added: "Whoever among you fulfills his pledge will be rewarded by Allah. And whoever indulges in any one of them (except the ascription of partners to Allah) and gets the punishment in this world, that punishment will be an expiation for that sin. And if one indulges in any of them, and Allah conceals his sin, it is up to Him to forgive or punish him (in the Hereafter)". Ubadah bin As-Samit (RA) added: "So we swore allegiance for these." (points to Allahs Apostle) ﷺ.
حَدَّثَنَا عُبَيْدُ اللَّهِ بْنُ مُوسَى ، قَالَ: أَخْبَرَنَا حَنْظَلَةُ بْنُ أَبِي سُفْيَانَ ، عَنْ عِكْرِمَةَ بْنِ خَالِدٍ ، عَنِ ابْنِ عُمَرَ رَضِيَ اللَّهُ عَنْهُمَا، قَالَ: قَالَ رَسُولُ اللَّهِ صَلَّى اللَّهُ عَلَيْهِ وَسَلَّمَ: بُنِيَ الْإِسْلَامُ عَلَى خَمْسٍ، شَهَادَةِ أَنْ لَا إِلَهَ إِلَّا اللَّهُ وَأَنَّ مُحَمَّدًا رَسُولُ اللَّهِ، وَإِقَامِ الصَّلَاةِ، وَإِيتَاءِ الزَّكَاةِ، وَالْحَجِّ، وَصَوْمِ رَمَضَانَ. الحج لمن استطاع اليه سبيلا*
Translation:Narrated Ibn Umar (RA) : Allahs Apostle ﷺ said: Islam is based on (the following) five (principles): 1. To testify that none has the right to be worshipped but Allah and Muhammad ﷺ is Allahs Apostle. 2. To offer the (compulsory Salat) prayers dutifully and perfectly. 3. To pay Zakat (i.e. obligatory charity). 4. To perform Hajj. (i.e. Pilgrimage to Makkah only if the person is able to do so) 5. To observe fast during the month of Ramadan.
Also, in the following verses behaviours that must be adopted by practicing Muslims:
24:30 An-Noor
قُلْ لِلْمُؤْمِنِينَ يَغُضُّوا مِنْ أَبْصَارِهِمْ وَيَحْفَظُوا فُرُوجَهُمْ ۚ ذَٰلِكَ أَزْكَىٰ لَهُمْ ۗ إِنَّ اللَّهَ خَبِيرٌ بِمَا يَصْنَعُونَ
Tell the believing men to reduce [some] of their vision (lower their gazes) and guard their private parts. That is purer for them. Indeed, Allah is Acquainted with what they do.
24:31 An-Noor
وَقُلْ لِلْمُؤْمِنَاتِ يَغْضُضْنَ مِنْ أَبْصَارِهِنَّ وَيَحْفَظْنَ فُرُوجَهُنَّ وَلَا يُبْدِينَ زِينَتَهُنَّ إِلَّا مَا ظَهَرَ مِنْهَا ۖ وَلْيَضْرِبْنَ بِخُمُرِهِنَّ عَلَىٰ جُيُوبِهِنَّ ۖ وَلَا يُبْدِينَ زِينَتَهُنَّ إِلَّا لِبُعُولَتِهِنَّ أَوْ آبَائِهِنَّ أَوْ آبَاءِ بُعُولَتِهِنَّ أَوْ أَبْنَائِهِنَّ أَوْ أَبْنَاءِ بُعُولَتِهِنَّ أَوْ إِخْوَانِهِنَّ أَوْ بَنِي إِخْوَانِهِنَّ أَوْ بَنِي أَخَوَاتِهِنَّ أَوْ نِسَائِهِنَّ أَوْ مَا مَلَكَتْ أَيْمَانُهُنَّ أَوِ التَّابِعِينَ غَيْرِ أُولِي الْإِرْبَةِ مِنَ الرِّجَالِ أَوِ الطِّفْلِ الَّذِينَ لَمْ يَظْهَرُوا عَلَىٰ عَوْرَاتِ النِّسَاءِ ۖ وَلَا يَضْرِبْنَ بِأَرْجُلِهِنَّ لِيُعْلَمَ مَا يُخْفِينَ مِنْ زِينَتِهِنَّ ۚ وَتُوبُوا إِلَى اللَّهِ جَمِيعًا أَيُّهَ الْمُؤْمِنُونَ لَعَلَّكُمْ تُفْلِحُونَ
And tell the believing women to reduce [some] of their vision (lower their gazes) and guard their private parts and not expose their adornment except that which [necessarily] appears (to cover their bodies in full (the used clothes must not be tight or transparent) except hands and face and to cover the hair) thereof and to wrap [a portion of] their headcovers over their chests and not expose their adornment except to their husbands, their fathers, their husbands' fathers, their sons, their husbands' sons, their brothers, their brothers' sons, their sisters' sons, their women, that which their right hands possess, or those male attendants having no physical desire, or children who are not yet aware of the private aspects of women. And let them not stamp their feet to make known what they conceal of their adornment. And turn to Allah in repentance, all of you, O believers, that you might succeed.
In the following an app to teach Wudu (getting ready for the prayer) and Salat the Islamic compulsory prayers that must be performed 5 times a day:
https://apps.apple.com/app/id1187721510
https://play.google.com/store/apps/datasafety?id=com.salah.osratouna&hl=en
Keep in mind the following Hadiths and verses of the Quran while wishing to offer Salat:
4:43 An-Nisaa
يَا أَيُّهَا الَّذِينَ آمَنُوا لَا تَقْرَبُوا الصَّلَاةَ وَأَنْتُمْ سُكَارَىٰ حَتَّىٰ تَعْلَمُوا مَا تَقُولُونَ وَلَا جُنُبًا إِلَّا عَابِرِي سَبِيلٍ حَتَّىٰ تَغْتَسِلُوا ۚ وَإِنْ كُنْتُمْ مَرْضَىٰ أَوْ عَلَىٰ سَفَرٍ أَوْ جَاءَ أَحَدٌ مِنْكُمْ مِنَ الْغَائِطِ أَوْ لَامَسْتُمُ النِّسَاءَ فَلَمْ تَجِدُوا مَاءً فَتَيَمَّمُوا صَعِيدًا طَيِّبًا فَامْسَحُوا بِوُجُوهِكُمْ وَأَيْدِيكُمْ ۗ إِنَّ اللَّهَ كَانَ عَفُوًّا غَفُورًا
O you who have believed, do not approach prayer while you are intoxicated (drunk or under the effect of drugs) until you know what you are saying or in a state of janabah (have had a lawful sexual intercourse or have had a wet dream) , except those passing through [a place of prayer], until you have washed [your whole body]. And if you are ill or on a journey or one of you comes from the place of relieving himself or you have contacted women and find no water, then seek clean earth and wipe over your faces and your hands [with it]. Indeed, Allah is ever Pardoning and Forgiving.
Narrated `Aisha: Whenever the Prophet (ﷺ) took a bath after Janaba he started by washing his hands and then performed ablution like that for the prayer. After that he would put his fingers in water and move the roots of his hair with them, and then pour three handfuls of water over his head and then pour water all over his body.
حَدَّثَنَا عَبْدُ اللَّهِ بْنُ يُوسُفَ، قَالَ أَخْبَرَنَا مَالِكٌ، عَنْ هِشَامٍ، عَنْ أَبِيهِ، عَنْ عَائِشَةَ، زَوْجِ النَّبِيِّ صلى الله عليه وسلم أَنَّ النَّبِيَّ صلى الله عليه وسلم كَانَ إِذَا اغْتَسَلَ مِنَ الْجَنَابَةِ بَدَأَ فَغَسَلَ يَدَيْهِ، ثُمَّ يَتَوَضَّأُ كَمَا يَتَوَضَّأُ لِلصَّلاَةِ، ثُمَّ يُدْخِلُ أَصَابِعَهُ فِي الْمَاءِ، فَيُخَلِّلُ بِهَا أُصُولَ شَعَرِهِ ثُمَّ يَصُبُّ عَلَى رَأْسِهِ ثَلاَثَ غُرَفٍ بِيَدَيْهِ، ثُمَّ يُفِيضُ الْمَاءَ عَلَى جِلْدِهِ كُلِّهِ.
Narrated Maimuna bint Al-Harith: I placed water for the bath of Allah's Messenger (ﷺ) and put a screen. He poured water over his hands, and washed them once or twice. (The sub-narrator added that he did not remember if she had said thrice or not). Then he poured water with his right hand over his left one and washed his private parts. He rubbed his hand over the earth or the wall and washed it. He rinsed his mouth and washed his nose by putting water in it and blowing it out. He washed his face, forearms and head. He poured water over his body and then withdrew from that place and washed his feet. I presented him a piece of cloth (towel) and he pointed with his hand (that he does not want it) and did not take it.
حَدَّثَنَا مُوسَى بْنُ إِسْمَاعِيلَ، قَالَ حَدَّثَنَا أَبُو عَوَانَةَ، حَدَّثَنَا الأَعْمَشُ، عَنْ سَالِمِ بْنِ أَبِي الْجَعْدِ، عَنْ كُرَيْبٍ، مَوْلَى ابْنِ عَبَّاسٍ عَنِ ابْنِ عَبَّاسٍ، عَنْ مَيْمُونَةَ بِنْتِ الْحَارِثِ، قَالَتْ وَضَعْتُ لِرَسُولِ اللَّهِ صلى الله عليه وسلم غُسْلاً وَسَتَرْتُهُ، فَصَبَّ عَلَى يَدِهِ، فَغَسَلَهَا مَرَّةً أَوْ مَرَّتَيْنِ ـ قَالَ سُلَيْمَانُ لاَ أَدْرِي أَذَكَرَ الثَّالِثَةَ أَمْ لاَ ـ ثُمَّ أَفْرَغَ بِيَمِينِهِ عَلَى شِمَالِهِ، فَغَسَلَ فَرْجَهُ، ثُمَّ دَلَكَ يَدَهُ بِالأَرْضِ أَوْ بِالْحَائِطِ، ثُمَّ تَمَضْمَضَ وَاسْتَنْشَقَ، وَغَسَلَ وَجْهَهُ وَيَدَيْهِ، وَغَسَلَ رَأْسَهُ، ثُمَّ صَبَّ عَلَى جَسَدِهِ، ثُمَّ تَنَحَّى فَغَسَلَ قَدَمَيْهِ، فَنَاوَلْتُهُ خِرْقَةً، فَقَالَ بِيَدِهِ هَكَذَا، وَلَمْ يُرِدْهَا.
Finally, it’s advisable to read the Quran in full to develop better understanding about Islam and about being a Muslim. Also, the collection of Hadiths, sayings, of prophet Mohamed peace be upon such as Sahih Bukhari ( https://sunnah.com/bukhari) offers further guidance to be followed.
41:13 Fussilat
فَإِنْ أَعْرَضُوا فَقُلْ أَنْذَرْتُكُمْ صَاعِقَةً مِثْلَ صَاعِقَةِ عَادٍ وَثَمُودَ
But if they turn away, then say, "I have warned you of a thunderbolt like the thunderbolt [that struck] 'Aad and Thamud.
41:14 Fussilat
إِذْ جَاءَتْهُمُ الرُّسُلُ مِنْ بَيْنِ أَيْدِيهِمْ وَمِنْ خَلْفِهِمْ أَلَّا تَعْبُدُوا إِلَّا اللَّهَ ۖ قَالُوا لَوْ شَاءَ رَبُّنَا لَأَنْزَلَ مَلَائِكَةً فَإِنَّا بِمَا أُرْسِلْتُمْ بِهِ كَافِرُونَ
[That occurred] when the messengers had come to them before them and after them, [saying], "Worship not except Allah." They said, "If our Lord had willed, He would have sent down the angels, so indeed we, in that with which you have been sent, are disbelievers."
41:15 Fussilat
فَأَمَّا عَادٌ فَاسْتَكْبَرُوا فِي الْأَرْضِ بِغَيْرِ الْحَقِّ وَقَالُوا مَنْ أَشَدُّ مِنَّا قُوَّةً ۖ أَوَلَمْ يَرَوْا أَنَّ اللَّهَ الَّذِي خَلَقَهُمْ هُوَ أَشَدُّ مِنْهُمْ قُوَّةً ۖ وَكَانُوا بِآيَاتِنَا يَجْحَدُونَ
As for 'Aad, they were arrogant upon the earth without right and said, "Who is greater than us in strength?" Did they not consider that Allah who created them was greater than them in strength? But they were rejecting Our signs.
41:16 Fussilat
فَأَرْسَلْنَا عَلَيْهِمْ رِيحًا صَرْصَرًا فِي أَيَّامٍ نَحِسَاتٍ لِنُذِيقَهُمْ عَذَابَ الْخِزْيِ فِي الْحَيَاةِ الدُّنْيَا ۖ وَلَعَذَابُ الْآخِرَةِ أَخْزَىٰ ۖ وَهُمْ لَا يُنْصَرُونَ
So We sent upon them a screaming wind during days of misfortune to make them taste the punishment of disgrace in the worldly life; but the punishment of the Hereafter is more disgracing, and they will not be helped.
41:17 Fussilat
وَأَمَّا ثَمُودُ فَهَدَيْنَاهُمْ فَاسْتَحَبُّوا الْعَمَىٰ عَلَى الْهُدَىٰ فَأَخَذَتْهُمْ صَاعِقَةُ الْعَذَابِ الْهُونِ بِمَا كَانُوا يَكْسِبُونَ
And as for Thamud, We guided them, but they preferred blindness over guidance, so the thunderbolt of humiliating punishment seized them for what they used to earn.
41:18 Fussilat
وَنَجَّيْنَا الَّذِينَ آمَنُوا وَكَانُوا يَتَّقُونَ
And We saved those who believed and used to fear Allah.
41:19 Fussilat
وَيَوْمَ يُحْشَرُ أَعْدَاءُ اللَّهِ إِلَى النَّارِ فَهُمْ يُوزَعُونَ
And [mention, O Muhammad], the Day when the enemies of Allah will be gathered to the Fire while they are [driven] assembled in rows,
41:20 Fussilat
حَتَّىٰ إِذَا مَا جَاءُوهَا شَهِدَ عَلَيْهِمْ سَمْعُهُمْ وَأَبْصَارُهُمْ وَجُلُودُهُمْ بِمَا كَانُوا يَعْمَلُونَ
Until, when they reach it, their hearing and their eyes and their skins will testify against them of what they used to do.
41:21 Fussilat
وَقَالُوا لِجُلُودِهِمْ لِمَ شَهِدْتُمْ عَلَيْنَا ۖ قَالُوا أَنْطَقَنَا اللَّهُ الَّذِي أَنْطَقَ كُلَّ شَيْءٍ وَهُوَ خَلَقَكُمْ أَوَّلَ مَرَّةٍ وَإِلَيْهِ تُرْجَعُونَ
And they will say to their skins, "Why have you testified against us?" They will say, "We were made to speak by Allah, who has made everything speak; and He created you the first time, and to Him you are returned.
41:22 Fussilat
وَمَا كُنْتُمْ تَسْتَتِرُونَ أَنْ يَشْهَدَ عَلَيْكُمْ سَمْعُكُمْ وَلَا أَبْصَارُكُمْ وَلَا جُلُودُكُمْ وَلَٰكِنْ ظَنَنْتُمْ أَنَّ اللَّهَ لَا يَعْلَمُ كَثِيرًا مِمَّا تَعْمَلُونَ
And you were not covering yourselves, lest your hearing testify against you or your sight or your skins, but you assumed that Allah does not know much of what you do.
41:23 Fussilat
وَذَٰلِكُمْ ظَنُّكُمُ الَّذِي ظَنَنْتُمْ بِرَبِّكُمْ أَرْدَاكُمْ فَأَصْبَحْتُمْ مِنَ الْخَاسِرِينَ
And that was your assumption which you assumed about your Lord. It has brought you to ruin, and you have become among the losers."
41:24 Fussilat
فَإِنْ يَصْبِرُوا فَالنَّارُ مَثْوًى لَهُمْ ۖ وَإِنْ يَسْتَعْتِبُوا فَمَا هُمْ مِنَ الْمُعْتَبِينَ
So [even] if they are patient, the Fire is a residence for them; and if they ask to appease [Allah], they will not be of those who are allowed to appease.
41:25 Fussilat
۞ وَقَيَّضْنَا لَهُمْ قُرَنَاءَ فَزَيَّنُوا لَهُمْ مَا بَيْنَ أَيْدِيهِمْ وَمَا خَلْفَهُمْ وَحَقَّ عَلَيْهِمُ الْقَوْلُ فِي أُمَمٍ قَدْ خَلَتْ مِنْ قَبْلِهِمْ مِنَ الْجِنِّ وَالْإِنْسِ ۖ إِنَّهُمْ كَانُوا خَاسِرِينَ
And We appointed for them companions who made attractive to them what was before them and what was behind them [of sin], and the word has come into effect upon them among nations which had passed on before them of jinn and men. Indeed, they [all] were losers.
41:26 Fussilat
وَقَالَ الَّذِينَ كَفَرُوا لَا تَسْمَعُوا لِهَٰذَا الْقُرْآنِ وَالْغَوْا فِيهِ لَعَلَّكُمْ تَغْلِبُونَ
And those who disbelieve say, "Do not listen to this Qur'an and speak noisily during [the recitation of] it that perhaps you will overcome."
41:27 Fussilat
فَلَنُذِيقَنَّ الَّذِينَ كَفَرُوا عَذَابًا شَدِيدًا وَلَنَجْزِيَنَّهُمْ أَسْوَأَ الَّذِي كَانُوا يَعْمَلُونَ
But We will surely cause those who disbelieve to taste a severe punishment, and We will surely recompense them for the worst of what they had been doing.
41:28 Fussilat
ذَٰلِكَ جَزَاءُ أَعْدَاءِ اللَّهِ النَّارُ ۖ لَهُمْ فِيهَا دَارُ الْخُلْدِ ۖ جَزَاءً بِمَا كَانُوا بِآيَاتِنَا يَجْحَدُونَ
That is the recompense of the enemies of Allah - the Fire. For them therein is the home of eternity as recompense for what they, of Our verses, were rejecting.
41:29 Fussilat
وَقَالَ الَّذِينَ كَفَرُوا رَبَّنَا أَرِنَا اللَّذَيْنِ أَضَلَّانَا مِنَ الْجِنِّ وَالْإِنْسِ نَجْعَلْهُمَا تَحْتَ أَقْدَامِنَا لِيَكُونَا مِنَ الْأَسْفَلِينَ
And those who disbelieved will [then] say, "Our Lord, show us those who misled us of the jinn and men [so] we may put them under our feet that they will be among the lowest."
41:30 Fussilat
إِنَّ الَّذِينَ قَالُوا رَبُّنَا اللَّهُ ثُمَّ اسْتَقَامُوا تَتَنَزَّلُ عَلَيْهِمُ الْمَلَائِكَةُ أَلَّا تَخَافُوا وَلَا تَحْزَنُوا وَأَبْشِرُوا بِالْجَنَّةِ الَّتِي كُنْتُمْ تُوعَدُونَ
Indeed, those who have said, "Our Lord is Allah " and then remained on a right course - the angels will descend upon them, [saying], "Do not fear and do not grieve but receive good tidings of Paradise, which you were promised.
41:31 Fussilat
نَحْنُ أَوْلِيَاؤُكُمْ فِي الْحَيَاةِ الدُّنْيَا وَفِي الْآخِرَةِ ۖ وَلَكُمْ فِيهَا مَا تَشْتَهِي أَنْفُسُكُمْ وَلَكُمْ فِيهَا مَا تَدَّعُونَ
We [angels] were your allies in worldly life and [are so] in the Hereafter. And you will have therein whatever your souls desire, and you will have therein whatever you request [or wish]
41:32 Fussilat
نُزُلًا مِنْ غَفُورٍ رَحِيمٍ
As accommodation from a [Lord who is] Forgiving and Merciful."
41:33 Fussilat
وَمَنْ أَحْسَنُ قَوْلًا مِمَّنْ دَعَا إِلَى اللَّهِ وَعَمِلَ صَالِحًا وَقَالَ إِنَّنِي مِنَ الْمُسْلِمِينَ
And who is better in speech than one who invites to Allah and does righteousness and says, "Indeed, I am of the Muslims."
41:34 Fussilat
وَلَا تَسْتَوِي الْحَسَنَةُ وَلَا السَّيِّئَةُ ۚ ادْفَعْ بِالَّتِي هِيَ أَحْسَنُ فَإِذَا الَّذِي بَيْنَكَ وَبَيْنَهُ عَدَاوَةٌ كَأَنَّهُ وَلِيٌّ حَمِيمٌ
And not equal are the good deed and the bad. Repel [evil] by that [deed] which is better; and thereupon the one whom between you and him is enmity [will become] as though he was a devoted friend.
41:35 Fussilat
وَمَا يُلَقَّاهَا إِلَّا الَّذِينَ صَبَرُوا وَمَا يُلَقَّاهَا إِلَّا ذُو حَظٍّ عَظِيمٍ
But none is granted it except those who are patient, and none is granted it except one having a great portion [of good].
41:36 Fussilat
وَإِمَّا يَنْزَغَنَّكَ مِنَ الشَّيْطَانِ نَزْغٌ فَاسْتَعِذْ بِاللَّهِ ۖ إِنَّهُ هُوَ السَّمِيعُ الْعَلِيمُ
And if there comes to you from Satan an evil suggestion, then seek refuge in Allah. Indeed, He is the Hearing, the Knowing.
41:37 Fussilat
وَمِنْ آيَاتِهِ اللَّيْلُ وَالنَّهَارُ وَالشَّمْسُ وَالْقَمَرُ ۚ لَا تَسْجُدُوا لِلشَّمْسِ وَلَا لِلْقَمَرِ وَاسْجُدُوا لِلَّهِ الَّذِي خَلَقَهُنَّ إِنْ كُنْتُمْ إِيَّاهُ تَعْبُدُونَ
And of His signs are the night and day and the sun and moon. Do not prostrate to the sun or to the moon, but prostate to Allah, who created them, if it should be Him that you worship.
41:38 Fussilat
فَإِنِ اسْتَكْبَرُوا فَالَّذِينَ عِنْدَ رَبِّكَ يُسَبِّحُونَ لَهُ بِاللَّيْلِ وَالنَّهَارِ وَهُمْ لَا يَسْأَمُونَ ۩
But if they are arrogant - then those who are near your Lord exalt Him by night and by day, and they do not become weary.
41:39 Fussilat
وَمِنْ آيَاتِهِ أَنَّكَ تَرَى الْأَرْضَ خَاشِعَةً فَإِذَا أَنْزَلْنَا عَلَيْهَا الْمَاءَ اهْتَزَّتْ وَرَبَتْ ۚ إِنَّ الَّذِي أَحْيَاهَا لَمُحْيِي الْمَوْتَىٰ ۚ إِنَّهُ عَلَىٰ كُلِّ شَيْءٍ قَدِيرٌ
And of His signs is that you see the earth stilled, but when We send down upon it rain, it shakes and grows. Indeed, He who has given it life is the Giver of Life to the dead. Indeed, He is over all things competent.
41:40 Fussilat
إِنَّ الَّذِينَ يُلْحِدُونَ فِي آيَاتِنَا لَا يَخْفَوْنَ عَلَيْنَا ۗ أَفَمَنْ يُلْقَىٰ فِي النَّارِ خَيْرٌ أَمْ مَنْ يَأْتِي آمِنًا يَوْمَ الْقِيَامَةِ ۚ اعْمَلُوا مَا شِئْتُمْ ۖ إِنَّهُ بِمَا تَعْمَلُونَ بَصِيرٌ
Indeed, those who inject deviation into Our verses are not concealed from Us. So, is he who is cast into the Fire better or he who comes secure on the Day of Resurrection? Do whatever you will; indeed, He (God, Allah) is Seeing what you do.
-
 @ d34e832d:383f78d0
2025-04-22 08:40:25
@ d34e832d:383f78d0
2025-04-22 08:40:25
In the twilight of forgotten eras, where the whispers of the past wove through the air like a ghostly melody, two shadowy figures emerged beneath an ageless sky. She was Eve, not the emblem of gardens, but the Mitochondrial Eve—her essence pulsing within the very mitochondria that spark life in each human heartbeat. He stood before her as Adam, not forged from soil, but the Y-Chromosome Adam—guardian of a singular lineage, his heritage dancing through the veins of sons alone.
Their encounter was not one of flesh and blood, but a meeting of symbols, sparked by the insatiable curiosity of humanity, prowling through the labyrinth of DNA, seeking to uncover the tales of their primordial roots.
In the ethereal glimmer of a timeless pool, two figures stood, their outlines rippling like whispered secrets. They were neither lovers nor allies, nor of the same age, yet their names danced together in every headline and wisdom-filled book.
Today, however, was different—they had gathered at the brink of the infinite to unravel the threads of their intertwined destinies.
As the twilight draped its ethereal cloak over the meadow, Eve let her fingers dance through the glimmering starlight, weaving dreams from its luminous threads.
“You know,” she mused, her voice a whisper carried by the evening breeze, “they often ponder why fate kept us apart. Why our paths never crossed beneath the same sun.”Adam’s lips curled into a wry smile, his eyes reflecting the cosmos above.
“Perhaps they seek a narrative that is neat and orderly, a story with perfect symmetry,” he replied, the gentle rustle of leaves echoing his words.Eve shook her head softly, her gaze fixed on the swirling constellations.
“Ah, but nature, dear Adam,” she countered with a glimmer of mischief, “is a master of chaos. It delights in the untamed, the beautiful mess of existence.”In the grand tapestry of time, two figures emerged from the mists of ancient Africa:
Mitochondrial Eve, a woman of vibrant spirit, who roamed the earth around 150,000 to 200,000 years ago, and
Y-Chromosome Adam, a man of strength and wisdom, appearing some 60,000 to 100,000 years later.Though separated by a chasm of tens of thousands of years, they were not the sole beings of their era, yet in the intricate web of life, they were the most recent ancestors, bearers of unbroken trails of maternal and paternal lines, from which all humanity flows.
Their stories intertwine, echoing through generations, whispers of a time long past.
In a hushed tone, Eve shared the tale of her lineage, weaving a rich tapestry of time.
“Behold my daughters,” she said, her eyes gleaming with pride. “From them sprang another generation, and those daughters too have borne daughters.This precious thread of life, my mitochondrial DNA, weaves through the tapestry, handed down solely by women.
With each passing age, while many lines faded into shadows—some in mere moments, others enduring for centuries—mine flowed on, a river of continuity and strength.
My legacy, a steadfast whisper across generations, defied the silence of so many others.”In a dimly lit room, Adam pondered the weight of generations past.
“And what of mine?” he inquired, his voice tinged with a mix of curiosity and melancholy.He shook his head slowly, as if unraveling a forgotten tale.
“The Y-chromosome, it weaves a delicate thread through the tapestry of life.
Passed from fathers to sons, a fleeting whisper of legacy, vanishing if a man begets no heirs.Like branches of a grand oak, countless lines have been severed by the cruel hands of war, the relentless march of disease, and the silent grasp of chance.
Mine is not the sole survivor in this timeless struggle, but it is the one that defied extinction—standing resilient against the bottleneck of time, thriving into the present day, a testament to tenacity and fate.”Their inheritance patterns are straightforward but ruthless.
Mitochondrial DNA (mtDNA) is stable and abundant, making it a powerful marker for tracing maternal lineage.
It mutates slowly, preserving a clear path backward.In contrast, the Y-chromosome, despite its utility in tracing paternal lines, is subject to greater volatility: smaller effective population sizes, male-specific extinction events, and the disproportionate reproductive success of a few males—all contribute to a narrower, more chaotic record.
In a dimly lit chamber nestled among ancient trees, Eve’s voice resonated with the wisdom of ages.
“The numbers are not our destiny,” she declared, her finger tracing a pattern in the soil.
“They are mere echoes of survival, tales of those who dared to pass their legacy—a lineage of children begetting children, weaving a tapestry of existence.”Adam stood by, thoughtful as a storm brewing on a distant horizon.
“Indeed, lineages dissolve like whispers in the wind,” he mused, his gaze fixed on the moonlight filtering through the leaves.
“Some genetic threads endure not from superiority, but sheer fortune. Bottlenecks of fate, the whims of founders, the swirling dance of genetic drift—these unseen forces hold the key to who emerges amidst the chaos of time.”Together, they pondered the intricate dance of life, where luck and survival intertwined, crafting the very fabric of their world.
Eve paused, her voice a whisper woven with time.
“And so it is,” she mused, “the humans trace their lineage back to me, painting me as the primordial bloom of existence.Yet, shadows linger—my cousins, neighbors, even rivals shared this space, vibrant as I, yet their stories faded like whispers in the wind.
They bore no daughters to carry forth their tales, only their echoes lingered, lost in the tapestry of forgotten history…”
In the shadow of an ancient, pulsing tree that mirrored their very essence, Adam mused aloud,
“I came along far down the line, but not right at the start.
I am but one among countless men, and in the end, only my Y-line remained, a solitary thread in the tapestry of time.
Your lineage, however, stretches across continents, vibrant and thriving.”They stood quietly, lost in the vast glow of humanity’s fractal branches, each flicker representing a birth, a connection, a glimmer of possibility.
“Isn’t it amusing?” Adam chuckled, breaking the reverie.
“They pair us as if we were a couple, forever intertwined.”Eve’s laughter echoed like sweet music.
“Merely symbols, nothing deeper. We are called ancestors, yet we are merely the fortunate survivors of an exquisite genetic lottery.”Adam continued,
“And yet, the very essence of your spark resides in every human’s mitochondria, while half of them carry my signature in their Y chromosome.”Eve’s voice was soft as she spoke, weaving a tapestry of understanding.
“Ah, but dear friend, ancestry is far more than mere lineage.
It’s like tracing the delicate threads of a grand tapestry, where some strands are visible, yet countless others lie hidden in the shadows of time.Each soul walking upon this earth is a descendant of a multitude of individuals from ages long past.
Their names may fade like whispers in the wind, and their unique genes become mere echoes of history.
Yet, amidst this beautiful chaos, the patterns of our heritage forever linger, binding us in an unseen embrace of shared existence.”As Adam stood beneath the shimmering canopy of stars, he pondered aloud,
“Maybe the tale isn’t solely ours. It’s about the delicate yet unwavering dance of life itself.”Eve, her eyes reflecting the celestial lights, agreed with a subtle nod.
“Indeed, for no single thread can unveil the entirety of the narrative.
One must gaze upon the grand tapestry woven through time.”They dimmed away, not with finality, but like starlight traversing the vastness of the cosmos—whispers that remind us history bends and weaves, a spider’s web of fate, woven with threads of fortune, affection, and heartache, where beams of hope dance through the dark.
Within each of us, they linger still, a harmonious symphony resonating with the voices of billions, echoing through time.
-
 @ c631e267:c2b78d3e
2025-03-31 07:23:05
@ c631e267:c2b78d3e
2025-03-31 07:23:05Der Irrsinn ist bei Einzelnen etwas Seltenes – \ aber bei Gruppen, Parteien, Völkern, Zeiten die Regel. \ Friedrich Nietzsche
Erinnern Sie sich an die Horrorkomödie «Scary Movie»? Nicht, dass ich diese Art Filme besonders erinnerungswürdig fände, aber einige Szenen daraus sind doch gewissermaßen Klassiker. Dazu zählt eine, die das Verhalten vieler Protagonisten in Horrorfilmen parodiert, wenn sie in Panik flüchten. Welchen Weg nimmt wohl die Frau in der Situation auf diesem Bild?

Diese Szene kommt mir automatisch in den Sinn, wenn ich aktuelle Entwicklungen in Europa betrachte. Weitreichende Entscheidungen gehen wider jede Logik in die völlig falsche Richtung. Nur ist das hier alles andere als eine Komödie, sondern bitterernst. Dieser Horror ist leider sehr real.
Die Europäische Union hat sich selbst über Jahre konsequent in eine Sackgasse manövriert. Sie hat es versäumt, sich und ihre Politik selbstbewusst und im Einklang mit ihren Wurzeln auf dem eigenen Kontinent zu positionieren. Stattdessen ist sie in blinder Treue den vermeintlichen «transatlantischen Freunden» auf ihrem Konfrontationskurs gen Osten gefolgt.
In den USA haben sich die Vorzeichen allerdings mittlerweile geändert, und die einst hoch gelobten «Freunde und Partner» erscheinen den europäischen «Führern» nicht mehr vertrauenswürdig. Das ist spätestens seit der Münchner Sicherheitskonferenz, der Rede von Vizepräsident J. D. Vance und den empörten Reaktionen offensichtlich. Große Teile Europas wirken seitdem wie ein aufgescheuchter Haufen kopfloser Hühner. Orientierung und Kontrolle sind völlig abhanden gekommen.
Statt jedoch umzukehren oder wenigstens zu bremsen und vielleicht einen Abzweig zu suchen, geben die Crash-Piloten jetzt auf dem Weg durch die Sackgasse erst richtig Gas. Ja sie lösen sogar noch die Sicherheitsgurte und deaktivieren die Airbags. Den vor Angst dauergelähmten Passagieren fällt auch nichts Besseres ein und so schließen sie einfach die Augen. Derweil übertrumpfen sich die Kommentatoren des Events gegenseitig in sensationslüsterner «Berichterstattung».
Wie schon die deutsche Außenministerin mit höchsten UN-Ambitionen, Annalena Baerbock, proklamiert auch die Europäische Kommission einen «Frieden durch Stärke». Zu dem jetzt vorgelegten, selbstzerstörerischen Fahrplan zur Ankurbelung der Rüstungsindustrie, genannt «Weißbuch zur europäischen Verteidigung – Bereitschaft 2030», erklärte die Kommissionspräsidentin, die «Ära der Friedensdividende» sei längst vorbei. Soll das heißen, Frieden bringt nichts ein? Eine umfassende Zusammenarbeit an dauerhaften europäischen Friedenslösungen steht demnach jedenfalls nicht zur Debatte.
Zusätzlich brisant ist, dass aktuell «die ganze EU von Deutschen regiert wird», wie der EU-Parlamentarier und ehemalige UN-Diplomat Michael von der Schulenburg beobachtet hat. Tatsächlich sitzen neben von der Leyen und Strack-Zimmermann noch einige weitere Deutsche in – vor allem auch in Krisenzeiten – wichtigen Spitzenposten der Union. Vor dem Hintergrund der Kriegstreiberei in Deutschland muss eine solche Dominanz mindestens nachdenklich stimmen.
Ihre ursprünglichen Grundwerte wie Demokratie, Freiheit, Frieden und Völkerverständigung hat die EU kontinuierlich in leere Worthülsen verwandelt. Diese werden dafür immer lächerlicher hochgehalten und beschworen.
Es wird dringend Zeit, dass wir, der Souverän, diesem erbärmlichen und gefährlichen Trauerspiel ein Ende setzen und die Fäden selbst in die Hand nehmen. In diesem Sinne fordert uns auch das «European Peace Project» auf, am 9. Mai im Rahmen eines Kunstprojekts den Frieden auszurufen. Seien wir dabei!
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 6a6be47b:3e74e3e1
2025-04-12 12:13:13
@ 6a6be47b:3e74e3e1
2025-04-12 12:13:13Hi frens! How's your weekend starting? I'm just finishing a newblog entry 🖋️on my website and I'm going to be selling a few things on my Ko-fi shop 🛍️.
Before I post everything, I wanted to share a special treat with my Nostr family:
🎁 I've created two beautiful postcard-sized (148mm x 210mm or 5.83 in x 8.27 in)artworks inspired by Holy Week. Here they are:
Palm Day
 Resurrection Day
Resurrection Day

✉️ If you'd like one, just DM me with your email address, and I'll send it your way! Zaps are always appreciated and help keep me going. 🙏
❤️ This is big thank you to you my frens Have fun and stay safe
✝️ This is an INSTANT DIGITAL DOWNLOAD, no physical item will be shipped to you.
✝️ The frames and accessories in the listing images are not included.
🚨 DISCLAIMER 🚨
❤️ Copyright Retention: I, the artist, retain full copyright of all original artwork, even after the digital print is purchased.
❤️ Limited License: The digital print provides a limited, non-transferable license for personal use only. It is not intended for commercial use or resale.
❤️ No Reproduction Rights: The purchase of this digital print does not grant any rights to reproduce, distribute, or create derivative works based on the design.
🚨 By proceeding with the purchase of this digital print, you acknowledge and agree to these terms. 🚨
-
 @ 57d1a264:69f1fee1
2025-03-29 18:02:16
@ 57d1a264:69f1fee1
2025-03-29 18:02:16This UX research has been redacted by @iqra from the Bitcoin.Design community, and shared for review and feedback! Don't be shy, share your thoughts.
1️⃣ Introduction
Project Overview
📌 Product: BlueWallet (Bitcoin Wallet) 📌 Goal: Improve onboarding flow and enhance accessibility for a better user experience. 📌 Role: UX Designer 📌 Tools Used: Figma, Notion
Why This Case Study?
🔹 BlueWallet is a self-custodial Bitcoin wallet, but users struggle with onboarding due to unclear instructions. 🔹 Accessibility issues (low contrast, small fonts) create barriers for visually impaired users. 🔹 Competitors like Trust Wallet and MetaMask offer better-guided onboarding.
This case study presents UX/UI improvements to make BlueWallet more intuitive and inclusive.
2️⃣ Problem Statement: Why BlueWalletʼs Onboarding Needs Improvement
🔹 Current Challenges:
1️⃣ Onboarding Complexity - BlueWallet lacks step-by-step guidance, leaving users confused about wallet creation and security.
2️⃣ No Educational Introduction - Users land directly on the wallet screen with no explanation of private keys, recovery phrases, or transactions. 3️⃣ Transaction Flow Issues - Similar-looking "Send" and "Receive" buttons cause confusion. 4️⃣ Poor Accessibility - Small fonts and low contrast make navigation difficult.
🔍 Impact on Users:
Higher drop-off rates due to frustration during onboarding. Security risks as users skip key wallet setup steps. Limited accessibility for users with visual impairments.
📌 Competitive Gap:
Unlike competitors (Trust Wallet, MetaMask), BlueWallet does not offer: ✅ A guided onboarding process ✅ Security education during setup ✅ Intuitive transaction flow
Somehow, this wallet has much better UI than the BlueWallet Bitcoin wallet.
3️⃣ User Research & Competitive Analysis
User Testing Findings
🔹 Conducted usability testing with 5 users onboarding for the first time. 🔹 Key Findings: ✅ 3 out of 5 users felt lost due to missing explanations. ✅ 60% had trouble distinguishing transaction buttons. ✅ 80% found the text difficult to read due to low contrast.
Competitive Analysis
We compared BlueWallet with top crypto wallets:
| Wallet | Onboarding UX | Security Guidance | Accessibility Features | |---|---|---|---| | BlueWallet | ❌ No guided onboarding | ❌ Minimal explanation | ❌ Low contrast, small fonts | | Trust Wallet | ✅ Step-by-step setup | ✅ Security best practices | ✅ High contrast UI | | MetaMask | ✅ Interactive tutorial | ✅ Private key education | ✅ Clear transaction buttons |
📌 Key Insight: BlueWallet lacks guided setup and accessibility enhancements, making it harder for beginners.
📌 User Persona
To better understand the users facing onboarding challenges, I developed a persona based on research and usability testing.
🔹 Persona 1: Alex Carter (Bitcoin Beginner & Investor)
👤 Profile: - Age: 28 - Occupation: Freelance Digital Marketer - Tech Knowledge: Moderate - Familiar with online transactions, new to Bitcoin) - Pain Points: - Finds Bitcoin wallets confusing. - - Doesnʼt understand seed phrases & security features. - - Worried about losing funds due to a lack of clarity in transactions.
📌 Needs: ✅ A simple, guided wallet setup. ✅ Clear explanations of security terms (without jargon). ✅ Easy-to-locate Send/Receive buttons.
📌 Persona Usage in Case Study: - Helps define who we are designing for. - Guides design decisions by focusing on user needs.
🔹 Persona 2: Sarah Mitchell (Accessibility Advocate & Tech Enthusiast)
👤 Profile: - Age: 35 - Occupation: UX Researcher & Accessibility Consultant - Tech Knowledge: High (Uses Bitcoin but struggles with accessibility barriers)
📌 Pain Points: ❌ Struggles with small font sizes & low contrast. ❌ Finds the UI difficult to navigate with a screen reader. ❌ Confused by identical-looking transaction buttons.
📌 Needs: ✅ A high-contrast UI that meets WCAG accessibility standards. ✅ Larger fonts & scalable UI elements for better readability. ✅ Keyboard & screen reader-friendly navigation for seamless interaction.
📌 Why This Persona Matters: - Represents users with visual impairments who rely on accessible design. - Ensures the design accommodates inclusive UX principles.
4️⃣ UX/UI Solutions & Design Improvements
📌 Before (Current Issues)
❌ Users land directly on the wallet screen with no instructions. ❌ "Send" & "Receive" buttons look identical , causing transaction confusion. ❌ Small fonts & low contrast reduce readability.
✅ After (Proposed Fixes)
✅ Step-by-step onboarding explaining wallet creation, security, and transactions. ✅ Visually distinct transaction buttons (color and icon changes). ✅ WCAG-compliant text contrast & larger fonts for better readability.
1️⃣ Redesigned Onboarding Flow
✅ Added a progress indicator so users see where they are in setup. ✅ Used plain, non-technical language to explain wallet creation & security. ✅ Introduced a "Learn More" button to educate users on security.
2️⃣ Accessibility Enhancements
✅ Increased contrast ratio for better text readability. ✅ Used larger fonts & scalable UI elements. ✅ Ensured screen reader compatibility (VoiceOver & TalkBack support).
3️⃣ Transaction Flow Optimization
✅ Redesigned "Send" & "Receive" buttons for clear distinction. ✅ Added clearer icons & tooltips for transaction steps.
5️⃣ Wireframes & Design Improvements:
🔹 Welcome Screen (First Screen When User Opens Wallet)
📌 Goal: Give a brief introduction & set user expectations
✅ App logo + short tagline (e.g., "Secure, Simple, Self-Custody Bitcoin Wallet") ✅ 1-2 line explanation of what BlueWallet is (e.g., "Your gateway to managing Bitcoin securely.") ✅ "Get Started" button → Le ads to next step: Wallet Setup ✅ "Already have a wallet?" → Import option
🔹 Example UI Elements: - BlueWallet Logo - Title: "Welcome to BlueWallet" - Subtitle: "Easily store, send, and receive Bitcoin." - CTA: "Get Started" (Primary) | "Import Wallet" (Secondary)
🔹 Screen 2: Choose Wallet Type (New or Import)
📌 Goal: Let users decide how to proceed
✅ Two clear options: - Create a New Wallet (For first-time users) - Import Existing Wallet (For users with a backup phrase) ✅ Brief explanation of each option 🔹 Example UI Elements: - Title: "How do you want to start?" - Buttons:** "Create New Wallet" | "Import Wallet"
🔹 Screen 3: Security & Seed Phrase Setup (Critical Step)
📌 Goal: Educate users about wallet security & backups
✅ Explain why seed phrases are important ✅ Clear step-by-step instructions on writing down & storing the phrase ✅ Warning: "If you lose your recovery phrase, you lose access to your wallet." ✅ CTA: "Generate Seed Phrase" → Next step
🔹 Example UI Elements: - Title: "Secure Your Wallet" - Subtitle: "Your seed phrase is the key to your Bitcoin. Keep it safe!" - Button: "Generate Seed Phrase"
🔹 Screen 4: Seed Phrase Display & Confirmation
📌 Goal: Ensure users write down the phrase correctly
✅ Display 12- or 24-word seed phrase ✅ “I have written it downˮ checkbox before proceeding ✅ Next screen: Verify seed phrase (drag & drop, re-enter some words)
🔹 Example UI Elements: - Title: "Write Down Your Seed Phrase" - List of 12/24 Words (Hidden by Default) - Checkbox: "I have safely stored my phrase" - Button: "Continue"
🔹 Screen 5: Wallet Ready! (Final Step)
📌 Goal: Confirm setup & guide users on next actions
✅ Success message ("Your wallet is ready!") ✅ Encourage first action: - “Receive Bitcoinˮ → Show wallet address - “Send Bitcoinˮ → Walkthrough on making transactions
✅ Short explainer: Where to find the Send/Receive buttons
🔹 Example UI Elements: - Title: "You're All Set!" - Subtitle: "Start using BlueWallet now." - Buttons: "Receive Bitcoin" | "View Wallet"
5️⃣ Prototype & User Testing Results
🔹 Created an interactive prototype in Figma to test the new experience. 🔹 User Testing Results: ✅ 40% faster onboarding completion time. ✅ 90% of users found transaction buttons clearer. 🔹 User Feedback: ✅ “Now I understand the security steps clearly.ˮ ✅ “The buttons are easier to find and use.ˮ
6️⃣ Why This Matters: Key Takeaways
📌 Impact of These UX/UI Changes: ✅ Reduced user frustration by providing a step-by-step onboarding guide. ✅ Improved accessibility , making the wallet usable for all. ✅ More intuitive transactions , reducing errors.
7️⃣ Direct link to figma file and Prototype
Original PDF available from here
originally posted at https://stacker.news/items/928822
-
 @ 7d33ba57:1b82db35
2025-04-22 08:35:57
@ 7d33ba57:1b82db35
2025-04-22 08:35:57Nestled in Lower Saxony’s East Frisia region, Leer is a charming canal town known for its historic tea culture, maritime heritage, and postcard-worthy Altstadt (Old Town). With colorful gabled houses, cobbled streets, and a relaxed pace, Leer offers a taste of northern Germany’s quiet beauty—without the crowds.
🏘️ Things to See & Do in Leer
🚶♂️ Altstadt (Old Town)
- Stroll through narrow lanes lined with 17th and 18th-century houses
- Highlights include Waageplatz, the Reformed Church, and Evenburg Castle
- Perfect for a slow wander, especially during golden hour
🛶 Canal Walks & Harbor
- Take a peaceful walk along the Leda and Ems rivers
- Watch boats pass through the small port and historic trading canals
- In summer, you can even book a scenic canal cruise
🍵 East Frisian Tea Culture
- Leer is considered the tea capital of Germany
- Visit the Bünting Teemuseum to learn about the centuries-old tea tradition
- Don’t miss a tea session with rock sugar and cream—served the traditional East Frisian way
🌳 Nature Nearby
- Cycle or walk through the flat green landscapes of East Frisia
- Great routes along rivers and meadows, with plenty of windmills and grazing sheep
- A short drive takes you to the Wadden Sea, a UNESCO site and tidal wonder
🍽️ Local Eats
- Sample Matjes (pickled herring), smoked fish, and hearty stews
- East Frisian cakes pair beautifully with black tea
- Cozy inns and riverside cafés make for a warm, welcoming meal
🚆 Getting There
- Easily accessible by train from Bremen or Emden
- Compact and walkable—no car needed in the town center
Leer is a peaceful, picturesque retreat where canals, culture, and comfort flow together. Whether you're cycling through the countryside or sipping tea by the harbor, it’s a place to unwind and soak up the slow life.
-
 @ caa88a52:6c226a91
2025-04-11 22:58:40
@ caa88a52:6c226a91
2025-04-11 22:58:40Running Nestr!
-
 @ 57d1a264:69f1fee1
2025-03-29 17:15:17
@ 57d1a264:69f1fee1
2025-03-29 17:15:17- Once activated, "Accept From Any Mint” is the default setting. This is the easiest way to get started, let's the user start acceptance Cashu ecash just out of the box.
- If someone does want to be selective, they can choose “Accept From Trusted Mints,” and that brings up a field where they can add specific mint URLs they trust.
- “Find a Mint” section on the right with a button links directly to bitcoinmints.com, already filtered for Cashu mints, so users can easily browse options.
- Mint info modal shows mint technical details stuff from the NUT06 spec. Since this is geared towards the more technical users I left the field names and NUT number as-is instead of trying to make it more semantic.
originally posted at https://stacker.news/items/928800
-
 @ 70c48e4b:00ce3ccb
2025-04-22 08:35:52
@ 70c48e4b:00ce3ccb
2025-04-22 08:35:52Hello reader,
I can say from personal experience that crowdfunding has truly changed my life. I found people who believed in my dream of using Bitcoin as money. Every single one of my videos was made possible through crowdfunding. And I’m not alone. I know several Bitcoiners who have raised funds this way, from Africa to Korea to Haiti.
https://images.forbesindia.com/media/images/2022/Jul/img_190501_runwithbitcoin_bg.jpg
Crowdfunding is deeply rooted in the traditional financial world. From raising money for life-saving surgeries to helping someone open a local coffee shop, platforms like GoFundMe, Kickstarter, and Indiegogo have become essential tools for many. But behind all the heartwarming stories and viral campaigns, there’s a side of crowdfunding that doesn’t get talked about enough. Traditional platforms are far from perfect.
They are centralized, which means there’s always someone in control. These platforms can freeze campaigns, delay payouts, or take a significant cut of the money. And often, the people who need funding the most, those without access to strong banking systems or large social media followings are the ones who get left out.
Here are some of the problems I’ve noticed with these platforms:
Problem 1: Inequality in Who Gets Funded
A recent article in The Guardian pointed out something that’s hard to ignore. Crowdfunding often benefits people who already have influence. After the Los Angeles wildfires in January 2025, celebrities like Mandy Moore were able to raise funds quickly. At the same time, everyday people who lost their homes struggled to get noticed.
https://i.guim.co.uk/img/media/f8398505e58ec3c04685aab06e94048e5d7b6a0c/0_127_4800_2880/master/4800.jpg?width=1300&dpr=1&s=none&crop=none
Angor (https://angor.io/) changes that by removing the need for a central platform to choose which projects get featured or promoted. Anyone can share their project. People can find them on Angor Hub (https://hub.angor.io/), which is a public directory built on the Nostr protocol. Instead of relying on popularity, projects are highlighted based on transparency and engagement.
Problem 2: Platform Dependence and Middlemen
Here’s something people don’t often realize. When you raise funds online, the platform usually has control. It holds the money, decides when to release it, and can freeze everything without warning. This happened during the trucker protests in Canada in 2022. Tens of millions of dollars were raised, but platforms like GoFundMe and GiveSendGo froze the donations. The funds never reached the people they were meant for. Supporters were left confused, and the recipients had no way to access what had been raised for them.
https://upload.wikimedia.org/wikipedia/commons/thumb/2/2d/Convoi_de_la_libert%C3%A9_%C3%A0_Ottawa_01.jpg/800px-Convoi_de_la_libert%C3%A9_%C3%A0_Ottawa_01.jpg
Angor avoids all of this. It does not hold the funds, does not require approval processes, and only the project creator has control over the campaign. Contributions go directly from supporters to the people building the project, using Bitcoin. It is a peer-to-peer system that works without any gatekeepers. Angor never touches the money. It simply provides the tools people need to raise funds and build, while staying fully in control.
Problem 3: Global Access
Another major issue is that these platforms often exclude people based on where they live. If you're in a region with limited banking access or outside the supported list of countries, you’re likely shut out. In 2023, a woman named Samar in Gaza tried to raise funds for food and medical supplies during a crisis. A friend abroad set up a campaign to help, but the platform froze it due to "location-related concerns." The funds were locked, and the support never arrived in time.
https://images.gofundme.com/EMFtPWSLs3P9SewkzwZ4FtaBQSA=/720x405/https://d2g8igdw686xgo.cloudfront.net/78478731_1709065237698709_r.jpeg
Angor removes these barriers by using Bitcoin, which works globally without needing banks or approvals. Anyone, anywhere, can raise and receive support directly.
Problem 4: Lack of Transparency
Post-funding transparency is often lacking. Backers rarely get consistent updates, making it difficult to track a project's progress or hold anyone accountable.
In 2015, the Zano drone project on Kickstarter raised over £2.3 million from more than 12,000 backers. It promised a compact, smart drone for aerial photography. But as time went on, updates became rare and vague. Backers had little insight into the project’s struggles, and eventually, it was canceled. The company shut down, and most backers never received their product or a refund.
https://ichef.bbci.co.uk/ace/standard/976/cpsprodpb/2A0A/production/_86626701_ff861eeb-ce94-43b7-9a43-b30b5adbd7ab.jpg
Angor takes a different approach. Project updates are shared through Nostr, a decentralized and tamper-proof communication protocol. This allows backers to follow progress in real time, with no corporate filters and no blackout periods. Everyone stays in the loop, from start to finish.
Problem 5: Fraud and Accountability
Scams are a growing problem in the crowdfunding world. People can launch fake campaigns, collect donations, and vanish — leaving supporters with empty promises and no way to recover their money. One well-known example was the "Homeless Vet GoFundMe scam" in the U.S.
https://a57.foxnews.com/static.foxnews.com/foxnews.com/content/uploads/2018/09/720/405/1536549443584.jpg
A couple and a homeless man raised over $400,000 by telling a heartwarming story that later turned out to be completely fake. The money was spent on luxury items, and it took a legal investigation to uncover the truth. By the time it was resolved, most of the funds were gone.
This kind of fraud is hard to stop on traditional platforms, because once the funds are transferred, there’s no built-in structure to verify how they’re used.
On Angor, projects are funded in stages, with each step tied to a specific milestone. Bitcoin is held in a shared wallet that only unlocks funds when both the backer and the creator agree that the milestone is complete. If something feels off, backers can choose to stop and recover unspent funds.
This structure discourages scammers from even trying. It adds friction for bad actors, while still giving honest creators the freedom to build trust, deliver value, and raise support transparently. It can’t get any better than this
So, does Angor matter?
For me, it really does. I’m genuinely excited to have my project listed on Angorhub. In a world shaped by AI, open source and transparency light the way forward. Let the work shine on its own.
Have you tried Angor yet? Thanks for tuning in. Catch you next week. Ciao!
Guest blog: Paco nostr:npub1v67clmf4jrezn8hsz28434nc0y5fu65e5esws04djnl2kasxl5tskjmjjk
References:
• The Guardian, 2025: Crowdfunding after LA fires and inequality - https://www.theguardian.com/us-news/2025/jan/17/la-fires-gofundme-mandy-moore • https://www.theguardian.com/us-news/2018/nov/15/johnny-bobbitt-gofundme-scam-arrest-viral-gas-story-couple-charged • FundsforNGOs: The Success Story of an NGO That Scaled with Limited Resourceshttps://www2.fundsforngos.org/articles/the-success-story-of-an-ngo-that-scaled-with-limited-resources/ • https://www.freightwaves.com/news/gofundme-freezes-37m-until-organizers-of-canada-trucker-convoy-detail-spending-plan
-
 @ 5ffb8e1b:255b6735
2025-03-29 13:57:02
@ 5ffb8e1b:255b6735
2025-03-29 13:57:02As a fellow Nostrich you might have noticed some of my #arlist posts. It is my effort to curate artists that are active on Nostr and make it easier for other users to find content that they are interested in.
By now I have posted six or seven posts mentioning close to fifty artists, the problem so far is that it's only a list of handles and it is up to reader to click on each in order to find out what are the artist behind the names all about. Now I am going to start creating blog posts with a few artists mentioned in each, with short descriptions of their work and an image or to.
I would love to have some more automated mode of curation but I still couldn't figure out what is a good way for it. I've looked at Listr, Primal custom feeds and Yakihonne curations but none seem to enable me to make a list of npubs that is then turned into a feed that I could publicly share for others to views. Any advice on how to achieve this is VERY welcome !
And now lets get to the first batch of artists I want to share with you.
Eugene Gorbachenko
nostr:npub1082uhnrnxu7v0gesfl78uzj3r89a8ds2gj3dvuvjnw5qlz4a7udqwrqdnd Artist from Ukrain creating amazing realistic watercolor paintings. He is very active on Nostr but is very unnoticed for some stange reason. Make sure to repost the painting that you liked the most to help other Nostr users to discover his great art.
Siritravelsketch
nostr:npub14lqzjhfvdc9psgxzznq8xys8pfq8p4fqsvtr6llyzraq90u9m8fqevhssu a a lovely lady from Thailand making architecture from all around the world spring alive in her ink skethes. Dynamic lines gives it a dreamy magical feel, sometimes supported by soft watercolor strokes takes you to a ferytale layer of reality.
BureuGewas
nostr:npub1k78qzy2s9ap4klshnu9tcmmcnr3msvvaeza94epsgptr7jce6p9sa2ggp4 a a master of the clasic oil painting. From traditional still life to modern day subjects his paintings makes you feel the textures and light of the scene more intense then reality itself.
You can see that I'm no art critic, but I am trying my best. If anyone else is interested to join me in this curration adventure feel free to reach out !
With love, Agi Choote
-
 @ a0c34d34:fef39af1
2025-04-10 09:13:12
@ a0c34d34:fef39af1
2025-04-10 09:13:12Let’s talk longevity and quality of life. Have you prepared for Passover or Easter? Do you celebrate either? I’m going to my niece’s house for Passover and I will be devouring brisket and strawberry shortcake. I use to love the Easter candy my neighbor shared when I was a kid. Taboo during Passover but I snuck a peep or two. How afraid are you about the future? Are you keeping up with longevity technology? Do you have the dream of living a long, long life? Longevity technology combines the power of medicine, biotechnology and artificial intelligence to extend a healthy human lifespan. It’s about using cutting edge technology and medical advancements to extend the years we live in good health. The focus is on quality of life during extended years. With the rise of AI powered longevity clinics, treatments tailored to an individual’s genetic profile, lifestyle and medical history, and customized anti-aging interventions, personalized healthcare will become a reality over the next decade. I’m scared I won’t be able to afford housing or healthcare. Advanced medical services cost money, and they are only going to rise. As we stay independent longer and capable of living on our own, there will be more “smart” solutions available, more longevity technology advances. Imagine using the technology of today to have a home where you feel safe for your mother or grandmother so they can live independently. The costs of technology for a “smart” house? Running lights on the floorboards light up as you walk by, just one item I can think of that can keep senior citizens safe at home. I developed a plan for a 55+ community for senior citizens. I have seen similar plans. I think blockchain technology and utilizing tokenomics can only make housing cost effective for senior citizens in the future. When I sat down and wrote the Executive Summary for Onboard60 three years ago, a component was to develop a 55+ Active Senior Community using tokenomics, smart contracts and blockchain technology. Since then, when I say I want to make Onboard60 like the AARP of today, I’ve been told that’s impossible, not going to work and I am wasting my time with this whole project, senior citizens aren’t interested. They will be. As we move into a population explosion of senior citizens living longer, healthy and independently, I think we need to consider how we are going to afford our longevity. What type of care will you receive, how much will it cost? What will you be able to control as in the cost, the level of care you receive. What currency is used? Yes, currency. As we move forward with the integration of cryptocurrency into our financial system, we need to think of what currency is accepted. There will be facilities that use their own stablecoin or accept certain others. The non-traditional financial systems are here to stay. The United States has incorporated a few different cryptocurrencies. Large financial institutions have adapted to putting cryptocurrency into their investment portfolios. I didn’t expect this to happen in my lifetime. Seriously, I thought Onboard60 would have a few more years to develop, create a community of senior citizens. That’s not the case. The world is accelerating at an impossible rate to keep up with everything. It can be overwhelming and scary. How do I find companies that use blockchain and smart contracts? Are there companies where I can protect my property rights by putting them on chain? Are there health insurance companies that use smart contracts? Onboard60 is more than the Metaverse, YouTube and A Handbook for Noobies (Web3 1101 for Seniors). It’s about staying informed, safely, to achieve the future every senior citizen deserves. If you have any knowledge of such companies, please let me know. I have crypto accountants and lawyers in my toolbox. I look forward to adding to my toolbox. I want to be like the AARP for today’s world.
Thanks for reading, Be fabulous, Sandra Abrams Founder Onboard60
-
 @ 592295cf:413a0db9
2025-03-29 10:59:52
@ 592295cf:413a0db9
2025-03-29 10:59:52The journey starts from the links in this article nostr-quick-start-guide
Starting from these links building a simple path should not cover everything, because impossible.
Today I saw that Verbiricha in his workshop on his channel used nstart, but then I distracted And I didn't see how he did it.
Go to nstart.me and read: Each user is identified by a cryptographic keypair Public key, Private key (is a lot of stuff)
You can insert a nickname and go, the nickname is not unique
there is a email backup things interesting, but a little boring, i try to generate an email
doesn't even require a strong password ok.
I received the email, great, it shows me the nsec encrypted in clear,
Send a copy of the file with a password, which contains the password encrypted key I know and I know it's a tongue dump.
Multi signer bunker
That's stuff, let's see what he says.
They live the private key and send it to servers and you can recompose it to login at a site of the protocol nostr. If one of these servers goes offline you have the private key that you downloaded first and then reactivate a bunker. All very complicated. But if one of the servers goes offline, how can I remake the split? Maybe he's still testing.
Nobody tells you where these bunkers are.
Okay I have a string that is my bunker (buker://), I downloaded it, easy no, now will tell me which client accepts the bunker.. .
Follow someone before you start?
Is a cluster of 5 people Snowden, Micheal Dilger, jb55, Fiatjaf, Dianele.
I choice Snowden profile, or you can select multiple profiles, extra wild.
Now select 5 clients
Coracle, Chachi, Olas, Nostur, Jumble
The first is Coracle
Login, ok I try to post a note and signing your note the spin does not end.
Maybe the bunker is diffective.
Let's try Chachi
Simpler than Coracle, it has a type login that says bunker. see if I can post
It worked, cool, I managed to post in a group.
Olas is an app but also a website, but on the website requires an extension, which I do not have with this account.
If I download an app how do I pass the bunker on the phone, is it still a password, a qrcode, a qrcode + password, something like that, but many start from the phone so maybe it's easy for them. I try to download it and see if it allows me to connect with a bunker.
Okay I used private-qrcode and it worked, I couldn't do it directly from Olas because it didn't have permissions and the qrcode was < encrypted, so I went to the same site and had the bunker copied and glued on Olas
Ok then I saw that there was the qrcode image of the bunker for apps lol moment
Ok, I liked it, I can say it's a victory.
Looks like none of Snowden's followers are Olas's lover, maybe the smart pack has to predict a photographer or something like that.
Okay I managed to post on Olas, so it works, Expiration time is broken.
As for Nostur, I don't have an ios device so I'm going to another one.
Login with Jumble, it works is a web app
I took almost an hour to do the whole route.
But this was just one link there are two more
Extensions nostr NIP-07
The true path is nip-07-browser-extensions | nostr.net
There are 19 links, maybe there are too many?
I mention the most famous, or active at the moment
- Aka-profiles: Aka-profiles
Alby I don't know if it's a route to recommend
-
Blockcore Blockcore wallet
-
Nos2x Nos2x
-
Nos2xfox (fork for firefox) Nos2xfox
Nostore is (archived, read-only)
Another half hour to search all sites
Nostrapps
Here you can make paths
Then nstart selects Coracle, Chachi, Olas,Nostur and Jumble
Good apps might be Amethyst, 0xchat, Yakihonne, Primal, Damus
for IOS maybe: Primal, Olas, Damus, Nostur, Nos-Social, Nostrmo
On the site there are some categories, I select some with the respective apps
Let's see the categories
Go to Nostrapps and read:
Microbbloging: Primal
Streaming: Zap stream
Blogging: Yakihonne
Group chat: Chachi
Community: Flotilla
Tools: Form *
Discovery: Zapstore (even if it is not in this catrgory)
Direct Message: 0xchat
-
 @ fd208ee8:0fd927c1
2025-04-05 21:51:52
@ fd208ee8:0fd927c1
2025-04-05 21:51:52Markdown: Syntax
Note: This document is itself written using Markdown; you can see the source for it by adding '.text' to the URL.
Overview
Philosophy
Markdown is intended to be as easy-to-read and easy-to-write as is feasible.
Readability, however, is emphasized above all else. A Markdown-formatted document should be publishable as-is, as plain text, without looking like it's been marked up with tags or formatting instructions. While Markdown's syntax has been influenced by several existing text-to-HTML filters -- including Setext, atx, Textile, reStructuredText, Grutatext, and EtText -- the single biggest source of inspiration for Markdown's syntax is the format of plain text email.
Block Elements
Paragraphs and Line Breaks
A paragraph is simply one or more consecutive lines of text, separated by one or more blank lines. (A blank line is any line that looks like a blank line -- a line containing nothing but spaces or tabs is considered blank.) Normal paragraphs should not be indented with spaces or tabs.
The implication of the "one or more consecutive lines of text" rule is that Markdown supports "hard-wrapped" text paragraphs. This differs significantly from most other text-to-HTML formatters (including Movable Type's "Convert Line Breaks" option) which translate every line break character in a paragraph into a
<br />tag.When you do want to insert a
<br />break tag using Markdown, you end a line with two or more spaces, then type return.Headers
Markdown supports two styles of headers, [Setext] [1] and [atx] [2].
Optionally, you may "close" atx-style headers. This is purely cosmetic -- you can use this if you think it looks better. The closing hashes don't even need to match the number of hashes used to open the header. (The number of opening hashes determines the header level.)
Blockquotes
Markdown uses email-style
>characters for blockquoting. If you're familiar with quoting passages of text in an email message, then you know how to create a blockquote in Markdown. It looks best if you hard wrap the text and put a>before every line:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Markdown allows you to be lazy and only put the
>before the first line of a hard-wrapped paragraph:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Blockquotes can be nested (i.e. a blockquote-in-a-blockquote) by adding additional levels of
>:This is the first level of quoting.
This is nested blockquote.
Back to the first level.
Blockquotes can contain other Markdown elements, including headers, lists, and code blocks:
This is a header.
- This is the first list item.
- This is the second list item.
Here's some example code:
return shell_exec("echo $input | $markdown_script");Any decent text editor should make email-style quoting easy. For example, with BBEdit, you can make a selection and choose Increase Quote Level from the Text menu.
Lists
Markdown supports ordered (numbered) and unordered (bulleted) lists.
Unordered lists use asterisks, pluses, and hyphens -- interchangably -- as list markers:
- Red
- Green
- Blue
is equivalent to:
- Red
- Green
- Blue
and:
- Red
- Green
- Blue
Ordered lists use numbers followed by periods:
- Bird
- McHale
- Parish
It's important to note that the actual numbers you use to mark the list have no effect on the HTML output Markdown produces. The HTML Markdown produces from the above list is:
If you instead wrote the list in Markdown like this:
- Bird
- McHale
- Parish
or even:
- Bird
- McHale
- Parish
you'd get the exact same HTML output. The point is, if you want to, you can use ordinal numbers in your ordered Markdown lists, so that the numbers in your source match the numbers in your published HTML. But if you want to be lazy, you don't have to.
To make lists look nice, you can wrap items with hanging indents:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
But if you want to be lazy, you don't have to:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
List items may consist of multiple paragraphs. Each subsequent paragraph in a list item must be indented by either 4 spaces or one tab:
-
This is a list item with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus.
Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus. Donec sit amet nisl. Aliquam semper ipsum sit amet velit.
-
Suspendisse id sem consectetuer libero luctus adipiscing.
It looks nice if you indent every line of the subsequent paragraphs, but here again, Markdown will allow you to be lazy:
-
This is a list item with two paragraphs.
This is the second paragraph in the list item. You're only required to indent the first line. Lorem ipsum dolor sit amet, consectetuer adipiscing elit.
-
Another item in the same list.
To put a blockquote within a list item, the blockquote's
>delimiters need to be indented:-
A list item with a blockquote:
This is a blockquote inside a list item.
To put a code block within a list item, the code block needs to be indented twice -- 8 spaces or two tabs:
- A list item with a code block:
<code goes here>
Code Blocks
Pre-formatted code blocks are used for writing about programming or markup source code. Rather than forming normal paragraphs, the lines of a code block are interpreted literally. Markdown wraps a code block in both
<pre>and<code>tags.To produce a code block in Markdown, simply indent every line of the block by at least 4 spaces or 1 tab.
This is a normal paragraph:
This is a code block.Here is an example of AppleScript:
tell application "Foo" beep end tellA code block continues until it reaches a line that is not indented (or the end of the article).
Within a code block, ampersands (
&) and angle brackets (<and>) are automatically converted into HTML entities. This makes it very easy to include example HTML source code using Markdown -- just paste it and indent it, and Markdown will handle the hassle of encoding the ampersands and angle brackets. For example, this:<div class="footer"> © 2004 Foo Corporation </div>Regular Markdown syntax is not processed within code blocks. E.g., asterisks are just literal asterisks within a code block. This means it's also easy to use Markdown to write about Markdown's own syntax.
tell application "Foo" beep end tellSpan Elements
Links
Markdown supports two style of links: inline and reference.
In both styles, the link text is delimited by [square brackets].
To create an inline link, use a set of regular parentheses immediately after the link text's closing square bracket. Inside the parentheses, put the URL where you want the link to point, along with an optional title for the link, surrounded in quotes. For example:
This is an example inline link.
This link has no title attribute.
Emphasis
Markdown treats asterisks (
*) and underscores (_) as indicators of emphasis. Text wrapped with one*or_will be wrapped with an HTML<em>tag; double*'s or_'s will be wrapped with an HTML<strong>tag. E.g., this input:single asterisks
single underscores
double asterisks
double underscores
Code
To indicate a span of code, wrap it with backtick quotes (
`). Unlike a pre-formatted code block, a code span indicates code within a normal paragraph. For example:Use the
printf()function. -
 @ d360efec:14907b5f
2025-04-22 08:12:27
@ d360efec:14907b5f
2025-04-22 08:12:27ความทรงจำเรานั้นเชื่อได้แน่หรือ ?
"เพราะจิตเราเกิดดับทุกเสี้ยววินาที ทุกความทรงจำจึงสร้างขึ้นมาใหม่เสมอ ดังนั้นมันก็ไม่เหมือนต้นฉบับเป็นธรรมดา แต่ยังคงเค้าโครงเดิมอยู่ ความเปลี่ยนแปลงจึงเป็นนิรันดร์ค่ะ" - Lina Engword
เรามักจะคิดว่าความทรงจำของเราคือการบันทึกเหตุการณ์ในอดีตไว้อย่างแม่นยำ เหมือนการดูวิดีโอ 📼 หรือเปิดไฟล์คอมพิวเตอร์ 💾 แต่ในความเป็นจริงแล้ว แนวคิดนี้อาจไม่ใช่ภาพที่สมบูรณ์ บทความที่เรานำมาวิเคราะห์นี้ได้นำเสนอข้อคิดที่น่าสนใจเกี่ยวกับธรรมชาติของความทรงจำมนุษย์ ความน่าเชื่อถือของมัน และเชื่อมโยงไปถึงความจำเป็นในการฝึกฝนจิตตามหลักพุทธศาสนาเพื่อเข้าถึงความจริงที่เที่ยงแท้ 🧘♀️🔍
ความทรงจำไม่ใช่การบันทึก แต่เป็นการสร้างใหม่ 🏗️🧩
ประเด็นสำคัญที่บทความชี้ให้เห็นคือ ความทรงจำของมนุษย์ไม่ได้ทำงานเหมือนการ "บันทึก" เหตุการณ์ไว้ตายตัว 📼❌ แต่เปรียบเสมือน "ชิ้นส่วนของโค้ด" 💻 ที่จะถูก "สร้างขึ้นใหม่" 🏗️ ทุกครั้งที่เราพยายามระลึกถึง นั่นหมายความว่า ทุกครั้งที่เราดึงความทรงจำเก่าๆ กลับมา มันไม่ใช่การเปิดไฟล์เดิมซ้ำๆ แต่เป็นการประกอบชิ้นส่วนเหล่านั้นขึ้นมาใหม่ในห้วงเวลานั้นๆ กระบวนการนี้เองที่เปิดโอกาสให้เกิดการ "เติมเต็ม" ✨ หรือ "แก้ไข" ✏️ ข้อมูลในความทรงจำอยู่เสมอ ทำให้ความทรงจำที่เราเพิ่งนึกถึงอาจไม่เหมือนกับความทรงจำครั้งก่อนหน้าเสียทีเดียว 🔄
การปรุงแต่งด้วยเหตุผลและความคุ้นเคย 🤔➕🏠
สิ่งที่น่าสนใจอย่างยิ่งคือ ในกระบวนการ "สร้างใหม่" หรือ "ประกอบ" ความทรงจำขึ้นมานี้ มนุษย์มักจะเติม "เหตุผล"💡 หรือใส่สิ่งที่ตนเอง "คุ้นเคย" 🏠 ลงไปในเรื่องราวที่ระลึกได้เสมอ แม้ว่าสิ่งเหล่านั้นอาจจะไม่ได้เกิดขึ้นจริงหรือไม่เกี่ยวข้องโดยตรงกับเหตุการณ์นั้นๆ ก็ตาม ยกตัวอย่างเช่น เมื่อเราเล่าเรื่องในอดีต เรามักจะอธิบายว่าทำไมเราถึงทำสิ่งนั้น หรือทำไมเหตุการณ์นี้ถึงเกิดขึ้น โดยใส่เหตุผลที่เราคิดว่าสมเหตุสมผลในปัจจุบันลงไป สิ่งนี้ทำให้เรื่องราวในความทรงจำของเราดูมีความเชื่อมโยงและฟังดู "จริง" ✅ มากขึ้นในสายตาของเราเอง
เมื่อเราใส่เหตุผลหรือรายละเอียดที่คุ้นเคยลงไปในความทรงจำบ่อยครั้งเข้า มันก็จะยิ่งทำให้เรา "เชื่อ" 👍 โดยสนิทใจว่าสิ่งที่เราระลึกได้นั้นคือความจริงทั้งหมด ทั้งที่ความเป็นจริงของเหตุการณ์ดั้งเดิมอาจแตกต่างออกไป 🤥 นี่คือสาเหตุว่าทำไมคนสองคนจึงอาจมีความทรงจำเกี่ยวกับเหตุการณ์เดียวกันที่แตกต่างกันอย่างสิ้นเชิง ซึ่งปรากฏการณ์นี้สามารถอธิบายได้ดีด้วยตัวอย่างคลาสสิกในภาพยนตร์เรื่อง "ราโชมอน" (Rashomon) 🎬 ที่นำเสนอเหตุการณ์เดียวผ่านมุมมองและความทรงจำของตัวละครที่ขัดแย้งกันอย่างสิ้นเชิง แต่ทุกคนต่างเชื่อในสิ่งที่ตนเองจำได้ว่าเป็นความจริง 🤔❓
เครื่องมือและกระบวนการช่วยตรวจสอบความจริง 📱📹📝🔍
จากข้อจำกัดโดยธรรมชาติของความทรงจำนี้เอง ทำให้เห็นว่าเราไม่สามารถพึ่งพาสิ่งที่ 'จำได้' เพียงอย่างเดียวได้หากต้องการเข้าถึงความจริงที่เที่ยงแท้ เราจึงจำเป็นต้องมี 'กระบวนการตรวจสอบ' 🤔🔍 มาช่วยยืนยันหรือแก้ไขข้อมูลในความทรงจำ
ในยุคปัจจุบัน เรามีเครื่องมือภายนอกมากมายที่ช่วยในกระบวนการนี้ เช่น กล้องจากสมาร์ทโฟน 📱 หรือกล้องวงจรปิด 📹 ที่บันทึกเหตุการณ์ต่างๆ ไว้ได้อย่างเป็นกลาง ทำให้เรามี 'หลักฐาน' 📄 ที่เป็นรูปธรรมไว้อ้างอิงเพื่อเปรียบเทียบกับความทรงจำส่วนตัว ซึ่งบ่อยครั้งสิ่งที่กล้องเห็นนั้น 'ตรงกับความจริง' ✅ ในมุมมองที่ปราศจากอคติมากกว่าสิ่งที่ใจเราจำได้ การจดบันทึกด้วยเสียง 🎤 หรือการจดบันทึกเป็นลายลักษณ์อักษร 📝 ในทันที ก็เป็นอีกวิธีหนึ่งที่ช่วย 'ตรึง' ข้อมูลเบื้องต้นไว้ได้ระดับหนึ่งเช่นกัน ✍️
นอกจากเครื่องมือภายนอกแล้ว 'กระบวนการตรวจสอบเชิงจิตวิทยา' 🤔🧠 ที่เป็นระบบ ก็สามารถช่วยให้มนุษย์ค้นพบความจริงได้เช่นกัน ไม่ว่าจะเป็นกระบวนการซักถามในเชิงนิติวิทยาศาสตร์ 👮♀️ หรือแม้กระทั่งการฝึกฝนจิตเพื่อให้สามารถสังเกตการณ์ทำงานของตนเองได้อย่างละเอียดลึกซึ้ง ซึ่งนำเราไปสู่แนวคิดตามหลักพุทธศาสนา...
ทำไมพุทธศาสนาจึงสอนไม่ให้เชื่อแม้เป็นความคิดตัวเอง? 🙏🧠❌
จากธรรมชาติของความทรงจำและกระบวนการปรุงแต่งของจิตใจที่อธิบายมานี้เอง ทำให้เราเห็นความเชื่อมโยงกับหลักคำสอนในพุทธศาสนา 🙏 ที่เน้นย้ำให้เรา "ไม่เชื่อแม้แต่ความคิดตัวเอง" 🧠❌ อย่างปราศจากการพิจารณา เพราะความคิด อารมณ์ ความทรงจำ หรือแม้แต่ความรู้สึกมั่นใจอย่างแรงกล้าที่เรามีนั้น อาจถูกสร้างขึ้นหรือปรุงแต่งโดยกลไกของจิตใจที่ไม่ได้สะท้อนความจริงทั้งหมด 🤥
พุทธศาสนาชี้ให้เห็นว่า การจะเข้าถึงความจริงที่แท้จริงได้นั้น 🔍 จำเป็นต้องมีกระบวนการตรวจสอบภายในจิตใจ เปรียบเสมือนการสร้าง "อัลกอริทึม" 🤖 เพื่อตรวจทานว่าสิ่งที่เราคิดหรือจำได้นั้นเป็นความจริงหรือไม่ ✅❌ การจะทำเช่นนี้ได้ ไม่ใช่เรื่องง่าย และต้องอาศัยการฝึกฝนจิตอย่าง "สมาธิอย่างมาก" 🧘♂️🧘♀️ เพื่อให้จิตมีความตั้งมั่น เป็นระบบ และสามารถ "เห็นการดำเนินไปของจิตได้อย่างเป็นระบบ" 👀🔬 เห็นว่าจิตปรุงแต่งความทรงจำอย่างไร เห็นว่าเหตุผลที่เราใส่เข้าไปนั้นจริงหรือไม่ เป็นเพียงการตีความ หรือเป็นเพียงสิ่งที่ใจเราอยากให้เป็น
บทความยังกล่าวเสริมว่า ความทรงจำที่ "สด" ✨ หรือใกล้เคียงกับเวลาที่เกิดเหตุการณ์นั้นมักจะมีความน่าเชื่อถือมากกว่า 👍 แม้จะดู "ดิบๆ" หรือไม่ผ่านการปรุงแต่งมากนัก ซึ่งสอดคล้องกับแนวคิดที่ว่ายิ่งระยะเวลาผ่านไปนานเท่าไหร่ ⏳ ยิ่งมีการเรียกคืนความทรงจำนั้นๆ บ่อยครั้ง ความทรงจำก็ยิ่งมีโอกาสถูกแก้ไข เติมเต็ม หรือปรุงแต่งด้วยเหตุผลและความคุ้นเคยมากขึ้นเท่านั้น 🔄✏️
"ใดๆในโลกนั้นคือสมมุติ ความคิดความทรงจำ ก็เป็นสมมุติเพียง แต่เราต้องรู้จักใช้สมมุติให้เป็นประโยชน์ และรู้จักใช้มันให้เป็นเพื่อดำรงอยู่บนโลก"
สรุป ✨🧠🔍
โดยสรุปแล้ว บทความนี้เตือนใจเราว่า ความทรงจำของเราไม่ใช่กล้องวิดีโอที่บันทึกทุกอย่างไว้แม่นยำ 📼❌ แต่เป็นกระบวนการสร้างสรรค์ที่ซับซ้อนซึ่งมีแนวโน้มที่จะถูกปรุงแต่งด้วยเหตุผล ความคุ้นเคย และการตีความของเราเอง 🏗️🤔🏠 ความมั่นใจที่เรามีต่อสิ่งที่จำได้นั้น ไม่ได้เป็นหลักประกันว่าเป็นความจริงเสมอไป 👍🤥
การตระหนักถึงธรรมชาติข้อนี้ของจิต และการใช้เครื่องมือภายนอก 📱📹📝 รวมถึงการฝึกฝนจิตให้สามารถสังเกตการณ์ทำงานของมันได้อย่างละเอียดรอบคอบตามหลักพุทธศาสนา 🙏🧘♀️ จึงเป็นกุญแจสำคัญที่จะช่วยให้เราสามารถแยกแยะระหว่าง "ความจริง" ✅ กับ "สิ่งที่จิตปรุงแต่งขึ้น" 🤥 ได้มากขึ้น และช่วยให้เราเข้าใกล้ความเข้าใจในธรรมชาติของสรรพสิ่งได้อย่างเที่ยงตรง ไม่หลงติดอยู่ในวังวนของความทรงจำและความคิดที่อาจบิดเบือนไปจากความเป็นจริง 🔄
**#ความทรงจำ #จิตวิทยา #พุทธศาสนา #สมอง #สมาธิ #การฝึกจิต #ราโชมอน #ความจริง #ไม่เชื่อความคิด #ธรรมชาติของจิต #พัฒนาตนเอง #บทความน่ารู้ #เทคโนโลยี #บันทึกความจริง #พระอภิธรรม #พระหฤทัยสูตร #LinaEngword **
-
 @ 0edc2f47:730cff1b
2025-04-04 03:37:15
@ 0edc2f47:730cff1b
2025-04-04 03:37:15Chef's notes
This started as a spontaneous kitchen experiment—an amalgamation of recipes from old cookbooks and online finds. My younger daughter wanted to surprise her sister with something quick but fancy ("It's a vibe, Mom."), and this is what we came up with. It’s quickly established itself as a go-to favorite: simple, rich, and deeply satisfying. It serves 4 (or 1, depending on the day; I am not here to judge). Tightly wrapped, it will keep up to 3 days in the fridge, but I bet it won't last that long!
Details
- ⏲️ Prep time: 10 min
- 🍳 Cook time: 0 min
Ingredients
- 1 cup (240mL) heavy whipping cream
- 1/4 cup (24g) cocoa powder
- 5 tbsp (38g) Confectioners (powdered) sugar
- 1/4 tsp (1.25mL) vanilla extract (optional)
- Flaky sea salt (optional, but excellent)
Directions
-
- Whip the cream until frothy.
-
- Sift in cocoa and sugar, fold or gently mix (add vanilla if using).
-
- Whip to medium peaks (or stiff peaks, if that's more your thing). Chill and serve (topped with a touch of sea salt if you’re feeling fancy).
-
 @ d360efec:14907b5f
2025-04-22 07:54:51
@ d360efec:14907b5f
2025-04-22 07:54:51“คณิตศาสตร์” กุญแจเวทมนตร์ นักพนัน และ นักลงทุน ในนครเฮรันเทล นามกระฉ่อนเลื่องลือในหมู่นักเสี่ยงโชค เมื่อเอ่ยถึง “การพนัน” ภาพที่ชาวเมืองมักนึกถึงคือ “ยาจกข้างถนน”
มิใช่เรื่องแปลกประหลาดอันใด เพราะเป็นที่ร่ำลือกันว่า จ้าวแห่งหอคอยรัตติกาล ผู้คุมบ่อนพนัน มักร่ายเวทมนตร์สร้างเกมให้ตนเองได้เปรียบ เพื่อดูดกลืนเงินทองของผู้มาเยือน ดังนั้น การที่สามัญชนจะพิชิตเกมในระยะยาว จึงเป็นดั่งเงามายาที่จับต้องมิได้ กระนั้น ยังมีตำนานกล่าวขานถึงผู้กล้า ที่สามารถสร้างชื่อจาก “เกมพนัน” เช่น เวเนสซา รุสโซ นักเวทย์มนตร์ผู้ใช้กฎหมายแห่งแดนไกล ใช้เวลายาวนานถึงหกปี ร่ายเวทย์สะสมทรัพย์สินกว่าร้อยล้านเหรียญทอง จากการเล่นเกมไพ่ศักดิ์สิทธิ์ “โป๊กเกอร์” หรือแม้แต่ เอ็ดเวิร์ด โอ. ทอร์ป จอมปราชญ์ผู้สร้างกำไรถึงสามแสนหกหมื่นเหรียญทอง ภายในเจ็ดราตรี จากการเล่นเกมไพ่มนตรา “แบล็กแจ็ก” ด้วยเงินทุนตั้งต้นเพียงสามแสนสามหมื่นเหรียญทอง คิดเป็นอัตราเวทย์ตอบแทนร้อยสิบส่วน! เหล่าจอมยุทธ์เหล่านี้ มิได้อาศัยเพียงโชคช่วยชั่วครั้งชั่วคราวแล้วเลือนหาย แต่พวกเขากลับสามารถร่ายเวทย์สร้างผลตอบแทนระยะยาว จนเรียกได้ว่า ใช้ “หอคอยรัตติกาล” เป็นแหล่งเสบียงเลี้ยงชีพ โดยกุญแจเวทย์ที่บุคคลเหล่านี้ใช้ ก็คือ “คณิตศาสตร์” เหตุใด “คณิตศาสตร์” จึงช่วยให้ผู้คนเอาชนะ “การพนัน” ได้? และนอกจาก “การพนัน” แล้ว “คณิตศาสตร์” ยังสามารถประยุกต์ใช้กับสิ่งใดได้อีก? นักเล่าเรื่องแห่งเฮรันเทล จักไขปริศนาให้ฟัง เบื้องต้น ขอให้ท่านลองพิจารณาตนเอง ว่าเคยประสบพบพานเหตุการณ์เหล่านี้หรือไม่: * ตั้งมั่นว่า จักเสี่ยงโชคให้ได้กำไรเพียงเล็กน้อย แล้วจักหยุดพัก * แต่หากพลาดท่าเสียที จักจำกัดการสูญเสียให้เท่าทุนเดิมที่ตั้งไว้ * ครั้นเมื่อเวทมนตร์เข้าข้าง ได้กำไรมาแล้ว กลับโลภโมโทสัน อยากได้เพิ่มอีกนิด จึงร่ายเวทย์ต่อ * ทว่ากำไรเริ่มร่อยหรอ จนเหลือเพียงทุนเดิม สุดท้ายทุนที่ตั้งไว้คราแรกก็มลายสิ้น * จำต้องหาเงินทองมาลงเพิ่ม หวังทวงทุนคืน และพบว่าต้องสูญเสียเงินก้อนนั้นไปในห้วงเวลาต่อมา ลำดับเหตุการณ์ดังกล่าว เรียกได้ว่าเป็น “วงจรอุบาทว์” สำหรับนักพนันมากมายในเฮรันเทล ปริศนาที่ตามมาก็คือ เหตุใด “วงจรอุบาทว์” นี้จึงเกิดขึ้นซ้ำแล้วซ้ำเล่า? ส่วนหนึ่ง ย่อมเป็นเพราะอารมณ์อันแปรปรวนในการเสี่ยงโชคของแต่ละคน แต่อีกส่วนที่สำคัญยิ่งกว่า ต้องกล่าวว่าเป็นผลจาก “กลไกต้องสาป” ของจ้าวแห่งหอคอยรัตติกาล ซึ่งต้องกล่าวว่า เหล่าเจ้าของหอคอยรัตติกาลนั้น จักใช้หลักการทำนองเดียวกับ “สมาคมพ่อค้าผู้พิทักษ์” คือจักเก็บเงินทองจากชนจำนวนมาก เพื่อนำมาจ่ายให้กับชนเพียงหยิบมือ เพื่อล่อลวงให้ชนทั้งหลายเสี่ยงโชคต่อไป หรือทำให้เหล่านักพนันหวังว่า จักเป็นผู้โชคดีเฉกเช่นพวกเขาบ้าง แม้จะมีผู้โชคดีที่สามารถได้กำไรในเบื้องต้น แต่ในบั้นปลายก็จักพ่ายแพ้อยู่ดี ซึ่งเป็นไปตาม “กฎแห่งจำนวนมหาศาล” เพราะจ้าวแห่งหอคอยรัตติกาลนั้น ได้คำนวณและออกแบบระบบเกมที่ตนเองได้เปรียบในระยะยาวแล้ว จากตำนานนี้ ย่อมประจักษ์ชัดว่า แม้การพนันจักเป็นเรื่องของดวงชะตา แต่ก็ถูกรังสรรค์ขึ้นจากการคำนวณทางคณิตศาสตร์ ดังนั้น หากปรารถนาจะหาหนทางเอาชนะจ้าวแห่งหอคอยรัตติกาล ก็จำต้องเข้าใจ “คณิตศาสตร์” เสียก่อน ทีนี้ จงเงี่ยหูฟัง แล้วท่านจักได้ยินข้าไขปริศนา: ๑. ปริศนาแห่ง “กำไรคาดหวัง” สำหรับการแสวงหา “เกมเสี่ยงทาย” ที่ควรค่าแก่การเล่น หรือการเสี่ยง สิ่งแรกที่นักพนันพึงกระทำคือ “การประเมินกำไรคาดหวัง” หรือ “เวทคำนวณอนาคต” “กำไรคาดหวัง” ถูกคิดค้นโดย คริสเตียน ฮอยเกนส์ นักปราชญ์เวทย์ชาวดัตช์ เพื่อประเมินว่าเกมพนันแบบใดควรค่าแก่การเล่น ซึ่งมิใช่เพียงแค่การประเมินโอกาสแห่งชัยชนะเท่านั้น แต่ต้องคิดรวมขนาดของเงินเดิมพันไปด้วย โดยสูตรเวทย์คือ: กำไรคาดหวัง = (เงินที่ได้ x โอกาสชนะ) + (เงินที่เสีย x โอกาสแพ้) ดังนั้น หากปรารถนาจะสะสม “ทองคำมายา” ในระยะยาว จงเลือกเกมที่มี “กำไรคาดหวัง” เป็นบวก แต่หากพลาดพลั้งเข้าไปเล่นเกมที่ “กำไรคาดหวัง” เป็นลบ และบังเอิญว่าโชคชะตาเล่นตลกให้ได้เงินทองมาครอง พึงละทิ้งเกมนั้นเสียโดยพลัน เพราะท้ายที่สุดหากยังคงเล่นต่อไป ผู้อับโชคผู้นั้นก็คือตัวท่านเอง อย่างไรก็ตาม โดยธรรมดาแล้ว “กำไรคาดหวัง” ของเกมพนันที่มีเจ้ามือมักจักติดลบ จึงเป็นเรื่องยากยิ่งที่จะเอาชนะได้ เฉกเช่นตัวอย่างที่เราเห็น คือเกมในบ่อนพนัน หรือแม้แต่ “สลากกินแบ่งรัฐบาล” ก็ล้วนเป็นเกมที่มี “กำไรคาดหวัง” ติดลบทั้งสิ้น นอกจาก “กำไรคาดหวัง” จักถูกใช้กับการพนันได้แล้ว หลักเวทย์ “คณิตศาสตร์” ก็ยังสามารถประยุกต์ใช้กับการลงทุนได้ไม่แตกต่างกัน ตัวอย่างเช่น หากท่านเก็บสถิติข้อมูลการลงทุนของตนเอง แล้วพบว่ามีเพียงสามสิบส่วนร้อยเท่านั้น ที่ท่านซื้อ “ศิลาแห่งโชค” แล้วสร้างผลตอบแทนเป็นบวก แต่ท่านยังคงปรารถนาความสำเร็จในการลงทุน ก็จงจำกัดการขาดทุนแต่ละคราให้น้อยเข้าไว้ เช่น -๕% และปล่อยให้มีกำไรในแต่ละคราที่ลงทุน เช่น อย่างน้อย ๒๐% ซึ่งจากการใช้กลยุทธ์นี้ ท่านจักมี “กำไรคาดหวัง” = (๒๐% x ๐.๓) + (-๕% x ๐.๗) = ๒.๕% จักเห็นได้ว่า แม้ท่านจักมีจำนวนคราที่ขาดทุนบ่อยครั้ง แต่ก็ยังสามารถสร้างกำไรได้ หากคราที่กำไรนั้น สามารถทำเงินทองเป็นจำนวนมากได้ ๒. ปริศนาแห่ง “การบริหารหน้าตัก” หรือ “การบริหารเงินทุน” แม้ว่าท่านจักรับรู้ “กำไรคาดหวัง” แล้ว แต่หากท่านเผชิญหน้ากับการขาดทุนต่อเนื่องกัน ท่านก็อาจหมดเนื้อหมดตัวก่อนถึงคราที่จะกอบโกยเงินทองจากคราที่กำไร วิธีคลายปมปริศนานี้ก็คือ การมิลงเงินทองทั้งหมดของท่านในการลงทุนเพียงคราเดียว ซึ่งนอกจากการกระจายความเสี่ยงในการลงทุนหลาย “ศิลาแห่งโชค” หรือหลาย “เกมเสี่ยงทาย” แล้ว ท่านอาจกำหนดขนาดของการลงทุนแต่ละคราให้มิมากเกินไป แบบง่าย ๆ เช่น มิเกิน ๑๐% ของเงินลงทุนทั้งหมด หรือท่านอาจคำนวณขนาดของการลงทุนแต่ละคราด้วยสูตรทางคณิตศาสตร์ เช่น สูตร “การขาดทุนสูงสุดที่ท่านรับได้ (Value at Risk)” หรือ สูตร “ขนาดเดิมพันที่เหมาะสม (Kelly Formula)” ๓. ปริศนาแห่ง “อคติ” ในวงการพนัน มักมีอคติหนึ่งที่บังเกิดบ่อยครั้งกับผู้คน คือ “Gambler's Fallacy” หรือ “ความเชื่อผิด ๆ แห่งนักพนัน” ว่าหากเหตุการณ์หนึ่งบังเกิดบ่อยครั้งกว่าปรกติในช่วงเวลาหนึ่ง ๆ เหตุการณ์นั้นจักบังเกิดบ่อยครั้งน้อยลงในอนาคต ทั้ง ๆ ที่เหตุการณ์เหล่านั้นเป็นอิสระจากกันในทางสถิติ ยกตัวอย่างเช่น หากโยนเหรียญมนตราออกหัวไปแล้วสามครา ในคราที่สี่ หลายคนอาจคิดว่าโอกาสออกก้อยมากกว่าหัว แม้ว่าการโยนเหรียญแต่ละคราจะมิได้ส่งผลอันใดต่อกันเลย (จะโยนกี่ครา โอกาสหัวหรือก้อย ก็คือ ๕๐:๕๐ อยู่ยั่งยืน) หรือแม้กระทั่ง “สลากกินแบ่งรัฐบาล” มีหลายคนที่ซื้อเลขซ้ำกัน เพื่อหวังว่าจะถูกในงวดต่อ ๆ ไป ในวงการการลงทุน ก็มีลักษณะที่คล้ายคลึงกัน เช่น หาก “ศิลาแห่งโชค A” ราคาตกต่ำลงมาห้าครา บางคนอาจคิดว่าในคราที่หก ราคาของมันจักต้องเด้งขึ้นมา ซึ่งในความเป็นจริง หาได้เป็นเช่นนั้นเสมอไป จักเห็นได้ว่า แท้จริงแล้ว ไม่ว่าจักเป็น “เกมเสี่ยงทายแห่งโชคชะตา” หรือ “การผจญภัยในตลาดทุน” หากท่านมีความเข้าใจ และนำ “คณิตศาสตร์” เข้ามาเป็นรากฐาน มันก็อาจนำพาตัวท่านเอง ไปสู่จุดที่ได้เปรียบในเกมนั้น ได้เฉกเช่นกัน.. สูตรเวทย์มนตร์ที่ปรากฏในตำนาน: * กำไรคาดหวัง = (เงินที่ได้ x โอกาสชนะ) + (เงินที่เสีย x โอกาสแพ้) คำเตือนจากนักเล่าเรื่องแห่งเฮรันเทล: "พึงระลึกไว้เสมอว่า โชคชะตาเป็นสิ่งที่คาดเดาได้ยาก แม้เวทมนตร์คณิตศาสตร์จักช่วยนำทาง แต่ท้ายที่สุดแล้ว ความสำเร็จยังคงขึ้นอยู่กับการตัดสินใจและสติปัญญาของท่านเอง"
หวังว่าตำนานบทนี้จักเป็นประโยชน์แก่ท่านนะคะ
-
 @ 7bdef7be:784a5805
2025-04-02 12:37:35
@ 7bdef7be:784a5805
2025-04-02 12:37:35The following script try, using nak, to find out the last ten people who have followed a
target_pubkey, sorted by the most recent. It's possibile to shortensearch_timerangeto speed up the search.```
!/usr/bin/env fish
Target pubkey we're looking for in the tags
set target_pubkey "6e468422dfb74a5738702a8823b9b28168abab8655faacb6853cd0ee15deee93"
set current_time (date +%s) set search_timerange (math $current_time - 600) # 24 hours = 86400 seconds
set pubkeys (nak req --kind 3 -s $search_timerange wss://relay.damus.io/ wss://nos.lol/ 2>/dev/null | \ jq -r --arg target "$target_pubkey" ' select(. != null and type == "object" and has("tags")) | select(.tags[] | select(.[0] == "p" and .[1] == $target)) | .pubkey ' | sort -u)
if test -z "$pubkeys" exit 1 end
set all_events "" set extended_search_timerange (math $current_time - 31536000) # One year
for pubkey in $pubkeys echo "Checking $pubkey" set events (nak req --author $pubkey -l 5 -k 3 -s $extended_search_timerange wss://relay.damus.io wss://nos.lol 2>/dev/null | \ jq -c --arg target "$target_pubkey" ' select(. != null and type == "object" and has("tags")) | select(.tags[][] == $target) ' 2>/dev/null)
set count (echo "$events" | jq -s 'length') if test "$count" -eq 1 set all_events $all_events $events endend
if test -n "$all_events" echo -e "Last people following $target_pubkey:" echo -e ""
set sorted_events (printf "%s\n" $all_events | jq -r -s ' unique_by(.id) | sort_by(-.created_at) | .[] | @json ') for event in $sorted_events set npub (echo $event | jq -r '.pubkey' | nak encode npub) set created_at (echo $event | jq -r '.created_at') if test (uname) = "Darwin" set follow_date (date -r "$created_at" "+%Y-%m-%d %H:%M") else set follow_date (date -d @"$created_at" "+%Y-%m-%d %H:%M") end echo "$follow_date - $npub" endend ```
-
 @ 57d1a264:69f1fee1
2025-03-29 09:31:13
@ 57d1a264:69f1fee1
2025-03-29 09:31:13"THE NATURE OF BITCOIN IS SUCH THAT ONCE VERSION 0.1 WAS RELEASED, THE CORE DESIGN WAS SET IN STONE FOR THE REST OF ITS LIFETIME." - SATOSHI NAKAMOTO
"Reborn" is inspired by my Bitcoin journey and the many other people whose lives have been changed by Bitcoin. I’ve carved the hand in the “Gyan Mudra” or the “Mudra of Wisdom or Knowledge,” with an Opendime grasped between thumb and index finger alluding to the pursuit of Bitcoin knowledge. The hand emerges from rough, choppy water, and I've set the hand against an archway, through which, the copper leaf hints at the bright orange future made possible by Bitcoin.
Materials: Carrara Marble, Copper leaf, Opendime
Dimensions: 6" x 9" x 13"
Price: $30,000 or BTC equivalent
Enquire: https://www.vonbitcoin.com/available-works
X: https://x.com/BVBTC/status/1894463357316419960/photo/1
originally posted at https://stacker.news/items/928510
-
 @ ef53426a:7e988851
2025-04-22 07:47:07
@ ef53426a:7e988851
2025-04-22 07:47:07In 1997, an IBM supercomputer beat the sport’s greatest mind. Deep Blue II became the first machine to defeat a chess world champion — Garry Kasparov. Humans would never win at chess again.
But if computers have been better than us for so long, why do we still play chess? Don’t we always play to win?
Well, even though we’re unlikely to record a victory over the machines, chess has become more popular than ever. According to a June 2023 PBS feature, subscriptions to chess clubs have soared and earlier this year chess.com servers overloaded due to a the highest number of active users ever.
This is not just a fad based on The Queen’s Gambit (a 2020 Netflix adaptation). Over 100m people have registered on chess.com since then, and books, YouTube channels and other content is flourishing. A Grandmaster recently visited the city in Spain where I live, and thousands of people came to watch her play.
Here’s my theory behind the recent revival of chess. The answer to why we still play is what’s behind the game of chess — strategy and spatial recognition.
It’s a system of training ourselves to appreciate cause and consequence, to improve our decision making. The best players train against computers, knowing they can’t win, but they can learn.
The same is true with today’s writing landscape. Professionals are panicking that machines will produce most of the content we’ll read from now on. Writing will change — that’s true. AI can write faster and more (grammatically) accurately.
But what’s behind writing? 🧠 Patterns of structured thought 🗣️ Sound rhetoric 🖊️ The creativity of language 📚 The beauty of stories.
Writing is a skill that we still need to train.
If we don’t, how will we know what makes our words effective? How will we communicate? How will we make sense of our past?
We can use AI to help, but the words it processes belong to us.
Just as we have recognised the importance of the concepts behind chess, we must do the same for the process of writing.
-
 @ 2183e947:f497b975
2025-03-29 02:41:34
@ 2183e947:f497b975
2025-03-29 02:41:34Today I was invited to participate in the private beta of a new social media protocol called Pubky, designed by a bitcoin company called Synonym with the goal of being better than existing social media platforms. As a heavy nostr user, I thought I'd write up a comparison.
I can't tell you how to create your own accounts because it was made very clear that only some of the software is currently open source, and how this will all work is still a bit up in the air. The code that is open source can be found here: https://github.com/pubky -- and the most important repo there seems to be this one: https://github.com/pubky/pubky-core
You can also learn more about Pubky here: https://pubky.org/
That said, I used my invite code to create a pubky account and it seemed very similar to onboarding to nostr. I generated a private key, backed up 12 words, and the onboarding website gave me a public key.
Then I logged into a web-based client and it looked a lot like twitter. I saw a feed for posts by other users and saw options to reply to posts and give reactions, which, I saw, included hearts, thumbs up, and other emojis.
Then I investigated a bit deeper to see how much it was like nostr. I opened up my developer console and navigated to my networking tab, where, if this was nostr, I would expect to see queries to relays for posts. Here, though, I saw one query that seemed to be repeated on a loop, which went to a single server and provided it with my pubkey. That single query (well, a series of identical queries to the same server) seemed to return all posts that showed up on my feed. So I infer that the server "knows" what posts to show me (perhaps it has some sort of algorithm, though the marketing material says it does not use algorithms) and the query was on a loop so that if any new posts came in that the server thinks I might want to see, it can add them to my feed.
Then I checked what happens when I create a post. I did so and looked at what happened in my networking tab. If this was nostr, I would expect to see multiple copies of a signed messaged get sent to a bunch of relays. Here, though, I saw one message get sent to the same server that was populating my feed, and that message was not signed, it was a plaintext copy of my message.
I happened to be in a group chat with John Carvalho at the time, who is associated with pubky. I asked him what was going on, and he said that pubky is based around three types of servers: homeservers, DHT servers, and indexer servers. The homeserver is where you create posts and where you query for posts to show on your feed. DHT servers are used for censorship resistance: each user creates an entry on a DHT server saying what homeserver they use, and these entries are signed by their key.
As for indexers, I think those are supposed to speed up the use of the DHT servers. From what I could tell, indexers query DHT servers to find out what homeservers people use. When you query a homeserver for posts, it is supposed to reach out to indexer servers to find out the homeservers of people whose posts the homeserver decided to show you, and then query those homeservers for those posts. I believe they decided not to look up what homeservers people use directly on DHT servers directly because DHT servers are kind of slow, due to having to store and search through all sorts of non-social-media content, whereas indexers only store a simple db that maps each user's pubkey to their homeserver, so they are faster.
Based on all of this info, it seems like, to populate your feed, this is the series of steps:
- you tell your homeserver your pubkey
- it uses some sort of algorithm to decide whose posts to show you
- then looks up the homeservers used by those people on an indexer server
- then it fetches posts from their homeservers
- then your client displays them to you
To create a post, this is the series of steps:
- you tell your homeserver what you want to say to the world
- it stores that message in plaintext and merely asserts that it came from you (it's not signed)
- other people can find out what you said by querying for your posts on your homeserver
Since posts on homeservers are not signed, I asked John what prevents a homeserver from just making up stuff and claiming I said it. He said nothing stops them from doing that, and if you are using a homeserver that starts acting up in that manner, what you should do is start using a new homeserver and update your DHT record to point at your new homeserver instead of the old one. Then, indexers should update their db to show where your new homeserver is, and the homeservers of people who "follow" you should stop pulling content from your old homeserver and start pulling it from your new one. If their homeserver is misbehaving too, I'm not sure what would happen. Maybe it could refuse to show them the content you've posted on your new homeserver, keeping making up fake content on your behalf that you've never posted, and maybe the people you follow would never learn you're being impersonated or have moved to a new homeserver.
John also clarified that there is not currently any tooling for migrating user content from one homeserver to another. If pubky gets popular and a big homeserver starts misbehaving, users will probably need such a tool. But these are early days, so there aren't that many homeservers, and the ones that exist seem to be pretty trusted.
Anyway, those are my initial thoughts on Pubky. Learn more here: https://pubky.org/
-
 @ 83279ad2:bd49240d
2025-03-30 14:21:49
@ 83279ad2:bd49240d
2025-03-30 14:21:49Test
-
 @ 37c10448:f8256861
2025-04-22 07:44:10
@ 37c10448:f8256861
2025-04-22 07:44:10Title H1
Hello !
-
 @ d4cb227b:edca6019
2025-03-30 04:26:51
@ d4cb227b:edca6019
2025-03-30 04:26:51Dose: 30g coffee (Fine-medium grind size) 500mL soft or bottled water (97°C / 206.6°F)
Instructions: 1. Rinse out your filter paper with hot water to remove the papery taste. This will also preheat the brewer.
-
Add your grounds carefully to the center of the V60 and then create a well in the middle of the grounds.
-
For the bloom, start to gently pour 60mL of water, making sure that all the coffee is wet in this initial phase.
-
As soon as you’ve added your water, grab your V60 and begin to swirl in a circular motion. This will ensure the water and coffee are evenly mixed. Let this rest and bloom for up to 45 seconds.
-
Pour the rest of the water in in 2 phases. You want to try and get 60% of your total water in, within 30 seconds.
-
Pour until you reach 300mL total with a time at 1:15. Here you want to pour with a little agitation, but not so much that you have an uneven extraction.
-
Once you hit 60% of your total brew weight, start to pour a little slower and more gently, keeping your V60 cone topped up. Aim to have 100% of your brew weight in within the next 30 seconds.
-
Once you get to 500mL, with a spoon give the V60 a small stir in one direction, and then again in the other direction. This will release any grounds stuck to the side of the paper.
-
Allow the V60 to drain some more, and then give it one final swirl. This will help keep the bed flat towards the end of the brew, giving you the most even possible extraction.
-
-
 @ 57d1a264:69f1fee1
2025-03-28 10:32:15
@ 57d1a264:69f1fee1
2025-03-28 10:32:15Bitcoin.design community is organizing another Designathon, from May 4-18. Let's get creative with bitcoin together. More to come very soon.
The first edition was a bursting success! the website still there https://events.bitcoin.design, and here their previous announcement.
Look forward for this to happen!
Spread the voice:
N: https://njump.me/nevent1qqsv9w8p93tadlnyx0rkhexj5l48l... X: https://x.com/bitcoin_design/status/1905547407405768927
originally posted at https://stacker.news/items/927650
-
 @ 57d1a264:69f1fee1
2025-03-27 10:42:05
@ 57d1a264:69f1fee1
2025-03-27 10:42:05What we have been missing in SN Press kit? Most important, who the press kit is for? It's for us? It's for them? Them, who?
The first few editions of the press kit, I agree are mostly made by us, for us. A way to try to homogenize how we speek out SN into the wild web. A way to have SN voice sync, loud and clear, to send out our message. In this case, I squeezed my mouse, creating a template for us [^1], stackers, to share when talking sales with possible businesses and merchants willing to invest some sats and engage with SN community. Here's the message and the sales pitch, v0.1:
Reach Bitcoin’s Most Engaged Community – Zero Noise, Pure Signal.
Contributions to improve would be much appreciated. You can also help by simply commenting on each slide or leaving your feedback below, especially if you are a sale person or someone that has seen similar documents before.
This is the first interaction. Already noticed some issues, for example with the emojis and the fonts, especially when exporting, probably related to a penpot issue. The slides maybe render differently depending on the browser you're using.
@k00b it will be nice to have some real data, how we can get some basic audience insights? Even some inputs from Plausible, if still active, will be much useful.
[^1]: Territory founders. FYI: @Aardvark, @AGORA, @anna, @antic, @AtlantisPleb, @av, @Bell_curve, @benwehrman, @bitcoinplebdev, @Bitter, @BlokchainB, @ch0k1, @davidw, @ek, @elvismercury, @frostdragon, @grayruby, @HODLR, @inverselarp, @Jon_Hodl, @MaxAWebster, @mega_dreamer, @mrtali, @niftynei, @nout, @OneOneSeven, @PlebLab, @Public_N_M_E, @RDClark, @realBitcoinDog, @roytheholographicuniverse, @siggy47, @softsimon, @south_korea_ln, @theschoolofbitcoin, @TNStacker. @UCantDoThatDotNet, @Undisciplined
originally posted at https://stacker.news/items/926557
-
 @ d4cb227b:edca6019
2025-03-30 04:23:22
@ d4cb227b:edca6019
2025-03-30 04:23:22This method focuses on the amount of water in the first pour, which ultimately defines the coffee’s acidity and sweetness (more water = more acidity, less water = more sweetness). For the remainder of the brew, the water is divided into equal parts according to the strength you wish to attain.
Dose: - 20g coffee (Coarse ground coffee) - 300mL water (92°C / 197.6°F) Time: 3:30
Instructions: Pour 1: 0:00 > 50mL (42% of 120mL = 40% of total – less water in the ratio, targeting sweetness.) Pour 2: 0:45 > 70mL (58% of 120mL = 40% of total – the top up for 40% of total.) Pour 3: 1:30 > 60mL (The remaining water is 180mL / 3 pours = 60mL per pour) Pour 4: 2:10 > 60mL Pour 5: 2:40 > 60mL Remove the V60 at 3:30







