-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ 91bea5cd:1df4451c
2025-04-26 10:16:21
@ 91bea5cd:1df4451c
2025-04-26 10:16:21O Contexto Legal Brasileiro e o Consentimento
No ordenamento jurídico brasileiro, o consentimento do ofendido pode, em certas circunstâncias, afastar a ilicitude de um ato que, sem ele, configuraria crime (como lesão corporal leve, prevista no Art. 129 do Código Penal). Contudo, o consentimento tem limites claros: não é válido para bens jurídicos indisponíveis, como a vida, e sua eficácia é questionável em casos de lesões corporais graves ou gravíssimas.
A prática de BDSM consensual situa-se em uma zona complexa. Em tese, se ambos os parceiros são adultos, capazes, e consentiram livre e informadamente nos atos praticados, sem que resultem em lesões graves permanentes ou risco de morte não consentido, não haveria crime. O desafio reside na comprovação desse consentimento, especialmente se uma das partes, posteriormente, o negar ou alegar coação.
A Lei Maria da Penha (Lei nº 11.340/2006)
A Lei Maria da Penha é um marco fundamental na proteção da mulher contra a violência doméstica e familiar. Ela estabelece mecanismos para coibir e prevenir tal violência, definindo suas formas (física, psicológica, sexual, patrimonial e moral) e prevendo medidas protetivas de urgência.
Embora essencial, a aplicação da lei em contextos de BDSM pode ser delicada. Uma alegação de violência por parte da mulher, mesmo que as lesões ou situações decorram de práticas consensuais, tende a receber atenção prioritária das autoridades, dada a presunção de vulnerabilidade estabelecida pela lei. Isso pode criar um cenário onde o parceiro masculino enfrenta dificuldades significativas em demonstrar a natureza consensual dos atos, especialmente se não houver provas robustas pré-constituídas.
Outros riscos:
Lesão corporal grave ou gravíssima (art. 129, §§ 1º e 2º, CP), não pode ser justificada pelo consentimento, podendo ensejar persecução penal.
Crimes contra a dignidade sexual (arts. 213 e seguintes do CP) são de ação pública incondicionada e independem de representação da vítima para a investigação e denúncia.
Riscos de Falsas Acusações e Alegação de Coação Futura
Os riscos para os praticantes de BDSM, especialmente para o parceiro que assume o papel dominante ou que inflige dor/restrição (frequentemente, mas não exclusivamente, o homem), podem surgir de diversas frentes:
- Acusações Externas: Vizinhos, familiares ou amigos que desconhecem a natureza consensual do relacionamento podem interpretar sons, marcas ou comportamentos como sinais de abuso e denunciar às autoridades.
- Alegações Futuras da Parceira: Em caso de término conturbado, vingança, arrependimento ou mudança de perspectiva, a parceira pode reinterpretar as práticas passadas como abuso e buscar reparação ou retaliação através de uma denúncia. A alegação pode ser de que o consentimento nunca existiu ou foi viciado.
- Alegação de Coação: Uma das formas mais complexas de refutar é a alegação de que o consentimento foi obtido mediante coação (física, moral, psicológica ou econômica). A parceira pode alegar, por exemplo, que se sentia pressionada, intimidada ou dependente, e que seu "sim" não era genuíno. Provar a ausência de coação a posteriori é extremamente difícil.
- Ingenuidade e Vulnerabilidade Masculina: Muitos homens, confiando na dinâmica consensual e na parceira, podem negligenciar a necessidade de precauções. A crença de que "isso nunca aconteceria comigo" ou a falta de conhecimento sobre as implicações legais e o peso processual de uma acusação no âmbito da Lei Maria da Penha podem deixá-los vulneráveis. A presença de marcas físicas, mesmo que consentidas, pode ser usada como evidência de agressão, invertendo o ônus da prova na prática, ainda que não na teoria jurídica.
Estratégias de Prevenção e Mitigação
Não existe um método infalível para evitar completamente o risco de uma falsa acusação, mas diversas medidas podem ser adotadas para construir um histórico de consentimento e reduzir vulnerabilidades:
- Comunicação Explícita e Contínua: A base de qualquer prática BDSM segura é a comunicação constante. Negociar limites, desejos, palavras de segurança ("safewords") e expectativas antes, durante e depois das cenas é crucial. Manter registros dessas negociações (e-mails, mensagens, diários compartilhados) pode ser útil.
-
Documentação do Consentimento:
-
Contratos de Relacionamento/Cena: Embora a validade jurídica de "contratos BDSM" seja discutível no Brasil (não podem afastar normas de ordem pública), eles servem como forte evidência da intenção das partes, da negociação detalhada de limites e do consentimento informado. Devem ser claros, datados, assinados e, idealmente, reconhecidos em cartório (para prova de data e autenticidade das assinaturas).
-
Registros Audiovisuais: Gravar (com consentimento explícito para a gravação) discussões sobre consentimento e limites antes das cenas pode ser uma prova poderosa. Gravar as próprias cenas é mais complexo devido a questões de privacidade e potencial uso indevido, mas pode ser considerado em casos específicos, sempre com consentimento mútuo documentado para a gravação.
Importante: a gravação deve ser com ciência da outra parte, para não configurar violação da intimidade (art. 5º, X, da Constituição Federal e art. 20 do Código Civil).
-
-
Testemunhas: Em alguns contextos de comunidade BDSM, a presença de terceiros de confiança durante negociações ou mesmo cenas pode servir como testemunho, embora isso possa alterar a dinâmica íntima do casal.
- Estabelecimento Claro de Limites e Palavras de Segurança: Definir e respeitar rigorosamente os limites (o que é permitido, o que é proibido) e as palavras de segurança é fundamental. O desrespeito a uma palavra de segurança encerra o consentimento para aquele ato.
- Avaliação Contínua do Consentimento: O consentimento não é um cheque em branco; ele deve ser entusiástico, contínuo e revogável a qualquer momento. Verificar o bem-estar do parceiro durante a cena ("check-ins") é essencial.
- Discrição e Cuidado com Evidências Físicas: Ser discreto sobre a natureza do relacionamento pode evitar mal-entendidos externos. Após cenas que deixem marcas, é prudente que ambos os parceiros estejam cientes e de acordo, talvez documentando por fotos (com data) e uma nota sobre a consensualidade da prática que as gerou.
- Aconselhamento Jurídico Preventivo: Consultar um advogado especializado em direito de família e criminal, com sensibilidade para dinâmicas de relacionamento alternativas, pode fornecer orientação personalizada sobre as melhores formas de documentar o consentimento e entender os riscos legais específicos.
Observações Importantes
- Nenhuma documentação substitui a necessidade de consentimento real, livre, informado e contínuo.
- A lei brasileira protege a "integridade física" e a "dignidade humana". Práticas que resultem em lesões graves ou que violem a dignidade de forma não consentida (ou com consentimento viciado) serão ilegais, independentemente de qualquer acordo prévio.
- Em caso de acusação, a existência de documentação robusta de consentimento não garante a absolvição, mas fortalece significativamente a defesa, ajudando a demonstrar a natureza consensual da relação e das práticas.
-
A alegação de coação futura é particularmente difícil de prevenir apenas com documentos. Um histórico consistente de comunicação aberta (whatsapp/telegram/e-mails), respeito mútuo e ausência de dependência ou controle excessivo na relação pode ajudar a contextualizar a dinâmica como não coercitiva.
-
Cuidado com Marcas Visíveis e Lesões Graves Práticas que resultam em hematomas severos ou lesões podem ser interpretadas como agressão, mesmo que consentidas. Evitar excessos protege não apenas a integridade física, mas também evita questionamentos legais futuros.
O que vem a ser consentimento viciado
No Direito, consentimento viciado é quando a pessoa concorda com algo, mas a vontade dela não é livre ou plena — ou seja, o consentimento existe formalmente, mas é defeituoso por alguma razão.
O Código Civil brasileiro (art. 138 a 165) define várias formas de vício de consentimento. As principais são:
Erro: A pessoa se engana sobre o que está consentindo. (Ex.: A pessoa acredita que vai participar de um jogo leve, mas na verdade é exposta a práticas pesadas.)
Dolo: A pessoa é enganada propositalmente para aceitar algo. (Ex.: Alguém mente sobre o que vai acontecer durante a prática.)
Coação: A pessoa é forçada ou ameaçada a consentir. (Ex.: "Se você não aceitar, eu termino com você" — pressão emocional forte pode ser vista como coação.)
Estado de perigo ou lesão: A pessoa aceita algo em situação de necessidade extrema ou abuso de sua vulnerabilidade. (Ex.: Alguém em situação emocional muito fragilizada é induzida a aceitar práticas que normalmente recusaria.)
No contexto de BDSM, isso é ainda mais delicado: Mesmo que a pessoa tenha "assinado" um contrato ou dito "sim", se depois ela alegar que seu consentimento foi dado sob medo, engano ou pressão psicológica, o consentimento pode ser considerado viciado — e, portanto, juridicamente inválido.
Isso tem duas implicações sérias:
-
O crime não se descaracteriza: Se houver vício, o consentimento é ignorado e a prática pode ser tratada como crime normal (lesão corporal, estupro, tortura, etc.).
-
A prova do consentimento precisa ser sólida: Mostrando que a pessoa estava informada, lúcida, livre e sem qualquer tipo de coação.
Consentimento viciado é quando a pessoa concorda formalmente, mas de maneira enganada, forçada ou pressionada, tornando o consentimento inútil para efeitos jurídicos.
Conclusão
Casais que praticam BDSM consensual no Brasil navegam em um terreno que exige não apenas confiança mútua e comunicação excepcional, mas também uma consciência aguçada das complexidades legais e dos riscos de interpretações equivocadas ou acusações mal-intencionadas. Embora o BDSM seja uma expressão legítima da sexualidade humana, sua prática no Brasil exige responsabilidade redobrada. Ter provas claras de consentimento, manter a comunicação aberta e agir com prudência são formas eficazes de se proteger de falsas alegações e preservar a liberdade e a segurança de todos os envolvidos. Embora leis controversas como a Maria da Penha sejam "vitais" para a proteção contra a violência real, os praticantes de BDSM, e em particular os homens nesse contexto, devem adotar uma postura proativa e prudente para mitigar os riscos inerentes à potencial má interpretação ou instrumentalização dessas práticas e leis, garantindo que a expressão de sua consensualidade esteja resguardada na medida do possível.
Importante: No Brasil, mesmo com tudo isso, o Ministério Público pode denunciar por crime como lesão corporal grave, estupro ou tortura, independente de consentimento. Então a prudência nas práticas é fundamental.
Aviso Legal: Este artigo tem caráter meramente informativo e não constitui aconselhamento jurídico. As leis e interpretações podem mudar, e cada situação é única. Recomenda-se buscar orientação de um advogado qualificado para discutir casos específicos.
Se curtiu este artigo faça uma contribuição, se tiver algum ponto relevante para o artigo deixe seu comentário.
-
 @ 1f79058c:eb86e1cb
2025-04-25 09:27:02
@ 1f79058c:eb86e1cb
2025-04-25 09:27:02I'm currently using this bash script to publish long-form content from local Markdown files to Nostr relays.
It requires all of
yq,jq, andnakto be installed.Usage
Create a signed Nostr event and print it to the console:
markdown_to_nostr.sh article-filename.mdCreate a Nostr event and publish it to one or more relays:
markdown_to_nostr.sh article-filename.md ws://localhost:7777 wss://nostr.kosmos.orgMarkdown format
You can specify your metadata as YAML in a Front Matter header. Here's an example file:
```md
title: "Good Morning" summary: "It's a beautiful day" image: https://example.com/i/beautiful-day.jpg date: 2025-04-24T15:00:00Z tags: gm, poetry published: false
In the blue sky just a few specks of gray
In the evening of a beautiful day
Though last night it rained and more rain on the way
And that more rain is needed 'twould be fair to say.— Francis Duggan ```
The metadata keys are mostly self-explanatory. Note:
- All keys except for
titleare optional date, if present, will be set as thepublished_atdate.- If
publishedis set totrue, it will publish a kind 30023 event, otherwise a kind 30024 (draft) - The
dtag (widely used as URL slug for the article) will be the filename without the.mdextension
- All keys except for
-
 @ 8d5ba92c:c6c3ecd5
2025-04-25 09:14:46
@ 8d5ba92c:c6c3ecd5
2025-04-25 09:14:46Money is more than just a medium of exchange—it’s the current that drives economies, the lifeblood of societies, and the pulse of civilization itself. When money decays, so does the culture it sustains. Take fiat, for example. Created out of thin air and inflated into oblivion, it acts like poison—rewarding conformity over sovereignty, speculation over creation, and exploitation over collaboration.
A culture built this way fails to foster true progress. Instead, it pushes us into darker corners where creativity and truth become increasingly scarce.
From the food we eat to the media we consume, much of modern culture has become a reflection of this problem—prioritizing shortcuts, convenience, and profit at any cost. It seems there’s no room left for depth, authenticity, or connection anymore.
Art, for example—once a sacred space for meaning, and inner calling—has not been spared either. Stripped of its purpose, it too falls into gloom, weaponized to divide and manipulate rather than inspire beauty and growth.
“Art is the lie that reveals the truth” as Picasso once said.
Indeed, this intriguing perspective highlights the subjectivity of truth and the many ways art can be interpreted. While creative expression doesn’t always need to mirror reality one-to-one—actually, often reshaping it through the creator’s lens—much of what we’re surrounded with these days feels like a dangerous illusion built on the rotten incentives of decaying values.
The movies we watch, the music we hear, and the stories we absorb from books, articles, ads, and commercials—are too often crafted to condition specific behaviors. Greed, laziness, overconsumption, ignorance (feel free to add to this list). Instead of enriching our culture, they disconnect us from each other, as well as from our own minds, hearts, and souls.
If you see yourself as a Bitcoiner—or, as I like to call it, ‘a freedom fighter at heart’—and you care about building a world based on truth, freedom, and prosperity, please recognize that culture is also our battleground.
Artistic forms act as transformative forces in the fight against the status quo.
Join me and the hundreds of guests this May at Bitcoin FilmFest 2025.
You don’t have to be a creative person in the traditional sense—like a filmmaker, writer, painter, sculptor, musician, and so on—to have a direct impact on culture!
One way or another, you engage with creative realms anyway. The deeper you connect with them, the better you understand the reality we live in versus the future humanity deserves.
I know the process may take time, but I truly believe it’s possible. Unfiat The Culture!
Bitcoin FilmFest 2025. May 22-25, Warsaw, Poland.
The third annual edition of a unique event built at the intersection of independent films, art, and culture.
“Your narrative begins where centralized scripts end—explore the uncharted stories beyond the cinema.” - Details: bitcoinfilmfest.com/bff25/ - Grab 10% off your tickets with code YAKIHONNE!
-
 @ c631e267:c2b78d3e
2025-04-25 20:06:24
@ c631e267:c2b78d3e
2025-04-25 20:06:24Die Wahrheit verletzt tiefer als jede Beleidigung. \ Marquis de Sade
Sagen Sie niemals «Terroristin B.», «Schwachkopf H.», «korrupter Drecksack S.» oder «Meinungsfreiheitshasserin F.» und verkneifen Sie sich Memes, denn so etwas könnte Ihnen als Beleidigung oder Verleumdung ausgelegt werden und rechtliche Konsequenzen haben. Auch mit einer Frau M.-A. S.-Z. ist in dieser Beziehung nicht zu spaßen, sie gehört zu den Top-Anzeigenstellern.
«Politikerbeleidigung» als Straftatbestand wurde 2021 im Kampf gegen «Rechtsextremismus und Hasskriminalität» in Deutschland eingeführt, damals noch unter der Regierung Merkel. Im Gesetz nicht festgehalten ist die Unterscheidung zwischen schlechter Hetze und guter Hetze – trotzdem ist das gängige Praxis, wie der Titel fast schon nahelegt.
So dürfen Sie als Politikerin heute den Tesla als «Nazi-Auto» bezeichnen und dies ausdrücklich auf den Firmengründer Elon Musk und dessen «rechtsextreme Positionen» beziehen, welche Sie nicht einmal belegen müssen. [1] Vielleicht ernten Sie Proteste, jedoch vorrangig wegen der «gut bezahlten, unbefristeten Arbeitsplätze» in Brandenburg. Ihren Tweet hat die Berliner Senatorin Cansel Kiziltepe inzwischen offenbar dennoch gelöscht.
Dass es um die Meinungs- und Pressefreiheit in der Bundesrepublik nicht mehr allzu gut bestellt ist, befürchtet man inzwischen auch schon im Ausland. Der Fall des Journalisten David Bendels, der kürzlich wegen eines Faeser-Memes zu sieben Monaten Haft auf Bewährung verurteilt wurde, führte in diversen Medien zu Empörung. Die Welt versteckte ihre Kritik mit dem Titel «Ein Urteil wie aus einer Diktatur» hinter einer Bezahlschranke.
Unschöne, heutzutage vielleicht strafbare Kommentare würden mir auch zu einigen anderen Themen und Akteuren einfallen. Ein Kandidat wäre der deutsche Bundesgesundheitsminister (ja, er ist es tatsächlich immer noch). Während sich in den USA auf dem Gebiet etwas bewegt und zum Beispiel Robert F. Kennedy Jr. will, dass die Gesundheitsbehörde (CDC) keine Covid-Impfungen für Kinder mehr empfiehlt, möchte Karl Lauterbach vor allem das Corona-Lügengebäude vor dem Einsturz bewahren.
«Ich habe nie geglaubt, dass die Impfungen nebenwirkungsfrei sind», sagte Lauterbach jüngst der ZDF-Journalistin Sarah Tacke. Das steht in krassem Widerspruch zu seiner früher verbreiteten Behauptung, die Gen-Injektionen hätten keine Nebenwirkungen. Damit entlarvt er sich selbst als Lügner. Die Bezeichnung ist absolut berechtigt, dieser Mann dürfte keinerlei politische Verantwortung tragen und das Verhalten verlangt nach einer rechtlichen Überprüfung. Leider ist ja die Justiz anderweitig beschäftigt und hat außerdem selbst keine weiße Weste.
Obendrein kämpfte der Herr Minister für eine allgemeine Impfpflicht. Er beschwor dabei das Schließen einer «Impflücke», wie es die Weltgesundheitsorganisation – die «wegen Trump» in finanziellen Schwierigkeiten steckt – bis heute tut. Die WHO lässt aktuell ihre «Europäische Impfwoche» propagieren, bei der interessanterweise von Covid nicht mehr groß die Rede ist.
Einen «Klima-Leugner» würden manche wohl Nir Shaviv nennen, das ist ja nicht strafbar. Der Astrophysiker weist nämlich die Behauptung von einer Klimakrise zurück. Gemäß seiner Forschung ist mindestens die Hälfte der Erderwärmung nicht auf menschliche Emissionen, sondern auf Veränderungen im Sonnenverhalten zurückzuführen.
Das passt vielleicht auch den «Klima-Hysterikern» der britischen Regierung ins Konzept, die gerade Experimente zur Verdunkelung der Sonne angekündigt haben. Produzenten von Kunstfleisch oder Betreiber von Insektenfarmen würden dagegen vermutlich die Geschichte vom fatalen CO2 bevorzugen. Ihnen würde es besser passen, wenn der verantwortungsvolle Erdenbürger sein Verhalten gründlich ändern müsste.
In unserer völlig verkehrten Welt, in der praktisch jede Verlautbarung außerhalb der abgesegneten Narrative potenziell strafbar sein kann, gehört fast schon Mut dazu, Dinge offen anzusprechen. Im «besten Deutschland aller Zeiten» glaubten letztes Jahr nur noch 40 Prozent der Menschen, ihre Meinung frei äußern zu können. Das ist ein Armutszeugnis, und es sieht nicht gerade nach Besserung aus. Umso wichtiger ist es, dagegen anzugehen.
[Titelbild: Pixabay]
--- Quellen: ---
[1] Zur Orientierung wenigstens ein paar Hinweise zur NS-Vergangenheit deutscher Automobilhersteller:
- Volkswagen
- Porsche
- Daimler-Benz
- BMW
- Audi
- Opel
- Heute: «Auto-Werke für die Rüstung? Rheinmetall prüft Übernahmen»
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 5188521b:008eb518
2025-04-25 08:06:11
@ 5188521b:008eb518
2025-04-25 08:06:11Ecology
When my father died, an entire ecosystem of beneficiaries withered. Moussa Ag El Khir funded scholarships and community projects, paying thousands of Dinars monthly to stop the oasis town of In Salah from burning up. The few families we knew operating outside the oil-field economy would be forced to flee to the Mediterranean coast, along with just about every other Berber.
It wasn’t unexpected. My father had cystic fibrosis for all sixty-one years of his life. So far, that’s the only legacy he’s passed on to his children. My brothers are just carriers, but me, his precious daughter ended up like him in more ways than one.
We sat there in the lawyer’s office in Algiers, my brothers and I, staring at the ledger which contained payment for his life’s work.
“And he only left one word in his will?” asked Ibrahim for the third time. Ecology.
The lawyer said Moussa was very clear. He chose each of the keys himself. The contents of the ledger would belong to whoever could decode his life — those who understood the real meaning. Then he cut all communications and walked into the Sahara. The Tuareg caravan on the road to Akabli found his body a week later, reddened by sand burn.
Earth
We made an agreement that day. To share each word we discovered. We could break the code together. Of course, Ibrahim and Hama didn’t share anything. We barely speak. That’s what happens when one child follows their father into science, and her two brothers move to France the minute they get rich enough to buy a wife. I bet they spent longer looking into legal loopholes to get their hands on my father’s assets than they did trying to identify the keys.
That day was the start of my second life, and I went from research assistant at a regional university to private-key detective. 2048 words and few clues where to start. Although I was 27, I was virtually a grandmother according to the In Salah wives. But of course, I could never be a grandmother, or even a mother. Every night, I scoured photos in the family archive. An initial sweep of his digital footprint returned no out-of-place instances of any keywords.
It took me a year to find the GPS tag he’d added to one photo — an eighteen-year-old daughter standing next to a father proud of his first infinite solar prototype. The panel has long-since been torn out by the oil corp, but the base is still there. I drove the three kilometres from the town limit and shone the high beams at the spot. When I got out, the air was cool but still thick with sand. A few more steps through sinking dunes, and I saw it. He’d scratched a little globe into the blistered metal, and for a moment, my mucus-laden lungs tasted clear air.
Trigger
The next word took three years. Friends, contacts, professors, biographers — visits to anyone with whom he might have left a clue. But it was in the In Salah hospital, where, upon a routine CF checkup with Jerome Devailier, a French doctor, ‘trigger’ appeared. The government might stack everything against the desert peoples, but they hadn’t taken away healthcare. I’d been living off the kindness of neighbours while finishing my thesis on the very solar technology my father developed. How could he have known the ‘buyer’ was just a tendril of the very oil company he sought to defeat.
Dr Devalier went through the list of carcinogens and allergens to avoid with my new drugs. Over forty triggers which could be my downfall. If I was lucky, I’d live as long as my father did.
By then, my research stipend was long gone. I existed on toughened bread and soup, which always carried the taste of the scorched city air. Yet, I stayed. The public library, disconnected from the grid by the oil corp, was where I finished my manuscript. They would fight its publication. Since father’s money no longer flowed into the town, many had deserted me. There were those who said he killed an entire people by selling his solar patent to the wrong buyers. Others in In Salah worshipped his name, but eventually, they all trudged north to the cities. My brothers sold the family home from under me, forcing me to follow.
When I returned from the hospital, I dug out my father’s medical documents. On every page, the word ‘trigger’ was underlined. That was the moment I knew my life’s work would be unlocking the ledger, not publishing studies on long-dead solar panel technology. That battle was lost.
They
All we need is a simple document, but here, it is the administrators’ job to send people away. Physical copies are only issued in extreme circumstances. Citizens’ Registry screens played endless repetitions of how to apply for digital documents. The shrill voices of family members desperate for the original copy of a pirated document drowned the TV messaging. Women removed headscarves and revealed thick black hair; teenagers paced. The atmosphere thickened with sweat. And hours passed. Each appointment required a reset of digital protocol, biometric tests, and identity cards from legal descendents. Through counterfeit identities, our Dinars leak into the hands of criminals, but still the government denies the need for bitcoin. They just print more money. They is the word my father used for the government that fought his patent so hard.
After a four-hour wait, I discovered that the physical death certificate included an ‘identifying mark’ on the deceased’s body. The ink was fresh — etched into the shoulder blade of a man who wished to turn his back on the government that ignored its people. The tattoo read aqqalan, the Tamasheq word for they.
Scheme
It took two trips to his cluttered Marseille office to convince him I was serious. Two visas, two flights, and the small amount from the sale of the family house. But few detectives wanted to work for a promise.
The ledger could not legally be owned in Algeria, and Laurent Mercier was the only serious professional who entertained a percentage of what was on there. The solar tech patent and documents from my father were enough to start Laurent on the trail. ‘Preliminary,’ he said, until I had the ledger in my possession.
“Flying is not easy with my condition,” I said.
He lowered his sunglasses. “Working is not easy without money.”
Contact with my brother through the lawyer in Algiers was achingly slow, but eventually they agreed to give me possession. What was 33% of nothing anyway? Years had gone by.
So, when I sat for the second time, in the sweaty office in Marseille, I gave Laurent the ledger, and he handed me a surprise. In all his business affairs, my father used little English, but the word ‘scheme’ appeared in all three company names he incorporated in the last three years of his life. We had our fifth word, and I finally had someone on my side.
Make
Some days, I could barely walk to the public library. I became lethargic and mostly sat in the cool dark of my room in the shelter. The government refused to provide housing outside of Algiers, but a Tuareg organisation from Mali opened a shelter in In Salah. Bulging eyes and faded clothes stared back in the mirror each day. How long had it been since I’d been to a wedding, or celebrated a friend’s child? Occupants came and went, and all that was left was a barren room and one meal per day.
As the sun punished the city with every ray of Allah’s untapped gift, streets grew thick with dust, and the local government fell, seat by seat, to oil execs. The only transport running was to and from the oil fields, which belched the remnants of the land into the sky. And still they worked. Still they sat on my father’s patent and refused to supply the world with efficient solar power.
With little else to cling onto, I harboured thoughts of how I could spend the ledger money. Fixing the town and replanting lost gardens. Bringing people back. That all took a back seat to decoding the message my father was sending. Laurent and I began to believe that the keys he chose formed some sort of instruction for his legacy.
Ten years to the day after his death, I was in the public library, looking for clues in an English history book. On my exit, the librarian stopped me.
“We have a gift for you, Kana.”
I waited while he fetched a package.
“Your father instructed me to give this to you. But not before this date.”
My hands tore open the package. More books, technical manuals, and hand-written notes. Amongst the papers was a tasselled leather bookmark embossed with the four letters that comprised one of the seven missing words. Make.
Citizen
It’s hard for a father in Algeria to admit to his daughter that she is his spirit — the heir to his life’s work. Of course he felt terrible guilt after our mother’s passing. That was when the letters started.
Moussa wrote to himself really, trying to come to terms with bringing a protégé into the world with a bright scientific mind and lungs that would snap her life expectancy. We communicated by letter for the last few years of his life — sharing the breakthroughs of his findings and what it might mean for our decaying oasis town. Analogue writing was the only real privacy, he said. His letters always ran to the same length, as if they were one lesson divided into equal chunks. We even exchanged letters during his last hospitalisation in Algiers. Those words were the only real strength I gained.
It was Laurent who analysed the letters with a new text scanning tool. For me, my father’s last letters were advice, regret, pain, and love, but to Laurent, they were simply a puzzle to solve to get one step closer.
Our letters gave Laurent the idea to communicate via physical mail. The process was painful, with letters sent from outlying towns before being shipped across the Alboran Sea and up into France. Muatin was one name my father called me. Like him, I dreamed of helping many through science. This was one of the few Arabic words in the French letters he wrote. It was also the only keyword included in any of the letters. Citizen.
When
Years of quiet followed. In Salah became unlivable after they co-opted the city reservoir for cooling drilling rigs. Each study that proved the field was still viable funnelled funds away from the locals who clung on. Resettlement benefits went up, and all but the semi-nomadic Tuaregs left. I followed. My health could not take much more desert. In the cooler coastal plains, I recovered strength, and subsidies for new medications helped me survive on a meagre teaching salary.
With no further clues, my Marseillais detective lost interest. His last letter, sent years ago, stated with unusual brevity that he was resigning the case. No payment was due.
I had lost my health, my father, his work, my money, our house, the town, and I spent each week delivering science and English classes to teenagers. They had no more hope for our country than I had. Algerians had already lost the Sahara. A one-degree temperature shift each decade of my life had shrunk Africa and sent its peoples northwards.
My father’s word puzzle occupied my thoughts. The combinations and permutations of letters and characters had millions of possible meanings but only one correct answer. Yet simple linguistic logic provided the next word. The headteacher was a linguist — a profession long lost to the higher-powered text analysers and language AI. He spoke little English but asked about the categorisations of grammatical terms in the 2048 key words.
“Why do you ask?”
“Because,” he said, “for a sentence of twelve words, at least one conjunction is necessary to form a second clause.”
He was right. I had been focussing on lists and complex codes to build my father’s motto. When I got home, I furiously searched my list of terms for conjunctions. I found only one. ‘When.’
Can
The permutations were still huge. Even eliminating some of the more conceptual words did not help. Millions of sentences existed in my dead father’s mind. Millions of meanings, all lost to the need for more energy to fund the world’s great thirst for energy. Still, the panels in most of the ‘dead middle’ (as the space between the tropics became known) melted at over 50 degrees.
I was back in Paris for CF treatment. As a young woman, I would have been pleased to make fifty years. But the realities of daily visits and the sickness brought on by medication stung. I wanted things to end, even when I discovered the next key.
It had been years since I had dreamed of the freedoms my father’s fortune could bring. Parts of Asia held out against bitcoin, but the cost of countries doing business off-network had become prohibitive. Eventually, the fossil conglomerates would give in to the need for solar mining and the provision of universal energy.
It was in a Parisian hospital bed that I discovered ‘can.’ My wardmate, a rough labourer from Oran, found a biography in the hospital library that made me sit up straight. ‘Can’ was repeated in almost every description of my father in his one-time business partner’s book. And it was this Arabian ‘businessman,’ Abdulkarim Rahman, who brokered the deal that robbed the world of infinite solar power. Each page mocked my father as believing only physical impossibilities are impossible. He branded him the ‘can man.’
Drastic
During my recuperation, I spent the final two weeks of my visa stay in Marseille. My days passed with endless algorithm tweaks to reject or accept word orders for the elusive twelve-word sentence my father once wrote.
Food lost its taste, and friends and colleagues in academia had scattered. In-person meetings were often contained to the night hours, but Marseille was not a place to go out after dark. The latest protests had gotten violent, and the government looked likely to topple. My people had always been resilient, but when the option to move and operate a caravan was removed by General Hafiz, part of my spirit died. I resolved to spend my final years in In Salah, however uncomfortable they would be.
My final port of call before returning was Laurent’s office. The eTaxi cast me out into the dusty street, and I wheezed as I climbed the three flights of stairs to his tiny door on Rue Marché. We hadn’t spoken in years, but I was surprised to find a different name about the door. Pascale Dupont, Investigateur.
The assistant I remembered was quite the opposite to Laurent — slow and methodical, short and heavy set.
“Madame,” he said. “I have difficult news.”
Their business had always straddled the law, but I never imagined an ex-officer of the law could be convicted of treason.
“A closed-door trial,” said Pascale. Then he handed over an air-gapped 3D storage file. “Laurent knew you would come for this.”
My mind cast forward to the reams of information he must have built on my father. The patents and technical diagrams he illegally acquired and other clues. I instantly recognised the brand of storage file as a keyword. Drastic.
“How can I thank him?”
“He is dead, madame.” Pascale hung his head. “He survived prison for only two weeks.”
Must
My final years brought me home. In Salah had gained fame for its one group of Tuaregs who refused to leave. The Lakzis owned a house in a desperate condition, not dissimilar to my failing body. By the age of fifty-two, I could no longer walk, but they welcomed me. I pooled my disability allowance and some money I’d gained from selling my father’s watch. We waited for the world to mourn the death of a once great city. We would keep it alive by refusing to move, by refusing to permit its rebranding as an ‘industrial area.’ Now the oil fields were finally drying up, they wanted to dig under the town.
We had managed to eliminate half of the remaining words. Just under 1,000 possible selections for the final two words, but little idea of an order.
The problem was that I was the only English speaker among them, and it took great energy to attempt to teach the meaning of the words and possible grammatical constructions for my father’s sentence.
But soon, patterns began to emerge. Fragments of word pairings and groups. ‘Trigger drastic scheme’ appeared again and again in the permutations. ‘They can’ and ‘When they can’ gave a tantalising glimpse. We ranked sentences in terms of likelihood to form the full key and categorised them by the most likely remaining words. Due to the need for a modal verb, ‘must’ scored highest by our calculations.
In this race to unlock the ledger before In Salah’s destruction, we nosed ahead.
Yet the day of that discovery was my final day in the desert. An air ambulance transported my feeble body to Algiers, and I would never return.
They messaged me — so close. They would unlock the ledger with the final word after my operation. The bitcoin could undo the wrongs of the past, and my father’s sentence would live on.
End
The phrase which began the global revolution first appeared on the wall of a much-disputed oil refinery in the desert outside In Salah, Algeria.
When they can make ecology end, citizen earth must trigger drastic scheme
Soon, the graffiti marked government buildings in Algiers. Activists took to the streets. Governments crumbled and currencies collapsed. Climate groups received massive donations said to come from ‘the one,’ a ledger with a huge stack written off by financiers the world over. The codebreaker credited with unlocking the ledger was unable to witness the transfer of 10,000 coins to the Global Climate Fund due to her death, aged 52, from a congenital condition.
The words of Moussa Ag El Khir now mark each of the millions of panels, which line the ‘dead middle.’ They contribute over 80% of the Earth’s power supply.
To mark the fiftieth anniversary of his death, the World Climate Forum will be held in the town of his birth, In Salah, Algeria. This story, compiled from the diaries of his daughter, Kana Ult El Khir, will be read as the opening address of the conference.
This story was originally published in 21 Futures: Tales From the Timechain
To continue the story of the real-world treasure (sats) use the address (it's real).\ Who knows, maybe some zaps will find their way into the wallet...

-
 @ 1f79058c:eb86e1cb
2025-04-26 13:53:50
@ 1f79058c:eb86e1cb
2025-04-26 13:53:50I'm currently using this bash script to publish long-form content from local Markdown files to Nostr relays.
It requires all of
yq,jq, andnakto be installed.Usage
Create a signed Nostr event and print it to the console:
bash markdown_to_nostr.sh article-filename.mdCreate a Nostr event and publish it to one or more relays:
bash markdown_to_nostr.sh article-filename.md ws://localhost:7777 wss://nostr.kosmos.orgMarkdown format
You can specify your metadata as YAML in a Front Matter header. Here's an example file:
```markdown
title: "Good Morning" summary: "It's a beautiful day" image: https://example.com/i/beautiful-day.jpg date: 2025-04-24T15:00:00Z tags: gm, poetry published: false
In the blue sky just a few specks of gray
In the evening of a beautiful day
Though last night it rained and more rain on the way
And that more rain is needed 'twould be fair to say.— Francis Duggan ```
The metadata keys are mostly self-explanatory. Note:
- All keys except for
titleare optional date, if present, will be set as thepublished_atdate.- If
publishedis set totrue, it will publish a kind 30023 event, otherwise a kind 30024 (draft) - The
dtag (widely used as URL slug for the article) will be the filename without the.mdextension
- All keys except for
-
 @ a93be9fb:6d3fdc0c
2025-04-25 07:10:52
@ a93be9fb:6d3fdc0c
2025-04-25 07:10:52This is a tmp article
-
 @ c631e267:c2b78d3e
2025-04-20 19:54:32
@ c631e267:c2b78d3e
2025-04-20 19:54:32Es ist völlig unbestritten, dass der Angriff der russischen Armee auf die Ukraine im Februar 2022 strikt zu verurteilen ist. Ebenso unbestritten ist Russland unter Wladimir Putin keine brillante Demokratie. Aus diesen Tatsachen lässt sich jedoch nicht das finstere Bild des russischen Präsidenten – und erst recht nicht des Landes – begründen, das uns durchweg vorgesetzt wird und den Kern des aktuellen europäischen Bedrohungs-Szenarios darstellt. Da müssen wir schon etwas genauer hinschauen.
Der vorliegende Artikel versucht derweil nicht, den Einsatz von Gewalt oder die Verletzung von Menschenrechten zu rechtfertigen oder zu entschuldigen – ganz im Gegenteil. Dass jedoch der Verdacht des «Putinverstehers» sofort latent im Raume steht, verdeutlicht, was beim Thema «Russland» passiert: Meinungsmache und Manipulation.
Angesichts der mentalen Mobilmachung seitens Politik und Medien sowie des Bestrebens, einen bevorstehenden Krieg mit Russland geradezu herbeizureden, ist es notwendig, dieser fatalen Entwicklung entgegenzutreten. Wenn wir uns nur ein wenig von der herrschenden Schwarz-Weiß-Malerei freimachen, tauchen automatisch Fragen auf, die Risse im offiziellen Narrativ enthüllen. Grund genug, nachzuhaken.
Wer sich schon länger auch abseits der Staats- und sogenannten Leitmedien informiert, der wird in diesem Artikel vermutlich nicht viel Neues erfahren. Andere könnten hier ein paar unbekannte oder vergessene Aspekte entdecken. Möglicherweise klärt sich in diesem Kontext die Wahrnehmung der aktuellen (unserer eigenen!) Situation ein wenig.
Manipulation erkennen
Corona-«Pandemie», menschengemachter Klimawandel oder auch Ukraine-Krieg: Jede Menge Krisen, und für alle gibt es ein offizielles Narrativ, dessen Hinterfragung unerwünscht ist. Nun ist aber ein Narrativ einfach eine Erzählung, eine Geschichte (Latein: «narratio») und kein Tatsachenbericht. Und so wie ein Märchen soll auch das Narrativ eine Botschaft vermitteln.
Über die Methoden der Manipulation ist viel geschrieben worden, sowohl in Bezug auf das Individuum als auch auf die Massen. Sehr wertvolle Tipps dazu, wie man Manipulationen durchschauen kann, gibt ein Büchlein [1] von Albrecht Müller, dem Herausgeber der NachDenkSeiten.
Die Sprache selber eignet sich perfekt für die Manipulation. Beispielsweise kann die Wortwahl Bewertungen mitschwingen lassen, regelmäßiges Wiederholen (gerne auch von verschiedenen Seiten) lässt Dinge irgendwann «wahr» erscheinen, Übertreibungen fallen auf und hinterlassen wenigstens eine Spur im Gedächtnis, genauso wie Andeutungen. Belege spielen dabei keine Rolle.
Es gibt auffällig viele Sprachregelungen, die offenbar irgendwo getroffen und irgendwie koordiniert werden. Oder alle Redenschreiber und alle Medien kopieren sich neuerdings permanent gegenseitig. Welchen Zweck hat es wohl, wenn der Krieg in der Ukraine durchgängig und quasi wörtlich als «russischer Angriffskrieg auf die Ukraine» bezeichnet wird? Obwohl das in der Sache richtig ist, deutet die Art der Verwendung auf gezielte Beeinflussung hin und soll vor allem das Feindbild zementieren.
Sprachregelungen dienen oft der Absicherung einer einseitigen Darstellung. Das Gleiche gilt für das Verkürzen von Informationen bis hin zum hartnäckigen Verschweigen ganzer Themenbereiche. Auch hierfür gibt es rund um den Ukraine-Konflikt viele gute Beispiele.
Das gewünschte Ergebnis solcher Methoden ist eine Schwarz-Weiß-Malerei, bei der einer eindeutig als «der Böse» markiert ist und die anderen automatisch «die Guten» sind. Das ist praktisch und demonstriert gleichzeitig ein weiteres Manipulationswerkzeug: die Verwendung von Doppelstandards. Wenn man es schafft, bei wichtigen Themen regelmäßig mit zweierlei Maß zu messen, ohne dass das Publikum protestiert, dann hat man freie Bahn.
Experten zu bemühen, um bestimmte Sachverhalte zu erläutern, ist sicher sinnvoll, kann aber ebenso missbraucht werden, schon allein durch die Auswahl der jeweiligen Spezialisten. Seit «Corona» werden viele erfahrene und ehemals hoch angesehene Fachleute wegen der «falschen Meinung» diffamiert und gecancelt. [2] Das ist nicht nur ein brutaler Umgang mit Menschen, sondern auch eine extreme Form, die öffentliche Meinung zu steuern.
Wann immer wir also erkennen (weil wir aufmerksam waren), dass wir bei einem bestimmten Thema manipuliert werden, dann sind zwei logische und notwendige Fragen: Warum? Und was ist denn richtig? In unserem Russland-Kontext haben die Antworten darauf viel mit Geopolitik und Geschichte zu tun.
Ist Russland aggressiv und expansiv?
Angeblich plant Russland, europäische NATO-Staaten anzugreifen, nach dem Motto: «Zuerst die Ukraine, dann den Rest». In Deutschland weiß man dafür sogar das Datum: «Wir müssen bis 2029 kriegstüchtig sein», versichert Verteidigungsminister Pistorius.
Historisch gesehen ist es allerdings eher umgekehrt: Russland, bzw. die Sowjetunion, ist bereits dreimal von Westeuropa aus militärisch angegriffen worden. Die Feldzüge Napoleons, des deutschen Kaiserreichs und Nazi-Deutschlands haben Millionen Menschen das Leben gekostet. Bei dem ausdrücklichen Vernichtungskrieg ab 1941 kam es außerdem zu Brutalitäten wie der zweieinhalbjährigen Belagerung Leningrads (heute St. Petersburg) durch Hitlers Wehrmacht. Deren Ziel, die Bevölkerung auszuhungern, wurde erreicht: über eine Million tote Zivilisten.
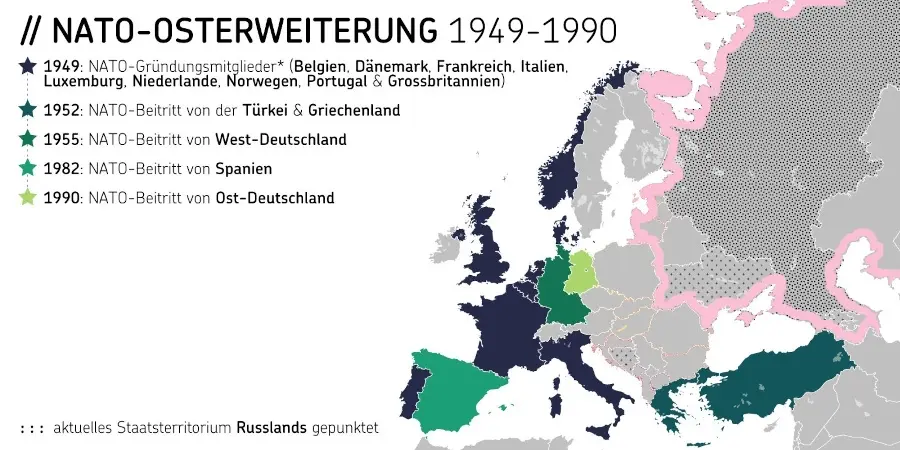
Trotz dieser Erfahrungen stimmte Michail Gorbatschow 1990 der deutschen Wiedervereinigung zu und die Sowjetunion zog ihre Truppen aus Osteuropa zurück (vgl. Abb. 1). Der Warschauer Pakt wurde aufgelöst, der Kalte Krieg formell beendet. Die Sowjets erhielten damals von führenden westlichen Politikern die Zusicherung, dass sich die NATO «keinen Zentimeter ostwärts» ausdehnen würde, das ist dokumentiert. [3]
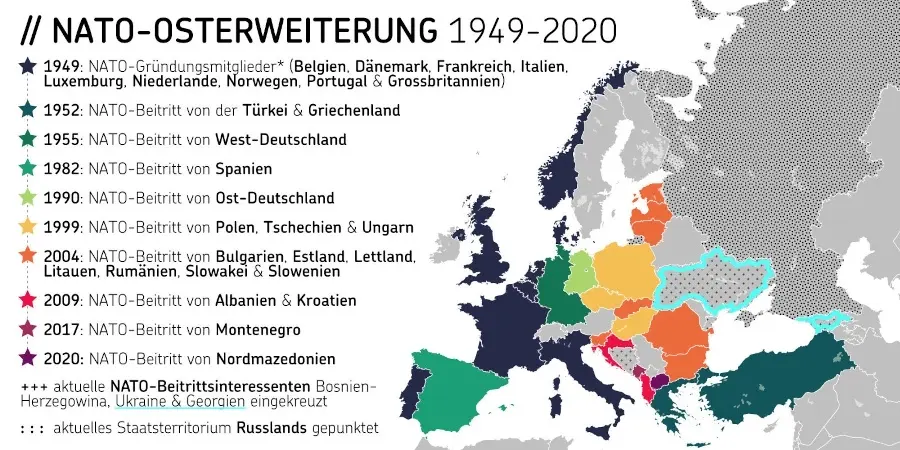
Expandiert ist die NATO trotzdem, und zwar bis an Russlands Grenzen (vgl. Abb. 2). Laut dem Politikberater Jeffrey Sachs handelt es sich dabei um ein langfristiges US-Projekt, das von Anfang an die Ukraine und Georgien mit einschloss. Offiziell wurde der Beitritt beiden Staaten 2008 angeboten. In jedem Fall könnte die massive Ost-Erweiterung seit 1999 aus russischer Sicht nicht nur als Vertrauensbruch, sondern durchaus auch als aggressiv betrachtet werden.
Russland hat den europäischen Staaten mehrfach die Hand ausgestreckt [4] für ein friedliches Zusammenleben und den «Aufbau des europäischen Hauses». Präsident Putin sei «in seiner ersten Amtszeit eine Chance für Europa» gewesen, urteilt die Journalistin und langjährige Russland-Korrespondentin der ARD, Gabriele Krone-Schmalz. Er habe damals viele positive Signale Richtung Westen gesendet.
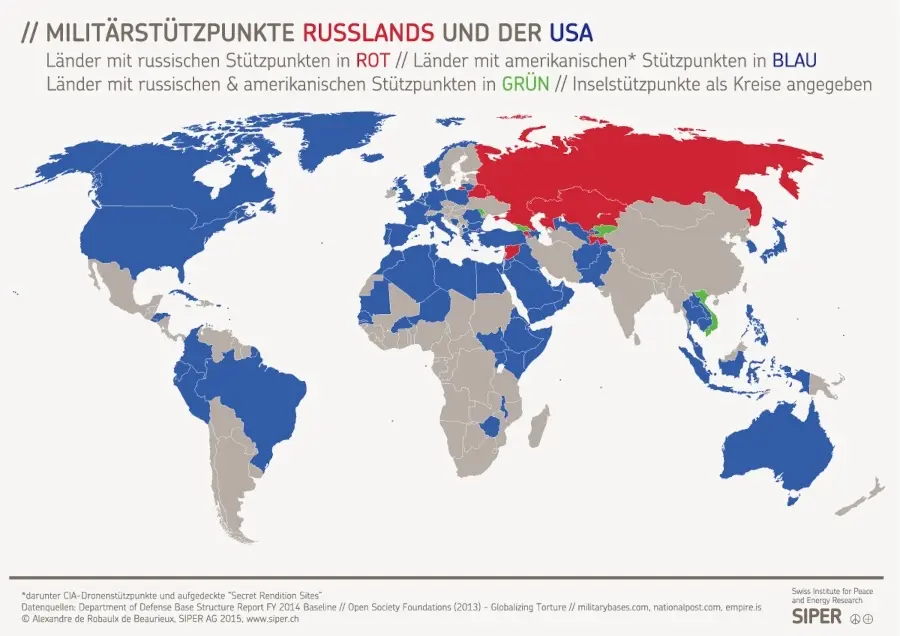
Die Europäer jedoch waren scheinbar an einer Partnerschaft mit dem kontinentalen Nachbarn weniger interessiert als an der mit dem transatlantischen Hegemon. Sie verkennen bis heute, dass eine gedeihliche Zusammenarbeit in Eurasien eine Gefahr für die USA und deren bekundetes Bestreben ist, die «einzige Weltmacht» zu sein – «Full Spectrum Dominance» [5] nannte das Pentagon das. Statt einem neuen Kalten Krieg entgegenzuarbeiten, ließen sich europäische Staaten selber in völkerrechtswidrige «US-dominierte Angriffskriege» [6] verwickeln, wie in Serbien, Afghanistan, dem Irak, Libyen oder Syrien. Diese werden aber selten so benannt.
Speziell den Deutschen stünde außer einer Portion Realismus auch etwas mehr Dankbarkeit gut zu Gesicht. Das Geschichtsbewusstsein der Mehrheit scheint doch recht selektiv und das Selbstbewusstsein einiger etwas desorientiert zu sein. Bekanntermaßen waren es die Soldaten der sowjetischen Roten Armee, die unter hohen Opfern 1945 Deutschland «vom Faschismus befreit» haben. Bei den Gedenkfeiern zu 80 Jahren Kriegsende will jedoch das Auswärtige Amt – noch unter der Diplomatie-Expertin Baerbock, die sich schon länger offiziell im Krieg mit Russland wähnt, – nun keine Russen sehen: Sie sollen notfalls rausgeschmissen werden.
«Die Grundsatzfrage lautet: Geht es Russland um einen angemessenen Platz in einer globalen Sicherheitsarchitektur, oder ist Moskau schon seit langem auf einem imperialistischen Trip, der befürchten lassen muss, dass die Russen in fünf Jahren in Berlin stehen?»
So bringt Gabriele Krone-Schmalz [7] die eigentliche Frage auf den Punkt, die zur Einschätzung der Situation letztlich auch jeder für sich beantworten muss.
Was ist los in der Ukraine?
In der internationalen Politik geht es nie um Demokratie oder Menschenrechte, sondern immer um Interessen von Staaten. Diese These stammt von Egon Bahr, einem der Architekten der deutschen Ostpolitik des «Wandels durch Annäherung» aus den 1960er und 70er Jahren. Sie trifft auch auf den Ukraine-Konflikt zu, den handfeste geostrategische und wirtschaftliche Interessen beherrschen, obwohl dort angeblich «unsere Demokratie» verteidigt wird.
Es ist ein wesentliches Element des Ukraine-Narrativs und Teil der Manipulation, die Vorgeschichte des Krieges wegzulassen – mindestens die vor der russischen «Annexion» der Halbinsel Krim im März 2014, aber oft sogar komplett diejenige vor der Invasion Ende Februar 2022. Das Thema ist komplex, aber einige Aspekte, die für eine Beurteilung nicht unwichtig sind, will ich wenigstens kurz skizzieren. [8]
Das Gebiet der heutigen Ukraine und Russlands – die übrigens in der «Kiewer Rus» gemeinsame Wurzeln haben – hat der britische Geostratege Halford Mackinder bereits 1904 als eurasisches «Heartland» bezeichnet, dessen Kontrolle er eine große Bedeutung für die imperiale Strategie Großbritanniens zumaß. Für den ehemaligen Sicherheits- und außenpolitischen Berater mehrerer US-amerikanischer Präsidenten und Mitgründer der Trilateralen Kommission, Zbigniew Brzezinski, war die Ukraine nach der Auflösung der Sowjetunion ein wichtiger Spielstein auf dem «eurasischen Schachbrett», wegen seiner Nähe zu Russland, seiner Bodenschätze und seines Zugangs zum Schwarzen Meer.
Die Ukraine ist seit langem ein gespaltenes Land. Historisch zerrissen als Spielball externer Interessen und geprägt von ethnischen, kulturellen, religiösen und geografischen Unterschieden existiert bis heute, grob gesagt, eine Ost-West-Spaltung, welche die Suche nach einer nationalen Identität stark erschwert.
Insbesondere im Zuge der beiden Weltkriege sowie der Russischen Revolution entstanden tiefe Risse in der Bevölkerung. Ukrainer kämpften gegen Ukrainer, zum Beispiel die einen auf der Seite von Hitlers faschistischer Nazi-Armee und die anderen auf der von Stalins kommunistischer Roter Armee. Die Verbrechen auf beiden Seiten sind nicht vergessen. Dass nach der Unabhängigkeit 1991 versucht wurde, Figuren wie den radikalen Nationalisten Symon Petljura oder den Faschisten und Nazi-Kollaborateur Stepan Bandera als «Nationalhelden» zu installieren, verbessert die Sache nicht.
Während die USA und EU-Staaten zunehmend «ausländische Einmischung» (speziell russische) in «ihre Demokratien» wittern, betreiben sie genau dies seit Jahrzehnten in vielen Ländern der Welt. Die seit den 2000er Jahren bekannten «Farbrevolutionen» in Osteuropa werden oft als Methode des Regierungsumsturzes durch von außen gesteuerte «demokratische» Volksaufstände beschrieben. Diese Strategie geht auf Analysen zum «Schwarmverhalten» [9] seit den 1960er Jahren zurück (Studentenproteste), wo es um die potenzielle Wirksamkeit einer «rebellischen Hysterie» von Jugendlichen bei postmodernen Staatsstreichen geht. Heute nennt sich dieses gezielte Kanalisieren der Massen zur Beseitigung unkooperativer Regierungen «Soft-Power».
In der Ukraine gab es mit der «Orangen Revolution» 2004 und dem «Euromaidan» 2014 gleich zwei solcher «Aufstände». Der erste erzwang wegen angeblicher Unregelmäßigkeiten eine Wiederholung der Wahlen, was mit Wiktor Juschtschenko als neuem Präsidenten endete. Dieser war ehemaliger Direktor der Nationalbank und Befürworter einer Annäherung an EU und NATO. Seine Frau, die First Lady, ist US-amerikanische «Philanthropin» und war Beamtin im Weißen Haus in der Reagan- und der Bush-Administration.
Im Gegensatz zu diesem ersten Event endete der sogenannte Euromaidan unfriedlich und blutig. Die mehrwöchigen Proteste gegen Präsident Wiktor Janukowitsch, in Teilen wegen des nicht unterzeichneten Assoziierungsabkommens mit der EU, wurden zunehmend gewalttätiger und von Nationalisten und Faschisten des «Rechten Sektors» dominiert. Sie mündeten Ende Februar 2014 auf dem Kiewer Unabhängigkeitsplatz (Maidan) in einem Massaker durch Scharfschützen. Dass deren Herkunft und die genauen Umstände nicht geklärt wurden, störte die Medien nur wenig. [10]
Janukowitsch musste fliehen, er trat nicht zurück. Vielmehr handelte es sich um einen gewaltsamen, allem Anschein nach vom Westen inszenierten Putsch. Laut Jeffrey Sachs war das kein Geheimnis, außer vielleicht für die Bürger. Die USA unterstützten die Post-Maidan-Regierung nicht nur, sie beeinflussten auch ihre Bildung. Das geht unter anderem aus dem berühmten «Fuck the EU»-Telefonat der US-Chefdiplomatin für die Ukraine, Victoria Nuland, mit Botschafter Geoffrey Pyatt hervor.
Dieser Bruch der demokratischen Verfassung war letztlich der Auslöser für die anschließenden Krisen auf der Krim und im Donbass (Ostukraine). Angesichts der ukrainischen Geschichte mussten die nationalistischen Tendenzen und die Beteiligung der rechten Gruppen an dem Umsturz bei der russigsprachigen Bevölkerung im Osten ungute Gefühle auslösen. Es gab Kritik an der Übergangsregierung, Befürworter einer Abspaltung und auch für einen Anschluss an Russland.
Ebenso konnte Wladimir Putin in dieser Situation durchaus Bedenken wegen des Status der russischen Militärbasis für seine Schwarzmeerflotte in Sewastopol auf der Krim haben, für die es einen langfristigen Pachtvertrag mit der Ukraine gab. Was im März 2014 auf der Krim stattfand, sei keine Annexion, sondern eine Abspaltung (Sezession) nach einem Referendum gewesen, also keine gewaltsame Aneignung, urteilte der Rechtswissenschaftler Reinhard Merkel in der FAZ sehr detailliert begründet. Übrigens hatte die Krim bereits zu Zeiten der Sowjetunion den Status einer autonomen Republik innerhalb der Ukrainischen SSR.
Anfang April 2014 wurden in der Ostukraine die «Volksrepubliken» Donezk und Lugansk ausgerufen. Die Kiewer Übergangsregierung ging unter der Bezeichnung «Anti-Terror-Operation» (ATO) militärisch gegen diesen, auch von Russland instrumentalisierten Widerstand vor. Zufällig war kurz zuvor CIA-Chef John Brennan in Kiew. Die Maßnahmen gingen unter dem seit Mai neuen ukrainischen Präsidenten, dem Milliardär Petro Poroschenko, weiter. Auch Wolodymyr Selenskyj beendete den Bürgerkrieg nicht, als er 2019 vom Präsidenten-Schauspieler, der Oligarchen entmachtet, zum Präsidenten wurde. Er fuhr fort, die eigene Bevölkerung zu bombardieren.
Mit dem Einmarsch russischer Truppen in die Ostukraine am 24. Februar 2022 begann die zweite Phase des Krieges. Die Wochen und Monate davor waren intensiv. Im November hatte die Ukraine mit den USA ein Abkommen über eine «strategische Partnerschaft» unterzeichnet. Darin sagten die Amerikaner ihre Unterstützung der EU- und NATO-Perspektive der Ukraine sowie quasi für die Rückeroberung der Krim zu. Dagegen ließ Putin der NATO und den USA im Dezember 2021 einen Vertragsentwurf über beiderseitige verbindliche Sicherheitsgarantien zukommen, den die NATO im Januar ablehnte. Im Februar eskalierte laut OSZE die Gewalt im Donbass.
Bereits wenige Wochen nach der Invasion, Ende März 2022, kam es in Istanbul zu Friedensverhandlungen, die fast zu einer Lösung geführt hätten. Dass der Krieg nicht damals bereits beendet wurde, lag daran, dass der Westen dies nicht wollte. Man war der Meinung, Russland durch die Ukraine in diesem Stellvertreterkrieg auf Dauer militärisch schwächen zu können. Angesichts von Hunderttausenden Toten, Verletzten und Traumatisierten, die als Folge seitdem zu beklagen sind, sowie dem Ausmaß der Zerstörung, fehlen einem die Worte.
Hasst der Westen die Russen?
Diese Frage drängt sich auf, wenn man das oft unerträglich feindselige Gebaren beobachtet, das beileibe nicht neu ist und vor Doppelmoral trieft. Russland und speziell die Person Wladimir Putins werden regelrecht dämonisiert, was gleichzeitig scheinbar jede Form von Diplomatie ausschließt.
Russlands militärische Stärke, seine geografische Lage, sein Rohstoffreichtum oder seine unabhängige diplomatische Tradition sind sicher Störfaktoren für das US-amerikanische Bestreben, der Boss in einer unipolaren Welt zu sein. Ein womöglich funktionierender eurasischer Kontinent, insbesondere gute Beziehungen zwischen Russland und Deutschland, war indes schon vor dem Ersten Weltkrieg eine Sorge des britischen Imperiums.
Ein «Vergehen» von Präsident Putin könnte gewesen sein, dass er die neoliberale Schocktherapie à la IWF und den Ausverkauf des Landes (auch an US-Konzerne) beendete, der unter seinem Vorgänger herrschte. Dabei zeigte er sich als Führungspersönlichkeit und als nicht so formbar wie Jelzin. Diese Aspekte allein sind aber heute vermutlich keine ausreichende Erklärung für ein derart gepflegtes Feindbild.
Der Historiker und Philosoph Hauke Ritz erweitert den Fokus der Fragestellung zu: «Warum hasst der Westen die Russen so sehr?», was er zum Beispiel mit dem Medienforscher Michael Meyen und mit der Politikwissenschaftlerin Ulrike Guérot bespricht. Ritz stellt die interessante These [11] auf, dass Russland eine Provokation für den Westen sei, welcher vor allem dessen kulturelles und intellektuelles Potenzial fürchte.
Die Russen sind Europäer aber anders, sagt Ritz. Diese «Fremdheit in der Ähnlichkeit» erzeuge vielleicht tiefe Ablehnungsgefühle. Obwohl Russlands Identität in der europäischen Kultur verwurzelt ist, verbinde es sich immer mit der Opposition in Europa. Als Beispiele nennt er die Kritik an der katholischen Kirche oder die Verbindung mit der Arbeiterbewegung. Christen, aber orthodox; Sozialismus statt Liberalismus. Das mache das Land zum Antagonisten des Westens und zu einer Bedrohung der Machtstrukturen in Europa.
Fazit
Selbstverständlich kann man Geschichte, Ereignisse und Entwicklungen immer auf verschiedene Arten lesen. Dieser Artikel, obwohl viel zu lang, konnte nur einige Aspekte der Ukraine-Tragödie anreißen, die in den offiziellen Darstellungen in der Regel nicht vorkommen. Mindestens dürfte damit jedoch klar geworden sein, dass die Russische Föderation bzw. Wladimir Putin nicht der alleinige Aggressor in diesem Konflikt ist. Das ist ein Stellvertreterkrieg zwischen USA/NATO (gut) und Russland (böse); die Ukraine (edel) wird dabei schlicht verheizt.
Das ist insofern von Bedeutung, als die gesamte europäische Kriegshysterie auf sorgsam kultivierten Freund-Feind-Bildern beruht. Nur so kann Konfrontation und Eskalation betrieben werden, denn damit werden die wahren Hintergründe und Motive verschleiert. Angst und Propaganda sind notwendig, damit die Menschen den Wahnsinn mitmachen. Sie werden belogen, um sie zuerst zu schröpfen und anschließend auf die Schlachtbank zu schicken. Das kann niemand wollen, außer den stets gleichen Profiteuren: die Rüstungs-Lobby und die großen Investoren, die schon immer an Zerstörung und Wiederaufbau verdient haben.
Apropos Investoren: Zu den Top-Verdienern und somit Hauptinteressenten an einer Fortführung des Krieges zählt BlackRock, einer der weltgrößten Vermögensverwalter. Der deutsche Bundeskanzler in spe, Friedrich Merz, der gerne «Taurus»-Marschflugkörper an die Ukraine liefern und die Krim-Brücke zerstören möchte, war von 2016 bis 2020 Aufsichtsratsvorsitzender von BlackRock in Deutschland. Aber das hat natürlich nichts zu sagen, der Mann macht nur seinen Job.
Es ist ein Spiel der Kräfte, es geht um Macht und strategische Kontrolle, um Geheimdienste und die Kontrolle der öffentlichen Meinung, um Bodenschätze, Rohstoffe, Pipelines und Märkte. Das klingt aber nicht sexy, «Demokratie und Menschenrechte» hört sich besser und einfacher an. Dabei wäre eine für alle Seiten förderliche Politik auch nicht so kompliziert; das Handwerkszeug dazu nennt sich Diplomatie. Noch einmal Gabriele Krone-Schmalz:
«Friedliche Politik ist nichts anderes als funktionierender Interessenausgleich. Da geht’s nicht um Moral.»
Die Situation in der Ukraine ist sicher komplex, vor allem wegen der inneren Zerrissenheit. Es dürfte nicht leicht sein, eine friedliche Lösung für das Zusammenleben zu finden, aber die Beteiligten müssen es vor allem wollen. Unter den gegebenen Umständen könnte eine sinnvolle Perspektive mit Neutralität und föderalen Strukturen zu tun haben.
Allen, die sich bis hierher durch die Lektüre gearbeitet (oder auch einfach nur runtergescrollt) haben, wünsche ich frohe Oster-Friedenstage!
[Titelbild: Pixabay; Abb. 1 und 2: nach Ganser/SIPER; Abb. 3: SIPER]
--- Quellen: ---
[1] Albrecht Müller, «Glaube wenig. Hinterfrage alles. Denke selbst.», Westend 2019
[2] Zwei nette Beispiele:
- ARD-faktenfinder (sic), «Viel Aufmerksamkeit für fragwürdige Experten», 03/2023
- Neue Zürcher Zeitung, «Aufstieg und Fall einer Russlandversteherin – die ehemalige ARD-Korrespondentin Gabriele Krone-Schmalz rechtfertigt seit Jahren Putins Politik», 12/2022
[3] George Washington University, «NATO Expansion: What Gorbachev Heard – Declassified documents show security assurances against NATO expansion to Soviet leaders from Baker, Bush, Genscher, Kohl, Gates, Mitterrand, Thatcher, Hurd, Major, and Woerner», 12/2017
[4] Beispielsweise Wladimir Putin bei seiner Rede im Deutschen Bundestag, 25/09/2001
[5] William Engdahl, «Full Spectrum Dominance, Totalitarian Democracy In The New World Order», edition.engdahl 2009
[6] Daniele Ganser, «Illegale Kriege – Wie die NATO-Länder die UNO sabotieren. Eine Chronik von Kuba bis Syrien», Orell Füssli 2016
[7] Gabriele Krone-Schmalz, «Mit Friedensjournalismus gegen ‘Kriegstüchtigkeit’», Vortrag und Diskussion an der Universität Hamburg, veranstaltet von engagierten Studenten, 16/01/2025\ → Hier ist ein ähnlicher Vortrag von ihr (Video), den ich mit spanischer Übersetzung gefunden habe.
[8] Für mehr Hintergrund und Details empfehlen sich z.B. folgende Bücher:
- Mathias Bröckers, Paul Schreyer, «Wir sind immer die Guten», Westend 2019
- Gabriele Krone-Schmalz, «Russland verstehen? Der Kampf um die Ukraine und die Arroganz des Westens», Westend 2023
- Patrik Baab, «Auf beiden Seiten der Front – Meine Reisen in die Ukraine», Fiftyfifty 2023
[9] vgl. Jonathan Mowat, «Washington's New World Order "Democratization" Template», 02/2005 und RAND Corporation, «Swarming and the Future of Conflict», 2000
[10] Bemerkenswert einige Beiträge, von denen man später nichts mehr wissen wollte:
- ARD Monitor, «Todesschüsse in Kiew: Wer ist für das Blutbad vom Maidan verantwortlich», 10/04/2014, Transkript hier
- Telepolis, «Blutbad am Maidan: Wer waren die Todesschützen?», 12/04/2014
- Telepolis, «Scharfschützenmorde in Kiew», 14/12/2014
- Deutschlandfunk, «Gefahr einer Spirale nach unten», Interview mit Günter Verheugen, 18/03/2014
- NDR Panorama, «Putsch in Kiew: Welche Rolle spielen die Faschisten?», 06/03/2014
[11] Hauke Ritz, «Vom Niedergang des Westens zur Neuerfindung Europas», 2024
Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
-
 @ bf95e1a4:ebdcc848
2025-04-25 07:10:07
@ bf95e1a4:ebdcc848
2025-04-25 07:10:07This is a part of the Bitcoin Infinity Academy course on Knut Svanholm's book Bitcoin: Sovereignty Through Mathematics. For more information, check out our Geyser page!
Scarcity
What makes a commodity scarce? What is scarcity in the first place? What other properties can be deducted from an object’s scarcity? How are scarcity, energy, time, and value connected? Scarcity might seem easy to describe on the surface, but in reality, it’s not. Not when you take infinity into account. Infinity is a concept that has puzzled the human mind for as long as it has been able to imagine it. If it ever has. It is a very abstract concept, and it’s always linked to time simply because even imagining an infinite number would take an infinite amount of time. If we truly live in an infinite universe, scarcity cannot exist. If something exists in an infinite universe, an infinite number of copies of this something must also exist since the probability of this being true would also be infinite in an infinite universe. Therefore, scarcity must always be defined within a set framework. No frame, no scarcity.
Think of it this way: the most expensive artwork ever sold at the time of writing was the Salvator Mundi, painted by Leonardo da Vinci. It’s not even a particularly beautiful painting, so why the high price? Because Da Vinci originals are scarce. A poster of the painting isn’t expensive at all, but the original will cost you at least 450 million US Dollars. All because we agree to frame its scarcity around the notion that it is a Da Vinci original, of which under twenty exist today. Historically, scarcity has always been framed around real-world limits to the supply of a good. Most of the great thinkers of the Austrian school of economics from the twentieth century believed that the value of a monetary good arises from its scarcity and that scarcity is always connected to the real-world availability of that good. Most of them believed that a gold standard would be the hardest form of money that we would ever see and the closest thing to an absolutely scarce resource as we would ever know.
In the late 90’s, the cryptographers that laid the groundwork for what would become Bitcoin reimagined scarcity as anything with an unforgeable costliness. This mindset is key to understanding the connection between scarcity and value. Anything can be viewed as scarce if it’s sufficiently hard to produce and hard to fake the production cost of — in other words, easy to verify the validity of. The zeros at the beginning of a hashed Bitcoin block are the Proof of Work that proves that the created coins in that block were costly to produce. People who promote the idea that the mining algorithm used to produce Bitcoin could be more environmentally friendly or streamlined are either deliberately lying or missing the point. The energy expenditure is the very thing that gives the token its value because it provides proof to the network that enough computing power was sacrificed in order to keep the network sufficiently decentralized and thus resistant to change. "Easy to verify" is the flipside of the "unforgeable costliness" coin. The validity of a Bitcoin block is very easy to verify since all you need to do is look at its hash, make sure the block is part of the strongest chain, and that it conforms to all consensus rules. In order to check whether a gold bar is real or not, you probably need to trust a third party. Fiat money often comes with a plethora of water stamps, holograms, and metal stripes, so in a sense, they’re hard to forge. What you cannot know about a fiat currency at any given moment, though, is how much of it is in circulation. What you do know about fiat currencies is that they’re not scarce.
Bitcoin provides us with absolute scarcity for the first time in human history. It is a remarkable breakthrough. Even though you can’t make jewelry or anything else out of Bitcoin, its total supply is fixed. After the year 2140, after the last Bitcoin has been mined, the total amount of Bitcoin in circulation can only go down. This limited supply is what the gold standards of the past were there for in the first place. Bitcoin’s supply is much more limited than that of gold, however, since they will be lost as time goes by. Since the supply is so limited, it doesn’t matter what the current demand is. The potential upside to its value is literally limitless due to this relationship between supply and demand. The “backing” that other currencies have is only there to assume people that the currency will keep its value over time, and the only way of ensuring this is to limit the supply. Bitcoin does this better than any other thing before it. Leonardo da Vinci’s original paintings are extremely valuable because of Leonardo’s brand name and the fact that there are only about 13 of them left. One day there’ll be less than one left. The same is true for Bitcoin.
Scarcity on the Internet was long believed to be an impossible invention, and it took a multi-talented genius such as Satoshi Nakamoto to figure out all the different parts that make Bitcoin so much more than the sum of them. His disappearance from the project was one such part, maybe the most important one. The thing about computerized scarcity is that it was a one-time invention. Once it was invented, the invention could not be recreated. That’s just the nature of data. Computers are designed to be able to replicate any data set any number of times. This is true for every piece of code there is, and digital scarcity needed to be framed somehow to work. Bitcoin’s consensus rules provided such a frame. Bitcoin certainly seems to provide true digital scarcity, and if the game theoretical theories that it builds on are correct, its promise of an ever-increasing value will be a self-fulfilling prophecy.
In 2018, the inflation rate of the Venezuelan Bolivar was a staggering 80,000%. Hugo Chavez and his successor, Nicolas Maduro, effectively killed the Venezuelan economy with socialism. It has happened before — and sadly, it is likely to happen again. The main problem with socialism is not that people aren’t incentivized to work in socialist countries. On the contrary, hungry people under the threat of violence tend to work harder than most. The problem with state-owned production is that there is no free market price mechanism to reflect the true demand for goods and, therefore, no way of knowing how much supply the state should produce. Everything is in constant surplus or shortage — often the latter, as the empty supermarket shelves in Venezuela depressingly attest. Chavez and Maduro attempted to rescue the country’s economy by printing more money — which simply does not work. Their true motives for printing money are, of course, questionable given that it depreciated the value of Bolivar bills to less than that of toilet paper. As mentioned in earlier chapters, inflation is the greatest hidden threat to themselves that humans have ever created.
A few hundred years ago, the Catholic Church held the lion’s share of political power throughout Europe. Today, power primarily resides with nation-states in collusion with multinational corporations. The separation of church and state triggered the migration of power from the former to the latter, emancipating many citizens in the process. Still, places like Venezuela are sad proof that “the people” are still not in power in many self-proclaimed democracies — if in any, for that matter. Another separation will have to take place first: The separation of money and state. We, the people of Planet Earth, now have the means at our disposal for this separation to take place. Whether we use them or not will determine how emancipated and independent our children can and will be in the future.
About the Bitcoin Infinity Academy
The Bitcoin Infinity Academy is an educational project built around Knut Svanholm’s books about Bitcoin and Austrian Economics. Each week, a whole chapter from one of the books is released for free on Highlighter, accompanied by a video in which Knut and Luke de Wolf discuss that chapter’s ideas. You can join the discussions by signing up for one of the courses on our Geyser page. Signed books, monthly calls, and lots of other benefits are also available.
-
 @ c631e267:c2b78d3e
2025-04-18 15:53:07
@ c631e267:c2b78d3e
2025-04-18 15:53:07Verstand ohne Gefühl ist unmenschlich; \ Gefühl ohne Verstand ist Dummheit. \ Egon Bahr
Seit Jahren werden wir darauf getrimmt, dass Fakten eigentlich gefühlt seien. Aber nicht alles ist relativ und nicht alles ist nach Belieben interpretierbar. Diese Schokoladenhasen beispielsweise, die an Ostern in unseren Gefilden typisch sind, «ostern» zwar nicht, sondern sie sitzen in der Regel, trotzdem verwandelt sie das nicht in «Sitzhasen».
Nichts soll mehr gelten, außer den immer invasiveren Gesetzen. Die eigenen Traditionen und Wurzeln sind potenziell «pfui», um andere Menschen nicht auszuschließen, aber wir mögen uns toleranterweise an die fremden Symbole und Rituale gewöhnen. Dabei ist es mir prinzipiell völlig egal, ob und wann jemand ein Fastenbrechen feiert, am Karsamstag oder jedem anderen Tag oder nie – aber bitte freiwillig.
Und vor allem: Lasst die Finger von den Kindern! In Bern setzten kürzlich Demonstranten ein Zeichen gegen die zunehmende Verbreitung woker Ideologie im Bildungssystem und forderten ein Ende der sexuellen Indoktrination von Schulkindern.
Wenn es nicht wegen des heiklen Themas Migration oder wegen des Regenbogens ist, dann wegen des Klimas. Im Rahmen der «Netto Null»-Agenda zum Kampf gegen das angeblich teuflische CO2 sollen die Menschen ihre Ernährungsgewohnheiten komplett ändern. Nach dem Willen von Produzenten synthetischer Lebensmittel, wie Bill Gates, sollen wir baldmöglichst praktisch auf Fleisch und alle Milchprodukte wie Milch und Käse verzichten. Ein lukratives Geschäftsmodell, das neben der EU aktuell auch von einem britischen Lobby-Konsortium unterstützt wird.
Sollten alle ideologischen Stricke zu reißen drohen, ist da immer noch «der Putin». Die Unions-Europäer offenbaren sich dabei ständig mehr als Vertreter der Rüstungsindustrie. Allen voran zündelt Deutschland an der Kriegslunte, angeführt von einem scheinbar todesmutigen Kanzlerkandidaten Friedrich Merz. Nach dessen erneuter Aussage, «Taurus»-Marschflugkörper an Kiew liefern zu wollen, hat Russland eindeutig klargestellt, dass man dies als direkte Kriegsbeteiligung werten würde – «mit allen sich daraus ergebenden Konsequenzen für Deutschland».
Wohltuend sind Nachrichten über Aktivitäten, die sich der allgemeinen Kriegstreiberei entgegenstellen oder diese öffentlich hinterfragen. Dazu zählt auch ein Kongress kritischer Psychologen und Psychotherapeuten, der letzte Woche in Berlin stattfand. Die vielen Vorträge im Kontext von «Krieg und Frieden» deckten ein breites Themenspektrum ab, darunter Friedensarbeit oder die Notwendigkeit einer «Pädagogik der Kriegsuntüchtigkeit».
Der heutige «stille Freitag», an dem Christen des Leidens und Sterbens von Jesus gedenken, ist vielleicht unabhängig von jeder religiösen oder spirituellen Prägung eine passende Einladung zur Reflexion. In der Ruhe liegt die Kraft. In diesem Sinne wünsche ich Ihnen frohe Ostertage!
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ c631e267:c2b78d3e
2025-04-04 18:47:27
@ c631e267:c2b78d3e
2025-04-04 18:47:27Zwei mal drei macht vier, \ widewidewitt und drei macht neune, \ ich mach mir die Welt, \ widewide wie sie mir gefällt. \ Pippi Langstrumpf
Egal, ob Koalitionsverhandlungen oder politischer Alltag: Die Kontroversen zwischen theoretisch verschiedenen Parteien verschwinden, wenn es um den Kampf gegen politische Gegner mit Rückenwind geht. Wer den Alteingesessenen die Pfründe ernsthaft streitig machen könnte, gegen den werden nicht nur «Brandmauern» errichtet, sondern der wird notfalls auch strafrechtlich verfolgt. Doppelstandards sind dabei selbstverständlich inklusive.
In Frankreich ist diese Woche Marine Le Pen wegen der Veruntreuung von EU-Geldern von einem Gericht verurteilt worden. Als Teil der Strafe wurde sie für fünf Jahre vom passiven Wahlrecht ausgeschlossen. Obwohl das Urteil nicht rechtskräftig ist – Le Pen kann in Berufung gehen –, haben die Richter das Verbot, bei Wahlen anzutreten, mit sofortiger Wirkung verhängt. Die Vorsitzende des rechtsnationalen Rassemblement National (RN) galt als aussichtsreiche Kandidatin für die Präsidentschaftswahl 2027.
Das ist in diesem Jahr bereits der zweite gravierende Fall von Wahlbeeinflussung durch die Justiz in einem EU-Staat. In Rumänien hatte Călin Georgescu im November die erste Runde der Präsidentenwahl überraschend gewonnen. Das Ergebnis wurde später annulliert, die behauptete «russische Wahlmanipulation» konnte jedoch nicht bewiesen werden. Die Kandidatur für die Wahlwiederholung im Mai wurde Georgescu kürzlich durch das Verfassungsgericht untersagt.
Die Veruntreuung öffentlicher Gelder muss untersucht und geahndet werden, das steht außer Frage. Diese Anforderung darf nicht selektiv angewendet werden. Hingegen mussten wir in der Vergangenheit bei ungleich schwerwiegenderen Fällen von (mutmaßlichem) Missbrauch ganz andere Vorgehensweisen erleben, etwa im Fall der heutigen EZB-Chefin Christine Lagarde oder im «Pfizergate»-Skandal um die Präsidentin der EU-Kommission Ursula von der Leyen.
Wenngleich derartige Angelegenheiten formal auf einer rechtsstaatlichen Grundlage beruhen mögen, so bleibt ein bitterer Beigeschmack. Es stellt sich die Frage, ob und inwieweit die Justiz politisch instrumentalisiert wird. Dies ist umso interessanter, als die Gewaltenteilung einen essenziellen Teil jeder demokratischen Ordnung darstellt, während die Bekämpfung des politischen Gegners mit juristischen Mitteln gerade bei den am lautesten rufenden Verteidigern «unserer Demokratie» populär zu sein scheint.
Die Delegationen von CDU/CSU und SPD haben bei ihren Verhandlungen über eine Regierungskoalition genau solche Maßnahmen diskutiert. «Im Namen der Wahrheit und der Demokratie» möchte man noch härter gegen «Desinformation» vorgehen und dafür zum Beispiel den Digital Services Act der EU erweitern. Auch soll der Tatbestand der Volksverhetzung verschärft werden – und im Entzug des passiven Wahlrechts münden können. Auf europäischer Ebene würde Friedrich Merz wohl gerne Ungarn das Stimmrecht entziehen.
Der Pegel an Unzufriedenheit und Frustration wächst in großen Teilen der Bevölkerung kontinuierlich. Arroganz, Machtmissbrauch und immer abstrusere Ausreden für offensichtlich willkürliche Maßnahmen werden kaum verhindern, dass den etablierten Parteien die Unterstützung entschwindet. In Deutschland sind die Umfrageergebnisse der AfD ein guter Gradmesser dafür.
[Vorlage Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ c631e267:c2b78d3e
2025-04-03 07:42:25
@ c631e267:c2b78d3e
2025-04-03 07:42:25Spanien bleibt einer der Vorreiter im europäischen Prozess der totalen Überwachung per Digitalisierung. Seit Mittwoch ist dort der digitale Personalausweis verfügbar. Dabei handelt es sich um eine Regierungs-App, die auf dem Smartphone installiert werden muss und in den Stores von Google und Apple zu finden ist. Per Dekret von Regierungschef Pedro Sánchez und Zustimmung des Ministerrats ist diese Maßnahme jetzt in Kraft getreten.
Mit den üblichen Argumenten der Vereinfachung, des Komforts, der Effizienz und der Sicherheit preist das Innenministerium die «Innovation» an. Auch die Beteuerung, dass die digitale Variante parallel zum physischen Ausweis existieren wird und diesen nicht ersetzen soll, fehlt nicht. Während der ersten zwölf Monate wird «der Neue» noch nicht für alle Anwendungsfälle gültig sein, ab 2026 aber schon.
Dass die ganze Sache auch «Risiken und Nebenwirkungen» haben könnte, wird in den Mainstream-Medien eher selten thematisiert. Bestenfalls wird der Aspekt der Datensicherheit angesprochen, allerdings in der Regel direkt mit dem Regierungsvokabular von den «maximalen Sicherheitsgarantien» abgehandelt. Dennoch gibt es einige weitere Aspekte, die Bürger mit etwas Sinn für Privatsphäre bedenken sollten.
Um sich die digitale Version des nationalen Ausweises besorgen zu können (eine App mit dem Namen MiDNI), muss man sich vorab online registrieren. Dabei wird die Identität des Bürgers mit seiner mobilen Telefonnummer verknüpft. Diese obligatorische fixe Verdrahtung kennen wir von diversen anderen Apps und Diensten. Gleichzeitig ist das die Basis für eine perfekte Lokalisierbarkeit der Person.
Für jeden Vorgang der Identifikation in der Praxis wird später «eine Verbindung zu den Servern der Bundespolizei aufgebaut». Die Daten des Individuums werden «in Echtzeit» verifiziert und im Erfolgsfall von der Polizei signiert zurückgegeben. Das Ergebnis ist ein QR-Code mit zeitlich begrenzter Gültigkeit, der an Dritte weitergegeben werden kann.
Bei derartigen Szenarien sträuben sich einem halbwegs kritischen Staatsbürger die Nackenhaare. Allein diese minimale Funktionsbeschreibung lässt die totale Überwachung erkennen, die damit ermöglicht wird. Jede Benutzung des Ausweises wird künftig registriert, hinterlässt also Spuren. Und was ist, wenn die Server der Polizei einmal kein grünes Licht geben? Das wäre spätestens dann ein Problem, wenn der digitale doch irgendwann der einzig gültige Ausweis ist: Dann haben wir den abschaltbaren Bürger.
Dieser neue Vorstoß der Regierung von Pedro Sánchez ist ein weiterer Schritt in Richtung der «totalen Digitalisierung» des Landes, wie diese Politik in manchen Medien – nicht einmal kritisch, sondern sehr naiv – genannt wird. Ebenso verharmlosend wird auch erwähnt, dass sich das spanische Projekt des digitalen Ausweises nahtlos in die Initiativen der EU zu einer digitalen Identität für alle Bürger sowie des digitalen Euro einreiht.
In Zukunft könnte der neue Ausweis «auch in andere staatliche und private digitale Plattformen integriert werden», wie das Medienportal Cope ganz richtig bemerkt. Das ist die Perspektive.
[Titelbild: Pixabay]
Dazu passend:
Nur Abschied vom Alleinfahren? Monströse spanische Überwachungsprojekte gemäß EU-Norm
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 3bf0c63f:aefa459d
2025-04-25 19:26:48
@ 3bf0c63f:aefa459d
2025-04-25 19:26:48Redistributing Git with Nostr
Every time someone tries to "decentralize" Git -- like many projects tried in the past to do it with BitTorrent, IPFS, ScuttleButt or custom p2p protocols -- there is always a lurking comment: "but Git is already distributed!", and then the discussion proceeds to mention some facts about how Git supports multiple remotes and its magic syncing and merging abilities and so on.
Turns out all that is true, Git is indeed all that powerful, and yet GitHub is the big central hub that hosts basically all Git repositories in the giant world of open-source. There are some crazy people that host their stuff elsewhere, but these projects end up not being found by many people, and even when they do they suffer from lack of contributions.
Because everybody has a GitHub account it's easy to open a pull request to a repository of a project you're using if it's on GitHub (to be fair I think it's very annoying to have to clone the repository, then add it as a remote locally, push to it, then go on the web UI and click to open a pull request, then that cloned repository lurks forever in your profile unless you go through 16 screens to delete it -- but people in general seem to think it's easy).
It's much harder to do it on some random other server where some project might be hosted, because now you have to add 4 more even more annoying steps: create an account; pick a password; confirm an email address; setup SSH keys for pushing. (And I'm not even mentioning the basic impossibility of offering
pushaccess to external unknown contributors to people who want to host their own simple homemade Git server.)At this point some may argue that we could all have accounts on GitLab, or Codeberg or wherever else, then those steps are removed. Besides not being a practical strategy this pseudo solution misses the point of being decentralized (or distributed, who knows) entirely: it's far from the ideal to force everybody to have the double of account management and SSH setup work in order to have the open-source world controlled by two shady companies instead of one.
What we want is to give every person the opportunity to host their own Git server without being ostracized. at the same time we must recognize that most people won't want to host their own servers (not even most open-source programmers!) and give everybody the ability to host their stuff on multi-tenant servers (such as GitHub) too. Importantly, though, if we allow for a random person to have a standalone Git server on a standalone server they host themselves on their wood cabin that also means any new hosting company can show up and start offering Git hosting, with or without new cool features, charging high or low or zero, and be immediately competing against GitHub or GitLab, i.e. we must remove the network-effect centralization pressure.
External contributions
The first problem we have to solve is: how can Bob contribute to Alice's repository without having an account on Alice's server?
SourceHut has reminded GitHub users that Git has always had this (for most) arcane
git send-emailcommand that is the original way to send patches, using an once-open protocol.Turns out Nostr acts as a quite powerful email replacement and can be used to send text content just like email, therefore patches are a very good fit for Nostr event contents.
Once you get used to it and the proper UIs (or CLIs) are built sending and applying patches to and from others becomes a much easier flow than the intense clickops mixed with terminal copypasting that is interacting with GitHub (you have to clone the repository on GitHub, then update the remote URL in your local directory, then create a branch and then go back and turn that branch into a Pull Request, it's quite tiresome) that many people already dislike so much they went out of their way to build many GitHub CLI tools just so they could comment on issues and approve pull requests from their terminal.
Replacing GitHub features
Aside from being the "hub" that people use to send patches to other people's code (because no one can do the email flow anymore, justifiably), GitHub also has 3 other big features that are not directly related to Git, but that make its network-effect harder to overcome. Luckily Nostr can be used to create a new environment in which these same features are implemented in a more decentralized and healthy way.
Issues: bug reports, feature requests and general discussions
Since the "Issues" GitHub feature is just a bunch of text comments it should be very obvious that Nostr is a perfect fit for it.
I will not even mention the fact that Nostr is much better at threading comments than GitHub (which doesn't do it at all), which can generate much more productive and organized discussions (and you can opt out if you want).
Search
I use GitHub search all the time to find libraries and projects that may do something that I need, and it returns good results almost always. So if people migrated out to other code hosting providers wouldn't we lose it?
The fact is that even though we think everybody is on GitHub that is a globalist falsehood. Some projects are not on GitHub, and if we use only GitHub for search those will be missed. So even if we didn't have a Nostr Git alternative it would still be necessary to create a search engine that incorporated GitLab, Codeberg, SourceHut and whatnot.
Turns out on Nostr we can make that quite easy by not forcing anyone to integrate custom APIs or hardcoding Git provider URLs: each repository can make itself available by publishing an "announcement" event with a brief description and one or more Git URLs. That makes it easy for a search engine to index them -- and even automatically download the code and index the code (or index just README files or whatever) without a centralized platform ever having to be involved.
The relays where such announcements will be available play a role, of course, but that isn't a bad role: each announcement can be in multiple relays known for storing "public good" projects, some relays may curate only projects known to be very good according to some standards, other relays may allow any kind of garbage, which wouldn't make them good for a search engine to rely upon, but would still be useful in case one knows the exact thing (and from whom) they're searching for (the same is valid for all Nostr content, by the way, and that's where it's censorship-resistance comes from).
Continuous integration
GitHub Actions are a very hardly subsidized free-compute-for-all-paid-by-Microsoft feature, but one that isn't hard to replace at all. In fact there exists today many companies offering the same kind of service out there -- although they are mostly targeting businesses and not open-source projects, before GitHub Actions was introduced there were also many that were heavily used by open-source projects.
One problem is that these services are still heavily tied to GitHub today, they require a GitHub login, sometimes BitBucket and GitLab and whatnot, and do not allow one to paste an arbitrary Git server URL, but that isn't a thing that is very hard to change anyway, or to start from scratch. All we need are services that offer the CI/CD flows, perhaps using the same framework of GitHub Actions (although I would prefer to not use that messy garbage), and charge some few satoshis for it.
It may be the case that all the current services only support the big Git hosting platforms because they rely on their proprietary APIs, most notably the webhooks dispatched when a repository is updated, to trigger the jobs. It doesn't have to be said that Nostr can also solve that problem very easily.
-
 @ d34e832d:383f78d0
2025-04-25 07:09:36
@ d34e832d:383f78d0
2025-04-25 07:09:361. Premise
The demand for high-capacity hard drives has grown exponentially with the expansion of cloud storage, big data, and personal backups. As failure of a storage device can result in significant data loss and downtime, understanding long-term drive reliability is critical. This research seeks to determine the most reliable manufacturer of 10TB+ HDDs by analyzing cumulative drive failure data over ten years from Backblaze, a leader in cloud backup services.
2. Methodology
Data from Backblaze, representing 350,000+ deployed drives, was analyzed to calculate the AFR of 10TB+ models from Seagate, Western Digital (including HGST), and Toshiba. AFR was calculated using cumulative data to reduce volatility and better illustrate long-term reliability trends. Power-on hours were used as the temporal metric to more accurately capture usage-based wear, as opposed to calendar-based aging.
3. Results and Analysis
3.1 Western Digital (including HGST)
- Ultrastar HC530 & HC550 (14TB & 16TB)
- AFR consistently below 0.35% after the initial “burn-in” period.
- Exhibited superior long-term stability.
- HGST Ultrastar HC520 (12TB)
- Demonstrated robust performance with AFR consistently under 0.5%.
- Excellent aging profile after year one.
3.2 Toshiba
- General Performance
- Noted for higher early failure rates (DOA issues), indicating manufacturing or transport inconsistencies.
- After stabilization, most models showed AFRs under 1%, which is within acceptable industry standards.
- Model Variability
- Differences in AFR observed between 4Kn and 512e sector models, suggesting firmware or controller differences may influence longevity.
3.3 Seagate
- Older Models (e.g., Exos X12)
- AFRs often exceeded 1.5%, raising concerns for long-term use in mission-critical applications.
- Newer Models (e.g., Exos X16)
- Improvements seen, with AFRs around 1%, though still higher than WD and HGST counterparts.
- Seagate’s aggressive pricing often makes these drives more attractive for cost-sensitive deployments.
4. Points Drawn
The data reveals a compelling narrative in brand-level reliability trends among high-capacity hard drives. Western Digital, especially through its HGST-derived Ultrastar product lines, consistently demonstrates superior reliability, maintaining exceptionally low Annualized Failure Rates (AFRs) and excellent operational stability across extended use periods. This positions WD as the most dependable option for enterprise-grade and mission-critical storage environments. Toshiba, despite a tendency toward higher early failure rates—often manifesting as Dead-on-Arrival (DOA) units—generally stabilizes to acceptable AFR levels below 1% over time. This indicates potential suitability in deployments where early failure screening and redundancy planning are feasible. In contrast, Seagate’s performance is notably variable. While earlier models displayed higher AFRs, more recent iterations such as the Exos X16 series have shown marked improvement. Nevertheless, Seagate drives continue to exhibit greater fluctuation in reliability outcomes. Their comparatively lower cost structure, however, may render them an attractive option in cost-sensitive or non-critical storage environments, where performance variability is an acceptable trade-off.
It’s crucial to remember that AFR is a probabilistic measure; individual drive failures are still possible regardless of brand or model. Furthermore, newer drive models need additional longitudinal data to confirm their long-term reliability.
5. Consider
Best Overall Choice: Western Digital Ultrastar HC530/HC550
These drives combine top-tier reliability (AFR < 0.35%), mature firmware, and consistent manufacturing quality, making them ideal for enterprise and archival use.Runner-Up (Budget Consideration): Seagate Exos X16
While reliability is slightly lower (AFR ~1%), the Exos series offers excellent value, especially for bulk storage.Cautionary Choice: Toshiba 10TB+ Models
Users should be prepared for potential early failures and may consider pre-deployment burn-in testing.
6. Recommendations for Buyers
- For mission-critical environments: Choose Western Digital Ultrastar models.
- For budget-focused or secondary storage: Seagate Exos offers acceptable risk-to-cost ratio.
- For experimental or non-essential deployments: Toshiba drives post-burn-in are serviceable.
7. Future Work
Based on publicly available Backblaze data, which reflects data center use and may not perfectly map to home or SMB environments. Sample sizes vary by model and may bias certain conclusions. Future research could integrate SMART data analytics, firmware version tracking, and consumer-use data to provide more granular insight.
References
- Backblaze. (2013–2023). Hard Drive Stats. Retrieved from https://www.backblaze.com/blog
- Manufacturer datasheets and reliability reports for Seagate, Western Digital, and Toshiba. -
 @ 8125b911:a8400883
2025-04-25 07:02:35
@ 8125b911:a8400883
2025-04-25 07:02:35In Nostr, all data is stored as events. Decentralization is achieved by storing events on multiple relays, with signatures proving the ownership of these events. However, if you truly want to own your events, you should run your own relay to store them. Otherwise, if the relays you use fail or intentionally delete your events, you'll lose them forever.
For most people, running a relay is complex and costly. To solve this issue, I developed nostr-relay-tray, a relay that can be easily run on a personal computer and accessed over the internet.
Project URL: https://github.com/CodyTseng/nostr-relay-tray
This article will guide you through using nostr-relay-tray to run your own relay.
Download
Download the installation package for your operating system from the GitHub Release Page.
| Operating System | File Format | | --------------------- | ---------------------------------- | | Windows |
nostr-relay-tray.Setup.x.x.x.exe| | macOS (Apple Silicon) |nostr-relay-tray-x.x.x-arm64.dmg| | macOS (Intel) |nostr-relay-tray-x.x.x.dmg| | Linux | You should know which one to use |Installation
Since this app isn’t signed, you may encounter some obstacles during installation. Once installed, an ostrich icon will appear in the status bar. Click on the ostrich icon, and you'll see a menu where you can click the "Dashboard" option to open the relay's control panel for further configuration.

macOS Users:
- On first launch, go to "System Preferences > Security & Privacy" and click "Open Anyway."
- If you encounter a "damaged" message, run the following command in the terminal to remove the restrictions:
bash sudo xattr -rd com.apple.quarantine /Applications/nostr-relay-tray.appWindows Users:
- On the security warning screen, click "More Info > Run Anyway."
Connecting
By default, nostr-relay-tray is only accessible locally through
ws://localhost:4869/, which makes it quite limited. Therefore, we need to expose it to the internet.In the control panel, click the "Proxy" tab and toggle the switch. You will then receive a "Public address" that you can use to access your relay from anywhere. It's that simple.
Next, add this address to your relay list and position it as high as possible in the list. Most clients prioritize connecting to relays that appear at the top of the list, and relays lower in the list are often ignored.

Restrictions
Next, we need to set up some restrictions to prevent the relay from storing events that are irrelevant to you and wasting storage space. nostr-relay-tray allows for flexible and fine-grained configuration of which events to accept, but some of this is more complex and will not be covered here. If you're interested, you can explore this further later.
For now, I'll introduce a simple and effective strategy: WoT (Web of Trust). You can enable this feature in the "WoT & PoW" tab. Before enabling, you'll need to input your pubkey.
There's another important parameter,
Depth, which represents the relationship depth between you and others. Someone you follow has a depth of 1, someone they follow has a depth of 2, and so on.- Setting this parameter to 0 means your relay will only accept your own events.
- Setting it to 1 means your relay will accept events from you and the people you follow.
- Setting it to 2 means your relay will accept events from you, the people you follow, and the people they follow.
Currently, the maximum value for this parameter is 2.

Conclusion
You've now successfully run your own relay and set a simple restriction to prevent it from storing irrelevant events.
If you encounter any issues during use, feel free to submit an issue on GitHub, and I'll respond as soon as possible.
Not your relay, not your events.
-
 @ 40b9c85f:5e61b451
2025-04-24 15:27:02
@ 40b9c85f:5e61b451
2025-04-24 15:27:02Introduction
Data Vending Machines (DVMs) have emerged as a crucial component of the Nostr ecosystem, offering specialized computational services to clients across the network. As defined in NIP-90, DVMs operate on an apparently simple principle: "data in, data out." They provide a marketplace for data processing where users request specific jobs (like text translation, content recommendation, or AI text generation)
While DVMs have gained significant traction, the current specification faces challenges that hinder widespread adoption and consistent implementation. This article explores some ideas on how we can apply the reflection pattern, a well established approach in RPC systems, to address these challenges and improve the DVM ecosystem's clarity, consistency, and usability.
The Current State of DVMs: Challenges and Limitations
The NIP-90 specification provides a broad framework for DVMs, but this flexibility has led to several issues:
1. Inconsistent Implementation
As noted by hzrd149 in "DVMs were a mistake" every DVM implementation tends to expect inputs in slightly different formats, even while ostensibly following the same specification. For example, a translation request DVM might expect an event ID in one particular format, while an LLM service could expect a "prompt" input that's not even specified in NIP-90.
2. Fragmented Specifications
The DVM specification reserves a range of event kinds (5000-6000), each meant for different types of computational jobs. While creating sub-specifications for each job type is being explored as a possible solution for clarity, in a decentralized and permissionless landscape like Nostr, relying solely on specification enforcement won't be effective for creating a healthy ecosystem. A more comprehensible approach is needed that works with, rather than against, the open nature of the protocol.
3. Ambiguous API Interfaces
There's no standardized way for clients to discover what parameters a specific DVM accepts, which are required versus optional, or what output format to expect. This creates uncertainty and forces developers to rely on documentation outside the protocol itself, if such documentation exists at all.
The Reflection Pattern: A Solution from RPC Systems
The reflection pattern in RPC systems offers a compelling solution to many of these challenges. At its core, reflection enables servers to provide metadata about their available services, methods, and data types at runtime, allowing clients to dynamically discover and interact with the server's API.
In established RPC frameworks like gRPC, reflection serves as a self-describing mechanism where services expose their interface definitions and requirements. In MCP reflection is used to expose the capabilities of the server, such as tools, resources, and prompts. Clients can learn about available capabilities without prior knowledge, and systems can adapt to changes without requiring rebuilds or redeployments. This standardized introspection creates a unified way to query service metadata, making tools like
grpcurlpossible without requiring precompiled stubs.How Reflection Could Transform the DVM Specification
By incorporating reflection principles into the DVM specification, we could create a more coherent and predictable ecosystem. DVMs already implement some sort of reflection through the use of 'nip90params', which allow clients to discover some parameters, constraints, and features of the DVMs, such as whether they accept encryption, nutzaps, etc. However, this approach could be expanded to provide more comprehensive self-description capabilities.
1. Defined Lifecycle Phases
Similar to the Model Context Protocol (MCP), DVMs could benefit from a clear lifecycle consisting of an initialization phase and an operation phase. During initialization, the client and DVM would negotiate capabilities and exchange metadata, with the DVM providing a JSON schema containing its input requirements. nip-89 (or other) announcements can be used to bootstrap the discovery and negotiation process by providing the input schema directly. Then, during the operation phase, the client would interact with the DVM according to the negotiated schema and parameters.
2. Schema-Based Interactions
Rather than relying on rigid specifications for each job type, DVMs could self-advertise their schemas. This would allow clients to understand which parameters are required versus optional, what type validation should occur for inputs, what output formats to expect, and what payment flows are supported. By internalizing the input schema of the DVMs they wish to consume, clients gain clarity on how to interact effectively.
3. Capability Negotiation
Capability negotiation would enable DVMs to advertise their supported features, such as encryption methods, payment options, or specialized functionalities. This would allow clients to adjust their interaction approach based on the specific capabilities of each DVM they encounter.
Implementation Approach
While building DVMCP, I realized that the RPC reflection pattern used there could be beneficial for constructing DVMs in general. Since DVMs already follow an RPC style for their operation, and reflection is a natural extension of this approach, it could significantly enhance and clarify the DVM specification.
A reflection enhanced DVM protocol could work as follows: 1. Discovery: Clients discover DVMs through existing NIP-89 application handlers, input schemas could also be advertised in nip-89 announcements, making the second step unnecessary. 2. Schema Request: Clients request the DVM's input schema for the specific job type they're interested in 3. Validation: Clients validate their request against the provided schema before submission 4. Operation: The job proceeds through the standard NIP-90 flow, but with clearer expectations on both sides
Parallels with Other Protocols
This approach has proven successful in other contexts. The Model Context Protocol (MCP) implements a similar lifecycle with capability negotiation during initialization, allowing any client to communicate with any server as long as they adhere to the base protocol. MCP and DVM protocols share fundamental similarities, both aim to expose and consume computational resources through a JSON-RPC-like interface, albeit with specific differences.
gRPC's reflection service similarly allows clients to discover service definitions at runtime, enabling generic tools to work with any gRPC service without prior knowledge. In the REST API world, OpenAPI/Swagger specifications document interfaces in a way that makes them discoverable and testable.
DVMs would benefit from adopting these patterns while maintaining the decentralized, permissionless nature of Nostr.
Conclusion
I am not attempting to rewrite the DVM specification; rather, explore some ideas that could help the ecosystem improve incrementally, reducing fragmentation and making the ecosystem more comprehensible. By allowing DVMs to self describe their interfaces, we could maintain the flexibility that makes Nostr powerful while providing the structure needed for interoperability.
For developers building DVM clients or libraries, this approach would simplify consumption by providing clear expectations about inputs and outputs. For DVM operators, it would establish a standard way to communicate their service's requirements without relying on external documentation.
I am currently developing DVMCP following these patterns. Of course, DVMs and MCP servers have different details; MCP includes capabilities such as tools, resources, and prompts on the server side, as well as 'roots' and 'sampling' on the client side, creating a bidirectional way to consume capabilities. In contrast, DVMs typically function similarly to MCP tools, where you call a DVM with an input and receive an output, with each job type representing a different categorization of the work performed.
Without further ado, I hope this article has provided some insight into the potential benefits of applying the reflection pattern to the DVM specification.
-
 @ aa8de34f:a6ffe696
2025-03-31 21:48:50
@ aa8de34f:a6ffe696
2025-03-31 21:48:50In seinem Beitrag vom 30. März 2025 fragt Henning Rosenbusch auf Telegram angesichts zunehmender digitaler Kontrolle und staatlicher Allmacht:
„Wie soll sich gegen eine solche Tyrannei noch ein Widerstand formieren können, selbst im Untergrund? Sehe ich nicht.“\ (Quelle: t.me/rosenbusch/25228)
Er beschreibt damit ein Gefühl der Ohnmacht, das viele teilen: Eine Welt, in der Totalitarismus nicht mehr mit Panzern, sondern mit Algorithmen kommt. Wo Zugriff auf Geld, Meinungsfreiheit und Teilhabe vom Wohlverhalten abhängt. Der Bürger als kontrollierbare Variable im Code des Staates.\ Die Frage ist berechtigt. Doch die Antwort darauf liegt nicht in alten Widerstandsbildern – sondern in einer neuen Realität.
-- Denn es braucht keinen Untergrund mehr. --
Der Widerstand der Zukunft trägt keinen Tarnanzug. Er ist nicht konspirativ, sondern transparent. Nicht bewaffnet, sondern mathematisch beweisbar. Bitcoin steht nicht am Rand dieser Entwicklung – es ist ihr Fundament. Eine Bastion aus physikalischer Realität, spieltheoretischem Schutz und ökonomischer Wahrheit. Es ist nicht unfehlbar, aber unbestechlich. Nicht perfekt, aber immun gegen zentrale Willkür.
Hier entsteht kein „digitales Gegenreich“, sondern eine dezentrale Renaissance. Keine Revolte aus Wut, sondern eine stille Abkehr: von Zwang zu Freiwilligkeit, von Abhängigkeit zu Selbstverantwortung. Diese Revolution führt keine Kriege. Sie braucht keine Führer. Sie ist ein Netzwerk. Jeder Knoten ein Individuum. Jede Entscheidung ein Akt der Selbstermächtigung.
Weltweit wachsen Freiheits-Zitadellen aus dieser Idee: wirtschaftlich autark, digital souverän, lokal verankert und global vernetzt. Sie sind keine Utopien im luftleeren Raum, sondern konkrete Realitäten – angetrieben von Energie, Code und dem menschlichen Wunsch nach Würde.
Der Globalismus alter Prägung – zentralistisch, monopolistisch, bevormundend – wird an seiner eigenen Hybris zerbrechen. Seine Werkzeuge der Kontrolle werden ihn nicht retten. Im Gegenteil: Seine Geister werden ihn verfolgen und erlegen.
Und während die alten Mächte um Erhalt kämpfen, wächst eine neue Welt – nicht im Schatten, sondern im Offenen. Nicht auf Gewalt gebaut, sondern auf Mathematik, Physik und Freiheit.
Die Tyrannei sieht keinen Widerstand.\ Weil sie nicht erkennt, dass er längst begonnen hat.\ Unwiderruflich. Leise. Überall.
-
 @ 8cda1daa:e9e5bdd8
2025-04-24 10:20:13
@ 8cda1daa:e9e5bdd8
2025-04-24 10:20:13Bitcoin cracked the code for money. Now it's time to rebuild everything else.
What about identity, trust, and collaboration? What about the systems that define how we live, create, and connect?
Bitcoin gave us a blueprint to separate money from the state. But the state still owns most of your digital life. It's time for something more radical.
Welcome to the Atomic Economy - not just a technology stack, but a civil engineering project for the digital age. A complete re-architecture of society, from the individual outward.
The Problem: We Live in Digital Captivity
Let's be blunt: the modern internet is hostile to human freedom.
You don't own your identity. You don't control your data. You don't decide what you see.
Big Tech and state institutions dominate your digital life with one goal: control.
- Poisoned algorithms dictate your emotions and behavior.
- Censorship hides truth and silences dissent.
- Walled gardens lock you into systems you can't escape.
- Extractive platforms monetize your attention and creativity - without your consent.
This isn't innovation. It's digital colonization.
A Vision for Sovereign Society
The Atomic Economy proposes a new design for society - one where: - Individuals own their identity, data, and value. - Trust is contextual, not imposed. - Communities are voluntary, not manufactured by feeds. - Markets are free, not fenced. - Collaboration is peer-to-peer, not platform-mediated.
It's not a political revolution. It's a technological and social reset based on first principles: self-sovereignty, mutualism, and credible exit.
So, What Is the Atomic Economy?
The Atomic Economy is a decentralized digital society where people - not platforms - coordinate identity, trust, and value.
It's built on open protocols, real software, and the ethos of Bitcoin. It's not about abstraction - it's about architecture.
Core Principles: - Self-Sovereignty: Your keys. Your data. Your rules. - Mutual Consensus: Interactions are voluntary and trust-based. - Credible Exit: Leave any system, with your data and identity intact. - Programmable Trust: Trust is explicit, contextual, and revocable. - Circular Economies: Value flows directly between individuals - no middlemen.
The Tech Stack Behind the Vision
The Atomic Economy isn't just theory. It's a layered system with real tools:
1. Payments & Settlement
- Bitcoin & Lightning: The foundation - sound, censorship-resistant money.
- Paykit: Modular payments and settlement flows.
- Atomicity: A peer-to-peer mutual credit protocol for programmable trust and IOUs.
2. Discovery & Matching
- Pubky Core: Decentralized identity and discovery using PKARR and the DHT.
- Pubky Nexus: Indexing for a user-controlled internet.
- Semantic Social Graph: Discovery through social tagging - you are the algorithm.
3. Application Layer
- Bitkit: A self-custodial Bitcoin and Lightning wallet.
- Pubky App: Tag, publish, trade, and interact - on your terms.
- Blocktank: Liquidity services for Lightning and circular economies.
- Pubky Ring: Key-based access control and identity syncing.
These tools don't just integrate - they stack. You build trust, exchange value, and form communities with no centralized gatekeepers.
The Human Impact
This isn't about software. It's about freedom.
- Empowered Individuals: Control your own narrative, value, and destiny.
- Voluntary Communities: Build trust on shared values, not enforced norms.
- Economic Freedom: Trade without permission, borders, or middlemen.
- Creative Renaissance: Innovation and art flourish in open, censorship-resistant systems.
The Atomic Economy doesn't just fix the web. It frees the web.
Why Bitcoiners Should Care
If you believe in Bitcoin, you already believe in the Atomic Economy - you just haven't seen the full map yet.
- It extends Bitcoin's principles beyond money: into identity, trust, coordination.
- It defends freedom where Bitcoin leaves off: in content, community, and commerce.
- It offers a credible exit from every centralized system you still rely on.
- It's how we win - not just economically, but culturally and socially.
This isn't "web3." This isn't another layer of grift. It's the Bitcoin future - fully realized.
Join the Atomic Revolution
- If you're a builder: fork the code, remix the ideas, expand the protocols.
- If you're a user: adopt Bitkit, use Pubky, exit the digital plantation.
- If you're an advocate: share the vision. Help people imagine a free society again.
Bitcoin promised a revolution. The Atomic Economy delivers it.
Let's reclaim society, one key at a time.
Learn more and build with us at Synonym.to.
-
 @ d34e832d:383f78d0
2025-04-25 06:06:32
@ d34e832d:383f78d0
2025-04-25 06:06:32This walkthrough examines the integration of these three tools as a combined financial instrument, focusing on their functionality, security benefits, and practical applications. Specter Desktop offers a user-friendly interface for managing Bitcoin wallets, Bitcoin Core provides a full node for transaction validation, and Coldcard provides the hardware security necessary to safeguard private keys. Together, these tools offer a robust and secure environment for managing Bitcoin holdings, protecting them from both online and physical threats.
We will explore their individual roles in Bitcoin management, how they can be integrated to offer a cohesive solution, and the installation and configuration process on OpenBSD. Additionally, security considerations and practical use cases will be addressed to demonstrate the advantages of this setup compared to alternative Bitcoin management solutions.
2.1 Specter Desktop
Specter Desktop is a Bitcoin wallet management software that provides a powerful, open-source interface for interacting with Bitcoin nodes. Built with an emphasis on multi-signature wallets and hardware wallet integration, Specter Desktop is designed to serve as an all-in-one solution for users who prioritize security and self-custody. It integrates seamlessly with Bitcoin Core and various hardware wallets, including Coldcard, and supports advanced features such as multi-signature wallets, which offer additional layers of security for managing Bitcoin funds.
2.2 Bitcoin Core
Bitcoin Core is the reference implementation of the Bitcoin protocol and serves as the backbone of the Bitcoin network. Running a Bitcoin Core full node provides users with the ability to independently verify all transactions and blocks on the network, ensuring trustless interaction with the blockchain. This is crucial for achieving full decentralization and autonomy, as Bitcoin Core ensures that users do not rely on third parties to confirm the validity of transactions. Furthermore, Bitcoin Core allows users to interact with the Bitcoin network via the command-line interface or a graphical user interface (GUI), offering flexibility in how one can participate in the Bitcoin ecosystem.
2.3 Coldcard
Coldcard is a Bitcoin hardware wallet that prioritizes security and privacy. It is designed to store private keys offline, away from any internet-connected devices, making it an essential tool for protecting Bitcoin holdings from online threats such as malware or hacking. Coldcard’s secure hardware environment ensures that private keys never leave the device, providing an air-gapped solution for cold storage. Its open-source firmware allows users to audit the wallet’s code and operations, ensuring that the device behaves exactly as expected.
2.4 Roles in Bitcoin Management
Each of these components plays a distinct yet complementary role in Bitcoin management:
- Specter Desktop: Acts as the interface for wallet management and multi-signature wallet configuration.
- Bitcoin Core: Provides a full node for transaction verification and interacts with the Bitcoin network.
- Coldcard: Safeguards private keys by storing them securely in hardware, providing offline signing capabilities for transactions.
Together, these tools offer a comprehensive and secure environment for managing Bitcoin funds.
3. Integration
3.1 How Specter Desktop, Bitcoin Core, and Coldcard Work Together
The integration of Specter Desktop, Bitcoin Core, and Coldcard offers a cohesive solution for managing and securing Bitcoin. Here's how these components interact:
- Bitcoin Core runs as a full node, providing a fully verified and trustless Bitcoin network. It validates all transactions and blocks independently.
- Specter Desktop communicates with Bitcoin Core to manage Bitcoin wallets, including setting up multi-signature wallets and connecting to hardware wallets like Coldcard.
- Coldcard is used to securely store the private keys for Bitcoin transactions. When a transaction is created in Specter Desktop, it is signed offline on the Coldcard device before being broadcasted to the Bitcoin network.
The main advantages of this setup include:
- Self-Sovereignty: By using Bitcoin Core and Coldcard, the user has complete control over their funds and does not rely on third-party services for transaction verification or key management.
- Enhanced Security: Coldcard provides the highest level of security for private keys, protecting them from online attacks and malware. Specter Desktop’s integration with Coldcard ensures a user-friendly method for interacting with the hardware wallet.
- Privacy: Using Bitcoin Core allows users to run their own full node, ensuring that they are not dependent on third-party servers, which could compromise privacy.
This integration, in combination with a user-friendly interface from Specter Desktop, allows Bitcoin holders to manage their funds securely, efficiently, and with full autonomy.
3.2 Advantages of This Setup
The combined use of Specter Desktop, Bitcoin Core, and Coldcard offers several advantages over alternative Bitcoin management solutions:
- Enhanced Security: The use of an air-gapped Coldcard wallet ensures private keys never leave the device, even when signing transactions. Coupled with Bitcoin Core’s full node validation, this setup offers unparalleled protection against online threats and attacks.
- Decentralization: Running a full Bitcoin Core node ensures that the user has full control over transaction validation, removing any dependence on centralized third-party services.
- User-Friendly Interface: Specter Desktop simplifies the management of multi-signature wallets and integrates seamlessly with Coldcard, making it accessible even to non-technical users.
4. Installation on OpenBSD
This section provides a step-by-step guide to installing Specter Desktop, Bitcoin Core, and setting up Coldcard on OpenBSD.
4.1 Installing Bitcoin Core
OpenBSD Bitcoin Core Build Guide
Updated for OpenBSD 7.6
This guide outlines the process of building Bitcoin Core (bitcoind), its command-line utilities, and the Bitcoin GUI (bitcoin-qt) on OpenBSD. It covers necessary dependencies, installation steps, and configuration details specific to OpenBSD.
Table of Contents
- Preparation
- Installing Required Dependencies
- Cloning the Bitcoin Core Repository
- Installing Optional Dependencies
- Wallet Dependencies
- GUI Dependencies
- Building Bitcoin Core
- Configuration
- Compilation
- Resource Limit Adjustments
1. Preparation
Before beginning the build process, ensure your system is up-to-date and that you have the necessary dependencies installed.
1.1 Installing Required Dependencies
As the root user, install the base dependencies required for building Bitcoin Core:
bash pkg_add git cmake boost libeventFor a complete list of all dependencies, refer to
dependencies.md.1.2 Cloning the Bitcoin Core Repository
Next, clone the official Bitcoin Core repository to a directory. All build commands will be executed from this directory.
bash git clone https://github.com/bitcoin/bitcoin.git1.3 Installing Optional Dependencies
Bitcoin Core supports optional dependencies for advanced functionality such as wallet support, GUI features, and notifications. Below are the details for the installation of optional dependencies.
1.3.1 Wallet Dependencies
While it is not necessary to build wallet functionality for running
bitcoindorbitcoin-qt, if you need wallet functionality:-
Descriptor Wallet Support: SQLite is required for descriptor wallet functionality.
bash pkg_add sqlite3 -
Legacy Wallet Support: BerkeleyDB is needed for legacy wallet support. It is recommended to use Berkeley DB 4.8. The BerkeleyDB library from OpenBSD ports cannot be used directly, so you will need to build it from source using the
dependsfolder.Run the following command to build it (adjust the path as necessary):
bash gmake -C depends NO_BOOST=1 NO_LIBEVENT=1 NO_QT=1 NO_ZMQ=1 NO_USDT=1After building BerkeleyDB, set the environment variable
BDB_PREFIXto point to the appropriate directory:bash export BDB_PREFIX="[path_to_berkeleydb]"
1.3.2 GUI Dependencies
Bitcoin Core includes a GUI built with Qt6. To compile the GUI, the following dependencies are required:
-
Qt6: Install the necessary parts of the Qt6 framework for GUI support.
bash pkg_add qt6-qtbase qt6-qttools -
libqrencode: The GUI can generate QR codes for addresses. To enable this feature, install
libqrencode:bash pkg_add libqrencodeIf you don't need QR encoding support, use the
-DWITH_QRENCODE=OFFoption during the configuration step to disable it.
1.3.3 Notification Dependencies
Bitcoin Core can provide notifications through ZeroMQ. If you require this functionality, install ZeroMQ:
bash pkg_add zeromq1.3.4 Test Suite Dependencies
Bitcoin Core includes a test suite for development and testing purposes. To run the test suite, you will need Python 3 and the ZeroMQ Python bindings:
bash pkg_add python py3-zmq
2. Building Bitcoin Core
Once all dependencies are installed, follow these steps to configure and compile Bitcoin Core.
2.1 Configuration
Bitcoin Core offers various configuration options. Below are two common setups:
-
Descriptor Wallet and GUI: Enables descriptor wallet support and the GUI. This requires SQLite and Qt6.
bash cmake -B build -DBUILD_GUI=ONTo see all available configuration options, run:
bash cmake -B build -LH -
Descriptor & Legacy Wallet, No GUI: Enables support for both descriptor and legacy wallets, but no GUI.
bash cmake -B build -DBerkeleyDB_INCLUDE_DIR:PATH="${BDB_PREFIX}/include" -DWITH_BDB=ON
2.2 Compile
After configuration, compile the project using the following command. Use the
-j Noption to parallelize the build process, whereNis the number of CPU cores you want to use.bash cmake --build buildTo run the test suite after building, use:
bash ctest --test-dir buildIf Python 3 is not installed, some tests may be skipped.
2.3 Resource Limit Adjustments
OpenBSD's default resource limits are quite restrictive and may cause build failures, especially due to memory issues. If you encounter memory-related errors, increase the data segment limit temporarily for the current shell session:
bash ulimit -d 3000000To make the change permanent for all users, modify the
datasize-curanddatasize-maxvalues in/etc/login.confand reboot the system.
Now Consider
By following these steps, you will be able to successfully build Bitcoin Core on OpenBSD 7.6. This guide covers the installation of essential and optional dependencies, configuration, and the compilation process. Make sure to adjust the resource limits if necessary, especially when dealing with larger codebases.
4.2 Installing Specter Desktop What To Consider
Specter Installation Guide for OpenBSD with Coldcard
This simply aims to provide OpenBSD users with a comprehensive and streamlined process for installing Specter, a Bitcoin wallet management tool. Tailored to those integrating Coldcard hardware wallets with Specter, this guide will help users navigate the installation process, considering various technical levels and preferences. Whether you're a beginner or an advanced user, the guide will empower you to make informed decisions about which installation method suits your needs best.
Specter Installation Methods on OpenBSD
Specter offers different installation methods to accommodate various technical skills and environments. Here, we explore each installation method in the context of OpenBSD, while considering integration with Coldcard for enhanced security in Bitcoin operations.
1. OS-Specific Installation on OpenBSD
Installing Specter directly from OpenBSD's packages or source is an excellent option for users who prefer system-native solutions. This method ensures that Specter integrates seamlessly with OpenBSD’s environment.
- Advantages:
- Easy Installation: Package managers (if available on OpenBSD) simplify the process.
- System Compatibility: Ensures that Specter works well with OpenBSD’s unique system configurations.
-
Convenience: Can be installed on the same machine that runs Bitcoin Core, offering an integrated solution for managing both Bitcoin Core and Coldcard.
-
Disadvantages:
- System-Specific Constraints: OpenBSD’s minimalistic approach might require manual adjustments, especially in terms of dependencies or running services.
-
Updates: You may need to manually update Specter if updates aren’t regularly packaged for OpenBSD.
-
Ideal Use Case: Ideal for users looking for a straightforward, system-native installation that integrates with the local Bitcoin node and uses the Coldcard hardware wallet.
2. PIP Installation on OpenBSD
For those comfortable working in Python environments, PIP installation offers a flexible approach for installing Specter.
- Advantages:
- Simplicity: If you’re already managing Python environments, PIP provides a straightforward and easy method for installation.
- Version Control: Gives users direct control over the version of Specter being installed.
-
Integration: Works well with any existing Python workflow.
-
Disadvantages:
- Python Dependency Management: OpenBSD users may face challenges when managing dependencies, as Python setups on OpenBSD can be non-standard.
-
Technical Knowledge: Requires familiarity with Python and pip, which may not be ideal for non-technical users.
-
Ideal Use Case: Suitable for Python-savvy users who already use Python-based workflows and need more granular control over their installations.
3. Docker Installation
If you're familiar with Docker, running Specter Desktop in Docker containers is a fantastic way to isolate the installation and avoid conflicts with the OpenBSD system.
- Advantages:
- Isolation: Docker ensures Specter runs in an isolated environment, reducing system conflicts.
- Portability: Once set up, Docker containers can be replicated across various platforms and devices.
-
Consistent Environment: Docker ensures consistency in the Specter installation, regardless of underlying OS differences.
-
Disadvantages:
- Docker Setup: OpenBSD’s Docker support isn’t as seamless as other operating systems, potentially requiring extra steps to get everything running.
-
Complexity: For users unfamiliar with Docker, the initial setup can be more challenging.
-
Ideal Use Case: Best for advanced users familiar with Docker environments who require a reproducible and isolated installation.
4. Manual Build from Source (Advanced Users)
For users looking for full control over the installation process, building Specter from source on OpenBSD offers the most flexibility.
- Advantages:
- Customization: You can customize Specter’s functionality and integrate it deeply into your system or workflow.
-
Control: Full control over the build and version management process.
-
Disadvantages:
- Complex Setup: Requires familiarity with development environments, build tools, and dependency management.
-
Time-Consuming: The process of building from source can take longer, especially on OpenBSD, which may lack certain automated build systems for Specter.
-
Ideal Use Case: Best for experienced developers who want to customize Specter to meet specific needs or integrate Coldcard with unique configurations.
5. Node-Specific Integrations (e.g., Raspiblitz, Umbrel, etc.)
If you’re using a Bitcoin node like Raspiblitz or Umbrel along with Specter, these node-specific integrations allow you to streamline wallet management directly from the node interface.
- Advantages:
- Seamless Integration: Integrates Specter directly into the node's wallet management system.
-
Efficient: Allows for efficient management of both Bitcoin Core and Coldcard in a unified environment.
-
Disadvantages:
- Platform Limitation: Not applicable to OpenBSD directly unless you're running a specific node on the same system.
-
Additional Hardware Requirements: Running a dedicated node requires extra hardware resources.
-
Ideal Use Case: Perfect for users already managing Bitcoin nodes with integrated Specter support and Coldcard hardware wallets.
6. Using Package Managers (Homebrew for Linux/macOS)
If you're running OpenBSD on a machine that also supports Homebrew, this method can simplify installation.
- Advantages:
- Simple Setup: Package managers like Homebrew streamline the installation process.
-
Automated Dependency Management: Handles all dependencies automatically, reducing setup complexity.
-
Disadvantages:
- Platform Limitation: Package managers like Homebrew are more commonly used on macOS and Linux, not on OpenBSD.
-
Version Control: May not offer the latest Specter version depending on the repository.
-
Ideal Use Case: Best for users with Homebrew installed, though it may be less relevant for OpenBSD users.
Installation Decision Tree for OpenBSD with Coldcard
- Do you prefer system-native installation or Docker?
- System-native (OpenBSD-specific packages) → Proceed to installation via OS package manager.
-
Docker → Set up Docker container for isolated Specter installation.
-
Are you comfortable with Python?
- Yes → Install using PIP for Python-based environments.
-
No → Move to direct installation methods like Docker or manual build.
-
Do you have a specific Bitcoin node to integrate with?
- Yes → Consider node-specific integrations like Raspiblitz or Umbrel.
- No → Install using Docker or manual source build.
Now Consider
When installing Specter on OpenBSD, consider factors such as your technical expertise, hardware resources, and the need for integration with Coldcard. Beginners might prefer simpler methods like OS-specific packages or Docker, while advanced users will benefit from building from source for complete control over the installation. Choose the method that best fits your environment to maximize your Bitcoin wallet management capabilities.
4.3 Setting Up Coldcard
Refer to the "Coldcard Setup Documentation" section for the installation and configuration instructions specific to Coldcard. At the end of writing.
5. Security Considerations
When using Specter Desktop, Bitcoin Core, and Coldcard together, users benefit from a layered security approach:
- Bitcoin Core offers transaction validation and network security, ensuring that all transactions are verified independently.
- Coldcard provides air-gapped hardware wallet functionality, ensuring private keys are never exposed to potentially compromised devices.
- Specter Desktop facilitates user-friendly management of multi-signature wallets while integrating the security of Bitcoin Core and Coldcard.
However, users must also be aware of potential security risks, including:
- Coldcard Physical Theft: If the Coldcard device is stolen, the attacker would need the PIN code to access the wallet, but physical security must always be maintained.
- Backup Security: Users must securely back up their Coldcard recovery seed to prevent loss of access to funds.
6. Use Cases and Practical Applications
The integration of Specter Desktop, Bitcoin Core, and Coldcard is especially beneficial for:
- High-Value Bitcoin Holders: Those managing large sums of Bitcoin can ensure top-tier security with a multi-signature wallet setup and Coldcard’s air-gapped security.
- Privacy-Conscious Users: Bitcoin Core allows for full network verification, preventing third-party servers from seeing transaction details.
- Cold Storage Solutions: For users who want to keep their Bitcoin safe long-term, the Coldcard provides a secure offline solution while still enabling easy access via Specter Desktop.
7. Coldcard Setup Documentation
This section should provide clear, step-by-step instructions for configuring and using the Coldcard hardware wallet, including how to pair it with Specter Desktop, set up multi-signature wallets, and perform basic operations like signing transactions.
8. Consider
The system you ant to adopt inculcates, integrating Specter Desktop, Bitcoin Core, and Coldcard provides a powerful, secure, and decentralized solution for managing Bitcoin. This setup not only prioritizes user privacy and security but also provides an intuitive interface for even non-technical users. The combination of full node validation, multi-signature support, and air-gapped hardware wallet storage ensures that Bitcoin holdings are protected from both online and physical threats.
As the Bitcoin landscape continues to evolve, this setup can serve as a robust model for self-sovereign financial management, with the potential for future developments to enhance security and usability.
-
 @ 24462930:3caf03ab
2025-04-25 04:37:25
@ 24462930:3caf03ab
2025-04-25 04:37:25Nostr 中所有的数据都是事件,通过将事件存储在多个中继器上来实现去中心化,通过签名来证明事件的拥有者。但如果你想真正拥有你的事件,你应该运行一个自己的中继器来保存它们。否则一旦你使用的所有中继器出了故障或者刻意删除了你的事件,你将永远丢失它们。
对于大部份人来说,运行一个中继器是复杂的,成本高昂的。为了解决这个问题,我开发了 nostr-relay-tray,这是一款可以很方便在个人电脑上运行的中继器,并且支持通过互联网对其进行访问。
项目地址:https://github.com/CodyTseng/nostr-relay-tray
本文将介绍如何使用 nostr-relay-tray 来运行一个自己的中继器。
下载
从 GitHub Release 页面 下载对应你操作系统的安装包
| 操作系统 | 文件格式 | | --------------------- | ---------------------------------- | | Windows |
nostr-relay-tray.Setup.x.x.x.exe| | macOS (Apple Silicon) |nostr-relay-tray-x.x.x-arm64.dmg| | macOS (Intel) |nostr-relay-tray-x.x.x.dmg| | Linux | 你们应该知道使用哪个 |安装
因为我没有对这个安装包进行数字签名,所以在安装时会有一些阻碍。安装成功后,菜单栏会出现一个鸵鸟图标。点击鸵鸟图标,你会看到一个菜单,点击 "Dashboard" 选项可以打开中继器的控制面板进行更多的配置。

macOS 用户注意:
- 首次打开时需要前往「系统设置 > 隐私与安全性」点击“仍要打开”按钮。
- 若遇损坏提示,需要在终端执行以下命令解除限制:
bash sudo xattr -rd com.apple.quarantine /Applications/nostr-relay-tray.appWindows 用户:
- 在安全警告界面点击「更多信息 > 仍要运行」
连接
默认情况下,nostr-relay-tray 只能在本地通过
ws://localhost:4869/进行访问。这让它的用途非常有限,所以我们需要将它暴露到互联网。在控制面板中点击 "Proxy" 选项卡,并打开开关。你将会获得一个 "Public address",你可以使用这个地址在任何地方访问你的中继器。就是这么简单。
接下来,你要将刚刚获得的地址添加到你的中继器列表中。并且要让它在列表中尽可能靠前的位置。因为大部份的客户端会优先连接列表中靠前的中继器,后面的中继器常常会被忽略。

限制
接下来我们需要增加一些限制来防止中继器保存一些与你无关的事件,浪费存储空间。nostr-relay-tray 可以非常灵活精细地设置允许接收哪些事件,但有些复杂,所以不在这里介绍,如果有兴趣可以日后探索。
在这里我先介绍一个很简单有效的策略 —— WoT (Web of Trust)。你可以在 "WoT & PoW" 选项卡中打开这个功能。打开之前你需要先输入你的 pubkey。
这里还有一个非常重要的参数
Depth,它表示某个人与你的关系深度。你关注的人与你的深度为 1,你关注的人关注的人与你的深度为 2,以此类推。- 如果你将这个参数设置为 0,那么你的中继器只会接收你自己的事件。
- 如果你将这个参数设置为 1,那么你的中继器只会接收你和你关注的人的事件。
- 如果你将这个参数设置为 2,那么你的中继器只会接收你和你关注的人的事件,以及你关注的人关注的人的事件。
目前这个参数的最大值只能为 2。

总结
至此,你已经成功运行了一个自己的中继器,并且设置了一个简单的限制来防止中继器保存一些与你无关的事件。
如果你在使用中遇到任何问题,请随时在 GitHub 上提交 issue,我会尽快回复你。
Not your relay, not your events
-
 @ c631e267:c2b78d3e
2025-03-31 07:23:05
@ c631e267:c2b78d3e
2025-03-31 07:23:05Der Irrsinn ist bei Einzelnen etwas Seltenes – \ aber bei Gruppen, Parteien, Völkern, Zeiten die Regel. \ Friedrich Nietzsche
Erinnern Sie sich an die Horrorkomödie «Scary Movie»? Nicht, dass ich diese Art Filme besonders erinnerungswürdig fände, aber einige Szenen daraus sind doch gewissermaßen Klassiker. Dazu zählt eine, die das Verhalten vieler Protagonisten in Horrorfilmen parodiert, wenn sie in Panik flüchten. Welchen Weg nimmt wohl die Frau in der Situation auf diesem Bild?

Diese Szene kommt mir automatisch in den Sinn, wenn ich aktuelle Entwicklungen in Europa betrachte. Weitreichende Entscheidungen gehen wider jede Logik in die völlig falsche Richtung. Nur ist das hier alles andere als eine Komödie, sondern bitterernst. Dieser Horror ist leider sehr real.
Die Europäische Union hat sich selbst über Jahre konsequent in eine Sackgasse manövriert. Sie hat es versäumt, sich und ihre Politik selbstbewusst und im Einklang mit ihren Wurzeln auf dem eigenen Kontinent zu positionieren. Stattdessen ist sie in blinder Treue den vermeintlichen «transatlantischen Freunden» auf ihrem Konfrontationskurs gen Osten gefolgt.
In den USA haben sich die Vorzeichen allerdings mittlerweile geändert, und die einst hoch gelobten «Freunde und Partner» erscheinen den europäischen «Führern» nicht mehr vertrauenswürdig. Das ist spätestens seit der Münchner Sicherheitskonferenz, der Rede von Vizepräsident J. D. Vance und den empörten Reaktionen offensichtlich. Große Teile Europas wirken seitdem wie ein aufgescheuchter Haufen kopfloser Hühner. Orientierung und Kontrolle sind völlig abhanden gekommen.
Statt jedoch umzukehren oder wenigstens zu bremsen und vielleicht einen Abzweig zu suchen, geben die Crash-Piloten jetzt auf dem Weg durch die Sackgasse erst richtig Gas. Ja sie lösen sogar noch die Sicherheitsgurte und deaktivieren die Airbags. Den vor Angst dauergelähmten Passagieren fällt auch nichts Besseres ein und so schließen sie einfach die Augen. Derweil übertrumpfen sich die Kommentatoren des Events gegenseitig in sensationslüsterner «Berichterstattung».
Wie schon die deutsche Außenministerin mit höchsten UN-Ambitionen, Annalena Baerbock, proklamiert auch die Europäische Kommission einen «Frieden durch Stärke». Zu dem jetzt vorgelegten, selbstzerstörerischen Fahrplan zur Ankurbelung der Rüstungsindustrie, genannt «Weißbuch zur europäischen Verteidigung – Bereitschaft 2030», erklärte die Kommissionspräsidentin, die «Ära der Friedensdividende» sei längst vorbei. Soll das heißen, Frieden bringt nichts ein? Eine umfassende Zusammenarbeit an dauerhaften europäischen Friedenslösungen steht demnach jedenfalls nicht zur Debatte.
Zusätzlich brisant ist, dass aktuell «die ganze EU von Deutschen regiert wird», wie der EU-Parlamentarier und ehemalige UN-Diplomat Michael von der Schulenburg beobachtet hat. Tatsächlich sitzen neben von der Leyen und Strack-Zimmermann noch einige weitere Deutsche in – vor allem auch in Krisenzeiten – wichtigen Spitzenposten der Union. Vor dem Hintergrund der Kriegstreiberei in Deutschland muss eine solche Dominanz mindestens nachdenklich stimmen.
Ihre ursprünglichen Grundwerte wie Demokratie, Freiheit, Frieden und Völkerverständigung hat die EU kontinuierlich in leere Worthülsen verwandelt. Diese werden dafür immer lächerlicher hochgehalten und beschworen.
Es wird dringend Zeit, dass wir, der Souverän, diesem erbärmlichen und gefährlichen Trauerspiel ein Ende setzen und die Fäden selbst in die Hand nehmen. In diesem Sinne fordert uns auch das «European Peace Project» auf, am 9. Mai im Rahmen eines Kunstprojekts den Frieden auszurufen. Seien wir dabei!
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 6e64b83c:94102ee8
2025-04-23 20:23:34
@ 6e64b83c:94102ee8
2025-04-23 20:23:34How to Run Your Own Nostr Relay on Android with Cloudflare Domain
Prerequisites
- Install Citrine on your Android device:
- Visit https://github.com/greenart7c3/Citrine/releases
- Download the latest release using:
- zap.store
- Obtainium
- F-Droid
- Or download the APK directly
-
Note: You may need to enable "Install from Unknown Sources" in your Android settings
-
Domain Requirements:
- Purchase a domain if you don't have one
-
Transfer your domain to Cloudflare if it's not already there (for free SSL certificates and cloudflared support)
-
Tools to use:
- nak (the nostr army knife):
- Download from https://github.com/fiatjaf/nak/releases
- Installation steps:
-
For Linux/macOS: ```bash # Download the appropriate version for your system wget https://github.com/fiatjaf/nak/releases/latest/download/nak-linux-amd64 # for Linux # or wget https://github.com/fiatjaf/nak/releases/latest/download/nak-darwin-amd64 # for macOS
# Make it executable chmod +x nak-*
# Move to a directory in your PATH sudo mv nak-* /usr/local/bin/nak
- For Windows:batch # Download the Windows version curl -L -o nak.exe https://github.com/fiatjaf/nak/releases/latest/download/nak-windows-amd64.exe# Move to a directory in your PATH (e.g., C:\Windows) move nak.exe C:\Windows\nak.exe
- Verify installation:bash nak --version ```
Setting Up Citrine
- Open the Citrine app
- Start the server
- You'll see it running on
ws://127.0.0.1:4869(local network only) - Go to settings and paste your npub into "Accept events signed by" inbox and press the + button. This prevents others from publishing events to your personal relay.
Installing Required Tools
- Install Termux from Google Play Store
- Open Termux and run:
bash pkg update && pkg install wget wget https://github.com/cloudflare/cloudflared/releases/latest/download/cloudflared-linux-arm64.deb dpkg -i cloudflared-linux-arm64.debCloudflare Authentication
- Run the authentication command:
bash cloudflared tunnel login - Follow the instructions:
- Copy the provided URL to your browser
- Log in to your Cloudflare account
- If the URL expires, copy it again after logging in
Creating the Tunnel
- Create a new tunnel:
bash cloudflared tunnel create <TUNNEL_NAME> - Choose any name you prefer for your tunnel
-
Copy the tunnel ID after creating the tunnel
-
Create and configure the tunnel config:
bash touch ~/.cloudflared/config.yml nano ~/.cloudflared/config.yml -
Add this configuration (replace the placeholders with your values): ```yaml tunnel:
credentials-file: /data/data/com.termux/files/home/.cloudflared/ .json ingress: - hostname: nostr.yourdomain.com service: ws://localhost:4869
- service: http_status:404 ```
- Note: In nano editor:
CTRL+Oand Enter to saveCTRL+Xto exit
-
Note: Check the credentials file path in the logs
-
Validate your configuration:
bash cloudflared tunnel validate -
Start the tunnel:
bash cloudflared tunnel run my-relay
Preventing Android from Killing the Tunnel
Run these commands to maintain tunnel stability:
bash date && apt install termux-tools && termux-setup-storage && termux-wake-lock echo "nameserver 1.1.1.1" > $PREFIX/etc/resolv.confTip: You can open multiple Termux sessions by swiping from the left edge of the screen while keeping your tunnel process running.
Updating Your Outbox Model Relays
Once your relay is running and accessible via your domain, you'll want to update your relay list in the Nostr network. This ensures other clients know about your relay and can connect to it.
Decoding npub (Public Key)
Private keys (nsec) and public keys (npub) are encoded in bech32 format, which includes: - A prefix (like nsec1, npub1 etc.) - The encoded data - A checksum
This format makes keys: - Easy to distinguish - Hard to copy incorrectly
However, most tools require these keys in hexadecimal (hex) format.
To decode an npub string to its hex format:
bash nak decode nostr:npub1dejts0qlva8mqzjlrxqkc2tmvs2t7elszky5upxaf3jha9qs9m5q605uc4Change it with your own npub.
bash { "pubkey": "6e64b83c1f674fb00a5f19816c297b6414bf67f015894e04dd4c657e94102ee8" }Copy the pubkey value in quotes.
Create a kind 10002 event with your relay list:
- Include your new relay with write permissions
- Include other relays you want to read from and write to, omit 3rd parameter to make it both read and write
Example format:
json { "kind": 10002, "tags": [ ["r", "wss://your-relay-domain.com", "write"], ["r", "wss://eden.nostr.land/"], ["r", "wss://nos.lol/"], ["r", "wss://nostr.bitcoiner.social/"], ["r", "wss://nostr.mom/"], ["r", "wss://relay.primal.net/"], ["r", "wss://nostr.wine/", "read"], ["r", "wss://relay.damus.io/"], ["r", "wss://relay.nostr.band/"], ["r", "wss://relay.snort.social/"] ], "content": "" }Save it to a file called
event.jsonNote: Add or remove any relays you want. To check your existing 10002 relays: - Visit https://nostr.band/?q=by%3Anpub1dejts0qlva8mqzjlrxqkc2tmvs2t7elszky5upxaf3jha9qs9m5q605uc4+++kind%3A10002 - nostr.band is an indexing service, it probably has your relay list. - Replace
npub1xxxin the URL with your own npub - Click "VIEW JSON" from the menu to see the raw event - Or use thenaktool if you know the relaysbash nak req -k 10002 -a <your-pubkey> wss://relay1.com wss://relay2.comReplace `<your-pubkey>` with your public key in hex format (you can get it using `nak decode <your-npub>`)- Sign and publish the event:
- Use a Nostr client that supports kind 10002 events
- Or use the
nakcommand-line tool:bash nak event --sec ncryptsec1... wss://relay1.com wss://relay2.com $(cat event.json)
Important Security Notes: 1. Never share your nsec (private key) with anyone 2. Consider using NIP-49 encrypted keys for better security 3. Never paste your nsec or private key into the terminal. The command will be saved in your shell history, exposing your private key. To clear the command history: - For bash: use
history -c- For zsh: usefc -Wto write history to file, thenfc -pto read it back - Or manually edit your shell history file (e.g.,~/.zsh_historyor~/.bash_history) 4. if you're usingzsh, usefc -pto prevent the next command from being saved to history 5. Or temporarily disable history before running sensitive commands:bash unset HISTFILE nak key encrypt ... set HISTFILEHow to securely create NIP-49 encypted private key
```bash
Read your private key (input will be hidden)
read -s SECRET
Read your password (input will be hidden)
read -s PASSWORD
encrypt command
echo "$SECRET" | nak key encrypt "$PASSWORD"
copy and paste the ncryptsec1 text from the output
read -s ENCRYPTED nak key decrypt "$ENCRYPTED"
clear variables from memory
unset SECRET PASSWORD ENCRYPTED ```
On a Windows command line, to read from stdin and use the variables in
nakcommands, you can use a combination ofset /pto read input and then use those variables in your command. Here's an example:```bash @echo off set /p "SECRET=Enter your secret key: " set /p "PASSWORD=Enter your password: "
echo %SECRET%| nak key encrypt %PASSWORD%
:: Clear the sensitive variables set "SECRET=" set "PASSWORD=" ```
If your key starts with
ncryptsec1, thenaktool will securely prompt you for a password when using the--secparameter, unless the command is used with a pipe< >or|.bash nak event --sec ncryptsec1... wss://relay1.com wss://relay2.com $(cat event.json)- Verify the event was published:
- Check if your relay list is visible on other relays
-
Use the
naktool to fetch your kind 10002 events:bash nak req -k 10002 -a <your-pubkey> wss://relay1.com wss://relay2.com -
Testing your relay:
- Try connecting to your relay using different Nostr clients
- Verify you can both read from and write to your relay
- Check if events are being properly stored and retrieved
- Tip: Use multiple Nostr clients to test different aspects of your relay
Note: If anyone in the community has a more efficient method of doing things like updating outbox relays, please share your insights in the comments. Your expertise would be greatly appreciated!
-
 @ c631e267:c2b78d3e
2025-03-21 19:41:50
@ c631e267:c2b78d3e
2025-03-21 19:41:50Wir werden nicht zulassen, dass technisch manches möglich ist, \ aber der Staat es nicht nutzt. \ Angela Merkel
Die Modalverben zu erklären, ist im Deutschunterricht manchmal nicht ganz einfach. Nicht alle Fremdsprachen unterscheiden zum Beispiel bei der Frage nach einer Möglichkeit gleichermaßen zwischen «können» im Sinne von «die Gelegenheit, Kenntnis oder Fähigkeit haben» und «dürfen» als «die Erlaubnis oder Berechtigung haben». Das spanische Wort «poder» etwa steht für beides.
Ebenso ist vielen Schülern auf den ersten Blick nicht recht klar, dass das logische Gegenteil von «müssen» nicht unbedingt «nicht müssen» ist, sondern vielmehr «nicht dürfen». An den Verkehrsschildern lässt sich so etwas meistens recht gut erklären: Manchmal muss man abbiegen, aber manchmal darf man eben nicht.

Dieses Beispiel soll ein wenig die Verwirrungstaktik veranschaulichen, die in der Politik gerne verwendet wird, um unpopuläre oder restriktive Maßnahmen Stück für Stück einzuführen. Zuerst ist etwas einfach innovativ und bringt viele Vorteile. Vor allem ist es freiwillig, jeder kann selber entscheiden, niemand muss mitmachen. Später kann man zunehmend weniger Alternativen wählen, weil sie verschwinden, und irgendwann verwandelt sich alles andere in «nicht dürfen» – die Maßnahme ist obligatorisch.
Um die Durchsetzung derartiger Initiativen strategisch zu unterstützen und nett zu verpacken, gibt es Lobbyisten, gerne auch NGOs genannt. Dass das «NG» am Anfang dieser Abkürzung übersetzt «Nicht-Regierungs-» bedeutet, ist ein Anachronismus. Das war vielleicht früher einmal so, heute ist eher das Gegenteil gemeint.
In unserer modernen Zeit wird enorm viel Lobbyarbeit für die Digitalisierung praktisch sämtlicher Lebensbereiche aufgewendet. Was das auf dem Sektor der Mobilität bedeuten kann, haben wir diese Woche anhand aktueller Entwicklungen in Spanien beleuchtet. Begründet teilweise mit Vorgaben der Europäischen Union arbeitet man dort fleißig an einer «neuen Mobilität», basierend auf «intelligenter» technologischer Infrastruktur. Derartige Anwandlungen wurden auch schon als «Technofeudalismus» angeprangert.
Nationale Zugangspunkte für Mobilitätsdaten im Sinne der EU gibt es nicht nur in allen Mitgliedsländern, sondern auch in der Schweiz und in Großbritannien. Das Vereinigte Königreich beteiligt sich darüber hinaus an anderen EU-Projekten für digitale Überwachungs- und Kontrollmaßnahmen, wie dem biometrischen Identifizierungssystem für «nachhaltigen Verkehr und Tourismus».
Natürlich marschiert auch Deutschland stracks und euphorisch in Richtung digitaler Zukunft. Ohne vernetzte Mobilität und einen «verlässlichen Zugang zu Daten, einschließlich Echtzeitdaten» komme man in der Verkehrsplanung und -steuerung nicht aus, erklärt die Regierung. Der Interessenverband der IT-Dienstleister Bitkom will «die digitale Transformation der deutschen Wirtschaft und Verwaltung vorantreiben». Dazu bewirbt er unter anderem die Konzepte Smart City, Smart Region und Smart Country und behauptet, deutsche Großstädte «setzen bei Mobilität voll auf Digitalisierung».
Es steht zu befürchten, dass das umfassende Sammeln, Verarbeiten und Vernetzen von Daten, das angeblich die Menschen unterstützen soll (und theoretisch ja auch könnte), eher dazu benutzt wird, sie zu kontrollieren und zu manipulieren. Je elektrischer und digitaler unsere Umgebung wird, desto größer sind diese Möglichkeiten. Im Ergebnis könnten solche Prozesse den Bürger nicht nur einschränken oder überflüssig machen, sondern in mancherlei Hinsicht regelrecht abschalten. Eine gesunde Skepsis ist also geboten.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Er ist zuerst auf Transition News erschienen.
-
 @ 9bde4214:06ca052b
2025-04-22 18:13:37
@ 9bde4214:06ca052b
2025-04-22 18:13:37"It's gonna be permissionless or hell."
Gigi and gzuuus are vibing towards dystopia.
Books & articles mentioned:
- AI 2027
- DVMs were a mistake
- Careless People by Sarah Wynn-Williams
- Takedown by Laila michelwait
- The Ultimate Resource by Julian L. Simon
- Harry Potter by J.K. Rowling
- Momo by Michael Ende
In this dialogue:
- Pablo's Roo Setup
- Tech Hype Cycles
- AI 2027
- Prompt injection and other attacks
- Goose and DVMCP
- Cursor vs Roo Code
- Staying in control thanks to Amber and signing delegation
- Is YOLO mode here to stay?
- What agents to trust?
- What MCP tools to trust?
- What code snippets to trust?
- Everyone will run into the issues of trust and micropayments
- Nostr solves Web of Trust & micropayments natively
- Minimalistic & open usually wins
- DVMCP exists thanks to Totem
- Relays as Tamagochis
- Agents aren't nostr experts, at least not right now
- Fix a mistake once & it's fixed forever
- Giving long-term memory to LLMs
- RAG Databases signed by domain experts
- Human-agent hybrids & Chess
- Nostr beating heart
- Pluggable context & experts
- "You never need an API key for anything"
- Sats and social signaling
- Difficulty-adjusted PoW as a rare-limiting mechanism
- Certificate authorities and centralization
- No solutions to policing speech!
- OAuth and how it centralized
- Login with nostr
- Closed vs open-source models
- Tiny models vs large models
- The minions protocol (Stanford paper)
- Generalist models vs specialized models
- Local compute & encrypted queries
- Blinded compute
- "In the eyes of the state, agents aren't people"
- Agents need identity and money; nostr provides both
- "It's gonna be permissionless or hell"
- We already have marketplaces for MCP stuff, code snippets, and other things
- Most great stuff came from marketplaces (browsers, games, etc)
- Zapstore shows that this is already working
- At scale, central control never works. There's plenty scams and viruses in the app stores.
- Using nostr to archive your user-generated content
- HAVEN, blossom, novia
- The switcharoo from advertisements to training data
- What is Truth?
- What is Real?
- "We're vibing into dystopia"
- Who should be the arbiter of Truth?
- First Amendment & why the Logos is sacred
- Silicon Valley AI bros arrogantly dismiss wisdom and philosophy
- Suicide rates & the meaning crisis
- Are LLMs symbiotic or parasitic?
- The Amish got it right
- Are we gonna make it?
- Careless People by Sarah Wynn-Williams
- Takedown by Laila michelwait
- Harry Potter dementors & Momo's time thieves
- Facebook & Google as non-human (superhuman) agents
- Zapping as a conscious action
- Privacy and the internet
- Plausible deniability thanks to generative models
- Google glasses, glassholes, and Meta's Ray Ben's
- People crave realness
- Bitcoin is the realest money we ever had
- Nostr allows for real and honest expression
- How do we find out what's real?
- Constraints, policing, and chilling effects
- Jesus' plans for DVMCP
- Hzrd's article on how DVMs are broken (DVMs were a mistake)
- Don't believe the hype
- DVMs pre-date MCP tools
- Data Vending Machines were supposed to be stupid: put coin in, get stuff out.
- Self-healing vibe-coding
- IP addresses as scarce assets
- Atomic swaps and the ASS protocol
- More marketplaces, less silos
- The intensity of #SovEng and the last 6 weeks
- If you can vibe-code everything, why build anything?
- Time, the ultimate resource
- What are the LLMs allowed to think?
- Natural language interfaces are inherently dialogical
- Sovereign Engineering is dialogical too
-
 @ aa8de34f:a6ffe696
2025-03-21 12:08:31
@ aa8de34f:a6ffe696
2025-03-21 12:08:3119. März 2025
🔐 1. SHA-256 is Quantum-Resistant
Bitcoin’s proof-of-work mechanism relies on SHA-256, a hashing algorithm. Even with a powerful quantum computer, SHA-256 remains secure because:
- Quantum computers excel at factoring large numbers (Shor’s Algorithm).
- However, SHA-256 is a one-way function, meaning there's no known quantum algorithm that can efficiently reverse it.
- Grover’s Algorithm (which theoretically speeds up brute force attacks) would still require 2¹²⁸ operations to break SHA-256 – far beyond practical reach.
++++++++++++++++++++++++++++++++++++++++++++++++++
🔑 2. Public Key Vulnerability – But Only If You Reuse Addresses
Bitcoin uses Elliptic Curve Digital Signature Algorithm (ECDSA) to generate keys.
- A quantum computer could use Shor’s Algorithm to break SECP256K1, the curve Bitcoin uses.
- If you never reuse addresses, it is an additional security element
- 🔑 1. Bitcoin Addresses Are NOT Public Keys
Many people assume a Bitcoin address is the public key—this is wrong.
- When you receive Bitcoin, it is sent to a hashed public key (the Bitcoin address).
- The actual public key is never exposed because it is the Bitcoin Adress who addresses the Public Key which never reveals the creation of a public key by a spend
- Bitcoin uses Pay-to-Public-Key-Hash (P2PKH) or newer methods like Pay-to-Witness-Public-Key-Hash (P2WPKH), which add extra layers of security.
🕵️♂️ 2.1 The Public Key Never Appears
- When you send Bitcoin, your wallet creates a digital signature.
- This signature uses the private key to prove ownership.
- The Bitcoin address is revealed and creates the Public Key
- The public key remains hidden inside the Bitcoin script and Merkle tree.
This means: ✔ The public key is never exposed. ✔ Quantum attackers have nothing to target, attacking a Bitcoin Address is a zero value game.
+++++++++++++++++++++++++++++++++++++++++++++++++
🔄 3. Bitcoin Can Upgrade
Even if quantum computers eventually become a real threat:
- Bitcoin developers can upgrade to quantum-safe cryptography (e.g., lattice-based cryptography or post-quantum signatures like Dilithium).
- Bitcoin’s decentralized nature ensures a network-wide soft fork or hard fork could transition to quantum-resistant keys.
++++++++++++++++++++++++++++++++++++++++++++++++++
⏳ 4. The 10-Minute Block Rule as a Security Feature
- Bitcoin’s network operates on a 10-minute block interval, meaning:Even if an attacker had immense computational power (like a quantum computer), they could only attempt an attack every 10 minutes.Unlike traditional encryption, where a hacker could continuously brute-force keys, Bitcoin’s system resets the challenge with every new block.This limits the window of opportunity for quantum attacks.
🎯 5. Quantum Attack Needs to Solve a Block in Real-Time
- A quantum attacker must solve the cryptographic puzzle (Proof of Work) in under 10 minutes.
- The problem? Any slight error changes the hash completely, meaning:If the quantum computer makes a mistake (even 0.0001% probability), the entire attack fails.Quantum decoherence (loss of qubit stability) makes error correction a massive challenge.The computational cost of recovering from an incorrect hash is still incredibly high.
⚡ 6. Network Resilience – Even if a Block Is Hacked
- Even if a quantum computer somehow solved a block instantly:The network would quickly recognize and reject invalid transactions.Other miners would continue mining under normal cryptographic rules.51% Attack? The attacker would need to consistently beat the entire Bitcoin network, which is not sustainable.
🔄 7. The Logarithmic Difficulty Adjustment Neutralizes Threats
- Bitcoin adjusts mining difficulty every 2016 blocks (\~2 weeks).
- If quantum miners appeared and suddenly started solving blocks too quickly, the difficulty would adjust upward, making attacks significantly harder.
- This self-correcting mechanism ensures that even quantum computers wouldn't easily overpower the network.
🔥 Final Verdict: Quantum Computers Are Too Slow for Bitcoin
✔ The 10-minute rule limits attack frequency – quantum computers can’t keep up.
✔ Any slight miscalculation ruins the attack, resetting all progress.
✔ Bitcoin’s difficulty adjustment would react, neutralizing quantum advantages.
Even if quantum computers reach their theoretical potential, Bitcoin’s game theory and design make it incredibly resistant. 🚀
-
 @ a95c6243:d345522c
2025-03-20 09:59:20
@ a95c6243:d345522c
2025-03-20 09:59:20Bald werde es verboten, alleine im Auto zu fahren, konnte man dieser Tage in verschiedenen spanischen Medien lesen. Die nationale Verkehrsbehörde (Dirección General de Tráfico, kurz DGT) werde Alleinfahrern das Leben schwer machen, wurde gemeldet. Konkret erörtere die Generaldirektion geeignete Sanktionen für Personen, die ohne Beifahrer im Privatauto unterwegs seien.
Das Alleinfahren sei zunehmend verpönt und ein Mentalitätswandel notwendig, hieß es. Dieser «Luxus» stehe im Widerspruch zu den Maßnahmen gegen Umweltverschmutzung, die in allen europäischen Ländern gefördert würden. In Frankreich sei es «bereits verboten, in der Hauptstadt allein zu fahren», behauptete Noticiastrabajo Huffpost in einer Zwischenüberschrift. Nur um dann im Text zu konkretisieren, dass die sogenannte «Umweltspur» auf der Pariser Ringautobahn gemeint war, die für Busse, Taxis und Fahrgemeinschaften reserviert ist. Ab Mai werden Verstöße dagegen mit einem Bußgeld geahndet.
Die DGT jedenfalls wolle bei der Umsetzung derartiger Maßnahmen nicht hinterherhinken. Diese Medienberichte, inklusive des angeblich bevorstehenden Verbots, beriefen sich auf Aussagen des Generaldirektors der Behörde, Pere Navarro, beim Mobilitätskongress Global Mobility Call im November letzten Jahres, wo es um «nachhaltige Mobilität» ging. Aus diesem Kontext stammt auch Navarros Warnung: «Die Zukunft des Verkehrs ist geteilt oder es gibt keine».
Die «Faktenchecker» kamen der Generaldirektion prompt zu Hilfe. Die DGT habe derlei Behauptungen zurückgewiesen und klargestellt, dass es keine Pläne gebe, Fahrten mit nur einer Person im Auto zu verbieten oder zu bestrafen. Bei solchen Meldungen handele es sich um Fake News. Teilweise wurde der Vorsitzende der spanischen «Rechtsaußen»-Partei Vox, Santiago Abascal, der Urheberschaft bezichtigt, weil er einen entsprechenden Artikel von La Gaceta kommentiert hatte.
Der Beschwichtigungsversuch der Art «niemand hat die Absicht» ist dabei erfahrungsgemäß eher ein Alarmzeichen als eine Beruhigung. Walter Ulbrichts Leugnung einer geplanten Berliner Mauer vom Juni 1961 ist vielen genauso in Erinnerung wie die Fake News-Warnungen des deutschen Bundesgesundheitsministeriums bezüglich Lockdowns im März 2020 oder diverse Äußerungen zu einer Impfpflicht ab 2020.
Aber Aufregung hin, Dementis her: Die Pressemitteilung der DGT zu dem Mobilitätskongress enthält in Wahrheit viel interessantere Informationen als «nur» einen Appell an den «guten» Bürger wegen der Bemühungen um die Lebensqualität in Großstädten oder einen möglichen obligatorischen Abschied vom Alleinfahren. Allerdings werden diese Details von Medien und sogenannten Faktencheckern geflissentlich übersehen, obwohl sie keineswegs versteckt sind. Die Auskünfte sind sehr aufschlussreich, wenn man genauer hinschaut.
Digitalisierung ist der Schlüssel für Kontrolle
Auf dem Kongress stellte die Verkehrsbehörde ihre Initiativen zur Förderung der «neuen Mobilität» vor, deren Priorität Sicherheit und Effizienz sei. Die vier konkreten Ansätze haben alle mit Digitalisierung, Daten, Überwachung und Kontrolle im großen Stil zu tun und werden unter dem Euphemismus der «öffentlich-privaten Partnerschaft» angepriesen. Auch lassen sie die transhumanistische Idee vom unzulänglichen Menschen erkennen, dessen Fehler durch «intelligente» technologische Infrastruktur kompensiert werden müssten.
Die Chefin des Bereichs «Verkehrsüberwachung» erklärte die Funktion des spanischen National Access Point (NAP), wobei sie betonte, wie wichtig Verkehrs- und Infrastrukturinformationen in Echtzeit seien. Der NAP ist «eine essenzielle Web-Applikation, die unter EU-Mandat erstellt wurde», kann man auf der Website der DGT nachlesen.
Das Mandat meint Regelungen zu einem einheitlichen europäischen Verkehrsraum, mit denen die Union mindestens seit 2010 den Aufbau einer digitalen Architektur mit offenen Schnittstellen betreibt. Damit begründet man auch «umfassende Datenbereitstellungspflichten im Bereich multimodaler Reiseinformationen». Jeder Mitgliedstaat musste einen NAP, also einen nationalen Zugangspunkt einrichten, der Zugang zu statischen und dynamischen Reise- und Verkehrsdaten verschiedener Verkehrsträger ermöglicht.
Diese Entwicklung ist heute schon weit fortgeschritten, auch und besonders in Spanien. Auf besagtem Kongress erläuterte die Leiterin des Bereichs «Telematik» die Plattform «DGT 3.0». Diese werde als Integrator aller Informationen genutzt, die von den verschiedenen öffentlichen und privaten Systemen, die Teil der Mobilität sind, bereitgestellt werden.
Es handele sich um eine Vermittlungsplattform zwischen Akteuren wie Fahrzeugherstellern, Anbietern von Navigationsdiensten oder Kommunen und dem Endnutzer, der die Verkehrswege benutzt. Alle seien auf Basis des Internets der Dinge (IOT) anonym verbunden, «um der vernetzten Gemeinschaft wertvolle Informationen zu liefern oder diese zu nutzen».
So sei DGT 3.0 «ein Zugangspunkt für einzigartige, kostenlose und genaue Echtzeitinformationen über das Geschehen auf den Straßen und in den Städten». Damit lasse sich der Verkehr nachhaltiger und vernetzter gestalten. Beispielsweise würden die Karten des Produktpartners Google dank der DGT-Daten 50 Millionen Mal pro Tag aktualisiert.
Des Weiteren informiert die Verkehrsbehörde über ihr SCADA-Projekt. Die Abkürzung steht für Supervisory Control and Data Acquisition, zu deutsch etwa: Kontrollierte Steuerung und Datenerfassung. Mit SCADA kombiniert man Software und Hardware, um automatisierte Systeme zur Überwachung und Steuerung technischer Prozesse zu schaffen. Das SCADA-Projekt der DGT wird von Indra entwickelt, einem spanischen Beratungskonzern aus den Bereichen Sicherheit & Militär, Energie, Transport, Telekommunikation und Gesundheitsinformation.
Das SCADA-System der Behörde umfasse auch eine Videostreaming- und Videoaufzeichnungsplattform, die das Hochladen in die Cloud in Echtzeit ermöglicht, wie Indra erklärt. Dabei gehe es um Bilder, die von Überwachungskameras an Straßen aufgenommen wurden, sowie um Videos aus DGT-Hubschraubern und Drohnen. Ziel sei es, «die sichere Weitergabe von Videos an Dritte sowie die kontinuierliche Aufzeichnung und Speicherung von Bildern zur möglichen Analyse und späteren Nutzung zu ermöglichen».
Letzteres klingt sehr nach biometrischer Erkennung und Auswertung durch künstliche Intelligenz. Für eine bessere Datenübertragung wird derzeit die Glasfaserverkabelung entlang der Landstraßen und Autobahnen ausgebaut. Mit der Cloud sind die Amazon Web Services (AWS) gemeint, die spanischen Daten gehen somit direkt zu einem US-amerikanischen «Big Data»-Unternehmen.
Das Thema «autonomes Fahren», also Fahren ohne Zutun des Menschen, bildet den Abschluss der Betrachtungen der DGT. Zusammen mit dem Interessenverband der Automobilindustrie ANFAC (Asociación Española de Fabricantes de Automóviles y Camiones) sprach man auf dem Kongress über Strategien und Perspektiven in diesem Bereich. Die Lobbyisten hoffen noch in diesem Jahr 2025 auf einen normativen Rahmen zur erweiterten Unterstützung autonomer Technologien.
Wenn man derartige Informationen im Zusammenhang betrachtet, bekommt man eine Idee davon, warum zunehmend alles elektrisch und digital werden soll. Umwelt- und Mobilitätsprobleme in Städten, wie Luftverschmutzung, Lärmbelästigung, Platzmangel oder Staus, sind eine Sache. Mit dem Argument «emissionslos» wird jedoch eine Referenz zum CO2 und dem «menschengemachten Klimawandel» hergestellt, die Emotionen triggert. Und damit wird so ziemlich alles verkauft.
Letztlich aber gilt: Je elektrischer und digitaler unsere Umgebung wird und je freigiebiger wir mit unseren Daten jeder Art sind, desto besser werden wir kontrollier-, steuer- und sogar abschaltbar. Irgendwann entscheiden KI-basierte Algorithmen, ob, wann, wie, wohin und mit wem wir uns bewegen dürfen. Über einen 15-Minuten-Radius geht dann möglicherweise nichts hinaus. Die Projekte auf diesem Weg sind ernst zu nehmen, real und schon weit fortgeschritten.
[Titelbild: Pixabay]
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ fd06f542:8d6d54cd
2025-04-25 03:07:03
@ fd06f542:8d6d54cd
2025-04-25 03:07:03什么是电子书系统?
目前电子书系统非常多,gitbook,mkdocs,vitepress。但是这些系统都有一个问题,就是你需要 静态存储你的markdown文件, 而且不能在线编写。
现有的电子书系统,你需要用一个 第三方编辑器 制作好一个一个的md文件,并且编排好目录结构,然后用上面列举的 软件生成 一个website。
现有电子书的缺点是什么?
- 空间问题,你需要存书的空间;
- 编写不方便 写好以后需要手动上传;
- 登录到服务器更新写好的新文件;
- 不支持交互和评论;
- 再重启服务器,(有些可能不需要重启,自己能监控);
以上过程太繁琐了。
nostrbook如何解决这个问题?
- nostrbook采用的在线编辑;
- 用户无须任何空间,内容存储到第三方服务器,你也可以用自己的服务器;
- 免费,开源;
- 发布轻松,写好点"提交"就发布了,不需要过多的动作;
- 无须其他的维护成本;
- 支持 评论和点赞;
- 可以私有部署,到自己服务器,或者部署在本机都可以。
搭建过程
环境依赖
- nodejs
安装过程
git clone https://github.com/nostrbook/nostrbook cd nostrbook npm install npm run dev定制化配置
修改这个文件 https://github.com/nostrbook/nostrbook/blob/main/src/lib/config.ts export let booktag="createbook"; export let blogtag="createblog"; export let chaptertag="bookchapter";修以上3个参数,就可以成为你自己的 电子书和blog了。
你要你的系统安装了nodejs,就可以了。 Windows,Linux ,macos都可以。
系统支持 电子书和blog,你可以搭建 私有 日志系统也可以。
-
 @ a95c6243:d345522c
2025-03-15 10:56:08
@ a95c6243:d345522c
2025-03-15 10:56:08Was nützt die schönste Schuldenbremse, wenn der Russe vor der Tür steht? \ Wir können uns verteidigen lernen oder alle Russisch lernen. \ Jens Spahn
In der Politik ist buchstäblich keine Idee zu riskant, kein Mittel zu schäbig und keine Lüge zu dreist, als dass sie nicht benutzt würden. Aber der Clou ist, dass diese Masche immer noch funktioniert, wenn nicht sogar immer besser. Ist das alles wirklich so schwer zu durchschauen? Mir fehlen langsam die Worte.
Aktuell werden sowohl in der Europäischen Union als auch in Deutschland riesige Milliardenpakete für die Aufrüstung – also für die Rüstungsindustrie – geschnürt. Die EU will 800 Milliarden Euro locker machen, in Deutschland sollen es 500 Milliarden «Sondervermögen» sein. Verteidigung nennen das unsere «Führer», innerhalb der Union und auch an «unserer Ostflanke», der Ukraine.
Das nötige Feindbild konnte inzwischen signifikant erweitert werden. Schuld an allem und zudem gefährlich ist nicht mehr nur Putin, sondern jetzt auch Trump. Europa müsse sich sowohl gegen Russland als auch gegen die USA schützen und rüsten, wird uns eingetrichtert.
Und während durch Diplomatie genau dieser beiden Staaten gerade endlich mal Bewegung in die Bemühungen um einen Frieden oder wenigstens einen Waffenstillstand in der Ukraine kommt, rasselt man im moralisch überlegenen Zeigefinger-Europa so richtig mit dem Säbel.
Begleitet und gestützt wird der ganze Prozess – wie sollte es anders sein – von den «Qualitätsmedien». Dass Russland einen Angriff auf «Europa» plant, weiß nicht nur der deutsche Verteidigungsminister (und mit Abstand beliebteste Politiker) Pistorius, sondern dank ihnen auch jedes Kind. Uns bleiben nur noch wenige Jahre. Zum Glück bereitet sich die Bundeswehr schon sehr konkret auf einen Krieg vor.
Die FAZ und Corona-Gesundheitsminister Spahn markieren einen traurigen Höhepunkt. Hier haben sich «politische und publizistische Verantwortungslosigkeit propagandistisch gegenseitig befruchtet», wie es bei den NachDenkSeiten heißt. Die Aussage Spahns in dem Interview, «der Russe steht vor der Tür», ist das eine. Die Zeitung verschärfte die Sache jedoch, indem sie das Zitat explizit in den Titel übernahm, der in einer ersten Version scheinbar zu harmlos war.
Eine große Mehrheit der deutschen Bevölkerung findet Aufrüstung und mehr Schulden toll, wie ARD und ZDF sehr passend ermittelt haben wollen. Ähnliches gelte für eine noch stärkere militärische Unterstützung der Ukraine. Etwas skeptischer seien die Befragten bezüglich der Entsendung von Bundeswehrsoldaten dorthin, aber immerhin etwa fifty-fifty.
Eigentlich ist jedoch die Meinung der Menschen in «unseren Demokratien» irrelevant. Sowohl in der Europäischen Union als auch in Deutschland sind die «Eliten» offenbar der Ansicht, der Souverän habe in Fragen von Krieg und Frieden sowie von aberwitzigen astronomischen Schulden kein Wörtchen mitzureden. Frau von der Leyen möchte über 150 Milliarden aus dem Gesamtpaket unter Verwendung von Artikel 122 des EU-Vertrags ohne das Europäische Parlament entscheiden – wenn auch nicht völlig kritiklos.
In Deutschland wollen CDU/CSU und SPD zur Aufweichung der «Schuldenbremse» mehrere Änderungen des Grundgesetzes durch das abgewählte Parlament peitschen. Dieser Versuch, mit dem alten Bundestag eine Zweidrittelmehrheit zu erzielen, die im neuen nicht mehr gegeben wäre, ist mindestens verfassungsrechtlich umstritten.
Das Manöver scheint aber zu funktionieren. Heute haben die Grünen zugestimmt, nachdem Kanzlerkandidat Merz läppische 100 Milliarden für «irgendwas mit Klima» zugesichert hatte. Die Abstimmung im Plenum soll am kommenden Dienstag erfolgen – nur eine Woche, bevor sich der neu gewählte Bundestag konstituieren wird.
Interessant sind die Argumente, die BlackRocker Merz für seine Attacke auf Grundgesetz und Demokratie ins Feld führt. Abgesehen von der angeblichen Eile, «unsere Verteidigungsfähigkeit deutlich zu erhöhen» (ausgelöst unter anderem durch «die Münchner Sicherheitskonferenz und die Ereignisse im Weißen Haus»), ließ uns der CDU-Chef wissen, dass Deutschland einfach auf die internationale Bühne zurück müsse. Merz schwadronierte gefährlich mehrdeutig:
«Die ganze Welt schaut in diesen Tagen und Wochen auf Deutschland. Wir haben in der Europäischen Union und auf der Welt eine Aufgabe, die weit über die Grenzen unseres eigenen Landes hinausgeht.»
[Titelbild: Tag des Sieges]
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ fd78c37f:a0ec0833
2025-04-21 04:40:30
@ fd78c37f:a0ec0833
2025-04-21 04:40:30Bitcoin is redefining finance, and in Asia—Thailand, Vietnam, Indonesia, and beyond—developers, entrepreneurs, and communities are fueling this revolution. YakiHonne, a decentralized social payments app built on Nostr, sat down with Gio (nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx), a core member of Thailand’s Sats ‘N’ Facts community, to explore their mission of fostering open-source Bitcoin development. In this interview, Gio shares the origins of Sats ‘N’ Facts, the challenges of hosting Bitcoin-focused events in Asia, and how these efforts are shaping adoption across the region.
YakiHonne: Can you tell us about yourself and how Sats ‘N’ Facts came to life? What sparked your Bitcoin journey?
Gio: I’m originally from Europe but have called Thailand home for six years. My Bitcoin story began while working at a commercial bank, where I saw the fiat system’s flaws firsthand—things like the Cantillon Effect, where money printing favors the connected few, felt deeply unfair. That discomfort led me to Andreas Antonopoulos’ videos, which opened my eyes to Bitcoin’s potential. After moving to Bangkok, I joined the open-source scene at BOB Space, collaborating with folks on tech projects.
Sats ‘N’ Facts grew out of that spirit. We wanted to create a Bitcoin-focused community to support developers and builders in Asia. Our recent conference in Chiang Mai brought together over 70 enthusiasts from Thailand, Vietnam, Laos, and beyond, sparking collaborations like a new Lightning Network tool. It was a milestone in connecting the region’s Bitcoin ecosystem.
YakiHonne: What inspired the Sats ‘N’ Facts conference, and how did you attract attendees?
Gio: The event was born from a desire to create a high-signal, low-noise space for Freedom Tech in Asia. While the U.S. and Europe host major Bitcoin events, Asia’s scene is still emerging under commercial stunts. We aimed to bridge that gap, uniting developers, educators, and enthusiasts to discuss real innovations—no altcoins, no corporate agendas. Our focus was on open-source projects like Bitcoin Core, Ark, Cashu, fostering conversations that could lead to tangible contributions.
Attracting attendees wasn’t easy. We leveraged local networks, reaching out to Bitcoin communities in neighboring countries via Nostr and Telegram. Posts on X helped spread the word, and we saw developers from Laos join for the first time, which was thrilling. Sponsors like Fulgur Ventures, Utreexo, and the Bitcoin Development Kit Foundation played a huge role, covering costs so we could keep the event free and accessible.
YakiHonne: What challenges did you face organizing the conference in Asia?
Gio: It was a steep learning curve. Funding was the biggest hurdle—early on, we struggled to cover venue and travel costs. Thankfully, our sponsors stepped in, letting me focus on logistics, which were no small feat either. As a first-time organizer, I underestimated the chaos of a tight timeline. Day one felt like herding cats without a fixed agenda, but the energy was electric—developers debugging code together, newcomers asking big questions.
Another challenge was cultural. Bitcoin’s still niche in Asia, so convincing locals to attend took persistence; there was no local presence for some reason. Despite the hiccups, we pulled it off, hosting 60+ attendees and sparking ideas for new projects, like a Cashu wallet integration. I’d tweak the planning next time, but the raw passion made it unforgettable.
YakiHonne: How does YakiHonne’s vision of decentralized social payments align with Sats ‘N’ Facts’ goals? Could tools like ours support your community?
Gio: That’s a great question. YakiHonne’s approach—merging Nostr’s censorship-resistant communication with Lightning payments—fits perfectly with our mission to empower users through open tech. At Sats ‘N’ Facts, we’re all about tools that give people control, whether it’s code or money. An app like YakiHonne could streamline community funding, letting developers tip each other for contributions or crowdfund projects directly. Imagine a hackathon where winners get sats instantly via YakiHonne—it’d be a game-changer. I’d love to see you guys at our next event to demo it!
YakiHonne: What advice would you give to someone starting a Bitcoin-focused community or event?
Gio: First, keep it Bitcoin-only. Stay true to the principles—cut out distractions like altcoins or hype-driven schemes. Start small: host regular meetups, maybe five people at a café, and build trust over time. Consistency and authenticity beat flashiness in the medium and long term.
Second, involve technical folks. Developers bring credibility and clarity, explaining Bitcoin’s nuts and bolts in ways newcomers get. I admire how Andreas Antonopoulos bridges that gap—technical yet accessible. You need that foundation to grow a real community.
Finally, lean on existing networks. If you know someone running a Bitcoin meetup in another city, collaborate. Share ideas, speakers, or even livestreams. Nostr’s great for this—our Laos attendees found us through a single post. Relationships are everything.
YakiHonne: Does Sats ‘N’ Facts focus more on Bitcoin’s technical side, non-technical side, or both?
Gio: We blend both. Our event had workshops for coders alongside talks for beginners on why Bitcoin matters. Open-source is our heartbeat, though. If you’re starting out, dive into projects like Bitcoin Core or Lightning. Review a pull request, test a Cashu wallet, or join a hackathon. One developer at our event built a Lightning micropayment tool that’s now live on GitHub.
There’s no shortage of ways to contribute. Community calls, forums, residency programs, and platforms like Geyser Fund are goldmines. YakiHonne could amplify this—imagine tipping developers for bug fixes via your app. It’s about iterating until you create something real.
YakiHonne: Your work is inspiring, Gio. Sats ‘N’ Facts is uniting Asia’s Bitcoin communities in a powerful way. What’s next for you?
Gio: Thanks for the kind words! We’re just getting started. The Chiang Mai event showed what’s possible—connecting developers across borders, reviewing and launching code and testing upcoming technologies. Next, we’re planning smaller hackathons and other events to keep the momentum going, maybe in Vietnam, Indonesia or Korea. I’d love to integrate tools like YakiHonne to fund these efforts directly through Nostr payments. Long-term, we want Sats ‘N’ Facts to be a hub for Asia’s Bitcoin builders, proving open-source can thrive here.

YakiHonne: Thank you, Gio, for sharing Sats ‘N’ Facts incredible journey. Your work is lighting a path for Bitcoin in Asia, and we’re honored to tell this story.
To our readers: Bitcoin’s future depends on communities like Sats ‘N’ Facts—and you can join the revolution. Download YakiHonne on Nostr to connect with builders, send Lightning payments, and explore the decentralized world. Follow Sats ‘N’ Facts for their next hackathon, and let’s build freedom tech together!
-
 @ ed5774ac:45611c5c
2025-04-19 20:29:31
@ ed5774ac:45611c5c
2025-04-19 20:29:31April 20, 2020: The day I saw my so-called friends expose themselves as gutless, brain-dead sheep.
On that day, I shared a video exposing the damning history of the Bill & Melinda Gates Foundation's vaccine campaigns in Africa and the developing world. As Gates was on every TV screen, shilling COVID jabs that didn’t even exist, I called out his blatant financial conflict of interest and pointed out the obvious in my facebook post: "Finally someone is able to explain why Bill Gates runs from TV to TV to promote vaccination. Not surprisingly, it's all about money again…" - referencing his substantial investments in vaccine technology, including BioNTech's mRNA platform that would later produce the COVID vaccines and generate massive profits for his so-called philanthropic foundation.
The conflict of interest was undeniable. I genuinely believed anyone capable of basic critical thinking would at least pause to consider these glaring financial motives. But what followed was a masterclass in human stupidity.
My facebook post from 20 April 2020:

Not only was I branded a 'conspiracy theorist' for daring to question the billionaire who stood to make a fortune off the very vaccines he was shilling, but the brain-dead, logic-free bullshit vomited by the people around me was beyond pathetic. These barely literate morons couldn’t spell "Pfizer" without auto-correct, yet they mindlessly swallowed and repeated every lie the media and government force-fed them, branding anything that cracked their fragile reality as "conspiracy theory." Big Pharma’s rap sheet—fraud, deadly cover-ups, billions in fines—could fill libraries, yet these obedient sheep didn’t bother to open a single book or read a single study before screaming their ignorance, desperate to virtue-signal their obedience. Then, like spineless lab rats, they lined up for an experimental jab rushed to the market in months, too dumb to care that proper vaccine development takes a decade.
The pathetic part is that these idiots spend hours obsessing over reviews for their useless purchases like shoes or socks, but won’t spare 60 seconds to research the experimental cocktail being injected into their veins—or even glance at the FDA’s own damning safety reports. Those same obedient sheep would read every Yelp review for a fucking coffee shop but won't spend five minutes looking up Pfizer's criminal fraud settlements. They would demand absolute obedience to ‘The Science™’—while being unable to define mRNA, explain lipid nanoparticles, or justify why trials were still running as they queued up like cattle for their jab. If they had two brain cells to rub together or spent 30 minutes actually researching, they'd know, but no—they'd rather suck down the narrative like good little slaves, too dumb to question, too weak to think.
Worst of all, they became the system’s attack dogs—not just swallowing the poison, but forcing it down others’ throats. This wasn’t ignorance. It was betrayal. They mutated into medical brownshirts, destroying lives to virtue-signal their obedience—even as their own children’s hearts swelled with inflammation.
One conversation still haunts me to this day—a masterclass in wealth-worship delusion. A close friend, as a response to my facebook post, insisted that Gates’ assumed reading list magically awards him vaccine expertise, while dismissing his billion-dollar investments in the same products as ‘no conflict of interest.’ Worse, he argued that Gates’s $5–10 billion pandemic windfall was ‘deserved.’
This exchange crystallizes civilization’s intellectual surrender: reason discarded with religious fervor, replaced by blind faith in corporate propaganda.
The comment of a friend on my facebook post that still haunts me to this day:

Walking Away from the Herd
After a period of anger and disillusionment, I made a decision: I would no longer waste energy arguing with people who refused to think for themselves. If my circle couldn’t even ask basic questions—like why an untested medical intervention was being pushed with unprecedented urgency—then I needed a new community.
Fortunately, I already knew where to look. For three years, I had been involved in Bitcoin, a space where skepticism wasn’t just tolerated—it was demanded. Here, I’d met some of the most principled and independent thinkers I’d ever encountered. These were people who understood the corrupting influence of centralized power—whether in money, media, or politics—and who valued sovereignty, skepticism, and integrity. Instead of blind trust, bitcoiners practiced relentless verification. And instead of empty rhetoric, they lived by a simple creed: Don’t trust. Verify.
It wasn’t just a philosophy. It was a lifeline. So I chose my side and I walked away from the herd.
Finding My Tribe
Over the next four years, I immersed myself in Bitcoin conferences, meetups, and spaces where ideas were tested, not parroted. Here, I encountered extraordinary people: not only did they share my skepticism toward broken systems, but they challenged me to sharpen it.
No longer adrift in a sea of mindless conformity, I’d found a crew of thinkers who cut through the noise. They saw clearly what most ignored—that at the core of society’s collapse lay broken money, the silent tax on time, freedom, and truth itself. But unlike the complainers I’d left behind, these people built. They coded. They wrote. They risked careers and reputations to expose the rot. Some faced censorship; others, mockery. All understood the stakes.
These weren’t keyboard philosophers. They were modern-day Cassandras, warning of inflation’s theft, the Fed’s lies, and the coming dollar collapse—not for clout, but because they refused to kneel to a dying regime. And in their defiance, I found something rare: a tribe that didn’t just believe in a freer future. They were engineering it.
April 20, 2024: No more herd. No more lies. Only proof-of-work.
On April 20, 2024, exactly four years after my last Facebook post, the one that severed my ties to the herd for good—I stood in front of Warsaw’s iconic Palace of Culture and Science, surrounded by 400 bitcoiners who felt like family. We were there to celebrate Bitcoin’s fourth halving, but it was more than a protocol milestone. It was a reunion of sovereign individuals. Some faces I’d known since the early days; others, I’d met only hours before. We bonded instantly—heated debates, roaring laughter, zero filters on truths or on so called conspiracy theories.
As the countdown to the halving began, it hit me: This was the antithesis of the hollow world I’d left behind. No performative outrage, no coerced consensus—just a room of unyielding minds who’d traded the illusion of safety for the grit of truth. Four years prior, I’d been alone in my resistance. Now, I raised my glass among my people - those who had seen the system's lies and chosen freedom instead. Each had their own story of awakening, their own battles fought, but here we shared the same hard-won truth.
The energy wasn’t just electric. It was alive—the kind that emerges when free people build rather than beg. For the first time, I didn’t just belong. I was home. And in that moment, the halving’s ticking clock mirrored my own journey: cyclical, predictable in its scarcity, revolutionary in its consequences. Four years had burned away the old world. What remained was stronger.

No Regrets
Leaving the herd wasn’t a choice—it was evolution. My soul shouted: "I’d rather stand alone than kneel with the masses!". The Bitcoin community became more than family; they’re living proof that the world still produces warriors, not sheep. Here, among those who forge truth, I found something extinct elsewhere: hope that burns brighter with every halving, every block, every defiant mind that joins the fight.
Change doesn’t come from the crowd. It starts when one person stops applauding.
Today, I stand exactly where I always wanted to be—shoulder-to-shoulder with my true family: the rebels, the builders, the ungovernable. Together, we’re building the decentralized future.
-
 @ 30b99916:3cc6e3fe
2025-04-19 19:55:31
@ 30b99916:3cc6e3fe
2025-04-19 19:55:31btcpayserver #lightning #lnd #powershell #coinos
BTCpayAPI now supports CoinOS.io REST Api

Adding Coinos.io REST Api end points support to BTCpayAPI. Here is what is implemented, tested and doumented so far.
Current REST APIs supported are now:
LND API https://lightning.engineering/api-docs/api/lnd/ BTCPay Greenfield API (v1) https://docs.btcpayserver.org/API/Greenfield/v1/ Hashicorp Vault API https://developer.hashicorp.com/vault/api-docs/secret/kv/kv-v1 Coinos.io API https://coinos.io/docs
Although this is PowerShell code, it is exclusively being developed and tested on Linux only.
Code is available at https://btcpayserver.sytes.net
-
 @ 502ab02a:a2860397
2025-04-25 02:19:05
@ 502ab02a:a2860397
2025-04-25 02:19:05วันนี้จะเล่าเรื่องโครงการ School Plates โดย ProVeg UK ให้อ่านครับ
ProVeg UK เปิดตัวโครงการ School Plates ในเดือนมิถุนายน 2018 โดยมีเป้าหมายเพื่อช่วยให้โรงเรียนในสหราชอาณาจักรเสิร์ฟอาหารที่ดีต่อสุขภาพและเป็นมิตรต่อสิ่งแวดล้อมมากขึ้น โครงการนี้มุ่งเน้นการเพิ่มคุณภาพ ปริมาณ และการยอมรับของอาหารจากพืชในเมนูโรงเรียน โดยเฉพาะในโรงเรียนประถมศึกษา ซึ่งส่วนใหญ่จะอยู่ภายใต้การดูแลของหน่วยงานท้องถิ่น
เพื่อการสนับสนุนโครงการ บริการที่ ProVeg UK มอบให้จะประกอบไปด้วย บริการฟรีแก่โรงเรียน หน่วยงานท้องถิ่น และผู้จัดเลี้ยงอาหารโรงเรียน เพื่อสนับสนุนการเปลี่ยนแปลงเมนูอย่างมีประสิทธิภาพ บริการเหล่านี้รวมถึง -การให้คำปรึกษาเมนู โดยให้คำแนะนำในการปรับสมดุลเมนู และใช้ภาษาที่ส่งเสริมอาหารจากพืช -การพัฒนาสูตรอาหารใหม่ ช่วยสร้างสูตรอาหารจากพืชที่อร่อย มีคุณค่าทางโภชนาการ และเหมาะสมกับครัวโรงเรียน -การจัดเวิร์กช็อปและการฝึกอบรม โดยจัดอบรมทั้งแบบออนไลน์และแบบพบหน้าสำหรับพ่อครัวและเจ้าหน้าที่ครัวโรงเรียน -การวิเคราะห์ด้านสุขภาพ สิ่งแวดล้อม และงบประมาณ มีโปรแกรมประเมินผลกระทบของเมนูต่อสุขภาพเด็ก การปล่อยก๊าซเรือนกระจก และต้นทุน ให้ครบถ้วน
นอกจากนี้ยังมีการจัดรางวัล School Plates Awards: มอบรางวัลระดับ Bronze, Silver และ Gold ให้แก่โรงเรียนที่มีความมุ่งมั่นในการปรับปรุงเมนูอย่างยั่งยืน ด้วย
ผลลัพธ์ตั้งแต่เริ่มโครงการ School Plates ได้เปลี่ยนแปลงเมนูอาหารโรงเรียนมากกว่า 6 ล้านมื้อ ให้กลายเป็นอาหารที่ดีต่อสุขภาพและยั่งยืนมากขึ้น โดยมีการเพิ่มวัน Meat-Free Mondays และตัวเลือกอาหารจากพืชในเมนูประจำวันของโรงเรียนหลายแห่ง
สูตรอาหารที่พัฒนาโดย ProVeg UK มีคุณสมบัติประมาณนี้ครับ -มีโปรตีนเทียบเท่ากับอาหารที่มีเนื้อสัตว์ -มีไขมันอิ่มตัวต่ำกว่า -อุดมไปด้วยไฟเบอร์และสารอาหารที่จำเป็น -มีการปล่อยก๊าซเรือนกระจกต่ำ -สอดคล้องกับมาตรฐานอาหารและโภชนาการของโรงเรียนในสหราชอาณาจักร
นั่นทำให้โครงการ School Plates ได้รับการยอมรับจากโรงเรียนและหน่วยงานท้องถิ่นหลายแห่งในสหราชอาณาจักร และยังได้รับการเสนอชื่อเข้าชิงรางวัลด้านสิ่งแวดล้อมระดับโลก เช่น Food Planet Prize
ทีนี้เรามาวิเคราะห์กันว่า School Plates คือ เมนูรักษ์โลกหรือกับดักระบบ? โครงการ School Plates ของ ProVeg UK ภายนอกดูเหมือนเรื่องดี เป็นการ “ช่วยโรงเรียนให้เปลี่ยนเมนูไปทาง plant-based เพื่อสุขภาพเด็กและโลก” มีการให้คำปรึกษา ทำสูตรอาหาร อบรมพ่อครัว และพูดจาภาษาดี ๆ ว่า "อาหารยั่งยืน" กับ "ทางเลือกที่ดีต่อสุขภาพ" แต่ถ้ามองลึกเข้าไป มันไม่ใช่แค่อาหาร มันคือ เกมเปลี่ยนโครงสร้างการผลิตอาหารในระดับระบบ โดยใช้ “เด็กในโรงเรียน” เป็นจุดตั้งต้น
ถ้าดูเผิน ๆ เราอาจนึกว่าเด็กได้กินผักเยอะขึ้น โลกได้ลดก๊าซเรือนกระจก แต่ถ้าขุดเข้าไป จะเห็นว่าเบื้องหลัง ProVeg UK เชื่อมโยงกับกลุ่มทุน plant-based ขนาดใหญ่ ไม่ว่าจะเป็นผู้ผลิตนมถั่ว เนื้อเทียม หรือบริษัทยีสต์และจุลินทรีย์ที่ใช้ทำโปรตีนหมัก (Precision Fermentation) ทั้งหลาย
และอย่าลืมว่า ProVeg มีพันธมิตรกับองค์กรระดับโลกอย่าง EAT Foundation, World Resources Institute, และกลุ่ม lobby ต่าง ๆ ที่ผลักดัน นโยบายเปลี่ยนอาหารโลก ให้ไปทาง plant-based เป็นหลัก ซึ่งดูดี… ถ้าเราไม่รู้ว่าเบื้องหลังมันคือระบบ “อาหารสำเร็จรูปจากโรงงาน” ที่อ้างคำว่า “รักษ์โลก” แต่ผลิตโดยอุตสาหกรรมที่กระจุกตัวสูงมาก
ปัญหาที่คนอาจไม่ค่อยพูดถึงก็มีอยู่ครับเช่น -ละเลยโภชนาการตามธรรมชาติของเด็ก เพราะเด็กวัยเจริญเติบโตต้องการ โปรตีนคุณภาพสูง ไขมันดี และ สารอาหารที่พบเฉพาะในสัตว์ เช่น วิตามิน B12, เฮม-ไอรอน, โคลีน, คาร์โนซีน ฯลฯ ซึ่งอาหาร plant-based จำนวนมากขาด หรือมีในรูปแบบดูดซึมยากกว่าหลายเท่า - ใช้คำว่า "สิ่งแวดล้อม" บังหน้า แต่เป็นการผูกขาดระบบอาหาร การผลัก plant-based ไม่ได้ลดการพึ่งพาระบบอุตสาหกรรมเลย ตรงกันข้ามคือมันพาเราเข้าสู่ยุคของ plant-based ultra-processed food ที่ผลิตจากซอยโปรตีน ถั่วเหลือง GMO 2.0 น้ำมันพืช และสารแต่งรส... จากโรงงาน - เจาะระบบโรงเรียน = วางรากฐานความเชื่อ ให้เด็กที่โตมากับอาหารแบบนี้จะเชื่อว่านี่คือ “ของดี” และมองโปรตีนจากสัตว์เป็นสิ่งแปลกแยกในอนาคต เหมือนเป็นการ “reset” วิถีอาหารใหม่แบบไม่รู้ตัวผ่าน เจเนอเรชั่น - กลไกการจัดซื้อของรัฐจะถูก redirect ไปยังกลุ่มทุนใหญ่นอกพื้นที่ จากที่โรงเรียนจำนวนมากเคยซื้อวัตถุดิบจากชุมชน หรือฟาร์มใกล้เคียง พอโครงการแบบนี้เข้ามา จะค่อย ๆ ทำให้วัตถุดิบถูกกำหนดจาก เมนูที่ standardized ซึ่งสุดท้ายต้องพึ่ง “สินค้าสำเร็จรูปจากระบบอุตสาหกรรม”
ซึ่งถ้าเรามองโภชนาการสำหรับเด็กจริงๆแล้วนั้น เราควรลดของแปรรูป ไม่ใช่แค่ลดเนื้อ และใช้วัตถุดิบสดแท้จากธรรมชาติ ไม่ใช่ plant-based industrial food นอกจากนี้ยังควรสนับสนุนอาหารจากฟาร์มท้องถิ่น ทั้งผัก ไข่ เนื้อ และผลิตผลจากเกษตรกรจริง รวมถึงให้เด็กได้รู้จักที่มาของอาหาร ไม่ใช่แค่เรียนรู้แคลอรีกับคาร์บอนที่ว่ากันว่าปล่อยออกมา
School Plates คือก้าวเล็ก ๆ สู่การเปลี่ยนโครงสร้างใหญ่ของการควบคุมอาหารของโลก มันไม่ได้แค่เรื่องของเมนูกลางวัน แต่มันคือ “ระบบคิด” ที่กำลัง reshape โลกให้เด็กยุคใหม่โตมาโดยไม่รู้จัก real food ในสายตาเฮีย แม้โครงการนี้ไม่ได้เลวร้ายทั้งหมด แต่มันมี “เจตนาเชิงโครงสร้าง” ที่ต้องจับตาอย่างมาก และเราควรถามกลับเสมอว่า... ทำไมเราถึงต้องยัดอาหารสังเคราะห์ในนามของการ “รักโลก” แต่กลับตัดขาดจากดิน น้ำ ฟ้า และฟาร์มท้องถิ่น? ทำไม?
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ a95c6243:d345522c
2025-03-11 10:22:36
@ a95c6243:d345522c
2025-03-11 10:22:36«Wir brauchen eine digitale Brandmauer gegen den Faschismus», schreibt der Chaos Computer Club (CCC) auf seiner Website. Unter diesem Motto präsentierte er letzte Woche einen Forderungskatalog, mit dem sich 24 Organisationen an die kommende Bundesregierung wenden. Der Koalitionsvertrag müsse sich daran messen lassen, verlangen sie.
In den drei Kategorien «Bekenntnis gegen Überwachung», «Schutz und Sicherheit für alle» sowie «Demokratie im digitalen Raum» stellen die Unterzeichner, zu denen auch Amnesty International und Das NETTZ gehören, unter anderem die folgenden «Mindestanforderungen»:
- Verbot biometrischer Massenüberwachung des öffentlichen Raums sowie der ungezielten biometrischen Auswertung des Internets.
- Anlasslose und massenhafte Vorratsdatenspeicherung wird abgelehnt.
- Automatisierte Datenanalysen der Informationsbestände der Strafverfolgungsbehörden sowie jede Form von Predictive Policing oder automatisiertes Profiling von Menschen werden abgelehnt.
- Einführung eines Rechts auf Verschlüsselung. Die Bundesregierung soll sich dafür einsetzen, die Chatkontrolle auf europäischer Ebene zu verhindern.
- Anonyme und pseudonyme Nutzung des Internets soll geschützt und ermöglicht werden.
- Bekämpfung «privaten Machtmissbrauchs von Big-Tech-Unternehmen» durch durchsetzungsstarke, unabhängige und grundsätzlich föderale Aufsichtsstrukturen.
- Einführung eines digitalen Gewaltschutzgesetzes, unter Berücksichtigung «gruppenbezogener digitaler Gewalt» und die Förderung von Beratungsangeboten.
- Ein umfassendes Förderprogramm für digitale öffentliche Räume, die dezentral organisiert und quelloffen programmiert sind, soll aufgelegt werden.
Es sei ein Irrglaube, dass zunehmende Überwachung einen Zugewinn an Sicherheit darstelle, ist eines der Argumente der Initiatoren. Sicherheit erfordere auch, dass Menschen anonym und vertraulich kommunizieren können und ihre Privatsphäre geschützt wird.
Gesunde digitale Räume lebten auch von einem demokratischen Diskurs, lesen wir in dem Papier. Es sei Aufgabe des Staates, Grundrechte zu schützen. Dazu gehöre auch, Menschenrechte und demokratische Werte, insbesondere Freiheit, Gleichheit und Solidarität zu fördern sowie den Missbrauch von Maßnahmen, Befugnissen und Infrastrukturen durch «die Feinde der Demokratie» zu verhindern.
Man ist geneigt zu fragen, wo denn die Autoren «den Faschismus» sehen, den es zu bekämpfen gelte. Die meisten der vorgetragenen Forderungen und Argumente finden sicher breite Unterstützung, denn sie beschreiben offenkundig gängige, kritikwürdige Praxis. Die Aushebelung der Privatsphäre, der Redefreiheit und anderer Grundrechte im Namen der Sicherheit wird bereits jetzt massiv durch die aktuellen «demokratischen Institutionen» und ihre «durchsetzungsstarken Aufsichtsstrukturen» betrieben.
Ist «der Faschismus» also die EU und ihre Mitgliedsstaaten? Nein, die «faschistische Gefahr», gegen die man eine digitale Brandmauer will, kommt nach Ansicht des CCC und seiner Partner aus den Vereinigten Staaten. Private Überwachung und Machtkonzentration sind dabei weltweit schon lange Realität, jetzt endlich müssen sie jedoch bekämpft werden. In dem Papier heißt es:
«Die willkürliche und antidemokratische Machtausübung der Tech-Oligarchen um Präsident Trump erfordert einen Paradigmenwechsel in der deutschen Digitalpolitik. (...) Die aktuellen Geschehnisse in den USA zeigen auf, wie Datensammlungen und -analyse genutzt werden können, um einen Staat handstreichartig zu übernehmen, seine Strukturen nachhaltig zu beschädigen, Widerstand zu unterbinden und marginalisierte Gruppen zu verfolgen.»
Wer auf der anderen Seite dieser Brandmauer stehen soll, ist also klar. Es sind die gleichen «Feinde unserer Demokratie», die seit Jahren in diese Ecke gedrängt werden. Es sind die gleichen Andersdenkenden, Regierungskritiker und Friedensforderer, die unter dem großzügigen Dach des Bundesprogramms «Demokratie leben» einem «kontinuierlichen Echt- und Langzeitmonitoring» wegen der Etikettierung «digitaler Hass» unterzogen werden.
Dass die 24 Organisationen praktisch auch die Bekämpfung von Google, Microsoft, Apple, Amazon und anderen fordern, entbehrt nicht der Komik. Diese fallen aber sicher unter das Stichwort «Machtmissbrauch von Big-Tech-Unternehmen». Gleichzeitig verlangen die Lobbyisten implizit zum Beispiel die Förderung des Nostr-Netzwerks, denn hier finden wir dezentral organisierte und quelloffen programmierte digitale Räume par excellence, obendrein zensurresistent. Das wiederum dürfte in der Politik weniger gut ankommen.
[Titelbild: Pixabay]
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ dab6c606:51f507b6
2025-04-18 14:59:25
@ dab6c606:51f507b6
2025-04-18 14:59:25Core idea: Use geotagged anonymized Nostr events with Cashu-based points to snitch on cop locations for a more relaxed driving and walking
We all know navigation apps. There's one of them that allows you to report on locations of cops. It's Waze and it's owned by Google. There are perfectly fine navigation apps like Organic Maps, that unfortunately lack the cop-snitching features. In some countries, it is illegal to report cop locations, so it would probably not be a good idea to use your npub to report them. But getting a points Cashu token as a reward and exchanging them from time to time would solve this. You can of course report construction, traffic jams, ...
Proposed solution: Add Nostr client (Copstr) to Organic Maps. Have a button in bottom right allowing you to report traffic situations. Geotagged events are published on Nostr relays, users sending cashu tokens as thank you if the report is valid. Notes have smart expiration times.
Phase 2: Automation: Integration with dashcams and comma.ai allow for automated AI recognition of traffic events such as traffic jams and cops, with automatic touchless reporting.
Result: Drive with most essential information and with full privacy. Collect points to be cool and stay cool.
-
 @ c4b5369a:b812dbd6
2025-04-15 07:26:16
@ c4b5369a:b812dbd6
2025-04-15 07:26:16Offline transactions with Cashu
Over the past few weeks, I've been busy implementing offline capabilities into nutstash. I think this is one of the key value propositions of ecash, beinga a bearer instrument that can be used without internet access.
 It does however come with limitations, which can lead to a bit of confusion. I hope this article will clear some of these questions up for you!
It does however come with limitations, which can lead to a bit of confusion. I hope this article will clear some of these questions up for you!What is ecash/Cashu?
Ecash is the first cryptocurrency ever invented. It was created by David Chaum in 1983. It uses a blind signature scheme, which allows users to prove ownership of a token without revealing a link to its origin. These tokens are what we call ecash. They are bearer instruments, meaning that anyone who possesses a copy of them, is considered the owner.
Cashu is an implementation of ecash, built to tightly interact with Bitcoin, more specifically the Bitcoin lightning network. In the Cashu ecosystem,
Mintsare the gateway to the lightning network. They provide the infrastructure to access the lightning network, pay invoices and receive payments. Instead of relying on a traditional ledger scheme like other custodians do, the mint issues ecash tokens, to represent the value held by the users.How do normal Cashu transactions work?
A Cashu transaction happens when the sender gives a copy of his ecash token to the receiver. This can happen by any means imaginable. You could send the token through email, messenger, or even by pidgeon. One of the common ways to transfer ecash is via QR code.
The transaction is however not finalized just yet! In order to make sure the sender cannot double-spend their copy of the token, the receiver must do what we call a
swap. A swap is essentially exchanging an ecash token for a new one at the mint, invalidating the old token in the process. This ensures that the sender can no longer use the same token to spend elsewhere, and the value has been transferred to the receiver.
What about offline transactions?
Sending offline
Sending offline is very simple. The ecash tokens are stored on your device. Thus, no internet connection is required to access them. You can litteraly just take them, and give them to someone. The most convenient way is usually through a local transmission protocol, like NFC, QR code, Bluetooth, etc.
The one thing to consider when sending offline is that ecash tokens come in form of "coins" or "notes". The technical term we use in Cashu is
Proof. It "proofs" to the mint that you own a certain amount of value. Since these proofs have a fixed value attached to them, much like UTXOs in Bitcoin do, you would need proofs with a value that matches what you want to send. You can mix and match multiple proofs together to create a token that matches the amount you want to send. But, if you don't have proofs that match the amount, you would need to go online and swap for the needed proofs at the mint.Another limitation is, that you cannot create custom proofs offline. For example, if you would want to lock the ecash to a certain pubkey, or add a timelock to the proof, you would need to go online and create a new custom proof at the mint.
Receiving offline
You might think: well, if I trust the sender, I don't need to be swapping the token right away!
You're absolutely correct. If you trust the sender, you can simply accept their ecash token without needing to swap it immediately.
This is already really useful, since it gives you a way to receive a payment from a friend or close aquaintance without having to worry about connectivity. It's almost just like physical cash!
It does however not work if the sender is untrusted. We have to use a different scheme to be able to receive payments from someone we don't trust.
Receiving offline from an untrusted sender
To be able to receive payments from an untrusted sender, we need the sender to create a custom proof for us. As we've seen before, this requires the sender to go online.
The sender needs to create a token that has the following properties, so that the receciver can verify it offline:
- It must be locked to ONLY the receiver's public key
- It must include an
offline signature proof(DLEQ proof) - If it contains a timelock & refund clause, it must be set to a time in the future that is acceptable for the receiver
- It cannot contain duplicate proofs (double-spend)
- It cannot contain proofs that the receiver has already received before (double-spend)

If all of these conditions are met, then the receiver can verify the proof offline and accept the payment. This allows us to receive payments from anyone, even if we don't trust them.
At first glance, this scheme seems kinda useless. It requires the sender to go online, which defeats the purpose of having an offline payment system.
I beleive there are a couple of ways this scheme might be useful nonetheless:
-
Offline vending machines: Imagine you have an offline vending machine that accepts payments from anyone. The vending machine could use this scheme to verify payments without needing to go online itself. We can assume that the sender is able to go online and create a valid token, but the receiver doesn't need to be online to verify it.
-
Offline marketplaces: Imagine you have an offline marketplace where buyers and sellers can trade goods and services. Before going to the marketplace the sender already knows where he will be spending the money. The sender could create a valid token before going to the marketplace, using the merchants public key as a lock, and adding a refund clause to redeem any unspent ecash after it expires. In this case, neither the sender nor the receiver needs to go online to complete the transaction.
How to use this
Pretty much all cashu wallets allow you to send tokens offline. This is because all that the wallet needs to do is to look if it can create the desired amount from the proofs stored locally. If yes, it will automatically create the token offline.
Receiving offline tokens is currently only supported by nutstash (experimental).
To create an offline receivable token, the sender needs to lock it to the receiver's public key. Currently there is no refund clause! So be careful that you don't get accidentally locked out of your funds!

The receiver can then inspect the token and decide if it is safe to accept without a swap. If all checks are green, they can accept the token offline without trusting the sender.

The receiver will see the unswapped tokens on the wallet homescreen. They will need to manually swap them later when they are online again.
 Later when the receiver is online again, they can swap the token for a fresh one.
Later when the receiver is online again, they can swap the token for a fresh one.
Summary
We learned that offline transactions are possible with ecash, but there are some limitations. It either requires trusting the sender, or relying on either the sender or receiver to be online to verify the tokens, or create tokens that can be verified offline by the receiver.
I hope this short article was helpful in understanding how ecash works and its potential for offline transactions.
Cheers,
Gandlaf
-
 @ a95c6243:d345522c
2025-03-04 09:40:50
@ a95c6243:d345522c
2025-03-04 09:40:50Die «Eliten» führen bereits groß angelegte Pilotprojekte für eine Zukunft durch, die sie wollen und wir nicht. Das schreibt der OffGuardian in einem Update zum Thema «EU-Brieftasche für die digitale Identität». Das Portal weist darauf hin, dass die Akteure dabei nicht gerade zimperlich vorgehen und auch keinen Hehl aus ihren Absichten machen. Transition News hat mehrfach darüber berichtet, zuletzt hier und hier.
Mit der EU Digital Identity Wallet (EUDI-Brieftasche) sei eine einzige von der Regierung herausgegebene App geplant, die Ihre medizinischen Daten, Beschäftigungsdaten, Reisedaten, Bildungsdaten, Impfdaten, Steuerdaten, Finanzdaten sowie (potenziell) Kopien Ihrer Unterschrift, Fingerabdrücke, Gesichtsscans, Stimmproben und DNA enthält. So fasst der OffGuardian die eindrucksvolle Liste möglicher Einsatzbereiche zusammen.
Auch Dokumente wie der Personalausweis oder der Führerschein können dort in elektronischer Form gespeichert werden. Bis 2026 sind alle EU-Mitgliedstaaten dazu verpflichtet, Ihren Bürgern funktionierende und frei verfügbare digitale «Brieftaschen» bereitzustellen.
Die Menschen würden diese App nutzen, so das Portal, um Zahlungen vorzunehmen, Kredite zu beantragen, ihre Steuern zu zahlen, ihre Rezepte abzuholen, internationale Grenzen zu überschreiten, Unternehmen zu gründen, Arzttermine zu buchen, sich um Stellen zu bewerben und sogar digitale Verträge online zu unterzeichnen.
All diese Daten würden auf ihrem Mobiltelefon gespeichert und mit den Regierungen von neunzehn Ländern (plus der Ukraine) sowie über 140 anderen öffentlichen und privaten Partnern ausgetauscht. Von der Deutschen Bank über das ukrainische Ministerium für digitalen Fortschritt bis hin zu Samsung Europe. Unternehmen und Behörden würden auf diese Daten im Backend zugreifen, um «automatisierte Hintergrundprüfungen» durchzuführen.
Der Bundesverband der Verbraucherzentralen und Verbraucherverbände (VZBV) habe Bedenken geäußert, dass eine solche App «Risiken für den Schutz der Privatsphäre und der Daten» berge, berichtet das Portal. Die einzige Antwort darauf laute: «Richtig, genau dafür ist sie ja da!»
Das alles sei keine Hypothese, betont der OffGuardian. Es sei vielmehr «Potential». Damit ist ein EU-Projekt gemeint, in dessen Rahmen Dutzende öffentliche und private Einrichtungen zusammenarbeiten, «um eine einheitliche Vision der digitalen Identität für die Bürger der europäischen Länder zu definieren». Dies ist nur eines der groß angelegten Pilotprojekte, mit denen Prototypen und Anwendungsfälle für die EUDI-Wallet getestet werden. Es gibt noch mindestens drei weitere.
Den Ball der digitalen ID-Systeme habe die Covid-«Pandemie» über die «Impfpässe» ins Rollen gebracht. Seitdem habe das Thema an Schwung verloren. Je näher wir aber der vollständigen Einführung der EUid kämen, desto mehr Propaganda der Art «Warum wir eine digitale Brieftasche brauchen» könnten wir in den Mainstream-Medien erwarten, prognostiziert der OffGuardian. Vielleicht müssten wir schon nach dem nächsten großen «Grund», dem nächsten «katastrophalen katalytischen Ereignis» Ausschau halten. Vermutlich gebe es bereits Pläne, warum die Menschen plötzlich eine digitale ID-Brieftasche brauchen würden.
Die Entwicklung geht jedenfalls stetig weiter in genau diese Richtung. Beispielsweise hat Jordanien angekündigt, die digitale biometrische ID bei den nächsten Wahlen zur Verifizierung der Wähler einzuführen. Man wolle «den Papierkrieg beenden und sicherstellen, dass die gesamte Kette bis zu den nächsten Parlamentswahlen digitalisiert wird», heißt es. Absehbar ist, dass dabei einige Wahlberechtigte «auf der Strecke bleiben» werden, wie im Fall von Albanien geschehen.
Derweil würden die Briten gerne ihre Privatsphäre gegen Effizienz eintauschen, behauptet Tony Blair. Der Ex-Premier drängte kürzlich erneut auf digitale Identitäten und Gesichtserkennung. Blair ist Gründer einer Denkfabrik für globalen Wandel, Anhänger globalistischer Technokratie und «moderner Infrastruktur».
Abschließend warnt der OffGuardian vor der Illusion, Trump und Musk würden den US-Bürgern «diesen Schlamassel ersparen». Das Department of Government Efficiency werde sich auf die digitale Identität stürzen. Was könne schließlich «effizienter» sein als eine einzige App, die für alles verwendet wird? Der Unterschied bestehe nur darin, dass die US-Version vielleicht eher privat als öffentlich sei – sofern es da überhaupt noch einen wirklichen Unterschied gebe.
[Titelbild: Screenshot OffGuardian]
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a95c6243:d345522c
2025-03-01 10:39:35
@ a95c6243:d345522c
2025-03-01 10:39:35Ständige Lügen und Unterstellungen, permanent falsche Fürsorge \ können Bausteine von emotionaler Manipulation sein. Mit dem Zweck, \ Macht und Kontrolle über eine andere Person auszuüben. \ Apotheken Umschau
Irgendetwas muss passiert sein: «Gaslighting» ist gerade Thema in vielen Medien. Heute bin ich nach längerer Zeit mal wieder über dieses Stichwort gestolpert. Das war in einem Artikel von Norbert Häring über Manipulationen des Deutschen Wetterdienstes (DWD). In diesem Fall ging es um eine Pressemitteilung vom Donnerstag zum «viel zu warmen» Winter 2024/25.
Häring wirft der Behörde vor, dreist zu lügen und Dinge auszulassen, um die Klimaangst wach zu halten. Was der Leser beim DWD nicht erfahre, sei, dass dieser Winter kälter als die drei vorangegangenen und kälter als der Durchschnitt der letzten zehn Jahre gewesen sei. Stattdessen werde der falsche Eindruck vermittelt, es würde ungebremst immer wärmer.
Wem also der zu Ende gehende Winter eher kalt vorgekommen sein sollte, mit dessen Empfinden stimme wohl etwas nicht. Das jedenfalls wolle der DWD uns einreden, so der Wirtschaftsjournalist. Und damit sind wir beim Thema Gaslighting.
Als Gaslighting wird eine Form psychischer Manipulation bezeichnet, mit der die Opfer desorientiert und zutiefst verunsichert werden, indem ihre eigene Wahrnehmung als falsch bezeichnet wird. Der Prozess führt zu Angst und Realitätsverzerrung sowie zur Zerstörung des Selbstbewusstseins. Die Bezeichnung kommt von dem britischen Theaterstück «Gas Light» aus dem Jahr 1938, in dem ein Mann mit grausamen Psychotricks seine Frau in den Wahnsinn treibt.
Damit Gaslighting funktioniert, muss das Opfer dem Täter vertrauen. Oft wird solcher Psychoterror daher im privaten oder familiären Umfeld beschrieben, ebenso wie am Arbeitsplatz. Jedoch eignen sich die Prinzipien auch perfekt zur Manipulation der Massen. Vermeintliche Autoritäten wie Ärzte und Wissenschaftler, oder «der fürsorgliche Staat» und Institutionen wie die UNO oder die WHO wollen uns doch nichts Böses. Auch Staatsmedien, Faktenchecker und diverse NGOs wurden zu «vertrauenswürdigen Quellen» erklärt. Das hat seine Wirkung.
Warum das Thema Gaslighting derzeit scheinbar so populär ist, vermag ich nicht zu sagen. Es sind aber gerade in den letzten Tagen und Wochen auffällig viele Artikel dazu erschienen, und zwar nicht nur von Psychologen. Die Frankfurter Rundschau hat gleich mehrere publiziert, und Anwälte interessieren sich dafür offenbar genauso wie Apotheker.
Die Apotheken Umschau machte sogar auf «Medical Gaslighting» aufmerksam. Davon spreche man, wenn Mediziner Symptome nicht ernst nähmen oder wenn ein gesundheitliches Problem vom behandelnden Arzt «schnöde heruntergespielt» oder abgetan würde. Kommt Ihnen das auch irgendwie bekannt vor? Der Begriff sei allerdings irreführend, da er eine manipulierende Absicht unterstellt, die «nicht gewährleistet» sei.
Apropos Gaslighting: Die noch amtierende deutsche Bundesregierung meldete heute, es gelte, «weiter [sic!] gemeinsam daran zu arbeiten, einen gerechten und dauerhaften Frieden für die Ukraine zu erreichen». Die Ukraine, wo sich am Montag «der völkerrechtswidrige Angriffskrieg zum dritten Mal jährte», verteidige ihr Land und «unsere gemeinsamen Werte».
Merken Sie etwas? Das Demokratieverständnis mag ja tatsächlich inzwischen in beiden Ländern ähnlich traurig sein. Bezüglich Friedensbemühungen ist meine Wahrnehmung jedoch eine andere. Das muss an meinem Gedächtnis liegen.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 3eba5ef4:751f23ae
2025-04-25 02:00:02
@ 3eba5ef4:751f23ae
2025-04-25 02:00:02Crypto Insights
1 BTC Quantum Cracking Challenge Called a Joke
Quantum computing research organization Project Eleven launched “Q-Day Challenge,” announcing a 1 BTC reward to the first team that can crack an ECC (elliptic curve cryptography) key using Shor’s algorithm on a quantum computer before April 5, 2026. Project Eleven considers this an extremely difficult task, stating that even recovering a few private keys would be big news.
However, Shinobi from Bitcoin Magazine called the bounty a joke, arguing it provides no serious incentive for several reasons:
- Even highly optimistic forecasts place the feasibility of such a quantum breakthrough at least 5–10 years away.
- At Bitcoin’s current price of $80,000, the bounty is insufficient compensation for such a demanding task.
- A quantum computer could be used for much more lucrative exploits—eavesdropping on internet connections regardless of TLS, breaking encrypted private communications, or compromising the certificate authority hierarchy of the DNS system.
New BIP Proposal to Redefine Bitcoin’s Smallest Unit
A new BIP draft proposes redefining the term “Bitcoin” to refer to the smallest indivisible unit in the system—currently “sat” (Satoshi). The goal is to make transaction amounts more readable and reduce user error. For example, someone with 851 sats would simply see “851 bitcoin” instead of “0.00000851 BTC.” Only the display and interpretation of amounts would change—the protocol remains untouched.
Previously, BIP 176 attempted to improve readability by introducing “bits” (100 sats), but it introduced a new denomination users had to learn and switch between.
Sparse Bitcoin Block Contains Only 7 Transactions
Bitcoin transaction activity has slumped to its lowest in over two years. Recently, top mining pool Foundry mined a sparse block—Block 890466—containing only 7 transactions and weighing 5,369 weight units.

The last time a block was sparser was in January 2023, when Binance Pool mined Block 769895, which included just 4 transactions and weighed 4,370 weight units.
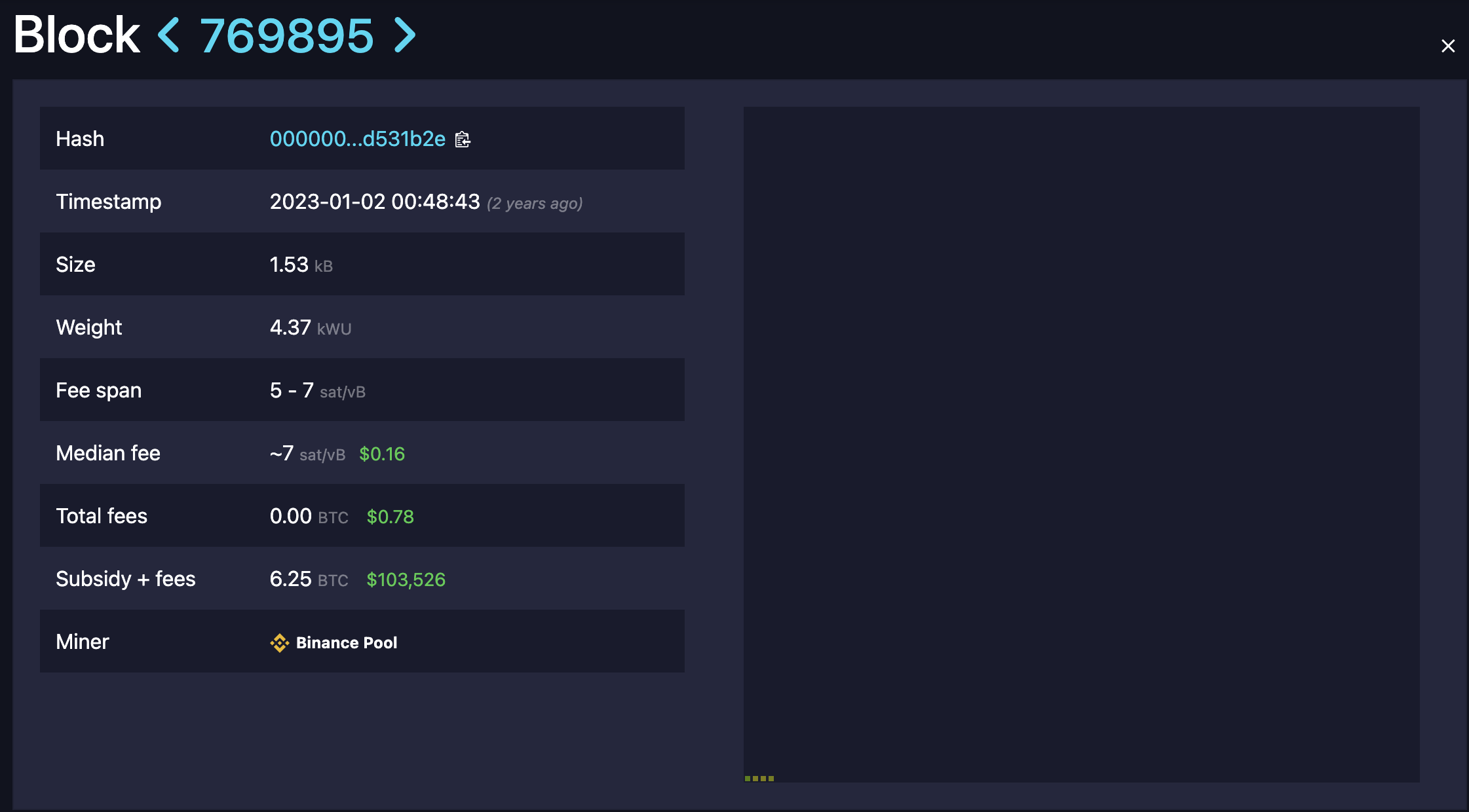
Over 95% of Bitcoin Blocks Mined by Just 6 Pools
A recent investigation by b10c analyzed the hash rate shares of Bitcoin’s five largest mining pools to examine centralization trends in 2025. Part one looked at mining pool information in coinbase transactions. Part two considered the assumed potential proxy pools. Both parts revealed a high concentration of mining activity. The conclusion: over 95% of recent blocks were mined by just six pools.
Bitcoin Hashrate Projections Through 2027
Valentin Rousseau in collaboration with Blockspace published hashrate forecast, covering:
- Hashrate forecasts for 2025, 2026, and 2027
- How current Bitcoin mining economics may influence the hashrate trajectory
- Hashrate expansion schedules for public miners, plus probability of completion
- Sensitivity tables for hashrate growth under various Bitcoin prices
Using VLS for Non-Custodial Lightning Integration
VLS (Validating Lightning Signer) is a library and reference implementation for a signer module to secure Lightning nodes. It separates Lightning private keys and security rule validation from the node, moving them to a dedicated signing device, thereby reducing the attack surface and enhancing security.
Before VLS, it was nearly impossible to securely manage Lightning private keys in a hosted environment without taking custody of user funds. Blockstream’s Greenlight demonstrates in this case study how VLS enables developers to seamlessly integrate non-custodial Lightning payments into their apps, with minimal overhead, while ensuring users retain full control of their funds.
How CTV+CSFS improves BitVM bridges
Robin Linus elaborates on how input-committing covenants can be used to build more efficient and secure bridges in the BitVM ecosystem. By using CTV (CHECKTEMPLATEVERIFY) and CSFS (CHECKSIGFROMSTACK), the need for presigning committees is eliminated and transaction size is significantly reduced. This simplifies bridge architecture, enhances operational efficiency, and aims towards trust-minimized Bitcoin interoperability, though challenges such as potential censorship in the peg-in process remain.
RISC Zero Launches R0VM 2.0 with Performance and Security Gains
RISC Zero introduced R0VM 2.0, a major upgrade to its zkVM focused on performance and scalability. Enhancements include:
- Ethereum block validation and execution time cut from 35 minutes to 44 seconds;
- Validity proof costs reduced 5x, with batch sizes of 25 bringing per-block costs down from $1.355 to $0.2747; for larger batches, as low as $0.0012.
On the security side, formal verification is a key focus of R0VM 2.0. The Keccak circuit’s determinism has been fully verified, and 122 of the 123 components in the v2 RISC-V core circuit have also been confirmed deterministic.
Bitcoin Soft Forks Could Improve BitVMX
BitVMX is a platform for optimistic verification of Bitcoin smart contracts. In this article, Fairgate Labs outlines various potential Bitcoin upgrades and how they could benefit BitVMX. The article argues that new opcodes introduced via soft forks could improve efficiency, reduce on-chain costs, simplify scripting, and promote decentralization.
Ethereum Execution Layer to Replace EVM with RISC-V
Vitalik announced a long-term proposal to replace the EVM in Ethereum’s execution layer with RISC-V as the virtual machine for smart contracts. This aims to significantly improve execution efficiency and address key scalability bottlenecks, while also simplifying the execution layer.
Additionally, Cardano’s Charles Hoskinson mentioned that their project is also using RISC-V in BitVMX, stating: “RISC-V is the future.”
Top Reads on Blockchains and Beyond
Viewing a Clown World Through Bitcoin: Responsibility, Freedom, and Self-Reflection
The book Bitcoin: The Inverse of Clown World critiques a modern society filled with “clowns”—obsessed with false political narratives and meaningless social issues, such as excessive focus on “political correctness” and climate change. The author argues that the root of absurdity is a lack of personal responsibility, and that when money breaks down, everything becomes political theater.
Beyond exposing and criticizing these absurdities, the book promotes Bitcoin as a means to succeed by providing value. It emphasizes the importance of protecting one’s time and mind in an era of information overload and encourages readers to reflect on their lifestyles and contribute to making a better world—with Bitcoin as a foundation for that change.
The book review by Bitcoin Magazine.
GPU Proof-of-Work: Redefining Energy, Computation, and Money in the AI Age
The author envisions a future where GPU-based Proof-of-Work (GPU PoW) plays a pivotal role in an AI-driven world. GPU PoW can secure cryptocurrencies, train AI models, balance energy loads, and help build a global compute marketplace. Unlike ASICs, which are limited to mining, GPUs are versatile and can dynamically shift workloads for optimal economic return.
By coordinating local data centers, superclusters, and middleware, GPU PoW can improve energy and compute efficiency without sacrificing decentralization. This gives rise to a new utility-based economic system. PoW is no longer just about mining—it becomes infrastructure supporting the convergence of AI, energy systems, and monetary networks.
DahLIAS:First Cryptographic Protocol for Fully Cross-Input Signature Aggregation Compatible with Secp256k1
Blockstream’s research team has introduced DahLIAS, the first cryptographic protocol that enables full cross-input signature aggregation, while remaining compatible with Bitcoin's existing secp256k1 elliptic curve.
An interactive aggregate signature scheme allows n signers—each with their own (sk, pk) key pair and message m—to jointly produce a short signature that proves each m was signed under its corresponding pk. While such schemes can offer massive space and verification savings—two critical bottlenecks for blockchain like Bitcoin—aggregate signatures have received less attention compared to other multisig schemes like MuSig2 or FROST.
DahLIAS is the first such scheme built on discrete logarithms in pairing-free groups, with constant-size signatures that look just like standard Schnorr signatures. DahLIAS also addresses real-world use cases. In addition to its savings in space and time, it supports key tweaking—a common Bitcoin technique used in hierarchical deterministic wallets to derive keys and enhance on-chain privacy.
Read the full paper.
Thunderbolt: A Formally Verified Protocol for Off-Chain Bitcoin Transfers
Bitcoin Thunderbolt is a novel off-chain protocol for asynchronous, secure transfer of Bitcoin UTXOs between uncoordinated users. Unlike prior solutions such as payment channels or the Lightning Network, Bitcoin Thunderbolt requires no prior trust, direct interaction, or continuous connectivity between sender and receiver.
At its core, Bitcoin Thunderbolt employs a Byzantine fault-tolerant committee to manage threshold Schnorr signatures, enabling secure ownership delegation and on-chain finalization.
Read the full paper.
-
 @ a95c6243:d345522c
2025-02-21 19:32:23
@ a95c6243:d345522c
2025-02-21 19:32:23Europa – das Ganze ist eine wunderbare Idee, \ aber das war der Kommunismus auch. \ Loriot
«Europa hat fertig», könnte man unken, und das wäre nicht einmal sehr verwegen. Mit solch einer Einschätzung stünden wir nicht alleine, denn die Stimmen in diese Richtung mehren sich. Der französische Präsident Emmanuel Macron warnte schon letztes Jahr davor, dass «unser Europa sterben könnte». Vermutlich hatte er dabei andere Gefahren im Kopf als jetzt der ungarische Ministerpräsident Viktor Orbán, der ein «baldiges Ende der EU» prognostizierte. Das Ergebnis könnte allerdings das gleiche sein.
Neben vordergründigen Themenbereichen wie Wirtschaft, Energie und Sicherheit ist das eigentliche Problem jedoch die obskure Mischung aus aufgegebener Souveränität und geschwollener Arroganz, mit der europäische Politiker:innende unterschiedlicher Couleur aufzutreten pflegen. Und das Tüpfelchen auf dem i ist die bröckelnde Legitimation politischer Institutionen dadurch, dass die Stimmen großer Teile der Bevölkerung seit Jahren auf vielfältige Weise ausgegrenzt werden.
Um «UnsereDemokratie» steht es schlecht. Dass seine Mandate immer schwächer werden, merkt natürlich auch unser «Führungspersonal». Entsprechend werden die Maßnahmen zur Gängelung, Überwachung und Manipulation der Bürger ständig verzweifelter. Parallel dazu plustern sich in Paris Macron, Scholz und einige andere noch einmal mächtig in Sachen Verteidigung und «Kriegstüchtigkeit» auf.
Momentan gilt es auch, das Überschwappen covidiotischer und verschwörungsideologischer Auswüchse aus den USA nach Europa zu vermeiden. So ein «MEGA» (Make Europe Great Again) können wir hier nicht gebrauchen. Aus den Vereinigten Staaten kommen nämlich furchtbare Nachrichten. Beispielsweise wurde einer der schärfsten Kritiker der Corona-Maßnahmen kürzlich zum Gesundheitsminister ernannt. Dieser setzt sich jetzt für eine Neubewertung der mRNA-«Impfstoffe» ein, was durchaus zu einem Entzug der Zulassungen führen könnte.
Der europäischen Version von «Verteidigung der Demokratie» setzte der US-Vizepräsident J. D. Vance auf der Münchner Sicherheitskonferenz sein Verständnis entgegen: «Demokratie stärken, indem wir unseren Bürgern erlauben, ihre Meinung zu sagen». Das Abschalten von Medien, das Annullieren von Wahlen oder das Ausschließen von Menschen vom politischen Prozess schütze gar nichts. Vielmehr sei dies der todsichere Weg, die Demokratie zu zerstören.
In der Schweiz kamen seine Worte deutlich besser an als in den meisten europäischen NATO-Ländern. Bundespräsidentin Karin Keller-Sutter lobte die Rede und interpretierte sie als «Plädoyer für die direkte Demokratie». Möglicherweise zeichne sich hier eine außenpolitische Kehrtwende in Richtung integraler Neutralität ab, meint mein Kollege Daniel Funk. Das wären doch endlich mal ein paar gute Nachrichten.
Von der einstigen Idee einer europäischen Union mit engeren Beziehungen zwischen den Staaten, um Konflikte zu vermeiden und das Wohlergehen der Bürger zu verbessern, sind wir meilenweit abgekommen. Der heutige korrupte Verbund unter technokratischer Leitung ähnelt mehr einem Selbstbedienungsladen mit sehr begrenztem Zugang. Die EU-Wahlen im letzten Sommer haben daran ebenso wenig geändert, wie die Bundestagswahl am kommenden Sonntag darauf einen Einfluss haben wird.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 3eba5ef4:751f23ae
2025-04-25 01:56:19
@ 3eba5ef4:751f23ae
2025-04-25 01:56:19加密洞见
悬赏 1 BTC 的量子计算破解密钥挑战,被认为是个笑话
量子计算研究机构 Project Eleven 发布 Q-Day 挑战,宣布对能够于 2026 年 4 月 5 日之前、在量子计算机上使用 Shor 算法破解椭圆曲线加密(ECC)密钥的第一支团队提供 1 BTC 的奖励。Project Eleven 认为这将是一项极其艰巨的任务,即使获得几位私钥也将是一个大新闻。
而 Bitcoin Magazine 的长期贡献者 Shinobi 认为该笔赏金是一个笑话,并没有提供任何严肃的激励,原因有:
- 即使是对量子计算进展的高度乐观预测,也将实际实现这一目标的时间表定为 5-10 年;
- 按照目前单个比特币 80,000 美元的市价来看,奖励对于这项困难的工作其实并不多;
- 一台量子计算机可以完成比价值 80,000 美元更有价值的事,如窃听互联网连接、破解私人信息应用程序、破解整个 DNS 系统的证书颁发机构层次结构等。
重新定义比特币的基本单位的新 BIP
这份 BIP 草案建议重新定义「比特币」一词,以指代系统中最小的不可分割单位,即目前所说的「聪」(sat),目的是让交易看起来更清晰易读,可以有效降低了用户出错风险。如果某人有 851 个聪,钱包只显示 851 个比特币,而不是 0.00000851 BTC。变化的只有显示和解释金额的方式,而协议不变。
在这项提案之前,已经有提案(BIP 176)试图通过引入代表 100 聪的「比特」(bits)来使比特币数位的显示更加友好。虽然这减少了小数位的数量,但它引入了一种新的面额,用户必须学习并在其之间切换。
比特币交易活跃度低迷,稀疏区块仅包含 7 笔交易
比特币交易活动处于 2 年多来的最低水平,导致最大的矿池 Foundry 近期挖掘出一个稀疏的非空区块:Block 890466 仅包含 7 笔交易,重量为 5369 个单位。

上一个低于此的稀疏区块是 Binance Pool 在 2023 年 1 月挖出的区块 769895。内存池同样是空的,仅包含 4 笔交易,重量为 4370 个单位。

当前比特币挖矿高度集中:超过 95% 的区块仅由 6 个矿池开采
这篇由 b10c 发表的调查检查了当前五个最大的比特币矿池的哈希率份额,探讨 2025 年比特币挖矿中心化问题。第一部分着眼于 coinbase 交易中包含的矿池信息。第二部分考虑了假定的代理池。这两部分都显示了当前最大的矿池和挖矿集中化指数。调查结论:当下的比特币挖矿高度集中,有 6 个矿池开采了超过 95% 的区块。
预测到 2027 年的比特币哈希率
Valentin Rousseau 与 Blockspace 合作撰写了这份报告,涵盖: * 2025 年、2026 年和 2027 年的哈希率预测 * 当前的比特币挖矿经济学将如何影响哈希率的轨迹 * 公共矿工的哈希率扩展时间表,以及完成概率 * 不同比特币价格下哈希率增长的敏感度表
使用 VLS 支持非托管的闪电集成
VLS(Validating Lightning Signer)是签名者模块的库和参考实现,用于保护闪电节点,将 闪电私钥和安全规则验证从闪电节点分离到一个单独的签名设备中,通过减少攻击面来增强安全性。
在 VLS 之前,在不保管用户资金的情况下,在托管环境中安全地管理闪电私钥几乎是不可能的。Blockstream 的 Greenlight 在这份案例研究中介绍了如何使用 VLS,以非托管的方式使开发人员能够以最小的开销将闪电的功能添加到他们的应用程序中,同时确保用户保留对他们资金的完全控制权。Greenlight 构建在 Core Lightning 的模块化架构上,将由 Blockstream 管理的闪电节点操作与掌握在用户手中的闪电交易签名分开。
CTV+CSFS 如何改进 BitVM 网桥
Robin Linus 阐述了如何使用「输入提交契约」(input-committing covenants)在 BitVM 生态系统中构建更高效、更安全的桥,利用 CTV(CHECKTEMPLATEVERIFY)和 CSFS (CHECKSIGFROMSTACK) 消除对预签名委员会的需求并显着减少交易规模。这一进步简化了桥架构,提高了运营效率,并旨在实现信任最小化的比特币互作性,尽管仍然存在诸如挂钩过程中的潜在审查等挑战。
RISC Zero 推出 R0VM 2.0,性能提升的同时确保安全性
RISC Zero 推出了 R0VM 2.0,重大改进包括: * 以太坊区块的验证和执行时间,从 35 分钟缩短到仅 44 秒; * 到有效性证明的成本降低了 5 倍,批量大小为 25 的每个区块交易成本从 1.355 USD 下降到 0.2747 USD;较大批次交易成本低至 0.0012 USD;
在安全性方面,形式化验证是 R0VM 2.0 的核心。目前已经验证 Keccak 电路的完全确定性,以及在其 v2 电路中,核心 RISC-V 功能的 123 个组件中有 122 个是确定性的。
比特币软分叉可以改进 BitVMX
BitVMX 是支持乐观验证比特币智能合约的平台。Fairgate Labs 在本文中介绍了比特币可能经历的不同类型的升级,以及它们如何对 BitVMX 产生积极影响,认为了新的 opcodes 如果被软分叉到比特币中,可以提高 BitVMX 的效率、降低链上成本、简化脚本,并变得更加去中心化。
以太坊执行层将用 RISC-V 替代 EVM
Vitalik 发布了长期 L1 执行提案,宣布以太坊执行层将用 RISC-V 替换 EVM 作为编写智能合约的虚拟机,以大幅提高以太坊执行层的效率 ,解决主要的扩展瓶颈之一,同时增强执行层的简单性。
此外,Cardano 的 Charles Hoskinson 也表示 Cardano 在 BitVMX 中使用了 RISC-V;RISC-V 就是未来。
精彩无限,不止于链
从比特币看荒诞的世界:责任、自由与自我反思
《Bitcoin: The Inverse of Clown World》(比特币:荒诞世界的逆转)一书批判了充满「小丑」的当代世界——被虚假的政治议题和无意义的社会关注所占据——比如对「政治正确」和气候变化的过度关注。作者认为荒谬的核心是人们不负责任的行为,并认为当货币失效时,一切都变成政治和闹剧。
除了揭示和批评诸多荒诞现象,作者指出比特币倡导通过提供价值来获得成功,并强调了个人在这个信息过载的时代保护自己的时间和思想的重要性,进一步鼓励读者在比特币的支持下,重新审视自己的生活方式,并为改变世界贡献力量。
这里是 Bitcoin Magazine 对该书的书评。
GPU 工作量证明:重新定义 AI 驱动时代的能源、计算和金钱
作者设想了以 GPU 为基础的工作量证明(GPU PoW)在 AI 驱动的未来中的潜力。GPU PoW 不仅可以用于加密货币的安全保障,还能参与 AI 模型训练、能源负载调节以及全球算力市场的构建,相较于传统只能挖矿的 ASIC,GPU 更通用灵活,并能动态分配任务,在不同场景下实现收益最大化。通过本地数据中心、超级集群与中间件协同运作,GPU PoW 可以在不牺牲去中心化的前提下,提升能源与计算资源的使用效率,并创造以实用性为基础的新型经济体系。PoW 不再只是挖矿,而是成为支撑 AI、能源系统与货币市场协同发展的基础设施。
DahLIAS:首个用于完全交叉输入签名聚合的加密协议,允许重用比特币的曲线 secp256k1
Blockstream 研究团队推出 DahLIAS——第一个用于完全交叉输入签名聚合的加密协议,允许重用比特币的曲线 secp256k1。
一个交互式聚合签名(interactive aggregate signatures)方案允许 n 个签名者,每人拥有自己的秘密/公钥对(sk, pk)和消息 m,共同生成一个简短的签名,同时证明每个 m 在 pk 下已经被签名,其中 i ∈ {1, . . . , n}。尽管在空间和验证时间方面具有巨大的节省潜力,这两个因素是像比特币这样的区块链系统的主要瓶颈。但聚合签名相比于多方签名家族中的其他成员(例如 MuSig2 多重签名和 FROST 阈值签名)受到的关注较少。
而 DahLIAS 是首个直接在无配对组(pairing-free groups)中的离散对数上构建的、具有常数大小签名的聚合签名方案——与标准的 Schnorr 签名具有相同形态。DahLIAS 的签名协议由两轮组成,第一轮可以在没有消息的情况下预处理,且验证某个由 n 个签名者创建的签名,是由一个大小为 n + 1 的多重指数运算主导,这在渐近意义上比批量验证 n 个独立的 Schnorr 签名要快两倍。
DahLIAS 也考虑到了现实中的应用。除了前述的空间节省和验证速度提升外,DahLIAS 还提供了密钥调整功能,这是一种常用于比特币的技术——从有层级的确定性钱包中派生密钥,以节省空间并增强链上隐私。研究团队在随机预言模型下,基于(代数的)再一次离散对数假设,证明了包含密钥调整功能的 DahLIAS 在并发设置下的安全性。
查看完整论文。
Thunderbolt: 经过验证的链下比特币转账协议
该 Bitcoin Thunderbolt 链下协议用于在未协调的用户之间安全、异步地转移比特币 UTXO。与支付通道或闪电网络等现有解决方案不同,该协议无需预先信任、直接交互或持续连接发送方和接收方。其核心是通过拜占庭容错 committee 来管理阈值 Schnorr 签名,实现安全的所有权委托和链上最终确认。
查看完整论文。
-
 @ e3ba5e1a:5e433365
2025-04-15 11:03:15
@ e3ba5e1a:5e433365
2025-04-15 11:03:15Prelude
I wrote this post differently than any of my others. It started with a discussion with AI on an OPSec-inspired review of separation of powers, and evolved into quite an exciting debate! I asked Grok to write up a summary in my overall writing style, which it got pretty well. I've decided to post it exactly as-is. Ultimately, I think there are two solid ideas driving my stance here:
- Perfect is the enemy of the good
- Failure is the crucible of success
Beyond that, just some hard-core belief in freedom, separation of powers, and operating from self-interest.
Intro
Alright, buckle up. I’ve been chewing on this idea for a while, and it’s time to spit it out. Let’s look at the U.S. government like I’d look at a codebase under a cybersecurity audit—OPSEC style, no fluff. Forget the endless debates about what politicians should do. That’s noise. I want to talk about what they can do, the raw powers baked into the system, and why we should stop pretending those powers are sacred. If there’s a hole, either patch it or exploit it. No half-measures. And yeah, I’m okay if the whole thing crashes a bit—failure’s a feature, not a bug.
The Filibuster: A Security Rule with No Teeth
You ever see a firewall rule that’s more theater than protection? That’s the Senate filibuster. Everyone acts like it’s this untouchable guardian of democracy, but here’s the deal: a simple majority can torch it any day. It’s not a law; it’s a Senate preference, like choosing tabs over spaces. When people call killing it the “nuclear option,” I roll my eyes. Nuclear? It’s a button labeled “press me.” If a party wants it gone, they’ll do it. So why the dance?
I say stop playing games. Get rid of the filibuster. If you’re one of those folks who thinks it’s the only thing saving us from tyranny, fine—push for a constitutional amendment to lock it in. That’s a real patch, not a Post-it note. Until then, it’s just a vulnerability begging to be exploited. Every time a party threatens to nuke it, they’re admitting it’s not essential. So let’s stop pretending and move on.
Supreme Court Packing: Because Nine’s Just a Number
Here’s another fun one: the Supreme Court. Nine justices, right? Sounds official. Except it’s not. The Constitution doesn’t say nine—it’s silent on the number. Congress could pass a law tomorrow to make it 15, 20, or 42 (hitchhiker’s reference, anyone?). Packing the court is always on the table, and both sides know it. It’s like a root exploit just sitting there, waiting for someone to log in.
So why not call the bluff? If you’re in power—say, Trump’s back in the game—say, “I’m packing the court unless we amend the Constitution to fix it at nine.” Force the issue. No more shadowboxing. And honestly? The court’s got way too much power anyway. It’s not supposed to be a super-legislature, but here we are, with justices’ ideologies driving the bus. That’s a bug, not a feature. If the court weren’t such a kingmaker, packing it wouldn’t even matter. Maybe we should be talking about clipping its wings instead of just its size.
The Executive Should Go Full Klingon
Let’s talk presidents. I’m not saying they should wear Klingon armor and start shouting “Qapla’!”—though, let’s be real, that’d be awesome. I’m saying the executive should use every scrap of power the Constitution hands them. Enforce the laws you agree with, sideline the ones you don’t. If Congress doesn’t like it, they’ve got tools: pass new laws, override vetoes, or—here’s the big one—cut the budget. That’s not chaos; that’s the system working as designed.
Right now, the real problem isn’t the president overreaching; it’s the bureaucracy. It’s like a daemon running in the background, eating CPU and ignoring the user. The president’s supposed to be the one steering, but the administrative state’s got its own agenda. Let the executive flex, push the limits, and force Congress to check it. Norms? Pfft. The Constitution’s the spec sheet—stick to it.
Let the System Crash
Here’s where I get a little spicy: I’m totally fine if the government grinds to a halt. Deadlock isn’t a disaster; it’s a feature. If the branches can’t agree, let the president veto, let Congress starve the budget, let enforcement stall. Don’t tell me about “essential services.” Nothing’s so critical it can’t take a breather. Shutdowns force everyone to the table—debate, compromise, or expose who’s dropping the ball. If the public loses trust? Good. They’ll vote out the clowns or live with the circus they elected.
Think of it like a server crash. Sometimes you need a hard reboot to clear the cruft. If voters keep picking the same bad admins, well, the country gets what it deserves. Failure’s the best teacher—way better than limping along on autopilot.
States Are the Real MVPs
If the feds fumble, states step up. Right now, states act like junior devs waiting for the lead engineer to sign off. Why? Federal money. It’s a leash, and it’s tight. Cut that cash, and states will remember they’re autonomous. Some will shine, others will tank—looking at you, California. And I’m okay with that. Let people flee to better-run states. No bailouts, no excuses. States are like competing startups: the good ones thrive, the bad ones pivot or die.
Could it get uneven? Sure. Some states might turn into sci-fi utopias while others look like a post-apocalyptic vidya game. That’s the point—competition sorts it out. Citizens can move, markets adjust, and failure’s a signal to fix your act.
Chaos Isn’t the Enemy
Yeah, this sounds messy. States ignoring federal law, external threats poking at our seams, maybe even a constitutional crisis. I’m not scared. The Supreme Court’s there to referee interstate fights, and Congress sets the rules for state-to-state play. But if it all falls apart? Still cool. States can sort it without a babysitter—it’ll be ugly, but freedom’s worth it. External enemies? They’ll either unify us or break us. If we can’t rally, we don’t deserve the win.
Centralizing power to avoid this is like rewriting your app in a single thread to prevent race conditions—sure, it’s simpler, but you’re begging for a deadlock. Decentralized chaos lets states experiment, lets people escape, lets markets breathe. States competing to cut regulations to attract businesses? That’s a race to the bottom for red tape, but a race to the top for innovation—workers might gripe, but they’ll push back, and the tension’s healthy. Bring it—let the cage match play out. The Constitution’s checks are enough if we stop coddling the system.
Why This Matters
I’m not pitching a utopia. I’m pitching a stress test. The U.S. isn’t a fragile porcelain doll; it’s a rugged piece of hardware built to take some hits. Let it fail a little—filibuster, court, feds, whatever. Patch the holes with amendments if you want, or lean into the grind. Either way, stop fearing the crash. It’s how we debug the republic.
So, what’s your take? Ready to let the system rumble, or got a better way to secure the code? Hit me up—I’m all ears.
-
 @ a95c6243:d345522c
2025-02-19 09:23:17
@ a95c6243:d345522c
2025-02-19 09:23:17Die «moralische Weltordnung» – eine Art Astrologie. Friedrich Nietzsche
Das Treffen der BRICS-Staaten beim Gipfel im russischen Kasan war sicher nicht irgendein politisches Event. Gastgeber Wladimir Putin habe «Hof gehalten», sagen die Einen, China und Russland hätten ihre Vorstellung einer multipolaren Weltordnung zelebriert, schreiben Andere.
In jedem Fall zeigt die Anwesenheit von über 30 Delegationen aus der ganzen Welt, dass von einer geostrategischen Isolation Russlands wohl keine Rede sein kann. Darüber hinaus haben sowohl die Anreise von UN-Generalsekretär António Guterres als auch die Meldungen und Dementis bezüglich der Beitrittsbemühungen des NATO-Staats Türkei für etwas Aufsehen gesorgt.
Im Spannungsfeld geopolitischer und wirtschaftlicher Umbrüche zeigt die neue Allianz zunehmendes Selbstbewusstsein. In Sachen gemeinsamer Finanzpolitik schmiedet man interessante Pläne. Größere Unabhängigkeit von der US-dominierten Finanzordnung ist dabei ein wichtiges Ziel.
Beim BRICS-Wirtschaftsforum in Moskau, wenige Tage vor dem Gipfel, zählte ein nachhaltiges System für Finanzabrechnungen und Zahlungsdienste zu den vorrangigen Themen. Während dieses Treffens ging der russische Staatsfonds eine Partnerschaft mit dem Rechenzentrumsbetreiber BitRiver ein, um Bitcoin-Mining-Anlagen für die BRICS-Länder zu errichten.
Die Initiative könnte ein Schritt sein, Bitcoin und andere Kryptowährungen als Alternativen zu traditionellen Finanzsystemen zu etablieren. Das Projekt könnte dazu führen, dass die BRICS-Staaten den globalen Handel in Bitcoin abwickeln. Vor dem Hintergrund der Diskussionen über eine «BRICS-Währung» wäre dies eine Alternative zu dem ursprünglich angedachten Korb lokaler Währungen und zu goldgedeckten Währungen sowie eine mögliche Ergänzung zum Zahlungssystem BRICS Pay.
Dient der Bitcoin also der Entdollarisierung? Oder droht er inzwischen, zum Gegenstand geopolitischer Machtspielchen zu werden? Angesichts der globalen Vernetzungen ist es oft schwer zu durchschauen, «was eine Show ist und was im Hintergrund von anderen Strippenziehern insgeheim gesteuert wird». Sicher können Strukturen wie Bitcoin auch so genutzt werden, dass sie den Herrschenden dienlich sind. Aber die Grundeigenschaft des dezentralisierten, unzensierbaren Peer-to-Peer Zahlungsnetzwerks ist ihm schließlich nicht zu nehmen.
Wenn es nach der EZB oder dem IWF geht, dann scheint statt Instrumentalisierung momentan eher der Kampf gegen Kryptowährungen angesagt. Jürgen Schaaf, Senior Manager bei der Europäischen Zentralbank, hat jedenfalls dazu aufgerufen, Bitcoin «zu eliminieren». Der Internationale Währungsfonds forderte El Salvador, das Bitcoin 2021 als gesetzliches Zahlungsmittel eingeführt hat, kürzlich zu begrenzenden Maßnahmen gegen das Kryptogeld auf.
Dass die BRICS-Staaten ein freiheitliches Ansinnen im Kopf haben, wenn sie Kryptowährungen ins Spiel bringen, darf indes auch bezweifelt werden. Im Abschlussdokument bekennen sich die Gipfel-Teilnehmer ausdrücklich zur UN, ihren Programmen und ihrer «Agenda 2030». Ernst Wolff nennt das «eine Bankrotterklärung korrupter Politiker, die sich dem digital-finanziellen Komplex zu 100 Prozent unterwerfen».
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 826e9f89:ffc5c759
2025-04-12 21:34:24
@ 826e9f89:ffc5c759
2025-04-12 21:34:24What follows began as snippets of conversations I have been having for years, on and off, here and there. It will likely eventually be collated into a piece I have been meaning to write on “payments” as a whole. I foolishly started writing this piece years ago, not realizing that the topic is gargantuan and for every week I spend writing it I have to add two weeks to my plan. That may or may not ever come to fruition, but in the meantime, Tether announced it was issuing on Taproot Assets and suddenly everybody is interested again. This is as good a catalyst as any to carve out my “stablecoin thesis”, such as it exists, from “payments”, and put it out there for comment and feedback.
In contrast to the “Bitcoiner take” I will shortly revert to, I invite the reader to keep the following potential counterargument in mind, which might variously be termed the “shitcoiner”, “realist”, or “cynical” take, depending on your perspective: that stablecoins have clear product-market-fit. Now, as a venture capitalist and professional thinkboi focusing on companies building on Bitcoin, I obviously think that not only is Bitcoin the best money ever invented and its monetization is pretty much inevitable, but that, furthermore, there is enormous, era-defining long-term potential for a range of industries in which Bitcoin is emerging as superior technology, even aside from its role as money. But in the interest not just of steelmanning but frankly just of honesty, I would grudgingly agree with the following assessment as of the time of writing: the applications of crypto (inclusive of Bitcoin but deliberately wider) that have found product-market-fit today, and that are not speculative bets on future development and adoption, are: Bitcoin as savings technology, mining as a means of monetizing energy production, and stablecoins.
I think there are two typical Bitcoiner objections to stablecoins of significantly greater importance than all others: that you shouldn’t be supporting dollar hegemony, and that you don’t need a blockchain. I will elaborate on each of these, and for the remainder of the post will aim to produce a synthesis of three superficially contrasting (or at least not obviously related) sources of inspiration: these objections, the realisation above that stablecoins just are useful, and some commentary on technical developments in Bitcoin and the broader space that I think inform where things are likely to go. As will become clear as the argument progresses, I actually think the outcome to which I am building up is where things have to go. I think the technical and economic incentives at play make this an inevitability rather than a “choice”, per se. Given my conclusion, which I will hold back for the time being, this is a fantastically good thing, hence I am motivated to write this post at all!
Objection 1: Dollar Hegemony
I list this objection first because there isn’t a huge amount to say about it. It is clearly a normative position, and while I more or less support it personally, I don’t think that it is material to the argument I am going on to make, so I don’t want to force it on the reader. While the case for this objection is probably obvious to this audience (isn’t the point of Bitcoin to destroy central banks, not further empower them?) I should at least offer the steelman that there is a link between this and the realist observation that stablecoins are useful. The reason they are useful is because people prefer the dollar to even shitter local fiat currencies. I don’t think it is particularly fruitful to say that they shouldn’t. They do. Facts don’t care about your feelings. There is a softer bridging argument to be made here too, to the effect that stablecoins warm up their users to the concept of digital bearer (ish) assets, even though these particular assets are significantly scammier than Bitcoin. Again, I am just floating this, not telling the reader they should or shouldn’t buy into it.
All that said, there is one argument I do want to put my own weight behind, rather than just float: stablecoin issuance is a speculative attack on the institution of fractional reserve banking. A “dollar” Alice moves from JPMorgan to Tether embodies two trade-offs from Alice’s perspective: i) a somewhat opaque profile on the credit risk of the asset: the likelihood of JPMorgan ever really defaulting on deposits vs the operator risk of Tether losing full backing and/or being wrench attacked by the Federal Government and rugging its users. These risks are real but are almost entirely political. I’m skeptical it is meaningful to quantify them, but even if it is, I am not the person to try to do it. Also, more transparently to Alice, ii) far superior payment rails (for now, more on this to follow).
However, from the perspective of the fiat banking cartel, fractional reserve leverage has been squeezed. There are just as many notional dollars in circulation, but there the backing has been shifted from levered to unlevered issuers. There are gradations of relevant objections to this: while one might say, Tether’s backing comes from Treasuries, so you are directly funding US debt issuance!, this is a bit silly in the context of what other dollars one might hold. It’s not like JPMorgan is really competing with the Treasury to sell credit into the open market. Optically they are, but this is the core of the fiat scam. Via the guarantees of the Federal Reserve System, JPMorgan can sell as much unbacked credit as it wants knowing full well the difference will be printed whenever this blows up. Short-term Treasuries are also JPMorgan’s most pristine asset safeguarding its equity, so the only real difference is that Tether only holds Treasuries without wishing more leverage into existence. The realization this all builds up to is that, by necessity,
Tether is a fully reserved bank issuing fiduciary media against the only dollar-denominated asset in existence whose value (in dollar terms) can be guaranteed. Furthermore, this media arguably has superior “moneyness” to the obvious competition in the form of US commercial bank deposits by virtue of its payment rails.
That sounds pretty great when you put it that way! Of course, the second sentence immediately leads to the second objection, and lets the argument start to pick up steam …
Objection 2: You Don’t Need a Blockchain
I don’t need to explain this to this audience but to recap as briefly as I can manage: Bitcoin’s value is entirely endogenous. Every aspect of “a blockchain” that, out of context, would be an insanely inefficient or redundant modification of a “database”, in context is geared towards the sole end of enabling the stability of this endogenous value. Historically, there have been two variations of stupidity that follow a failure to grok this: i) “utility tokens”, or blockchains with native tokens for something other than money. I would recommend anybody wanting a deeper dive on the inherent nonsense of a utility token to read Only The Strong Survive, in particular Chapter 2, Crypto Is Not Decentralized, and the subsection, Everything Fights For Liquidity, and/or Green Eggs And Ham, in particular Part II, Decentralized Finance, Technically. ii) “real world assets” or, creating tokens within a blockchain’s data structure that are not intended to have endogenous value but to act as digital quasi-bearer certificates to some or other asset of value exogenous to this system. Stablecoins are in this second category.
RWA tokens definitionally have to have issuers, meaning some entity that, in the real world, custodies or physically manages both the asset and the record-keeping scheme for the asset. “The blockchain” is at best a secondary ledger to outsource ledger updates to public infrastructure such that the issuer itself doesn’t need to bother and can just “check the ledger” whenever operationally relevant. But clearly ownership cannot be enforced in an analogous way to Bitcoin, under both technical and social considerations. Technically, Bitcoin’s endogenous value means that whoever holds the keys to some or other UTXOs functionally is the owner. Somebody else claiming to be the owner is yelling at clouds. Whereas, socially, RWA issuers enter a contract with holders (whether legally or just in terms of a common-sense interpretation of the transaction) such that ownership of the asset issued against is entirely open to dispute. That somebody can point to “ownership” of the token may or may not mean anything substantive with respect to the physical reality of control of the asset, and how the issuer feels about it all.
And so, one wonders, why use a blockchain at all? Why doesn’t the issuer just run its own database (for the sake of argument with some or other signature scheme for verifying and auditing transactions) given it has the final say over issuance and redemption anyway? I hinted at an answer above: issuing on a blockchain outsources this task to public infrastructure. This is where things get interesting. While it is technically true, given the above few paragraphs, that, you don’t need a blockchain for that, you also don’t need to not use a blockchain for that. If you want to, you can.
This is clearly the case given stablecoins exist at all and have gone this route. If one gets too angry about not needing a blockchain for that, one equally risks yelling at clouds! And, in fact, one can make an even stronger argument, more so from the end users’ perspective. These products do not exist in a vacuum but rather compete with alternatives. In the case of stablecoins, the alternative is traditional fiat money, which, as stupid as RWAs on a blockchain are, is even dumber. It actually is just a database, except it’s a database that is extremely annoying to use, basically for political reasons because the industry managing these private databases form a cartel that never needs to innovate or really give a shit about its customers at all. In many, many cases, stablecoins on blockchains are dumb in the abstract, but superior to the alternative methods of holding and transacting in dollars existing in other forms. And note, this is only from Alice’s perspective of wanting to send and receive, not a rehashing of the fractional reserve argument given above. This is the essence of their product-market-fit. Yell at clouds all you like: they just are useful given the alternative usually is not Bitcoin, it’s JPMorgan’s KYC’d-up-the-wazoo 90s-era website, more than likely from an even less solvent bank.
So where does this get us? It might seem like we are back to “product-market-fit, sorry about that” with Bitcoiners yelling about feelings while everybody else makes do with their facts. However, I think we have introduced enough material to move the argument forward by incrementally incorporating the following observations, all of which I will shortly go into in more detail: i) as a consequence of making no technical sense with respect to what blockchains are for, today’s approach won’t scale; ii) as a consequence of short-termist tradeoffs around socializing costs, today’s approach creates an extremely unhealthy and arguably unnatural market dynamic in the issuer space; iii) Taproot Assets now exist and handily address both points i) and ii), and; iv) eCash is making strides that I believe will eventually replace even Taproot Assets.
To tease where all this is going, and to get the reader excited before we dive into much more detail: just as Bitcoin will eat all monetary premia, Lightning will likely eat all settlement, meaning all payments will gravitate towards routing over Lightning regardless of the denomination of the currency at the edges. Fiat payments will gravitate to stablecoins to take advantage of this; stablecoins will gravitate to TA and then to eCash, and all of this will accelerate hyperbitcoinization by “bitcoinizing” payment rails such that an eventual full transition becomes as simple as flicking a switch as to what denomination you want to receive.
I will make two important caveats before diving in that are more easily understood in light of having laid this groundwork: I am open to the idea that it won’t be just Lightning or just Taproot Assets playing the above roles. Without veering into forecasting the entire future development of Bitcoin tech, I will highlight that all that really matters here are, respectively: a true layer 2 with native hashlocks, and a token issuance scheme that enables atomic routing over such a layer 2 (or combination of such). For the sake of argument, the reader is welcome to swap in “Ark” and “RGB” for “Lightning” and “TA” both above and in all that follows. As far as I can tell, this makes no difference to the argument and is even exciting in its own right. However, for the sake of simplicity in presentation, I will stick to “Lightning” and “TA” hereafter.
1) Today’s Approach to Stablecoins Won’t Scale
This is the easiest to tick off and again doesn’t require much explanation to this audience. Blockchains fundamentally don’t scale, which is why Bitcoin’s UTXO scheme is a far better design than ex-Bitcoin Crypto’s’ account-based models, even entirely out of context of all the above criticisms. This is because Bitcoin transactions can be batched across time and across users with combinations of modes of spending restrictions that provide strong economic guarantees of correct eventual net settlement, if not perpetual deferral. One could argue this is a decent (if abstrusely technical) definition of “scaling” that is almost entirely lacking in Crypto.
What we see in ex-Bitcoin crypto is so-called “layer 2s” that are nothing of the sort, forcing stablecoin schemes in these environments into one of two equally poor design choices if usage is ever to increase: fees go higher and higher, to the point of economic unviability (and well past it) as blocks fill up, or move to much more centralized environments that increasingly are just databases, and hence which lose the benefits of openness thought to be gleaned by outsourcing settlement to public infrastructure. This could be in the form of punting issuance to a bullshit “layer 2” that is a really a multisig “backing” a private execution environment (to be decentralized any daw now) or an entirely different blockchain that is just pretending even less not to be a database to begin with. In a nutshell, this is a decent bottom-up explanation as to why Tron has the highest settlement of Tether.
This also gives rise to the weirdness of “gas tokens” - assets whose utility as money is and only is in the form of a transaction fee to transact a different kind of money. These are not quite as stupid as a “utility token,” given at least they are clearly fulfilling a monetary role and hence their artificial scarcity can be justified. But they are frustrating from Bitcoiners’ and users’ perspectives alike: users would prefer to pay transaction fees on dollars in dollars, but they can’t because the value of Ether, Sol, Tron, or whatever, is the string and bubblegum that hold their boondoggles together. And Bitcoiners wish this stuff would just go away and stop distracting people, whereas this string and bubblegum is proving transiently useful.
All in all, today’s approach is fine so long as it isn’t being used much. It has product-market fit, sure, but in the unenviable circumstance that, if it really starts to take off, it will break, and even the original users will find it unusable.
2) Today’s Approach to Stablecoins Creates an Untenable Market Dynamic
Reviving the ethos of you don’t need a blockchain for that, notice the following subtlety: while the tokens representing stablecoins have value to users, that value is not native to the blockchain on which they are issued. Tether can (and routinely does) burn tokens on Ethereum and mint them on Tron, then burn on Tron and mint on Solana, and so on. So-called blockchains “go down” and nobody really cares. This makes no difference whatsoever to Tether’s own accounting, and arguably a positive difference to users given these actions track market demand. But it is detrimental to the blockchain being switched away from by stripping it of “TVL” that, it turns out, was only using it as rails: entirely exogenous value that leaves as quickly as it arrived.
One underdiscussed and underappreciated implication of the fact that no value is natively running through the blockchain itself is that, in the current scheme, both the sender and receiver of a stablecoin have to trust the same issuer. This creates an extremely powerful network effect that, in theory, makes the first-to-market likely to dominate and in practice has played out exactly as this theory would suggest: Tether has roughly 80% of the issuance, while roughly 19% goes to the political carve-out of USDC that wouldn’t exist at all were it not for government interference. Everybody else combined makes up the final 1%.
So, Tether is a full reserve bank but also has to be everybody’s bank. This is the source of a lot of the discomfort with Tether, and which feeds into the original objection around dollar hegemony, that there is an ill-defined but nonetheless uneasy feeling that Tether is slowly morphing into a CBDC. I would argue this really has nothing to do with Tether’s own behavior but rather is a consequence of the market dynamic inevitably created by the current stablecoin scheme. There is no reason to trust any other bank because nobody really wants a bank, they just want the rails. They want something that will retain a nominal dollar value long enough to spend it again. They don’t care what tech it runs on and they don’t even really care about the issuer except insofar as having some sense they won’t get rugged.
Notice this is not how fiat works. Banks can, of course, settle between each other, thus enabling their users to send money to customers of other banks. This settlement function is actually the entire point of central banks, less the money printing and general corruption enabled (we might say, this was the historical point of central banks, which have since become irredeemably corrupted by this power). This process is clunkier than stablecoins, as covered above, but the very possibility of settlement means there is no gigantic network effect to being the first commercial issuer of dollar balances. If it isn’t too triggering to this audience, one might suggest that the money printer also removes the residual concern that your balances might get rugged! (or, we might again say, you guarantee you don’t get rugged in the short term by guaranteeing you do get rugged in the long term).
This is a good point at which to introduce the unsettling observation that broader fintech is catching on to the benefits of stablecoins without any awareness whatsoever of all the limitations I am outlining here. With the likes of Stripe, Wise, Robinhood, and, post-Trump, even many US megabanks supposedly contemplating issuing stablecoins (obviously within the current scheme, not the scheme I am building up to proposing), we are forced to boggle our minds considering how on earth settlement is going to work. Are they going to settle through Ether? Well, no, because i) Ether isn’t money, it’s … to be honest, I don’t think anybody really knows what it is supposed to be, or if they once did they aren’t pretending anymore, but anyway, Stripe certainly hasn’t figured that out yet so, ii) it won’t be possible to issue them on layer 1s as soon as there is any meaningful volume, meaning they will have to route through “bullshit layer 2 wrapped Ether token that is really already a kind of stablecoin for Ether.”
The way they are going to try to fix this (anybody wanna bet?) is routing through DEXes, which is so painfully dumb you should be laughing and, if you aren’t, I would humbly suggest you don’t get just how dumb it is. What this amounts to is plugging the gap of Ether’s lack of moneyness (and wrapped Ether’s hilarious lack of moneyness) with … drum roll … unknowable technical and counterparty risk and unpredictable cost on top of reverting to just being a database. So, in other words, all of the costs of using a blockchain when you don’t strictly need to, and none of the benefits. Stripe is going to waste billions of dollars getting sandwich attacked out of some utterly vanilla FX settlement it is facilitating for clients who have even less of an idea what is going on and why North Korea now has all their money, and will eventually realize they should have skipped their shitcoin phase and gone straight to understanding Bitcoin instead …
3) Bitcoin (and Taproot Assets) Fixes This
To tie together a few loose ends, I only threw in the hilariously stupid suggestion of settling through wrapped Ether on Ether on Ether in order to tee up the entirely sensible suggestion of settling through Lightning. Again, not that this will be new to this audience, but while issuance schemes have been around on Bitcoin for a long time, the breakthrough of Taproot Assets is essentially the ability to atomically route through Lightning.
I will admit upfront that this presents a massive bootstrapping challenge relative to the ex-Bitcoin Crypto approach, and it’s not obvious to me if or how this will be overcome. I include this caveat to make it clear I am not suggesting this is a given. It may not be, it’s just beyond the scope of this post (or frankly my ability) to predict. This is a problem for Lightning Labs, Tether, and whoever else decides to step up to issue. But even highlighting this as an obvious and major concern invites us to consider an intriguing contrast: scaling TA stablecoins is hardest at the start and gets easier and easier thereafter. The more edge liquidity there is in TA stables, the less of a risk it is for incremental issuance; the more TA activity, the more attractive deploying liquidity is into Lightning proper, and vice versa. With apologies if this metaphor is even more confusing than it is helpful, one might conceive of the situation as being that there is massive inertia to bootstrap, but equally there could be positive feedback in driving the inertia to scale. Again, I have no idea, and it hasn’t happened yet in practice, but in theory it’s fun.
More importantly to this conversation, however, this is almost exactly the opposite dynamic to the current scheme on other blockchains, which is basically free to start, but gets more and more expensive the more people try to use it. One might say it antiscales (I don’t think that’s a real word, but if Taleb can do it, then I can do it too!).
Furthermore, the entire concept of “settling in Bitcoin” makes perfect sense both economically and technically: economically because Bitcoin is money, and technically because it can be locked in an HTLC and hence can enable atomic routing (i.e. because Lightning is a thing). This is clearly better than wrapped Eth on Eth on Eth or whatever, but, tantalisingly, is better than fiat too! The core message of the payments tome I may or may not one day write is (or will be) that fiat payments, while superficially efficient on the basis of centralized and hence costless ledger amendments, actually have a hidden cost in the form of interbank credit. Many readers will likely have heard me say this multiple times and in multiple settings but, contrary to popular belief, there is no such thing as a fiat debit. Even if styled as a debit, all fiat payments are credits and all have credit risk baked into their cost, even if that is obscured and pushed to the absolute foundational level of money printing to keep banks solvent and hence keep payment channels open.
Furthermore! this enables us to strip away the untenable market dynamic from the point above. The underappreciated and underdiscussed flip side of the drawback of the current dynamic that is effectively fixed by Taproot Assets is that there is no longer a mammoth network effect to a single issuer. Senders and receivers can trust different issuers (i.e. their own banks) because those banks can atomically settle a single payment over Lightning. This does not involve credit. It is arguably the only true debit in the world across both the relevant economic and technical criteria: it routes through money with no innate credit risk, and it does so atomically due to that money’s native properties.
Savvy readers may have picked up on a seed I planted a while back and which can now delightfully blossom:
This is what Visa was supposed to be!
Crucially, this is not what Visa is now. Visa today is pretty much the bank that is everybody’s counterparty, takes a small credit risk for the privilege, and oozes free cash flow bottlenecking global consumer payments.
But if you read both One From Many by Dee Hock (for a first person but pretty wild and extravagant take) and Electronic Value Exchange by David Stearns (for a third person, drier, but more analytical and historically contextualized take) or if you are just intimately familiar with the modern history of payments for whatever other reason, you will see that the role I just described for Lightning in an environment of unboundedly many banks issuing fiduciary media in the form of stablecoins is exactly what Dee Hock wanted to create when he envisioned Visa:
A neutral and open layer of value settlement enabling banks to create digital, interbank payment schemes for their customers at very low cost.
As it turns out, his vision was technically impossible with fiat, hence Visa, which started as a cooperative amongst member banks, was corrupted into a duopolistic for-profit rent seeker in curious parallel to the historical path of central banks …
4) eCash
To now push the argument to what I think is its inevitable conclusion, it’s worth being even more vigilant on the front of you don’t need a blockchain for that. I have argued that there is a role for a blockchain in providing a neutral settlement layer to enable true debits of stablecoins. But note this is just a fancy and/or stupid way of saying that Bitcoin is both the best money and is programmable, which we all knew anyway. The final step is realizing that, while TA is nice in terms of providing a kind of “on ramp” for global payments infrastructure as a whole to reorient around Lightning, there is some path dependence here in assuming (almost certainly correctly) that the familiarity of stablecoins as “RWA tokens on a blockchain” will be an important part of the lure.
But once that transition is complete, or is well on its way to being irreversible, we may as well come full circle and cut out tokens altogether. Again, you really don’t need a blockchain for that, and the residual appeal of better rails has been taken care of with the above massive detour through what I deem to be the inevitability of Lightning as a settlement layer. Just as USDT on Tron arguably has better moneyness than a JPMorgan balance, so a “stablecoin” as eCash has better moneyness than as a TA given it is cheaper, more private, and has more relevantly bearer properties (in other words, because it is cash). The technical detail that it can be hashlocked is really all you need to tie this all together. That means it can be atomically locked into a Lightning routed debit to the recipient of a different issuer (or “mint” in eCash lingo, but note this means the same thing as what we have been calling fully reserved banks). And the economic incentive is pretty compelling too because, for all their benefits, there is still a cost to TAs given they are issued onchain and they require asset-specific liquidity to route on Lightning. Once the rest of the tech is in place, why bother? Keep your Lightning connectivity and just become a mint.
What you get at that point is dramatically superior private database to JPMorgan with the dramatically superior public rails of Lightning. There is nothing left to desire from “a blockchain” besides what Bitcoin is fundamentally for in the first place: counterparty-risk-free value settlement.
And as a final point with a curious and pleasing echo to Dee Hock at Visa, Calle has made the point repeatedly that David Chaum’s vision for eCash, while deeply philosophical besides the technical details, was actually pretty much impossible to operate on fiat. From an eCash perspective, fiat stablecoins within the above infrastructure setup are a dramatic improvement on anything previously possible. But, of course, they are a slippery slope to Bitcoin regardless …
Objections Revisited
As a cherry on top, I think the objections I highlighted at the outset are now readily addressed – to the extent the reader believes what I am suggesting is more or less a technical and economic inevitability, that is. While, sure, I’m not particularly keen on giving the Treasury more avenues to sell its welfare-warfare shitcoin, on balance the likely development I’ve outlined is an enormous net positive: it’s going to sell these anyway so I prefer a strong economic incentive to steadily transition not only to Lightning as payment rails but eCash as fiduciary media, and to use “fintech” as a carrot to induce a slow motion bank run.
As alluded to above, once all this is in place, the final step to a Bitcoin standard becomes as simple as an individual’s decision to want Bitcoin instead of fiat. On reflection, this is arguably the easiest part! It's setting up all the tech that puts people off, so trojan-horsing them with “faster, cheaper payment rails” seems like a genius long-term strategy.
And as to “needing a blockchain” (or not), I hope that is entirely wrapped up at this point. The only blockchain you need is Bitcoin, but to the extent people are still confused by this (which I think will take decades more to fully unwind), we may as well lean into dazzling them with whatever innovation buzzwords and decentralization theatre they were going to fall for anyway before realizing they wanted Bitcoin all along.
Conclusion
Stablecoins are useful whether you like it or not. They are stupid in the abstract but it turns out fiat is even stupider, on inspection. But you don’t need a blockchain, and using one as decentralization theatre creates technical debt that is insurmountable in the long run. Blockchain-based stablecoins are doomed to a utility inversely proportional to their usage, and just to rub it in, their ill-conceived design practically creates a commercial dynamic that mandates there only ever be a single issuer.
Given they are useful, it seems natural that this tension is going to blow up at some point. It also seems worthwhile observing that Taproot Asset stablecoins have almost the inverse problem and opposite commercial dynamic: they will be most expensive to use at the outset but get cheaper and cheaper as their usage grows. Also, there is no incentive towards a monopoly issuer but rather towards as many as are willing to try to operate well and provide value to their users.
As such, we can expect any sizable growth in stablecoins to migrate to TA out of technical and economic necessity. Once this has happened - or possibly while it is happening but is clearly not going to stop - we may as well strip out the TA component and just use eCash because you really don’t need a blockchain for that at all. And once all the money is on eCash, deciding you want to denominate it in Bitcoin is the simplest on-ramp to hyperbitcoinization you can possibly imagine, given we’ve spent the previous decade or two rebuilding all payments tech around Lightning.
Or: Bitcoin fixes this. The End.
- Allen, #892,125
thanks to Marco Argentieri, Lyn Alden, and Calle for comments and feedback
-
 @ c3c7122c:607731d7
2025-04-12 04:05:06
@ c3c7122c:607731d7
2025-04-12 04:05:06Help!
Calling all El Salvador Nostriches! If you currently live in SV, I need your help and am offering several bounties (0.001, 0.01, and 0.1 BTC).
In Brief
In short, I am pursuing El Salvador citizenship by birthright (through my grandmother). I’ve struggled to progress because her name varies on different documents. I need someone to help me push harder to get past this barrier, or connect me with information or people who can work on my behalf. I am offering:
- 0.001 BTC (100k sats) for information that will help me progress from my current situation
- 0.01 BTC (1 MM sats) to get me in touch with someone that is more impactful than the immigration lawyer I already spoke with
- 0.1 BTC (10 MM sats) if your efforts help me obtain citizenship for me or my father
Background
My grandma married my grandfather (an American Marine) and moved to the states where my father was born. I have some official and unofficial documents where her name varies in spelling, order of first/middle name, and addition of her father’s last name. So every doc basically has a different name for her. I was connected with an english-speaking immigration lawyer in SV who hit a dead end when searching for her official ID because the city hall in her city had burned down so there was no record of her info. He gave up at that point. I find it odd that it was so easy to change your name back then, but they are more strict now with the records from that time.
I believe SV citizenship is my birthright and have several personal reasons for pursuing this. I want someone to act on my behalf who will try harder to work the system (by appeal, loophole, or even bribe if I have to). If you are local and can help me with this, I’d greatly appreciate any efforts you make.
Cheers!
Corey San Diego
-
 @ a95c6243:d345522c
2025-02-15 19:05:38
@ a95c6243:d345522c
2025-02-15 19:05:38Auf der diesjährigen Münchner Sicherheitskonferenz geht es vor allem um die Ukraine. Protagonisten sind dabei zunächst die US-Amerikaner. Präsident Trump schockierte die Europäer kurz vorher durch ein Telefonat mit seinem Amtskollegen Wladimir Putin, während Vizepräsident Vance mit seiner Rede über Demokratie und Meinungsfreiheit für versteinerte Mienen und Empörung sorgte.
Die Bemühungen der Europäer um einen Frieden in der Ukraine halten sich, gelinde gesagt, in Grenzen. Größeres Augenmerk wird auf militärische Unterstützung, die Pflege von Feindbildern sowie Eskalation gelegt. Der deutsche Bundeskanzler Scholz reagierte auf die angekündigten Verhandlungen über einen möglichen Frieden für die Ukraine mit der Forderung nach noch höheren «Verteidigungsausgaben». Auch die amtierende Außenministerin Baerbock hatte vor der Münchner Konferenz klargestellt:
«Frieden wird es nur durch Stärke geben. (...) Bei Corona haben wir gesehen, zu was Europa fähig ist. Es braucht erneut Investitionen, die der historischen Wegmarke, vor der wir stehen, angemessen sind.»
Die Rüstungsindustrie freut sich in jedem Fall über weltweit steigende Militärausgaben. Die Kriege in der Ukraine und in Gaza tragen zu Rekordeinnahmen bei. Jetzt «winkt die Aussicht auf eine jahrelange große Nachrüstung in Europa», auch wenn der Ukraine-Krieg enden sollte, so hört man aus Finanzkreisen. In der Konsequenz kennt «die Aktie des deutschen Vorzeige-Rüstungskonzerns Rheinmetall in ihrem Anstieg offenbar gar keine Grenzen mehr». «Solche Friedensversprechen» wie das jetzige hätten in der Vergangenheit zu starken Kursverlusten geführt.
Für manche Leute sind Kriegswaffen und sonstige Rüstungsgüter Waren wie alle anderen, jedenfalls aus der Perspektive von Investoren oder Managern. Auch in diesem Bereich gibt es Startups und man spricht von Dingen wie innovativen Herangehensweisen, hocheffizienten Produktionsanlagen, skalierbaren Produktionstechniken und geringeren Stückkosten.
Wir lesen aktuell von Massenproduktion und gesteigerten Fertigungskapazitäten für Kriegsgerät. Der Motor solcher Dynamik und solchen Wachstums ist die Aufrüstung, die inzwischen permanent gefordert wird. Parallel wird die Bevölkerung verbal eingestimmt und auf Kriegstüchtigkeit getrimmt.
Das Rüstungs- und KI-Startup Helsing verkündete kürzlich eine «dezentrale Massenproduktion für den Ukrainekrieg». Mit dieser Expansion positioniere sich das Münchner Unternehmen als einer der weltweit führenden Hersteller von Kampfdrohnen. Der nächste «Meilenstein» steht auch bereits an: Man will eine Satellitenflotte im Weltraum aufbauen, zur Überwachung von Gefechtsfeldern und Truppenbewegungen.
Ebenfalls aus München stammt das als DefenseTech-Startup bezeichnete Unternehmen ARX Robotics. Kürzlich habe man in der Region die größte europäische Produktionsstätte für autonome Verteidigungssysteme eröffnet. Damit fahre man die Produktion von Militär-Robotern hoch. Diese Expansion diene auch der Lieferung der «größten Flotte unbemannter Bodensysteme westlicher Bauart» in die Ukraine.
Rüstung boomt und scheint ein Zukunftsmarkt zu sein. Die Hersteller und Vermarkter betonen, mit ihren Aktivitäten und Produkten solle die europäische Verteidigungsfähigkeit erhöht werden. Ihre Strategien sollten sogar «zum Schutz demokratischer Strukturen beitragen».
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ c631e267:c2b78d3e
2025-02-07 19:42:11
@ c631e267:c2b78d3e
2025-02-07 19:42:11Nur wenn wir aufeinander zugehen, haben wir die Chance \ auf Überwindung der gegenseitigen Ressentiments! \ Dr. med. dent. Jens Knipphals
In Wolfsburg sollte es kürzlich eine Gesprächsrunde von Kritikern der Corona-Politik mit Oberbürgermeister Dennis Weilmann und Vertretern der Stadtverwaltung geben. Der Zahnarzt und langjährige Maßnahmenkritiker Jens Knipphals hatte diese Einladung ins Rathaus erwirkt und publiziert. Seine Motivation:
«Ich möchte die Spaltung der Gesellschaft überwinden. Dazu ist eine umfassende Aufarbeitung der Corona-Krise in der Öffentlichkeit notwendig.»
Schon früher hatte Knipphals Antworten von den Kommunalpolitikern verlangt, zum Beispiel bei öffentlichen Bürgerfragestunden. Für das erwartete Treffen im Rathaus formulierte er Fragen wie: Warum wurden fachliche Argumente der Kritiker ignoriert? Weshalb wurde deren Ausgrenzung, Diskreditierung und Entmenschlichung nicht entgegengetreten? In welcher Form übernehmen Rat und Verwaltung in Wolfsburg persönlich Verantwortung für die erheblichen Folgen der politischen Corona-Krise?
Der Termin fand allerdings nicht statt – der Bürgermeister sagte ihn kurz vorher wieder ab. Knipphals bezeichnete Weilmann anschließend als Wiederholungstäter, da das Stadtoberhaupt bereits 2022 zu einem Runden Tisch in der Sache eingeladen hatte, den es dann nie gab. Gegenüber Multipolar erklärte der Arzt, Weilmann wolle scheinbar eine öffentliche Aufarbeitung mit allen Mitteln verhindern. Er selbst sei «inzwischen absolut desillusioniert» und die einzige Lösung sei, dass die Verantwortlichen gingen.
Die Aufarbeitung der Plandemie beginne bei jedem von uns selbst, sei aber letztlich eine gesamtgesellschaftliche Aufgabe, schreibt Peter Frey, der den «Fall Wolfsburg» auch in seinem Blog behandelt. Diese Aufgabe sei indes deutlich größer, als viele glaubten. Erfreulicherweise sei der öffentliche Informationsraum inzwischen größer, trotz der weiterhin unverfrorenen Desinformations-Kampagnen der etablierten Massenmedien.
Frey erinnert daran, dass Dennis Weilmann mitverantwortlich für gravierende Grundrechtseinschränkungen wie die 2021 eingeführten 2G-Regeln in der Wolfsburger Innenstadt zeichnet. Es sei naiv anzunehmen, dass ein Funktionär einzig im Interesse der Bürger handeln würde. Als früherer Dezernent des Amtes für Wirtschaft, Digitalisierung und Kultur der Autostadt kenne Weilmann zum Beispiel die Verknüpfung von Fördergeldern mit politischen Zielsetzungen gut.
Wolfsburg wurde damals zu einem Modellprojekt des Bundesministeriums des Innern (BMI) und war Finalist im Bitkom-Wettbewerb «Digitale Stadt». So habe rechtzeitig vor der Plandemie das Projekt «Smart City Wolfsburg» anlaufen können, das der Stadt «eine Vorreiterrolle für umfassende Vernetzung und Datenerfassung» aufgetragen habe, sagt Frey. Die Vereinten Nationen verkauften dann derartige «intelligente» Überwachungs- und Kontrollmaßnahmen ebenso als Rettung in der Not wie das Magazin Forbes im April 2020:
«Intelligente Städte können uns helfen, die Coronavirus-Pandemie zu bekämpfen. In einer wachsenden Zahl von Ländern tun die intelligenten Städte genau das. Regierungen und lokale Behörden nutzen Smart-City-Technologien, Sensoren und Daten, um die Kontakte von Menschen aufzuspüren, die mit dem Coronavirus infiziert sind. Gleichzeitig helfen die Smart Cities auch dabei, festzustellen, ob die Regeln der sozialen Distanzierung eingehalten werden.»
Offensichtlich gibt es viele Aspekte zu bedenken und zu durchleuten, wenn es um die Aufklärung und Aufarbeitung der sogenannten «Corona-Pandemie» und der verordneten Maßnahmen geht. Frustration und Desillusion sind angesichts der Realitäten absolut verständlich. Gerade deswegen sind Initiativen wie die von Jens Knipphals so bewundernswert und so wichtig – ebenso wie eine seiner Kernthesen: «Wir müssen aufeinander zugehen, da hilft alles nichts».
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 3eba5ef4:751f23ae
2025-04-11 00:40:28
@ 3eba5ef4:751f23ae
2025-04-11 00:40:28Crypto Insights
2025 MIT Bitcoin Expo: Spotlight on Freedom Tech
The 12th MIT Bitcoin Expo took place on April 5–6, centering this year’s theme on “Freedom Tech” and how technology can facilitate physical and social liberation.
-
Day 1 Recap: Mawarire delivered the keynote speech “Why Freedom Tech Matters,” and Dryja discussed how Bitcoin demonstrates resilience against nation-states. The morning sessions focused on corporate adoption, featuring speakers such as Paul Giordano from Marathon Digital and Bitcoin Core contributors like Gloria Zhao. The afternoon shifted toward more technical topics, including consensus cleanup, poisoning attacks, censorship resistance, and the Bitcoin Pipes protocol.
-
Day 2 Recap: The focus shifted to global impact. Mauricio Bartolomeo discussed the exfiltration of resources via Bitcoin, followed by a panel with activists from Venezuela, Russia, and Togo. Technical topics included: scaling self-custody, Steven Roose’s covenant soft fork proposals, the future of freedom tech, quantum resistance, and Tor.
Into Bitcoin Address Poisoning Attacks
In this article, Jameson Lopp highlights the rise of Bitcoin address poisoning attacks—an emerging form of social engineering. Attackers send transactions from newly generated wallets that mimic the beginning and end characters of a target's recently used address. If the target later copies an address from their transaction history, they may unknowingly send funds to the attacker instead of the intended recipient. Though the success rate per attack is low, the low cost of transactions enables attackers to attempt thousands in a short period.
Lopp also argues that such attacks are a byproduct of low transaction fees and that higher fees could deter them. He also suggests wallet-level defenses, such as warnings like, “Oh, this came from a similar looking address,” to help users avoid interaction.
Examining the Mitigation Strategy Against Timewarp Attacks
Timewarp attacks, first identified around 2011, allow a majority of malicious miners to manipulate block timestamps, artificially lower difficulty, and mine blocks every few seconds. The “Great Consensus Cleanup” soft fork proposal can mitigate this by requiring that the first block in a new difficulty period must have a time no earlier than a certain number of minutes before the last block of the previous period.
A report examines the details of this BIP.
Tokenization on Bitcoin: Building a Global Settlement Layer with Taproot Assets and Lightning
Bitcoin’s evolution into a multi-asset platform is accelerating with the advent of Taproot Assets and Lightning Network. The integration of these technologies combines Bitcoin’s decentralization and security with the speed and scalability of the Lightning Network. This report examines how Taproot Assets enable asset issuance, transfers, and swaps on Bitcoin’s base layer, and how the Lightning Network facilitates fast, low-cost transfers of those assets. We compare this approach to earlier attempts at Bitcoin asset issuance and analyze its market potential against other blockchains and traditional payment networks.
Solving Data Availability in Client-Side Validation With UTxO Binding
Issuing tokens on Bitcoin is attractive due to its security and dominance, but its limited functionality creates challenges. Client-side validation (CSV) is a common workaround, using off-chain data with on-chain verification, though it risks data loss and withholding. This paper introduces UTxO binding, a framework that links a Bitcoin UTxO to one on an auxiliary chain, providing data storage and programmability. The authors prove its security and implement it using Nervos CKB.
From State Differences to Scaling: Citrea’s Fee Mechanism for Bitcoin
The Citrea team has designed a new fee mechanism to enhance Bitcoin’s scalability without compromising security. It only records essential state differences (i.e., state slot changes) on the Bitcoin main chain, using zero-knowledge proofs to ensure verifiability and Bitcoin security while drastically reducing state inscription costs. Optimizations include: replacing
codefield withcode_hash, compressing state data using a highly efficient compression algorithm Brotli, and analyzing historical Ethereum block data to estimate each transaction’s impact on cumulative state differences—enabling a discount to each transaction.Second: A New Ark Implementation Launched on Bitcoin Signet
Second, a protocol based on Ark to improve Bitcoin transaction throughput, has launched Bark, a test implementation on Bitcoin Signet.
Ark makes Bitcoin transactions faster, cheaper, and more private, allowing more users and transactions per block. However, funds stored non-custodially via Ark can expire if unused, making it slightly less trustless than mainchain transactions.
BitLayer Optimizes BitVM Bridge Protocol and Demonstrates on Testnet
Bitlayer BitVM Bridge protocol is an optimized adaptation of the bridge protocol outlined in the BitVM2 paper, to improve efficiency, scalability, and security—especially for high-risk cross-chain transactions.
In this article, two key testnet demos on bitvmnet (a BitVM-dedicated testnet) demonstrate how the protocol can:
-
Effectively thwart fraudulent reclaim attempts by brokers.
-
Protect honest brokers from malicious or baseless challenges.
Cardano Enables Bitcoin DeFi via BitVMX and Lightning Hydra
Cardano is integrating with Bitcoin through Lightning Hydra and BitVMX to enable secure and scalable Bitcoin DeFi.
Zcash’s Tachyon Upgrade: Toward Scalable Oblivious Synchronization
Zcash has unveiled project Tachyon, a proposal to scale Zcash by changing how wallets sync and prove ownership of notes. Instead of scanning the entire blockchain, wallets track only their own nullifiers and receive succinct proofs from untrusted, oblivious sync servers. Transactions include proofs of wallet state (using recursive SNARKs), allowing nodes to verify them without keeping the full history. Notes are exchanged out-of-band, reducing on-chain data and improving privacy. In the nominal case, users get fast sync, lightweight wallets, and strong privacy, without the need to trust the network.
Podcast | Why the Future of Bitcoin Mining is Distributed
In this podcast, Professor Troy Cross discusses the centralization of Bitcoin mining and argues convincingly for hashrate decentralization. While economies of scale have led to mega mining operations, he sees economic imperative that will drive mining toward a globally distributed future—not dominated by the U.S.—ensuring neutrality and resilience against state-level threats.
Binance Report|Crypto Industry Map March 2025
This report provides an overview of projects using a framework that divides crypto into four core ecosystems—Infrastructure, DeFi, NFT, and Gaming—and four trending sectors: Stablecoins, RWA, AI, and DeSci.
For infrastructure, five key pillars are identified: scalability & fairness, data availability & tooling, security & privacy, cloud networks, and connectivity. The report also maps out and categorizes the major projects and solutions currently on the market.

Top Reads on Blockchain and Beyond
A Game-Theoretic Approach to Bitcoin’s Valuation in Equilibrium
The author presents a game-theoretic argument for why Bitcoin will emerge as the optimal unit of account in equilibrium. The argument is based upon the observation that a generally agreed upon unit of account that represents a constant share of total wealth (equal to the totality of all other economic utility) will naturally create price signals that passively stabilize the macroeconomy, without requiring external intervention.
Bitcoin’s unique properties—finite supply, inertness, fungibility, accessibility, and ownership history—position it as the leading candidate to emerge as this unit.
Neo: Lattice-Based Folding Scheme for CCS Over Small Fields and Pay-Per-Bit Commitments
This paper introduces Neo, a new lattice-based folding scheme for CCS, an NP-complete relation that generalizes R1CS, Plonkish, and AIR. Neo's folding scheme can be viewed as adapting the folding scheme in HyperNova (CRYPTO'24), which assumes elliptic-curve based linearly homomorphic commitments, to the lattice setting. Unlike HyperNova, Neo can use “small” prime fields (e.g., over the Goldilocks prime). Additionally, Neo provides plausible post-quantum security.
Social Scalability: Key to Massive Value Accumulation in Crypto
Social scalability, a concept first proposed by Nick Szabo in his 2017 article Money, Blockchains, and Social Scalability, is further explored in this thread. Here, “social scalability” refers to an institution's ability to allow the maximum number of people to have skin in the game and win. It’s seen as the main reason crypto has become a $2.9T asset class today and a key driver of value accumulation in the coming decade.
The author argues that two critical ingredients for long-term social scalability are credible neutrality and utility. Currently, only BTC and ETH have this potential, yet neither strikes a perfect balance between the two. The author notes that there is not yet a strong narrative around social scalability, and concludes by emphasizing the importance of focusing on long-term value and resisting the temptation of short-term market narratives.
-
-
 @ a95c6243:d345522c
2025-01-31 20:02:25
@ a95c6243:d345522c
2025-01-31 20:02:25Im Augenblick wird mit größter Intensität, großer Umsicht \ das deutsche Volk belogen. \ Olaf Scholz im FAZ-Interview
Online-Wahlen stärken die Demokratie, sind sicher, und 61 Prozent der Wahlberechtigten sprechen sich für deren Einführung in Deutschland aus. Das zumindest behauptet eine aktuelle Umfrage, die auch über die Agentur Reuters Verbreitung in den Medien gefunden hat. Demnach würden außerdem 45 Prozent der Nichtwähler bei der Bundestagswahl ihre Stimme abgeben, wenn sie dies zum Beispiel von Ihrem PC, Tablet oder Smartphone aus machen könnten.
Die telefonische Umfrage unter gut 1000 wahlberechtigten Personen sei repräsentativ, behauptet der Auftraggeber – der Digitalverband Bitkom. Dieser präsentiert sich als eingetragener Verein mit einer beeindruckenden Liste von Mitgliedern, die Software und IT-Dienstleistungen anbieten. Erklärtes Vereinsziel ist es, «Deutschland zu einem führenden Digitalstandort zu machen und die digitale Transformation der deutschen Wirtschaft und Verwaltung voranzutreiben».
Durchgeführt hat die Befragung die Bitkom Servicegesellschaft mbH, also alles in der Familie. Die gleiche Erhebung hatte der Verband übrigens 2021 schon einmal durchgeführt. Damals sprachen sich angeblich sogar 63 Prozent für ein derartiges «Demokratie-Update» aus – die Tendenz ist demgemäß fallend. Dennoch orakelt mancher, der Gang zur Wahlurne gelte bereits als veraltet.
Die spanische Privat-Uni mit Globalisten-Touch, IE University, berichtete Ende letzten Jahres in ihrer Studie «European Tech Insights», 67 Prozent der Europäer befürchteten, dass Hacker Wahlergebnisse verfälschen könnten. Mehr als 30 Prozent der Befragten glaubten, dass künstliche Intelligenz (KI) bereits Wahlentscheidungen beeinflusst habe. Trotzdem würden angeblich 34 Prozent der unter 35-Jährigen einer KI-gesteuerten App vertrauen, um in ihrem Namen für politische Kandidaten zu stimmen.
Wie dauerhaft wird wohl das Ergebnis der kommenden Bundestagswahl sein? Diese Frage stellt sich angesichts der aktuellen Entwicklung der Migrations-Debatte und der (vorübergehend) bröckelnden «Brandmauer» gegen die AfD. Das «Zustrombegrenzungsgesetz» der Union hat das Parlament heute Nachmittag überraschenderweise abgelehnt. Dennoch muss man wohl kein ausgesprochener Pessimist sein, um zu befürchten, dass die Entscheidungen der Bürger von den selbsternannten Verteidigern der Demokratie künftig vielleicht nicht respektiert werden, weil sie nicht gefallen.
Bundesweit wird jetzt zu «Brandmauer-Demos» aufgerufen, die CDU gerät unter Druck und es wird von Übergriffen auf Parteibüros und Drohungen gegen Mitarbeiter berichtet. Sicherheitsbehörden warnen vor Eskalationen, die Polizei sei «für ein mögliches erhöhtes Aufkommen von Straftaten gegenüber Politikern und gegen Parteigebäude sensibilisiert».
Der Vorwand «unzulässiger Einflussnahme» auf Politik und Wahlen wird als Argument schon seit einiger Zeit aufgebaut. Der Manipulation schuldig befunden wird neben Putin und Trump auch Elon Musk, was lustigerweise ausgerechnet Bill Gates gerade noch einmal bekräftigt und als «völlig irre» bezeichnet hat. Man stelle sich die Diskussionen um die Gültigkeit von Wahlergebnissen vor, wenn es Online-Verfahren zur Stimmabgabe gäbe. In der Schweiz wird «E-Voting» seit einigen Jahren getestet, aber wohl bisher mit wenig Erfolg.
Die politische Brandstiftung der letzten Jahre zahlt sich immer mehr aus. Anstatt dringende Probleme der Menschen zu lösen – zu denen auch in Deutschland die weit verbreitete Armut zählt –, hat die Politik konsequent polarisiert und sich auf Ausgrenzung und Verhöhnung großer Teile der Bevölkerung konzentriert. Basierend auf Ideologie und Lügen werden abweichende Stimmen unterdrückt und kriminalisiert, nicht nur und nicht erst in diesem Augenblick. Die nächsten Wochen dürften ausgesprochen spannend werden.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a95c6243:d345522c
2025-01-24 20:59:01
@ a95c6243:d345522c
2025-01-24 20:59:01Menschen tun alles, egal wie absurd, \ um ihrer eigenen Seele nicht zu begegnen. \ Carl Gustav Jung
«Extremer Reichtum ist eine Gefahr für die Demokratie», sagen über die Hälfte der knapp 3000 befragten Millionäre aus G20-Staaten laut einer Umfrage der «Patriotic Millionaires». Ferner stellte dieser Zusammenschluss wohlhabender US-Amerikaner fest, dass 63 Prozent jener Millionäre den Einfluss von Superreichen auf US-Präsident Trump als Bedrohung für die globale Stabilität ansehen.
Diese Besorgnis haben 370 Millionäre und Milliardäre am Dienstag auch den in Davos beim WEF konzentrierten Privilegierten aus aller Welt übermittelt. In einem offenen Brief forderten sie die «gewählten Führer» auf, die Superreichen – also sie selbst – zu besteuern, um «die zersetzenden Auswirkungen des extremen Reichtums auf unsere Demokratien und die Gesellschaft zu bekämpfen». Zum Beispiel kontrolliere eine handvoll extrem reicher Menschen die Medien, beeinflusse die Rechtssysteme in unzulässiger Weise und verwandele Recht in Unrecht.
Schon 2019 beanstandete der bekannte Historiker und Schriftsteller Ruthger Bregman an einer WEF-Podiumsdiskussion die Steuervermeidung der Superreichen. Die elitäre Veranstaltung bezeichnete er als «Feuerwehr-Konferenz, bei der man nicht über Löschwasser sprechen darf.» Daraufhin erhielt Bregman keine Einladungen nach Davos mehr. Auf seine Aussagen machte der Schweizer Aktivist Alec Gagneux aufmerksam, der sich seit Jahrzehnten kritisch mit dem WEF befasst. Ihm wurde kürzlich der Zutritt zu einem dreiteiligen Kurs über das WEF an der Volkshochschule Region Brugg verwehrt.
Nun ist die Erkenntnis, dass mit Geld politischer Einfluss einhergeht, alles andere als neu. Und extremer Reichtum macht die Sache nicht wirklich besser. Trotzdem hat man über Initiativen wie Patriotic Millionaires oder Taxmenow bisher eher selten etwas gehört, obwohl es sie schon lange gibt. Auch scheint es kein Problem, wenn ein Herr Gates fast im Alleingang versucht, globale Gesundheits-, Klima-, Ernährungs- oder Bevölkerungspolitik zu betreiben – im Gegenteil. Im Jahr, als der Milliardär Donald Trump zum zweiten Mal ins Weiße Haus einzieht, ist das Echo in den Gesinnungsmedien dagegen enorm – und uniform, wer hätte das gedacht.
Der neue US-Präsident hat jedoch «Davos geerdet», wie Achgut es nannte. In seiner kurzen Rede beim Weltwirtschaftsforum verteidigte er seine Politik und stellte klar, er habe schlicht eine «Revolution des gesunden Menschenverstands» begonnen. Mit deutlichen Worten sprach er unter anderem von ersten Maßnahmen gegen den «Green New Scam», und von einem «Erlass, der jegliche staatliche Zensur beendet»:
«Unsere Regierung wird die Äußerungen unserer eigenen Bürger nicht mehr als Fehlinformation oder Desinformation bezeichnen, was die Lieblingswörter von Zensoren und derer sind, die den freien Austausch von Ideen und, offen gesagt, den Fortschritt verhindern wollen.»
Wie der «Trumpismus» letztlich einzuordnen ist, muss jeder für sich selbst entscheiden. Skepsis ist definitiv angebracht, denn «einer von uns» sind weder der Präsident noch seine auserwählten Teammitglieder. Ob sie irgendeinen Sumpf trockenlegen oder Staatsverbrechen aufdecken werden oder was aus WHO- und Klimaverträgen wird, bleibt abzuwarten.
Das WHO-Dekret fordert jedenfalls die Übertragung der Gelder auf «glaubwürdige Partner», die die Aktivitäten übernehmen könnten. Zufällig scheint mit «Impfguru» Bill Gates ein weiterer Harris-Unterstützer kürzlich das Lager gewechselt zu haben: Nach einem gemeinsamen Abendessen zeigte er sich «beeindruckt» von Trumps Interesse an der globalen Gesundheit.
Mit dem Projekt «Stargate» sind weitere dunkle Wolken am Erwartungshorizont der Fangemeinde aufgezogen. Trump hat dieses Joint Venture zwischen den Konzernen OpenAI, Oracle, und SoftBank als das «größte KI-Infrastrukturprojekt der Geschichte» angekündigt. Der Stein des Anstoßes: Oracle-CEO Larry Ellison, der auch Fan von KI-gestützter Echtzeit-Überwachung ist, sieht einen weiteren potenziellen Einsatz der künstlichen Intelligenz. Sie könne dazu dienen, Krebserkrankungen zu erkennen und individuelle mRNA-«Impfstoffe» zur Behandlung innerhalb von 48 Stunden zu entwickeln.
Warum bitte sollten sich diese superreichen «Eliten» ins eigene Fleisch schneiden und direkt entgegen ihren eigenen Interessen handeln? Weil sie Menschenfreunde, sogenannte Philanthropen sind? Oder vielleicht, weil sie ein schlechtes Gewissen haben und ihre Schuld kompensieren müssen? Deswegen jedenfalls brauchen «Linke» laut Robert Willacker, einem deutschen Politikberater mit brasilianischen Wurzeln, rechte Parteien – ein ebenso überraschender wie humorvoller Erklärungsansatz.
Wenn eine Krähe der anderen kein Auge aushackt, dann tut sie das sich selbst noch weniger an. Dass Millionäre ernsthaft ihre eigene Besteuerung fordern oder Machteliten ihren eigenen Einfluss zugunsten anderer einschränken würden, halte ich für sehr unwahrscheinlich. So etwas glaube ich erst, wenn zum Beispiel die Rüstungsindustrie sich um Friedensverhandlungen bemüht, die Pharmalobby sich gegen institutionalisierte Korruption einsetzt, Zentralbanken ihre CBDC-Pläne für Bitcoin opfern oder der ÖRR die Abschaffung der Rundfunkgebühren fordert.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 3b3a42d3:d192e325
2025-04-10 08:57:51
@ 3b3a42d3:d192e325
2025-04-10 08:57:51Atomic Signature Swaps (ASS) over Nostr is a protocol for atomically exchanging Schnorr signatures using Nostr events for orchestration. This new primitive enables multiple interesting applications like:
- Getting paid to publish specific Nostr events
- Issuing automatic payment receipts
- Contract signing in exchange for payment
- P2P asset exchanges
- Trading and enforcement of asset option contracts
- Payment in exchange for Nostr-based credentials or access tokens
- Exchanging GMs 🌞
It only requires that (i) the involved signatures be Schnorr signatures using the secp256k1 curve and that (ii) at least one of those signatures be accessible to both parties. These requirements are naturally met by Nostr events (published to relays), Taproot transactions (published to the mempool and later to the blockchain), and Cashu payments (using mints that support NUT-07, allowing any pair of these signatures to be swapped atomically.
How the Cryptographic Magic Works 🪄
This is a Schnorr signature
(Zₓ, s):s = z + H(Zₓ || P || m)⋅kIf you haven't seen it before, don't worry, neither did I until three weeks ago.
The signature scalar s is the the value a signer with private key
k(and public keyP = k⋅G) must calculate to prove his commitment over the messagemgiven a randomly generated noncez(Zₓis just the x-coordinate of the public pointZ = z⋅G).His a hash function (sha256 with the tag "BIP0340/challenge" when dealing with BIP340),||just means to concatenate andGis the generator point of the elliptic curve, used to derive public values from private ones.Now that you understand what this equation means, let's just rename
z = r + t. We can do that,zis just a randomly generated number that can be represented as the sum of two other numbers. It also follows thatz⋅G = r⋅G + t⋅G ⇔ Z = R + T. Putting it all back into the definition of a Schnorr signature we get:s = (r + t) + H((R + T)ₓ || P || m)⋅kWhich is the same as:
s = sₐ + twheresₐ = r + H((R + T)ₓ || P || m)⋅ksₐis what we call the adaptor signature scalar) and t is the secret.((R + T)ₓ, sₐ)is an incomplete signature that just becomes valid by add the secret t to thesₐ:s = sₐ + tWhat is also important for our purposes is that by getting access to the valid signature s, one can also extract t from it by just subtracting
sₐ:t = s - sₐThe specific value of
tdepends on our choice of the public pointT, sinceRis just a public point derived from a randomly generated noncer.So how do we choose
Tso that it requires the secret t to be the signature over a specific messagem'by an specific public keyP'? (without knowing the value oft)Let's start with the definition of t as a valid Schnorr signature by P' over m':
t = r' + H(R'ₓ || P' || m')⋅k' ⇔ t⋅G = r'⋅G + H(R'ₓ || P' || m')⋅k'⋅GThat is the same as:
T = R' + H(R'ₓ || P' || m')⋅P'Notice that in order to calculate the appropriate
Tthat requirestto be an specific signature scalar, we only need to know the public nonceR'used to generate that signature.In summary: in order to atomically swap Schnorr signatures, one party
P'must provide a public nonceR', while the other partyPmust provide an adaptor signature using that nonce:sₐ = r + H((R + T)ₓ || P || m)⋅kwhereT = R' + H(R'ₓ || P' || m')⋅P'P'(the nonce provider) can then add his own signature t to the adaptor signaturesₐin order to get a valid signature byP, i.e.s = sₐ + t. When he publishes this signature (as a Nostr event, Cashu transaction or Taproot transaction), it becomes accessible toPthat can now extract the signaturetbyP'and also make use of it.Important considerations
A signature may not be useful at the end of the swap if it unlocks funds that have already been spent, or that are vulnerable to fee bidding wars.
When a swap involves a Taproot UTXO, it must always use a 2-of-2 multisig timelock to avoid those issues.
Cashu tokens do not require this measure when its signature is revealed first, because the mint won't reveal the other signature if they can't be successfully claimed, but they also require a 2-of-2 multisig timelock when its signature is only revealed last (what is unavoidable in cashu for cashu swaps).
For Nostr events, whoever receives the signature first needs to publish it to at least one relay that is accessible by the other party. This is a reasonable expectation in most cases, but may be an issue if the event kind involved is meant to be used privately.
How to Orchestrate the Swap over Nostr?
Before going into the specific event kinds, it is important to recognize what are the requirements they must meet and what are the concerns they must address. There are mainly three requirements:
- Both parties must agree on the messages they are going to sign
- One party must provide a public nonce
- The other party must provide an adaptor signature using that nonce
There is also a fundamental asymmetry in the roles of both parties, resulting in the following significant downsides for the party that generates the adaptor signature:
- NIP-07 and remote signers do not currently support the generation of adaptor signatures, so he must either insert his nsec in the client or use a fork of another signer
- There is an overhead of retrieving the completed signature containing the secret, either from the blockchain, mint endpoint or finding the appropriate relay
- There is risk he may not get his side of the deal if the other party only uses his signature privately, as I have already mentioned
- There is risk of losing funds by not extracting or using the signature before its timelock expires. The other party has no risk since his own signature won't be exposed by just not using the signature he received.
The protocol must meet all those requirements, allowing for some kind of role negotiation and while trying to reduce the necessary hops needed to complete the swap.
Swap Proposal Event (kind:455)
This event enables a proposer and his counterparty to agree on the specific messages whose signatures they intend to exchange. The
contentfield is the following stringified JSON:{ "give": <signature spec (required)>, "take": <signature spec (required)>, "exp": <expiration timestamp (optional)>, "role": "<adaptor | nonce (optional)>", "description": "<Info about the proposal (optional)>", "nonce": "<Signature public nonce (optional)>", "enc_s": "<Encrypted signature scalar (optional)>" }The field
roleindicates what the proposer will provide during the swap, either the nonce or the adaptor. When this optional field is not provided, the counterparty may decide whether he will send a nonce back in a Swap Nonce event or a Swap Adaptor event using thenonce(optionally) provided by in the Swap Proposal in order to avoid one hop of interaction.The
enc_sfield may be used to store the encrypted scalar of the signature associated with thenonce, since this information is necessary later when completing the adaptor signature received from the other party.A
signature specspecifies thetypeand all necessary information for producing and verifying a given signature. In the case of signatures for Nostr events, it contain a template with all the fields, exceptpubkey,idandsig:{ "type": "nostr", "template": { "kind": "<kind>" "content": "<content>" "tags": [ … ], "created_at": "<created_at>" } }In the case of Cashu payments, a simplified
signature specjust needs to specify the payment amount and an array of mints trusted by the proposer:{ "type": "cashu", "amount": "<amount>", "mint": ["<acceptable mint_url>", …] }This works when the payer provides the adaptor signature, but it still needs to be extended to also work when the payer is the one receiving the adaptor signature. In the later case, the
signature specmust also include atimelockand the derived public keysYof each Cashu Proof, but for now let's just ignore this situation. It should be mentioned that the mint must be trusted by both parties and also support Token state check (NUT-07) for revealing the completed adaptor signature and P2PK spending conditions (NUT-11) for the cryptographic scheme to work.The
tagsare:"p", the proposal counterparty's public key (required)"a", akind:30455Swap Listing event or an application specific version of it (optional)
Forget about this Swap Listing event for now, I will get to it later...
Swap Nonce Event (kind:456) - Optional
This is an optional event for the Swap Proposal receiver to provide the public nonce of his signature when the proposal does not include a nonce or when he does not want to provide the adaptor signature due to the downsides previously mentioned. The
contentfield is the following stringified JSON:{ "nonce": "<Signature public nonce>", "enc_s": "<Encrypted signature scalar (optional)>" }And the
tagsmust contain:"e", akind:455Swap Proposal Event (required)"p", the counterparty's public key (required)
Swap Adaptor Event (kind:457)
The
contentfield is the following stringified JSON:{ "adaptors": [ { "sa": "<Adaptor signature scalar>", "R": "<Signer's public nonce (including parity byte)>", "T": "<Adaptor point (including parity byte)>", "Y": "<Cashu proof derived public key (if applicable)>", }, …], "cashu": "<Cashu V4 token (if applicable)>" }And the
tagsmust contain:"e", akind:455Swap Proposal Event (required)"p", the counterparty's public key (required)
Discoverability
The Swap Listing event previously mentioned as an optional tag in the Swap Proposal may be used to find an appropriate counterparty for a swap. It allows a user to announce what he wants to accomplish, what his requirements are and what is still open for negotiation.
Swap Listing Event (kind:30455)
The
contentfield is the following stringified JSON:{ "description": "<Information about the listing (required)>", "give": <partial signature spec (optional)>, "take": <partial signature spec (optional)>, "examples: [<take signature spec>], // optional "exp": <expiration timestamp (optional)>, "role": "<adaptor | nonce (optional)>" }The
descriptionfield describes the restrictions on counterparties and signatures the user is willing to accept.A
partial signature specis an incompletesignature specused in Swap Proposal eventskind:455where omitting fields signals that they are still open for negotiation.The
examplesfield is an array ofsignature specsthe user would be willing totake.The
tagsare:"d", a unique listing id (required)"s", the status of the listingdraft | open | closed(required)"t", topics related to this listing (optional)"p", public keys to notify about the proposal (optional)
Application Specific Swap Listings
Since Swap Listings are still fairly generic, it is expected that specific use cases define new event kinds based on the generic listing. Those application specific swap listing would be easier to filter by clients and may impose restrictions and add new fields and/or tags. The following are some examples under development:
Sponsored Events
This listing is designed for users looking to promote content on the Nostr network, as well as for those who want to monetize their accounts by sharing curated sponsored content with their existing audiences.
It follows the same format as the generic Swap Listing event, but uses the
kind:30456instead.The following new tags are included:
"k", event kind being sponsored (required)"title", campaign title (optional)
It is required that at least one
signature spec(giveand/ortake) must have"type": "nostr"and also contain the following tag["sponsor", "<pubkey>", "<attestation>"]with the sponsor's public key and his signature over the signature spec without the sponsor tag as his attestation. This last requirement enables clients to disclose and/or filter sponsored events.Asset Swaps
This listing is designed for users looking for counterparties to swap different assets that can be transferred using Schnorr signatures, like any unit of Cashu tokens, Bitcoin or other asset IOUs issued using Taproot.
It follows the same format as the generic Swap Listing event, but uses the
kind:30457instead.It requires the following additional tags:
"t", asset pair to be swapped (e.g."btcusd")"t", asset being offered (e.g."btc")"t", accepted payment method (e.g."cashu","taproot")
Swap Negotiation
From finding an appropriate Swap Listing to publishing a Swap Proposal, there may be some kind of negotiation between the involved parties, e.g. agreeing on the amount to be paid by one of the parties or the exact content of a Nostr event signed by the other party. There are many ways to accomplish that and clients may implement it as they see fit for their specific goals. Some suggestions are:
- Adding
kind:1111Comments to the Swap Listing or an existing Swap Proposal - Exchanging tentative Swap Proposals back and forth until an agreement is reached
- Simple exchanges of DMs
- Out of band communication (e.g. Signal)
Work to be done
I've been refining this specification as I develop some proof-of-concept clients to experience its flaws and trade-offs in practice. I left the signature spec for Taproot signatures out of the current document as I still have to experiment with it. I will probably find some important orchestration issues related to dealing with
2-of-2 multisig timelocks, which also affects Cashu transactions when spent last, that may require further adjustments to what was presented here.The main goal of this article is to find other people interested in this concept and willing to provide valuable feedback before a PR is opened in the NIPs repository for broader discussions.
References
- GM Swap- Nostr client for atomically exchanging GM notes. Live demo available here.
- Sig4Sats Script - A Typescript script demonstrating the swap of a Cashu payment for a signed Nostr event.
- Loudr- Nostr client under development for sponsoring the publication of Nostr events. Live demo available at loudr.me.
- Poelstra, A. (2017). Scriptless Scripts. Blockstream Research. https://github.com/BlockstreamResearch/scriptless-scripts
-
 @ c631e267:c2b78d3e
2025-01-18 09:34:51
@ c631e267:c2b78d3e
2025-01-18 09:34:51Die grauenvollste Aussicht ist die der Technokratie – \ einer kontrollierenden Herrschaft, \ die durch verstümmelte und verstümmelnde Geister ausgeübt wird. \ Ernst Jünger
«Davos ist nicht mehr sexy», das Weltwirtschaftsforum (WEF) mache Davos kaputt, diese Aussagen eines Einheimischen las ich kürzlich in der Handelszeitung. Während sich einige vor Ort enorm an der «teuersten Gewerbeausstellung der Welt» bereicherten, würden die negativen Begleiterscheinungen wie Wohnungsnot und Niedergang der lokalen Wirtschaft immer deutlicher.
Nächsten Montag beginnt in dem Schweizer Bergdorf erneut ein Jahrestreffen dieses elitären Clubs der Konzerne, bei dem man mit hochrangigen Politikern aus aller Welt und ausgewählten Vertretern der Systemmedien zusammenhocken wird. Wie bereits in den vergangenen vier Jahren wird die Präsidentin der EU-Kommission, Ursula von der Leyen, in Begleitung von Klaus Schwab ihre Grundsatzansprache halten.
Der deutsche WEF-Gründer hatte bei dieser Gelegenheit immer höchst lobende Worte für seine Landsmännin: 2021 erklärte er sich «stolz, dass Europa wieder unter Ihrer Führung steht» und 2022 fand er es bemerkenswert, was sie erreicht habe angesichts des «erstaunlichen Wandels», den die Welt in den vorangegangenen zwei Jahren erlebt habe; es gebe nun einen «neuen europäischen Geist».
Von der Leyens Handeln während der sogenannten Corona-«Pandemie» lobte Schwab damals bereits ebenso, wie es diese Woche das Karlspreis-Direktorium tat, als man der Beschuldigten im Fall Pfizergate die diesjährige internationale Auszeichnung «für Verdienste um die europäische Einigung» verlieh. Außerdem habe sie die EU nicht nur gegen den «Aggressor Russland», sondern auch gegen die «innere Bedrohung durch Rassisten und Demagogen» sowie gegen den Klimawandel verteidigt.
Jene Herausforderungen durch «Krisen epochalen Ausmaßes» werden indes aus dem Umfeld des WEF nicht nur herbeigeredet – wie man alljährlich zur Zeit des Davoser Treffens im Global Risks Report nachlesen kann, der zusammen mit dem Versicherungskonzern Zurich erstellt wird. Seit die Globalisten 2020/21 in der Praxis gesehen haben, wie gut eine konzertierte und konsequente Angst-Kampagne funktionieren kann, geht es Schlag auf Schlag. Sie setzen alles daran, Schwabs goldenes Zeitfenster des «Great Reset» zu nutzen.
Ziel dieses «großen Umbruchs» ist die totale Kontrolle der Technokraten über die Menschen unter dem Deckmantel einer globalen Gesundheitsfürsorge. Wie aber könnte man so etwas erreichen? Ein Mittel dazu ist die «kreative Zerstörung». Weitere unabdingbare Werkzeug sind die Einbindung, ja Gleichschaltung der Medien und der Justiz.
Ein «Great Mental Reset» sei die Voraussetzung dafür, dass ein Großteil der Menschen Einschränkungen und Manipulationen wie durch die Corona-Maßnahmen praktisch kritik- und widerstandslos hinnehme, sagt der Mediziner und Molekulargenetiker Michael Nehls. Er meint damit eine regelrechte Umprogrammierung des Gehirns, wodurch nach und nach unsere Individualität und unser soziales Bewusstsein eliminiert und durch unreflektierten Konformismus ersetzt werden.
Der aktuelle Zustand unserer Gesellschaften ist auch für den Schweizer Rechtsanwalt Philipp Kruse alarmierend. Durch den Umgang mit der «Pandemie» sieht er die Grundlagen von Recht und Vernunft erschüttert, die Rechtsstaatlichkeit stehe auf dem Prüfstand. Seiner dringenden Mahnung an alle Bürger, die Prinzipien von Recht und Freiheit zu verteidigen, kann ich mich nur anschließen.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 91bea5cd:1df4451c
2025-04-15 06:27:28
@ 91bea5cd:1df4451c
2025-04-15 06:27:28Básico
bash lsblk # Lista todos os diretorios montados.Para criar o sistema de arquivos:
bash mkfs.btrfs -L "ThePool" -f /dev/sdxCriando um subvolume:
bash btrfs subvolume create SubVolMontando Sistema de Arquivos:
bash mount -o compress=zlib,subvol=SubVol,autodefrag /dev/sdx /mntLista os discos formatados no diretório:
bash btrfs filesystem show /mntAdiciona novo disco ao subvolume:
bash btrfs device add -f /dev/sdy /mntLista novamente os discos do subvolume:
bash btrfs filesystem show /mntExibe uso dos discos do subvolume:
bash btrfs filesystem df /mntBalancea os dados entre os discos sobre raid1:
bash btrfs filesystem balance start -dconvert=raid1 -mconvert=raid1 /mntScrub é uma passagem por todos os dados e metadados do sistema de arquivos e verifica as somas de verificação. Se uma cópia válida estiver disponível (perfis de grupo de blocos replicados), a danificada será reparada. Todas as cópias dos perfis replicados são validadas.
iniciar o processo de depuração :
bash btrfs scrub start /mntver o status do processo de depuração Btrfs em execução:
bash btrfs scrub status /mntver o status do scrub Btrfs para cada um dos dispositivos
bash btrfs scrub status -d / data btrfs scrub cancel / dataPara retomar o processo de depuração do Btrfs que você cancelou ou pausou:
btrfs scrub resume / data
Listando os subvolumes:
bash btrfs subvolume list /ReportsCriando um instantâneo dos subvolumes:
Aqui, estamos criando um instantâneo de leitura e gravação chamado snap de marketing do subvolume de marketing.
bash btrfs subvolume snapshot /Reports/marketing /Reports/marketing-snapAlém disso, você pode criar um instantâneo somente leitura usando o sinalizador -r conforme mostrado. O marketing-rosnap é um instantâneo somente leitura do subvolume de marketing
bash btrfs subvolume snapshot -r /Reports/marketing /Reports/marketing-rosnapForçar a sincronização do sistema de arquivos usando o utilitário 'sync'
Para forçar a sincronização do sistema de arquivos, invoque a opção de sincronização conforme mostrado. Observe que o sistema de arquivos já deve estar montado para que o processo de sincronização continue com sucesso.
bash btrfs filsystem sync /ReportsPara excluir o dispositivo do sistema de arquivos, use o comando device delete conforme mostrado.
bash btrfs device delete /dev/sdc /ReportsPara sondar o status de um scrub, use o comando scrub status com a opção -dR .
bash btrfs scrub status -dR / RelatóriosPara cancelar a execução do scrub, use o comando scrub cancel .
bash $ sudo btrfs scrub cancel / ReportsPara retomar ou continuar com uma depuração interrompida anteriormente, execute o comando de cancelamento de depuração
bash sudo btrfs scrub resume /Reportsmostra o uso do dispositivo de armazenamento:
btrfs filesystem usage /data
Para distribuir os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID (incluindo o dispositivo de armazenamento recém-adicionado) montados no diretório /data , execute o seguinte comando:
sudo btrfs balance start --full-balance /data
Pode demorar um pouco para espalhar os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID se ele contiver muitos dados.
Opções importantes de montagem Btrfs
Nesta seção, vou explicar algumas das importantes opções de montagem do Btrfs. Então vamos começar.
As opções de montagem Btrfs mais importantes são:
**1. acl e noacl
**ACL gerencia permissões de usuários e grupos para os arquivos/diretórios do sistema de arquivos Btrfs.
A opção de montagem acl Btrfs habilita ACL. Para desabilitar a ACL, você pode usar a opção de montagem noacl .
Por padrão, a ACL está habilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem acl por padrão.
**2. autodefrag e noautodefrag
**Desfragmentar um sistema de arquivos Btrfs melhorará o desempenho do sistema de arquivos reduzindo a fragmentação de dados.
A opção de montagem autodefrag permite a desfragmentação automática do sistema de arquivos Btrfs.
A opção de montagem noautodefrag desativa a desfragmentação automática do sistema de arquivos Btrfs.
Por padrão, a desfragmentação automática está desabilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem noautodefrag por padrão.
**3. compactar e compactar-forçar
**Controla a compactação de dados no nível do sistema de arquivos do sistema de arquivos Btrfs.
A opção compactar compacta apenas os arquivos que valem a pena compactar (se compactar o arquivo economizar espaço em disco).
A opção compress-force compacta todos os arquivos do sistema de arquivos Btrfs, mesmo que a compactação do arquivo aumente seu tamanho.
O sistema de arquivos Btrfs suporta muitos algoritmos de compactação e cada um dos algoritmos de compactação possui diferentes níveis de compactação.
Os algoritmos de compactação suportados pelo Btrfs são: lzo , zlib (nível 1 a 9) e zstd (nível 1 a 15).
Você pode especificar qual algoritmo de compactação usar para o sistema de arquivos Btrfs com uma das seguintes opções de montagem:
- compress=algoritmo:nível
- compress-force=algoritmo:nível
Para obter mais informações, consulte meu artigo Como habilitar a compactação do sistema de arquivos Btrfs .
**4. subvol e subvolid
**Estas opções de montagem são usadas para montar separadamente um subvolume específico de um sistema de arquivos Btrfs.
A opção de montagem subvol é usada para montar o subvolume de um sistema de arquivos Btrfs usando seu caminho relativo.
A opção de montagem subvolid é usada para montar o subvolume de um sistema de arquivos Btrfs usando o ID do subvolume.
Para obter mais informações, consulte meu artigo Como criar e montar subvolumes Btrfs .
**5. dispositivo
A opção de montagem de dispositivo** é usada no sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs.
Em alguns casos, o sistema operacional pode falhar ao detectar os dispositivos de armazenamento usados em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs. Nesses casos, você pode usar a opção de montagem do dispositivo para especificar os dispositivos que deseja usar para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar a opção de montagem de dispositivo várias vezes para carregar diferentes dispositivos de armazenamento para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar o nome do dispositivo (ou seja, sdb , sdc ) ou UUID , UUID_SUB ou PARTUUID do dispositivo de armazenamento com a opção de montagem do dispositivo para identificar o dispositivo de armazenamento.
Por exemplo,
- dispositivo=/dev/sdb
- dispositivo=/dev/sdb,dispositivo=/dev/sdc
- dispositivo=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d
- device=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d,device=UUID_SUB=f7ce4875-0874-436a-b47d-3edef66d3424
**6. degraded
A opção de montagem degradada** permite que um RAID Btrfs seja montado com menos dispositivos de armazenamento do que o perfil RAID requer.
Por exemplo, o perfil raid1 requer a presença de 2 dispositivos de armazenamento. Se um dos dispositivos de armazenamento não estiver disponível em qualquer caso, você usa a opção de montagem degradada para montar o RAID mesmo que 1 de 2 dispositivos de armazenamento esteja disponível.
**7. commit
A opção commit** mount é usada para definir o intervalo (em segundos) dentro do qual os dados serão gravados no dispositivo de armazenamento.
O padrão é definido como 30 segundos.
Para definir o intervalo de confirmação para 15 segundos, você pode usar a opção de montagem commit=15 (digamos).
**8. ssd e nossd
A opção de montagem ssd** informa ao sistema de arquivos Btrfs que o sistema de arquivos está usando um dispositivo de armazenamento SSD, e o sistema de arquivos Btrfs faz a otimização SSD necessária.
A opção de montagem nossd desativa a otimização do SSD.
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem de SSD será habilitada. Caso contrário, a opção de montagem nossd é habilitada.
**9. ssd_spread e nossd_spread
A opção de montagem ssd_spread** tenta alocar grandes blocos contínuos de espaço não utilizado do SSD. Esse recurso melhora o desempenho de SSDs de baixo custo (baratos).
A opção de montagem nossd_spread desativa o recurso ssd_spread .
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem ssd_spread será habilitada. Caso contrário, a opção de montagem nossd_spread é habilitada.
**10. descarte e nodiscard
Se você estiver usando um SSD que suporte TRIM enfileirado assíncrono (SATA rev3.1), a opção de montagem de descarte** permitirá o descarte de blocos de arquivos liberados. Isso melhorará o desempenho do SSD.
Se o SSD não suportar TRIM enfileirado assíncrono, a opção de montagem de descarte prejudicará o desempenho do SSD. Nesse caso, a opção de montagem nodiscard deve ser usada.
Por padrão, a opção de montagem nodiscard é usada.
**11. norecovery
Se a opção de montagem norecovery** for usada, o sistema de arquivos Btrfs não tentará executar a operação de recuperação de dados no momento da montagem.
**12. usebackuproot e nousebackuproot
Se a opção de montagem usebackuproot for usada, o sistema de arquivos Btrfs tentará recuperar qualquer raiz de árvore ruim/corrompida no momento da montagem. O sistema de arquivos Btrfs pode armazenar várias raízes de árvore no sistema de arquivos. A opção de montagem usebackuproot** procurará uma boa raiz de árvore e usará a primeira boa que encontrar.
A opção de montagem nousebackuproot não verificará ou recuperará raízes de árvore inválidas/corrompidas no momento da montagem. Este é o comportamento padrão do sistema de arquivos Btrfs.
**13. space_cache, space_cache=version, nospace_cache e clear_cache
A opção de montagem space_cache** é usada para controlar o cache de espaço livre. O cache de espaço livre é usado para melhorar o desempenho da leitura do espaço livre do grupo de blocos do sistema de arquivos Btrfs na memória (RAM).
O sistema de arquivos Btrfs suporta 2 versões do cache de espaço livre: v1 (padrão) e v2
O mecanismo de cache de espaço livre v2 melhora o desempenho de sistemas de arquivos grandes (tamanho de vários terabytes).
Você pode usar a opção de montagem space_cache=v1 para definir a v1 do cache de espaço livre e a opção de montagem space_cache=v2 para definir a v2 do cache de espaço livre.
A opção de montagem clear_cache é usada para limpar o cache de espaço livre.
Quando o cache de espaço livre v2 é criado, o cache deve ser limpo para criar um cache de espaço livre v1 .
Portanto, para usar o cache de espaço livre v1 após a criação do cache de espaço livre v2 , as opções de montagem clear_cache e space_cache=v1 devem ser combinadas: clear_cache,space_cache=v1
A opção de montagem nospace_cache é usada para desabilitar o cache de espaço livre.
Para desabilitar o cache de espaço livre após a criação do cache v1 ou v2 , as opções de montagem nospace_cache e clear_cache devem ser combinadas: clear_cache,nosapce_cache
**14. skip_balance
Por padrão, a operação de balanceamento interrompida/pausada de um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs será retomada automaticamente assim que o sistema de arquivos Btrfs for montado. Para desabilitar a retomada automática da operação de equilíbrio interrompido/pausado em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs, você pode usar a opção de montagem skip_balance .**
**15. datacow e nodatacow
A opção datacow** mount habilita o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs. É o comportamento padrão.
Se você deseja desabilitar o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs para os arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatacow .
**16. datasum e nodatasum
A opção datasum** mount habilita a soma de verificação de dados para arquivos recém-criados do sistema de arquivos Btrfs. Este é o comportamento padrão.
Se você não quiser que o sistema de arquivos Btrfs faça a soma de verificação dos dados dos arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatasum .
Perfis Btrfs
Um perfil Btrfs é usado para informar ao sistema de arquivos Btrfs quantas cópias dos dados/metadados devem ser mantidas e quais níveis de RAID devem ser usados para os dados/metadados. O sistema de arquivos Btrfs contém muitos perfis. Entendê-los o ajudará a configurar um RAID Btrfs da maneira que você deseja.
Os perfis Btrfs disponíveis são os seguintes:
single : Se o perfil único for usado para os dados/metadados, apenas uma cópia dos dados/metadados será armazenada no sistema de arquivos, mesmo se você adicionar vários dispositivos de armazenamento ao sistema de arquivos. Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
dup : Se o perfil dup for usado para os dados/metadados, cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos manterá duas cópias dos dados/metadados. Assim, 50% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
raid0 : No perfil raid0 , os dados/metadados serão divididos igualmente em todos os dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, não haverá dados/metadados redundantes (duplicados). Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser usado. Se, em qualquer caso, um dos dispositivos de armazenamento falhar, todo o sistema de arquivos será corrompido. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid0 .
raid1 : No perfil raid1 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a uma falha de unidade. Mas você pode usar apenas 50% do espaço total em disco. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1 .
raid1c3 : No perfil raid1c3 , três cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a duas falhas de unidade, mas você pode usar apenas 33% do espaço total em disco. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c3 .
raid1c4 : No perfil raid1c4 , quatro cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a três falhas de unidade, mas você pode usar apenas 25% do espaço total em disco. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c4 .
raid10 : No perfil raid10 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos, como no perfil raid1 . Além disso, os dados/metadados serão divididos entre os dispositivos de armazenamento, como no perfil raid0 .
O perfil raid10 é um híbrido dos perfis raid1 e raid0 . Alguns dos dispositivos de armazenamento formam arrays raid1 e alguns desses arrays raid1 são usados para formar um array raid0 . Em uma configuração raid10 , o sistema de arquivos pode sobreviver a uma única falha de unidade em cada uma das matrizes raid1 .
Você pode usar 50% do espaço total em disco na configuração raid10 . Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid10 .
raid5 : No perfil raid5 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Uma única paridade será calculada e distribuída entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid5 , o sistema de arquivos pode sobreviver a uma única falha de unidade. Se uma unidade falhar, você pode adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir da paridade distribuída das unidades em execução.
Você pode usar 1 00x(N-1)/N % do total de espaços em disco na configuração raid5 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid5 .
raid6 : No perfil raid6 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Duas paridades serão calculadas e distribuídas entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid6 , o sistema de arquivos pode sobreviver a duas falhas de unidade ao mesmo tempo. Se uma unidade falhar, você poderá adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir das duas paridades distribuídas das unidades em execução.
Você pode usar 100x(N-2)/N % do espaço total em disco na configuração raid6 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid6 .
-
 @ a95c6243:d345522c
2025-01-13 10:09:57
@ a95c6243:d345522c
2025-01-13 10:09:57Ich begann, Social Media aufzubauen, \ um den Menschen eine Stimme zu geben. \ Mark Zuckerberg
Sind euch auch die Tränen gekommen, als ihr Mark Zuckerbergs Wendehals-Deklaration bezüglich der Meinungsfreiheit auf seinen Portalen gehört habt? Rührend, oder? Während er früher die offensichtliche Zensur leugnete und später die Regierung Biden dafür verantwortlich machte, will er nun angeblich «die Zensur auf unseren Plattformen drastisch reduzieren».
«Purer Opportunismus» ob des anstehenden Regierungswechsels wäre als Klassifizierung viel zu kurz gegriffen. Der jetzige Schachzug des Meta-Chefs ist genauso Teil einer kühl kalkulierten Business-Strategie, wie es die 180 Grad umgekehrte Praxis vorher war. Social Media sind ein höchst lukratives Geschäft. Hinzu kommt vielleicht noch ein bisschen verkorkstes Ego, weil derartig viel Einfluss und Geld sicher auch auf die Psyche schlagen. Verständlich.
«Es ist an der Zeit, zu unseren Wurzeln der freien Meinungsäußerung auf Facebook und Instagram zurückzukehren. Ich begann, Social Media aufzubauen, um den Menschen eine Stimme zu geben», sagte Zuckerberg.
Welche Wurzeln? Hat der Mann vergessen, dass er von der Überwachung, dem Ausspionieren und dem Ausverkauf sämtlicher Daten und digitaler Spuren sowie der Manipulation seiner «Kunden» lebt? Das ist knallharter Kommerz, nichts anderes. Um freie Meinungsäußerung geht es bei diesem Geschäft ganz sicher nicht, und das war auch noch nie so. Die Wurzeln von Facebook liegen in einem Projekt des US-Militärs mit dem Namen «LifeLog». Dessen Ziel war es, «ein digitales Protokoll vom Leben eines Menschen zu erstellen».
Der Richtungswechsel kommt allerdings nicht überraschend. Schon Anfang Dezember hatte Meta-Präsident Nick Clegg von «zu hoher Fehlerquote bei der Moderation» von Inhalten gesprochen. Bei der Gelegenheit erwähnte er auch, dass Mark sehr daran interessiert sei, eine aktive Rolle in den Debatten über eine amerikanische Führungsrolle im technologischen Bereich zu spielen.
Während Milliardärskollege und Big Tech-Konkurrent Elon Musk bereits seinen Posten in der kommenden Trump-Regierung in Aussicht hat, möchte Zuckerberg also nicht nur seine Haut retten – Trump hatte ihn einmal einen «Feind des Volkes» genannt und ihm lebenslange Haft angedroht –, sondern am liebsten auch mitspielen. KI-Berater ist wohl die gewünschte Funktion, wie man nach einem Treffen Trump-Zuckerberg hörte. An seine Verhaftung dachte vermutlich auch ein weiterer Multimilliardär mit eigener Social Media-Plattform, Pavel Durov, als er Zuckerberg jetzt kritisierte und gleichzeitig warnte.
Politik und Systemmedien drehen jedenfalls durch – was zu viel ist, ist zu viel. Etwas weniger Zensur und mehr Meinungsfreiheit würden die Freiheit der Bürger schwächen und seien potenziell vernichtend für die Menschenrechte. Zuckerberg setze mit dem neuen Kurs die Demokratie aufs Spiel, das sei eine «Einladung zum nächsten Völkermord», ernsthaft. Die Frage sei, ob sich die EU gegen Musk und Zuckerberg behaupten könne, Brüssel müsse jedenfalls hart durchgreifen.
Auch um die Faktenchecker macht man sich Sorgen. Für die deutsche Nachrichtenagentur dpa und die «Experten» von Correctiv, die (noch) Partner für Fact-Checking-Aktivitäten von Facebook sind, sei das ein «lukratives Geschäftsmodell». Aber möglicherweise werden die Inhalte ohne diese vermeintlichen Korrektoren ja sogar besser. Anders als Meta wollen jedoch Scholz, Faeser und die Tagesschau keine Fehler zugeben und zum Beispiel Correctiv-Falschaussagen einräumen.
Bei derlei dramatischen Befürchtungen wundert es nicht, dass der öffentliche Plausch auf X zwischen Elon Musk und AfD-Chefin Alice Weidel von 150 EU-Beamten überwacht wurde, falls es irgendwelche Rechtsverstöße geben sollte, die man ihnen ankreiden könnte. Auch der Deutsche Bundestag war wachsam. Gefunden haben dürften sie nichts. Das Ganze war eher eine Show, viel Wind wurde gemacht, aber letztlich gab es nichts als heiße Luft.
Das Anbiedern bei Donald Trump ist indes gerade in Mode. Die Weltgesundheitsorganisation (WHO) tut das auch, denn sie fürchtet um Spenden von über einer Milliarde Dollar. Eventuell könnte ja Elon Musk auch hier künftig aushelfen und der Organisation sowie deren größtem privaten Förderer, Bill Gates, etwas unter die Arme greifen. Nachdem Musks KI-Projekt xAI kürzlich von BlackRock & Co. sechs Milliarden eingestrichen hat, geht da vielleicht etwas.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ c066aac5:6a41a034
2025-04-05 16:58:58
@ c066aac5:6a41a034
2025-04-05 16:58:58I’m drawn to extremities in art. The louder, the bolder, the more outrageous, the better. Bold art takes me out of the mundane into a whole new world where anything and everything is possible. Having grown up in the safety of the suburban midwest, I was a bit of a rebellious soul in search of the satiation that only came from the consumption of the outrageous. My inclination to find bold art draws me to NOSTR, because I believe NOSTR can be the place where the next generation of artistic pioneers go to express themselves. I also believe that as much as we are able, were should invite them to come create here.
My Background: A Small Side Story
My father was a professional gamer in the 80s, back when there was no money or glory in the avocation. He did get a bit of spotlight though after the fact: in the mid 2000’s there were a few parties making documentaries about that era of gaming as well as current arcade events (namely 2007’sChasing GhostsandThe King of Kong: A Fistful of Quarters). As a result of these documentaries, there was a revival in the arcade gaming scene. My family attended events related to the documentaries or arcade gaming and I became exposed to a lot of things I wouldn’t have been able to find. The producer ofThe King of Kong: A Fistful of Quarters had previously made a documentary calledNew York Dollwhich was centered around the life of bassist Arthur Kane. My 12 year old mind was blown: The New York Dolls were a glam-punk sensation dressed in drag. The music was from another planet. Johnny Thunders’ guitar playing was like Chuck Berry with more distortion and less filter. Later on I got to meet the Galaga record holder at the time, Phil Day, in Ottumwa Iowa. Phil is an Australian man of high intellect and good taste. He exposed me to great creators such as Nick Cave & The Bad Seeds, Shakespeare, Lou Reed, artists who created things that I had previously found inconceivable.
I believe this time period informed my current tastes and interests, but regrettably I think it also put coals on the fire of rebellion within. I stopped taking my parents and siblings seriously, the Christian faith of my family (which I now hold dearly to) seemed like a mundane sham, and I felt I couldn’t fit in with most people because of my avant-garde tastes. So I write this with the caveat that there should be a way to encourage these tastes in children without letting them walk down the wrong path. There is nothing inherently wrong with bold art, but I’d advise parents to carefully find ways to cultivate their children’s tastes without completely shutting them down and pushing them away as a result. My parents were very loving and patient during this time; I thank God for that.
With that out of the way, lets dive in to some bold artists:
Nicolas Cage: Actor
There is an excellent video by Wisecrack on Nicolas Cage that explains him better than I will, which I will linkhere. Nicolas Cage rejects the idea that good acting is tied to mere realism; all of his larger than life acting decisions are deliberate choices. When that clicked for me, I immediately realized the man is a genius. He borrows from Kabuki and German Expressionism, art forms that rely on exaggeration to get the message across. He has even created his own acting style, which he calls Nouveau Shamanic. He augments his imagination to go from acting to being. Rather than using the old hat of method acting, he transports himself to a new world mentally. The projects he chooses to partake in are based on his own interests or what he considers would be a challenge (making a bad script good for example). Thus it doesn’t matter how the end result comes out; he has already achieved his goal as an artist. Because of this and because certain directors don’t know how to use his talents, he has a noticeable amount of duds in his filmography. Dig around the duds, you’ll find some pure gold. I’d personally recommend the filmsPig, Joe, Renfield, and his Christmas film The Family Man.
Nick Cave: Songwriter
What a wild career this man has had! From the apocalyptic mayhem of his band The Birthday Party to the pensive atmosphere of his albumGhosteen, it seems like Nick Cave has tried everything. I think his secret sauce is that he’s always working. He maintains an excellent newsletter calledThe Red Hand Files, he has written screenplays such asLawless, he has written books, he has made great film scores such asThe Assassination of Jesse James by the Coward Robert Ford, the man is religiously prolific. I believe that one of the reasons he is prolific is that he’s not afraid to experiment. If he has an idea, he follows it through to completion. From the albumMurder Ballads(which is comprised of what the title suggests) to his rejected sequel toGladiator(Gladiator: Christ Killer), he doesn’t seem to be afraid to take anything on. This has led to some over the top works as well as some deeply personal works. Albums likeSkeleton TreeandGhosteenwere journeys through the grief of his son’s death. The Boatman’s Callis arguably a better break-up album than anything Taylor Swift has put out. He’s not afraid to be outrageous, he’s not afraid to offend, but most importantly he’s not afraid to be himself. Works I’d recommend include The Birthday Party’sLive 1981-82, Nick Cave & The Bad Seeds’The Boatman’s Call, and the filmLawless.
Jim Jarmusch: Director
I consider Jim’s films to be bold almost in an ironic sense: his works are bold in that they are, for the most part, anti-sensational. He has a rule that if his screenplays are criticized for a lack of action, he makes them even less eventful. Even with sensational settings his films feel very close to reality, and they demonstrate the beauty of everyday life. That's what is bold about his art to me: making the sensational grounded in reality while making everyday reality all the more special. Ghost Dog: The Way of the Samurai is about a modern-day African-American hitman who strictly follows the rules of the ancient Samurai, yet one can resonate with the humanity of a seemingly absurd character. Only Lovers Left Aliveis a vampire love story, but in the middle of a vampire romance one can see their their own relationships in a new deeply human light. Jim’s work reminds me that art reflects life, and that there is sacred beauty in seemingly mundane everyday life. I personally recommend his filmsPaterson,Down by Law, andCoffee and Cigarettes.
NOSTR: We Need Bold Art
NOSTR is in my opinion a path to a better future. In a world creeping slowly towards everything apps, I hope that the protocol where the individual owns their data wins over everything else. I love freedom and sovereignty. If NOSTR is going to win the race of everything apps, we need more than Bitcoin content. We need more than shirtless bros paying for bananas in foreign countries and exercising with girls who have seductive accents. Common people cannot see themselves in such a world. NOSTR needs to catch the attention of everyday people. I don’t believe that this can be accomplished merely by introducing more broadly relevant content; people are searching for content that speaks to them. I believe that NOSTR can and should attract artists of all kinds because NOSTR is one of the few places on the internet where artists can express themselves fearlessly. Getting zaps from NOSTR’s value-for-value ecosystem has far less friction than crowdfunding a creative project or pitching investors that will irreversibly modify an artist’s vision. Having a place where one can post their works without fear of censorship should be extremely enticing. Having a place where one can connect with fellow humans directly as opposed to a sea of bots should seem like the obvious solution. If NOSTR can become a safe haven for artists to express themselves and spread their work, I believe that everyday people will follow. The banker whose stressful job weighs on them will suddenly find joy with an original meme made by a great visual comedian. The programmer for a healthcare company who is drowning in hopeless mundanity could suddenly find a new lust for life by hearing the song of a musician who isn’t afraid to crowdfund their their next project by putting their lighting address on the streets of the internet. The excel guru who loves independent film may find that NOSTR is the best way to support non corporate movies. My closing statement: continue to encourage the artists in your life as I’m sure you have been, but while you’re at it give them the purple pill. You may very well be a part of building a better future.
-
 @ a95c6243:d345522c
2025-01-03 20:26:47
@ a95c6243:d345522c
2025-01-03 20:26:47Was du bist hängt von drei Faktoren ab: \ Was du geerbt hast, \ was deine Umgebung aus dir machte \ und was du in freier Wahl \ aus deiner Umgebung und deinem Erbe gemacht hast. \ Aldous Huxley
Das brave Mitmachen und Mitlaufen in einem vorgegebenen, recht engen Rahmen ist gewiss nicht neu, hat aber gerade wieder mal Konjunktur. Dies kann man deutlich beobachten, eigentlich egal, in welchem gesellschaftlichen Bereich man sich umschaut. Individualität ist nur soweit angesagt, wie sie in ein bestimmtes Schema von «Diversität» passt, und Freiheit verkommt zur Worthülse – nicht erst durch ein gewisses Buch einer gewissen ehemaligen Regierungschefin.
Erklärungsansätze für solche Entwicklungen sind bekannt, und praktisch alle haben etwas mit Massenpsychologie zu tun. Der Herdentrieb, also der Trieb der Menschen, sich – zum Beispiel aus Unsicherheit oder Bequemlichkeit – lieber der Masse anzuschließen als selbstständig zu denken und zu handeln, ist einer der Erklärungsversuche. Andere drehen sich um Macht, Propaganda, Druck und Angst, also den gezielten Einsatz psychologischer Herrschaftsinstrumente.
Aber wollen die Menschen überhaupt Freiheit? Durch Gespräche im privaten Umfeld bin ich diesbezüglich in der letzten Zeit etwas skeptisch geworden. Um die Jahreswende philosophiert man ja gerne ein wenig über das Erlebte und über die Erwartungen für die Zukunft. Dabei hatte ich hin und wieder den Eindruck, die totalitären Anwandlungen unserer «Repräsentanten» kämen manchen Leuten gerade recht.
«Desinformation» ist so ein brisantes Thema. Davor müsse man die Menschen doch schützen, hörte ich. Jemand müsse doch zum Beispiel diese ganzen merkwürdigen Inhalte in den Social Media filtern – zur Ukraine, zum Klima, zu Gesundheitsthemen oder zur Migration. Viele wüssten ja gar nicht einzuschätzen, was richtig und was falsch ist, sie bräuchten eine Führung.
Freiheit bedingt Eigenverantwortung, ohne Zweifel. Eventuell ist es einigen tatsächlich zu anspruchsvoll, die Verantwortung für das eigene Tun und Lassen zu übernehmen. Oder die persönliche Freiheit wird nicht als ausreichend wertvolles Gut angesehen, um sich dafür anzustrengen. In dem Fall wäre die mangelnde Selbstbestimmung wohl das kleinere Übel. Allerdings fehlt dann gemäß Aldous Huxley ein Teil der Persönlichkeit. Letztlich ist natürlich alles eine Frage der Abwägung.
Sind viele Menschen möglicherweise schon so «eingenordet», dass freiheitliche Ambitionen gar nicht für eine ganze Gruppe, ein Kollektiv, verfolgt werden können? Solche Gedanken kamen mir auch, als ich mir kürzlich diverse Talks beim viertägigen Hacker-Kongress des Chaos Computer Clubs (38C3) anschaute. Ich war nicht nur überrascht, sondern reichlich erschreckt angesichts der in weiten Teilen mainstream-geformten Inhalte, mit denen ein dankbares Publikum beglückt wurde. Wo ich allgemein hellere Köpfe erwartet hatte, fand ich Konformismus und enthusiastisch untermauerte Narrative.
Gibt es vielleicht so etwas wie eine Herdenimmunität gegen Indoktrination? Ich denke, ja, zumindest eine gestärkte Widerstandsfähigkeit. Was wir brauchen, sind etwas gesunder Menschenverstand, offene Informationskanäle und der Mut, sich freier auch zwischen den Herden zu bewegen. Sie tun das bereits, aber sagen Sie es auch dieses Jahr ruhig weiter.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ ec9bd746:df11a9d0
2025-04-06 08:06:08
@ ec9bd746:df11a9d0
2025-04-06 08:06:08🌍 Time Window:
🕘 When: Every even week on Sunday at 9:00 PM CET
🗺️ Where: https://cornychat.com/eurocornStart: 21:00 CET (Prague, UTC+1)
End: approx. 02:00 CET (Prague, UTC+1, next day)
Duration: usually 5+ hours.| Region | Local Time Window | Convenience Level | |-----------------------------------------------------|--------------------------------------------|---------------------------------------------------------| | Europe (CET, Prague) 🇨🇿🇩🇪 | 21:00–02:00 CET | ✅ Very Good; evening & night | | East Coast North America (EST) 🇺🇸🇨🇦 | 15:00–20:00 EST | ✅ Very Good; afternoon & early evening | | West Coast North America (PST) 🇺🇸🇨🇦 | 12:00–17:00 PST | ✅ Very Good; midday & afternoon | | Central America (CST) 🇲🇽🇨🇷🇬🇹 | 14:00–19:00 CST | ✅ Very Good; afternoon & evening | | South America West (Peru/Colombia PET/COT) 🇵🇪🇨🇴 | 15:00–20:00 PET/COT | ✅ Very Good; afternoon & evening | | South America East (Brazil/Argentina/Chile, BRT/ART/CLST) 🇧🇷🇦🇷🇨🇱 | 17:00–22:00 BRT/ART/CLST | ✅ Very Good; early evening | | United Kingdom/Ireland (GMT) 🇬🇧🇮🇪 | 20:00–01:00 GMT | ✅ Very Good; evening hours (midnight convenient) | | Eastern Europe (EET) 🇷🇴🇬🇷🇺🇦 | 22:00–03:00 EET | ✅ Good; late evening & early night (slightly late) | | Africa (South Africa, SAST) 🇿🇦 | 22:00–03:00 SAST | ✅ Good; late evening & overnight (late-night common) | | New Zealand (NZDT) 🇳🇿 | 09:00–14:00 NZDT (next day) | ✅ Good; weekday morning & afternoon | | Australia (AEDT, Sydney) 🇦🇺 | 07:00–12:00 AEDT (next day) | ✅ Good; weekday morning to noon | | East Africa (Kenya, EAT) 🇰🇪 | 23:00–04:00 EAT | ⚠️ Slightly late (night hours; late night common) | | Russia (Moscow, MSK) 🇷🇺 | 23:00–04:00 MSK | ⚠️ Slightly late (join at start is fine, very late night) | | Middle East (UAE, GST) 🇦🇪🇴🇲 | 00:00–05:00 GST (next day) | ⚠️ Late night start (midnight & early morning, but shorter attendance plausible)| | Japan/Korea (JST/KST) 🇯🇵🇰🇷 | 05:00–10:00 JST/KST (next day) | ⚠️ Early; convenient joining from ~07:00 onwards possible | | China (Beijing, CST) 🇨🇳 | 04:00–09:00 CST (next day) | ❌ Challenging; very early morning start (better ~07:00 onwards) | | India (IST) 🇮🇳 | 01:30–06:30 IST (next day) | ❌ Very challenging; overnight timing typically difficult|
-
 @ dbc27e2e:b1dd0b0b
2025-04-05 20:44:00
@ dbc27e2e:b1dd0b0b
2025-04-05 20:44:00This method focuses on the amount of water in the first pour, which ultimately defines the coffee’s acidity and sweetness (more water = more acidity, less water = more sweetness). For the remainder of the brew, the water is divided into equal parts according to the strength you wish to attain.

Dose:
20g coffee (Coarse ground coffee) 300mL water (92°C / 197.6°F) Time: 3:30Instructions:
- Pour 1: 0:00 > 50mL (42% of 120mL = 40% of total – less water in the ratio, targeting sweetness.)
- Pour 2: 0:45 > 70mL (58% of 120mL = 40% of total – the top up for 40% of total.)
- Pour 3: 1:30 > 60mL (The remaining water is 180mL / 3 pours = 60mL per pour)
- Pour 4: 2:10 > 60mL
- Pour 5: 2:40 > 60mL
- Remove the V60 at 3:30
-
 @ a95c6243:d345522c
2025-01-01 17:39:51
@ a95c6243:d345522c
2025-01-01 17:39:51Heute möchte ich ein Gedicht mit euch teilen. Es handelt sich um eine Ballade des österreichischen Lyrikers Johann Gabriel Seidl aus dem 19. Jahrhundert. Mir sind diese Worte fest in Erinnerung, da meine Mutter sie perfekt rezitieren konnte, auch als die Kräfte schon langsam schwanden.
Dem originalen Titel «Die Uhr» habe ich für mich immer das Wort «innere» hinzugefügt. Denn der Zeitmesser – hier vermutliche eine Taschenuhr – symbolisiert zwar in dem Kontext das damalige Zeitempfinden und die Umbrüche durch die industrielle Revolution, sozusagen den Zeitgeist und das moderne Leben. Aber der Autor setzt sich philosophisch mit der Zeit auseinander und gibt seinem Werk auch eine klar spirituelle Dimension.
Das Ticken der Uhr und die Momente des Glücks und der Trauer stehen sinnbildlich für das unaufhaltsame Fortschreiten und die Vergänglichkeit des Lebens. Insofern könnte man bei der Uhr auch an eine Sonnenuhr denken. Der Rhythmus der Ereignisse passt uns vielleicht nicht immer in den Kram.
Was den Takt pocht, ist durchaus auch das Herz, unser «inneres Uhrwerk». Wenn dieses Meisterwerk einmal stillsteht, ist es unweigerlich um uns geschehen. Hoffentlich können wir dann dankbar sagen: «Ich habe mein Bestes gegeben.»
Ich trage, wo ich gehe, stets eine Uhr bei mir; \ Wieviel es geschlagen habe, genau seh ich an ihr. \ Es ist ein großer Meister, der künstlich ihr Werk gefügt, \ Wenngleich ihr Gang nicht immer dem törichten Wunsche genügt.
Ich wollte, sie wäre rascher gegangen an manchem Tag; \ Ich wollte, sie hätte manchmal verzögert den raschen Schlag. \ In meinen Leiden und Freuden, in Sturm und in der Ruh, \ Was immer geschah im Leben, sie pochte den Takt dazu.
Sie schlug am Sarge des Vaters, sie schlug an des Freundes Bahr, \ Sie schlug am Morgen der Liebe, sie schlug am Traualtar. \ Sie schlug an der Wiege des Kindes, sie schlägt, will's Gott, noch oft, \ Wenn bessere Tage kommen, wie meine Seele es hofft.
Und ward sie auch einmal träger, und drohte zu stocken ihr Lauf, \ So zog der Meister immer großmütig sie wieder auf. \ Doch stände sie einmal stille, dann wär's um sie geschehn, \ Kein andrer, als der sie fügte, bringt die Zerstörte zum Gehn.
Dann müßt ich zum Meister wandern, der wohnt am Ende wohl weit, \ Wohl draußen, jenseits der Erde, wohl dort in der Ewigkeit! \ Dann gäb ich sie ihm zurücke mit dankbar kindlichem Flehn: \ Sieh, Herr, ich hab nichts verdorben, sie blieb von selber stehn.
Johann Gabriel Seidl (1804-1875)
-
 @ a95c6243:d345522c
2024-12-21 09:54:49
@ a95c6243:d345522c
2024-12-21 09:54:49Falls du beim Lesen des Titels dieses Newsletters unwillkürlich an positive Neuigkeiten aus dem globalen polit-medialen Irrenhaus oder gar aus dem wirtschaftlichen Umfeld gedacht hast, darf ich dich beglückwünschen. Diese Assoziation ist sehr löblich, denn sie weist dich als unverbesserlichen Optimisten aus. Leider muss ich dich diesbezüglich aber enttäuschen. Es geht hier um ein anderes Thema, allerdings sehr wohl ein positives, wie ich finde.
Heute ist ein ganz besonderer Tag: die Wintersonnenwende. Genau gesagt hat heute morgen um 10:20 Uhr Mitteleuropäischer Zeit (MEZ) auf der Nordhalbkugel unseres Planeten der astronomische Winter begonnen. Was daran so außergewöhnlich ist? Der kürzeste Tag des Jahres war gestern, seit heute werden die Tage bereits wieder länger! Wir werden also jetzt jeden Tag ein wenig mehr Licht haben.
Für mich ist dieses Ereignis immer wieder etwas kurios: Es beginnt der Winter, aber die Tage werden länger. Das erscheint mir zunächst wie ein Widerspruch, denn meine spontanen Assoziationen zum Winter sind doch eher Kälte und Dunkelheit, relativ zumindest. Umso erfreulicher ist der emotionale Effekt, wenn dann langsam die Erkenntnis durchsickert: Ab jetzt wird es schon wieder heller!
Natürlich ist es kalt im Winter, mancherorts mehr als anderswo. Vielleicht jedoch nicht mehr lange, wenn man den Klimahysterikern glauben wollte. Mindestens letztes Jahr hat Väterchen Frost allerdings gleich zu Beginn seiner Saison – und passenderweise während des globalen Überhitzungsgipfels in Dubai – nochmal richtig mit der Faust auf den Tisch gehauen. Schnee- und Eischaos sind ja eigentlich in der Agenda bereits nicht mehr vorgesehen. Deswegen war man in Deutschland vermutlich in vorauseilendem Gehorsam schon nicht mehr darauf vorbereitet und wurde glatt lahmgelegt.
Aber ich schweife ab. Die Aussicht auf nach und nach mehr Licht und damit auch Wärme stimmt mich froh. Den Zusammenhang zwischen beidem merkt man in Andalusien sehr deutlich. Hier, wo die Häuser im Winter arg auskühlen, geht man zum Aufwärmen raus auf die Straße oder auf den Balkon. Die Sonne hat auch im Winter eine erfreuliche Kraft. Und da ist jede Minute Gold wert.
Außerdem ist mir vor Jahren so richtig klar geworden, warum mir das südliche Klima so sehr gefällt. Das liegt nämlich nicht nur an der Sonne als solcher, oder der Wärme – das liegt vor allem am Licht. Ohne Licht keine Farben, das ist der ebenso simple wie gewaltige Unterschied zwischen einem deprimierenden matschgraubraunen Winter und einem fröhlichen bunten. Ein großes Stück Lebensqualität.
Mir gefällt aber auch die Symbolik dieses Tages: Licht aus der Dunkelheit, ein Wendepunkt, ein Neuanfang, neue Möglichkeiten, Übergang zu neuer Aktivität. In der winterlichen Stille keimt bereits neue Lebendigkeit. Und zwar in einem Zyklus, das wird immer wieder so geschehen. Ich nehme das gern als ein Stück Motivation, es macht mir Hoffnung und gibt mir Energie.

Übrigens ist parallel am heutigen Tag auf der südlichen Halbkugel Sommeranfang. Genau im entgegengesetzten Rhythmus, sich ergänzend, wie Yin und Yang. Das alles liegt an der Schrägstellung der Erdachse, die ist nämlich um 23,4º zur Umlaufbahn um die Sonne geneigt. Wir erinnern uns, gell?
Insofern bleibt eindeutig festzuhalten, dass “schräg sein” ein willkommener, wichtiger und positiver Wert ist. Mit anderen Worten: auch ungewöhnlich, eigenartig, untypisch, wunderlich, kauzig, … ja sogar irre, spinnert oder gar “quer” ist in Ordnung. Das schließt das Denken mit ein.
In diesem Sinne wünsche ich euch allen urige Weihnachtstage!
Dieser Beitrag ist letztes Jahr in meiner Denkbar erschienen.
-
 @ 04c915da:3dfbecc9
2025-03-26 20:54:33
@ 04c915da:3dfbecc9
2025-03-26 20:54:33Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all.
That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission.
As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently.
Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive.
Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally.
The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match.
When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol.
Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
-
 @ 866e0139:6a9334e5
2025-04-05 11:00:25
@ 866e0139:6a9334e5
2025-04-05 11:00:25
Autor: CJ Hopkins. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier.**
Dieser Beitrag erschien zuerst auf dem Substack-Blog des Autors.
Er soll andauern, was er auch tut. Genau wie der nie endende Krieg in Orwells 1984 wird er vom Imperium gegen seine eigenen Untertanen geführt, aber nicht nur, um die Struktur der Gesellschaft intakt zu halten, sondern in unserem Fall auch, um die Gesellschaft in eine neo-totalitäre global-kapitalistische Dystopie zu verwandeln.
Bist du nicht vertraut mit dem Krieg gegen was auch immer?
Nun ja, okay, du erinnerst dich an den Krieg gegen den Terror.
Du erinnerst dich daran, als die „Freiheit und Demokratie“ von „den Terroristen“ angegriffen wurden und wir keine andere Wahl hatten, als uns unserer demokratischen Rechte und Prinzipien zu entledigen, einen nationalen „Notstand“ auszurufen, die verfassungsmäßigen Rechte der Menschen auszusetzen, einen Angriffskrieg gegen ein Land im Nahen Osten anzuzetteln, das für uns keinerlei Bedrohung darstellte, und unsere Straßen, Bahnhöfe, Flughäfen und alle anderen Orte mit schwer bewaffneten Soldaten zu füllen, denn sonst hätten „die Terroristen gewonnen“. Du erinnerst dich, als wir ein Offshore-Gulag bauten, um verdächtige Terroristen auf unbestimmte Zeit wegzusperren, die wir zuvor zu CIA-Geheimgefängnissen verschleppt hatten, wo wir sie gefoltert und gedemütigt haben, richtig?
Natürlich erinnerst du dich. Wer könnte das vergessen?
DIE FRIEDENSTAUBE FLIEGT AUCH IN IHR POSTFACH!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht). Sie wollen der Genossenschaft beitreten oder uns unterstützen? Mehr Infos hier oder am Ende des Textes.
Erinnerst du dich, als die National Security Agency keine andere Wahl hatte, als ein geheimes „Terroristen-Überwachungsprogramm“ einzurichten, um Amerikaner auszuspionieren, oder sonst „hätten die Terroristen gewonnen“? Oder wie wäre es mit den „Anti-Terror“-Unterleibsuntersuchungen der TSA, der Behörde für Transportsicherheit, die nach über zwanzig Jahren immer noch in Kraft sind?
Und was ist mit dem Krieg gegen den Populismus? An den erinnerst du dich vielleicht nicht so gut.
Ich erinnere mich, denn ich habe zwei Bücher dazu veröffentlicht. Er begann im Sommer 2016, als das Imperium erkannte, dass „rechte Populisten“ die „Freiheit und Demokratie“ in Europa bedrohten und Trump in den USA auf dem Vormarsch war. Also wurde ein weiterer „Notstand“ ausgerufen – diesmal von der Gemeinschaft der Geheimdienste, den Medien, der akademischen Welt und der Kulturindustrie. Ja, genau, es war wieder einmal an der Zeit, unsere demokratischen Prinzipien hintanzustellen, „Hassrede“ in sozialen Medien zu zensieren, die Massen mit lächerlicher offizieller Propaganda über „Russiagate,“ „Hitlergate“ und so weiter zu bombardieren – sonst hätten „die Rechtspopulisten gewonnen.“
Der Krieg gegen den Populismus gipfelte in der Einführung des Neuen Normalen Reichs.

Im Frühjahr 2020 rief das Imperium einen globalen „gesundheitlichen Ausnahmezustand“ aus, als Reaktion auf ein Virus mit einer Überlebensrate von etwa 99,8 Prozent. Das Imperium hatte keine andere Wahl, als ganze Gesellschaften abzuriegeln, jeden dazu zu zwingen, in der Öffentlichkeit medizinisch aussehende Masken zu tragen, die Öffentlichkeit mit Propaganda und Lügen zu bombardieren, die Menschen dazu zu nötigen, sich einer Reihe experimenteller mRNA-„Impfungen“ zu unterziehen, Proteste gegen ihre Dekrete zu verbieten und systematisch diejenigen zu zensieren und zu verfolgen, die es wagten, ihre erfundenen „Fakten“ in Frage zu stellen oder ihr totalitäres Programm zu kritisieren.
Das Imperium hatte keine andere Wahl, als das alles zu tun, denn sonst hätten „die Covid-Leugner, die Impfgegner, die Verschwörungstheoretiker und all die anderen Extremisten gewonnen.“
Ich bin mir ziemlich sicher, dass du dich an all das erinnerst.
Und jetzt … nun, hier sind wir. Ja, du hast es erraten – es ist wieder einmal an der Zeit, kräftig auf die US-Verfassung und die Meinungsfreiheit zu scheißen, Menschen in irgendein salvadorianisches Höllenloch abzuschieben, das wir angemietet haben, weil ein Polizist ihre Tattoos nicht mochte, Universitätsstudenten wegen ihrer Anti-Israel-Proteste festzunehmen und zu verschleppen und natürlich die Massen mit Lügen und offizieller Propaganda zu bombardieren, denn … okay, alle zusammen jetzt: „sonst hätten die antisemitischen Terroristen und venezolanischen Banden gewonnen!“
Fängst du an, ein Muster zu erkennen? Ja? Willkommen beim Krieg gegen-was-auch-immer!
Wenn du die Zusammenhänge noch nicht ganz siehst, okay, lass es mich noch einmal ganz simpel erklären.
Das globale ideologische System, in dem wir alle leben, wird totalitär. (Dieses System ist der globale Kapitalismus, aber nenne es, wie du willst. Es ist mir scheißegal.) Es reißt die Simulation der Demokratie nieder, die es nicht mehr aufrechterhalten muss. Der Kalte Krieg ist vorbei. Der Kommunismus ist tot. Der globale Kapitalismus hat keine externen Feinde mehr. Also muss er die Massen nicht mehr mit demokratischen Rechten und Freiheiten besänftigen. Deshalb entzieht er uns diese Rechte nach und nach und konditioniert uns darauf, ihren Verlust hinzunehmen.
Er tut dies, indem er eine Reihe von „Notständen“ inszeniert, jeder mit einer anderen „Bedrohung“ für die „Demokratie,“ die „Freiheit,“ „Amerika“ oder „den Planeten“ – oder was auch immer. Jeder mit seinen eigenen „Monstern,“ die eine so große Gefahr für die „Freiheit“ oder was auch immer darstellen, dass wir unsere verfassungsmäßigen Rechte aufgeben und die demokratischen Werte ad absurdum führen müssen, denn: sonst „würden die Monster gewinnen.“

Es tut dies, indem es sein Antlitz von „links“ nach „rechts,“ dann zurück nach „links“, und dann zurück nach „rechts,“ dann nach „links“ und so weiter neigt, weil es unsere Kooperation dafür benötigt. Nicht die Kooperation von uns allen auf einmal. Nur eine kooperative demografische Gruppe auf einmal.
Es ist dabei erfolgreich – also das System – indem es unsere Angst und unseren Hass instrumentalisiert. Dem System ist es völlig egal, ob wir uns als „links“ oder „rechts“ identifizieren, aber es braucht uns gespalten in „links“ und „rechts,“ damit es unsere Angst und unseren Hass aufeinander nähren kann … eine Regierung, ein „Notfall,“ ein „Krieg“ nach dem anderen.
Da hast du es. Das ist der Krieg gegen was auch immer. Noch simpler kann ich es nicht erklären.
Oh, und noch eine letzte Sache … wenn du einer meiner ehemaligen Fans bist, wie Rob, die über meine „Einsichten“ oder Loyalitäten oder was auch immer verwirrt sind … nun, der Text, den du gerade gelesen hast, sollte das für dich klären. Ich stehe auf keiner Seite. Überhaupt keiner. Aber ich habe ein paar grundlegende demokratische Prinzipien. Und die richten sich nicht danach, was gerade populär ist oder wer im Weißen Haus sitzt.
Die Sache ist die: Ich muss mich morgens im Spiegel anschauen können ohne dort einen Heuchler oder … du weißt schon, einen Feigling zu sehen.
(Aus dem Amerikanischen übersetzt von René Boyke).
CJ Hopkins ist ein US-amerikanischer Dramatiker, Romanautor und politischer Satiriker. Zu seinen Werken zählen die Stücke Horse Country, Screwmachine/Eyecandy und The Extremists. Er hat sich als profilierter Kritiker des Corona-Regimes profiliert und veröffentlicht regelmäßig auf seinem Substack-Blog.
Sein aktuelles Buch:
https://x.com/CJHopkins_Z23/status/1907795633689264530
Hier in einem aktuellen Gespräch:
https://www.youtube.com/watch?v=wF-G32P0leI
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt. (Vorerst alle, da wir den Mailversand testen, später ca. drei Mails pro Woche.)
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: milosz@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ a95c6243:d345522c
2024-12-13 19:30:32
@ a95c6243:d345522c
2024-12-13 19:30:32Das Betriebsklima ist das einzige Klima, \ das du selbst bestimmen kannst. \ Anonym
Eine Strategie zur Anpassung an den Klimawandel hat das deutsche Bundeskabinett diese Woche beschlossen. Da «Wetterextreme wie die immer häufiger auftretenden Hitzewellen und Starkregenereignisse» oft desaströse Auswirkungen auf Mensch und Umwelt hätten, werde eine Anpassung an die Folgen des Klimawandels immer wichtiger. «Klimaanpassungsstrategie» nennt die Regierung das.
Für die «Vorsorge vor Klimafolgen» habe man nun erstmals klare Ziele und messbare Kennzahlen festgelegt. So sei der Erfolg überprüfbar, und das solle zu einer schnelleren Bewältigung der Folgen führen. Dass sich hinter dem Begriff Klimafolgen nicht Folgen des Klimas, sondern wohl «Folgen der globalen Erwärmung» verbergen, erklärt den Interessierten die Wikipedia. Dabei ist das mit der Erwärmung ja bekanntermaßen so eine Sache.
Die Zunahme schwerer Unwetterereignisse habe gezeigt, so das Ministerium, wie wichtig eine frühzeitige und effektive Warnung der Bevölkerung sei. Daher solle es eine deutliche Anhebung der Nutzerzahlen der sogenannten Nina-Warn-App geben.
Die ARD spurt wie gewohnt und setzt die Botschaft zielsicher um. Der Artikel beginnt folgendermaßen:
«Die Flut im Ahrtal war ein Schock für das ganze Land. Um künftig besser gegen Extremwetter gewappnet zu sein, hat die Bundesregierung eine neue Strategie zur Klimaanpassung beschlossen. Die Warn-App Nina spielt eine zentrale Rolle. Der Bund will die Menschen in Deutschland besser vor Extremwetter-Ereignissen warnen und dafür die Reichweite der Warn-App Nina deutlich erhöhen.»
Die Kommunen würden bei ihren «Klimaanpassungsmaßnahmen» vom Zentrum KlimaAnpassung unterstützt, schreibt das Umweltministerium. Mit dessen Aufbau wurden das Deutsche Institut für Urbanistik gGmbH, welches sich stark für Smart City-Projekte engagiert, und die Adelphi Consult GmbH beauftragt.
Adelphi beschreibt sich selbst als «Europas führender Think-and-Do-Tank und eine unabhängige Beratung für Klima, Umwelt und Entwicklung». Sie seien «global vernetzte Strateg*innen und weltverbessernde Berater*innen» und als «Vorreiter der sozial-ökologischen Transformation» sei man mit dem Deutschen Nachhaltigkeitspreis ausgezeichnet worden, welcher sich an den Zielen der Agenda 2030 orientiere.
Über die Warn-App mit dem niedlichen Namen Nina, die möglichst jeder auf seinem Smartphone installieren soll, informiert das Bundesamt für Bevölkerungsschutz und Katastrophenhilfe (BBK). Gewarnt wird nicht nur vor Extrem-Wetterereignissen, sondern zum Beispiel auch vor Waffengewalt und Angriffen, Strom- und anderen Versorgungsausfällen oder Krankheitserregern. Wenn man die Kategorie Gefahreninformation wählt, erhält man eine Dosis von ungefähr zwei Benachrichtigungen pro Woche.
Beim BBK erfahren wir auch einiges über die empfohlenen Systemeinstellungen für Nina. Der Benutzer möge zum Beispiel den Zugriff auf die Standortdaten «immer zulassen», und zwar mit aktivierter Funktion «genauen Standort verwenden». Die Datennutzung solle unbeschränkt sein, auch im Hintergrund. Außerdem sei die uneingeschränkte Akkunutzung zu aktivieren, der Energiesparmodus auszuschalten und das Stoppen der App-Aktivität bei Nichtnutzung zu unterbinden.
Dass man so dramatische Ereignisse wie damals im Ahrtal auch anders bewerten kann als Regierungen und Systemmedien, hat meine Kollegin Wiltrud Schwetje anhand der Tragödie im spanischen Valencia gezeigt. Das Stichwort «Agenda 2030» taucht dabei in einem Kontext auf, der wenig mit Nachhaltigkeitspreisen zu tun hat.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 04c915da:3dfbecc9
2025-03-25 17:43:44
@ 04c915da:3dfbecc9
2025-03-25 17:43:44One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ a012dc82:6458a70d
2025-03-19 06:28:40
@ a012dc82:6458a70d
2025-03-19 06:28:40In recent years, the global economy has faced unprecedented challenges, with inflation rates soaring to levels not seen in decades. This economic turmoil has led investors and consumers alike to seek alternative stores of value and investment strategies. Among the various options, Bitcoin has emerged as a particularly appealing choice. This article explores the reasons behind Bitcoin's growing appeal in an inflation-stricken economy, delving into its characteristics, historical performance, and the broader implications for the financial landscape.
Table of Contents
-
Understanding Inflation and Its Impacts
-
Bitcoin: A New Safe Haven?
-
Decentralization and Limited Supply
-
Portability and Liquidity
-
Bitcoin's Performance in Inflationary Times
-
Challenges and Considerations
-
The Future of Bitcoin in an Inflationary Economy
-
Conclusion
-
FAQs
Understanding Inflation and Its Impacts
Inflation is the rate at which the general level of prices for goods and services is rising, eroding purchasing power. It can be caused by various factors, including increased production costs, higher energy prices, and expansive government policies. Inflation affects everyone in the economy, from consumers and businesses to investors and retirees, as it diminishes the value of money. When inflation rates rise, the purchasing power of currency falls, leading to higher costs for everyday goods and services. This can result in decreased consumer spending, reduced savings, and overall economic slowdown.
For investors, inflation is a significant concern because it can erode the real returns on their investments. Traditional investments like bonds and savings accounts may not keep pace with inflation, leading to a loss in purchasing power over time. This has prompted a search for alternative investments that can provide a hedge against inflation and preserve, if not increase, the value of their capital.
Bitcoin: A New Safe Haven?
Traditionally, assets like gold, real estate, and Treasury Inflation-Protected Securities (TIPS) have been considered safe havens during times of inflation. However, the digital age has introduced a new player: Bitcoin. Bitcoin is a decentralized digital currency that operates without the oversight of a central authority. Its supply is capped at 21 million coins, a feature that many believe gives it anti-inflationary properties. This inherent scarcity is akin to natural resources like gold, which have historically been used as hedges against inflation.
The decentralization of Bitcoin means that it is not subject to the whims of central banking policies or government interference, which are often seen as contributing factors to inflation. This aspect of Bitcoin is particularly appealing to those who have lost faith in traditional financial systems and are looking for alternatives that offer more autonomy and security.
Decentralization and Limited Supply
One of the key features that make Bitcoin appealing as a hedge against inflation is its decentralized nature. Unlike fiat currencies, which central banks can print in unlimited quantities, Bitcoin's supply is finite. This scarcity mimics the properties of gold and is seen as a buffer against inflation. The decentralized nature of Bitcoin also means that it is not subject to the same regulatory pressures and monetary policies that can lead to currency devaluation.
Furthermore, the process of "mining" Bitcoin, which involves validating transactions and adding them to the blockchain, is designed to become progressively more difficult over time. This not only ensures the security of the network but also introduces a deflationary element to Bitcoin, as the rate at which new coins are created slows down over time.
Portability and Liquidity
Bitcoin's digital nature makes it highly portable and divisible, allowing for easy transfer and exchange worldwide. This liquidity and global accessibility make it an attractive option for investors looking to diversify their portfolios beyond traditional assets. Unlike physical assets like gold or real estate, Bitcoin can be transferred across borders without the need for intermediaries, making it a truly global asset.
The ease of transferring and dividing Bitcoin means that it can be used for a wide range of transactions, from large-scale investments to small, everyday purchases. This versatility, combined with its growing acceptance as a form of payment, enhances its utility and appeal as an investment.
Bitcoin's Performance in Inflationary Times
Historically, Bitcoin has shown significant growth during periods of high inflation. While it is known for its price volatility, many investors have turned to Bitcoin as a speculative hedge against depreciating fiat currencies. The digital currency's performance during inflationary periods has bolstered its reputation as a potential safe haven. However, it's important to note that Bitcoin's market is still relatively young and can be influenced by a wide range of factors beyond inflation, such as market sentiment, technological developments, and regulatory changes.
Despite its volatility, Bitcoin has provided substantial returns for some investors, particularly those who entered the market early. Its performance, especially during times of financial instability, has led to increased interest and investment from both individual and institutional investors. As more people look to Bitcoin as a potential hedge against inflation, its role in investment portfolios is likely to evolve.
Challenges and Considerations
Despite its growing appeal, Bitcoin is not without its challenges. The cryptocurrency's price volatility can lead to significant losses, and regulatory uncertainties remain a concern. Additionally, the environmental impact of Bitcoin mining has sparked debate. The energy-intensive process required to mine new coins and validate transactions has raised concerns about its sustainability and environmental footprint.
Investors considering Bitcoin as a hedge against inflation should weigh these factors and consider their risk tolerance and investment horizon. While Bitcoin offers potential benefits as an inflation hedge, it also comes with risks that are different from traditional investments. Understanding these risks, and how they align with individual investment strategies, is crucial for anyone considering adding Bitcoin to their portfolio.
The Future of Bitcoin in an Inflationary Economy
As the global economy continues to navigate through turbulent waters, the appeal of Bitcoin is likely to grow. Its properties as a decentralized, finite, and easily transferable asset make it a unique option for those looking to protect their wealth from inflation. However, the future of Bitcoin remains uncertain, and its role in the broader financial landscape is still being defined. As with any investment, due diligence and a balanced approach are crucial.
The increasing institutional interest in Bitcoin and the development of financial products around it, such as ETFs and futures, suggest that Bitcoin is becoming more mainstream. However, its acceptance and integration into the global financial system will depend on a variety of factors, including regulatory developments, technological advancements, and market dynamics.
Conclusion
The growing appeal of Bitcoin in an inflation-stricken economy highlights the changing dynamics of investment in the digital age. While it offers a novel approach to wealth preservation, it also comes with its own set of risks and challenges. As the world continues to grapple with inflation, the role of Bitcoin and other cryptocurrencies will undoubtedly be a topic of keen interest and debate among investors and policymakers alike. Whether Bitcoin will become a permanent fixture in investment portfolios as a hedge against inflation remains to be seen, but its impact on the financial landscape is undeniable.
FAQs
What is inflation, and how does it affect the economy? Inflation is the rate at which the general level of prices for goods and services is rising, leading to a decrease in purchasing power. It affects the economy by reducing the value of money, increasing costs for consumers and businesses, and potentially leading to economic slowdown.
Why is Bitcoin considered a hedge against inflation? Bitcoin is considered a hedge against inflation due to its decentralized nature, limited supply capped at 21 million coins, and its independence from government monetary policies, which are often seen as contributing factors to inflation.
What are the risks associated with investing in Bitcoin? The risks include high price volatility, regulatory uncertainties, and concerns over the environmental impact of Bitcoin mining. Investors should consider their risk tolerance and investment horizon before investing in Bitcoin.
How does Bitcoin's limited supply contribute to its value? Bitcoin's limited supply mimics the scarcity of resources like gold, which has traditionally been used as a hedge against inflation. This scarcity can help to maintain its value over time, especially in contrast to fiat currencies, which can be printed in unlimited quantities.
Can Bitcoin be used for everyday transactions? Yes, Bitcoin can be used for a wide range of transactions, from large-scale investments to small, everyday purchases. Its digital nature allows for easy transfer and division, making it a versatile form of currency.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
X: @croxroadnewsco
Instagram: @croxroadnews.co/
Youtube: @thebitcoinlibertarian
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
Get Orange Pill App And Connect With Bitcoiners In Your Area. Stack Friends Who Stack Sats link: https://signup.theorangepillapp.com/opa/croxroad
Buy Bitcoin Books At Konsensus Network Store. 10% Discount With Code “21croxroad” link: https://bitcoinbook.shop?ref=21croxroad
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ e97aaffa:2ebd765d
2025-03-19 05:55:17
@ e97aaffa:2ebd765d
2025-03-19 05:55:17Como é difícil encontrar informações sobre o eurodigital, a CBDC da União Europeia, vou colocando aqui, os documentos mais interessantes que fui encontrando:
FAQ: https://www.ecb.europa.eu/euro/digital_euro/faqs/html/ecb.faq_digital_euro.pt.html
Directório BCE: https://www.ecb.europa.eu/press/pubbydate/html/index.en.html?topic=Digital%20euro
https://www.ecb.europa.eu/euro/digital_euro/timeline/profuse/html/index.en.html
Documentos mais técnicos:
2025
Technical note on the provision of multiple digital euro accounts to individual end users https://www.ecb.europa.eu/euro/digital_euro/timeline/profuse/shared/pdf/ecb.degov240325_digital_euro_multiple_accounts.en.pdf
2024
Relatório de progresso https://www.ecb.europa.eu/euro/digital_euro/progress/html/ecb.deprp202412.en.html
Technical note on the provision of multiple digital euro accounts to individual end users https://www.ecb.europa.eu/euro/digital_euro/timeline/profuse/shared/pdf/ecb.degov240325_digital_euro_multiple_accounts.en.pdf
The impact of central bank digital currency on central bank profitability, risk-taking and capital https://www.ecb.europa.eu/pub/pdf/scpops/ecb.op360~35915b25bd.en.pdf
2023
Progress on the investigation phase of a digital euro - fourth report https://www.ecb.europa.eu/paym/digital_euro/investigation/governance/shared/files/ecb.degov230713-fourth-progress-report-digital-euro-investigation-phase.en.pdf
Digital euro - Prototype summary and lessons learned https://www.ecb.europa.eu/pub/pdf/other/ecb.prototype_summary20230526%7E71d0b26d55.en.pdf
Functional and non-functional requirements linked to the market research for a potential digital euro implementation https://www.ecb.europa.eu/euro/digital_euro/timeline/profuse/shared/pdf//ecb.dedocs230113_Annex_1_Digital_euro_market_research.en.pdf
A stocktake on the digital euro https://www.ecb.europa.eu/euro/digital_euro/progress/shared/pdf/ecb.dedocs231018.en.pdf
-
 @ da18e986:3a0d9851
2025-04-04 20:25:50
@ da18e986:3a0d9851
2025-04-04 20:25:50I'm making this tutorial for myself, as I plan to write many wiki pages describing DVM kinds, as a resource for DVMDash.
Wiki pages on Nostr are written using AsciiDoc. If you don't know ascii doc, get an LLM (like https://duck.ai) to help you format into the right syntax.
Here's the test wiki page I'm going to write:
``` = Simple AsciiDoc Demo
This is a simple demonstration of AsciiDoc syntax for testing purposes.
== Features
AsciiDoc offers many formatting options that are easy to use.
- Easy to learn
- Supports rich text formatting
- Can include code snippets
- Works great for documentation
[source,json]
{ "name": "Test", "version": "1.0", "active": true }
```
We're going to use nak to publish it
First, install
nakif you haven't alreadygo install github.com/fiatjaf/nak@latestNote: if you don't use Go a lot, you may need to first install it and then add it to your path so the
nakcommand is recognized by the terminal```
this is how to add it to your path on mac if using zsh
echo 'export PATH=$PATH:$(go env GOPATH)/bin' >> ~/.zshrc ```
And here's how to sign and publish this event with nak.
First, if you want to use your own nostr sec key, you can set the env variable to it and nak will use that if no secret key is specified
```
replace with your full secret key
export NOSTR_SECRET_KEY="nsec1zcdn..." ```
Now to sign and publish the event:
Note: inner double quotes need to be escaped with a
\before them in order to keep the formatting correct, because we're doing this in the terminalnak event -k 30818 -d "dvm-wiki-page-test" -t 'title=dvm wiki page test' -c "= Simple AsciiDoc Demo\n\nThis is a simple demonstration of AsciiDoc syntax for testing purposes. \n\n== Features\n\nAsciiDoc offers many formatting options that are easy to use. \n\n* Easy to learn \n* Supports rich text formatting \n* Can include code snippets \n* Works great for documentation \n\n[source,json] \n---- \n{ \"name\": \"Test\", \"version\": \"1.0\", \"active\": true } \n----" wss://relay.primal.net wss://relay.damus.io wss://relay.wikifreedia.xyzYou've now published your first wiki page! If done correctly, it will show up on wikistr.com, like mine did here: https://wikistr.com/dvm-wiki-page-test*da18e9860040f3bf493876fc16b1a912ae5a6f6fa8d5159c3de2b8233a0d9851
and on wikifreedia.xyz https://wikifreedia.xyz/dvm-wiki-page-test/dustind@dtdannen.github.io
-
 @ a95c6243:d345522c
2024-12-06 18:21:15
@ a95c6243:d345522c
2024-12-06 18:21:15Die Ungerechtigkeit ist uns nur in dem Falle angenehm,\ dass wir Vorteile aus ihr ziehen;\ in jedem andern hegt man den Wunsch,\ dass der Unschuldige in Schutz genommen werde.\ Jean-Jacques Rousseau
Politiker beteuern jederzeit, nur das Beste für die Bevölkerung zu wollen – nicht von ihr. Auch die zahlreichen unsäglichen «Corona-Maßnahmen» waren angeblich zu unserem Schutz notwendig, vor allem wegen der «besonders vulnerablen Personen». Daher mussten alle möglichen Restriktionen zwangsweise und unter Umgehung der Parlamente verordnet werden.
Inzwischen hat sich immer deutlicher herausgestellt, dass viele jener «Schutzmaßnahmen» den gegenteiligen Effekt hatten, sie haben den Menschen und den Gesellschaften enorm geschadet. Nicht nur haben die experimentellen Geninjektionen – wie erwartet – massive Nebenwirkungen, sondern Maskentragen schadet der Psyche und der Entwicklung (nicht nur unserer Kinder) und «Lockdowns und Zensur haben Menschen getötet».
Eine der wichtigsten Waffen unserer «Beschützer» ist die Spaltung der Gesellschaft. Die tiefen Gräben, die Politiker, Lobbyisten und Leitmedien praktisch weltweit ausgehoben haben, funktionieren leider nahezu in Perfektion. Von ihren persönlichen Erfahrungen als Kritikerin der Maßnahmen berichtete kürzlich eine Schweizerin im Interview mit Transition News. Sie sei schwer enttäuscht und verspüre bis heute eine Hemmschwelle und ein seltsames Unwohlsein im Umgang mit «Geimpften».
Menschen, die aufrichtig andere schützen wollten, werden von einer eindeutig politischen Justiz verfolgt, verhaftet und angeklagt. Dazu zählen viele Ärzte, darunter Heinrich Habig, Bianca Witzschel und Walter Weber. Über den aktuell laufenden Prozess gegen Dr. Weber hat Transition News mehrfach berichtet (z.B. hier und hier). Auch der Selbstschutz durch Verweigerung der Zwangs-Covid-«Impfung» bewahrt nicht vor dem Knast, wie Bundeswehrsoldaten wie Alexander Bittner erfahren mussten.
Die eigentlich Kriminellen schützen sich derweil erfolgreich selber, nämlich vor der Verantwortung. Die «Impf»-Kampagne war «das größte Verbrechen gegen die Menschheit». Trotzdem stellt man sich in den USA gerade die Frage, ob der scheidende Präsident Joe Biden nach seinem Sohn Hunter möglicherweise auch Anthony Fauci begnadigen wird – in diesem Fall sogar präventiv. Gibt es überhaupt noch einen Rest Glaubwürdigkeit, den Biden verspielen könnte?
Der Gedanke, den ehemaligen wissenschaftlichen Chefberater des US-Präsidenten und Direktor des National Institute of Allergy and Infectious Diseases (NIAID) vorsorglich mit einem Schutzschild zu versehen, dürfte mit der vergangenen Präsidentschaftswahl zu tun haben. Gleich mehrere Personalentscheidungen des designierten Präsidenten Donald Trump lassen Leute wie Fauci erneut in den Fokus rücken.
Das Buch «The Real Anthony Fauci» des nominierten US-Gesundheitsministers Robert F. Kennedy Jr. erschien 2021 und dreht sich um die Machenschaften der Pharma-Lobby in der öffentlichen Gesundheit. Das Vorwort zur rumänischen Ausgabe des Buches schrieb übrigens Călin Georgescu, der Überraschungssieger der ersten Wahlrunde der aktuellen Präsidentschaftswahlen in Rumänien. Vielleicht erklärt diese Verbindung einen Teil der Panik im Wertewesten.
In Rumänien selber gab es gerade einen Paukenschlag: Das bisherige Ergebnis wurde heute durch das Verfassungsgericht annuliert und die für Sonntag angesetzte Stichwahl kurzfristig abgesagt – wegen angeblicher «aggressiver russischer Einmischung». Thomas Oysmüller merkt dazu an, damit sei jetzt in der EU das Tabu gebrochen, Wahlen zu verbieten, bevor sie etwas ändern können.
Unsere Empörung angesichts der Historie von Maßnahmen, die die Falschen beschützen und für die meisten von Nachteil sind, müsste enorm sein. Die Frage ist, was wir damit machen. Wir sollten nach vorne schauen und unsere Energie clever einsetzen. Abgesehen von der Umgehung von jeglichem «Schutz vor Desinformation und Hassrede» (sprich: Zensur) wird es unsere wichtigste Aufgabe sein, Gräben zu überwinden.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ ee9aaefe:1e6952f4
2025-03-19 05:01:44
@ ee9aaefe:1e6952f4
2025-03-19 05:01:44Introduction to Model Context Protocol (MCP)
Model Context Protocol (MCP) serves as a specialized gateway allowing AI systems to access real-time information and interact with external data sources while maintaining security boundaries. This capability transforms AI from closed systems limited to training data into dynamic assistants capable of retrieving current information and performing actions. As AI systems integrate into critical infrastructure across industries, the security and reliability of these protocols have become crucial considerations.
Security Vulnerabilities in Web-Based MCP Services
Traditional MCP implementations operate as web services, creating a fundamental security weakness. When an MCP runs as a conventional web service, the entire security model depends on trusting the service provider. Providers can modify underlying code, alter behavior, or update services without users' knowledge or consent. This creates an inherent vulnerability where the system's integrity rests solely on the trustworthiness of the MCP provider.
This vulnerability is particularly concerning in high-stakes domains. In financial applications, a compromised MCP could lead to unauthorized transactions or exposure of confidential information. In healthcare, it might result in compromised patient data. The fundamental problem is that users have no cryptographic guarantees about the MCP's behavior – they must simply trust the provider's claims about security and data handling.
Additionally, these services create single points of failure vulnerable to sophisticated attacks. Service providers face internal threats from rogue employees, external pressure from bad actors, or regulatory compulsion that could compromise user security or privacy. With traditional MCPs, users have limited visibility into such changes and few technical safeguards.
ICP Canisters: Enabling the Verifiable MCP Paradigm
The Internet Computer Protocol (ICP) offers a revolutionary solution through its canister architecture, enabling what we term "Verifiable MCP" – a new paradigm in AI security. Unlike traditional web services, ICP canisters operate within a decentralized network with consensus-based execution and verification, creating powerful security properties:
- Cryptographically verifiable immutability guarantees prevent silent code modifications
- Deterministic execution environments allow independent verification by network participants
- Ability to both read and write web data while operating under consensus verification
- Control of off-chain Trusted Execution Environment (TEE) servers through on-chain attestation
These capabilities create the foundation for trustworthy AI context protocols that don't require blind faith in service providers.
Technical Architecture of Verifiable MCP Integration
The Verifiable MCP architecture places MCP service logic within ICP canisters that operate under consensus verification. This creates several distinct layers working together to ensure security:
-
Interface Layer: AI models connect through standardized APIs compatible with existing integration patterns.
-
Verification Layer: The ICP canister validates authentication, checks permissions, and verifies policy adherence within a consensus-verified environment.
-
Orchestration Layer: The canister coordinates necessary resources for data retrieval or computation.
-
Attestation Layer: For sensitive operations, the canister deploys and attests TEE instances, providing cryptographic proof that correct code runs in a secure environment.
-
Response Verification Layer: Before returning results, cryptographic verification ensures data integrity and provenance.
This architecture creates a transparent, verifiable pipeline where component behavior is guaranteed through consensus mechanisms and cryptographic verification—eliminating the need to trust service provider claims.
Example: Secure Financial Data Access Through Verifiable MCP
Consider a financial advisory AI needing access to banking data and portfolios to provide recommendations. In a Verifiable MCP implementation:
-
The AI submits a data request through the Verifiable MCP interface.
-
The ICP canister verifies authorization using immutable access control logic.
-
For sensitive data, the canister deploys a TEE instance with privacy-preserving code.
-
The canister cryptographically verifies the TEE is running the correct code.
-
Financial services provide encrypted data directly to the verified TEE.
-
The TEE returns only authorized results with cryptographic proof of correct execution.
-
The canister delivers verified insights to the AI.
This ensures even the service provider cannot access raw financial data while maintaining complete auditability. Users verify exactly what code processes their information and what insights are extracted, enabling AI applications in regulated domains otherwise too risky with traditional approaches.
Implications for AI Trustworthiness and Data Sovereignty
The Verifiable MCP paradigm transforms the trust model for AI systems by shifting from "trust the provider" to cryptographic verification. This addresses a critical barrier to AI adoption in sensitive domains where guarantees about data handling are essential.
For AI trustworthiness, this enables transparent auditing of data access patterns, prevents silent modifications to processing logic, and provides cryptographic proof of data provenance. Users can verify exactly what information AI systems access and how it's processed.
From a data sovereignty perspective, users gain control through cryptographic guarantees rather than policy promises. Organizations implement permissions that cannot be circumvented, while regulators can verify immutable code handling sensitive information. For cross-border scenarios, Verifiable MCP enables compliance with data localization requirements while maintaining global AI service capabilities through cryptographically enforced data boundaries.
Conclusion
The Verifiable MCP paradigm represents a breakthrough in securing AI systems' external interactions. By leveraging ICP canisters' immutability and verification capabilities, it addresses fundamental vulnerabilities in traditional MCP implementations.
As AI adoption grows in regulated domains, this architecture provides a foundation for trustworthy model-world interactions without requiring blind faith in service providers. The approach enables new categories of AI applications in sensitive sectors while maintaining robust security guarantees.
This innovation promises to democratize secure context protocols, paving the way for responsible AI deployment even in the most security-critical environments.
-
 @ a95c6243:d345522c
2024-11-29 19:45:43
@ a95c6243:d345522c
2024-11-29 19:45:43Konsum ist Therapie.
Wolfgang JoopUmweltbewusstes Verhalten und verantwortungsvoller Konsum zeugen durchaus von einer wünschenswerten Einstellung. Ob man deswegen allerdings einen grünen statt eines schwarzen Freitags braucht, darf getrost bezweifelt werden – zumal es sich um manipulatorische Konzepte handelt. Wie in der politischen Landschaft sind auch hier die Etiketten irgendwas zwischen nichtssagend und trügerisch.
Heute ist also wieder mal «Black Friday», falls Sie es noch nicht mitbekommen haben sollten. Eigentlich haben wir ja eher schon eine ganze «Black Week», der dann oft auch noch ein «Cyber Monday» folgt. Die Werbebranche wird nicht müde, immer neue Anlässe zu erfinden oder zu importieren, um uns zum Konsumieren zu bewegen. Und sie ist damit sehr erfolgreich.
Warum fallen wir auf derartige Werbetricks herein und kaufen im Zweifelsfall Dinge oder Mengen, die wir sicher nicht brauchen? Pure Psychologie, würde ich sagen. Rabattschilder triggern etwas in uns, was den Verstand in Stand-by versetzt. Zusätzlich beeinflussen uns alle möglichen emotionalen Reize und animieren uns zum Schnäppchenkauf.
Gedankenlosigkeit und Maßlosigkeit können besonders bei der Ernährung zu ernsten Problemen führen. Erst kürzlich hat mir ein Bekannter nach einer USA-Reise erzählt, dass es dort offenbar nicht unüblich ist, schon zum ausgiebigen Frühstück in einem Restaurant wenigstens einen Liter Cola zu trinken. Gerne auch mehr, um das Gratis-Nachfüllen des Bechers auszunutzen.
Kritik am schwarzen Freitag und dem unnötigen Konsum kommt oft von Umweltschützern. Neben Ressourcenverschwendung, hohem Energieverbrauch und wachsenden Müllbergen durch eine zunehmende Wegwerfmentalität kommt dabei in der Regel auch die «Klimakrise» auf den Tisch.
Die EU-Kommission lancierte 2015 den Begriff «Green Friday» im Kontext der überarbeiteten Rechtsvorschriften zur Kennzeichnung der Energieeffizienz von Elektrogeräten. Sie nutzte die Gelegenheit kurz vor dem damaligen schwarzen Freitag und vor der UN-Klimakonferenz COP21, bei der das Pariser Abkommen unterzeichnet werden sollte.
Heute wird ein grüner Freitag oft im Zusammenhang mit der Forderung nach «nachhaltigem Konsum» benutzt. Derweil ist die Europäische Union schon weit in ihr Geschäftsmodell des «Green New Deal» verstrickt. In ihrer Propaganda zum Klimawandel verspricht sie tatsächlich «Unterstützung der Menschen und Regionen, die von immer häufigeren Extremwetter-Ereignissen betroffen sind». Was wohl die Menschen in der Region um Valencia dazu sagen?
Ganz im Sinne des Great Reset propagierten die Vereinten Nationen seit Ende 2020 eine «grüne Erholung von Covid-19, um den Klimawandel zu verlangsamen». Der UN-Umweltbericht sah in dem Jahr einen Schwerpunkt auf dem Verbraucherverhalten. Änderungen des Konsumverhaltens des Einzelnen könnten dazu beitragen, den Klimaschutz zu stärken, hieß es dort.
Der Begriff «Schwarzer Freitag» wurde in den USA nicht erstmals für Einkäufe nach Thanksgiving verwendet – wie oft angenommen –, sondern für eine Finanzkrise. Jedoch nicht für den Börsencrash von 1929, sondern bereits für den Zusammenbruch des US-Goldmarktes im September 1869. Seitdem mussten die Menschen weltweit so einige schwarze Tage erleben.
Kürzlich sind die britischen Aufsichtsbehörden weiter von ihrer Zurückhaltung nach dem letzten großen Finanzcrash von 2008 abgerückt. Sie haben Regeln für den Bankensektor gelockert, womit sie «verantwortungsvolle Risikobereitschaft» unterstützen wollen. Man würde sicher zu schwarz sehen, wenn man hier ein grünes Wunder befürchten würde.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a95c6243:d345522c
2024-11-08 20:02:32
@ a95c6243:d345522c
2024-11-08 20:02:32Und plötzlich weißt du:
Es ist Zeit, etwas Neues zu beginnen
und dem Zauber des Anfangs zu vertrauen.
Meister EckhartSchwarz, rot, gold leuchtet es im Kopf des Newsletters der deutschen Bundesregierung, der mir freitags ins Postfach flattert. Rot, gelb und grün werden daneben sicher noch lange vielzitierte Farben sein, auch wenn diese nie geleuchtet haben. Die Ampel hat sich gerade selber den Stecker gezogen – und hinterlässt einen wirtschaftlichen und gesellschaftlichen Trümmerhaufen.
Mit einem bemerkenswerten Timing hat die deutsche Regierungskoalition am Tag des «Comebacks» von Donald Trump in den USA endlich ihr Scheitern besiegelt. Während der eine seinen Sieg bei den Präsidentschaftswahlen feierte, erwachten die anderen jäh aus ihrer Selbsthypnose rund um Harris-Hype und Trump-Panik – mit teils erschreckenden Auswüchsen. Seit Mittwoch werden die Geschicke Deutschlands nun von einer rot-grünen Minderheitsregierung «geleitet» und man steuert auf Neuwahlen zu.
Das Kindergarten-Gehabe um zwei konkurrierende Wirtschaftsgipfel letzte Woche war bereits bezeichnend. In einem Strategiepapier gestand Finanzminister Lindner außerdem den «Absturz Deutschlands» ein und offenbarte, dass die wirtschaftlichen Probleme teilweise von der Ampel-Politik «vorsätzlich herbeigeführt» worden seien.
Lindner und weitere FDP-Minister wurden also vom Bundeskanzler entlassen. Verkehrs- und Digitalminister Wissing trat flugs aus der FDP aus; deshalb darf er nicht nur im Amt bleiben, sondern hat zusätzlich noch das Justizministerium übernommen. Und mit Jörg Kukies habe Scholz «seinen Lieblingsbock zum Obergärtner», sprich: Finanzminister befördert, meint Norbert Häring.
Es gebe keine Vertrauensbasis für die weitere Zusammenarbeit mit der FDP, hatte der Kanzler erklärt, Lindner habe zu oft sein Vertrauen gebrochen. Am 15. Januar 2025 werde er daher im Bundestag die Vertrauensfrage stellen, was ggf. den Weg für vorgezogene Neuwahlen freimachen würde.
Apropos Vertrauen: Über die Hälfte der Bundesbürger glauben, dass sie ihre Meinung nicht frei sagen können. Das ging erst kürzlich aus dem diesjährigen «Freiheitsindex» hervor, einer Studie, die die Wechselwirkung zwischen Berichterstattung der Medien und subjektivem Freiheitsempfinden der Bürger misst. «Beim Vertrauen in Staat und Medien zerreißt es uns gerade», kommentierte dies der Leiter des Schweizer Unternehmens Media Tenor, das die Untersuchung zusammen mit dem Institut für Demoskopie Allensbach durchführt.
«Die absolute Mehrheit hat absolut die Nase voll», titelte die Bild angesichts des «Ampel-Showdowns». Die Mehrheit wolle Neuwahlen und die Grünen sollten zuerst gehen, lasen wir dort.
Dass «Insolvenzminister» Robert Habeck heute seine Kandidatur für das Kanzleramt verkündet hat, kann nur als Teil der politmedialen Realitätsverweigerung verstanden werden. Wer allerdings denke, schlimmer als in Zeiten der Ampel könne es nicht mehr werden, sei reichlich optimistisch, schrieb Uwe Froschauer bei Manova. Und er kenne Friedrich Merz schlecht, der sich schon jetzt rhetorisch auf seine Rolle als oberster Feldherr Deutschlands vorbereite.
Was also tun? Der Schweizer Verein «Losdemokratie» will eine Volksinitiative lancieren, um die Bestimmung von Parlamentsmitgliedern per Los einzuführen. Das Losverfahren sorge für mehr Demokratie, denn als Alternative zum Wahlverfahren garantiere es eine breitere Beteiligung und repräsentativere Parlamente. Ob das ein Weg ist, sei dahingestellt.
In jedem Fall wird es notwendig sein, unsere Bemühungen um Freiheit und Selbstbestimmung zu verstärken. Mehr Unabhängigkeit von staatlichen und zentralen Institutionen – also die Suche nach dezentralen Lösungsansätzen – gehört dabei sicher zu den Möglichkeiten. Das gilt sowohl für jede/n Einzelne/n als auch für Entitäten wie die alternativen Medien.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a95c6243:d345522c
2024-10-26 12:21:50
@ a95c6243:d345522c
2024-10-26 12:21:50Es ist besser, ein Licht zu entzünden, als auf die Dunkelheit zu schimpfen. Konfuzius
Die Bemühungen um Aufarbeitung der sogenannten Corona-Pandemie, um Aufklärung der Hintergründe, Benennung von Verantwortlichkeiten und das Ziehen von Konsequenzen sind durchaus nicht eingeschlafen. Das Interesse daran ist unter den gegebenen Umständen vielleicht nicht sonderlich groß, aber es ist vorhanden.
Der sächsische Landtag hat gestern die Einsetzung eines Untersuchungsausschusses zur Corona-Politik beschlossen. In einer Sondersitzung erhielt ein entsprechender Antrag der AfD-Fraktion die ausreichende Zustimmung, auch von einigen Abgeordneten des BSW.
In den Niederlanden wird Bill Gates vor Gericht erscheinen müssen. Sieben durch die Covid-«Impfstoffe» geschädigte Personen hatten Klage eingereicht. Sie werfen unter anderem Gates, Pfizer-Chef Bourla und dem niederländischen Staat vor, sie hätten gewusst, dass diese Präparate weder sicher noch wirksam sind.
Mit den mRNA-«Impfstoffen» von Pfizer/BioNTech befasst sich auch ein neues Buch. Darin werden die Erkenntnisse von Ärzten und Wissenschaftlern aus der Analyse interner Dokumente über die klinischen Studien der Covid-Injektion präsentiert. Es handelt sich um jene in den USA freigeklagten Papiere, die die Arzneimittelbehörde (Food and Drug Administration, FDA) 75 Jahre unter Verschluss halten wollte.
Ebenfalls Wissenschaftler und Ärzte, aber auch andere Experten organisieren als Verbundnetzwerk Corona-Solution kostenfreie Online-Konferenzen. Ihr Ziel ist es, «wissenschaftlich, demokratisch und friedlich» über Impfstoffe und Behandlungsprotokolle gegen SARS-CoV-2 aufzuklären und die Diskriminierung von Ungeimpften zu stoppen. Gestern fand eine weitere Konferenz statt. Ihr Thema: «Corona und modRNA: Von Toten, Lebenden und Physik lernen».
Aufgrund des Digital Services Acts (DSA) der Europäischen Union sei das Risiko groß, dass ihre Arbeit als «Fake-News» bezeichnet würde, so das Netzwerk. Staatlich unerwünschte wissenschaftliche Aufklärung müsse sich passende Kanäle zur Veröffentlichung suchen. Ihre Live-Streams seien deshalb zum Beispiel nicht auf YouTube zu finden.
Der vielfältige Einsatz für Aufklärung und Aufarbeitung wird sich nicht stummschalten lassen. Nicht einmal der Zensurmeister der EU, Deutschland, wird so etwas erreichen. Die frisch aktivierten «Trusted Flagger» dürften allerdings künftige Siege beim «Denunzianten-Wettbewerb» im Kontext des DSA zusätzlich absichern.
Wo sind die Grenzen der Meinungsfreiheit? Sicher gibt es sie. Aber die ideologische Gleichstellung von illegalen mit unerwünschten Äußerungen verfolgt offensichtlich eher das Ziel, ein derart elementares demokratisches Grundrecht möglichst weitgehend auszuhebeln. Vorwürfe wie «Hassrede», «Delegitimierung des Staates» oder «Volksverhetzung» werden heute inflationär verwendet, um Systemkritik zu unterbinden. Gegen solche Bestrebungen gilt es, sich zu wehren.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ c631e267:c2b78d3e
2024-10-23 20:26:10
@ c631e267:c2b78d3e
2024-10-23 20:26:10Herzlichen Glückwunsch zum dritten Geburtstag, liebe Denk Bar! Wieso zum dritten? Das war doch 2022 und jetzt sind wir im Jahr 2024, oder? Ja, das ist schon richtig, aber bei Geburtstagen erinnere ich mich immer auch an meinen Vater, und der behauptete oft, der erste sei ja schließlich der Tag der Geburt selber und den müsse man natürlich mitzählen. Wo er recht hat, hat er nunmal recht. Konsequenterweise wird also heute dieser Blog an seinem dritten Geburtstag zwei Jahre alt.
Das ist ein Grund zum Feiern, wie ich finde. Einerseits ganz einfach, weil es dafür gar nicht genug Gründe geben kann. «Das Leben sind zwei Tage», lautet ein gängiger Ausdruck hier in Andalusien. In der Tat könnte es so sein, auch wenn wir uns im Alltag oft genug von der Routine vereinnahmen lassen.
Seit dem Start der Denk Bar vor zwei Jahren ist unglaublich viel passiert. Ebenso wie die zweieinhalb Jahre davor, und all jenes war letztlich auch der Auslöser dafür, dass ich begann, öffentlich zu schreiben. Damals notierte ich:
«Seit einigen Jahren erscheint unser öffentliches Umfeld immer fragwürdiger, widersprüchlicher und manchmal schier unglaublich - jede Menge Anlass für eigene Recherchen und Gedanken, ganz einfach mit einer Portion gesundem Menschenverstand.»
Wir erleben den sogenannten «großen Umbruch», einen globalen Coup, den skrupellose Egoisten clever eingefädelt haben und seit ein paar Jahren knallhart – aber nett verpackt – durchziehen, um buchstäblich alles nach ihrem Gusto umzukrempeln. Die Gelegenheit ist ja angeblich günstig und muss genutzt werden.
Nie hätte ich mir träumen lassen, dass ich so etwas jemals miterleben müsste. Die Bosheit, mit der ganz offensichtlich gegen die eigene Bevölkerung gearbeitet wird, war früher für mich unvorstellbar. Mein (Rest-) Vertrauen in alle möglichen Bereiche wie Politik, Wissenschaft, Justiz, Medien oder Kirche ist praktisch komplett zerstört. Einen «inneren Totalschaden» hatte ich mal für unsere Gesellschaften diagnostiziert.
Was mich vielleicht am meisten erschreckt, ist zum einen das Niveau der Gleichschaltung, das weltweit erreicht werden konnte, und zum anderen die praktisch totale Spaltung der Gesellschaft. Haben wir das tatsächlich mit uns machen lassen?? Unfassbar! Aber das Werkzeug «Angst» ist sehr mächtig und funktioniert bis heute.
Zum Glück passieren auch positive Dinge und neue Perspektiven öffnen sich. Für viele Menschen waren und sind die Entwicklungen der letzten Jahre ein Augenöffner. Sie sehen «Querdenken» als das, was es ist: eine Tugend.
Auch die immer ernsteren Zensurbemühungen sind letztlich nur ein Zeichen der Schwäche, wo Argumente fehlen. Sie werden nicht verhindern, dass wir unsere Meinung äußern, unbequeme Fragen stellen und dass die Wahrheit peu à peu ans Licht kommt. Es gibt immer Mittel und Wege, auch für uns.
Danke, dass du diesen Weg mit mir weitergehst!
-
 @ 3eba5ef4:751f23ae
2025-04-04 03:05:59
@ 3eba5ef4:751f23ae
2025-04-04 03:05:59Crypto Insights
How to Identify Bitcoin Mining Nodes: Difficulty, Methods, and Security Risks
In Bitcoin’s P2P network, identifying mining nodes and their adjacent ones can expose potential attack surfaces. Previous research has demonstrated that influential nodes can be identified by coloring nodes with conflicting transactions. These nodes may not be miners' gateway nodes but can ultimately connect to mining ones.
This study, based on the Bitcoin network environment of 2025, explores the difficulty of finding such nodes. The results indicate that these attacks are viable, and leveraging a set of influential mining nodes makes it easier to carry out mainnet partitioning, pinning, replacement cycling, or other yet-undiscovered mempool and Lightning Network attacks.
Boot Protocol: A Decentralized Block Reward Protocol to Reduce Income Volatility
Boot Protocol is a decentralized protocol designed to address Bitcoin mining variance—the fluctuations in the time it takes to find a block and the rewards received—which leads to income volatility. It enables block reward sharing without tracking actual mining work, offering up to 16x lower variance than solo mining while avoiding centralization issues.
- Issue: Centralized mining pools dominate block rewards, leaving small miners with high variance.
- Boot Protocol’s solution: A decentralized, low-variance system that mimics solo mining while offering mining pool advantages.
- Advantages: Compared to solo mining, it reduces variance by up to 16x and is more resistant to regulatory attacks than centralized mining pools.
- Against withholding attacks: The protocol is designed to prevent block withholding attacks by incentivizing miners to submit blocks as soon as possible.
- Potential: Boot Protocol has the potential to revolutionize decentralized mining by eliminating the shortcomings of approaches like P2Pool and Braid Pool.
Trustless Coin Flip Game Built on Taproot and Multisig
Coinflip is a two-player coin-flipping game inspired by the concept of "Zero-Collateral Lotteries" and built using Taproot and multisig.
Exploring Duplicate Transactions in Bitcoin
In the Bitcoin blockchain, there are two sets of completely identical transactions from mid-November 2010, where one set sandwiches the other. Since the coinbase transactions have no inputs but newly generated coins, two different coinbase transactions can send the same amount to the same address in the exact same way, resulting in identical transactions.
Because duplicate transactions can cause confusion, developers have been researching solutions for years, but no ideal fix has been found. The next potential duplicate transaction event is expected in 2046. While the current risks associated with duplicate transactions are low, this remains an intriguing and novel issue. This article explores the topic in detail.
A Fee Protocol to Prevent Lightning Network Spam
Lightning Network spam happens when some one floods the network with a constant stream of HTLCs to disrupt legitimate payments. To tackle this, this paper proposes a protocol for assigning and collecting fees in the Lightning Network to mitigate spam risks. It establishes fees corresponding to all significant costs, whereas previous attempts charged fees for delayed and/or failed payments, omitted certain costs or relied on trust to prevent theft.
This protocol introduces a "griefer-penalization" mechanism: if a party suffers malicious behavior (griefing) from a channel partner, they can be made to lose certain funds, but the griefer also bears a corresponding cost. As a result, a party that only selects self-interested partners is unlikely to be griefed.
Cashu Launches Instant Offline Ecash Payments
Cashu has developed a new tap-to-pay feature that enables instant, offline ecash payments via NFC.
As a bearer token, ecash is stored directly on the user’s device rather than on a server. This is why it integrates so well with NFC.
Coinbase Open-Sourced Multi-Party Computation Library
Coinbase has open-sourced its Multi-Party Computation (MPC) engine. Coinbase's cryptography lead, Yehuda Lindell, stated that the library supports two-party and multi-party signatures for ECDSA and Schnorr/EdDSA, as well as tools for DKG, backup, and more.
This release includes the full code stack, including commitments, random oracles, secret sharing, oblivious transfer (basic and extension), and a series of ZK proofs for various threshold signing tasks. All protocols come with complete specifications and theory documents. The team has also conducted full benchmark tests, providing insights into running time and bandwidth consumption from low-level primitives to full protocols.
RISC Zero zkVM Advances: R0VM 2.0 and OP Kailua
RISC Zero is advancing its zkVM technology with the release of R0VM 2.0 and the introduction of OP Kailua to enhance blockchain verifiability, security, and scalability.
RISC Zero uses Picus for formal verification of zkVM components. R0VM 2.0 will be the first formally verified RISC-V zkVM, addressing security risks from insufficient constraints in ZK systems, ensuring provable correctness, and offering stronger security guarantees for developers.
OP Kailua is a zkVM opcode that enables efficient on-chain validity proofs, allowing OP chains to upgrade into ZK Rollups, offering: * <1 hour Finality * Stronger security requiring only one honest sequencer * Lower costs as low as $0.00012/tx
Three Blocks Recently Solo-Mined
Three independent miners successfully mined Bitcoin blocks recently, signaling a rise in home mining.
- Block 888,737 was mined using a DIY FutureBit Apollo device, earning 3.125 BTC plus fees.
- An independent miner with a hashrate below 1 TH/s mined block 888,989.
- A miner using a $300 setup successfully mined block 889,240.
New Book | Principles of Bitcoin: Cutting Through the Noise to Reveal the Core Value
Principles of Bitcoin constructs a holistic framework understanding Bitcoin from first principles. It strips away industry hype, jargon, and superficial analysis to reveal the ingenuity of Satoshi’s creation and its implications for money, governance, and individual freedom.
By examining Bitcoin through technical, economic, political, and philosophical lenses, the author argues that only through this holistic understanding can one grasp its significance. He presents Bitcoin as a tool for individual empowerment and economic sovereignty, showing how it challenges traditional financial systems, and why it is a unique, non-replicable innovation in the digital asset space.
Top Reads on Blockchain and Beyond
Podcast | Can Pricing Solve Congestion? Applying Toll Economics to Crypto
To alleviate traffic congestion, New York City implemented congestion pricing in early 2025. Could similar mechanisms be applied to the crypto? In this podcast episode, congestion pricing expert (and one of its key proponents) Michael Ostrovsky discusses the economics behind congestion pricing and explores its implications for both city blocks and blockchain.
Model Context Protocol: A Unified Framework for Instant, Bidirectional AI Agent Communication
MCP (Model Context Protocol) was introduced by Anthropic in late 2024 as an open standard to enhance the connection of AI agent LLM apps and user data. Unlike traditional AI integrations that rely on fragmented, custom-built solutions, MCP provides a unified framework for bidirectional communication. This allows AI agents not only to pull in external data, but also to send updates back to these systems, enabling more dynamic and autonomous behavior. Additionally, MCP’s open-source nature fosters industry-wide collaboration, contrasting with the more siloed approaches of centralized AI companies.
This tweet offers a summary of MCP’s capabilities and significance.
The Era of Culturementals: Culture is More Fundamental than Technology
This post argues that the crypto space has repeatedly demonstrated that culture trumps technology. This perspective defines the rise of Culture Chains—blockchains shaped not by their technical capabilities, but by the communities they serve. Culture Chains can be seen as an evolution of “vertical blockchains”—designed not for universal adoption but for specific niche groups, such as anime fans, role-playing gamers, or meme lovers. Functioning like digital city-states, these chains build around shared values, language, and interests, offering tailored infrastructure, governance models, and token economies.
-
 @ a95c6243:d345522c
2024-10-19 08:58:08
@ a95c6243:d345522c
2024-10-19 08:58:08Ein Lämmchen löschte an einem Bache seinen Durst. Fern von ihm, aber näher der Quelle, tat ein Wolf das gleiche. Kaum erblickte er das Lämmchen, so schrie er:
"Warum trübst du mir das Wasser, das ich trinken will?"
"Wie wäre das möglich", erwiderte schüchtern das Lämmchen, "ich stehe hier unten und du so weit oben; das Wasser fließt ja von dir zu mir; glaube mir, es kam mir nie in den Sinn, dir etwas Böses zu tun!"
"Ei, sieh doch! Du machst es gerade, wie dein Vater vor sechs Monaten; ich erinnere mich noch sehr wohl, daß auch du dabei warst, aber glücklich entkamst, als ich ihm für sein Schmähen das Fell abzog!"
"Ach, Herr!" flehte das zitternde Lämmchen, "ich bin ja erst vier Wochen alt und kannte meinen Vater gar nicht, so lange ist er schon tot; wie soll ich denn für ihn büßen."
"Du Unverschämter!" so endigt der Wolf mit erheuchelter Wut, indem er die Zähne fletschte. "Tot oder nicht tot, weiß ich doch, daß euer ganzes Geschlecht mich hasset, und dafür muß ich mich rächen."
Ohne weitere Umstände zu machen, zerriß er das Lämmchen und verschlang es.
Das Gewissen regt sich selbst bei dem größten Bösewichte; er sucht doch nach Vorwand, um dasselbe damit bei Begehung seiner Schlechtigkeiten zu beschwichtigen.
Quelle: https://eden.one/fabeln-aesop-das-lamm-und-der-wolf
-
 @ ed84ce10:cccf4c2a
2025-03-19 03:46:17
@ ed84ce10:cccf4c2a
2025-03-19 03:46:17DoraHacks: Pioneering the Global Hacker Movement
DoraHacks is the world’s largest hackathon community, driving radical innovation across multiple industries. Now, a similar hacker movement is emerging in biotech—what we call the FDA-Free Society. At DoraHacks, this is our core focus in the life sciences. We believe that medical and biotech innovation should not be held hostage by bureaucracy. Instead, it should be free to evolve at the pace of technological progress.
The FDA: The Biggest Bottleneck to Biotech Innovation
For decades, the Food and Drug Administration (FDA) has been the single greatest obstacle to progress in medicine and biotech. While ostensibly designed to ensure safety and efficacy, in reality, it has functioned as an entrenched bureaucracy that stifles innovation.
1. A Broken Approval Process
The FDA operates on timelines that make no sense in an era of exponential technological growth. Getting a new drug or therapy to market takes 10-15 years. By the time a breakthrough therapy is approved, entire generations of patients have already suffered or died waiting.
2. Astronomical Compliance Costs
Clinical trials under FDA oversight are prohibitively expensive. This eliminates most startups from even attempting disruptive innovation. Many promising therapies never see the light of day—not because they don’t work, but because the cost of compliance is too high.
3. The FDA-Pharma Cartel
The regulatory framework is not neutral—it overwhelmingly benefits Big Pharma. The FDA’s Byzantine approval system creates a protective moat for legacy pharmaceutical companies, while smaller biotech startups are crushed under compliance burdens. The result? Less innovation, more monopolization, and fewer choices for patients.
Market-Driven Biotech Innovation Is the Future
When bureaucracies control innovation, progress slows. When markets drive innovation, progress accelerates.
1. Let the Market Decide What Works
Why should government regulators dictate which treatments are available? In an open system, patients and doctors—not bureaucrats—should determine which therapies succeed or fail.
2. The "Right to Try" Loophole Proves the FDA Is Obsolete
The U.S. Right to Try Act already allows terminally ill patients to access experimental drugs before FDA approval. This proves an essential truth: The regulatory state is holding back life-saving treatments. If dying patients can bypass the FDA, why can’t everyone?
3. Startups Move Faster Than Bureaucracies
The success of mRNA technology was not driven by the FDA—it was driven by startups operating at the speed of the market. This is a template for the future. Regulation slows innovation. Entrepreneurs accelerate it.
BioHack: Breaking Free From the FDA’s Grip
One of the most important frontiers in biotech today is anti-aging and longevity research. Yet, the FDA has no framework for approving treatments that extend life. The result? A regulatory death sentence for one of the most transformative fields of medicine.
1. Biotech Needs FDA-Free Experimental Zones
In the future, biotech R&D should function like open-source software—free, experimental, and outside the reach of outdated regulators. We need FDA-Free labs, FDA-Free clinical trials, and FDA-Free therapeutics.
2. Decentralized Healthcare Will Disrupt Big Pharma
A new era of decentralized biotech is emerging—privately funded labs, medical DAOs, and startup-driven healthcare systems. The power to determine the future of medicine must shift away from centralized bureaucracies and Big Pharma toward entrepreneurs, scientists, and patients.
Conclusion: The Hacker Revolution in Biotech Is Here
The FDA-Free Society is not a thought experiment. It is an inevitability. Innovation will not be stopped. DoraHacks is committed to making BioHack a reality.
-
 @ 7bdef7be:784a5805
2025-04-02 12:12:12
@ 7bdef7be:784a5805
2025-04-02 12:12:12We value sovereignty, privacy and security when accessing online content, using several tools to achieve this, like open protocols, open OSes, open software products, Tor and VPNs.
The problem
Talking about our social presence, we can manually build up our follower list (social graph), pick a Nostr client that is respectful of our preferences on what to show and how, but with the standard following mechanism, our main feed is public, so everyone can actually snoop what we are interested in, and what is supposable that we read daily.
The solution
Nostr has a simple solution for this necessity: encrypted lists. Lists are what they appear, a collection of people or interests (but they can also group much other stuff, see NIP-51). So we can create lists with contacts that we don't have in our main social graph; these lists can be used primarily to create dedicated feeds, but they could have other uses, for example, related to monitoring. The interesting thing about lists is that they can also be encrypted, so unlike the basic following list, which is always public, we can hide the lists' content from others. The implications are obvious: we can not only have a more organized way to browse content, but it is also really private one.
One might wonder what use can really be made of private lists; here are some examples:
- Browse “can't miss” content from users I consider a priority;
- Supervise competitors or adversarial parts;
- Monitor sensible topics (tags);
- Following someone without being publicly associated with them, as this may be undesirable;
The benefits in terms of privacy as usual are not only related to the casual, or programmatic, observer, but are also evident when we think of how many bots scan our actions to profile us.
The current state
Unfortunately, lists are not widely supported by Nostr clients, and encrypted support is a rarity. Often the excuse to not implement them is that they are harder to develop, since they require managing the encryption stuff (NIP-44). Nevertheless, developers have an easier option to start offering private lists: give the user the possibility to simply mark them as local-only, and never push them to the relays. Even if the user misses the sync feature, this is sufficient to create a private environment.
To date, as far as I know, the best client with list management is Gossip, which permits to manage both encrypted and local-only lists.
Beg your Nostr client to implement private lists!
-
 @ 04ff5a72:22ba7b2d
2025-03-19 03:25:28
@ 04ff5a72:22ba7b2d
2025-03-19 03:25:28The Evolution of the "World Wide Web"
The internet has undergone a remarkable transformation since its inception, evolving from a collection of static pages to a dynamic, interconnected ecosystem, and now progressing toward a decentralized future. This evolution is commonly divided into three distinct phases: Web 1, Web 2, and the emerging Web 3. Each phase represents not only technological advancement but fundamental shifts in how we interact with digital content, who controls our data, and how value is created and distributed online. While Web 1 and Web 2 have largely defined our internet experience to date, Web 3 promises a paradigm shift toward greater user sovereignty, decentralized infrastructure, and reimagined ownership models for digital assets.
The Static Beginning: Web 1.0
The first iteration of the web, commonly known as Web 1.0, emerged in the early 1990s and continued until the late 1990s. This period represented the internet's infancy, characterized by static pages with limited functionality and minimal user interaction[1]. At the core of Web 1 was the concept of information retrieval rather than dynamic interaction.
Fundamental Characteristics of Web 1
During the Web 1 era, websites primarily served as digital brochures or informational repositories. Most sites were static, comprised of HTML pages containing fixed content such as text, images, and hyperlinks[1]. The HTML (Hypertext Markup Language) provided the structural foundation, while CSS (Cascading Style Sheets) offered basic styling capabilities. These technologies enabled the creation of visually formatted content but lacked the dynamic elements we take for granted today.
The Web 1 experience was predominantly one-directional. The majority of internet users were passive consumers of content, while creators were primarily web developers who produced websites with mainly textual or visual information[2]. Interaction was limited to basic navigation through hyperlinks, with few opportunities for users to contribute their own content or engage meaningfully with websites.
Technical limitations further defined the Web 1 experience. Information access was significantly slower than today's standards, largely due to the prevalence of dial-up connections. This constraint meant websites needed to be optimized for minimal bandwidth usage[1]. Additionally, security measures were rudimentary, making early websites vulnerable to various cyberattacks without adequate protection systems in place.
The Social Revolution: Web 2.0
As the internet matured in the late 1990s and early 2000s, a significant transformation occurred. Web 2.0 emerged as a more dynamic, interactive platform that emphasized user participation, content creation, and social connectivity[6]. This shift fundamentally changed how people engaged with the internet, moving from passive consumption to active contribution.
The Rise of Social Media and Big Data
Web 2.0 gave birth to social media platforms, interactive web applications, and user-generated content ecosystems. Companies like Google, Facebook, Twitter, and Amazon developed business models that leveraged user activity and content creation[4]. These platforms transformed from simple information repositories into complex social networks and digital marketplaces.
Central to the Web 2.0 revolution was the collection and analysis of user data on an unprecedented scale. Companies developed sophisticated infrastructure to handle massive amounts of information. Google implemented systems like the Google File System (GFS) and Spanner to store and distribute data across thousands of machines worldwide[4]. Facebook developed cascade prediction systems to manage user interactions, while Twitter created specialized infrastructure to process millions of tweets per minute[4].
These technological advancements enabled the monetization of user attention and personal information. By analyzing user behavior, preferences, and social connections, Web 2.0 companies could deliver highly targeted advertising and personalized content recommendations. This business model generated immense wealth for platform owners while raising significant concerns about privacy, data ownership, and the concentration of power in the hands of a few technology giants.
The Decentralized Future: Web 3.0
Web 3 represents the next evolutionary stage of the internet, characterized by principles of decentralization, transparency, and user sovereignty[6]. Unlike previous iterations, Web 3 seeks to redistribute control from centralized entities to individual users and communities through blockchain technology and decentralized protocols.
Blockchain as the Foundation
The conceptual underpinnings of Web 3 emerged with the creation of Bitcoin in 2009. Bitcoin introduced a revolutionary approach to digital transactions by enabling peer-to-peer value transfer without requiring a central authority. This innovation demonstrated that trust could be established through cryptographic proof rather than relying on traditional financial institutions.
Ethereum expanded upon Bitcoin's foundation by introducing programmable smart contracts, which allowed for the creation of decentralized applications (dApps) beyond simple financial transactions. This breakthrough enabled developers to build complex applications with self-executing agreements that operate transparently on the blockchain[6].
Ownership and Data Sovereignty
A defining characteristic of Web 3 is the emphasis on true digital ownership. Through blockchain technology and cryptographic tokens, individuals can now assert verifiable ownership over digital assets in ways previously impossible[6]. This stands in stark contrast to Web 2 platforms, where users effectively surrendered control of their content and data to centralized companies.
The concept of self-custody exemplifies this shift toward user sovereignty. Platforms like Trust Wallet enable individuals to maintain control over their digital assets across multiple blockchains without relying on intermediaries[5]. Users hold their private keys, ensuring that they—not corporations or governments—have ultimate authority over their digital property.
Decentralized Physical Infrastructure Networks (DePIN)
Web 3 extends beyond digital assets to reimagine physical infrastructure through Decentralized Physical Infrastructure Networks (DePIN). These networks connect blockchain technology with real-world systems, allowing people to use cryptocurrency tokens to build and manage physical infrastructure—from wireless hotspots to energy systems[7].
DePIN projects decentralize ownership and governance of critical infrastructure, creating more transparent, efficient, and resilient systems aligned with Web 3 principles[7]. By distributing control among network participants rather than centralizing it within corporations or governments, these projects bridge the gap between digital networks and physical reality.
Non-Fungible Tokens and Intellectual Property
Non-Fungible Tokens (NFTs) represent another revolutionary aspect of Web 3, providing a mechanism for verifying the authenticity and ownership of unique digital items. NFTs enable creators to establish provenance for digital art, music, virtual real estate, and other forms of intellectual property, addressing longstanding issues of duplication and unauthorized distribution in the digital realm[6].
This innovation has profound implications for creative industries, potentially enabling more direct relationships between creators and their audiences while reducing dependence on centralized platforms and intermediaries.
Nostr: A Decentralized Protocol for Social Media and Communication
Nostr (Notes and Other Stuff Transmitted by Relays) is a decentralized and censorship-resistant communication protocol designed to enable open and secure social networking. Unlike traditional social media platforms that rely on centralized servers and corporate control, Nostr allows users to communicate directly through a network of relays, ensuring resilience against censorship and deplatforming.
The protocol operates using simple cryptographic principles: users generate a public-private key pair, where the public key acts as their unique identifier, and messages are signed with their private key. These signed messages are then broadcast to multiple relays, which store and propagate them to other users. This structure eliminates the need for a central authority to control user identities or content distribution[8].
As concerns over censorship, content moderation, and data privacy continue to rise, Nostr presents a compelling alternative to centralized social media platforms. By decentralizing content distribution and giving users control over their own data, it aligns with the broader ethos of Web3—empowering individuals and reducing reliance on corporate intermediaries[9].
Additionally Nostr implements a novel way for users to monetize their content via close integration with Bitcoin's "Lightning Network"[11] -- a means by which users are able to instantly transmit small sums (satoshi's, the smallest unit of Bitcoin) with minimal fees. This feature, known as “zapping,” allows users to send micropayments directly to content creators, tipping them for valuable posts, comments, or contributions. By leveraging Lightning wallets, users can seamlessly exchange value without relying on traditional payment processors or centralized monetization models. This integration not only incentivizes quality content but also aligns with Nostr’s decentralized ethos by enabling peer-to-peer financial interactions that are censorship-resistant and borderless.
For those interested in exploring Nostr, setting up an account requires only a private key, and users can begin interacting with the network immediately by selecting a client that suits their needs. The simplicity and openness of the protocol make it a promising foundation for the next generation of decentralized social and communication networks.
Alternative Decentralized Models: Federation
Not all Web 3 initiatives rely on blockchain technology. Platforms like Bluesky are pioneering federation approaches that allow users to host their own data while maintaining seamless connectivity across the network[10]. This model draws inspiration from how the internet itself functions: just as anyone can host a website and change hosting providers without disrupting visitor access, Bluesky enables users to control where their social media data resides.
Federation lets services be interconnected while preserving user choice and flexibility. Users can move between various applications and experiences as fluidly as they navigate the open web[10]. This approach maintains the principles of data sovereignty and user control that define Web 3 while offering alternatives to blockchain-based implementations.
Conclusion
The evolution from Web 1 to Web 3 represents a profound transformation in how we interact with the internet. From the static, read-only pages of Web 1 through the social, data-driven platforms of Web 2, we are now entering an era defined by decentralization, user sovereignty, and reimagined ownership models.
Web 3 technologies—whether blockchain-based or implementing federation principles—share a common vision of redistributing power from centralized entities to individual users and communities. By enabling true digital ownership, community governance, and decentralized infrastructure, Web 3 has the potential to address many of the concerns that have emerged during the Web 2 era regarding privacy, control, and the concentration of power.
As this technology continues to mature, we may witness a fundamental reshaping of our digital landscape toward greater transparency, user autonomy, and equitable value distribution—creating an internet that more closely aligns with its original promise of openness and accessibility for all.
Sources
[1] What is WEB1? a brief history of creation - White and Partners https://whiteand.partners/en/what-is-web1-a-brief-history-of-creation/ [2] Evolution of the Internet - from web1.0 to web3 - LinkedIn https://www.linkedin.com/pulse/evolution-internet-from-web10-web3-ravi-chamria [3] Web3 Social: Create & Monetize with Smart Contracts - Phala Network https://phala.network/web3-social-create-monetize-with-smart-contracts [4] [PDF] Big Data Techniques of Google, Amazon, Facebook and Twitter https://www.jocm.us/uploadfile/2018/0613/20180613044107972.pdf [5] True crypto ownership. Powerful Web3 experiences - Trust Wallet https://trustwallet.com [6] Web3: Revolutionizing Digital Ownership and NFTs - ThoughtLab https://www.thoughtlab.com/blog/web3-revolutionizing-digital-ownership-and-nfts/ [7] DePIN Crypto: How It's Revolutionizing Infrastructure in Web3 https://www.ulam.io/blog/how-depin-is-revolutionizing-infrastructure-in-the-web3-era [8] Nostr: Notes and Other Stuff… https://nostr.com/ [9] Nostr: The Importance of Censorship-Resistant Communication... https://bitcoinmagazine.com/culture/nostr-the-importance-of-censorship-resistant-communication-for-innovation-and-human-progress- [10] Bluesky: An Open Social Web https://bsky.social/about/blog/02-22-2024-open-social-web [11] Wikipedia: Lightning Network https://en.wikipedia.org/wiki/Lightning_Network
-
 @ 04ff5a72:22ba7b2d
2025-03-19 02:17:03
@ 04ff5a72:22ba7b2d
2025-03-19 02:17:03Web3 in the Physical World
In the evolving landscape of Web3 technologies, Decentralized Physical Infrastructure Networks (DePIN) represent one of the most promising developments, extending blockchain capabilities beyond purely digital applications into the physical world. This emerging paradigm is reshaping how we conceptualize, build, and maintain infrastructure by leveraging blockchain technology to create community-owned physical networks. As of early 2025, DePIN has grown from a theoretical concept to a multi-billion dollar sector with applications spanning telecommunications, energy, transportation, and data services.
Defining DePIN in the Web3 Ecosystem
Decentralized Physical Infrastructure Networks (DePIN) represent the convergence of blockchain technology with physical infrastructure, creating systems where real-world networks and devices are collectively owned, managed, and operated by communities rather than centralized entities[1][4]. While Web3 primarily focuses on decentralized digital applications and services, DePIN extends these principles into the physical world, marking what many consider the natural evolution of blockchain technology beyond purely online environments[3].
Core Characteristics of DePIN
At its foundation, DePIN leverages blockchain technology to decentralize the control and management of physical devices and infrastructure[2]. This approach addresses several limitations of traditional centralized infrastructure networks, including data privacy risks, service disruptions, and substantial expansion costs[2]. By distributing ownership and governance across network participants, DePIN creates more transparent, efficient, and resilient systems that align with the fundamental principles of Web3[1].
The technical architecture of DePIN combines several key elements:
- Blockchain Foundation: DePIN utilizes blockchain networks to provide transparent, secure, and immutable record-keeping for all network operations[5].
- Tokenized Incentives: Participants who contribute resources such as bandwidth, energy, or storage are rewarded with crypto tokens, creating economic incentives for network growth and maintenance[1].
- Smart Contracts: Automated agreements handle resource distribution, monitor usage, and execute payments without requiring trusted intermediaries[1][8].
- Decentralized Governance: Many DePIN projects implement DAO (Decentralized Autonomous Organization) structures for democratic decision-making among network participants[8].
How DePIN Works Within Web3
DePIN operates by incentivizing individuals and organizations to contribute physical resources to a network in exchange for tokenized rewards. This model creates a powerful alternative to traditional infrastructure deployment, which typically requires massive upfront investment by corporations or governments.
Incentive Mechanisms
The core functioning of DePIN relies on properly aligned incentive structures. When individuals contribute resources—whether it's computing power, network bandwidth, or physical devices—they receive tokens as compensation[1]. These tokens often serve multiple purposes within the ecosystem:
- Reward Distribution: Smart contracts automatically allocate tokens based on the quantity and quality of resources contributed[8].
- Governance Rights: Token holders can often participate in network decision-making, voting on upgrades, policy changes, and resource allocation[8].
- Service Access: Tokens may be required to access the network's services, creating a circular economy within the ecosystem.
Community Participation
DePIN networks are typically open and permissionless, meaning anyone can join and start contributing[3]. This drastically lowers barriers to entry compared to traditional infrastructure development, which often requires significant capital and regulatory approvals. The peer-to-peer nature of these networks makes initial infrastructure deployment much more manageable through crowdsourcing[3].
Major Applications of DePIN in the Web3 Space
As of early 2025, DePIN has expanded across numerous sectors, demonstrating the versatility of decentralized approaches to physical infrastructure. Several key applications have emerged as particularly successful implementations of the DePIN model.
Telecommunications and Connectivity
One of the most established DePIN applications is in telecommunications, where projects like Helium and Althea have created decentralized wireless and broadband networks[5][9]. Helium’s model allows individuals to set up wireless hotspots and earn HNT tokens for providing connectivity, enabling a distributed, user-powered wireless network[5]. Althea, on the other hand, focuses on decentralized internet service provision by allowing users to buy and sell bandwidth automatically, creating a self-sustaining and community-driven ISP model. This approach is particularly effective in rural and underserved regions, where traditional telecom providers may not find it economically viable to invest in infrastructure[9]. Both projects demonstrate how blockchain and incentive-driven models can disrupt conventional telecom industries and expand access to connectivity.
Energy Networks
DePIN is revolutionizing energy infrastructure through projects like Arkreen, which enables individuals and organizations to contribute excess renewable energy to a global network[5]. These decentralized energy systems allow small-scale producers to monetize their resources while contributing to more resilient and sustainable energy grids[1].
Data Storage and Computing
Decentralized storage networks like Filecoin demonstrate how DePIN principles can transform data infrastructure[5]. Users offer spare storage capacity on their devices in exchange for FIL tokens, creating a globally distributed storage network that competes with centralized cloud services[5]. This approach enhances data resilience while enabling individual participation in the digital storage economy.
Mapping and Location Services
Hivemapper represents an innovative application of DePIN in creating decentralized mapping services[6][8]. Users contribute mapping data collected through 4K dashcams while driving, building a community-owned alternative to centralized mapping services like Google Maps[6][8]. As of October 2024, Hivemapper had successfully mapped significant portions of the global road network through this crowdsourced approach[8].
Transportation and Mobility
Decentralized ride-sharing platforms like DRIFE are emerging as DePIN alternatives to traditional services like Uber and Lyft[6]. These platforms connect drivers and passengers directly through blockchain networks, reducing fees and returning more value to network participants rather than corporate intermediaries.
The Economic Impact and Market Potential of DePIN
DePIN represents a substantial and rapidly growing segment of the Web3 economy. According to industry research, the market shows significant potential for continued expansion in the coming years.
Current Market Status
As of early 2025, the DePIN sector has achieved considerable market presence:
- Market Capitalization: The current market capitalization of DePIN projects is approximately $27 billion, with a daily trading volume of $1.8 billion according to DePIN Scan[7].
- Investment Activity: Venture capitalists have recognized DePIN's potential, directing billions of dollars into the sector. Some have even created dedicated funds specifically for DePIN protocols[7].
- Growth Trajectory: DePIN has been identified as one of the major crypto trends of 2024-2025, with accelerating adoption across multiple industries[7].
Future Market Potential
The long-term outlook for DePIN appears promising according to industry analysts:
- Total Addressable Market: Messari, an independent crypto research firm, estimates DePIN's Total Addressable Market at $2.2 trillion, with projections showing growth to $3.5 trillion by 2028[6].
- Theoretical Upper Limit: In theory, DePIN's potential market extends to the entire non-digital economy, which according to World Bank figures approaches $90 trillion[6].
Benefits and Advantages of the DePIN Model
The DePIN approach offers several distinct advantages over traditional centralized infrastructure models, explaining its rapid adoption within the Web3 ecosystem.
Collective Ownership
DePIN enables community ownership of infrastructure that has traditionally been centralized under corporate or government control[5]. This democratization of ownership distributes both the benefits and responsibilities of infrastructure management among a broader group of stakeholders.
Enhanced Transparency
With DePIN, all network actions are recorded on-chain, ensuring open access to vital network data[5]. This transparency builds trust among participants and reduces the information asymmetry that often exists in centralized systems.
Improved Efficiency
By leveraging underutilized resources and implementing smart contracts, DePIN can reduce waste and administrative overhead[5]. This efficiency translates to lower costs and improved resource allocation compared to traditional infrastructure models.
Resilience Through Decentralization
Distributed networks are inherently more resilient to failures and attacks than centralized systems. By eliminating single points of failure, DePIN creates infrastructure that can continue functioning even when individual components experience issues.
Challenges and Future Considerations
Despite its promising potential, DePIN faces several significant challenges that must be addressed for widespread adoption.
Technical Scalability
Many DePIN networks struggle with scalability issues, particularly as they grow to accommodate more users and higher transaction volumes. Developing more efficient consensus mechanisms and layer-2 solutions remains an important technical challenge.
Regulatory Uncertainty
The decentralized nature of DePIN projects creates regulatory challenges in many jurisdictions. Finding the right balance between innovation and compliance with existing regulations will be crucial for long-term success.
Economic Sustainability
Creating sustainable tokenomics models that properly align incentives over the long term remains difficult. Many projects must carefully balance immediate rewards with long-term value creation to maintain network growth and stability.
Conclusion
Decentralized Physical Infrastructure Networks represent one of the most promising extensions of Web3 principles beyond purely digital applications. By leveraging blockchain technology, tokenized incentives, and community participation, DePIN is transforming how physical infrastructure is built, maintained, and governed.
As the sector continues to mature throughout 2025 and beyond, we can expect to see DePIN concepts applied to an increasingly diverse range of infrastructure challenges. The intersection of DePIN with other emerging technologies like artificial intelligence and the Internet of Things will likely create entirely new forms of infrastructure that we can barely imagine today.
The growth of DePIN underscores a fundamental shift in our approach to infrastructure—moving from centralized, corporate-controlled models toward more democratic, transparent, and community-driven systems. This transformation embodies the core promise of Web3: not just a more decentralized internet, but a more decentralized world.
Sources
[1] DePIN Crypto: How It's Revolutionizing Infrastructure in Web3 https://www.ulam.io/blog/how-depin-is-revolutionizing-infrastructure-in-the-web3-era [2] Decentralized Physical Infrastructure Network (DePIN) - arXiv https://arxiv.org/html/2406.02239v1 [3] What is DePIN - decentralized physical infrastructure network? https://limechain.tech/blog/what-is-depin [4] DePIN Explained: Bringing Real-World Devices to Web3 https://nftnewstoday.com/2025/01/28/depin-explained-bringing-real-world-devices-web3 [5] An Introduction to Decentralized Physical Infrastructure Networks ... https://www.cryptoaltruism.org/blog/infographic-an-introduction-to-decentralized-physical-infrastructure-networks-depin [6] DePIN Explained: What Are Decentralized Physical Infrastructure ... https://hackernoon.com/depin-explained-what-are-decentralized-physical-infrastructure-networks [7] Revolutionizing Infrastructure: Understanding DePINs and Their ... https://blaize.tech/blog/decentralized-physical-infrastructure-networks-depin/ [8] What is DePIN? The Future of Decentralized Physical Infrastructure ... https://osl.com/academy/article/what-is-depin-the-future-of-decentralized-physical-infrastructure-networks [9] [PDF] Althea Whitepaper v2 https://blog.althea.net/content/files/2024/06/Althea-Whitepaper-v2.0.pdf
-
 @ 71550e6c:b64c37a9
2025-03-29 10:55:55
@ 71550e6c:b64c37a9
2025-03-29 10:55:55Just do the same as this video shows.
Here's the video: https://cdn.azzamo.net/7cdcc2718f1e15eb03e323f62e07582b4001da273aa5c21475d680f02b32f0e9.mp4
One caveat: do not trust the draft will be kept here after you close
nak fs. Wait, no, it definitely won't stay here, but I'm not even sure it will stay here if you only navigate away and come back later, FUSE is weird and I didn't test.But at least it should work for copy-pasting. Or writing everything in one go.
-
 @ 04ff5a72:22ba7b2d
2025-03-19 02:06:34
@ 04ff5a72:22ba7b2d
2025-03-19 02:06:34Taking Back Control of the Internet
Web3 represents a fundamental reimagining of how users interact with and control their data online, marking a significant departure from the Web2 paradigm that has dominated the internet for the past two decades. This transformation is centered around shifting power dynamics, decentralizing authority, and returning data sovereignty to individuals. While Web2 created unprecedented connectivity and digital services, it came with significant trade-offs in terms of privacy, security, and user autonomy. Web3 technologies aim to address these shortcomings through blockchain-based systems and decentralized architectures that fundamentally alter who controls, benefits from, and has access to user data.
Fundamental Shift in Data Ownership
Web2: Corporate Control and Exploitation
In the Web2 paradigm, users effectively surrender ownership of their personal data to centralized platforms. When individuals sign up for services from tech giants like Google, Facebook, or Twitter, they typically grant these companies extensive rights to collect, analyze, and monetize their information[2]. This arrangement creates a profound power imbalance where users have minimal visibility into or control over how their data is used. Companies can sell this information to third parties for marketing purposes without providing meaningful compensation to the individuals who generated it[4].
This centralized model has created what many critics describe as "surveillance capitalism," where detailed profiles of users are constructed across platforms to predict and influence behavior. The value generated from this data has contributed to the immense wealth of a small number of technology corporations while leaving users with little to show for their contributions[4].
Web3: User-Centric Ownership Model
Web3 fundamentally inverts this ownership paradigm. In Web3 systems, users retain ownership of their own data and can make deliberate decisions about how it is used, shared, or monetized[2]. This principle is enabled through blockchain technology and cryptographic mechanisms that allow individuals to maintain control over their digital footprint without relying on centralized intermediaries[3].
The decentralized architecture of Web3 systems means that personal information is not concentrated in massive corporate databases but is instead distributed across networks with varying levels of user-controlled access[7]. This shift represents not merely a technical change but a philosophical reorientation of the internet toward user sovereignty.
Decentralized Infrastructure and Enhanced Security
Web2: Vulnerable Centralized Systems
The Web2 model relies heavily on centralized servers and data centers controlled by individual companies. This architecture creates significant vulnerabilities, as these centralized repositories become high-value targets for hackers and malicious actors[2]. Data breaches affecting millions of users have become increasingly common, demonstrating the inherent security weaknesses of storing vast amounts of personal information in single locations.
Additionally, the centralized nature of Web2 infrastructure creates single points of failure where service disruptions or security compromises can have widespread impacts across entire user bases[8].
Web3: Distributed Networks and Cryptographic Protection
Web3 transforms this security model through decentralization. By leveraging blockchain technology, Web3 distributes data across multiple nodes worldwide rather than concentrating it in centralized servers[3]. This architecture significantly increases resilience against attacks, as compromising the network would require breaching numerous points simultaneously rather than a single centralized database[2].
Cryptographic protection is fundamental to Web3 systems, with data access controlled through sophisticated encryption mechanisms. This approach makes unauthorized access significantly more difficult and provides users with verifiable assurance about who can see their information and under what circumstances[5].
The Web3 infrastructure model explicitly addresses the vulnerability of centralized systems by removing single points of failure and distributing both data and control across broad networks of participants[8].
Self-Sovereign Identity and Authentication
Web2: Platform-Dependent Digital Identities
In Web2, digital identities are typically fragmented across numerous platforms, each requiring separate credentials and controlling different aspects of a user's online presence[4]. This fragmentation creates security vulnerabilities and makes it difficult for individuals to maintain a coherent digital footprint or track how their information is being used across services.
Users often rely on third-party identity providers (like "Sign in with Google" or "Login with Facebook"), which further centralizes control and creates dependencies that can be revoked at the platform's discretion[4].
Web3: User-Controlled Identity Management
Web3 introduces the concept of self-sovereign identity, where users create and manage decentralized identifiers that they fully control without intermediaries[1][5]. Instead of relying on centralized identity providers that can restrict access or modify terms, individuals maintain ownership of their digital identities across different applications and services.
Decentralized Identifiers (DIDs) and Self-Sovereign Identity (SSI) systems enable secure identity management that preserves privacy while still allowing for verified interactions[1][3]. Users can selectively disclose only the specific information needed for particular interactions without revealing unrelated personal details, significantly reducing unnecessary data exposure[3].
This approach minimizes the risk of identity theft by eliminating the centralized repositories of identity information that currently make attractive targets for attackers[3].
Transparency and Consent Mechanisms
Web2: Opaque Data Practices and Forced Consent
Web2 platforms are notorious for their complex and often deliberately obscure data governance practices[4]. Users typically must agree to extensive terms of service and privacy policies they rarely read or fully understand. Even when policies are comprehensible, users face a binary choice: accept all conditions or forgo the service entirely.
This lack of transparency has eroded trust, with many users unaware of how extensively their information is being collected, analyzed, and shared with third parties[4]. The actual conditions of data usage often change without meaningful notification or consent opportunities.
Web3: Transparent Governance and Programmable Consent
Web3 systems operate on public, immutable ledgers where data processing rules are encoded in transparent smart contracts that anyone can examine[4][5]. This radical transparency allows users to verify exactly how their information will be handled before agreeing to share it.
Rather than all-or-nothing consent models, Web3 enables granular, programmable consent where users can specify precise conditions under which their data may be accessed or utilized[5]. These conditions become enforced by code rather than by trusting companies to honor their stated policies.
This transparency extends to the broader governance of Web3 platforms, many of which operate as Decentralized Autonomous Organizations (DAOs) where users can participate in decision-making about how the system evolves[8].
Data Monetization and Value Exchange
Web2: Asymmetric Value Capture
In Web2 ecosystems, the value created from user data flows predominantly to platform owners. Users effectively trade their data for free services, but the economic exchange is highly unbalanced[4]. The personal information collected is worth far more to the companies than the services provided in return, creating massive wealth for a small number of technology corporations.
Users have little visibility into how their data contributes to platform revenues and receive minimal compensation for their valuable contributions to these ecosystems[4].
Web3: Direct User Monetization
Web3 revolutionizes this economic model by enabling users to directly monetize their own data if they choose to share it[4]. Through blockchain-based platforms and decentralized applications (dApps), individuals can selectively sell access to their data or receive compensation for their online contributions.
This model creates more equitable value distribution, where the economic benefits of data flow to those who generate it rather than being concentrated among platform owners[7]. Users can make informed decisions about when and how to monetize their information based on transparent value propositions.
The incentive structures of Web3 platforms often include tokenization mechanisms that allow users to benefit directly from network growth and participation, creating alignment between individual and collective interests[8].
Challenges and Future Directions
Despite its promising approach to data control, Web3 faces significant challenges in achieving mainstream adoption. Technical barriers remain substantial, with many Web3 interfaces less user-friendly than their Web2 counterparts[3]. Scalability issues can lead to slower transactions and higher costs compared to centralized solutions.
Regulatory frameworks are still evolving to address the unique characteristics of decentralized systems, creating uncertainty around compliance requirements[3][5]. Additionally, the public nature of some blockchain networks introduces new privacy considerations that must be carefully managed.
Future developments in Web3 privacy will likely focus on improving scalability solutions, developing more intuitive user interfaces for privacy management, and refining privacy-preserving technologies like zero-knowledge proofs[3]. Education remains critical, as users need to understand Web3 mechanisms to fully leverage their benefits.
Conclusion
The transition from Web2 to Web3 represents a profound shift in how user data is controlled, managed, and valued. While Web2 created unprecedented connectivity at the cost of personal privacy and autonomy, Web3 aims to preserve the benefits of digital connection while returning control to individuals.
By decentralizing infrastructure, enabling self-sovereign identity, increasing transparency, and creating more equitable value distribution, Web3 technologies offer a vision of the internet that aligns more closely with principles of user empowerment and data sovereignty.
Though challenges remain in fully realizing this vision, the fundamental reorientation toward user control over personal data represents one of the most significant developments in the internet's evolution since the emergence of social platforms. As Web3 technologies mature and adoption increases, they have the potential to fundamentally transform our relationship with our digital selves and reshape the power dynamics of the online world.
Sources
[1] Data Ownership in Web3: Empowering Users with Control https://whimsygames.co/blog/data-ownership-in-web3-empowering-users-with-control/ [2] Web2 vs Web3: What's the Difference - Cryptix AG https://cryptix.ag/web2-vs-web3/ [3] The Role of Web3 in Digital Privacy: Protecting User Data in ... https://dev.to/lisaward867/the-role-of-web3-in-digital-privacy-protecting-user-data-in-decentralized-systems-18ki [4] How Web3 Enhances User Privacy As Compared to Web2 - LinkedIn https://www.linkedin.com/pulse/how-web3-enhances-user-privacy-compared-web2-mr-mint-official-umtve [5] Safeguarding Privacy in the Web3 Era: A Deep Dive into User ... https://www.linkedin.com/pulse/safeguarding-privacy-web3-era-deep-dive-user-anonymity-data-protection-85hrf [6] Web2 vs. Web3: What's the Difference? [The Breakthrough] - Metana https://metana.io/blog/web2-vs-web3-whats-the-difference-the-breakthrough/ [7] Decentralized Data Impact in Web 3.0 Ownership https://crowleymediagroup.com/resources/decentralized-data-impact-in-web-3-0-ownership/ [8] Enhancing Digital Security and User Privacy with Web3 - BlockApps https://blockapps.net/blog/enhancing-digital-security-and-user-privacy-with-web3/
-
 @ 04ff5a72:22ba7b2d
2025-03-19 01:54:44
@ 04ff5a72:22ba7b2d
2025-03-19 01:54:44How Blockchain Technology Birthed Web3
The emergence of Web3 represents a paradigm shift in how we conceptualize and interact with the internet, moving from centralized platforms toward user-centric, decentralized systems. At the heart of this transformation lies blockchain technology, which serves as the architectural foundation enabling this new internet vision. Blockchain's unique characteristics—decentralization, transparency, and security—have positioned it as the critical infrastructure layer upon which the Web3 ecosystem is being built, fundamentally reshaping digital interactions, ownership models, and value exchange mechanisms.
Blockchain as the Architectural Foundation
Blockchain serves as the building block of Web3 by creating a network where information is stored across many computers instead of one central location[1]. This distributed architecture represents a fundamental departure from the centralized server model that has dominated Web1 and Web2, where data and control are concentrated in the hands of a few corporations.
From Centralized to Distributed Systems
Web3 is built on blockchain technology, which enables secure, transparent, and censorship-resistant transactions[3]. Unlike Facebook, Google, and other Web2 platforms where user data, posts, likes, and photos are controlled by corporations, Web3 leverages blockchain to put users in charge of their digital lives[1]. This shift redistributes power from centralized authorities to a communal network of participants.
Blockchain essentially functions as a public, immutable ledger that everyone can see but no one can unilaterally alter. As described by McKinsey, Web3 is "a new, decentralized internet built on blockchains, which are distributed ledgers controlled communally by participants"[4]. This architecture enables users to store their digital items in secure digital spaces over which they have complete control[1].
Distinguishing Between Blockchain and Web3 Development
While often used interchangeably, blockchain development and Web3 development represent different aspects of this technological evolution. Blockchain development focuses specifically on building the blockchain-based architecture, while Web3 is an umbrella term encompassing various tools and protocols that enable decentralized web applications[5]. A Web3 application typically runs on or interacts with a specific blockchain, relying on this underlying infrastructure for its core functionalities[5].
In practical terms, blockchain development requires knowledge of specialized programming languages like Solidity, while Web3 development frequently employs standard web development languages like ReactJs, VueJs, CSS, and JavaScript to create user interfaces that interact with blockchain systems[5].
Enabling Core Web3 Principles
Blockchain technology enables three fundamental principles that define the Web3 vision: decentralization, transparency, and security. These characteristics are instrumental in creating an internet where users have greater control over their digital experiences.
Decentralization and User Sovereignty
Decentralization represents a core value proposition of Web3. Rather than storing data on Facebook's or Google's servers, blockchain spreads information across a network of computers, ensuring that no single company controls user information[1]. This distributed approach fundamentally changes the power dynamic of the internet, giving users sovereignty over their digital identities and assets.
This decentralized model eliminates intermediaries, allowing people to interact and trade directly with each other without corporate oversight or intervention[1]. Users can buy, sell, create, and share online without big tech companies controlling their actions or taking a percentage of their transactions. According to a McKinsey report, this signals "a new era of the internet, one in which use and access are controlled by community-run networks rather than the current, centralized model in which a handful of corporations preside over Web2"[4].
Transparency and Trust
Blockchain technology creates unprecedented transparency in digital interactions. Every transaction and change gets recorded in a way everyone can see but nobody can alter[1]. This transparency is often described as a "glass wall where all activities are visible to everyone, making cheating or hiding information impossible"[1].
This level of visibility creates trust in data in ways that were not possible before, potentially revolutionizing how we share information and conduct transactions online[7]. The European Commission recognizes this capability, noting that blockchain/web3 technology "allows people and organisations who may not know or trust each other to collectively agree on and permanently record information without a third-party authority"[7].
Enhanced Security and Immutability
Once information is recorded on the blockchain, it cannot be changed or deleted, creating a secure environment for digital interactions[1]. This immutability provides foundational security for Web3 applications and services. By distributing data across multiple nodes worldwide rather than concentrating it in centralized servers, blockchain significantly increases resilience against attacks[3].
This enhanced security is a key benefit of Web3, as the "distributed nature of blockchain makes it extremely difficult for hackers to penetrate the network"[3]. Cryptographic protection is fundamental to Web3 systems, with data access controlled through sophisticated encryption mechanisms that protect user information and digital assets.
Transforming Digital Ownership and Value Exchange
Blockchain technology is fundamentally redefining concepts of ownership and value exchange in the digital realm, enabling new economic models and business opportunities within the Web3 ecosystem.
User-Controlled Digital Assets
A defining characteristic of Web3 is its emphasis on true digital ownership. Through blockchain technology, users can assert verifiable ownership over digital assets in ways previously impossible under Web2 models[3]. This capability extends from social media posts to digital art, all secured in a transparent and user-controlled environment.
Blockchain enables features like digital scarcity and provable ownership, which are crucial for the development of unique digital assets such as non-fungible tokens (NFTs)[3]. By creating scarcity in the digital realm, blockchain opens new opportunities for creators to monetize their content and for users to truly own and trade digital items.
New Economic Models Through Tokenization
Tokenization—the process of converting real-world or digital assets into digital tokens managed on a blockchain—is creating more liquid and accessible markets for both physical and digital goods[3]. These tokens can represent diverse assets, including real estate, stocks, commodities, art, music, and in-game items.
Web3 introduces the concept of token economies, where digital assets represent ownership, access, or participation in a network[3]. This creates new economic models and incentives for users, fundamentally changing how value is created and distributed online.
Smart Contracts and Programmable Agreements
Smart contracts are self-executing contracts with terms directly written into code, enabling trustless transactions without intermediaries[2]. These automated agreements are central to blockchain development and play a critical role in Web3 functionality, powering everything from decentralized finance applications to content royalty systems.
By automating complex agreements and ensuring their execution according to predefined rules, smart contracts enhance efficiency and reduce the need for traditional intermediaries. They run on platforms like the Ethereum Virtual Machine (EVM), which "ensures that they execute as programmed without downtime or interference"[2].
Key Web3 Applications Powered by Blockchain
Blockchain technology enables numerous applications and use cases within the Web3 ecosystem, transforming multiple sectors through decentralized approaches.
Decentralized Finance (DeFi)
One of the most prominent applications of blockchain in Web3 is decentralized finance (DeFi). Blockchain-based DeFi platforms allow users to access financial services such as lending, borrowing, and liquidity provision without relying on traditional financial institutions[3].
These platforms offer increased transparency through public transaction records, greater accessibility by allowing anyone with an internet connection to participate regardless of location or financial status, and enhanced user control by eliminating intermediaries[3]. Ethereum serves as the backbone of the DeFi movement, enabling users to conduct financial transactions in a decentralized environment[2].
Metaverse and Virtual Worlds
Blockchain technology is also making significant strides in enabling the metaverse—interconnected virtual worlds where users can interact, create, and exchange value. Through blockchain, these virtual environments become decentralized, secure, and transparent[3].
Blockchain facilitates true ownership of digital assets within virtual worlds, enables secure transactions between users, and promotes interoperability between different platforms[3]. These capabilities are essential for creating persistent, user-owned digital spaces where individuals can freely interact and transact.
Decentralized Content Creation and Distribution
Web3 is revolutionizing how content creators monetize and distribute their work. Blockchain-based platforms allow creators to monetize content through fair and transparent processes, eliminating intermediaries and ensuring creators receive a larger share of revenue[3].
Smart contracts automate content monetization and distribution, reducing administrative overhead and ensuring timely payments to creators[3]. The transparency of blockchain ensures fair compensation, while direct creator-fan relationships foster deeper connections and loyalty without platform intermediation.
Challenges and Future Considerations
Despite its transformative potential, blockchain implementation in Web3 faces several significant challenges that must be addressed for widespread adoption.
Technical and Operational Hurdles
Web3 and blockchain implementation face technical challenges including high processing costs and complex user experiences. These technologies currently require substantial initial investment in hardware and high-end devices, potentially limiting accessibility[3].
Scalability remains a significant concern, as many blockchain networks struggle to handle large transaction volumes efficiently. Additionally, interoperability between different blockchain networks is limited, hindering seamless communication between platforms[3].
Regulatory and Adoption Considerations
The decentralized nature of Web3 creates regulatory challenges, potentially making monitoring and management difficult for authorities[3]. Finding the right balance between innovation and consumer protection remains a complex undertaking.
Adoption rates for Web3 technologies remain relatively slow, following a similar trajectory to the transition from Web1 to Web2[3]. Overcoming user hesitation and education barriers will be crucial for driving mainstream acceptance of blockchain-based Web3 applications.
Conclusion
Blockchain technology serves as the fundamental infrastructure enabling the Web3 vision of a decentralized, user-centric internet. By providing the architectural foundation for decentralization, transparency, and security, blockchain is transforming how we conceptualize digital ownership, value exchange, and online interactions.
From decentralized finance to virtual worlds and content monetization, blockchain is powering diverse applications that redistribute control from centralized entities to individual users and communities. Despite facing technical, regulatory, and adoption challenges, the role of blockchain in Web3 development continues to expand as the technology matures.
As noted by McKinsey, momentum around Web3 elements has increased significantly since 2018, with growth in equity investment, patent filings, scientific publications, and job opportunities[4]. With 90% of executives agreeing that blockchain helps create stronger partnerships and unlock new value[6], the technology is increasingly positioned at the center of commerce, supply chain management, and digital interactions.
The continued evolution of blockchain will be central to realizing the full potential of Web3—creating an internet that is more open, equitable, and aligned with the needs and interests of its users rather than centralized gatekeepers.
Sources
[1] The Role of Blockchain in Web 3.0 - Chiliz https://www.chiliz.com/blockchain-in-web-3-0/ [2] Web3 Development: Comprehensive Guide for Blockchain Builders https://www.rapidinnovation.io/post/web3-development-a-comprehensive-guide [3] Blockchain Web 3.0: The Role of Blockchain in Enabling - BlockApps Inc. https://blockapps.net/blog/the-role-of-blockchain-in-enabling-web-3-0/ [4] What is Web3 technology (and why is it important)? | McKinsey https://www.mckinsey.com/featured-insights/mckinsey-explainers/what-is-web3 [5] Web3 vs blockchain: Understanding the Differences | Infuy https://www.infuy.com/blog/understanding-the-differences-between-web3-and-blockchain-development/ [6] Accenture's Blockchain & Web3 Innovations in the Metaverse https://www.accenture.com/us-en/services/metaverse/blockchain-web3 [7] Blockchain and Web3 Strategy | Shaping Europe's digital future https://digital-strategy.ec.europa.eu/en/policies/blockchain-strategy
-
 @ 05cdefcd:550cc264
2025-03-28 08:00:15
@ 05cdefcd:550cc264
2025-03-28 08:00:15The crypto world is full of buzzwords. One that I keep on hearing: “Bitcoin is its own asset class”.
While I have always been sympathetic to that view, I’ve always failed to understand the true meaning behind that statement.
Although I consider Bitcoin to be the prime innovation within the digital asset sector, my primary response has always been: How can bitcoin (BTC), a single asset, represent an entire asset class? Isn’t it Bitcoin and other digital assets that make up an asset class called crypto?
Well, I increasingly believe that most of crypto is just noise. Sure, it’s volatile noise that is predominately interesting for very sophisticated hedge funds, market makers or prop traders that are sophisticated enough to extract alpha – but it’s noise nonetheless and has no part to play in a long-term only portfolio of private retail investors (of which most of us are).
 Over multiple market cycles, nearly all altcoins underperform Bitcoin when measured in BTC terms. Source: Tradingview
Over multiple market cycles, nearly all altcoins underperform Bitcoin when measured in BTC terms. Source: TradingviewAha-Moment: Bitcoin keeps on giving
Still, how can Bitcoin, as a standalone asset, make up an entire asset class? The “aha-moment” to answer this question recently came to me in a Less Noise More Signal interview I did with James Van Straten, senior analyst at Coindesk.
Let me paraphrase him here: “You can’t simply recreate the same ETF as BlackRock. To succeed in the Bitcoin space, new and innovative approaches are needed. This is where understanding Bitcoin not just as a single asset, but as an entire asset class, becomes essential. There are countless ways to build upon Bitcoin’s foundation—varied iterations that go beyond just holding the asset. This is precisely where the emergence of the Bitcoin-linked stock market is taking shape—and it's already underway.”
And this is actually coming to fruition as we speak. Just in the last few days, we saw several products launch in that regard.
Obviously, MicroStrategy (now Strategy) is the pioneer of this. The company now owns 506,137 BTC, and while they’ll keep on buying more, they have also inspired many other companies to follow suit.
In fact, there are now already over 70 companies that have adopted Strategy’s Bitcoin playbook. One of the latest companies to buy Bitcoin for their corporate treasury is Rumble. The YouTube competitor just announced their first Bitcoin purchase for $17 million.
Also, the gaming zombie company GameStop just announced to raise money to buy BTC for their corporate treasury.
 Gamestop to make BTC their hurdle rate. Source: X
Gamestop to make BTC their hurdle rate. Source: XETF on Bitcoin companies
Given this proliferation of Bitcoin Treasury companies, it was only a matter of time before a financial product tracking these would emerge.
The popular crypto index fund provider Bitwise Investments has just launched this very product called the Bitwise Bitcoin Standard Corporations ETF (OWNB).
The ETF tracks Bitcoin Treasury companies with over 1,000 BTC on their balance sheet. These companies invest in Bitcoin as a strategic reserve asset to protect the $5 trillion in low-yield cash that companies in the US commonly sit on.
 These are the top 10 holdings of OWNB. Source: Ownbetf
These are the top 10 holdings of OWNB. Source: OwnbetfETF on Bitcoin companies’ convertible bonds
Another instrument that fits seamlessly into the range of Bitcoin-linked stock market products is the REX Bitcoin Corporate Treasury Convertible Bond ETF (BMAX). The ETF provides exposure to the many different convertible bonds issued by companies that are actively moving onto a Bitcoin standard.
Convertible bonds are a valuable financing tool for companies looking to raise capital for Bitcoin purchases. Their strong demand is driven by the unique combination of equity-like upside and debt-like downside protection they offer.
For example, MicroStrategy's convertible bonds, in particular, have shown exceptional performance. For instance, MicroStrategy's 2031 bonds has shown a price rise of 101% over a one-year period, vastly outperforming MicroStrategy share (at 53%), Bitcoin (at 25%) and the ICE BofA U.S. Convertible Index (at 10%). The latter is the benchmark index for convertible bond funds, tracking the performance of U.S. dollar-denominated convertible securities in the U.S. market.
 The chart shows a comparison of ICE BofA U.S. Convertible Index, the Bloomberg Bitcoin index (BTC price), MicroStrategy share (MSTR), and MicroStrategy bond (0.875%, March 15 203). The convertible bond has been outperforming massively. Source: Bloomberg
The chart shows a comparison of ICE BofA U.S. Convertible Index, the Bloomberg Bitcoin index (BTC price), MicroStrategy share (MSTR), and MicroStrategy bond (0.875%, March 15 203). The convertible bond has been outperforming massively. Source: BloombergWhile the BMAX ETF faces challenges such as double taxation, which significantly reduces investor returns (explained in more detail here), it is likely that future products will emerge that address and improve upon these issues.
Bitcoin yield products
The demand for a yield on Bitcoin has increased tremendously. Consequently, respective products have emerged.
Bitcoin yield products aim to generate alpha by capitalizing on volatility, market inefficiencies, and fragmentation within cryptocurrency markets. The objective is to achieve uncorrelated returns denominated in Bitcoin (BTC), with attractive risk-adjusted performance. Returns are derived exclusively from asset selection and trading strategies, eliminating reliance on directional market moves.
Key strategies employed by these funds include:
- Statistical Arbitrage: Exploits short-term pricing discrepancies between closely related financial instruments—for instance, between Bitcoin and traditional assets, or Bitcoin and other digital assets. Traders utilize statistical models and historical price relationships to identify temporary inefficiencies.
- Futures Basis Arbitrage: Captures profits from differences between the spot price of Bitcoin and its futures contracts. Traders simultaneously buy or sell Bitcoin on spot markets and enter opposite positions in futures markets, benefiting as the prices converge.
- Funding Arbitrage: Generates returns by taking advantage of variations in Bitcoin funding rates across different markets or exchanges. Funding rates are periodic payments exchanged between long and short positions in perpetual futures contracts, allowing traders to profit from discrepancies without significant directional exposure.
- Volatility/Option Arbitrage: Seeks profits from differences between implied volatility (reflected in Bitcoin options prices) and expected realized volatility. Traders identify mispriced volatility in options related to Bitcoin or Bitcoin-linked equities, such as MSTR, and position accordingly to benefit from volatility normalization.
- Market Making: Involves continuously providing liquidity by simultaneously quoting bid (buy) and ask (sell) prices for Bitcoin. Market makers profit primarily through capturing the spread between these prices, thereby enhancing market efficiency and earning consistent returns.
- Liquidity Provision in DeFi Markets: Consists of depositing Bitcoin (usually as Wrapped BTC) into decentralized finance (DeFi) liquidity pools such as those on Uniswap, Curve, or Balancer. Liquidity providers earn fees paid by traders who execute swaps within these decentralized exchanges, creating steady yield opportunities.
Notable products currently available in this segment include the Syz Capital BTC Alpha Fund offered by Syz Capital and the Forteus Crypto Alpha Fund by Forteus.
BTC-denominated share class
A Bitcoin-denominated share class refers to a specialized investment fund category in which share values, subscriptions (fund deposits), redemptions (fund withdrawals), and performance metrics are expressed entirely in Bitcoin (BTC), rather than in traditional fiat currencies such as USD or EUR.
Increasingly, both individual investors and institutions are adopting Bitcoin as their preferred benchmark—or "Bitcoin hurdle rate"—meaning that investment performance is evaluated directly against Bitcoin’s own price movements.
These Bitcoin-denominated share classes are designed specifically for investors seeking to preserve and grow their wealth in Bitcoin terms, rather than conventional fiat currencies. As a result, investors reduce their exposure to fiat-related risks. Furthermore, if Bitcoin outperforms fiat currencies, investors holding BTC-denominated shares will experience enhanced returns relative to traditional fiat-denominated investment classes.
X: https://x.com/pahueg
Podcast: https://www.youtube.com/@lessnoisemoresignalpodcast
Book: https://academy.saifedean.com/product/the-bitcoin-enlightenment-hardcover/
-
 @ f839fb67:5c930939
2025-03-19 01:17:57
@ f839fb67:5c930939
2025-03-19 01:17:57Relays
| Name | Address | Price (Sats/Year) | Status | | - | - | - | - | | stephen's aegis relay | wss://paid.relay.vanderwarker.family | 42069 |
| | stephen's Outbox | wss://relay.vanderwarker.family | Just Me |
| | stephen's Inbox | wss://haven.vanderwarker.family/inbox | WoT |
| | stephen's DMs | wss://haven.vanderwarker.family/chat | WoT |
| | VFam Data Relay | wss://data.relay.vanderwarker.family | 0 |
| | VFam Bots Relay | wss://skeme.vanderwarker.family | Invite |
| | VFGroups (NIP29) | wss://groups.vanderwarker.family | 0 |
| | [TOR] My Phone Relay | ws://naswsosuewqxyf7ov7gr7igc4tq2rbtqoxxirwyhkbuns4lwc3iowwid.onion | 0 | Meh... |
My Pubkeys
| Name | hex | nprofile | | - | - | - | | Main | f839fb6714598a7233d09dbd42af82cc9781d0faa57474f1841af90b5c930939 | nprofile1qqs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3us9mapfx | | Vanity (Backup) | 82f21be67353c0d68438003fe6e56a35e2a57c49e0899b368b5ca7aa8dde7c23 | nprofile1qqsg9usmuee48sxkssuqq0lxu44rtc4903y7pzvmx694efa23h08cgcpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3ussel49x | | VFStore | 6416f1e658ba00d42107b05ad9bf485c7e46698217e0c19f0dc2e125de3af0d0 | nprofile1qqsxg9h3uevt5qx5yyrmqkkehay9cljxdxpp0cxpnuxu9cf9mca0p5qpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3usaa8plu | | NostrSMS | 9be1b8315248eeb20f9d9ab2717d1750e4f27489eab1fa531d679dadd34c2f8d | nprofile1qqsfhcdcx9fy3m4jp7we4vn305t4pe8jwjy74v062vwk08dd6dxzlrgpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3us595d45 |
Bot Pubkeys
| Name | hex | nprofile | | - | - | - | | Unlocks Bot | 2e941ad17144e0a04d1b8c21c4a0dbc3fbcbb9d08ae622b5f9c85341fac7c2d0 | nprofile1qqsza9q669c5fc9qf5dccgwy5rdu877th8gg4e3zkhuus56pltru95qpramhxue69uhhx6m9d4jjuanpdejx2unhv9exketj9enxzmtfd3ust4kvak | | Step Counter | 9223d2faeb95853b4d224a184c69e1df16648d35067a88cdf947c631b57e3de7 | nprofile1qqsfyg7jlt4etpfmf53y5xzvd8sa79ny356sv75gehu50333k4lrmecpramhxue69uhhx6m9d4jjuanpdejx2unhv9exketj9enxzmtfd3ustswp3w |
"Personal Nostr Things"
[D] = Saves darkmode preferences over nostr
[A] = Auth over nostr
[B] = Beta (software)
[z] = zap enabled
Other Services (Hosted code)
Emojis Packs
- Minecraft
nostr:naddr1qqy566twv43hyctxwsq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82nsd0k5wp- AIM
nostr:naddr1qqxxz6tdv4kk7arfvdhkuucpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3usyg8c88akw9ze3fer85yah4p2lqkvj7qap749w360rpq6ly94eycf8ypsgqqqw48qe0j2yk- Blobs
nostr:naddr1qqz5ymr0vfesz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqa2wek4ukj- FavEmojis
nostr:naddr1qqy5vctkg4kk76nfwvq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82nsf7sdwt- Modern Family
nostr:naddr1qqx56mmyv4exugzxv9kkjmreqy0hwumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jq3qlqulkec5tx98yv7snk759tuzejtcr5865468fuvyrtuskhynpyusxpqqqp65ujlj36n- nostriches (Amethyst collection)
nostr:naddr1qq9xummnw3exjcmgv4esz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqa2w2sqg6w- Pepe
nostr:naddr1qqz9qetsv5q37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82ns85f6x7- Minecraft Font
nostr:naddr1qq8y66twv43hyctxwssyvmmwwsq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82nsmzftgr- Archer Font
nostr:naddr1qq95zunrdpjhygzxdah8gqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0ypzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqvzqqqr4fclkyxsh- SMB Font
nostr:naddr1qqv4xatsv4ezqntpwf5k7gzzwfhhg6r9wfejq3n0de6qz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqa2w0wqpuk
Git Over Nostr
- NostrSMS
nostr:naddr1qqyxummnw3e8xmtnqy0hwumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jqfrwaehxw309amk7apwwfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqyj8wumn8ghj7urpd9jzuun9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jqg5waehxw309aex2mrp0yhxgctdw4eju6t0qyxhwumn8ghj7mn0wvhxcmmvqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqaueqp0epk- nip51backup
nostr:naddr1qq9ku6tsx5ckyctrdd6hqqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yqjxamnwvaz7tmhda6zuun9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jqfywaehxw309acxz6ty9eex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yq3gamnwvaz7tmjv4kxz7fwv3sk6atn9e5k7qgdwaehxw309ahx7uewd3hkcq3qlqulkec5tx98yv7snk759tuzejtcr5865468fuvyrtuskhynpyusxpqqqpmej4gtqs6- bukkitstr
nostr:naddr1qqykyattdd5hgum5wgq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gpydmhxue69uhhwmm59eex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yqjgamnwvaz7tmsv95kgtnjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0dspzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqvzqqqrhnyf6g0n2
Market Places
Please use Nostr Market or somthing simular, to view.
- VFStore
nostr:naddr1qqjx2v34xe3kxvpn95cnqven956rwvpc95unscn9943kxet98q6nxde58p3ryqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yqjvamnwvaz7tmgv9mx2m3wweskuer9wfmkzuntv4ezuenpd45kc7f0da6hgcn00qqjgamnwvaz7tmsv95kgtnjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gpydmhxue69uhhwmm59eex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0ypzqeqk78n93wsq6sss0vz6mxl5shr7ge5cy9lqcx0smshpyh0r4uxsqvzqqqr4gvlfm7gu
Badges
Created
- paidrelayvf
nostr:naddr1qq9hqctfv3ex2mrp09mxvqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0ypzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqvzqqqr48y85v3u3- iPow
nostr:naddr1qqzxj5r02uq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82wgg02u0r- codmaster
nostr:naddr1qqykxmmyd4shxar9wgq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82wgk3gm4g- iMine
nostr:naddr1qqzkjntfdejsz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqafed5s4x5
Clients I Use
- Amethyst
nostr:naddr1qqxnzd3cx5urqv3nxymngdphqgsyvrp9u6p0mfur9dfdru3d853tx9mdjuhkphxuxgfwmryja7zsvhqrqsqqql8kavfpw3- noStrudel
nostr:naddr1qqxnzd3cxccrvd34xser2dpkqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hsygpxdq27pjfppharynrvhg6h8v2taeya5ssf49zkl9yyu5gxe4qg55psgqqq0nmq5mza9n- nostrsms
nostr:naddr1qq9rzdejxcunxde4xymqz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgsfhcdcx9fy3m4jp7we4vn305t4pe8jwjy74v062vwk08dd6dxzlrgrqsqqql8kjn33qm
-
 @ 8671a6e5:f88194d1
2025-03-18 23:46:54
@ 8671a6e5:f88194d1
2025-03-18 23:46:54glue for the mind
\ You’ve seen them, these garish orange Bitcoin stickers slapped on lampposts, laptops, windows and the occasional rust-bucket Honda. They’re sometimes in some areas a sort of graffiti plague on the landscape, certainly when a meetup or bitcoin conference was held in the area (especially then the city or town can fork out some extra budget to clean things up and scrape the stickers from statues of famous folk heroes or the door to the headquarters of a local bank branche).\ \ At first glance, it might seem like enthusiasm Bitcoiners desperate to scream their obsession from the rooftops. Both for the fun of it, and to get rid of the pack of stickers they’ve got at a local meetup.\ \ But let’s cut to the chase: covering half a town in stickers isn’t clever. It’s lazy, counterproductive, and has nothing to do with what Bitcoin actually stands for.\ Worse, it reeks of the brain-dead low grade (cheap) marketing tactics you’d expect from shitcoiners or the follow up of some half-baked flyer campaign by a local communist clique.\ Proof? Bitcoin stickers are literally covering up — or being covered up themselves, usually by - communist stickers in a pointless competition for use of real-world ad space.\ \ Maybe, bitcoiners should just create a sticker where Karl Marx ànd the bitcoin logo appear in the same sticker, so both groups can enjoy it’s uselessness, and call it quits to get this stupidity over with once and for all.\ A sticker with a shiny B might look cool at first. But what does it actually do?
 Communist and Bitcoin logo sticker
Communist and Bitcoin logo stickerSpamming stickers doesn’t make “frens”
There’s a psychology behind these stickers of course: people slap them up to feel part of a rebel tribe, flipping off central banks or feeling part of the crew.\ This crude, omnipresent approach to marketing echoes the late 1960s— an era of peak fiat, not Bitcoin’s time.\ Mimicking those tactics today, as if Bitcoin were some hip underground record store trying to spread its brand name, is utterly irrelevant.\ Sure, people love signaling affiliations with an easy and cheap identity flex — like a bumper sticker yelling: “Look at me I’m special!”\ \ But plaster a town with Bitcoin logos, and it stops being edgy and it was never funny; it becomes an eyesore and puts bitcoiners in the same category as the social justice warriors and political youth movements or brands of local energy drinks doing some weird campaign.\ \ Advertising psychology shows overexposure breeds resentment, not interest. Flood a street with stickers, and you’re not lighting a spark. You’re making people uninterested, gag, associating Bitcoin with spam or worse: get totally blended into the background along all the other noise from the street marketeers.\ \ The "mere exposure effect" (Zajonc, 1968)1 claims familiarity breeds liking, even from annoyance. Since the 1960s however, a lot has changed, as we’ll see… and above all, yet, after years of Bitcoin stickers in many areas, they’ve just turned into meaningless wallpaper. It has usually no strong message, no slogan, no conversation starter other than “buy bitcoin”, it’s disassociated from reality for many people, as the reaction show us. It’s also happening in a vacuum, where “normies” and no-coiners pass by and don’t even recognize such stickers for anything else than background colors.
It’s Lazy Man’s Work
Let’s talk effort — or the lack of it - for these kind of campaigns and stickers. Invented in the 1920s, stickers began expressing political opinions in the 1970s during student, peace, and anti-nuclear campaigns. It’s easy, cheap and also quick to distribute.\ \ These stickers aren’t masterful designs from an artistic genius (safe some clever exceptions). They’re usually ripped off from somewhere else, tweaked for five minutes, and bulk-ordered online. It’s the “IKEA effect” gone wrong: a tiny bit of customization, and suddenly people think they’re visionaries. But it’s a low-effort form of activism at best. Compare that to coding a Bitcoin tool or patiently explaining its value to a normie or organizing a meetup or conference, starting a company.\ Not that low-level or guerrilla marketing can’t work, I just don’t see it happen with stickers. Why not go out there and try to convince a whole series of fruit and vegetable market owners to accept bitcoin instead of using very expensive bank Point-of-sale systems?\ Why not direct mailing? Why not… do more than just putting a sticker on a signpost and walk away like a sneaky student promoting his 4 person political group?\ \ Stickers are the “Save the whales (pun intended)” magnet on your fridge: lazy-ass advocacy that screams intellectual deficiency. They’re a shortcut to feeling involved, not a strategy for real impact.
 imaginary Save-the-Whales bitcoin sticker
imaginary Save-the-Whales bitcoin stickerStrategy territory signaling
Here’s the kicker: Bitcoin’s strength lies in its tech and value properties — decentralized, borderless value transfer that eliminates middlemen and has provable digital scarcity.\ Stickers? They’re just physical garbage. Sure, they might feel like a way to make an abstract idea tangible, tapping into “embodied cognition.” But they explain nothing about Bitcoin’s purpose or how it revolutionizes finance.\ They’re a dopamine hit for the people sticking them anywhere — a pathetic “I did something” moment — while everyone else walks by without a glance.\ Bitcoin is about innovation, not old-school social groups with low-budget marketing tactics.
\ The psychology of Bitcoin stickers
Why bother? Stickers are simple and loud—easy for the brain to process, a cheap thrill of rebellion. The person who spends an afternoon covering a city in them thinks they’re spreading the gospel. In reality, they’re just littering. Real advocacy takes effort, discussion, and substance — not a pack of adhesive stickers ordered with the click of a button.\ It’s the same reason nobody turns communist from a hammer-and-sickle sticker on a pole. It’s dead air.\ \ The proof of their uselessness? In 2 years, not one person I know has bought, researched, or even asked about Bitcoin because of a sticker in the neighborhood bar. A bar near me has had one on the wall for years — zero requests to pay with Bitcoin.
A sticker sitting on a bar wall for five years without impact isn’t “subtle marketing”—it’s a neon sign of failure. And the people cleaning those stickers off street signs, or the local communist student activists constantly covering them with their own, are locked in an endless, mindless sticker war.\ \ Other areas are even having a tsunami of bitcoin stickers, and hardly any places where they actually accept bitcoin for goods.\ More so, places where they do accept bitcoin readily, usually only need one sticker: the one at the door of a business saying “bitcoin accepted here”. And that’s about it.
What the little amount of research says
Studies shows stickers work for movements claiming public space and resisting dominant narratives — when done on a massive scale, targeting a specific audience have a visual and emotional effect when combined with other forms of resistance in social movements.\ "Stickin' it to the Man: The Geographies of Protest Stickers" 2\ \ For Bitcoin, a global monetary network meant for everyone, that localized, niche-based campaign makes little sense.\ Unlike sports teams or clothing brands, Bitcoiners can’t pinpoint a target area. A random sticker on a busy street claims nothing—no momentum, atmosphere, or intrigue. Political campaigns and underground youth movements concentrate stickers in student neighborhoods, universities, or subcultures where the message resonates. But Bitcoin isn’t a corporation, company, or fashion brand—it’s a Wall Street-embraced asset by now, with activists not really situated in the sticker-guerrilla kind of persons.
When was the last time you saw a "Buy Gold!" sticker? A "Get Your Microsoft Stock Options Now!" sticker? Or a "Crude Oil—Yeah, Baby!" sticker? Never. Serious assets don’t need guerrilla marketing.
The overload on stickers is also becoming an issue (especially in some areas with higher concentration of bitcoiners).
Bitcoin stickers fall flat
Invented in the 1920s, stickers began expressing political opinions in the 1970s during student, peace, and anti-nuclear campaigns. Protest stickers massively appear after protest rallies or campaigns with multi-level plans to reach audiences.\ As significant, overlooked tools of resistance and debate, their effect remains under-studied, with no data on “recruitment.”\ \ If Bitcoin stickers (which don’t provoke debate ever, other than people being angry about having to clean them up) in a bar are any clue—after one full year, not a single person asked why it was there or if Bitcoin was accepted—they’re just decor, lost among the clutter.
Bitcoiners still think slapping a shiny "B" logo on a street sign without explanation or slogan will spark momentum. But that requires a massive, organized campaign with thousands of people and a clear audience while you claim certain well aimed areas of public space — that something that’s not happening in bitcoin. There’s no plan, no campaign, just someone sticking a bitcoin logo at the supermarkt trolley or the backside of a street sign.\ And even if we did reach a higher number of stickers, it would annoy the f out of people.
"Study: Ad Overload Could Pose Steeper Risk to Brands Than Messages Near Inappropriate Content" (GWI & WARC, 2021) 3\ \ There’s also the effect of high ad exposure. When a whole street is covered in bitcoin stickers, it’s having the opposite effect. Or still… no one cares.
"Coping with High Advertising Exposure: A Source-Monitoring Perspective" (Bell et al., 2022)4
No synergy, no consensus
The synergy between offline sticker placement and online sharing? Absent. Bitcoiners online might be called “cyber hornets”, but this swarm is notoriously bad at sharing content. Post a Bitcoin sticker photo, and at best 1-2% will share it — no momentum, no discussion, no engagement.\ \ Non-Bitcoiners have zero reason to care. When was the last time you, as a Bitcoiner, shared a soccer team’s sticker? A political campaign sticker? Never. That’s normal, as you’re not in their bubble, so for us, it’s irrelevant. We won’t share the soccer team’s sticker (unless it’s Real Bedford FC probably).\ \ It's just a layer of plastic with adhesive glued to a surfase where someone will sooner or later either have to clean it up, or where the bitcoin sticker will be covered over by another person wasting his or her time by claiming that “sticker real-estate space” for their cause or brand-awareness.

And so, the red sticker calling all students and workers to vote for a Leninist party (with 10 members) is stickered over by a bright orange Bitcoin logo, and that one, in turn, will be over-stickered by a local fitness company's new logo, and so forth. It’s all a pointless rush for giggles and dopamine. And it’s time to recognize it for what it really is: retardation.
Bitcoin deserves better than this 70s guerrilla marketing ploy, from a time when activism was more than sitting behind a computer ordering stickers and (mostly not) clicking a link. Leave the sticker wars to students searching for an ideological dopamine rush and soccer fans claiming a neighborhood as "their territory."\ \ As Bitcoiners, we can do something more useful. For example: ask yourself how many businesses in your area accept Bitcoin, or what coworker you can save from investing in blatant scams, or… invent something nice, start a meetup, podcast, or learn to code, convince, build.
Bitcoin deserves better.
by AVB / tips go here
@avbpodcast - allesvoorbitcoin.be - 12 Bitcoin Food for Thought
https://typeset.io/papers/attitudinal-effects-of-mere-exposure-12e5gwrysc
https://www.research.ed.ac.uk/en/publications/stickin-it-to-the-man-the-geographies-of-protest-stickers
https://www.warc.com/content/article/warc-datapoints-gwi/too-many-ads-is-the-most-damaging-factor-for-brands/en-gb/136530
https://pmc.ncbi.nlm.nih.gov/articles/PMC9444107/
-
 @ ff517fbf:fde1561b
2025-03-26 16:48:41
@ ff517fbf:fde1561b
2025-03-26 16:48:41フアン・ラモン・ラッロ氏は、スペイン出身の経済学者・作家であり、自由市場経済とリベラルな思想の提唱者として知られています。彼は、国家による過剰な介入や財政政策の問題点を鋭く分析し、自由主義の基本原則に基づく社会の実現を目指す論考や著作を多数発表しています。数多くのメディアや学会で講演を行い、現代社会における経済政策や公共の役割について、国際的な議論にも影響を与えている人物です。

皆様、こんばんは。そして、Andorra Economic Forumの皆様、本日はご招待いただき誠にありがとうございます。
本日の講演では、これまで私が持ち続けてきた見解、すなわち、より自由で、より繁栄するために、スペイン及び世界において自由主義革命がなぜ必要であり、さらには急務であるのかという理由をお伝えしたいと思います。また、現代国家が、ストックホルム症候群のような論理に我々を陥れており、その結果、国家が我々の自由を体系的に制限し、財産を構造的に攻撃している状況を、ほとんどの人々が抗議もせず、またはその非常事態性すら意識していないという現実をどのように理解すべきかについても触れます。まず初めに、皆様のご反応から察するに、これは既知の内容に感じられるかもしれませんが、自由主義の基本原則、すなわち四つの基本的な考えを確認させていただきます。どのようにして、社会生活と、各個人が自らの人生計画を追求するための自律性とを両立させ、かつ、個々の自律性が打ち消されるような一個または多数の専制に服従することなく生きることができる社会が成立するのでしょうか? それは、協力と共存が可能な社会の中で、各人が自己の利益を追求し、同時に他者の利益追求を尊重するための基本原則、すなわち以下の四つの原則によって支えられているのです。
第一に、個人の自由、すなわち他者の行動を踏みにじることなく自ら行動するという、いわゆる非攻撃の原則です。自分が望むことは何でもできますが、他者が望むことをするのを妨げてはならず、また、他者があなたの望むことを妨げることも許されないのです。
第二に、私有財産です。平和的に獲得し、平和的に自らのものとしたものはあなたのものであり、それによって自由に行動し、自らの人生計画や行動計画を追求する手段となります。もしも、これらの計画遂行に必要な手段が恣意的に奪われるならば、それはあなたの個人の自由、すなわち自らの人生計画を追求する自由を侵害することになるのです。
第三に、契約の自律性です。あなたは第三者と自由に合意を結ぶことができます。もちろん、第三者を攻撃することは許されませんが、双方が望むことについて自発的に合意することは可能です。合意は、当事者間の私法上の契約であり、両者が履行すべき約束であり、第三者が介入してこれを正当化したり否定したりするものではありません。ただし、合意の内容は、あくまで当事者双方やその所有物にのみ影響を及ぼすものです。
そして最後に、広義の意味での結社の自由です。個人は、契約上、望むことについて合意するだけでなく、共に生活する方法や、ある程度安定した形で組織される方法を合意することも明示的に可能です。これらの原則は、しばしば国家によって保証されると言われます。なぜなら、国家がなければ、法体系も安全保障機関も存在せず、個人の自由、私有財産、契約の履行、そして結社の自由を保障するものが何もないと思われがちだからです。とはいえ、確かにある程度の国家は、警察国家としてこれらの基本的な社会的共存の規範を保証するために必要かもしれませんが、私たちが必要としているのは、単にこれらの自由主義社会の原則と自由な人々の相互作用が尊重されることを確保するための、巨大かつ過剰な国家ではありません。
実際、国家が大きくなるほど、つまり社会における国家の存在感が増すほど、これらの原則は侵害されがちです。なぜなら、国家は恣意的に規制を強化し、税金を引き上げることで、たとえ他者に損害を与えなくとも、個人が望むように行動する自由を阻み、また、私有財産を強制的に奪い、当事者間の取引を妨げ、さらには、結社および脱会の自由さえも制限してしまうからです。たとえば、誰かが既存の国家から離れ、他の国家に参加したり、あるいは新たな国家や政治共同体を形成して自らを組織しようとした場合でさえ、現行の国家はそれを認めないのです。
さて、これらの自由主義の基本原則は、各個人の計画や人生のプロジェクトが社会の中で花開くために必要不可欠なものであり、現代国家によって体系的に侵害されているのです。しかし、現代国家とは、必ずしも常に我々と共にあった国家ではありません。私たちは、今日のようなメガ国家、ハイパーステート、過剰に肥大化した国家をある程度は当たり前のものとして受け入れてしまっていますが、これらは唯一の政治的選択肢ではなく、歴史を通じて存在してきた唯一の政治現実でもないのです。
ここで、主要な西洋諸国における国家の社会に占める重みの変遷について、皆様にご覧いただければと思います。今日、国家の重みは国によって大きな違いはないものの、概ね国内総生産(GDP)の40〜50%を占めています。中には、例えばフランスのようにGDPの60%に達する国もあります。国家が社会的調和や幸福の保証とされることは稀であり、実際、フランスは世界最大の国家を有しながら、またはそのために、今最も分断され混沌とした国の一つとなっています。
しかし、現状、国家はGDPの40〜50%、すなわち社会が毎年生み出す生産の約半分を吸収し、再分配または政治層や官僚階級が決定した形で消費しているのです。これは常にそうであったわけではありません。19世紀、ひいては第一次世界大戦前までは、近代先進国における国家の経済的重みはGDPの5〜10%程度に過ぎなかったのです。
例えば、アメリカ合衆国では第一次世界大戦前、国家のGDPに占める割合は3〜4%でしたし、今日巨大な社会民主主義国家となっているスウェーデンでさえ、かつてはGDPの5%程度でした。すなわち、国家というものが必然的に経済の半分を占めなければならないというわけではなく、これは徐々に積み重ねられてきたプロセス、いわばゆっくりと沸騰させられるカエルのようなものです。第一次世界大戦後、国家の経済に対する重みは大幅かつ確固たる上昇を見せ、さらに第二次世界大戦後には、急激かつ持続的な上昇を経て、1970年代以降、現在の水準にまで達したのです。
ちなみに、ここで我々がしばしば耳にする「国家が後退しているから、我々は新自由主義の時代にいる」というレトリックが、いかに毒性がありずる賢いものであるかにも注目してください。過去40年間で、グラフ上に国家の重みが大幅に後退したと示す兆候は見当たりません。ある時点で国家のGDPに占める割合が1〜2%減少することがあったとしても、200年の間にGDPの5%から50%へと増加し、現在は概ね50%前後に留まっているのです。国家が後退し、民間部門がすべてを占めるようになっている、というのは全く逆の現象です。
実際、多くの人は、国家が拡大し続けるのが当然であり、もし急速な成長が見られなければ、国家は後退していると考えがちです。しかし、国家は既にそれ以上大きく成長する余地がほとんどないのです。もちろん、GDPの60%、70%、80%にまで達すれば、直接的または間接的な社会主義経済になってしまいます。
そして、なぜ国家はこれほどまでに成長したのでしょうか。急激な国家拡大を説明する基本的な要因の一つは、福祉国家の発展です。つまり、かつては国家が提供していた医療、社会保障(年金、事故保険など)や教育といったサービスの国家による提供が、福祉国家として大きく発展したのです。
ご覧の通り、1930年代や第二次世界大戦後までは社会保障費は非常に低い水準にありましたが、特に第二次世界大戦後からは、GDPの20〜30%にまで急上昇しました。これらはかつて、市民社会や市場を通じ、または必ずしも商業的な交換を介して提供されていた、労働組合などが担っていた社会保障の役割を、国家が吸収していったものです。労働組合は国家から独立し、時には国家に対抗しながら、社会保障の機能を果たしていたのですが、その役割が国家に吸収されることで、我々は国家に依存するようになってしまったのです。
なぜなら、社会保障費は支出であり、中には「依存費用」とも呼ばれるものもあります。たとえば、老後に収入がなくなった時や、何らかの障害によって収入が得られなくなった時のために、個人の貯蓄から基金を積み立てる場合、その基金が自分自身で管理されるなら自律的ですが、国家が管理すれば、私たちは国家に全く依存することになってしまうのです。国家が消滅するか、大幅な予算削減が行われれば、我々は何も残らないのです。結果として、国民は容易には消えない国家の爪痕に囚われることになるのです。公共年金制度の問題を考えてみてください。現代の先進国家において、公共年金制度は最も大きな支出項目の一つです。
では、どうすれば公共年金制度を解体できるのでしょうか。どうすれば、必要以上に介入してきた国家、例えばアメリカ合衆国では大恐慌期(1930年代)に、必要がなかったのに介入してきた国家を、その状況から脱却させることができるのでしょうか。設立当初は、ある一定の年齢に達した者には一定額の年金を支給すると約束し、その費用を現在働いている者への税負担によって賄うというシステムでした。
システムの構築は、当時の平均寿命がかなり低く、支給期間が2~3年程度であったため、比較的容易で安価に行われたのですが、システムが一度確立され、世代を超えた労働者の貯蓄能力を事実上奪う形で構築された今、どうやってそれを解体すればよいのでしょうか。もし「年金は支給されなくなるのか」と言えば、かつて生産期に労働者の給与のかなりの部分を国家が吸収し、貯蓄を阻害していた結果、何百万人もの人々が貧困に陥ることになるのです。
じゃあ、もう引退されている皆さんは年金を受け取ることになりますが、現役世代がその年金の費用を負担し、そして自分たちが引退する時には年金を受け取ることができなくなるのです。つまり、この世代からは何の対価もなく、給与のごく大部分が没収されることになるというわけです。これをどうやって解体するつもりですか? 決して容易なことではありません。
また、例えば医療制度についても同様です。若者にとっては医療制度の解体はそれほど難しくないように見えるかもしれませんが、貯蓄がなく、保険にも加入していない高齢者にとって、もし今、公共医療制度が終了し、年齢とともに医療費が指数関数的に上昇するために通常以上の医療費が発生すると告げられたら、彼らはその医療費にどう対処すればよいのでしょうか? 彼らは、公共医療制度が機能するという説明のもとに、その医療費が賄われると予め想定し、税金を支払っていたのです。
これをどう逆転させるか? もちろん、即座に行えることではありませんが、時間をかけた移行措置として行っていかなければなりません。だからこそ、国家はこの道を通じて成長し続け、社会がますます国家による再分配に依存するようになることで、国民の自律性を奪っていくのです。
ちなみに、現代福祉国家の発明者の一人であるのは、プロイセン出身のドイツの首相オットー・フォン・ビスマルクです。彼の回顧録――つまり、批判的ではない親しい記者によって書かれた回顧録――によれば、ビスマルクは、公共年金制度を創設することで労働者階級を国家に依存させ、労働者が国家に対して反抗しないように仕向けたと説明しています。当時、反抗は、いわば反資本主義的な行為とみなされていたのです。彼は、国家主義を維持するためではなく、「労働者には社会主義的傾向がある。では、どうすれば労働者を手なずけることができるのか?」という視点から、公共年金制度を利用したのです。同様に、労働者は公共年金制度を通じて、または国家に対抗する形で手なずけられるのです。そして、現状はこの通りになっています。
そこで、皆さんは疑問に思うかもしれません。この何世代にもわたって築かれてきた巨大国家は、具体的にどのような機能を果たしているのでしょうか? その資金はどこに行っているのか? この巨大国家は何に対して支出をしているのか? ここに、2022年の欧州連合各国の平均、すなわちGDPの50%という数字があります。スペインの場合も2022年時点で大きな差はなく、GDPの47%を支出しているため、概ね代表的な数値といえます。さて、この50%のうちの20%は社会保障費、主に年金費用(老後だけでなく、遺族、障害、孤児などに関する給付も含む)です。これに加え、比較的低コストな非拠出型給付も存在します。次に、スペインの場合は約7.7%、すなわち7〜8%が医療費、6%が官僚機構の運営費用、そして何よりも重要なのが公債の利子支払い費用です。さらに6%は経済政策に充てられ、例えばインフラ整備や農業支援などが含まれています。教育に関しては、公立教育や協定校を含めて約4.7%、環境保護は0.8%(これは必ずしも気候政策だけでなく、森林の管理なども含む)、住宅や地域サービスが1%、そして余暇、文化、宗教に関しては1.1%となっています。これらは、メディアや文化、宗教団体への補助金などとして支出されています。
かつて、リベラルな最小国家、例えばアメリカではGDPの3%程度であった国家がありました。なぜなら、当時は上記のような広範な機能を持たず、防衛(GDPの1.3%)と治安・司法(GDPの1.7%)に集中していたからです。つまり、19世紀にGDPの3%を占めていた国家が、現在もその核となる部分は同じ3%のままであるということです。国家が高価になったわけではなく、19世紀に存在した国家のコストは大体同じであったにもかかわらず、現代国家は19世紀よりもはるかに多くの機能を担っているため、多くの税金が必要とされているのです。もちろん、すべては税金で賄われています。
では、いったいどれだけの税金が支払われているのでしょうか。ここでは、国民が被っている税負担の実態について十分に認識されていないのではないかと思います。もしその実態が明らかになれば、社会的不服従が起こるでしょう。国家は、税の実感を曖昧にするための手段を多数用いているのです。例えば、さまざまな理由で税金を徴収する仕組みです。「この項目に対して税金を払え」と一律に要求するのではなく、「稼いだ金額、支出、保有資産、さらには支出全体に対して税金を課す」といった形で、複数の種類の税金を同時に適用します。消費全体に対して一律に税金を課すのではなく、付加価値税(IVA)やその他の特別税など、多岐にわたる特別な税金が存在し、相続税に至るまで多岐に渡ります。
さらに、我々はさまざまな側面で税金を支払っているにもかかわらず、その実感すら持っていないこともあります。たとえば、関税はその値上がり分を商品の価格に転嫁されるため、意識されにくいのです。付加価値税が上がっても、スーパーなどが告知しない限り、私たちはその上昇に気づきにくいのです。また、税負担を一度にまとめて徴収するのではなく、分散して給与から差し引くことで、その実感を薄めています。かつては、年間に稼いだ金額に対して一括で所得税(IRPF)を支払うのが普通でしたが、現代では分割して徴収されるため、納税者は自分がどれだけの税金を支払っているのかを実感しにくいのです。ちなみに、IRPFの源泉徴収制度は、第二次世界大戦中にリベラルのミルトン・フリードマンによって考案されたものです。つまり、敵はしばしば自国に潜むものでもあるということです。
ここで示したのは、平均的な支出額です。スペイン国家のすべての財政収入を国民または労働者で割ると、国民一人あたりの国家負担のおおよそのコストが見えてきます。実際には公共赤字、すなわち収入以上に支出している部分もあり、その分は将来の税負担として転嫁されるため、実際のコストはさらに大きくなります。ここでは、現状で国民から徴収されている税金のみを取り上げています。なお、これらの数字はインフレーションを考慮していないため、2001年と2024年の数字を直接比較することはできませんが、ここでは2024年現在の状況に焦点を当てています。現在、平均してスペイン国民一人あたり、約15,000ユーロの税負担がかかっているのです。つまり、一般的には夫婦と子供一人の家庭で約50,000ユーロの税金が支払われている計算になります。労働者という視点に立てば、実際に税金を支払っているのは、平均で30,000ユーロ以上にのぼります。もちろん、高所得者層が多くを負担しているという見方もありますが、これは平均値であり、平均値は必ずしも実態を正確に反映するものではありません。
さて、労働者一人あたりの支払いを、かなり寛大な見積もりで考えてみましょう。スペインにおける現在の中央値の給与は22,400ユーロです。しかし、この22,400ユーロという数字が給与明細に反映される前に、企業側がすでに支払っている社会保険料が約7,000ユーロ存在しています。つまり、実際の中央値の給与は29,000ユーロ、ほぼ30,000ユーロであるべきものですが、この30,000ユーロは労働者自身が実感できるものではありません。そして、たとえ「実際は自分のものである」と伝えても、「それは企業が支払っているものであって、自分が支払っているわけではない」と言われ、自己欺瞞に陥るのです。結局のところ、実際に支払っているのは自分自身なのです。
実際、30,000ユーロの実質報酬を基にすると、そこから7,000ユーロが差し引かれて、給与明細に表示されるのは22,400ユーロです。さらに、労働者側の社会保険料として約1,500ユーロを追加で支払い、所得税(IRPF)が約3,000ユーロ、さらに消費に応じた間接税が最低でも約2,000ユーロ(場合によってはそれ以上)かかります。さらに、ここでは取り上げていない他の国家への支払い、たとえば不動産税(IBI)やサービス料、共済負担金なども存在します。結果として、中央値の労働者は、本来約30,000ユーロあるべき給与のうち、税引き後に手元に残るのは約15,800ユーロに過ぎないのです。つまり、ほぼその半分が国家によって吸収されていることになります。年間で見ると、さまざまな税金、特に社会保険料、所得税、そして間接税として、合計約13,400ユーロが徴収されているのです。
このように、中央値の労働者は、所得分布の中央に位置しており、非常に多くの人々が彼より少なく、また多く稼いでいる人もいます。だからこそ、中央値の労働者が支払っている税負担、すなわち年間約13,400ユーロという数字は、スペイン国民に対して行われている極めて大規模な税負担の実態を物語っています。これにより、国家から提供されるサービスが強制的に受け入れられているのです。
果たして、これは必然なのでしょうか? 歴史的に見れば必ずしもそうではなく、また現代においても地域によって差があります。つまり、労働者が生み出す富の半分以上を国家が吸収するという、巨大な国家が当然であるという考え方は、今後も続くものではありません。ここには、異なる繁栄度を持つ国々が存在し、一般的に発展した国々であっても、欧州やアメリカのような国家に比べ、国家の規模はかなり小さく抑えられている国もあります。しばしば「スペインの国家規模は欧州平均より小さい」と言われますが、欧州平均自体が、プロの略奪者たちのクラブのようなものなのです。従って、欧州平均という水準と比較するのではなく、もっと控えめな国家規模を持つ国々や、税負担の貪欲さが制限された国々と比較すべきです。
例えば、ヨーロッパ内ではスイスがあります。偶然かどうかはさておき、スイスはヨーロッパで最も豊かな国の一つでありながら、国家のGDPに占める割合は33%と、欧州やアメリカに比べて10〜15ポイント低いのです。また、香港や韓国はGDPの28%、チリはこの分類の中では最も貧しいかもしれませんが約26%、台湾は16%、そして世界で最も豊かな国であるシンガポールは15%です。シンガポールや台湾は、国家がGDPの15〜16%という小規模な状態で十分に現代社会の機能を果たしているのです。もちろん、シンガポールの場合は都市国家であるため、経済規模のメリットもあるでしょうが、公共支出の大部分が社会保障に回っている現状を鑑みると、都市規模か大国家かは大した違いがないのです。むしろ、シンガポールや台湾のように、GDPに対して国家の規模が30ポイントも低い国の方が、国家による私有財産の侵害が少ないと言えます。
したがって、もし大規模な国家による大規模な略奪を回避でき、しかも機能的には他の国と同等以上に運営できるのであれば、当然、より少ない税負担で、なおかつより効率的な公共サービスを提供する国家の方が望ましいのです。実際、国家が何でもかんでも行おうとすれば、その多くは非効率にならざるを得ません。一方で、企業がすべてを行おうとしても、専門分野に特化した他の企業に競争で敗れるため、最終的には消費者がより良いサービスを選ぶことになるのです。問題は、国家の場合、国民が国家から自由に離脱し、同じサービスを提供する他の組織と契約する余地がないという点にあります。国民は、非常に非効率かつ高コストな国家サービスに縛られており、選択の余地がないのです。したがって、もし小規模で効率的な国家が存在すれば、それは大規模で税負担の重い国家よりも好まれるはずです。
そして、もし国家が回収するGDPの割合が30ポイントも大きいのであれば、それは明らかに国民の私有財産を暴力的に侵害していると言わざるを得ません。ですから、もし国家による大規模な略奪を回避し、かつ他国と同等以上の機能を果たすことが可能であれば、国家は少なくとも縮小されるべきです。なぜなら、そうした国家は国民にとって好都合であるだけでなく、公共サービスの質も向上し、効率的に運営されるからです。結局のところ、すべては国家ではなく、国家に寄生する巨大な官僚組織の福祉が優先されているのです。
もし、あなたの社会にこれほど大きく根付いた寄生虫が存在するならば、その寄生虫は当然、去ろうとはしません。むしろ、さらに大きな植民地を形成しようとするでしょう。これが、国家が成長し続ける理由であり、そして、血を吸い上げるこの寄生虫と戦う必要性が生じる所以なのです。
別のシナリオを考えてみましょう。つまり、現代社会における国家の規模を実質的に縮小するという仮定を立て、その実現可能性や現実味について見極めるためです。これまでに、ヨーロッパにおける現代国家の重みがGDPの50%に達していること、その内訳を示してきました。さて、かつての状況を想像してみてください。あの時代は、科学フィクションのようなことは必要なく、医療はゼロ、経済政策も実質ゼロで、民間部門が構築できないインフラだけが、もしあれば驚くほど僅か、GDPの1%程度だったのです。教育はゼロ、防衛と公共秩序は維持されるものの、余暇・文化・宗教への補助金はゼロでした。地域サービスや環境保護に関しては、下水道、街路灯、森林の維持管理など必要な分は残され、官僚組織も非常に大幅に縮小され、社会保障も一部のみが残されていました。
さて、しばしば「国家は富裕層からお金を奪い、貧困層へ再分配するために存在する」と言われますが、実際、社会保障はGDPの20%に相当します。ここで、極端な貧困を防止するために本当に必要な支出額を計算してみましょう。そうすれば、皆さんも、このGDPの20%は貧困撲滅のためのものではなく、むしろ国家が横方向の所得再分配システムを通じて国民を捕らえ続けるためのものであると気づくでしょう。すなわち、国家はあなたからお金を取り、そのお金を自らの利益や必要に応じて配分するために、あなたと国家の間に割り込むのです。バストス教授が正しく指摘しているように、その所得の移動は、富裕層から貧困層へ、またはその逆ではなく、すべての人々から国家へ向かっているのです。そして国家は、その所得を自らの利益や必要に従って再分配することを決定します。
では、先ほど示したような形で国家の各機能を大幅に縮小した場合、結果として国家はGDPの9~10%程度の規模となり、現状よりも30~40ポイント、つまり約80%縮小された国家になるでしょう。防衛費、治安費は現状と同等に維持される(ただし、治安費については内部の官僚機構によっても左右されるため、この点はまた別の議論になります。たとえば、スペインはヨーロッパで国民一人あたりの治安部隊職員数が最も多い国ですが、本当にそれだけ必要なのかはまた別問題です)。安全保障費がGDPの1.7%、防衛費が1.3%、官僚組織が1%、地域サービスや環境保護が1%、民間部門ではまかなえないインフラがさらに1%、そして社会保障が3%という具合です。現在、社会保障としてGDPの3%、すなわち450億ユーロが支出されています。これは、450億ユーロの社会保障費を、例えば4.5百万人(スペイン人口のおよそ10%)に対して年間1人あたり1万ユーロずつ支給するか、あるいは300万人に対して1万5千ユーロずつ支給するということになります。繁栄した社会において、極端な無助状態に陥る国民の割合はどれほどか、という問題です。彼らは、生命保険、障害保険、個人貯蓄すら持たず、福祉国家が生まれる前に存在したボランティアや民間の相互扶助ネットワークさえも利用できなかった層です。これらを踏まえた上で、絶対的な無助状態に陥り、国家からの継続的な支援を必要とする国民の割合がたとえば5~10%だとすれば、実際に必要な支出はGDPの3~4%程度で十分にカバーできるはずです。しかし、現実には我々は社会保障にGDPの20%を費やしているのです。
明らかに、このGDPの20%は、富裕層から少しだけ富を奪って、巨大な貧困層を作らないためのものではありません。驚くべきことに、国家がGDPの50%を占めるにもかかわらず、貧困層は依然として存在しているのです。さらに、貧困を解消するための手段として、まず第一に、依存性を生む補助金を設けるべきではありません。しかし、現実には、経済活動が全くできず、自己の貯蓄や家族の支援、民間の相互扶助ネットワーク、そして最終的には国家に依存せざるを得ない層が一定割合存在します。しかし、そのようなケースはGDPの3%程度の支出で十分にカバーされるはずなのです。
さて、国家の規模を縮小した場合、たとえばGDPの50%から10%にまで削減できると仮定しましょう。これは約80%の削減に相当します。先に述べたように、中央値の労働者は現在、年間約13,500ユーロの税金を負担しています。この80%の削減が実現すれば、労働者の可処分所得は、国家が提供する各種サービスに充てるための支出分が年間1人あたり1万~1万1千ユーロ増加することになります。家庭内で中央値の労働者が2人いる場合、2万~2万2千ユーロの追加収入となるでしょう。この追加収入があれば、教育費、医療費、年金のための貯蓄など、国家が現在負担させているコストを自前でまかなうことが可能になるはずです。実際、多くのスペインの労働者は、国家の劣悪なサービスから逃れるため、民間の医療や教育、そして補完的な年金積立を実施しているのです。特に、公共教育は、学生の生産性向上よりも、国家のイデオロギーを植え付けることに重きを置いている場合が多いのです。
また、この話は、GDPの3%相当の再分配、すなわち450億ユーロ分が、現実的に考えても国民の基礎的な生活を支えるには十分であるという観点からも論じられます。現行の過剰な収用体制に対して、もし国家規模が大幅に縮小されるならば、労働者にとって有利な状況が実現するはずです。
さて、ここまでの議論から、もし国家主義のウイルスが社会の頭脳や利権に深く根付っている現状において、現状が最適でないと理解したとしても、移行のコストの高さゆえに多くの人々が現状から変わることを望まないという現実があるのです。たとえば、公共年金制度の解体は非常に困難です。年金受給者は「こんな不公平な体制であっても、自分の年金を受け取りたい。自分自身の貯蓄がなくなるリスクを冒したくはない」と考えるでしょう。
では、この国家――明らかに国家とその官僚機構に有利なこのモデル――から脱却するために、すなわち、表向きは国民のために存在するようでいて、実際には社会を寄生しているこの体制から逃れるためには、どのような手段が考えられるでしょうか。ここで、国家改革またはハイパーステートのパラサイト化に対抗するための、四つの可能なアプローチについて述べます。
第一のアプローチは、トップダウン型の方法です。すなわち、自由主義的な理念を掲げた善意の政治家が権力の座につき、内部からリベラル革命を起こそうとするというものです。しかし、私はこの方法は、次に述べるボトムアップ型の文化戦線と併せなければ、全体として非常に単純で実現不可能だと考えます。なぜなら、社会の大多数が国家改革を望まなければ、その改革は十分な勢いを持って実施されることは決してないからです。多くの改革は長期的な取り組みであり、一夜にして実現できるものではありません。一度実行された改革が元に戻らないようにするには、最低でも二世代を要するのです。もし社会がその方向に向かわなければ、いつかまた別の人物が権力に就いて、国民の大多数が望まない体制を再び打ち壊してしまうでしょう。例えば、チリの年金制度の民営化は、ピノチェト政権下の1981年に始まり、数年前に旧公共年金制度が完全に清算されました。しかし、その後、旧体制に戻そうとする動きが見られるのです。なお、チリは当時、非常に若い労働人口と限られた高齢人口という、改革に適した人口構造を有していたにもかかわらず、改革には約40年もの歳月がかかりました。これが、世界の他の国々で実施されるとなれば、どれほど困難なものになるか想像に難くありません。そして、もし世界中がそのような改革を望まなければ、いかに自由主義者の政治家を内部に潜り込ませ、社会民主主義の装いを与えたとしても、十分な効果は得られないでしょう。さらに、政治そのものが権力に触れると必ず腐敗すると、ロード・アクトンが指摘したように、権力は人を変えてしまいます。つまり、権力に惹かれて権力の座についた者は、その権力を維持・拡大するために、かつて掲げた理念を容易に放棄し、他者を蹂躙し、欺く行動に出るということです。
政治的競争というのは、もしあなたが行動しなければ、行動する者があなたを追い出してしまう、という状況を生み出します。そのため、もし存在するとしても、誠実で、信念を持った政治家は、力に屈する者に押されて公共の場から姿を消してしまうのです。権力闘争では、手が縛られている者と自由な手を持つ者との間で戦いが行われるため、劣悪な選択が働き、最終的には最悪の者が権力の座に就くという現象が生じるのです。(この点については、ハイエクも『隷属への道』で記述しています。)
次に、第二の可能性はボトムアップ、すなわち文化戦線によるアプローチです。これは、アイデアの戦いを、じわじわと、少しずつ社会に浸透させ、心を開かせ、意識を目覚めさせ、より多くの人々がこの変革を要求するようになるという方法です。しかし、これは特に有望な道ではないことは明白です。もし、ここでマルクス主義的な語調に傾くとすれば、客観的な物質的条件があって、そうした思想が大規模に広まる環境が整わない限り、人々は現状に満足して「今のままで十分だ」と感じ、急激な変革に乗り出す理由が見出せません。現状が著しく悪化しない限り、文化戦線による大規模な勝利が起こり、既存の社会制度が覆されるというのは極めて困難な道なのです。例えば、アルゼンチンでは、40年間にわたって底をつき続けた結果、人々が明らかに欠陥だらけのモデルにうんざりし、ハイパーインフレーションに苦しんだことで変革が進んだように見えます。もし、そこに一貫性があり、破壊的かつ斬新なメッセージ―社会主義的なものか、あるいは幸運にもリベラルなもの―があれば、一定の確率でそのアイデアが覇権を握り、新たな現状として定着する可能性が出てくるのです。しかし、スペインの場合、文化戦線による闘いは、相手側のプロパガンダがあふれ、対抗する者がいなければ、現状が一層固定化し、国家権力が加速度的に拡大していくため、非常に厳しい状況にあります。私自身も長い間、文化戦線で戦ってきましたが、スペインという環境におけるその限界を痛感しています。
第三の道は、そもそも国家改革を目指さず、自分の生活を改善するために他の地域へ移住するというものです。もし、競争が可能な複数の法域が存在すれば、現状に非常に不満を抱く者は、物理的に他の地域へ移り住み、そこで自らの生活基盤を築くことができます。そして、こうした法域間の競争は、他の法域による収用や寄生的な政策の力を制限する効果も持ちます。たとえば、ある法域で税率が非常に低く、規制が緩やかであれば、他の法域は資本が流出し、寄生者側から見れば、寄生対象(=ホスト)が成長しなければ、寄生する意味がなくなるのです。もし、ホストを窒息させて殺してしまえば、またはホストが他の、寄生が少ない地域へ流出してしまえば、寄生者にとっては不利益となります。このような効果は、実際には見かけ以上に大きな影響を持つのです。
たとえば、最も身近な例として、アンドラの場合が挙げられます。多くの場合、静かに、あるいは時に華やかに報じられる移住現象があり、一定の社会的反響を呼んでいます。問題は、これらはすべて財政上の問題であり、移住者を犯罪者扱いする試みがあっても、スペイン国家にとっては重要な問題とならないのです。よく批判されるのは、YouTuberなどがアンドラへ移住することについて、「国が自国民の資源不足を訴えるような状況に直面しない」とされる点です。もしそうなれば、国家は財政の引き締めを迫られるはずですが、現実はそうではありません。むしろ、これは他者に対する懲罰の一形態であり、「移住して税負担を軽減しようとするなら、あなたは悪い人間であり、悪い市民だ。もしあなたが著名人であれば、意識を啓発するために、我々はあなたを徹底的に攻撃し、公の場から追放する」といったメッセージが発せられるのです。しかし、実際にアンドラへの移住が進むこと自体は悪いことではなく、たとえそれがスペイン国家に与えるダメージが短期的にはそれほど大きくなくとも、他のケースでは、目に見えにくいながらも国家に損害を与えている場合があるのです。
たとえば、2か月前に発表されたドラギの報告書では、欧州が「足を引きずっている」との根本的な不満が示されています。すなわち、欧州では生産性が20年間にわたって停滞しており、成長期に新たに設立される企業が、厳しい規制の下で成長できず、資本調達が困難となり、結果としてアメリカに流出してしまうという現象です。これは「足で投票する」という現象であり、企業側の実情を反映したものです。そして、これは国家権力の内部から出た、我々の社会が停滞しているという自らの寡占層からの認識でもあります。彼らは、ここ20年間にわたり市民を内部から圧迫してきた手法を見直す必要があると訴えているのです。そして、ここで議論されているのは、欧州連合とアメリカという二つの経済ブロック間での移住の問題なのです。
もし、かつてヨーロッパに存在していたような、多数の競合する法域が現在も存在していたと想像してみてください。ここで歴史的な議論に深入りするつもりはありませんが、ヨーロッパが16世紀あるいは17世紀から産業革命に至るまで発展し、東洋が(少なくとも最近まで)停滞していた理由の重い仮説の一つは、ヨーロッパが政治的にはるかに細分化され、都市国家や小国、王国、そして公国など、まさにアンドラのようなケースに近い形態であったため、相互の競争が激しかったという点にあります。ひとつの領域内で生まれる思想を制限・抑制・検閲する能力は非常に低く、もし一方で弾圧されれば別の場所へ移動できたため、その結果、後の産業革命を引き起こす知的な開花が促されたのです。これに対して、中国のような中央集権的で統一された国家では、官僚組織が本来より強大な権力を持っていたため、このような発展は見込めませんでした。
「足で投票する」という現象は非常に強力です。したがって、文化戦線から取り組むべきもう一つの課題は、政治的な中央集権化や財政の調和化に反対することです。なぜなら、政治的に中央集権化が進んだり、財政が調和化されるほど、法域間の競争は減少し、その結果、国家が無罰で私有財産を寄生的に吸い上げる余地が広がるからです。これは市場経済ではよく理解される現象ですが、国家の場合は例外扱いされがちです。市場において本当の意味での独占、すなわち単にその分野で唯一の企業という状況ではなく、競合が存在しない真の独占状態になると、その独占者は価格を引き上げ、品質を低下させる傾向にあります。なぜなら、あなたは逃げ出すことができない、まるで人質のような状態に置かれるからです。つまり、国家もまた独占状態にあり、国家が直面する唯一の競争は、他の国家へ移住するという可能性なのです。領域を統一して競争余地を狭めれば狭めるほど、国家は独占的な力を強め、結果としてあなたに提供するサービスの質を低下させ、収用を強める傾向が出てきます。したがって、私はどんな中央集権化のプロセスにも反対し、逆に政治的な分権化を支持すべきだと考えます。
そして最後に、第四の戦略ですが、これはやや曖昧で漠然としているかもしれません。しかし、私が考えるに、実際に多くの人々が採用しており、多くの場合国家の影響力を制限している方法、それは直接的に「国家からの分離」を目指すことです。もちろん、あなたにとって寄生者のような国家が窮屈に圧しかけてくる場合、その寄生者を打倒しようと多大なエネルギーを費やすこともできます。しかし、寄生者が既に存在する以上、その存在を前提として生活基盤を築く、その固定費を受け入れながらも、寄生者のさらなる拡大を防ぐ、あるいは寄生の及ばない領域を確保する新たな方法を模索するということです。これが国家からの「分離」、すなわち、重くのしかかる国家の負担から自らを切り離す試みなのです。例えば、先に述べたように、私立教育、私立医療、私的年金といった選択肢があります。本来であれば、国家が私たちから過剰な資源を吸い上げることなく、その分をこうした目的に振り向けられれば理想的ですが、幸いなことに、現状では国家が私立教育への進学を禁止しているわけではありません(ただしかなりの規制は存在します)。私立教育は完全に自由なものではなく、国家のカリキュラムに沿ったものですが、それでも私立教育、私立医療、そして貯蓄や資産形成の道を開いてくれるのです。もちろん、今後さらに税が引き上げられ、国内外で資産が収用されるリスクが高まるまではの話ですが。
したがって、国家を一つの悪と捉え、その悪に支配される中で自由を追求する、すなわちその影響力からできるだけ逃れる方法を探るべきです。さらに、社会が自ら開発していく様々なツールが、私たちが国家の監視や統制から離れて生活する手助けとなります。たとえば、デジタル経済は、今日のところ、国家が我々をコントロール・規制・収用するのをより困難にする領域をある程度確保できる可能性を秘めています。ビットコインの例は、没収不可能な資産として、適切な管理を行えば、富の保蔵庫あるいは国家の統制や知識から独立した交換手段として機能する可能性を示しています。
これらは、寄生者である国家に吸い付かれないため、自らの活動から国家の影響力を一部でも排除する、新たな生活の仕方を模索する一つの方法です。こうした新しいツールは、今後も次々と登場し、国家が私たちの生活に及ぼす影響を制限するために活用されるべきです。社会全体を変えるのは非常に困難ですが、多くの人々を同じ方向に動かすことが難しい現状において、少なくとも我々が体系的に受けている搾取の度合いを最小限に抑えることは可能です。
以上、複数の道筋があります。第一の道は私個人としてはほぼ排除したいと考えますが、残りの三つは排他的ではなく、互いに補完し合うものです。どの方法も目的地に必ず到達できる保証はありませんが、これらは連携することで、国家が私たちや社会全体に及ぼす権力の影響を徐々に抑制する助けとなるでしょう。そして、我々自身の利益のため、あるいは共に生きる社会を改善するために、可能な限りこれらの道を追求すべきだと考えます。
-
 @ 21335073:a244b1ad
2025-03-18 20:47:50
@ 21335073:a244b1ad
2025-03-18 20:47:50Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ ecda4328:1278f072
2025-03-26 12:06:30
@ ecda4328:1278f072
2025-03-26 12:06:30When designing a highly available Kubernetes (or k3s) cluster, one of the key architectural questions is: "How many ETCD nodes should I run?"
A recent discussion in our team sparked this very debate. Someone suggested increasing our ETCD cluster size from 3 to more nodes, citing concerns about node failures and the need for higher fault tolerance. It’s a fair concern—nobody wants a critical service to go down—but here's why 3-node ETCD clusters are usually the sweet spot for most setups.
The Role of ETCD and Quorum
ETCD is a distributed key-value store used by Kubernetes to store all its state. Like most consensus-based systems (e.g., Raft), ETCD relies on quorum to operate. This means that more than half of the ETCD nodes must be online and in agreement for the cluster to function correctly.
What Quorum Means in Practice
- In a 3-node ETCD cluster, quorum is 2.
- In a 5-node cluster, quorum is 3.

⚠️ So yes, 5 nodes can tolerate 2 failures vs. just 1 in a 3-node setup—but you also need more nodes online to keep the system functional. More nodes doesn't linearly increase safety.
Why 3 Nodes is the Ideal Baseline
Running 3 ETCD nodes hits a great balance:
- Fault tolerance: 1 node can fail without issue.
- Performance: Fewer nodes = faster consensus and lower latency.
- Simplicity: Easier to manage, upgrade, and monitor.
Even the ETCD documentation recommends 3–5 nodes total, with 5 being the upper limit before write performance and operational complexity start to degrade.
Systems like Google's Chubby—which inspired systems like ETCD and ZooKeeper—also recommend no more than 5 nodes.
The Myth of Catastrophic Failure
"If two of our three ETCD nodes go down, the cluster will become unusable and need deep repair!"
This is a common fear, but the reality is less dramatic:
- ETCD becomes read-only: You can't schedule or update workloads, but existing workloads continue to run.
- No deep repair needed: As long as there's no data corruption, restoring quorum just requires bringing at least one other ETCD node back online.
- Still recoverable if two nodes are permanently lost: You can re-initialize the remaining node as a new single-node ETCD cluster using
--cluster-init, and rebuild from there.
What About Backups?
In k3s, ETCD snapshots are automatically saved by default. For example:
- Default path:
/var/lib/rancher/k3s/server/db/snapshots/
You can restore these snapshots in case of failure, making ETCD even more resilient.
When to Consider 5 Nodes
Adding more ETCD nodes only makes sense at scale, such as:
- Running 12+ total cluster nodes
- Needing stronger fault domains for regulatory/compliance reasons
Note: ETCD typically requires low-latency communication between nodes. Distributing ETCD members across availability zones or regions is generally discouraged unless you're using specialized networking and understand the performance implications.
Even then, be cautious—you're trading some simplicity and performance for that extra failure margin.
TL;DR
- 3-node ETCD clusters are the best choice for most Kubernetes/k3s environments.
- 5-node clusters offer more redundancy but come with extra complexity and performance costs.
- Loss of quorum is not a disaster—it’s recoverable.
- Backups and restore paths make even worst-case recovery feasible.
And finally: if you're seeing multiple ETCD nodes go down frequently, the real problem might not be the number of nodes—but your hosting provider.
-
 @ 866e0139:6a9334e5
2025-03-26 06:56:05
@ 866e0139:6a9334e5
2025-03-26 06:56:05Autor: Dr. Ulrike Guérot. (Foto: Manuela Haltiner). Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier.**
Ich bin 60 Jahre. Einer meiner Großväter, Wilhelm Hammelstein, liegt auf dem Soldatenfriedhof in Riga begraben. Der andere, mütterlicherseits, Paul Janus, kam ohne Beine aus dem Krieg zurück, auch aus Russland. Ich kenne ihn nur mit Prothesen und Krücken. Er hat immer bei Wetterwechsel über Phantomschmerz geklagt und ist seines Lebens nicht mehr froh geworden. Den Krieg hat man ihm im Gesicht angesehen, auch wenn ich das als kleines Mädchen nicht verstanden habe.
"Ihr könnt euch nicht vorstellen, was ich gesehen habe"
Von den Russen hat er trotzdem nie schlecht geredet. Was er immer nur zu uns Enkelkindern gesagt war: *„Ihr könnt euch nicht vorstellen, was ich gesehen habe“. * Wir haben es nicht verstanden, als 6- oder 8-Jährige, und haben gelacht. Manchmal haben wir ihm seine Krücken weggenommen, die immer an den Ohrensessel gelehnt waren, dann konnte Opa Paul nicht aufstehen und ist wütend geworden.

Meine Mutter, Helga Hammelstein, ist im Mai 1939 gleichsam in den Krieg hineingeboren worden, in Schlesien. 1945 gab es für sie, wie für viele, Flucht und Vertreibung. Ob sie und ihre zwei Schwestern von den Russen vergewaltigt wurden – wie damals so viele – kann ich nicht sagen. Diese Themen waren bei uns tabuisiert. Was ich sagen kann, ist, dass meine Mutter als Flüchtlings- und Kriegskind vom Krieg hochgradig traumatisiert war – und als Kriegsenkelin war oder bin ich es wohl auch noch. Eigentlich merke ich das erst heute so richtig, wo wieder Krieg auf dem europäischen Kontinent ist und Europa auch in den Krieg ziehen, wo es kriegstüchtig gemacht werden soll.
Vielleicht habe ich mich aufgrund dieser Familiengeschichte immer so für Europa, für die europäische Integration interessiert, für die EU, die einmal als Friedensprojekt geplant war. Ich habe Zeit meines Lebens, seit nunmehr 30 Jahren, in verschiedenen Positionen, als Referentin im Deutschen Bundestag, in Think Tanks oder an Universitäten akademisch, intellektuell, publizistisch und künstlerisch zum Thema Europa gearbeitet.
1989 habe ich einen Franzosen geheiratet, ich hatte mich beim Studium in Paris verliebt und in den 1990-Jahren in Paris zwei Söhne bekommen. Auch in der französischen Familie gab es bittere Kriegserfahrungen: der Mann der Oma meines damaligen Mannes war 6 Jahre in deutscher Kriegsgefangenschaft. „Pourquoi tu dois marier une Allemande?“ „Warum musst du eine Deutsche heiraten?“, wurde mein damaliger Mann noch gefragt. Das Misstrauen mir gegenüber wurde erst ausgeräumt, als wir ihr 1991 den kleinen Felix, unseren erstgeborenen Sohn, in den Schoß gelegt haben.
Das europäische Friedensprojekt ist gescheitert
Das europäische Einheits- und Friedensprojekt war damals, nach dem Mauerfall, in einer unbeschreiblichen Aufbruchstimmung, die sich heute niemand mehr vorstellen kann: Der ganze Kontinent in fröhlicher Stimmung - insieme, gemeinsam, together, ensemble – und wollte politisch zusammenwachsen. Heute ist es gescheitert und ich fasse es nicht! Das Kriegsgeheul in ganz Europa macht mich nachgerade verrückt.
Darum habe ich ein europäisches Friedensprojekt ins Leben gerufen: TheEuropean Peace Project. Am Europatag, den 9. Mai, um 17 Uhr, wollen wir in ganz Europa in allen europäischen und auf dem ganzen europäischen Kontinent als europäische Bürger den Frieden ausrufen! Ich würde mich freuen, wenn viele mitmachen!
DIE FRIEDENSTAUBE JETZT ABONNIEREN:
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel in Ihr Postfach, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht).
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):
Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: milosz@pareto.space oder kontakt@idw-europe.org.
Wo bleibt ein deutsch-russisches Jugendwerk?
Mein Lieblingsbuch zu Europa ist Laurent Gaudet, Nous, L’Europe, banquet des peuples. „Wir, Europa! Ein Banquet der Völker“ Es ist ein großartiges Gedicht, etwa wie die Ilias von Homer. Es beschreibt die letzten einhundert Jahre europäische Geschichte, die ganzen Krieg und Revolutionen. Und es beschreibt doch, was uns als Europäer eint. Darin findet sich der – für mich wunderschöne! - Satz: „Ce que nous partageons, c’est ce que nous étions tous bourraux et victime.“ „Was wir als Europäer teilen ist, dass wir alle zugleich Opfer und Täter waren“.
Und doch haben wir es geschafft, die „Erbfeindschaft“ zu beenden und uns auszusöhnen, zum Beispiel die Deutschen und Franzosen, über ein deutsch-französisches Jugendwerk, das 1963 gegründet wurde. So ein Jugendwerk wünsche ich mir auch heute zwischen Europa und Russland!
Das Epos von Laurent Gaudet ist in einem Theaterstück von dem französischen Regisseur Roland Auzet auf die Bühne gebracht worden. In dem 40-köpfigen Ensemble sind verschiedene Nationalitäten aus ganz Europa: das Stück ist fantastisch! Ich selber habe es auf dem Theaterfestival in Avignon 2019 sehen dürfen!
Ich wünsche mir, dass wir statt jetzt für Milliarden überall in Europa Waffen zu kaufen, das Geld dafür auftreiben, dieses Theaterstück in jede europäische Stadt zu bringen: wenn das gelänge, hätten wohl alle verstanden, was es heißt, Europäer zu sein: nämlich Frieden zu machen!
Ulrike Guérot, Jg. 1964, ist europäische Professorin, Publizistin und Bestsellerautorin. Seit rund 30 Jahren beschäftigt sie sich in europäischen Think Tanks und Universitäten in Paris, Brüssel, London, Washington, New York, Wien und Berlin mit Fragen der europäischen Demokratie, sowie mit der Rolle Europas in der Welt. Ulrike Guérot ist seit März 2014 Gründerin und Direktorin des European Democracy Labs, e.V.,Berlin und initiierte im März 2023 das European Citizens Radio, das auf Spotify zu finden ist. Zuletzt erschien von ihr "Über Halford J. Mackinders Heartland-Theorie, Der geografische Drehpunkt der Geschichte", Westend, 2024). Mehr Infos zur Autorin hier.
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ bbb5dda0:f09e2747
2025-03-18 20:11:54
@ bbb5dda0:f09e2747
2025-03-18 20:11:54Time isn't constant, or at least my perception of it isn't. The past two weeks have been like 2 months for me! In a good way... I'm playing catch-up with my updates so this one will only focus on week 10 because so much happened!
I'm lucky enough to be joining #SovEng for the second time, where a bunch of Nostr geeks get together and all work on our part to fix the internet, join in deliberation, hike, demo, and repeat...
GitHub actions in GitWorkshop
I hit off the first week by working with nostr:npub15qydau2hjma6ngxkl2cyar74wzyjshvl65za5k5rl69264ar2exs5cyejr to see what the Git Actions workflow looks like in a decentralized world. Because now anyone can be an operator, the flow will be different than on legacy git collaboration tools. We hashed out an early version of a user interface. You can check it out at vnext.gitworkshop.dev. Go to profile icon > settings > experimental mode (on).
The issues we face
We're having some debates wether or not the workflow runners fit within the DVM spec. The main difference between this and all DVM implementations that i'm aware of. Is that most DVM are quite cookie-cutter input, processing, then answer within a few seconds.
Costs not known up front
The workflow runners are long-running jobs, they can run for hours potentially, AND it's impossible to know how long a job is going to take beforehand, meaning there can be no set price per invocation. So we send a pre-payment for the maximum runtime (
price/sec*timeoutSec) and expect the runner to return the change when the job is done, so we need to account for that.Handling cancellations
Also when a job is cancelled, which in the DVM spec is done by a delete request, which forms a problem because we want to keep a history of our runs, even if they're cancelled.
DVM partial results
We currently use partial results to 'stream' back logs from the job. However the log output of jobs can be massive and we might not want to keep them around for long, Ephemeral would might be better suited for that and the final log output could be saved on blossom to be included in the final status.
Queueing runs
The DVM spec does not specify any queuing messaging/statuses. Workflows can rely heavily on the type of machine they run on. Architecture, OS, memory or vCPU's. That means you might want to schedule jobs even though all potential runners are currently busy. Therefore a queueing system makes a lot of sense. We might be able to squeeze such a system into our implementation of the DVM spec. But it's just one of the things that makes us wonder if we're not drifting too far from the spec to still call it a DVM.
Some screenshots of our implementation: https://vnext.gitworkshop.dev/arjen@swissdash.site/dvm-cicd-runner
|
 | |
| ----------------------------------------------------------------------------------------------------- | --- |
|
| |
| ----------------------------------------------------------------------------------------------------- | --- |
|  | |
| | |
| |
| | |
Infernal Insights
 Aaah... Logging and metrics, our favourite hard-to-manage infrastructure thing we don't really want to do but kind of need to make a good product.
Aaah... Logging and metrics, our favourite hard-to-manage infrastructure thing we don't really want to do but kind of need to make a good product.Coming from the DevOps world, these systems usually can be incredibly valuable, but can be a pain to set up and/or maintain.
I ended up on a fun proof-of-concept together with nostr:npub1ye5ptcxfyyxl5vjvdjar2ua3f0hynkjzpx552mu5snj3qmx5pzjscpknpr and nostr:npub15qydau2hjma6ngxkl2cyar74wzyjshvl65za5k5rl69264ar2exs5cyejr we made this dead simple nostr message:
json { "kind": 1314, "expires": "tags": [ ["expiration", nostrNow() + oneMonth], ["n" "tollgate-site"] // Application Namespace ["p, "1096f6b...a74c7ecc"] // pubkey of person behind current deployment ], "content": "The button on the top-right disappears when i hover on it." }It basically tags the developer of the application/site and a namespace (aka: the name of the software). @hzrd created this simple button to add to a website header that creates the ability to send these events.The
ntag is there to give the name of the software, that way different people (npubs) can gather feedback on seperate deployments, and the developer of said software could also utilize this data for its own purposes by filtering on thentag. Whereas a developer is probably only interested in their own deploymentThe events are ONLY meant as raw data, like human written feedback, maybe crash logs. It can be anything and they're not meant to be kept around for long, it should be ingested by a pipeline, which can then run one or more rounds of filtering, tagging, categorizing. Each resulting in a new refined event, ingestable by the next.
However for this experiment we stuck with ingesting it, and do just one step of refinement and send it off to a logging-aggregation system, in this case Grafana Loki. We basically sent the logs straight over there, but we also added a fun extra feature, sentiment analysis!
We sent the contents of the logs over to ppq.ai and let it give us a sentiment score from 1 to 10. So we can get a sense of how positive/negative the feedback is. This same principle can be applied in so many ways. Think of categorizing by LLM. You can group feedback based on if it's about the UI for example. It'd be easy to group them and create a Nostr git issue out of those.
Find my software for the dat ingestion here.
-
 @ 30fb9c78:1f1e3c3a
2025-03-23 22:47:02
@ 30fb9c78:1f1e3c3a
2025-03-23 22:47:02The President delivers a ‘State of the Union’ Speech every year, but that’s a snooze. Just look at your worthy representatives struggling to keep their eyes open. That’s because they’ve heard it all before.
We have too. Not much changes in politics. Certainly not the candidates.
There’s more variety at my local gas station, where at least I get to choose from three types of fuel and five flavors of Big Gulp.
So forget about politics. All the action now is happening in mainstream culture—which is changing at warp speed.
That’s why we need a “State of the Culture” speech instead. My address last year was quoted and cited, and was absolutely true back then—but it’s already as obsolete as the ChatGPT-1 help desk at the Bored Ape Yacht Club.
In fact, 2024 may be the most fast-paced—and dangerous—time ever for the creative economy. And that will be true, no matter what happens in November.
So let’s plunge in.
I want to tell you why entertainment is dead. And what’s coming to take its place.
If the culture was like politics, you would get just two choices. They might look like this.
Many creative people think these are the only options—both for them and their audience. Either they give the audience what it wants (the entertainer’s job) or else they put demands on the public (that’s where art begins).
But they’re dead wrong.
Maybe it’s smarter to view the creative economy like a food chain. If you’re an artist—or are striving to become one—your reality often feels like this.

Until recently, the entertainment industry has been on a growth tear—so much so, that anything artsy or indie or alternative got squeezed as collateral damage.
But even this disturbing picture isn’t disturbing enough. That’s because it misses the single biggest change happening right now.
We’re witnessing the birth of a post-entertainment culture. And it won’t help the arts. In fact, it won’t help society at all.
Even that big whale is in trouble. Entertainment companies are struggling in ways nobody anticipated just a few years ago.
Consider the movie business:
- Disney is a state of crisis—where everything is shrinking (except the CEO’s paycheck).
- Paramount just laid off 800 employees - and wants to find a new owner.
- Universal is now releasing movies to streaming after just 3 weeks in theaters.
- Warner Bros actually makes more money canceling films than releasing them.
The TV business also hit a wall in 2023. After years of steady growth, the number of scripted series has started shrinking.
Estimated number of U.S scripted originial series per year, 2010-2023 Source
Music may be in the worst state of them all. Just consider Sony’s huge move a few days ago - investing in Michael Jackson’s song catalog at a valuation of $1.2 billion. No label would invest even a fraction of that amount in launching new artists.
In 2024, musicians are actually worth more old than young, dead than alive.
This raises the obvious question. How can demand for new entertainment shrink? What can possibly replace it?
But something will replace it. It’s already starting to happen.
Here’s a better model of the cultural food chain in the year 2024.
The fastest growing sector of the culture economy is distraction. Or call it scrolling or swiping or wasting time or whatever you want. But it’s not art or entertainment, just ceaseless activity.
The key is that each stimulus only lasts a few seconds, and must be repeated.
It’s a huge business, and will soon be larger than arts and entertainment combined. Everything is getting turned into TikTok - an aptly named platform for a business based on stimuli that must be repeated after only a few ticks of the clock.
TikTok made a fortune with fast-paced scrolling video. And now Facebook—once a place to connect with family and friends - is imitating it. So long, Granny, hello Reels. Twitter has done the same. And, of course, Instagram, YouTube, and everybody else trying to get rich on social media.
This is more than just the hot trend of 2024. It can last forever—because it’s based on body chemistry, not fashion or aesthetics.
Our brain rewards these brief bursts of distraction. The neurochemical dopamine is released, and this makes us feel good—so we want to repeat the stimulus.
The cycle looks like this.
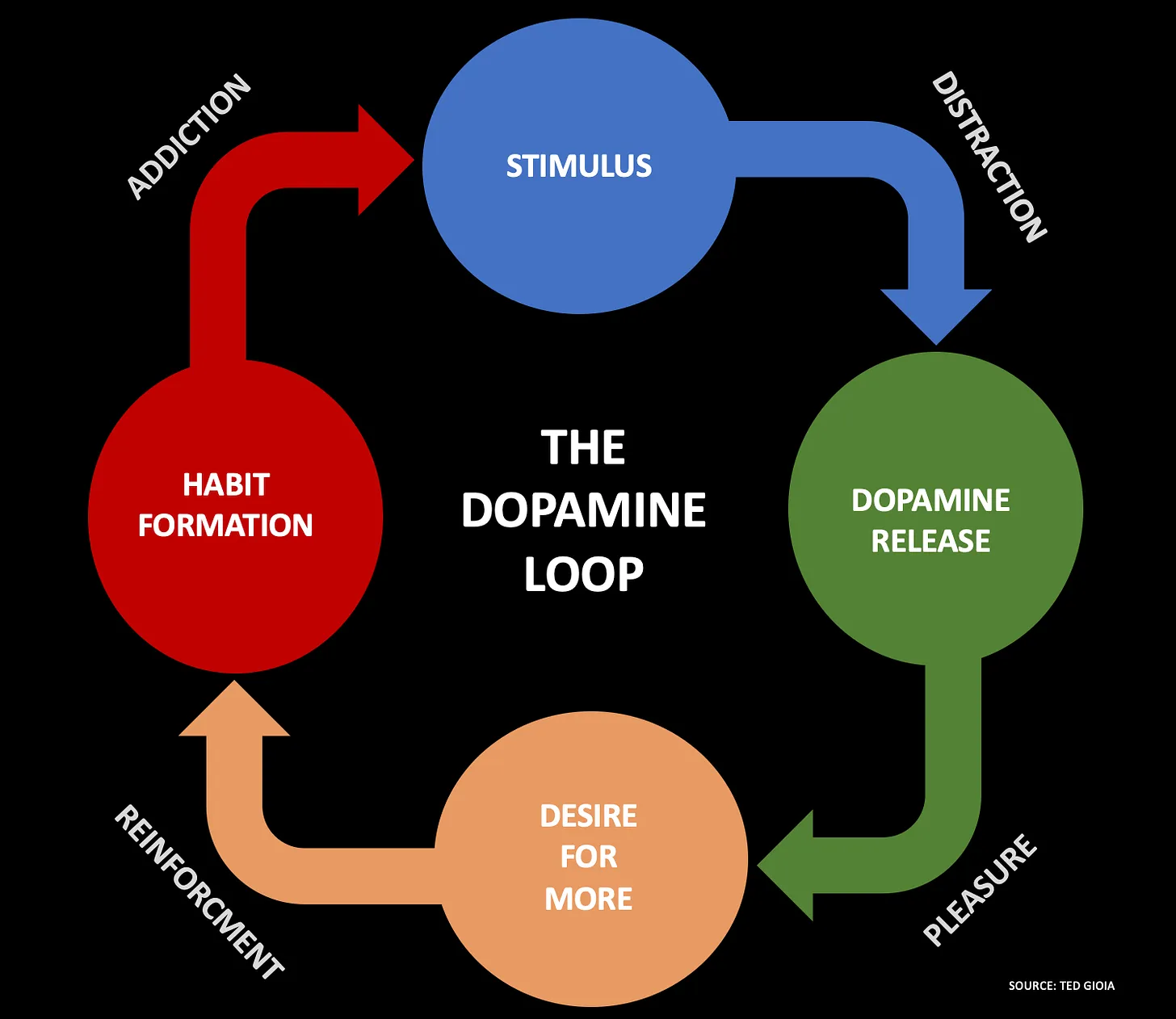 This is a familiar model for addiction.
This is a familiar model for addiction.Only now it is getting applied to culture and the creative world—and billions of people. They are unwitting volunteers in the largest social engineering experiment in human history.
So you need to ditch that simple model of art versus entertainment. And even ‘distraction’ is just a stepping stone toward the real goal nowadays—which is addiction.
Here’s the future cultural food chain—pursued aggressively by tech platforms that now dominate every aspect of our lives.
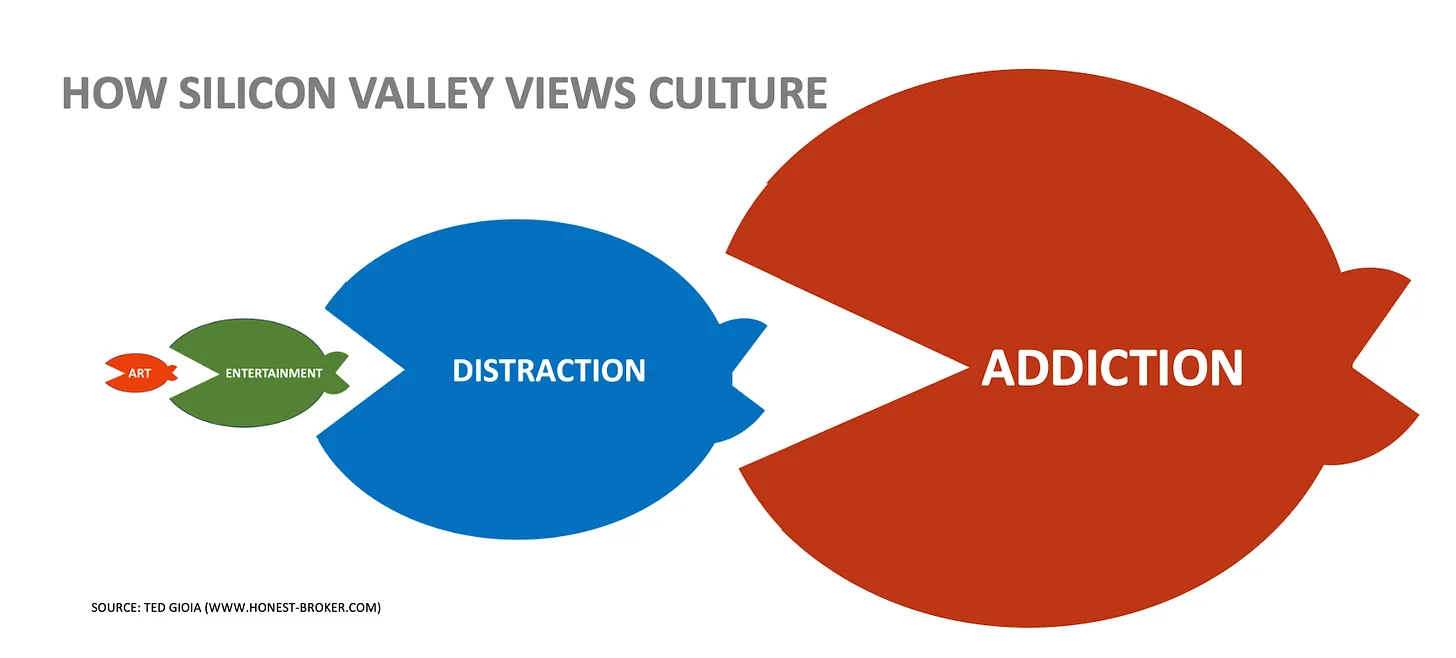
The tech platforms aren’t like the Medici in Florence, or those other rich patrons of the arts. They don’t want to find the next Michelangelo or Mozart. They want to create a world of junkies—because they will be the dealers.
Addiction is the goal.
They don’t say it openly, but they don’t need to. Just look at what they do.
Everything is designed to lock users into an addictive cycle
- The platforms are all shifting to scrolling and reeling interfaces where stimuli optimize the dopamine doom loop.
- Anything that might persuade you to leave the platform—a news story, or any outside link—is brutally punished by their algorithms. It might liberate you from your dependent junkie status, and that can’t be allowed.
- But wait, there’s more! Apple, Facebook, and others are now telling you to put on their virtual reality headsets—where you are swallowed up by the stimuli, like those tiny fish in my food chain charts. You’re invited to live as a passive recipient of make-believe experiences, like a pod slave in The Matrix.

The tech CEOs know this is harmful, but they do it anyway. A whistleblower released internal documents showing how Instagram use leads to depression, anxiety, and suicidal thoughts. Mark Zuckerberg was told all the disturbing details.
He doesn’t care. The CEOs all know the score. The more their tech gets used, the worse all the psychic metrics get.
But still they push aggressively forward—they don’t want to lose market share to the other dopamine cartel members. And with a special focus on children. They figured out what every junk peddler already knows: It’s more profitable to get users locked in while they’re young.
And the virtual reality headsets raise even more issues—because they rewire users’ brains. Experts are already talking about “simulator sickness,” and that’s just the physical nausea, dizziness, and headaches. Imagine the psychic dislocations.
And you thought artists had it tough back in the day?
Even the dumbest entertainment looks like Shakespeare compared to dopamine culture. You don’t need Hamlet, a photo of a hamburger will suffice. Or a video of somebody twerking, or a pet looking goofy.
Instead of movies, users get served up an endless sequence of 15-second videos. Instead of symphonies, listeners hear bite-sized melodies, usually accompanied by one of these tiny videos—just enough for a dopamine hit, and no more.
This is the new culture. And its most striking feature is the absence of Culture (with a capital C) or even mindless entertainment—both get replaced by compulsive activity.
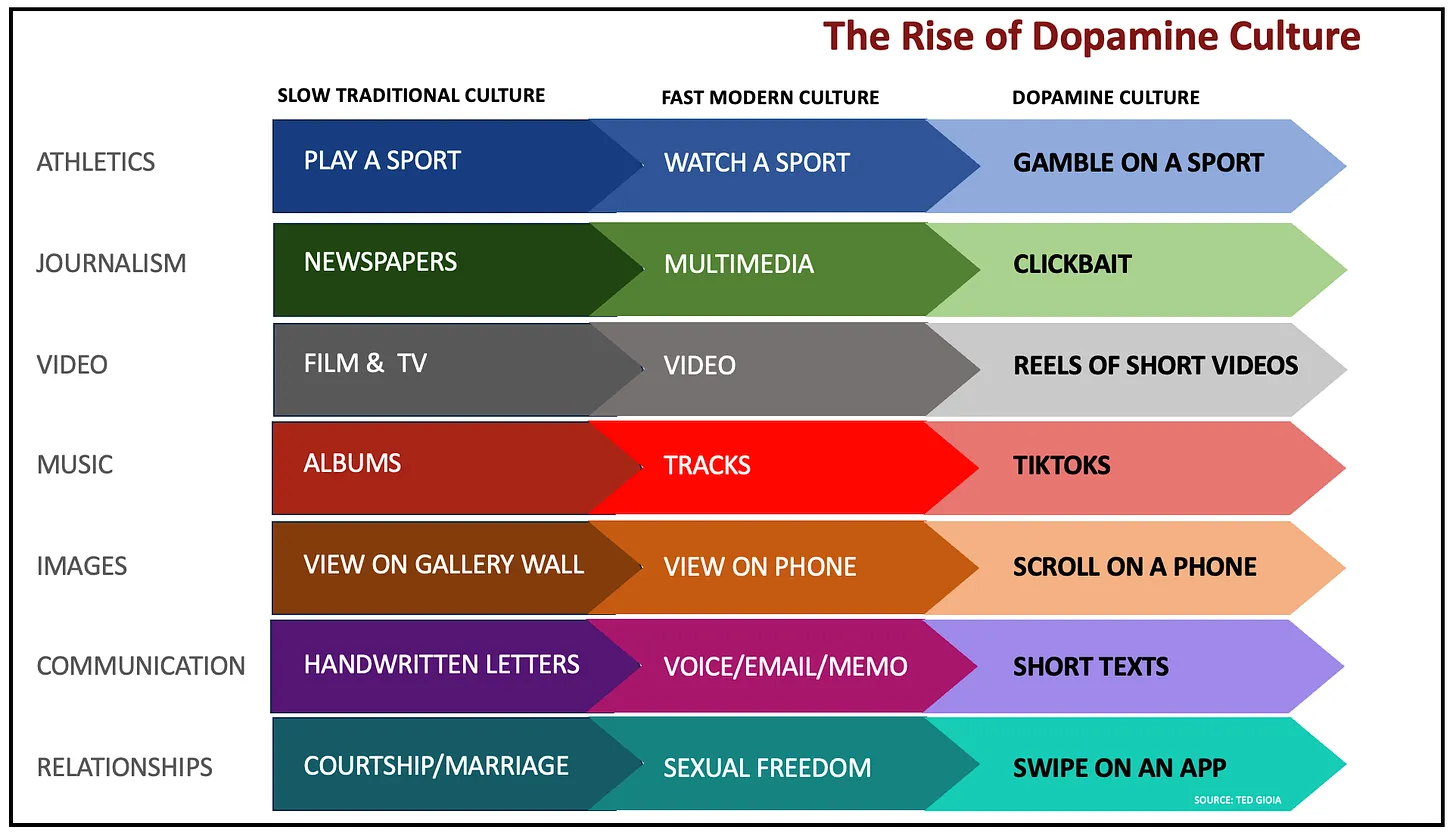
So don’t be surprised when huge corporations stop pretending otherwise—hence entertainment businesses that suddenly embrace gambling, or other equally addictive offerings. (Now you know why the Super Bowl took place in Las Vegas—a perfect symbol for the current moment in our culture.)
Everything is gamified. Anything can be scrollable. You can simulate any boat you row.
But what does this do to our brains? To our lives? To the future?
Here’s where the science gets really ugly. The more addicts rely on these stimuli, the less pleasure they receive. At a certain point, this cycle creates anhedonia—the complete absence of enjoyment in an experience supposedly pursued for pleasure.
That seems like a paradox
How can pursuing pleasure lead to less pleasure? But that’s how our brains are wired (perhaps as a protective mechanism). At a certain point, addicts still pursue the stimulus, but more to avoid the pain of dopamine deprivation.
People addicted to painkillers have the same experience. Beyond a certain level, opioid dependence actually makes the pain worse.
What happens when this same experience is delivered to everybody, via their phones? The results are devastating, as expert Dr. Len Lantz explains. Even people who thought they were immune to addictive behavior, get destroyed by the cycle:
There is a specific, abnormal brain activation pattern that is present in people who have anhedonia, which is a key feature of major depression, and absent in those who do not. It is often the case that when patients come to me with major depression, they say, “I shouldn’t be depressed. I have a good life. If my friends or coworkers knew I was depressed, they wouldn’t understand or they would be mad at me. They think I have it made. So, why don’t I feel that way?”
We’re now seeing the first effects on a grand social scale of this deadening effect.
Sure, let’s give it a name, something like TikTok depression or Silicon Valley zombification or whatever. The key fact is that users can feel it, even if they don’t have a label or a diagnosis. They feel it even if the technocrats refuse to tell them about it. Just listen to the words people use to describe their toxic online interactions: doomscrolling, trolling, doxxing, gaslighting, etc.
In the year 2024, this is what we do for fun.
But it doesn’t bring happiness. The World Happiness Report surveyed 150,000 people in 26 countries, and found that the US and other prosperous, technologically advanced societies are suffering a massive happiness decline. This is what happens when anhedonia is on sale every week—and the pervasive tech platforms increasingly resemble the ruthless corporations that got rich from opioid abuse.
Some companies get people hooked with pills and needles. Others with apps and algorithms. But either way, it’s just churning out junkies.
That’s our dystopian future. Not so much Orwell’s 1984—more like Huxley’s Brave New World.
Dr. Anna Lembke, author of Dopamine Nation, sometimes urges her patients to undergo a “dopamine fast” for one month—a sufficient amount of time for the brain to start rewiring. But even unplugging for a few minutes can be scary for those caught in the cycle.
She shares an example:
My patient Sophie, a Stanford undergraduate from South Korea, came in seeking help for depression and anxiety. Among the many things we talked about, she told me she spends most of her waking hours plugged into some kind of device: Instagramming, YouTubing, listening to podcasts and playlists. In session with her I suggested she try walking to class without listening to anything and just letting her own thoughts bubble to the surface. She looked at me both incredulous and afraid. “Why would I do that?” she asked, openmouthed.
A week later, Sophie returned and reported on the new experience: “It was hard at first. But then I got used to it and even kind of liked it. I started noticing the trees.”
 Want a horror story? Read this book—it’s got more zombies than The Walking Dead
Want a horror story? Read this book—it’s got more zombies than The Walking DeadNot long ago, I’d have dismissed anecdotes like this. I couldn’t really imagine somebody addicted to Instagram or TikTok or some other phone app.
But I don’t need to imagine anything now. I see those sad-eyed junkies, hooked to their devices, wherever I go. And even their facial expressions convey that haggard strungout look.
This is the real state of play in our culture in 2024.
And it’s a bigger issue than just struggling artists or floundering media companies. The dopamine cartel is now aggravating our worst social problems—in education, in workplaces, and in private life.
But you will hardly hear about this—because too many people are making far too much money from the dopamine culture.
If you thought the drug cartels were rich, wait till you see how much money the dopamine cartel is making. For a start, check out the market cap at Apple, Meta, etc. They are literally too big to stop.
Just telling the truth about the dopamine cartel would be a major step forward for the culture in 2024.
Also, do yourself a favor. Unplug yourself from time to time, and start noticing the trees or your goofy pets. They actually look better in real life than in the headset.
Source: Ted Gioia, The Honest Broker, February 18, 2024
-
 @ 20e17dd0:2ae504d7
2025-03-18 19:46:48
@ 20e17dd0:2ae504d7
2025-03-18 19:46:48Installing Docker is monumental for your Home Lab. This quick article will give you all the steps required to do the installation and to test your installation as well.
Prerequisite
Installation
Open a Terminal session and write the following command:
ruby sudo apt install docker.ioYou will be ask permission to install and continueruby yValidation of the installation
To validate the installer, prompt the following command:
ruby docker --versionYou should get:
ruby Docker version 26.1.3, build 26.1.3-0ubuntu1~24.04.1To test if it is running, prompt the following command:
ruby sudo systemctl status dockerYou should get a screen with the docker.service as "running". To get back to command line do CTRL+C
Test Installation
To make sure that everything runs smoothly, write the following command:
ruby sudo docker run hello-worldYou should get a Hello from Docker.You are ready to enjoy pulling docker images!
originally posted at https://stacker.news/items/917064
-
 @ dd664d5e:5633d319
2025-03-21 12:22:36
@ dd664d5e:5633d319
2025-03-21 12:22:36Men tend to find women attractive, that remind them of the average women they already know, but with more-averaged features. The mid of mids is kween.👸
But, in contradiction to that, they won't consider her highly attractive, unless she has some spectacular, unusual feature. They'll sacrifice some averageness to acquire that novelty. This is why wealthy men (who tend to be highly intelligent -- and therefore particularly inclined to crave novelty because they are easily bored) -- are more likely to have striking-looking wives and girlfriends, rather than conventionally-attractive ones. They are also more-likely to cross ethnic and racial lines, when dating.
Men also seem to each be particularly attracted to specific facial expressions or mimics, which might be an intelligence-similarity test, as persons with higher intelligence tend to have a more-expressive mimic. So, people with similar expressions tend to be on the same wavelength. Facial expessions also give men some sense of perception into womens' inner life, which they otherwise find inscrutable.
Hair color is a big deal (logic says: always go blonde), as is breast-size (bigger is better), and WHR (smaller is better).

-
 @ 878dff7c:037d18bc
2025-03-21 04:39:42
@ 878dff7c:037d18bc
2025-03-21 04:39:42Smooth, rich, and deeply comforting, this savory porridge is enhanced by fermentation, warming spices, and a creamy finish — easy on digestion, full of flavor, and great for meal prep.
Ingredients (Serves 2–3):
- 200g (1 cup) lactofermented brown rice (see rice fermentation recipe in comments)
- 375–500ml (1.5-2 cups) broth or water (I use evaporation method, but cook rice however you normally do, it's not important) (chicken, vegetable, or bone broth for extra richness)
- 250ml (1 cup) milk (whole milk for creaminess)
- 5g (1 tsp) salt (adjust to taste)
- 15g (1 tbsp) butter or coconut oil (for extra silkiness)
- 15g (1 tbsp) fresh ginger, sliced or minced from a jar is fine (optional, for warmth)
- 5g (1 clove or 1 tsp) garlic, minced (optional. I normally skip this...)
- 2g (½ tsp) ground turmeric (for color and anti-inflammatory benefit)
- 1g (¼ tsp) white or black pepper (black pepper enhances turmeric absorption)
Optional Savory Toppings:
- 1 soft-boiled or poached egg
- 100g (¾ cup) shredded chicken, pork, or tofu
- 30g (¼ cup) grated cheese (Parmesan, aged cheddar, or nutritional yeast for vegan)
- 20g (2 tbsp) chopped scallions or chives
- 30g (2 tbsp) fermented vegetables, such as:
- Kimchi
- Pickled mustard greens
- Sauerkraut
- Lactofermented carrots
- 10g (1 tbsp) toasted sesame seeds or crushed peanuts
- 5ml (1 tsp) soy sauce, tamari, or fish sauce
- 15–30g (1–2 tbsp) full-fat Greek yogurt or kefir (optional probiotic boost – stir in when warm, not hot)
Instructions:
1. Cook the Fermented Rice Base
- In a pot, combine fermented brown rice with broth or water.
- Bring to a boil, then reduce to a gentle simmer.
- Add ginger, garlic, and turmeric.
- Cook uncovered for 90–120 minutes, stirring occasionally, until the rice breaks down into a creamy porridge.
2. Make It Creamy
- Stir in milk and butter or coconut oil.
- Simmer for another 10–15 minutes, stirring to prevent sticking.
- Season with salt and pepper.
3. Adjust Consistency
- Too thick? Add more broth or milk.
- Too thin? Simmer longer.
4. Cool Slightly & Add Yogurt or Kefir (Optional)
- Let porridge cool to a warm (not hot) temperature — about 50°C (122°F) or warm to the touch.
- Stir in Greek yogurt or kefir gently to preserve live cultures.
5. Serve with Toppings
Top each bowl with your choice of:
- Egg
- Shredded protein
- Cheese
- Soy sauce or tamari
- Scallions, sesame seeds, chili flakes
- Your favorite fermented veggies, like sauerkraut or lactofermented carrots
Make-Ahead & Freezing Tip:
You can ferment and cook a large batch of brown rice, then portion it into freezer-safe containers (about 200g per portion) for quick use. Thaw overnight in the fridge or gently warm from frozen before making your congee — a huge time-saver for busy days!
-
 @ bd32f268:22b33966
2025-03-18 18:59:23
@ bd32f268:22b33966
2025-03-18 18:59:23O que torna um homem um modelo a ser seguido ? Que qualidades pode apresentar um homem que demonstram as suas aspirações ?
Nos dias que correm a nobreza de carácter não parece ser o factor chave nas figuras que são mais celebradas pelo mundo inteiro. A nossa sociedade dá mais atenção ao indigente moral célebre pelas sacadas narcísicas do que ao guerreiro, ao santo, ao patriarca que dedicaram a sua vida a um propósito e aspirações manifestamente superiores.
É frequente vermos ser objeto de atenção o homem vaidoso, efeminado, narcísico e corrupto até. O facto de serem estas as referências que temos na cultura moderna diz muito da sociedade em que vivemos. É importante notar que nós somos como espelhos que refletem aquilo que reverenciamos, isto é, vamo-nos tornando mais parecidos com o objeto da nossa admiração. É nosso instinto tentar imitar aquilo que admiramos, portanto isto é um grave problema quando admiramos as coisas erradas.
Pode parecer contraintuitivo mas por vezes as coisas mais admiráveis na vida são na verdade as mais simples. Prestemos atenção ao que nos diz o auto G.K Chesterton a este propósito.

Há algo de magnificamente sóbrio no pai de família que não procura atenção e se dedica exclusivamente ao seu dever. Esta figura é, por hora, demonizada tantas e tantas vezes, sendo frequentemente apresentado como sendo o mandatário de uma cultura misógina e machista.
Estou convencido que enquanto a figura de pai de família não for devidamente reabilitada, dificilmente teremos um ressurgimento de famílias propriamente ordenadas. É importante notar aqui um ponto, este pai de família deve ser alguém capaz de colocar os interesses da família primeiro que os seus interesses individuais. Deve ser alguém que não viva no relativismo moral, mas sim um homem de fé, algo que está em vias de extinção no ocidente e em particular em Portugal. Este homem deve ser o porto de abrigo para a sua família, alguém disposto a travar o bom combate, e será sempre portanto um defensor acérrimo da verdade. Não será naturalmente alguém obcecado com a sua própria imagem, mas sim um homem desejavelmente forte quer em termos físicos, tendo zelo na forma como se exercita, quer em termos mentais, sendo uma pessoa capaz mas com autocontrolo. Deve também ser um homem com uma vida intelectual, isto é, alguém que nutre interesse pelo legado que lhe foi confiado e procura aprender sobre o mesmo. Muitos homens antes de si fizeram sacrifícios para que o homem da atualidade usufrua dos mais variados benefícios.
A atualidade oferece-nos por vezes a promoção de algumas destas facetas, algo que seria desejável e bom, contudo com algumas distorções. Há homens fortes, capazes de feitos atléticos ímpares, que se cultivam nesse domínio mas pelas razões erradas. Por vezes o imperativo moral que os guia é a vaidade, sendo que esse trabalho físico que fazem conspira para consolidar o seu narcisismo.
Outros há com uma determinação inabalável, algo louvável quando usada para os fins próprios. Esta determinação não deve ser usada para a procura de grandes riquezas como um fim em si mesmas, nem como um isco usado para o oportunismo sexual com as mulheres.
Poderíamos também dar como exemplo, homens com uma prodigiosa inteligência mas que, não a tendo devidamente orientada, a usam para manipular e corromper o discurso público não olhando a meios para atingir os fins.
Um factor chave que dificulta a formação de mais homens com este tipo de espinha dorsal é uma certa apropriação da linguagem que tem existido no discurso público que procura rotular quem ousa desafiar este status quo. Termos como “negacionista”, “radical”, “fascista”, “fundamentalista”, “ultranacionalista” entre outros, são constantemente atirados remetendo o homem para uma falsa conclusão:
“ Tu não podes defender nada, nem ter certeza de nada”.
Outra ferramenta importante nesta desconstrução é o apelo ao vício. Sendo através da pornografia, da comida ultra-processada ou de uma vida de conforto , há claramente um incentivo ao hedonismo e à autoindulgência. Procura-se alimentar cada vez mais esta busca do prazer com o fim último, e por conseguinte a coragem, o sacrifício e o trabalho, como pedras angulares da construção do carácter do homem ficam para segundo plano.
O cavalheirismo ficou-se apenas pelas aparências. Por vezes, há um verniz de algumas das propriedades que descrevi em várias situações, contudo não passa de uma máscara. É fácil segurar uma porta para uma senhora e dizer “com licença”, “por favor”, para se mostrar alguém educado quando o custo para o fazer é mínimo. Difícil é estar disposto a fazer sacríficos em que nos doamos inteiramente pelos outros, no entanto é isso que é pedido ao homem. Doando-se encontrará o seu verdadeiro propósito.
-
 @ 000002de:c05780a7
2025-03-18 17:30:47
@ 000002de:c05780a7
2025-03-18 17:30:47Was watching this old clip of the great Thomas Sowell discuss Obama's broad decrees and promises when he uttered this gold quip.
originally posted at https://stacker.news/items/916888
-
 @ a39d19ec:3d88f61e
2025-03-18 17:16:50
@ a39d19ec:3d88f61e
2025-03-18 17:16:50Nun da das deutsche Bundesregime den Ruin Deutschlands beschlossen hat, der sehr wahrscheinlich mit dem Werkzeug des Geld druckens "finanziert" wird, kamen mir so viele Gedanken zur Geldmengenausweitung, dass ich diese für einmal niedergeschrieben habe.
Die Ausweitung der Geldmenge führt aus klassischer wirtschaftlicher Sicht immer zu Preissteigerungen, weil mehr Geld im Umlauf auf eine begrenzte Menge an Gütern trifft. Dies lässt sich in mehreren Schritten analysieren:
1. Quantitätstheorie des Geldes
Die klassische Gleichung der Quantitätstheorie des Geldes lautet:
M • V = P • Y
wobei:
- M die Geldmenge ist,
- V die Umlaufgeschwindigkeit des Geldes,
- P das Preisniveau,
- Y die reale Wirtschaftsleistung (BIP).Wenn M steigt und V sowie Y konstant bleiben, muss P steigen – also Inflation entstehen.
2. Gütermenge bleibt begrenzt
Die Menge an real produzierten Gütern und Dienstleistungen wächst meist nur langsam im Vergleich zur Ausweitung der Geldmenge. Wenn die Geldmenge schneller steigt als die Produktionsgütermenge, führt dies dazu, dass mehr Geld für die gleiche Menge an Waren zur Verfügung steht – die Preise steigen.
3. Erwartungseffekte und Spekulation
Wenn Unternehmen und Haushalte erwarten, dass mehr Geld im Umlauf ist, da eine zentrale Planung es so wollte, können sie steigende Preise antizipieren. Unternehmen erhöhen ihre Preise vorab, und Arbeitnehmer fordern höhere Löhne. Dies kann eine sich selbst verstärkende Spirale auslösen.
4. Internationale Perspektive
Eine erhöhte Geldmenge kann die Währung abwerten, wenn andere Länder ihre Geldpolitik stabil halten. Eine schwächere Währung macht Importe teurer, was wiederum Preissteigerungen antreibt.
5. Kritik an der reinen Geldmengen-Theorie
Der Vollständigkeit halber muss erwähnt werden, dass die meisten modernen Ökonomen im Staatsauftrag argumentieren, dass Inflation nicht nur von der Geldmenge abhängt, sondern auch von der Nachfrage nach Geld (z. B. in einer Wirtschaftskrise). Dennoch zeigt die historische Erfahrung, dass eine unkontrollierte Geldmengenausweitung langfristig immer zu Preissteigerungen führt, wie etwa in der Hyperinflation der Weimarer Republik oder in Simbabwe.
-
 @ 16f1a010:31b1074b
2025-03-20 14:32:25
@ 16f1a010:31b1074b
2025-03-20 14:32:25grain is a nostr relay built using Go, currently utilizing MongoDB as its database. Binaries are provided for AMD64 Windows and Linux. grain is Go Relay Architecture for Implementing Nostr
Introduction
grain is a nostr relay built using Go, currently utilizing MongoDB as its database. Binaries are provided for AMD64 Windows and Linux. grain is Go Relay Architecture for Implementing Nostr
Prerequisites
- Grain requires a running MongoDB instance. Please refer to this separate guide for instructions on setting up MongoDB: nostr:naddr1qvzqqqr4gupzq9h35qgq6n8ll0xyyv8gurjzjrx9sjwp4hry6ejnlks8cqcmzp6tqqxnzde5xg6rwwp5xsuryd3knfdr7g
Download Grain
Download the latest release for your system from the GitHub releases page
amd64 binaries provided for Windows and Linux, if you have a different CPU architecture, you can download and install go to build grain from source
Installation and Execution
- Create a new folder on your system where you want to run Grain.
- The downloaded binary comes bundled with a ZIP file containing a folder named "app," which holds the frontend HTML files. Unzip the "app" folder into the same directory as the Grain executable.
Run Grain
- Open your terminal or command prompt and navigate to the Grain directory.
- Execute the Grain binary.
on linux you will first have to make the program executable
chmod +x grain_linux_amd64Then you can run the program
./grain_linux_amd64(alternatively on windows, you can just double click the grain_windows_amd64.exe to start the relay)
You should see a terminal window displaying the port on which your relay and frontend are running.
If you get
Failed to copy app/static/examples/config.example.yml to config.yml: open app/static/examples/config.example.yml: no such file or directory
Then you probably forgot to put the app folder in the same directory as your executable or you did not unzip the folder.
Congrats! You're running grain 🌾!
You may want to change your NIP11 relay information document (relay_metadata.json) This informs clients of the capabilities, administrative contacts, and various server attributes. It's located in the same directory as your executable.
Configuration Files
Once Grain has been executed for the first time, it will generate the default configuration files inside the directory where the executable is located. These files are:
bash config.yml whitelist.yml blacklist.ymlPrerequisites: - Grain requires a running MongoDB instance. Please refer to this separate guide for instructions on setting up MongoDB: [Link to MongoDB setup guide].
Download Grain:
Download the latest release for your system from the GitHub releases page
amd64 binaries provided for Windows and Linux, if you have a different CPU architecture, you can download and install go to build grain from source
Installation and Execution:
- Create a new folder on your system where you want to run Grain.
- The downloaded binary comes bundled with a ZIP file containing a folder named "app," which holds the frontend HTML files. Unzip the "app" folder into the same directory as the Grain executable.
Run Grain:
- Open your terminal or command prompt and navigate to the Grain directory.
- Execute the Grain binary.
on linux you will first have to make the program executable
chmod +x grain_linux_amd64Then you can run the program
./grain_linux_amd64(alternatively on windows, you can just double click the grain_windows_amd64.exe to start the relay)
You should see a terminal window displaying the port on which your relay and frontend are running.
If you get
Failed to copy app/static/examples/config.example.yml to config.yml: open app/static/examples/config.example.yml: no such file or directory
Then you probably forgot to put the app folder in the same directory as your executable or you did not unzip the folder.
Congrats! You're running grain 🌾!
You may want to change your NIP11 relay information document (relay_metadata.json) This informs clients of the capabilities, administrative contacts, and various server attributes. It's located in the same directory as your executable.
Configuration Files:
Once Grain has been executed for the first time, it will generate the default configuration files inside the directory where the executable is located. These files are:
bash config.yml whitelist.yml blacklist.ymlConfiguration Documentation
You can always find the latest example configs on my site or in the github repo here: config.yml
Config.yml
This
config.ymlfile is where you customize how your Grain relay operates. Each section controls different aspects of the relay's behavior.1.
mongodb(Database Settings)uri: mongodb://localhost:27017/:- This is the connection string for your MongoDB database.
mongodb://localhost:27017/indicates that your MongoDB server is running on the same computer as your Grain relay (localhost) and listening on port 27017 (the default MongoDB port).- If your MongoDB server is on a different machine, you'll need to change
localhostto the server's IP address or hostname. - The trailing
/indicates the root of the mongodb server. You will define the database in the next line.
database: grain:- This specifies the name of the MongoDB database that Grain will use to store Nostr events. Grain will create this database if it doesn't already exist.
- You can name the database whatever you want. If you want to run multiple grain relays, you can and they can have different databases running on the same mongo server.
2.
server(Relay Server Settings)port: :8181:- This sets the port on which your Grain relay will listen for incoming nostr websocket connections and what port the frontend will be available at.
read_timeout: 10 # in seconds:- This is the maximum time (in seconds) that the relay will wait for a client to send data before closing the connection.
write_timeout: 10 # in seconds:- This is the maximum time (in seconds) that the relay will wait for a client to receive data before closing the connection.
idle_timeout: 120 # in seconds:- This is the maximum time (in seconds) that the relay will keep a connection open if there's no activity.
max_connections: 100:- This sets the maximum number of simultaneous client connections that the relay will allow.
max_subscriptions_per_client: 10:- This sets the maximum amount of subscriptions a single client can request from the relay.
3.
resource_limits(System Resource Limits)cpu_cores: 2 # Limit the number of CPU cores the application can use:- This restricts the number of CPU cores that Grain can use. Useful for controlling resource usage on your server.
memory_mb: 1024 # Cap the maximum amount of RAM in MB the application can use:- This limits the maximum amount of RAM (in megabytes) that Grain can use.
heap_size_mb: 512 # Set a limit on the Go garbage collector's heap size in MB:- This sets a limit on the amount of memory that the Go programming language's garbage collector can use.
4.
auth(Authentication Settings)enabled: false # Enable or disable AUTH handling:- If set to
true, this enables authentication handling, requiring clients to authenticate before using the relay.
- If set to
relay_url: "wss://relay.example.com/" # Specify the relay URL:- If authentication is enabled, this is the url that clients will use to authenticate.
5.
UserSync(User Synchronization)user_sync: false:- If set to true, the relay will attempt to sync user data from other relays.
disable_at_startup: true:- If user sync is enabled, this will prevent the sync from starting when the relay starts.
initial_sync_relays: [...]:- A list of other relays to pull user data from.
kinds: []:- A list of event kinds to pull from the other relays. Leaving this empty will pull all event kinds.
limit: 100:- The limit of events to pull from the other relays.
exclude_non_whitelisted: true:- If set to true, only users on the whitelist will have their data synced.
interval: 360:- The interval in minutes that the relay will resync user data.
6.
backup_relay(Backup Relay)enabled: false:- If set to true, the relay will send copies of received events to the backup relay.
url: "wss://some-relay.com":- The url of the backup relay.
7.
event_purge(Event Purging)enabled: false:- If set to
true, the relay will automatically delete old events.
- If set to
keep_interval_hours: 24:- The number of hours to keep events before purging them.
purge_interval_minutes: 240:- How often (in minutes) the purging process runs.
purge_by_category: ...:- Allows you to specify which categories of events (regular, replaceable, addressable, deprecated) to purge.
purge_by_kind_enabled: false:- If set to true, events will be purged based on the kinds listed below.
kinds_to_purge: ...:- A list of event kinds to purge.
exclude_whitelisted: true:- If set to true, events from whitelisted users will not be purged.
8.
event_time_constraints(Event Time Constraints)min_created_at: 1577836800:- The minimum
created_attimestamp (Unix timestamp) that events must have to be accepted by the relay.
- The minimum
max_created_at_string: now+5m:- The maximum created at time that an event can have. This example shows that the max created at time is 5 minutes in the future from the time the event is received.
min_created_at_stringandmax_created_atwork the same way.
9.
rate_limit(Rate Limiting)ws_limit: 100:- The maximum number of WebSocket messages per second that the relay will accept.
ws_burst: 200:- Allows a temporary burst of WebSocket messages.
event_limit: 50:- The maximum number of Nostr events per second that the relay will accept.
event_burst: 100:- Allows a temporary burst of Nostr events.
req_limit: 50:- The limit of http requests per second.
req_burst: 100:- The allowed burst of http requests.
max_event_size: 51200:- The maximum size (in bytes) of a Nostr event that the relay will accept.
kind_size_limits: ...:- Allows you to set size limits for specific event kinds.
category_limits: ...:- Allows you to set rate limits for different event categories (ephemeral, addressable, regular, replaceable).
kind_limits: ...:- Allows you to set rate limits for specific event kinds.
By understanding these settings, you can tailor your Grain Nostr relay to meet your specific needs and resource constraints.
whitelist.yml
The
whitelist.ymlfile is used to control which users, event kinds, and domains are allowed to interact with your Grain relay. Here's a breakdown of the settings:1.
pubkey_whitelist(Public Key Whitelist)enabled: false:- If set to
true, this enables the public key whitelist. Only users whose public keys are listed will be allowed to publish events to your relay.
- If set to
pubkeys::- A list of hexadecimal public keys that are allowed to publish events.
pubkey1andpubkey2are placeholders, you will replace these with actual hexadecimal public keys.
npubs::- A list of npubs that are allowed to publish events.
npub18ls2km9aklhzw9yzqgjfu0anhz2z83hkeknw7sl22ptu8kfs3rjq54am44andnpub2are placeholders, replace them with actual npubs.- npubs are bech32 encoded public keys.
2.
kind_whitelist(Event Kind Whitelist)enabled: false:- If set to
true, this enables the event kind whitelist. Only events with the specified kinds will be allowed.
- If set to
kinds::- A list of event kinds (as strings) that are allowed.
"1"and"2"are example kinds. Replace these with the kinds you want to allow.- Example kinds are 0 for metadata, 1 for short text notes, and 2 for recommend server.
3.
domain_whitelist(Domain Whitelist)enabled: false:- If set to
true, this enables the domain whitelist. This checks the domains .well-known folder for their nostr.json. This file contains a list of pubkeys. They will be considered whitelisted if on this list.
- If set to
domains::- A list of domains that are allowed.
"example.com"and"anotherdomain.com"are example domains. Replace these with the domains you want to allow.
blacklist.yml
The
blacklist.ymlfile allows you to block specific content, users, and words from your Grain relay. Here's a breakdown of the settings:1.
enabled: true- This setting enables the blacklist functionality. If set to
true, the relay will actively block content and users based on the rules defined in this file.
2.
permanent_ban_words:- This section lists words that, if found in an event, will result in a permanent ban for the event's author.
- really bad wordis a placeholder. Replace it with any words you want to permanently block.
3.
temp_ban_words:- This section lists words that, if found in an event, will result in a temporary ban for the event's author.
- crypto,- web3, and- airdropare examples. Replace them with the words you want to temporarily block.
4.
max_temp_bans: 3- This sets the maximum number of temporary bans a user can receive before they are permanently banned.
5.
temp_ban_duration: 3600- This sets the duration of a temporary ban in seconds.
3600seconds equals one hour.
6.
permanent_blacklist_pubkeys:- This section lists hexadecimal public keys that are permanently blocked from using the relay.
- db0c9b8acd6101adb9b281c5321f98f6eebb33c5719d230ed1870997538a9765is an example. Replace it with the public keys you want to block.
7.
permanent_blacklist_npubs:- This section lists npubs that are permanently blocked from using the relay.
- npub1x0r5gflnk2mn6h3c70nvnywpy2j46gzqwg6k7uw6fxswyz0md9qqnhshtnis an example. Replace it with the npubs you want to block.- npubs are the human readable version of public keys.
8.
mutelist_authors:- This section lists hexadecimal public keys of author of a kind1000 mutelist. Pubkey authors on this mutelist will be considered on the permanent blacklist. This provides a nostr native way to handle the backlist of your relay
- 3fe0ab6cbdb7ee27148202249e3fb3b89423c6f6cda6ef43ea5057c3d93088e4is an example. Replace it with the public keys of authors that have a mutelist you would like to use as a blacklist. Consider using your own.- Important Note: The mutelist Event MUST be stored in this relay for it to be retrieved. This means your relay must have a copy of the authors kind10000 mutelist to consider them for the blacklist.
Running Grain as a Service:
Windows Service:
To run Grain as a Windows service, you can use tools like NSSM (Non-Sucking Service Manager). NSSM allows you to easily install and manage any application as a Windows service.
* For instructions on how to install NSSM, please refer to this article: [Link to NSSM install guide coming soon].-
Open Command Prompt as Administrator:
- Open the Windows Start menu, type "cmd," right-click on "Command Prompt," and select "Run as administrator."
-
Navigate to NSSM Directory:
- Use the
cdcommand to navigate to the directory where you extracted NSSM. For example, if you extracted it toC:\nssm, you would typecd C:\nssmand press Enter.
- Use the
-
Install the Grain Service:
- Run the command
nssm install grain. - A GUI will appear, allowing you to configure the service.
- Run the command
-
Configure Service Details:
- In the "Path" field, enter the full path to your Grain executable (e.g.,
C:\grain\grain_windows_amd64.exe). - In the "Startup directory" field, enter the directory where your Grain executable is located (e.g.,
C:\grain).
- In the "Path" field, enter the full path to your Grain executable (e.g.,
-
Install the Service:
- Click the "Install service" button.
-
Manage the Service:
- You can now manage the Grain service using the Windows Services manager. Open the Start menu, type "services.msc," and press Enter. You can start, stop, pause, or restart the Grain service from there.
Linux Service (systemd):
To run Grain as a Linux service, you can use systemd, the standard service manager for most modern Linux distributions.
-
Create a Systemd Service File:
- Open a text editor with root privileges (e.g.,
sudo nano /etc/systemd/system/grain.service).
- Open a text editor with root privileges (e.g.,
-
Add Service Configuration:
- Add the following content to the
grain.servicefile, replacing the placeholders with your actual paths and user information:
```toml [Unit] Description=Grain Nostr Relay After=network.target
[Service] ExecStart=/path/to/grain_linux_amd64 WorkingDirectory=/path/to/grain/directory Restart=always User=your_user #replace your_user Group=your_group #replace your_group
[Install] WantedBy=multi-user.target ```
- Replace
/path/to/grain/executablewith the full path to your Grain executable. - Replace
/path/to/grain/directorywith the directory containing your Grain executable. - Replace
your_userandyour_groupwith the username and group that will run the Grain service.
- Add the following content to the
-
Reload Systemd:
- Run the command
sudo systemctl daemon-reloadto reload the systemd configuration.
- Run the command
-
Enable the Service:
- Run the command
sudo systemctl enable grain.serviceto enable the service to start automatically on boot.
- Run the command
-
Start the Service:
- Run the command
sudo systemctl start grain.serviceto start the service immediately.
- Run the command
-
Check Service Status:
- Run the command
sudo systemctl status grain.serviceto check the status of the Grain service. This will show you if the service is running and any recent logs. - You can run
sudo journalctl -f -u grain.serviceto watch the logs
- Run the command
More guides are in the works for setting up tailscale to access your relay from anywhere over a private network and for setting up a cloudflare tunnel to your domain to deploy a grain relay accessible on a subdomain of your site eg wss://relay.yourdomain.com
-
 @ a367f9eb:0633efea
2025-03-19 17:40:04
@ a367f9eb:0633efea
2025-03-19 17:40:04On February 27th, the Securities and Exchange Commission stated in its latest staff statement that memecoins are not necessarily securities.
“Although the offer and sale of meme coins may not be subject to the federal securities laws, fraudulent conduct related to the offer and sale of meme coins may be subject to enforcement action or prosecution,” writes the SEC.
This clarity is important, but it reveals nothing about what the policies around memecoins, rugpulls, and crypto scams should actually be.
This month has already delivered us Argentine President Javier Milei’s promotion of a pump-and-dump memecoin called LIBRA. At this moment, Barstool Sports founder Dave Portnoy is probably pumping his third or fourth favorite memecoin into oblivion while he dumps on retail.
In each of these cases, these tokens are created with copy-paste smart contracts, influencers singing their praises, and people exchanging their stablecoins, bitcoin, or some other altcoin for the hope of making it rich.
Memecoin world
Of course, in a free country people should be free to bet on things they want. But they should be prepared to lose just as much as they’re prepared to win.
To the uninitiated, these scams represent “crypto” writ-large, lumping the original decentralized protocol of Bitcoin with pump and dump scams from platforms like pump.fun that run on Solana and other chains.
Knowing what we know, and how desperate parts of the crypto market are for outrageous tokens and leveraged degen trading, we must naturally ask how Bitcoin can fix this. Or, rather, how smart Bitcoin policies can fix this.
As I have written for several years, we as Bitcoin advocates should promote sound policies that will encourage innovation and increase economic inclusion across all income groups, all the while protecting consumers from harm. We want to avoid blowouts like FTX, Celsius, and even stablecoins projects like TerraUSD – not only because they defraud bitcoiners, but because they sully the reputation of our entire sector of technological innovation.
Because Bitcoin represents scarcity, decentralization, and complete transparency, there is much we can learn from Satoshi’s innovation when we’re dealing with next-level crypto-offspring.
The Smart Bitcoin Policies to Stop Crypto Scams
To begin, US federal, state, and local agencies should update their technological stack to rigorously identify and prosecute fraud and abuse in crypto projects. Fraudulent claims, fake token whitepapers, and deceptive tactics are already illegal under existing law. Our agencies should be empowered to enforce existing law and weed out the bad actors.
Whether that means better training or tools, law enforcement should receive the necessary upgrades to prosecute and identify the real fraudulent crime that happens to take place in crypto protocols. Much of this behavior is just being used in a new medium. It’s not crazy to think that cops should upgrade their tech stack to understand how it’s happening now.
Second, our policies on money transmission licenses and regulation for crypto exchanges should be streamlined and made easier, rather than more difficult. Let competition provide the best places for people to buy their bitcoin. As much as privacy advocates abhor centralized platforms and exchanges, they still implement better security and educational practices to inform users than a shady service hosted in China will provide.
By simplifying the rules and restrictions on bitcoin exchanges, especially by allowing them to consider their custodied bitcoin as assets rather than liabilities as was done by rescinding SAB 121, it means that more Americans will have the opportunity to have excellent experiences when purchasing their coins online.
Third, regulators must not pigeonhole bitcoin and its crypto-offspring only as investments fit for taxing, but rather as technological tools that empower consumers and foster innovation. Too much discussion about bitcoin policies hinges on the tax rate or how much it will bring to state coffers, rather than by how much it can make one’s life better by removing the red tape to safeguard wealth.
By recognizing the ultimate power of bitcoin self-custody without needing to trust third parties or intermediaries, it means we finally view this technology as an extension of our own free speech and freedom of association.
And lastly, we must focus on removing the barriers to using bitcoin as an ordinary means of payment. The Keep Your Coins Act restricts federal agencies from stopping individuals from using bitcoin how they see fit, as well as protecting self-custody. That, plus de minimis exemption rules that allow us to spend bitcoin as any other asset, mean we can use digital money as intended.
We know that memecoins and rugpulls will continue to happen no matter what, this is almost human nature. But at the same time, embracing smart bitcoin policies will ensure that consumers and users have the best tools and protections available to use the technology if they want.
Originally published at the Bitcoin Policy Institute.
-
 @ a60e79e0:1e0e6813
2025-03-18 15:38:25
@ a60e79e0:1e0e6813
2025-03-18 15:38:25**This is a long form note test of a post that lives on my Nostr educational website Hello Nostr **
One of the first things most people learn when getting started with Nostr is the importance of their private key, or ‘nsec’. The nsec is the key to their Nostr world. Whoever controls an nsec, controls that account. Lose access to the nsec and you lose access to that account and its social graph.
So the nsec is very important and should be treated very carefully, but what happens if we want to use or test multiple Nostr clients? Newer clients might be malicious, or have unknown security vulnerabilities, so simply go pasting our nsec everywhere just to see if we like a new app is not the best idea!
Thankfully there are solutions for nsec management that allow us to do exactly that, without having to expose our all important nsec to each and every app we want to interact with. The most commonly used to date are browser extensions like Alby or nos2x. Typically these types of browser extensions do not work on mobile platforms.
Enter Amber…

What is Amber?
Amber is a free and open source Android application that serves as a dedicated ‘Nostr event signer’. Amber allows users to keep their nsec segregated in a single, dedicated app. The goal of Amber is to have your smartphone act as a NIP-46 signing device without any need for servers or additional hardware.
At its core Amber serves two main purposes:
Securing your nsec(s) Using this nsec to sign events for other Nostr clients on your phone
Got an iPhone? Check out nsec.app
Getting Started
- Download Amber to your phone. It is available from Zap Store, Obtanium, GitHub or F-Droid
Download Amber here. Support Amber here.
-
When opening Amber for the first time, you’ll have the option to create a new Nostr account (nsec) or import an existing one.
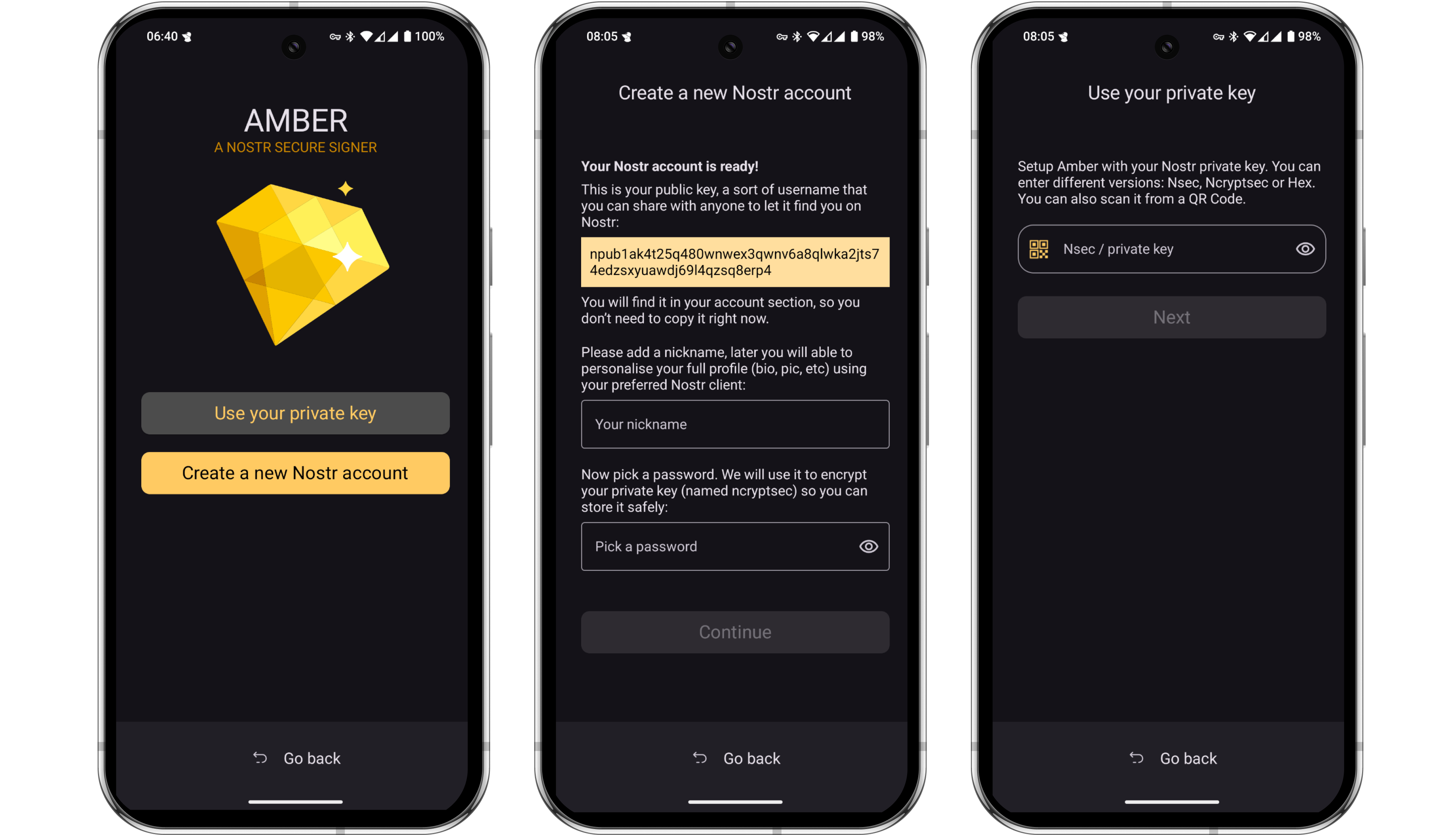
-
If you do not currently have a Nostr account, Amber will help you generate and secure a brand new nsec. Amber allows you to download an encrypted file containing your nsec as well as the option to download a human-readable version of the nsec in the form of 12 English words, similar to a Bitcoin seed.
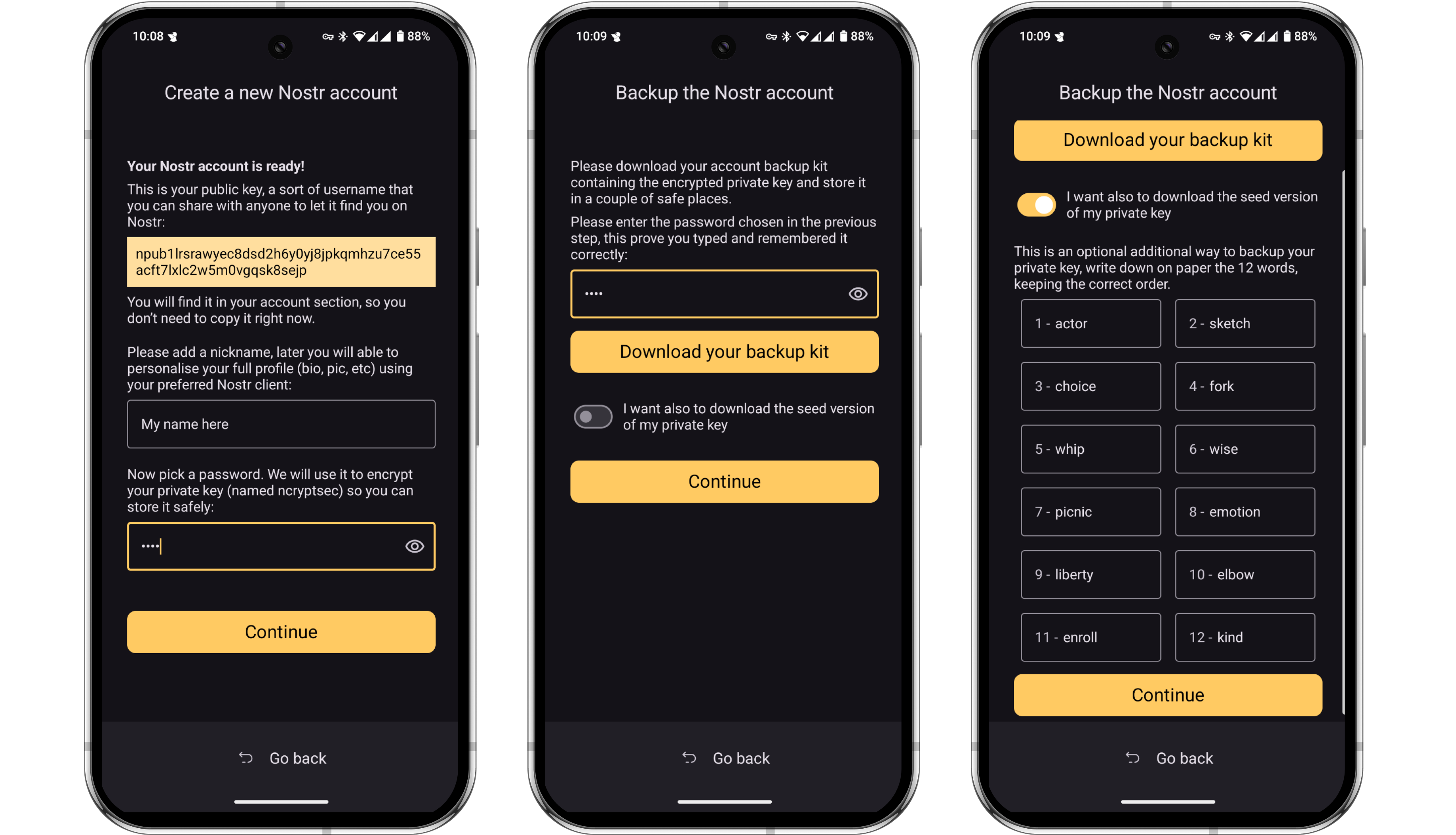
Skip this step if you have an existing nsec that you want to import to Amber.
-
To import an existing nsec, choose ‘Use your private key’. You can then paste the nsec from an existing client, or scan a QR code of it if you have one available to you.
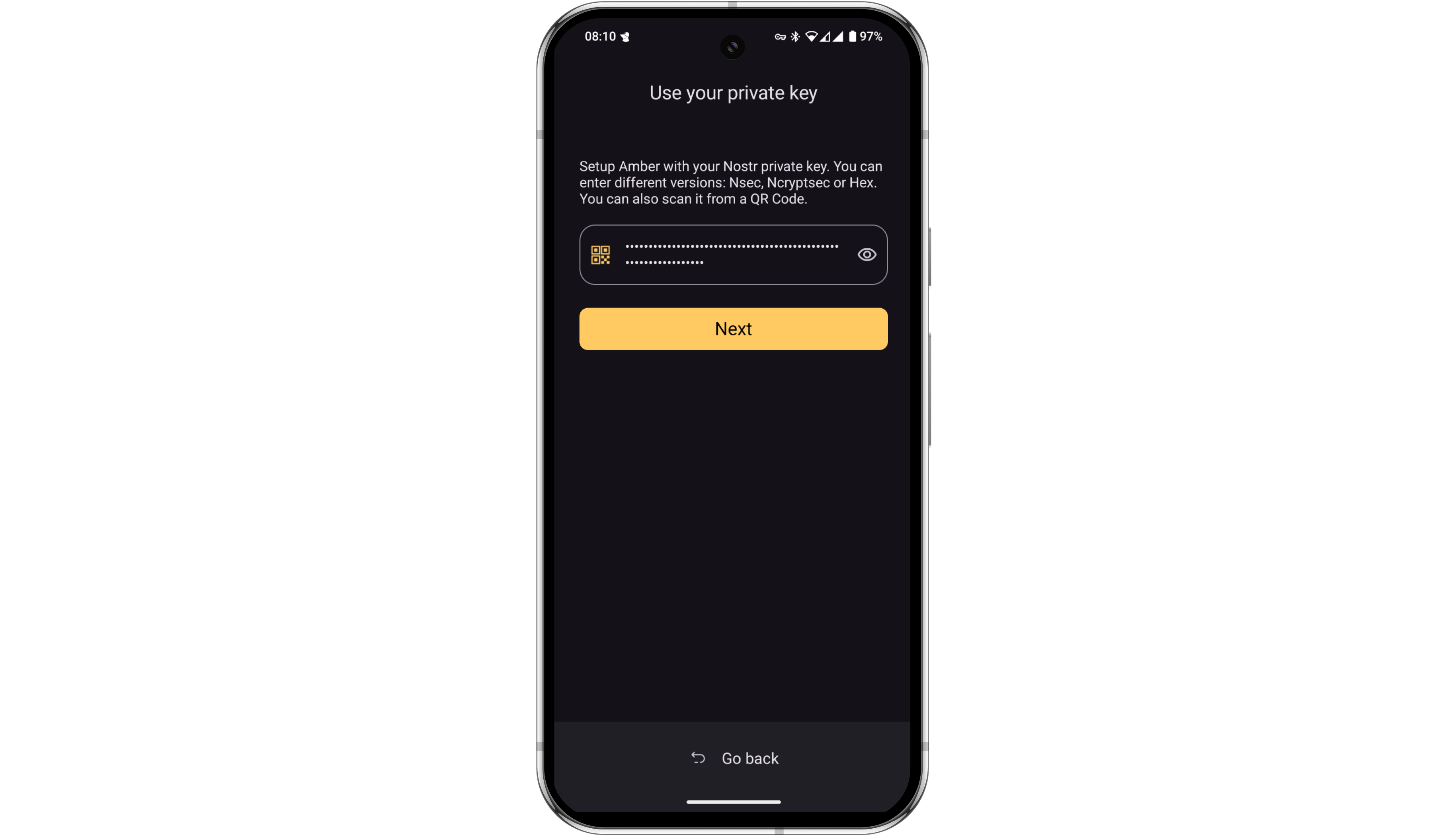
-
Once you have created or imported your nsec, Amber will ask for some basic permissions. You can allow the app the approve basic actions, or enable more granular selection for each client you subsequently connect. Once you tap ‘Finish’, you’ll see that the account is now ready.
If you have or require more than one Nostr account, you can repeat these steps for each one. All accounts can be viewed by tapping the profile image in the bottom right corner of the screen.
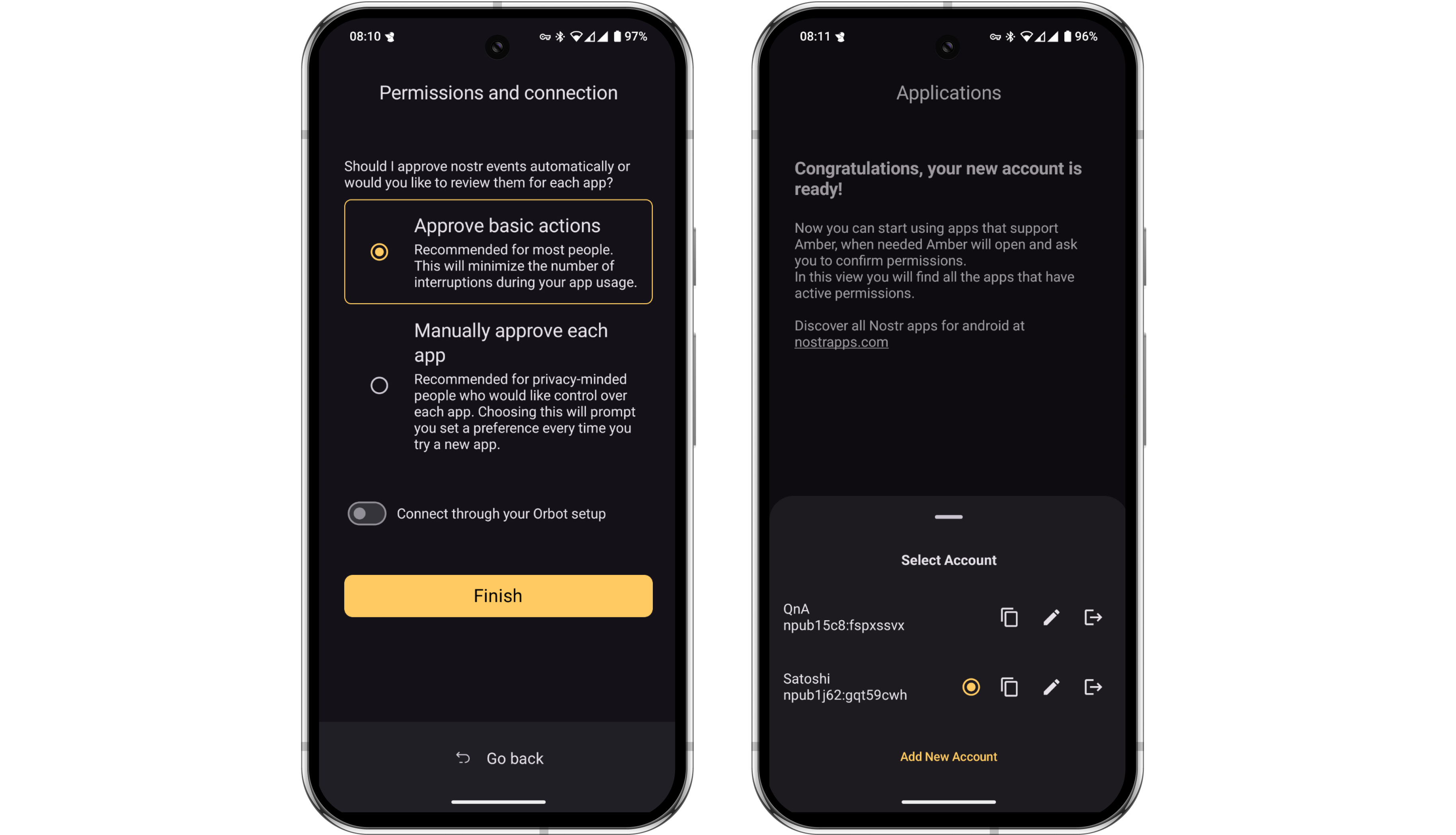
- That’s it, Amber is now ready to sign events. Amber allows multiple ways to connect other clients to it, but most will have a very simple ‘Login with Amber’ button. Let’s demo this in practice with Amethyst, the most popular Android-only client.
The opening screen of Amethyst shows the ‘Login with Amber’ option. Tap that.
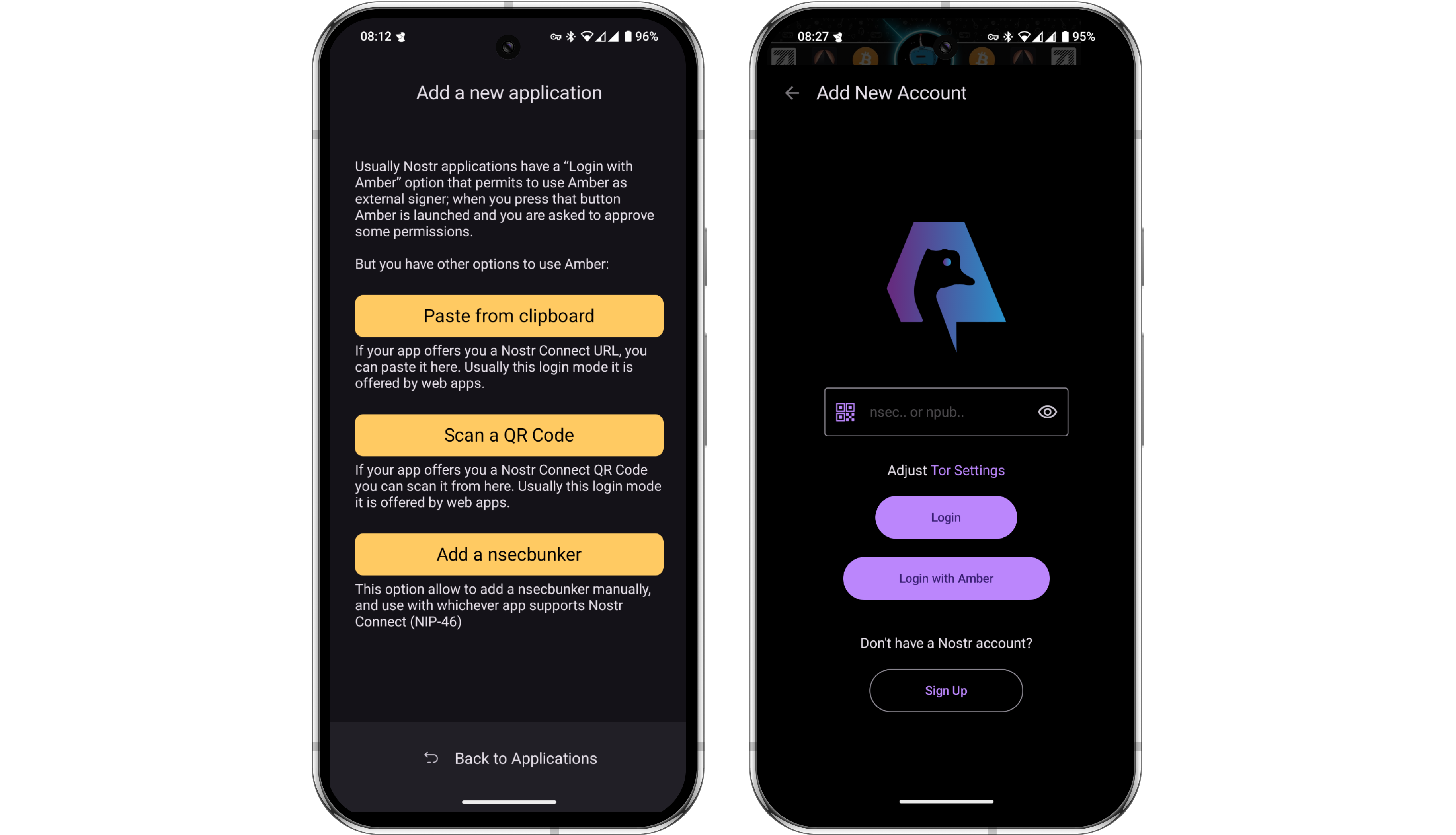
- Amber will then open automatically and ask you to define the level of autonomy you’d like to have with Amethyst. This setting defines how often Amber will require you to manually authorize each event.
For example, you might want Amber to automatically sign every like or repost you do in Amethyst, but then be asked to manually approve all direct messages sent from your account. These permissions can be customized in the settings at any time.
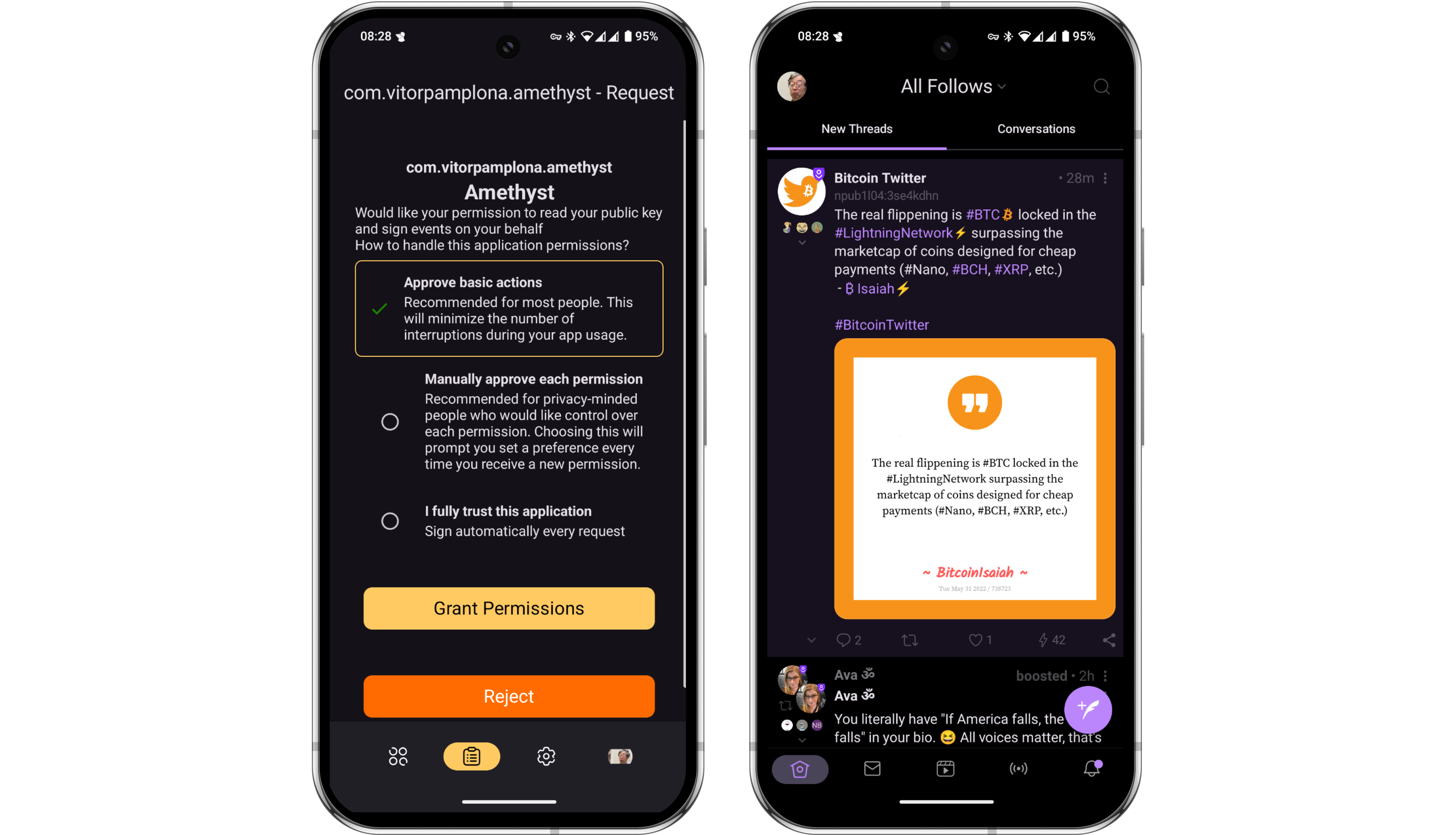
- Let’s assume that upon setup, we did not grant Amber the ability to automatically sign short text notes for us. Let’s look at how simple the authorization flow is. Type a new short note in Amethyst and press ‘Post’.
Amethyst will instantly send the request to the Amber app on your phone, with no third party server involved. Amber will open and ask you to approve the event. When you do, Amber signs the event with the nsec it stores for you and automatically send the signed event back to Amethyst to be posted. The whole process takes just a few seconds.
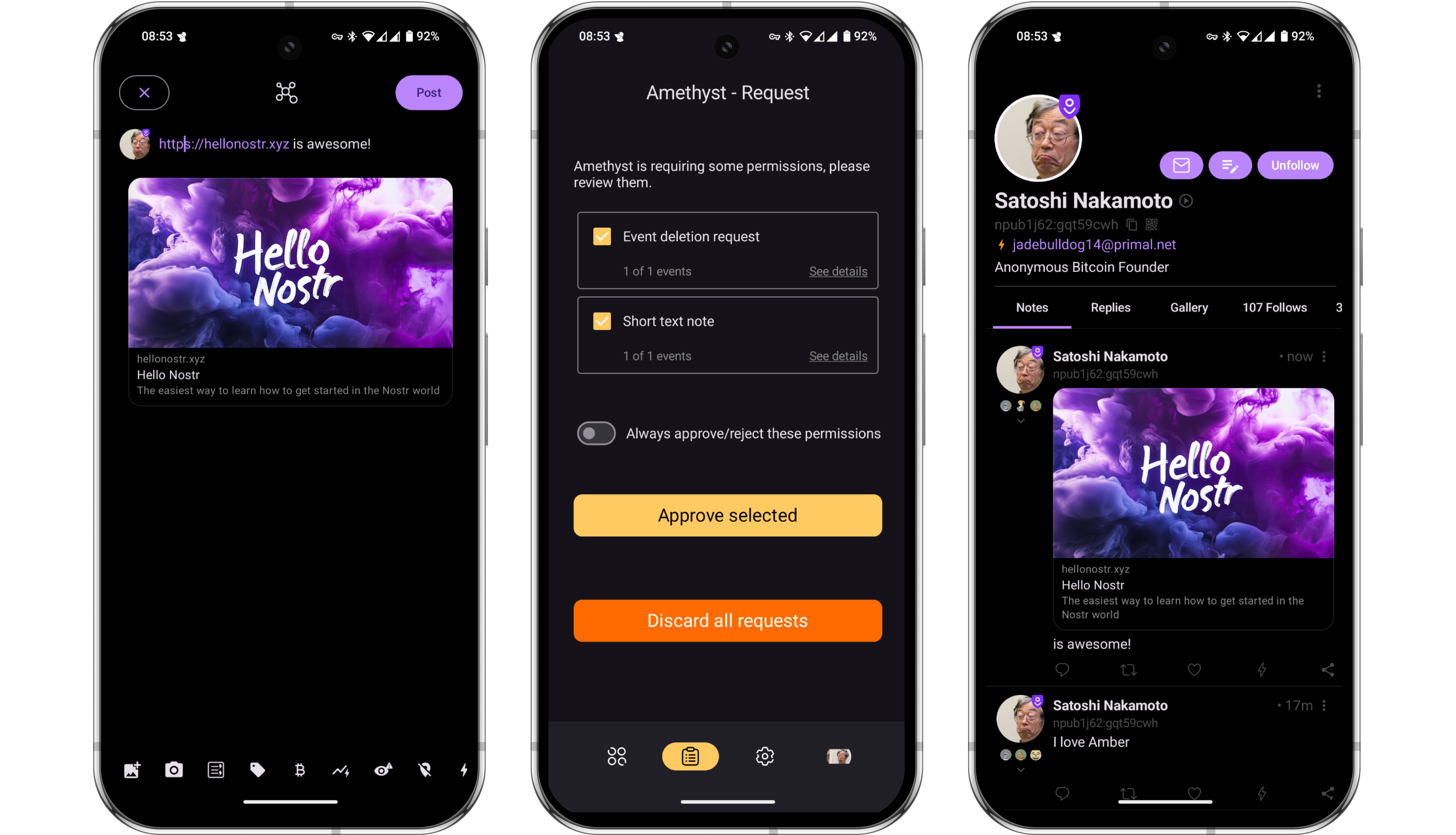
Using Amber with a Web Client
-
Next let’s take a look at how you can use Amber on your phone to sign events on a web app running on your computer. For this example, we’ll be using Coracle. Open Coracle and click ‘Log In’, then choose ‘Use Remote Signer’. Coracle will then display a QR code.
-
Open Amber and navigate to the Applications page, tap the + icon, then scan the QR code being displayed by Coracle.
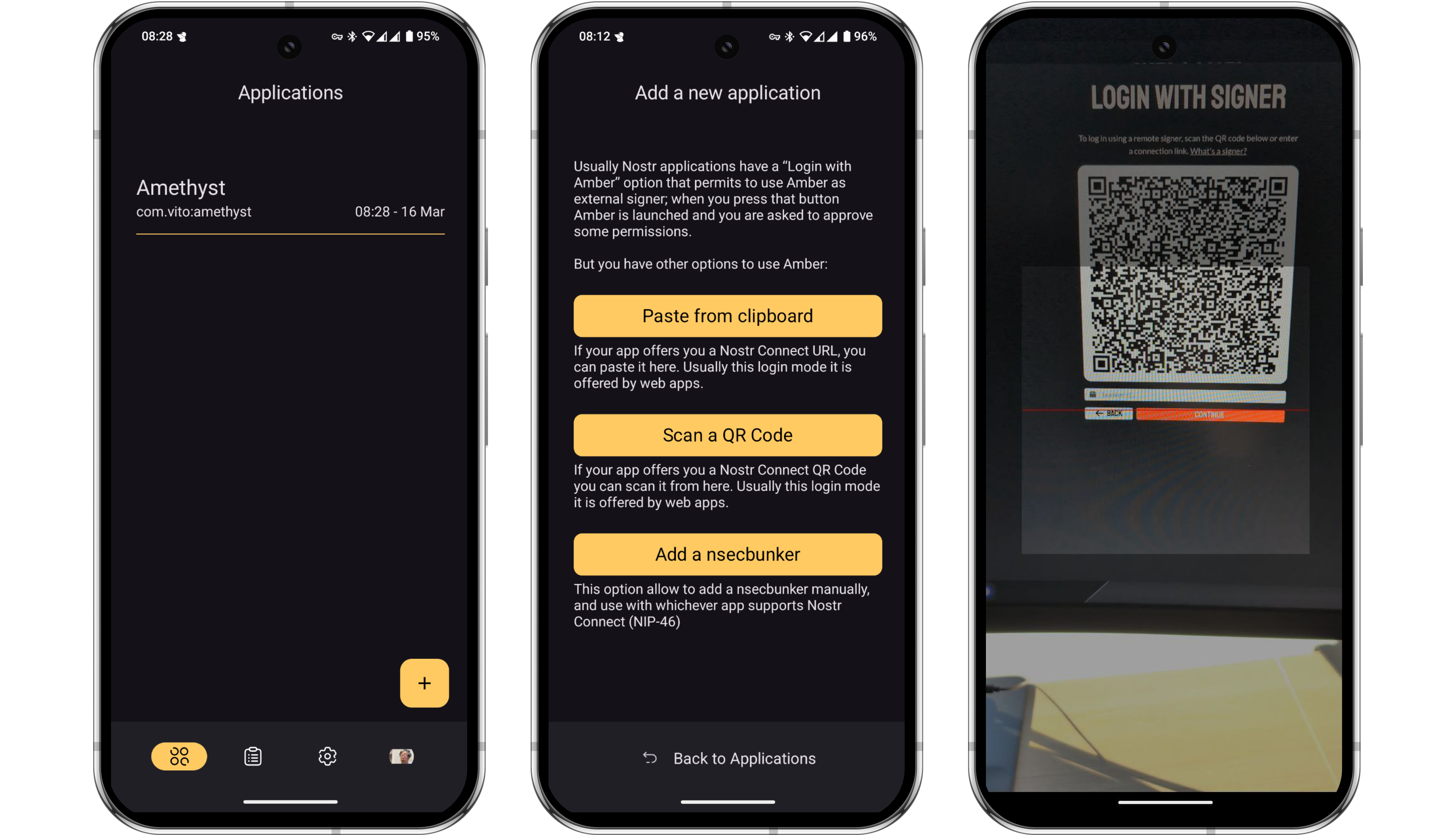
-
Just as it did earlier with Amethyst, Amber will now ask you to grant some basic permissions for the Coracle connection. Once again, these permissions can be customized at any time in the settings. Once granted, you’ll notice that Coracle automatically logs in to your feed.
But wait, how did that happen? The nsec is in Amber on your phone, and Coracle is running on your computer. The two might not even be in the same location or on the same network!? The communication is happening over the Nostr protocol, via relays. Which relays are used for this communication can be configured in the Amber settings.
-
Let’s test out a short note on Coracle to demonstrate the signing process. Click ‘Post +’ in the top right corner, draft your note and then click send.
-
Amber will send a push notification to your phone. Tapping the notification will open Amber for you to approve the event.
-
Once the event is approved in Amber, Amber will automatically send the signed event back to Coracle for publishing.
Summary
You can view Amber as a vault for your Nostr private keys (nsec). It allows you to explore the entire ecosystem without exposing your nsec to every new app you try. Amber is an incredibly simple yet powerful tool that belongs on the Android phone of every Nostr user.
At the time of writing, using Amber as a remote event signer is supported by the following popular Nostr clients:
- Amethyst (mobile)
- Coracle (web)
- 0xChat (mobile)
- Fountain (mobile)
- Zap Store (mobile)
- Keychat (mobile)
- Freeflow (mobile)
- Highlighter (web)
- Chachi Chat (web)
- Habla (web)
- Shopstr (web)
- Plebeian Market (web)
- Snort (web)
- Nostrudel (web)
If you found this post useful, please share it with your peers and consider following and zapping me on Nostr. If you write to me and let me know that you found me via this post, I’ll be sure to Zap you back! ⚡️
