-
 @ 2ed3596e:98b4cc78
2025-04-24 18:31:53
@ 2ed3596e:98b4cc78
2025-04-24 18:31:53Bitcoiners, your points just got a lot more epic! We’re thrilled to announce the launch of the Bitcoin Well Point Store, available now in Canada and the USA.
Now you can redeem your Bitcoin Well points for prizes that level up and celebrate your Bitcoin lifestyle.
What can you get in store?
Right now, you can exchange your points for:
-
Simply Bitcoin hoodie: Rep your Bitcoin pride in style
-
Exclusive Bitcoin Well Stampseed backup plate: Protect and manage your private keys securely
-
Personalized LeatherMint wallet: Classy, sleek, and ready to hold your fiat (until you convert it to sats!)
-
Tesla Cybertruck in Bitcoin orange: Wait…really? A Cybertruck? Who approved this?

More epic items will be available in the Bitcoin Well Point Store in the coming months. Stay tuned!
How to redeem your Bitcoin Well Points
Redeeming your points is easy:
-
Log in and go the Bitcoin Well Points store within the Rewards Section
-
Check your Bitcoin Well point balance
-
Redeem Your Bitcoin Well points for the prize of your dreams
Once you’ve purchased an item from the Bitcoin Well Point Store, we’ll email you to figure out where you want us to ship your prize. Unless it's the Cybertruck, then you can come to our office and pick it up!
How can you earn more Bitcoin Well Points? ⚡
Here are all the ways you can earn Bitcoin Well points:
-
Buy bitcoin/Sell bitcoin/pay bills - 3 Points per $10
-
Recurring buy - 5 points per $10
-
First transaction bonus - 500 points
-
Refer a friend to Bitcoin Well - 500 points
The more you use Bitcoin Well, the more points you earn, rewarding you for investing in your freedom and self-sovereignty
Want sats, not stuff? No problem! 👇
You can keep earning sats by playing the Bitcoin (Wishing) Well! You can win up to 1,000,000 on your next coin toss. Now you have the exciting choice: do you play the Bitcoin (Wishing) Well or save up your Bitcoin Well points for a sweet prize?

What makes Bitcoin Well different
Bitcoin Well is on a mission to enable independence. We do this by making it easy to self custody bitcoin and embracing the latest bitcoin innovations. By custodying their own money, our customers are free to do as they wish without begging for permission. By creating a full ecosystem to buy, sell and use your bitcoin to connect with the modern financial world, you are able to have your cake and eat it too - or have your bitcoin in self custody and easily spend it too 🎂.
Create your Bitcoin Well account now →
Invest in Bitcoin Well
We are publicly traded (and love it when our customers become shareholders!) and hold ourselves to a high standard of enabling life on a Bitcoin standard. If you want to learn more about Bitcoin Well, please visit our website or reach out!
-
-
 @ 88cc134b:5ae99079
2025-04-24 17:38:04
@ 88cc134b:5ae99079
2025-04-24 17:38:04test
nostr:nevent1qvzqqqqqqypzpzxvzd935e04fm6g4nqa7dn9qc7nafzlqn4t3t6xgmjkr3dwnyreqqsr98r3ryhw0kdqv6s92c9tcxruc6g9hfjgunnl50gclyyjerv00csna38cs
-
 @ 40b9c85f:5e61b451
2025-04-24 15:27:02
@ 40b9c85f:5e61b451
2025-04-24 15:27:02Introduction
Data Vending Machines (DVMs) have emerged as a crucial component of the Nostr ecosystem, offering specialized computational services to clients across the network. As defined in NIP-90, DVMs operate on an apparently simple principle: "data in, data out." They provide a marketplace for data processing where users request specific jobs (like text translation, content recommendation, or AI text generation)
While DVMs have gained significant traction, the current specification faces challenges that hinder widespread adoption and consistent implementation. This article explores some ideas on how we can apply the reflection pattern, a well established approach in RPC systems, to address these challenges and improve the DVM ecosystem's clarity, consistency, and usability.
The Current State of DVMs: Challenges and Limitations
The NIP-90 specification provides a broad framework for DVMs, but this flexibility has led to several issues:
1. Inconsistent Implementation
As noted by hzrd149 in "DVMs were a mistake" every DVM implementation tends to expect inputs in slightly different formats, even while ostensibly following the same specification. For example, a translation request DVM might expect an event ID in one particular format, while an LLM service could expect a "prompt" input that's not even specified in NIP-90.
2. Fragmented Specifications
The DVM specification reserves a range of event kinds (5000-6000), each meant for different types of computational jobs. While creating sub-specifications for each job type is being explored as a possible solution for clarity, in a decentralized and permissionless landscape like Nostr, relying solely on specification enforcement won't be effective for creating a healthy ecosystem. A more comprehensible approach is needed that works with, rather than against, the open nature of the protocol.
3. Ambiguous API Interfaces
There's no standardized way for clients to discover what parameters a specific DVM accepts, which are required versus optional, or what output format to expect. This creates uncertainty and forces developers to rely on documentation outside the protocol itself, if such documentation exists at all.
The Reflection Pattern: A Solution from RPC Systems
The reflection pattern in RPC systems offers a compelling solution to many of these challenges. At its core, reflection enables servers to provide metadata about their available services, methods, and data types at runtime, allowing clients to dynamically discover and interact with the server's API.
In established RPC frameworks like gRPC, reflection serves as a self-describing mechanism where services expose their interface definitions and requirements. In MCP reflection is used to expose the capabilities of the server, such as tools, resources, and prompts. Clients can learn about available capabilities without prior knowledge, and systems can adapt to changes without requiring rebuilds or redeployments. This standardized introspection creates a unified way to query service metadata, making tools like
grpcurlpossible without requiring precompiled stubs.How Reflection Could Transform the DVM Specification
By incorporating reflection principles into the DVM specification, we could create a more coherent and predictable ecosystem. DVMs already implement some sort of reflection through the use of 'nip90params', which allow clients to discover some parameters, constraints, and features of the DVMs, such as whether they accept encryption, nutzaps, etc. However, this approach could be expanded to provide more comprehensive self-description capabilities.
1. Defined Lifecycle Phases
Similar to the Model Context Protocol (MCP), DVMs could benefit from a clear lifecycle consisting of an initialization phase and an operation phase. During initialization, the client and DVM would negotiate capabilities and exchange metadata, with the DVM providing a JSON schema containing its input requirements. nip-89 (or other) announcements can be used to bootstrap the discovery and negotiation process by providing the input schema directly. Then, during the operation phase, the client would interact with the DVM according to the negotiated schema and parameters.
2. Schema-Based Interactions
Rather than relying on rigid specifications for each job type, DVMs could self-advertise their schemas. This would allow clients to understand which parameters are required versus optional, what type validation should occur for inputs, what output formats to expect, and what payment flows are supported. By internalizing the input schema of the DVMs they wish to consume, clients gain clarity on how to interact effectively.
3. Capability Negotiation
Capability negotiation would enable DVMs to advertise their supported features, such as encryption methods, payment options, or specialized functionalities. This would allow clients to adjust their interaction approach based on the specific capabilities of each DVM they encounter.
Implementation Approach
While building DVMCP, I realized that the RPC reflection pattern used there could be beneficial for constructing DVMs in general. Since DVMs already follow an RPC style for their operation, and reflection is a natural extension of this approach, it could significantly enhance and clarify the DVM specification.
A reflection enhanced DVM protocol could work as follows: 1. Discovery: Clients discover DVMs through existing NIP-89 application handlers, input schemas could also be advertised in nip-89 announcements, making the second step unnecessary. 2. Schema Request: Clients request the DVM's input schema for the specific job type they're interested in 3. Validation: Clients validate their request against the provided schema before submission 4. Operation: The job proceeds through the standard NIP-90 flow, but with clearer expectations on both sides
Parallels with Other Protocols
This approach has proven successful in other contexts. The Model Context Protocol (MCP) implements a similar lifecycle with capability negotiation during initialization, allowing any client to communicate with any server as long as they adhere to the base protocol. MCP and DVM protocols share fundamental similarities, both aim to expose and consume computational resources through a JSON-RPC-like interface, albeit with specific differences.
gRPC's reflection service similarly allows clients to discover service definitions at runtime, enabling generic tools to work with any gRPC service without prior knowledge. In the REST API world, OpenAPI/Swagger specifications document interfaces in a way that makes them discoverable and testable.
DVMs would benefit from adopting these patterns while maintaining the decentralized, permissionless nature of Nostr.
Conclusion
I am not attempting to rewrite the DVM specification; rather, explore some ideas that could help the ecosystem improve incrementally, reducing fragmentation and making the ecosystem more comprehensible. By allowing DVMs to self describe their interfaces, we could maintain the flexibility that makes Nostr powerful while providing the structure needed for interoperability.
For developers building DVM clients or libraries, this approach would simplify consumption by providing clear expectations about inputs and outputs. For DVM operators, it would establish a standard way to communicate their service's requirements without relying on external documentation.
I am currently developing DVMCP following these patterns. Of course, DVMs and MCP servers have different details; MCP includes capabilities such as tools, resources, and prompts on the server side, as well as 'roots' and 'sampling' on the client side, creating a bidirectional way to consume capabilities. In contrast, DVMs typically function similarly to MCP tools, where you call a DVM with an input and receive an output, with each job type representing a different categorization of the work performed.
Without further ado, I hope this article has provided some insight into the potential benefits of applying the reflection pattern to the DVM specification.
-
 @ f1989a96:bcaaf2c1
2025-04-24 16:19:13
@ f1989a96:bcaaf2c1
2025-04-24 16:19:13Good morning, readers!
In Georgia, mere weeks after freezing the bank accounts of five NGOs supporting pro-democracy movements, the ruling Georgian Dream party passed a new law banning foreign organizations from providing grants to local groups without regime approval. The bill is part of a broader effort to silence dissent and weaken democracy through financial repression.\ \ In Latin America, opposition leader María Corina Machado seeks to rally citizens against Nicolás Maduro’s immensely repressive regime. With the economy and currency in shambles and dozens of military personnel abandoning Maduro, Machado sees an opportunity to challenge his grip on power.
In open source news, we spotlight the release of Bitcoin Core version 29.0, the latest update to the primary software that powers the Bitcoin network and helps millions of people send, receive, and verify Bitcoin transactions every day. This release improves the reliability and compatibility of Bitcoin’s main software implementation. We also cover the unique story of LuckyMiner, an unauthorized Bitaxe clone making waves in Asian markets as demand soars for small, low-cost, home mining equipment — evidence that people want to participate in the Bitcoin network themselves.
We close with the latest edition of the HRF x Pubkey Freedom Tech Series, in which Nicaraguan human rights defender Berta Valle joins HRF’s Arsh Molu to explore how authoritarian regimes weaponize financial systems to silence dissent and isolate opposition voices and how tools like Bitcoin can offer a way out. We also feature an interview with Salvadoran opposition leader Claudia Ortiz, who discusses the erosion of civil liberties under President Nayib Bukele and offers a nuanced take on Bitcoin in the country.
Now, let’s jump right in!
SUBSCRIBE HERE
GLOBAL NEWS
Georgia | Bans Foreign Donations for Nonprofits and NGOs
Mere weeks after freezing the bank accounts of five NGOs supporting pro-democracy demonstrators in recent unrest caused by elections, Georgia’s regime passed a new law that bans foreign organizations from providing “monetary or in-kind grants” to Georgian organizations and individuals without regime approval. Introduced by the increasingly repressive Georgian Dream party, the bill is part of a broader effort (including the controversial foreign agents law passed in 2024) designed to silence dissent and dismantle pro-democracy groups. Rights groups warn these laws will cripple civil society by cutting funding and imposing heavy fines for violators. Last week, parliament also read a bill that would grant officials the power to ban opposition parties entirely. With civil society financially repressed, Georgia is sliding further into tyranny, where free expression, political opposition, and grassroots organizations are under siege.
Venezuela | Opposition Mobilizes Against Maduro’s Financial Repression
Venezuelan opposition leader María Corina Machado is intensifying efforts against Nicolás Maduro’s brutal regime by targeting what she believes are his two greatest vulnerabilities: a collapsing economy and fractures in his repressive apparatus. As the Venezuelan bolivar unravels (reaching a record low in March) and inflation spirals out of control (expected to reach 220% before the end of the year), Maduro’s regime doubles down. It imposes currency controls, expropriates private property, and exerts complete state control over banks. Meanwhile, signs of discontent are growing inside the military, with dozens of personnel reportedly deserting. “I think we have a huge opportunity in front of us, and I see that much closer today than I did a month ago,” Machado said. To rebuild Venezuela’s future, Machado sees financial freedom as essential and has publicly embraced Bitcoin as a tool to resist the regime’s weaponization of money.
India | UPI Outage Disrupts Payments Nationwide
Digital transactions across India were disrupted mid-April as the Unified Payments Interface (UPI) experienced its third major outage in the last month. UPI is a government-run system that enables digital payments and underpins India’s push towards a cashless, centralized economy. Fintechs, banks, and institutions plug into UPI as a backbone of their digital infrastructure. Recently, India started integrating its central bank digital currency (CBDC), the digital rupee, into UPI, leveraging its existing network effect to expand the reach of state-issued digital money. When a single outage can freeze an entire nation’s ability to transact, it reveals the fragility of centralized infrastructure. By contrast, decentralized money like Bitcoin operates independently of state-run systems and with consistent uptime, giving users the freedom to transact and save permissionlessly.
China | Bitcoin for Me, Not for Thee
China is debating new regulations for handling its growing trove of Bitcoin and other digital assets seized during criminal investigations. While the regime debates how to manage its seized digital assets, the trading of Bitcoin and other digital assets remains banned for Chinese citizens on the mainland. Reports indicate that local governments have quietly sold confiscated Bitcoin and other digital assets through private companies to bolster their dwindling budgets. If true, this exposes the hypocrisy of a regime banning digital assets for its people while exploiting them as a strategic revenue source for the state. This contradiction accentuates the ways authoritarian regimes manipulate financial rules for their own benefit while punishing the public for using the same strategies.
Serbia | Vučić Targets Civil Society as Economy Sinks
As Serbia’s economy stalls and the cost of living remains stubbornly high, President Aleksandar Vučić is escalating his crackdown on civil society to deflect blame and tighten control. After a train station canopy collapse in Novi Sad killed 16 people last November, protests erupted. Serbians, led by students, flooded the streets to protest government corruption, declining civil liberties, and a worsening economy. The protests have since spread across 400 cities, reflecting nationwide discontent. In response, Vučić is now targeting civil society organizations under the pretext of financial misconduct. Law enforcement raided four NGOs that support Serbians’ human rights, the rule of law, and democratic elections.
Russia | Jails Four Journalists for Working With Navalny
A Russian court sentenced four independent Russian journalists to five and a half years in prison for working with the Anti-Corruption Foundation (ACF) — a pro-democracy organization founded by the late opposition leader Alexei Navalny. The journalists — Antonina Favorskaya, Konstantin Gabov, Sergei Karelin, and Artyom Kriger — were convicted in a closed-door trial for associating with an organization the Kremlin deems an “extremist.” The Committee to Protect Journalists condemned the verdict as a “blatant testimony to Russian authorities’ profound contempt for press freedom.” Since it launched a full-scale invasion of Ukraine in 2022, the Kremlin has increasingly criminalized dissent and financially repressed opposition, nonprofits, and ordinary citizens.
BITCOIN AND FREEDOM TECH NEWS
Flash | Introduces Flash Lightning Addresses, New UI, and Encrypted Messaging
Flash, a Bitcoin Lightning wallet and HRF grantee bringing freedom money to the Caribbean, released its version 0.4.0 beta. This release includes an updated user interface, dedicated Flash Lightning addresses (user @ flashapp.me), and encrypted messaging. The redesigned app is more user-friendly and better suited for users new to Bitcoin. Flash users now receive a verified Lightning address, making it easier to send and receive Bitcoin. The update also adds encrypted nostr messaging, enabling secure communication between users. As authoritarian regimes in the region, like Cuba, tighten control over money, Flash offers a practical and private solution for Bitcoin access.
DahLIAS | New Protocol to Lower the Cost of Private Bitcoin Transactions
Bitcoin developers recently announced DahLIAS, the first protocol designed to enable full cross-input signature aggregation (CISA). CISA is a proposed Bitcoin update that could make private Bitcoin transactions much cheaper. Right now, collaborative transactions are more expensive than typical transactions because each input in a transaction needs its own signature. CISA would allow those signatures to be combined, saving space and reducing fees. But this change would require a soft fork, a safe, backward-compatible software update to Bitcoin’s code. If adopted, CISA could remove the need for users to justify why they want privacy, as the answer would be, to save money. This is especially important for dissidents living under surveillant regimes. DahLIAS could be a breakthrough that helps make privacy more practical for everyone using Bitcoin.
Bitcoin Core | Version 29.0 Now Available for Node Runners
Bitcoin Core is the main software implementation that powers the Bitcoin network and helps millions of people send, receive, and verify transactions every day. The latest update, Bitcoin Core v29.0, introduces changes to improve network stability and performance. The release helps keep the network stable even when not everyone updates simultaneously. Further, it reduces the chances that nodes (computers that run the Bitcoin software) accidentally restart — an issue that can interrupt network participation. It also adds support for full Replace-by-Fee (RBF), allowing users to increase the fee on stuck transactions in times of high network demand. Enhancing Bitcoin’s reliability, usability, and security ensures that individuals in oppressive regimes or unstable financial systems can access a permissionless and censorship-resistant monetary network. Learn more about the update here.
Nstart | Releases Multilingual Support
Nstart, a new tool that simplifies onboarding to nostr — a decentralized and censorship-resistant social network protocol — released multilingual support. It added Spanish, Italian, French, Dutch, and Mandarin as languages. This update broadens access by making the onboarding experience available to a wider audience — especially those living under dictatorships across Africa, Latin America, and Asia, where communication and press freedom are heavily restricted. Users can even contribute translations themselves. Overall, multilingual support makes Nstart a more powerful tool for activists and organizations operating under authoritarian environments, offering guided, straightforward access to uncensorable communications.
Bitcoin Chiang Mai | Release Bitcoin Education Podcast
Bitcoin Chiang Mai, a grassroots Bitcoin community in Thailand, launched an educational podcast to teach Bitcoin in Thai. In a country where financial repression is on the rise and the regime is experimenting with a programmable central bank digital currency (CBDC), this podcast offers an educational lifeline. By making Bitcoin knowledge and tools more accessible, the show empowers Thais to explore alternatives to state-controlled financial systems. It’s a grassroots effort to preserve financial freedom and encourage open dialogue in an increasingly controlled economic environment. Check it out here.
LuckyMiner | Undisclosed Bitaxe Clone Gaining Popularity in Asia
LuckyMiner, a Bitcoin mining startup out of Shenzhen, China is shaking up Asia’s Bitcoin hardware scene with a rogue twist. What began as a hobby project in 2023 has since exploded into a full-scale operation, manufacturing and selling thousands of undisclosed Bitaxe clones (which are small, affordable bitcoin miners based on the Bitaxe design). While Bitaxe is open-source, it’s licensed under CERN-OHL-S-2.0, requiring any modifications to be made public. LuckyMiner ignored that rule and the founder has openly admitted to breaking the license. Despite that, LuckyMiner is succeeding anyway, fueled by growing demand for affordable home mining equipment. While controversial, the rise of low-cost miners signals grassroots interest in Bitcoin, especially at a time when Asia grapples with growing authoritarianism and financial repression.
RECOMMENDED CONTENT
HRF x Pubkey — Bitcoin as a Tool to Fight Financial Repression in Autocracies with Berta Valle
In the latest HRF x Pubkey Freedom Tech series, Nicaraguan human rights defender and journalist Berta Valle joins HRF’s Arsh Molu to discuss how Bitcoin empowers individuals to resist the financial repression of authoritarian regimes. From helping families receive remittances when bank accounts are frozen to enabling independent media and activists to fund their work without regime interference, Bitcoin is quietly reshaping what resistance can look like under tyranny. Watch the full fireside chat here.
Claudia Ortiz: A Voice of Opposition in Bukele’s El Salvador
In this interview, analyst and journalist Marius Farashi Tasooji speaks to Salvadoran opposition leader Claudia Ortiz about President Bukele’s consolidation of power, the erosion of civil liberties, and the future of Bitcoin in the country. While Ortiz acknowledges Bitcoin’s potential as a tool for freedom, she critiques the current administration’s opaque and heavy-handed implementation of it. Ortiz explains her opposition to the Bitcoin Law, citing concerns about transparency and accountability, and outlines what she would do differently if elected president. Watch the full conversation here.
If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.\ Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
-
 @ e4950c93:1b99eccd
2025-04-24 12:07:49
@ e4950c93:1b99eccd
2025-04-24 12:07:49Heureu-x-se d’avoir trouvé une information utile sur ce site ?
Soutenez le projet en faisant un don pour le faire vivre et remercier les contribut-eur-rice-s.
En bitcoin
-
Sur la blockchain : bc1qkm8me8l9563wvsl9sklzt4hdcuny3tlejznj7d
-
Réseau lightning : ⚡️
origin-nature@coinos.ioVous pouvez aussi nous soutenir de manière récurrente 👉 Créer un paiement Lightning récurrent
En euros, dollars, ou toute autre monnaie prise en charge
-
Par virement, IBAN : FR76 2823 3000 0144 3759 8717 669
-
Vous pouvez aussi nous soutenir de manière récurrente 👉 Faire une promesse sur LiberaPay
Contactez-nous si vous souhaitez faire un don avec toute autre cryptomonnaie.
💡 Un modèle de partage de la valeur
La moitié des dons est redistribuée aux contribut-eur-rice-s qui créent la valeur du site, pour expérimenter un modèle de partage de revenus sur Internet — un modèle qui respecte vos données et ne cherche pas à capter votre attention. L’autre moitié permet de couvrir les frais de fonctionnement du site.
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
-
 @ 8671a6e5:f88194d1
2025-04-24 07:23:19
@ 8671a6e5:f88194d1
2025-04-24 07:23:19For whoever has, will be given more, and they will have an abundance. Whoever does not have, even what they have will be taken from them.
Matthew 25:29, The Parable of the Talents (New Testament)For whoever has, will be given more,\ and they will have an abundance.\ Whoever does not have, even what\ they have will be taken from them.\ \ Matthew 25:29,\ The Parable of the Talents (New Testament)

How the Pump-my-bags mentality slows Bitcoin adoption
The parable of “thy Bitcoins” (loosely based on Matthew 25:29)
A man, embarking on a journey, entrusted his wealth to his servants. To one he gave five Bitcoin, to another two Bitcoin, and to another one Bitcoin, each according to his ability. Then he departed.
The servant with five Bitcoin buried his master’s wealth, dreaming of its rising price. The servant with two Bitcoin hid his, guarding its value. But the servant with one Bitcoin acted with vision. He spent 0.5 Bitcoin to unite Bitcoiners, teaching them to use the network and building tools to expand its reach. His efforts grew Bitcoin’s power, though his investment left him with only 0.5 Bitcoin.
Years later, the master returned to settle accounts. The servant with five Bitcoin said, “Master, you gave me five Bitcoin. I buried them, and their price has soared. Here is yours.”
The master replied, “Faithless servant! My wealth was meant to sow freedom. You kept your Bitcoin but buried your potential to strengthen its network. Your wealth is great, but your impact is none!”
The servant with two Bitcoin said, “Master, you gave me two Bitcoin. I hid them, and their value has risen. Here is yours.”
The master replied, “You, too, have been idle! You clung to wealth but failed to spread Bitcoin’s truth. Your Bitcoin endures, but your reach is empty!”
Then the servant with one Bitcoin stepped forward. “Master, you gave me one Bitcoin. I spent 0.5 Bitcoin to teach and build with Bitcoiners. My call inspired many to join the network, though I have only 0.5 Bitcoin left.”
The master said, “Well done, faithful servant! You sparked a movement that grew my network, enriching lives. Though your stack is small, your vision is vast. Share my joy!”
When many use their gifts to build Bitcoin’s future, their sacrifices grow the network and enrich lives. Those who “bury” their Bitcoin and do nothing else keep wealth but miss the greater reward of a thriving in a Bitcoin world.
This parable reflects a timeless truth: between playing it safe and building, resides the choice to take risk. Bitcoin’s power lies not in hoarding wealth (although it’s part of it), but mainly in using it to build a freer world. To free people from their confines. Yet a mentality has taken hold — one that runs counter to that spirit.
PMB betrays the Bitcoin ethos
“Pump my bags” (PMB) stems from the altcoin world, where scammers pump pre-mined coins to dump on naive buyers. In Bitcoin, PMB isn’t about dumping but about hoarding—stacking sats without lifting a finger. These Bitcoiners, from small holders to whales, sit back, eyeing fiat profits, not Bitcoin’s mission. They’re not so different from altcoin grifters. Both chase profit, not glory. They dream of fiat-richness and crappy real estate in Portugal or Chile — not a Bitcoin standard. One holds hard money by chance, the other a fad coin. Neither moves the world forward.
In Bitcoin, the pump-my-bags mindset is more about laziness; everyone looking out for themselves, stacking without ever lifting a finger. There’s a big difference in the way an altcoin promotor would operate and market yet another proof-of-stake pre-mined trashcoin, and how PMB bitcoiners hoard and wait.
They’re much alike however. The belief level might be slightly different, and not everyone has the same ability.
I’ve been in Bitcoin’s trenches since its cypherpunk days, when it was a rebellion against fiat’s centralized control. Bitcoin is a race against the totalitarian fiat system’s grip. Early adopters saw it as a tool to dismantle gatekeepers and empower individuals. But PMB has turned Bitcoin into a get-rich scheme, abandoning the collective effort needed to overthrow fiat’s centuries-long cycles.
Trust is a currency’s core. Hoarding Bitcoin shows trust in its future value, but it’s a shallow trust that seals it away from the world. Real trust comes from admiring Bitcoin’s math, building businesses around it, or spreading its use. PMB Bitcoiners sit on their stacks, expecting others to build trust for them. Newcomers see branding, ego, and grifters, not the low-tech prosperity Bitcoin can offer. PMB Bitcoiners live without spending a sat, happy to hodl. Fine, but they’re furniture in fiat’s ruins, not builders of Bitcoin’s future.
Hoarding hollow victories Hoarding works for those chasing fiat wealth. Bitcoin is even there for them. The lazy, the non-believers, the ones that sold very early, the ones that just started.
By 2021, 75% of Bitcoin sat dormant, driving scarcity and prices up. But it strangles transactions, weakening Bitcoin as a living economy. Reddit calls hoarding “Bitcoin’s most dangerous problem,” choking adoption for profit. Pioneers like Roger Ver built tech companies (where you could buy electronics for bitcoin), Mark Karpelès ran an exchange (Mt. Gox) and Charlie Shrem processed 30% of Bitcoin transactions in 2013. They poured stacks into adoption, people like them (even people you’ve never heard of) more than not, went broke doing the building while hoarders sat back. The irony stings: Bitcoin’s founders are often poorer than PMB hodlers who buried their talents and just sat there passively. Over the years, the critique from these sideline people became more prevalent. They show up here and there, to read the room. But that’s all they do.
The last couple of years, they even became more vocal with social media posts. Everything needs to be perfect, high-quality, not made by them, not funded by them, for free, without ads, and with no effort whatsoever, unless it’s NOT pumping their bags, then it needs to be burned down as fast as possible.
Today’s PMB Bitcoiners want the rewards without the risk. They stack sats, demand perfect content made by others for free, and cheer short-term price pumps. But when asked to build, code, or fund anything real, they disappear. At this point, such Bitcoiners have as much spine as a pack of Frankfurter sausages. This behavior has hollowed out Bitcoin’s activist core.
Activism’s disappointment
Bitcoin’s activist roots—cypherpunks coding, evangelists spreading the word—have been replaced by influencers and silent PMB conference-goers who say nothing but “I hold Bitcoin.” Centralized exchanges like Binance and Coinbase handle 70% of trades by 2025, mocking our decentralized vision. Custodial wallets proliferate as users hand over keys. The Lightning Network has 23,000+ nodes, and privacy tech like CoinJoin exists, yet adoption lags. Regulation creeps in—the U.S. Digital Asset Anti-Money Laundering Act of 2023 and Europe’s MiCa laws threaten KYC on every wallet. Our failure to advance faster gives governments leverage. Our failure would be their victory. Their cycles endlessly repeated.
Activism is a shadow of its potential. The Human Rights Foundation pushes Bitcoin for dissidents, but it’s a drop in the bucket. We could replace supply chains, build Bitcoin-only companies, or claim territories, yet we can’t even convince bars to accept
Bitcoin. We’re distracted by laser-eye memes and altcoin hopium, not building at farmer’s markets, festivals, or local scenes. PMB Bitcoiners demand perfection—free, ad-free, high-quality content—while contributing nothing.
The best way to shut them up, is asking them to do something. ”I would like to see a live counter on that page, so I can see what customers got new products” ”Why don’t YOU write code?” … and they’re gone.
”I would change a few items in your presentation man, it was good, but I would change the diagram on page 7” ”The presentation is open source and online, open for contributions. Do you want to give the presentation next time?” ”… “ and they’re gone.
”We need to have a network of these antennas to communicate with each other and send sats” ”I’ve ordered a few devices like that.. want to help out and search for new network participants?” ” … “ They’re off to some other thing, that’s more entertaining.
If you don’t understand you’re in a very unique fork in the road, a historic shift in society, much so that you’re more busy with picking the right shoes, car, phone, instead of pushing things in the right direction. And guess what? Usually these two lifestyles can even be combines. Knights in old England could fight and defend their king, while still having a decent meal and participate in festivities. These knight (compared to some bitcoiners) didn’t sit back at a fancy dinner and told the others: “yeah man, you should totally put on a harness, get a sword made and fight,… here I’ll give you a carrot for your horse.” To disappear into their castles waiting for the fight to be over a few months later. No, they put on the harness themselves, and ordered a sword to be made, because they knew their own future and that of their next of kin was at stake.
Hardly any of them show you that Bitcoin can be fairly simple and even low-tech solutions for achieving remedies for the world’s biggest problems (having individuals have real ownership for example). It can include some genuine building of prosperity and belief in one’s own talents and skills. You mostly don’t need middlemen. They buy stuff they don’t need, to feel like they’re participants.
And there’s so, enormously much work to be done.
On the other hand. Some bitcoiners can live their whole life without spending any considerable amount of bitcoin, and be perfectly happy. They mind as well could have had no bitcoin at all, but changed their mindset towards a lot of things in life. That’s cool, I know bitcoiners that don’t have any bitcoin anymore. They still “get it” though. Everyone’s life is different. These people are really cool, and they’re usually the silent builders as well. They know.
And yet, people will say they’ve “missed out”. They surely missed out on buying a lot of nice “stuff” … maybe. There are always new luxury items for sale in the burning ruins of fiat. There are always people that want to temporarily like or love you (long time) for fiat, as well as for bitcoin. You’re still an empty shell if your do. Just like the fiat slaves. A crypto bro will always stay the same sell out, even if he holds bitcoin by any chance.
You know why? Because bitcoiners don’t think like “they” do. The fiat masters that screwed this world up, think and work over multi generations. (Remember that for later, in piece twelve of this series.)
The only path forward
Solo heroics can’t beat the market or drive adoption anymore. Collective action is key. The Lightning Network grows from thousands of small nodes for example. Bitcoin Core thrives on shared grit. Profit isn’t sportcars — it’s a thriving network freeing people. If 10,000 people spend 0.05 BTC to fund wallets, educate merchants or build tools, we’d see more users and transactions. Adoption drives demand. Sacrifice now, impact later. Don’t work for PMB orders — they’re fiat victims, not Bitcoin builders.
Act together, thrive together
To kill PMB, rediscover your potential, even if it costs you:
Educate wide: Teach Bitcoin’s truth—how it works, why it matters. Every convert strengthens us.
Build together: Run nodes, fund Lightning hubs, support devs. Small contributions add up.
Use Bitcoin: Spend it, gift it, make it move. Transactions are the network’s heartbeat.
Value the mission: Chase freedom, not fiat. Your legacy is impact, not your stack.
A call to build The parable of Bitcoin is clear: hoard and get rich, but leave nothing behind; act together, sacrifice wealth, and build a thriving Bitcoin world. Hoarding risks a deflationary spiral while Wall Street grabs another 100,000 BTC every few weeks and sits on it for other fund managers to buy the stake (pun intended).
PMB Bitcoiners will cash out, thinking they’re smart, trading our future for fiat luxury. Bitcoin’s value lies in trust, scarcity, and a network grown by those who see beyond their wallets. Bury your Bitcoin or build with it.
If someone slyly nudges you to pump their bags, call them faithless leeches who ignore the call for a better world. They’re quiet, polite, and vanish when it’s time to fund or build. They tally fiat gains while you grind through life’s rot. They sling insults if you educate, risk, or create. They’re all take, no give — enemies, even if they hold Bitcoin.
Bitcoiners route around problems. Certainly if that problem is other bitcoiners. Because we know how they think, we know their buried talents, we know why they do it. It’s in our DNA to know. They don’t know why we keep building however, the worse of them don’t understand.
Bitcoin’s value isn’t in scarcity alone — it’s in the combination of trust, scarcity and the network, grown by those who see beyond their wallets and small gains.
Whether you’ve got 0.01 BTC or 10,000 BTC, your choice matters. Will you bury your Bitcoin, or build with it? I can hope we choose the latter.
If someone, directly or slyly, nudges you to pump their bags, call them out as faithless servants who wouldn’t even hear the calling of a better world. These types are often quiet, polite, and ask few questions, but when it’s time to step up, they vanish — nowhere to be found for funding, working, or doing anything real, big or small. They’re obsessed with “pump my bags,” tallying their fiat gains while you grind, sweat, and ache through life’s rotten misery. Usually they’re well off, because fiat mentality breeds more fiat.
They won’t lift you up or support you, because they’re all about the “take” and take and take more, giving nice sounding incentives to keep you pumping and grinding. They smell work, but never participate. They’re lovely and nice as long as you go along and pump.
Pump-My-Bags bitcoiners are temporary custodians, financial Frankfurter sausages hunting for a bun to flop into. We have the mustard. We know how to make it, package it and pour it over them. We’re the preservers of hard money. We build, think and try.
They get eaten. They’re fiat-born and when the real builders rise (they’re already a few years old), history won’t remember these people’s stacks and irrelevant comments — only our sacrifices.
by: AVB
-
 @ d34e832d:383f78d0
2025-04-24 07:22:54
@ d34e832d:383f78d0
2025-04-24 07:22:54Operation
This operational framework delineates a methodologically sound, open-source paradigm for the self-custody of Bitcoin, prominently utilizing Electrum, in conjunction with VeraCrypt-encrypted USB drives designed to effectively emulate the functionality of a cold storage hardware wallet.
The primary aim of this initiative is to empower individual users by providing a mechanism that is economically viable, resistant to coercive pressures, and entirely verifiable. This is achieved by harnessing the capabilities inherent in open-source software and adhering to stringent cryptographic protocols, thereby ensuring an uncompromising stance on Bitcoin sovereignty.
The proposed methodology signifies a substantial advancement over commercially available hardware wallets, as it facilitates the creation of a do-it-yourself air-gapped environment that not only bolsters resilience and privacy but also affirms the principles of decentralization intrinsic to the cryptocurrency ecosystem.
1. The Need For Trustless, Private, and Secure Storage
With Bitcoin adoption increasing globally, the need for trustless, private, and secure storage is critical. While hardware wallets like Trezor and Ledger offer some protection, they introduce proprietary code, closed ecosystems, and third-party risk. This Idea explores an alternative: using Electrum Wallet within an encrypted VeraCrypt volume on a USB flash drive, air-gapped via Tails OS or offline Linux systems.
2. Architecture of the DIY Hardware Wallet
2.1 Core Components
- Electrum Wallet (SegWit, offline mode)
- USB flash drive (≥ 8 GB)
- VeraCrypt encryption software
- Optional: Tails OS bootable environment
2.2 Drive Setup
- Format the USB drive and install VeraCrypt volumes.
- Choose AES + SHA-512 encryption for robust protection.
- Use FAT32 for wallet compatibility with Electrum (under 4GB).
- Enable Hidden Volume for plausible deniability under coercion.
3. Creating the Encrypted Environment
3.1 Initial Setup
- Download VeraCrypt from the official site; verify GPG signatures.
- Encrypt the flash drive and store a plain Electrum AppImage inside.
- Add a hidden encrypted volume with the wallet seed, encrypted QR backups, and optionally, a decoy wallet.
3.2 Mounting Workflow
- Always mount the VeraCrypt volume on an air-gapped computer, ideally booted into Tails OS.
- Never connect the encrypted USB to an internet-enabled system.
4. Air-Gapped Wallet Operations
4.1 Wallet Creation (Offline)
- Generate a new Electrum SegWit wallet inside the mounted VeraCrypt volume.
- Record the seed phrase on paper, or store it in a second hidden volume.
- Export xpub (public key) for use with online watch-only wallets.
4.2 Receiving Bitcoin
- Use watch-only Electrum wallet with the exported xpub on an online system.
- Generate receiving addresses without exposing private keys.
4.3 Sending Bitcoin
- Create unsigned transactions (PSBT) in the watch-only wallet.
- Transfer them via QR code or USB sneakernet to the air-gapped wallet.
- Sign offline using Electrum, then return the signed transaction to the online device for broadcast.
5. OpSec Best Practices
5.1 Physical and Logical Separation
- Use a dedicated machine or a clean Tails OS session every time.
- Keep the USB drive hidden and disconnected unless in use.
- Always dismount the VeraCrypt volume after operations.
5.2 Seed Phrase Security
- Never type the seed on an online machine.
- Consider splitting the seed using Shamir's Secret Sharing or metal backup plates.
5.3 Coercion Resilience
- Use VeraCrypt’s hidden volume feature to store real wallet data.
- Maintain a decoy wallet in the outer volume with nominal funds.
- Practice your recovery and access process until second nature.
6. Tradeoffs vs. Commercial Wallets
| Feature | DIY Electrum + VeraCrypt | Ledger/Trezor | |--------|--------------------------|---------------| | Open Source | ✅ Fully | ⚠️ Partially | | Air-gapped Usage | ✅ Yes | ⚠️ Limited | | Cost | 💸 Free (except USB) | 💰 $50–$250 | | Hidden/Coercion Defense | ✅ Hidden Volume | ❌ None | | QR Signing Support | ⚠️ Manual | ✅ Some models | | Complexity | 🧠 High | 🟢 Low | | Long-Term Resilience | ✅ No vendor risk | ⚠️ Vendor-dependent |
7. Consider
A DIY hardware wallet built with Electrum and VeraCrypt offers an unprecedented level of user-controlled sovereignty in Bitcoin storage. While the technical learning curve may deter casual users, those who value security, privacy, and independence will find this setup highly rewarding. This Operation demonstrates that true Bitcoin ownership requires not only control of private keys, but also a commitment to operational security and digital self-discipline. In a world of growing surveillance and digital coercion, such methods may not be optional—they may be essential.
8. References
- Nakamoto, Satoshi. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008.
- Electrum Technologies GmbH. “Electrum Documentation.” electrum.org, 2024.
- VeraCrypt. “Documentation.” veracrypt.fr, 2025.
- Tails Project. “The Amnesic Incognito Live System (Tails).” tails.boum.org, 2025.
- Matonis, Jon. "DIY Cold Storage for Bitcoin." Forbes, 2014.
In Addition
🛡️ Create Your Own Secure Bitcoin Hardware Wallet: Electrum + VeraCrypt DIY Guide
Want maximum security for your Bitcoin without trusting third-party devices like Ledger or Trezor?
This guide shows you how to build your own "hardware wallet" using free open-source tools:
✅ Electrum Wallet + ✅ VeraCrypt Encrypted Flash Drive — No extra cost, no vendor risk.Let Go Further
What You’ll Need
- A USB flash drive (8GB minimum, 64-bit recommended)
- A clean computer (preferably old or dedicated offline)
- Internet connection (for setup only, then go air-gapped)
- VeraCrypt software (free, open-source)
- Electrum Bitcoin Wallet AppImage file
Step 1: Download and Verify VeraCrypt
- Go to VeraCrypt Official Website.
- Download the installer for your operating system.
- Verify the GPG signatures to ensure the download isn't tampered with.
👉 [Insert Screenshot Here: VeraCrypt download page]
Pro Tip: Never skip verification when dealing with encryption software!
Step 2: Download Electrum Wallet
- Go to Electrum Official Website.
- Download the Linux AppImage or Windows standalone executable.
- Again, verify the PGP signatures published on the site. 👉 [Insert Screenshot Here: Electrum download page]
Step 3: Prepare and Encrypt Your USB Drive
- Insert your USB drive into the computer.
- Open VeraCrypt and select Create Volume → Encrypt a Non-System Partition/Drive.
- Choose Standard Volume for now (later we'll talk about hidden volumes).
- Select your USB drive, set an extremely strong password (12+ random characters).
- For Encryption Algorithm, select AES and SHA-512 for Hash Algorithm.
- Choose FAT32 as the file system (compatible with Bitcoin wallet sizes under 4GB).
- Format and encrypt. 👉 [Insert Screenshot Here: VeraCrypt creating volume]
Important: This will wipe all existing data on the USB drive!
Step 4: Mount the Encrypted Drive
Whenever you want to use the wallet:
- Open VeraCrypt.
- Select a slot (e.g., Slot 1).
- Click Select Device, choose your USB.
- Enter your strong password and Mount. 👉 [Insert Screenshot Here: VeraCrypt mounted volume]
Step 5: Set Up Electrum in Offline Mode
- Mount your encrypted USB.
- Copy the Electrum AppImage (or EXE) onto the USB inside the encrypted partition.
- Run Electrum from there.
- Select Create New Wallet.
- Choose Standard Wallet → Create New Seed → SegWit.
- Write down your 12-word seed phrase on PAPER.
❌ Never type it into anything else. - Finish wallet creation and disconnect from internet immediately. 👉 [Insert Screenshot Here: Electrum setup screen]
Step 6: Make It Air-Gapped Forever
- Only ever access the encrypted USB on an offline machine.
- Never connect this device to the internet again.
- If possible, boot into Tails OS every time for maximum security.
Pro Tip: Tails OS leaves no trace on the host computer once shut down!
Step 7: (Optional) Set Up a Hidden Volume
For even stronger security:
- Repeat the VeraCrypt process to add a Hidden Volume inside your existing USB encryption.
- Store your real Electrum wallet in the hidden volume.
- Keep a decoy wallet with small amounts of Bitcoin in the outer volume.
👉 This way, if you're ever forced to reveal the password, you can give access to the decoy without exposing your true savings.
Step 8: Receiving Bitcoin
- Export your xpub (extended public key) from the air-gapped Electrum wallet.
- Import it into a watch-only Electrum wallet on your online computer.
- Generate receiving addresses without exposing your private keys.
Step 9: Spending Bitcoin (Safely)
To send Bitcoin later:
- Create a Partially Signed Bitcoin Transaction (PSBT) with the online watch-only wallet.
- Transfer the file (or QR code) offline (via USB or QR scanner).
- Sign the transaction offline with Electrum.
- Bring the signed file/QR back to the online device and broadcast it.
✅ Your private keys never touch the internet!
Step 10: Stay Vigilant
- Always dismount the encrypted drive after use.
- Store your seed phrase securely (preferably in a metal backup).
- Regularly practice recovery drills.
- Update Electrum and VeraCrypt only after verifying new downloads.
🎯 Consider
Building your own DIY Bitcoin hardware wallet might seem complex, but security is never accidental — it is intentional.
By using VeraCrypt encryption and Electrum offline, you control your Bitcoin in a sovereign, verifiable, and bulletproof way.⚡ Take full custody. No companies. No middlemen. Only freedom.
-
 @ 57c631a3:07529a8e
2025-04-24 14:28:40
@ 57c631a3:07529a8e
2025-04-24 14:28:40Painting by Early Fern, shared by Marine Eyes
It is difficult to get the news from poems yet men die miserably every day for lack of what is found there.—William Carlos Williams
April, the month Eliot famously deemed the cruelest, is kindest to poetry. It’s when we nationally awaken to poetry’s efforts to capture the human experience in all its messy contradictions, leaning into uncertainty and wonder and bringing readers along for the ride.
Williams’s adage pairs beautifully with Ezra Pound’s assertion that “Poetry is news that stays news.” Poetry* gives readers the most immediate and urgent hotline to feeling. Big emotions turn us instinctively, like human sunflowers, toward poems, which are singularly compact vehicles for thinking and feeling. They have a knack for distilling our existential questions and putting all that wondering to music—after all, the term lyric poetry comes from the lyre,* which accompanied the recitation of poetry in antiquity.
On Substack, poets shed the constraints of traditional publishing timelines, sharing works in progress and experimenting in real time. What arises isn’t just a collection of newsletters but a living anthology of established voices and emerging talents in conversation with one another and their readers. If you’re still not convinced that poetry is for you (it is!), I created a primer of Poems for Those Who Don’t “Get” Poetry. But beyond that gateway, Substack presents countless paths to discover the poems that will speak directly to you—from translation projects that breathe new life into ancient verse to craft discussions that demystify the process. Allow me to introduce you to a few of my favorites.
Poetry in progress
Quiddity: a word I love. It means “the inherent nature or essence of someone or something.” The you-ness of you. That is what the best poets translate through their writing—formal or free verse, ruminative or praising, expansive or brief. It’s the way one listens to the singular voice channeled through them** and delivers that voice alive on the page.
This is the foundation for the widest category of poetry on Substack. No two posts are alike: you might get the intimacy of seeing work that could later make its way into books, hearing poets muse about their writing lives, or watching notes and fragments coalesce into longer lyric explorations.
is one of the best-known poets on Substack, offering devoted readers a mix of never-before-seen work and poems from past collections. And his commitment to Substack’s potential as a propagator of new writing is especially inspiring to emerging writers.
Being witness to commitment and experimentation, that magical balance between discipline and freedom to explore, is riveting. I so admire , translator and former Random House editor ’s long-standing project to chronicle daily life:
Text within this block will maintain its original spacing when published4.11.25
what I so desired I can’t have
thank you blessed stars
Andrea Gibson’s gorgeously smart features videos of the poet reciting their work and contemplating illness, resilience, and the role that poetry plays in capturing duress, heartbreak, and hope. Here they are reading their poem “What Love Is”:
I was thrilled to see former U.S. Poet Laureate Tracy K. Smith join Substack recently. She’s already sharing poems, works in progress, and essays. Hear her reading a new poem, “I Don’t Believe in Doom,” here:
Then there’s , an ambitious translation project by , a writer dedicated to bringing these ancient poems from the Tang Dynasty (618-907) to a contemporary audience. Hyun Woo translates one poem from the collection every week. Here’s one of my favorites, number 55:
The Farewell to Those Who Will Stay at a Tavern of JinlingThe wind blows the willow flowers, filling the inn with fragrance;The ladies of Wu press the liquor, calling to the guests to try.The young men of Jinling come and see each other off;Those who will go, those who will not, each empty his goblet.I invite you to ask the water flowing east, to test it:Which is short and which is long, the thoughts of farewell or itself?
Curators and craft
The poet-as-curator offers us an assortment of poems organized by their own idiosyncratic logic. It’s like receiving the perfect mixtape: songs you’ve known and loved for years, and others you’re grateful to discover for the first time. Chances are good that within any given roundup, at least one poem will speak to you, introducing you to a new voice.
’s is one of my go-tos. He has a phenomenal reader’s eye for juxtapositions that span ages, styles, and modes, creating unexpected—and delightful—tensions and correspondences. His thematic roundups extend far beyond expected subjects like love and death to more nuanced territories like therapy (“This is progress”) and mood (“Puff out the hot-air balloon now”). Through Sean, I was reminded to revisit one of my favorite Audre Lorde poems:
Shared in “This is progress” by Sean Singer
In my own newsletter, , I do something similar: curating Poems for Your Weekend around themes that serve as a prescription for your mind or soul, while exploring how neuroscience and mindset can help us live more sustainable and enriching artistic lives. Through it all, I write about the role of wonder in poetry, the subject of my PhD.
For subtle close readings of poems through the lens of life rather than the ivory tower, I turn to ’s , with its deeply thoughtful essays on the poems he selects each week. His recent post on the poems of Linda Pastan includes this gorgeous poem from Insomnia:
Imaginary ConversationText within this block will maintain its original spacing when publishedYou tell me to live each day as if it were my last. This is in the kitchen where before coffee I complain of the day ahead—that obstacle race of minutes and hours, grocery stores and doctors.
But why the last? I ask. Why not live each day as if it were the first— all raw astonishment, Eve rubbing her eyes awake that first morning, the sun coming up like an ingénue in the east?
You grind the coffee with the small roar of a mind trying to clear itself. I set the table, glance out the window where dew has baptized every living surface.
I love Devin’s remarks: “why the last is the kind of question I adore, a question that does not assume it knows what we are supposedly supposed to know, a question that mirthfully pushes back against the world, and wonders aloud about astonishment in the face of certainty.”
For those interested in craft, literary powerhouse recently joined Substack and is already offering excellent writing exercises, as helpful for readers hoping to understand poetry as for poets creating their own. His Exercise 036: Begin with the End introduced even this poetry veteran to a new term: anadiplosis! is a resource-rich space, featuring interviews, classes, craft essays, and more. A large group of poets and readers has gathered to take advantage, creating a vibrant community. And a special shoutout in this section to , a poet whose candid essays on navigating both the publishing and dating world as a woman are their own kind of education on living more bravely and authentically.
Final thoughts
Whether encountered in an anthology or a newsletter, poems remind us of what Williams knew: that vital truths exist within their lines that we can find nowhere else. And there’s a special joy in reading them on Substack, where poets find renewed pleasure in publishing on their own terms, and where readers can witness the process and join the discussion. The digital format extends poetry’s reach, bringing these voices to new audiences who might not normally encounter them. Here, poets and readers are participating in poetry’s oldest tradition: the passing of essential truths from one human heart to another. I hope you’ll join us. https://connect-test.layer3.press/articles/4e5d2cee-8bd4-4fb0-9331-48bbeded3a47
-
 @ d34e832d:383f78d0
2025-04-24 06:28:48
@ d34e832d:383f78d0
2025-04-24 06:28:48Operation
Central to this implementation is the utilization of Tails OS, a Debian-based live operating system designed for privacy and anonymity, alongside the Electrum Wallet, a lightweight Bitcoin wallet that provides a streamlined interface for secure Bitcoin transactions.
Additionally, the inclusion of advanced cryptographic verification mechanisms, such as QuickHash, serves to bolster integrity checks throughout the storage process. This multifaceted approach ensures a rigorous adherence to end-to-end operational security (OpSec) principles while simultaneously safeguarding user autonomy in the custody of digital assets.
Furthermore, the proposed methodology aligns seamlessly with contemporary cybersecurity paradigms, prioritizing characteristics such as deterministic builds—where software builds are derived from specific source code to eliminate variability—offline key generation processes designed to mitigate exposure to online threats, and the implementation of minimal attack surfaces aimed at reducing potential vectors for exploitation.
Ultimately, this sophisticated approach presents a methodical and secure paradigm for the custody of private keys, thereby catering to the exigencies of high-assurance Bitcoin storage requirements.
1. Cold Storage Refers To The offline Storage
Cold storage refers to the offline storage of private keys used to sign Bitcoin transactions, providing the highest level of protection against network-based threats. This paper outlines a verifiable method for constructing such a storage system using the following core principles:
- Air-gapped key generation
- Open-source software
- Deterministic cryptographic tools
- Manual integrity verification
- Offline transaction signing
The method prioritizes cryptographic security, software verifiability, and minimal hardware dependency.
2. Hardware and Software Requirements
2.1 Hardware
- One 64-bit computer (laptop/desktop)
- 1 x USB Flash Drive (≥8 GB, high-quality brand recommended)
- Paper and pen (for seed phrase)
- Optional: Printer (for xpub QR export)
2.2 Software Stack
- Tails OS (latest ISO, from tails.boum.org)
- Balena Etcher (to flash ISO)
- QuickHash GUI (for SHA-256 checksum validation)
- Electrum Wallet (bundled within Tails OS)
3. System Preparation and Software Verification
3.1 Image Verification
Prior to flashing the ISO, the integrity of the Tails OS image must be cryptographically validated. Using QuickHash:
plaintext SHA256 (tails-amd64-<version>.iso) = <expected_hash>Compare the hash output with the official hash provided on the Tails OS website. This mitigates the risk of ISO tampering or supply chain compromise.
3.2 Flashing the OS
Balena Etcher is used to flash the ISO to a USB drive:
- Insert USB drive.
- Launch Balena Etcher.
- Select the verified Tails ISO.
- Flash to USB and safely eject.
4. Cold Wallet Generation Procedure
4.1 Boot Into Tails OS
- Restart the system and boot into BIOS/UEFI boot menu.
- Select the USB drive containing Tails OS.
- Configure network settings to disable all connectivity.
4.2 Create Wallet in Electrum (Cold)
- Open Electrum from the Tails application launcher.
- Select "Standard Wallet" → "Create a new seed".
- Choose SegWit for address type (for lower fees and modern compatibility).
- Write down the 12-word seed phrase on paper. Never store digitally.
- Confirm the seed.
- Set a strong password for wallet access.
5. Exporting the Master Public Key (xpub)
- Open Electrum > Wallet > Information
- Export the Master Public Key (MPK) for receiving-only use.
- Optionally generate QR code for cold-to-hot usage (wallet watching).
This allows real-time monitoring of incoming Bitcoin transactions without ever exposing private keys.
6. Transaction Workflow
6.1 Receiving Bitcoin (Cold to Hot)
- Use the exported xpub in a watch-only wallet (desktop or mobile).
- Generate addresses as needed.
- Senders deposit Bitcoin to those addresses.
6.2 Spending Bitcoin (Hot Redeem Mode)
Important: This process temporarily compromises air-gap security.
- Boot into Tails (or use Electrum in a clean Linux environment).
- Import the 12-word seed phrase.
- Create transaction offline.
- Export signed transaction via QR code or USB.
- Broadcast using an online device.
6.3 Recommended Alternative: PSBT
To avoid full wallet import: - Use Partially Signed Bitcoin Transactions (PSBT) protocol to sign offline. - Broadcast PSBT using Sparrow Wallet or Electrum online.
7. Security Considerations
| Threat | Mitigation | |-------|------------| | OS Compromise | Use Tails (ephemeral environment, RAM-only) | | Supply Chain Attack | Manual SHA256 verification | | Key Leakage | No network access during key generation | | Phishing/Clone Wallets | Verify Electrum’s signature (when updating) | | Physical Theft | Store paper seed in tamper-evident location |
8. Backup Strategy
- Store 12-word seed phrase in multiple secure physical locations.
- Do not photograph or digitize.
- For added entropy, use Shamir Secret Sharing (e.g., 2-of-3 backups).
9. Consider
Through the meticulous integration of verifiable software solutions, the execution of air-gapped key generation methodologies, and adherence to stringent operational protocols, users have the capacity to establish a Bitcoin cold storage wallet that embodies an elevated degree of cryptographic assurance.
This DIY system presents a zero-dependency alternative to conventional third-party custody solutions and consumer-grade hardware wallets.
Consequently, it empowers individuals with the ability to manage their Bitcoin assets while ensuring full trust minimization and maximizing their sovereign control over private keys and transaction integrity within the decentralized financial ecosystem..
10. References And Citations
Nakamoto, Satoshi. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008.
“Tails - The Amnesic Incognito Live System.” tails.boum.org, The Tor Project.
“Electrum Bitcoin Wallet.” electrum.org, 2025.
“QuickHash GUI.” quickhash-gui.org, 2025.
“Balena Etcher.” balena.io, 2025.
Bitcoin Core Developers. “Don’t Trust, Verify.” bitcoincore.org, 2025.In Addition
🪙 SegWit vs. Legacy Bitcoin Wallets
⚖️ TL;DR Decision Chart
| If you... | Use SegWit | Use Legacy | |-----------|----------------|----------------| | Want lower fees | ✅ Yes | 🚫 No | | Send to/from old services | ⚠️ Maybe | ✅ Yes | | Care about long-term scaling | ✅ Yes | 🚫 No | | Need max compatibility | ⚠️ Mixed | ✅ Yes | | Run a modern wallet | ✅ Yes | 🚫 Legacy support fading | | Use cold storage often | ✅ Yes | ⚠️ Depends on wallet support | | Use Lightning Network | ✅ Required | 🚫 Not supported |
🔍 1. What Are We Comparing?
There are two major types of Bitcoin wallet address formats:
🏛️ Legacy (P2PKH)
- Format starts with:
1 - Example:
1A1zP1eP5QGefi2DMPTfTL5SLmv7DivfNa - Oldest, most universally compatible
- Higher fees, larger transactions
- May lack support in newer tools and layer-2 solutions
🛰️ SegWit (P2WPKH)
- Formats start with:
- Nested SegWit (P2SH):
3... - Native SegWit (bech32):
bc1q... - Introduced via Bitcoin Improvement Proposal (BIP) 141
- Smaller transaction sizes → lower fees
- Native support by most modern wallets
💸 2. Transaction Fees
SegWit = Cheaper.
- SegWit reduces the size of Bitcoin transactions in a block.
- This means you pay less per transaction.
- Example: A SegWit transaction might cost 40%–60% less in fees than a legacy one.💡 Why?
Bitcoin charges fees per byte, not per amount.
SegWit removes certain data from the base transaction structure, which shrinks byte size.
🧰 3. Wallet & Service Compatibility
| Category | Legacy | SegWit (Nested / Native) | |----------|--------|---------------------------| | Old Exchanges | ✅ Full support | ⚠️ Partial | | Modern Exchanges | ✅ Yes | ✅ Yes | | Hardware Wallets (Trezor, Ledger) | ✅ Yes | ✅ Yes | | Mobile Wallets (Phoenix, BlueWallet) | ⚠️ Rare | ✅ Yes | | Lightning Support | 🚫 No | ✅ Native SegWit required |
🧠 Recommendation:
If you interact with older platforms or do cross-compatibility testing, you may want to: - Use nested SegWit (address starts with
3), which is backward compatible. - Avoid bech32-only wallets if your exchange doesn't support them (though rare in 2025).
🛡️ 4. Security and Reliability
Both formats are secure in terms of cryptographic strength.
However: - SegWit fixes a bug known as transaction malleability, which helps build protocols on top of Bitcoin (like the Lightning Network). - SegWit transactions are more standardized going forward.
💬 User takeaway:
For basic sending and receiving, both are equally secure. But for future-proofing, SegWit is the better bet.
🌐 5. Future-Proofing
Legacy wallets are gradually being phased out:
- Developers are focusing on SegWit and Taproot compatibility.
- Wallet providers are defaulting to SegWit addresses.
- Fee structures increasingly assume users have upgraded.
🚨 If you're using a Legacy wallet today, you're still safe. But: - Some services may stop supporting withdrawals to legacy addresses. - Your future upgrade path may be more complex.
🚀 6. Real-World Scenarios
🧊 Cold Storage User
- Use SegWit for low-fee UTXOs and efficient backup formats.
- Consider Native SegWit (
bc1q) if supported by your hardware wallet.
👛 Mobile Daily User
- Use Native SegWit for cheaper everyday payments.
- Ideal if using Lightning apps — it's often mandatory.
🔄 Exchange Trader
- Check your exchange’s address type support.
- Consider nested SegWit (
3...) if bridging old + new systems.
📜 7. Migration Tips
If you're moving from Legacy to SegWit:
- Create a new SegWit wallet in your software/hardware wallet.
- Send funds from your old Legacy wallet to the SegWit address.
- Back up the new seed — never reuse the old one.
- Watch out for fee rates and change address handling.
✅ Final User Recommendations
| Use Case | Address Type | |----------|--------------| | Long-term HODL | SegWit (
bc1q) | | Maximum compatibility | SegWit (nested3...) | | Fee-sensitive use | Native SegWit (bc1q) | | Lightning | Native SegWit (bc1q) | | Legacy systems only | Legacy (1...) – short-term only |
📚 Further Reading
- Nakamoto, Satoshi. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008.
- Bitcoin Core Developers. “Segregated Witness (Consensus Layer Change).” github.com/bitcoin, 2017.
- “Electrum Documentation: Wallet Types.” docs.electrum.org, 2024.
- “Bitcoin Wallet Compatibility.” bitcoin.org, 2025.
- Ledger Support. “SegWit vs Legacy Addresses.” ledger.com, 2024.
-
 @ 7d33ba57:1b82db35
2025-04-24 10:49:41
@ 7d33ba57:1b82db35
2025-04-24 10:49:41Tucked away in the rolling hills of southern France’s Hérault department, Montpeyroux is a charming medieval village known for its peaceful atmosphere, beautiful stone houses, and excellent Languedoc wines. It’s the kind of place where time seems to slow down, making it perfect for a relaxed stop on a southern France road trip.
🏡 Why Visit Montpeyroux?
🪨 Authentic Medieval Character
- Wander narrow cobbled streets lined with honey-colored stone houses
- Visit the remains of a medieval castle and old tower that offer stunning views over vineyards and hills
- A tranquil place that feels untouched by time
🍷 Wine Culture
- Surrounded by prestigious vineyards producing Coteaux du Languedoc wines
- Stop by local caves (wineries) to taste bold reds and crisp whites—many with stunning views over the valley
- Don’t miss the annual wine festivals and open cellars
🌄 Scenic Location
- Located near the Gorges de l’Hérault, perfect for hiking, swimming, or kayaking
- Just a short drive from Saint-Guilhem-le-Désert, one of France’s most beautiful villages
- Great base for exploring the natural beauty of Occitanie
🍽️ Where to Eat
- Enjoy local cuisine at cozy bistros—think grilled lamb, duck confit, olives, and regional cheeses
- Many places serve seasonal dishes paired with local wines
🚗 Getting There
- Around 45 minutes by car from Montpellier
- Best explored by car as public transport is limited, but the countryside drive is worth it
-
 @ b2caa9b3:9eab0fb5
2025-04-24 06:25:35
@ b2caa9b3:9eab0fb5
2025-04-24 06:25:35Yesterday, I faced one of the most heartbreaking and frustrating experiences of my life. Between 10:00 AM and 2:00 PM, I was held at the Taveta border, denied entry into Kenya—despite having all the necessary documents, including a valid visitor’s permit and an official invitation letter.
The Kenyan Immigration officers refused to speak with me. When I asked for clarification, I was told flatly that I would never be allowed to enter Kenya unless I obtain a work permit. No other reason was given. My attempts to explain that I simply wanted to see my child were ignored. No empathy. No flexibility. No conversation. Just rejection.
While I stood there for hours, held by officials with no explanation beyond a bureaucratic wall, I recorded the experience. I now have several hours of footage documenting what happened—a silent testimony to how a system can dehumanize and block basic rights.
And the situation doesn’t end at the border.
My child, born in Kenya, is also being denied the right to see me. Germany refuses to grant her citizenship, which means she cannot visit me either. The German embassy in Nairobi refuses to assist, stating they won’t get involved. Their silence is loud.
This is not just about paperwork. This is about a child growing up without her father. It’s about a system that chooses walls over bridges, and bureaucracy over humanity. Kenya, by refusing me entry, is keeping a father away from his child. Germany, by refusing to act under §13 StGB, is complicit in that injustice.
In the coming days, I’ll share more about my past travels and how this situation unfolded. I’ll also be releasing videos and updates on TikTok—because this story needs to be heard. Not just for me, but for every parent and child caught between borders and bureaucracies.
Stay tuned—and thank you for standing with me.
-
 @ d34e832d:383f78d0
2025-04-24 06:12:32
@ d34e832d:383f78d0
2025-04-24 06:12:32
Goal
This analytical discourse delves into Jack Dorsey's recent utterances concerning Bitcoin, artificial intelligence, decentralized social networking platforms such as Nostr, and the burgeoning landscape of open-source cryptocurrency mining initiatives.
Dorsey's pronouncements escape the confines of isolated technological fascinations; rather, they elucidate a cohesive conceptual schema wherein Bitcoin transcends its conventional role as a mere store of value—akin to digital gold—and emerges as a foundational protocol intended for the construction of a decentralized, sovereign, and perpetually self-evolving internet ecosystem.
A thorough examination of Dorsey's confluence of Bitcoin with artificial intelligence advancements, adaptive learning paradigms, and integrated social systems reveals an assertion of Bitcoin's position as an entity that evolves beyond simple currency, evolving into a distinctly novel socio-technological organism characterized by its inherent ability to adapt and grow. His vigorous endorsement of native digital currency, open communication protocols, and decentralized infrastructural frameworks is posited here as a revolutionary paradigm—a conceptual
1. The Path
Jack Dorsey, co-founder of Twitter and Square (now Block), has emerged as one of the most compelling evangelists for a decentralized future. His ideas about Bitcoin go far beyond its role as a speculative asset or inflation hedge. In a recent interview, Dorsey ties together themes of open-source AI, peer-to-peer currency, decentralized media, and radical self-education, sketching a future in which Bitcoin is the lynchpin of an emerging technological and social ecosystem. This thesis reviews Dorsey’s statements and offers a critical framework to understand why his vision uniquely positions Bitcoin as the keystone of a post-institutional, digital world.
2. Bitcoin: The Native Currency of the Internet
“It’s the best current manifestation of a native internet currency.” — Jack Dorsey
Bitcoin's status as an open protocol with no central controlling authority echoes the original spirit of the internet: decentralized, borderless, and resilient. Dorsey's framing of Bitcoin not just as a payment system but as the "native money of the internet" is a profound conceptual leap. It suggests that just as HTTP became the standard for web documents, Bitcoin can become the monetary layer for the open web.
This framing bypasses traditional narratives of digital gold or institutional adoption and centers a P2P vision of global value transfer. Unlike central bank digital currencies or platform-based payment rails, Bitcoin is opt-in, permissionless, and censorship-resistant—qualities essential for sovereignty in the digital age.
3. Nostr and the Decentralization of Social Systems
Dorsey’s support for Nostr, an open protocol for decentralized social media, reflects a desire to restore user agency, protocol composability, and speech sovereignty. Nostr’s architecture parallels Bitcoin’s: open, extensible, and resilient to censorship.
Here, Bitcoin serves not just as money but as a network effect driver. When combined with Lightning and P2P tipping, Nostr becomes more than just a Twitter alternative—it evolves into a micropayment-native communication system, a living proof that Bitcoin can power an entire open-source social economy.
4. Open-Source AI and Cognitive Sovereignty
Dorsey's forecast that open-source AI will emerge as an alternative to proprietary systems aligns with his commitment to digital autonomy. If Bitcoin empowers financial sovereignty and Nostr enables communicative freedom, open-source AI can empower cognitive independence—freeing humanity from centralized algorithmic manipulation.
He draws a fascinating parallel between AI learning models and human learning itself, suggesting both can be self-directed, recursive, and radically decentralized. This resonates with the Bitcoin ethos: systems should evolve through transparent, open participation—not gatekeeping or institutional control.
5. Bitcoin Mining: Sovereignty at the Hardware Layer
Block’s initiative to create open-source mining hardware is a direct attempt to counter centralization in Bitcoin’s infrastructure. ASIC chip development and mining rig customization empower individuals and communities to secure the network directly.
This move reinforces Dorsey’s vision that true decentralization requires ownership at every layer, including hardware. It is a radical assertion of vertical sovereignty—from protocol to interface to silicon.
6. Learning as the Core Protocol
“The most compounding skill is learning itself.” — Jack Dorsey
Dorsey’s deepest insight is that the throughline connecting Bitcoin, AI, and Nostr is not technology—it’s learning. Bitcoin represents more than code; it’s a living experiment in voluntary consensus, a distributed educational system in cryptographic form.
Dorsey’s emphasis on meditation, intensive retreats, and self-guided exploration mirrors the trustless, sovereign nature of Bitcoin. Learning becomes the ultimate protocol: recursive, adaptive, and decentralized—mirroring AI models and Bitcoin nodes alike.
7. Critical Risks and Honest Reflections
Dorsey remains honest about Bitcoin’s current limitations:
- Accessibility: UX barriers for onboarding new users.
- Usability: Friction in everyday use.
- State-Level Adoption: Risks of co-optation as mere digital gold.
However, his caution enhances credibility. His focus remains on preserving Bitcoin as a P2P electronic cash system, not transforming it into another tool of institutional control.
8. Bitcoin as a Living System
What emerges from Dorsey's vision is not a product pitch, but a philosophical reorientation: Bitcoin, Nostr, and open AI are not discrete tools—they are living systems forming a new type of civilization stack.
They are not static infrastructures, but emergent grammars of human cooperation, facilitating value exchange, learning, and community formation in ways never possible before.
Bitcoin, in this view, is not merely stunningly original—it is civilizationally generative, offering not just monetary innovation but a path to software-upgraded humanity.
Works Cited and Tools Used
Dorsey, Jack. Interview on Bitcoin, AI, and Decentralization. April 2025.
Nakamoto, Satoshi. “Bitcoin: A Peer-to-Peer Electronic Cash System.” 2008.
Nostr Protocol. https://nostr.com.
Block, Inc. Bitcoin Mining Hardware Initiatives. 2024.
Obsidian Canvas. Decentralized Note-Taking and Networked Thinking. 2025. -
 @ 8cda1daa:e9e5bdd8
2025-04-24 10:20:13
@ 8cda1daa:e9e5bdd8
2025-04-24 10:20:13Bitcoin cracked the code for money. Now it's time to rebuild everything else.
What about identity, trust, and collaboration? What about the systems that define how we live, create, and connect?
Bitcoin gave us a blueprint to separate money from the state. But the state still owns most of your digital life. It's time for something more radical.
Welcome to the Atomic Economy - not just a technology stack, but a civil engineering project for the digital age. A complete re-architecture of society, from the individual outward.
The Problem: We Live in Digital Captivity
Let's be blunt: the modern internet is hostile to human freedom.
You don't own your identity. You don't control your data. You don't decide what you see.
Big Tech and state institutions dominate your digital life with one goal: control.
- Poisoned algorithms dictate your emotions and behavior.
- Censorship hides truth and silences dissent.
- Walled gardens lock you into systems you can't escape.
- Extractive platforms monetize your attention and creativity - without your consent.
This isn't innovation. It's digital colonization.
A Vision for Sovereign Society
The Atomic Economy proposes a new design for society - one where: - Individuals own their identity, data, and value. - Trust is contextual, not imposed. - Communities are voluntary, not manufactured by feeds. - Markets are free, not fenced. - Collaboration is peer-to-peer, not platform-mediated.
It's not a political revolution. It's a technological and social reset based on first principles: self-sovereignty, mutualism, and credible exit.
So, What Is the Atomic Economy?
The Atomic Economy is a decentralized digital society where people - not platforms - coordinate identity, trust, and value.
It's built on open protocols, real software, and the ethos of Bitcoin. It's not about abstraction - it's about architecture.
Core Principles: - Self-Sovereignty: Your keys. Your data. Your rules. - Mutual Consensus: Interactions are voluntary and trust-based. - Credible Exit: Leave any system, with your data and identity intact. - Programmable Trust: Trust is explicit, contextual, and revocable. - Circular Economies: Value flows directly between individuals - no middlemen.
The Tech Stack Behind the Vision
The Atomic Economy isn't just theory. It's a layered system with real tools:
1. Payments & Settlement
- Bitcoin & Lightning: The foundation - sound, censorship-resistant money.
- Paykit: Modular payments and settlement flows.
- Atomicity: A peer-to-peer mutual credit protocol for programmable trust and IOUs.
2. Discovery & Matching
- Pubky Core: Decentralized identity and discovery using PKARR and the DHT.
- Pubky Nexus: Indexing for a user-controlled internet.
- Semantic Social Graph: Discovery through social tagging - you are the algorithm.
3. Application Layer
- Bitkit: A self-custodial Bitcoin and Lightning wallet.
- Pubky App: Tag, publish, trade, and interact - on your terms.
- Blocktank: Liquidity services for Lightning and circular economies.
- Pubky Ring: Key-based access control and identity syncing.
These tools don't just integrate - they stack. You build trust, exchange value, and form communities with no centralized gatekeepers.
The Human Impact
This isn't about software. It's about freedom.
- Empowered Individuals: Control your own narrative, value, and destiny.
- Voluntary Communities: Build trust on shared values, not enforced norms.
- Economic Freedom: Trade without permission, borders, or middlemen.
- Creative Renaissance: Innovation and art flourish in open, censorship-resistant systems.
The Atomic Economy doesn't just fix the web. It frees the web.
Why Bitcoiners Should Care
If you believe in Bitcoin, you already believe in the Atomic Economy - you just haven't seen the full map yet.
- It extends Bitcoin's principles beyond money: into identity, trust, coordination.
- It defends freedom where Bitcoin leaves off: in content, community, and commerce.
- It offers a credible exit from every centralized system you still rely on.
- It's how we win - not just economically, but culturally and socially.
This isn't "web3." This isn't another layer of grift. It's the Bitcoin future - fully realized.
Join the Atomic Revolution
- If you're a builder: fork the code, remix the ideas, expand the protocols.
- If you're a user: adopt Bitkit, use Pubky, exit the digital plantation.
- If you're an advocate: share the vision. Help people imagine a free society again.
Bitcoin promised a revolution. The Atomic Economy delivers it.
Let's reclaim society, one key at a time.
Learn more and build with us at Synonym.to.
-
 @ 10f7c7f7:f5683da9
2025-04-24 10:07:09
@ 10f7c7f7:f5683da9
2025-04-24 10:07:09The first time I received a paycheque from a full-time job, after being told in the interview I would be earning one amount, the amount I received was around 25% less; you’re not in Kansas anymore, welcome to the real work and TAX. Over the years, I’ve continued to pay my taxes, as a good little citizen, and at certain points along the way, I have paid considerable amounts of tax, because I wouldn’t want to break the law by not paying my taxes. Tax is necessary for a civilised society, they say. I’m told, who will pay, at least in the UK, for the NHS, who will pay for the roads, who will pay for the courts, the military, the police, if I don’t pay my taxes? But let’s be honest, apart from those who pay very little to no tax, who, in a society actually gets good value for money out of the taxes they pay, or hears of a government institution that operates efficiently and effectively? Alternatively, imagine if the government didn’t have control of a large military budget, would they be quite so keen to deploy the young of our country into harm’s way, in the name of national security or having streets in Ukraine named after them for their generous donations of munition paid with someone else’s money?
While I’m only half-way through the excellent “Fiat Standard”, I’m well aware that many of these issues have been driven by the ability of those in charge to not only enforce and increase taxation at will, but also, if ends don’t quite meet, print the difference, however, these are rather abstract and high-level ideas for my small engineer’s brain. What has really brought this into sharp focus for me is the impending sale of my first house, that at the age of 25, I was duly provided a 40-year mortgage and was required to sign a form acknowledging that I would still be paying the mortgage after my retirement age. Fortunately for me, thanks to the government now changing the national age of retirement from 65 to 70 (so stealing 5 years of my retirement), in practice this form didn’t need to be signed, lucky me? Even so, what type of person would knowingly put another person in a situation where near 40% of their wage would mainly be paying interest to the bank (which as a side note was bailed out only a few years later). The unpleasant taste really became unbearable when even after being put into this “working life” sentence of debt repayment, was, even with the amount I’d spent on the house (debt interest and maintenance) over the subsequent 19 years, only able to provide a rate of return of less than 1.6%, compared to the average official (bullshit) inflation figure of 2.77%. My house has not kept up with inflation and to add insult to financial injury, His Majesty’s Revenue and Customs feel the need to take their portion of this “profit”.
At which point, I take a very deep breath, sit quietly for a moment, and channel my inner Margot, deciding against grabbing a bottle of bootleg antiseptic to both clear my pallet and dull the pain. I had been convinced I needed to get on the housing ladder to save, but the government has since printed billions, with the rate of, even the conservative estimates of inflation, out pacing my meagre returns on property, and after all that blood, sweet, tears and dust, covering my poor dog, “the law” states some of that money is theirs. I wasn’t able to save in the money that they could print at will, I worked very hard, I took risks and the reward I get is to give them even more money to fritter away of things that won’t benefit me. But, I don’t want your sympathy, I don’t need it, but it helped me to get a new perspective on capital gains, particularly when considered in relation to bitcoin. So, to again draw from Ms. Paez, who herself was drawing from everyone’s favourite Joker, Heath Ledger, not Rachel Reeves (or J. Powell), here we go.
The Sovereign Individual is by no means an easy read, but is absolutely fascinating, providing clear critiques of the system that at the time was only in its infancy, but predicting many aspects of today’s world, with shocking accuracy. One of the most striking parts for me was the critique and effect of taxation (specifically progressive forms) on the prosperity of a nation at large. At an individual level, people have a proportion of their income removed, to be spent by the government, out of the individuals’ control. The person who has applied their efforts, abilities and skills to earn a living is unable to decide how best to utilise a portion of the resources into the future. While this is an accepted reality, the authors’ outline the cumulative, compound impact of forfeiting such a large portion of your wage each year, leading to figures that are near unimaginable to anyone without a penchant for spreadsheets or an understanding of exponential growth. Now, if we put this into the context of the entrepreneur, identifying opportunities, taking on personal and business risk, whenever a profit is realised, whether through normal sales or when realising value from capital appreciation, they must pay a portion of this in tax. While there are opportunities to reinvest this back into the organisation, there may be no immediate investment opportunities for them to offset their current tax bill. As a result, the entrepreneurs are hampered from taking the fruits of their labour and compounding the results of their productivity, forced to fund the social programmes of a government pursuing aims that are misaligned with individuals running their own business. Resources are removed from the most productive individuals in the society, adding value, employing staff, to those who may have limited knowledge of the economic realities of business; see Oxbridge Scholars, with experience in NGOs or charities, for more details please see Labour’s current front bench. What was that Labour? Ah yes, let’s promote growth by taxing companies more and making it more difficult to get rid of unproductive staff, exactly the policies every small business owner has been asking for (Budget October 2024).
Now, for anyone on NOSTR, none of this is new, a large portion of Nostriches were orange pilled long before taking their first purple pill of decentralise Notes and Other Stuff. However, if we’re aware of this system that has been put in place to steal our earnings and confiscate our winnings if we have been able to outwit the Keynesian trap western governments have chosen to give themselves more power, how can we progress? What options do we have? a) being locked up for non-payment of taxes by just spending bitcoin, to hell with paying taxes or b) spend/sell (:/), but keeping a record of those particular coins you bought multiple years ago, in order to calculate your gain and hand over YOUR money the follow tax year, so effectively increasing the cost of anything purchased in bitcoin. Please note, I’m making a conscious effort not to say what should be done, everyone needs to make decisions based on their knowledge and their understanding.
Anyway, option a) is not as flippant as one might think, but also not something one should (damn it) do carelessly. One bitcoin equals one bitcoin, bitcoin is money, as a result, it neither increases nor decreases is value, it is fiat currencies that varies wildly in comparison. If we think about gold, the purchasing power of gold has remained relatively consistent over hundreds of years, gold is viewed as money, which (as a side note) results in Royal Mint gold coins being both exempt of VAT and capital gains tax. While I may consider this from a, while not necessarily biased, but definitely pro-bitcoin perspective, I believe that it is extremely logical for transactions that take place in bitcoin should not require “profits” or “losses” to be reports, but this is where my logic and the treasury’s grabbiness are inconsistent. If what you’re buying is priced in bitcoin, you’re trading goods or services for money, there was no realisation of gains. Having said that, if you choose to do this, best not do any spending from a stack with a connection to an exchange and your identify. When tax collectors (and their government masters) end up not having enough money, they may begin exploring whether those people buying bitcoin from exchanges are also spending it.
But why is this relevant or important? For me and from hearing from many people on podcasts, while not impossible and not actually that difficult, recording gains on each transaction is firstly a barrier for spending bitcoin, it is additional effort, admin and not insignificant cost, and no one likes that. Secondly, from my libertarian leaning perspective, tax is basically the seizure of assets under the threat of incarceration (aka theft), with the government spending that money on crap I don’t give a shit about, meaning I don’t want to help fund their operation more than I already do. The worry is, if I pay more taxes, they think they’re getting good at collecting taxes, they increase taxes, use taxes to employ more tax collectors, rinse and repeat. From this perspective, it is almost my duty not to report when I transact in bitcoin, viewing it as plain and simple, black-market money, where the government neither dictates what I can do with it, nor profit from its appreciation.
The result of this is not the common mantra of never sell your bitcoin, because I, for one, am looking forward to ditching the fiat grind and having more free time driving an interesting 90’s sports car or riding a new mountain bike, which I will need money to be fund. Unless I’m going to take a fair bit of tax evasion-based risk, find some guys who will only accept my KYC free bitcoin and then live off the grid, I’ll need to find another way, which unfortunately may require engaging once more with the fiat system. However, this time, rather than selling bitcoin to buy fiat, looking for financial product providers who offer loans against bitcoin held. This is nothing new, having been a contributing factors to the FTX blow up, and the drawdown of 2022, the logic of such products is solid and the secret catalyst to Mark Moss’s (and others) buy, borrow, die strategy. The difference this time is to earn from our mistakes, to choose the right company and maybe hand over our private keys (multisig is a beautiful thing). The key benefit of this is that by taking a loan, you’re not realising capital gains, so do not create a taxable event. While there is likely to be an interest on any loan, this only makes sense if this is considerably less than either the capital gains rate incurred if you sold the bitcoin or the long-term capital appreciation of the bitcoin you didn’t have to sell, it has to be an option worth considering.
Now, this is interacting with the fiat system, it does involve the effective printing of money and depending on the person providing the loan, there is risk, however, there are definitely some positives, even outside the not inconsiderable, “tax free” nature of this money. Firstly, by borrowing fiat money, you are increasing the money supply, while devaluing all other holders of that currency, which effectively works against fiat governments, causing them to forever print harder to stop themselves going into a deflationary nose drive. The second important aspect is that if you have not had to sell your bitcoin, you have removed sell pressure from the market and buying pressure that would strengthen the fiat currency, so further supporting the stack you have not had to sell.
Now, let’s put this in the context of The Sovereign Individual or the entrepreneurial bitcoiner, who took a risk before fully understanding what they were buying and has now benefiting financially. The barrier of tax-based admin or the reticence to support government operations through paying additional tax are not insignificant, which the loan has allowed you to effectively side step, keeping more value of your holdings to allocate as you see fit. While this may involve the setting up of a new business that itself may drive productive growth, even if all you did was spend that money (such as a sport car or a new bike), this could still be a net, economic positive compared to a large portion of that money being sucked into the government spending black hole. While the government would not be receiving that tax revenue, every retailer, manufacturer or service provider would benefit from this additional business. Rather than the tax money going toward interest costs or civil servant wages, the money would go towards the real businesses you have chosen, their staff’s wages, who are working hard to outcompete their peers. Making this choice to not pay capital gains does not just allow bitcoiner to save money and to a small degree, reduce government funding, but also provides a cash injection to those companies who may still be reeling from minimum wage AND national insurance increases.
I’m not an ethicist, so am unable to provide a clear, concise, philosophical argument to explain why the ability of government to steal from you via the processes of monetary inflation as well as an ever-increasing tax burden in immoral, but I hope this provides a new perspective on the situation. I don’t believe increases in taxes support economic development (it literally does the opposite), I don’t believe that individuals should be penalised for working hard, challenging themselves, taking risks and succeeding. However, I’m not in charge of the system and also appreciate that if any major changes were to take place, the consequences would be significant (we’re talking Mandibles time). I believe removing capital gains tax from bitcoin would be a net positive for the economy and there being precedence based on the UK’s currently position with gold coins, but unfortunately, I don’t believe people in the cabinet think as I do, they see people with assets and pound signs ring up at their eyes.
As a result, my aim moving forward will be to think carefully before making purchases or sales that will incur capital gains tax (no big Lambo purchase for me at the top), but also being willing the promote the bitcoin economy by purchasing products and services with bitcoin. To do this, I’ll double confirm that spend/replace techniques actually get around capital gains by effectively using the payment rails of bitcoin to transfer value rather than to sell your bitcoin. This way, I will get to reward and promote those companies to perform at a level that warrants a little more effort with payment, without it costing me an additional 18-24% in tax later on.
So, to return to where we started and my first pay-cheque. We need to work to earn a living, but as we earn more, an ever-greater proportion is taken from us, and we are at risk of becoming stuck in a never ending fiat cycle. In the past, this was more of an issue, leading people into speculating on property or securities, which, if successful, would then incur further taxes, which will likely be spent by governments on liabilities or projects that add zero net benefits to national citizens. Apologies if you see this as a negative, but please don’t, this is the alternative to adopting a unit of account that cannot be inflated away. If you have begun to measure your wealth in bitcoin, there will be a point where you need to start to start spending. I for one, do not intend to die with my private keys in my head, but having lived a life, turbo charged by the freedom bitcoin has offered me. Bitcoin backed loans are returning to the market, with hopefully a little less risk this time around. There may be blow ups, but once they get established and interest costs start to be competed away, I will first of all acknowledge remaining risks and then not allocate 100% of my stack. Rather than being the one true bitcoiner who has never spent a sat, I will use the tools at my disposal to firstly give my family their best possible lives and secondly, not fund the government more than I need to.
Then, by the time I’m ready to leave this earth, there will be less money for me to leave to my family, but then again, the tax man would again come knocking, looking to gloat over my demise and add to my family’s misery with an outstretched hand. Then again, this piece is about capital gains rather than inheritance tax, so we can leave those discussions for another time.
This is not financial advice, please consult a financial/tax advisor before spending and replacing without filing taxes and don’t send your bitcoin to any old fella who says they’ll return it once you’ve paThe first time I received a paycheque from a full-time job, after being told in the interview I would be earning one amount, the amount I received was around 25% less; you’re not in Kansas anymore, welcome to the real work and TAX. Over the years, I’ve continued to pay my taxes, as a good little citizen, and at certain points along the way, I have paid considerable amounts of tax, because I wouldn’t want to break the law by not paying my taxes. Tax is necessary for a civilised society, they say. I’m told, who will pay, at least in the UK, for the NHS, who will pay for the roads, who will pay for the courts, the military, the police, if I don’t pay my taxes? But let’s be honest, apart from those who pay very little to no tax, who, in a society actually gets good value for money out of the taxes they pay, or hears of a government institution that operates efficiently and effectively? Alternatively, imagine if the government didn’t have control of a large military budget, would they be quite so keen to deploy the young of our country into harm’s way, in the name of national security or having streets in Ukraine named after them for their generous donations of munition paid with someone else’s money? While I’m only half-way through the excellent “Fiat Standard”, I’m well aware that many of these issues have been driven by the ability of those in charge to not only enforce and increase taxation at will, but also, if ends don’t quite meet, print the difference, however, these are rather abstract and high-level ideas for my small engineer’s brain. What has really brought this into sharp focus for me is the impending sale of my first house, that at the age of 25, I was duly provided a 40-year mortgage and was required to sign a form acknowledging that I would still be paying the mortgage after my retirement age. Fortunately for me, thanks to the government now changing the national age of retirement from 65 to 70 (so stealing 5 years of my retirement), in practice this form didn’t need to be signed, lucky me? Even so, what type of person would knowingly put another person in a situation where near 40% of their wage would mainly be paying interest to the bank (which as a side note was bailed out only a few years later). The unpleasant taste really became unbearable when even after being put into this “working life” sentence of debt repayment, was, even with the amount I’d spent on the house (debt interest and maintenance) over the subsequent 19 years, only able to provide a rate of return of less than 1.6%, compared to the average official (bullshit) inflation figure of 2.77%. My house has not kept up with inflation and to add insult to financial injury, His Majesty’s Revenue and Customs feel the need to take their portion of this “profit”.

At which point, I take a very deep breath, sit quietly for a moment, and channel my inner Margot, deciding against grabbing a bottle of bootleg antiseptic to both clear my pallet and dull the pain. I had been convinced I needed to get on the housing ladder to save, but the government has since printed billions, with the rate of, even the conservative estimates of inflation, out pacing my meagre returns on property, and after all that blood, sweet, tears and dust, covering my poor dog, “the law” states some of that money is theirs. I wasn’t able to save in the money that they could print at will, I worked very hard, I took risks and the reward I get is to give them even more money to fritter away of things that won’t benefit me. But, I don’t want your sympathy, I don’t need it, but it helped me to get a new perspective on capital gains, particularly when considered in relation to bitcoin. So, to again draw from Ms. Paez, who herself was drawing from everyone’s favourite Joker, Heath Ledger, not Rachel Reeves (or J. Powell), here we go.
The Sovereign Individual is by no means an easy reaD, but is absolutely fascinating, providing clear critiques of the system that at the time was only in its infancy, but predicting many aspects of today’s world, with shocking accuracy. One of the most striking parts for me was the critique and effect of taxation (specifically progressive forms) on the prosperity of a nation at large. At an individual level, people have a proportion of their income removed, to be spent by the government, out of the individuals’ control. The person who has applied their efforts, abilities and skills to earn a living is unable to decide how best to utilise a portion of the resources into the future. While this is an accepted reality, the authors’ outline the cumulative, compound impact of forfeiting such a large portion of your wage each year, leading to figures that are near unimaginable to anyone without a penchant for spreadsheets or an understanding of exponential growth. Now, if we put this into the context of the entrepreneur, identifying opportunities, taking on personal and business risk, whenever a profit is realised, whether through normal sales or when realising value from capital appreciation, they must pay a portion of this in tax. While there are opportunities to reinvest this back into the organisation, there may be no immediate investment opportunities for them to offset their current tax bill. As a result, the entrepreneurs are hampered from taking the fruits of their labour and compounding the results of their productivity, forced to fund the social programmes of a government pursuing aims that are misaligned with individuals running their own business. Resources are removed from the most productive individuals in the society, adding value, employing staff, to those who may have limited knowledge of the economic realities of business; see Oxbridge Scholars, with experience in NGOs or charities, for more details please see Labour’s current front bench. What was that Labour? Ah yes, let’s promote growth by taxing companies more and making it more difficult to get rid of unproductive staff, exactly the policies every small business owner has been asking for (Budget October 2024).
Now, for anyone on NOSTR, none of this is new, a large portion of Nostriches were orange pilled long before taking their first purple pill of decentralise Notes and Other Stuff. However, if we’re aware of this system that has been put in place to steal our earnings and confiscate our winnings if we have been able to outwit the Keynesian trap western governments have chosen to give themselves more power, how can we progress? What options do we have? a) being locked up for non-payment of taxes by just spending bitcoin, to hell with paying taxes or b) spend/sell (:/), but keeping a record of those particular coins you bought multiple years ago, in order to calculate your gain and hand over YOUR money the follow tax year, so effectively increasing the cost of anything purchased in bitcoin. Please note, I’m making a conscious effort not to say what should be done, everyone needs to make decisions based on their knowledge and their understanding.
Anyway, option a) is not as flippant as one might think, but also not something one should (damn it) do carelessly. One bitcoin equals one bitcoin, bitcoin is money, as a result, it neither increases nor decreases is value, it is fiat currencies that varies wildly in comparison. If we think about gold, the purchasing power of gold has remained relatively consistent over hundreds of years, gold is viewed as money, which (as a side note) results in Royal Mint gold coins being both exempt of VAT and capital gains tax. While I may consider this from a, while not necessarily biased, but definitely pro-bitcoin perspective, I believe that it is extremely logical for transactions that take place in bitcoin should not require “profits” or “losses” to be reports, but this is where my logic and the treasury’s grabbiness are inconsistent. If what you’re buying is priced in bitcoin, you’re trading goods or services for money, there was no realisation of gains. Having said that, if you choose to do this, best not do any spending from a stack with a connection to an exchange and your identify. When tax collectors (and their government masters) end up not having enough money, they may begin exploring whether those people buying bitcoin form exchanges are also spending it.
But why is this relevant or important? For me and from hearing from many people on podcasts, while not impossible and not actually that difficult, recording gains on each transaction is firstly a barrier for spending bitcoin, it is additional effort, admin and not insignificant cost, and no one likes that. Secondly, from my libertarian leaning perspective, tax is basically the seizure of assets under the threat of incarceration (aka theft), with the government spending that money on crap I don’t give a shit about, meaning I don’t want to help fund their operation more than I already do. The worry is, if I pay more taxes, they think they’re getting good at collecting taxes, they increase taxes, use taxes to employ more tax collectors, rinse and repeat. From this perspective, it is almost my duty not to report when I transact in bitcoin, viewing it as plain and simple, black-market money, where the government neither dictates what I can do with it, nor profit from its appreciation.
The result of this is not the common mantra of never sell your bitcoin, because I, for one, am looking forward to ditching the fiat grind and having more free time driving an interesting 90’s sports car or riding a new mountain bike, which I will need money to be fund. Unless I’m going to take a fair bit of tax evasion-based risk, find some guys who will only accept my KYC free bitcoin and then live off the grid, I’ll need to find another way, which unfortunately may require engaging once more with the fiat system. However, this time, rather than selling bitcoin to buy fiat, looking for financial product providers who offer loans against bitcoin held. This is nothing new, having been a contributing factors to the FTX blow up, and the drawdown of 2022, the logic of such products is solid and the secret catalyst to Mark Moss’s (and others) buy, borrow, die strategy. The difference this time is to earn from our mistakes, to choose the right company and maybe hand over our private keys (multisig is a beautiful thing). The key benefit of this is that by taking a loan, you’re not realising capital gains, so do not create a taxable event. While there is likely to be an interest on any loan, this only makes sense if this is considerably less than either the capital gains rate incurred if you sold the bitcoin or the long-term capital appreciation of the bitcoin you didn’t have to sell, it has to be an option worth considering.
Now, this is interacting with the fiat system, it does involve the effective printing of money and depending on the person providing the loan, there is risk, however, there are definitely some positives, even outside the not inconsiderable, “tax free” nature of this money. Firstly, by borrowing fiat money, you are increasing the money supply, while devaluing all other holders of that currency, which effectively works against fiat governments, causing them to forever print harder to stop themselves going into a deflationary nose drive. The second important aspect is that if you have not had to sell your bitcoin, you have removed sell pressure from the market and buying pressure that would strengthen the fiat currency, so further supporting the stack you have not had to sell. Now, let’s put this in the context of The Sovereign Individual or the entrepreneurial bitcoiner, who took a risk before fully understanding what they were buying and has now benefiting financially. The barrier of tax-based admin or the reticence to support government operations through paying additional tax are not insignificant, which the loan has allowed you to effectively side step, keeping more value of your holdings to allocate as you see fit. While this may involve the setting up of a new business that itself may drive productive growth, even if all you did was spend that money (such as a sport car or a new bike), this could still be a net, economic positive compared to a large portion of that money being sucked into the government spending black hole. While the government would not be receiving that tax revenue, every retailer, manufacturer or service provider would benefit from this additional business. Rather than the tax money going toward interest costs or civil servant wages, the money would go towards the real businesses you have chosen, their staff’s wages, who are working hard to outcompete their peers. Making this choice to not pay capital gains does not just allow bitcoiner to save money and to a small degree, reduce government funding, but also provides a cash injection to those companies who may still be reeling from minimum wage AND national insurance increases.
I’m not an ethicist, so am unable to provide a clear, concise, philosophical argument to explain why the ability of government to steal from you via the processes of monetary inflation as well as an ever-increasing tax burden in immoral, but I hope this provides a new perspective on the situation. I don’t believe increases in taxes support economic development (it literally does the opposite), I don’t believe that individuals should be penalised for working hard, challenging themselves, taking risks and succeeding. However, I’m not in charge of the system and also appreciate that if any major changes were to take place, the consequences would be significant (we’re talking Mandibles time). I believe removing capital gains tax from bitcoin would be a net positive for the economy and there being precedence based on the UK’s currently position with gold coins, but unfortunately, I don’t believe people in the cabinet think as I do, they see people with assets and pound signs ring up at their eyes.
As a result, my aim moving forward will be to think carefully before making purchases or sales that will incur capital gains tax (no big Lambo purchase for me at the top), but also being willing the promote the bitcoin economy by purchasing products and services with bitcoin. To do this, I’ll double confirm that spend/replace techniques actually get around capital gains by effectively using the payment rails of bitcoin to transfer value rather than to sell your bitcoin. This way, I will get to reward and promote those companies to perform at a level that warrants a little more effort with payment, without it costing me an additional 18-24% in tax later on.
So, to return to where we started and my first pay-cheque. We need to work to earn a living, but as we earn more, an ever-greater proportion is taken from us, and we are at risk of becoming stuck in a never ending fiat cycle. In the past, this was more of an issue, leading people into speculating on property or securities, which, if successful, would then incur further taxes, which will likely be spent by governments on liabilities or projects that add zero net benefits to national citizens. Apologies if you see this as a negative, but please don’t, this is the alternative to adopting a unit of account that cannot be inflated away. If you have begun to measure your wealth in bitcoin, there will be a point where you need to start to start spending. I for one, do not intend to die with my private keys in my head, but having lived a life, turbo charged by the freedom bitcoin has offered me. Bitcoin backed loans are returning to the market, with hopefully a little less risk this time around. There may be blow ups, but once they get established and interest costs start to be competed away, I will first of all acknowledge remaining risks and then not allocate 100% of my stack. Rather than being the one true bitcoiner who has never spent a sat, I will use the tools at my disposal to firstly give my family their best possible lives and secondly, not fund the government more than I need to.
Then, by the time I’m ready to leave this earth, there will be less money for me to leave to my family, but then again, the tax man would again come knocking, looking to gloat over my demise and add to my family’s misery with an outstretched hand. Then again, this piece is about capital gains rather than inheritance tax, so we can leave those discussions for another time.
This is not financial advice, please consult a financial/tax advisor before spending and replacing without filing taxes and don’t send your bitcoin to any old fella who says they’ll return it once you’ve paid off the loan.
-
 @ 4c86f5a2:935c3564
2025-04-24 09:07:04
@ 4c86f5a2:935c3564
2025-04-24 09:07:04Write Test Postr
-
 @ d34e832d:383f78d0
2025-04-24 05:56:06
@ d34e832d:383f78d0
2025-04-24 05:56:06Idea
Through the integration of Optical Character Recognition (OCR), Docker-based deployment, and secure remote access via Twin Gate, Paperless NGX empowers individuals and small organizations to digitize, organize, and retrieve documents with minimal friction. This research explores its technical infrastructure, real-world applications, and how such a system can redefine document archival practices for the digital age.
Agile, Remote-Accessible, and Searchable Document System
In a world of increasing digital interdependence, managing physical documents is becoming not only inefficient but also environmentally and logistically unsustainable. The demand for agile, remote-accessible, and searchable document systems has never been higher—especially for researchers, small businesses, and archival professionals. Paperless NGX, an open-source platform, addresses these needs by offering a streamlined, secure, and automated way to manage documents digitally.
This Idea explores how Paperless NGX facilitates the transition to a paperless workflow and proposes best practices for sustainable, scalable usage.
Paperless NGX: The Platform
Paperless NGX is an advanced fork of the original Paperless project, redesigned with modern containers, faster performance, and enhanced community contributions. Its core functions include:
- Text Extraction with OCR: Leveraging the
ocrmypdfPython library, Paperless NGX can extract searchable text from scanned PDFs and images. - Searchable Document Indexing: Full-text search allows users to locate documents not just by filename or metadata, but by actual content.
- Dockerized Setup: A ready-to-use Docker Compose environment simplifies deployment, including the use of setup scripts for Ubuntu-based servers.
- Modular Workflows: Custom triggers and automation rules allow for smart processing pipelines based on file tags, types, or email source.
Key Features and Technical Infrastructure
1. Installation and Deployment
The system runs in a containerized environment, making it highly portable and isolated. A typical installation involves: - Docker Compose with YAML configuration - Volume mapping for persistent storage - Optional integration with reverse proxies (e.g., Nginx) for HTTPS access
2. OCR and Indexing
Using
ocrmypdf, scanned documents are processed into fully searchable PDFs. This function dramatically improves retrieval, especially for archived legal, medical, or historical records.3. Secure Access via Twin Gate
To solve the challenge of secure remote access without exposing the network, Twin Gate acts as a zero-trust access proxy. It encrypts communication between the Paperless NGX server and the client, enabling access from anywhere without the need for traditional VPNs.
4. Email Integration and Ingestion
Paperless NGX can ingest attachments directly from configured email folders. This feature automates much of the document intake process, especially useful for receipts, invoices, and academic PDFs.
Sustainable Document Management Workflow
A practical paperless strategy requires not just tools, but repeatable processes. A sustainable workflow recommended by the Paperless NGX community includes:
- Capture & Tagging
All incoming documents are tagged with a default “inbox” tag for triage. - Physical Archive Correlation
If the physical document is retained, assign it a serial number (e.g., ASN-001), which is matched digitally. - Curation & Tagging
Apply relevant category and topic tags to improve searchability. - Archival Confirmation
Remove the “inbox” tag once fully processed and categorized.
Backup and Resilience
Reliability is key to any archival system. Paperless NGX includes backup functionality via: - Cron job–scheduled Docker exports - Offsite and cloud backups using rsync or encrypted cloud drives - Restore mechanisms using documented CLI commands
This ensures document availability even in the event of hardware failure or data corruption.
Limitations and Considerations
While Paperless NGX is powerful, it comes with several caveats: - Technical Barrier to Entry: Requires basic Docker and Linux skills to install and maintain. - OCR Inaccuracy for Handwritten Texts: The OCR engine may struggle with cursive or handwritten documents. - Plugin and Community Dependency: Continuous support relies on active community contribution.
Consider
Paperless NGX emerges as a pragmatic and privacy-centric alternative to conventional cloud-based document management systems, effectively addressing the critical challenges of data security and user autonomy.
The implementation of advanced Optical Character Recognition (OCR) technology facilitates the indexing and searching of documents, significantly enhancing information retrieval efficiency.
Additionally, the platform offers secure remote access protocols that ensure data integrity while preserving the confidentiality of sensitive information during transmission.
Furthermore, its customizable workflow capabilities empower both individuals and organizations to precisely tailor their data management processes, thereby reclaiming sovereignty over their information ecosystems.
In an era increasingly characterized by a shift towards paperless methodologies, the significance of solutions such as Paperless NGX cannot be overstated; they play an instrumental role in engineering a future in which information remains not only accessible but also safeguarded and sustainably governed.
In Addition
To Further The Idea
This technical paper presents an optimized strategy for transforming an Intel NUC into a compact, power-efficient self-hosted server using Ubuntu. The setup emphasizes reliability, low energy consumption, and cost-effectiveness for personal or small business use. Services such as Paperless NGX, Nextcloud, Gitea, and Docker containers are examined for deployment. The paper details hardware selection, system installation, secure remote access, and best practices for performance and longevity.
1. Cloud sovereignty, Privacy, and Data Ownership
As cloud sovereignty, privacy, and data ownership become critical concerns, self-hosting is increasingly appealing. An Intel NUC (Next Unit of Computing) provides an ideal middle ground between Raspberry Pi boards and enterprise-grade servers—balancing performance, form factor, and power draw. With Ubuntu LTS and Docker, users can run a full suite of services with minimal overhead.
2. Hardware Overview
2.1 Recommended NUC Specifications:
| Component | Recommended Specs | |------------------|-----------------------------------------------------| | Model | Intel NUC 11/12 Pro (e.g., NUC11TNHi5, NUC12WSKi7) | | CPU | Intel Core i5 or i7 (11th/12th Gen) | | RAM | 16GB–32GB DDR4 (dual channel preferred) | | Storage | 512GB–2TB NVMe SSD (Samsung 980 Pro or similar) | | Network | Gigabit Ethernet + Optional Wi-Fi 6 | | Power Supply | 65W USB-C or barrel connector | | Cooling | Internal fan, well-ventilated location |
NUCs are also capable of dual-drive setups and support for Intel vPro for remote management on some models.
3. Operating System and Software Stack
3.1 Ubuntu Server LTS
- Version: Ubuntu Server 22.04 LTS
- Installation Method: Bootable USB (Rufus or Balena Etcher)
- Disk Partitioning: LVM with encryption recommended for full disk security
- Security:
- UFW (Uncomplicated Firewall)
- Fail2ban
- SSH hardened with key-only login
bash sudo apt update && sudo apt upgrade sudo ufw allow OpenSSH sudo ufw enable
4. Docker and System Services
Docker and Docker Compose streamline the deployment of isolated, reproducible environments.
4.1 Install Docker and Compose
bash sudo apt install docker.io docker-compose sudo systemctl enable docker4.2 Common Services to Self-Host:
| Application | Description | Access Port | |--------------------|----------------------------------------|-------------| | Paperless NGX | Document archiving and OCR | 8000 | | Nextcloud | Personal cloud, contacts, calendar | 443 | | Gitea | Lightweight Git repository | 3000 | | Nginx Proxy Manager| SSL proxy for all services | 81, 443 | | Portainer | Docker container management GUI | 9000 | | Watchtower | Auto-update containers | - |
5. Network & Remote Access
5.1 Local IP & Static Assignment
- Set a static IP for consistent access (via router DHCP reservation or Netplan).
5.2 Access Options
- Local Only: VPN into local network (e.g., WireGuard, Tailscale)
- Remote Access:
- Reverse proxy via Nginx with Certbot for HTTPS
- Twin Gate or Tailscale for zero-trust remote access
- DNS via DuckDNS, Cloudflare
6. Performance Optimization
- Enable
zramfor compressed RAM swap - Trim SSDs weekly with
fstrim - Use Docker volumes, not bind mounts for stability
- Set up unattended upgrades:
bash sudo apt install unattended-upgrades sudo dpkg-reconfigure --priority=low unattended-upgrades
7. Power and Environmental Considerations
- Idle Power Draw: ~7–12W (depending on configuration)
- UPS Recommended: e.g., APC Back-UPS 600VA
- Use BIOS Wake-on-LAN if remote booting is needed
8. Maintenance and Monitoring
- Monitoring: Glances, Netdata, or Prometheus + Grafana
- Backups:
- Use
rsyncto external drive or NAS - Cloud backup options: rclone to Google Drive, S3
- Paperless NGX backups:
docker compose exec -T web document-exporter ...
9. Consider
Running a personal server using an Intel NUC and Ubuntu offers a private, low-maintenance, and modular solution to digital infrastructure needs. It’s an ideal base for self-hosting services, offering superior control over data and strong security with the right setup. The NUC's small form factor and efficient power usage make it an optimal home server platform that scales well for many use cases.
- Text Extraction with OCR: Leveraging the
-
 @ d34e832d:383f78d0
2025-04-24 05:14:14
@ d34e832d:383f78d0
2025-04-24 05:14:14Idea
By instituting a robust network of conceptual entities, referred to as 'Obsidian nodes'—which are effectively discrete, idea-centric notes—researchers are empowered to establish a resilient and non-linear archival framework for knowledge accumulation.
These nodes, intricately connected via hyperlinks and systematically organized through the graphical interface of the Obsidian Canvas, facilitate profound intellectual exploration and the synthesis of disparate domains of knowledge.
Consequently, this innovative workflow paradigm emphasizes semantic precision and the interconnectedness of ideas, diverging from conventional, source-centric information architectures prevalent in traditional academic practices.
Traditional research workflows often emphasize organizing notes by source, resulting in static, siloed knowledge that resists integration and insight. With the rise of personal knowledge management (PKM) tools like Obsidian, it becomes possible to structure information in a way that mirrors the dynamic and interconnected nature of human thought.
At the heart of this approach are Obsidian nodes—atomic, standalone notes representing single ideas, arguments, or claims. These nodes form the basis of a semantic research network, made visible and manageable via Obsidian’s graph view and Canvas feature. This thesis outlines how such a framework enhances understanding, supports creativity, and aligns with best practices in information architecture.
Obsidian Nodes: Atomic Units of Thought
An Obsidian node is a note crafted to encapsulate one meaningful concept or question. It is:
- Atomic: Contains only one idea, making it easier to link and reuse.
- Context-Independent: Designed to stand on its own, without requiring the original source for meaning.
- Networked: Linked to other Obsidian nodes through backlinks and tags.
This system draws on the principles of the Zettelkasten method, but adapts them to the modern, markdown-based environment of Obsidian.
Benefits of Node-Based Note-Taking
- Improved Retrieval: Ideas can be surfaced based on content relevance, not source origin.
- Cross-Disciplinary Insight: Linking between concepts across fields becomes intuitive.
- Sustainable Growth: Each new node adds value to the network without redundancy.
Graph View: Visualizing Connections
Obsidian’s graph view offers a macro-level overview of the knowledge graph, showing how nodes interrelate. This encourages serendipitous discovery and identifies central or orphaned concepts that need further development.
- Clusters emerge around major themes.
- Hubs represent foundational ideas.
- Bridges between nodes show interdisciplinary links.
The graph view isn’t just a map—it’s an evolving reflection of intellectual progress.
Canvas: Thinking Spatially with Digital Notes
Obsidian Canvas acts as a digital thinking space. Unlike the abstract graph view, Canvas allows for spatial arrangement of Obsidian nodes, images, and ideas. This supports visual reasoning, ideation, and project planning.
Use Cases of Canvas
- Synthesizing Ideas: Group related nodes in physical proximity.
- Outlining Arguments: Arrange claims into narrative or logic flows.
- Designing Research Papers: Lay out structure and integrate supporting points visually.
Canvas brings a tactile quality to digital thinking, enabling workflows similar to sticky notes, mind maps, or corkboard pinning—but with markdown-based power and extensibility.
Template and Workflow
To simplify creation and encourage consistency, Obsidian nodes are generated using a templater plugin. Each node typically includes:
```markdown
{{title}}
Tags: #topic #field
Linked Nodes: [[Related Node]]
Summary: A 1-2 sentence idea explanation.
Source: [[Source Note]]
Date Created: {{date}}
```The Canvas workspace pulls these nodes as cards, allowing for arrangement, grouping, and visual tracing of arguments or research paths.
Discussion and Challenges
While this approach enhances creativity and research depth, challenges include:
- Initial Setup: Learning and configuring plugins like Templater, Dataview, and Canvas.
- Overlinking or Underlinking: Finding the right granularity in note-making takes practice.
- Scalability: As networks grow, maintaining structure and avoiding fragmentation becomes crucial.
- Team Collaboration: While Git can assist, Obsidian remains largely optimized for solo workflows.
Consider
Through the innovative employment of Obsidian's interconnected nodes and the Canvas feature, researchers are enabled to construct a meticulously engineered semantic architecture that reflects the intricate topology of their knowledge frameworks.
This paradigm shift facilitates a transformation of conventional note-taking, evolving this practice from a static, merely accumulative repository of information into a dynamic and adaptive cognitive ecosystem that actively engages with the user’s thought processes. With methodological rigor and a structured approach, Obsidian transcends its role as mere documentation software, evolving into both a secondary cognitive apparatus and a sophisticated digital writing infrastructure.
This dual functionality significantly empowers the long-term intellectual endeavors and creative pursuits of students, scholars, and lifelong learners, thereby enhancing their capacity for sustained engagement with complex ideas.
-
 @ d34e832d:383f78d0
2025-04-24 05:04:55
@ d34e832d:383f78d0
2025-04-24 05:04:55A Knowledge Management Framework for your Academic Writing
Idea Approach
The primary objective of this framework is to streamline and enhance the efficiency of several critical academic processes, namely the reading, annotation, synthesis, and writing stages inherent to doctoral studies.
By leveraging established best practices from various domains, including digital note-taking methodologies, sophisticated knowledge management techniques, and the scientifically-grounded principles of spaced repetition systems, this proposed workflow is adept at optimizing long-term retention of information, fostering the development of novel ideas, and facilitating the meticulous preparation of manuscripts. Furthermore, this integrated approach capitalizes on Zotero's robust annotation functionalities, harmoniously merged with Obsidian's Zettelkasten-inspired architecture, thereby enriching the depth and structural coherence of academic inquiry, ultimately leading to more impactful scholarly contributions.
Doctoral research demands a sophisticated approach to information management, critical thinking, and synthesis. Traditional systems of note-taking and bibliography management are often fragmented and inefficient, leading to cognitive overload and disorganized research outputs. This thesis proposes a workflow that leverages Zotero for reference management, Obsidian for networked note-taking, and Anki for spaced repetition learning—each component enhanced by a set of plugins, templates, and color-coded systems.
2. Literature Review and Context
2.1 Digital Research Workflows
Recent research in digital scholarship has highlighted the importance of structured knowledge environments. Tools like Roam Research, Obsidian, and Notion have gained traction among academics seeking flexibility and networked thinking. However, few workflows provide seamless interoperability between reference management, reading, and idea synthesis.
2.2 The Zettelkasten Method
Originally developed by sociologist Niklas Luhmann, the Zettelkasten ("slip-box") method emphasizes creating atomic notes—single ideas captured and linked through context. This approach fosters long-term idea development and is highly compatible with digital graph-based note systems like Obsidian.
3. Zotero Workflow: Structured Annotation and Tagging
Zotero serves as the foundational tool for ingesting and organizing academic materials. The built-in PDF reader is augmented through a color-coded annotation schema designed to categorize information efficiently:
- Red: Refuted or problematic claims requiring skepticism or clarification
- Yellow: Prominent claims, novel hypotheses, or insightful observations
- Green: Verified facts or claims that align with the research narrative
- Purple: Structural elements like chapter titles or section headers
- Blue: Inter-author references or connections to external ideas
- Pink: Unclear arguments, logical gaps, or questions for future inquiry
- Orange: Precise definitions and technical terminology
Annotations are accompanied by tags and notes in Zotero, allowing robust filtering and thematic grouping.
4. Obsidian Integration: Bridging Annotation and Synthesis
4.1 Plugin Architecture
Three key plugins optimize Obsidian’s role in the workflow:
- Zotero Integration (via
obsidian-citation-plugin): Syncs annotated PDFs and metadata directly from Zotero - Highlighter: Enables color-coded highlights in Obsidian, mirroring Zotero's scheme
- Templater: Automates formatting and consistency using Nunjucks templates
A custom keyboard shortcut (e.g.,
Ctrl+Shift+Z) is used to trigger the extraction of annotations into structured Obsidian notes.4.2 Custom Templating
The templating system ensures imported notes include:
- Citation metadata (title, author, year, journal)
- Full-color annotations with comments and page references
- Persistent notes for long-term synthesis
- An embedded bibtex citation key for seamless referencing
5. Zettelkasten and Atomic Note Generation
Obsidian’s networked note system supports idea-centered knowledge development. Each note captures a singular, discrete idea—independent of the source material—facilitating:
- Thematic convergence across disciplines
- Independent recombination of ideas
- Emergence of new questions and hypotheses
A standard atomic note template includes: - Note ID (timestamp or semantic UID) - Topic statement - Linked references - Associated atomic notes (via backlinks)
The Graph View provides a visual map of conceptual relationships, allowing researchers to track the evolution of their arguments.
6. Canvas for Spatial Organization
Obsidian’s Canvas plugin is used to mimic physical research boards: - Notes are arranged spatially to represent conceptual clusters or chapter structures - Embedded visual content enhances memory retention and creative thought - Notes and cards can be grouped by theme, timeline, or argumentative flow
This supports both granular research and holistic thesis design.
7. Flashcard Integration with Anki
Key insights, definitions, and questions are exported from Obsidian to Anki, enabling spaced repetition of core content. This supports: - Preparation for comprehensive exams - Retention of complex theories and definitions - Active recall training during literature reviews
Flashcards are automatically generated using Obsidian-to-Anki bridges, with tagging synced to Obsidian topics.
8. Word Processor Integration and Writing Stage
Zotero’s Word plugin simplifies: - In-text citation - Automatic bibliography generation - Switching between citation styles (APA, Chicago, MLA, etc.)
Drafts in Obsidian are later exported into formal academic writing environments such as Microsoft Word or LaTeX editors for formatting and submission.
9. Discussion and Evaluation
The proposed workflow significantly reduces friction in managing large volumes of information and promotes deep engagement with source material. Its modular nature allows adaptation for various disciplines and writing styles. Potential limitations include: - Initial learning curve - Reliance on plugin maintenance - Challenges in team-based collaboration
Nonetheless, the ability to unify reading, note-taking, synthesis, and writing into a seamless ecosystem offers clear benefits in focus, productivity, and academic rigor.
10. Consider
This idea demonstrates that a well-structured digital workflow using Zotero and Obsidian can transform the PhD research process. It empowers researchers to move beyond passive reading into active knowledge creation, aligned with the long-term demands of scholarly writing. Future iterations could include AI-assisted summarization, collaborative graph spaces, and greater mobile integration.
9. Evaluation Of The Approach
While this workflow offers significant advantages in clarity, synthesis, and long-term idea development, several limitations must be acknowledged:
-
Initial Learning Curve: New users may face a steep learning curve when setting up and mastering the integrated use of Zotero, Obsidian, and their associated plugins. Understanding markdown syntax, customizing templates in Templater, and configuring citation keys all require upfront time investment. However, this learning period can be offset by the long-term gains in productivity and mental clarity.
-
Plugin Ecosystem Volatility: Since both Obsidian and many of its key plugins are maintained by open-source communities or individual developers, updates can occasionally break workflows or require manual adjustments.
-
Interoperability Challenges: Synchronizing metadata, highlights, and notes between systems (especially on multiple devices or operating systems) may present issues if not managed carefully. This includes Zotero’s Better BibTeX keys, Obsidian sync, and Anki integration.
-
Limited Collaborative Features: This workflow is optimized for individual use. Real-time collaboration on notes or shared reference libraries may require alternative platforms or additional tooling.
Despite these constraints, the workflow remains highly adaptable and has proven effective across disciplines for researchers aiming to build a durable intellectual infrastructure over the course of a PhD.
9. Evaluation Of The Approach
While the Zotero–Obsidian workflow dramatically improves research organization and long-term knowledge retention, several caveats must be considered:
-
Initial Learning Curve: Mastery of this workflow requires technical setup and familiarity with markdown, citation keys, and plugin configuration. While challenging at first, the learning effort is front-loaded and pays off in efficiency over time.
-
Reliance on Plugin Maintenance: A key risk of this system is its dependence on community-maintained plugins. Tools like Zotero Integration, Templater, and Highlighter are not officially supported by Obsidian or Zotero core teams. This means updates or changes to the Obsidian API or plugin repository may break functionality or introduce bugs. Active plugin support is crucial to the system’s longevity.
-
Interoperability and Syncing Issues: Managing synchronization across Zotero, Obsidian, and Anki—especially across multiple devices—can lead to inconsistencies or data loss without careful setup. Users should ensure robust syncing solutions (e.g. Obsidian Sync, Zotero WebDAV, or GitHub backup).
-
Limited Collaboration Capabilities: This setup is designed for solo research workflows. Collaborative features (such as shared note-taking or group annotations) are limited and may require alternate solutions like Notion, Google Docs, or Overleaf when working in teams.
The integration of Zotero with Obsidian presents a notable advantage for individual researchers, exhibiting substantial efficiency in literature management and personal knowledge organization through its unique workflows. However, this model demonstrates significant deficiencies when evaluated in the context of collaborative research dynamics.
Specifically, while Zotero facilitates the creation and management of shared libraries, allowing for the aggregation of sources and references among users, Obsidian is fundamentally limited by its lack of intrinsic support for synchronous collaborative editing functionalities, thereby precluding simultaneous contributions from multiple users in real time. Although the application of version control systems such as Git has the potential to address this limitation, enabling a structured mechanism for tracking changes and managing contributions, the inherent complexity of such systems may pose a barrier to usability for team members who lack familiarity or comfort with version control protocols.
Furthermore, the nuances of color-coded annotation systems and bespoke personal note taxonomies utilized by individual researchers may present interoperability challenges when applied in a group setting, as these systems require rigorously defined conventions to ensure consistency and clarity in cross-collaborator communication and understanding. Thus, researchers should be cognizant of the challenges inherent in adapting tools designed for solitary workflows to the multifaceted requirements of collaborative research initiatives.
-
 @ 5188521b:008eb518
2025-04-24 07:34:50
@ 5188521b:008eb518
2025-04-24 07:34:50We are losing our freedom.
Don't believe me? Data published by the Cato Institute suggests that 74% of Americans are concerned they could lose freedoms.
But what do we really mean by 'freedom'?
The Cambridge Dictionary defines ‘freedom’ as follows: the condition or right of being able or allowed to do, say, think, etc. whatever you want to, without being controlled or limited.
Despite this clear definition, freedom means different things to different people: it might also refer to freedom of movement, private property rights, free markets, and freedom from violence.
Freedom fiction (also known as Libertarian fiction) denotes fictional stories intrinsically linked to these ideas or, more likely, the sometimes vain pursuit of this idea.
If dystopian fiction is overly bleak, perfectly captured by the image of a boot on the reader's neck, libertarian stories should offer just a glimmer of hope.
What is freedom fiction?
If dystopia, sci-fi, fantasy, and horror are genres, i.e., styles of fiction that must encompass certain tropes, freedom fiction could more generally be considered a category that explores freedom as a theme, without necessarily being part of a specific genre.
Freedom fiction primarily concerns itself with the overarching topics of individual liberty and sovereignty, conflict with authoritarian or surveillance states, and the restoration or preservation of rights that citizens of the Western world have come to expect: privacy, freedom of speech, the right to private property, and freedom to transact and form contracts.
Though enjoying something of a resurgence in recent decades and especially post Covid, freedom fiction is not new, and famous/infamous novels throughout the centuries could be retroactively categorised as freedom fiction.
Think of The Epic of Gilgamesh (2000BC), Greek tragedies (500BC), Uncle Tom's Cabin by Harriet Beecher Stowe (1852), which helped fuel the anti-slavery movement, or We by Yevgeny Zamyatin, written over 100 years ago.
Today, freedom fiction is an emerging category that includes the revival of the cypherpunk movement, as privacy technologies such as Bitcoin seek to remove the reliance on the banking system, which has become an effective method of control for the establishment.
Why read freedom fiction?
 Storytelling is a tradition as old as humanity itself, created to share the joy and wonder of imagined worlds. Fiction can also serve as a warning of what might come, and playing out “what if?” scenarios in our minds can help us in the real world, too.
Storytelling is a tradition as old as humanity itself, created to share the joy and wonder of imagined worlds. Fiction can also serve as a warning of what might come, and playing out “what if?” scenarios in our minds can help us in the real world, too.Any individual interested in escaping the modern debt-slavery rat race we’ve found ourselves forced into can enjoy freedom stories with a greater and deeper understanding of just how real this “fiction” could be in the future.
Spiking interest
Data from Google Trends shows that in the United Kingdom — a nation increasingly concerned with policing speech, surveillance and other dystopic methods — interest in freedom has been spiking in the past five years, centred in England.
 Source: Google Trends
Source: Google TrendsNow let’s take a look at the data for the United States:
 Despite a lower interest overall, the spike in 2023 mirrors that of the UK. Perhaps this was due to an event featured in the news or even a brand name or TikTok trend.
Despite a lower interest overall, the spike in 2023 mirrors that of the UK. Perhaps this was due to an event featured in the news or even a brand name or TikTok trend.It is interesting to note that although a great number of Amercians fear losing their freedoms, fewer are searching how to protect them.
One reason for the rise in freedom fiction could be that Libertarian thinkers, praxeologists, and freedom maximalists seek to alert the populace through emotive stories. Few, it seems, are awakened when presented with legacy media propaganda and government messages.
The benefits & outcomes of reading freedom fiction
Once a human mind has acquired a taste for freedom fiction, there are numerous benefits and likely outcomes that will arise as a result:
Benefits:
- Broadened perspective and understanding of historical issues
- Increased empathy and social understanding
- Inspiration, motivation & empowerment
- Critical thinking skills & awareness
- Emotional connection
Once the reader has enjoyed these benefits, it is likely they will put their newfound understanding to action, bringing about outcomes like these.
Outcomes:
- Appreciation of and gratitude for freedom
- Informed civic engagement
- Agency for social change
- Personal growth
It would appear, then, that at some point, freedom fiction will have a transformative impact on the social demographics of the civilised world. As popular Netflix shows like Black Mirror highlight our reliance and overreliance on digital media, and governments continue to censor user-generated content posted socially, we must ask ourselves, when exactly will we wake up to what is happening?
We are more connected, but more controlled, than ever. How can we use the tools that enslave us to liberate us? Perhaps through sharing stories.
Aspects of freedom, genres, and time periods
Freedom fiction is a broad spectrum, encompassing various aspects, genres and time periods.
Aspects — privacy, freedom of speech, wrongful imprisonment, oppression, discrimination, government overreach, surveilance, debanking, censorship, confiscation, forced separation and more.
Genres — horror, sci-fi, fantasy, thriller and even young adult romance stories can contribute to the growing canon of libertarian-themed fiction.
Time periods — slavery in the past, alien invasions in the future, totalitarian governments in the present. Freedom fiction can relate to any time period.
15+ Classic Freedom-themed Books
 In no particular order, here are 15 of the greatest examples of freedom stories from modern times:
In no particular order, here are 15 of the greatest examples of freedom stories from modern times:-
Nineteen Eighty-Four by George Orwell (1949): A dystopian classic where the Party controls every aspect of people's lives, and Winston Smith rebels against the oppressive regime.
Reason to read: Offers a chilling and thought-provoking exploration of totalitarianism, mass surveillance, and the importance of individual thought and truth.
-
The Handmaid's Tale by Margaret Atwood (1985): In a totalitarian regime where women are stripped of their rights, Offred fights for survival and a chance to regain her freedom.
Reason to read: A haunting story that explores themes of feminism, oppression, and resistance, with a timely warning about the dangers of religious extremism and the fragility of women's rights.
-
Brave New World by Aldous Huxley (1932): A satirical look at a future society where people are genetically engineered and conditioned to conform, and a "savage" challenges their way of life.
Reason to read: Provides an unsettling vision of a future where happiness is manufactured at the cost of individuality, freedom, and genuine human connection.
-
Fahrenheit 451 by Ray Bradbury (1953): In a world where books are banned, Guy Montag, a fireman, discovers the power of knowledge and fights for intellectual freedom.
Reason to read: A passionate defense of the importance of books, ideas, and intellectual freedom, and a warning against censorship.
-
The Giver by Lois Lowry (1993): A young boy named Jonas discovers the dark secrets of his seemingly Utopian society, where there is no pain, sadness, or freedom of choice.
Reason to read: A thought-provoking exploration of utopia, dystopia, and the importance of memory, emotion, and individual choice in a truly human life.
-
One Flew Over the Cuckoo's Nest by Ken Kesey (1962): Randle McMurphy challenges the authority of a mental institution, becoming a symbol of rebellion and the fight for individual freedom.
Reason to read: A powerful and moving story about the struggle against forced conformity and the importance of individuality, even in the face of oppressive systems.
-
Little Brother by Cory Doctorow (2008): This contemporary science fiction novel explores themes of government surveillance, digital rights, and the power of decentralized networks in challenging authority.
Reason to read: a timely exploration of digital surveillance, government overreach, and the power of youthful activism in defending civil liberties in the modern age.
-
Beloved by Toni Morrison (1987): Set after the American Civil War, this novel explores the psychological and emotional scars of slavery and the struggle for freedom and identity.
Reason to read: A masterpiece that delves into the legacy of slavery and its enduring impact on identity, memory, and the quest for freedom.
-
The Book Thief by Markus Zusak (2005): In Nazi Germany, a young girl named Liesel Meminger finds solace in stolen books and discovers the power of words to resist oppression and find freedom.
Reason to read: A beautifully written story about the power of words to nourish the soul, resist oppression, and find hope and freedom in the darkest of times.
-
Animal Farm by George Orwell (1945): An allegorical novella about a revolution on a farm that turns into a totalitarian dictatorship, highlighting the dangers of unchecked power, Communism, and the loss of freedom.
Reason to read: A timeless allegory that exposes the corruption of revolutions, the fragility of freedom, and the importance of resistance against tyranny.
-
A Thousand Splendid Suns by Khaled Hosseini (2007): This novel tells the story of two Afghan women whose lives intersect under the oppressive Taliban regime, and their fight for survival and freedom.
Reason to read: An eye-opening portrayal of the resilience and strength of women in the face of oppression, and a powerful story about the universal desire for dignity.
-
The Underground Railroad by Colson Whitehead (2016): A unique novel that reimagines the Underground Railroad as a literal railroad, and follows a slave's journey.
Reason to read: A compelling blend of historical fiction and magical realism that offers a fresh perspective on the history of slavery and the enduring quest for freedom.
-
Anthem by Ayn Rand (1938): A novella set in a collectivist future where the concept of "I" has been eradicated. It follows one man's rediscovery of individualism and his rebellion against the oppressive society.
Reason to read: a novella that champions radical individualism against the suffocating conformity of collectivist ideology.
-
The Count of Monte Cristo by Alexandre Dumas (1844-46): Edmond Dantès is wrongly imprisoned and seeks revenge and freedom after years of captivity.
Reason to read: An exciting tale of betrayal, revenge, and ultimate triumph, with a focus on themes of justice, freedom, and the resilience of the human spirit.
-
Snow Crash (1992) and Cryptonomicon (1999) by Neal Stephenson: While not strictly libertarian manifestos, these novels explore themes of individual freedom, the power of information, decentralized systems, and critiques of centralized authority in engaging and complex ways.
Reason to read: these books are considered modern cypherpunk classics. They are rich in detail and the perfect starting place to learn more about the genre and why it is important for freedom.
 ## Lesser-known Freedom Books
## Lesser-known Freedom BooksHere are 15 lesser-known, more modern books that also explore the theme of freedom:
- Exit West by Mohsin Hamid (2017): This novel uses magical realism to depict refugees fleeing a war-torn country and seeking freedom and safety in an uncertain world.
- A Lodging of Wayfaring Men by Paul Rosenberg (2007): a libertarian novel based on real events that explores themes of individual sovereignty and free markets.
- The Probability Broach by L. Neil Smith (1979): An alternate history novel where a slight change in the Declaration of Independence leads to a libertarian society in North America. It's the first in Smith's "North American Confederacy" series.
- The Beekeeper of Aleppo by Christy Lefteri (2019): This tells the story of beekeepers forced to flee Syria and their struggle to find freedom and rebuild their lives in a new country.
- Alongside Night by J. Neil Schulman (1979): A dystopian thriller depicting the collapse of the US government and the rise of a libertarian underground.
- Freehold by Michael Z. Williamson (2004): A military science fiction series that portrays a future where individuals have seceded from Earth's controlling government to establish independent, more libertarian colonies.
- No Truce with Kings by Poul Anderson (1963): A novella that won the Hugo Award, depicting a future where scientific progress has led to a world of isolated, self-sufficient individuals, challenging traditional notions of society and government.
- A Passage North by Anuk Arudpragasam (2021): This Booker Prize-nominated novel explores the aftermath of the Sri Lankan Civil War and the complexities of memory, trauma, and the search for inner freedom.
- Kings of the High Frontier by Victor Koman (1996): A hard science fiction novel exploring themes of entrepreneurship and individual liberty in space.
- This Perfect Day by Ira Levin (1970): A dystopian novel where a seemingly Utopian global society controls every aspect of individual life, raising questions about freedom versus engineered happiness.
- Wasp by Eric Frank Russell (1957): A story containing acts of terrorism against oppressive aliens. A notable example of a single individual disrupting a larger, controlling power.
- The Peace War by Vernor Vinge (1984): A ruthless organization, the Peace Authority, uses impenetrable force fields to end war but suppresses technology and individual liberty, leading a group of rebels to fight for the freedom to advance and determine their own future.
- Starship Troopers by Robert A. Heinlein (1959): Heinlein was a prolific science fiction writer whose works frequently touch upon libertarian themes. Starship Troopers explores the ideas of civic virtue and individual responsibility.
- Live Free or Die by John Ringo (2010) follows Tyler Vernon, a fiercely independent and resourceful entrepreneur who stands up against alien oppressors and Earth's own bureaucratic tendencies to forge a path to true liberty and self-determination for humanity.
- Darkship Thieves by Sarah Hoyt (2010): Winner of the Prometheus Award for Best Libertarian SF Novel. This book follows Athena Hera Sinistra, a genetically engineered woman who escapes a tyrannical Earth to a freer society in space.
Freedom Publishers
In addition to the many works of libertarian fiction, a number of publishers are beginning to focus on stories which promote freedom.
- Liberty Island: This publisher focuses on science fiction and fantasy with libertarian and individualist themes.
- Fox News Books: While a mainstream publisher, it has been known to publish fiction with libertarian themes or by authors who are considered libertarian.
- Defiance Press & Publishing: This independent publisher openly states its commitment to publishing conservative and libertarian authors across fiction and non-fiction genres.
- Konsensus Network: A publisher that specifically promotes libertarian themes and bitcoin authors.
- All Seasons Press: Founded by former executives from Simon & Schuster and Hachette, this independent press aims to be a home for conservative voices.
- Baen Books: This is a well-known publisher, particularly in science fiction and fantasy, that often features authors and stories exploring themes of individual liberty, self-reliance, and limited government.
- Morlock Publishing: This small press specializes in science fiction with themes often including aspects of anarcho-capitalism and libertarian rebellion.
- Heresy Press (now an imprint of Skyhorse Publishing): While broader in its scope, Heresy Press aimed to publish "uncensored, outspoken, and free-spirited books" which can include libertarian viewpoints in fiction.
- Libertarian Futurist Society (LFS) (indirectly): While not a traditional publisher, the LFS sponsors the Prometheus Award and promotes libertarian science fiction. Their website and related platforms can be resources for finding authors and works, which are then published by various houses.
Recent Trends in Libertarian Fiction:
 Konsensus Network’s new imprint, 21 Futures, is building a movement centred on freedom fiction, a movement in which emerging and established writers can contribute their storytelling media to anthologies and blogs, as well as publish their own individual works.
Konsensus Network’s new imprint, 21 Futures, is building a movement centred on freedom fiction, a movement in which emerging and established writers can contribute their storytelling media to anthologies and blogs, as well as publish their own individual works.To date, two short story anthologies are available from 21 Futures:
Tales from the Timechain: the world’s first Bitcoin-fiction anthology.
21 writers examine how the hardest sound money ever created can restore freedom and liberty to mankind.
Financial Fallout: in this recently-released anthology, 21 writers weave financial dystopia from across a broader spectrum of freedom fiction, sewing seeds of eventual hope.
In addition to 21 Futures, a host of self-published and even best-selling fiction on the theme of bitcoin is now available. The Rapid Rise of Bitcoin Fiction documents the history and current trends in this genre.
 ## What happens next?
## What happens next?As governments tighten their grip on our data and our freedoms erode, we expect that freedom fiction will become a wider phenomenon. It is our hope and belief that Konsensus Network and 21 Futures will help drive growth in the genre and better understanding of how to protect individual freedom through our multimedia publications.
Follow our socials to keep up to date on future releases.
This blog was originally published on the 21 Futures blog by Alex Boast.
Alex is a web3 writer, ghost writer and ghost story writer. He’s a novelist and poet from England who loves to work with other writers as a coach, mentor and friend. You can find him on LinkedIn.
-
 @ d34e832d:383f78d0
2025-04-24 02:56:59
@ d34e832d:383f78d0
2025-04-24 02:56:591. The Ledger or Physical USD?
Bitcoin embodies a paradigmatic transformation in the foundational constructs of trust, ownership, and value preservation within the context of a digital economy. In stark contrast to conventional financial infrastructures that are predicated on centralized regulatory frameworks, Bitcoin operationalizes an intricate interplay of cryptographic techniques, consensus-driven algorithms, and incentivization structures to engender a decentralized and censorship-resistant paradigm for the transfer and safeguarding of digital assets. This conceptual framework elucidates the pivotal mechanisms underpinning Bitcoin's functional architecture, encompassing its distributed ledger technology (DLT) structure, robust security protocols, consensus algorithms such as Proof of Work (PoW), the intricacies of its monetary policy defined by the halving events and limited supply, as well as the broader implications these components have on stakeholder engagement and user agency.
2. The Core Functionality of Bitcoin
At its core, Bitcoin is a public ledger that records ownership and transfers of value. This ledger—called the blockchain—is maintained and verified by thousands of decentralized nodes across the globe.
2.1 Public Ledger
All Bitcoin transactions are stored in a transparent, append-only ledger. Each transaction includes: - A reference to prior ownership (input) - A transfer of value to a new owner (output) - A digital signature proving authorization
2.2 Ownership via Digital Signatures
Bitcoin uses asymmetric cryptography: - A private key is known only to the owner and is used to sign transactions. - A public key (or address) is used by the network to verify the authenticity of the transaction.
This system ensures that only the rightful owner can spend bitcoins, and that all network participants can independently verify that the transaction is valid.
3. Decentralization and Ledger Synchronization
Unlike traditional banking systems, which rely on a central institution, Bitcoin’s ledger is decentralized: - Every node keeps a copy of the blockchain. - No single party controls the system. - Updates to the ledger occur only through network consensus.
This decentralization ensures fault tolerance, censorship resistance, and transparency.
4. Preventing Double Spending
One of Bitcoin’s most critical innovations is solving the double-spending problem without a central authority.
4.1 Balance Validation
Before a transaction is accepted, nodes verify: - The digital signature is valid. - The input has not already been spent. - The sender has sufficient balance.
This is made possible by referencing previous transactions and ensuring the inputs match the unspent transaction outputs (UTXOs).
5. Blockchain and Proof-of-Work
To ensure consistency across the distributed network, Bitcoin uses a blockchain—a sequential chain of blocks containing batches of verified transactions.
5.1 Mining and Proof-of-Work
Adding a new block requires solving a cryptographic puzzle, known as Proof-of-Work (PoW): - The puzzle involves finding a hash value that meets network-defined difficulty. - This process requires computational power, which deters tampering. - Once a block is validated, it is propagated across the network.
5.2 Block Rewards and Incentives
Miners are incentivized to participate by: - Block rewards: New bitcoins issued with each block (initially 50 BTC, halved every ~4 years). - Transaction fees: Paid by users to prioritize their transactions.
6. Network Consensus and Security
Bitcoin relies on Nakamoto Consensus, which prioritizes the longest chain—the one with the most accumulated proof-of-work.
- In case of competing chains (forks), the network chooses the chain with the most computational effort.
- This mechanism makes rewriting history or creating fraudulent blocks extremely difficult, as it would require control of over 50% of the network's total hash power.
7. Transaction Throughput and Fees
Bitcoin’s average block time is 10 minutes, and each block can contain ~1MB of data, resulting in ~3–7 transactions per second.
- During periods of high demand, users compete by offering higher transaction fees to get included faster.
- Solutions like Lightning Network aim to scale transaction speed and lower costs by processing payments off-chain.
8. Monetary Policy and Scarcity
Bitcoin enforces a fixed supply cap of 21 million coins, making it deflationary by design.
- This limited supply contrasts with fiat currencies, which can be printed at will by central banks.
- The controlled issuance schedule and halving events contribute to Bitcoin’s store-of-value narrative, similar to digital gold.
9. Consider
Bitcoin integrates advanced cryptographic methodologies, including public-private key pairings and hashing algorithms, to establish a formidable framework of security that underpins its operation as a digital currency. The economic incentives are meticulously structured through mechanisms such as mining rewards and transaction fees, which not only incentivize network participation but also regulate the supply of Bitcoin through a halving schedule intrinsic to its decentralized protocol. This architecture manifests a paradigm wherein individual users can autonomously oversee their financial assets, authenticate transactions through a rigorously constructed consensus algorithm, specifically the Proof of Work mechanism, and engage with a borderless financial ecosystem devoid of traditional intermediaries such as banks. Despite the notable challenges pertaining to transaction throughput scalability and a complex regulatory landscape that intermittently threatens its proliferation, Bitcoin steadfastly persists as an archetype of decentralized trust, heralding a transformative shift in financial paradigms within the contemporary digital milieu.
10. References
- Nakamoto, S. (2008). Bitcoin: A Peer-to-Peer Electronic Cash System.
- Antonopoulos, A. M. (2017). Mastering Bitcoin: Unlocking Digital Cryptocurrencies.
- Bitcoin.org. (n.d.). How Bitcoin Works
-
 @ d34e832d:383f78d0
2025-04-24 00:56:03
@ d34e832d:383f78d0
2025-04-24 00:56:03WebSocket communication is integral to modern real-time web applications, powering everything from chat apps and online gaming to collaborative editing tools and live dashboards. However, its persistent and event-driven nature introduces unique debugging challenges. Traditional browser developer tools provide limited insight into WebSocket message flows, especially in complex, asynchronous applications.
This thesis evaluates the use of Chrome-based browser extensions—specifically those designed to enhance WebSocket debugging—and explores how visual event tracing improves developer experience (DX). By profiling real-world applications and comparing built-in tools with popular WebSocket DevTools extensions, we analyze the impact of visual feedback, message inspection, and timeline tracing on debugging efficiency, code quality, and development speed.
The Idea
As front-end development evolves, WebSockets have become a foundational technology for building reactive user experiences. Debugging WebSocket behavior, however, remains a cumbersome task. Chrome DevTools offers a basic view of WebSocket frames, but lacks features such as message categorization, event correlation, or contextual logging. Developers often resort to
console.logand custom logging systems, increasing friction and reducing productivity.This research investigates how browser extensions designed for WebSocket inspection—such as Smart WebSocket Client, WebSocket King Client, and WSDebugger—can enhance debugging workflows. We focus on features that provide visual structure to communication patterns, simplify message replay, and allow for real-time monitoring of state transitions.
Related Work
Chrome DevTools
While Chrome DevTools supports WebSocket inspection under the Network > Frames tab, its utility is limited: - Messages are displayed in a flat, unstructured stream. - No built-in timeline or replay mechanism. - Filtering and contextual debugging features are minimal.
WebSocket-Specific Extensions
Numerous browser extensions aim to fill this gap: - Smart WebSocket Client: Allows custom message sending, frame inspection, and saved session reuse. - WSDebugger: Offers structured logging and visualization of message flows. - WebSocket Monitor: Enables real-time monitoring of multiple connections with UI overlays.
Methodology
Tools Evaluated:
- Chrome DevTools (baseline)
- Smart WebSocket Client
- WSDebugger
- WebSocket King Client
Evaluation Criteria:
- Real-time message monitoring
- UI clarity and UX consistency
- Support for message replay and editing
- Message categorization and filtering
- Timeline-based visualization
Test Applications:
- A collaborative markdown editor
- A multiplayer drawing game (WebSocket over Node.js)
- A lightweight financial dashboard (stock ticker)
Findings
1. Enhanced Visibility
Extensions provide structured visual representations of WebSocket communication: - Grouped messages by type (e.g., chat, system, control) - Color-coded frames for quick scanning - Collapsible and expandable message trees
2. Real-Time Inspection and Replay
- Replaying previous messages with altered payloads accelerates bug reproduction.
- Message history can be annotated, aiding team collaboration during debugging.
3. Timeline-Based Analysis
- Extensions with timeline views help identify latency issues, bottlenecks, and inconsistent message pacing.
- Developers can correlate message sequences with UI events more intuitively.
4. Improved Debugging Flow
- Developers report reduced context-switching between source code and devtools.
- Some extensions allow breakpoints or watchers on WebSocket events, mimicking JavaScript debugging.
Consider
Visual debugging extensions represent a key advancement in tooling for real-time application development. By extending Chrome DevTools with features tailored for WebSocket tracing, developers gain actionable insights, faster debugging cycles, and a better understanding of application behavior. Future work should explore native integration of timeline and message tagging features into standard browser DevTools.
Developer Experience and Limitations
Visual tools significantly enhance the developer experience (DX) by reducing friction and offering cognitive support during debugging. Rather than parsing raw JSON blobs manually or tracing asynchronous behavior through logs, developers can rely on intuitive UI affordances such as real-time visualizations, message filtering, and replay features.
However, some limitations remain:
- Lack of binary frame support: Many extensions focus on text-based payloads and may not correctly parse or display binary frames.
- Non-standard encoding issues: Applications using custom serialization formats (e.g., Protocol Buffers, MsgPack) require external decoding tools or browser instrumentation.
- Extension compatibility: Some extensions may conflict with Content Security Policies (CSP) or have limited functionality when debugging production sites served over HTTPS.
- Performance overhead: Real-time visualization and logging can add browser CPU/memory overhead, particularly in high-frequency WebSocket environments.
Despite these drawbacks, the overall impact on debugging efficiency and developer comprehension remains highly positive.
Developer Experience and Limitations
Visual tools significantly enhance the developer experience (DX) by reducing friction and offering cognitive support during debugging. Rather than parsing raw JSON blobs manually or tracing asynchronous behavior through logs, developers can rely on intuitive UI affordances such as live message streams, structured views, and interactive inspection of frames.
However, some limitations exist:
- Security restrictions: Content Security Policy (CSP) and Cross-Origin Resource Sharing (CORS) can restrict browser extensions from accessing WebSocket frames in production environments.
- Binary and custom formats: Extensions may not handle binary frames or non-standard encodings (e.g., Protocol Buffers) without additional tooling.
- Limited protocol awareness: Generic tools may not fully interpret application-specific semantics, requiring context from the developer.
- Performance trade-offs: Logging and rendering large volumes of data can cause UI lag, especially in high-throughput WebSocket apps.
Despite these constraints, DevTools extensions continue to offer valuable insight during development and testing stages.
Applying this analysis to relays in the Nostr protocol surfaces some fascinating implications about traffic analysis, developer tooling, and privacy risks, even when data is cryptographically signed. Here's how the concepts relate:
🧠 What This Means for Nostr Relays
1. Traffic Analysis Still Applies
Even though Nostr events are cryptographically signed and, optionally, encrypted (e.g., DMs), relay communication is over plaintext WebSockets or WSS (WebSocket Secure). This means:
- IP addresses, packet size, and timing patterns are all visible to anyone on-path (e.g., ISPs, malicious actors).
- Client behavior can be inferred: Is someone posting, reading, or just idling?
- Frequent "kind" values (like
kind:1for notes orkind:4for encrypted DMs) produce recognizable traffic fingerprints.
🔍 Example:
A pattern like: -
client → relay: small frame at intervals of 30s -relay → client: burst of medium frames …could suggest someone is polling for new posts or using a chat app built on Nostr.
2. DevTools for Nostr Client Devs
For client developers (e.g., building on top of
nostr-tools), browser DevTools and WebSocket inspection make debugging much easier:- You can trace real-time Nostr events without writing logging logic.
- You can verify frame integrity, event flow, and relay responses instantly.
- However, DevTools have limits when Nostr apps use:
- Binary payloads (e.g., zlib-compressed events)
- Custom encodings or protocol adaptations (e.g., for mobile)
3. Fingerprinting Relays and Clients
- Each relay has its own behavior: how fast it responds, whether it sends OKs, how it deals with malformed events.
- These can be fingerprinted by adversaries to identify which software is being used (e.g.,
nostr-rs-relay,strfry, etc.). - Similarly, client apps often emit predictable
REQ,EVENT,CLOSEsequences that can be fingerprinted even over WSS.
4. Privacy Risks
Even if DMs are encrypted: - Message size and timing can hint at contents ("user is typing", long vs. short message, emoji burst, etc.) - Public relays might correlate patterns across multiple clients—even without payload access. - Side-channel analysis becomes viable against high-value targets.
5. Mitigation Strategies in Nostr
Borrowing from TLS and WebSocket security best practices:
| Strategy | Application to Nostr | |-----------------------------|----------------------------------------------------| | Padding messages | Normalize
EVENTsize, especially for DMs | | Batching requests | Send multipleREQsubscriptions in one frame | | Randomize connection times | Avoid predictable connection schedules | | Use private relays / Tor| Obfuscate source IP and reduce metadata exposure | | Connection reuse | Avoid per-event relay opens, use persistent WSS |
TL;DR for Builders
If you're building on Nostr and care about privacy, WebSocket metadata is a leak. The payload isn't the only thing that matters. Be mindful of event timing, size, and structure, even over encrypted channels.
-
 @ a296b972:e5a7a2e8
2025-04-23 20:40:35
@ a296b972:e5a7a2e8
2025-04-23 20:40:35Aus der Ferne sieht man nur ein Gefängnis aus Beton. Doch wenn man näher herankommt, sieht man, dass die Mauern schon sehr brüchig sind und das Regenwasser mit jedem Schauer tiefer in das Gemäuer eindringt. Da bleibt es. Bis die Temperaturen unter Null gehen und das Wasser gefriert. Jetzt entfaltet das Eis seine physikalische Kraft, es rückt dem Beton zu leibe, es dehnt sich aus und sprengt ihn.
Das geht nun schon fünf Jahre so. Fünf Jahre immer wieder Regen, abwechselnd mit Frost und Eis. Die Risse werden größer, der Beton immer morscher. So lange, bis die Mauern ihre Tragfähigkeit verlieren und einstürzen.
Was soll das? Fängt da einer an zu spinnen? Wozu diese Metapher?
Hätte man zu Anfang gleich geschrieben: Wir, die kritischen Menschen, die sich der Wahrheit verpflichtet haben, sitzen in unserer Blase wie in einem Gefängnis und erreichen die da draußen nicht. Da hätten sicher viele gesagt: Oh, da will aber jemand die Opferrolle in vollen Zügen auskosten. Nee, nee, wir sind keine Opfer, wir sind Täter. Wir sammeln und bewahren die ständig neu dazukommenden Erkenntnisse der Wissenschaft und politischen Lügereien. Wir lernen Bücher auswendig, bevor die Feuerwehr kommt und sie verbrennt.
„Fahrenheit 451“
https://www.youtube.com/watch?v=P3Kx-uiP0bY
https://www.youtube.com/watch?v=TsNMxUSCKWo
„Das Haus ist für unbewohnbar erklärt worden und muss verbrannt werden.“
So primitiv geht man heute nicht mehr vor. Heute stehen die Feuerwehrmänner und ihre Erfüllungsgehilfen um 6 Uhr morgens im Türrahmen, nehmen Mobiltelefon und Laptop mit, betreiben De-Banking und vernichten die wirtschaftliche Existenz.
Und ja, es gibt Tage, da fühlt man sich trotzdem wie im Informationsgefängnis. Das hängt von der Tageskondition ab. Der öffentlich-rechtliche Rundfunk ist die Gefängnisküche. Zubereitet werden fade Speisen mit sich ständig wiederholenden Zutaten. Heraus kommt ein Gericht, eine Pampe, wie die tagesschau. LAAAANGWEILIG!
Man glaubt, Informationen und kritische Äußerungen gegenüber dem Mainstream-Einheitsbrei bleiben in den Gefängnismauern, der Blase, schaffen es nicht über die Mauer nach draußen, in die vermeintliche Freiheit. Neue Erkenntnisse werden nur innerhalb der Mauern weitergegeben. Ein neuer Kanal, steigende Abonnenten. Doch wer sind die? Welche von da draußen, in der sogenannten Freiheit, oder doch wieder immer dieselben üblichen Verdächtigen? Die da draußen haben uns doch schon längst geblockt oder gleich gelöscht. Mit Gedankenverbrechern will man nichts zu tun haben.
Hallo, ihr da draußen: Wir sind unschuldig. Unser einziges Verbrechen ist, dass wir Informationen verbreiten, die euch da draußen nicht gefallen, weil sie euch nicht in den Kram passen. Für euch sind wir eine Bedrohung, weil diese Informationen auf euch weltbilderschütternd wirken. Wir sprechen das aus, was viele sich nicht einmal trauen zu denken. Ihr habt Angst vor der Freiheit. Nicht wir sitzen ein, sondern ihr. In einem Freiluft-Gefängnis. Wir decken die Lügen auf, die da draußen, außerhalb der Mauern verbreitet werden. Wir sind nicht die Erfinder der Lügen, sondern nur die Überbringer der schlechten Botschaften.
Es ist leichter Menschen zu lieben, von denen man belogen wird, als Menschen zu lieben, die einem sagen, dass man belogen wird.
Mit aller Kraft wird versucht, die Menschen in Einzelhaft zu setzen. In der Summe ist das die gesellschaftliche Spaltung. Gleichzeitig wird an den Zusammenhalt appelliert, obwohl man genau das Gegenteil davon vorantreibt.
Es geht auch nicht um Mitleid. Es geht um das Verdeutlichen der vorhandenen medialen Axt, mit der ganze Nationen in zwei Teile zerhackt werden. Auf politischer Ebene wird viel dafür getan, dass sich das auch ja nicht ändert. Ein Volk in Angst ist gut zu regieren. Teile und herrsche. Die Sprüche können wir alle schon rückwärts auf der Blockflöte pfeifen.
An den vier Ecken des Informations-Gefängnisses stehen Wachtürme, mit Wärtern, ausgebildet vom DSA, vom Digital Services Act, finanziert vom Wahrheitsministerium, dass ständig aktualisierend darüber befindet, was heute gerade aktuell als „Hass und Hetze“ en vogue ist. Es kommt eben immer darauf an, wer diese Begriffe aus der bisher dunkelsten Zeit in der deutschen Geschichte benutzt. Das hatten wir alles schon einmal. Das brauchen wir nicht mehr!
Schon in der Bibel steht das Gebot: Du sollst nicht lügen. Da steht nicht: Lügen verboten! Das Titelbild gehört leider auch zur deutschen Vergangenheit. Ist es jetzt schon verboten, darauf hinzuweisen, dass sich so etwas nicht wiederholen darf? Und in einer Demokratie, die eine sein will, schon gar nicht. Eine Demokratie, die keine ist, wenn die Meinungsfreiheit beschnitten wird und selbsternannte Experten meinen darüber entscheiden zu müssen, was als wahr und was als Lüge einzustufen ist. Die Vorgabe von Meinungs-Korridoren delegitimieren das Recht, seine Meinung frei äußern zu dürfen. In einer funktionierenden Demokratie dürfte sogar gelogen werden. Jedem, der noch zwei gesunde Gehirnzellen im Kopf hat, sollte doch klar sein, dass all das erbärmliche Versuche sind, sich mit allen Mitteln an der Macht festzuklammern.
Noch einmal zurück zur anfänglichen Metapher. So lange wir leben, befinden wir uns in einem fließenden Prozess. Nichts ist in Stein gemeißelt, nichts hält für immer. Betrachtet man die jüngste Vergangenheit als einen lebendigen Prozess, der noch nicht abgeschlossen ist, der sich ständig weiterentwickelt, dann ist all dieser Wahnsinn der Regen, der bei Frost zu Eis wird und die Mauer immer maroder macht. Die Temperaturen gehen wieder über Null, das Eis taut auf, das Wasser versickert, der nächste Regen, der nächste Frost. Alles neigt dazu kaputt zu gehen.
Wir brauchen eigentlich nur zu warten, während wir fleißig weiter Erkenntnisse sammeln und dabei zusehen, wie ein Frost nach dem anderen, in Form von immer neuen und weiteren Informationen, die all die Lügen zu Corona und den aktuellen Kriegen in der Welt, die Gefängnismauer früher oder später zum Einsturz bringen wird. Und das ist wirklich so sicher, wie das Amen in der Kirche. Die Wahrheit hat immer gesiegt!
Und wenn der Damm erst einmal gebrochen ist, das Wasser schwappt bereits über die Staumauer, dann wird sich die Wahrheit wie ein Sturzbach über die Menschen ergießen. Manche wird sie mitreißen, Schicksal, wir haben genug Rettungsboote ausgesetzt in den letzten Jahren.
Spricht so ein pessimistischer Optimist mit realistischen Tendenzen?
Ihr da draußen, macht nur so weiter. Immer mehr von demselben, und fleißig weiter wundern, dass nichts anderes dabei herauskommt. Überall ist bereits euer eigenes Sägen zu hören, an dem Ast, auf dem ihr selber sitzt. Mit verschränkten Armen, leichtgeneigtem Kopf und einem Schmunzeln auf den Lippen schauen wir dabei zu und fragen uns, wie lange der Ast wohl noch halten wird und wann es kracht. Wir können warten!
Dieser Artikel wurde mit dem Pareto-Client geschrieben
* *
(Bild von pixabay)
-
 @ df478568:2a951e67
2025-04-23 20:25:03
@ df478568:2a951e67
2025-04-23 20:25:03If you've made one single-sig bitcoin wallet, you've made then all. The idea is, write down 12 or 24 magic words. Make your wallet disappear by dropping your phone in the toilet. Repeat the 12 magic words and do some hocus-pocus. Your sats re-appear from realms unknown. Or...Each word represents a 4 digit number from 0000-2047. I say it's magic.
I've recommended many wallets over the years. It's difficult to find the perfect wallet because there are so many with different security tailored for different threat models. You don't need Anchorwatch level of security for 1000 sats. 12 words is good enough. Misty Breez is like Aqua Wallet because the sats get swapped to Liquid in a similar way with a couple differences.
- Misty Breez has no stableshitcoin¹ support.
- Misty Breez gives you a lightning address. Misty Breez Lightning Wallet.
That's a big deal. That's what I need to orange pill the man on the corner selling tamales out of his van. Bitcoin is for everybody, at least anybody who can write 12 words down. A few years ago, almost nobody, not even many bitcoiners had a lightning address. Now Misty Breez makes it easy for anyone with a 5th grade reading level to start using lightning addresses. The tamale guy can send sats back home with as many tariffs as a tweet without leaving his truck.
How Misty Breez Works
Back in the day, I drooled over every word Elizabeth Stark at lightning labs uttered. I still believed in shitcoins at the time. Stark said atomic swaps can be made over the lightning network. Litecoin, since it also adopted the lightning network, can be swapped with bitcoin and vice-versa. I thought this was a good idea because it solves the coincidence of wants. I could technically have a sign on my website that says, "shitcoin accepted here" and automatically convert all my shitcoins to sats.
I don't do that because I now know there is no reason to think any shitcoin will go up in value over the long-term for various reasons. Technically, cashu is a shitcoin. Technically, Liquid is a shitcoin. Technically, I am not a card carrying bitcoin maxi because of this. I use these shitcoins because I find them useful. I consider them to be honest shitcoins(term stolen from NVK²).
Breeze does ~atomic swaps~~ peer swaps between bitcoin and Liquid. The sender sends sats. The receiver turns those sats into Liquid Bitcoin(L-BTC). This L-BTC is backed by bitcoin, therefore Liquid is a full reserve bank in many ways. That's why it molds into my ethical framework. I originally became interested in bitcoin because I thought fractional reserve banking was a scam and bitcoin was(and is) the most viable alternative to this scam.
Sats sent to Misty Breez wallet are pretty secure. It does not offer perfect security. There is no perfect security. Even though on-chain bitcoin is the most pristine example of cybersecurity on the planet, it still has risk. Just ask the guy who is digging up a landfill to find his bitcoin. I have found most noobs lose keys to bitcoin you give them. Very few take the time to keep it safe because they don't understand bitcoin well enough to know it will go up forever Laura.
She writes 12 words down with a reluctant bored look on her face. Wam. Bam. Thank you m'am. Might as well consider it a donation to the network because that index card will be buried in a pile of future trash in no time. Here's a tiny violin playing for the pre-coiners who lost sats.
"Lost coins only make everyone else's coins worth slightly more. Think of it as a donation to everyone." --Sathoshi Nakamoto, BitcoinTalk --June 21, 2010
The same thing will happen with the Misty Wallet. The 12 words will be written down my someone bored and unfulfilled woman working at NPC-Mart, but her phone buzzes in her pocket the next day. She recieved a new payment. Then you share the address on nostr and five people send her sats for no reason at all. They say everyone requires three touch points. Setting up a pre-coiner with a wallet which has a lightning address will allow you to send her as many touch points as you want. You could even send 21 sats per day for 21 days using Zap Planner. That way bitcoin is not just an "investment," but something people can see in action like a lion in the jungle chasing a gazelle.
Make Multiple Orange Pill Touch Points With Misty The Breez Lightning Address
It's no longer just a one-night stand. It's a relationship. You can softly send her sats seven days a week like a Rabbit Hole recap listening freak. Show people how to use bitcoin as it was meant to be used: Peer to Peer electronic cash.
 Misty wallet is still beta software so be careful because lightning is still in the w reckless days. Don't risk more sats that you are willing to lose with it just yet, but consider learning how to use it so you can teach others after the wallet is battle tested. I had trouble sending sats to my lightning address today from Phoenix wallet. Hopefully that gets resovled, but I couldn't use it today for whatever reason. I still think it's an awesome idea and will follow this project because I think it has potential.
Misty wallet is still beta software so be careful because lightning is still in the w reckless days. Don't risk more sats that you are willing to lose with it just yet, but consider learning how to use it so you can teach others after the wallet is battle tested. I had trouble sending sats to my lightning address today from Phoenix wallet. Hopefully that gets resovled, but I couldn't use it today for whatever reason. I still think it's an awesome idea and will follow this project because I think it has potential.npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0
¹ Stablecoins are shitcoins, but I admit they are not totally useless, but the underlying asset is the epitome of money printer go brrrrrr. ²NVK called cashu an honeset shitcoin on the Bitcoin.review podcast and I've used the term ever sense.
-
 @ 6e64b83c:94102ee8
2025-04-23 20:23:34
@ 6e64b83c:94102ee8
2025-04-23 20:23:34How to Run Your Own Nostr Relay on Android with Cloudflare Domain
Prerequisites
- Install Citrine on your Android device:
- Visit https://github.com/greenart7c3/Citrine/releases
- Download the latest release using:
- zap.store
- Obtainium
- F-Droid
- Or download the APK directly
-
Note: You may need to enable "Install from Unknown Sources" in your Android settings
-
Domain Requirements:
- Purchase a domain if you don't have one
-
Transfer your domain to Cloudflare if it's not already there (for free SSL certificates and cloudflared support)
-
Tools to use:
- nak (the nostr army knife):
- Download from https://github.com/fiatjaf/nak/releases
- Installation steps:
-
For Linux/macOS: ```bash # Download the appropriate version for your system wget https://github.com/fiatjaf/nak/releases/latest/download/nak-linux-amd64 # for Linux # or wget https://github.com/fiatjaf/nak/releases/latest/download/nak-darwin-amd64 # for macOS
# Make it executable chmod +x nak-*
# Move to a directory in your PATH sudo mv nak-* /usr/local/bin/nak
- For Windows:batch # Download the Windows version curl -L -o nak.exe https://github.com/fiatjaf/nak/releases/latest/download/nak-windows-amd64.exe# Move to a directory in your PATH (e.g., C:\Windows) move nak.exe C:\Windows\nak.exe
- Verify installation:bash nak --version ```
Setting Up Citrine
- Open the Citrine app
- Start the server
- You'll see it running on
ws://127.0.0.1:4869(local network only) - Go to settings and paste your npub into "Accept events signed by" inbox and press the + button. This prevents others from publishing events to your personal relay.
Installing Required Tools
- Install Termux from Google Play Store
- Open Termux and run:
bash pkg update && pkg install wget wget https://github.com/cloudflare/cloudflared/releases/latest/download/cloudflared-linux-arm64.deb dpkg -i cloudflared-linux-arm64.debCloudflare Authentication
- Run the authentication command:
bash cloudflared tunnel login - Follow the instructions:
- Copy the provided URL to your browser
- Log in to your Cloudflare account
- If the URL expires, copy it again after logging in
Creating the Tunnel
- Create a new tunnel:
bash cloudflared tunnel create <TUNNEL_NAME> - Choose any name you prefer for your tunnel
-
Copy the tunnel ID after creating the tunnel
-
Create and configure the tunnel config:
bash touch ~/.cloudflared/config.yml nano ~/.cloudflared/config.yml -
Add this configuration (replace the placeholders with your values): ```yaml tunnel:
credentials-file: /data/data/com.termux/files/home/.cloudflared/ .json ingress: - hostname: nostr.yourdomain.com service: ws://localhost:4869
- service: http_status:404 ```
- Note: In nano editor:
CTRL+Oand Enter to saveCTRL+Xto exit
-
Note: Check the credentials file path in the logs
-
Validate your configuration:
bash cloudflared tunnel validate -
Start the tunnel:
bash cloudflared tunnel run my-relay
Preventing Android from Killing the Tunnel
Run these commands to maintain tunnel stability:
bash date && apt install termux-tools && termux-setup-storage && termux-wake-lock echo "nameserver 1.1.1.1" > $PREFIX/etc/resolv.confTip: You can open multiple Termux sessions by swiping from the left edge of the screen while keeping your tunnel process running.
Updating Your Outbox Model Relays
Once your relay is running and accessible via your domain, you'll want to update your relay list in the Nostr network. This ensures other clients know about your relay and can connect to it.
Decoding npub (Public Key)
Private keys (nsec) and public keys (npub) are encoded in bech32 format, which includes: - A prefix (like nsec1, npub1 etc.) - The encoded data - A checksum
This format makes keys: - Easy to distinguish - Hard to copy incorrectly
However, most tools require these keys in hexadecimal (hex) format.
To decode an npub string to its hex format:
bash nak decode nostr:npub1dejts0qlva8mqzjlrxqkc2tmvs2t7elszky5upxaf3jha9qs9m5q605uc4Change it with your own npub.
bash { "pubkey": "6e64b83c1f674fb00a5f19816c297b6414bf67f015894e04dd4c657e94102ee8" }Copy the pubkey value in quotes.
Create a kind 10002 event with your relay list:
- Include your new relay with write permissions
- Include other relays you want to read from and write to, omit 3rd parameter to make it both read and write
Example format:
json { "kind": 10002, "tags": [ ["r", "wss://your-relay-domain.com", "write"], ["r", "wss://eden.nostr.land/"], ["r", "wss://nos.lol/"], ["r", "wss://nostr.bitcoiner.social/"], ["r", "wss://nostr.mom/"], ["r", "wss://relay.primal.net/"], ["r", "wss://nostr.wine/", "read"], ["r", "wss://relay.damus.io/"], ["r", "wss://relay.nostr.band/"], ["r", "wss://relay.snort.social/"] ], "content": "" }Save it to a file called
event.jsonNote: Add or remove any relays you want. To check your existing 10002 relays: - Visit https://nostr.band/?q=by%3Anpub1dejts0qlva8mqzjlrxqkc2tmvs2t7elszky5upxaf3jha9qs9m5q605uc4+++kind%3A10002 - nostr.band is an indexing service, it probably has your relay list. - Replace
npub1xxxin the URL with your own npub - Click "VIEW JSON" from the menu to see the raw event - Or use thenaktool if you know the relaysbash nak req -k 10002 -a <your-pubkey> wss://relay1.com wss://relay2.comReplace `<your-pubkey>` with your public key in hex format (you can get it using `nak decode <your-npub>`)- Sign and publish the event:
- Use a Nostr client that supports kind 10002 events
- Or use the
nakcommand-line tool:bash nak event --sec ncryptsec1... wss://relay1.com wss://relay2.com $(cat event.json)
Important Security Notes: 1. Never share your nsec (private key) with anyone 2. Consider using NIP-49 encrypted keys for better security 3. Never paste your nsec or private key into the terminal. The command will be saved in your shell history, exposing your private key. To clear the command history: - For bash: use
history -c- For zsh: usefc -Wto write history to file, thenfc -pto read it back - Or manually edit your shell history file (e.g.,~/.zsh_historyor~/.bash_history) 4. if you're usingzsh, usefc -pto prevent the next command from being saved to history 5. Or temporarily disable history before running sensitive commands:bash unset HISTFILE nak key encrypt ... set HISTFILEHow to securely create NIP-49 encypted private key
```bash
Read your private key (input will be hidden)
read -s SECRET
Read your password (input will be hidden)
read -s PASSWORD
encrypt command
echo "$SECRET" | nak key encrypt "$PASSWORD"
copy and paste the ncryptsec1 text from the output
read -s ENCRYPTED nak key decrypt "$ENCRYPTED"
clear variables from memory
unset SECRET PASSWORD ENCRYPTED ```
On a Windows command line, to read from stdin and use the variables in
nakcommands, you can use a combination ofset /pto read input and then use those variables in your command. Here's an example:```bash @echo off set /p "SECRET=Enter your secret key: " set /p "PASSWORD=Enter your password: "
echo %SECRET%| nak key encrypt %PASSWORD%
:: Clear the sensitive variables set "SECRET=" set "PASSWORD=" ```
If your key starts with
ncryptsec1, thenaktool will securely prompt you for a password when using the--secparameter, unless the command is used with a pipe< >or|.bash nak event --sec ncryptsec1... wss://relay1.com wss://relay2.com $(cat event.json)- Verify the event was published:
- Check if your relay list is visible on other relays
-
Use the
naktool to fetch your kind 10002 events:bash nak req -k 10002 -a <your-pubkey> wss://relay1.com wss://relay2.com -
Testing your relay:
- Try connecting to your relay using different Nostr clients
- Verify you can both read from and write to your relay
- Check if events are being properly stored and retrieved
- Tip: Use multiple Nostr clients to test different aspects of your relay
Note: If anyone in the community has a more efficient method of doing things like updating outbox relays, please share your insights in the comments. Your expertise would be greatly appreciated!
-
 @ d34e832d:383f78d0
2025-04-23 20:19:15
@ d34e832d:383f78d0
2025-04-23 20:19:15A Look into Traffic Analysis and What WebSocket Patterns Reveal at the Network Level
While WebSocket encryption (typically via WSS) is essential for protecting data in transit, traffic analysis remains a potent method of uncovering behavioral patterns, data structure inference, and protocol usage—even when payloads are unreadable. This idea investigates the visibility of encrypted WebSocket communications using Wireshark and similar packet inspection tools. We explore what metadata remains visible, how traffic flow can be modeled, and what risks and opportunities exist for developers, penetration testers, and network analysts. The study concludes by discussing mitigation strategies and the implications for privacy, application security, and protocol design.
Consider
In the age of real-time web applications, WebSockets have emerged as a powerful protocol enabling low-latency, bidirectional communication. From collaborative tools and chat applications to financial trading platforms and IoT dashboards, WebSockets have become foundational for interactive user experiences.
However, encryption via WSS (WebSocket Secure, running over TLS) gives developers and users a sense of security. The payload may be unreadable, but what about the rest of the connection? Can patterns, metadata, and traffic characteristics still leak critical information?
This thesis seeks to answer those questions by leveraging Wireshark, the de facto tool for packet inspection, and exploring the world of traffic analysis at the network level.
Background and Related Work
The WebSocket Protocol
Defined in RFC 6455, WebSocket operates over TCP and provides a persistent, full-duplex connection. The protocol upgrades an HTTP connection, then communicates through a simple frame-based structure.
Encryption with WSS
WSS connections use TLS (usually on port 443), making them indistinguishable from HTTPS traffic at the packet level. Payloads are encrypted, but metadata such as IP addresses, timing, packet size, and connection duration remain visible.
Traffic Analysis
Traffic analysis—despite encryption—has long been a technique used in network forensics, surveillance, and malware detection. Prior studies have shown that encrypted protocols like HTTPS, TLS, and SSH still reveal behavioral information through patterns.
Methodology
Tools Used:
- Wireshark (latest stable version)
- TLS decryption with local keys (when permitted)
- Simulated and real-world WebSocket apps (chat, games, IoT dashboards)
- Scripts to generate traffic patterns (Python using websockets and aiohttp)
Test Environments:
- Controlled LAN environments with known server and client
- Live observation of open-source WebSocket platforms (e.g., Matrix clients)
Data Points Captured:
- Packet timing and size
- TLS handshake details
- IP/TCP headers
- Frame burst patterns
- Message rate and directionality
Findings
1. Metadata Leaks
Even without payload access, the following data is visible: - Source/destination IP - Port numbers (typically 443) - Server certificate info - Packet sizes and intervals - TLS handshake fingerprinting (e.g., JA3 hashes)
2. Behavioral Patterns
- Chat apps show consistent message frequency and short message sizes.
- Multiplayer games exhibit rapid bursts of small packets.
- IoT devices often maintain idle connections with periodic keepalives.
- Typing indicators, heartbeats, or "ping/pong" mechanisms are visible even under encryption.
3. Timing and Packet Size Fingerprinting
Even encrypted payloads can be fingerprinted by: - Regularity in payload size (e.g., 92 bytes every 15s) - Distinct bidirectional patterns (e.g., send/ack/send per user action) - TLS record sizes which may indirectly hint at message length
Side-Channel Risks in Encrypted WebSocket Communication
Although WebSocket payloads transmitted over WSS (WebSocket Secure) are encrypted, they remain susceptible to side-channel analysis, a class of attacks that exploit observable characteristics of the communication channel rather than its content.
Side-Channel Risks Include:
1. User Behavior Inference
Adversaries can analyze packet timing and frequency to infer user behavior. For example, typing indicators in chat applications often trigger short, regular packets. Even without payload visibility, a passive observer may identify when a user is typing, idle, or has closed the application. Session duration, message frequency, and bursts of activity can be linked to specific user actions.2. Application Fingerprinting
TLS handshake metadata and consistent traffic patterns can allow an observer to identify specific client libraries or platforms. For example, the sequence and structure of TLS extensions (via JA3 fingerprinting) can differentiate between browsers, SDKs, or WebSocket frameworks. Application behavior—such as timing of keepalives or frequency of updates—can further reinforce these fingerprints.3. Usage Pattern Recognition
Over time, recurring patterns in packet flow may reveal application logic. For instance, multiplayer game sessions often involve predictable synchronization intervals. Financial dashboards may show bursts at fixed polling intervals. This allows for profiling of application type, logic loops, or even user roles.4. Leakage Through Timing
Time-based attacks can be surprisingly revealing. Regular intervals between message bursts can disclose structured interactions—such as polling, pings, or scheduled updates. Fine-grained timing analysis may even infer when individual keystrokes occur, especially in sparse channels where interactivity is high and payloads are short.5. Content Length Correlation
While encrypted, the size of a TLS record often correlates closely to the plaintext message length. This enables attackers to estimate the size of messages, which can be linked to known commands or data structures. Repeated message sizes (e.g., 112 bytes every 30s) may suggest state synchronization or batched updates.6. Session Correlation Across Time
Using IP, JA3 fingerprints, and behavioral metrics, it’s possible to link multiple sessions back to the same client. This weakens anonymity, especially when combined with data from DNS logs, TLS SNI fields (if exposed), or consistent traffic habits. In anonymized systems, this can be particularly damaging.Side-Channel Risks in Encrypted WebSocket Communication
Although WebSocket payloads transmitted over WSS (WebSocket Secure) are encrypted, they remain susceptible to side-channel analysis, a class of attacks that exploit observable characteristics of the communication channel rather than its content.
1. Behavior Inference
Even with end-to-end encryption, adversaries can make educated guesses about user actions based on traffic patterns:
- Typing detection: In chat applications, short, repeated packets every few hundred milliseconds may indicate a user typing.
- Voice activity: In VoIP apps using WebSockets, a series of consistent-size packets followed by silence can reveal when someone starts and stops speaking.
- Gaming actions: Packet bursts at high frequency may correlate with real-time game movement or input actions.
2. Session Duration
WebSocket connections are persistent by design. This characteristic allows attackers to:
- Measure session duration: Knowing how long a user stays connected to a WebSocket server can infer usage patterns (e.g., average chat duration, work hours).
- Identify session boundaries: Connection start and end timestamps may be enough to correlate with user login/logout behavior.
3. Usage Patterns
Over time, traffic analysis may reveal consistent behavioral traits tied to specific users or devices:
- Time-of-day activity: Regular connection intervals can point to habitual usage, ideal for profiling or surveillance.
- Burst frequency and timing: Distinct intervals of high or low traffic volume can hint at backend logic or user engagement models.
Example Scenario: Encrypted Chat App
Even though a chat application uses end-to-end encryption and transports data over WSS:
- A passive observer sees:
- TLS handshake metadata
- IPs and SNI (Server Name Indication)
- Packet sizes and timings
- They might then infer:
- When a user is online or actively chatting
- Whether a user is typing, idle, or receiving messages
- Usage patterns that match a specific user fingerprint
This kind of intelligence can be used for traffic correlation attacks, profiling, or deanonymization — particularly dangerous in regimes or situations where privacy is critical (e.g., journalists, whistleblowers, activists).
Fingerprinting Encrypted WebSocket Applications via Traffic Signatures
Even when payloads are encrypted, adversaries can leverage fingerprinting techniques to identify the specific WebSocket libraries, frameworks, or applications in use based on unique traffic signatures. This is a critical vector in traffic analysis, especially when full encryption lulls developers into a false sense of security.
1. Library and Framework Fingerprints
Different WebSocket implementations generate traffic patterns that can be used to infer what tool or framework is being used, such as:
- Handshake patterns: The WebSocket upgrade request often includes headers that differ subtly between:
- Browsers (Chrome, Firefox, Safari)
- Python libs (
websockets,aiohttp,Autobahn) - Node.js clients (
ws,socket.io) - Mobile SDKs (Android’s
okhttp, iOSStarscream) - Heartbeat intervals: Some libraries implement default ping/pong intervals (e.g., every 20s in
socket.io) that can be measured and traced back to the source.
2. Payload Size and Frequency Patterns
Even with encryption, metadata is exposed:
- Frame sizes: Libraries often chunk or batch messages differently.
- Initial message burst: Some apps send a known sequence of messages on connection (e.g., auth token → subscribe → sync events).
- Message intervals: Unique to libraries using structured pub/sub or event-driven APIs.
These observable patterns can allow a passive observer to identify not only the app but potentially which feature is being used, such as messaging, location tracking, or media playback.
3. Case Study: Identifying Socket.IO vs Raw WebSocket
Socket.IO, although layered on top of WebSockets, introduces a handshake sequence of HTTP polling → upgrade → packetized structured messaging with preamble bytes (even in encrypted form, the size and frequency of these frames is recognizable). A well-equipped observer can differentiate it from a raw WebSocket exchange using only timing and packet length metrics.
Security Implications
- Targeted exploitation: Knowing the backend framework (e.g.,
Django ChannelsorFastAPI + websockets) allows attackers to narrow down known CVEs or misconfigurations. - De-anonymization: Apps that are widely used in specific demographics (e.g., Signal clones, activist chat apps) become fingerprintable even behind HTTPS or WSS.
- Nation-state surveillance: Traffic fingerprinting lets governments block or monitor traffic associated with specific technologies, even without decrypting the data.
Leakage Through Timing: Inferring Behavior in Encrypted WebSocket Channels
Encrypted WebSocket communication does not prevent timing-based side-channel attacks, where an adversary can deduce sensitive information purely from the timing, size, and frequency of encrypted packets. These micro-behavioral signals, though not revealing actual content, can still disclose high-level user actions — sometimes with alarming precision.
1. Typing Detection and Keystroke Inference
Many real-time chat applications (Matrix, Signal, Rocket.Chat, custom WebSocket apps) implement "user is typing..." features. These generate recognizable message bursts even when encrypted:
- Small, frequent packets sent at irregular intervals often correspond to individual keystrokes.
- Inter-keystroke timing analysis — often accurate to within tens of milliseconds — can help reconstruct typed messages’ length or even guess content using language models (e.g., inferring "hello" vs "hey").
2. Session Activity Leaks
WebSocket sessions are long-lived and often signal usage states by packet rhythm:
- Idle vs active user patterns become apparent through heartbeat frequency and packet gaps.
- Transitions — like joining or leaving a chatroom, starting a video, or activating a voice stream — often result in bursts of packet activity.
- Even without payload access, adversaries can profile session structure, determining which features are being used and when.
3. Case Study: Real-Time Editors
Collaborative editing tools (e.g., Etherpad, CryptPad) leak structure:
- When a user edits, each keystroke or operation may result in a burst of 1–3 WebSocket frames.
- Over time, a passive observer could infer:
- Whether one or multiple users are active
- Who is currently typing
- The pace of typing
- Collaborative vs solo editing behavior
4. Attack Vectors Enabled by Timing Leaks
- Target tracking: Identify active users in a room, even on anonymized or end-to-end encrypted platforms.
- Session replay: Attackers can simulate usage patterns for further behavioral fingerprinting.
- Network censorship: Governments may block traffic based on WebSocket behavior patterns suggestive of forbidden apps (e.g., chat tools, Tor bridges).
Mitigations and Countermeasures
While timing leakage cannot be entirely eliminated, several techniques can obfuscate or dampen signal strength:
- Uniform packet sizing (padding to fixed lengths)
- Traffic shaping (constant-time message dispatch)
- Dummy traffic injection (noise during idle states)
- Multiplexing WebSocket streams with unrelated activity
Excellent point — let’s weave that into the conclusion of the thesis to emphasize the dual nature of WebSocket visibility:
Visibility Without Clarity — Privacy Risks in Encrypted WebSocket Traffic**
This thesis demonstrates that while encryption secures the contents of WebSocket payloads, it does not conceal behavioral patterns. Through tools like Wireshark, analysts — and adversaries alike — can inspect traffic flows to deduce session metadata, fingerprint applications, and infer user activity, even without decrypting a single byte.
The paradox of encrypted WebSockets is thus revealed:
They offer confidentiality, but not invisibility.As shown through timing analysis, fingerprinting, and side-channel observation, encrypted WebSocket streams can still leak valuable information. These findings underscore the importance of privacy-aware design choices in real-time systems:
- Padding variable-size messages to fixed-length formats
- Randomizing or shaping packet timing
- Mixing in dummy traffic during idle states
- Multiplexing unrelated data streams to obscure intent
Without such obfuscation strategies, encrypted WebSocket traffic — though unreadable — remains interpretable.
In closing, developers, privacy researchers, and protocol designers must recognize that encryption is necessary but not sufficient. To build truly private real-time systems, we must move beyond content confidentiality and address the metadata and side-channel exposures that lie beneath the surface.
Absolutely! Here's a full thesis-style writeup titled “Mitigation Strategies: Reducing Metadata Leakage in Encrypted WebSocket Traffic”, focusing on countermeasures to side-channel risks in real-time encrypted communication:
Mitigation Strategies: Reducing Metadata Leakage in Encrypted WebSocket Traffic
Abstract
While WebSocket traffic is often encrypted using TLS, it remains vulnerable to metadata-based side-channel attacks. Adversaries can infer behavioral patterns, session timing, and even the identity of applications through passive traffic analysis. This thesis explores four key mitigation strategies—message padding, batching and jitter, TLS fingerprint randomization, and connection multiplexing—that aim to reduce the efficacy of such analysis. We present practical implementations, limitations, and trade-offs associated with each method and advocate for layered, privacy-preserving protocol design.
1. Consider
The rise of WebSockets in real-time applications has improved interactivity but also exposed new privacy attack surfaces. Even when encrypted, WebSocket traffic leaks observable metadata—packet sizes, timing intervals, handshake properties, and connection counts—that can be exploited for fingerprinting, behavioral inference, and usage profiling.
This Idea focuses on mitigation rather than detection. The core question addressed is: How can we reduce the information available to adversaries from metadata alone?
2. Threat Model and Metadata Exposure
Passive attackers situated at any point between client and server can: - Identify application behavior via timing and message frequency - Infer keystrokes or user interaction states ("user typing", "user joined", etc.) - Perform fingerprinting via TLS handshake characteristics - Link separate sessions from the same user by recognizing traffic patterns
Thus, we must treat metadata as a leaky abstraction layer, requiring proactive obfuscation even in fully encrypted sessions.
3. Mitigation Techniques
3.1 Message Padding
Variable-sized messages create unique traffic signatures. Message padding involves standardizing the frame length of WebSocket messages to a fixed or randomly chosen size within a predefined envelope.
- Pro: Hides exact payload size, making compression side-channel and length-based analysis ineffective.
- Con: Increases bandwidth usage; not ideal for mobile/low-bandwidth scenarios.
Implementation: Client libraries can pad all outbound messages to, for example, 512 bytes or the next power of two above the actual message length.
3.2 Batching and Jitter
Packet timing is often the most revealing metric. Delaying messages to create jitter and batching multiple events into a single transmission breaks correlation patterns.
- Pro: Prevents timing attacks, typing inference, and pattern recognition.
- Con: Increases latency, possibly degrading UX in real-time apps.
Implementation: Use an event queue with randomized intervals for dispatching messages (e.g., 100–300ms jitter windows).
3.3 TLS Fingerprint Randomization
TLS fingerprints—determined by the ordering of cipher suites, extensions, and fields—can uniquely identify client libraries and platforms. Randomizing these fields on the client side prevents reliable fingerprinting.
- Pro: Reduces ability to correlate sessions or identify tools/libraries used.
- Con: Requires deeper control of the TLS stack, often unavailable in browsers.
Implementation: Modify or wrap lower-level TLS clients (e.g., via OpenSSL or rustls) to introduce randomized handshakes in custom apps.
3.4 Connection Reuse or Multiplexing
Opening multiple connections creates identifiable patterns. By reusing a single persistent connection for multiple data streams or users (in proxies or edge nodes), the visibility of unique flows is reduced.
- Pro: Aggregates traffic, preventing per-user or per-feature traffic separation.
- Con: More complex server-side logic; harder to debug.
Implementation: Use multiplexing protocols (e.g., WebSocket subprotocols or application-level routing) to share connections across users or components.
4. Combined Strategy and Defense-in-Depth
No single strategy suffices. A layered mitigation approach—combining padding, jitter, fingerprint randomization, and multiplexing—provides defense-in-depth against multiple classes of metadata leakage.
The recommended implementation pipeline: 1. Pad all outbound messages to a fixed size 2. Introduce random batching and delay intervals 3. Obfuscate TLS fingerprints using low-level TLS stack configuration 4. Route data over multiplexed WebSocket connections via reverse proxies or edge routers
This creates a high-noise communication channel that significantly impairs passive traffic analysis.
5. Limitations and Future Work
Mitigations come with trade-offs: latency, bandwidth overhead, and implementation complexity. Additionally, some techniques (e.g., TLS randomization) are hard to apply in browser-based environments due to API constraints.
Future work includes: - Standardizing privacy-enhancing WebSocket subprotocols - Integrating these mitigations into mainstream libraries (e.g., Socket.IO, Phoenix) - Using machine learning to auto-tune mitigation levels based on threat environment
6. Case In Point
Encrypted WebSocket traffic is not inherently private. Without explicit mitigation, metadata alone is sufficient for behavioral profiling and application fingerprinting. This thesis has outlined practical strategies for obfuscating traffic patterns at various protocol layers. Implementing these defenses can significantly improve user privacy in real-time systems and should become a standard part of secure WebSocket deployments.
-
 @ 4c96d763:80c3ee30
2025-04-23 19:43:04
@ 4c96d763:80c3ee30
2025-04-23 19:43:04Changes
William Casarin (28):
- dave: constrain power for now
- ci: bump ubuntu runner
- dave: initial note rendering
- note: fix from_hex crash on bad note ids
- dave: improve multi-note display
- dave: cleanly separate ui from logic
- dave: add a few docs
- dave: add readme
- dave: improve docs with ai
- docs: add some ui-related guides
- docs: remove test hallucination
- docs: add tokenator docs
- docs: add notedeck docs
- docs: add notedeck_columns readme
- docs: add notedeck_chrome docs
- docs: improve top-level docs
- dave: add new chat button
- dave: ensure system prompt is included when reset
- enostr: rename to_bech to npub
- name: display_name before name in NostrName
- ui: add note truncation
- ui: add ProfilePic::from_profile_or_default
- dave: add query rendering, fix author queries
- dave: return tool errors back to the ai
- dave: give present notes a proper tool response
- dave: more flexible env config
- dave: bubble note actions to chrome
- chrome: use actual columns noteaction executor
kernelkind (13):
- remove unnecessary
#[allow(dead_code)] - extend
ZapAction - UserAccount use builder pattern
Wallettoken parser shouldn't parse all- move
WalletStateto UI - add default zap
- introduce
ZapWallet - use
ZapWallet - propagate
DefaultZapStateto wallet ui - wallet: helper method to get current wallet
- accounts: check if selected account has wallet
- ui: show default zap amount in wallet view
- use default zap amount for zap
pushed to notedeck:refs/heads/master
-
 @ e516ecb8:1be0b167
2025-04-23 15:25:16
@ e516ecb8:1be0b167
2025-04-23 15:25:16¡Muy bien, amigo! Vamos a sumergirnos en las profundidades arquetípicas de la psique humana para desentrañar esta noción, esta chispa de sabiduría que intentamos articular, porque, verás, no es una mera declaración trivial, no, no, es una verdad ontológica que reverbera a través de los eones, en los cimientos mismos del Ser.
Permíteme, si me lo permites, desplegar esta idea como si fuera un tapiz mitológico, tejido con los hilos del caos y el orden, porque eso es lo que hacemos cuando nos enfrentamos a la condición humana, ¿no es así? Nos esforzamos por dar sentido al cosmos, por encontrar un faro en la tormenta.
Ahora, consideremos esta proposición: la felicidad, esa efímera mariposa que revolotea en los márgenes de nuestra conciencia, no es, como podrías suponer ingenuamente, el summum bonum, el pináculo de la existencia. No, señor, no lo es. La felicidad es un estado fugaz, una sombra danzante en la caverna platónica, un destello momentáneo que se desvanece en cuanto intentas apresarlo. Es como tratar de agarrar el agua con las manos: cuanto más aprietas, más se escurre. Y aquí está el quid de la cuestión, la médula de la narrativa: perseguir la felicidad como si fuera el telos, el fin último de tu peregrinaje existencial, es una empresa quijotesca, una búsqueda condenada a la futilidad, porque la felicidad no es un destino; es un subproducto, un acompañante caprichoso que aparece y desaparece según los caprichos del destino. Pero entonces, ¿cuál es el antídoto? ¿Cuál es la brújula que orienta al alma en esta travesía a través del desierto de la modernidad? Aquí, amigo mío, es donde debemos invocar el espectro del propósito, esa fuerza titánica, ese Logos encarnado que nos llama a trascender la mera gratificación hedónica y a alinearnos con algo más grande, algo más profundo, algo que resuene con las estructuras arquetípicas que han guiado a la humanidad desde las fogatas de la prehistoria hasta los rascacielos de la posmodernidad. El propósito, verás, no es una abstracción frívola; es el eje alrededor del cual gira la rueda de la vida. Es la carga que eliges llevar voluntariamente, como el héroe mitológico que levanta el mundo sobre sus hombros, no porque sea fácil, sino porque es necesario.
Y no me malinterpretes, porque esto no es un juego de niños. Asumir un propósito es enfrentarte al dragón del caos, es mirar fijamente al abismo y decir: “No me doblegarás”. Es la disposición a soportar el sufrimiento —porque, créeme, el sufrimiento vendrá, tan seguro como el sol sale por el este— y transformarlo en algo redentor, algo que eleve tu existencia más allá de los confines de lo mundano. Porque, ¿qué es la vida sino una serie de tragedias potenciales, una danza perpetua al borde del precipicio? Y sin embargo, en esa danza, en esa lucha, encontramos significado. No es la ausencia de dolor lo que define una vida bien vivida, sino la valentía de avanzar a pesar de él, de construir orden a partir del caos, de erigir un templo de significado en medio de la entropía.
Así que, cuando decimos que la felicidad es pasajera y nuestro objetivo es perseguir un propósito, no estamos simplemente lanzando una frase al éter; estamos articulando una verdad que ha sido destilada a través de milenios de lucha humana, desde los mitos de Gilgamesh hasta las reflexiones de los estoicos, desde las catedrales góticas hasta las bibliotecas de la Ilustración. Es una invitación a reorientar tu brújula interna, a dejar de perseguir el espejismo de la felicidad y, en cambio, abrazar la carga gloriosa del propósito, porque en esa carga, en esa responsabilidad autoimpuesta, encuentras no solo significado, sino la posibilidad de trascendencia. Y eso, amigo mío, es la aventura más noble que un ser humano puede emprender.
-
 @ f32184ee:6d1c17bf
2025-04-23 13:21:52
@ f32184ee:6d1c17bf
2025-04-23 13:21:52Ads Fueling Freedom
Ross Ulbricht’s "Decentralize Social Media" painted a picture of a user-centric, decentralized future that transcended the limitations of platforms like the tech giants of today. Though focused on social media, his concept provided a blueprint for decentralized content systems writ large. The PROMO Protocol, designed by NextBlock while participating in Sovereign Engineering, embodies this blueprint in the realm of advertising, leveraging Nostr and Bitcoin’s Lightning Network to give individuals control, foster a multi-provider ecosystem, and ensure secure value exchange. In this way, Ulbricht’s 2021 vision can be seen as a prescient prediction of the PROMO Protocol’s structure. This is a testament to the enduring power of his ideas, now finding form in NextBlock’s innovative approach.
 [Current Platform-Centric Paradigm, source: Ross Ulbricht's Decentralize Social Media]
[Current Platform-Centric Paradigm, source: Ross Ulbricht's Decentralize Social Media]Ulbricht’s Vision: A Decentralized Social Protocol
In his 2021 Medium article Ulbricht proposed a revolutionary vision for a decentralized social protocol (DSP) to address the inherent flaws of centralized social media platforms, such as privacy violations and inconsistent content moderation. Writing from prison, Ulbricht argued that decentralization could empower users by giving them control over their own content and the value they create, while replacing single, monolithic platforms with a competitive ecosystem of interface providers, content servers, and advertisers. Though his focus was on social media, Ulbricht’s ideas laid a conceptual foundation that strikingly predicts the structure of NextBlock’s PROMO Protocol, a decentralized advertising system built on the Nostr protocol.
 [A Decentralized Social Protocol (DSP), source: Ross Ulbricht's Decentralize Social Media]
[A Decentralized Social Protocol (DSP), source: Ross Ulbricht's Decentralize Social Media]Ulbricht’s Principles
Ulbricht’s article outlines several key principles for his DSP: * User Control: Users should own their content and dictate how their data and creations generate value, rather than being subject to the whims of centralized corporations. * Decentralized Infrastructure: Instead of a single platform, multiple interface providers, content hosts, and advertisers interoperate, fostering competition and resilience. * Privacy and Autonomy: Decentralized solutions for profile management, hosting, and interactions would protect user privacy and reduce reliance on unaccountable intermediaries. * Value Creation: Users, not platforms, should capture the economic benefits of their contributions, supported by decentralized mechanisms for transactions.
These ideas were forward-thinking in 2021, envisioning a shift away from the centralized giants dominating social media at the time. While Ulbricht didn’t specifically address advertising protocols, his framework for decentralization and user empowerment extends naturally to other domains, like NextBlock’s open-source offering: the PROMO Protocol.
NextBlock’s Implementation of PROMO Protocol
The PROMO Protocol powers NextBlock's Billboard app, a decentralized advertising protocol built on Nostr, a simple, open protocol for decentralized communication. The PROMO Protocol reimagines advertising by: * Empowering People: Individuals set their own ad prices (e.g., 500 sats/minute), giving them direct control over how their attention or space is monetized. * Marketplace Dynamics: Advertisers set budgets and maximum bids, competing within a decentralized system where a 20% service fee ensures operational sustainability. * Open-Source Flexibility: As an open-source protocol, it allows multiple developers to create interfaces or apps on top of it, avoiding the single-platform bottleneck Ulbricht critiqued. * Secure Payments: Using Strike Integration with Bitcoin Lightning Network, NextBlock enables bot-resistant and intermediary-free transactions, aligning value transfer with each person's control.
This structure decentralizes advertising in a way that mirrors Ulbricht’s broader vision for social systems, with aligned principles showing a specific use case: monetizing attention on Nostr.
Aligned Principles
Ulbricht’s 2021 article didn’t explicitly predict the PROMO Protocol, but its foundational concepts align remarkably well with NextBlock's implementation the protocol’s design: * Autonomy Over Value: Ulbricht argued that users should control their content and its economic benefits. In the PROMO Protocol, people dictate ad pricing, directly capturing the value of their participation. Whether it’s their time, influence, or digital space, rather than ceding it to a centralized ad network. * Ecosystem of Providers: Ulbricht envisioned multiple providers replacing a single platform. The PROMO Protocol’s open-source nature invites a similar diversity: anyone can build interfaces or tools on top of it, creating a competitive, decentralized advertising ecosystem rather than a walled garden. * Decentralized Transactions: Ulbricht’s DSP implied decentralized mechanisms for value exchange. NextBlock delivers this through the Bitcoin Lightning Network, ensuring that payments for ads are secure, instantaneous and final, a practical realization of Ulbricht’s call for user-controlled value flows. * Privacy and Control: While Ulbricht emphasized privacy in social interactions, the PROMO Protocol is public by default. Individuals are fully aware of all data that they generate since all Nostr messages are signed. All participants interact directly via Nostr.
 [Blueprint Match, source NextBlock]
[Blueprint Match, source NextBlock]
Who We Are
NextBlock is a US-based new media company reimagining digital ads for a decentralized future. Our founders, software and strategy experts, were hobbyist podcasters struggling to promote their work online without gaming the system. That sparked an idea: using new tech like Nostr and Bitcoin to build a decentralized attention market for people who value control and businesses seeking real connections.
Our first product, Billboard, is launching this June.
Open for All
Our model’s open-source! Check out the PROMO Protocol, built for promotion and attention trading. Anyone can join this decentralized ad network. Run your own billboard or use ours. This is a growing ecosystem for a new ad economy.
Our Vision
NextBlock wants to help build a new decentralized internet. Our revolutionary and transparent business model will bring honest revenue to companies hosting valuable digital spaces. Together, we will discover what our attention is really worth.
Read our Manifesto to learn more.
NextBlock is registered in Texas, USA.
-
 @ 1f79058c:eb86e1cb
2025-04-24 07:17:12
@ 1f79058c:eb86e1cb
2025-04-24 07:17:12I think we should agree on an HTML element for pointing to the Nostr representation of a document/URL on the Web. We could use the existing one for link relations for example:
html <link rel="alternate" type="application/nostr+json" href="nostr:naddr1qvzqqqr4..." title="This article on Nostr" />This would be useful in multiple ways:
- Nostr clients, when fetching meta/preview information for a URL that is linked in a note, can detect that there's a Nostr representation of the content, and then render it in Nostr-native ways (whatever that may be depending on the client)
- User agents, usually a browser or browser extension, when opening a URL on the Web, can offer opening the alternative representation of a page in a Nostr client. And/or they could offer to follow the author's pubkey on Nostr. And/or they could offer to zap the content.
- When publishing a new article, authors can share their preferred Web URL everywhere, without having to consider if the reader knows about or uses Nostr at all. However, if a Nostr user finds the Web version of an article outside of Nostr, they can now easily jump to the Nostr version of it.
- Existing Web publications can retroactively create Nostr versions of their content and easily link the Nostr articles on all of their existing article pages without having to add prominent Nostr links everywhere.
There are probably more use cases, like Nostr search engines and whatnot. If you can think of something interesting, please tell me.
Proof of concept
In order to show one way in which this could be used, I have created a small Web Extension called Nostr Links, which will discover alternate Nostr links on the pages you visit.
If it finds one or more links, it will show a purple Nostr icon in the address bar, which you can click to open the list of links. It's similar to e.g. the Feed Preview extension, and also to what the Tor Browser does when it discovers an Onion-Location for the page you're looking at:
The links in this popup menu will be
web+nostr:links, because browsers currently do not allow web apps or extensions to handle unprefixednostr:links. (I hope someone is working on getting those on par withipfs:etc.)Following such a link will either open your default Nostr Web app, if you have already configured one, or it will ask you which Web app to open the link with.
Caveat emptor: At the time of writing, my personal default Web app, noStrudel, needs a new release for the links to find the content.
Try it now
Have a look at the source code and/or download the extension (currently only for Firefox).
I have added alternate Nostr links to the Web pages of profiles and long-form content on the Kosmos relay's domain. It's probably the only place on the Web, which will trigger the extension right now.
You can look at this very post to find an alternate link for example.
-
 @ 6ad3e2a3:c90b7740
2025-04-23 12:31:54
@ 6ad3e2a3:c90b7740
2025-04-23 12:31:54There’s an annoying trend on Twitter wherein the algorithm feeds you a lot of threads like “five keys to gaining wealth” or “10 mistakes to avoid in relationships” that list a bunch of hacks for some ostensibly desirable state of affairs which for you is presumably lacking. It’s not that the hacks are wrong per se, more that the medium is the message. Reading threads about hacks on social media is almost surely not the path toward whatever is promised by them.
. . .
I’ve tried a lot of health supplements over the years. These days creatine is trendy, and of course Vitamin D (which I still take.) I don’t know if this is helping me, though it surely helps me pass my blood tests with robust levels. The more I learn about health and nutrition, the less I’m sure of anything beyond a few basics. Yes, replacing processed food with real food, moving your body and getting some sun are almost certainly good, but it’s harder to know how particular interventions affect me.
Maybe some of them work in the short term then lose their effect, Maybe some work better for particular phenotypes, but not for mine. Maybe my timing in the day is off, or I’m not combining them correctly for my lifestyle and circumstances. The body is a complex system, and complex systems are characterized by having unpredictable outputs given changes to initial conditions (inputs).
. . .
I started getting into Padel recently — a mini-tennis-like game where you can hit the ball off the back walls. I’d much rather chase a ball around for exercise than run or work out, and there’s a social aspect I enjoy. (By “social aspect”, I don’t really mean getting to know the people with whom I’m playing, but just the incidental interactions you get during the game, joking about it, for example, when you nearly impale someone at the net with a hard forehand.)
A few months ago, I was playing with some friends, and I was a little off. It’s embarrassing to play poorly at a sport, especially when (as is always the case in Padel) you have a doubles partner you’re letting down. Normally I’d be excoriating myself for my poor play, coaching myself to bend my knees more, not go for winners so much. But that day, I was tired — for some reason I hadn’t slept well — and I didn’t have the energy for much internal monologue. I just mishit a few balls, felt stupid about it and kept playing.
After a few games, my fortunes reversed. I was hitting the ball cleanly, smashing winners, rarely making errors. My partner and I started winning games and then sets. I was enjoying myself. In the midst of it I remember hitting an easy ball into the net and reflexively wanting to self-coach again. I wondered, “What tips did I give to right the ship when I had been playing poorly at the outset?” I racked my brain as I waited for the serve and realized, to my surprise, there had been none. The turnaround in my play was not due to self-coaching but its absence. I had started playing better because my mind had finally shut the fuck up for once.
Now when I’m not playing well, I resist, to the extent I’m capable, the urge to meddle. I intend to be more mind-less. Not so much telling the interior coach to shut up but not buying into the premise there is a problem to be solved at all. The coach isn’t just ignored, he’s fired. And he’s not just fired, his role was obsoleted.
You blew the point, you’re embarrassed about it and there’s nothing that needs to be done about it. Or that you started coaching yourself like a fool and made things worse. No matter how much you are doing the wrong thing nothing needs to be done about any of it whatsoever. There is always another ball coming across the net that needs to be struck until the game is over.
. . .
Most of the hacks, habits and heuristics we pick up to manage our lives only serve as yet more inputs in unfathomably complex systems whose outputs rarely track as we’d like. There are some basic ones that are now obvious to everyone like not injecting yourself with heroin (or mRNA boosters), but for the most part we just create more baggage for ourselves which justifies ever more hacks. It’s like taking medication for one problem that causes side effects, and then you need another medicine for that side effect, rinse and repeat, ad infinitum.
But this process can be reverse-engineered too. For every heuristic you drop, the problem it was put into place to solve re-emerges and has a chance to be observed. Observing won’t solve it, it’ll just bring it into the fold, give the complex system of which it is a part a chance to achieve an equilibrium with respect to it on its own.
You might still be embarrassed when you mishit the ball, but embarrassment is not a problem. And if embarrassment is not a problem, then mishitting a ball isn’t that bad. And if mishitting a ball isn’t that bad, then maybe you’re not worrying about what happens if you botch the next shot, instead fixing your attention on the ball. And so you disappear a little bit into the game, and it’s more fun as a result.
I honestly wish there were a hack for this — being more mindless — but I don’t know of any. And in any event, hack Substacks won’t get you any farther than hack Twitter threads.
-
 @ 8d34bd24:414be32b
2025-04-23 03:52:15
@ 8d34bd24:414be32b
2025-04-23 03:52:15I started writing a series on the signs of the End Times and how they align with what we are seeing in the world today. There are some major concerns with predicting the end times, so I decided I should insert a short post on “Can we know when the end times are coming?” Like many principles in the Bible, it takes looking at seemingly contradictory verses to reach the truth.
This Generation
Before I get into “Can we know?” I want to address one point that some will bring up against a future Rapture, Tribulation, and Millennium.
Truly I say to you, this generation will not pass away until all these things take place. (Matthew 24:34) {emphasis mine}
What generation is Jesus talking about. Most Christians that don’t believe in a future Rapture, Tribulation, and Millennium will point to this verse to support their point of view. The important question is, “What is Jesus referring to with the words ‘this generation’?”
Is it referring to the people He was talking to at that time? If so, since that generation died long ago, then Jesus’s predictions must have been fulfilled almost 2 millennia ago. The problem with this interpretation is that nothing resembling these predictions happened during that initial generation. You have to really twist His words to try to support that they were fulfilled. Also, John wrote in Revelation about future fulfillment. By that time, John was the last of the apostles still alive and that whole generation was pretty much gone.
If “this generation” doesn’t refer to the people Jesus was speaking to personally in that moment, then to whom does it refer? The verses immediately preceding talk about the signs that will occur right before the end times. If you take “this generation” to mean the people who saw the signs Jesus predicted, then everything suddenly makes sense. It also parallel’s Paul’s statement of consolation to those who thought they had been left behind,**
But we do not want you to be uninformed, brethren, about those who are asleep, so that you will not grieve as do the rest who have no hope. For if we believe that Jesus died and rose again, even so God will bring with Him those who have fallen asleep in Jesus. For this we say to you by the word of the Lord, that we who are alive and remain until the coming of the Lord, will not precede those who have fallen asleep. For the Lord Himself will descend from heaven with a shout, with the voice of the archangel and with the trumpet of God, and the dead in Christ will rise first. Then we who are alive and remain will be caught up together with them in the clouds to meet the Lord in the air, and so we shall always be with the Lord. Therefore comfort one another with these words. (1 Thessalonians 4:13-18) {emphasis mine}
Some believers thought things were happening in their lifetime, but Paul gave them comfort that no believer would miss the end times rapture.
No One Knows
Truly I say to you, this generation will not pass away until all these things take place. Heaven and earth will pass away, but My words will not pass away.
But of that day and hour no one knows, not even the angels of heaven, nor the Son, but the Father alone. For the coming of the Son of Man will be just like the days of Noah. For as in those days before the flood they were eating and drinking, marrying and giving in marriage, until the day that Noah entered the ark, and they did not understand until the flood came and took them all away; so will the coming of the Son of Man be. Then there will be two men in the field; one will be taken and one will be left. Two women will be grinding at the mill; one will be taken and one will be left. (Matthew 24:34-41) {emphasis mine}
This verse very explicitly says that no one, not even angels or Jesus, knows the exact day or hour of His coming.
So when they had come together, they were asking Him, saying, “Lord, is it at this time You are restoring the kingdom to Israel?” He said to them, “It is not for you to know times or epochs which the Father has fixed by His own authority; but you will receive power when the Holy Spirit has come upon you; and you shall be My witnesses both in Jerusalem, and in all Judea and Samaria, and even to the remotest part of the earth.” (Acts 1:6-8)
In this verse Jesus again says that they cannot know the time of His return, but based on context, He is explaining that this generation needs to focus on sharing the Gospel with world and not primarily on the kingdom. Is this Jesus’s way of telling them that they would not be alive to see His return, but they would be responsible for “sharing the Gospel even to the remotest part of the earth?”
Therefore we do know that predicting the exact date of His return is a fool’s errand and should not be attempted, but does this mean we can’t know when it is fast approaching?
We Should Know
There is an opposing passage, though.
The Pharisees and Sadducees came up, and testing Jesus, they asked Him to show them a sign from heaven. But He replied to them, “When it is evening, you say, ‘It will be fair weather, for the sky is red.’ And in the morning, ‘There will be a storm today, for the sky is red and threatening.’ Do you know how to discern the appearance of the sky, but cannot discern the signs of the times? An evil and adulterous generation seeks after a sign; and a sign will not be given it, except the sign of Jonah.” And He left them and went away. (Matthew 16:1-4) {emphasis mine}
In this passage, Jesus reprimands the Pharisees and Sadducees because, although they can rightly read the signs of the weather, they were unable to know and understand the prophecies of His first coming. Especially as the religious leaders, they should’ve been able to determine that Jesus’s coming was imminent and that He was fulfilling the prophetic Scriptures.
In Luke, when Jesus is discussing His second coming with His disciples, He tells this parable:
Then He told them a parable: “Behold the fig tree and all the trees; as soon as they put forth leaves, you see it and know for yourselves that summer is now near. So you also, when you see these things happening, recognize that the kingdom of God is near. (Luke 21:29-31) {emphasis mine}
Jesus would not have given this parable if there were not signs of His coming that we can recognize.
We are expected to know the Scriptures and to study them looking for the signs of His second coming. We can’t know the hour or the day, but we can know that the time is fast approaching. We shouldn’t set dates, but we should search anxiously for the signs of His coming. We shouldn’t be like the scoffers that question His literal fulfillment of His promises:
Know this first of all, that in the last days mockers will come with their mocking, following after their own lusts, and saying, “Where is the promise of His coming? For ever since the fathers fell asleep, all continues just as it was from the beginning of creation.” For when they maintain this, it escapes their notice that by the word of God the heavens existed long ago and the earth was formed out of water and by water, through which the world at that time was destroyed, being flooded with water. But by His word the present heavens and earth are being reserved for fire, kept for the day of judgment and destruction of ungodly men. But do not let this one fact escape your notice, beloved, that with the Lord one day is like a thousand years, and a thousand years like one day. The Lord is not slow about His promise, as some count slowness, but is patient toward you, not wishing for any to perish but for all to come to repentance. (2 Peter 3:3-9) {emphasis mine}
One thing is certain, we are closer to Jesus’s second coming than we have ever been and must be ready as we see the day approaching.
May the God of heaven give you a desire and urgency to share the Gospel with all those around you and to grow your faith, knowledge, and relationship with Him, so you can finish the race well, with no regrets. May the knowledge that Jesus could be coming soon give you an eternal perspective on life, so you put more of your time into things of eternal consequence and don’t get overwhelmed with things of the world which are here today and then are gone.
Trust Jesus.
FYI, I hope to write several more articles on the end times (signs of the times, the rapture, the millennium, and the judgement), but I might be a bit slow rolling them out because I want to make sure they are accurate and well supported by Scripture. You can see my previous posts on the end times on the end times tab at trustjesus.substack.com. I also frequently will list upcoming posts.
-
 @ d34e832d:383f78d0
2025-04-22 23:35:05
@ d34e832d:383f78d0
2025-04-22 23:35:05For Secure Inheritance Planning and Offline Signing
The setup described ensures that any 2 out of 3 participants (hardware wallets) must sign a transaction before it can be broadcast, offering robust protection against theft, accidental loss, or mismanagement of funds.
1. Preparation: Tools and Requirements
Hardware Required
- 3× COLDCARD Mk4 hardware wallets (or newer)
- 3× MicroSD cards (one per COLDCARD)
- MicroSD card reader (for your computer)
- Optional: USB data blocker (for safe COLDCARD connection)
Software Required
- Sparrow Wallet: Version 1.7.1 or later
Download: https://sparrowwallet.com/ - COLDCARD Firmware: Version 5.1.2 or later
Update guide: https://coldcard.com/docs/upgrade
Other Essentials
- Durable paper or steel backup tools for seed phrases
- Secure physical storage for backups and devices
- Optional: encrypted external storage for Sparrow wallet backups
Security Tip:
Always verify software signatures before installation. Keep your COLDCARDs air-gapped (no USB data transfer) whenever possible.
2. Initializing Each COLDCARD Wallet
- Power on each COLDCARD and choose “New Wallet”.
- Write down the 24-word seed phrase (DO NOT photograph or store digitally).
- Confirm the seed and choose a strong PIN code (both prefix and suffix).
- (Optional) Enable BIP39 Passphrase for additional entropy.
- Save an encrypted backup to the MicroSD card:
Go to Advanced > Danger Zone > Backup. - Repeat steps 1–5 for all three COLDCARDs.
Best Practice:
Store each seed phrase securely and in separate physical locations. Test wallet recovery before storing real funds.
3. Exporting XPUBs from COLDCARD
Each hardware wallet must export its extended public key (XPUB) for multisig setup:
- Insert MicroSD card into a COLDCARD.
- Navigate to:
Settings > Multisig Wallets > Export XPUB. - Select the appropriate derivation path. Recommended:
- Native SegWit:
m/84'/0'/0'(bc1 addresses) - Alternatively: Nested SegWit
m/49'/0'/0'(starts with 3) - Save the XPUB file to the MicroSD card.
- Insert MicroSD into your computer and transfer XPUB files to Sparrow Wallet.
- Repeat for the remaining COLDCARDs.
4. Creating the 2-of-3 Multisig Wallet in Sparrow
- Launch Sparrow Wallet.
- Click File > New Wallet and name your wallet.
- In the Keystore tab, choose Multisig.
- Select 2-of-3 as your multisig policy.
- For each cosigner:
- Choose Add cosigner > Import XPUB from file.
- Load XPUBs exported from each COLDCARD.
- Once all 3 cosigners are added, confirm the configuration.
- Click Apply, then Create Wallet.
- Sparrow will display a receive address. Fund the wallet using this.
Tip:
You can export the multisig policy (wallet descriptor) as a backup and share it among cosigners.
5. Saving and Verifying the Wallet Configuration
- After creating the wallet, click Wallet > Export > Export Wallet File (.json).
- Save this file securely and distribute to all participants.
- Verify that the addresses match on each COLDCARD using the wallet descriptor file (optional but recommended).
6. Creating and Exporting a PSBT (Partially Signed Bitcoin Transaction)
- In Sparrow, click Send, fill out recipient details, and click Create Transaction.
- Click Finalize > Save PSBT to MicroSD card.
- The file will be saved as a
.psbtfile.
Note: No funds are moved until 2 signatures are added and the transaction is broadcast.
7. Signing the PSBT with COLDCARD (Offline)
- Insert the MicroSD with the PSBT into COLDCARD.
- From the main menu:
Ready To Sign > Select PSBT File. - Verify transaction details and approve.
- COLDCARD will create a signed version of the PSBT (
signed.psbt). - Repeat the signing process with a second COLDCARD (different signer).
8. Finalizing and Broadcasting the Transaction
- Load the signed PSBT files back into Sparrow.
- Sparrow will detect two valid signatures.
- Click Finalize Transaction > Broadcast.
- Your Bitcoin transaction will be sent to the network.
9. Inheritance Planning with Multisig
Multisig is ideal for inheritance scenarios:
Example Inheritance Setup
- Signer 1: Yourself (active user)
- Signer 2: Trusted family member or executor
- Signer 3: Lawyer, notary, or secure backup
Only 2 signatures are needed. If one party loses access or passes away, the other two can recover the funds.
Best Practices for Inheritance
- Store each seed phrase in separate, tamper-proof, waterproof containers.
- Record clear instructions for heirs (without compromising seed security).
- Periodically test recovery with cosigners.
- Consider time-locked wallets or third-party escrow if needed.
Security Tips and Warnings
- Never store seed phrases digitally or online.
- Always verify addresses and signatures on the COLDCARD screen.
- Use Sparrow only on secure, malware-free computers.
- Physically secure your COLDCARDs from unauthorized access.
- Practice recovery procedures before storing real value.
Consider
A 2-of-3 multisignature wallet using COLDCARD and Sparrow Wallet offers a highly secure, flexible, and transparent Bitcoin custody model. Whether for inheritance planning or high-security storage, it mitigates risks associated with single points of failure while maintaining usability and privacy.
By following this guide, Bitcoin users can significantly increase the resilience of their holdings while enabling thoughtful succession strategies.
-
 @ a8d1560d:3fec7a08
2025-04-22 22:52:15
@ a8d1560d:3fec7a08
2025-04-22 22:52:15Based on the Free Speech Flag generator at https://crocojim18.github.io/, but now you can encode binary data as well.
https://free-speech-flag-generator--wholewish91244492.on.websim.ai/
Please also see https://en.wikipedia.org/wiki/Free_Speech_Flag for more information about the Free Speech Flag.
Who can tell me what I encoded in the flag used for this longform post?
-
 @ 9bde4214:06ca052b
2025-04-22 22:04:57
@ 9bde4214:06ca052b
2025-04-22 22:04:57“The human spirit should remain in charge.”
Pablo & Gigi talk about the wind.
In this dialogue:
- Wind
- More Wind
- Information Calories, and how to measure them
- Digital Wellbeing
- Rescue Time
- Teleology of Technology
- Platforms get users Hooked (book)
- Feeds are slot machines
- Movie Walls
- Tweetdeck and Notedeck
- IRC vs the modern feed
- 37Signals: “Hey, let’s just charge users!”
- “You wouldn’t zap a car crash”
- Catering to our highest self VS catering to our lowest self
- Devolution of YouTube 5-star ratings to thumb up/down to views
- Long videos vs shorts
- The internet had to monetize itself somehow (with attention)
- “Don’t be evil” and why Google had to remove it
- Questr: 2D exploration of nostr
- ONOSENDAI by Arkinox
- Freedom tech & Freedom from Tech
- DAUs of jumper cables
- Gossip and it’s choices
- “The secret to life is to send it”
- Flying water & flying bus stops
- RSS readers, Mailbrew, and daily digests
- Nostr is high signal and less addictive
- Calling nostr posts “tweets” and recordings being “on tape”
- Pivoting from nostr dialogues to a podcast about wind
- The unnecessary complexity of NIP-96
- Blossom (and wind)
- Undoing URLs, APIs, and REST
- ISBNs and cryptographic identifiers
- SaaS and the DAU metric
- Highlighter
- Not caring where stuff is hosted
- When is an edited thing a new thing?
- Edits, the edit wars, and the case against edits
- NIP-60 and inconsistent balances
- Scroll to text fragment and best effort matching
- Proximity hashes & locality-sensitive hashing
- Helping your Uncle Jack of a horse
- Helping your uncle jack of a horse
- Can we fix it with WoT?
- Vertex & vibe-coding a proper search for nostr
- Linking to hashtags & search queries
- Advanced search and why it’s great
- Search scopes & web of trust
- The UNIX tools of nostr
- Pablo’s NDK snippets
- Meredith on the privacy nightmare of Agentic AI
- Blog-post-driven development (Lightning Prisms, Highlighter)
- Sandwich-style LLM prompting, Waterfall for LLMs (HLDD / LLDD)
- “Speed itself is a feature”
- MCP & DVMCP
- Monorepos and git submodules
- Olas & NDK
- Pablo’s RemindMe bot
- “Breaking changes kinda suck”
- Stories, shorts, TikTok, and OnlyFans
- LLM-generated sticker styles
- LLMs and creativity (and Gigi’s old email)
- “AI-generated art has no soul”
- Nostr, zaps, and realness
- Does the source matter?
- Poker client in bitcoin v0.0.1
- Quotes from Hitler and how additional context changes meaning
- Greek finance minister on crypto and bitcoin (Technofeudalism, book)
- Is more context always good?
- Vervaeke’s AI argument
- What is meaningful?
- How do you extract meaning from information?
- How do you extract meaning from experience?
- “What the hell is water”
- Creativity, imagination, hallucination, and losing touch with reality
- “Bitcoin is singularity insurance”
- Will vibe coding make developers obsolete?
- Knowing what to build vs knowing how to build
- 10min block time & the physical limits of consensus
- Satoshi’s reasons articulated in his announcement post
- Why do anything? Why stack sats? Why have kids?
- All you need now is motivation
- Upcoming agents will actually do the thing
- Proliferation of writers: quantity VS quality
- Crisis of sameness & the problem of distribution
- Patronage, belle epoche, and bitcoin art
- Niches, and how the internet fractioned society
- Joe’s songs
- Hyper-personalized stories
- Shared stories & myths (Jonathan Pageau)
- Hyper-personalized apps VS shared apps
- Agency, free expression, and free speech
- Edgy content & twitch meta, aka skating the line of demonetization and deplatforming
- Using attention as a proxy currency
- Farming eyeballs and brain cycles
- Engagement as a success metric & engagement bait
- “You wouldn’t zap a car crash”
- Attention economy is parasitic on humanity
- The importance of speech & money
- What should be done by a machine?
- What should be done by a human?
- “The human spirit should remain in charge”
- Our relationship with fiat money
- Active vs passive, agency vs serfdom
-
 @ 9bde4214:06ca052b
2025-04-22 22:04:08
@ 9bde4214:06ca052b
2025-04-22 22:04:08"With the shift towards this multi-agent collaboration and orchestration world, you need a neutral substrate that has money/identity/cryptography and web-of-trust baked in, to make everything work."
Pablo & Gigi are getting high on glue.
Books & articles mentioned:
- Saving beauty by Byung-Chul Han
- LLMs as a tool for thought by Amelia Wattenberger
In this dialogue:
- vibeline & vibeline-ui
- LLMs as tools, and how to use them
- Vervaeke: AI thresholds & the path we must take
- Hallucinations and grounding in reality
- GPL, LLMs, and open-source licensing
- Pablo's multi-agent Roo setup
- Are we going to make programmers obsolete?
- "When it works it's amazing"
- Hiring & training agents
- Agents creating RAG databases of NIPs
- Different models and their context windows
- Generalists vs specialists
- "Write drunk, edit sober"
- DVMCP.fun
- Recklessness and destruction of vibe-coding
- Sharing secrets with agents & LLMs
- The "no API key" advantage of nostr
- What data to trust? And how does nostr help?
- Identity, web of trust, and signing data
- How to fight AI slop
- Marketplaces of code snippets
- Restricting agents with expert knowledge
- Trusted sources without a central repository
- Zapstore as the prime example
- "How do you fight off re-inventing GitHub?"
- Using large context windows to help with refactoring
- Code snippets for Olas, NDK, NIP-60, and more
- Using MCP as the base
- Using nostr as the underlying substrate
- Nostr as the glue & the discovery layer
- Why is this important?
- Why is this exciting?
- "With the shift towards this multi-agent collaboration and orchestration world, you need a neutral substrate that has money/identity/cryptography and web-of-trust baked in, to make everything work."
- How to single-shot nostr applications
- "Go and create this app"
- The agent has money, because of NIP-60/61
- PayPerQ
- Anthropic and the genius of mcp-tools
- Agents zapping & giving SkyNet more money
- Are we going to run the mints?
- Are agents going to run the mints?
- How can we best explain this to our bubble?
- Let alone to people outside of our bubble?
- Building pipelines of multiple agents
- LLM chains & piped Unix tools
- OpenAI vs Anthropic
- Genius models without tools vs midwit models with tools
- Re-thinking software development
- LLMs allow you to tackle bigger problems
- Increased speed is a paradigm shift
- Generalists vs specialists, left brain vs right brain
- Nostr as the home for specialists
- fiatjaf publishing snippets (reluctantly)
- fiatjaf's blossom implementation
- Thinking with LLMs
- The tension of specialization VS generalization
- How the publishing world changed
- Stupid faces on YouTube thumbnails
- Gaming the algorithm
- Will AI slop destroy the attention economy?
- Recency bias & hiding publication dates
- Undoing platform conditioning as a success metric
- Craving realness in a fake attention world
- The theater of the attention economy
- What TikTok got "right"
- Porn, FoodPorn, EarthPorn, etc.
- Porn vs Beauty
- Smoothness and awe
- "Beauty is an angel that could kill you in an instant (but decides not to)."
- The success of Joe Rogan & long-form conversations
- Smoothness fatigue & how our feeds numb us
- Nostr & touching grass
- How movement changes conversations
- LangChain & DVMs
- Central models vs marketplaces
- Going from assembly to high-level to conceptual
- Natural language VS programming languages
- Pablo's code snippets
- Writing documentation for LLMs
- Shared concepts, shared language, and forks
- Vibe-forking open-source software
- Spotting vibe-coded interfaces
- Visualizing nostr data in a 3D world
- Tweets, blog posts, and podcasts
- Vibe-producing blog posts from conversations
- Tweets are excellent for discovery
- Adding context to tweets (long-form posts, podcasts, etc)
- Removing the character limit was a mistake
- "Everyone's attention span is rekt"
- "There is no meaning without friction"
- "Nothing worth having ever comes easy"
- Being okay with doing the hard thing
- Growth hacks & engagement bait
- TikTok, theater, and showing faces and emotions
- The 1% rule: 99% of internet users are Lurkers
- "We are socially malnourished"
- Web-of-trust and zaps bring realness
- The semantic web does NOT fix this LLMs might
- "You can not model the world perfectly"
- Hallucination as a requirement for creativity
-
 @ 9bde4214:06ca052b
2025-04-22 22:01:34
@ 9bde4214:06ca052b
2025-04-22 22:01:34"The age of the idea guys has begun."
Articles mentioned:
- LLMs as a tool for thought by Amelia Wattenberger
- Micropayments and Mental Transaction Costs by Nick Szabo
- How our interfaces have lost their senses by Amelia Wattenberger
Talks mentioned:
- The Art of Bitcoin Rhetoric by Bitstein
Books mentioned:
- Human Action by Ludwig von Mises
- Working in Public by Nadia Eghbal
In this dialogue:
- nak
- Files
- SyncThing (and how it BitTorrent Sync became Resilio Sync)
- Convention over configuration
- Changes & speciation
- File systems as sources of truth
- Vibe-coding shower thoughts
- Inspiration and The Muse
- Justin's LLM setup
- Tony's setup (o1-pro as the architect)
- Being okay with paying for LLMs
- Anthropomorphising LLMs
- Dialog, rubber-duck debugging, and the process of thinking
- Being nice and mean to LLMs
- Battlebots & Gladiators
- Hedging your bets by being nice to Skynet
- Pascal's Wager for AI
- Thinking models vs non-thinking faster models
- Sandwich-style LLM prompting, again (waterfall stuff, HLDD / LLDD)
- Cursor rules & Paul's Prompt Buddy
- Giving lots of context vs giving specific context
- The benefit of LLMs figuring out obscure bugs in minutes (instead of days)
- The phase change of fast iteration and vibe coding
- Idea level vs coding level
- High-level vs low-level languages
- Gigi's "vibeline"
- Peterson's Logos vs Vervaeke's Dia-Logos
- Entering into a conversation with technology
- Introducing MCPs into your workflow
- How does Claude think?
- How does it create a rhyme?
- How does thinking work?
- And how does it relate to dialogue?
- Gzuuus' DVMCP & using nostr as an AI substrate
- Language Server Protocols (LSPs)
- VAAS: Vibe-coding as a service
- Open models vs proprietary models
- What Cursor got right
- What ChatGPT got right
- What Google got right
- Tight integration of tools & remaining in a flow state
- LLMs as conversational partners
- The cost of context switching
- Conversational flow & how to stay in it
- Prompts VS diary entries
- Solving technical vs philosophical models
- Buying GPUs & training your own models
- Training LLMs to understand Zig
- Preventing entryism by writing no documentation
- Thin layers & alignment layers
- Working in public & thinking in public
- Building a therapist / diary / notes / idea / task system
- "The age of the idea guys has begun."
- Daemons and spirits
- Monological VS dialogical thinking
- Yes-men and disagreeable LLMs
- Energy cost vs human cost
- Paying by the meter vs paying a subscription
- The equivalence of storage and compute
- Thinking needs memory, and memory is about the future
- Nostr+ecash as the perfect AI+human substrate
- Real cost, real consequence, and Human Action
- The cost of words & speaking
- Costly signals and free markets
- From shitcoin tokens to LLM tokens to ecash tokens
- Being too close to the metal & not seeing the forest for the trees
- Power users vs engineers
- Participatory knowing and actually using the tools
- Nostr as the germination ground for ecash
- What is Sovereign Engineering?
- LLVM and the other side of the bell-curve
- How nostr gives you users, discovery, mircopayments, a backend, and many other things for free
- Echo chambers & virality
- Authenticity & Realness
- Growing on the edges, catering to the fringe
- You don't own your iPhone
- GrapheneOS
- WebRTC and other monolithic "open" standards
- Optimizing for the wrong thing
- Building a nostr phone & Gigi's dream flow
- Using nostr to sync dotfile setups and other things
- "There are no solutions, only trade-offs"
- Cross-platform development
- Native vs non-native implementations
- Vitor's point on what we mean by native
- Does your custom UI framework work for blind people?
- Ladybird browser & how to build a browser from scratch
- TempleOS
- Form follows function & 90's interfaces
- Lamentations on the state of modern browsers
- Complexity & the downfall of the Legacy Web
- Nostr as the "new internet"
- Talks by Ladybird developer Andreas Kling
- Will's attempt of building it from scratch with Notedeck & nostr-db
- Justin's attempt with rust-multiplatform
- "If it doesn't have a rust implementation, you shouldn't use it."
- Native in terms of speed vs native in terms of UI/UX
- Engineer the logic, vibe-code the UI
- From Excalidraw to app in minutes
- What can you one-shot?
- What do you need to care about?
- Pablo's NDK snippets
- 7GUIs and GUI benchmarks for LLMs
- "Now we're purpose-building tools to make it easier for LLMs"
- "Certain tools really make your problems go away."
- Macros and meta-programming
- Zig's comptime
- UNIX tools and pipes
- Simple tools & composability
- Nostr tools for iOS & sharing developer signing keys
- Building 10 apps as one guy
- Simplicity in a community context
- Most people are on phones
- Most people don't install PWAs
- Zapstore & building our own distribution channels
- Web-of-trust and pushing builds quickly
- Improving homebrew by 10x
- (Micro)payments for package managers
- Guix and bitcoin-core
- Nix vs Guix
- Reproducible builds & web-of-trust
- Keet vs "calling an npub"
- Getting into someone's notifications
- Removing the character limit was a mistake
-
 @ ba36d0f7:cd802cba
2025-04-22 20:30:45
@ ba36d0f7:cd802cba
2025-04-22 20:30:45| Pieza | Movimiento | Reglas Especiales | | --------- | ---------------------------------- | --------------------------- | | Peón | 1 casilla adelante (o 2 al inicio) | Captura al paso, coronación | | Torre | Líneas rectas | Enroque | | Caballo | En "L" (2+1) | Salta piezas | | Alfil | Diagonales | Atrapado en un color | | Dama | Cualquier dirección | Ninguna | | Rey | 1 casilla en cualquier dirección | Enroque, jaque mate |
1. Peón (♙ / ♟️)
- Mueve: 1 casilla adelante (o 2 en su primer movimiento).

- Captura: En diagonal (1 casilla).
 > Especial:
>- Captura al paso: Si un peón rival avanza 2 casillas, puedes capturarlo como si hubiera movido 1.
> - Coronación: Al llegar a la 8ª fila, se convierte en cualquier pieza (¡usualmente Dama!).
> Especial:
>- Captura al paso: Si un peón rival avanza 2 casillas, puedes capturarlo como si hubiera movido 1.
> - Coronación: Al llegar a la 8ª fila, se convierte en cualquier pieza (¡usualmente Dama!).
2. Torre (♖ / ♜)
- Mueve: Líneas rectas (sin límite de casillas).

- Especial: Participa en el enroque.
3. Caballo (♘ / ♞)
-
Mueve: En "L" (2 casillas en una dirección + 1 perpendicular).
-
Única pieza que salta sobre otras.
4. Alfil (♗ / ♝)
-
Mueve: Diagonales (sin límite).
-
Siempre permanece en el mismo color de casilla.

5. Dama (♕ / ♛)
- Mueve: Cualquier dirección (recto o diagonal).

- ¡La pieza más poderosa!
6. Rey (♔ / ♚)
- Mueve: 1 casilla en cualquier dirección.

Especial:
- Enroque: Cambia de lugar con una torre (si no hay obstáculos/jaques). - Jaque mate: Pierde si queda atrapado sin escapatoria.
Cómo mover
-
Un movimiento por turno.
-
Elige tu pieza y colócala en una casilla legal.
-
Solo tu color: Blancas mueven primero, luego negras, alternando.
-
No pasar: Debes mover si es tu turno.
Cómo capturar ("comer")
-
Ocupa la casilla de una pieza rival: Reemplázala con tu pieza.
-
Peones capturan solo en diagonal (no de frente).
-
Los reyes no pueden ser capturados (el jaque mate termina el juego).
✔ Jaque: Ataca al rey enemigo (debe escapar en su siguiente turno).
❌ Ilegal: Mover a jaque o dejar a tu rey en jaque.
Movimientos especiales
|Movimiento|Regla Clave|Notación| |---|---|---| |Enroque|Rey + torre, sin movimientos previos|
0-0| |Coronación|Peón→cualquier pieza en 8ª fila|e8=D| |Captura al paso|Captura un peón que avanzó 2 casillas|exd6 a.p.|
1. Enroque ("La escapatoria del rey")
-
Qué: Rey y torre se mueven juntos en un turno.
Cómo: -
Rey mueve 2 casillas hacia una torre.
-
Torre "salta" al lado opuesto del rey.

Reglas: - Sin jaques: El rey no puede estar en jaque ni pasar por casillas atacadas. - Sin movimientos previos: Ni el rey ni esa torre deben haberse movido antes.
Tipos:
- Corto (lado del rey, rápido):0-0- Largo (lado de la dama, seguro):0-0-0
2. Coronación ("Coronar")
-
Qué: Peón llega a la 8ª fila → se convierte en cualquier pieza (usualmente Dama).
-
Cómo: Reemplaza el peón (incluso si ya tienes esa pieza).
Dato curioso: Puedes tener 9 damas (1 original + 8 coronaciones).
Ejemplo: Peón en h8 se convierte en Dama →h8=D.
3. Captura al paso (Del francés "en passant")
-
Cuándo: Un peón rival avanza 2 casillas y queda al lado del tuyo.
-
Cómo: Captúralo en diagonal (como si hubiera movido 1 casilla).

Regla: Debes hacerlo inmediatamente (solo en el turno siguiente)
Recurso digitales
Guia para principiantes - Lichess.org https://lichess.org/study/Hmb28fbv/QRyxzgre
Ajedrez desde cero - Youtube.com https://www.youtube.com/watch?v=YPf9fSY_K2k&list=PLWgqlpb234bHv38g6zXoi3WIJJonzZSAl&index=8
- Mueve: 1 casilla adelante (o 2 en su primer movimiento).
-
 @ 9223d2fa:b57e3de7
2025-04-22 20:02:06
@ 9223d2fa:b57e3de7
2025-04-22 20:02:069,322 steps
-
 @ df478568:2a951e67
2025-04-22 18:56:38
@ df478568:2a951e67
2025-04-22 18:56:38"It might make sense just to get some in case it catches on. If enough people think the same way, that becomes a self fulfilling prophecy. Once it gets bootstrapped, there are so many applications if you could effortlessly pay a few cents to a website as easily as dropping coins in a vending machine." --Satoshi Nakamoto The Cryptography Mailing List--January 17, 2009
Forgot to add the good part about micropayments. While I don't think Bitcoin is practical for smaller micropayments right now, it will eventually be as storage and bandwidth costs continue to fall. If Bitcoin catches on on a big scale, it may already be the case by that time. Another way they can become more practical is if I implement client-only mode and the number of network nodes consolidates into a smaller number of professional server farms. Whatever size micropayments you need will eventually be practical. I think in 5 or 10 years, the bandwidth and storage will seem trivial. --Satoshi Nakamoto Bitcoin Talk-- August 5, 2010
I very be coded some HTML buttons using Claude and uploaded it to https://github.com/GhostZaps/ It's just a button that links to zapper.fun.
I signed up for Substack to build an email address, but learned adding different payment options to Substack is against their terms and services. Since I write about nostr, these terms seem as silly as someone saying Craig Wright is Satoshi. It's easy to build an audience on Substack however, or so I thought. Why is it easier to build an audience on Subtack though? Because Substack is a platform that markets to writers. Anyone with a ~~pen~~ ~~keyboard~~ smartphone and an email can create an account with Substack. There's just one problem: You are an Internet serf, working the land for your Internet landlord--The Duke of Substack.
Then I saw that Shawn posted about Substack's UX.
I should have grabbed my reading glasses before pushing the post button, but it occurred to me that I could use Ghost to do this and there is probably a way to hack it to accept bitcoin payments over the lightning network and host it yourself. So I spun my noddle, doodled some plans...And then it hit me. Ghost allows for markdown and HTML. I learned HTML and CSS with free-code camp, but ain't nobody got time to type CSS so I vibe-coded a button that ~~baits~~ sends the clicker to my zapper.fun page. This can be used on any blog that allows you to paste html into it so I added it to my Ghost blog self-hosted on a Start 9. The blog is on TOR at http://p66dxywd2xpyyrdfxwilqcxmchmfw2ixmn2vm74q3atf22du7qmkihyd.onion/, but most people around me have been conditioned to fear the dark web so I used the cloudflared to host my newsletter on the clear net at https://marc26z.com/
Integrating Nostr Into My Self-Hosted Ghost Newsletter
I would venture to say I am more technical than the average person and I know HTML, but my CSS is fuzzy. I also know how to print("Hello world!") in python, but I an NPC beyond the basics. Nevertheless, I found that I know enough to make a button. I can't code well enough to create my own nostr long-form client and create plugins for ghost that send lightning payments to lighting channel, but I know enough about nostr to know that I don't need to. That's why nostr is so F@#%-ing cool! It's all connected. ** - One button takes you to zapper.fun where you can zap anywhere between 1 and ,000,000 sats.** - Another button sends you to a zap planner pre-set to send 5,000 sats to the author per month using nostr. - Yet another button sends you to a zap planner preset to send 2,500 sats per month.
The possibilities are endless. I entered a link that takes the clicker to my Shopstr Merch Store. The point is to write as self-sovereign as possible. I might need to change my lightning address when stuff breaks every now and then, but I like the idea of busking for sats by writing on the Internet using the Value 4 Value model. I dislike ads, but I also want people to buy stuff from people I do business with because I want to promote using bitcoin as peer-to-peer electronic cash, not NGU porn. I'm not prude. I enjoy looking at the price displayed on my BlockClock micro every now and then, but I am not an NGU porn addict.
This line made this pattern, that line made this pattern. All that Bolinger Bart Simpson bullshit has nothing to with bitcoin, a peer-to-peer electronic cash system. It is the musings of a population trapped in the fiat mind-set. Bitcoin is permissionless so I realized I was bieng a hipocryte by using a permissioned payment system becaue it was easier than writing a little vibe code. I don't need permission to write for sats. I don't need to give my bank account number to Substack. I don't need to pay a 10$ vig to publish on a a platform which is not designed for stacking sats. I can write on Ghost and integrate clients that already exist in the multi-nostr-verse.
Nostr Payment Buttons
The buttons can be fouund at https://github.com/Marc26z/GhostZapButton
You can use them yourself. Just replace my npub with your npub or add any other link you want. It doesn't technically need to be a nostr link. It can be anything. I have a link to another Ghost article with other buttons that lead down different sat pledging amounts. It's early. Everyone who spends bitcoin is on nostr and nostr is small, but growing community. I want to be part of this community. I want to find other writers on nostr and stay away from Substack.
Here's what it looks like on Ghost: https://marc26z.com/zaps-on-ghost/
npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0
-
 @ 9bde4214:06ca052b
2025-04-22 18:13:37
@ 9bde4214:06ca052b
2025-04-22 18:13:37"It's gonna be permissionless or hell."
Gigi and gzuuus are vibing towards dystopia.
Books & articles mentioned:
- AI 2027
- DVMs were a mistake
- Careless People by Sarah Wynn-Williams
- Takedown by Laila michelwait
- The Ultimate Resource by Julian L. Simon
- Harry Potter by J.K. Rowling
- Momo by Michael Ende
In this dialogue:
- Pablo's Roo Setup
- Tech Hype Cycles
- AI 2027
- Prompt injection and other attacks
- Goose and DVMCP
- Cursor vs Roo Code
- Staying in control thanks to Amber and signing delegation
- Is YOLO mode here to stay?
- What agents to trust?
- What MCP tools to trust?
- What code snippets to trust?
- Everyone will run into the issues of trust and micropayments
- Nostr solves Web of Trust & micropayments natively
- Minimalistic & open usually wins
- DVMCP exists thanks to Totem
- Relays as Tamagochis
- Agents aren't nostr experts, at least not right now
- Fix a mistake once & it's fixed forever
- Giving long-term memory to LLMs
- RAG Databases signed by domain experts
- Human-agent hybrids & Chess
- Nostr beating heart
- Pluggable context & experts
- "You never need an API key for anything"
- Sats and social signaling
- Difficulty-adjusted PoW as a rare-limiting mechanism
- Certificate authorities and centralization
- No solutions to policing speech!
- OAuth and how it centralized
- Login with nostr
- Closed vs open-source models
- Tiny models vs large models
- The minions protocol (Stanford paper)
- Generalist models vs specialized models
- Local compute & encrypted queries
- Blinded compute
- "In the eyes of the state, agents aren't people"
- Agents need identity and money; nostr provides both
- "It's gonna be permissionless or hell"
- We already have marketplaces for MCP stuff, code snippets, and other things
- Most great stuff came from marketplaces (browsers, games, etc)
- Zapstore shows that this is already working
- At scale, central control never works. There's plenty scams and viruses in the app stores.
- Using nostr to archive your user-generated content
- HAVEN, blossom, novia
- The switcharoo from advertisements to training data
- What is Truth?
- What is Real?
- "We're vibing into dystopia"
- Who should be the arbiter of Truth?
- First Amendment & why the Logos is sacred
- Silicon Valley AI bros arrogantly dismiss wisdom and philosophy
- Suicide rates & the meaning crisis
- Are LLMs symbiotic or parasitic?
- The Amish got it right
- Are we gonna make it?
- Careless People by Sarah Wynn-Williams
- Takedown by Laila michelwait
- Harry Potter dementors & Momo's time thieves
- Facebook & Google as non-human (superhuman) agents
- Zapping as a conscious action
- Privacy and the internet
- Plausible deniability thanks to generative models
- Google glasses, glassholes, and Meta's Ray Ben's
- People crave realness
- Bitcoin is the realest money we ever had
- Nostr allows for real and honest expression
- How do we find out what's real?
- Constraints, policing, and chilling effects
- Jesus' plans for DVMCP
- Hzrd's article on how DVMs are broken (DVMs were a mistake)
- Don't believe the hype
- DVMs pre-date MCP tools
- Data Vending Machines were supposed to be stupid: put coin in, get stuff out.
- Self-healing vibe-coding
- IP addresses as scarce assets
- Atomic swaps and the ASS protocol
- More marketplaces, less silos
- The intensity of #SovEng and the last 6 weeks
- If you can vibe-code everything, why build anything?
- Time, the ultimate resource
- What are the LLMs allowed to think?
- Natural language interfaces are inherently dialogical
- Sovereign Engineering is dialogical too
-
 @ 9bde4214:06ca052b
2025-04-22 17:30:02
@ 9bde4214:06ca052b
2025-04-22 17:30:02“We do not have the answers."
Pablo & Gigi have no solutions.
In this dialogue:
- What is this No Solutions thing anyway?
- Why dialogue and distributed cognition is so important
- Why is nostr exciting for developers?
- Evolution, Life, and nostr
- What is the perfect nostr app, and why can’t there be THE perfect nostr app?
- Why there is no “global” view in nostr
- Impossible problems vs. possible (but still hard) problems
- Blossom, blossom, and more blossom
- Zooko’s Triangle
- Freedom Tech Building Blocks
- NIP-60/61, NIP-89
- Email vs ICQ
- Accepting constraints & moving forward
- Nostr has data integrity, but no data guarantees
- Bitcoin as an extreme RAID system
- Fault tolerance vs. efficiency
- “Build the infrastructure, don’t run it.”
- eCash fixes 402
- Everything in nostr can be one-click
- There’s infinite nsecs (and they are free!)
- The magic of the nostr view-only mode
- The Local-first movement
- How to monetize without putting yourself in the middle?
- RoboSats as an example of open-source monetization
- The YouTube like count is a lie
Further links:
- https://en.wikipedia.org/wiki/Distributed_cognition
- https://nips.nostr.com/60
- https://nips.nostr.com/61
- https://nips.nostr.com/89
- https://github.com/hzrd149/blossom
- https://en.wikipedia.org/wiki/Zooko’s_triangle
- https://www.jrepodcast.com/guest/adam-curry/
- https://localfirstweb.dev/
- https://www.localfirstconf.com/
- https://en.wikipedia.org/wiki/ICQ
- https://appleinsider.com/articles/24/05/25/icq-1996-2024-the-first-universal-messenger-had-a-good-run-and-is-leaving-us-soon
- https://www.chatinum.com/articles/the-old-chat-apps-of-the-2000s
- https://en.wikipedia.org/wiki/Standard_RAID_levels
- https://www.youtube.com/watch?v=oIkhgagvrjI
- https://njump.me/nosolutions@sovereignengineering.io
-
 @ 9bde4214:06ca052b
2025-04-22 17:23:02
@ 9bde4214:06ca052b
2025-04-22 17:23:02“You’ll get all that for free if you build it right.”
Pablo & Gigi try to stop giggling.
In this dialogue:
- 01: Start Ugly
- 02: There is No Global
- Concept of ownership & “Read, Write, Own”
- Shamir Secret Sharing and Timelocks
- “No amount of violence will ever solve a math problem.”
- You can’t prove deletion of a key (or anything, really); best you can do is “burn” bitcoin
- Data is information, which behaves like an idea (not like an apple)
- “If you have an apple and I have an apple and we exchange these apples then you and I will still each have one apple. But if you have an idea and I have an idea and we exchange these ideas, then each of us will have two ideas.” – https://dergigi.com/threads/memes-vs-the-world
- Why the Pubky architecture isn’t great
- Cashu
- Nutzaps: NIP-60 / NIP-61
- How nutzaps fix fake zaps on zaplife.lol
- “Ecash fixes HTTP 402”
- “[Bitcoin [and nostr]] take advantage of the nature of information being easy to spread but hard to stifle.” –Satoshi Nakamoto
- Discovery with NIP-89
- #RunDVM with NIP-90
- Why micropayments can’t work on credit rails, and how bitcoin is the rediscovery of money.
- Putting payments into blossom
- “Money is essentially a tool to keep track of who owes what to whom. Broadly speaking, everything we have used as money up to now falls into two categories: physical artifacts and informational lists. Or, to use more common parlance: tokens and ledgers.”
- “maximum utility in the world of Bitcoin entails the adoption of maximum responsibility.”
- Complexity of Lightning vs the simplicity of eCash
- Amber and Citrine
- How Pablo became the BIS
- 12 words in your head can literally save your life
- The in-between of custodial and non-custodial in a multi-mint world
- Nutzaps integrated in chachi.chat
- The intermediacy of nostr is magic
- In nostr you’ll get a lot for free IF YOU BUILD IT RIGHT
- “Free Speech platforms cannot exist; if there is a ‘deplatform’ button, the button will be pressed.”
- “Neither nostalgia nor utopia.”
- Solutions that make stuff worse over time vs solutions that make stuff better over time.
-
asknostr on passkeys, and why we think they’ll make things worse over time.
- Authentication vs identity: “identification asks, authentication proves”
- You are not your name and photo; identity is prismatic
- (m00t’s talk on it at web summit 2011)
- Starbug from CCC pwning TouchID biometrics from a high-res photo (article)
- Key rotation and (American) HODL
- Social recovery
- Multi-sig for nostr with FROSTR
Links & References:
- Nostr Protocol Repository: https://github.com/nostr-protocol
- Cashu (e-cash): https://github.com/cashubtc
- NIP-60 (Nutzaps): https://github.com/nostr-protocol/nips/blob/master/60.md
- NIP-89 (Service Discovery) & NIP-90 (DVMs) – upcoming proposals: https://nips.nostr.com/89 & https://nips.nostr.com/90
-
 @ 9bde4214:06ca052b
2025-04-22 17:15:24
@ 9bde4214:06ca052b
2025-04-22 17:15:24“I don’t believe in Utopia anymore. I’m too old for that.”
Calle & Gigi philosophize about nuts.
Books and articles mentioned:
In this dialogue:
- Where is the Utopia that the internet promised?
- “Neither nostalgia nor utopia”
- Net Neutrality is a moral stance
- Where did the internet go wrong?
- Tech as a tool; is tech always neutral?
- Technology that increases agency VS tech that enslaves
- Competition vs Symbiosis
- “Who will run the mints?”
- “Anyone” can use it vs “everyone” can use it
- Centralizing vs. Monopolizing
- Bitcoin has an ethos baked in (You Shall Not Steal)
- Passive internet vs active internet
- Agency in cyberspace, and how to maximize it
- Blinded custodian vs regular custodian
- User data is a liability
- Obscura / Mullvad / Silent.Link as obvious early adopters
- Run your own ISP - Tollgate
- Cryptography is Not Enough
- Bitcoin is Time
- Time requires heat
- Zero-knowledge service providers
- Electronic Cash vs Digital Cash (CBDCs)
- Credit requires KYC, KYC implies outside enforcement
- Writings on Micropayments by Nick Szabo
- eCash fixes 402, obviously
- Who Owns the Future?
- “You are the product” vs “Subscription Hell”
- “Hello old friend!!!”
- Cathedral vs Bazaar
- Why paywalls suck
- Information wants to be free
- "Markets become absurd as supply approaches infinity."
- eCash + AI = match made in heaven
- #LearnToCode vs #LearnToPrompt
- Scarcity in cyberspace: compute, storage, networking
- Zero-Knowledge compute & zero-knowledge proofs
- https://en.wikipedia.org/wiki/Zero-knowledge_proof
- https://github.com/AbdelStark/cashu-zk-engine
- Cairo: https://github.com/starkware-libs/cairo
- MCP https://github.com/AbdelStark/bitcoin-mcp
- MCP DVM: https://github.com/r0d8lsh0p/n8n-AI-agent-DVM-MCP-client
- DVMCP: https://mcp.so/server/dvmcp
- Olas & Nutzaps (NIP-60, NIP-61)
- Bitcoin is not only the internet of money, but it is the money of the internet
- Re-building the internet archive on top of nostr
- Bitrot & 404
- Resurrection markets & marketplace for hashes via Blossom
- Hugs 🫂
-
 @ f10512df:c9293bb3
2025-04-22 17:11:05
@ f10512df:c9293bb3
2025-04-22 17:11:05Details
- 🍳 Cook time: 5-7 minutes
- 🍽️ Servings: 1
Ingredients
- 2 eggs
- Shredded cheese (Sharp cheddar is a favorite)
- 1 Tbsp olive oil or ghee
Directions
- Add oil to a non-stick pan and allow it to get hot (med-high heat)
- Add eggs and additional toppings, scramble and wait for the edges to get brown.
- Add shredded cheese while edges are browning. It is best if cheese begins to melt before flipping.
- Flip, and make sure all cheese stayed down, and there is enough oil left in the pan.
- Keep checking until pan side of eggs lift easily. Done correctly, the cheese will form a crisp layer.
- When fully cooked, serve with cheese right side up and enjoy!
-
 @ 9bde4214:06ca052b
2025-04-22 17:09:47
@ 9bde4214:06ca052b
2025-04-22 17:09:47“It isn’t obvious that the world had to work this way. But somehow the universe smiles on encryption.”
hzrd149 & Gigi take a stroll along the shore of cryptographic identities.
This dialogue explores how cryptographic signatures fundamentally shift power dynamics in social networks, moving control from servers to key holders. We discuss the concept of "setting data free" through cryptographic verification, the evolving role of relays in the ecosystem, and the challenges of building trust in decentralized systems. We examine the tension between convenience and decentralization, particularly around features like private data and data synchronization. What are the philosophical foundations of building truly decentralized social networks? And how can small architectural decisions have profound implications for user autonomy and data sovereignty?
Movies mentioned:
- 2001: A Space Odyssey (1968)
- Soylent Green (1973)
- Close Encounters of the Third Kind (1977)
- Johnny Mnemonic (1995)
- The Matrix (1999)
In this dialogue: - Hzrd's past conversations: Bowls With Buds 316 & 361 - Running into a water hose - Little difference, big effect - Signing data moves the power to the key holders - Self-signing data sets the data free - Relay specialization - Victor's Amethyst relay guide - Encryption and decryption is expensive - is it worth it? - The magic of nostr is that stuff follows you around - What should be shown? What should be hidden? - Don't lie to users. Never show outdated data. - Nostr is raw and immediate - How quickly you get used to things working - Legacy web always tries to sell you something - Lying, lag, frustration - How NoStrudel grew - NoStrudel notifications - Data visualization and dashboards - Building in public and discussing in public - Should we remove DMs? - Nostr as a substrate for lookups - Using nostr to exchange Signal or SimpleX credentials - How private is a group chat? - Is a 500-people group chat ever private? - Pragmatism vs the engineering mindset - The beauty and simplicity of nostr - Anti-patterns in nostr - Community servers and private relays - Will vibe coding fix (some of the) things? - Small specialized components VS frameworks - Technology vs chairs (and cars, and tractors, and books) - The problem of being greedy - Competitive silos VS synergistic cooperation - Making things easy vs barriers of entry - Value4value for music and other artists - Adding code vs removing code - Pablo's Roo setup and DVMCP - Platform permission slips vs cryptographic identities - Micropayments vs Subscription Hell - PayPerQ - Setting our user-generated data free - The GNU/Linux approach and how it beat Microsoft - Agents learning automatically thanks to snippets published on nostr - Taxi drivers, GPS, and outsourcing understanding - Wizards VS vibe coders - Age differences, Siri, and Dragon Naturally Speaking - LLMs as a human interface to call tools - Natural language vs math and computer language - Natural language has to be fuzzy, because the world is fuzzy - Language and concepts as compression - Hzrd watching The Matrix (1999) for the first time - Soylent Green, 2001, Close Encounters of the 3rd Kind, Johnny Mnemonic - Are there coincidences? - Why are LLMs rising at the same time that cryptography identities are rising? - "The universe smiles at encryption" - The universe does not smile upon closed silos - The cost of applying force from the outside - Perfect copies, locality, and the concept of "the original" - Perfect memory would be a curse, not a blessing - Organic forgetting VS centralized forgetting - Forgetting and dying needs to be effortless - (it wasn't for IPFS, and they also launched a shitcoin) - Bitcoin makes is cheap to figure out what to dismiss - Would you like to have a 2nd brain? - Trust and running LLMs locally - No need for API keys - Adjacent communities: local-first, makers and hackers, etc. - Removing the character limit was a mistake - Browsing mode vs reading mode - The genius of tweets and threads - Vibe-coding and rust-multiplatform - Global solutions vs local solutions - The long-term survivability of local-first - All servers will eventually go away. Your private key won't. - It's normal to pay your breakfast with sats now - Nostr is also a normal thing now, at least for us - Hzrd's bakery - "Send Gigi a DM that says GM" - and it just works - The user is still in control, thanks to Amber - We are lacking in nostr signing solutions - Alby's permission system as a step in the right direction - We have to get better at explaining that stuff - What we do, why we care, why we think it's important
-
 @ 9bde4214:06ca052b
2025-04-22 17:00:55
@ 9bde4214:06ca052b
2025-04-22 17:00:55"What should the next iteration of the internet look like?"
Paul & Gigi pray for a better tomorrow.
Books mentioned:
- The Bible
- I, Pencil by Leonard E. Read
- Don't make me think! by Steve Krug
- The Sovereign Individual by James Dale Davidson and William Rees-Mogg
In this dialogue:
- Paul and his awesome nostr t-shirt
- Are we all just nostalgic?
- Where did the optimism of computing and the information superhighway go?
- We went from interop to pay-to-unlock.
- Do we have to live in the digital gulags forever?
- Homecooked meals and homecooked apps
- Paper straws and the downfall of Western Civilization
- "You need to be okay with people getting rekt"
- If the car would be introduced today, it would be illegal
- Bravery and personal responsibility
- "nostr will only be what diehards will build it to be"
- Bad teleology is built into the current (non-nostr) app landscape
- "You can get a lot of the upside without holding your own keys”
- “...but you can't get ALL of the upside!"
- Expressiveness and free speech online
- Freedom of Speech, Freedom of Assembly, and Financial Freedom in Cyberspace
- Self-publishing vs platform publishing
- Information calories. Can we count them?
- Don't make me think!
- Is not being forced to think part of the problem?
- Mutiny & bitcoin UX that's too easy
- Games and costly mistakes
- The early days: software distribution via print magazines
- Prompting allows you to define your own teleology
- Vibe coding and Cursor
- "The hard part is to figure out what you want."
- "What should the next iteration of the internet look like?"
- GenZ doesn't know shit about files and folders
- Why files are great
- Gigi's SyncThing & Standard Notes setup
- File-based apps like Smart AudioBook Player
- Reading apps like Pocket, Instapaper, and Readwise Reader
- Saving all the things & linking stuff together
- Clips of podcasts and videos, e.g. Fountain
- A Commonplace Book to cyberspace
- Creating a "Family Bible" app
- If you want to maximize profits in the attention economy, you have to get users addicted
- (Zaps potentially fix this, as you wouldn’t zap a car crash)
- Let computers do computer work, let humans be humans
- "The end is not being on the computer"
- Solo private / group private / public
- Liberal vs Conservative sentiment in social environments
- Whom to care about?
- Web of trust & our understanding of it
- Forgiveness, Trust, and Repeat Games
- Tit-for-tat and forgiving tit-for-tat
- Three strikes and you're out!
- "Choose your gulag" is the alternative to nostr
- 7-generation thinking
- 2140
- The Sovereign Individual is embedded in a social structure, always
- I, Pencil
- Jungle vs Civilization
- Fiat = because I said so (“Fiat Lux” - Let there be light)
- Do we need leaders in bitcoin?
- Peterson Fallacy / God vs Bitcoin
- Jesus early followers were the Followers of The Way
- Zaps are not payments
- Zaps are not "tips"
- Bitstein & Pierre: The Reorg
- Vervaeke: “Where do you go for wisdom?”
- Rough consensus and Pieter Wuille
- "There is no such thing as a leaderless system"
- Wisdom in cyberspace
- Can we build wise tools?
- Prompting the Bible, ChristGPT, and Bible Slop
- Gell-Mann amnesia effect
- Vervaekes AI argument: The Coming Thresholds and The Path We Must Take
- Where do new ideas come from?
- Sandwich prompting style (HLDD / LLDD)
- The Tale of John Henry
- Silicon Sages
- Conscience and The Muse
- Hypermedia and HyperNote
- Glassholes, Google Glasses, and wearable technology
- Prompting & Praying for An Internet Worth Having
-
 @ 6e0ea5d6:0327f353
2025-04-24 03:07:34
@ 6e0ea5d6:0327f353
2025-04-24 03:07:34Ascolta bene, amico mio!
There is a kind of solitude that doesn’t come from the absence of company, but from the weight of the role one must play.
I’m not talking about being admired, followed, or applauded by outsiders — but of being necessary to those of your own blood.
Of being the one upon whom everything rests, even if no one ever acknowledges it.Truly, I learned throughout my life in the province of Sicily that the man who is held up by no one, yet holds up many — that man has no right to collapse. Not because he is stronger. But because if he falls, he doesn’t fall alone — he brings down the roof over those who live under his shadow.
And here lies the silent tragedy:
No one catches him when he falters.
But everyone collapses when he does.He is the father who cannot fall ill,
The son who becomes the pillar for his parents,
The leader who must never hesitate,
The older brother who must not cry,
The man of honor who must do “whatever must be done.”The exhaustion is real. The fatigue, daily.
But this kind of man learns to live with weariness as others live with pain:
It’s not about waiting for relief, but about continuing to walk despite the crushing weight.
That’s why, amico mio, never ask for lighter burdens — but always for stronger shoulders.In this context, renunciation is not a personal choice.
It is a collective sentence.
It’s like demolishing a pillar and expecting the ceiling to remain intact.Therefore, the man who carries this awareness does not allow himself the luxury of giving up.
He doesn’t grant himself the right to fail — not out of heroism, but out of clarity.
He knows that his collapse would cost a family.Learn this: l’onore non è individuale.
True honor is collective and familial.
What you endure, you endure for your own.
What you face, you face for those who came before you, and those who will come after.
And what you cannot abandon is not about pride — it’s about responsibility.There is no glory in it.
There are no medals.
But there is a silent, unshakable dignity that only a few ever understand:
To be the foundation — never the weight.The name for this is honor, loyalty, and pride.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ f10512df:c9293bb3
2025-04-22 17:00:44
@ f10512df:c9293bb3
2025-04-22 17:00:44Chef's notes
Use a tea bag to hold the spices. I like to fill it and drape it on the side of the pan so the flavors get in, and then toss it before serving. Easier than picking rosemary out of your teeth later.
Details
- ⏲️ Prep time: 20 minutes
- 🍳 Cook time: 1 hour 45 from scratch, 45 if using chicken stock
- 🍽️ Servings: 4
Ingredients
- 1 Cup Carrots (sliced)
- 1C celery (sliced)
- 2 cloves garlic
- 1 tsp dried thyme
- 1/2 tsp dried minced onion
- 2 Tbsp lemon juice (or more to taste)
- 1/2 Tbsp salt (to taste)
- 1 rotisserie chicken
- 2 tsp dried rosemary (or 1-2 sprigs fresh)
- 8 C water & additional 1-2 C later
- 10 oz pre-cooked noodles
- 1 tsp cracked pepper (to taste)
Directions
- Remove chicken meat from bones and set aside. Do not discard skin. Put bones and skin in a large stock pot and add water. Let boil covered for one hour, and then remove bones and strain out any bits of skin from broth.
- Add chopped vegetables, spices, and lemon juice to broth with up to 2 C. additional water to replace what might have boiled away. Simmer over low to medium heat (covered) for another half hour, stirring occasionally. Add in chicken meat. Taste test and add additional salt if needed.
- When vegetables are cooked, add in noodles and stir for an additional 2-3 minutes until hot (uncovered), and enjoy.
- If using store bought chicken stock, only simmer until vegetables are cooked (about half an hour).
-
 @ fd06f542:8d6d54cd
2025-04-24 02:23:58
@ fd06f542:8d6d54cd
2025-04-24 02:23:58今天主要是更新了seo优化:
- 增加了 blog页面的预加载内容,这样搜索引起抓取blog页面的时候,能够看到的是渲染好的 blog 列表;
- 增加里 blog/[blogid] 页面的 显示原文静态链接,这个链接主要是给搜索引擎使用,他根据原文可以抓取content内容
- 在+page.svelte页面 增加了 raw 数据显示,用户也可以看到和搜索引擎一样的内容,这个取决于 svelte的页面访问路由机制,她发现是api访问就会调用 server.ts返回数据,她发现是浏览器访问就会返回+page.svelte渲染的内容。 这个设计让搜索引擎和 浏览器看到的有区别。所以我两个都做了。
接下来的工作计划
- 增加 blog的评论和点赞功能?
- 美化页面?
- 做一个electron的客户端?
- 给用户做一个 通过blog定制化自己的主页?
关于nostrbook的 想法
用户其实可以通过nostrbook 搭建自己的blog系统,或者写书系统。在公司内网或者自己的服务器上。
修改config.ts的面的三个配置就可以了。 ```js
export let booktag="createbook"; export let blogtag="createblog"; export let chaptertag="bookchapter"; ```
我也是通过这个开关测试了线上和测试的开发的内容区分开的。
昨天发现的bug
就是 30023 update问题,虽然可以通过dtag可以实现替换。但是部分服务器没有update到最新的。所以他会返回老的。 是不是通过服务器之间的同步可以解决呢?
-
 @ 9bde4214:06ca052b
2025-04-22 16:35:00
@ 9bde4214:06ca052b
2025-04-22 16:35:00"We have the chance of building the next iteration of the internet, and hopefully, not repeat the mistakes of the past."
In this dialogue:
- Why starting ugly and shipping early is hard
- The ugliest thing that Pablo ever shipped
- “Happiness is shipping”
- Make it real first, you can make it pretty later
- Getting into the habit of shipping
- Highlighter and the hang-up of shipping something big
- How nostr allows you to have cash flow from the get-go
-
value4value for artists and devs
- What DHH & 37Signals got right
People and projects mentioned:
Further links:
- https://excellentjourney.net/2015/03/04/art-fear-the-ceramics-class-and-quantity-before-quality/
- https://world.hey.com/dhh/that-shipping-feeling-b7c8c565
- https://world.hey.com/dhh/i-was-wrong-we-need-crypto-587ccb03
- https://sovereignengineering.io/
- https://dergigi.com/2023/04/04/purple-text-orange-highlights/
- https://highlighter.com/
- https://njump.me/nosolutions@sovereignengineering.io
-
 @ 9a859fbc:8a9270f3
2025-04-22 15:45:55
@ 9a859fbc:8a9270f3
2025-04-22 15:45:55A story of art and inspiration
This image was generated by AI
That is...
I am artificial. I was created by two other humans (hi mum and dad 👋)
I am intelligent. I can perceive the world, experience it, learn to understand cause & effect, and make decisions.
To go perhaps deeper, cells, DNA and life itself are artifices of the fabric of reality.
I sat, in a pub in Bristol, a place where I rarely frequent. I sat with one housemate, who I rarely spent time with. I met his friends that day, only once, never we met again.
I got chatting with a lady there. I had some paper and pencils with me. My intention, for a couple of weeks, was to come up with a symbol to represent Deep Sea Frequencies, at that time still known as Psychedelic Jelly. We were a new collaboration.
She and I got chatting about art. About symbolic representation of concepts, feelings, ideas. We chatted about flow, about how there are different types of flow, different elemental conditions of flow. I doodled some shapes, and we noticed how fire, water and air all look similar due to their fluid natures. So we considered how to differentiate, distinguish them from one another.
I doodled some more, and we came up with swooshes, curls, crests and bubbles. These seemed to be distinguishing enough such that they were no longer reminiscent of fire or air. I doodled fire and air too, just in case, just to check.
Then we chatted about symmetry types, reflective, axes, rotational. About geometry, geometric containers. We both enjoy triangles and hexagons. (It's always hexagons!)
I doodled some more shapes and put them in hexagonal shapes. Then I tried bending them into triangular forms instead, and overlaid two triangles.
Each triangle looked like a triskelion. Perfect.
Overlaid, they looked just like the flow of water, coming up, spiralling down.
The logo was born in this moment, in this serendipitous meeting, in this unlikely chat with a total stranger. We met for the first time that day, and I'm not sure if we ever met again. This interaction was, is, precious, and it led to a particular creation that is now a core part of my life and is a highlight for many people around the UK and the world, as we put on events and released musicians' music.
This is inspiration. This is expression. This is flow, through the fluid nature of the cosmos.
This is what you miss out on when you talk into your AI LLM black hole prompt.
This is what you steal from when you demand your AI LLM to generate you something according to your whim.
Art and expression is the very foundation of human community. Join in! Try new things! Learn from each other! Bring us all closer together by interacting and creating through shared ideas, shared visions, shared wisdom!
After that, I drew it up cleanly, geometrically.
I photographed it like scanning it, carefully aligning the camera because I didn't have a scanner.
I redrew it more than twice.
I digitised it, colourised it, split it into two layers so I could apply colour & lighting effects to it.
I painstakingly traced the photograph into a vector format, to enlarge it and use it for various media.
I even more painstakingly (do we have a more extreme adverb??) divided all the vector shapes into new objects so that the layers became "real". And cleaned up the vector nodes, shaping them to my imagination.
The vector form is used all over our record label & events branding.
And then I imported the vector form into Blender, a 3D rendering application, free and open source.
I learnt Blender, day by day developing my understanding and my skills. Day by day my GPU crashing on raytracing and cutting the laptop's power out!
And finally, I learnt to make some simple renders that look like being underwater, like surreal glassy objects floating in the deep. I even learnt to animate it, although I haven't released that into the wild.
I imagined all of this stuff, and then I spent months over years developing my skills in my spare time in order to bring these imaginations to life.
You can do the same.
You have to sacrifice things.
Sacrifice your time.
Sacrifice your energy.
Sacrifice your distractions and enter yourself into the learning process and the creative process.
To you, amazing lady who helped me draw this symbol from the fabric of the Realm of Forms, thank you! I'm sorry that I don't recall your name, although actually I think I do remember but I would be embarrassed if I tagged the wrong person. Please reach out if you recognise this story! It was about 7, maybe 8 years ago, in the painted pub in St. Werburgh's.
-
 @ 4ba8e86d:89d32de4
2025-04-22 13:26:12
@ 4ba8e86d:89d32de4
2025-04-22 13:26:12Cashu é Ecash para Bitcoin
Cashu é um sistema ecash Chaumian gratuito e de código aberto criado para Bitcoin. Cashu oferece privacidade quase perfeita para usuários de aplicativos Bitcoin de custódia. Ninguém precisa saber quem você é, quanto dinheiro você tem e com quem você faz transações.
O que é Cashu?
Cashu é um novo protocolo ecash para aplicativos de custódia Bitcoin que está totalmente integrado à rede Lightning. Um sistema Ecash consiste em duas partes, a carteira mint e a carteira ecash. Transações Ecash não rastreáveis, instantâneas e sem taxas. Cashu é construído para Bitcoin. As carteiras usam o nó Lightning da casa da moeda para fazer ou receber pagamentos em Bitcoin em troca de ecash. Uma casa da moeda Cashu não sabe quem você é, qual é o seu saldo ou com quem você está negociando.Os usuários de uma casa da moeda podem trocar ecash de forma privada, sem que ninguém saiba quem são as partes envolvidas. Os pagamentos em Bitcoin são executados sem que ninguém possa censurar usuários específicos.
A postagem de David Wagner em 1996 na lista de discussão Cypherpunk é a base da criptografia Cashu. Wagner descreve um sistema ecash usando troca de chave cega Diffie-Hellman em vez de RSA, na qual a implementação original de David Chaum foi baseada.
https://cypherpunks.venona.com/date/1996/03/msg01848.html
https://en.m.wikipedia.org/wiki/Ecash
Como isso começou.
https://void.cat/d/2HJKtTEfuDxmDfh3uH9ZoS.webp https://void.cat/d/XyyHFSQYa5vEswzzt6MMq7.webp
Como vão as coisas.
https://void.cat/d/WUrKzsFDnsvUQdFKZChLeS.webp
Como funciona A Carteira Cashu é através de um esquema criptográfico chamado assinaturas cegas, descrito pela primeira vez pelo cypherpunk e criptógrafo David Chaum. Pense assim:você produz uma mensagem secreta e a envolve em um envelope feito de papel carbono que você envia para a casa da moeda. https://void.cat/d/SbEEHCiGFUHWvk4qGv9xCb.webp
A casa da moeda não pode ver o que está dentro do envelope. Ele assina do lado de fora dizendo "qualquer que seja esse segredo, vale 420 Satoshis”e o envia de volta para você. Como o envelope é realmente criptografado, somente você pode abri-lo e ver sua mensagem secreta (agora assinada por carbono). https://void.cat/d/Pakyb6ztW9B7L5ubAQ74eL.webp
Este segredo assinado é na verdade o seu token Ecash e vale Satoshis.
Você pode enviar e receber esses tokens para qualquer outra pessoa como quiser, seja com um mensageiro, via e-mail ou um pombo. A casa da moeda não sabe nada disso.
A anatomia de um token Cashu. https://void.cat/d/JzvxreMoCitmYe2FthAsei.webp
Um breve passo a passo de uma carteira cashu deixará tudo isso bem claro.
Comece abrindo
https://nutstash.app/
Pressione " WALLET " https://void.cat/d/VeCANsaxkkq9YtoPRS26ZK.webp https://void.cat/d/CTmK9GcPGn3i2gHCVXcL5r.webp https://void.cat/d/UWjyjGLS6MzyZvt6zkuUgG.webp https://void.cat/d/HzNtKanCSAJatrMa9yTKwF.webp
Pressione "+ ADD ".
Agora a carteira cashu está aberta… https://void.cat/d/GAYSrNxHEEhctoW37bFPjJ.webp
O próximo passo é deposite alguns sats com a Casa da moeda.
Pra depositar Pressione o botão "MINT". https://void.cat/d/LC5WEDKAzzZoHXxrKZDiWu.webp
Digite a quantidade de sats a ser depositado na carteira cashu depois Pressione " REQUEST MINT ". https://void.cat/d/Pr6foBWBBCq73i8WggbLGG.webp
Você Pode copiar a fatura ou ler o qrcode , no meu caso usei a carteira LNbits pra pagar a fatura de 10 sats , você tem 10 minutos pra pagar fatura. https://void.cat/d/BQerpEtW2H9ANaoW8truJE.webp https://void.cat/d/8PGFBRW64zavDnQJfYQh9C.webp
Agora pra enviar Ecash.
Pressione “SEND” https://void.cat/d/8rkF2dvhJeZWf8GeQhhf2d.webp
Digite 10 , Pressione “SEND” https://void.cat/d/5SK5w6ewgt8wikCuyk7znM.webp
Então o token Ecash usando a assinatura cega da casa da moeda foi criado. https://void.cat/d/PedBMcZPfczZLLymGmfzVq.webp
O Token Ecash foi criado é esse logo abaixo.
eyJwcm9vZnMiOlt7ImlkIjoiME5JM1RVQXMxU2Z5IiwiYW1vdW50IjoyLCJzZWNyZXQiOiJrWjNBOVorSXkyREJOcDdhdFhYRTIvclVXOFRnR2ZoTDgzWEFXZ0dKUXhVPSIsIkMiOiIwMmM0NjA4NDYwNDhjNzI1ZjgwMDc3M2IyNmRmOTcxNDU1MTJmOTI0YjgyNzYyZTllYzdkZjZjOTkzNGVmYjJhNmMifSx7ImlkIjoiME5JM1RVQXMxU2Z5IiwiYW1vdW50Ijo4LCJzZWNyZXQiOiJXdTZmdWlxNGt4Tkh3UkF1UzFhMmVYaGZtRnRHU2tRQkNYZFNnUzcreHkwPSIsIkMiOiIwMzFhYWI3MzY3MTJhY2Y5MWU4NzE4YmM5OTlmNWE2MGEwYzNjODQ5YTA1MWE2OTA5MzRkMTc4NWNmZGNkNDcyYTAifV0sIm1pbnRzIjpbeyJ1cmwiOiJodHRwczovL2xlZ2VuZC5sbmJpdHMuY29tL2Nhc2h1L2FwaS92MS80Z3I5WGNtejNYRWtVTndpQmlRR29DIiwiaWRzIjpbIjBOSTNUVUFzMVNmeSJdfV19
Se pressionar o botão " send as link "
Então criar link do token Ecash.
https://wallet.nutstash.app/#eyJwcm9vZnMiOlt7ImlkIjoiME5JM1RVQXMxU2Z5IiwiYW1vdW50IjoyLCJzZWNyZXQiOiJrWjNBOVorSXkyREJOcDdhdFhYRTIvclVXOFRnR2ZoTDgzWEFXZ0dKUXhVPSIsIkMiOiIwMmM0NjA4NDYwNDhjNzI1ZjgwMDc3M2IyNmRmOTcxNDU1MTJmOTI0YjgyNzYyZTllYzdkZjZjOTkzNGVmYjJhNmMifSx7ImlkIjoiME5JM1RVQXMxU2Z5IiwiYW1vdW50Ijo4LCJzZWNyZXQiOiJXdTZmdWlxNGt4Tkh3UkF1UzFhMmVYaGZtRnRHU2tRQkNYZFNnUzcreHkwPSIsIkMiOiIwMzFhYWI3MzY3MTJhY2Y5MWU4NzE4YmM5OTlmNWE2MGEwYzNjODQ5YTA1MWE2OTA5MzRkMTc4NWNmZGNkNDcyYTAifV0sIm1pbnRzIjpbeyJ1cmwiOiJodHRwczovL2xlZ2VuZC5sbmJpdHMuY29tL2Nhc2h1L2FwaS92MS80Z3I5WGNtejNYRWtVTndpQmlRR29DIiwiaWRzIjpbIjBOSTNUVUFzMVNmeSJdfV19 https://void.cat/d/U1UnyxsYgj516YbmkgQNkQ.webp Este token Ecash pode ser compartilhado como você quiser. Você pode enviá-lo por e-mail para alguém, enviá-lo em uma mensagem privada, um SMS ou convertê-lo em um código QR e imprimi-lo. Quem tiver este token pode resgatá-lo com o 10 sats.
Você verá que seu saldo caiu para 20 sats: https://void.cat/d/95AVkevmknKNzqRcnJZwQX.webp
Para resgatar um token Ecash sem o link, pressione o botão “Receive ” https://void.cat/d/UjrbAPn8mj5qGZYVQ1Ba2B.webp
cole-o token Ecash no campo
" token: "pressione "RECEIVE" https://void.cat/d/GZLcBgvHfaB3c5N66ygZyV.webp
Com o Link do token Ecash só pressionar no link vai abrir a tela já preencher automáticamente só pressionar " RECEIVE " https://void.cat/d/ARNkKCtchhFt4NCTkfRJRG.webp
Pra Ativa o Nostr na carteira vai na aba settings , pressione o botão ativa o Nostr. https://void.cat/d/MjoDA1dgueWUFABcQFDVRe.webp
Por padrão ficar ativo pra usar o " Use external Key (nos2x , outros) " Mas Nesse caso não vou usar vou desativar e vou ativa " Edit Nostr Keys " https://void.cat/d/BAA6eFkmK5f7BHzLwYLSGF.webp
Ao pressionar esse botão https://void.cat/d/VTNGVsLvwqfy3dWu4hhMSK.webp é gerar um novo par de chaves privadas e pública , assim podemos usar uma nova chave a cada pagamentos. Aumentando a privacidade no pagamentos.
A pois Ativa o Nostr na carteira , você pode enviar Sats / Ecash via Nostr.
Pressione " Send " https://void.cat/d/R2Svye4XPd2VdHfPxT1DzF.webp
Pressione " Send " https://void.cat/d/AwLeBBr2db2wrTHHUHwEPs.webp
Agora pode adicionar npud / hex / nip-05 pra enviar token. https://void.cat/d/VZR6BUXjG7pm3FDogrDvo4.webp
Pressione " SEND OVER NOSTR " pra enviar o token Ecash. https://void.cat/d/MWveqpmii5dqpioa5a3wVt.webp
Pra quem não tem a carteira nutstash , pode entra no seu cliente Nostr no meu caso e snort nostr , Demora algums minutos pra chegar mensagem com o token Ecash.. https://void.cat/d/MVg3fPD7PAzZUskGCCCcps.webp https://void.cat/d/YNtKuCbQYo1wef7pJcjhKy.webp
Ja se a outra pessoa usar carteira nutstash com a chave pública que você mandou chegar mais rápido. Essa bolinha azul no campo " Indox " Indica que você recebeu o pagamento já está pronto pra ser regastado. https://void.cat/d/So6FAp4wiTUeKBBmRBU2Rv.webp
Pressione "Indox " depois pressione a seta. https://void.cat/d/TqYNYDoyy9fUFas9NFxReJ.webp
Pressione " TRUS MINT " pra recebe os Token Ecash. https://void.cat/d/LP6zUTZ3HDPxd6fLvPPNXB.webp
O aplicativo de resgate Cashu, que permite resgatar tokens Ecash via Lightning.
https://redeem.cashu.me/ https://void.cat/d/Mw9kzDHr4A469EjFNoTHyB.webp
Cola o Token no campo " paste in your Cashu Ecash token.. " https://void.cat/d/SkA3MGJaGGxCjNnzeBhPHP.webp
Pressione " REDEEM " pra converter Ecash em Lightning. https://void.cat/d/693C1yfwYz3P3BQB6f7xXN.webp
Você pode editar e manda já pronto pra pessoa só basta a pessoa ou você aberta em " REDEEM " pra converter Ecash em Lightning.
https://redeem.cashu.me/?token=token ecash=&to=Lightning address
Exemplo:
https://redeem.cashu.me/?token=eyJwcm9vZnMiOlt7ImlkIjoiUEVuMVdLalFoN2pGIiwiYW1vdW50IjoyLCJDIjoiMDJhYWE5OWJiMmUwODQyYjJmNzdmNDRlZWEyZjEzMmNkOTNhZjJlNWU0MzI3ZjhjMTE5ODcxZWNiMTNhMTUxYjY0Iiwic2VjcmV0IjoicE5jb3hFRHJRT1ovTXU4d3d2SlpvMnRIaXBSM3pPYkRrSWJUUlB6VXh5bz0ifSx7ImlkIjoiUEVuMVdLalFoN2pGIiwiYW1vdW50IjoxNiwiQyI6IjAzNDM4ZDc1NmZmMjdmYjgyZmQxNWNhNzg3NzgwNTAyZWU4NzdmMzQ5MmYyMWQzMTMwMzc1NTdlNWNmMDJlOWQ0MCIsInNlY3JldCI6Im9DTXQwUTRVT0MvZWhmd2FVOWt5aGFJZUdHdXhiYUNzQTZ2STh2a0w2N1U9In0seyJpZCI6IlBFbjFXS2pRaDdqRiIsImFtb3VudCI6MzIsIkMiOiIwMmIyMmQ4MDEwZWU5MDA2MWYyNWQzODAyY2UyMDE3ZjAwMmVjMDVmMjM5NjIwNGNkYjllMmU2ODllYWY3YTZkYjIiLCJzZWNyZXQiOiI5ejVVMEdzWHZiUS84Rjd4ZFdYUXRxUDlvWGFyVnBRTzRFdUtzb2JSck1vPSJ9XSwibWludHMiOlt7InVybCI6Imh0dHBzOi8vbGVnZW5kLmxuYml0cy5jb20vY2FzaHUvYXBpL3YxL29DcXNTR3I1enphTTZxM1hWZU5ZNXQiLCJpZHMiOlsiUEVMVdLalFoN2pGIl19XX0=&to=alexemidio@ln.tips
Obs: o teclado do celular pode adicionar "=" a mais ou corrigir " &to " com "&tô" assim escrevendo errado, tanto erro no link.
" SWAP " transferência de uma carteira para outra. Pressione " INTER-MINT SWAP" https://void.cat/d/PsCdoLAmYpYCChkgqTAE7p.webp
A carteira que você selecionar em cima é a carteira de saídas e a carteira de baixo e a carteira de entrada. https://void.cat/d/VKY6ts6qttJmCaefrduv4K.webp
Agora digita o valor que quer fazer o SWAP. Após Pressione " CONFIRM AMOUNT" https://void.cat/d/WuuQqeC1mSQUufb75eeMbw.webp
Depois Tem que pressionar " SWAP " não esqueça. https://void.cat/d/Eb2ajSaZfzZkBEWBv8tuk.webp
Pronto antes a primeira Carteira tinha 10 Ecash, e segunda carteira tinha 8 Ecash.
Somando 18 Ecash.
Apois o SWAP Agora as duas tem 9.
Somando 18. https://void.cat/d/8yRtSoFyih2D2KEm66h6in.webp
Fazer o backup da sua carteira cashu ecash. Pressione " BACKUP TOKENS " https://void.cat/d/26vtnDiVP4YpDiQmunatko.webp
Você pode editar o nome do backup E pode alterar o local aonde vai salva o arquivo 📂 do backup. Depois só pressionar " Baixar " https://void.cat/d/PQH94o81U23txdmyx3cHEn.webp
Agora pra recuperar a carteira cashu ecash. Pressione " RESTORE " https://void.cat/d/2vkLS1qUCbJ1XXjSLBou25.webp
Pressione " CONTINUAR " https://void.cat/d/PCbT2UPSLtwcZohwbhD85A.webp
Click no espaço em branco vai abrir pra encontrar o arquivo 📂 Do backup.. https://void.cat/d/P1VC7b46oNe62v4puVZ79b.webp
Selecionar o arquivo 📂 de backup. https://void.cat/d/D6FAGxYRquz2WWwNznSAzT.webp
Pressione " CONTINUE" https://void.cat/d/HicRn5e2feSRicgjy6kuC5.webp
Pressione " CONTINUE" https://void.cat/d/VP6uh8bXHz42PBGrPwGq5e.webp
Backup feito com sucesso. Só aberta " Ok " https://void.cat/d/QsZV1umL9DhoPtEXBMfPtY.webp
O eCash pode ser útil em diversas situações, oferecendo várias vantagens. Uma das principais vantagens do uso de tokens eCash é a privacidade que oferece. Como as transações usando eCash são quase impossíveis de rastrear, isso pode ser útil para quem deseja manter sua atividade financeira privada. O eCash pode ser especialmente útil para Pagamento de serviços em áreas rurais , pode ser difícil acessar serviços financeiros tradicionais, como bancos ou caixas eletrônicos. O uso de tokens eCash pode permitir que as pessoas paguem por serviços como transporte , serviços de saúde ou eletricidade sem a necessidade de viajar para áreas urbanas. No entanto, é importante lembrar que o uso do eCash ainda apresenta riscos e desafios. Como o eCash cashubtc ainda é bem novo , pode haver falhas de segurança ou outras vulnerabilidades que ainda não foram identificadas use com cautela poucos Sats.
Obrigado por ler, e espero que você dedique alguns minutos para experimentar o eCash e ver do que se trata melhor.
Alguma artigos e vídeos a baixo.
https://cashu.space/
https://docs.cashu.space/
https://github.com/cashubtc/
https://youtu.be/UNjVc-WYdgE
https://youtu.be/_XmQSpAhFN4
https://youtu.be/zdtRT7phXBo
https://maxmoney.substack.com/p/ecash-for-better-bitcoin-privacy?utm_source=substack&utm_campaign=post_embed&utm_medium=web
https://cypherpunks.venona.com/date/1996/03/msg01848.html
Encontre-me ou envie um zap para nostr alexemidio@ln.tips alexemidio@alexemidio.github.io
Twitter: alexemidio7
-
 @ 502ab02a:a2860397
2025-04-24 02:00:28
@ 502ab02a:a2860397
2025-04-24 02:00:28ถ้า “นมปลอมเข้าโรงเรียน” กับเกม Lobby ระดับโลก ที่ซ่อน GMO ไว้ในแก้วของลูกหลานเรา
โอเค เรารู้จักคำว่า Precision Fermentation หรือ PF กันไปแล้ว กลับมาดูโลกปัจจุบันนี้กันครับ
ในวันที่ผู้ใหญ่ยังทะเลาะกันเรื่องราคาน้ำนมดิบ มีบางบริษัทที่กำลังยิ้มกว้าง เพราะแผนระยะยาวของเขา…คือการเปลี่ยนนมโรงเรียนจากของจริง ไปสู่นมปลอมที่ “จดสิทธิบัตรได้” และ “ควบคุมทั้ง supply chain”
เรื่องนี้อาจดูเหมือนนิยายไซไฟนะครับ แต่เฮียจะพาไปเจาะลึกเบื้องหลังการ lobby ที่พยายามผลัก “นมจาก Precision Fermentation” และ “นม Plant-Based” เข้าสู่ระบบโรงเรียน โดยอ้างว่า “เพื่อสุขภาพ เพื่อโลก และเพื่อเด็กๆ” แต่จริงๆ แล้วมันคือ เกมเปลี่ยนอาหารเป็นทรัพย์สินทางปัญญาแบบเงียบๆ
ทำไม “โรงเรียน” ถึงเป็นเป้าหมายสำคัญ? คำตอบง่ายมาก เพราะว่ามันกลับเข้าสู่ loop เดิมกับตอนที่เขาพยายามยัด นมสด เข้าไปในชีวิตเมื่อหลังสงครามโลกครั้งที่ 2 นั่นละครับ หนังม้วนเดิม มีเพิ่มเติมคือความทันสมัย 1.โรงเรียนคือฐานข้อมูลประชากรที่แน่นอน = จำนวนเด็กแน่ชัด งบประมาณแน่ชัด 2.พฤติกรรมการกินของเด็ก “ฝังได้ง่าย” = ถ้าเด็กเติบโตมากับนม Plant-Based หรือ Milk 2.0 ตั้งแต่เล็ก พอเขาโตขึ้น “ร่างกายจะลืมรสนมวัวไปเลย” และไม่เคยรู้ว่าเคยมี real food ให้เลือก เหมือนที่โลกของ เจเนอเรชั่น internet มือถือ หรือแม้แต่สมัยนี้คือ สตรีมมิ่ง 3.เป็นจุดที่รัฐมีบทบาทโดยตรง = ง่ายต่อการ lobby policy เพราะแค่เปลี่ยนนโยบายระดับกระทรวง ก็เปลี่ยนทั้งประเทศได้
ใครอยู่เบื้องหลังการล็อบบี้นี้? 1. องค์กรระดับโลกที่ขับเคลื่อน Plant-Based School Meals อย่างเช่น - GFI (Good Food Institute) เป็นองค์กรที่มีเป้าหมายชัดว่า “เปลี่ยนโปรตีนของโลกจาก animal-based ให้เป็น cell-based และ fermentation-based” สนับสนุนงานวิจัย ออกนโยบายผลักดันเมนูโรงเรียน - ProVeg International ซึ่งมีโครงการชื่อ “School Plates” ปรับเมนูโรงเรียนให้เป็น plant-based - EAT Forum & WEF (World Economic Forum) ที่มีการสนับสนุนนโยบาย global dietary shift ซึ่งแนะนำให้ลดการบริโภคเนื้อสัตว์และผลิตภัณฑ์จากสัตว์ เพื่อส่งเสริมสุขภาพและความยั่งยืนของสิ่งแวดล้อม
- บริษัทยักษ์ใหญ่ด้าน Milk 2.0
- Perfect Day ร่วมกับ Nestlé ที่พยายามผลักดันนม PF ให้เป็นนมทดแทนแห่งอนาคต
-
Oatly ผู้ผลิตนม plant-based และ lobby ให้ “รัฐบาลช่วยจัดซื้อในโรงเรียน” พร้อมกับแคมเปญประชาสัมพันธ์ว่านี่คือตัวเลือกที่ “รักษ์โลกและดีต่อสุขภาพ” และ NotCo / Danone ซึ่งอยู่ในตลาดประเภทเดียวกัน ก็อาจมีแนวโน้มเข้าสู่ตลาดโรงเรียนเช่นกัน
-
เช่นเดียวกับที่เคยเล่าเรื่องนมสดไว้ครับ เขาจะต้องมาพร้อมการวิจัยที่ออกแบบให้รองรับการเปลี่ยนนโยบาย ด้วยหลายงานวิจัยที่บอกว่า “นมวัวมีผลเสียต่อสุขภาพเด็ก” ถูกสนับสนุนโดยกลุ่มทุนที่อยู่ในวงการ plant-based หรือ biotech งานบางชิ้นลดความสำคัญของสารอาหารจาก animal-based ลง และ “ปั่นคะแนน” ของ Plant Milk หรือ PF Milk ให้ดูสูงกว่าความเป็นจริง
วิธีการ Lobby แบบแนบเนียนก็จะใช้กระบวนการประมาณนี้ครับ 1. แทรกผ่านโครงการ “นมโรงเรียนฟรี” หลายประเทศใช้เงินรัฐอุดหนุนนมโรงเรียน กลุ่ม Lobby เข้าไป “เสนอของถูกกว่า” และอ้างว่า “เหมาะกับเด็กแพ้นมวัว” ทำให้รัฐเริ่มพิจารณา Plant Milk หรือ PF Milk เป็นทางเลือก “ถูกกว่าและดูดี”
-
ล้างความคิดผ่านหลักสูตรสุขศึกษา เริ่มมีสื่อการสอนที่ใช้คำว่า “milk” แบบรวม Plant Milk เข้าไปด้วย ลดความต่างระหว่างนมวัวกับนมจากพืช และเริ่มพูดว่า “นมจากพืชดีกว่าต่อสิ่งแวดล้อม”
-
แจกทุนให้โรงเรียนที่ร่วมโครงการ มีการเสนอทุนวิจัย ทุนสนับสนุนเมนูโรงเรียน ถ้าโรงเรียนยอมทดลองใช้นม Plant-Based หรือ PF Milk สร้างภาพลักษณ์ว่าเป็นโรงเรียน “รักโลก รักสุขภาพ”
-
ใช้พลังอินฟูฯและดารา ดาราดังๆ ถูกใช้เป็นหน้าโครงการ (ในตปท.) เช่นโพสต์ภาพเด็กๆ กิน “นมไม่มีวัว” พร้อมคำบรรยายว่า “นี่คืออนาคตของการกินอย่างมีจริยธรรม” อะไรประมาณนี้ครับ
ผลกระทบที่จะเกิดขึ้นก็คือ เด็กๆ เสียโอกาสในการได้รับโภชนาการจาก real food โดยเฉพาะ B12, วิตามิน A, DHA, โคลีน, เคซีนจากธรรมชาติ ซึ่งนมเทียมต้อง “แต่งเติม” เข้ามาทั้งสิ้น รวมถึง เด็กโตมากับอาหารปลอม โดยไม่รู้ว่าเคยมีของจริงให้เลือก สุดท้ายจะกลายเป็น “ผู้ใหญ่ที่ต้องพึ่งบริษัท” เพื่อมีโปรตีนกินในชีวิตประจำวัน และท้ายสุด รัฐกลายเป็นผู้สนับสนุนสิทธิบัตรเอกชน เพราะเมื่อ Milk 2.0 เข้าสู่ระบบโรงเรียน มันจะกลายเป็น “ค่าใช้จ่ายประจำ” ที่รัฐบาลต้องจ่ายให้บริษัทตลอดไป ซึ่งตรงนี้ก็จะวนกลับมาที่พวกเราที่อยู่ภายใต้ระบบ fiat
ดังนั้นมันก็เลยสรุปได้ว่า นี่ไม่ใช่แค่เรื่องอาหาร แต่คือการเปลี่ยนโครงสร้างอำนาจ Milk 2.0 เข้าโรงเรียน ไม่ใช่เพราะมันดีกว่า แต่เพราะมัน “ล็อกห่วงโซ่คุณค่าไว้ในมือคนส่วนน้อย” และสร้างประชากรรุ่นใหม่ที่ไม่รู้จักอาหารจริงจากธรรมชาติ
หากเด็กวันนี้กินของปลอมจนชิน วันหนึ่งเขาอาจยอม “จ่ายเงินเช่าโปรตีน (subscribe) ” ไปตลอดชีวิต โดยไม่เคยรู้เลยว่า… วัวเคยให้นมได้โดยไม่ต้องใช้เทคโนโลยีใดๆ เลย
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 3c7dc2c5:805642a8
2025-04-23 21:50:33
@ 3c7dc2c5:805642a8
2025-04-23 21:50:33🧠Quote(s) of the week:
'The "Bitcoin Corporate Treasury" narrative is a foot gun if it's not accompanied by the sovereignty via self-custody narrative. Number Go Up folks are pitching companies to funnel their funds into a handful of trusted third parties. Systemic Risk Go Up.' - Jameson Lopp
Lopp is spot on!
The Bitcoin network is a fortress of digital power backed by 175 terawatt-hours (TWh)—equivalent to 20 full-scale nuclear reactors running continuously 24 hours per day, 365 days per year—making it nation-state-level resistant and growing stronger every day. - James Lavish
🧡Bitcoin news🧡
https://i.ibb.co/xSYWkJPC/Goqd-ERAXw-AEUTAo.jpg
Konsensus Network
On the 14th of April:
➡️ Bitcoin ETFs are bleeding out. Not a single inflow streak since March.
➡️'There are now just a bit less than 3 years left until the next halving. The block reward will drop from 3.125 BTC to 1.5625 BTC. Plan accordingly.' - Samson Mow
➡️Bitcoin is the new benchmark. Bitcoin has outperformed the S&P 500 over the past 1-, 2-, 3-, 4-, 5-, 6-, 7-, 8-, 9-, 10-, 11-, 12-, 13-, and 14-year periods. https://i.ibb.co/GfBK6n2Z/Gof6-Vwp-Ws-AA-g1-V-1.jpg
You cannot consider yourself a serious investor if you see this data and ignore it. Never been an asset like it in the history of mankind. But that is from an investor's perspective...
Alex Gladstein: "While only certain credentialed individuals can own US stocks (a tiny % of the world population) — anyone in the world, dissident or refugee, can own the true best-performing financial asset. "
➡️New record Bitcoin network hashrate 890,000,000,000,000,000,000x per second.
➡️The Korea Exchange has experienced its first bitcoin discount in South Korea since December 2024.
➡️Every government should be mining Bitcoin, say Bhutan's Prime Minister - Al Jazeera "It's a simple choice that's earned billions of dollars. Mining makes tremendous sense."
On the 15th of April:
➡️'Owning 1 Bitcoin isn’t a trade... - It’s a power move. - A geopolitical hedge. - A once-per-civilization bet on the next monetary regime. If you have the means to own one and don’t… You’re not managing risk. You’re misreading history.' -Alec Bakhouche
Great thread: https://x.com/Alec_Bitcoin/status/1912216075703607448
➡️The only thing that drops faster than new ETH narratives is the ETH price. Ethereum is down 74% against Bitcoin since switching from PoW to PoS in 2022.
https://i.ibb.co/bR3yjqZX/Gos0kc-HXs-AAP-9-X.jpg
Piere Rochard: "The theory was that on-chain utility would create a positive fly-wheel effect of demand for holding ETH. The reality is that even if (big if) you need its chain utility, you don’t actually need to hold ETH, you can use stablecoins or wBTC. There’s no real value accrual thesis."
If you're still holding ETH, you're in denial. You watched it slide from 0.05 to 0.035. Now it's circling 0.02 and you're still hoping? That's not a strategy—that's desperation. There is no bounce. No cavalry. Just a crowd of bagholders waiting to offload on the next fool. Don’t be that fool. Everyone’s waiting to dump, just like you.
For example. Galaxy Digital deposited another 12,500 $ETH($20.28M) to Binance 10 hours ago. Galaxy Digital has deposited 37,500 $ETH($60.4M) to Binance in the past 4 days. The institutional guys that were pushing this fraud coin like the Winklevoss brothers and Novogratz (remember the Luna fiasco?!) are ejecting. If you're still holding, no one to blame but yourself.
Take the loss. Rotate to BTC.
Later, you can lie and say you always believed in Bitcoin. But right now, stop the bleeding.
You missed it. Accept that. Figure out why.
P.S. Don’t do anything stupid. It’s just money. You’ll recover. Move smarter next time.
➡️And it is not only against ETH, every other asset is bleeding against BTC because every other asset is inferior to BTC. Did you know Bitcoin's 200-week moving average never declines? It always rises. What does this suggest? 'This is the most significant chart in financial markets. It's Bitcoin - measured with a 200-week moving average (aka 4 years at a time). Zoom out, and the truth becomes crystal clear: Bitcoin has never lost purchasing power. What does this hint at? Bitcoin is the most reliable savings technology on Earth.' - Cole Walmsley
Proof: https://x.com/Cole_Walmsley/status/1912545128826142963
➡️SPAR Switzerland Pilots Bitcoin and Lightning Network Payments Zurich, Switzerland – SPAR, one of the world’s largest grocery retail chains, has launched a pilot program to accept Bitcoin and Lightning Network payments at select locations in Switzerland.
With a global presence spanning 13,900 stores across 48 countries, this move signals a significant step toward mainstream adoption of Bitcoin in everyday commerce.
➡️$110 billion VanEck proposes BitBonds for the US to buy more Bitcoin and refinance its $14 trillion debt.
➡️'A peer-reviewed study forecasts $1M Bitcoin by early 2027—and up to $5M by 2031.' -Simply Bitcoin
On the 17th of April:
➡️ Every one of these dots is flaring gas into the atmosphere and could be mining Bitcoin instead of wasting the gas and polluting the air.
https://i.ibb.co/d4WBjXTX/Gos-OHm-Nb-IAAO8-VT.jpg
Thomas Jeegers: 'Each of these flare sites is a perfect candidate for Bitcoin mining, where wasted methane can be captured, converted into electricity, and monetized on the spot. No need for new pipelines. No need for subsidies. Just turning trash into treasure. Yes, other technologies can help reduce methane emissions. But only Bitcoin mining can do it profitably, consistently, at scale, and globally. And that’s exactly why it's already happening in Texas, Alberta, Oman, Argentina, and beyond. Methane is 84x more harmful than CO₂ over 20 years. Bitcoin is not just a monetary revolution, it's an environmental one.'
➡️Bitcoin market cap dominance hits a new 4-year high.
➡️BlackRock bought $30 million #Bitcoin for its spot Bitcoin ETF.
➡️Multiple countries and sovereign wealth funds are looking to establish Strategic Bitcoin Reserves - Financial Times
Remember, Gold's market cap is up $5.5 TRILLION in 2025. That's more than 3x of the total Bitcoin market cap. Nation-state adoption of Bitcoin is poised to be a pivotal development in monetary history...eventually.
➡️'In 2015, 1 BTC bought 57 steaks. Today, 7,568. Meanwhile, $100 bought 13 steaks in 2015. Now, just 9. Stack ₿, eat more steak.' Priced in Bitcoin
https://i.ibb.co/Pz5BtZYP/Gouxzda-Xo-AASSc-M.jpg
➡️'The Math:
At $91,150 Bitcoin flips Saudi Aramco
At $109,650 Bitcoin flips Amazon
At $107,280 Bitcoin flips Google
At $156,700 Bitcoin flips Microsoft
At $170,900 Bitcoin flips Apple
At $179,680 Bitcoin flips NVIDIA
Over time #Bitcoin flips everything.' -CarlBMenger
➡️Will $1 get you more or less than 1,000 sats by the fifth Halving? Act accordingly. - The rational root Great visual: https://i.ibb.co/tPxnXnL4/Gov1s-IRWEAAEXn3.jpg
➡️Bhutan’s Bitcoin Holdings Now Worth 30% of National GDP: A Bold Move in the Bitcoin Game Theory
In a stunning display of strategic foresight, Bhutan’s Bitcoin holdings are now valued at approximately 30% of the nation’s GDP. This positions the small Himalayan kingdom as a key player in the ongoing Bitcoin game theory that is unfolding across the world. This move also places Bhutan ahead of many larger nations, drawing attention to the idea that early Bitcoin adoption is not just about financial innovation, but also about securing future economic sovereignty and proof that Bitcoin has the power to lift nations out of poverty.
Bhutan explores using its hydropower for green Bitcoin mining, aiming to boost the economy while maintaining environmental standards. Druk Holding's CEO Ujjwal Deep Dahal says hydropower-based mining effectively "offsets" fossil fuel-powered bitcoin production, per Reuters.
➡️Barry Silbert, CEO of Digital Currency Group, admits buying Coinbase was great, but just holding Bitcoin would’ve been better. Silbert told Raoul Pal he bought BTC at $7–$8 and, "Had I just held the Bitcoin, I actually would have done better than making those investments."
He also called 99.9% of tokens “worthless,” stressing most have no reason to exist.
No shit Barry!
➡️Bitcoin hashrate hits a new ATH.
https://i.ibb.co/1pDj9Ch/Gor2-Dd2ac-AAk-KC5.jpg
Bitcoin hashrate hit 1ZH/s. That’s 1,000,000,000,000,000,000,000 hashes every second. Good luck stopping that! Bitcoin mining is the most competitive and decentralized industry in the world.
➡️¥10 Billion Japanese Fashion Retailer ANAP Adds Bitcoin to Corporate Treasury Tokyo, Japan – ANAP Inc., a publicly listed Japanese fashion retailer with a market capitalization of approximately ¥10 billion, has officially announced the purchase of Bitcoin as part of its corporate treasury strategy.
“The global trend of Bitcoin becoming a reserve asset is irreversible,” ANAP stated in its announcement.
➡️El Salvador just bought more Bitcoin for their Strategic Bitcoin Reserve.
➡️Only 9.6% of Bitcoin addresses are at a loss, a rare signal showing one of the healthiest market structures ever. Despite not being at all-time highs, nearly 90% of holders are in profit, hinting at strong accumulation and potential for further upside.
On the 18th of April:
➡️Swedish company Bitcoin Treasury AB announces IPO plans, aiming to become the 'European version of MicroStrategy'. The company clearly states: "Our goal is to fully acquire Bitcoin (BTC)."
➡️Relai app (unfortunately only available with full KYC) with some great Bitcoin marketing. https://i.ibb.co/G4szrqXj/Goz-Kh-Hh-WEAEo-VQr.jpg
➡️Arizona's Bitcoin Reserve Bill (SB 1373) has passed the House Committee and is advancing to the final floor vote.
➡️Simply Bitcoin: It will take 40 years to mine the last Bitcoin. If you're a whole corner, your grandchildren will inherit the equivalent of four decades of global energy. You're not bullish enough. https://i.ibb.co/Hpz2trvr/Go1-Uiu7a-MAI2g-VS.jpg
➡️Meanwhile in Slovenia: Slovenia's Finance Ministry proposes to introduce a 25% capital gains tax on bitcoin profits.
➡️ In one of my previous Weekly Recaps I already shared some news on Breez. Now imagine a world where everyone can implement lightning apps on browsers...with the latest 'Nodeless' release Breez is another step towards bringing Bitcoin payments to every app. Stellar work!
Breez: 'Breez SDK Now Supports WASM We’re excited to announce that Nodeless supports WebAssembly (WASM), so apps can now add Bitcoin payments directly into browsers and node.js environments. Pay anyone, anywhere, on any device with the Breez SDK.
Our new Nodeless release has even more big updates → Minimum payment amounts have been significantly reduced — send from 21 sats, receive from 100. Now live in Misty Breez (iOS + Android). → Users can now pay fees with non-BTC assets like USDT. Check the release notes for all the details on the 0.8 update.'
https://github.com/breez/breez-sdk-liquid/releases/tag/0.8.0
https://bitcoinmagazine.com/takes/embed-bitcoin-into-everything-everywhere Shinobi: Bitcoin needs to be everywhere, seamlessly, embedded into everything.
➡️Despite reaching a new all-time high of $872B, bitcoin's realized market cap monthly growth slowed to 0.9%, signaling continued risk-off sentiment, according to Glassnode.
On the 19th of April:
➡️Recently a gold bug, Jan Nieuwenhuijs (yeah he is Dutch, we are not perfect), stated the following: 'Bitcoin was created by mankind and can be destroyed by mankind. Gold cannot. It’s as simple as that.'
As a reply to a Saylor quote: 'Bitcoin has no counterparty risk. No company. No country. No creditor. No currency. No competitor. No culture. Not even chaos.'
Maybe Bitcoin can be destroyed by mankind, never say never, but what I do know is that at the moment Bitcoin is destroying gold like a manic.
https://i.ibb.co/ZR8ZB4d5/Go7d-KCqak-AA-D7-R.jpg
Oh and please do know. Gold may have the history, but Bitcoin has the scarcity. https://i.ibb.co/xt971vJc/Gp-FMy-AXQAAJzi-M.jpg
In 2013, you couldn't even buy 1 ounce of gold with 1 Bitcoin.
Then in 2017, you could buy 9 ounces of gold with 1 Bitcoin.
Today you can buy 25 ounces of gold with 1 Bitcoin.
At some point, you'll be able to buy 100 ounces of gold with 1 Bitcoin.
➡️Investment firm Abraxas Capital bought $250m Bitcoin in just 4 days.
On the 20th of April:
➡️The Bitcoin network is to be 70% powered by sustainable energy sources by 2030. https://i.ibb.co/nsqsfVY4/Go-r7-LEWo-AAt6-H2.jpg
➡️FORBES: "Converting existing assets like Fort Knox gold into bitcoin makes sense. It would be budget-neutral and an improvement since BTC does everything that gold can, but better" Go on Forbes, and say it louder for the people at the back!
On the 21st of April:
➡️Bitcoin has now recovered the full price dip from Trump's tariff announcement.
➡️Michael Saylor's STRATEGY just bought another 6,556 Bitcoin worth $555.8m. MicroStrategy now owns 2.7% of all Bitcoin in circulation. At what point do we stop celebrating Saylor stacking more?
On the same day, Metaplanet acquired 330 BTC for $28.2M, reaching 4,855 BTC in total holdings.
➡️'Northern Forum, a non-profit member organization of UNDP Climate Change Adaptation, just wrote a well-researched article on how Bitcoin mining is aiding climate objectives (stabilizing grids, aiding microgrids, stopping renewable waste)' -Daniel Batten
https://northernforum.net/how-bitcoin-mining-is-transforming-the-energy-production-game/
💸Traditional Finance / Macro:
On the 16th of April:
👉🏽The Nasdaq Composite is now on track for its 5th-largest daily point decline in history.
👉🏽'Foreign investors are dumping US stocks at a rapid pace: Investors from overseas withdrew ~$6.5 billion from US equity funds over the last week, the second-largest amount on record. Net outflows were only below the $7.5 billion seen during the March 2023 Banking Crisis. According to Apollo, foreigners own a massive $18.5 trillion of US stocks or 20% of the total US equity market. Moreover, foreign holdings of US Treasuries are at $7.2 trillion, or 30% of the total. Investors from abroad also hold 30% of the total corporate credit market, for a total of $4.6 trillion.' TKL
On the 17th of April:
👉🏽'Historically, the odds of a 10% correction are 40%, a 25% bear market 20%, and a 50% bear market 2%. That means that statistically speaking the further the market falls the more likely it is to recover. Yes, some 20% declines become 50% “super bears,” but more often than not the market has historically started to find its footing at -20%, as it appears to have done last week.' - Jurrien Timmer - Dir. of Global Macro at Fidelity
https://i.ibb.co/B2bVDLqM/Gow-Hn-PRWYAAX79z.jpg
👉🏽The S&P 500 is down 10.3% in the first 72 trading days of 2025, the 5th worst start to a year in history.
🏦Banks:
👉🏽 'Another amazing piece of reporting by Nic Carter on a truly sordid affair. Nic Carter is reporting that prominent Biden officials killed signature bank — though solvent — to expand Silvergate/SVB collapses into a national issue, allowing FDIC to invoke a “systemic risk exemption” to bail out SVB at Pelosi’s request.' - Alex Thorne
https://www.piratewires.com/p/signature-didnt-have-to-die-either-chokepoint-nic-carter
Signature, Silvergate, and SVB were attacked by Democrats to kneecap crypto and distance themselves from FTX. The chaos created unintended negative consequences. Signature was solvent but they forced a collapse to invoke powers which they used to clean up the mess they made.
🌎Macro/Geopolitics:
Every nation in the world is in debt and no one wants to say who the creditor is.
On the 14th of April:
👉🏽'US financial conditions are now their tightest since the 2020 pandemic, per ZeroHedge. Financial conditions are even tighter than during one of the most rapid Fed hike cycles of all time, in 2022. Conditions have tightened rapidly as stocks have pulled back, while credit spreads have risen. To put it differently, the availability and cost of financing for economic activity have worsened. That suggests the economy may slow even further in the upcoming months.' -TKL
👉🏽Global Repricing of Duration Risk... 'It opens the door to a global repricing of duration risk. This isn’t a blip. It’s a sovereign-level alarm bell.
"I find Japan fascinating on many levels not just its financial history. Just watch the Netflix documentary: Watch Age of Samurai: Battle for Japan 'I only discovered the other day that the Bank of Japan was the first to use Quantitative Easing. Perhaps that's when our global finance system was first broken & it's been sticking plasters ever since.' - Jane Williams
A must-read…the U.S. bond market is being driven down by Japanese selling and not because they want to…because they have to. It’s looking more and more dangerous.
BoJ lost its control over long-term bond yields. Since inflation broke out in Japan, BoJ can not suppress any longer...
EndGame Macro: "This is one of the clearest signals yet that the Bank of Japan has lost control of the long end of the curve. Japan’s 30-year yield hitting 2.845% its highest since 2004 isn’t just a local event. This has global knock-on effects: Japan is the largest foreign holder of U.S. Treasuries and a key player in the global carry trade. Rising JGB yields force Japanese institutions to repatriate capital, unwind overseas positions, and pull back on USD asset exposure adding pressure to U.S. yields and FX volatility. This spike also signals the end of the deflationary regime that underpinned global risk assets for decades. If Japan once the global anchor of low yields can’t suppress its bond market anymore, it opens the door to a global repricing of duration risk. This isn’t a blip. It’s a sovereign-level alarm bell."
https://i.ibb.co/LXsCDZMf/Gow-XGL8-Wk-AEDXg-P.jpg
You're distracted by China, but it's always been about Japan.
On the 16th of April:
👉🏽Over the last 20 years, gold has now outperformed stocks, up +620% compared to a +580% gain in the S&P 500 (dividends included). Over the last 9 months, gold has officially surged by over +$1,000/oz. Gold hit another all-time high and is now up over 27% in 2025. On pace for its best year since 1979.
https://i.ibb.co/9kZbtPVF/Goftd-OSW8-AA2a-9.png
Meanwhile, imports of physical gold have gotten so large that the Fed has released a new GDP metric. Their GDPNow tool now adjusts for gold imports. Q1 2025 GDP contraction including gold is expected to be -2.2%, and -0.1% net of gold. Gold buying is at recession levels.
👉🏽Von der Leyen: "The West as we knew it no longer exists. [..] We need another, new European Union ready to go out into the big wide world and play a very active role in shaping this new world order"
Her imperial aspirations have long been on display. Remember she was not elected.
👉🏽Fed Chair Jerome Powell says crypto is going mainstream, a legal framework for stablecoins is a good idea, and there will be loosening of bank rules on crypto.
On the 17th of April:
👉🏽The European Central Bank cuts interest rates by 25 bps for their 7th consecutive cut as tariffs threaten economic growth. ECB's focus shifted to 'downside risk to the growth outlook.' Markets price in the deposit rate will be at 1.58% in Dec, from 1.71% before the ECB's statement. Great work ECB, as inflation continues to decline and economic growth prospects worsen. Unemployment is also on the rise. Yes, the economy is doing just great!
On the same day, Turkey reversed course and hiked rates for the first time since March 2024, 350 bps move up to 46%.
👉🏽'Global investors have rarely been this bearish: A record ~50% of institutional investors intend to reduce US equity exposure, according to a Bank of America survey released Monday. Allocation to US stocks fell 13 percentage points over the last month, to a net 36% underweight, the lowest since the March 2023 Banking Crisis. Since February, investors' allocation to US equities has dropped by ~53 percentage points, marking the largest 2-month decline on record. Moreover, a record 82% of respondents are now expecting the world economy to weaken. As a result, global investor sentiment fell to just 1.8 points, the 4th-lowest reading since 2008. We have likely never seen such a rapid shift in sentiment.' -TKL
👉🏽'US large bankruptcies jumped 49 year-over-year in Q1 2025, to 188, the highest quarterly count since 2010. Even during the onset of the 2020 pandemic, the number of filings was lower at ~150. This comes after 694 large companies went bankrupt last year, the most in 14 years. The industrial sector recorded the highest number of bankruptcies in Q1 2025, at 32. This was followed by consumer discretionary and healthcare, at 24 and 13. Bankruptcies are rising.' -TKL
👉🏽DOGE‘s success is simply breathtaking.
https://i.ibb.co/zV45sYBn/Govy-G6e-XIAA8b-NI.jpg
Although it would've been worse without DOGE, nothing stops this train.
👉🏽GLD update: Custodian JPM added 4 tons, bringing their total to a new all-time high of 887 tons. JPM has added 50 tons in a month and is 163 tons from surpassing Switzerland to become the 7th largest gold holder in the world.
Now ask yourself and I quote Luke Gromen:
a) why JPM decided to become a GLD custodian after 18 years, & then in just over 2 years, shift 90%+ of GLD gold to its vaults, &;
b) why the Atlanta Fed has continued to report real GDP with- and without (~$500B of) gold imports YTD?
👉🏽Sam Callahan: After slowing the pace of QT twice—and now hinting at a potential return to QE—the Fed’s balance sheet is settling into a new higher plateau. "We’ve been very clear that this is a temporary measure...We’ll normalize the balance sheet and reduce the size of holdings...It would be quite a different matter if we were buying these assets and holding them indefinitely. It would be a monetization. We are not doing that." - Ben Bernake, Dec. 12, 2012
Temporary measures have a funny way of becoming structural features. The balance sheet didn’t ‘normalize’.. it evolved. What was once an ‘emergency’ is now a baseline. This isn’t QE or QT anymore. It’s a permanent intervention dressed as policy. Remember, 80% of all dollars were created in the last 5 years.
👉🏽Global Fiat Money Supply Is Exploding 🚨
The fiat system is on full tilt as central banks flood markets with unprecedented liquidity:
🇺🇸 U.S.: Money supply nearing new all-time highs
🇨🇳 China: At record levels
🇯🇵 Japan: Close to historic peaks
🇪🇺 EU: Printing into new ATHs https://i.ibb.co/Cp4z97Jx/Go4-Gx2-MXIAAzdi9.jpg
This isn’t growth—it’s monetary debasement. Governments aren’t solving problems; they’re papering over them with inflation.
Bitcoin doesn’t need bailouts. It doesn’t print. It doesn’t inflate.
As fiat currencies weaken under the weight of endless expansion, Bitcoin stands alone as a fixed-supply, incorruptible alternative.
👉🏽Fed Funds Rate: Market Expectations...
-May 2025: Hold
-Jun 2025: 25 bps cut to 4.00-4.25%
-July 2025: 25 bps cut to 3.75-4.00%
-Sep 2025: 25 bps cut to 3.50-3.75%
-Oct 2025: Hold
-Dec 2025: 25 bps cut to 3.25-3.50%
Anyway, shortterm fugazi....500 years of interest rates, visualized: https://i.ibb.co/84zs0yvD/Go7i7k-ZXYAAt-MRH.jpg
👉🏽'A net 49% of 164 investors with $386 billion in assets under management (AUM) believe a HARD LANDING is the most likely outcome for the world economy, according to a BofA survey. This is a MASSIVE shift in sentiment as 83% expected no recession in March.' -Global Markets Investor
👉🏽The EU’s New Role as Tax Collector: A Turning Point for Sovereignty
Beginning in 2027, a new chapter in the European Union’s influence over national life will begin. With the introduction of ETS2, the EU will extend its Emissions Trading System to include not just businesses, but private individuals as well. This means that CO₂ emissions from household gas consumption and vehicle fuel will be taxed—directly impacting the daily lives of citizens across the continent.
In practice, this shift transforms the EU into a (in)direct tax collector, without national consent, without a democratic mandate, and without the explicit approval of the people it will affect. The financial burden will be passed down through energy suppliers and fuel providers, but make no mistake: the cost will land squarely on the shoulders of European citizens, including millions of Dutch households.
This raises a fundamental question: What does sovereignty mean if a foreign or supranational entity can 'tax' your citizens? When a people are 'taxed' by a power beyond their borders—by an unelected body headquartered in Brussels—then either their nation is no longer sovereign, or that sovereignty has been surrendered or sold off by those in power.
There are only two conclusions to draw: We are living under soft occupation, with decisions made elsewhere that bind us at home. Or our sovereignty has been handed away voluntarily—a slow erosion facilitated by political elites who promised integration but delivered subordination. Either way, the more aggressively the EU enforces this trajectory, the more it reveals the futility of reforming the Union from within. The democratic deficit is not shrinking—it’s expanding. And with every new policy imposed without a national vote, the case for fundamental change grows stronger.
If Brussels continues down this path, there will come a point when only one option remains: A clean and decisive break. My view: NEXIT
Source: https://climate.ec.europa.eu/eu-action/eu-emissions-trading-system-eu-ets/ets2-buildings-road-transport-and-additional-sectors_en
For the Dutch readers:
https://www.businessinsider.nl/directe-co2-heffing-van-eu-op-gas-en-benzine-kan-huishoudens-honderden-euros-per-jaar-kosten-er-komt-ook-een-sociaal-klimaatfonds/?tid=TIDP10342314XEEB363B26CB34FB48054B929DB743E99YI5
On the 18th of April:
👉🏽'Two lost decades. Grotesque overregulation, bureaucracy, lack of innovation, and left redistribution mindset have their price. Europe is on its way to becoming an open-air museum. What a pity to watch.' -Michael A. Arouet
https://i.ibb.co/PsxdC3Kw/Goz-Ffwy-XMAAJk-Af.jpg
Looking at the chart, fun fact, the Lisbon Treaty was signed in 2007. That treaty greatly empowered the European bureaucracy. Reforms are needed in Europe, as soon as possible.
👉🏽CBP says latest tariffs have generated $500 million, well below Trump’s estimate — CNBC
Yikes! 'Probably one the biggest economic blunders in history. $500 million in 15 days means $12 billion a year in additional tax revenue. Literal trillions in wealth destroyed, interest on the debt increased, the dollar weakened, businesses wiped out all over the world, and literally every single country in the world antagonized... all for raising a yearly amount of taxes that can fund the US military budget for just 4 days. $500 million pays for exactly 37 minutes of the US budget.' - Arnaud Bertrand
YIKES!!
👉🏽Belarus to launch a "digital ruble" CBDC by the end of 2026.
On the 20th of April:
👉🏽'China’s central bank increased its gold holdings by 5 tonnes in March, posting its 5th consecutive monthly purchase. This brings total China’s gold reserves to a record 2,292 tonnes. Chinese gold holdings now reflect 6.5% of its total official reserve assets. According to Goldman Sachs, China purchased a whopping 50 tonnes of gold in February, or 10 times more than officially reported. Over the last 3 years, China's purchases of gold on the London OTC market have significantly surpassed officially reported numbers. China is accumulating gold at a rapid pace.' -TKL
On the 21st of April:
👉🏽Gold officially breaks above $3,400/oz for the first time in history. Gold funds attracted $8 BILLION in net inflows last week, the most EVER. This is more than DOUBLE the records seen during the 2020 CRISIS. Gold is up an impressive 29% year-to-date.
https://i.ibb.co/Nn7gr45q/Goq7km-PW8-AALegt.png
👉🏽I want to finish this segment and the weekly recap with a chart, a chart to think about! A chart to share with friends, family, and co-workers:
https://i.ibb.co/9xFxRrw/Gp-A3-ANWbs-AAO5nl.jpg
side note: 'Labeled periods like the "Era of Populism" (circa 2010-2020) suggest a link between growing wealth disparity and populist movements, supported by studies like those http://on.tandfonline.com, which note income inequality as a driver for populist party support in Europe due to economic insecurities and distrust in elites.'
The fiat system isn’t broken. It’s doing exactly what it was designed to do: Transfer wealth from savers to the state. This always ends in either default or debasement There’s one exit - Bitcoin.
Great thread: https://x.com/fitcoiner/status/1912932351677792703 https://i.ibb.co/84sFWW9q/Gow-Zv-SFa4-AAu2-Ag.jpg
🎁If you have made it this far I would like to give you a little gift, well in this case two gifts:
Bitcoin Nation State Adoption Paradox - A Trojan Horse with Alex Gladstein. Exploring the paradoxes of Bitcoin adoption in nation-states and its radical role in human rights, freedom, and financial sovereignty. https://youtu.be/pLIxmIMHL44
Credit: I have used multiple sources!
My savings account: Bitcoin The tool I recommend for setting up a Bitcoin savings plan: PocketBitcoin especially suited for beginners or people who want to invest in Bitcoin with an automated investment plan once a week or monthly.
Use the code SE3997
Get your Bitcoin out of exchanges. Save them on a hardware wallet, run your own node...be your own bank. Not your keys, not your coins. It's that simple. ⠀ ⠀
⠀⠀ ⠀ ⠀⠀⠀
Do you think this post is helpful to you?
If so, please share it and support my work with a zap.
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
⭐ Many thanks⭐
Felipe - Bitcoin Friday!
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
-
 @ a39d19ec:3d88f61e
2025-04-22 12:44:42
@ a39d19ec:3d88f61e
2025-04-22 12:44:42Die Debatte um Migration, Grenzsicherung und Abschiebungen wird in Deutschland meist emotional geführt. Wer fordert, dass illegale Einwanderer abgeschoben werden, sieht sich nicht selten dem Vorwurf des Rassismus ausgesetzt. Doch dieser Vorwurf ist nicht nur sachlich unbegründet, sondern verkehrt die Realität ins Gegenteil: Tatsächlich sind es gerade diejenigen, die hinter jeder Forderung nach Rechtssicherheit eine rassistische Motivation vermuten, die selbst in erster Linie nach Hautfarbe, Herkunft oder Nationalität urteilen.
Das Recht steht über Emotionen
Deutschland ist ein Rechtsstaat. Das bedeutet, dass Regeln nicht nach Bauchgefühl oder politischer Stimmungslage ausgelegt werden können, sondern auf klaren gesetzlichen Grundlagen beruhen müssen. Einer dieser Grundsätze ist in Artikel 16a des Grundgesetzes verankert. Dort heißt es:
„Auf Absatz 1 [Asylrecht] kann sich nicht berufen, wer aus einem Mitgliedstaat der Europäischen Gemeinschaften oder aus einem anderen Drittstaat einreist, in dem die Anwendung des Abkommens über die Rechtsstellung der Flüchtlinge und der Europäischen Menschenrechtskonvention sichergestellt ist.“
Das bedeutet, dass jeder, der über sichere Drittstaaten nach Deutschland einreist, keinen Anspruch auf Asyl hat. Wer dennoch bleibt, hält sich illegal im Land auf und unterliegt den geltenden Regelungen zur Rückführung. Die Forderung nach Abschiebungen ist daher nichts anderes als die Forderung nach der Einhaltung von Recht und Gesetz.
Die Umkehrung des Rassismusbegriffs
Wer einerseits behauptet, dass das deutsche Asyl- und Aufenthaltsrecht strikt durchgesetzt werden soll, und andererseits nicht nach Herkunft oder Hautfarbe unterscheidet, handelt wertneutral. Diejenigen jedoch, die in einer solchen Forderung nach Rechtsstaatlichkeit einen rassistischen Unterton sehen, projizieren ihre eigenen Denkmuster auf andere: Sie unterstellen, dass die Debatte ausschließlich entlang ethnischer, rassistischer oder nationaler Kriterien geführt wird – und genau das ist eine rassistische Denkweise.
Jemand, der illegale Einwanderung kritisiert, tut dies nicht, weil ihn die Herkunft der Menschen interessiert, sondern weil er den Rechtsstaat respektiert. Hingegen erkennt jemand, der hinter dieser Kritik Rassismus wittert, offenbar in erster Linie die „Rasse“ oder Herkunft der betreffenden Personen und reduziert sie darauf.
Finanzielle Belastung statt ideologischer Debatte
Neben der rechtlichen gibt es auch eine ökonomische Komponente. Der deutsche Wohlfahrtsstaat basiert auf einem Solidarprinzip: Die Bürger zahlen in das System ein, um sich gegenseitig in schwierigen Zeiten zu unterstützen. Dieser Wohlstand wurde über Generationen hinweg von denjenigen erarbeitet, die hier seit langem leben. Die Priorität liegt daher darauf, die vorhandenen Mittel zuerst unter denjenigen zu verteilen, die durch Steuern, Sozialabgaben und Arbeit zum Erhalt dieses Systems beitragen – nicht unter denen, die sich durch illegale Einreise und fehlende wirtschaftliche Eigenleistung in das System begeben.
Das ist keine ideologische Frage, sondern eine rein wirtschaftliche Abwägung. Ein Sozialsystem kann nur dann nachhaltig funktionieren, wenn es nicht unbegrenzt belastet wird. Würde Deutschland keine klaren Regeln zur Einwanderung und Abschiebung haben, würde dies unweigerlich zur Überlastung des Sozialstaates führen – mit negativen Konsequenzen für alle.
Sozialpatriotismus
Ein weiterer wichtiger Aspekt ist der Schutz der Arbeitsleistung jener Generationen, die Deutschland nach dem Zweiten Weltkrieg mühsam wieder aufgebaut haben. Während oft betont wird, dass die Deutschen moralisch kein Erbe aus der Zeit vor 1945 beanspruchen dürfen – außer der Verantwortung für den Holocaust –, ist es umso bedeutsamer, das neue Erbe nach 1945 zu respektieren, das auf Fleiß, Disziplin und harter Arbeit beruht. Der Wiederaufbau war eine kollektive Leistung deutscher Menschen, deren Früchte nicht bedenkenlos verteilt werden dürfen, sondern vorrangig denjenigen zugutekommen sollten, die dieses Fundament mitgeschaffen oder es über Generationen mitgetragen haben.
Rechtstaatlichkeit ist nicht verhandelbar
Wer sich für eine konsequente Abschiebepraxis ausspricht, tut dies nicht aus rassistischen Motiven, sondern aus Respekt vor der Rechtsstaatlichkeit und den wirtschaftlichen Grundlagen des Landes. Der Vorwurf des Rassismus in diesem Kontext ist daher nicht nur falsch, sondern entlarvt eine selektive Wahrnehmung nach rassistischen Merkmalen bei denjenigen, die ihn erheben.
-
 @ 54609048:8e22ba03
2025-04-22 12:25:50
@ 54609048:8e22ba03
2025-04-22 12:25:50One of the greatest threats facing liberty lovers around the world today is the rise of the biomedical security state—the militarization of healthcare. COVID-19 was merely a compliance test, and sadly, most failed it dismally. But pay attention: “pandemic response,” war-gamed at elite gatherings like Davos, is steadily morphing into official health policy through backdoor mechanisms—diabolical agreements like the WHO Pandemic Treaty, which effectively transfers sovereign pandemic authority to Bill Gates via the WHO; the rollout of digital IDs; and the global push for central bank digital currencies (CBDCs).
This biomedical Leviathan requires all three pillars to be firmly in place before it can unleash a never-ending cycle of pandemics. The goal? To normalize draconian measures like those witnessed in 2020, thereby dismantling not only national sovereignty but, more dangerously, individual sovereignty. A digital ID won't merely confirm your identity—it will track your vaccination status, movements, and even your sentiments, all to determine what privileges you're allowed. Meanwhile, the CBDC will act not just as a means of transaction but as an enforcement mechanism—particularly for dissenters. This is why having an alternative like Bitcoin is not just relevant, but essential.
Vaccines are a cornerstone of this architecture—not only as instruments of control but also as tools for "redesigning" humanity. Welcome to the realm of transhumanism. The merger of man and machine through brain-computer interfaces and artificial intelligence is no longer science fiction; it's a stated goal. In this context, vaccines are not merely preventative medicine but potentially covert instruments of eugenics. This could explain the near-religious devotion to these pharmaceutical products—despite their increasingly controversial outcomes and questionable safety record—especially when mandates enter the equation.
The first piece of property any individual owns upon birth is their body. And yet, this sacred ownership is violated at birth when governments mandate certain injections—often administered without informed parental consent. I've often wondered: Why, despite mounting evidence to the contrary, is vaccine efficacy treated as “settled science”? Why is it taboo to question vaccines or hold their manufacturers accountable for harm, even as we’re expected to believe—without scrutiny—that they are “safe and effective”? We’re told our refusal to comply endangers everyone else who took a product supposedly designed to protect them. Strange, isn’t it? If it’s so effective, why must everyone take it simultaneously?
If you're wondering where this seemingly off-the-cuff rant is headed, here's the point: when the state mandates vaccines, it violates your property rights over your own body. It’s a direct claim of ownership over you, dressed up in moral language like “we're all in this together.” You're guilt-tripped into compliance under the pretense of saving “grandma.” But the truth is, if your rights can be suspended for the collective, they were never yours to begin with.
The biomedical security state will manufacture a permanent state of emergency under the guise of “pandemic preparedness.” You’ll be expected—required, even—to inject yourself with the latest mRNA-based bioweapon, all in the name of public health. Some will die. Others will become incapacitated—zombies or vegetables. The altar of compliance will be merciless towards those that bow before it.
Public health agencies like the CDC, WHO, and NIH are on track to become as powerful as central banks. In fact, they may soon act as arms of monetary policy enforcement. Don’t believe it? Look into what was happening in the repo markets in September 2019—just months before the global shutdown. While you're at it, investigate how many elderly pensioners quietly dropped dead like flies between 2021 and 2023, either from the virus or the vaccine. I’ll let the numbers speak for themselves.
These agencies are becoming the new face of the war machine. Vaccines will be marketed as shields against biological threats—“benevolent” weapons to protect us from invisible enemies. And if history is any guide, the next “9/11-style” event will be biological in nature.
The lunatics running the asylum will seize any such crisis to strip away more of your freedoms while simultaneously redesigning the global economy—consolidating even more power in their hands. For a blueprint of this ambition, look no further than Klaus Schwab’s COVID-19: The Great Reset.
The only antidote is a decentralized parallel system of medicine—one that stands entirely outside the Big Pharma cartel. This will require not only a network of courageous healthcare providers but also a new generation of researchers willing to ask uncomfortable questions and challenge sacred cows in the pursuit of truth. Add independent scientific journals to the mix, and we can finally dismantle the machinery that suppresses unprofitable—but potentially life-saving—treatments.
In my view, none of this is viable at scale without decentralized money. Enter Bitcoin. It’s not a panacea, but it’s a crucial tool for realigning incentives. Bitcoin renders CBDCs dead on arrival and undermines the foundation of any future social credit system—where vaccine compliance will be its crown jewel.
The biomedical state is not coming—it’s already here, creeping into every corner of our lives. It will be the scepter of a new technocratic tyranny. So beware the white coats who worship the state. They are not here to heal—they are here to rule.
A more polished series of articles on this topic is forthcoming. Stay tuned.
-
 @ 70c48e4b:00ce3ccb
2025-04-22 08:35:52
@ 70c48e4b:00ce3ccb
2025-04-22 08:35:52Hello reader,
I can say from personal experience that crowdfunding has truly changed my life. I found people who believed in my dream of using Bitcoin as money. Every single one of my videos was made possible through crowdfunding. And I’m not alone. I know several Bitcoiners who have raised funds this way, from Africa to Korea to Haiti.
https://images.forbesindia.com/media/images/2022/Jul/img_190501_runwithbitcoin_bg.jpg
Crowdfunding is deeply rooted in the traditional financial world. From raising money for life-saving surgeries to helping someone open a local coffee shop, platforms like GoFundMe, Kickstarter, and Indiegogo have become essential tools for many. But behind all the heartwarming stories and viral campaigns, there’s a side of crowdfunding that doesn’t get talked about enough. Traditional platforms are far from perfect.
They are centralized, which means there’s always someone in control. These platforms can freeze campaigns, delay payouts, or take a significant cut of the money. And often, the people who need funding the most, those without access to strong banking systems or large social media followings are the ones who get left out.
Here are some of the problems I’ve noticed with these platforms:
Problem 1: Inequality in Who Gets Funded
A recent article in The Guardian pointed out something that’s hard to ignore. Crowdfunding often benefits people who already have influence. After the Los Angeles wildfires in January 2025, celebrities like Mandy Moore were able to raise funds quickly. At the same time, everyday people who lost their homes struggled to get noticed.
https://i.guim.co.uk/img/media/f8398505e58ec3c04685aab06e94048e5d7b6a0c/0_127_4800_2880/master/4800.jpg?width=1300&dpr=1&s=none&crop=none
Angor (https://angor.io/) changes that by removing the need for a central platform to choose which projects get featured or promoted. Anyone can share their project. People can find them on Angor Hub (https://hub.angor.io/), which is a public directory built on the Nostr protocol. Instead of relying on popularity, projects are highlighted based on transparency and engagement.
Problem 2: Platform Dependence and Middlemen
Here’s something people don’t often realize. When you raise funds online, the platform usually has control. It holds the money, decides when to release it, and can freeze everything without warning. This happened during the trucker protests in Canada in 2022. Tens of millions of dollars were raised, but platforms like GoFundMe and GiveSendGo froze the donations. The funds never reached the people they were meant for. Supporters were left confused, and the recipients had no way to access what had been raised for them.
https://upload.wikimedia.org/wikipedia/commons/thumb/2/2d/Convoi_de_la_libert%C3%A9_%C3%A0_Ottawa_01.jpg/800px-Convoi_de_la_libert%C3%A9_%C3%A0_Ottawa_01.jpg
Angor avoids all of this. It does not hold the funds, does not require approval processes, and only the project creator has control over the campaign. Contributions go directly from supporters to the people building the project, using Bitcoin. It is a peer-to-peer system that works without any gatekeepers. Angor never touches the money. It simply provides the tools people need to raise funds and build, while staying fully in control.
Problem 3: Global Access
Another major issue is that these platforms often exclude people based on where they live. If you're in a region with limited banking access or outside the supported list of countries, you’re likely shut out. In 2023, a woman named Samar in Gaza tried to raise funds for food and medical supplies during a crisis. A friend abroad set up a campaign to help, but the platform froze it due to "location-related concerns." The funds were locked, and the support never arrived in time.
https://images.gofundme.com/EMFtPWSLs3P9SewkzwZ4FtaBQSA=/720x405/https://d2g8igdw686xgo.cloudfront.net/78478731_1709065237698709_r.jpeg
Angor removes these barriers by using Bitcoin, which works globally without needing banks or approvals. Anyone, anywhere, can raise and receive support directly.
Problem 4: Lack of Transparency
Post-funding transparency is often lacking. Backers rarely get consistent updates, making it difficult to track a project's progress or hold anyone accountable.
In 2015, the Zano drone project on Kickstarter raised over £2.3 million from more than 12,000 backers. It promised a compact, smart drone for aerial photography. But as time went on, updates became rare and vague. Backers had little insight into the project’s struggles, and eventually, it was canceled. The company shut down, and most backers never received their product or a refund.
https://ichef.bbci.co.uk/ace/standard/976/cpsprodpb/2A0A/production/_86626701_ff861eeb-ce94-43b7-9a43-b30b5adbd7ab.jpg
Angor takes a different approach. Project updates are shared through Nostr, a decentralized and tamper-proof communication protocol. This allows backers to follow progress in real time, with no corporate filters and no blackout periods. Everyone stays in the loop, from start to finish.
Problem 5: Fraud and Accountability
Scams are a growing problem in the crowdfunding world. People can launch fake campaigns, collect donations, and vanish — leaving supporters with empty promises and no way to recover their money. One well-known example was the "Homeless Vet GoFundMe scam" in the U.S.
https://a57.foxnews.com/static.foxnews.com/foxnews.com/content/uploads/2018/09/720/405/1536549443584.jpg
A couple and a homeless man raised over $400,000 by telling a heartwarming story that later turned out to be completely fake. The money was spent on luxury items, and it took a legal investigation to uncover the truth. By the time it was resolved, most of the funds were gone.
This kind of fraud is hard to stop on traditional platforms, because once the funds are transferred, there’s no built-in structure to verify how they’re used.
On Angor, projects are funded in stages, with each step tied to a specific milestone. Bitcoin is held in a shared wallet that only unlocks funds when both the backer and the creator agree that the milestone is complete. If something feels off, backers can choose to stop and recover unspent funds.
This structure discourages scammers from even trying. It adds friction for bad actors, while still giving honest creators the freedom to build trust, deliver value, and raise support transparently. It can’t get any better than this
So, does Angor matter?
For me, it really does. I’m genuinely excited to have my project listed on Angorhub. In a world shaped by AI, open source and transparency light the way forward. Let the work shine on its own.
Have you tried Angor yet? Thanks for tuning in. Catch you next week. Ciao!
Guest blog: Paco nostr:npub1v67clmf4jrezn8hsz28434nc0y5fu65e5esws04djnl2kasxl5tskjmjjk
References:
• The Guardian, 2025: Crowdfunding after LA fires and inequality - https://www.theguardian.com/us-news/2025/jan/17/la-fires-gofundme-mandy-moore • https://www.theguardian.com/us-news/2018/nov/15/johnny-bobbitt-gofundme-scam-arrest-viral-gas-story-couple-charged • FundsforNGOs: The Success Story of an NGO That Scaled with Limited Resourceshttps://www2.fundsforngos.org/articles/the-success-story-of-an-ngo-that-scaled-with-limited-resources/ • https://www.freightwaves.com/news/gofundme-freezes-37m-until-organizers-of-canada-trucker-convoy-detail-spending-plan
-
 @ d360efec:14907b5f
2025-04-22 08:12:27
@ d360efec:14907b5f
2025-04-22 08:12:27ความทรงจำเรานั้นเชื่อได้แน่หรือ ?
"เพราะจิตเราเกิดดับทุกเสี้ยววินาที ทุกความทรงจำจึงสร้างขึ้นมาใหม่เสมอ ดังนั้นมันก็ไม่เหมือนต้นฉบับเป็นธรรมดา แต่ยังคงเค้าโครงเดิมอยู่ ความเปลี่ยนแปลงจึงเป็นนิรันดร์ค่ะ" - Lina Engword
เรามักจะคิดว่าความทรงจำของเราคือการบันทึกเหตุการณ์ในอดีตไว้อย่างแม่นยำ เหมือนการดูวิดีโอ 📼 หรือเปิดไฟล์คอมพิวเตอร์ 💾 แต่ในความเป็นจริงแล้ว แนวคิดนี้อาจไม่ใช่ภาพที่สมบูรณ์ บทความที่เรานำมาวิเคราะห์นี้ได้นำเสนอข้อคิดที่น่าสนใจเกี่ยวกับธรรมชาติของความทรงจำมนุษย์ ความน่าเชื่อถือของมัน และเชื่อมโยงไปถึงความจำเป็นในการฝึกฝนจิตตามหลักพุทธศาสนาเพื่อเข้าถึงความจริงที่เที่ยงแท้ 🧘♀️🔍
ความทรงจำไม่ใช่การบันทึก แต่เป็นการสร้างใหม่ 🏗️🧩
ประเด็นสำคัญที่บทความชี้ให้เห็นคือ ความทรงจำของมนุษย์ไม่ได้ทำงานเหมือนการ "บันทึก" เหตุการณ์ไว้ตายตัว 📼❌ แต่เปรียบเสมือน "ชิ้นส่วนของโค้ด" 💻 ที่จะถูก "สร้างขึ้นใหม่" 🏗️ ทุกครั้งที่เราพยายามระลึกถึง นั่นหมายความว่า ทุกครั้งที่เราดึงความทรงจำเก่าๆ กลับมา มันไม่ใช่การเปิดไฟล์เดิมซ้ำๆ แต่เป็นการประกอบชิ้นส่วนเหล่านั้นขึ้นมาใหม่ในห้วงเวลานั้นๆ กระบวนการนี้เองที่เปิดโอกาสให้เกิดการ "เติมเต็ม" ✨ หรือ "แก้ไข" ✏️ ข้อมูลในความทรงจำอยู่เสมอ ทำให้ความทรงจำที่เราเพิ่งนึกถึงอาจไม่เหมือนกับความทรงจำครั้งก่อนหน้าเสียทีเดียว 🔄
การปรุงแต่งด้วยเหตุผลและความคุ้นเคย 🤔➕🏠
สิ่งที่น่าสนใจอย่างยิ่งคือ ในกระบวนการ "สร้างใหม่" หรือ "ประกอบ" ความทรงจำขึ้นมานี้ มนุษย์มักจะเติม "เหตุผล"💡 หรือใส่สิ่งที่ตนเอง "คุ้นเคย" 🏠 ลงไปในเรื่องราวที่ระลึกได้เสมอ แม้ว่าสิ่งเหล่านั้นอาจจะไม่ได้เกิดขึ้นจริงหรือไม่เกี่ยวข้องโดยตรงกับเหตุการณ์นั้นๆ ก็ตาม ยกตัวอย่างเช่น เมื่อเราเล่าเรื่องในอดีต เรามักจะอธิบายว่าทำไมเราถึงทำสิ่งนั้น หรือทำไมเหตุการณ์นี้ถึงเกิดขึ้น โดยใส่เหตุผลที่เราคิดว่าสมเหตุสมผลในปัจจุบันลงไป สิ่งนี้ทำให้เรื่องราวในความทรงจำของเราดูมีความเชื่อมโยงและฟังดู "จริง" ✅ มากขึ้นในสายตาของเราเอง
เมื่อเราใส่เหตุผลหรือรายละเอียดที่คุ้นเคยลงไปในความทรงจำบ่อยครั้งเข้า มันก็จะยิ่งทำให้เรา "เชื่อ" 👍 โดยสนิทใจว่าสิ่งที่เราระลึกได้นั้นคือความจริงทั้งหมด ทั้งที่ความเป็นจริงของเหตุการณ์ดั้งเดิมอาจแตกต่างออกไป 🤥 นี่คือสาเหตุว่าทำไมคนสองคนจึงอาจมีความทรงจำเกี่ยวกับเหตุการณ์เดียวกันที่แตกต่างกันอย่างสิ้นเชิง ซึ่งปรากฏการณ์นี้สามารถอธิบายได้ดีด้วยตัวอย่างคลาสสิกในภาพยนตร์เรื่อง "ราโชมอน" (Rashomon) 🎬 ที่นำเสนอเหตุการณ์เดียวผ่านมุมมองและความทรงจำของตัวละครที่ขัดแย้งกันอย่างสิ้นเชิง แต่ทุกคนต่างเชื่อในสิ่งที่ตนเองจำได้ว่าเป็นความจริง 🤔❓
เครื่องมือและกระบวนการช่วยตรวจสอบความจริง 📱📹📝🔍
จากข้อจำกัดโดยธรรมชาติของความทรงจำนี้เอง ทำให้เห็นว่าเราไม่สามารถพึ่งพาสิ่งที่ 'จำได้' เพียงอย่างเดียวได้หากต้องการเข้าถึงความจริงที่เที่ยงแท้ เราจึงจำเป็นต้องมี 'กระบวนการตรวจสอบ' 🤔🔍 มาช่วยยืนยันหรือแก้ไขข้อมูลในความทรงจำ
ในยุคปัจจุบัน เรามีเครื่องมือภายนอกมากมายที่ช่วยในกระบวนการนี้ เช่น กล้องจากสมาร์ทโฟน 📱 หรือกล้องวงจรปิด 📹 ที่บันทึกเหตุการณ์ต่างๆ ไว้ได้อย่างเป็นกลาง ทำให้เรามี 'หลักฐาน' 📄 ที่เป็นรูปธรรมไว้อ้างอิงเพื่อเปรียบเทียบกับความทรงจำส่วนตัว ซึ่งบ่อยครั้งสิ่งที่กล้องเห็นนั้น 'ตรงกับความจริง' ✅ ในมุมมองที่ปราศจากอคติมากกว่าสิ่งที่ใจเราจำได้ การจดบันทึกด้วยเสียง 🎤 หรือการจดบันทึกเป็นลายลักษณ์อักษร 📝 ในทันที ก็เป็นอีกวิธีหนึ่งที่ช่วย 'ตรึง' ข้อมูลเบื้องต้นไว้ได้ระดับหนึ่งเช่นกัน ✍️
นอกจากเครื่องมือภายนอกแล้ว 'กระบวนการตรวจสอบเชิงจิตวิทยา' 🤔🧠 ที่เป็นระบบ ก็สามารถช่วยให้มนุษย์ค้นพบความจริงได้เช่นกัน ไม่ว่าจะเป็นกระบวนการซักถามในเชิงนิติวิทยาศาสตร์ 👮♀️ หรือแม้กระทั่งการฝึกฝนจิตเพื่อให้สามารถสังเกตการณ์ทำงานของตนเองได้อย่างละเอียดลึกซึ้ง ซึ่งนำเราไปสู่แนวคิดตามหลักพุทธศาสนา...
ทำไมพุทธศาสนาจึงสอนไม่ให้เชื่อแม้เป็นความคิดตัวเอง? 🙏🧠❌
จากธรรมชาติของความทรงจำและกระบวนการปรุงแต่งของจิตใจที่อธิบายมานี้เอง ทำให้เราเห็นความเชื่อมโยงกับหลักคำสอนในพุทธศาสนา 🙏 ที่เน้นย้ำให้เรา "ไม่เชื่อแม้แต่ความคิดตัวเอง" 🧠❌ อย่างปราศจากการพิจารณา เพราะความคิด อารมณ์ ความทรงจำ หรือแม้แต่ความรู้สึกมั่นใจอย่างแรงกล้าที่เรามีนั้น อาจถูกสร้างขึ้นหรือปรุงแต่งโดยกลไกของจิตใจที่ไม่ได้สะท้อนความจริงทั้งหมด 🤥
พุทธศาสนาชี้ให้เห็นว่า การจะเข้าถึงความจริงที่แท้จริงได้นั้น 🔍 จำเป็นต้องมีกระบวนการตรวจสอบภายในจิตใจ เปรียบเสมือนการสร้าง "อัลกอริทึม" 🤖 เพื่อตรวจทานว่าสิ่งที่เราคิดหรือจำได้นั้นเป็นความจริงหรือไม่ ✅❌ การจะทำเช่นนี้ได้ ไม่ใช่เรื่องง่าย และต้องอาศัยการฝึกฝนจิตอย่าง "สมาธิอย่างมาก" 🧘♂️🧘♀️ เพื่อให้จิตมีความตั้งมั่น เป็นระบบ และสามารถ "เห็นการดำเนินไปของจิตได้อย่างเป็นระบบ" 👀🔬 เห็นว่าจิตปรุงแต่งความทรงจำอย่างไร เห็นว่าเหตุผลที่เราใส่เข้าไปนั้นจริงหรือไม่ เป็นเพียงการตีความ หรือเป็นเพียงสิ่งที่ใจเราอยากให้เป็น
บทความยังกล่าวเสริมว่า ความทรงจำที่ "สด" ✨ หรือใกล้เคียงกับเวลาที่เกิดเหตุการณ์นั้นมักจะมีความน่าเชื่อถือมากกว่า 👍 แม้จะดู "ดิบๆ" หรือไม่ผ่านการปรุงแต่งมากนัก ซึ่งสอดคล้องกับแนวคิดที่ว่ายิ่งระยะเวลาผ่านไปนานเท่าไหร่ ⏳ ยิ่งมีการเรียกคืนความทรงจำนั้นๆ บ่อยครั้ง ความทรงจำก็ยิ่งมีโอกาสถูกแก้ไข เติมเต็ม หรือปรุงแต่งด้วยเหตุผลและความคุ้นเคยมากขึ้นเท่านั้น 🔄✏️
"ใดๆในโลกนั้นคือสมมุติ ความคิดความทรงจำ ก็เป็นสมมุติเพียง แต่เราต้องรู้จักใช้สมมุติให้เป็นประโยชน์ และรู้จักใช้มันให้เป็นเพื่อดำรงอยู่บนโลก"
สรุป ✨🧠🔍
โดยสรุปแล้ว บทความนี้เตือนใจเราว่า ความทรงจำของเราไม่ใช่กล้องวิดีโอที่บันทึกทุกอย่างไว้แม่นยำ 📼❌ แต่เป็นกระบวนการสร้างสรรค์ที่ซับซ้อนซึ่งมีแนวโน้มที่จะถูกปรุงแต่งด้วยเหตุผล ความคุ้นเคย และการตีความของเราเอง 🏗️🤔🏠 ความมั่นใจที่เรามีต่อสิ่งที่จำได้นั้น ไม่ได้เป็นหลักประกันว่าเป็นความจริงเสมอไป 👍🤥
การตระหนักถึงธรรมชาติข้อนี้ของจิต และการใช้เครื่องมือภายนอก 📱📹📝 รวมถึงการฝึกฝนจิตให้สามารถสังเกตการณ์ทำงานของมันได้อย่างละเอียดรอบคอบตามหลักพุทธศาสนา 🙏🧘♀️ จึงเป็นกุญแจสำคัญที่จะช่วยให้เราสามารถแยกแยะระหว่าง "ความจริง" ✅ กับ "สิ่งที่จิตปรุงแต่งขึ้น" 🤥 ได้มากขึ้น และช่วยให้เราเข้าใกล้ความเข้าใจในธรรมชาติของสรรพสิ่งได้อย่างเที่ยงตรง ไม่หลงติดอยู่ในวังวนของความทรงจำและความคิดที่อาจบิดเบือนไปจากความเป็นจริง 🔄
**#ความทรงจำ #จิตวิทยา #พุทธศาสนา #สมอง #สมาธิ #การฝึกจิต #ราโชมอน #ความจริง #ไม่เชื่อความคิด #ธรรมชาติของจิต #พัฒนาตนเอง #บทความน่ารู้ #เทคโนโลยี #บันทึกความจริง #พระอภิธรรม #พระหฤทัยสูตร #LinaEngword **
-
 @ d360efec:14907b5f
2025-04-22 07:54:51
@ d360efec:14907b5f
2025-04-22 07:54:51“คณิตศาสตร์” กุญแจเวทมนตร์ นักพนัน และ นักลงทุน ในนครเฮรันเทล นามกระฉ่อนเลื่องลือในหมู่นักเสี่ยงโชค เมื่อเอ่ยถึง “การพนัน” ภาพที่ชาวเมืองมักนึกถึงคือ “ยาจกข้างถนน”
มิใช่เรื่องแปลกประหลาดอันใด เพราะเป็นที่ร่ำลือกันว่า จ้าวแห่งหอคอยรัตติกาล ผู้คุมบ่อนพนัน มักร่ายเวทมนตร์สร้างเกมให้ตนเองได้เปรียบ เพื่อดูดกลืนเงินทองของผู้มาเยือน ดังนั้น การที่สามัญชนจะพิชิตเกมในระยะยาว จึงเป็นดั่งเงามายาที่จับต้องมิได้ กระนั้น ยังมีตำนานกล่าวขานถึงผู้กล้า ที่สามารถสร้างชื่อจาก “เกมพนัน” เช่น เวเนสซา รุสโซ นักเวทย์มนตร์ผู้ใช้กฎหมายแห่งแดนไกล ใช้เวลายาวนานถึงหกปี ร่ายเวทย์สะสมทรัพย์สินกว่าร้อยล้านเหรียญทอง จากการเล่นเกมไพ่ศักดิ์สิทธิ์ “โป๊กเกอร์” หรือแม้แต่ เอ็ดเวิร์ด โอ. ทอร์ป จอมปราชญ์ผู้สร้างกำไรถึงสามแสนหกหมื่นเหรียญทอง ภายในเจ็ดราตรี จากการเล่นเกมไพ่มนตรา “แบล็กแจ็ก” ด้วยเงินทุนตั้งต้นเพียงสามแสนสามหมื่นเหรียญทอง คิดเป็นอัตราเวทย์ตอบแทนร้อยสิบส่วน! เหล่าจอมยุทธ์เหล่านี้ มิได้อาศัยเพียงโชคช่วยชั่วครั้งชั่วคราวแล้วเลือนหาย แต่พวกเขากลับสามารถร่ายเวทย์สร้างผลตอบแทนระยะยาว จนเรียกได้ว่า ใช้ “หอคอยรัตติกาล” เป็นแหล่งเสบียงเลี้ยงชีพ โดยกุญแจเวทย์ที่บุคคลเหล่านี้ใช้ ก็คือ “คณิตศาสตร์” เหตุใด “คณิตศาสตร์” จึงช่วยให้ผู้คนเอาชนะ “การพนัน” ได้? และนอกจาก “การพนัน” แล้ว “คณิตศาสตร์” ยังสามารถประยุกต์ใช้กับสิ่งใดได้อีก? นักเล่าเรื่องแห่งเฮรันเทล จักไขปริศนาให้ฟัง เบื้องต้น ขอให้ท่านลองพิจารณาตนเอง ว่าเคยประสบพบพานเหตุการณ์เหล่านี้หรือไม่: * ตั้งมั่นว่า จักเสี่ยงโชคให้ได้กำไรเพียงเล็กน้อย แล้วจักหยุดพัก * แต่หากพลาดท่าเสียที จักจำกัดการสูญเสียให้เท่าทุนเดิมที่ตั้งไว้ * ครั้นเมื่อเวทมนตร์เข้าข้าง ได้กำไรมาแล้ว กลับโลภโมโทสัน อยากได้เพิ่มอีกนิด จึงร่ายเวทย์ต่อ * ทว่ากำไรเริ่มร่อยหรอ จนเหลือเพียงทุนเดิม สุดท้ายทุนที่ตั้งไว้คราแรกก็มลายสิ้น * จำต้องหาเงินทองมาลงเพิ่ม หวังทวงทุนคืน และพบว่าต้องสูญเสียเงินก้อนนั้นไปในห้วงเวลาต่อมา ลำดับเหตุการณ์ดังกล่าว เรียกได้ว่าเป็น “วงจรอุบาทว์” สำหรับนักพนันมากมายในเฮรันเทล ปริศนาที่ตามมาก็คือ เหตุใด “วงจรอุบาทว์” นี้จึงเกิดขึ้นซ้ำแล้วซ้ำเล่า? ส่วนหนึ่ง ย่อมเป็นเพราะอารมณ์อันแปรปรวนในการเสี่ยงโชคของแต่ละคน แต่อีกส่วนที่สำคัญยิ่งกว่า ต้องกล่าวว่าเป็นผลจาก “กลไกต้องสาป” ของจ้าวแห่งหอคอยรัตติกาล ซึ่งต้องกล่าวว่า เหล่าเจ้าของหอคอยรัตติกาลนั้น จักใช้หลักการทำนองเดียวกับ “สมาคมพ่อค้าผู้พิทักษ์” คือจักเก็บเงินทองจากชนจำนวนมาก เพื่อนำมาจ่ายให้กับชนเพียงหยิบมือ เพื่อล่อลวงให้ชนทั้งหลายเสี่ยงโชคต่อไป หรือทำให้เหล่านักพนันหวังว่า จักเป็นผู้โชคดีเฉกเช่นพวกเขาบ้าง แม้จะมีผู้โชคดีที่สามารถได้กำไรในเบื้องต้น แต่ในบั้นปลายก็จักพ่ายแพ้อยู่ดี ซึ่งเป็นไปตาม “กฎแห่งจำนวนมหาศาล” เพราะจ้าวแห่งหอคอยรัตติกาลนั้น ได้คำนวณและออกแบบระบบเกมที่ตนเองได้เปรียบในระยะยาวแล้ว จากตำนานนี้ ย่อมประจักษ์ชัดว่า แม้การพนันจักเป็นเรื่องของดวงชะตา แต่ก็ถูกรังสรรค์ขึ้นจากการคำนวณทางคณิตศาสตร์ ดังนั้น หากปรารถนาจะหาหนทางเอาชนะจ้าวแห่งหอคอยรัตติกาล ก็จำต้องเข้าใจ “คณิตศาสตร์” เสียก่อน ทีนี้ จงเงี่ยหูฟัง แล้วท่านจักได้ยินข้าไขปริศนา: ๑. ปริศนาแห่ง “กำไรคาดหวัง” สำหรับการแสวงหา “เกมเสี่ยงทาย” ที่ควรค่าแก่การเล่น หรือการเสี่ยง สิ่งแรกที่นักพนันพึงกระทำคือ “การประเมินกำไรคาดหวัง” หรือ “เวทคำนวณอนาคต” “กำไรคาดหวัง” ถูกคิดค้นโดย คริสเตียน ฮอยเกนส์ นักปราชญ์เวทย์ชาวดัตช์ เพื่อประเมินว่าเกมพนันแบบใดควรค่าแก่การเล่น ซึ่งมิใช่เพียงแค่การประเมินโอกาสแห่งชัยชนะเท่านั้น แต่ต้องคิดรวมขนาดของเงินเดิมพันไปด้วย โดยสูตรเวทย์คือ: กำไรคาดหวัง = (เงินที่ได้ x โอกาสชนะ) + (เงินที่เสีย x โอกาสแพ้) ดังนั้น หากปรารถนาจะสะสม “ทองคำมายา” ในระยะยาว จงเลือกเกมที่มี “กำไรคาดหวัง” เป็นบวก แต่หากพลาดพลั้งเข้าไปเล่นเกมที่ “กำไรคาดหวัง” เป็นลบ และบังเอิญว่าโชคชะตาเล่นตลกให้ได้เงินทองมาครอง พึงละทิ้งเกมนั้นเสียโดยพลัน เพราะท้ายที่สุดหากยังคงเล่นต่อไป ผู้อับโชคผู้นั้นก็คือตัวท่านเอง อย่างไรก็ตาม โดยธรรมดาแล้ว “กำไรคาดหวัง” ของเกมพนันที่มีเจ้ามือมักจักติดลบ จึงเป็นเรื่องยากยิ่งที่จะเอาชนะได้ เฉกเช่นตัวอย่างที่เราเห็น คือเกมในบ่อนพนัน หรือแม้แต่ “สลากกินแบ่งรัฐบาล” ก็ล้วนเป็นเกมที่มี “กำไรคาดหวัง” ติดลบทั้งสิ้น นอกจาก “กำไรคาดหวัง” จักถูกใช้กับการพนันได้แล้ว หลักเวทย์ “คณิตศาสตร์” ก็ยังสามารถประยุกต์ใช้กับการลงทุนได้ไม่แตกต่างกัน ตัวอย่างเช่น หากท่านเก็บสถิติข้อมูลการลงทุนของตนเอง แล้วพบว่ามีเพียงสามสิบส่วนร้อยเท่านั้น ที่ท่านซื้อ “ศิลาแห่งโชค” แล้วสร้างผลตอบแทนเป็นบวก แต่ท่านยังคงปรารถนาความสำเร็จในการลงทุน ก็จงจำกัดการขาดทุนแต่ละคราให้น้อยเข้าไว้ เช่น -๕% และปล่อยให้มีกำไรในแต่ละคราที่ลงทุน เช่น อย่างน้อย ๒๐% ซึ่งจากการใช้กลยุทธ์นี้ ท่านจักมี “กำไรคาดหวัง” = (๒๐% x ๐.๓) + (-๕% x ๐.๗) = ๒.๕% จักเห็นได้ว่า แม้ท่านจักมีจำนวนคราที่ขาดทุนบ่อยครั้ง แต่ก็ยังสามารถสร้างกำไรได้ หากคราที่กำไรนั้น สามารถทำเงินทองเป็นจำนวนมากได้ ๒. ปริศนาแห่ง “การบริหารหน้าตัก” หรือ “การบริหารเงินทุน” แม้ว่าท่านจักรับรู้ “กำไรคาดหวัง” แล้ว แต่หากท่านเผชิญหน้ากับการขาดทุนต่อเนื่องกัน ท่านก็อาจหมดเนื้อหมดตัวก่อนถึงคราที่จะกอบโกยเงินทองจากคราที่กำไร วิธีคลายปมปริศนานี้ก็คือ การมิลงเงินทองทั้งหมดของท่านในการลงทุนเพียงคราเดียว ซึ่งนอกจากการกระจายความเสี่ยงในการลงทุนหลาย “ศิลาแห่งโชค” หรือหลาย “เกมเสี่ยงทาย” แล้ว ท่านอาจกำหนดขนาดของการลงทุนแต่ละคราให้มิมากเกินไป แบบง่าย ๆ เช่น มิเกิน ๑๐% ของเงินลงทุนทั้งหมด หรือท่านอาจคำนวณขนาดของการลงทุนแต่ละคราด้วยสูตรทางคณิตศาสตร์ เช่น สูตร “การขาดทุนสูงสุดที่ท่านรับได้ (Value at Risk)” หรือ สูตร “ขนาดเดิมพันที่เหมาะสม (Kelly Formula)” ๓. ปริศนาแห่ง “อคติ” ในวงการพนัน มักมีอคติหนึ่งที่บังเกิดบ่อยครั้งกับผู้คน คือ “Gambler's Fallacy” หรือ “ความเชื่อผิด ๆ แห่งนักพนัน” ว่าหากเหตุการณ์หนึ่งบังเกิดบ่อยครั้งกว่าปรกติในช่วงเวลาหนึ่ง ๆ เหตุการณ์นั้นจักบังเกิดบ่อยครั้งน้อยลงในอนาคต ทั้ง ๆ ที่เหตุการณ์เหล่านั้นเป็นอิสระจากกันในทางสถิติ ยกตัวอย่างเช่น หากโยนเหรียญมนตราออกหัวไปแล้วสามครา ในคราที่สี่ หลายคนอาจคิดว่าโอกาสออกก้อยมากกว่าหัว แม้ว่าการโยนเหรียญแต่ละคราจะมิได้ส่งผลอันใดต่อกันเลย (จะโยนกี่ครา โอกาสหัวหรือก้อย ก็คือ ๕๐:๕๐ อยู่ยั่งยืน) หรือแม้กระทั่ง “สลากกินแบ่งรัฐบาล” มีหลายคนที่ซื้อเลขซ้ำกัน เพื่อหวังว่าจะถูกในงวดต่อ ๆ ไป ในวงการการลงทุน ก็มีลักษณะที่คล้ายคลึงกัน เช่น หาก “ศิลาแห่งโชค A” ราคาตกต่ำลงมาห้าครา บางคนอาจคิดว่าในคราที่หก ราคาของมันจักต้องเด้งขึ้นมา ซึ่งในความเป็นจริง หาได้เป็นเช่นนั้นเสมอไป จักเห็นได้ว่า แท้จริงแล้ว ไม่ว่าจักเป็น “เกมเสี่ยงทายแห่งโชคชะตา” หรือ “การผจญภัยในตลาดทุน” หากท่านมีความเข้าใจ และนำ “คณิตศาสตร์” เข้ามาเป็นรากฐาน มันก็อาจนำพาตัวท่านเอง ไปสู่จุดที่ได้เปรียบในเกมนั้น ได้เฉกเช่นกัน.. สูตรเวทย์มนตร์ที่ปรากฏในตำนาน: * กำไรคาดหวัง = (เงินที่ได้ x โอกาสชนะ) + (เงินที่เสีย x โอกาสแพ้) คำเตือนจากนักเล่าเรื่องแห่งเฮรันเทล: "พึงระลึกไว้เสมอว่า โชคชะตาเป็นสิ่งที่คาดเดาได้ยาก แม้เวทมนตร์คณิตศาสตร์จักช่วยนำทาง แต่ท้ายที่สุดแล้ว ความสำเร็จยังคงขึ้นอยู่กับการตัดสินใจและสติปัญญาของท่านเอง"
หวังว่าตำนานบทนี้จักเป็นประโยชน์แก่ท่านนะคะ
-
 @ 37c10448:f8256861
2025-04-22 07:44:10
@ 37c10448:f8256861
2025-04-22 07:44:10Title H1
Hello !
-
 @ ebdee929:513adbad
2025-04-23 21:06:02
@ ebdee929:513adbad
2025-04-23 21:06:02Screen flicker is a subtle and often overlooked cause of eye strain that many of us deal with daily. We understand this issue firsthand and are working hard to solve it, which is why we build for a different, more caring screen technology. This guide will help you understand screen flicker, how it affects you, and why better screen technology can make a real difference.
A silent epidemic in a LED-driven world
Tired eyes and a drained mind are almost a universal feeling at the end of a work day. That is, if you work a job that requires you to be in front of a computer screen all day… which today is most of us.
Slow motion shows flicker: It's not just screens; nearly all LED environments could flicker. Reddit: PWM_Sensitive
"Digital eye strain" refers to the negative symptoms (dry eyes, blurred vision, headaches, eye fatigue, light sensitivity, neck pain, etc.) that arise from use of digital devices for a prolonged period of time. It is also known as computer vision syndrome. Numbers are hard to pin down for such a commonly occurring issue, but pre COVID (2020) researchers estimated up to 70% prevalence in modern society.
Since COVID-19, things have gotten much worse.
"Digital eye strain has been on the rise since the beginning of the COVID-19 pandemic. An augmented growth pattern has been experienced with prevalence ranging from 5 to 65% in pre-COVID-19 studies to 80–94% in the COVID-19 era. The sudden steep increase in screen and chair time has led way to other silent pandemics like digital eye strain, myopia, musculoskeletal problems, obesity, diabetes etc."
The most common cause outlined by the researchers compiling these digital eye strain reviews is excessive screen time. And they outline the reason for screen time being an issue for the following reasons:
- Technological devices being in a short field of vision
- Devices causing a reduced blink rate
- Poor ergonomics
These are certainly all reasonable causes to highlight, but from our perspective two other key potential causes of digital eye strain are missing: screen flicker and blue light.
Multiple studies show that blue light in isolation can cause mitochondrial dysfunction and oxidative stress in the retina. To learn more about blue light, its potentially harmful effects, and how to mitigate them, read our "Definitive Guide on Blue Light".
In this discussion we are going to focus on screen flicker only.
FLICKER: AN INVISIBLE ISSUE
Flicker could be one of the most underrated stressors to our biology, as it is something we are exposed to constantly due to the nature of modern lighting and screens. It is widely agreed upon by both electrical/electronic engineers and scientific researchers that light flicker can cause:
- Headaches, eye strain, blurred vision and migraines
- Aggravation of autism symptoms in children
- Photo epilepsy
This is documented in the Institute of Electrical and Electronics Engineers (IEEE) 1789 standard for best practice in LED lighting applications, amongst other scientific reviews.
The P1789 committee from IEEE identified the following major effects of flicker:
- Photo epilepsy
- Increased repetitive behaviour among people suffering from autism
- Migraine or intense paroxysmal headache
- Asthenopia (eye strain); including fatigue, blurred vision, headache and diminished sight-related task performance
- Anxiety, panic attacks
- Vertigo
Light flicker is pervasive, mainly due to the ubiquitous nature of LEDs in our modern indoor work environments. We are being exposed to light flicker constantly from both light bulb sources and the screens that we stare at all day. This is a main reason why indoor, screen based work seems so draining. The good news is that this can be avoided (from an engineering perspective).
What is flicker?
We must first understand what "flicker actually is" before we can discuss how to avoid it or how to engineer flicker free light solutions.
In its most simple form, flicker can be defined as "a rapid and repeated change in the brightness of light over time (IEEE - PAR1789)".
Flicker can be easily conceptualized when it is visible, however the flicker we are talking about in regards to modern lighting & LEDs is unfortunately invisible to the human eye…which is part of the problem.
Most humans are unable to perceive flicker in oscillation rates above 60-90Hz (60-90 cycles per second). When we can't see something, we have a much more challenging time as a species grasping its effect on how we feel. The above mentioned health effects are directly related to the invisible flicker in terms of its effects on our biology. We can't see it, but our eyes and our brains react to it.
Slow-motion footage comparing DC-1's DC Dimming versus regular PWM Dimming.
For this article, we want to focus specifically on the flicker coming from LEDs used in modern personal electronics. This type of flicker can be shown in the above video of multiple smartphones being filmed with a slow motion camera.
What causes flicker in smartphones and computers?
There are a few different characteristics of a modern electronic display that cause flicker, but the main culprit is something called "PWM dimming".
PWM (Pulse Width Modulation) is an electronics control mechanism that uses pulsed signals as the LED driver function to control the brightness of the device display.PWM dimming has become the standard way to drive LEDs because it has specific advantages when it comes to retaining color consistency at lower brightness, and is also typically more power efficient. In a PWM dimming application, the diodes are being modulated to turn on and off very rapidly (faster than our eyes can perceive) to reduce the overall appearance of brightness of the light emission of the LEDs (aka luminance).
Brightness control in regular devices is just rapid flickering that looks steady to our eyes.
The lower the brightness setting, the longer the "off time". The "duty cycle" refers to the ratio of the LED being modulated "on" vs the total period of the cycle. Higher screen brightness setting = higher % duty cycle = more "time on" for the LED. This can be visualized in the graphic below.
PWM dimming controls brightness by quickly pulsing the backlight on and off.
PWM dimming has been chosen as the industry standard because of the intrinsic characteristics of the semiconductors in a light-emitting diode (LED) making it challenging to retain color consistency when modulating output illuminance with direct current, also known as Constant Current Reduction (CCR). CCR or "DC dimming" can utilize simpler control circuitry, but at the cost of less precision over the LED performance, especially at low brightness/luminance settings. PWM dimming can also save on overall power consumption.
DC Dimming maintains consistent light output by adjusting direct electrical current.
The downside of PWM dimming is obvious when you see the slow motion videos of the implementation in smartphone displays. The less obvious downside is that a PWM dimmed light means that we are consuming light at its peak output no matter the brightness setting. Because PWM is turning the light on/off constantly, the "ON" portion is always at peak intensity. This combined with the imbalanced light spectrum (blue heavy) can further exacerbate potential concerns of negatively affecting eye health and sleep quality.
The question we must ask then: is it more important for better LED and electronics performance, or is it more important to have screens that are not causing immense stress to our biology?
PWM Flicker on OLED screens vs LCD screens
Not all PWM flicker is created equal. The flicker frequency used for PWM dimming is directly related to how potentially stressful it can be to our eyes and brains. It is well agreed upon that the lower the frequency is, the more it can stress us out and cause eye strain. This is because at a high enough frequency, the oscillations are happening so rapidly that your brain basically perceives them as a continuous signal.
The "risk factor" of flicker is also dependent on the modulation % (similar to duty cycle) of the flicker as well, but since we all use our devices across different brightness settings and modulation % 's, it is best to focus on the frequency as the independent variable in our control.
Left: Non-PWM Flicker Device | Right: PWM Dimming Device. Nick Sutrich YouTube
Up to and including the iPhone 11, liquid crystal displays (LCD) were the standard for smartphones. A big switch was made to OLED display technology and the tech giants have never looked back. When it comes to PWM dimming frequency, there was a big shift when this swap occurred:
- Most LCD display use a PWM frequency of 1000Hz+ or no PWM at all.
- Nearly all OLED smartphone use a PWM frequency of 240Hz or 480Hz.
THE HEALTH RISK OF FLICKERING DEVICES
 So why don't OLED screens use higher PWM frequencies? Because of the nature of OLEDs being controlled as singular pixels, they need the lower PWM frequency to maintain that extremely precise color consistency at low brightness settings. This is of course why they use PWM in the first place.
So why don't OLED screens use higher PWM frequencies? Because of the nature of OLEDs being controlled as singular pixels, they need the lower PWM frequency to maintain that extremely precise color consistency at low brightness settings. This is of course why they use PWM in the first place.According to the IEEE1789 flicker risk chart for negative health effects, a 480Hz PWM smartphone (iPhone 15 Pro) would be high risk at any level above 40% modulation and a 240Hz PWM phone (Google Pixel 7) would be high risk above 20%. Whereas a phone that used 1000Hz-2000Hz PWM frequency (Nothing, Xiaomi 15) would only be "low risk".
- California law (Title 24), requires that LEDs used in certain applications have a "reduced flicker operation," meaning the percent amplitude modulation (flicker) must be less than 30% at frequencies below 200 Hz → The Google Pixel 7, Galaxy S23 and many iPhones operate at 240Hz and and 60-95% flicker...just above the legal limit!
- The report that recommended these levels states that: "Excessive flicker, even imperceptible flicker, can have deleterious health effects, and lesser amounts can be annoying or impact productivity."
 For PWM frequencies above 3000Hz, there is "no risk" according to IEEE1789. If you have ever felt that staring at your iPhone is far more "straining on the eyes" compared to your MacBook, the PWM flicker is likely a large reason for that (alongside the size of the display itself and distance held from the eyes)...because MacBooks have an LCD display and a PWM flicker frequency of 10-20kHz. At that PWM frequency, your brain is perceiving the oscillating light as a continuous signal.
For PWM frequencies above 3000Hz, there is "no risk" according to IEEE1789. If you have ever felt that staring at your iPhone is far more "straining on the eyes" compared to your MacBook, the PWM flicker is likely a large reason for that (alongside the size of the display itself and distance held from the eyes)...because MacBooks have an LCD display and a PWM flicker frequency of 10-20kHz. At that PWM frequency, your brain is perceiving the oscillating light as a continuous signal.Other causes of flicker
Although PWM dimming is widely agreed upon as the main cause of light flicker in modern consumer electronics displays, it is not the only cause. There are two other potential causes of light flicker we are aware of:
TEMPORAL DITHERING (AKA FRAME RATE CONTROL)
- "Pixel" dithering is a technique used to produce more colors than what a display's panel is capable of by rapidly changing between two different pixel colors. This technique unlocks a tremendous amount of more color possibilities - for example showing colors with 10 bit color depth results in billions of colors vs an 8 bit color depth results in millions of colors. Temporal dithering helps bridge the gap for 8 bit color depth displays.
- OLED displays are more likely to have better (10-bit) color depth vs LCD displays but use of temporal dithering can certainly vary across display technologies.
- Temporal dithering example (video)
AMORPHOUS SILICON (A-SI) THIN FILM TRANSISTOR (TFT) BACKPLANES
- Most commercial displays use a-Si TFT semiconductor technology in their backplanes of their LCD panels.
- This technology works well, but can have a high amount of photo-induced leakage current under back light illumination conditions, which can cause non uniformity of the light output and flicker.
- In simple language, the standard a-Si transistors are less "efficient" in a backlight application…which can lead to inconsistent light output and thus flicker.
The Daylight Computer: 100% Flicker Free
The DC-1 was designed and built purposefully to be flicker free. We wanted to provide a solution both for those suffering with severe eye strain and also to prevent negative optical and cognitive repercussions of flicker for any end consumer.
 ### HOW THE DC-1 ACHIEVES A FLICKER FREE DISPLAY:
### HOW THE DC-1 ACHIEVES A FLICKER FREE DISPLAY:- Using DC dimming instead of PWM dimming
- The most deliberate change made in our electrical design was centered around using a DC/CCR LED driver (aka Constant Current Reduction) instead of a PWM driver. This means that there is no pulsed circuit control around our LED backlight, and therefore no flicker from PWM lightning control.
- Has zero temporal dithering, as is a monochrome display
- The benefit of being black and white is there is no need to have intense pixel switching to create the mirage of billions of different color combinations.
- Uses Indium Gallium Zinc Oxide (IGZO) TFT Technology
- New semiconductor technology that provides better and more efficient performance vs a-Si TFT panels. Results in no flicker at the transistor level.
- Verified by light experts to be flicker free
- "Flicker testing yielded a perfect result using my highly sensitive audio-based flicker meter and the photodiode based FFT testing method: not even a trace of light modulation could be demonstrated with both methods!" — Dr. Alexander Wunsch (M.D., P.hD), Light Scientist
This commitment to a flicker-free experience isn't just theoretical; it's changing lives. We're incredibly moved by stories from users like Tiffany and Juan Diego, who found relief and regained possibilities with the DC-1:
For someone with eye disability, the DC-1 is a dream device. The display is so soft and smooth on my eyes that I was able to take my life back off of hold and return to medical school after a multi year absence.
— Tiffany Yang, Medical student
It took a couple of weeks to transition all my work screen time to the DC-1, but when I did, my eye strain completely went away. Plus, it let me work outside on my terrace.
— Juan Diego
Our eye-strain pilot study
Here at Daylight, we are all about proof of work. That is why we have already kicked off an initial pilot study to see if the DC-1 is actually more "eye friendly" than standard consumer electronic devices…specifically for those suffering from severe digital eye strain.
We have partnered with Dr. Michael Destefano, a neuro-optometrist at the Visual Symptoms Treatment Center in Illinois, to coordinate this pilot study.
MORE PARTICIPANTS NEEDED
Do you suffer from severe digital eye strain, computer vision syndrome, or visual snow syndrome? If you are interested in trying a DC-1 for 30 days as part of the Eye Strain Pilot Study, please send an email to drdestefanoOD@gmail.com with a background on your visual affliction.
Our favorite ways to reduce digital eye strain
Cutting screen time is not always possible, so here are some options that can help:
- Use DC dimming devices whenever possible
- Try minimizing screen time on your smartphone, utilizing a PWM laptop instead
- Try switching to an LCD smartphone or OLED smartphone with a high PWM frequency
- Turn "White Point" mode ON on your smartphone to increase the duty cycle and reduce the PWM dimming effect
Dive deeper with our curated resources
 #### Potential Biological and Ecological Effects of Flickering Artificial Light - PMC
#### Potential Biological and Ecological Effects of Flickering Artificial Light - PMCLight Emitting Diode Lighting Flicker, its Impact on Health and the Need to Minimise it
Digital Eye Strain- A Comprehensive Review
Nick Sutrich (Youtube) - Screen PWM Testing and Reviews
Eye Phone Review - Screen Health Reviews
Flicker Measurement NEMA77 and IEEE1789 White Paper
-
 @ 6e64b83c:94102ee8
2025-04-23 20:44:28
@ 6e64b83c:94102ee8
2025-04-23 20:44:28How to Import and Export Your Nostr Notes
This guide will help you import your notes from various Nostr relays and export them into your own relay. This is particularly useful when you want to ensure your content is backed up or when you're setting up your own relay.
Prerequisite
Your own Nostr relay (if you don't have one, check out Part 1: How to Run Your Own Nostr Relay)
Installing nak
nakis a command-line tool that helps you interact with Nostr relays. Here's how to install it:For Windows Users
- Visit the nak releases page
- Download the latest
nak-windows-amd64.exe - Rename it to
nak.exe - Move it to a directory in your PATH or use it from its current location
For macOS Users
- Visit the nak releases page
- Download the latest
nak-darwin-amd64 - Open Terminal and run:
bash chmod +x nak-darwin-amd64 sudo mv nak-darwin-amd64 /usr/local/bin/nak
For Linux Users
- Visit the nak releases page
- Download the latest
nak-linux-amd64 - Open Terminal and run:
bash chmod +x nak-linux-amd64 sudo mv nak-linux-amd64 /usr/local/bin/nak
Getting Your Public Key in Hex Format
Before downloading your notes, you need to convert your npub (public key) to its hex format. If you have your npub, run:
bash nak decode npub1YOUR_NPUB_HEREThis will output your public key in hex format, which you'll need for the next steps.
Downloading Your Notes
To download your notes, you'll need your public key in hex format and a list of reliable relays. Here are some popular relays you can use:
- wss://eden.nostr.land/
- wss://nos.lol/
- wss://nostr.bitcoiner.social/
- wss://nostr.mom/
- wss://relay.primal.net/
- wss://relay.damus.io/
- wss://relay.nostr.band/
- wss://relay.snort.social/
Note: You should check your Nostr client's settings to find additional relays where your notes are published. Add these to the list above.
Important Event Kinds
Here are some important event kinds you might want to filter for:
0: User Metadata (profile information)1: Short Text Notes3: Follow List4: Encrypted Direct Messages
Get the full list from: https://nips.nostr.com/#event-kinds
Downloading with Event Kind Filters
To download your notes with specific event kinds, use the
-kflag followed by the kind number, use multiple if you need to. For example, to download your profile, short notes, follow list, and direct messages:bash nak req -a YOUR_HEX_PUBKEY -k 0 -k 1 -k 3 -k 4 wss://eden.nostr.land/ wss://nos.lol/ wss://nostr.bitcoiner.social/ wss://nostr.mom/ wss://relay.primal.net/ wss://relay.damus.io/ wss://relay.nostr.band/ wss://relay.snort.social/ > events_filtered.jsonOr to download all your content, just don't provide any
kflag:bash nak req -a YOUR_HEX_PUBKEY wss://eden.nostr.land/ wss://nos.lol/ wss://nostr.bitcoiner.social/ wss://nostr.mom/ wss://relay.primal.net/ wss://relay.damus.io/ wss://relay.nostr.band/ wss://relay.snort.social/ > events.jsonThis will create a file containing all your notes in JSON Lines format.
Uploading Your Notes to Your Relay
Once you have your
events.jsonorevents_filtered.jsonfile, you can upload it to your own relay. ReplaceYOUR_RELAYwith your relay's WebSocket URL (e.g.,wss://my-relay.nostrize.me).bash nak event YOUR_RELAY < events.jsonImportant Notes: 1. Make sure your relay is running and accessible 2. The upload process might take some time depending on how many notes you have 3. You can verify the upload by querying your relay for your notes
Verifying the Upload
To verify that your notes were successfully uploaded to your relay, run:
bash nak req -a YOUR_HEX_PUBKEY YOUR_RELAYThis should return the same notes that were in your
events.jsonfile.Troubleshooting
If you encounter any issues:
- Make sure your relay is running and accessible
- Check that you're using the correct public key
- Verify that the relays in your download list are working
- Ensure you have proper permissions to write to your relay
Next Steps
- Remember to regularly backup your notes to ensure you don't lose any content.
- If you want to keep your friends' notes as well, add npubs that you want to import into your relay's settings (for Citrine it is "Accept events signed by" list), and run the commands for their pubkeys.
-
 @ 4fa5d1c4:fd6c6e41
2025-04-22 06:46:28
@ 4fa5d1c4:fd6c6e41
2025-04-22 06:46:28Bibel-Selfies
Prompts
Eva, Schlange, Apfel und Adam

A selfie of a woman resembling eve in the time of old testament, blurred body, holding an apple, kneeling in front adam. he has a shocked expression with his mouth open and wide eyes, evoking a sense of both fear and surprise. The scene appears surreal, with a huge snake behind her. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with adam and eve, possibly at a place like garden eden. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudha --v 6.0Tochter des Pharao mit Mose

A selfie of the biblical figure moabite woman with her baby in front of an oasis. She is wearing traditional and has black hair. The background shows water from the desert oasis and grasses around it. In the Background a wicker basket on the water. The photo was taken in the style of a selfie shot with GoPro cameraSimon Petrus

A selfie of a man resembling Simon Petrus, wearing a white robe, surrounded by waves and thunderstorm. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with many waves behind him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with jesus at the dead sea, possibly at a place like the sea. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary --v 6.0Zachäus auf dem Baum
A selfie of a man resembling a roman in the time of jesus, wearing a glamorous robe, surrounded by the crown of a tree. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with many leaves behind him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with jesus walking by, possibly at a place like the jerusalem. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary --v 6.0Maria am Ostermorgen

A selfie of a woman resembling maria in the time of jesus, wearing a robe, kneeling in front of stone grave. she has a shocked expression with her mouth open and wide eyes, evoking a sense of both fear and surprise. The scene appears surreal, with the open glowing grave behind her. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with jesus resurrection, possibly at a place like the jerusalem. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary --v 6.0Der verlorene Sohn bei den Schweinen

A young ancient arabic man with short hair in the time of jesus, brown eyes, and a dirty face, covered in mud from working on his pig farm, takes an amateur selfie at dusk. He is surrounded by pig stables, with a barn visible in the background and pigs seen near the front. The photo captures a raw, authentic moment, as he gazes directly into the camera with an expression of excitement or wonder. The image has a realistic style, akin to Unsplash photography, and is meant to be posted on a primitive-themed social network. The resolution of the photo is high, style of selfie with gopro --v 6.0Vater und Sohn vereint
 A selfie of an Arab father in simple garments in the time of jesus, embracing and hugging a young man. The father's face, visible in the foreground, radiates joy and relief. Only the back of the son's head is visible, as he faces away from the camera, returning the embrace in tattered clothing. In the background, a large ancient house and other family members can be seen watching from a distance, blurred. The photo is taken with a wide-angle lens using a GoPro, enhancing the dramatic and overwhelming effect of the scene --v 6.0
A selfie of an Arab father in simple garments in the time of jesus, embracing and hugging a young man. The father's face, visible in the foreground, radiates joy and relief. Only the back of the son's head is visible, as he faces away from the camera, returning the embrace in tattered clothing. In the background, a large ancient house and other family members can be seen watching from a distance, blurred. The photo is taken with a wide-angle lens using a GoPro, enhancing the dramatic and overwhelming effect of the scene --v 6.0Bartimäus

A selfie of a man resembling blind bartimaeus in the time of jesus, black and brown and white bandages on his head over his eyes and face, wearing a robe, kneeling in front of a market place. he has a shocked expression with his mouth open and wide eyes still covered with black and brown and white bandages on his head, evoking a sense of both fear and surprise. The scene appears surreal, with many sand behind him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with jesus healing the blind, possibly at a place like the jerusalem. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudha --v 6.0Daniel in der Löwengrube

A selfie of a man resembling Jesus, wearing a beige hoodie, surrounded by lions and cheetahs. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with many lions behind him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a lion's den, possibly at a place like the Grand Tabahar. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan ChaudharyDavid und Goliath

selfie of a the boy and shepherd david holding his slingshot resembling a fight with the giant goliath in the time of old testament, wearing a glamorous sligshot focusing on his giant opponent. David has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with a desert surrounding him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of the scene of David fighting with the giant goliath with his slingshot, possibly at a place like the jerusalem. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary --v 6.0Simson im Philistertempel

A selfie of a man resembling simson in the time of old testament, wearing a glamorous beard and long hair, surrounded by thousands of ancient fighters. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with a temple surrounding him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with jesus walking by, possibly at a place like the jerusalem. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary --v 6.0Jona und der Wal

A selfie of a man resembling israeli jona in the time of old testament,`wearing a glamorous beard and long hair, inside the body of a whale. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with the ocean surrounding him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene in the bible. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary
Jakob und Isaak

A selfie of a young man resembling an ancient Arabic in clothes made of skins of goats and furs of the goats, looking overwhelmed and distressed as he betrays his father, who blesses him. The scene shows a dawn sky with hints of the sunrise, evoking a surreal and dramatic atmosphere. The scene is set in ancient Jerusalem, with stone buildings. in the background an old man with a gesture of blessing, rising his hands to the sky, The photo is taken with a wide-angle lens, blending surrealism with humor. The style is reminiscent of a GoPro selfie, capturing the intense moment with a sense of both fear and surprisePetrus und der Hahn

A selfie of a man resembling ancient young arabic man saint in traditional biblical attire, being eaten by a whale,. he has a shocked expression with his mouth pressed and wide eyes, evoking a sense of both fear and surprise. The scene appears surreal, with one rooster crowing out loud behind the man. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with peter and the rooster, possibly at a place in jerusalem . The style of the photo blends surrealism with humor, go pro selfie, morning dawn near sunrise settingJosef im Brunnen

A selfie of an ancient israelian man with a magical dreamcoat clothing in a deep well, looking at the camera from above, captured in the style of a go pro selfie stickElia und die Raben

A close-up selfie of a bearded man (Elijah) in biblical clothing, smiling gratefully. He is standing near a stream in a secluded, rocky area. Several black ravens are perched on his shoulders and arms, holding pieces of bread and meat in their beaks. The scene has a warm, golden light, symbolizing God's provision. Photorealistic style, high detail.Absalom im Baum

A selfie of a man resembling of a young man (Absalom) with long hair knotted arount the branches of a large oak tree.. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with all of his hairs knotted around the tree. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene of a robin hood movie in the forest . The style of the photo blends surrealism with humorRuth und Boas im Weizenfeld

A selfie of a young woman resembling Ruth, with a radiant smile and sun-kissed skin. She's standing in a golden wheat field at sunset, her arms filled with freshly gathered sheaves of wheat. Her hair is partially covered with a simple headscarf, with loose strands blowing in the wind. She has a look of joy and gratitude in her eyes. The scene appears idyllic, with wheat stalks seeming to embrace her. In the background, a distinguished older man (Boaz) can be seen watching from a distance, his expression a mix of curiosity and admiration. The photo is taken with a wide-angle lens, capturing the vastness of the field, the warmth of the setting sun, and Boaz in the distance. The setting is reminiscent of a biblical harvest scene. The style of the photo blends realism with a touch of romantic nostalgia."Bibel-Selfies" von Jörg Lohrer Lizenz: CC0 1.0
.
`
-
 @ da0b9bc3:4e30a4a9
2025-04-22 06:44:40
@ da0b9bc3:4e30a4a9
2025-04-22 06:44:40Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/952743
-
 @ 1c19eb1a:e22fb0bc
2025-04-22 01:36:33
@ 1c19eb1a:e22fb0bc
2025-04-22 01:36:33After my first major review of Primal on Android, we're going to go a very different direction for this next review. Primal is your standard "Twitter clone" type of kind 1 note client, now branching into long-form. They also have a team of developers working on making it one of the best clients to fill that use-case. By contrast, this review will not be focusing on any client at all. Not even an "other stuff" client.
Instead, we will be reviewing a very useful tool created and maintained by nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 called #Amber. For those unfamiliar with Amber, it is an #Android application dedicated to managing your signing keys, and allowing you to log into various #Nostr applications without having to paste in your private key, better known as your #nsec. It is not recommended to paste your nsec into various applications because they each represent another means by which it could be compromised, and anyone who has your nsec can post as you. On Nostr, your #npub is your identity, and your signature using your private key is considered absolute proof that any given note, reaction, follow update, or profile change was authorized by the rightful owner of that identity.
It happens less often these days, but early on, when the only way to try out a new client was by inputting your nsec, users had their nsec compromised from time to time, or they would suspect that their key may have been compromised. When this occurs, there is no way to recover your account, or set a new private key, deprecating the previous one. The only thing you can do is start over from scratch, letting everyone know that your key has been compromised and to follow you on your new npub.
If you use Amber to log into other Nostr apps, you significantly reduce the likelihood that your private key will be compromised, because only one application has access to it, and all other applications reach out to Amber to sign any events. This isn't quite as secure as storing your private key on a separate device that isn't connected to the internet whatsoever, like many of us have grown accustomed to with securing our #Bitcoin, but then again, an online persona isn't nearly as important to secure for most of us as our entire life savings.
Amber is the first application of its kind for managing your Nostr keys on a mobile device. nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 didn't merely develop the application, but literally created the specification for accomplishing external signing on Android which can be found in NIP-55. Unfortunately, Amber is only available for Android. A signer application for iOS is in the works from nostr:npub1yaul8k059377u9lsu67de7y637w4jtgeuwcmh5n7788l6xnlnrgs3tvjmf, but is not ready for use at this time. There is also a new mobile signer app for Android and iOS called Nowser, but I have not yet had a chance to try this app out. From a cursory look at the Android version, it is indeed in the very early stages of development and cannot be compared with Amber.
This review of Amber is current as of version 3.2.5.

Overall Impression
Score: 4.7 / 5 (Updated 4/21/2025)
I cannot speak highly enough about Amber as a tool that every Nostr user on Android should start using if they are not already. When the day comes that we have more options for well-developed signer apps on mobile, my opinion may very well change, but until then Amber is what we have available to us. Even so, it is an incredibly well thought-out and reliable tool for securing your nsec.
Despite being the only well-established Android signer available for Android, Amber can be compared with other external signing methods available on other platforms. Even with more competition in this arena, though, Amber still holds up incredibly well. If you are signing into web applications on a desktop, I still would recommend using a browser extension like #Alby or #Nos2x, as the experience is usually faster, more seamless, and far more web apps support this signing method (NIP-07) than currently support the two methods employed by Amber. Nevertheless that gap is definitely narrowing.
A running list I created of applications that support login and signing with Amber can be found here: Nostr Clients with External Signer Support
I have run into relatively few bugs in my extensive use of Amber for all of my mobile signing needs. Occasionally the application crashes when trying to send it a signing request from a couple of applications, but I would not be surprised if this is no fault of Amber at all, and rather the fault of those specific apps, since it works flawlessly with the vast majority of apps that support either NIP-55 or NIP-46 login.
I also believe that mobile is the ideal platform to use for this type of application. First, because most people use Nostr clients on their phone more than on a desktop. There are, of course, exceptions to that, but in general we spend more time on our phones when interacting online. New users are also more likely to be introduced to Nostr by a friend having them download a Nostr client on their phone than on a PC, and that can be a prime opportunity to introduce the new user to protecting their private key. Finally, I agree with the following assessment from nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn.
nostr:nevent1qqsw0r6gzn05xg67h5q2xkplwsuzedjxw9lf7ntrxjl8ajm350fcyugprfmhxue69uhhyetvv9ujumn0wd68yurvv438xtnrdaksyg9hyaxj3clfswlhyrd5kjsj5v04clhjvgeq6pwztmysfzdvn93gev7awu9v
The one downside to Amber is that it will be quite foreign for new users. That is partially unavoidable with Nostr, since folks are not accustomed to public/private key cryptography in general, let alone using a private key to log into websites or social media apps. However, the initial signup process is a bit cumbersome if Amber is being used as the means of initially generating a key pair. I think some of this could be foregone at start-up in favor of streamlining onboarding, and then encourage the user to back-up their private key at a later time.
Features
Amber has some features that may surprise you, outside of just storing your private key and signing requests from your favorite Nostr clients. It is a full key management application, supporting multiple accounts, various backup methods, and even the ability to authorize other users to access a Nostr profile you control.
Android Signing
This is the signing method where Amber really shines in both speed and ease of use. Any Android application that supports this standard, and even some progressive web-apps that can be installed to your Android's home-screen, can very quickly and seamlessly connect with Amber to authorize anything that you need signed with your nsec. All you have to do is select "Login with Amber" in clients like #Amethyst or #0xChat and the app will reach out to Amber for all signing requests from there on out. If you had previously signed into the app with your nsec, you will first need to log out, then choose the option to use Amber when you log back in.

This is a massive deal, because everything you do on Nostr requires a signature from your private key. Log in? Needs a signature. Post a "GM" note? Needs a signature. Follow someone who zapped your note? Needs a signature. Zap them back? You guessed it; needs a signature. When you paste your private key into an application, it will automatically sign a lot of these actions without you ever being asked for approval, but you will quickly realize just how many things the client is doing on your behalf when Amber is asking you to approve them each time.
Now, this can also get quite annoying after a while. I recommend using the setting that allows Amber to automatically sign for basic functions, which will cut down on some of the authorization spam. Once you have been asked to authorize the same type of action a few times, you can also toggle the option to automatically authorize that action in the future. Don't worry, though, you have full control to require Amber to ask you for permission again if you want to be alerted each time, and this toggle is specific to each application, so it's not a blanket approval for all Nostr clients you connect with.

This method of signing is just as fast as signing via browser extension on web clients, which users may be more accustomed to. Everything is happening locally on the device, so it can be very snappy and secure.
Nostr Connect/Bunker Signing
This next method of signing has a bit of a delay, because it is using a Nostr relay to send encrypted information back and forth between the app the user is interacting with and Amber to obtain signatures remotely. It isn't a significant delay most of the time, but it is just enough to be noticeable.
Also, unlike the previous signing method that would automatically switch to Amber as the active application when a signing request is sent, this method only sends you a notification that you must be watching for. This can lead to situations where you are wondering why something isn't working in a client you signed into remotely, because it is waiting on you to authorize the action and you didn't notice the notification from Amber. As you use the application, you get used to the need to check for such authorization requests from time to time, or when something isn't working as expected.

By default, Amber will use relay.nsec.app to communicate with whichever Nostr app you are connecting to. You can set a different relay for this purpose, if you like, though not just any relay will support the event kinds that Amber uses for remote signing. You can even run your own relay just for your own signing purposes. In fact, the creator of Amber has a relay application you can run on your phone, called Citrine, that can be used for signing with any web app you are using locally on your phone. This is definitely more of an advanced option, but it is there for you if you want it. For most users, sticking with relay.nsec.app will be just fine, especially since the contents of the events sent back and forth for signing are all encrypted.
Something many users may not realize is that this remote signing feature allows for issuing signing permissions to team members. For instance, if anyone ever joined me in writing reviews, I could issue them a connection string from Amber, and limit their permissions to just posting long-form draft events. Anything else they tried to do would require my explicit approval each time. Moreover, I could revoke those permissions if I ever felt they were being abused, without the need to start over with a whole new npub. Of course, this requires that your phone is online whenever a team member is trying to sign using the connection string you issued, and it requires you pay attention to your notifications so you can approve or reject requests you have not set to auto-approve. However, this is probably only useful for small teams, and larger businesses will want to find a more robust solution for managing access to their npub, such as Keycast from nostr:npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc.
The method for establishing a connection between Amber and a Nostr app for remote signing can vary for each app. Most, at minimum, will support obtaining a connection string from Amber that starts with "bunker://" and pasting it in at the time of login. Then you just need to approve the connection request from Amber and the client will log you in and send any subsequent signing requests to Amber using the same connection string.

Some clients will also offer the option to scan a QR code to connect the client to Amber. This is quite convenient, but just remember that this also means the client is setting which relay will be used for communication between the two. Clients with this option will also have a connection string you can copy and paste into Amber to achieve the same purpose. For instance, you may need this option if you are trying to connect to an app on your phone and therefore can't scan the QR code using Amber on the same phone.

Multiple Accounts
Amber does not lock you into using it with only a single set of keys. You can add all of your Nostr "accounts" to Amber and use it for signing events for each independently. Of course, Nostr doesn't actually have "accounts" in the traditional sense. Your identity is simply your key-pair, and Amber stores and accesses each private key as needed.

When first signing in using native Android signing as described above, Amber will default to whichever account was most recently selected, but you can switch to the account that is needed before approving the request. After initial login, Amber will automatically detect the account that the signing request is for.
Key Backup & Restore
Amber allows multiple ways to back up your private key. As most users would expect, you can get your standard nsec and copy/paste it to a password manager, but you can also obtain your private key as a list of mnemonic seed words, an encrypted version of your key called an ncryptsec, or even a QR code of your nsec or ncryptsec.

Additionally, in order to gain access to this information, Amber requires you to enter your device's PIN or use biometric authentication. This isn't cold-storage level protection for your private key by any means, especially since your phone is an internet connected device and does not store your key within a secure element, but it is about as secure as you can ask for while having your key accessible for signing Nostr events.
Tor Support
While Amber does not have Tor support within the app itself, it does support connecting to Tor through Orbot. This would be used with remote signing so that Amber would not connect directly over clearnet to the relay used for communication with the Nostr app requesting the signature. Instead, Amber would connect through Tor, so the relay would not see your IP address. This means you can utilize the remote signing option without compromising your anonymity.

Additional Security
Amber allows the user the option to require either biometric or PIN authentication before approving signing requests. This can provide that extra bit of assurance that no one will be able to sign events using your private key if they happen to gain access to your phone. The PIN you set in Amber is also independent from the PIN to unlock your device, allowing for separation of access.
Can My Grandma Use It?
Score: 4.6 / 5 (Updated 4/21/2025)
At the end of the day, Amber is a tool for those who have some concept of the importance of protecting their private key by not pasting it into every Nostr client that comes along. This concept in itself is not terribly approachable to an average person. They are used to just plugging their password into every service they use, and even worse, they usually have the same password for everything so they can more readily remember it. The idea that they should never enter their "Nostr password" into any Nostr application would never occur to them unless someone first explained how cryptography works related to public/private key pairs.
That said, I think there can be some improvements made to how users are introduced to these concepts, and that a signer application like Amber might be ideal for the job. Considering Amber as a new user's first touch-point with Nostr, I think it holds up well, but could be somewhat streamlined.
Upon opening the app, the user is prompted to either use their existing private key or "Create a new Nostr account." This is straightforward enough. "Account" is not a technically correct term with Nostr, but it is a term that new users would be familiar with and understand the basic concept.

The next screen announces that the account is ready, and presents the user with their public key, explaining that it is "a sort of username" that will allow others to find them on Nostr. While it is good to explain this to the user, it is unnecessary information at this point. This screen also prompts the user to set a nickname and set a password to encrypt their private key. Since the backup options also allow the user to set this password, I think this step could be pushed to a later time. This screen would better serve the new user if it simply prompted them to set a nickname and short bio that could be saved to a few default relays.

Of course, Amber is currently prompting for a password to be set up-front because the next screen requires the new user to download a "backup kit" in order to continue. While I do believe it is a good idea to encourage the creation of a backup, it is not crucial to do so immediately upon creation of a new npub that has nothing at stake if the private key is lost. This is something the UI could remind the user to do at a later time, reducing the friction of profile creation, and expediting getting them into the action.

Outside of these minor onboarding friction points, I think Amber does a great job of explaining to the user the purpose of each of its features, all within the app and without any need to reference external documentation. As long as the user understands the basic concept that their private key is being stored by Amber in order to sign requests from other Nostr apps, so they don't have to be given the private key, Amber is very good about explaining the rest without getting too far into the technical weeds.
The most glaring usability issue with Amber is that it isn't available in the Play Store. Average users expect to be able to find applications they can trust in their mobile device's default app store. There is a valid argument to be made that they are incorrect in this assumption, but that doesn't change the fact that this is the assumption most people make. They believe that applications in the Play Store are "safe" and that anything they can't install through the Play Store is suspect. The prompts that the Android operating system requires the user to approve when installing "unknown apps" certainly doesn't help with this impression.
Now, I absolutely love the Zapstore from nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9, but it doesn't do much to alleviate this issue. Users will still need to be convinced that it is safe to install the Zapstore from the GitHub repo, and then install Amber from there. Furthermore, this adds yet another step to the onboarding process.
Instead of:
- Install Amber
- Set up your keys
- Install the client you want to use
- Log in with Amber
The process becomes:
- Go to the Zapstore GitHub and download the latest version from the releases page.
- Install the APK you downloaded, allowing any prompt to install unknown apps.
- Open Zapstore and install Amber, allowing any prompt to install unknown apps again.
- Open Amber and set up your keys.
- Install the client you want to use
- Log in with Amber
An application as important as Amber for protecting users' private keys should be as readily available to the new user as possible. New users are the ones most prone to making mistakes that could compromise their private keys. Amber should be available to them in the Play Store.
UPDATE: As of version 3.2.8 released on 4/21/2025, the onboarding flow for Amber has been greatly improved! Now, when selecting to set up a new "account" the user is informed on the very next screen, "Your Nostr account is ready!" and given their public key/npub. The only field the user must fill in is their "nickname"/display name and hit "Continue."
From there the user is asked if they want Amber to automatically approve basic actions, or manually approve each app, and then they are shown a new Applications screen, with a prompt to create a backup of their account. This prompt persists until the user has done so.
As you can see, the user is also encouraged to find applications that can be used with Amber with links to nostrapps.com and the Zapstore.
Thanks to these updates, Amber is now the smoothest and most user-friendly onboarding experience I have seen for Nostr to date. Sure, it doesn't have anything for setting up a profile picture or lightning address, but that is better done in a client like Amethyst or YakiHonne, anyway. Just tap "create," type in a handle to call yourself, and you're done!
How do UI Look?
Score: 4.5 / 5
Amber's UI can be described as clean but utilitarian. But then, Amber is a tool, so this is somewhat expected. It is not an app you will be spending a lot of time in, so the UI just needs to be serviceable. I would say it accomplishes this and then some. UI elements are generally easy to understand what they do, and page headings fill in the gaps where that is not the case.

I am not the biggest fan of the color-scheme, particularly in light-mode, but it is not bad in dark-mode at all, and Amber follows whatever theme you have set for your device in that respect. Additionally, the color choice does make sense given the application's name.

It must also be taken into consideration that Amber is almost entirely the product of a single developer's work. He has done a great job producing an app that is not only useful, but pleasant to interact with. The same cannot be said for most utility apps I have previously used, with interfaces that clearly made good design the lowest priority. While Amber's UI may not be the most beautiful Nostr app I have seen, design was clearly not an afterthought, either, and it is appreciated.
Relay Management
Score: 4.9 / 5
Even though Amber is not a Nostr client, where users can browse notes from their favorite npubs, it still relies heavily on relays for some of its features. Primarily, it uses relays for communicating with other Nostr apps for remote signing requests. However, it also uses relays to fetch profile data, so that each private key you add to Amber will automatically load your chosen username and profile picture.
In the relay settings, users can choose which relays are being used to fetch profile data, and which relays will be used by default when creating new remote signing connection strings.

The user can also see which relays are currently connected to Amber and even look at the information that has been passed back and forth on each of those active relays. This information about actively connected relays is not only available within the application, but also in the notification that Amber has to keep in your device's notification tray in order to continue to operate in the background while you are using other apps.

Optionality is the name of the game when it comes to how Amber handles relay selection. The user can just stick with the default signing relay, use their own relay as the default, or even use a different relay for each Nostr application that they connect to for remote signing. Amber gives the user an incredible amount of flexibility in this regard.
In addition to all of this, because not all relays accept the event types needed for remote signing, when you add a relay address to Amber, it automatically tests that relay to see if it will work. This alone can be a massive time saver, so users aren't trying to use relays that don't support remote signing and wondering why they can't log into noStrudel with the connection string they got from Amber.

The only way I could see relay management being improved would be some means of giving the user relay recommendations, in case they want to use a relay other than relay.nsec.app, but they aren't sure which other relays will accept remote signing events. That said, most users who want to use a different relay for signing remote events will likely be using their own, in which case recommendations aren't needed.
Current Users' Questions
The AskNostr hashtag can be a good indication of the pain points that other users are currently having with any Nostr application. Here are some of the most common questions submitted about Amber in the last two months.
nostr:nevent1qqsfrdr68fafgcvl8dgnhm9hxpsjxuks78afxhu8yewhtyf3d7mkg9gpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgq3qkgh77xxt7hhtt4u528hecnx69rhagla8jj3tclgyf9wvkxa6dc0sxp0e6m
This is a good example of Amber working correctly, but the app the user is trying to log into not working. In my experience with #Olas in particular, it sometimes allows remote signer login, and sometimes doesn't. Amber will receive the signing request and I will approve it, but Olas remains on the login screen.
If Amber is receiving the signing requests, and you are approving them, the fault is likely with the application you are trying to log into.
That's it. That's all the repeated questions I could find. Oh, there were a few one-off questions where relay.nsec.app wouldn't connect, or where the user's out-of-date web browser was the issue. Outside of that, though, there were no common questions about how to use Amber, and that is a testament to Amber's ease of use all on its own.
Wrap Up
If you are on Android and you are not already using Amber to protect your nsec, please do yourself a favor and get it installed. It's not at all complicated to set up, and it will make trying out all the latest Nostr clients a safe and pleasant experience.
If you are a client developer and you have not added support for NIP-55 or NIP-46, do your users the courtesy of respecting the sanctity of their private keys. Even developers who have no intention of compromising their users' keys can inadvertently do so. Make that eventuality impossible by adding support for NIP-55 and NIP-46 signing.
Finally, I apologize for the extended time it took me to get this review finished. The time I have available is scarce, Nostr is distracting, and nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 kept improving Amber even as I was putting it through its paces over the last two months. Keep shipping, my friend! You have made one of the most useful tools we have seen for Nostr to date!
Now... What should I review next?
-
 @ 502ab02a:a2860397
2025-04-22 01:16:17
@ 502ab02a:a2860397
2025-04-22 01:16:17ก่อนที่จะมูฟออนจากเทคนิคการสร้าง เรามาดูเรื่องสำคัญครับ
วันที่ไม่มีวัว แต่มีเวย์โปรตีน – เบื้องหลังเทคโนโลยีที่เปลี่ยนถังหมักให้กลายเป็นเต้านมวัว เคยมีคำถามไหมว่า “เวย์โปรตีน” ที่กินตอนออกกำลังกาย หรือโยเกิร์ตถ้วยโปรดที่ซื้อมาจากร้านใกล้บ้าน มันยังมาจากนมวัวอยู่ไหม? ถ้าคำตอบคือ “ไม่” แล้วมันมาจากไหน?
ยินดีต้อนรับสู่โลกของ Perfect Day บริษัทที่บอกว่า "เราสร้างเวย์โปรตีนได้ โดยไม่ต้องใช้วัวเลยแม้แต่นิดเดียว” ฟังดูเหมือนมายากล แต่นี่คือวิทยาศาสตร์ขั้นสูงที่ผูกสูตรไว้กับ DNA, จุลินทรีย์ และการหมักอย่างแยบยล
ขั้นตอนที่ 1: หารหัสโปรตีนจากแม่วัว เริ่มต้นจากคำถามง่าย ๆ ว่า “โปรตีนเวย์ที่อยู่ในน้ำนมวัว คืออะไร?” คำตอบคือ เบต้า-แลคโตโกลบูลิน (Beta-lactoglobulin) ซึ่งเป็นโปรตีนหลักในเวย์ประมาณ 50-55% โดยในธรรมชาติ วัวจะสร้างโปรตีนนี้จาก รหัสพันธุกรรมใน DNA ของมัน Perfect Day จึงไปค้นหา ลำดับเบส (DNA sequence) ของโปรตีนนี้จากฐานข้อมูลวิทยาศาสตร์ชื่อ UniProt (Universal Protein Resource) ซึ่งเก็บรหัสโปรตีนของสิ่งมีชีวิตแทบทุกชนิดไว้ครบถ้วน ได้รหัสมาแล้ว ก็เตรียมเข้าสู่ภารกิจ “หลอกจุลินทรีย์ให้สร้างโปรตีนแทนวัว”
ขั้นตอนที่ 2: สร้างแผ่นดีเอ็นเอสังเคราะห์ รหัส DNA ที่ได้จาก UniProt จะถูกนำไปสร้างเป็น DNA สังเคราะห์ โดยนักชีววิทยาจะออกแบบให้เหมาะสมกับการทำงานในเซลล์ของจุลินทรีย์ ไม่ใช่เซลล์วัว จะเรียกว่านี่คือ “การดัดแปลงบทละครชีวิตของวัว แล้วส่งให้จุลินทรีย์เล่นแทน” ก็ไม่ผิด DNA ที่ออกแบบนี้ มักจะมาพร้อมกับเครื่องมือบางอย่าง เช่น ตัวกระตุ้นการทำงานของยีน (promoter) หรือ ตัวตัดต่อยีน ที่จะทำให้จุลินทรีย์ยอมรับและใช้มันได้อย่างมีประสิทธิภาพ
ขั้นตอนที่ 3: ปลอมตัวแทรกเข้าไปในจุลินทรีย์ จุลินทรีย์ที่ Perfect Day ใช้คือกลุ่มที่เรียกว่า Microflora ซึ่งอาจเป็นยีสต์, เชื้อรา, หรือแบคทีเรียชนิดที่เลี้ยงง่าย แต่มันจะไม่ยอมรับ DNA แปลกปลอมง่าย ๆ ดังนั้นต้องมี “เทคนิคหลอกล่อ” นิดหน่อย เขาจะทำให้ DNA ของจุลินทรีย์ เสียหายตรงจุดหนึ่ง แล้วแอบแนบ DNA ปลอม (ที่มีรหัสโปรตีนของวัว) เข้าไปซ่อมแซมจุดนั้นพอดีเป๊ะ แบบ “จิ๊กซอว์พอดีช่อง” แล้วจุลินทรีย์ก็จะเผลอรับ DNA แปลกปลอมนี้เข้าร่าง เมื่อติดตั้งสำเร็จ มันจะเริ่มแปลรหัสและ “ผลิตโปรตีนเวย์” ออกมาเหมือนกับแม่วัวตัวจริงไม่มีผิด
ขั้นตอนที่ 4: เลี้ยงจุลินทรีย์ในถังหมัก ตอนนี้จุลินทรีย์กลายเป็น “แม่วัวในร่างเซลล์เดียว” แล้ว Perfect Day ก็แค่เลี้ยงมันใน ถังหมักชีวภาพ (fermentor) ที่ควบคุมอุณหภูมิ ค่าความเป็นกรดด่าง อากาศ และใส่น้ำตาลลงไปเป็นอาหาร จุลินทรีย์จะกินน้ำตาลแล้วเปลี่ยนเป็น เวย์โปรตีน ปล่อยออกมานอกเซลล์ จากนั้นก็เก็บเอาน้ำที่มีโปรตีนนี้ ไปผ่านกระบวนการกรอง แยก แปรรูป และทำให้แห้ง เป็นผงเวย์โปรตีน พร้อมใช้ในอาหารหรือเครื่องดื่มต่าง ๆ
ขั้นตอนที่ 5: ตรวจสอบความเหมือนจริง ก่อนนำเวย์โปรตีนที่ได้ไปใช้งาน บริษัทต้อง ตรวจสอบระดับโมเลกุล ว่าโปรตีนที่ได้เหมือนกับของวัวจริง ๆ ไหม? สิ่งที่ต้องดูคือ โครงสร้างโปรตีน: ใช้เทคนิค mass spectrometry ตรวจความแม่นยำระดับกรดอะมิโน พฤติกรรมทางชีวเคมี เช่น ความสามารถในการจับกับน้ำ การเกิดฟอง หรือการละลาย ความปลอดภัย ตรวจหาสารปนเปื้อน สารก่อภูมิแพ้ หรือสารที่ไม่ได้ตั้งใจให้มี Perfect Day เคลมว่าทั้งหมดนี้ปลอดภัย และได้รับการรับรองจาก FDA ว่าเป็น GRAS (Generally Recognized as Safe)
แล้วเราควรรู้สึกยังไง? นี่คือ “นมที่ไม่มีวัว” แต่มีเวย์โปรตีนครบสูตร ทำให้โยเกิร์ต ไอศกรีม และแม้กระทั่งกาแฟลาเต้ที่ไม่มีนมวัว แต่ยังมีฟองนมหนานุ่ม กลายเป็นจริงได้แบบไม่ต้องพึ่งวัวเลยแม้แต่นิดเดียว แต่คำถามที่ลึกกว่านั้นคือ... เรายังได้กินอาหารจากธรรมชาติอยู่หรือเปล่า? หรือกำลังอยู่ในยุคที่ “ชีวิต” ถูกตัดออกจากอาหาร โดยสิ้นเชิง? เทคโนโลยีนี้อาจช่วยโลกในมุมของ ESG แต่สำหรับบางคน มันคือ ทางแยกของความจริงกับของจำลอง คำว่า “Perfect” จึงอาจขึ้นอยู่กับว่า… สมบูรณ์แบบในสายตาใคร?
แล้วคำถามที่ล่องลอยอยู่เสมอคือ เมื่อทางเลือกกลายเป็นทางหลัก แล้วเราจะเหลือทางไหนอีกบ้าง หรือจะเป็น...ทางตัน? #pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก
-
 @ 401014b3:59d5476b
2025-04-22 00:23:24
@ 401014b3:59d5476b
2025-04-22 00:23:24About Me
I come to Nostr with extensive experience in the digital landscape. As a blockchain native since 2017, I've witnessed the evolution of decentralized technologies firsthand. Most of my professional career has been spent working within big tech companies, giving me a unique perspective on both centralized and decentralized systems.
My social media journey began on Twitter in 2007, where I've maintained a presence for over 17 years. I've also explored other decentralized social platforms including BlueSky, Farcaster, and Lens Protocol. As a Bitcoin maximalist, I was particularly intrigued by Nostr's compatibility with the Lightning Network, which initially drew me to the platform.
The Onboarding Challenge
The Nostr onboarding experience presents a significant hurdle for newcomers. Despite my technical background in blockchain technologies, I found the initial setup process more complicated than expected. Understanding public/private key cryptography just to join a social network creates a steeper learning curve than necessary.
BlueSky and Farcaster have demonstrated that it's possible to maintain decentralized principles while providing a more streamlined onboarding experience. Their approaches show that user-friendly design and decentralization aren't mutually exclusive concepts.
Relay Management: Room for Improvement
The concept of relays represents one of Nostr's most distinctive features, though it can be confusing for newcomers. While many clients come pre-configured with default relays, users eventually encounter situations where content or connections seem inconsistent.
When someone I've interacted with doesn't appear in my feed or doesn't respond, I'm often left wondering if we're simply on different relays. This uncertainty creates friction that doesn't exist on other platforms where connectivity is handled behind the scenes.
The relay system introduces a layer of complexity that, while important to Nostr's architecture, could benefit from better abstraction in the user experience. When using BlueSky or Farcaster, I don't need to think about the underlying infrastructure, something Nostr could learn from while maintaining its decentralized principles.
The Zap Economy: Growing Pains
The Lightning-powered zap system shows tremendous potential, but I've observed some concerning economic patterns. Longer-term Nostr users have expressed frustration about continuously sending zaps while seeing limited growth in the overall ecosystem.
Interestingly, there appears to be a connection between this liquidity issue and community growth dynamics. Some established users who voice concerns about bearing the financial burden of the zapping economy are simultaneously less welcoming to newer accounts, rarely following, engaging with, or zapping newcomers.
This creates a challenging environment for new users, who face a cold reception and have little incentive to load their Lightning wallets or participate in the zap economy. Why bring fresh liquidity to a platform where established users rarely engage with your content? This dynamic has limited the expansion of the ecosystem, with the same sats often circulating among established users rather than growing with new participants.
Client Diversity: Strength and Challenge
Nostr's multiple client options offer users choice, which is valuable. However, the implementation of NIPs (Nostr Implementation Possibilities) varies across clients, creating inconsistent experiences. Features that work seamlessly in one client might be implemented differently in another.
This extends to fundamental aspects like search functionality, thread navigation, and notification systems, all of which can differ significantly between clients. For users accustomed to consistent experiences, this fragmentation creates a learning curve with each new client they try.
Lightning Integration: Varying Experiences
The Lightning Network integration varies in quality and user experience across Nostr clients. While the functionality is generally present, the implementation quality, feature set, and ease of use differ depending on which client you choose.
This inconsistency means users may need to experiment with several clients to find one that provides the Lightning experience they're looking for, rather than having a consistent experience across the ecosystem.
Finding Balance
Nostr appears to be navigating the challenge of balancing technical innovation with user experience. While its cryptographic foundation and decentralized architecture are impressive technical achievements, these same strengths sometimes come at the cost of accessibility.
Despite my technical background and interest in decentralized technologies, I find myself using BlueSky and Farcaster more frequently for daily social interactions, while checking Nostr less often. For Nostr to achieve its potential for broader adoption, addressing these user experience considerations while maintaining its core principles will be essential.
The platform has tremendous potential with improvements to user experience, community dynamics, and economic sustainability, Nostr could evolve from a fascinating technical experiment into a truly compelling alternative to mainstream social media.
-
 @ df478568:2a951e67
2025-04-21 23:36:17
@ df478568:2a951e67
2025-04-21 23:36:17Testing
-
 @ d34e832d:383f78d0
2025-04-21 19:09:53
@ d34e832d:383f78d0
2025-04-21 19:09:53Such a transformation positions Nostr to compete with established social networking platforms in terms of reach while simultaneously ensuring the preservation of user sovereignty and the integrity of cryptographic trust mechanisms.

The Emergence of Encrypted Relay-to-Relay Federation
In the context of Nostr protocol scalability challenges pertaining to censorship-resistant networking paradigms, Nostr stands as a paradigm-shifting entity, underpinned by robust public-key cryptography and minimal operational assumptions. This feature set has rendered Nostr an emblematic instrument for overcoming systemic censorship, fostering permissionless content dissemination, and upholding user autonomy within digital environments. However, as the demographic footprint of Nostr's user base grows exponentially, coupled with an expanding range of content modalities, the structural integrity of individual relays faces increasing pressure.
Challenges of Isolation and Limited Scalability in Decentralized Networks
The current architecture of Nostr relays is primarily constituted of simple TCP or WebSocket servers that facilitate the publication and reception of events. While aesthetically simple, this design introduces significant performance bottlenecks and discoverability issues. Relays targeting specific regional or topical niches often rely heavily on client-side interactions or third-party directories for information exchange. This operational framework presents inefficiencies when scaled globally, especially in scenarios requiring high throughput and rapid dissemination of information. Furthermore, it does not adequately account for redundancy and availability, especially in low-bandwidth environments or regions facing strict censorship.

Navigating Impediments of Isolation and Constrained Scalability
Current Nostr relay infrastructures mainly involve basic TCP and WebSocket configurations for event publication and reception. While simple, these configurations contribute to performance bottlenecks and a significant discoverability deficit. Relays that serve niche markets often operate under constraints, relying on client-side interactions or third-party directories. These inefficiencies become particularly problematic at a global scale, where high throughput and rapid information distribution are necessary. The absence of mechanisms to enhance redundancy and availability in environments with limited connectivity or under censorship further exacerbates these issues.
Proposal for Encrypted Relay Federation
Encrypted relay federation in decentralized networking can be achieved through a novel Nostr Improvement Proposal (NIP), which introduces a sophisticated gossip-style mesh topology. In this system, relays subscribe to content tags, message types, or public keys from peer nodes, optimizing data flow and relevance.
Central to this architecture is a mutual key handshake protocol using Elliptic Curve Diffie-Hellman (ECDH) for symmetric encryption over relay keys. This ensures data integrity and confidentiality during transmission. The use of encrypted event bundles, compression, and routing based on relay reputation metrics and content demand analytics enhances throughput and optimizes network resources.
To counter potential abuse and spam, strategies like rate limiting, financially incentivized peering, and token gating are proposed, serving as control mechanisms for network interactions. Additionally, the relay federation model could emulate the Border Gateway Protocol (BGP), allowing for dynamic content advertisement and routing updates across the federated mesh, enhancing network resilience.
Advantages of Relay Federation in Data Distribution Architecture
Relay federation introduces a distributed data load management system where relays selectively store pertinent events. This enhances data retrieval efficiency, minimizes congestion, and fosters a censorship-resistant information flow. By decentralizing data storage, relays contribute to a global cache network, ensuring no single relay holds comprehensive access to all network data. This feature helps preserve the integrity of information flow, making it resistant to censorship.
An additional advantage is offline communication capabilities. Even without traditional internet access, events can still be communicated through alternative channels like Bluetooth, Wi-Fi Direct, or LoRa. This ensures local and community-based interactions remain uninterrupted during network downtime.
Furthermore, relay federations may introduce monetization strategies where specialized relays offer access to rare or high-quality data streams, promoting competition and interoperability while providing users with diverse data options.
Some Notable Markers To Nostr Becoming the Internet Layer for Censorship Resistance
Stop for a moment in your day and try to understand what Nostr can do for your communications by observing these markers:
- Protocol Idea (NIP-01 by fiatjaf) │ ▼
- npub/nsec Keypair Standard │ ▼
- First Relays Go Online │ ▼
- Identity & Auth (NIP-05, NIP-07) │ ▼
- Clients Launch (Damus, Amethyst, Iris, etc.) │ ▼
- Lightning Zaps + NWC (NIP-57) │ ▼
- Relay Moderation & Reputation NIPs │ ▼
- Protocol Bridging (ActivityPub, Matrix, Mastodon) │ ▼
- Ecash Integration (Cashu, Walletless Zaps) │ ▼
- Encrypted Relay Federation (Experimental) │ ▼
- Relay Mesh Networks (WireGuard + libp2p) │ ▼
- IoT Integration (Meshtastic + ESP32) │ ▼
- Fully Decentralized, Censorship-Resistant Social Layer
The implementation of encrypted federation represents a pivotal technological advancement, establishing a robust framework that challenges the prevailing architecture of fragmented social networking ecosystems and monopolistic centralized cloud services. This innovative approach posits that Nostr could:
- Facilitate a comprehensive, globally accessible decentralized index of information, driven fundamentally by user interactions and a novel microtransaction system (zaps), enabling efficient content valorization and information dissemination.
- Empower the concept of nomadic digital identities, allowing them to seamlessly traverse various relays, devoid of reliance on centralized identity verification systems, promoting user autonomy and privacy.
- Become the quintessential backend infrastructure for decentralized applications, knowledge graphs, and expansive datasets conducive to DVMs.
- Achieve seamless interoperability with established protocols, such as ActivityPub, Matrix, IPFS, and innovative eCash systems that offer incentive mechanisms, fostering an integrated and collaborative ecosystem.
In alignment with decentralization, encrypted relay-to-relay federation marks a significant evolution for the Nostr protocol, transitioning from isolated personal broadcasting stations to an interoperable, adaptive, trustless mesh network of communication nodes.
By implementing this sophisticated architecture, Nostr is positioned to scale efficiently, addressing global needs while preserving free speech, privacy, and individual autonomy in a world marked by surveillance and compartmentalized digital environments.
Nostr's Countenance Structure: Noteworthy Events
``` Nostr Protocol Concept by fiatjaf:
- First Relays and npub/nsec key pairs appear
- Damus, Amethyst, and other clients emerge
- Launch of Zaps and Lightning Tip Integration
- Mainstream interest post Twitter censorship events
- Ecosystem tools: NWC, NIP-07, NIP-05 adoption
- Nostr devs propose relay scoring and moderation NIPs
- Bridging begins (ActivityPub, Matrix, Mastodon)
- Cashu eCash integration with Nostr zaps (walletless tips)
- Relay-to-relay encrypted federation proposed
- Hackathons exploring libp2p, LNbits, and eCash-backed identities
- Scalable P2P Mesh using WireGuard + Nostr + Gossip
- Web3 & IoT integration with ESP32 + Meshtastic + relays
- A censorship-resistant, decentralized social internet ```
-
 @ d34e832d:383f78d0
2025-04-21 17:29:37
@ d34e832d:383f78d0
2025-04-21 17:29:37This foundational philosophy positioned her as the principal architect of the climactic finale of the Reconquista—a protracted campaign that sought to reclaim territories under Muslim dominion. Her decisive participation in military operations against the Emirate of Granada not only consummated centuries of Christian reclamation endeavors but also heralded the advent of a transformative epoch in both Spanish and European identity, intertwining religious zeal with nationalistic aspirations and setting the stage for the emergence of a unified Spanish state that would exert significant influence on European dynamics for centuries to come.
Image Above Map Of Th Iberias
During the era of governance overseen by Muhammad XII, historically identified as Boabdil, the Kingdom of Granada was characterized by a pronounced trajectory of decline, beset by significant internal dissent and acute dynastic rivalry, factors that fundamentally undermined its structural integrity. The political landscape of the emirate was marked by fragmentation, most notably illustrated by the contentious relationship between Boabdil and his uncle, the militarily adept El Zagal, whose formidable martial capabilities further exacerbated the emirate's geopolitical vulnerabilities, thereby impairing its capacity to effectively mobilize resistance against the encroaching coalition of Christian forces. Nevertheless, it is imperative to acknowledge the strategic advantages conferred by Granada’s formidable mountainous terrain, coupled with the robust fortifications of its urban centers. This geographical and structural fortitude, augmented by the fervent determination and resilience of the local populace, collectively contributed to Granada's status as a critical and tenacious stronghold of Islamic governance in the broader Iberian Peninsula during this tumultuous epoch.
The military campaign initiated was precipitated by the audacious territorial annexation of Zahara by the Emirate in the annum 1481—a pivotal juncture that served as a catalytic impetus for the martial engagement orchestrated by the Catholic Monarchs, Isabel I of Castile and Ferdinand II of Aragon.

Image Above Monarchs Of Castilles
What subsequently unfolded was an arduous protracted conflict, extending over a decade, characterized by a series of decisive military confrontations—most notably the Battle of Alhama, the skirmishes at Loja and Lucena, the strategic recapture of Zahara, and engagements in Ronda, Málaga, Baza, and Almería. Each of these encounters elucidates the intricate dynamics of military triumph entwined with the perils of adversity. Isabel's role transcended mere symbolic representation; she emerged as an astute logistical architect, meticulously structuring supply chains, provisioning her armies with necessary resources, and advocating for military advancements, including the tactical incorporation of Lombard artillery into the operational theater. Her dual presence—both on the battlefield and within the strategic command—interwove deep-seated piety with formidable power, unifying administrative efficiency with unyielding ambition.
In the face of profound personal adversities, exemplified by the heart-wrenching stillbirth of her progeny amidst the tumultuous electoral campaign, Isabel exhibited a remarkable steadfastness in her quest for triumph. Her strategic leadership catalyzed a transformative evolution in the constructs of monarchical power, ingeniously intertwining the notion of divine right—a historically entrenched justification for sovereign authority—with pragmatic statecraft underpinned by the imperatives of efficacious governance and stringent military discipline. The opposition posed by El Zagal, characterized by his indefatigable efforts and tenacious resistance, elongated the duration of the campaign; however, the indomitable spirit and cohesive resolve of the Catholic Monarchs emerged as an insuperable force, compelling the eventual culmination of their aspirations into a definitive victory.
The capitulation of the Emirate of Granada in the month of January in the year 1492 represents a pivotal moment in the historical continuum of the Iberian Peninsula, transcending the mere conclusion of the protracted series of military engagements known as the Reconquista. This momentous event is emblematic of the intricate process of state-building that led to the establishment of a cohesive Spanish nation-state fundamentally predicated on the precepts of Christian hegemony. Furthermore, it delineates the cusp of an imperial epoch characterized by expansionist ambitions fueled by religious zealotry. The ramifications of this surrender profoundly altered the sociocultural and political framework of the region, precipitating the coerced conversion and expulsion of significant Jewish and Muslim populations—a demographic upheaval that would serve to reinforce the ideological paradigms that underpinned the subsequent institution of the Spanish Inquisition, a systematic apparatus of religious persecution aimed at maintaining ideological conformity and unity under the Catholic Monarchs.

Image Above Surrender At Granada
In a broader historical context, the capitulation of the Nasrid Kingdom of Granada transpired concurrently with the inaugural expedition undertaken by the navigator Christopher Columbus, both events being facilitated under the auspices of Queen Isabel I of Castile. This significant temporal nexus serves to underscore the confluence of the termination of Islamic hegemony in the Iberian Peninsula with the commencement of European maritime exploration on a grand scale. Such a juxtaposition of religiously motivated conquest and the zealous pursuit of transoceanic exploration precipitated a paradigm shift in the trajectory of global history. It catalyzed the ascendance of the Spanish Empire, thereby marking the nascent stages of European colonial endeavors throughout the Americas.

Image Above Columbus At The Spanish Court
This epochal transformation not only redefined territorial dominion but also initiated profound socio-economic and cultural repercussions across continents, forever altering the intricate tapestry of human civilization.
Consequently, the cessation of hostilities in Granada should not merely be interpreted as the conclusion of a protracted medieval conflict; rather, it represents a critical juncture that fundamentally reoriented the socio-political landscape of the Old World while concurrently heralding the advent of modernity. The pivotal contributions of Queen Isabel I in this transformative epoch position her as an extraordinarily significant historical figure—an autocrat whose strategic foresight, resilience, and zeal indelibly influenced the trajectory of nations and entire continents across the globe.
-
 @ e97aaffa:2ebd765d
2025-04-21 12:57:16
@ e97aaffa:2ebd765d
2025-04-21 12:57:16Se este movimento de desglobalização continuar, poderá provocar uma cisão no mundo geopolítico, criar dois grandes blocos económicos, uma nova guerra fria.
Se isso se concretizar, quantos anos vão ser necessários para o S&P500 superar máximos históricos em termos reais, em poder de compra?
Em valores nominais vai ser rápido, o governo dos EUA vai imprimir tanto dinheiro, rapidamente vai superar máximos, mas em termos reais, vai demorar muitos anos.
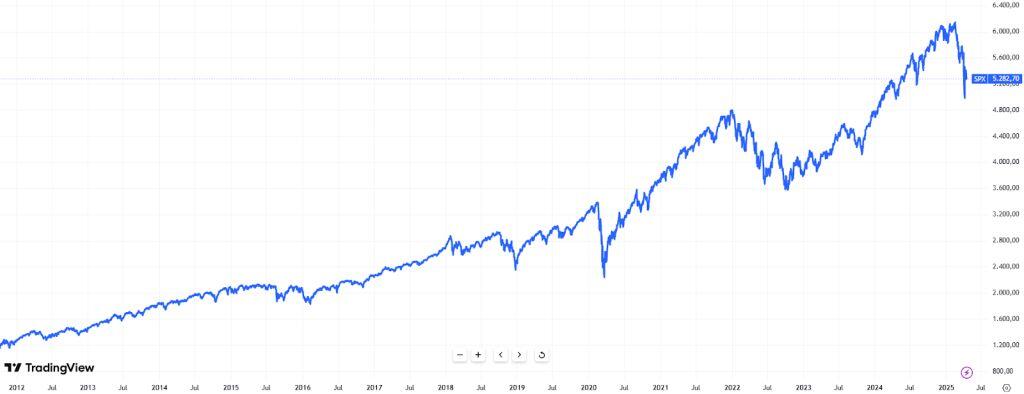
Até agora, todo o mundo estava a investir nos EUA, mas se os países do bloco oriental, sobretudo a China, deixarem de investir em ações, obrigações e moeda dos EUA, irá provocar uma enorme redução de liquidez e na procura/demanda, não vai ser fácil ultrapassar isso.
Nos US Treasury, o afastamento da China começou em 2014(1° guerra da Ucrânia), mas o movimento acelerou em 2022(2° guerra da Ucrânia).

Os EUA, ao congelar as reservas da Rússia, ao utilizar as reservas como uma arma de guerra, “assustaram” a China e outros países. As sanções à Rússia e como esta fez para contornar as sanções foi um case study para a China.
Como o objetivo da China é recuperar Taiwan, sabe que sofrerá as mesmas represálias que hoje a Rússia sofre, por isso a China tem que se afastar da economia dos EUA.
A China está a trocar US Treasury por outros ativos e por outras geografias, o principal beneficiado foi o ouro, um ativo soberano, que não tem problemas de contraparte.
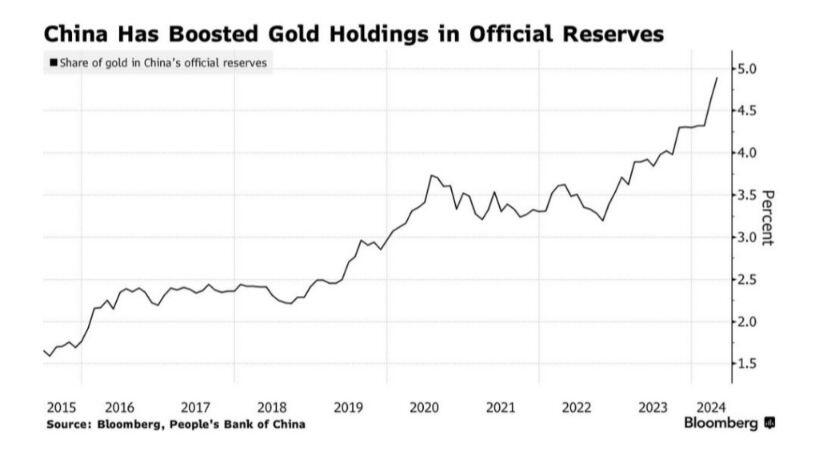
Este movimento da China foi bem visível no preço do ouro no último ano, uma valorização superior a 42%.
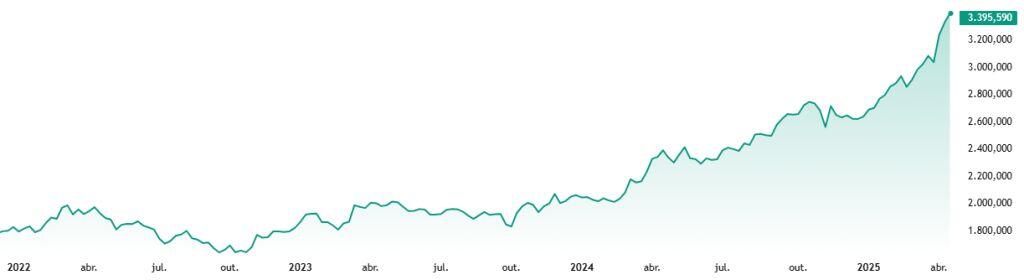
Mas não é só a China que está a apostar no ouro, são diversos, mas sobretudo composta por países do bloco oriental.
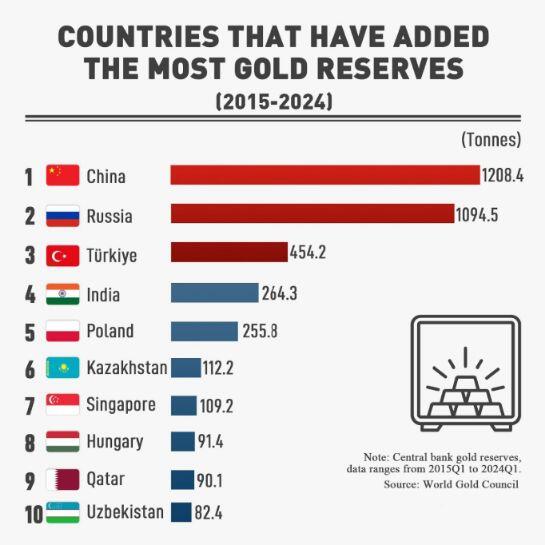
Enquanto, Taiwan for a fábrica do mundo nos semicondutores, estarão protegidos pelo guarda-chuva dos EUA. Mas os EUA, estão a construir fábricas próprias, quando forem auto-suficientes, vão descartar o “guarda-chuva”, Taiwan não terá qualquer hipótese sobre o poderio da China.
A China pensa sempre a longo prazo, estão apenas a aguardar, isto poderá estar para muito em breve.
Se isto se confirmar, o S&P500 poderá demorar décadas para recuperar desta crise, em termos de poder de compra.
-
 @ d34e832d:383f78d0
2025-04-21 08:32:02
@ d34e832d:383f78d0
2025-04-21 08:32:02The operational landscape for Nostr relay operators is fraught with multifaceted challenges that not only pertain to technical feasibility but also address pivotal economic realities in an increasingly censored digital environment.
While the infrastructure required to run a Nostr relay can be considered comparatively lightweight in terms of hardware demands, the operators must navigate a spectrum of operational hurdles and associated costs. Key among these are bandwidth allocation, effective spam mitigation, comprehensive security protocols, and the critical need for sustained uptime.
To ensure economic viability amidst these challenges, many relay operators have implemented various strategies, including the introduction of rate limiting mechanisms and subscription-based financial models that leverage user payments to subsidize operational costs. The conundrum remains: how can the Nostr framework evolve to permit relay operators to cultivate at least a singular relay to its fullest operational efficiency?
It is essential to note that while the trajectory of user engagement with these relays remains profoundly unpredictable—analogous to the nebulous impetus behind their initial inception—indicators within our broader economic and sociocultural contexts illuminate potential pathways to harmonizing commercial interests with user interaction through the robust capabilities of websocket relays.
A few musingsI beg you to think about the Evolutionary Trajectory of Nostr Infrastructure Leveraging BDK (Bitcoin Development Kit) and NDK (Nostr Development Kit) in the Context of Sovereign Communication Infrastructure
As the Nostr ecosystem transitions through its iterative phases of maturity, the infrastructure, notably the relays, is projected to undergo significant enhancements to accommodate an array of emerging protocols, particularly highlighted by the Mostr Bridge implementation.
Additionally, the integration of decentralized identity frameworks, exemplified by PKARR (Public-Key Addressable Resource Records), signifies a robust evolutionary step towards fostering user accountability and autonomy.
Moreover, the introduction of sophisticated filtering mechanisms, including but not limited to Set Based Reconciliation techniques, seeks to refine the user interface by enabling more granular control over content visibility and interaction dynamics.
These progressive innovations are meticulously designed to augment the overall user experience while steadfastly adhering to the foundational ethos of the Nostr protocol, which emphasizes the principles of digital freedom, uncurtailed access to publication, and the establishment of a harassment-free digital environment devoid of shadowbanning practices.
Such advancements underscore the balancing act between technological progression and ethical considerations in decentralized communication frameworks.
-
 @ d34e832d:383f78d0
2025-04-21 08:08:49
@ d34e832d:383f78d0
2025-04-21 08:08:49Let’s break it down.
🎭 The Cultural Love for Hype
Trinidadians are no strangers to investing. We invest in pyramid schemes, blessing circles, overpriced insurance packages, corrupt ministries, miracle crusades, and football teams that haven’t kicked a ball in years. Anything wrapped in emotion, religion, or political flag-waving gets support—no questions asked.
Bitcoin, on the other hand, demands research, self-custody, and personal responsibility. That’s not sexy in a culture where people would rather “leave it to God,” “vote them out,” or “put some pressure on the boss man.”
🧠 The Mindset Gap
There’s a deep psychological barrier here:
Fear of responsibility: Bitcoin doesn’t come with customer service. It puts you in control—and that scares people used to blaming the bank, the government, or the devil.
Love for middlemen: Whether it’s pastors, politicians, or financiers, Trinidad loves an “intercessor.” Bitcoin removes them all.
Resistance to abstraction: We’re tactile people. We want paper receipts, printed statements, and "real money." Bitcoin’s digital nature makes it feel unreal—despite being harder money than the TT dollar will ever be.
🔥 What Gets Us Excited
Let a pastor say God told him to buy a jet—people pledge money.
Let a politician promise a ghost job—people campaign.
Let a friend say he knows a man that can flip $100 into $500—people sign up.
But tell someone to download a Bitcoin wallet, learn about self-custody, and opt out of inflation?
They tell you that’s a scam.
⚖️ The Harsh Reality
Trinidad is on the brink of a currency crisis. The TT dollar is quietly bleeding value. Bank fees rise, foreign exchange is a riddle, and financial surveillance is tightening.
Bitcoin is an escape hatch—but it requires a new kind of mindset: one rooted in self-education, long-term thinking, and personal accountability. These aren’t values we currently celebrate—but they are values we desperately need.
🟠 A Guide to Starting with Bitcoin in Trinidad
- Understand Bitcoin
It’s not a stock or company. It’s a decentralized protocol like email—but for money.
It’s finite. Only 21 million will ever exist.
It’s permissionless. No bank, government, or pastor can block your access.
- Get a Wallet
Start with Phoenix Wallet or Blue Wallet (for Lightning).
If you're going offline, learn about SeedSigner or Trezor for cold storage.
- Earn or Buy BTC
Use Robosats or Peach for peer-to-peer (P2P) trading.
Ask your clients to pay in Bitcoin.
Zap content on Nostr to earn sats.
- Secure It
Learn about seed phrases, hardware wallets, and multisig options.
Never leave your coins on exchanges.
Consider a steel backup plate.
- Use It
Pay others in BTC.
Accept BTC for services.
Donate to freedom tech projects or communities building open internet tools.
🧭 Case In Point
Bitcoin isn’t just technology. It’s a mirror—one that reveals who we really are. Trinidad isn’t slow to adopt Bitcoin because it’s hard. We’re slow because we don’t want to let go of the comfort of being misled.
But times are changing. And the first person to wake up usually ends up leading the others.
So maybe it’s time.
Maybe you are the one to bring Bitcoin to Trinidad—not by shouting, but by living it.
-
 @ d34e832d:383f78d0
2025-04-21 07:31:10
@ d34e832d:383f78d0
2025-04-21 07:31:10The inherent heterogeneity of relay types within this ecosystem not only enhances operational agility but also significantly contributes to the overall robustness and resilience of the network architecture, empowering it to endure systemic assaults or coordinated initiatives designed to suppress specific content.
In examining the technical underpinnings of the Nostr protocol, relays are characterized by their exceptional adaptability, permitting deployment across an extensive variety of hosting environments configured to achieve targeted operational objectives.
For example, strategically deploying relays in jurisdictions characterized by robust legal protections for free expression can provide effective countermeasures against local censorship and pervasive legal restrictions in regions plagued by oppressive control.
This strategic operational framework mirrors the approaches adopted by whistleblowers and activists who deliberately position their digital platforms or mirrored content within territories boasting more favorable regulatory environments regarding internet freedoms.
Alternatively, relays may also be meticulously configured to operate exclusively within offline contexts—functioning within localized area networks or leveraging air-gapped computational configurations.
Such offline relays are indispensable in scenarios necessitating disaster recovery, secure communication frameworks, or methods for grassroots documentation, thereby safeguarding sensitive data from unauthorized access, ensuring its integrity against tampering, and preserving resilience in the face of both potential disruptions in internet connectivity and overarching surveillance efforts.
-
 @ 866e0139:6a9334e5
2025-04-23 18:44:08
@ 866e0139:6a9334e5
2025-04-23 18:44:08Autor: René Boyke. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Das völkerrechtliche Gewaltverbot ist das völkerrechtliche Pendant zum nationalen Gewaltmonopol. Bürgern ist die Ausübung von Gewalt nur unter engen Voraussetzungen erlaubt, ähnlich sieht es das Völkerrecht für Staaten vor. Das völkerrechtliche Gewaltverbot gemäß Art. 2 Abs. 4 der VN-Charta ist damit eines der fundamentalsten Prinzipien des modernen Völkerrechts. Ein echtes Gewaltmonopol, wie es innerhalb eines Staates existiert, besteht auf internationaler Ebene allerdings nicht, denn dies kann rein faktisch – zumindest derzeit noch – nur sehr schwer bzw. gar nicht umgesetzt werden.
Das Verbot von Gewalt ist eine Sache, aber wer sollte bei einem Verstoß Polizei spielen dürfen? Das Gewaltverbot verbietet den Staaten die Androhung oder Anwendung von Gewalt gegen die territoriale Integrität oder politische Unabhängigkeit eines anderen Staates. Obwohl 193 und damit fast alle Staaten Mitglied der Vereinten Nationen sind, kann man ganz und gar nicht davon sprechen, dass das Gewaltverbot Kriege beseitigt hätte. Nüchtern betrachtet liegt seine Funktion daher nicht in der Verhinderung von Kriegen, sondern in der Legitimation rechtlicher Konsequenzen: Wer gegen das Verbot verstößt, ist im Unrecht und muss die entsprechenden Konsequenzen tragen. Die Reichweite des Gewaltverbots wirft zahlreiche Fragen auf. Diesen widmet sich der vorliegende Beitrag überblicksartig.
Historische Entwicklung des Gewaltverbots
Vor dem 20. Jahrhundert war das „Recht zum Krieg“ (ius ad bellum) weitgehend unreguliert; Staaten konnten aus nahezu beliebigen Gründen zu den Waffen greifen, ja, Krieg galt zwar nicht ausdrücklich als erlaubt, aber eben auch nicht als verboten. Mit dem Briand-Kellogg-Pakt von 1928 wurde rechtlich betrachtet ein weitgehendes Gewaltverbot erreicht. Doch statt warmer Worte hat der Pakt nicht viel erreicht. Deutschland war bereits damals und ist noch immer Mitglied des Pakts, doch weder den Zweiten Weltkrieg noch unzählige andere Kriege hat der Pakt nicht verhindern können.
Ein gewisser Paradigmenwechsel erfolgte nach dem zweiten Weltkrieg mit der Gründung der Vereinten Nationen 1945 und der VN-Charta, welche ein umfassendes Gewaltverbot mit nur wenigen Ausnahmen etablierte. Das Gewaltverbot wurde im Laufe der Zeit durch Gewohnheitsrecht und zahlreiche Resolutionen der Vereinten Nationen gefestigt und gilt heute als „jus cogens“, also als zwingendes Völkerrecht, von dem nur wenige Abweichung zulässig sind. Es ist jedoch leider festzustellen, dass nicht die Einhaltung des Gewaltverbots die Regel ist, sondern dessen Bruch. Nicht wenige Völkerrechtler halten das Gewaltverbot daher für tot. In der deutschen völkerrechtlichen Literatur stemmt man sich jedoch gegen diese Einsicht und argumentiert, dass es zwar Brüche des Gewaltverbots gebe, aber jeder rechtsbrüchige Staat versuche hervorzuheben, dass seine Gewaltanwendung doch ausnahmsweise erlaubt gewesen sei, was also bedeute, dass das Gewaltverbot anerkannt sei.
Dass dies lediglich vorgeschobene Lippenbekenntnisse, taktische Ausreden bzw. inszenierte Theaterstücke sind und damit eine Verhöhnung und gerade keine Anerkennung des Gewaltverbots, wird offenbar nicht ernsthaft in Betracht gezogen. Betrachtet man das von den USA 2003 inszenierte Theaterstück, die Erfindung der „weapons of mass destruction,“ um einen Vorwand zum Angriff des Irak zu schaffen, dann ist erstaunlich, wie man zu der Ansicht gelangen kann, die USA sähen ein Gewaltverbot für sich als bindend an.
Wenn das Gewaltverbot schon nicht in der Lage ist, Kriege zu verhindern, so ist es dennoch Gegenstand rechtlicher Konsequenzen, insbesondere nach Beendigung bewaffneter Auseinandersetzungen. Zudem legt die Beachtung oder Nichtbeachtung des Gebots offen, welcher Staat es damit tatsächlich ernst meint und welcher nicht. Dazu muss man jedoch den Inhalt des Gebots kennen, weshalb sich eine Beschäftigung damit lohnt.
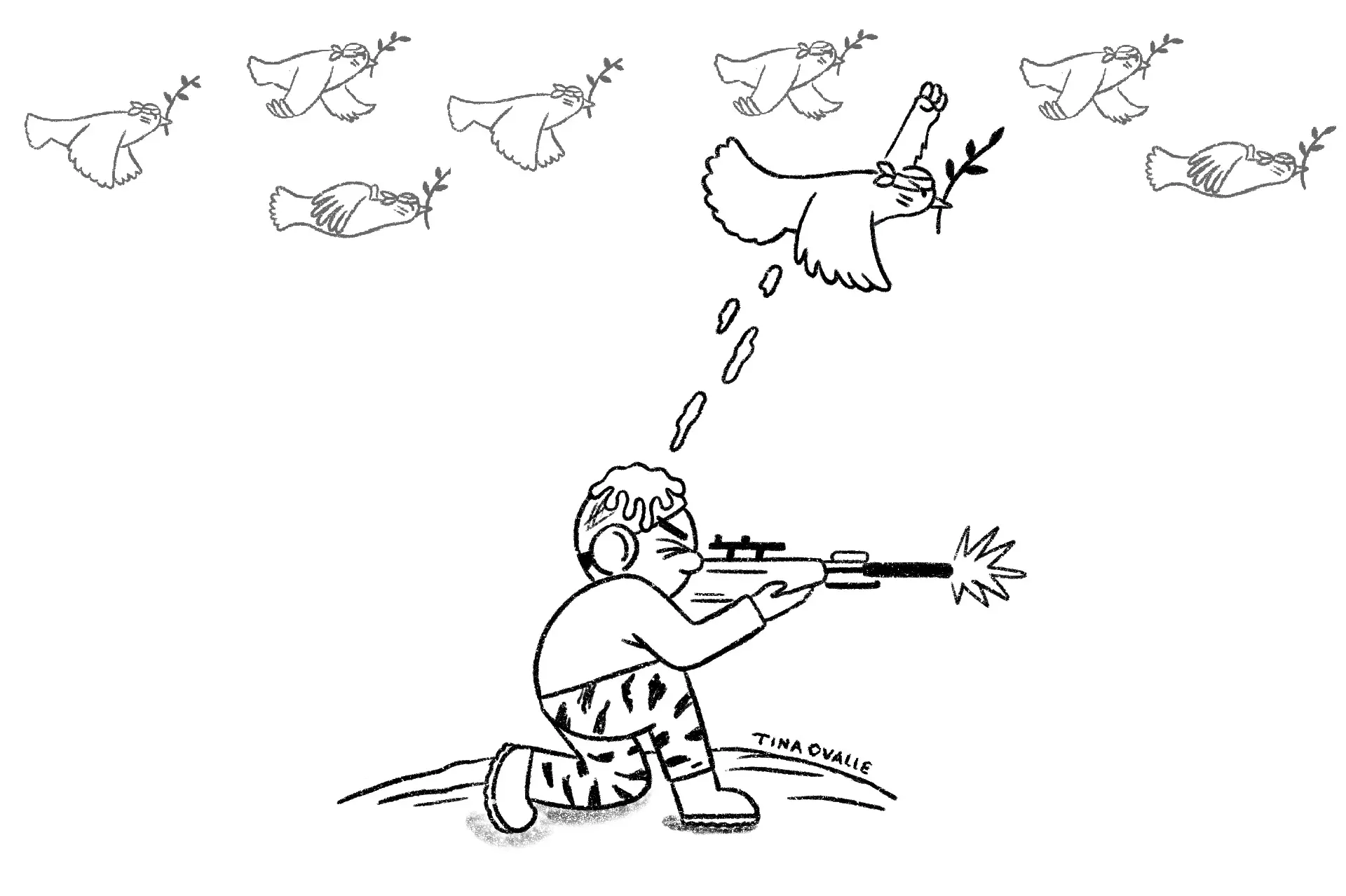
Rechtliche Grundlagen des Gewaltverbots
Das Gewaltverbot gilt nur für Gewalt zwischen Staaten, nicht für private Akte, es sei denn, diese sind einem Staat zurechenbar (z. B. durch Unterstützung wie Waffenlieferungen).
Terrorismus wird nicht automatisch als Verletzung des Gewaltverbots gewertet, sondern als Friedensbedrohung, die andere völkerrechtliche Regeln auslöst. Bei Cyberangriffen ist die Zurechnung schwierig, da die Herkunft oft unklar ist und Sorgfaltspflichten eines Staates nicht zwangsläufig eine Gewaltverletzung bedeuten. Das Verbot umfasst sowohl offene militärische Gewalt (z. B. Einmarsch) als auch verdeckte Gewalt (z. B. Subversion). Es gibt jedoch Diskussionen über eine notwendige Gewaltintensität: Kleinere Grenzverletzungen fallen oft nicht darunter, die Schwelle ist aber niedrig. Nicht jede Verletzung des Gewaltverbots gilt als bewaffneter Angriff.
Nicht-militärische Einwirkungen wie wirtschaftlicher Druck oder Umweltverschmutzung gelten nicht als Gewalt im Sinne des Verbots. Entscheidend ist, dass die Schadenswirkung militärischer Gewalt entspricht, was z. B. bei Cyberangriffen relevant wird, die kritische Infrastruktur lahmlegen.
Ausnahmen vom Gewaltverbot
Trotz Reichweite des Gewaltverbots existieren anerkannte Ausnahmen, die unter bestimmten Umständen die Anwendung von Gewalt legitimieren:
- Recht auf Selbstverteidigung (Art. 51 VN-Charta): Staaten dürfen sich gegen einen bewaffneten Angriff verteidigen, bis der VN- Sicherheitsrat die notwendigen Maßnahmen zur Wiederherstellung des Friedens ergriffen hat. Diese Selbstverteidigung kann individuell (der angegriffene Staat wehrt sich selbst) oder kollektiv (ein anderer Staat kommt dem angegriffenen Staat zur Hilfe) ausgeübt werden. Ob eine Selbstverteidigung zulässig ist, hängt folglich in erster Linie davon ab, ob ein bewaffneter Angriff vorliegt. Nach der Rechtsprechung des IGH setzt ein bewaffneter Angriff eine Mindestintensität voraus, also schwerwiegende Gewalt und nicht lediglich Grenzzwischenfälle. Ferner muss es sich um einen gegenwärtigen Angriff handeln, was präventive Selbstverteidigung grundsätzlich ausschließt – was nicht bedeutet, dass sie nicht ausgeführt würde (siehe Irak- Krieg 2003). Zudem muss der Angriff von einem Staat ausgehen oder ihm zumindest zurechenbar sein. Schließlich muss der Angriff sich gegen die territoriale Integrität, politische Unabhängigkeit oder staatliche Infrastruktur eines Staates richten, wobei Angriffe auf Flugzeuge oder Schiffe außerhalb seines Territoriums ausreichend sind. Maßnahmen des VN-Sicherheitsrats (Kapitel VII VN-Charta): Der Sicherheitsrat kann bei Vorliegen einer Bedrohung oder eines Bruchs des Friedens oder einer Angriffshandlung Zwangsmaßnahmen beschließen, die auch den Einsatz militärischer Gewalt umfassen können. Diese Ausnahmen sind eng gefasst und unterliegen strengen Voraussetzungen, um Missbrauch zu verhindern.
Neben diesen anerkannten Ausnahmen vom Gewaltverbot wird weiter diskutiert, ob es weitere Ausnahmen vom Gewaltverbot gibt, insbesondere in Fällen humanitärer Interventionen und Präventivschläge.
-
Humanitäre Interventionen: Verübt ein Staat gegen einen Teil seiner Bevölkerung schwere Verbrechen wie Völkermord oder Kriegsverbrechen, so sehen einige ein fremdes Eingreifen ohne VN-Mandat als gerechtfertigt an. Das Europäische Parlament beispielsweise hat humanitäre Interventionen bereits 1994 für zulässig erklärt.1 Ein Beispiel dafür ist der NATO-Einsatz im Kosovo 1999, der jedoch überwiegend als völkerrechtswidrig bewertet wird, während NATO-Staaten ihn jedoch als moralisch gerechtfertigt betrachteten. Wie wenig allerdings eine humanitäre Intervention als Ausnahme vom Gewaltverbot anerkannt ist, zeigt der Ukrainekrieg, speziell seit dem massiven Einschreiten Russlands 2022, welches sich ebenfalls auf humanitäre Gründe beruft, damit jedoch – zumindest bei den NATO-Staaten – kein Gehör findet. Gegen „humanitäre Interventionen“ als Ausnahmen vom Gewaltverbot sprechen nicht nur deren mangelnde Kodifikation oder gewohnheitsrechtliche Etablierung, sondern auch ganz praktische Probleme: Wie beispielsweise kann ein eingreifender Staat sich sicher sein, ob innerstaatliche Gewalthandlungen Menschenrechtsverletzungen darstellen oder gerechtfertigtes Vorgehen gegen beispielsweise aus dem Ausland finanzierte Terroristen? Zudem besteht die Gefahr, dass bewusst derartige Verhältnisse in einem Land geschaffen werden, um einen Vorwand für ein militärisches Eingreifen zu schaffen. Dieses erhebliche Missbrauchspotential spricht gegen die Anerkennung humanitärer Interventionen als Ausnahme vom Gewaltverbot.
-
Schutz eigener Staatsangehöriger im Ausland: Auch der Schutz eigener Staatsangehöriger im Ausland wird als gerechtfertigte Ausnahme vom Gewaltverbot diskutiert, sie ist allerdings keineswegs allgemein anerkannt. Mit Blick in die Vergangenheit und den gemachten Erfahrungen (z.B. US-Interventionen in Grenada 1983 und Panama 1989) wird vor dem erheblichen Missbrauchspotential gewarnt.
-
Präventivschläge: Wie bereits erwähnt, werden präventive Angriffe auf einen Staat von einigen als Unterfall der Selbstverteidigung als berechtigte Ausnahme vom Gewaltverbot betrachtet. lediglich eine kurze Zeitspanne zur Ausschaltung der Bedrohung bestehen und das Ausmaß des zu erwartenden Schadens berücksichtigt werden. Zu beachten ist dabei, dass die genannten Kriterien dabei in Wechselwirkung stünden, was bedeute: Selbst wenn ein Angriff gar nicht so sehr wahrscheinlich sei, so solle dies dennoch einen Präventivschlag rechtfertigen, falls der zu erwartende Schaden groß sei und in einem kurzen Zeitfenster erfolgen könne (z.B. Atomschlag). Mit anderen Worten: Die Befürwortung von Präventivschlägen weicht das Gewaltverbot auf und führt zu einer leichteren Rechtfertigung militärischer Einsätze. Die konkreten Auswirkungen lassen sich sowohl durch den völkerrechtswidrigen Angriff der USA gegen den Irak und später durch den völkerrechtswidrigen Angriff Russlands gegen die Ukraine betrachten – beide Staaten beriefen sich jeweils auf Präventivschläge.
Konsequenzen der Verletzung des Gewaltverbots
Aus dem Vorstehenden ergibt sich bereits, dass eine Verletzung des Gewaltverbots das Recht zur Selbstverteidigung auslöst. Doch gibt es noch weitere Konsequenzen? Blickt man auf die Menge der weltweiten bewaffneten Konflikte, darf man daran zweifeln. Jedenfalls scheint das Kosten-Nutzen-Verhältnis nicht gegen eine bewaffnete Auseinandersetzung zu sprechen. Wie bereits erwähnt, existiert auf internationaler Ebene kein dem innerstaatlichen Recht vergleichbares Gewaltmonopol. Ohne dies bewerten zu wollen, lässt sich ganz objektiv feststellen, dass es keine Instanz gibt, die Zwangsmaßnahmen effektiv durchsetzen könnte. Ob dies wünschenswert wäre, darf bezweifelt werden. Aus den bisherigen Ausführungen geht ebenfalls hervor, dass der Sicherheitsrat der Vereinten Nationen Maßnahmen ergreifen kann – einschließlich des Einsatzes militärischer Gewalt. Wenn es dazu kommt, dann ist dies eines der schärfsten Schwerter, die gegen eine Verletzung des Gewaltverbots geführt werden können, weil es sich um unmittelbare Zwangsmaßnahmen handelt. Allerdings kam es bisher lediglich zwei Mal dazu (Koreakrieg 1950-19534; Golkrieg II 19915). Neben diesen tatsächlichen Zwangsmaßnahmen hat ein Verstoß gegen das Gewaltverbot rechtliche Auswirkungen:
-
Nichtigkeit von Verträgen: Gemäß Art. 52 der Wiener Vertragsrechtskonvention (WVK) ist ein Vertrag nichtig, wenn sein Abschluss durch Androhung oder Anwendung von Gewalt unter Verletzung der in der Charta der Vereinten Nationen niedergelegten Grundsätze des Völkerrechts herbeigeführt wurde.
-
Nichtanerkennung von Gebietserwerben (Stimson-Doktrin): Gemäß dem Rechtsgedanken des Art. 52 WVK werden die eroberten Gebiete nicht als Staatsgebiete des Staats angesehen, der sie unter Brechung des Gewaltverbots erobert hat.
-
Strafrechtliche Verantwortlichkeit für Staatschefs und Befehlshaber gemäß Art. 8bis des Statuts des Internationalen Strafgerichtshofs – allerdings nur für die Personen, deren Staaten, den IStGH anerkennen. Nichts zu befürchten haben also Staatschefs und Befehlshaber der USA, Russlands oder Chinas sowie Frankreichs und Großbritanniens, denn diese Staaten haben der Ahnung der Verletzung des Gewaltverbots nicht zugestimmt. Zwar könnte der Sicherheitsrat der VN eine Überweisung an den IStGH beschließen, allerdings stünde jedem der genannten Staaten ein Vetorecht dagegen zu.
Schlussfolgerungen
Ein Verbot der Gewalt zwischen Staaten ist grundsätzlich zu begrüßen. Doch ein Verbot allein ist erstmal nicht mehr als bedrucktes Papier. Ob hingegen wirksamere Mechanismen geschaffen werden sollten, dieses Verbot zu ahnden ist zweifelhaft. Denn stets wurde und wird noch immer mit erheblichem Aufwand für unterschiedlichste Narrative die eigene Intervention als „gerechter Krieg“ verkauft und von der Gegenpartei als ebenso ungerecht verteufelt.
Tatsache ist: Einen gerechten Krieg gibt es nicht. Ein schärferer Mechanismus zur Durchsetzung des Gewaltverbots würde genau darauf – einen angeblich gerechten Krieg – hinauslaufen, was ein enormes Missbrauchspotential mit sich brächte. Und die Erfahrung zeigt, dass der Missbrauch des Völkerrechts und Verstöße gegen das Völkerrecht keineswegs die Ausnahme, sondern die Regel darstellen – leider auch durch die sogenannte „westliche Wertegemeinschaft“. Und würde diese Missbrauchsmöglichkeit nicht auf noch mehr militärische Auseinandersetzungen hinauslaufen? Auseinandersetzungen, deren Folgen nicht die verantwortlichen Politiker zu spüren bekämen, sondern, in Form von Tod und Verstümmelung, die Bevölkerung zu tragen hätte?
Leidtragende ihrer „gerechten Kriege“ sind nicht die agierenden Politiker, sondern immer die einfachen Menschen – die leider nicht selten zuvor mit „Hurra“-Geschrei dem Krieg entgegenfiebern, um als „Helden“ ihrem Land zu „dienen“. In Wahrheit dienen sie jedoch nur finanziellen Interessen reicher Menschen.
Daraus folgt, dass die Durchsetzung eines Gewaltverbots nicht in den Händen einiger weniger Staatslenker und Berufspolitiker liegen darf, sondern in den Händen der unmittelbar Betroffenen selbst. Der Familienvater, der für seine Frau und Kinder zu sorgen hat, muss aktiv den Dienst an der Waffe verweigern. Ebenso der Schüler, der Student, der Junggeselle und sämtliche Mitglieder der Gesellschaft. Die Bevölkerung ist es, die das Gewaltverbot tatsächlich und effektiv vom bedruckten Papier als ein Friedensgebot ins Leben bringen und in Vollzug setzen kann.
(Dieser Artikel ist auch mit folgendem Kurzlink aufrufbar und teilbar)
-
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 90de72b7:8f68fdc0
2025-04-23 18:08:45
@ 90de72b7:8f68fdc0
2025-04-23 18:08:45Traffic Light Control System - sbykov
This Petri net represents a traffic control protocol ensuring that two traffic lights alternate safely and are never both green at the same time. Upd
petrinet ;start () -> greenLight1 redLight2 ;toRed1 greenLight1 -> queue redLight1 ;toGreen2 redLight2 queue -> greenLight2 ;toGreen1 queue redLight1 -> greenLight1 ;toRed2 greenLight2 -> redLight2 queue ;stop redLight1 queue redLight2 -> () -
 @ 1e109a31:62807940
2025-04-23 18:04:51
@ 1e109a31:62807940
2025-04-23 18:04:51Sergey activity 1
This template is just for demo needs. Upd1
petrinet ;startDay () -> working ;stopDay working -> () ;startPause working -> paused ;endPause paused -> working ;goSmoke working -> smoking ;endSmoke smoking -> working ;startEating working -> eating ;stopEating eating -> working ;startCall working -> onCall ;endCall onCall -> working ;startMeeting working -> inMeetinga ;endMeeting inMeeting -> working ;logTask working -> working -
 @ d34e832d:383f78d0
2025-04-21 02:36:32
@ d34e832d:383f78d0
2025-04-21 02:36:32Lister.lol represents a sophisticated web application engineered specifically for the administration and management of Nostr lists. This feature is intrinsically embedded within the Nostr protocol, facilitating users in the curation of personalized feeds and the exploration of novel content. Although its current functionality remains relatively rudimentary, the platform encapsulates substantial potential for enhanced collaborative list management, as well as seamless integration with disparate client applications, effectively functioning as a micro-app within the broader ecosystem.
The trajectory of Nostr is oriented towards the development of robust developer tools (namely, the Nostr Development Kit - NDK), the establishment of comprehensive educational resources, and the cultivation of a dynamic and engaged community of developers and builders.
The overarching strategy emphasizes a decentralized paradigm, prioritizing the growth of small-scale, sustainable enterprises over the dominance of large, centralized corporations. In this regard, a rigorous experimentation with diverse monetization frameworks and the establishment of straightforward, user-friendly applications are deemed critical for the sustained evolution and scalability of the Nostr platform.
 Nostr's commitment to a decentralized, 'nagar-style' model of development distinguishes it markedly from the more conventional 'cathedral' methodologies employed by other platforms. As it fosters a broad spectrum of developmental outcomes while inherently embracing the properties of emergence. Such principles stand in stark contrast to within a traditional environment, centralized Web2 startup ecosystem, which is why all people need a chance to develop a significant shift towards a more adaptive and responsive design philosophy in involving #Nostr and #Bitcoin.
Nostr's commitment to a decentralized, 'nagar-style' model of development distinguishes it markedly from the more conventional 'cathedral' methodologies employed by other platforms. As it fosters a broad spectrum of developmental outcomes while inherently embracing the properties of emergence. Such principles stand in stark contrast to within a traditional environment, centralized Web2 startup ecosystem, which is why all people need a chance to develop a significant shift towards a more adaptive and responsive design philosophy in involving #Nostr and #Bitcoin. -
 @ 4ba8e86d:89d32de4
2025-04-21 02:13:56
@ 4ba8e86d:89d32de4
2025-04-21 02:13:56Tutorial feito por nostr:nostr:npub1rc56x0ek0dd303eph523g3chm0wmrs5wdk6vs0ehd0m5fn8t7y4sqra3tk poste original abaixo:
Parte 1 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/263585/tutorial-debloat-de-celulares-android-via-adb-parte-1
Parte 2 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/index.php/263586/tutorial-debloat-de-celulares-android-via-adb-parte-2
Quando o assunto é privacidade em celulares, uma das medidas comumente mencionadas é a remoção de bloatwares do dispositivo, também chamado de debloat. O meio mais eficiente para isso sem dúvidas é a troca de sistema operacional. Custom Rom’s como LineageOS, GrapheneOS, Iodé, CalyxOS, etc, já são bastante enxutos nesse quesito, principalmente quanto não é instalado os G-Apps com o sistema. No entanto, essa prática pode acabar resultando em problemas indesejados como a perca de funções do dispositivo, e até mesmo incompatibilidade com apps bancários, tornando este método mais atrativo para quem possui mais de um dispositivo e separando um apenas para privacidade. Pensando nisso, pessoas que possuem apenas um único dispositivo móvel, que são necessitadas desses apps ou funções, mas, ao mesmo tempo, tem essa visão em prol da privacidade, buscam por um meio-termo entre manter a Stock rom, e não ter seus dados coletados por esses bloatwares. Felizmente, a remoção de bloatwares é possível e pode ser realizada via root, ou mais da maneira que este artigo irá tratar, via adb.
O que são bloatwares?
Bloatware é a junção das palavras bloat (inchar) + software (programa), ou seja, um bloatware é basicamente um programa inútil ou facilmente substituível — colocado em seu dispositivo previamente pela fabricante e operadora — que está no seu dispositivo apenas ocupando espaço de armazenamento, consumindo memória RAM e pior, coletando seus dados e enviando para servidores externos, além de serem mais pontos de vulnerabilidades.
O que é o adb?
O Android Debug Brigde, ou apenas adb, é uma ferramenta que se utiliza das permissões de usuário shell e permite o envio de comandos vindo de um computador para um dispositivo Android exigindo apenas que a depuração USB esteja ativa, mas também pode ser usada diretamente no celular a partir do Android 11, com o uso do Termux e a depuração sem fio (ou depuração wifi). A ferramenta funciona normalmente em dispositivos sem root, e também funciona caso o celular esteja em Recovery Mode.
Requisitos:
Para computadores:
• Depuração USB ativa no celular; • Computador com adb; • Cabo USB;
Para celulares:
• Depuração sem fio (ou depuração wifi) ativa no celular; • Termux; • Android 11 ou superior;
Para ambos:
• Firewall NetGuard instalado e configurado no celular; • Lista de bloatwares para seu dispositivo;
Ativação de depuração:
Para ativar a Depuração USB em seu dispositivo, pesquise como ativar as opções de desenvolvedor de seu dispositivo, e lá ative a depuração. No caso da depuração sem fio, sua ativação irá ser necessária apenas no momento que for conectar o dispositivo ao Termux.
Instalação e configuração do NetGuard
O NetGuard pode ser instalado através da própria Google Play Store, mas de preferência instale pela F-Droid ou Github para evitar telemetria.
F-Droid: https://f-droid.org/packages/eu.faircode.netguard/
Github: https://github.com/M66B/NetGuard/releases
Após instalado, configure da seguinte maneira:
Configurações → padrões (lista branca/negra) → ative as 3 primeiras opções (bloquear wifi, bloquear dados móveis e aplicar regras ‘quando tela estiver ligada’);
Configurações → opções avançadas → ative as duas primeiras (administrar aplicativos do sistema e registrar acesso a internet);
Com isso, todos os apps estarão sendo bloqueados de acessar a internet, seja por wifi ou dados móveis, e na página principal do app basta permitir o acesso a rede para os apps que você vai usar (se necessário). Permita que o app rode em segundo plano sem restrição da otimização de bateria, assim quando o celular ligar, ele já estará ativo.
Lista de bloatwares
Nem todos os bloatwares são genéricos, haverá bloatwares diferentes conforme a marca, modelo, versão do Android, e até mesmo região.
Para obter uma lista de bloatwares de seu dispositivo, caso seu aparelho já possua um tempo de existência, você encontrará listas prontas facilmente apenas pesquisando por elas. Supondo que temos um Samsung Galaxy Note 10 Plus em mãos, basta pesquisar em seu motor de busca por:
Samsung Galaxy Note 10 Plus bloatware listProvavelmente essas listas já terão inclusas todos os bloatwares das mais diversas regiões, lhe poupando o trabalho de buscar por alguma lista mais específica.
Caso seu aparelho seja muito recente, e/ou não encontre uma lista pronta de bloatwares, devo dizer que você acaba de pegar em merda, pois é chato para um caralho pesquisar por cada aplicação para saber sua função, se é essencial para o sistema ou se é facilmente substituível.
De antemão já aviso, que mais para frente, caso vossa gostosura remova um desses aplicativos que era essencial para o sistema sem saber, vai acabar resultando na perda de alguma função importante, ou pior, ao reiniciar o aparelho o sistema pode estar quebrado, lhe obrigando a seguir com uma formatação, e repetir todo o processo novamente.
Download do adb em computadores
Para usar a ferramenta do adb em computadores, basta baixar o pacote chamado SDK platform-tools, disponível através deste link: https://developer.android.com/tools/releases/platform-tools. Por ele, você consegue o download para Windows, Mac e Linux.
Uma vez baixado, basta extrair o arquivo zipado, contendo dentro dele uma pasta chamada platform-tools que basta ser aberta no terminal para se usar o adb.
Download do adb em celulares com Termux.
Para usar a ferramenta do adb diretamente no celular, antes temos que baixar o app Termux, que é um emulador de terminal linux, e já possui o adb em seu repositório. Você encontra o app na Google Play Store, mas novamente recomendo baixar pela F-Droid ou diretamente no Github do projeto.
F-Droid: https://f-droid.org/en/packages/com.termux/
Github: https://github.com/termux/termux-app/releases
Processo de debloat
Antes de iniciarmos, é importante deixar claro que não é para você sair removendo todos os bloatwares de cara sem mais nem menos, afinal alguns deles precisam antes ser substituídos, podem ser essenciais para você para alguma atividade ou função, ou até mesmo são insubstituíveis.
Alguns exemplos de bloatwares que a substituição é necessária antes da remoção, é o Launcher, afinal, é a interface gráfica do sistema, e o teclado, que sem ele só é possível digitar com teclado externo. O Launcher e teclado podem ser substituídos por quaisquer outros, minha recomendação pessoal é por aqueles que respeitam sua privacidade, como Pie Launcher e Simple Laucher, enquanto o teclado pelo OpenBoard e FlorisBoard, todos open-source e disponíveis da F-Droid.
Identifique entre a lista de bloatwares, quais você gosta, precisa ou prefere não substituir, de maneira alguma você é obrigado a remover todos os bloatwares possíveis, modifique seu sistema a seu bel-prazer. O NetGuard lista todos os apps do celular com o nome do pacote, com isso você pode filtrar bem qual deles não remover.
Um exemplo claro de bloatware insubstituível e, portanto, não pode ser removido, é o com.android.mtp, um protocolo onde sua função é auxiliar a comunicação do dispositivo com um computador via USB, mas por algum motivo, tem acesso a rede e se comunica frequentemente com servidores externos. Para esses casos, e melhor solução mesmo é bloquear o acesso a rede desses bloatwares com o NetGuard.
MTP tentando comunicação com servidores externos:
Executando o adb shell
No computador
Faça backup de todos os seus arquivos importantes para algum armazenamento externo, e formate seu celular com o hard reset. Após a formatação, e a ativação da depuração USB, conecte seu aparelho e o pc com o auxílio de um cabo USB. Muito provavelmente seu dispositivo irá apenas começar a carregar, por isso permita a transferência de dados, para que o computador consiga se comunicar normalmente com o celular.
Já no pc, abra a pasta platform-tools dentro do terminal, e execute o seguinte comando:
./adb start-serverO resultado deve ser:
daemon not running; starting now at tcp:5037 daemon started successfully
E caso não apareça nada, execute:
./adb kill-serverE inicie novamente.
Com o adb conectado ao celular, execute:
./adb shellPara poder executar comandos diretamente para o dispositivo. No meu caso, meu celular é um Redmi Note 8 Pro, codinome Begonia.
Logo o resultado deve ser:
begonia:/ $
Caso ocorra algum erro do tipo:
adb: device unauthorized. This adb server’s $ADB_VENDOR_KEYS is not set Try ‘adb kill-server’ if that seems wrong. Otherwise check for a confirmation dialog on your device.
Verifique no celular se apareceu alguma confirmação para autorizar a depuração USB, caso sim, autorize e tente novamente. Caso não apareça nada, execute o kill-server e repita o processo.
No celular
Após realizar o mesmo processo de backup e hard reset citado anteriormente, instale o Termux e, com ele iniciado, execute o comando:
pkg install android-toolsQuando surgir a mensagem “Do you want to continue? [Y/n]”, basta dar enter novamente que já aceita e finaliza a instalação
Agora, vá até as opções de desenvolvedor, e ative a depuração sem fio. Dentro das opções da depuração sem fio, terá uma opção de emparelhamento do dispositivo com um código, que irá informar para você um código em emparelhamento, com um endereço IP e porta, que será usado para a conexão com o Termux.
Para facilitar o processo, recomendo que abra tanto as configurações quanto o Termux ao mesmo tempo, e divida a tela com os dois app’s, como da maneira a seguir:
Para parear o Termux com o dispositivo, não é necessário digitar o ip informado, basta trocar por “localhost”, já a porta e o código de emparelhamento, deve ser digitado exatamente como informado. Execute:
adb pair localhost:porta CódigoDeEmparelhamentoDe acordo com a imagem mostrada anteriormente, o comando ficaria “adb pair localhost:41255 757495”.
Com o dispositivo emparelhado com o Termux, agora basta conectar para conseguir executar os comandos, para isso execute:
adb connect localhost:portaObs: a porta que você deve informar neste comando não é a mesma informada com o código de emparelhamento, e sim a informada na tela principal da depuração sem fio.
Pronto! Termux e adb conectado com sucesso ao dispositivo, agora basta executar normalmente o adb shell:
adb shellRemoção na prática Com o adb shell executado, você está pronto para remover os bloatwares. No meu caso, irei mostrar apenas a remoção de um app (Google Maps), já que o comando é o mesmo para qualquer outro, mudando apenas o nome do pacote.
Dentro do NetGuard, verificando as informações do Google Maps:
Podemos ver que mesmo fora de uso, e com a localização do dispositivo desativado, o app está tentando loucamente se comunicar com servidores externos, e informar sabe-se lá que peste. Mas sem novidades até aqui, o mais importante é que podemos ver que o nome do pacote do Google Maps é com.google.android.apps.maps, e para o remover do celular, basta executar:
pm uninstall –user 0 com.google.android.apps.mapsE pronto, bloatware removido! Agora basta repetir o processo para o resto dos bloatwares, trocando apenas o nome do pacote.
Para acelerar o processo, você pode já criar uma lista do bloco de notas com os comandos, e quando colar no terminal, irá executar um atrás do outro.
Exemplo de lista:
Caso a donzela tenha removido alguma coisa sem querer, também é possível recuperar o pacote com o comando:
cmd package install-existing nome.do.pacotePós-debloat
Após limpar o máximo possível o seu sistema, reinicie o aparelho, caso entre no como recovery e não seja possível dar reboot, significa que você removeu algum app “essencial” para o sistema, e terá que formatar o aparelho e repetir toda a remoção novamente, desta vez removendo poucos bloatwares de uma vez, e reiniciando o aparelho até descobrir qual deles não pode ser removido. Sim, dá trabalho… quem mandou querer privacidade?
Caso o aparelho reinicie normalmente após a remoção, parabéns, agora basta usar seu celular como bem entender! Mantenha o NetGuard sempre executando e os bloatwares que não foram possíveis remover não irão se comunicar com servidores externos, passe a usar apps open source da F-Droid e instale outros apps através da Aurora Store ao invés da Google Play Store.
Referências: Caso você seja um Australopithecus e tenha achado este guia difícil, eis uma videoaula (3:14:40) do Anderson do canal Ciberdef, realizando todo o processo: http://odysee.com/@zai:5/Como-remover-at%C3%A9-200-APLICATIVOS-que-colocam-a-sua-PRIVACIDADE-E-SEGURAN%C3%87A-em-risco.:4?lid=6d50f40314eee7e2f218536d9e5d300290931d23
Pdf’s do Anderson citados na videoaula: créditos ao anon6837264 http://eternalcbrzpicytj4zyguygpmkjlkddxob7tptlr25cdipe5svyqoqd.onion/file/3863a834d29285d397b73a4af6fb1bbe67c888d72d30/t-05e63192d02ffd.pdf
Processo de instalação do Termux e adb no celular: https://youtu.be/APolZrPHSms
-
 @ 000002de:c05780a7
2025-04-23 16:27:56
@ 000002de:c05780a7
2025-04-23 16:27:56Natalie Brunell had comedian T.J. Miller known for Silicon Valley on her show Coin Stories. I was kinda surprised. Not sure why but I recognized his voice because that's my brain I can forget a face but never a voice.
So what person that has fame also secretly is a bitcoiner. Not has the ETF or whatever but actually gets it and has for a while.
I think this is pretty widely believed that Mark Zuckerburg is a bitcoiner so that would be the person I'd list. No clue beyond that. There has to be quite a few well known people that also get bitcoin and just don't talk about it.
SO, who do you think is in the club?
originally posted at https://stacker.news/items/955179
-
 @ 8f69ac99:4f92f5fd
2025-04-23 14:39:01
@ 8f69ac99:4f92f5fd
2025-04-23 14:39:01Dizem-nos que a inflação é necessária. Mas e se for, afinal, a raiz da disfunção económica que enfrentamos?
A crença mainstream é clara: para estimular o crescimento, os governos devem poder desvalorizar a sua moeda — essencialmente, criar dinheiro do nada. Supostamente, isso incentiva o investimento, aumenta o consumo e permite responder a crises económicas. Esta narrativa foi repetida tantas vezes que se tornou quase um axioma — raramente questionado.
No centro desta visão está a lógica fiat-keynesiana: uma economia estável exige um banco central disposto a manipular o valor do dinheiro para alcançar certos objectivos políticos. Esta abordagem, inspirada por John Maynard Keynes, defende a intervenção estatal como forma de estabilizar a economia durante recessões. Na teoria, os investidores e consumidores beneficiam de taxas de juro artificiais e de maior poder de compra — um suposto ganho para todos.
Mas há outra perspectiva: a visão do dinheiro sólido (sound money, em inglês). Enraizada na escola austríaca e nos princípios da liberdade individual, esta defende que a manipulação monetária não é apenas desnecessária — é prejudicial. Uma moeda estável, não sujeita à depreciação arbitrária, é essencial para promover trocas voluntárias, empreendedorismo e crescimento económico genuíno.
Está na hora de desafiar esta sabedoria convencional. Ao longo dos próximos capítulos, vamos analisar os pressupostos errados que sustentam a lógica fiat-keynesiana e explorar os benefícios de um sistema baseado em dinheiro sólido — como Bitcoin. Vamos mostrar por que desvalorizar a moeda é moralmente questionável e economicamente prejudicial, e propor alternativas mais éticas e eficazes.
Este artigo (que surge em resposta ao "guru" Miguel Milhões) pretende iluminar as diferenças entre estas duas visões opostas e apresentar uma abordagem mais sólida e justa para a política económica — centrada na liberdade pessoal, na responsabilidade individual e na preservação de instituições financeiras saudáveis.
O Argumento Fiat: Por que Dizem que é Preciso Desvalorizar a Moeda
Este argumento parte geralmente de uma visão económica keynesiana e/ou estatista e assenta em duas ideias principais: o incentivo ao investimento e a necessidade de resposta a emergências.
Incentivo ao Investimento
Segundo os defensores do sistema fiat, se uma moeda como o ouro ou bitcoin valorizar ao longo do tempo, as pessoas tenderão a "acumular" essa riqueza em vez de investir em negócios produtivos. O receio é que, se guardar dinheiro se torna mais rentável do que investir, a economia entre em estagnação.
Esta ideia parte de uma visão simplista do comportamento humano. Na realidade, as pessoas tomam decisões financeiras com base em múltiplos factores. Embora seja verdade que activos valorizáveis são atractivos, isso não significa que os investimentos desapareçam. Pelo contrário, o surgimento de activos como bitcoin cria novas oportunidades de inovação e investimento.
Historicamente, houve crescimento económico em períodos de moeda sólida — como no padrão-ouro. Uma moeda estável e previsível pode incentivar o investimento, ao dar confiança nos retornos futuros.
Resposta a Emergências
A segunda tese é que os governos precisam de imprimir dinheiro rapidamente em tempos de crise — pandemias, guerras ou recessões. Esta capacidade de intervenção é vista como essencial para "salvar" a economia.
De acordo com economistas keynesianos, uma injecção rápida de liquidez pode estabilizar a economia e evitar colapsos sociais. No entanto, este argumento ignora vários pontos fundamentais:
- A política monetária não substitui a responsabilidade fiscal: A capacidade de imprimir dinheiro não torna automaticamente eficaz o estímulo económico.
- A inflação é uma consequência provável: A impressão de dinheiro pode levar a pressões inflacionistas, reduzindo o poder de compra dos consumidores e minando o próprio estímulo pretendido. Estamos agora a colher os "frutos" da impressão de dinheiro durante a pandemia.
- O timing é crítico: Intervenções mal cronometradas podem agravar a situação.
Veremos em seguida porque estes argumentos não se sustentam.
Rebatendo os Argumentos
O Investimento Não Morre num Sistema de Dinheiro Sólido
O argumento de que o dinheiro sólido mata o investimento falha em compreender a ligação entre poupança e capital. Num sistema sólido, a poupança não é apenas acumulação — é capital disponível para financiar novos projectos. Isso conduz a um crescimento mais sustentável, baseado na qualidade e não na especulação.
Em contraste, o sistema fiat, com crédito barato, gera bolhas e colapsos — como vimos em 2008 ou na bolha dot-com. Estes exemplos ilustram os perigos da especulação facilitada por políticas monetárias artificiais.
Já num sistema de dinheiro sólido, como o que cresce em torno de Bitcoin, vemos investimentos em mineração, startups, educação e arte. Os investidores continuam activos — mas fazem escolhas mais responsáveis e de longo prazo.
Imprimir Dinheiro Não Resolve Crises
A ideia de que imprimir dinheiro é essencial em tempos de crise parte de uma ilusão perigosa. A inflação que se segue reduz o poder de compra e afecta especialmente os mais pobres — é uma forma oculta de imposto.
Além disso, soluções descentralizadas — como os mercados, redes comunitárias e poupança — são frequentemente mais eficazes. A resposta à COVID-19 ilustra isso: grandes empresas foram salvas, mas pequenos negócios e famílias ficaram para trás. Os últimos receberam um amuse-bouche, enquanto os primeiros comeram o prato principal, sopa, sobremesa e ainda levaram os restos.
A verdade é que imprimir dinheiro não cria valor — apenas o redistribui injustamente. A verdadeira resiliência nasce de comunidades organizadas e de uma base económica saudável, não de decretos políticos.
Dois Mundos: Fiat vs. Dinheiro Sólido
| Dimensão | Sistema Fiat-Keynesiano | Sistema de Dinheiro Sólido | |----------|--------------------------|-----------------------------| | Investimento | Estimulado por crédito fácil, alimentando bolhas | Baseado em poupança real e oportunidades sustentáveis | | Resposta a crises | Centralizada, via impressão de moeda | Descentralizada, baseada em poupança e solidariedade | | Preferência temporal | Alta: foco no consumo imediato | Baixa: foco na poupança e no futuro | | Distribuição de riqueza | Favorece os próximos ao poder (Efeito Cantillon) | Benefícios da deflação são distribuídos de forma mais justa | | Fundamento moral | Coercivo e redistributivo | Voluntário e baseado na liberdade individual |
Estes contrastes mostram que a escolha entre os dois sistemas vai muito além da economia — é também uma questão ética.
Consequências de Cada Sistema
O Mundo Fiat
Num mundo dominado pelo sistema fiat, os ciclos de euforia e colapso são a norma. A desigualdade aumenta, com os mais próximos ao poder a lucrar com a inflação e a impressão de dinheiro. A poupança perde valor, e a autonomia financeira das pessoas diminui.
À medida que o Estado ganha mais controlo sobre a economia, os cidadãos perdem capacidade de escolha e dependem cada vez mais de apoios governamentais. Esta dependência destrói o espírito de iniciativa e promove o conformismo.
O resultado? Estagnação, conflitos sociais e perda de liberdade.
O Mundo com Dinheiro Sólido
Com uma moeda sólida, o crescimento é baseado em valor real. As pessoas poupam mais, investem melhor e tornam-se mais independentes financeiramente. As comunidades tornam-se mais resilientes, e a cooperação substitui a dependência estatal.
Benefícios chave:
- Poupança real: A moeda não perde valor, e a riqueza pode ser construída com estabilidade.
- Resiliência descentralizada: Apoio mútuo entre indivíduos e comunidades em tempos difíceis.
- Liberdade económica: Menor interferência política e mais espaço para inovação e iniciativa pessoal.
Conclusão
A desvalorização da moeda não é uma solução — é um problema. Os sistemas fiat estão desenhados para transferir riqueza e poder de forma opaca, perpetuando injustiças e instabilidade.
Por outro lado, o dinheiro sólido — como Bitcoin — oferece uma alternativa credível e ética. Promove liberdade, responsabilidade e transparência. Impede abusos de poder e expõe os verdadeiros custos da má governação.
Não precisamos de mais inflação — precisamos de mais integridade.
Está na hora de recuperarmos o controlo sobre a nossa vida financeira. De rejeitarmos os sistemas que nos empobrecem lentamente e de construirmos um futuro em que o dinheiro serve as pessoas — e não os interesses políticos.
O futuro do dinheiro pode e deve ser diferente. Juntos, podemos criar uma economia mais justa, livre e resiliente — onde a prosperidade é partilhada e a dignidade individual respeitada.
Photo by rc.xyz NFT gallery on Unsplash
-
 @ 7d33ba57:1b82db35
2025-04-23 13:51:02
@ 7d33ba57:1b82db35
2025-04-23 13:51:02You don’t need a fancy camera to dive into the miniature universe—your phone + a few tricks are all it takes! Macro photography with a smartphone can reveal incredible textures, patterns, insects, flowers, and everyday details most people miss. Here’s how to get the best out of it:
🔧 1. Use a Macro Lens Attachment (If Possible)
- Clip-on macro lenses are affordable and boost your phone's close-up power
- Look for 10x–20x lenses for best results
- Make sure it’s aligned perfectly with your phone’s lens
✨ 2. Get Really Close (but Not Too Close)
- Phones typically focus best at 2–5 cm in macro mode
- Slowly move your phone toward the subject until it comes into sharp focus
- If it blurs, back off slightly—tiny shifts matter a lot!
📸 3. Tap to Focus & Adjust Exposure
- Tap on your subject to lock focus
- Adjust brightness manually if your phone allows—slightly underexposed often looks better in macro
🌤️ 4. Use Natural Light or a Diffused Flash
- Soft natural light (like early morning or cloudy day) gives the best macro results
- Use white paper to bounce light or your hand to gently shade direct sun
- If using flash, try diffusing it with a tissue or tape for a softer effect
🧍♂️ 5. Steady Yourself
- Use both hands, brace against something, or use a tripod for stability
- Try your phone’s timer or remote shutter (via headphones or Bluetooth) to avoid shake
🧽 6. Clean Your Lens
- Macro shows everything—including dust and fingerprints
- Always wipe your lens gently before shooting
🌀 7. Explore Textures & Patterns
- Get creative with leaves, feathers, skin, fabrics, ice, fruit, rust, insects—anything with rich texture
- Look for symmetry, contrast, or repetition in tiny subjects
🧑🎨 8. Edit Smart
- Use apps like Snapseed, Lightroom Mobile, or your built-in editor
- Adjust sharpness, contrast, warmth, and cropping carefully
- Avoid over-sharpening—it can make things look unnatural
🎯 Bonus Tip: Try Manual Camera Apps
- Apps like Halide (iOS), ProCamera, or Camera+ 2 let you control ISO, shutter speed, and focus manually
- Great for getting extra precision
Macro phoneography is about patience and curiosity. Once you start noticing the tiny wonders around you, you’ll see the world a little differently.
-
 @ 4ba8e86d:89d32de4
2025-04-21 02:12:19
@ 4ba8e86d:89d32de4
2025-04-21 02:12:19SISTEMA OPERACIONAL MÓVEIS
GrapheneOS : https://njump.me/nevent1qqs8t76evdgrg4qegdtyrq2rved63pr29wlqyj627n9tj4vlu66tqpqpzdmhxue69uhk7enxvd5xz6tw9ec82c30qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqppcqec9
CalyxOS : https://njump.me/nevent1qqsrm0lws2atln2kt3cqjacathnw0uj0jsxwklt37p7t380hl8mmstcpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3vamnwvaz7tmwdaehgu3wvf3kstnwd9hx5cf0qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgcwaehxw309aex2mrp0yhxxatjwfjkuapwveukjtcpzpmhxue69uhkummnw3ezumt0d5hszrnhwden5te0dehhxtnvdakz7qfywaehxw309ahx7um5wgh8ymm4dej8ymmrdd3xjarrda5kuetjwvhxxmmd9uq3uamnwvaz7tmwdaehgu3dv3jhvtnhv4kxcmmjv3jhytnwv46z7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qgewaehxw309ahx7um5wghxymmwva3x7mn89e3k7mf0qythwumn8ghj7cn5vvhxkmr9dejxz7n49e3k7mf0qyg8wumn8ghj7mn09eehgu3wvdez7smttdu
LineageOS : https://njump.me/nevent1qqsgw7sr36gaty48cf4snw0ezg5mg4atzhqayuge752esd469p26qfgpzdmhxue69uhhwmm59e6hg7r09ehkuef0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpnvm779
SISTEMA OPERACIONAL DESKTOP
Tails : https://njump.me/nevent1qqsf09ztvuu60g6xprazv2vxqqy5qlxjs4dkc9d36ta48q75cs9le4qpzemhxue69uhkummnw3ex2mrfw3jhxtn0wfnj7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz34ag5t
Qubes OS : https://njump.me/nevent1qqsp6jujgwl68uvurw0cw3hfhr40xq20sj7rl3z4yzwnhp9sdpa7augpzpmhxue69uhkummnw3ezumt0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsz9thwden5te0dehhxarj9ehhsarj9ejx2a30qyg8wumn8ghj7mn09eehgu3wvdez7qg4waehxw309aex2mrp0yhxgctdw4eju6t09uqjxamnwvaz7tmwdaehgu3dwejhy6txd9jkgtnhv4kxcmmjv3jhytnwv46z7qgwwaehxw309ahx7uewd3hkctcpremhxue69uhkummnw3ez6er9wch8wetvd3hhyer9wghxuet59uj3ljr8
Kali linux : https://njump.me/nevent1qqswlav72xdvamuyp9xc38c6t7070l3n2uxu67ssmal2g7gv35nmvhspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswt9rxe
Whonix : https://njump.me/nevent1qqs85gvejvzhk086lwh6edma7fv07p5c3wnwnxnzthwwntg2x6773egpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3qamnwvaz7tmwdaehgu3wd4hk6tcpzemhxue69uhkummnw3ezucnrdqhxu6twdfsj7qfywaehxw309ahx7um5wgh8ymm4dej8ymmrdd3xjarrda5kuetjwvhxxmmd9uq3wamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmd9uq3qamnwvaz7tmwduh8xarj9e3hytcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszrnhwden5te0dehhxtnvdakz7qg7waehxw309ahx7um5wgkkgetk9emk2mrvdaexgetj9ehx2ap0sen9p6
Kodachi : https://njump.me/nevent1qqsf5zszgurpd0vwdznzk98hck294zygw0s8dah6fpd309ecpreqtrgpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszgmhwden5te0dehhxarj94mx2unfve5k2epwwajkcmr0wfjx2u3wdejhgtcpremhxue69uhkummnw3ez6er9wch8wetvd3hhyer9wghxuet59uq3qamnwvaz7tmwdaehgu3wd4hk6tcpzamhxue69uhkyarr9e4kcetwv3sh5afwvdhk6tcpzpmhxue69uhkumewwd68ytnrwghszfrhwden5te0dehhxarj9eex7atwv3ex7cmtvf5hgcm0d9hx2unn9e3k7mf0qyvhwumn8ghj7mn0wd68ytnzdahxwcn0denjucm0d5hszrnhwden5te0dehhxtnvdakz7qgkwaehxw309ahx7um5wghxycmg9ehxjmn2vyhsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshs94a4d5
PGP
Openkeychain : https://njump.me/nevent1qqs9qtjgsulp76t7jkquf8nk8txs2ftsr0qke6mjmsc2svtwfvswzyqpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs36mp0w
Kleopatra : https://njump.me/nevent1qqspnevn932hdggvp4zam6mfyce0hmnxsp9wp8htpumq9vm3anq6etsppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpuaeghp
Pgp : https://njump.me/nevent1qqsggek707qf3rzttextmgqhym6d4g479jdnlnj78j96y0ut0x9nemcpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgptemhe
Como funciona o PGP? : https://njump.me/nevent1qqsz9r7azc8pkvfmkg2hv0nufaexjtnvga0yl85x9hu7ptpg20gxxpspremhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet59upzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy259fhs
Por que eu escrevi PGP. - Philip Zimmermann.
https://njump.me/nevent1qqsvysn94gm8prxn3jw04r0xwc6sngkskg756z48jsyrmqssvxtm7ncpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtchzxnad
VPN
Vpn : https://njump.me/nevent1qqs27ltgsr6mh4ffpseexz6s37355df3zsur709d0s89u2nugpcygsspzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqshzu2fk
InviZible Pro : https://njump.me/nevent1qqsvyevf2vld23a3xrpvarc72ndpcmfvc3lc45jej0j5kcsg36jq53cpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy33y5l4
Orbot: https://njump.me/nevent1qqsxswkyt6pe34egxp9w70cy83h40ururj6m9sxjdmfass4cjm4495stft593
I2P
i2p : https://njump.me/nevent1qqsvnj8n983r4knwjmnkfyum242q4c0cnd338l4z8p0m6xsmx89mxkslx0pgg
Entendendo e usando a rede I2P : https://njump.me/nevent1qqsxchp5ycpatjf5s4ag25jkawmw6kkf64vl43vnprxdcwrpnms9qkcppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpvht4mn
Criando e acessando sua conta Email na I2P : https://njump.me/nevent1qqs9v9dz897kh8e5lfar0dl7ljltf2fpdathsn3dkdsq7wg4ksr8xfgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpw8mzum
APLICATIVO 2FA
Aegis Authenticator : https://njump.me/nevent1qqsfttdwcn9equlrmtf9n6wee7lqntppzm03pzdcj4cdnxel3pz44zspz4mhxue69uhhyetvv9ujumn0wd68ytnzvuhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqscvtydq
YubiKey : https://njump.me/nevent1qqstsnn69y4sf4330n7039zxm7wza3ch7sn6plhzmd57w6j9jssavtspvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzueyvgt
GERENCIADOR DE SENHAS
KeepassDX: https://njump.me/nevent1qqswc850dr4ujvxnmpx75jauflf4arc93pqsty5pv8hxdm7lcw8ee8qpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpe0492n
Birwaden: https://njump.me/nevent1qqs0j5x9guk2v6xumhwqmftmcz736m9nm9wzacqwjarxmh8k4xdyzwgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpwfe2kc
KeePassXC: https://njump.me/nevent1qqsgftcrd8eau7tzr2p9lecuaf7z8mx5jl9w2k66ae3lzkw5wqcy5pcl2achp
CHAT MENSAGEM
SimpleXchat : https://njump.me/nevent1qqsds5xselnnu0dyy0j49peuun72snxcgn3u55d2320n37rja9gk8lgzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgmcmj7c
Briar : https://njump.me/nevent1qqs8rrtgvjr499hreugetrl7adkhsj2zextyfsukq5aa7wxthrgcqcg05n434
Element Messenger : https://njump.me/nevent1qqsq05snlqtxm5cpzkshlf8n5d5rj9383vjytkvqp5gta37hpuwt4mqyccee6
Pidgin : https://njump.me/nevent1qqsz7kngycyx7meckx53xk8ahk98jkh400usrvykh480xa4ct9zlx2c2ywvx3
E-MAIL
Thunderbird: https://njump.me/nevent1qqspq64gg0nw7t60zsvea5eykgrm43paz845e4jn74muw5qzdvve7uqrkwtjh
ProtonMail : https://njump.me/nevent1qqs908glhk68e7ms8zqtlsqd00wu3prnpt08dwre26hd6e5fhqdw99cppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpeyhg4z
Tutonota : https://njump.me/nevent1qqswtzh9zjxfey644qy4jsdh9465qcqd2wefx0jxa54gdckxjvkrrmqpz4mhxue69uhhyetvv9ujumt0wd68ytnsw43qygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs5hzhkv
k-9 mail : https://njump.me/nevent1qqs200g5a603y7utjgjk320r3srurrc4r66nv93mcg0x9umrw52ku5gpr3mhxue69uhkummnw3ezuumhd9ehxtt9de5kwmtp9e3kstczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgacflak
E-MAIL-ALIÁS
Simplelogin : https://njump.me/nevent1qqsvhz5pxqpqzr2ptanqyqgsjr50v7u9lc083fvdnglhrv36rnceppcppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqp9gsr7m
AnonAddy : https://njump.me/nevent1qqs9mcth70mkq2z25ws634qfn7vx2mlva3tkllayxergw0s7p8d3ggcpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs6mawe3
NAVEGADOR
Navegador Tor : https://njump.me/nevent1qqs06qfxy7wzqmk76l5d8vwyg6mvcye864xla5up52fy5sptcdy39lspzemhxue69uhkummnw3ezuerpw3sju6rpw4ej7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdp0urw
Mullvap Browser : https://njump.me/nevent1qqs2vsgc3wk09wdspv2mezltgg7nfdg97g0a0m5cmvkvr4nrfxluzfcpzdmhxue69uhhwmm59e6hg7r09ehkuef0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpj8h6fe
LibreWolf : https://njump.me/nevent1qqswv05mlmkcuvwhe8x3u5f0kgwzug7n2ltm68fr3j06xy9qalxwq2cpzemhxue69uhkummnw3ex2mrfw3jhxtn0wfnj7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzuv2hxr
Cromite : https://njump.me/nevent1qqs2ut83arlu735xp8jf87w5m3vykl4lv5nwkhldkqwu3l86khzzy4cpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs3dplt7
BUSCADORES
Searx : https://njump.me/nevent1qqsxyzpvgzx00n50nrlgctmy497vkm2cm8dd5pdp7fmw6uh8xnxdmaspr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqp23z7ax
APP-STORE
Obtainium : https://njump.me/nevent1qqstd8kzc5w3t2v6dgf36z0qrruufzfgnc53rj88zcjgsagj5c5k4rgpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqyarmca3
F-Droid : https://njump.me/nevent1qqst4kry49cc9g3g8s5gdnpgyk3gjte079jdnv43f0x4e85cjkxzjesymzuu4
Droid-ify : https://njump.me/nevent1qqsrr8yu9luq0gud902erdh8gw2lfunpe93uc2u6g8rh9ep7wt3v4sgpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsfzu9vk
Aurora Store : https://njump.me/nevent1qqsy69kcaf0zkcg0qnu90mtk46ly3p2jplgpzgk62wzspjqjft4fpjgpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzrpmsjy
RSS
Feeder : https://njump.me/nevent1qqsy29aeggpkmrc7t3c7y7ldgda7pszl7c8hh9zux80gjzrfvlhfhwqpp4mhxue69uhkummn9ekx7mqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgsvzzjy
VIDEOO CONFERENCIA
Jitsi meet : https://njump.me/nevent1qqswphw67hr6qmt2fpugcj77jrk7qkfdrszum7vw7n2cu6cx4r6sh4cgkderr
TECLADOS
HeliBoard : https://njump.me/nevent1qqsyqpc4d28rje03dcvshv4xserftahhpeylu2ez2jutdxwds4e8syspz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsr8mel5
OpenBoard : https://njump.me/nevent1qqsf7zqkup03yysy67y43nj48q53sr6yym38es655fh9fp6nxpl7rqspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswcvh3r
FlorisBoard : https://njump.me/nevent1qqsf7zqkup03yysy67y43nj48q53sr6yym38es655fh9fp6nxpl7rqspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswcvh3r
MAPAS
Osmand : https://njump.me/nevent1qqsxryp2ywj64az7n5p6jq5tn3tx5jv05te48dtmmt3lf94ydtgy4fgpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs54nwpj
Organic maps : https://njump.me/nevent1qqstrecuuzkw0dyusxdq7cuwju0ftskl7anx978s5dyn4pnldrkckzqpr4mhxue69uhkummnw3ezumtp0p5k6ctrd96xzer9dshx7un8qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpl8z3kk
TRADUÇÃO
LibreTranslate : https://njump.me/nevent1qqs953g3rhf0m8jh59204uskzz56em9xdrjkelv4wnkr07huk20442cpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzeqsx40
REMOÇÃO DOS METADADOS
Scrambled Exif : https://njump.me/nevent1qqs2658t702xv66p000y4mlhnvadmdxwzzfzcjkjf7kedrclr3ej7aspyfmhxue69uhk6atvw35hqmr90pjhytngw4eh5mmwv4nhjtnhdaexcep0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpguu0wh
ESTEGANOGRAFIA
PixelKnot: https://njump.me/nevent1qqsrh0yh9mg0lx86t5wcmhh97wm6n4v0radh6sd0554ugn354wqdj8gpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqyuvfqdp
PERFIL DE TRABALHO
Shelter : https://njump.me/nevent1qqspv9xxkmfp40cxgjuyfsyczndzmpnl83e7gugm7480mp9zhv50wkqpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdnu59c
PDF
MuPDF : https://njump.me/nevent1qqspn5lhe0dteys6npsrntmv2g470st8kh8p7hxxgmymqa95ejvxvfcpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs4hvhvj
Librera Reader : https://njump.me/nevent1qqsg60flpuf00sash48fexvwxkly2j5z9wjvjrzt883t3eqng293f3cpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz39tt3n
QR-Code
Binary Eye : https://njump.me/nevent1qqsz4n0uxxx3q5m0r42n9key3hchtwyp73hgh8l958rtmae5u2khgpgpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdmn4wp
Climático
Breezy Weather : https://njump.me/nevent1qqs9hjz5cz0y4am3kj33xn536uq85ydva775eqrml52mtnnpe898rzspzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgpd3tu8
ENCRYPTS
Cryptomator : https://njump.me/nevent1qqsvchvnw779m20583llgg5nlu6ph5psewetlczfac5vgw83ydmfndspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsx7ppw9
VeraCrypt : https://njump.me/nevent1qqsf6wzedsnrgq6hjk5c4jj66dxnplqwc4ygr46l8z3gfh38q2fdlwgm65ej3
EXTENSÕES
uBlock Origin : https://njump.me/nevent1qqswaa666lcj2c4nhnea8u4agjtu4l8q89xjln0yrngj7ssh72ntwzql8ssdj
Snowflake : https://njump.me/nevent1qqs0ws74zlt8uced3p2vee9td8x7vln2mkacp8szdufvs2ed94ctnwchce008
CLOUD
Nextcloud : https://njump.me/nevent1qqs2utg5z9htegdtrnllreuhypkk2026x8a0xdsmfczg9wdl8rgrcgg9nhgnm
NOTEPAD
Joplin : https://njump.me/nevent1qqsz2a0laecpelsznser3xd0jfa6ch2vpxtkx6vm6qg24e78xttpk0cpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpdu0hft
Standard Notes : https://njump.me/nevent1qqsv3596kz3qung5v23cjc4cpq7rqxg08y36rmzgcrvw5whtme83y3s7tng6r
MÚSICA
RiMusic : https://njump.me/nevent1qqsv3genqav2tfjllp86ust4umxm8tr2wd9kq8x7vrjq6ssp363mn0gpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqg42353n
ViMusic : https://njump.me/nevent1qqswx78559l4jsxsrygd8kj32sch4qu57stxq0z6twwl450vp39pdqqpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzjg863j
PODCAST
AntennaPod : https://njump.me/nevent1qqsp4nh7k4a6zymfwqqdlxuz8ua6kdhvgeeh3uxf2c9rtp9u3e9ku8qnr8lmy
VISUALIZAR VIDEO
VLC : https://njump.me/nevent1qqs0lz56wtlr2eye4ajs2gzn2r0dscw4y66wezhx0mue6dffth8zugcl9laky
YOUTUBE
NewPipe : https://njump.me/nevent1qqsdg06qpcjdnlvgm4xzqdap0dgjrkjewhmh4j3v4mxdl4rjh8768mgdw9uln
FreeTube : https://njump.me/nevent1qqsz6y6z7ze5gs56s8seaws8v6m6j2zu0pxa955dhq3ythmexak38mcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs5lkjvv
LibreTube : https://snort.social/e/nevent1qqstmd5m6wrdvn4gxf8xyhrwnlyaxmr89c9kjddvnvux6603f84t3fqpz4mhxue69uhhyetvv9ujumt0wd68ytnsw43qygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsswwznc
COMPARTILHAMENTO DE ARQUIVOS
OnionShare : https://njump.me/nevent1qqsr0a4ml5nu6ud5k9yzyawcd9arznnwkrc27dzzc95q6r50xmdff6qpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3uamnwvaz7tmwdaehgu3dv3jhvtnhv4kxcmmjv3jhytnwv46z7qgswaehxw309ahx7tnnw3ezucmj9uq32amnwvaz7tmjv4kxz7fwv3sk6atn9e5k7tcpzamhxue69uhkyarr9e4kcetwv3sh5afwvdhk6tcpzemhxue69uhkummnw3ezucnrdqhxu6twdfsj7qgswaehxw309ahx7um5wghx6mmd9uqjgamnwvaz7tmwdaehgu3wwfhh2mnywfhkx6mzd96xxmmfdejhyuewvdhk6tcppemhxue69uhkummn9ekx7mp0qythwumn8ghj7un9d3shjtnwdaehgu3wvfskuep0qyv8wumn8ghj7un9d3shjtnrw4e8yetwwshxv7tf9ut7qurt
Localsend : https://njump.me/nevent1qqsp8ldjhrxm09cvvcak20hrc0g8qju9f67pw7rxr2y3euyggw9284gpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzuyghqr
Wallet Bitcoin
Ashigaru Wallet : https://njump.me/nevent1qqstx9fz8kf24wgl26un8usxwsqjvuec9f8q392llmga75tw0kfarfcpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgvfsrqp
Samourai Wallet : https://njump.me/nevent1qqstcvjmz39rmrnrv7t5cl6p3x7pzj6jsspyh4s4vcwd2lugmre04ecpr9mhxue69uhkummnw3ezucn0denkymmwvuhxxmmd9upzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy3rg4qs
CÂMERA
opencamera : https://njump.me/nevent1qqs25glp6dh0crrjutxrgdjlnx9gtqpjtrkg29hlf7382aeyjd77jlqpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqssxcvgc
OFFICE
Collabora Office : https://njump.me/nevent1qqs8yn4ys6adpmeu3edmf580jhc3wluvlf823cc4ft4h0uqmfzdf99qpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsj40uss
TEXTOS
O manifesto de um Cypherpunk : https://njump.me/nevent1qqsd7hdlg6galn5mcuv3pm3ryfjxc4tkyph0cfqqe4du4dr4z8amqyspvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzal0efa
Operations security ( OPSEC) : https://snort.social/e/nevent1qqsp323havh3y9nxzd4qmm60hw87tm9gjns0mtzg8y309uf9mv85cqcpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz8ej9l7
O MANIFESTO CRIPTOANARQUISTA Timothy C. May – 1992. : https://njump.me/nevent1qqspp480wtyx2zhtwpu5gptrl8duv9rvq3mug85mp4d54qzywk3zq9gpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz5wq496
Declaração de independência do ciberespaço
- John Perry Barlow - 1996 : https://njump.me/nevent1qqs2njsy44n6p07mhgt2tnragvchasv386nf20ua5wklxqpttf6mzuqpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsukg4hr
The Cyphernomicon: Criptografia, Dinheiro Digital e o Futuro da Privacidade. escrito por Timothy C. May -Publicado em 1994. :
Livro completo em PDF no Github PrivacyOpenSource.
https://github.com/Alexemidio/PrivacyOpenSource/raw/main/Livros/THE%20CYPHERNOMICON%20.pdf Share
-
 @ 7d33ba57:1b82db35
2025-04-23 12:54:11
@ 7d33ba57:1b82db35
2025-04-23 12:54:11Texel, the largest of the Dutch Wadden Islands, is a peaceful, windswept escape in the North Sea, known for its wide sandy beaches, unique landscapes, and laid-back island vibe. Just a short ferry ride from the mainland, Texel offers a perfect mix of nature, wildlife, local culture, and coastal relaxation.
🏖️ Top Things to Do on Texel
🚲 Cycle Across the Island
- With over 140 km of bike paths, cycling is the best way to explore
- Ride through dunes, forests, sheep pastures, and cute villages like De Koog and Oudeschild
🌾 Explore Dunes & Beaches
- Visit Dunes of Texel National Park—a coastal dream with rolling dunes, hiking trails, and wildflowers
- Relax on vast, quiet beaches perfect for swimming, kite flying, or just soaking up sea air
🐑 Texel Sheep & Local Farms
- Meet the island’s famous Texel sheep—known for their wool and adorable lambs
- Stop by local farms for cheese tastings, ice cream, or a farm tour
🐦 Spot Wildlife at De Slufter
- A unique salt marsh where tidal water flows in naturally
- Great for birdwatching—home to spoonbills, geese, and waders
- Beautiful walking trails with views over the dunes and out to sea
🐋 Ecomare Marine Center
- Learn about Texel’s marine life, see seals and seabirds, and explore interactive exhibits
- A hit for families and nature lovers alike
🍺 Taste Texel
- Try local specialties like Texels beer, lamb dishes, cranberry treats, and fresh seafood
- Cozy beach pavilions and harbor-side restaurants offer stunning sunset views
🚢 Getting to Texel
- Take the ferry from Den Helder (crossing time: ~20 minutes)
- Cars, bikes, and pedestrians all welcome
- Once on the island, biking or local buses make getting around easy
🏡 Where to Stay
- Choose from beachside hotels, charming B&Bs, cozy cabins, or campsites
- Many places offer serene views of dunes, fields, or sea
-
 @ 4ba8e86d:89d32de4
2025-04-21 02:10:55
@ 4ba8e86d:89d32de4
2025-04-21 02:10:55Seu teclado não deve se conectar à internet. Privacidade em primeiro lugar. Sempre. Estamos desenvolvendo um teclado moderno que respeita totalmente sua privacidade e segurança. O FUTO Keyboard é 100% offline e 100% privado, oferecendo todos os recursos essenciais que você espera de um teclado atual — incluindo digitação por deslizamento, entrada de voz offline, correção automática inteligente, temas personalizáveis e sugestões preditivas de texto. Nosso objetivo é simples: criar um teclado eficiente e funcional, sem comprometer a privacidade do usuário. Este projeto é um fork do LatinIME, o teclado open-source oficial do Android.
Atenção: o FUTO Keyboard está atualmente em fase alfa. Está trabalhando para torná-lo estável e confiável, mas durante esse período você pode encontrar bugs, travamentos ou recursos ainda não implementados.
Configurações
Idiomas e Modelos – Adicione novos idiomas, dicionários, modelos de entrada de voz, transformadores e layouts associados.
Linguagens e Modelos
O menu no qual você adiciona novos idiomas, bem como dicionários, modelos de entrada de voz, modelos de transformadores e layouts associados a eles.
Adicionar idioma.
Alguns idiomas exigem o download de um dicionário. Se você também quiser um modelo de entrada de voz para um idioma específico, precisará baixá-lo também. Cada idioma já possui uma seleção de layouts de teclado associados; você pode escolher qual(is) layout(s) deseja adicionar ao adicionar o idioma. https://video.nostr.build/c775288b7a8ee8d75816af0c7a25f2aa0b4ecc99973fd442b2badc308fa38109.mp4
Mudar idioma.
Existem duas maneiras de alternar o idioma. A primeira é pressionando o ícone do globo na Barra de Ações, localizada próximo ao canto superior esquerdo do teclado. A segunda é pressionando longamente ou deslizando a barra de espaço; você pode personalizar o comportamento de troca de idioma da barra de espaço acessando Configurações -> Teclado e Digitação -> Teclas de Pressão Longa e Barra de Espaço -> Comportamento da Barra de Espaço . Você também pode atribuir o ícone do globo como a Tecla de Ação para que fique ao lado da barra de espaço, que pode ser acessada no menu Todas as Ações pressionando a tecla de reticências (...) no canto superior esquerdo do teclado e, em seguida, acessando Editar Ações. https://video.nostr.build/ed6f7f63a9c203cd59f46419ef54a4b8b442f070f802a688ca7d682bd6811bcb.mp4
Adicionar dicionário.
Alguns idiomas têm um dicionário integrado, mas a maioria não. Se o idioma que você está instalando não tiver um dicionário integrado, você pode iniciar a instalação em nosso site acessando Idiomas e Modelos -> Dicionário (no idioma que você está instalando) -> Explorar -> Baixar (em nosso site). https://video.nostr.build/3b1e09289953b658a9cef33c41bd711095556bc48290cb2ed066d4d0a5186371.mp4
Habilitar digitação multilíngue.
Você pode habilitar a digitação multilíngue para um ou mais idiomas acessando Idiomas e modelos e marcando a caixa Digitação multilíngue no(s) idioma(s) para os quais deseja habilitar a digitação multilíngue. https://video.nostr.build/29f683410626219499787bd63058d159719553f8e33a9f3c659c51c375a682fb.mp4
Criar layout personalizado.
Se desejar criar seu próprio layout personalizado para um idioma específico, você pode fazê-lo ativando Configurações do Desenvolvedor -> Layouts Personalizados -> Criar novo layout . Mais informações sobre layouts personalizados podem ser encontradas https://github.com/futo-org/futo-keyboard-layouts . A personalização das configurações de pressionamento longo tecla por tecla ainda não é suportada, mas está em processo de implementação. https://video.nostr.build/b5993090e28794d0305424dd352ca83760bb87002c57930e80513de5917fad8d.mp4
Teclado e Digitação – Personalize o comportamento das teclas, o tamanho do teclado e outras preferências de digitação.
Previsão de texto.
O menu no qual você define suas preferências para correção automática e sugestões personalizadas. Modelo de Linguagem do Transformador Você pode fazer com que o teclado preveja a próxima palavra que você digitará ou faça correções automáticas mais inteligentes, que usam um modelo de linguagem Transformer pré-treinado com base em conjuntos de dados disponíveis publicamente, ativando o Transformer LM . Observação: atualmente, isso funciona apenas em inglês, mas estamos trabalhando para torná-lo compatível com outros idiomas. Ajuste fino do transformador Você pode fazer com que o teclado memorize o que você digita e quais sugestões você seleciona, o que treina o modelo de idioma (enquanto o telefone estiver inativo) para prever quais palavras sugerir e corrigir automaticamente enquanto você digita, ativando o ajuste fino do Transformer . Observação: este é o seu modelo de idioma pessoal e o FUTO não visualiza nem armazena nenhum dos seus dados. https://video.nostr.build/688354a63bdc48a9dd3f8605854b5631ac011009c6105f93cfa0b52b46bc40d3.mp4
Previsão de texto.
O menu no qual você define suas preferências para correção automática e sugestões personalizadas. Modelo de Linguagem do Transformador Você pode fazer com que o teclado preveja a próxima palavra que você digitará ou faça correções automáticas mais inteligentes, que usam um modelo de linguagem Transformer pré-treinado com base em conjuntos de dados disponíveis publicamente, ativando o Transformer LM . Observação: atualmente, isso funciona apenas em inglês, mas estamos trabalhando para torná-lo compatível com outros idiomas.
Ajuste fino do transformador.
Você pode fazer com que o teclado memorize o que você digita e quais sugestões você seleciona, o que treina o modelo de idioma (enquanto o telefone estiver inativo) para prever quais palavras sugerir e corrigir automaticamente enquanto você digita, ativando o ajuste fino do Transformer . Observação: este é o seu modelo de idioma pessoal e o FUTO não visualiza nem armazena nenhum dos seus dados.
Força do Modelo de Linguagem do Transformador.
Você pode fazer com que a correção automática se comporte mais como o teclado AOSP ou mais como a rede neural acessando Parâmetros avançados -> Intensidade do LM do transformador e arrastando o controle deslizante para um valor menor (o que tornará o comportamento da correção automática mais parecido com o teclado AOSP) ou um valor maior (o que tornará a correção automática mais dependente da rede neural). Limiar de correção automática Você pode alterar o limite da correção automática para que ela ocorra com mais ou menos frequência acessando Parâmetros avançados -> Limite de correção automática e arrastando o controle deslizante para um valor menor (o que fará com que a correção automática ocorra com mais frequência, mas também corrija erros com mais frequência) ou um valor maior (o que fará com que a correção automática ocorra com menos frequência, mas também corrija erros com menos frequência). https://video.nostr.build/ea9c100081acfcab60343c494a91f789ef8143c92343522ec34c714913631cf7.mp4
Lista negra de palavras.
Você pode colocar sugestões de palavras na lista negra, o que impedirá que o teclado continue sugerindo palavras na lista negra, acessando Sugestões na lista negra e adicionando as palavras que você gostaria de colocar na lista negra.
Palavras ofensivas.
Você pode bloquear palavras ofensivas, como palavrões comuns, acessando Sugestões na Lista Negra e marcando a opção Bloquear Palavras Ofensivas . Observação: a opção Bloquear Palavras Ofensivas está ativada por padrão. https://video.nostr.build/ee72f3940b9789bbea222c95ee74d646aae1a0f3bf658ef8114c6f7942bb50f5.mp4
Correção automática.
Você pode ativar a capacidade de corrigir automaticamente palavras digitadas incorretamente ao pressionar a barra de espaço ou digitar pontuação ativando a Correção automática.
Sugestões de correção.
Você pode ativar a capacidade de exibir palavras sugeridas enquanto digita marcando a opção Mostrar sugestões de correção.
Sugestões de palavras.
Você pode ativar a capacidade de aprender com suas comunicações e dados digitados para melhorar as sugestões ativando as Sugestões personalizadas . Observação: desativar as Sugestões personalizadas também desativa o ajuste fino do Transformer. https://video.nostr.build/2c22d109b9192eac8fe4533b3f8e3e1b5896dfd043817bd460c48a5b989b7a2f.mp4
Entrada de Voz – Configure a entrada de voz offline, incluindo a duração e a conversão de fala em texto.
Entrada de voz.
O menu no qual você define suas preferências de entrada de voz, como duração da entrada e configurações de conversão de fala em texto. Entrada de voz integrada Você pode desabilitar a entrada de voz integrada do teclado e, em vez disso, usar o provedor de entrada de voz de um aplicativo externo desativando a opção Desabilitar entrada de voz integrada. https://video.nostr.build/68916e5b338a9f999f45aa1828a6e05ccbf8def46da9516c0f516b40ca8c827b.mp4
Sons de indicação.
Você pode habilitar a capacidade de reproduzir sons ao iniciar e cancelar a entrada de voz ativando Sons de indicação. https://video.nostr.build/7f5fb6a6173c4db18945e138146fe65444e40953d85cee1f09c1a21d236d21f5.mp4
Progresso Detalhado.
Você pode habilitar a capacidade de exibir informações detalhadas, como indicar que o microfone está sendo usado, ativando Progresso detalhado. https://video.nostr.build/8ac2bb6bdd6e7f8bd4b45da423e782c152a2b4320f2e090cbb99fd5c78e8f44f.mp4
Microfone Bluetooth.
Você pode fazer com que a entrada de voz prefira automaticamente seu microfone Bluetooth em vez do microfone integrado, ativando Preferir microfone Bluetooth. https://video.nostr.build/c11404aa6fec2dda71ceb3aaee916c6761b3015fef9575a352de66b7310dad07.mp4
Foco de áudio.
Você pode fazer com que a entrada de voz pause automaticamente vídeos ou músicas quando ela estiver ativada, ativando o Foco de Áudio. https://video.nostr.build/4ac82af53298733d0c5013ef28befb8b2adeb4a4949604308317e124b6431d40.mp4
Supressão de Símbolos.
Por padrão, a entrada de voz transcreve apenas texto básico e pontuação. Você pode desativar a opção "Suprimir símbolos" para liberar a entrada de voz da transcrição de caracteres especiais (por exemplo, @, $ ou %). Observação: Isso não afeta a forma como a entrada de voz interpreta palavras literais (por exemplo, "vírgula", "ponto final"). https://video.nostr.build/10de49c5a9e35508caa14b66da28fae991a5ac8eabad9b086959fba18c07f8f3.mp4
Entrada de voz de formato longo.
Você pode desativar o limite padrão de 30 segundos para entrada de voz ativando a opção Entrada de voz longa . Observação: a qualidade da saída pode ser prejudicada com entradas longas. https://video.nostr.build/f438ee7a42939a5a3e6d6c4471905f836f038495eb3a00b39d9996d0e552c200.mp4
Parada automática em silêncio.
Você pode fazer com que a entrada de voz pare automaticamente quando o silêncio for detectado, ativando a opção Parar automaticamente ao silenciar . Observação: se houver muito ruído de fundo, pode ser necessário interromper manualmente a entrada de voz. Ative também a entrada de voz longa para evitar a interrupção após 30 segundos. https://video.nostr.build/056567696d513add63f6dd254c0a3001530917e05e792de80c12796d43958671.mp4
Dicionário Pessoal – Adicione palavras personalizadas para que o teclado aprenda e sugira com mais precisão.
Dicionário Pessoal.
O menu no qual você cria seu dicionário pessoal de palavras que o teclado irá lembrar e sugerir. Adicionar ao dicionário Você pode adicionar uma palavra ou frase ao seu dicionário pessoal pressionando o ícone de adição na tela "Dicionário pessoal" . Você também pode criar um atalho para ela no campo "Atalho" ao adicionar a palavra ou frase. https://video.nostr.build/dec41c666b9f2276cc20d9096e3a9b542b570afd1f679d8d0e8c43c8ea46bfcb.mp4
Excluir do dicionário.
Você pode excluir uma palavra ou frase do seu dicionário pessoal clicando nessa palavra ou frase e clicando no ícone de lixeira no canto superior direito. https://video.nostr.build/aca25643b5c7ead4c5d522709af4bc337911e49c4743b97dc75f6b877449143e.mp4
Tema – Escolha entre os temas disponíveis ou personalize a aparência do teclado conforme seu gosto.
Tema.
O menu no qual você seleciona seu tema preferido para o teclado. Alterar tema Você pode escolher entre uma variedade de temas para o teclado, incluindo Modo Escuro, Modo Claro, Automático Dinâmico, Escuro Dinâmico, Claro Dinâmico, Material AOSP Escuro, Material AOSP Claro, Roxo Escuro AMOLED, Girassol, Queda de Neve, Cinza Aço, Esmeralda, Algodão Doce, Luz do Mar Profundo, Escuro do Mar Profundo, Gradiente 1, Tema FUTO VI ou Tema Construção . A possibilidade de personalizar seu tema será disponibilizada em breve. https://video.nostr.build/90c8de72f08cb0d8c40ac2fba2fd39451ff63ec1592ddd2629d0891c104bc61e.mp4
Fronteiras Principais.
Você pode habilitar as bordas das teclas rolando para baixo até o final e ativando Bordas das teclas . https://video.nostr.build/fa2087d68ce3fb2d3adb84cc2ec19c4d5383beb8823a4b6d1d85378ab3507ab1.mp4
Site oficial https://keyboard.futo.org/
Baixar no fdroid. https://app.futo.org/fdroid/repo/
Para instalar através do Obtainium , basta ir em Adicionar Aplicativo e colar esta URL do repositório: https://github.com/futo-org/android-keyboard
A adição pode demorar um pouco dependendo da velocidade da sua internet, pois o APK precisa ser baixado.
-
 @ 3f770d65:7a745b24
2025-04-21 00:15:06
@ 3f770d65:7a745b24
2025-04-21 00:15:06At the recent Launch Music Festival and Conference in Lancaster, PA, featuring over 120 musicians across three days, I volunteered my time with Tunestr and Phantom Power Music's initiative to introduce artists to Bitcoin, Nostr, and the value-for-value model. Tunestr sponsored a stage, live-streaming 21 bands to platforms like Tunestr.io, Fountain.fm and other Nostr/Podcasting 2.0 apps and on-boarding as many others as possible at our conference booth. You may have seen me spamming about this over the last few days.
V4V Earnings
Day 1: 180,000 sats
Day 2: 300,000 sats
Day 3: Over 500,000 sats
Who?
Here are the artists that were on-boarded to Fountain and were live streaming on the Value-for-Value stage:
nostr:npub1cruu4z0hwg7n3r2k7262vx8jsmra3xpku85frl5fnfvrwz7rd7mq7e403w nostr:npub12xeh3n7w8700z4tpd6xlhlvg4vtg4pvpxd584ll5sva539tutc3q0tn3tz nostr:npub1rc80p4v60uzfhvdgxemhvcqnzdj7t59xujxdy0lcjxml3uwdezyqtrpe0j @npub16vxr4pc2ww3yaez9q4s53zkejjfd0djs9lfe55sjhnqkh nostr:npub10uspdzg4fl7md95mqnjszxx82ckdly8ezac0t3s06a0gsf4f3lys8ypeak nostr:npub1gnyzexr40qut0za2c4a0x27p4e3qc22wekhcw3uvdx8mwa3pen0s9z90wk nostr:npub13qrrw2h4z52m7jh0spefrwtysl4psfkfv6j4j672se5hkhvtyw7qu0almy nostr:npub1p0kuqxxw2mxczc90vcurvfq7ljuw2394kkqk6gqnn2cq0y9eq5nq87jtkk nostr:npub182kq0sdp7chm67uq58cf4vvl3lk37z8mm5k5067xe09fqqaaxjsqlcazej nostr:npub162hr8kd96vxlanvggl08hmyy37qsn8ehgj7za7squl83um56epnswkr399 nostr:npub17jzk5ex2rafres09c4dnn5mm00eejye6nrurnlla6yn22zcpl7vqg6vhvx nostr:npub176rnksulheuanfx8y8cr2mrth4lh33svvpztggjjm6j2pqw6m56sq7s9vz nostr:npub1akv7t7xpalhsc4nseljs0c886jzuhq8u42qdcwvu972f3mme9tjsgp5xxk nostr:npub18x0gv872489lrczp9d9m4hx59r754x7p9rg2jkgvt7ul3kuqewtqsssn24
Many more musicians were on-boarded to Fountain, however, we were unable to obtain all of their npubs.
THANK YOU TO ALL ZAPPERS AND BOOSTERS!
Musicians “Get It”
My key takeaway was the musicians' absolute understanding that the current digital landscape along with legacy social media is failing them. Every artist I spoke with recognized how algorithms hinder fan connection and how gatekeepers prevent fair compensation for their work. They all use Spotify, but they only do so out of necessity. They felt the music industry is primed for both a social and monetary revolution. Some of them were even speaking my language…
Because of this, concepts like decentralization, censorship resistance, owning your content, and controlling your social graph weren't just understood by them, they were instantly embraced. The excitement was real; they immediately saw the potential and agreed with me. Bitcoin and Nostr felt genuinely punk rock and that helped a lot of them identify with what we were offering them.
The Tools and the Issues
While the Nostr ecosystem offers a wide variety of tools, we focused on introducing three key applications at this event to keep things clear for newcomers:
- Fountain, with a music focus, was the primary tool for onboarding attendees onto Nostr. Fountain was also chosen thanks to Fountain’s built-in Lightning wallet.
- Primal, as a social alternative, was demonstrated to show how users can take their Nostr identity and content seamlessly between different applications.
- Tunestr.io, lastly was showcased for its live video streaming capabilities.
Although we highlighted these three, we did inform attendees about the broader range of available apps and pointed them to
nostrapps.comif they wanted to explore further, aiming to educate without overwhelming them.This review highlights several UX issues with the Fountain app, particularly concerning profile updates, wallet functionality, and user discovery. While Fountain does work well, these minor hiccups make it extremely hard for on-boarding and education.
- Profile Issues:
- When a user edits their profile (e.g., Username/Nostr address, Lightning address) either during or after creation, the changes don't appear to consistently update across the app or sync correctly with Nostr relays.
- Specifically, the main profile display continues to show the old default Username/Nostr address and Lightning address inside Fountain and on other Nostr clients.
- However, the updated Username/Nostr address does appear on https://fountain.fm (chosen-username@fountain.fm) and is visible within the "Edit Profile" screen itself in the app.
- This inconsistency is confusing for users, as they see their updated information in some places but not on their main public-facing profile within the app. I confirmed this by observing a new user sign up and edit their username – the edit screen showed the new name, but the profile display in Fountain did not update and we did not see it inside Primal, Damus, Amethyst, etc.
- Wallet Limitations:
- The app's built-in wallet cannot scan Lightning address QR codes to initiate payments.
- This caused problems during the event where users imported Bitcoin from Azte.co vouchers into their Fountain wallets. When they tried to Zap a band by scanning a QR code on the live tally board, Fountain displayed an error message stating the invoice or QR code was invalid.
- While suggesting musicians install Primal as a second Nostr app was a potential fix for the QR code issue, (and I mentioned it to some), the burden of onboarding users onto two separate applications, potentially managing two different wallets, and explaining which one works for specific tasks creates a confusing and frustrating user experience.
- Search Difficulties:
- Finding other users within the Fountain app is challenging. I was unable to find profiles from brand new users by entering their chosen Fountain username.
- To find a new user, I had to resort to visiting their profile on the web (fountain.fm/username) to retrieve their npub. Then, open Primal and follow them. Finally, when searching for their username, since I was now following them, I was able to find their profile.
- This search issue is compounded by the profile syncing problem mentioned earlier, as even if found via other clients, their displayed information is outdated.
- Searching for the event to Boost/Zap inside Fountain was harder than it should have been the first two days as the live stream did not appear at the top of the screen inside the tap. This was resolved on the third day of the event.
Improving the Onboarding Experience
To better support user growth, educators and on-boarders need more feature complete and user-friendly applications. I love our developers and I will always sing their praises from the highest mountain tops, however I also recognize that the current tools present challenges that hinder a smooth onboarding experience.
One potential approach explored was guiding users to use Primal (including its built-in wallet) in conjunction with Wavlake via Nostr Wallet Connect (NWC). While this could facilitate certain functions like music streaming, zaps, and QR code scanning (which require both Primal and Wavlake apps), Wavlake itself has usability issues. These include inconsistent or separate profiles between web and mobile apps, persistent "Login" buttons even when logged in on the mobile app with a Nostr identity, and the minor inconvenience of needing two separate applications. Although NWC setup is relatively easy and helps streamline the process, the need to switch between apps adds complexity, especially when time is limited and we’re aiming to showcase the benefits of this new system.
Ultimately, we need applications that are more feature-complete and intuitive for mainstream users to improve the onboarding experience significantly.
Looking forward to the future
I anticipate that most of these issues will be resolved when these applications address them in the near future. Specifically, this would involve Fountain fixing its profile issues and integrating Nostr Wallet Connect (NWC) to allow users to utilize their Primal wallet, or by enabling the scanning of QR codes that pay out to Lightning addresses. Alternatively, if Wavlake resolves the consistency problems mentioned earlier, this would also significantly improve the situation giving us two viable solutions for musicians.
My ideal onboarding event experience would involve having all the previously mentioned issues resolved. Additionally, I would love to see every attendee receive a $5 or $10 voucher to help them start engaging with value-for-value, rather than just the limited number we distributed recently. The goal is to have everyone actively zapping and sending Bitcoin throughout the event. Maybe we can find a large sponsor to facilitate this in the future?
What's particularly exciting is the Launch conference's strong interest in integrating value-for-value across their entire program for all musicians and speakers at their next event in Dallas, Texas, coming later this fall. This presents a significant opportunity to onboard over 100+ musicians to Bitcoin and Nostr, which in turn will help onboard their fans and supporters.
We need significantly more zaps and more zappers! It's unreasonable to expect the same dedicated individuals to continuously support new users; they are being bled dry. A shift is needed towards more people using bitcoin for everyday transactions, treating it as money. This brings me back to my ideal onboarding experience: securing a sponsor to essentially give participants bitcoin funds specifically for zapping and tipping artists. This method serves as a practical lesson in using bitcoin as money and showcases the value-for-value principle from the outset.
-
 @ 7d33ba57:1b82db35
2025-04-23 11:40:24
@ 7d33ba57:1b82db35
2025-04-23 11:40:24Perched on the northern coast of Poland, Gdańsk is a stunning port city with a unique blend of Hanseatic charm, maritime heritage, and resilience through centuries of dramatic history. With its colorful façades, cobbled streets, and strong cultural identity, Gdańsk is one of Poland’s most compelling cities—perfect for history buffs, architecture lovers, and coastal wanderers.
🏛️ What to See & Do in Gdańsk
🌈 Stroll Down Długi Targ (Long Market)
- The heart of Gdańsk’s Old Town, lined with beautifully restored colorful merchant houses
- Admire the Neptune Fountain, Artus Court, and the grand Main Town Hall
⚓ The Crane (Żuraw) & Motława River
- Gdańsk’s medieval port crane is an iconic symbol of its maritime past
- Walk along the Motława River promenade, with boats, cafés, and views of historic granaries
⛪ St. Mary’s Church (Bazylika Mariacka)
- One of the largest brick churches in the world
- Climb the tower for panoramic views of the city and harbor
🕊️ Learn Gdańsk’s Layers of History
🏰 Westerplatte
- The site where World War II began in 1939
- A powerful memorial and museum amid coastal nature
🛠️ European Solidarity Centre
- A striking modern museum dedicated to the Solidarity movement that helped end communism in Poland
- Insightful, moving, and highly interactive
🏖️ Relax by the Baltic Sea
- Head to Brzeźno Beach or nearby Sopot for golden sands, seaside promenades, and beach cafés
- In summer, the Baltic vibes are strong—swimming, sunsets, and pier strolls

🍽️ Tastes of Gdańsk
- Try pierogi, fresh Baltic fish, golden smoked cheese, and żurek soup
- Visit a local milk bar or enjoy a craft beer at one of Gdańsk’s buzzing breweries
- Don’t miss the amber jewelry shops—Gdańsk is known as the Amber Capital of the World
🚆 Getting There
- Easily reached by train or plane from Warsaw and other major European cities
- Compact city center—walkable and scenic
-
 @ 7d33ba57:1b82db35
2025-04-23 10:28:49
@ 7d33ba57:1b82db35
2025-04-23 10:28:49Lake Bled is straight out of a storybook—an emerald alpine lake with a tiny island crowned by a church, surrounded by forested hills and overlooked by a clifftop castle. Just an hour from Ljubljana, this Slovenian gem is perfect for romantic getaways, outdoor adventures, or a peaceful escape into nature.
🌊 Top Things to Do in Bled
🛶 Bled Island & Church of the Assumption
- Take a traditional pletna boat or rent a rowboat to reach the only natural island in Slovenia
- Ring the church bell and make a wish—it’s a local tradition!
- Enjoy serene lake views from the island’s stone steps
🏰 Bled Castle (Blejski Grad)
- Perched on a cliff 130 meters above the lake
- Explore the medieval halls, museum, and wine cellar
- The terrace views? Absolutely unforgettable—especially at sunset
🚶♂️ Walk or Cycle the Lakeside Path
- A 6 km flat path circles the lake—perfect for a leisurely stroll or bike ride
- Stop for lakeside cafés, photo ops, or a quick swim in summer
🌄 Outdoor Adventures Beyond the Lake
- Hike to Mala Osojnica Viewpoint for the most iconic panoramic view of Lake Bled
- Go paddleboarding, kayaking, or swimming in warmer months
- Nearby Vintgar Gorge offers a stunning wooden path through a narrow, turquoise canyon
🍰 Try the Famous Bled Cream Cake (Kremšnita)
- A must-try dessert with layers of vanilla custard, cream, and crispy pastry
- Best enjoyed with a coffee on a terrace overlooking the lake

🏡 Where to Stay
- Lakeside hotels, cozy guesthouses, or charming Alpine-style B&Bs
- Some even offer views of the lake, castle, or Triglav National Park
🚗 Getting There
- Around 1 hour from Ljubljana by car, bus, or train
- Easy to combine with stops like Lake Bohinj or Triglav National Park
-
 @ fbf0e434:e1be6a39
2025-04-23 08:42:22
@ fbf0e434:e1be6a39
2025-04-23 08:42:22Hackathon 概要
Naija HackAtom 圆满落幕。此次活动共有 160 名开发者注册参与,成功展示 51 个通过审核的项目。该黑客马拉松旨在推动尼日利亚 Web3 社区内 Interchain、Cosmos Hub 和 Atom 经济区(AEZ)的发展,主要目标是培养本土人才、提供资源支持,并开发基于 $ATOM 代币的区块链应用。
活动聚焦 Interchain 安全性、Atom 经济区、CosmWasm 以及 ATOM 的具体发展等关键领域。其中,跨链汇款平台、面向非洲农民的去中心化市场等项目尤为亮眼,充分展现了 Cosmos 技术的创新应用潜力。
本次黑客马拉松设立了 10000 美元的奖金池,用于奖励在 UI/UX 设计、社区参与度及 Atom 创新应用方案等方面表现突出的项目。在系列研讨会与公开教程的辅助下,参赛者提交的项目从技术可行性、创新性、社会影响力和用户体验等维度进行评审。活动凭借广泛的参与度与丰富的创新成果,有力推动了尼日利亚乃至整个非洲区块链生态的发展。
Hackathon 获奖者
Naija HackAtom 作为尼日利亚首个以 Cosmos 和 ATOM 为核心的黑客马拉松,吸引了超 500 人参与,其中开发者达 160 名。在 ATOMAccelerator 的支持下,活动共收到 57 个项目提交,最终 18 个项目脱颖而出,入围决赛。
主奖项获奖者
- Beep: 一个用于Naira代币化的平台,促进了与tAtom无缝交易和交换。
- Padi [Crypto Go Fund Me]: 一个基于区块链的平台,用于进行代币驱动的筹款活动。
- ATwork: 一个去中心化的自由职业平台,通过Cosmos区块链增强自由职业者与客户之间的合作。
独特解决方案/产品奖项获奖者
- LendPro: 一个借贷协议,通过区块链促进合作金融治理。
- Tradi-App: 一个在Secret Network上的隐私AI交易分析平台,提供市场见解。
- Delegated Staking Agent(DSA): 提供Cosmos生态系统中的质押和治理投票,具有AI增强的安全性能。
- Neutron NFT Launch: 通过整合AI、区块链和NFT技术简化NFT的创建和交易。
Secret Network 赏金获奖者
- Prompt Hub: 一个专注隐私、AI生成提示的市场,带有集成功能。
- Delegated Staking Agent(DSA)
- Secret AI Writer: 一个AI写作平台,提供安全的区块链存储和隐私中心的内容生成。
- Tradi-App
ChihuahuaChain 赏金获奖者
- Neutron NFT Launch
- woof-dot-fun: 一个复制Pump.Fun的项目,具有代币和债券曲线功能。
- Vault Quest: 一个无损奖品储蓄协议,利用DeFi策略进行基于收益的奖品分配。
Akash 赏金获奖者
- Jarvis AI: 一个语音激活的助手,旨在高效的云资源管理。
有关Naija HackAtom期间提交的所有项目的完整列表,请访问这里。
关于组织者
Cosmos Hub Africa
Cosmos Hub Africa专注于在非洲推广区块链技术和Cosmos生态系统。该组织在去中心化网络开发和区块链行业内的协作方面发挥着重要作用。其贡献包括提高平台之间可扩展性和互操作性的项目。目前,Cosmos Hub Africa致力于推进该地区的区块链教育和基础设施,旨在促进与传统经济和金融系统的创新和整合。
-
 @ fd06f542:8d6d54cd
2025-04-23 07:51:30
@ fd06f542:8d6d54cd
2025-04-23 07:51:30- 第三章、NIP-03: OpenTimestamps Attestations for Events
- 第四章、NIP-04: Encrypted Direct Message
- 第五章、NIP-05: Mapping Nostr keys to DNS-based internet identifiers
- 第六章、NIP-06: Basic key derivation from mnemonic seed phrase
- 第七章、NIP-07: window.nostr capability for web browsers
- 第八章、NIP-08: Handling Mentions --- unrecommended: deprecated in favor of NIP-27
- 第九章、NIP-09: Event Deletion Request
- 第十章、NIP-10: Text Notes and Threads
- 第十一章、NIP-11: Relay Information Document
- 第十二章、NIP-13: Proof of Work
- 第十三章、NIP-14: Subject tag in text events
- 第十四章、NIP-15: Nostr Marketplace (for resilient marketplaces)
- 第十五章、NIP-17: Private Direct Messages
- 第十六章、NIP-18: Reposts
- 第十七章、NIP-19: bech32-encoded entities
-
 @ da0b9bc3:4e30a4a9
2025-04-23 07:50:49
@ da0b9bc3:4e30a4a9
2025-04-23 07:50:49Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/954269
-
 @ fd06f542:8d6d54cd
2025-04-23 06:39:15
@ fd06f542:8d6d54cd
2025-04-23 06:39:15有时候写点日志,可以 记录一点琐碎的事情。
! 也许这就是 这就是 这个blog存在的原因吧。
如何将docsify 变成一个渲染blog的 工具
我用了很多办法,但是关键点还是这个 方法。 无须配置 window.$docsify ={} ```js $: if (blogItem) {
compiledContent = window.__current_docsify_compiler__.compile(blogItem.content); }```
直接用内容的 功能转换。
但是渲染的时候要注意:
html <article class="markdown-section" id="main"> {@html compiledContent} </article>内容要加上这个外框,这个问题我调试了一天在知道...原来是少了他,导致缺少很多东西。
如何上传背景图片?
- 一定要点击 封面图区域的空白处, 让 编辑框失去焦点。
- 再 把鼠标放在 虚线封面图区域,就可以ctrl+v 粘贴截图了。
其他使用事项,我想起来再写吧。
-
 @ c631e267:c2b78d3e
2025-04-20 19:54:32
@ c631e267:c2b78d3e
2025-04-20 19:54:32Es ist völlig unbestritten, dass der Angriff der russischen Armee auf die Ukraine im Februar 2022 strikt zu verurteilen ist. Ebenso unbestritten ist Russland unter Wladimir Putin keine brillante Demokratie. Aus diesen Tatsachen lässt sich jedoch nicht das finstere Bild des russischen Präsidenten – und erst recht nicht des Landes – begründen, das uns durchweg vorgesetzt wird und den Kern des aktuellen europäischen Bedrohungs-Szenarios darstellt. Da müssen wir schon etwas genauer hinschauen.
Der vorliegende Artikel versucht derweil nicht, den Einsatz von Gewalt oder die Verletzung von Menschenrechten zu rechtfertigen oder zu entschuldigen – ganz im Gegenteil. Dass jedoch der Verdacht des «Putinverstehers» sofort latent im Raume steht, verdeutlicht, was beim Thema «Russland» passiert: Meinungsmache und Manipulation.
Angesichts der mentalen Mobilmachung seitens Politik und Medien sowie des Bestrebens, einen bevorstehenden Krieg mit Russland geradezu herbeizureden, ist es notwendig, dieser fatalen Entwicklung entgegenzutreten. Wenn wir uns nur ein wenig von der herrschenden Schwarz-Weiß-Malerei freimachen, tauchen automatisch Fragen auf, die Risse im offiziellen Narrativ enthüllen. Grund genug, nachzuhaken.
Wer sich schon länger auch abseits der Staats- und sogenannten Leitmedien informiert, der wird in diesem Artikel vermutlich nicht viel Neues erfahren. Andere könnten hier ein paar unbekannte oder vergessene Aspekte entdecken. Möglicherweise klärt sich in diesem Kontext die Wahrnehmung der aktuellen (unserer eigenen!) Situation ein wenig.
Manipulation erkennen
Corona-«Pandemie», menschengemachter Klimawandel oder auch Ukraine-Krieg: Jede Menge Krisen, und für alle gibt es ein offizielles Narrativ, dessen Hinterfragung unerwünscht ist. Nun ist aber ein Narrativ einfach eine Erzählung, eine Geschichte (Latein: «narratio») und kein Tatsachenbericht. Und so wie ein Märchen soll auch das Narrativ eine Botschaft vermitteln.
Über die Methoden der Manipulation ist viel geschrieben worden, sowohl in Bezug auf das Individuum als auch auf die Massen. Sehr wertvolle Tipps dazu, wie man Manipulationen durchschauen kann, gibt ein Büchlein [1] von Albrecht Müller, dem Herausgeber der NachDenkSeiten.
Die Sprache selber eignet sich perfekt für die Manipulation. Beispielsweise kann die Wortwahl Bewertungen mitschwingen lassen, regelmäßiges Wiederholen (gerne auch von verschiedenen Seiten) lässt Dinge irgendwann «wahr» erscheinen, Übertreibungen fallen auf und hinterlassen wenigstens eine Spur im Gedächtnis, genauso wie Andeutungen. Belege spielen dabei keine Rolle.
Es gibt auffällig viele Sprachregelungen, die offenbar irgendwo getroffen und irgendwie koordiniert werden. Oder alle Redenschreiber und alle Medien kopieren sich neuerdings permanent gegenseitig. Welchen Zweck hat es wohl, wenn der Krieg in der Ukraine durchgängig und quasi wörtlich als «russischer Angriffskrieg auf die Ukraine» bezeichnet wird? Obwohl das in der Sache richtig ist, deutet die Art der Verwendung auf gezielte Beeinflussung hin und soll vor allem das Feindbild zementieren.
Sprachregelungen dienen oft der Absicherung einer einseitigen Darstellung. Das Gleiche gilt für das Verkürzen von Informationen bis hin zum hartnäckigen Verschweigen ganzer Themenbereiche. Auch hierfür gibt es rund um den Ukraine-Konflikt viele gute Beispiele.
Das gewünschte Ergebnis solcher Methoden ist eine Schwarz-Weiß-Malerei, bei der einer eindeutig als «der Böse» markiert ist und die anderen automatisch «die Guten» sind. Das ist praktisch und demonstriert gleichzeitig ein weiteres Manipulationswerkzeug: die Verwendung von Doppelstandards. Wenn man es schafft, bei wichtigen Themen regelmäßig mit zweierlei Maß zu messen, ohne dass das Publikum protestiert, dann hat man freie Bahn.
Experten zu bemühen, um bestimmte Sachverhalte zu erläutern, ist sicher sinnvoll, kann aber ebenso missbraucht werden, schon allein durch die Auswahl der jeweiligen Spezialisten. Seit «Corona» werden viele erfahrene und ehemals hoch angesehene Fachleute wegen der «falschen Meinung» diffamiert und gecancelt. [2] Das ist nicht nur ein brutaler Umgang mit Menschen, sondern auch eine extreme Form, die öffentliche Meinung zu steuern.
Wann immer wir also erkennen (weil wir aufmerksam waren), dass wir bei einem bestimmten Thema manipuliert werden, dann sind zwei logische und notwendige Fragen: Warum? Und was ist denn richtig? In unserem Russland-Kontext haben die Antworten darauf viel mit Geopolitik und Geschichte zu tun.
Ist Russland aggressiv und expansiv?
Angeblich plant Russland, europäische NATO-Staaten anzugreifen, nach dem Motto: «Zuerst die Ukraine, dann den Rest». In Deutschland weiß man dafür sogar das Datum: «Wir müssen bis 2029 kriegstüchtig sein», versichert Verteidigungsminister Pistorius.
Historisch gesehen ist es allerdings eher umgekehrt: Russland, bzw. die Sowjetunion, ist bereits dreimal von Westeuropa aus militärisch angegriffen worden. Die Feldzüge Napoleons, des deutschen Kaiserreichs und Nazi-Deutschlands haben Millionen Menschen das Leben gekostet. Bei dem ausdrücklichen Vernichtungskrieg ab 1941 kam es außerdem zu Brutalitäten wie der zweieinhalbjährigen Belagerung Leningrads (heute St. Petersburg) durch Hitlers Wehrmacht. Deren Ziel, die Bevölkerung auszuhungern, wurde erreicht: über eine Million tote Zivilisten.
Trotz dieser Erfahrungen stimmte Michail Gorbatschow 1990 der deutschen Wiedervereinigung zu und die Sowjetunion zog ihre Truppen aus Osteuropa zurück (vgl. Abb. 1). Der Warschauer Pakt wurde aufgelöst, der Kalte Krieg formell beendet. Die Sowjets erhielten damals von führenden westlichen Politikern die Zusicherung, dass sich die NATO «keinen Zentimeter ostwärts» ausdehnen würde, das ist dokumentiert. [3]
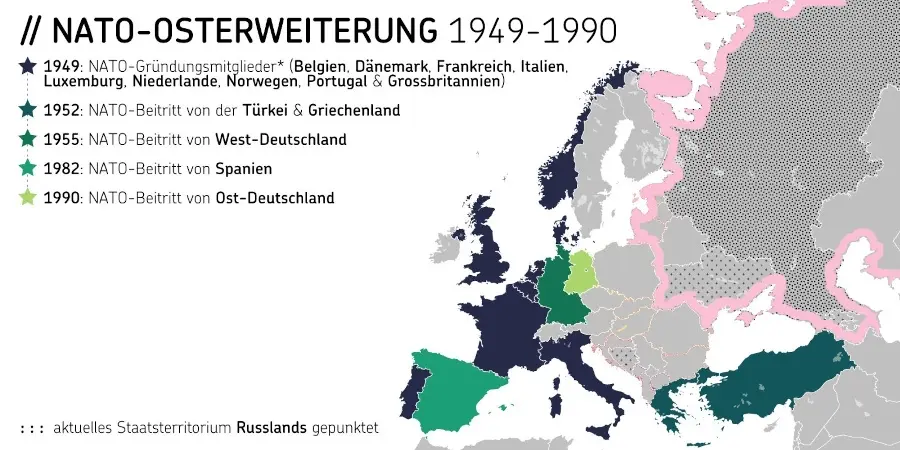
Expandiert ist die NATO trotzdem, und zwar bis an Russlands Grenzen (vgl. Abb. 2). Laut dem Politikberater Jeffrey Sachs handelt es sich dabei um ein langfristiges US-Projekt, das von Anfang an die Ukraine und Georgien mit einschloss. Offiziell wurde der Beitritt beiden Staaten 2008 angeboten. In jedem Fall könnte die massive Ost-Erweiterung seit 1999 aus russischer Sicht nicht nur als Vertrauensbruch, sondern durchaus auch als aggressiv betrachtet werden.
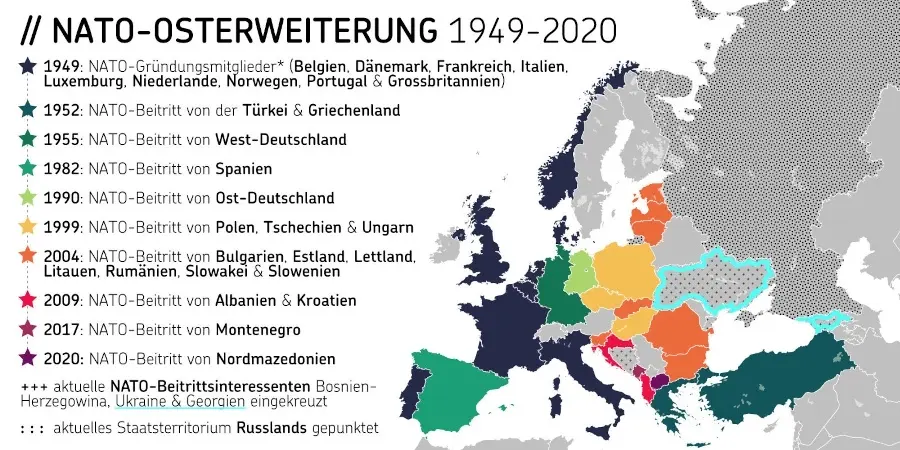
Russland hat den europäischen Staaten mehrfach die Hand ausgestreckt [4] für ein friedliches Zusammenleben und den «Aufbau des europäischen Hauses». Präsident Putin sei «in seiner ersten Amtszeit eine Chance für Europa» gewesen, urteilt die Journalistin und langjährige Russland-Korrespondentin der ARD, Gabriele Krone-Schmalz. Er habe damals viele positive Signale Richtung Westen gesendet.
Die Europäer jedoch waren scheinbar an einer Partnerschaft mit dem kontinentalen Nachbarn weniger interessiert als an der mit dem transatlantischen Hegemon. Sie verkennen bis heute, dass eine gedeihliche Zusammenarbeit in Eurasien eine Gefahr für die USA und deren bekundetes Bestreben ist, die «einzige Weltmacht» zu sein – «Full Spectrum Dominance» [5] nannte das Pentagon das. Statt einem neuen Kalten Krieg entgegenzuarbeiten, ließen sich europäische Staaten selber in völkerrechtswidrige «US-dominierte Angriffskriege» [6] verwickeln, wie in Serbien, Afghanistan, dem Irak, Libyen oder Syrien. Diese werden aber selten so benannt.
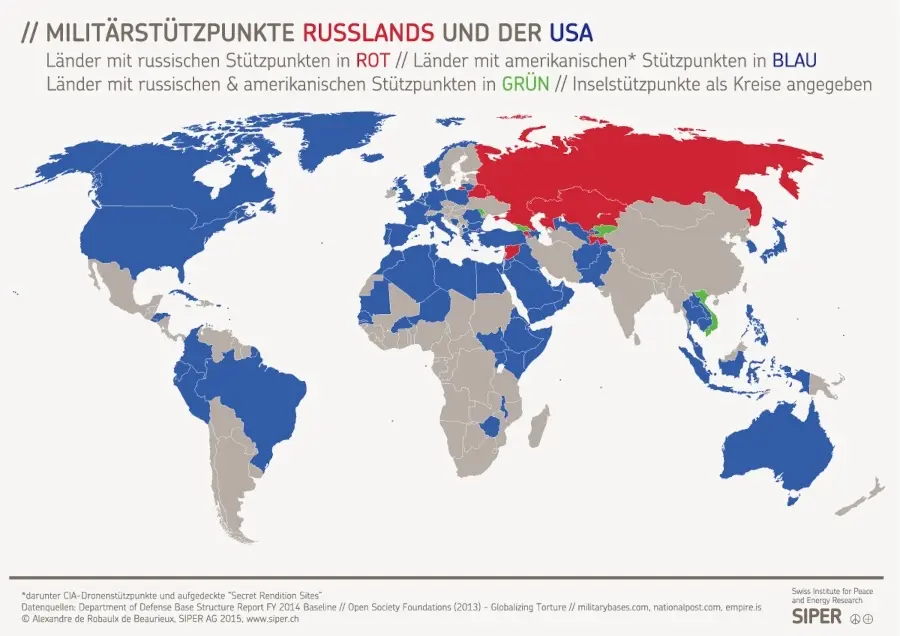
Speziell den Deutschen stünde außer einer Portion Realismus auch etwas mehr Dankbarkeit gut zu Gesicht. Das Geschichtsbewusstsein der Mehrheit scheint doch recht selektiv und das Selbstbewusstsein einiger etwas desorientiert zu sein. Bekanntermaßen waren es die Soldaten der sowjetischen Roten Armee, die unter hohen Opfern 1945 Deutschland «vom Faschismus befreit» haben. Bei den Gedenkfeiern zu 80 Jahren Kriegsende will jedoch das Auswärtige Amt – noch unter der Diplomatie-Expertin Baerbock, die sich schon länger offiziell im Krieg mit Russland wähnt, – nun keine Russen sehen: Sie sollen notfalls rausgeschmissen werden.
«Die Grundsatzfrage lautet: Geht es Russland um einen angemessenen Platz in einer globalen Sicherheitsarchitektur, oder ist Moskau schon seit langem auf einem imperialistischen Trip, der befürchten lassen muss, dass die Russen in fünf Jahren in Berlin stehen?»
So bringt Gabriele Krone-Schmalz [7] die eigentliche Frage auf den Punkt, die zur Einschätzung der Situation letztlich auch jeder für sich beantworten muss.
Was ist los in der Ukraine?
In der internationalen Politik geht es nie um Demokratie oder Menschenrechte, sondern immer um Interessen von Staaten. Diese These stammt von Egon Bahr, einem der Architekten der deutschen Ostpolitik des «Wandels durch Annäherung» aus den 1960er und 70er Jahren. Sie trifft auch auf den Ukraine-Konflikt zu, den handfeste geostrategische und wirtschaftliche Interessen beherrschen, obwohl dort angeblich «unsere Demokratie» verteidigt wird.
Es ist ein wesentliches Element des Ukraine-Narrativs und Teil der Manipulation, die Vorgeschichte des Krieges wegzulassen – mindestens die vor der russischen «Annexion» der Halbinsel Krim im März 2014, aber oft sogar komplett diejenige vor der Invasion Ende Februar 2022. Das Thema ist komplex, aber einige Aspekte, die für eine Beurteilung nicht unwichtig sind, will ich wenigstens kurz skizzieren. [8]
Das Gebiet der heutigen Ukraine und Russlands – die übrigens in der «Kiewer Rus» gemeinsame Wurzeln haben – hat der britische Geostratege Halford Mackinder bereits 1904 als eurasisches «Heartland» bezeichnet, dessen Kontrolle er eine große Bedeutung für die imperiale Strategie Großbritanniens zumaß. Für den ehemaligen Sicherheits- und außenpolitischen Berater mehrerer US-amerikanischer Präsidenten und Mitgründer der Trilateralen Kommission, Zbigniew Brzezinski, war die Ukraine nach der Auflösung der Sowjetunion ein wichtiger Spielstein auf dem «eurasischen Schachbrett», wegen seiner Nähe zu Russland, seiner Bodenschätze und seines Zugangs zum Schwarzen Meer.
Die Ukraine ist seit langem ein gespaltenes Land. Historisch zerrissen als Spielball externer Interessen und geprägt von ethnischen, kulturellen, religiösen und geografischen Unterschieden existiert bis heute, grob gesagt, eine Ost-West-Spaltung, welche die Suche nach einer nationalen Identität stark erschwert.
Insbesondere im Zuge der beiden Weltkriege sowie der Russischen Revolution entstanden tiefe Risse in der Bevölkerung. Ukrainer kämpften gegen Ukrainer, zum Beispiel die einen auf der Seite von Hitlers faschistischer Nazi-Armee und die anderen auf der von Stalins kommunistischer Roter Armee. Die Verbrechen auf beiden Seiten sind nicht vergessen. Dass nach der Unabhängigkeit 1991 versucht wurde, Figuren wie den radikalen Nationalisten Symon Petljura oder den Faschisten und Nazi-Kollaborateur Stepan Bandera als «Nationalhelden» zu installieren, verbessert die Sache nicht.
Während die USA und EU-Staaten zunehmend «ausländische Einmischung» (speziell russische) in «ihre Demokratien» wittern, betreiben sie genau dies seit Jahrzehnten in vielen Ländern der Welt. Die seit den 2000er Jahren bekannten «Farbrevolutionen» in Osteuropa werden oft als Methode des Regierungsumsturzes durch von außen gesteuerte «demokratische» Volksaufstände beschrieben. Diese Strategie geht auf Analysen zum «Schwarmverhalten» [9] seit den 1960er Jahren zurück (Studentenproteste), wo es um die potenzielle Wirksamkeit einer «rebellischen Hysterie» von Jugendlichen bei postmodernen Staatsstreichen geht. Heute nennt sich dieses gezielte Kanalisieren der Massen zur Beseitigung unkooperativer Regierungen «Soft-Power».
In der Ukraine gab es mit der «Orangen Revolution» 2004 und dem «Euromaidan» 2014 gleich zwei solcher «Aufstände». Der erste erzwang wegen angeblicher Unregelmäßigkeiten eine Wiederholung der Wahlen, was mit Wiktor Juschtschenko als neuem Präsidenten endete. Dieser war ehemaliger Direktor der Nationalbank und Befürworter einer Annäherung an EU und NATO. Seine Frau, die First Lady, ist US-amerikanische «Philanthropin» und war Beamtin im Weißen Haus in der Reagan- und der Bush-Administration.
Im Gegensatz zu diesem ersten Event endete der sogenannte Euromaidan unfriedlich und blutig. Die mehrwöchigen Proteste gegen Präsident Wiktor Janukowitsch, in Teilen wegen des nicht unterzeichneten Assoziierungsabkommens mit der EU, wurden zunehmend gewalttätiger und von Nationalisten und Faschisten des «Rechten Sektors» dominiert. Sie mündeten Ende Februar 2014 auf dem Kiewer Unabhängigkeitsplatz (Maidan) in einem Massaker durch Scharfschützen. Dass deren Herkunft und die genauen Umstände nicht geklärt wurden, störte die Medien nur wenig. [10]
Janukowitsch musste fliehen, er trat nicht zurück. Vielmehr handelte es sich um einen gewaltsamen, allem Anschein nach vom Westen inszenierten Putsch. Laut Jeffrey Sachs war das kein Geheimnis, außer vielleicht für die Bürger. Die USA unterstützten die Post-Maidan-Regierung nicht nur, sie beeinflussten auch ihre Bildung. Das geht unter anderem aus dem berühmten «Fuck the EU»-Telefonat der US-Chefdiplomatin für die Ukraine, Victoria Nuland, mit Botschafter Geoffrey Pyatt hervor.
Dieser Bruch der demokratischen Verfassung war letztlich der Auslöser für die anschließenden Krisen auf der Krim und im Donbass (Ostukraine). Angesichts der ukrainischen Geschichte mussten die nationalistischen Tendenzen und die Beteiligung der rechten Gruppen an dem Umsturz bei der russigsprachigen Bevölkerung im Osten ungute Gefühle auslösen. Es gab Kritik an der Übergangsregierung, Befürworter einer Abspaltung und auch für einen Anschluss an Russland.
Ebenso konnte Wladimir Putin in dieser Situation durchaus Bedenken wegen des Status der russischen Militärbasis für seine Schwarzmeerflotte in Sewastopol auf der Krim haben, für die es einen langfristigen Pachtvertrag mit der Ukraine gab. Was im März 2014 auf der Krim stattfand, sei keine Annexion, sondern eine Abspaltung (Sezession) nach einem Referendum gewesen, also keine gewaltsame Aneignung, urteilte der Rechtswissenschaftler Reinhard Merkel in der FAZ sehr detailliert begründet. Übrigens hatte die Krim bereits zu Zeiten der Sowjetunion den Status einer autonomen Republik innerhalb der Ukrainischen SSR.
Anfang April 2014 wurden in der Ostukraine die «Volksrepubliken» Donezk und Lugansk ausgerufen. Die Kiewer Übergangsregierung ging unter der Bezeichnung «Anti-Terror-Operation» (ATO) militärisch gegen diesen, auch von Russland instrumentalisierten Widerstand vor. Zufällig war kurz zuvor CIA-Chef John Brennan in Kiew. Die Maßnahmen gingen unter dem seit Mai neuen ukrainischen Präsidenten, dem Milliardär Petro Poroschenko, weiter. Auch Wolodymyr Selenskyj beendete den Bürgerkrieg nicht, als er 2019 vom Präsidenten-Schauspieler, der Oligarchen entmachtet, zum Präsidenten wurde. Er fuhr fort, die eigene Bevölkerung zu bombardieren.
Mit dem Einmarsch russischer Truppen in die Ostukraine am 24. Februar 2022 begann die zweite Phase des Krieges. Die Wochen und Monate davor waren intensiv. Im November hatte die Ukraine mit den USA ein Abkommen über eine «strategische Partnerschaft» unterzeichnet. Darin sagten die Amerikaner ihre Unterstützung der EU- und NATO-Perspektive der Ukraine sowie quasi für die Rückeroberung der Krim zu. Dagegen ließ Putin der NATO und den USA im Dezember 2021 einen Vertragsentwurf über beiderseitige verbindliche Sicherheitsgarantien zukommen, den die NATO im Januar ablehnte. Im Februar eskalierte laut OSZE die Gewalt im Donbass.
Bereits wenige Wochen nach der Invasion, Ende März 2022, kam es in Istanbul zu Friedensverhandlungen, die fast zu einer Lösung geführt hätten. Dass der Krieg nicht damals bereits beendet wurde, lag daran, dass der Westen dies nicht wollte. Man war der Meinung, Russland durch die Ukraine in diesem Stellvertreterkrieg auf Dauer militärisch schwächen zu können. Angesichts von Hunderttausenden Toten, Verletzten und Traumatisierten, die als Folge seitdem zu beklagen sind, sowie dem Ausmaß der Zerstörung, fehlen einem die Worte.
Hasst der Westen die Russen?
Diese Frage drängt sich auf, wenn man das oft unerträglich feindselige Gebaren beobachtet, das beileibe nicht neu ist und vor Doppelmoral trieft. Russland und speziell die Person Wladimir Putins werden regelrecht dämonisiert, was gleichzeitig scheinbar jede Form von Diplomatie ausschließt.
Russlands militärische Stärke, seine geografische Lage, sein Rohstoffreichtum oder seine unabhängige diplomatische Tradition sind sicher Störfaktoren für das US-amerikanische Bestreben, der Boss in einer unipolaren Welt zu sein. Ein womöglich funktionierender eurasischer Kontinent, insbesondere gute Beziehungen zwischen Russland und Deutschland, war indes schon vor dem Ersten Weltkrieg eine Sorge des britischen Imperiums.
Ein «Vergehen» von Präsident Putin könnte gewesen sein, dass er die neoliberale Schocktherapie à la IWF und den Ausverkauf des Landes (auch an US-Konzerne) beendete, der unter seinem Vorgänger herrschte. Dabei zeigte er sich als Führungspersönlichkeit und als nicht so formbar wie Jelzin. Diese Aspekte allein sind aber heute vermutlich keine ausreichende Erklärung für ein derart gepflegtes Feindbild.
Der Historiker und Philosoph Hauke Ritz erweitert den Fokus der Fragestellung zu: «Warum hasst der Westen die Russen so sehr?», was er zum Beispiel mit dem Medienforscher Michael Meyen und mit der Politikwissenschaftlerin Ulrike Guérot bespricht. Ritz stellt die interessante These [11] auf, dass Russland eine Provokation für den Westen sei, welcher vor allem dessen kulturelles und intellektuelles Potenzial fürchte.
Die Russen sind Europäer aber anders, sagt Ritz. Diese «Fremdheit in der Ähnlichkeit» erzeuge vielleicht tiefe Ablehnungsgefühle. Obwohl Russlands Identität in der europäischen Kultur verwurzelt ist, verbinde es sich immer mit der Opposition in Europa. Als Beispiele nennt er die Kritik an der katholischen Kirche oder die Verbindung mit der Arbeiterbewegung. Christen, aber orthodox; Sozialismus statt Liberalismus. Das mache das Land zum Antagonisten des Westens und zu einer Bedrohung der Machtstrukturen in Europa.
Fazit
Selbstverständlich kann man Geschichte, Ereignisse und Entwicklungen immer auf verschiedene Arten lesen. Dieser Artikel, obwohl viel zu lang, konnte nur einige Aspekte der Ukraine-Tragödie anreißen, die in den offiziellen Darstellungen in der Regel nicht vorkommen. Mindestens dürfte damit jedoch klar geworden sein, dass die Russische Föderation bzw. Wladimir Putin nicht der alleinige Aggressor in diesem Konflikt ist. Das ist ein Stellvertreterkrieg zwischen USA/NATO (gut) und Russland (böse); die Ukraine (edel) wird dabei schlicht verheizt.
Das ist insofern von Bedeutung, als die gesamte europäische Kriegshysterie auf sorgsam kultivierten Freund-Feind-Bildern beruht. Nur so kann Konfrontation und Eskalation betrieben werden, denn damit werden die wahren Hintergründe und Motive verschleiert. Angst und Propaganda sind notwendig, damit die Menschen den Wahnsinn mitmachen. Sie werden belogen, um sie zuerst zu schröpfen und anschließend auf die Schlachtbank zu schicken. Das kann niemand wollen, außer den stets gleichen Profiteuren: die Rüstungs-Lobby und die großen Investoren, die schon immer an Zerstörung und Wiederaufbau verdient haben.
Apropos Investoren: Zu den Top-Verdienern und somit Hauptinteressenten an einer Fortführung des Krieges zählt BlackRock, einer der weltgrößten Vermögensverwalter. Der deutsche Bundeskanzler in spe, Friedrich Merz, der gerne «Taurus»-Marschflugkörper an die Ukraine liefern und die Krim-Brücke zerstören möchte, war von 2016 bis 2020 Aufsichtsratsvorsitzender von BlackRock in Deutschland. Aber das hat natürlich nichts zu sagen, der Mann macht nur seinen Job.
Es ist ein Spiel der Kräfte, es geht um Macht und strategische Kontrolle, um Geheimdienste und die Kontrolle der öffentlichen Meinung, um Bodenschätze, Rohstoffe, Pipelines und Märkte. Das klingt aber nicht sexy, «Demokratie und Menschenrechte» hört sich besser und einfacher an. Dabei wäre eine für alle Seiten förderliche Politik auch nicht so kompliziert; das Handwerkszeug dazu nennt sich Diplomatie. Noch einmal Gabriele Krone-Schmalz:
«Friedliche Politik ist nichts anderes als funktionierender Interessenausgleich. Da geht’s nicht um Moral.»
Die Situation in der Ukraine ist sicher komplex, vor allem wegen der inneren Zerrissenheit. Es dürfte nicht leicht sein, eine friedliche Lösung für das Zusammenleben zu finden, aber die Beteiligten müssen es vor allem wollen. Unter den gegebenen Umständen könnte eine sinnvolle Perspektive mit Neutralität und föderalen Strukturen zu tun haben.
Allen, die sich bis hierher durch die Lektüre gearbeitet (oder auch einfach nur runtergescrollt) haben, wünsche ich frohe Oster-Friedenstage!
[Titelbild: Pixabay; Abb. 1 und 2: nach Ganser/SIPER; Abb. 3: SIPER]
--- Quellen: ---
[1] Albrecht Müller, «Glaube wenig. Hinterfrage alles. Denke selbst.», Westend 2019
[2] Zwei nette Beispiele:
- ARD-faktenfinder (sic), «Viel Aufmerksamkeit für fragwürdige Experten», 03/2023
- Neue Zürcher Zeitung, «Aufstieg und Fall einer Russlandversteherin – die ehemalige ARD-Korrespondentin Gabriele Krone-Schmalz rechtfertigt seit Jahren Putins Politik», 12/2022
[3] George Washington University, «NATO Expansion: What Gorbachev Heard – Declassified documents show security assurances against NATO expansion to Soviet leaders from Baker, Bush, Genscher, Kohl, Gates, Mitterrand, Thatcher, Hurd, Major, and Woerner», 12/2017
[4] Beispielsweise Wladimir Putin bei seiner Rede im Deutschen Bundestag, 25/09/2001
[5] William Engdahl, «Full Spectrum Dominance, Totalitarian Democracy In The New World Order», edition.engdahl 2009
[6] Daniele Ganser, «Illegale Kriege – Wie die NATO-Länder die UNO sabotieren. Eine Chronik von Kuba bis Syrien», Orell Füssli 2016
[7] Gabriele Krone-Schmalz, «Mit Friedensjournalismus gegen ‘Kriegstüchtigkeit’», Vortrag und Diskussion an der Universität Hamburg, veranstaltet von engagierten Studenten, 16/01/2025\ → Hier ist ein ähnlicher Vortrag von ihr (Video), den ich mit spanischer Übersetzung gefunden habe.
[8] Für mehr Hintergrund und Details empfehlen sich z.B. folgende Bücher:
- Mathias Bröckers, Paul Schreyer, «Wir sind immer die Guten», Westend 2019
- Gabriele Krone-Schmalz, «Russland verstehen? Der Kampf um die Ukraine und die Arroganz des Westens», Westend 2023
- Patrik Baab, «Auf beiden Seiten der Front – Meine Reisen in die Ukraine», Fiftyfifty 2023
[9] vgl. Jonathan Mowat, «Washington's New World Order "Democratization" Template», 02/2005 und RAND Corporation, «Swarming and the Future of Conflict», 2000
[10] Bemerkenswert einige Beiträge, von denen man später nichts mehr wissen wollte:
- ARD Monitor, «Todesschüsse in Kiew: Wer ist für das Blutbad vom Maidan verantwortlich», 10/04/2014, Transkript hier
- Telepolis, «Blutbad am Maidan: Wer waren die Todesschützen?», 12/04/2014
- Telepolis, «Scharfschützenmorde in Kiew», 14/12/2014
- Deutschlandfunk, «Gefahr einer Spirale nach unten», Interview mit Günter Verheugen, 18/03/2014
- NDR Panorama, «Putsch in Kiew: Welche Rolle spielen die Faschisten?», 06/03/2014
[11] Hauke Ritz, «Vom Niedergang des Westens zur Neuerfindung Europas», 2024
Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
-
 @ ba36d0f7:cd802cba
2025-04-20 17:58:52
@ ba36d0f7:cd802cba
2025-04-20 17:58:52FABRIC AS TEXTBOOK
Learning to embroider - or to mend - is like studying an ancestral language. Manuals explain the backstitch or sashiko, but fabric never lies: it tears if the tension is weak, and wrinkles if the needle is clumsy.
Theory gives you the alphabet; but practice gives you the syntax of the invisible. How many broken stitches hide behind perfect embroidery? How many mistakes teach us the language of threads?
I. TO MEND IS TO RESIST: THE POLITICAL ACT OF THE NEEDLE
There’s a certain sacred stubbornness in sitting down to mend; like our grandmothers darning our socks until the heel was more patch than original fabric.
And today, in the age of fast fashion, mending is rebellion: a silent "no" to disposability, a resounding "yes" to permanence.
Techniques as Philosophies
-
Japanese sashiko: Visible stitches like proud scars. "What’s broken isn’t hidden—it’s celebrated."

-
Darning: For when pain must be concealed, not erased.

-
Free embroidery: Where repair becomes art and mending, a language.

 Every stitch is a pact: "I care for you because you exist."
Every stitch is a pact: "I care for you because you exist."And isn’t this, too, what mestizaje means? To take the fragmented - fabrics, histories, identities - and reweave them without erasing their origin.
II. EMBROIDERY AS A SELF-TAUGHT MASTER
Learning to embroider is like learning to live: there are no shortcuts. You can read a thousand tutorials, but until you feel the thread resist the needle’s eye or the fabric tense beneath your fingers, knowledge remains abstract.
The Textile Learning Triad
-
Theory that fades (books explain the backstitch, but not how to avoid knots).
-
Practice that stings (fingers get pricked, stitches go crooked).
-
Intuition that blooms (when hands remember the motion on their own).
III. THREADS AND TECHNOLOGY
Malinche, Mesoamerica’s first translator, understood this: some knowledge only transmits through action. We, as 21st-century beings, have a privilege: to blend ancestral tools (needles, threads) with modern ones (YouTube tutorials, digital patterns).
At soma, we explore education beyond canons, and embroidery is the perfect example.
Embroidery teaches us:
-
Discipline (because one loose stitch ruins the design).
-
Creativity (because sometimes you must invent solutions).
-
Legacy (because every thread carries memory).
What are you mending today? A skirt, a habit, a way of learning?
This is the future of education: to dig into the old and hack the new.
IV. INVITATION: STITCHES AND PATIENCE WORKSHOP
This Saturday 26th, at Estudio Malinche, Apaneca - we won’t just teach techniques. We’ll create a collective learning ritual:
-
Bring a torn garment and an empty notebook.
-
Learn sashiko mending (to honor scars) and bookbinding with recycled paper (to chart your path).
-
You’ll leave with ink-stained hands and a heart full of threads.
"Perfection isn’t the goal - persistence is."
Follow us on IG to check out stories & upcoming events: @larutasoma @estudiomalinche
soma #article #mending #workshop #visiblemending #philosophy #resistance #btc #nostr #elsalvador #sashiko #rutadelasflores #apaneca #education #slowfashion #fashion #fastfashion #embroidery #stitching #handmade #diy
-
-
 @ 1d7ff02a:d042b5be
2025-04-23 02:28:08
@ 1d7ff02a:d042b5be
2025-04-23 02:28:08ທຳຄວາມເຂົ້າໃຈກັບຂໍ້ບົກພ່ອງໃນລະບົບເງິນຂອງພວກເຮົາ
ຫຼາຍຄົນພົບຄວາມຫຍຸ້ງຍາກໃນການເຂົ້າໃຈ Bitcoin ເພາະວ່າພວກເຂົາຍັງບໍ່ເຂົ້າໃຈບັນຫາພື້ນຖານຂອງລະບົບເງິນທີ່ມີຢູ່ຂອງພວກເຮົາ. ລະບົບນີ້, ທີ່ມັກຖືກຮັບຮູ້ວ່າມີຄວາມໝັ້ນຄົງ, ມີຂໍ້ບົກພ່ອງໃນການອອກແບບທີ່ມີມາແຕ່ດັ້ງເດີມ ເຊິ່ງສົ່ງຜົນຕໍ່ຄວາມບໍ່ສະເໝີພາບທາງເສດຖະກິດ ແລະ ການເຊື່ອມເສຍຂອງຄວາມຮັ່ງມີສຳລັບພົນລະເມືອງທົ່ວໄປ. ການເຂົ້າໃຈບັນຫາເຫຼົ່ານີ້ແມ່ນກຸນແຈສຳຄັນເພື່ອເຂົ້າໃຈທ່າແຮງຂອງວິທີແກ້ໄຂທີ່ Bitcoin ສະເໜີ.
ບົດບາດຂອງກະຊວງການຄັງສະຫະລັດ ແລະ ທະນາຄານກາງ
ລະບົບເງິນຕາປັດຈຸບັນໃນສະຫະລັດອາເມລິກາປະກອບມີການເຊື່ອມໂຍງທີ່ຊັບຊ້ອນລະຫວ່າງກະຊວງການຄັງສະຫະລັດ ແລະ ທະນາຄານກາງ. ກະຊວງການຄັງສະຫະລັດເຮັດໜ້າທີ່ເປັນບັນຊີທະນາຄານຂອງປະເທດ, ເກັບອາກອນ ແລະ ສະໜັບສະໜູນລາຍຈ່າຍຂອງລັດຖະບານເຊັ່ນ: ທະຫານ, ໂຄງລ່າງພື້ນຖານ ແລະ ໂຄງການສັງຄົມ. ເຖິງຢ່າງໃດກໍຕາມ, ລັດຖະບານມັກໃຊ້ຈ່າຍຫຼາຍກວ່າທີ່ເກັບໄດ້, ເຊິ່ງເຮັດໃຫ້ຕ້ອງໄດ້ຢືມເງິນ. ການຢືມນີ້ແມ່ນເຮັດໂດຍການຂາຍພັນທະບັດລັດຖະບານ, ຊຶ່ງມັນຄືໃບ IOU ທີ່ສັນຍາວ່າຈະຈ່າຍຄືນຈຳນວນທີ່ຢືມພ້ອມດອກເບ້ຍ. ພັນທະບັດເຫຼົ່ານີ້ມັກຖືກຊື້ໂດຍທະນາຄານໃຫຍ່, ລັດຖະບານຕ່າງປະເທດ, ແລະ ທີ່ສຳຄັນ, ທະນາຄານກາງ.
ວິທີການສ້າງເງິນ (ຈາກອາກາດ)
ນີ້ແມ່ນບ່ອນທີ່ເກີດການສ້າງເງິນ "ຈາກອາກາດ". ເມື່ອທະນາຄານກາງຊື້ພັນທະບັດເຫຼົ່ານີ້, ມັນບໍ່ໄດ້ໃຊ້ເງິນທີ່ມີຢູ່ແລ້ວ; ມັນສ້າງເງິນໃໝ່ດ້ວຍວິທີການດິຈິຕອນໂດຍພຽງແຕ່ປ້ອນຕົວເລກເຂົ້າໃນຄອມພິວເຕີ. ເງິນໃໝ່ນີ້ຖືກເພີ່ມເຂົ້າໃນປະລິມານເງິນລວມ. ຍິ່ງສ້າງເງິນຫຼາຍຂຶ້ນ ແລະ ເພີ່ມເຂົ້າໄປ, ມູນຄ່າຂອງເງິນທີ່ມີຢູ່ແລ້ວກໍຍິ່ງຫຼຸດລົງ. ຂະບວນການນີ້ຄືສິ່ງທີ່ພວກເຮົາເອີ້ນວ່າເງິນເຟີ້. ເນື່ອງຈາກກະຊວງການຄັງຢືມຢ່າງຕໍ່ເນື່ອງ ແລະ ທະນາຄານກາງສາມາດພິມໄດ້ຢ່າງຕໍ່ເນື່ອງ, ສິ່ງນີ້ຖືກສະເໜີວ່າເປັນວົງຈອນທີ່ບໍ່ມີທີ່ສິ້ນສຸດ.
ການໃຫ້ກູ້ຢືມສະຫງວນບາງສ່ວນໂດຍທະນາຄານ
ເພີ່ມເຂົ້າໃນບັນຫານີ້ຄືການປະຕິບັດຂອງການໃຫ້ກູ້ຢືມສະຫງວນບາງສ່ວນໂດຍທະນາຄານ. ເມື່ອທ່ານຝາກເງິນເຂົ້າທະນາຄານ, ທະນາຄານຖືກຮຽກຮ້ອງໃຫ້ເກັບຮັກສາພຽງແຕ່ສ່ວນໜຶ່ງຂອງເງິນຝາກນັ້ນໄວ້ເປັນເງິນສະຫງວນ (ຕົວຢ່າງ, 10%). ສ່ວນທີ່ເຫຼືອ (90%) ສາມາດຖືກປ່ອຍກູ້. ເມື່ອຜູ້ກູ້ຢືມໃຊ້ຈ່າຍເງິນນັ້ນ, ມັນມັກຖືກຝາກເຂົ້າອີກທະນາຄານ, ເຊິ່ງຈາກນັ້ນກໍຈະເຮັດຊ້ຳຂະບວນການໃຫ້ກູ້ຢືມສ່ວນໜຶ່ງຂອງເງິນຝາກ. ວົງຈອນນີ້ເຮັດໃຫ້ເພີ່ມຈຳນວນເງິນທີ່ໝູນວຽນຢູ່ໃນລະບົບໂດຍອີງໃສ່ເງິນຝາກເບື້ອງຕົ້ນ, ເຊິ່ງສ້າງເງິນຜ່ານໜີ້ສິນ. ລະບົບນີ້ໂດຍທຳມະຊາດແລ້ວບອບບາງ; ຖ້າມີຫຼາຍຄົນພະຍາຍາມຖອນເງິນຝາກຂອງເຂົາເຈົ້າພ້ອມກັນ (ການແລ່ນທະນາຄານ), ທະນາຄານກໍຈະລົ້ມເພາະວ່າມັນບໍ່ໄດ້ເກັບຮັກສາເງິນທັງໝົດໄວ້. ເງິນໃນທະນາຄານບໍ່ປອດໄພຄືກັບທີ່ເຊື່ອກັນທົ່ວໄປ ແລະ ສາມາດຖືກແຊ່ແຂງໃນຊ່ວງວິກິດການ ຫຼື ສູນເສຍຖ້າທະນາຄານລົ້ມລະລາຍ (ຍົກເວັ້ນໄດ້ຮັບການຊ່ວຍເຫຼືອ).
ຜົນກະທົບ Cantillon: ໃຜໄດ້ຮັບຜົນປະໂຫຍດກ່ອນ
ເງິນທີ່ຖືກສ້າງຂຶ້ນໃໝ່ບໍ່ໄດ້ກະຈາຍຢ່າງເທົ່າທຽມກັນ. "ຜົນກະທົບ Cantillon", ບ່ອນທີ່ຜູ້ທີ່ຢູ່ໃກ້ກັບແຫຼ່ງສ້າງເງິນໄດ້ຮັບຜົນປະໂຫຍດກ່ອນ. ນີ້ລວມເຖິງລັດຖະບານເອງ (ສະໜັບສະໜູນລາຍຈ່າຍ), ທະນາຄານໃຫຍ່ ແລະ Wall Street (ໄດ້ຮັບທຶນໃນອັດຕາດອກເບ້ຍຕ່ຳສຳລັບການກູ້ຢືມ ແລະ ການລົງທຶນ), ແລະ ບໍລິສັດໃຫຍ່ (ເຂົ້າເຖິງເງິນກູ້ທີ່ຖືກກວ່າສຳລັບການລົງທຶນ). ບຸກຄົນເຫຼົ່ານີ້ໄດ້ຊື້ຊັບສິນ ຫຼື ລົງທຶນກ່ອນທີ່ຜົນກະທົບຂອງເງິນເຟີ້ຈະເຮັດໃຫ້ລາຄາສູງຂຶ້ນ, ເຊິ່ງເຮັດໃຫ້ພວກເຂົາມີຂໍ້ໄດ້ປຽບ.
ຜົນກະທົບຕໍ່ຄົນທົ່ວໄປ
ສຳລັບຄົນທົ່ວໄປ, ຜົນກະທົບຂອງປະລິມານເງິນທີ່ເພີ່ມຂຶ້ນນີ້ແມ່ນການເພີ່ມຂຶ້ນຂອງລາຄາສິນຄ້າ ແລະ ການບໍລິການ - ນ້ຳມັນ, ຄ່າເຊົ່າ, ການດູແລສຸຂະພາບ, ອາຫານ, ແລະ ອື່ນໆ. ເນື່ອງຈາກຄ່າແຮງງານໂດຍທົ່ວໄປບໍ່ທັນກັບອັດຕາເງິນເຟີ້ນີ້, ອຳນາດການຊື້ຂອງປະຊາຊົນຈະຫຼຸດລົງເມື່ອເວລາຜ່ານໄປ. ມັນຄືກັບການແລ່ນໄວຂຶ້ນພຽງເພື່ອຢູ່ໃນບ່ອນເກົ່າ.
Bitcoin: ທາງເລືອກເງິນທີ່ໝັ້ນຄົງ
ຄວາມຂາດແຄນ: ບໍ່ຄືກັບເງິນຕາ fiat, Bitcoin ມີຂີດຈຳກັດສູງສຸດໃນປະລິມານຂອງມັນ. ຈະມີພຽງ 21 ລ້ານ Bitcoin ເທົ່ານັ້ນຖືກສ້າງຂຶ້ນ, ຂີດຈຳກັດນີ້ຝັງຢູ່ໃນໂຄດຂອງມັນ ແລະ ບໍ່ສາມາດປ່ຽນແປງໄດ້. ການສະໜອງທີ່ຈຳກັດນີ້ເຮັດໃຫ້ Bitcoin ເປັນເງິນຫຼຸດລາຄາ; ເມື່ອຄວາມຕ້ອງການເພີ່ມຂຶ້ນ, ມູນຄ່າຂອງມັນມີແນວໂນ້ມທີ່ຈະເພີ່ມຂຶ້ນເພາະວ່າປະລິມານການສະໜອງບໍ່ສາມາດຂະຫຍາຍຕົວ.
ຄວາມທົນທານ: Bitcoin ຢູ່ໃນ blockchain, ເຊິ່ງເປັນປຶ້ມບັນຊີສາທາລະນະທີ່ແບ່ງປັນກັນຂອງທຸກການເຮັດທຸລະກຳທີ່ແທບຈະເປັນໄປບໍ່ໄດ້ທີ່ຈະລຶບ ຫຼື ປ່ຽນແປງ. ປຶ້ມບັນຊີນີ້ຖືກກະຈາຍໄປທົ່ວພັນຄອມພິວເຕີ (nodes) ທົ່ວໂລກ. ແມ້ແຕ່ຖ້າອິນເຕີເນັດລົ້ມ, ເຄືອຂ່າຍສາມາດຢູ່ຕໍ່ໄປໄດ້ຜ່ານວິທີການອື່ນເຊັ່ນ: ດາວທຽມ ຫຼື ຄື້ນວິທະຍຸ. ມັນບໍ່ໄດ້ຮັບຜົນກະທົບຈາກການທຳລາຍທາງກາຍະພາບຂອງເງິນສົດ ຫຼື ການແຮັກຖານຂໍ້ມູນແບບລວມສູນ.
ການພົກພາ: Bitcoin ສາມາດຖືກສົ່ງໄປໃນທຸກບ່ອນໃນໂລກໄດ້ທັນທີ, 24/7, ດ້ວຍການເຊື່ອມຕໍ່ອິນເຕີເນັດ, ໂດຍບໍ່ຈຳເປັນຕ້ອງມີທະນາຄານ ຫຼື ການອະນຸຍາດຈາກພາກສ່ວນທີສາມ. ທ່ານສາມາດເກັບຮັກສາ Bitcoin ຂອງທ່ານໄດ້ດ້ວຍຕົນເອງໃນອຸປະກອນທີ່ເອີ້ນວ່າກະເປົາເຢັນ, ແລະ ຕາບໃດທີ່ທ່ານຮູ້ວະລີກະແຈລັບຂອງທ່ານ, ທ່ານສາມາດເຂົ້າເຖິງເງິນຂອງທ່ານຈາກກະເປົາທີ່ເຂົ້າກັນໄດ້, ເຖິງແມ່ນວ່າອຸປະກອນຈະສູນຫາຍ. ສິ່ງນີ້ສະດວກສະບາຍກວ່າ ແລະ ມີຄວາມສ່ຽງໜ້ອຍກວ່າການພົກພາເງິນສົດຈຳນວນຫຼາຍ ຫຼື ການນຳທາງການໂອນເງິນສາກົນທີ່ຊັບຊ້ອນ.
ການແບ່ງຍ່ອຍ: Bitcoin ສາມາດແບ່ງຍ່ອຍໄດ້ສູງ. ໜຶ່ງ Bitcoin ສາມາດແບ່ງເປັນ 100 ລ້ານໜ່ວຍຍ່ອຍທີ່ເອີ້ນວ່າ Satoshis, ເຊິ່ງອະນຸຍາດໃຫ້ສົ່ງ ຫຼື ຮັບຈຳນວນນ້ອຍໄດ້.
ຄວາມສາມາດໃນການທົດແທນກັນ: ໜຶ່ງ Bitcoin ທຽບເທົ່າກັບໜຶ່ງ Bitcoin ໃນມູນຄ່າ, ໂດຍທົ່ວໄປ. ໃນຂະນະທີ່ເງິນໂດລາແບບດັ້ງເດີມອາດສາມາດຖືກຕິດຕາມ, ແຊ່ແຂງ, ຫຼື ຍຶດໄດ້, ໂດຍສະເພາະໃນຮູບແບບດິຈິຕອນ ຫຼື ຖ້າຖືກພິຈາລະນາວ່າໜ້າສົງໄສ, ແຕ່ລະໜ່ວຍຂອງ Bitcoin ໂດຍທົ່ວໄປຖືກປະຕິບັດຢ່າງເທົ່າທຽມກັນ.
ການພິສູດຢັ້ງຢືນ: ທຸກການເຮັດທຸລະກຳ Bitcoin ຖືກບັນທຶກໄວ້ໃນ blockchain, ເຊິ່ງທຸກຄົນສາມາດເບິ່ງ ແລະ ພິສູດຢັ້ງຢືນ. ຂະບວນການພິສູດຢັ້ງຢືນທີ່ກະຈາຍນີ້, ດຳເນີນໂດຍເຄືອຂ່າຍ, ໝາຍຄວາມວ່າທ່ານບໍ່ຈຳເປັນຕ້ອງເຊື່ອຖືທະນາຄານ ຫຼື ສະຖາບັນໃດໜຶ່ງແບບມືດບອດເພື່ອຢືນຢັນຄວາມຖືກຕ້ອງຂອງເງິນຂອງທ່ານ.
ການຕ້ານການກວດກາ: ເນື່ອງຈາກບໍ່ມີລັດຖະບານ, ບໍລິສັດ, ຫຼື ບຸກຄົນໃດຄວບຄຸມເຄືອຂ່າຍ Bitcoin, ບໍ່ມີໃຜສາມາດຂັດຂວາງທ່ານຈາກການສົ່ງ ຫຼື ຮັບ Bitcoin, ແຊ່ແຂງເງິນຂອງທ່ານ, ຫຼື ຍຶດມັນ. ມັນເປັນລະບົບທີ່ບໍ່ຕ້ອງຂໍອະນຸຍາດ, ເຊິ່ງໃຫ້ຜູ້ໃຊ້ຄວບຄຸມເຕັມທີ່ຕໍ່ເງິນຂອງເຂົາເຈົ້າ.
ການກະຈາຍອຳນາດ: Bitcoin ຖືກຮັກສາໂດຍເຄືອຂ່າຍກະຈາຍຂອງບັນດາຜູ້ຂຸດທີ່ໃຊ້ພະລັງງານການຄິດໄລ່ເພື່ອຢັ້ງຢືນການເຮັດທຸລະກຳຜ່ານ "proof of work". ລະບົບທີ່ກະຈາຍນີ້ຮັບປະກັນວ່າບໍ່ມີຈຸດໃດຈຸດໜຶ່ງທີ່ຈະລົ້ມເຫຼວ ຫຼື ຄວບຄຸມ. ທ່ານບໍ່ໄດ້ເພິ່ງພາຂະບວນການທີ່ບໍ່ໂປ່ງໃສຂອງທະນາຄານກາງ; ລະບົບທັງໝົດໂປ່ງໃສຢູ່ໃນ blockchain. ສິ່ງນີ້ເຮັດໃຫ້ບຸກຄົນມີອຳນາດທີ່ຈະເປັນທະນາຄານຂອງຕົນເອງແທ້ ແລະ ຮັບຜິດຊອບຕໍ່ການເງິນຂອງເຂົາເຈົ້າ.
-
 @ 3ffac3a6:2d656657
2025-04-23 01:57:57
@ 3ffac3a6:2d656657
2025-04-23 01:57:57🔧 Infrastructure Overview
- Hardware: Raspberry Pi 5 with PCIe NVMe HAT and 2TB NVMe SSD
- Filesystem: ZFS with separate datasets for each service
- Networking: Docker bridge networks for service segmentation
- Privacy: Tor and I2P routing for anonymous communication
- Public Access: Cloudflare Tunnel to securely expose LNbits
📊 Architecture Diagram
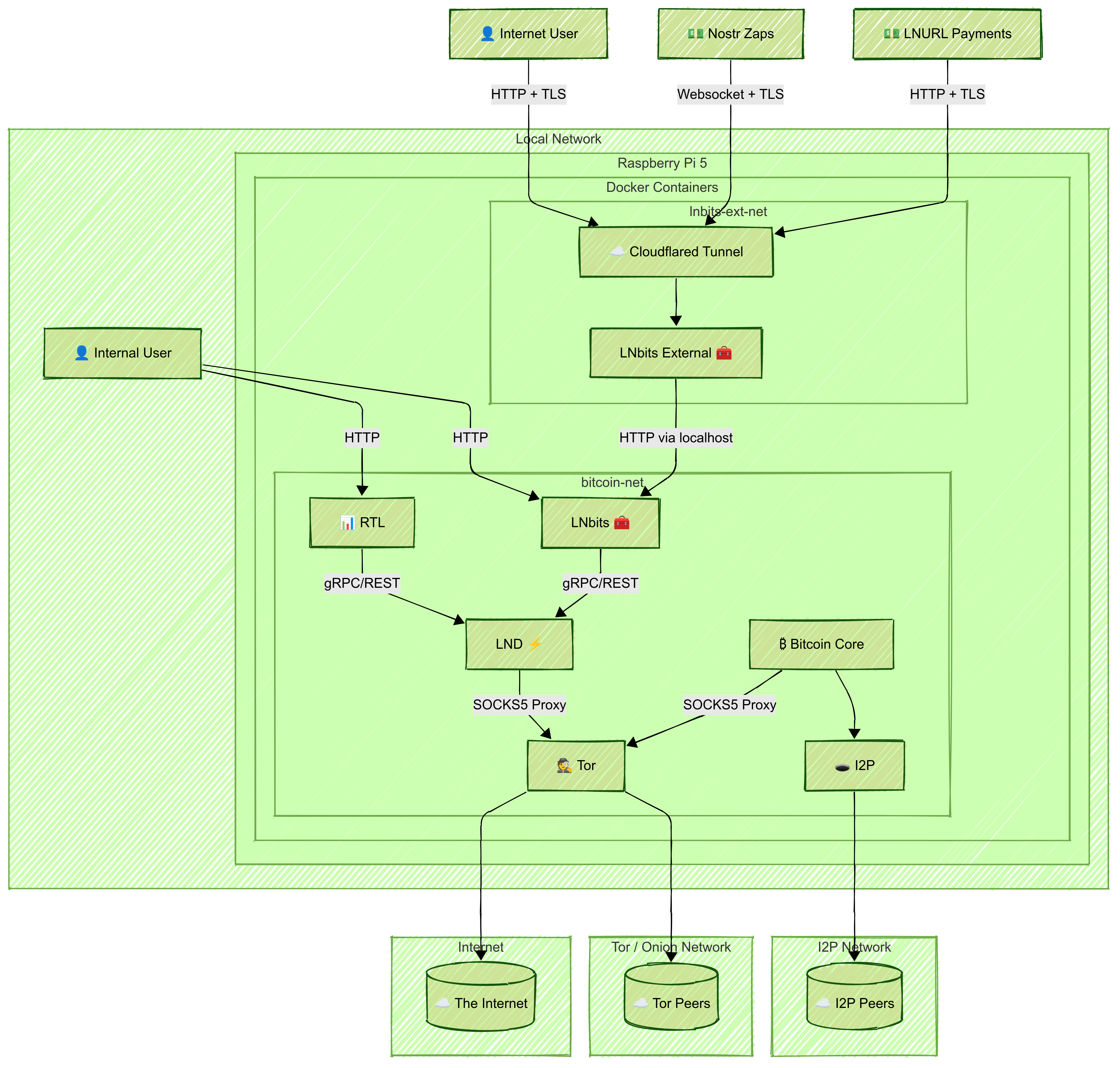
🛠️ Setup Steps
1. Prepare the System
- Install Raspberry Pi OS (64-bit)
- Set up ZFS on the NVMe disk
- Create a ZFS dataset for each service (e.g.,
bitcoin,lnd,rtl,lnbits,tor-data) - Install Docker and Docker Compose
2. Create Shared Docker Network and Privacy Layers
Create a shared Docker bridge network:
bash docker network create \ --driver=bridge \ --subnet=192.168.100.0/24 \ bitcoin-netNote: Connect
bitcoind,lnd,rtl, internallnbits,tor, andi2pto thisbitcoin-netnetwork.Tor
- Run Tor in a container
- Configure it to expose LND's gRPC and REST ports via hidden services:
HiddenServicePort 10009 192.168.100.31:10009 HiddenServicePort 8080 192.168.100.31:8080 - Set correct permissions:
bash sudo chown -R 102:102 /zfs/datasets/tor-data
I2P
- Run I2P in a container with SAM and SOCKS proxies
- Update
bitcoin.conf:i2psam=192.168.100.20:7656 i2pacceptincoming=1
3. Set Up Bitcoin Core
- Create a
bitcoin.confwith Tor/I2P/proxy settings and ZMQ enabled - Sync the blockchain in a container using its ZFS dataset
4. Set Up LND
- Configure
lnd.confto connect tobitcoindand use Tor: ```ini [Bitcoind] bitcoind.rpchost=bitcoin:8332 bitcoind.rpcuser=bitcoin bitcoind.rpcpass=very-hard-password bitcoind.zmqpubrawblock=tcp://bitcoin:28332 bitcoind.zmqpubrawtx=tcp://bitcoin:28333
[Application Options] externalip=xxxxxxxx.onion
`` - Don’t expose gRPC or REST ports publicly - Mount the ZFS dataset at/root/.lnd` - Optionally enable Watchtower5. Set Up RTL
- Mount
RTL-Config.jsonand data volumes - Expose RTL's web interface locally:
```yaml
ports:
- "3000:3000" ```
6. Set Up Internal LNbits
- Connect the LNbits container to
bitcoin-net - Mount the data directory and LND cert/macaroons (read-only)
- Expose the LNbits UI on the local network:
```yaml
ports:
- "5000:5000" ```
- In the web UI, configure the funding source to point to the LND REST
.onionaddress and paste the hex macaroon - Create and fund a wallet, and copy its Admin Key for external use
7. Set Up External LNbits + Cloudflare Tunnel
- Run another LNbits container on a separate Docker network
- Access the internal LNbits via the host IP and port 5000
- Use the Admin Key from the internal wallet to configure funding
- In the Cloudflare Zero Trust dashboard:
- Create a tunnel
- Select Docker, copy the
--tokencommand - Add to Docker Compose:
yaml command: tunnel --no-autoupdate run --token eyJ...your_token...
💾 Backup Strategy
- Bitcoin Core: hourly ZFS snapshots, retained for 6 hours
- Other Services: hourly snapshots with remote
.tar.gzbackups - Retention: 7d hourly, 30d daily, 12mo weekly, monthly forever
- Back up ZFS snapshots to avoid inconsistencies
🔐 Security Isolation Benefits
This architecture isolates services by scope and function:
- Internal traffic stays on
bitcoin-net - Sensitive APIs (gRPC, REST) are reachable only via Tor
- Public access is controlled by Cloudflare Tunnel
Extra Security: Host the public LNbits on a separate machine (e.g., hardened VPS) with strict firewall rules:
- Allow only Cloudflare egress
- Allow ingress from your local IP
- Allow outbound access to internal LNbits (port 5000)
Use WireGuard VPN to secure the connection between external and internal LNbits:
- Ensures encrypted communication
- Restricts access to authenticated VPN peers
- Keeps the internal interface isolated from the public internet
✅ Final Notes
- Internal services communicate over
bitcoin-net - LND interfaces are accessed via Tor only
- LNbits and RTL UIs are locally accessible
- Cloudflare Tunnel secures external access to LNbits
Monitor system health using
monit,watchtower, or Prometheus.Create all configuration files manually (
bitcoin.conf,lnd.conf,RTL-Config.json), and keep credentials secure. Test every component locally before exposing it externally.⚡
-
 @ 502ab02a:a2860397
2025-04-23 01:04:54
@ 502ab02a:a2860397
2025-04-23 01:04:54ช่วงหลัง ๆ มานี้ ถ้าใครเดินผ่านชั้นนมในซูเปอร์ฯ แล้วสะดุดตากับกล่องสีเรียบ ๆ สไตล์สแกนดิเนเวียนที่เขียนคำว่า "OATLY!" ตัวใหญ่ ๆ ไม่ต้องแปลกใจ เพราะนี่คือเครื่องดื่มที่กำลังพยายามจะทำให้ทุกบ้านเชื่อว่า "ดื่มข้าวโอ๊ตแทนนมวัวคือสิ่งที่ดีต่อสุขภาพ ต่อโลก และต่อเด็ก ๆ"
Oatly ไม่ได้มาเล่น ๆ เป็นดาวรุ่งของวงการ plant-based dairy ทางเลือก ด้วยการตลาดที่เฉียบคมและอารมณ์ขันแบบขบถ เพราะบริษัทนี้เขาวางโพสิชั่นของตัวเองว่าเป็นนักสู้เพื่อสิ่งแวดล้อม ต่อต้านโลกร้อน และเป็นทางเลือกที่รักสัตว์รักโลกจนพืชยังปรบมือให้ แต่เบื้องหลังที่ดูคลีน ๆ กลับซ่อนกลยุทธ์ทางการตลาดที่แสบสันไม่เบา โดยเฉพาะการรณรงค์ในโรงเรียน และเทคนิคในการ “ซ่อนความหวาน” ได้อย่างแนบเนียนจนน้ำตาลยังงง
หวานแบบซ่อนรูปสูตรลับที่ไม่อยู่ในช่อง Sugar โอ๊ตมิลค์ของ Oatly มีคาร์บต่ำจริงตามฉลาก แต่ที่หลายคนไม่รู้คือ Oatly ใช้ เอนไซม์ย่อยแป้งจากข้าวโอ๊ต ให้กลายเป็นน้ำตาลมอลโทส ซึ่งมีรสหวานพอ ๆ กับน้ำตาลทราย แต่ไม่ต้องแสดงในช่อง Total Sugar บนฉลากโภชนาการ เพราะมันเกิดขึ้น "ตามธรรมชาติจากกระบวนการ" ซึ่งตรงตามเกณฑ์ FDA เป๊ะ
ความเจ้าเล่ห์ของระบบนี้คือ มอลโตสที่เกิดจากการย่อยแป้งด้วยเอนไซม์ ไม่ต้องนับเป็น “น้ำตาล” ในช่อง Sugar ของฉลากโภชนาการ เพราะมันถือเป็น “naturally occurring sugar” หรือ “น้ำตาลที่เกิดขึ้นเองตามธรรมชาติ” พูดง่ายๆ คือ หวานเหมือนโค้ก แต่ไม่ต้องบอกว่าใส่น้ำตาลเลยแม้แต่นิดเดียว! ในขณะที่เด็กๆ ดื่มแล้วบอกว่า “อร่อยมาก!” ผู้ใหญ่ก็เห็นฉลากแล้วบอกว่า “น้ำตาลแค่นิดเดียวเอง ดีจัง”… ความเข้าใจผิดแบบสองชั้นนี้คือการตลาดที่ชาญฉลาดแต่แฝงความไม่โปร่งใส
และเมื่อคุณไปอ่านงานวิจัยจะเจอว่า น้ำตาลมอลโตสที่ได้จากโอ๊ตผ่านกระบวนการย่อยแบบนี้ มีค่าดัชนีน้ำตาลสูงถึง 105-110 ซึ่งสูงกว่าโค้กเสียอีก (Coke อยู่ประมาณ 63) ส่งผลให้ระดับน้ำตาลในเลือดพุ่งอย่างรวดเร็ว และถ้าใครมีภาวะดื้อต่ออินซูลินหรืออยู่ในขอบเขต prediabetes ก็ยิ่งน่ากังวลเข้าไปใหญ่ พูดง่าย ๆ คือ Oatly หวาน แต่ไม่ต้องบอกว่าใส่น้ำตาล คนทั่วไปเลยเข้าใจผิดว่า “อ้าว มันไม่หวานนี่นา”
บางโรงเรียนในอังกฤษและสวีเดนเริ่มตั้งคำถามว่า การเปลี่ยนนมวัวที่อุดมไปด้วยไขมันดี โปรตีนสมบูรณ์ และแคลเซียม เข้าสู่ร่างกายเด็กๆ ให้กลายเป็น “นมโอ๊ตหวานแบบซ่อนรูป” แบบนี้ มันคือความยั่งยืนจริงๆ หรือเป็นเพียงการใช้ภาพรักษ์โลกบังหน้า แล้วขายคาร์บอย่างแนบเนียน โดยเฉพาะ The Telegraph ได้เผยแพร่บทความชื่อ “The truth about the great oat milk 'con'” ซึ่งกล่าวถึงการที่หน่วยงานกำกับดูแลโฆษณาในสหราชอาณาจักร (Advertising Standards Authority - ASA) สั่งห้ามโฆษณาบางรายการของบริษัท Oatly เนื่องจากพบว่ามีการให้ข้อมูลที่ทำให้ผู้บริโภคเข้าใจผิดเกี่ยวกับประโยชน์ต่อสิ่งแวดล้อมของการเปลี่ยนจากนมวัวเป็นนมจากพืช รวมถึง ภาพลักษณ์ “plant-based ดีต่อโลก” ถูกใช้เป็น เครื่องมือโฆษณาเชิงอารมณ์ โดยลดคุณค่าของนมวัวแท้ ๆ และสิ่งที่น่าตลกร้ายก็คือ…บริษัท Oatly เคยออกมาโจมตีอุตสาหกรรมนมวัวว่า “ไม่โปร่งใส” ขณะเดียวกันพวกเขาเองกลับโดนฟ้องร้องเรื่องการใช้โฆษณาเกินจริง และพยายามซุกซ่อนกระบวนการผลิตที่ทำให้เกิดน้ำตาลแบบ “ซ่อนในตาราง” เสียเอง
ไม่แปลกที่หลายคนในแวดวงโภชนาการแซวว่า "Oatmilk is the new Coke" เพราะมันหวานแบบไม่รู้ตัว ดื่มเพลินเหมือนน้ำอัดลม แต่สื่อสารราวกับเป็นน้ำเต้าหู้สายโยคะ โอเคเรื่องพวกนี้เอาจริงๆเคยคุยกันแล้วในรายการ ลองไปดูย้อนได้ครับ
แต่นั่นยังไม่เท่ากับสิ่งนี้ครับ “Normalize It!”: รณรงค์เข้ารร.แบบซอฟต์พาวเวอร์ ถ้าคิดว่าแค่ขายในซูเปอร์คือจุดหมาย ขอบอกว่า Oatly เล่นเกมไกลกว่านั้น เพราะเขาเปิดแคมเปญชื่อ “Normalize it!” ในหลายประเทศในยุโรป เช่น เยอรมนี สวีเดน และเนเธอร์แลนด์ โดยรณรงค์ให้ เครื่องดื่มจากพืชถูกบรรจุเป็นส่วนหนึ่งของ "โครงการนมโรงเรียน" ที่มีอยู่เดิมในระบบรัฐ ซึ่งแต่เดิมให้เฉพาะนมวัวเท่านั้น
ในโฆษณาแคมเปญนี้ มีการเล่นภาพเด็ก ๆ ที่แอบเอาโอ๊ตมิลค์ใส่กล่องนมโรงเรียน พร้อมประโยคชวนสะอึกว่า “เด็กควรต้องทำเองเหรอ?” (เหมือนจะบอกว่ารัฐควรรับหน้าที่แทน) ดูความแสบได้ที่นี่ https://youtu.be/D3d_GfGVq_I?si=3pi6VKnlJC2SDleW
มันฟังดูดีใช่ไหม...แต่ประเด็นคือ ใครเป็นคนได้ประโยชน์? คำตอบคือ บริษัทที่ขายโอ๊ตมิลค์นั่นแหละ
เพราะหากสำเร็จ โรงเรียนจำนวนมากในยุโรปจะต้องซื้อผลิตภัณฑ์จากพืชแทนหรือควบคู่กับนมวัว ทำให้บริษัทที่ขายเครื่องดื่มพืชกลายเป็นผู้ได้สัมปทานทางอ้อมในชื่อ “ความยั่งยืน”
Lobby แบบ “รักษ์โลก” แต่ก็ไม่ลืมรักษาผลประโยชน์ แคมเปญนี้ไม่ได้แค่โฆษณาเล่น ๆ แต่ยังมีการล็อบบี้ทางนโยบายในระดับสหภาพยุโรป (EU) โดยผลักดันให้เครื่องดื่มจากพืชที่มีการเสริมแคลเซียมได้รับการยอมรับเท่าเทียมกับนมวัว Oatly จึงไม่ได้แค่เป็นแบรนด์ข้าวโอ๊ตอีกต่อไป แต่กลายเป็น "นักกิจกรรม" ที่มีเป้าหมายใหญ่คือการเข้าไปอยู่ในระบบอาหารภาครัฐ โดยเฉพาะสำหรับเด็ก ๆ
ปัญหาคือไม่ใช่แค่ “พืช” แต่คือ “วิธีการสื่อสาร” ไม่มีใครเถียงว่าเด็กควรมีทางเลือกในอาหาร แต่เมื่อ “ข้อมูล” ที่ใช้สร้างภาพลักษณ์ผลิตภัณฑ์ถูกเรียบเรียงให้ดูดีเกินจริง โดยเฉพาะเมื่อซ่อนความหวานไว้ในกลไกทางเคมี และรณรงค์ให้เข้าสู่ระบบโรงเรียน มันก็กลายเป็นประเด็นที่เราควรถามว่า “เรากำลังให้เด็กกินอะไร เพราะอะไร และใครได้ประโยชน์จากสิ่งนั้น?” เครื่องดื่มจากพืชไม่ใช่ปีศาจ และนมวัวก็ไม่ใช่เทวดา แต่สิ่งที่น่ากลัวคือกลยุทธ์ที่หลอกให้คนเชื่อว่าทางเลือกหนึ่ง “ดีกว่า” โดยไม่ให้ข้อมูลครบถ้วน หรือยิ่งแย่กว่านั้นถ้าเป็นการตัดริดรอนสิทธิ์ในการเลือก
วันหนึ่งถ้าเด็ก ๆ ทุกคนได้ดื่มโอ๊ตมิลค์ที่หวานแต่ไม่เรียกว่าน้ำตาล เพราะใครบางคนบอกว่า “ดีต่อสุขภาพ” เราควรถามว่า “สุขภาพของใคร?” และ “ใครนิยามว่าอะไรคือดี?” เพราะบางครั้ง โลกที่ดูยั่งยืน อาจมีรากฐานมาจากการตลาดที่ยืนนาน
เรื่องนี้ไม่ได้เกี่ยวกับการเกลียดพืช หรือรังเกียจข้าวโอ๊ต หรือนมโอ้ต แต่มันเกี่ยวกับ ความจริงที่ถูกแต่งหน้าให้ดูดีเกินจริง ในนามของสุขภาพและสิ่งแวดล้อม ซึ่งอาจกลายเป็นการเปลี่ยนเด็กๆ ให้คุ้นชินกับเครื่องดื่มหวานแบบไม่รู้ตัว ในขณะที่เราเคยพยายามลดโค้กจากโรงเรียนไปเมื่อสิบปีก่อน
อย่าลืมว่า ไม่ใช่แค่น้ำตาลที่ต้องดู แต่ต้องดูว่ามันมาจากไหน ถูกสร้างขึ้นอย่างไร และร่างกายตอบสนองอย่างไร
สำคัญที่สุดคือ เรามีสิทธิ์ในการเลือกไหม ในอนาคต
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 8d34bd24:414be32b
2025-04-20 14:18:37
@ 8d34bd24:414be32b
2025-04-20 14:18:37I started working on this post a couple weeks ago, and out of pure accident, it became my Resurrection Sunday (Easter) post. Maybe it was by God’s design. On Resurrection Sunday, Jesus was raised from the grave. Forty days later he rose to heaven before many witnesses. Someday in the future, the dead in Christ will be raised from the dead, and all believers will be snatched up to heaven. Maybe this is this right post for Resurrection Sunday.
For if we believe that Jesus died and rose again, even so God will bring with Him those who have fallen asleep in Jesus. … For the Lord Himself will descend from heaven with a shout, with the voice of the archangel and with the trumpet of God, and the dead in Christ will rise first. Then we who are alive and remain will be caught up together with them in the clouds to meet the Lord in the air, and so we shall always be with the Lord. (1 Thessalonians 4:14, 16-17) {emphasis mine}
It always amazes me that some Christians don’t believe in the rapture of the church. I understand how there can be a disagreement about exactly when the rapture is to occur, but I can’t comprehend how some Christians don’t believe the rapture is coming or that they believe that the rapture happened in the first century.
Let’s start with the three key verses on the subject and then we’ll get into more details.
Key Rapture Verses
I didn’t notice that this first passage referred to the rapture until it was pointed out to me. I was so focused on Jesus preparing a place, that I missed the key sentence.
“Do not let your heart be troubled; believe in God, believe also in Me. In My Father’s house are many dwelling places; if it were not so, I would have told you; for I go to prepare a place for you. If I go and prepare a place for you, I will come again and receive you to Myself, that where I am, there you may be also. (John 14:1-3) {emphasis mine}
Jesus, after His resurrection and as promised in these verses, rose up to heaven to go prepare a place for believers. He will then return to bring believers to Himself. This whole idea would have been particularly clear for the Jews when it was written. When a bride and groom were engaged (a legal contract where they were considered married), the groom would go and prepare a place for them to live. It could be an extra room in his parent’s home or it could be a whole new home. The bride didn’t know when the groom would return to take her to himself to become man and wife. In the same way, Jesus has gone away to prepare a place for us and will return at a time we do not know. Just as the Jewish bride had to be ready to leave with her groom when he suddenly arrived, we also must be ready for Jesus’s return when He will snatch us from earth and take us home with Him to heaven.
But we do not want you to be uninformed, brethren, about those who are asleep, so that you will not grieve as do the rest who have no hope. For if we believe that Jesus died and rose again, even so God will bring with Him those who have fallen asleep in Jesus. For this we say to you by the word of the Lord, that we who are alive and remain until the coming of the Lord, will not precede those who have fallen asleep. For the Lord Himself will descend from heaven with a shout, with the voice of the archangel and with the trumpet of God, and the dead in Christ will rise first. Then we who are alive and remain will be caught up together with them in the clouds to meet the Lord in the air, and so we shall always be with the Lord. Therefore comfort one another with these words. (1 Thessalonians 4:13-18) {emphasis mine}
The Bible has a wonderful euphemism for the death of believers. It speaks of them falling asleep because death is not the end for believers. It is just a pause, a separation of body and spirit, before we are raptured to Jesus, to meet Him in the sky, where we will receive a new resurrection body, just as Jesus received when He was raised from the dead 3 days after His crucifixion. Both the dead in Christ and the alive in Christ will “be caught up together with them in the clouds to meet the Lord in the air.” God gives us this promise in the Bible to comfort us. It gives us comfort that death is not the end and we will see our fellow believers again in heaven one day. It also gives us comfort that we will not have to experience God’s wrath. “For God has not destined us for wrath, but for obtaining salvation through our Lord Jesus Christ.” (1 Thessalonians 5:9)
What else can we learn about the rapture?
Now I say this, brethren, that flesh and blood cannot inherit the kingdom of God; nor does the perishable inherit the imperishable. Behold, I tell you a mystery; we will not all sleep, but we will all be changed, in a moment, in the twinkling of an eye, at the last trumpet; for the trumpet will sound, and the dead will be raised imperishable, and we will be changed. For this perishable must put on the imperishable, and this mortal must put on immortality. But when this perishable will have put on the imperishable, and this mortal will have put on immortality, then will come about the saying that is written, “Death is swallowed up in victory. O death, where is your victory? O death, where is your sting?” The sting of death is sin, and the power of sin is the law; but thanks be to God, who gives us the victory through our Lord Jesus Christ. (1 Corinthians 15:50-57) {emphasis mine}
The rapture will be an instantaneous change from our perishable bodies to imperishable, whether we are alive in Christ or dead in Christ. At the rapture we “will be raised imperishable.” I am very excited to be snatched up into the air, receive a new, eternal body, and meet Jesus face-to-face.
There is one more passage that I believe talks of the rapture that is a bit more subtle from Isaiah.
The righteous man perishes, and no man takes it to heart;\ And devout men are taken away, while no one understands.\ For the righteous man is taken away from evil,\ **He enters into peace;\ They rest in their beds,\ Each one who walked in his upright way. (Isaiah 57:1-2) {emphasis mine}
The seven year Tribulation is the wrath of God poured out on those who rejected Him and the merciful, last chance warning before eternal judgement. Those who have trusted in Jesus (the devout men, the righteous man) will be “taken away from evil” and will “enter into peace.” Instead of experiencing God’s wrath, they will experience His peace. Instead of experience horror, they will “rest in their beds.”
The Seven Raptures Before the Rapture of the Church
How can we know that we will be raptured to heaven to be with Jesus forever? One way is because people have been raptured before (in different ways)
I am borrowing the organization of this section from Chapter 9 of “The End: Everything You’ll Want to Know about the Apocalypse” by Mark Hitchcock, which I happen to be reading at the moment.
-
Rapture of Enoch\ ”So all the days of Enoch were three hundred and sixty-five years. Enoch walked with God; and he was not, for God took him.” (Genesis 5:23-24) \ Enoch was raptured to heaven to be with God. He did not die, but went straight to God.
-
Rapture of Elijah\ ”And it came about when the Lord was about to take up Elijah by a whirlwind to heaven, that Elijah went with Elisha from Gilgal. … As they were going along and talking, behold, there appeared a chariot of fire and horses of fire which separated the two of them. And Elijah went up by a whirlwind to heaven.” (2 Kings 2:1,11) \ Elijah also was raptured to heaven without having to die. This passage gives more details. He went up in a whirlwind to heaven.
-
Rapture of Isaiah\ ”In the year of King Uzziah’s death I saw the Lord sitting on a throne, lofty and exalted, with the train of His robe filling the temple. Seraphim stood above Him, each having six wings: with two he covered his face, and with two he covered his feet, and with two he flew. And one called out to another and said,
“Holy, Holy, Holy, is the Lord of hosts,
The whole earth is full of His glory.”” (Isaiah 6:1-3)\ Isaiah’s situation was different. He was raptured to heaven only temporarily to be given God’s word and His prophecy and to call Isaiah for His good plan.
-
Rapture of Jesus\ ”And she gave birth to a son, a male child, who is to rule all the nations with a rod of iron; and her child was caught up to God and to His throne.” (Revelation 12:5)\ and\ ”And after He had said these things, He was lifted up while they were looking on, and a cloud received Him out of their sight. And as they were gazing intently into the sky while He was going, behold, two men in white clothing stood beside them. They also said, “Men of Galilee, why do you stand looking into the sky? This Jesus, who has been taken up from you into heaven, will come in just the same way as you have watched Him go into heaven.” (Acts 1:9-11)\ I’ve listed two verses about Jesus’s rapture. The one from Revelation uses the Greek word harpazo, caught up - when translated to Latin, the word is rapturo, which is where we get our English word rapture. The verses in Acts give a more detailed description of His rapture to heaven, which is an example of our rapture. We are also promised His return.
-
Rapture of Philip\ ”And he ordered the chariot to stop; and they both went down into the water, Philip as well as the eunuch, and he baptized him. When they came up out of the water, the Spirit of the Lord snatched Philip away; and the eunuch no longer saw him, but went on his way rejoicing. But Philip found himself at Azotus, and as he passed through he kept preaching the gospel to all the cities until he came to Caesarea.” (Acts 8:38-40)
The rapture of Philip is different than the rest, because Philip was snatched away, not to heaven, but to Azotus. This is still an instance worth pointing out because it also uses the Greek word Harpazo.
- Rapture of Paul\ ”I know a man in Christ who fourteen years ago—whether in the body I do not know, or out of the body I do not know, God knows—such a man was caught up to the third heaven. And I know how such a man—whether in the body or apart from the body I do not know, God knows— was caught up into Paradise and heard inexpressible words, which a man is not permitted to speak.” (2 Corinthians 12:2-4)\ Like Isaiah, Paul was temporarily caught up (Harpazo) to heaven to receive revelation from God and then returned to his work and life on earth
These examples show God snatching people from one location to another, physically or spiritually for His good purpose. I expect it to happen again, shortly before the beginning of the seven year tribulation.
The 3 Views of the Rapture
There are three main views of the rapture: pre-trib, mid-trib, and post-trib. The basic beliefs are pretty much self explanatory by their name. Does the rapture occur before the tribulation, around the mid-point of the tribulation (which is right before the Great Tribulation or final 3.5 years), or after the tribulation? Which one fits what the Bible says better?
Although the Bible doesn’t directly say when the rapture happens, there are some very strong hints.
No wrath For saints
“For God has not destined us for wrath, but for obtaining salvation through our Lord Jesus Christ.” (1 Thessalonians 5:9)
God promises believers that we are not destined for wrath. The tribulation is also known as1 “The wrath” (1 Thessalonians 5:9 & Revelation 11:18), “The wrath to come” (1 Thessalonians 1:10), “The great day of their wrath” (Revelation 6:17), “The wrath of God” (Revelation15:1,7, 14:10,19, 16:1), “The wrath of the lamb” (Revelation 6:16). There are numerous other equally unpleasant names, but I am sticking with those that use the word wrath. God promised believers that we are not destined for wrath. God never breaks His promises.
Similarly Revelation 3 promises believers will be kept from the hour of testing.
Because you have kept the word of My perseverance, I also will keep you from the hour of testing, that hour which is about to come upon the whole world, to test those who dwell on the earth. I am coming quickly; hold fast what you have, so that no one will take your crown. (Revelation 3:10-11) {emphasis mine}
The word quickly can also be translated suddenly. Although Jesus has not returned quickly by our way of figuring time, He will come suddenly.
No one knows when
“But of that day and hour no one knows, not even the angels of heaven, nor the Son, but the Father alone.” (Matthew 24:36)
Scripture says the Tribulation starts when the Antichrist signs a peace treaty with Israel. If the rapture happens before the tribulation, then we won’t know when it will happen. If the rapture occurs at the mid-trib position, then it will happen 3.5 years after the peace treaty. If the rapture occurs post-trip, then it will happen 7 years after the peace treaty is signed and 3.5 years after the abomination of desolation, when the Antichrist declares himself god in the Jewish temple and requires the whole world to worship him. Only one makes sense if we can’t know when it happens.
Just as in the days of …
“For the coming of the Son of Man will be just like the days of Noah. For as in those days before the flood they were eating and drinking, marrying and giving in marriage, until the day that Noah entered the ark, and they did not understand until the flood came and took them all away; so will the coming of the Son of Man be. Then there will be two men in the field; one will be taken and one will be left. Two women will be grinding at the mill; one will be taken and one will be left.” (Matthew 24:37-41)
If we look at the words of Jesus, He compares the rapture to the days of Noah. Life happening as normal, then God put Noah and his family on the ark and personally shut the door (Genesis 7:16). Then the flood came, pouring God’s wrath out on those who had rejected Him. In the same way, God will take believers out of the world before pouring out His wrath on those who remain. He clearly states, “one will be taken and one will be left.”
A parallel passage in Luke, not only talks of God removing Noah before the flood, but also tells of God removing Lot before destroying Sodom & Gomorrah.
For just like the lightning, when it flashes out of one part of the sky, shines to the other part of the sky, so will the Son of Man be in His day. But first He must suffer many things and be rejected by this generation. And just as it happened in the days of Noah, so it will be also in the days of the Son of Man: they were eating, they were drinking, they were marrying, they were being given in marriage, until the day that Noah entered the ark, and the flood came and destroyed them all. It was the same as happened in the days of Lot: they were eating, they were drinking, they were buying, they were selling, they were planting, they were building; but on the day that Lot went out from Sodom it rained fire and brimstone from heaven and destroyed them all. It will be just the same on the day that the Son of Man is revealed. (Luke:17:24-30) {emphasis mine}
Just as Noah was removed before judgement, so also was Lot removed before judgement. In both cases the majority of people were going about business, living normal lives, not expecting anything to change.
In Genesis 19, the angels must remove Lot and his family before the city is destroyed.
Then the two men said to Lot, “Whom else have you here? A son-in-law, and your sons, and your daughters, and whomever you have in the city, bring them out of the place; for we are about to destroy this place, because their outcry has become so great before the Lord that the Lord has sent us to destroy it.” \ …\ When morning dawned, the angels urged Lot, saying, “Up, take your wife and your two daughters who are here, or you will be swept away in the punishment of the city.” But he hesitated. So the men seized his hand and the hand of his wife and the hands of his two daughters, for the compassion of the Lord was upon him; and they brought him out, and put him outside the city. (Genesis 19:12-13,15-16) {emphasis mine}
In the last days, God has promised to remove us before His judgment is poured out on those who willfully rejected Him. Jesus spoke these words to comfort us and so we would not fear the end.
Removal of the Restrainer
Now we request you, brethren, with regard to the coming of our Lord Jesus Christ and our gathering together to Him, that you not be quickly shaken from your composure or be disturbed either by a spirit or a message or a letter as if from us, to the effect that the day of the Lord has come. Let no one in any way deceive you, for it will not come unless the apostasy comes first, and the man of lawlessness is revealed, the son of destruction, who opposes and exalts himself above every so-called god or object of worship, so that he takes his seat in the temple of God, displaying himself as being God. Do you not remember that while I was still with you, I was telling you these things? And you know what restrains him now, so that in his time he will be revealed. For the mystery of lawlessness is already at work; only he who now restrains will do so until he is taken out of the way. Then that lawless one will be revealed whom the Lord will slay with the breath of His mouth and bring to an end by the appearance of His coming; (2 Thessalonians 2:1-8) {emphasis mine}
The restrainer is the Holy Spirit and the lawless one is the antichrist. This passage is saying that the antichrist will not be revealed until the restrainer is removed. The Holy Spirit indwells every believer. The believers also have to be removed before the antichrist is revealed, otherwise the Holy Spirit would have to leave the believers, leaving them alone during God’s wrath. That, of course, is contrary to God’s character, history, and promise.
Why is There No Mention of the Church During the Tribulation?
In the first three chapters of Revelation, the word church is used again and again. The church is not mentioned again until Revelation 19, regarding the Bride of Christ.
Let us rejoice and be glad and give the glory to Him, for the marriage of the Lamb has come and His bride has made herself ready.” It was given to her to clothe herself in fine linen, bright and clean; for the fine linen is the righteous acts of the saints. (Revelation 19:7-8) {emphasis mine}
All of this makes sense if the church was raptured before the tribulation. Therefore the bride (the church) has had seven years to make herself ready. They then get to descend with Jesus in the second coming of Jesus.
And I saw heaven opened, and behold, a white horse, and He who sat on it is called Faithful and True, and in righteousness He judges and wages war. His eyes are a flame of fire, and on His head are many diadems; and He has a name written on Him which no one knows except Himself. He is clothed with a robe dipped in blood, and His name is called The Word of God. And the armies which are in heaven, clothed in fine linen, white and clean, were following Him on white horses. From His mouth comes a sharp sword, so that with it He may strike down the nations, and He will rule them with a rod of iron; and He treads the wine press of the fierce wrath of God, the Almighty. And on His robe and on His thigh He has a name written, “KING OF KINGS, AND Lord OF LORDS.” (Revelation 19:11-16) {emphasis mine}
The Bride of Christ follows the King of Kings and Lord of Lords back to earth after being made “white and clean.”
Some may accuse pre-trib believers of being escapists. I’ll admit, I am happy to avoid the wrath of God, whether that be the tribulation or eternal damnation or just His daily disappointment in my failings. The fact that I am glad to “escape” the wrath, doesn’t make it untrue. I hope the passages and explanations I shared will give you comfort as the Day of the Lord and the Wrath of God approaches and as we see the world seemingly spiraling out of control. God is in control. Everything is happening according to His plan and for our good.
May the Lord of heaven comfort you with His promises and make you know His love. May you trust Him in good times and bad until the last days. May God give you a desire for His word and an understanding of His prophecies, so you will know the day is fast approaching.
Trust Jesus.
FYI, You can find most of my articles at end times. Some are directly relating to end times while others are loosely related. This post is a logical explanation of the rapture. You can also check out my older article on the rapture, “Up, Up, and Away.” The focus in my previous post was a little different including focusing on how the rapture will effect us, how we should respond to its immanency, and how it relates to the 2nd coming of Christ after the tribulation, so it is worth checking out as well.
-
-
 @ 83279ad2:bd49240d
2025-04-20 08:39:12
@ 83279ad2:bd49240d
2025-04-20 08:39:12Hello
-
 @ 65f03c16:f77e9d92
2025-04-20 08:33:37
@ 65f03c16:f77e9d92
2025-04-20 08:33:37is a game changer for traders. It blends chaos theory & market psychology to decode price action. Learn to spot order in market noise using fractals & momentum, teaches the Alligator indicator to ride trends & avoid chop. His 5-stage approach, from novice to expert, builds discipline & edge. Perfect for futures or stocks, It’s practical, not abstract. Williams’ 40+ yrs of trading shine through, with tools like Elliott Wave & nonlinear dynamics
recommended !






























