-
 @ c1e9ab3a:9cb56b43
2025-05-09 23:10:14
@ c1e9ab3a:9cb56b43
2025-05-09 23:10:14I. Historical Foundations of U.S. Monetary Architecture
The early monetary system of the United States was built atop inherited commodity money conventions from Europe’s maritime economies. Silver and gold coins—primarily Spanish pieces of eight, Dutch guilders, and other foreign specie—formed the basis of colonial commerce. These units were already integrated into international trade and piracy networks and functioned with natural compatibility across England, France, Spain, and Denmark. Lacking a centralized mint or formal currency, the U.S. adopted these forms de facto.
As security risks and the practical constraints of physical coinage mounted, banks emerged to warehouse specie and issue redeemable certificates. These certificates evolved into fiduciary media—claims on specie not actually in hand. Banks observed over time that substantial portions of reserves remained unclaimed for years. This enabled fractional reserve banking: issuing more claims than reserves held, so long as redemption demand stayed low. The practice was inherently unstable, prone to panics and bank runs, prompting eventual centralization through the formation of the Federal Reserve in 1913.
Following the Civil War and unstable reinstatements of gold convertibility, the U.S. sought global monetary stability. After World War II, the Bretton Woods system formalized the U.S. dollar as the global reserve currency. The dollar was nominally backed by gold, but most international dollars were held offshore and recycled into U.S. Treasuries. The Nixon Shock of 1971 eliminated the gold peg, converting the dollar into pure fiat. Yet offshore dollar demand remained, sustained by oil trade mandates and the unique role of Treasuries as global reserve assets.
II. The Structure of Fiduciary Media and Treasury Demand
Under this system, foreign trade surpluses with the U.S. generate excess dollars. These surplus dollars are parked in U.S. Treasuries, thereby recycling trade imbalances into U.S. fiscal liquidity. While technically loans to the U.S. government, these purchases act like interest-only transfers—governments receive yield, and the U.S. receives spendable liquidity without principal repayment due in the short term. Debt is perpetually rolled over, rarely extinguished.
This creates an illusion of global subsidy: U.S. deficits are financed via foreign capital inflows that, in practice, function more like financial tribute systems than conventional debt markets. The underlying asset—U.S. Treasury debt—functions as the base reserve asset of the dollar system, replacing gold in post-Bretton Woods monetary logic.
III. Emergence of Tether and the Parastatal Dollar
Tether (USDT), as a private issuer of dollar-denominated tokens, mimics key central bank behaviors while operating outside the regulatory perimeter. It mints tokens allegedly backed 1:1 by U.S. dollars or dollar-denominated securities (mostly Treasuries). These tokens circulate globally, often in jurisdictions with limited banking access, and increasingly serve as synthetic dollar substitutes.
If USDT gains dominance as the preferred medium of exchange—due to technological advantages, speed, programmability, or access—it displaces Federal Reserve Notes (FRNs) not through devaluation, but through functional obsolescence. Gresham’s Law inverts: good money (more liquid, programmable, globally transferable USDT) displaces bad (FRNs) even if both maintain a nominal 1:1 parity.
Over time, this preference translates to a systemic demand shift. Actors increasingly use Tether instead of FRNs, especially in global commerce, digital marketplaces, or decentralized finance. Tether tokens effectively become shadow base money.
IV. Interaction with Commercial Banking and Redemption Mechanics
Under traditional fractional reserve systems, commercial banks issue loans denominated in U.S. dollars, expanding the money supply. When borrowers repay loans, this destroys the created dollars and contracts monetary elasticity. If borrowers repay in USDT instead of FRNs:
- Banks receive a non-Fed liability (USDT).
- USDT is not recognized as reserve-eligible within the Federal Reserve System.
- Banks must either redeem USDT for FRNs, or demand par-value conversion from Tether to settle reserve requirements and balance their books.
This places redemption pressure on Tether and threatens its 1:1 peg under stress. If redemption latency, friction, or cost arises, USDT’s equivalence to FRNs is compromised. Conversely, if banks are permitted or compelled to hold USDT as reserve or regulatory capital, Tether becomes a de facto reserve issuer.
In this scenario, banks may begin demanding loans in USDT, mirroring borrower behavior. For this to occur sustainably, banks must secure Tether liquidity. This creates two options: - Purchase USDT from Tether or on the secondary market, collateralized by existing fiat. - Borrow USDT directly from Tether, using bank-issued debt as collateral.
The latter mirrors Federal Reserve discount window operations. Tether becomes a lender of first resort, providing monetary elasticity to the banking system by creating new tokens against promissory assets—exactly how central banks function.
V. Structural Consequences: Parallel Central Banking
If Tether begins lending to commercial banks, issuing tokens backed by bank notes or collateralized debt obligations: - Tether controls the expansion of broad money through credit issuance. - Its balance sheet mimics a central bank, with Treasuries and bank debt as assets and tokens as liabilities. - It intermediates between sovereign debt and global liquidity demand, replacing the Federal Reserve’s open market operations with its own issuance-redemption cycles.
Simultaneously, if Tether purchases U.S. Treasuries with FRNs received through token issuance, it: - Supplies the Treasury with new liquidity (via bond purchases). - Collects yield on government debt. - Issues a parallel form of U.S. dollars that never require redemption—an interest-only loan to the U.S. government from a non-sovereign entity.
In this context, Tether performs monetary functions of both a central bank and a sovereign wealth fund, without political accountability or regulatory transparency.
VI. Endgame: Institutional Inversion and Fed Redundancy
This paradigm represents an institutional inversion:
- The Federal Reserve becomes a legacy issuer.
- Tether becomes the operational base money provider in both retail and interbank contexts.
- Treasuries remain the foundational reserve asset, but access to them is mediated by a private intermediary.
- The dollar persists, but its issuer changes. The State becomes a fiscal agent of a decentralized financial ecosystem, not its monetary sovereign.
Unless the Federal Reserve reasserts control—either by absorbing Tether, outlawing its instruments, or integrating its tokens into the reserve framework—it risks becoming irrelevant in the daily function of money.
Tether, in this configuration, is no longer a derivative of the dollar—it is the dollar, just one level removed from sovereign control. The future of monetary sovereignty under such a regime is post-national and platform-mediated.
-
 @ a5ee4475:2ca75401
2025-05-09 17:10:35
@ a5ee4475:2ca75401
2025-05-09 17:10:35Título H1 - Formatação Markdown
[Titulo com '# ' antes do texto, pode não funcionar se o título H1 for iniciado depois de um texto normal]
list #descentralismo #markdown #clients #Amethyst #Yakihonne
Título H2 [2 hashtags e espaço]
Título H3 [3 hashtags e espaço]
Título H4 [4 hashtags e espaço]
Título H5 [5 hashtags e espaço]
Título H6 [6 hashtags e espaço]
*Copie e cole o texto para enxergar os caracteres usados
Réguas horizontais
- Com 3 sublinhados (_) seguidos:
- Com 3 hífens (-) seguidos:
- Com três asteriscos (*) seguidos:
Ênfases
Negrito: - Dois asteriscos antes e depois: Este é um texto em negrito
- Dois sublinhados antes e depois: Esse é um texto em negrito
Itálico - Um asterisco antes e um depois: Esse é um texto em itálico
- Um sublinhado antes e um depois: Esse é um texto em itálico
Tachado:
~~Aqui houve uma rasura~~
Bloco de citações
Usando 1 a 3 “>”:
O bloco de citações pode ser eninhado…
…Usando cada vez mais maior-que (>).
…Mesmo com espaços entre eles.
Listas
Não-ordenadas
- Crie um tópico começando com
+,-ou*. - Subtópicos são feitos adicionando 2 espaços:
- A mudança da marcação inicial não altera a lista:
- Com asterisco
- Com sinal de mais
- Com sinal de menos
- Muito fácil!
Ordenadas
- Lorem ipsum dolor sit amet
- Consectetur adipiscing elit
- Integer molestie lorem at massa
- Você pode usar números em sequência...
- ...ou deixar tudo como
1.ou outro número.
O número inicia com recuos:
- foo
- bar
Códigos
códigona mesma linhaCaixa de código
-
Códigos intentados com 4 espaços:
// Some comments line 1 of code line 2 of code line 3 of code
-
Com 3 acentos graves antes e depois:
Marcação de texto:
Insira o texto aqui...Marcação de sintaxe:
``` js var foo = function (bar) { return bar++; };
console.log(foo(5)); ```
Tabelas
| APP | Descrição | | ------ | ----------- | | Element | App de mensagens que usa a rede Matrix. | | Simplex | App de mensagens bastante usado. | | 0xchat | App de mensagens no Nostr. |
Links
-
Link autoconvertido https://github.com/nodeca/pica (habilite o linkify para ver)
Imagens nomeadas
Minion:

Stormtroopocat:
[https://octodex.github.com/images/stormtroopocat.jpg])
Como links, imagens também tem sintaxe footnote ‘!’ + ‘Outro texto’...
[https://octodex.github.com/images/dojocat.jpg])
…com uma referência id posterior da referência na localização da URL.
Plugins
O recurso de
markdown-ité um suporte muito eficaz de plugins de sintaxe.
Emojis
*Acesse o link para entender melhor
Marcação clássica: :wink: :cry: :laughing: :yum:
Figuras Ascii (emoticons): :-) :-( 8-) ;)
Veja como mudar a exibição com o twemoji.
Sobrescrito / Subscrito
*Acesse os links para entender melhor
- 19^th^
- H~2~O
\
*Acesse o link para entender melhor
++Texto Inserido++
\
*Acesse o link para entender melhor
==Texto marcado==
Notas de Rodapé
*Acesse o link para entender melhor
Nota de rodapé 1 link[^primeiro].
Nota de rodapé 2 link[^segundo].
Rodapé^[Texto do rodapé na linha] definição na linha.
Referência duplicada no rodapé[^segundo].
[^primeiro]: Rodapé pode ter marcação
e múltiplos parágrafos.[^segundo]: Texto de rodapé.
Listas de Definição
*Acesse o link para entender melhor
Termo 1
: Definição 1 com continuação preguiçosa.
Termo 2 com marcação na linha
: Definição 2
{ algum código, parte da Definição 2 } Third paragraph of definition 2.Estilo compacto:
Termo 1 ~ Definição 1
Termo 2 ~ Definição 2a ~ Definição 2b
Esse texto é uma adaptação do:
nostr:nevent1qqsv54qfgtme38r2tl9v6ghwfj09gdjukealstkzc77mwujr56tgfwspzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtczyqy0j6zknu2lr7qrge5yt725azecflhxv6d2tzwgtwrql5llukdqjqcyqqqqqqgfdk5w3
-
 @ 21335073:a244b1ad
2025-05-09 13:56:57
@ 21335073:a244b1ad
2025-05-09 13:56:57Someone asked for my thoughts, so I’ll share them thoughtfully. I’m not here to dictate how to promote Nostr—I’m still learning about it myself. While I’m not new to Nostr, freedom tech is a newer space for me. I’m skilled at advocating for topics I deeply understand, but freedom tech isn’t my expertise, so take my words with a grain of salt. Nothing I say is set in stone.
Those who need Nostr the most are the ones most vulnerable to censorship on other platforms right now. Reaching them requires real-time awareness of global issues and the dynamic relationships between governments and tech providers, which can shift suddenly. Effective Nostr promoters must grasp this and adapt quickly.
The best messengers are people from or closely tied to these at-risk regions—those who truly understand the local political and cultural dynamics. They can connect with those in need when tensions rise. Ideal promoters are rational, trustworthy, passionate about Nostr, but above all, dedicated to amplifying people’s voices when it matters most.
Forget influencers, corporate-backed figures, or traditional online PR—it comes off as inauthentic, corny, desperate and forced. Nostr’s promotion should be grassroots and organic, driven by a few passionate individuals who believe in Nostr and the communities they serve.
The idea that “people won’t join Nostr due to lack of reach” is nonsense. Everyone knows X’s “reach” is mostly with bots. If humans want real conversations, Nostr is the place. X is great for propaganda, but Nostr is for the authentic voices of the people.
Those spreading Nostr must be so passionate they’re willing to onboard others, which is time-consuming but rewarding for the right person. They’ll need to make Nostr and onboarding a core part of who they are. I see no issue with that level of dedication. I’ve been known to get that way myself at times. It’s fun for some folks.
With love, I suggest not adding Bitcoin promotion with Nostr outreach. Zaps already integrate that element naturally. (Still promote within the Bitcoin ecosystem, but this is about reaching vulnerable voices who needed Nostr yesterday.)
To promote Nostr, forget conventional strategies. “Influencers” aren’t the answer. “Influencers” are not the future. A trusted local community member has real influence—reach them. Connect with people seeking Nostr’s benefits but lacking the technical language to express it. This means some in the Nostr community might need to step outside of the Bitcoin bubble, which is uncomfortable but necessary. Thank you in advance to those who are willing to do that.
I don’t know who is paid to promote Nostr, if anyone. This piece isn’t shade. But it’s exhausting to see innocent voices globally silenced on corporate platforms like X while Nostr exists. Last night, I wondered: how many more voices must be censored before the Nostr community gets uncomfortable and thinks creatively to reach the vulnerable?
A warning: the global need for censorship-resistant social media is undeniable. If Nostr doesn’t make itself known, something else will fill that void. Let’s start this conversation.
-
 @ a5ee4475:2ca75401
2025-05-08 21:57:12
@ a5ee4475:2ca75401
2025-05-08 21:57:12brasil #portugal #portugues #bitcoin
Brasil
-
Jericoacoara - Ceará nostr:nprofile1qqsdc47glaz2z599a7utq9gk2xyf6z70t7ddyryrnweyt32z4sdarfsppemhxue69uhkummn9ekx7mp00ex584
-
Rolante - Rio Grande do Sul nostr:nprofile1qqsdrks96vr7vc7frjflm8lmhwleslwzgjlkpyj4ahjhzgm4n8dh0qqprdmhxue69uhkymm4de3k2u3wd45ku6tzdak8gtnfdenx7qgcwaen5te0xycrqt3hxyhryvfh9ccngde6xsurgwqpz3mhxue69uhhyetvv9ujuerpd46hxtnfduhxppd6
-
Santo Antonio do Pinhal - São Paulo nostr:nprofile1qqsr5maylee9j77ce0es6tgmxj3pax2dlsuuptkn2stuj95jzqysulgpzemhxue69uhhyetvv9ujuurjd9kkzmpwdejhgqgjwaehxw309ac82unsd3jhqct89ejhxqgdwaehxw309ahx7uewd3hkca6zsjl
Portugal
- Ilha da Madeira - nostr:nprofile1qqsv45qvfz5vdzwn9478wzusyggjf44x3w7xk8f3cgpe4px44wgv77cpr3mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmqpz3mhxue69uhhyetvv9ujumn0wd68ytnzvuq32amnwvaz7tmwdaehgu3dwfjkccte9eshquqzhddc4
-
-
 @ 57d1a264:69f1fee1
2025-05-11 06:23:03
@ 57d1a264:69f1fee1
2025-05-11 06:23:03Past week summary
From a Self Custody for Organizations perspective, after analyzing the existing protocols (Cerberus, 10xSecurityBTCguide and Glacier) and reading a bunch of relates articles and guides, have wrapped to the conclusion that this format it is good to have as reference. However, something else is needed. For example, a summary or a map of the whole process to provide an overview, plus a way to deliver all the information and the multy-process in a more enjoyable way. Not a job for this hackathon, but with the right collaborations I assume it's possible to: - build something that might introduce a bit more quests and gamification - provide a learning environment (with testnet funds) could also be crucial on educating those unfamiliar with bitcoin onchain dynamics.
Have been learning more and playing around practicing best accessibility practices and how it could be applied to a desktop software like Bitcoin Safe. Thanks to @johnjherzog for providing a screen recording of his first experience and @jasonb for suggesting the tools to be used. (in this case tested/testing on Windows with the Accessibility Insights app). Some insight shared have been also applied to the website, running a full accessibility check (under WCAG 2.2 ADA, and Section 508 standards) with 4 different plugins and two online tools. I recognize that not all of them works and analyze the same parameters, indeed they complement each other providing a more accurate review.
For Bitcoin Safe interface improvements, many suggestions have been shared with @andreasgriffin , including: - a new iconset, including a micro-set to display the number of confirmed blocs for each transaction - a redesigned History/Dashboard - small refinements like adding missing columns on the tables - allow the user to select which columns to be displayed - sorting of unconfirmed transactions - Defining a new style for design elements like mempool blocks and quick receive boxes You can find below some screenshots with my proposals that hopefully will be included in the next release.
Last achievement this week was to prepare the website https://Safe.BTC.pub, the container where all the outcomes f this experiment will be published. You can have a look, just consider it still WIP. Branding for the project has also been finalized and available in this penpot file https://design.penpot.app/#/workspace?team-id=cec80257-5021-8137-8005-eab60c043dd6&project-id=cec80257-5021-8137-8005-eab60c043dd8&file-id=95aea877-d515-80ac-8006-23a251886db3&page-id=132f519a-39f4-80db-8006-2a41c364a545
What's for next week
After spending most of the time learning and reading material, this coming week will be focused on deliverables. The goal as planned will be to provide: - Finalized Safe₿its brand and improve overall desktop app experience, including categorization of transactions and addresses - An accessibility report or guide for Bitcoin Safe and support to implement best practices - A first draft of the Self-Custody for Organizations guide/framework/protocol, ideally delivered through the website http://Safe.BTC.pub in written format, but also as FlowChart to help have an overview of the whole resources needed and the process itself. This will clearly define preparations and tools/hardwares needed to successfully complete the process.
To learn more about the project, you can visit: Designathon website: https://event.bitcoin.design/#project-recj4SVNLLkuWHpKq Discord channel: https://discord.com/channels/903125802726596648/1369200271632236574 Previous SN posts: https://stacker.news/items/974489/r/DeSign_r and https://stacker.news/items/974488/r/DeSign_r
Stay tuned, more will be happening this coming week
originally posted at https://stacker.news/items/977190
-
 @ b04082ac:29b5c55b
2025-05-08 14:35:02
@ b04082ac:29b5c55b
2025-05-08 14:35:02Money has always been more than a medium of exchange. It reflects what societies value, how they organize trust, and what they choose to remember. This article explores the idea that money functions as a form of collective memory, and how Bitcoin may be restoring this role in a new way.

The Asante Example
In the Asante Empire, which flourished in West Africa during the 18th and 19th centuries, gold dust served as the primary medium of exchange. To measure it, traders used ornate spoons made of brass. These spoons were often carved with birds, animals, or abstract symbols. They were not currency themselves, but tools used to handle gold dust accurately.
Importantly, these spoons also carried meaning. Symbols and proverbs embedded in the spoons conveyed lessons about honesty, community, and continuity. For example, the Sankofa bird, shown turning its head backward to retrieve an egg from its back, represented the proverb, “It is not wrong to go back for that which you have forgotten.” This was a reminder to learn from the past.

The spoons reflect an understanding that money and its instruments are not just practical tools. They are cultural artifacts that store shared values. In the Asante context, even measurement was ritualized and tied to ethics and memory.
Money as a Cultural Medium
This connection between money and cultural meaning is not unique to the Asante Empire. Modern fiat currencies also carry symbols, phrases, and designs that reflect national identity and political values.
The U.S. dollar includes Latin phrases and national symbols meant to convey stability and purpose. The British pound features royal iconography, reinforcing the idea of continuity and sovereignty. When the euro was introduced, it deliberately avoided specific national references. Itsdesign used bridges and windowsto suggest openness and cooperation across the continent.

These design choices show that societies still embed meaning into their money. Even in a digital or fiat context, money is used to transmit a story about who we are, where authority lies, and what we value.
The Fragility of Fiat Memory
While fiat money carries cultural symbols, the narratives behind those symbols can be fragile.
In 2021, the central bank of the Philippines removed democratic leaders from its banknotes,triggering public criticism. In the United States, attempts to replace Andrew Jackson with Harriet Tubman on the $20 billfaced repeated delays. These examples show how political control over money includes control over what stories are told and remembered.

Unlike objects passed down through generations, fiat memory can be edited or erased. In this sense, it is vulnerable. The meaning encoded in fiat systems can shift depending on who holds power.
Bitcoin as a New Form of Memory
Bitcoin is described as digital money. But it also introduces a different model of how societies can record value and preserve meaning.
The Bitcoin network launched in 2009 with a small message embedded in its first block: “Chancellor on brink of second bailout for banks.” This was a reference to a newspaper headline that day and a clear sign of protest against financial bailouts, centralized monetary policy, and forever wars.

This moment marked the beginning of a system where memory is stored differently. Instead of relying on governments or institutions, Bitcoin stores its history on a public ledger maintained by a decentralized network of participants. Its memory is not symbolic or political; it is structural. Every transaction, every block, is preserved through time-stamped computation and consensus.
No single authority can change it. The rules are clear and publicly auditable. In this way, Bitcoin offers a version of money where memory is both neutral and resilient.
Cultural Expression and Community Values
Even though Bitcoin lacks the traditional symbols found on banknotes, it has developed its own culture. Phrases like “Don’t trust, verify” or “Stay humble, stack sats” are shared widely in the Bitcoin community. These ideas reflect a focus on self-responsibility, verification, and long-term thinking.
These proverbs can be compared to the carved messages on the Asante spoons. While the contexts are very different, the underlying idea is similar: a community using language and symbols to reinforce its shared values.
Bitcoin also has a well established and growing art scene. Bitcoin conferences often feature dedicated sections for art inspired by the protocol and its culture. Statues of Satoshi Nakamoto have been installed in cities like Budapest, Lugano, and Fornelli. These physical works reflect the desire to link Bitcoin’s abstract values to something tangible.

Looking Back to Look Forward
The Asante example helps us see that money has long been tied to memory and meaning. Their spoons were practical tools but also cultural anchors. Bitcoin, while new and digital, may be playing a similar role.
Instead of relying on political symbols or national myths, Bitcoin uses code, transparency, and global consensus to create trust. In doing so, it offers a way to preserve economic memory that does not depend on power or politics.
It’s still early to know what kind of legacy Bitcoin will leave. But if it succeeds, it may not just change how money works. It may also change how civilizations remember.
-
 @ 57d1a264:69f1fee1
2025-05-11 05:52:56
@ 57d1a264:69f1fee1
2025-05-11 05:52:56Past week summary
From a Self Custody for Organizations perspective, after analyzing the existing protocols (Cerberus, 10xSecurityBTCguide and Glacier) and reading a bunch of relates articles and guides, have wrapped to the conclusion that this format it is good to have as reference. However, something else is needed. For example, a summary or a map of the whole process to provide an overview, plus a way to deliver all the information and the multy-process in a more enjoyable way. Not a job for this hackathon, but with the right collaborations I assume it's possible to: - build something that might introduce a bit more quests and gamification - provide a learning environment (with testnet funds) could also be crucial on educating those unfamiliar with bitcoin onchain dynamics.
Have been learning more and playing around practicing best accessibility practices and how it could be applied to a desktop software like Bitcoin Safe. Thanks to @johnjherzog for providing a screen recording of his first experience and @jasonbohio for suggesting the tools to be used. (in this case tested/testing on Windows with the Accessibility Insights app). Some insight shared have been also applied to the website, running a full accessibility check (under WCAG 2.2 ADA, and Section 508 standards) with 4 different plugins and two online tools. I recognize that not all of them works and analyze the same parameters, indeed they complement each other providing a more accurate review.
For Bitcoin Safe interface improvements, many suggestions have been shared with @andreasgriffin , including: - a new iconset, including a micro-set to display the number of confirmed blocs for each transaction - a redesigned History/Dashboard - small refinements like adding missing columns on the tables - allow the user to select which columns to be displayed - sorting of unconfirmed transactions - Defining a new style for design elements like mempool blocks and quick receive boxes You can find below some screenshots with my proposals that hopefully will be included in the next release.
Last achievement this week was to prepare the website https://Safe.BTC.pub, the container where all the outcomes f this experiment will be published. You can have a look, just consider it still WIP. Branding for the project has also been finalized and available in this penpot file https://design.penpot.app/#/workspace?team-id=cec80257-5021-8137-8005-eab60c043dd6&project-id=cec80257-5021-8137-8005-eab60c043dd8&file-id=95aea877-d515-80ac-8006-23a251886db3&page-id=132f519a-39f4-80db-8006-2a41c364a545
What's for next week
After spending most of the time learning and reading material, this coming week will be focused on deliverables. The goal as planned will be to provide: - Finalized Safe₿its brand and improve overall desktop app experience, including categorization of transactions and addresses - An accessibility report or guide for Bitcoin Safe and support to implement best practices - A first draft of the Self-Custody for Organizations guide/framework/protocol, ideally delivered through the website http://Safe.BTC.pub in written format, but also as FlowChart to help have an overview of the whole resources needed and the process itself. This will clearly define preparations and tools/hardwares needed to successfully complete the process.
To learn more about the project, you can visit: Designathon website: https://event.bitcoin.design/#project-recj4SVNLLkuWHpKq Discord channel: https://discord.com/channels/903125802726596648/1369200271632236574 Previous SN posts: https://stacker.news/items/974489/r/DeSign_r and https://stacker.news/items/974488/r/DeSign_r
Stay tuned, more will be happening this coming week
originally posted at https://stacker.news/items/977180
-
 @ c631e267:c2b78d3e
2025-05-10 09:50:45
@ c631e267:c2b78d3e
2025-05-10 09:50:45Information ohne Reflexion ist geistiger Flugsand. \ Ernst Reinhardt
Der lateinische Ausdruck «Quo vadis» als Frage nach einer Entwicklung oder Ausrichtung hat biblische Wurzeln. Er wird aber auch in unserer Alltagssprache verwendet, laut Duden meist als Ausdruck von Besorgnis oder Skepsis im Sinne von: «Wohin wird das führen?»
Der Sinn und Zweck von so mancher politischen Entscheidung erschließt sich heutzutage nicht mehr so leicht, und viele Trends können uns Sorge bereiten. Das sind einerseits sehr konkrete Themen wie die zunehmende Militarisierung und die geschichtsvergessene Kriegstreiberei in Europa, deren Feindbildpflege aktuell beim Gedenken an das Ende des Zweiten Weltkriegs beschämende Formen annimmt.
Auch das hohe Gut der Schweizer Neutralität scheint immer mehr in Gefahr. Die schleichende Bewegung der Eidgenossenschaft in Richtung NATO und damit weg von einer Vermittlerposition erhält auch durch den neuen Verteidigungsminister Anschub. Martin Pfister möchte eine stärkere Einbindung in die europäische Verteidigungsarchitektur, verwechselt bei der Argumentation jedoch Ursache und Wirkung.
Das Thema Gesundheit ist als Zugpferd für Geschäfte und Kontrolle offenbar schon zuverlässig etabliert. Die hauptsächlich privat finanzierte Weltgesundheitsorganisation (WHO) ist dabei durch ein Netzwerk von sogenannten «Collaborating Centres» sogar so weit in nationale Einrichtungen eingedrungen, dass man sich fragen kann, ob diese nicht von Genf aus gesteuert werden.
Das Schweizer Bundesamt für Gesundheit (BAG) übernimmt in dieser Funktion ebenso von der WHO definierte Aufgaben und Pflichten wie das deutsche Robert Koch-Institut (RKI). Gegen die Covid-«Impfung» für Schwangere, die das BAG empfiehlt, obwohl es fehlende wissenschaftliche Belege für deren Schutzwirkung einräumt, formiert sich im Tessin gerade Widerstand.
Unter dem Stichwort «Gesundheitssicherheit» werden uns die Bestrebungen verkauft, essenzielle Dienste mit einer biometrischen digitalen ID zu verknüpfen. Das dient dem Profit mit unseren Daten und führt im Ergebnis zum Verlust unserer demokratischen Freiheiten. Die deutsche elektronische Patientenakte (ePA) ist ein Element mit solchem Potenzial. Die Schweizer Bürger haben gerade ein Referendum gegen das revidierte E-ID-Gesetz erzwungen. In Thailand ist seit Anfang Mai für die Einreise eine «Digital Arrival Card» notwendig, die mit ihrer Gesundheitserklärung einen Impfpass «durch die Hintertür» befürchten lässt.
Der massive Blackout auf der iberischen Halbinsel hat vermehrt Fragen dazu aufgeworfen, wohin uns Klimawandel-Hysterie und «grüne» Energiepolitik führen werden. Meine Kollegin Wiltrud Schwetje ist dem nachgegangen und hat in mehreren Beiträgen darüber berichtet. Wenig überraschend führen interessante Spuren mal wieder zu internationalen Großbanken, Globalisten und zur EU-Kommission.
Zunehmend bedenklich ist aber ganz allgemein auch die manifestierte Spaltung unserer Gesellschaften. Angesichts der tiefen und sorgsam gepflegten Gräben fällt es inzwischen schwer, eine zukunftsfähige Perspektive zu erkennen. Umso begrüßenswerter sind Initiativen wie die Kölner Veranstaltungsreihe «Neue Visionen für die Zukunft». Diese möchte die Diskussionskultur reanimieren und dazu beitragen, dass Menschen wieder ohne Angst und ergebnisoffen über kontroverse Themen der Zeit sprechen.
Quo vadis – Wohin gehen wir also? Die Suche nach Orientierung in diesem vermeintlichen Chaos führt auch zur Reflexion über den eigenen Lebensweg. Das ist positiv insofern, als wir daraus Kraft schöpfen können. Ob derweil der neue Papst, dessen «Vorgänger» Petrus unsere Ausgangsfrage durch die christliche Legende zugeschrieben wird, dabei eine Rolle spielt, muss jede/r selbst wissen. Mir persönlich ist allein schon ein Führungsanspruch wie der des Petrusprimats der römisch-katholischen Kirche eher suspekt.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 57d1a264:69f1fee1
2025-05-10 05:45:52
@ 57d1a264:69f1fee1
2025-05-10 05:45:52Finale: once the industry-standard of music notation software, now a cautionary tale. In this video, I explore how it slowly lost its crown through decades of missed opportunities - eventually leading to creative collapse due to various bureaucratic intrigues, unforeseen technological changes and some of the jankiest UI/UX you've ever seen.
https://www.youtube.com/watch?v=Yqaon6YHzaU
originally posted at https://stacker.news/items/976219
-
 @ 57d1a264:69f1fee1
2025-05-10 05:34:46
@ 57d1a264:69f1fee1
2025-05-10 05:34:46
For generations before generative text, writers have used the em dash to hop between thoughts, emotions, and ideas. Dickens shaped his morality tales with it, Woolf’s stream-of-consciousness flowed through it, Kerouac let it drive his jazz-like prose. Today, Sally Rooney threads it through her quiet truths of the heart.
But this beloved punctuation mark has become a casualty of the algorithmic age. The em dash has been so widely adopted by AI-generated text that even when used by human hands, it begs the question: was this actually written or apathetically prompted?
The battle for the soul of writing is in full swing. And the human fightback starts here. With a new punctuation mark that serves as a symbol of real pondering, genuine daydreaming, and true editorial wordsmithery. Inspired by Descartes’ belief that thinking makes us human, the am dash is a small but powerful testament that the words you’ve painstakingly and poetically pulled together are unequivocally, certifiably, and delightfully your own.
Let's reclain writig from AI—oneam dash at time.
Download the fonts:
— Aereal https://bit.ly/3EO6fo8 — Times New Human https://bit.ly/4jQTcRS
Learn more about the am dash
https://www.theamdash.com
originally posted at https://stacker.news/items/976218
-
 @ a5ee4475:2ca75401
2025-05-07 20:00:42
@ a5ee4475:2ca75401
2025-05-07 20:00:42lista #descentralismo #comunidades #portugues
[em atualização]
*Até a criação desse post, só alguns clients têm acesso às comunidades, tal como o Satellite, o Coracle e o Amethyst.
**Se a comunidade não tiver proprietários ou moderadores ativos, o seu envio de mensagem poderá não ser aprovada para aparecer nela.
***Se criar uma, busque colocar um ou mais moderadores para a comunidade não acabar, caso você se ausente.
Geral:
n/Brasil (Por: nostr:nprofile1qqspxhftq9htg9njgaefr6nmetl97q8qqlwxvynppl6c5zr9t0qmp9gpzfmhxue69uhhqatjwpkx2urpvuhx2ucpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3qamnwvaz7tmwdaehgu3wwa5kueguy3tt5) nostr:naddr1qqryyunpwd5kcq3qzdwjkqtwkst8y3mjj848hjh7tuqwqp7uvcfxzrl43gyx2k7pkz2sxpqqqzr0v4va9m3
n/Portugal (por: nostr:nprofile1qqsddhy42shp3w9h4mp0z3ss74wrxk47hmrk70deukxz23np6pvn5rqpr9mhxue69uhhyetvv9ujuumwdae8gtnnda3kjctv9uqsuamnwvaz7tmwdaejumr0dshszynhwden5te0dehhxarj9ek82tntv5hsd2h46x) nostr:naddr1qqy9qmmjw36kwctvqgsddhy42shp3w9h4mp0z3ss74wrxk47hmrk70deukxz23np6pvn5rqrqsqqpphkc3wuaj
n/Moçambique (por: nostr:nprofile1qqszx6hsp38v2re3q2pzxpv3slg5u7pxklxze7evarqk4eugqmhntdcpzpmhxue69uhkummnw3ezumt0d5hszrnhwden5te0dehhxtnvdakz7qgawaehxw309ahx7um5wghxy6t5vdhkjmn9wgh8xmmrd9skctc082x0w) nostr:naddr1qqf56m7r5ask6cnfw96ktuyls7e0p8u8hupzqgm27qxya3g0xypgygc9jxraznncy6muct8m9n5vz6h83qrw7ddhqvzqqqyx7c0autxh
n/África (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqru8qtxwf5kxcgzyr4vnn3ff93j2539t3973a9c0ky8n67fsjmrc04s8vwc96gmrr2uxqcyqqqgdaspqgn0q
-
n/Perguntas-e-Respostas (Por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qq3lp8u85lcflpah2pz4y364fe2yz5edg5k4y32n2p84x4zp203fm980hz8sygy7fff8g6l23gp5uqtuyqwkqvucx6mhe7r9h7v6wyzzj0v6lrztcspsgqqqsmmqtz9a9x
n/Links-e-Tutoriais-Úteis (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qqj0p8u85lcflpahf3y5uj6n94zj64z42384yj2pf9fjmsu623z5j5lsn7ftkq3qne99yarta29qxnsp0ssp6cpnnqmtwl8cvklenfcsg2fantuvf0zqxpqqqzr0v3zu9fd
n/JornalismoNãoEstáMorto - Notícias e escrita informativa (Por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:nprofile1qqs0f74kketdcv63r53mlzgzfh93we3dkgzkldv2p6g62a8gf3g92yqpz4mhxue69uhkummnw3ezummcw3ezuer9wchszyrhwden5te0dehhxarj9ekk7mf0qywhwumn8ghj7mn0wd68ytnzd96xxmmfdejhytnnda3kjctv9ufhpwuw) nostr:naddr1qqd55n6jfeq5cj2nf48j6nkrsd8j632n2npczt2dfaf9gnczyrvvsrjnp9xgqysjendxg6x2q7fldu73ajnf5e2h7uspp9tjl7jvxqcyqqqgdasy2kfg4
n/Agorismo³-E-Mercado (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qqs0p8u85lcflpahg9r575jf2dx5ls4n94zj6n292fp5z3z094gry5qzyz0y55n5d04g5q6wq97zq8tqxwvrddmulpjmlxd8zppf8kd0339ugqcyqqqgdasrlnr7s
n/FeiraNostr - Marketplace (por: nostr:nprofile1qqstwrymlvj5kcrjspppyepmavrhk6afg9sfa4q9zhvmzztp6am83xgpr9mhxue69uhhyetvv9ujuumwdae8gtnnda3kjctv9u2dla7c) nostr:naddr1qq9yvetfwfs5ummnw3eqyg9hpjdlkf2tvpegqssjvsa7kpmmdw55zcy76sz3tkd3p9sawancnypsgqqqsmmqucz73h
Tecnologia:
n/ndevs-br (por: nostr:nprofile1qqs923ewnsqlx7347cpjhxmcmt0rsmnwf3tasr736pjx4wee9q89ufcppemhxue69uhkummn9ekx7mp0gc3lmk) nostr:naddr1qqyxuer9weej6cnjqgs923ewnsqlx7347cpjhxmcmt0rsmnwf3tasr736pjx4wee9q89ufcrqsqqpphk7z3axp
n/BrasilDev (por: nostr:nprofile1qqsyczyspluueyxautr3nxa2httku5e9m7d05dnu5zj3jnrg0jmucqcpr9mhxue69uhkyu3wwp6hyurvv4ex2mrp0yhxxmmd9uqs6amnwvaz7tmwdaejumr0dsq3camnwvaz7tmwdaehgu3wvf5hgcm0d9hx2u3wwdhkx6tpdsz8cl6e) nostr:naddr1qqy5yunpwd5kc3r9wcpzqnqgjq8lnnysmh3vwxvm42adwmjnyh0e473k0js22x2vdp7t0nqrqvzqqqyx7cvxdlla
n/Linux (por: nostr:nprofile1qqsxhewvq6fq9lzjmfwqrpg2ufgl09uh2cksupa853zxv04u2fva4uqpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsz9nhwden5te0dehhxarjv4kxjar9wvhx7un89uqsuamnwvaz7tmwdaejumr0dshs6tvc92 ) nostr:naddr1qqz5c6tww4uqz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsygrtuhxqdyszl3fd5hqps59wy50hj7t4vtgwq7n6g3rx8679ykw67qpsgqqqsmmqznes6u
n/IA - Inteligencia Artificial (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqpyjsgpzpmhxue69uhkummnw3ezumt0d5hsyg82e88zjjtry4fz2hztar6tslvg084unp9k8sltqwcast53kxx4cvpsgqqqsmmqs03ln5
n/HardwareBr - Dúvidas, experiências e atualizações sobre hardware (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qq9ysctjv3mkzun9gfeqyg82e88zjjtry4fz2hztar6tslvg084unp9k8sltqwcast53kxx4cvpsgqqqsmmq54k3eu
n/SegurançaDaInformação (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqv9xet8w4exzmkr5as5gc2fdenx7undv8p60sardupzp6kfec55jce92gj4cjlg7ju8mzrea0ycfd3u86crk8vzayd334wrqvzqqqyx7cpss4m0
n/Moneroptbr (Por: nostr:nprofile1qqsyrmue77dm5ef5pmqsly0wp3248mk3vr9temj5p54plygcr97pavcpzemhxue69uhhyetvv9ujuurjd9kkzmpwdejhgqgjwaehxw309ac82unsd3jhqct89ejhxqg5waehxw309aex2mrp0yhxgctdw4eju6t0tpqrvk) nostr:naddr1qq9y6mmwv4ex7ur5vfeqz3rhwvaz7tm8d9e8wmm5xf4k77fnddmx5dnxdvmk7um9dackz7nsx4m8wcn9v9mk7cmzxdknydm2vdchgctgxc6kvvnxddkrx7ty9ehku6t0dchsygzpa7vl0xa6v56qasg0j8hqc42namgkpj4uae2q62sljyvpjlq7kvpsgqqqsmmqknmdan
Ciência:
n/Astronomia - Espaço e astros (por: nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpzpmhxue69uhkummnw3ezumt0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0s8pkkr ) nostr:naddr1qq9yzum5wfhkummdd9ssz9thwden5te0dehhxarj9ehhsarj9ejx2a30qgs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgrqsqqpphkkdel5t
n/Mecatrônica-NOSTR (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4) nostr:naddr1qqfy6etrv9689sa5de5kxcfdfe84x4zjqythwumn8ghj76twvfhhstnp0faxzmt09ehx2ap0qgsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcrqsqqpphkgsy84w
n/Antropologystr - Antropologia (por: nostr:npub1fyd0awkakq4aap70ual7mtlszjle9krffgwnsrkyua2frzmysd8qjj8gvg ) nostr:naddr1qq85zmn5dpex7ur0d3hkw7tnw3eqygzfrtlt4hds900g0nl80lk6luq5h7fds622r5uqa3882jgckeyrfcpsgqqqsmmq4xrrgc
Cultura:
n/Estante-Nostr - Literatura e livros (por: nostr:nprofile1qqsdl72sxdne0yqwa7tpznlnc4yt5t9jf8htspnynrja92dcschm7sqpr4mhxue69uhkummnw3ez6vp39eukz6mfdphkumn99e3k7mf0qywhwumn8ghj7mn0wd68ytfsxgh8jcttd95x7mnwv5hxxmmd9uq37amnwvaz7tmwdaehgu3dxqejuer0wfskvctrw3hhy7fwdaexwtcjwfqr2) nostr:naddr1qqx52um5v9h8ge2lfehhxarjqgsdl72sxdne0yqwa7tpznlnc4yt5t9jf8htspnynrja92dcschm7sqrqsqqpphkwzdgct
n/Literatura-Arte-Cultura (por: nostr:nprofile1qqs92lr9pdcqnulddvzgj5twpz8ysdv7njhxagyxwtnlj8p3kpxxs9cprfmhxue69uhhq7tjv9kkjepwve5kzar2v9nzucm0d5hsz9nhwden5te0v4jx2m3wdehhxarj9ekxzmny9uqsuamnwvaz7tmwdaejumr0dshs8l9z0j) nostr:naddr1qqt5c6t5v4exzar4wfsj6stjw3jj6sm4d3682unpqgs92lr9pdcqnulddvzgj5twpz8ysdv7njhxagyxwtnlj8p3kpxxs9crqsqqpphkty54um
n/História-e-Filosofia (por: nostr:npub1ne99yarta29qxnsp0ssp6cpnnqmtwl8cvklenfcsg2fantuvf0zqmpxjxk ) nostr:naddr1qqjlp8u85lcflpahfpy4x4xrjdfyjsfdg5k5vj2vfaf573jfg8cflrum7z0cezczyz0y55n5d04g5q6wq97zq8tqxwvrddmulpjmlxd8zppf8kd0339ugqcyqqqgdas35g9vs
n/Urbanism - Urbanismo (por: nostr:nprofile1qqstwrymlvj5kcrjspppyepmavrhk6afg9sfa4q9zhvmzztp6am83xgpr9mhxue69uhhyetvv9ujuumwdae8gtnnda3kjctv9u2dla7c) nostr:naddr1qqy92unzv9hxjumdqgstwrymlvj5kcrjspppyepmavrhk6afg9sfa4q9zhvmzztp6am83xgrqsqqpphkyl5u8a
Fé:
n/Religião-e-Teologia - Cristianismo (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qqs0p8u85lcflpah2fz5cj28f8pcxnedg5k4g320f385wj2p7z0ehyqzyz0y55n5d04g5q6wq97zq8tqxwvrddmulpjmlxd8zppf8kd0339ugqcyqqqgdasta04x5
n/Ateismo-e-Agnosticismo (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqtyzar9d9ek6medv5k5zemwdaehg6trd9ek6mczyr4vnn3ff93j2539t3973a9c0ky8n67fsjmrc04s8vwc96gmrr2uxqcyqqqgdasuuzmw8
n/Budismo (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqr5yatyd9ek6mczyr4vnn3ff93j2539t3973a9c0ky8n67fsjmrc04s8vwc96gmrr2uxqcyqqqgdas0kmt4m
n/Taoismo - Daoismo (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqy9gct0cwkhxmt0qy88wumn8ghj7mn0wvhxcmmv9upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqyx7crkzqvd
n/Espiritualidade - Significação e sublimidade (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qq852umsd9exjar4v9kxjerpv3jszyrhwden5te0dehhxarj9ekk7mf0qgsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscrqsqqpphkxa5nfy
Entretenimento:
n/Equinox - Cinema no Nostr (por: nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpzpmhxue69uhkummnw3ezumt0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0s8pkkr) nostr:naddr1qqr52ut4d9hx77qpremhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet59upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqyx7cmc79n5
n/Rock/metal - Músicas Rock e Metal (por: nostr:nprofile1qqs9nyy7ctpy334n3p7gh4p93lmj2cch8ae8jgjsp8al2g32stdnpdcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpr9mhxue69uhhyetvv9ujumn0wd68ytnrdakjuct49us57cz4 e nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsz9mhwden5te0wfjkccte9ec8y6tdv9kzumn9wshszrnhwden5te0dehhxtnvdakz748t750 ) nostr:naddr1qq99ymmrdvh56et5v9kqzqqzypvep8kzcfyvdvug0j9agfv07ujkx9elwfujy5qfl06jy25zmvctwqcyqqqgdas306zj5
n/Música-Cinema-e-Livros (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qq4lp8u85lcflpahfhpe556fgdqj6s6ffez56sfdyck5cj2k2f848uyl366lp8unhhcflyu6qgsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qrqsqqpphkfyz9pf
n/Lugares-e-Viagens (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qqjlp8u85lcflpahf325ws2jg4fj63fd2ey5z369feflp8uv3mcflryd7z0cercpqqpzp8j22f6xh652qd8qzlpqr4sr8xpkka70sedlnxn3qs5nmxhccj7yqvzqqqyx7c965gfw
n/MídiasPerdidas - Lost Media (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qqw0p8u85lcflpahfhpc63zfg9fj65z92fzyj3zp20cflfusqgsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qrqsqqpphkdltjpa
n/Football - Futebol (Por: nostr:nprofile1qqsyjxh7htwmq277sl87wlld4lcpf0ujmp5558fcpmzww4y33djgxnsppemhxue69uhkummn9ekx7mp0qywhwumn8ghj7mn0wd68ytnzd96xxmmfdejhytnnda3kjctv9uq32amnwvaz7tmjv4kxz7fwv3sk6atn9e5k7tc9l2d6x / Moderadores: nostr:nprofile1qqsx5rzeds2gf6hzaqf35qc0y6v5fys72fsec8w3gwszn3jw5mxewvgpz4mhxue69uhkummnw3ezummcw3ezuer9wchszrnhwden5te0dehhxtnvdakz7qgswaehxw309ahx7um5wghx6mmd9u5c2kxa & nostr:nprofile1qqspxhftq9htg9njgaefr6nmetl97q8qqlwxvynppl6c5zr9t0qmp9gpzfmhxue69uhhqatjwpkx2urpvuhx2ucpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3qamnwvaz7tmwdaehgu3wwa5kueguy3tt5) nostr:naddr1qqyxvmm0w33xzmrvqgsyjxh7htwmq277sl87wlld4lcpf0ujmp5558fcpmzww4y33djgxnsrqsqqpphkg0nfw5
n/Formula-1 (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qqy5vmmjd46kccfdxypzp8j22f6xh652qd8qzlpqr4sr8xpkka70sedlnxn3qs5nmxhccj7yqvzqqqyx7cc95u5w
n/Games - Atualizações sobre jogos (por: nostr:npub1atyuu22fvvj4yf2uf050fwra3pu7hjvykc7ravpmrkpwjxcc6hpsfneh4e ) nostr:naddr1qqz5wctdv4esyg82e88zjjtry4fz2hztar6tslvg084unp9k8sltqwcast53kxx4cvpsgqqqsmmqn0x7k7
n/JogosBrasil - Clips de jogos (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4 ) nostr:naddr1qq955mm8dae5yunpwd5kcqghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7q3qj90yg0hl4e6qr7yg982dlh0qxdefy72d6ntuqet7hv3ateya782sxpqqqzr0vus9jl2
n/Minecraft (por: nostr:npub19xc7f5lg2z6svrjgye63rx44a96aq2ysqajx5tmum28cu6mk5j3qj3n9m9 ) nostr:naddr1qqy566twv43hyctxwspzq2d3unf7s594qc8ysfn4zxdtt6t46q5fqpmydghhek503e4hdf9zqvzqqqyx7ct7hldr
n/GenshinImpactBr (por: nostr:nprofile1qqs28fezzs5n2rdjh9deqv3ztk59mhg4j2jxaee7a4amkya30jnruggppemhxue69uhkummn9ekx7mp0qyg8wumn8ghj7mn0wd68ytnddakj7qgawaehxw309ahx7um5wghxy6t5vdhkjmn9wgh8xmmrd9skctcnffw22) nostr:naddr1qqtlp8u85lcflpahgajkuumgd9hyjmtsv93hgsnjq9z8wue69uhkw6tjwahhgvntdaunx6mkdgmxv6ehdaek2mm3v9a8qdtkwa3x2cthda3kyvmdxgmk5cm3w3sksd34vcexv6mvxdukgtn0de5k7m30qgs28fezzs5n2rdjh9deqv3ztk59mhg4j2jxaee7a4amkya30jnruggrqsqqpphkq4s4py
Libertarianismo:
n/Defensores-caseiros (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4) nostr:naddr1qq0lp8u85lcflpahg3jkvetwwdhhyetn943kzum9d9ex7ulsn78mgq3qgazxqfx8ldqkgaldz3hlwed2h3nwzfmwavkxp3s9j36qhfzeladsxpqqqzr0vcr78h2
n/Desobediência_Civil (por: nostr:nprofile1qqs2kw4x8jws3a4heehst0ywafwfymdqk35hx8mrf0dw6zdsnk5kj9gpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m30q9z8wue69uhk77r5wfjx2anpwcmrg73kx3ukydmcxeex5ee5de685ut2dpjkgmf4vg6h56n3w4k82emtde585u35xeh8jvn3vfskgtn0de5k7m306r5ytp) nostr:naddr1qq2ygetnda3x2erfcw4xucmfv905x6tkd9kqz3rhwvaz7tm8d9e8wmm5xf4k77fnddmx5dnxdvmk7um9dackz7nsx4m8wcn9v9mk7cmzxdknydm2vdchgctgxc6kvvnxddkrx7ty9ehku6t0dchsyg9t82nre8gg76muumc9hj8w5hyjdkstg6tnra35hkhdpxcfm2tfz5psgqqqsmmqlg3ata
n/sobreviNOSTR - Sobrevivencialismo (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4) nostr:naddr1qq20p8u85lcflpah2dhkyun9we55un6n23fqz3rhwvaz7tm8d9e8wmm5xf4k77fnddmx5dnxdvmk7um9dackz7nsx4m8wcn9v9mk7cmzxdknydm2vdchgctgxc6kvvnxddkrx7ty9ehku6t0dchsygz8g3szf3lmg9j80mg5dlmkt24uvmsjwmht93svvpv5ws96gk0ltvpsgqqqsmmqtempje
n/Triggr - Armas (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4) nostr:naddr1qqr9g5jfgar4yqghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7q3qgazxqfx8ldqkgaldz3hlwed2h3nwzfmwavkxp3s9j36qhfzeladsxpqqqzr0vt5085y
n/Kaboom - Química e explosivos (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4 ) nostr:naddr1qqt0p8u85lcflpahfdq5yn60fhcflra57z0602qppemhxue69uhkummn9ekx7mp0qgsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcrqsqqpphk637p09
n/CAVERNA-DO-PIRATA - Pirataria (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4) nostr:naddr1qq40p8u85lcflpahgdq4v32jfeqj63z094gyj5jp23qlp8u0kn3gpr0znzswlwy07z0ca2gpg3mhxw309ankjunhda6ry6m00yekkan2xenxkdm0wdjk7utp0fcr2anhvfjkzam0vd3rxmfjxa4xxut5v95rvdtxxfnxkmpn09jzummwd9hkutczypr5gcpycla5zerha52xlam9427xdcf8dm4jccxxqk28gzayt8l4kqcyqqqgdask5hmmn
n/PrivateSociety - Propostas e discussões para uma sociedade privada (por: nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qq89qunfweshge2nda3kjet50ypzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqyx7cfvhgrt
n/TeoriaDasBandeiras (por: nostr:nprofile1qqs8efvwljfdwa0qynp7n9dhqacf3llucdqtm9ge8kjv0dt40yw586gpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshszrnhwden5te0dehhxtnvdakz7ar9xsz) nostr:naddr1qqf9get0wf5kzerpwdpxzmnyv45hyctnqgs8efvwljfdwa0qynp7n9dhqacf3llucdqtm9ge8kjv0dt40yw586grqsqqpphkatc9rh
n/SemFronteiras (por: nostr:nprofile1qqs8efvwljfdwa0qynp7n9dhqacf3llucdqtm9ge8kjv0dt40yw586gpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshszrnhwden5te0dehhxtnvdakz7ar9xsz) nostr:naddr1qqx4xetdgeex7mn5v45hyctnqgs8efvwljfdwa0qynp7n9dhqacf3llucdqtm9ge8kjv0dt40yw586grqsqqpphkjs0cue
n/AnarcoSobrevivencialismo (por: nostr:nprofile1qqsfj5s9lrcckaxd8ul7vf3c4ajfg0n0ytcjvetclw679hy6p98wpfqpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy2hwumn8ghj7un9d3shjtnwdaehgu3wvfnj7qg4waehxw309ahx7um5wghx77r5wghxgetk9uykdgj7) nostr:naddr1qqdyzmnpwf3k75m0vfex2anfwejkucmfv9kxjumddap9yq3qn9fqt7833d6v60elucnr3tmyjslx7gh3yejh37a4utwf5z2wuzjqxpqqqzr0vsz5kcy
n/SociedadeAlternativaLibertaria - Libertários (por: nostr:nprofile1qqs2ph3za34henpq2y3rzgqwgdc4pjmpleqr5t62rf7kxj0lmdyxnfgppemhxue69uhkummn9ekx7mp0ydypw5) nostr:naddr1qq09xmmrd9jkgctyv4qkcar9wfhxzarfwes5c6tzv4e8gctjd9ssyg9qmc3wc6muess9zg33yq8yxu2sedslusp69a9p5ltrf8lakjrf55psgqqqsmmq8dtk3m
n/LibertariosPT - Libertários de Portugal (por: nostr:nprofile1qqszx8rlqax4pakclsxscudfset7fs37jm7rflnugh3nf8r4ehx4z4gppemhxue69uhkummn9ekx7mp05leack) nostr:naddr1qqx5c6tzv4e8gctjd9hhx5z5qgszx8rlqax4pakclsxscudfset7fs37jm7rflnugh3nf8r4ehx4z4grqsqqpphke05802
Discussões Sociais
n/Aliança-Conservadora-Brasileira (por: nostr:npub1atg5rgfuarup49470kqexfgcesdr85yru56y0y8qf3z6kc30g2vqyfyqyp ) nostr:naddr1qqsyzmrfv9hv8fmptapk7mnnv4e8vctydaexzh6zwfshx6tvv45hycgzyr4dzsdp8n50sx5khe7crye9rrxp5v7ss0jng3usupxyt2mz9apfsqcyqqqgdasue9j59
n/Ilha-de-Anhatomirin - Monarquia (Por: nostr:nprofile1qqsgzc22v804davx6vpwtwfu6j84yvupeld497tfr396usmu7s0m08qpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszymhwden5te0v9ehgunpdshxu6twdfsj7qguwaehxw309a5x7ervvfhkgtnrdaexzcmvv5h8gmm0d3ej7a2jp7u) nostr:naddr1qqf5jmrgvykkgefdg9hxsct5dakkjunfd5q3uamnwvaz7tmwdaehgu3dwp6kytnhv4kxcmmjv3jhytnwv46z7q3qs9s55cwl2m6cd5czukune4y02gecrn7m2tukj8zt4epheaqlk7wqxpqqqzr0vu2qg3m
n/ManosphereBrasil - Contra a misandria (Por: nostr:nprofile1qqs0p3yd48kzm56a4tual772y3vsjwehx6tc3rv8ht8q0zgncg5r7qgpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpjnhed) nostr:naddr1qqgy6ctwdaehq6r9wfj5yunpwd5kcqgawaehxw309ahx7um5wghxy6t5vdhkjmn9wgh8xmmrd9skctczyrcvfrdfaskaxhd2l80lhj3ytyynkdekj7ygmpa6ecrcjy7z9qlszqcyqqqgdasl3kaju
Memes
n/Shitposting (Por: nostr:nprofile1qqs9nyy7ctpy334n3p7gh4p93lmj2cch8ae8jgjsp8al2g32stdnpdcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpr9mhxue69uhhyetvv9ujumn0wd68ytnrdakjuct49us57cz4) nostr:naddr1qq94x6rfw3cx7um5d9hxwqgswaehxw309ahx7um5wghx6mmd9upzqkvsnmpvyjxxkwy8ez75yk8lwftrzulhy7fz2qylhafz92pdkv9hqvzqqqyx7chlz42w
n/Puro-caldo-do-Brasil. (por: nostr:nprofile1qqsztjv2pflmwcayr2jaq90astj94lu5l0smr0zhkfdct4ry7uxu7dqywzq8t) nostr:naddr1qq24qatjdukkxctvv3hj6er094p8yctnd9kzuqghwaehxw309aex2mrp0yh8qunfd4skctnwv46z7q3qyhyc5znlka36gx496q2lmqhyttlef7lpkx790vjmsh2xfacdeu6qxpqqqzr0vwh0r4w
Locais
n/NordesteLibertário - Nordeste (Por: nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpzpmhxue69uhkummnw3ezumt0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0s8pkkr ) nostr:naddr1qqf5ummjv3jhxar9f35kyetjwnp6zunfdupzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqyx7cnejrgl
n/BahiaLibertária - Bahia (por: nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpzpmhxue69uhkummnw3ezumt0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0s8pkkr ) nostr:naddr1qqgyyctgd9s5c6tzv4e8fsapwf5kzq3q5hhygatg5gmjyfkkguqn54f9r6k8m5m6ksyqffgjrf3uut982sqsxpqqqzr0vc4949j
n/LiberdadeMinas - Minas Gerais (Por: nostr:nprofile1qqsf0kszkmrmy9l3c7mxr3uhh3fmyjpq2z4hjvv7wdq84k5npd7gw3cpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszxthwden5te0wfjkccte9eekummjwsh8xmmrd9skctcprpmhxue69uhhyetvv9ujuurvv438xarj9e3k7mf0mx68nx) nostr:naddr1qq8yc6tzv4exgctyv4xkjmnpwvqsqq3qjldq9dk8kgtlr3akv8re00znkfyzq59t0yceuu6q0tdfxzmusarsxpqqqzr0vag4knt
n/CyberpunkManaus - Manaus (Por: nostr:nprofile1qqsz8v8zlrg0jclhasdksctsr2jw28lrqwn3zrsclnkpmytvmzhhdlqpz3mhxw309ucnqt3jx5cjuvpwxgarsvpcxqq3wamn8ghj7vfexghrzd3c9ccjuv3s8gurqwps9uq5gamn8ghj7entv43kjd3nvfcx5en6093h2up5w3ekgmn4xsekvatwx438xamywp6ksemcwp6xummzdgekzdmz0pmhzd3j0g6xzepwdahxjmmw9u2upp88) nostr:naddr1qqgyx7tzv4e8qatwdvk56ctwv96hxqgqqgsz8v8zlrg0jclhasdksctsr2jw28lrqwn3zrsclnkpmytvmzhhdlqrqsqqpphkgjh4rf
n/BelémLibertario (por: nostr:npub167s6q8sfzkhel4227kacu98zcg6e37v5sqwkv8mxaazrryz9huzqlhcu2t) nostr:nevent1qqsqnqgx3u2whdqdqmlstqcmgav6xfe4upz2qxfvj03tlk699dzlk7qzyrt6rgq7py26l874ft6mhrs5utprtx8ejjqp6eslvmh5gvvsgklsgqcyqqqqq2qqsdz6l
n/SãoPauloLivre - São Paulo (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qq898sardagxzatvdaxxjanjv5pzp6kfec55jce92gj4cjlg7ju8mzrea0ycfd3u86crk8vzayd334wrqvzqqqyx7cmls060
n/AcreLibertário - Acre (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qq85zcmjv4xxjcn9wf6v8gtjd9hsyg82e88zjjtry4fz2hztar6tslvg084unp9k8sltqwcast53kxx4cvpsgqqqsmmqftljpt
n/Alagoas (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqr5zmrpvahkzuczyr4vnn3ff93j2539t3973a9c0ky8n67fsjmrc04s8vwc96gmrr2uxqcyqqqgdas8qtaf4
Empreendedorismo:
n/Empreendedorismo/BR (por: nostr:npub14ysljm0gn6nnjv95yzeq6ffze4f3f9l0248kez4fhm4yz3fzardslwx5e8) nostr:naddr1qqd5y4zr9azk6urjv4jkuer9v3hhy6tnd4hj7snjv9ekjmqzyz5jr7tdaz02wwfsksstyrf9ytx4x9yhaa257my24xlw5s29yt5dkqcyqqqgdaslzrp3p
n/Empreendedorismo/SP (por: nostr:npub14ysljm0gn6nnjv95yzeq6ffze4f3f9l0248kez4fhm4yz3fzardslwx5e8) nostr:naddr1qqt5y4zr9azk6urjv4jkuer9v3hhy6tnd4hj756sqgs2jg0edh5fafeexz6zpvsdy53v65c5jlh42nmv325ma6jpg53w3kcrqsqqpphkcym25j
Análise
n/EBDV (Em Busca Da Verdade) - Análise geral e desenvolvimento pessoal (por: nostr:nprofile1qqs0xmu0skfdlmtl5tth6cv99za8f8kv7ulz5srkm8p6v5k03dx9lzspz4mhxue69uhkummnw3ezummcw3ezuer9wchszrnhwden5te0dehhxtnvdakz7qgswaehxw309ahx7um5wghx6mmd9usvrt9r) nostr:naddr1qqzy2sjy2cpzpum037ze9hld073dwltps55t5ay7enmnu2jqwmvu8fjje795chu2qvzqqqyx7cy9v5px
-
 @ 57d1a264:69f1fee1
2025-05-10 05:11:27
@ 57d1a264:69f1fee1
2025-05-10 05:11:27Consider the following two charts from A History of Clojure which detail the introduction and retention of new code by release for both Clojure and for Scala.
While this doesn't necessarily translate to library stability, it's reasonable to assume that the attitude of the Clojure maintainers will seep into the community. And that assumption is true.
Consider a typical Javascript program. What is it comprised of? Objects, objects, and more objects. Members of those objects must be either introspected or divined. Worse, it's normal to monkeypatch those objects, so the object members may (or may not) change over time.
Now, consider a typical Clojure program. What is it comprised of? Namespaces. Those namespaces contain functions and data. Functions may be dynamically generated (via macros), but it is extremely rare to "monkeypatch" a namespace. If you want to know what functions are available in a namespace, you can simply read the source file.
Continue reading https://potetm.com/devtalk/stability-by-design.html
originally posted at https://stacker.news/items/976215
-
 @ 40bdcc08:ad00fd2c
2025-05-06 14:24:22
@ 40bdcc08:ad00fd2c
2025-05-06 14:24:22Introduction
Bitcoin’s
OP_RETURNopcode, a mechanism for embedding small data in transactions, has ignited a significant debate within the Bitcoin community. Originally designed to support limited metadata while preserving Bitcoin’s role as a peer-to-peer electronic cash system,OP_RETURNis now at the center of proposals that could redefine Bitcoin’s identity. The immutable nature of Bitcoin’s timechain makes it an attractive platform for data storage, creating tension with those who prioritize its monetary function. This discussion, particularly around Bitcoin Core pull request #32406 (GitHub PR #32406), highlights a critical juncture for Bitcoin’s future.What is
OP_RETURN?Introduced in 2014,
OP_RETURNallows users to attach up to 80 bytes of data to a Bitcoin transaction. Unlike other transaction outputs,OP_RETURNoutputs are provably unspendable, meaning they don’t burden the Unspent Transaction Output (UTXO) set—a critical database for Bitcoin nodes. This feature was a compromise to provide a standardized, less harmful way to include metadata, addressing earlier practices that embedded data in ways that bloated the UTXO set. The 80-byte limit and restriction to oneOP_RETURNoutput per transaction are part of Bitcoin Core’s standardness rules, which guide transaction relay and mining but are not enforced by the network’s consensus rules (Bitcoin Stack Exchange).Standardness vs. Consensus Rules
Standardness rules are Bitcoin Core’s default policies for relaying and mining transactions. They differ from consensus rules, which define what transactions are valid across the entire network. For
OP_RETURN: - Consensus Rules: AllowOP_RETURNoutputs with data up to the maximum script size (approximately 10,000 bytes) and multiple outputs per transaction (Bitcoin Stack Exchange). - Standardness Rules: LimitOP_RETURNdata to 80 bytes and one output per transaction to discourage excessive data storage and maintain network efficiency.Node operators can adjust these policies using settings like
-datacarrier(enables/disablesOP_RETURNrelay) and-datacarriersize(sets the maximum data size, defaulting to 83 bytes to account for theOP_RETURNopcode and pushdata byte). These settings allow flexibility but reflect Bitcoin Core’s default stance on limiting data usage.The Proposal: Pull Request #32406
Bitcoin Core pull request #32406, proposed by developer instagibbs, seeks to relax these standardness restrictions (GitHub PR #32406). Key changes include: - Removing Default Size Limits: The default
-datacarriersizewould be uncapped, allowing largerOP_RETURNdata without a predefined limit. - Allowing Multiple Outputs: The restriction to oneOP_RETURNoutput per transaction would be lifted, with the total data size across all outputs subject to a configurable limit. - Deprecating Configuration Options: The-datacarrierand-datacarriersizesettings are marked as deprecated, signaling potential removal in future releases, which could limit node operators’ ability to enforce custom restrictions.This proposal does not alter consensus rules, meaning miners and nodes can already accept transactions with larger or multiple
OP_RETURNoutputs. Instead, it changes Bitcoin Core’s default relay policy to align with existing practices, such as miners accepting non-standard transactions via services like Marathon Digital’s Slipstream (CoinDesk).Node Operator Flexibility
Currently, node operators can customize
OP_RETURNhandling: - Default Settings: Relay transactions with oneOP_RETURNoutput up to 80 bytes. - Custom Settings: Operators can disableOP_RETURNrelay (-datacarrier=0) or adjust the size limit (e.g.,-datacarriersize=100). These options remain in #32406 but are deprecated, suggesting that future Bitcoin Core versions might not support such customization, potentially standardizing the uncapped policy.Arguments in Favor of Relaxing Limits
Supporters of pull request #32406 and similar proposals argue that the current restrictions are outdated and ineffective. Their key points include: - Ineffective Limits: Developers bypass the 80-byte limit using methods like Inscriptions, which store data in other transaction parts, often at higher cost and inefficiency (BitcoinDev Mailing List). Relaxing
OP_RETURNcould channel data into a more efficient format. - Preventing UTXO Bloat: By encouragingOP_RETURNuse, which doesn’t affect the UTXO set, the proposal could reduce reliance on harmful alternatives like unspendable Taproot outputs used by projects like Citrea’s Clementine bridge. - Supporting Innovation: Projects like Citrea require more data (e.g., 144 bytes) for security proofs, and relaxed limits could enable new Layer 2 solutions (CryptoSlate). - Code Simplification: Developers like Peter Todd argue that these limits complicate Bitcoin Core’s codebase unnecessarily (CoinGeek). - Aligning with Practice: Miners already process non-standard transactions, and uncapping defaults could improve fee estimation and reduce reliance on out-of-band services, as noted by ismaelsadeeq in the pull request discussion.In the GitHub discussion, developers like Sjors and TheCharlatan expressed support (Concept ACK), citing these efficiency and innovation benefits.
Arguments Against Relaxing Limits
Opponents, including prominent developers and community members, raise significant concerns about the implications of these changes: - Deviation from Bitcoin’s Purpose: Critics like Luke Dashjr, who called the proposal “utter insanity,” argue that Bitcoin’s base layer should prioritize peer-to-peer cash, not data storage (CoinDesk). Jason Hughes warned it could turn Bitcoin into a “worthless altcoin” (BeInCrypto). - Blockchain Bloat: Additional data increases the storage and processing burden on full nodes, potentially making node operation cost-prohibitive and threatening decentralization (CryptoSlate). - Network Congestion: Unrestricted data could lead to “spam” transactions, raising fees and hindering Bitcoin’s use for financial transactions. - Risk of Illicit Content: The timechain’s immutability means data, including potentially illegal or objectionable content, is permanently stored on every node. The 80-byte limit acts as a practical barrier, and relaxing it could exacerbate this issue. - Preserving Consensus: Developers like John Carvalho view the limits as a hard-won community agreement, not to be changed lightly.
In the pull request discussion, nsvrn and moth-oss expressed concerns about spam and centralization, advocating for gradual changes. Concept NACKs from developers like wizkid057 and Luke Dashjr reflect strong opposition.
Community Feedback
The GitHub discussion for pull request #32406 shows a divided community: - Support (Concept ACK): Sjors, polespinasa, ismaelsadeeq, miketwenty1, TheCharlatan, Psifour. - Opposition (Concept NACK): wizkid057, BitcoinMechanic, Retropex, nsvrn, moth-oss, Luke Dashjr. - Other: Peter Todd provided a stale ACK, indicating partial or outdated support.
Additional discussions on the BitcoinDev mailing list and related pull requests (e.g., #32359 by Peter Todd) highlight similar arguments, with #32359 proposing a more aggressive removal of all
OP_RETURNlimits and configuration options (GitHub PR #32359).| Feedback Type | Developers | Key Points | |---------------|------------|------------| | Concept ACK | Sjors, ismaelsadeeq, others | Improves efficiency, supports innovation, aligns with mining practices. | | Concept NACK | Luke Dashjr, wizkid057, others | Risks bloat, spam, centralization, and deviation from Bitcoin’s purpose. | | Stale ACK | Peter Todd | Acknowledges proposal but with reservations or outdated support. |
Workarounds and Their Implications
The existence of workarounds, such as Inscriptions, which exploit SegWit discounts to embed data, is a key argument for relaxing
OP_RETURNlimits. These methods are costlier and less efficient, often costing more thanOP_RETURNfor data under 143 bytes (BitcoinDev Mailing List). Supporters argue that formalizing largerOP_RETURNdata could streamline these use cases. Critics, however, see workarounds as a reason to strengthen, not weaken, restrictions, emphasizing the need to address underlying incentives rather than accommodating bypasses.Ecosystem Pressures
External factors influence the debate: - Miners: Services like Marathon Digital’s Slipstream process non-standard transactions for a fee, showing that market incentives already bypass standardness rules. - Layer 2 Projects: Citrea’s Clementine bridge, requiring more data for security proofs, exemplifies the demand for relaxed limits to support innovative applications. - Community Dynamics: The debate echoes past controversies, like the Ordinals debate, where data storage via inscriptions raised similar concerns about Bitcoin’s purpose (CoinDesk).
Bitcoin’s Identity at Stake
The
OP_RETURNdebate is not merely technical but philosophical, questioning whether Bitcoin should remain a focused monetary system or evolve into a broader data platform. Supporters see relaxed limits as a pragmatic step toward efficiency and innovation, while opponents view them as a risk to Bitcoin’s decentralization, accessibility, and core mission. The community’s decision will have lasting implications, affecting node operators, miners, developers, and users.Conclusion
As Bitcoin navigates this crossroads, the community must balance the potential benefits of relaxed
OP_RETURNlimits—such as improved efficiency and support for new applications—against the risks of blockchain bloat, network congestion, and deviation from its monetary roots. The ongoing discussion, accessible via pull request #32406 on GitHub (GitHub PR #32406). Readers are encouraged to explore the debate and contribute to ensuring that any changes align with Bitcoin’s long-term goals as a decentralized, secure, and reliable system. -
 @ d360efec:14907b5f
2025-05-10 03:57:17
@ d360efec:14907b5f
2025-05-10 03:57:17Disclaimer: * การวิเคราะห์นี้เป็นเพียงแนวทาง ไม่ใช่คำแนะนำในการซื้อขาย * การลงทุนมีความเสี่ยง ผู้ลงทุนควรตัดสินใจด้วยตนเอง
-
 @ d61f3bc5:0da6ef4a
2025-05-06 01:37:28
@ d61f3bc5:0da6ef4a
2025-05-06 01:37:28I remember the first gathering of Nostr devs two years ago in Costa Rica. We were all psyched because Nostr appeared to solve the problem of self-sovereign online identity and decentralized publishing. The protocol seemed well-suited for textual content, but it wasn't really designed to handle binary files, like images or video.
The Problem
When I publish a note that contains an image link, the note itself is resilient thanks to Nostr, but if the hosting service disappears or takes my image down, my note will be broken forever. We need a way to publish binary data without relying on a single hosting provider.
We were discussing how there really was no reliable solution to this problem even outside of Nostr. Peer-to-peer attempts like IPFS simply didn't work; they were hopelessly slow and unreliable in practice. Torrents worked for popular files like movies, but couldn't be relied on for general file hosting.
Awesome Blossom
A year later, I attended the Sovereign Engineering demo day in Madeira, organized by Pablo and Gigi. Many projects were presented over a three hour demo session that day, but one really stood out for me.
Introduced by hzrd149 and Stu Bowman, Blossom blew my mind because it showed how we can solve complex problems easily by simply relying on the fact that Nostr exists. Having an open user directory, with the corresponding social graph and web of trust is an incredible building block.
Since we can easily look up any user on Nostr and read their profile metadata, we can just get them to simply tell us where their files are stored. This, combined with hash-based addressing (borrowed from IPFS), is all we need to solve our problem.
How Blossom Works
The Blossom protocol (Blobs Stored Simply on Mediaservers) is formally defined in a series of BUDs (Blossom Upgrade Documents). Yes, Blossom is the most well-branded protocol in the history of protocols. Feel free to refer to the spec for details, but I will provide a high level explanation here.
The main idea behind Blossom can be summarized in three points:
- Users specify which media server(s) they use via their public Blossom settings published on Nostr;
- All files are uniquely addressable via hashes;
- If an app fails to load a file from the original URL, it simply goes to get it from the server(s) specified in the user's Blossom settings.
Just like Nostr itself, the Blossom protocol is dead-simple and it works!
Let's use this image as an example:
 If you look at the URL for this image, you will notice that it looks like this:
If you look at the URL for this image, you will notice that it looks like this:blossom.primal.net/c1aa63f983a44185d039092912bfb7f33adcf63ed3cae371ebe6905da5f688d0.jpgAll Blossom URLs follow this format:
[server]/[file-hash].[extension]The file hash is important because it uniquely identifies the file in question. Apps can use it to verify that the file they received is exactly the file they requested. It also gives us the ability to reliably get the same file from a different server.
Nostr users declare which media server(s) they use by publishing their Blossom settings. If I store my files on Server A, and they get removed, I can simply upload them to Server B, update my public Blossom settings, and all Blossom-capable apps will be able to find them at the new location. All my existing notes will continue to display media content without any issues.
Blossom Mirroring
Let's face it, re-uploading files to another server after they got removed from the original server is not the best user experience. Most people wouldn't have the backups of all the files, and/or the desire to do this work.
This is where Blossom's mirroring feature comes handy. In addition to the primary media server, a Blossom user can set one one or more mirror servers. Under this setup, every time a file is uploaded to the primary server the Nostr app issues a mirror request to the primary server, directing it to copy the file to all the specified mirrors. This way there is always a copy of all content on multiple servers and in case the primary becomes unavailable, Blossom-capable apps will automatically start loading from the mirror.
Mirrors are really easy to setup (you can do it in two clicks in Primal) and this arrangement ensures robust media handling without any central points of failure. Note that you can use professional media hosting services side by side with self-hosted backup servers that anyone can run at home.
Using Blossom Within Primal
Blossom is natively integrated into the entire Primal stack and enabled by default. If you are using Primal 2.2 or later, you don't need to do anything to enable Blossom, all your media uploads are blossoming already.
To enhance user privacy, all Primal apps use the "/media" endpoint per BUD-05, which strips all metadata from uploaded files before they are saved and optionally mirrored to other Blossom servers, per user settings. You can use any Blossom server as your primary media server in Primal, as well as setup any number of mirrors:
 ## Conclusion
## ConclusionFor such a simple protocol, Blossom gives us three major benefits:
- Verifiable authenticity. All Nostr notes are always signed by the note author. With Blossom, the signed note includes a unique hash for each referenced media file, making it impossible to falsify.
- File hosting redundancy. Having multiple live copies of referenced media files (via Blossom mirroring) greatly increases the resiliency of media content published on Nostr.
- Censorship resistance. Blossom enables us to seamlessly switch media hosting providers in case of censorship.
Thanks for reading; and enjoy! 🌸
-
 @ 57d1a264:69f1fee1
2025-05-08 05:25:48
@ 57d1a264:69f1fee1
2025-05-08 05:25:48Safe Bits & Self Custody Tips
The journey of onboarding a user and create a bitcoin multiSig setup begins far before opening a desktop like Bitcoin Safe (BS) or any other similar application. Bitcoin Safe seems designed for families and people that want to start exploring and learning about multiSig setup. The need for such application and use of it could go much further, defining best practices for private organizations that aim to custody bitcoin in a private and anonymous way, following and enjoy the values and standards bitcoin has been built for.
Intro
Organizations and small private groups like families, family offices and solopreneurs operating on a bitcoin standard will have the need to keep track of transactions and categorize them to keep the books in order. A part of our efforts will be spent ensuring accessibility standards are in place for everyone to use Bitcoin Safe with comfort and safety.
We aim with this project to bring together the three Designathon ideas below: - Bitcoin Safe: improve its overall design and usability. - No User Left Behind: improve Bitcoin Safe accessibility. - Self-custody guidelines for organizations: How Bitcoin Safe can be used by private organization following best self-custody practices.
We are already halfway of the first week, and here below the progress made so far.
Designing an icon Set for Bitcoin Safe
One of the noticeable things when using BS is the inconsistency of the icons, not just in colors and shapes, but also the way are used. The desktop app try to have a clean design that incorporate with all OS (Win, macOS, Linux) and for this reason it's hard to define when a system default icon need to be used or if a custom one can be applied instead. The use of QT Ui framework for python apps help to respond to these questions. It also incorporates and brig up dome default settings that aren't easily overwritten.
Here below you can see the current version of BS:
Defining a more strict color palette for Bitcoin Safe was the first thing!
How much the icons affect accessibility? How they can help users to reach the right functionality? I took the challenge and, with PenPot.app, redesigned the icons based on the grid defined in the https://bitcoinicons.com/ and proposing the implementation of it to have a cleaner and more consistent look'n feel, at least for the icons now.
What's next
I personally look forward to seeing these icons implemented soon in Bitcoin Safe interface. In the meantime, we'll focus on delivering an accessibility audit and evaluate options to see how BS could be used by private organizations aiming to become financially sovereign with self-custody or more complex bitcoin multiSig setups.
One of the greatest innovations BS is bringing to us is the ability to sync the multiSig wallets, including PBST, Categories and labels, through the nostr decentralized protocol, making current key custodial services somehow obsolete. Second-coolest feature that this nostr implementation brings is the ability to have a build-in private chat that connect and enable the various signers of a multiSig to communicate and sign transactions remotely. Where have you seen something like this before?
Categories UX and redesign is also considered in this project. We'll try to understand how to better serve this functionality to you, the user, really soon.
Stay tuned!
originally posted at https://stacker.news/items/974488
-
 @ 57d1a264:69f1fee1
2025-05-08 05:08:36
@ 57d1a264:69f1fee1
2025-05-08 05:08:36Welcome back to our weekly
JABBB, Just Another Bitcoin Bubble Boom, a comics and meme contest crafted for you, creative stackers!If you'd like to learn more, check our welcome post here.
This week sticker:
Bitcoin SirYou can download the source file directly from the HereComesBitcoin website in SVG and PNG. Use this sticker around SN with the code
The task
Make sure you use this week sticker to design a comic frame or a meme, add a message that perfectly captures the sentiment of the current most hilarious takes on the Bitcoin space. You can contextualize it or not, it's up to you, you chose the message, the context and anything else that will help you submit your comic art masterpiece.
Are you a meme creator? There's space for you too: select the most similar shot from the gifts hosted on the Gif Station section and craft your best meme... Let's Jabbb!
If you enjoy designing and memeing, feel free to check out the JABBB archive and create more to spread Bitcoin awareness to the moon.
Submit each proposal on the relative thread, bounties will be distributed when enough participants submit options.
PS: you can now use HereComesBitcoin stickers to use on Stacker.News
₿e creative, have fun! :D
originally posted at https://stacker.news/items/974483
-
 @ a296b972:e5a7a2e8
2025-05-05 22:45:01
@ a296b972:e5a7a2e8
2025-05-05 22:45:01Zur Gründung der Bundesrepublik Deutschland wurde infolge der Auswirkungen des 2. Weltkriegs auf einem Teil des ehemaligen Deutschen Reiches (nicht des 3. Reiches!) auf Initiative der westlichen Alliierten, federführend die USA als stärkste Kraft, eine demokratische Grundordnung erarbeitet, die wir als das Grundgesetz für die Bundesrepublik Deutschland kennen und schätzen gelernt haben. Da man zum damaligen Zeitpunkt, im Gegensatz zu heute, noch sehr genau mit der Sprache war, hat das Wort „für“ größere Bedeutung, als ihm heute zugesprochen wird. Hätte der unter westlich-alliierter Besatzung stehende Rumpf des Deutschen Reiches eigenständig eine Verfassung erstellen können, wäre es nicht Grundgesetz (das laut Definition einen provisorischen Charakter hat) genannt worden, sondern eben Verfassung. Und hätte diese Verfassung eigenständig erarbeitet werden können, hätte sie geheißen: Verfassung der Bundesrepublik Deutschland.
Es heißt zum Beispiel auch: Costituzione della Repubblica Italiana. also Konstitution der Republik Italien, und nicht Costituzione per La Repubblica Italiana.
Es ist nachvollziehbar, dass die Bedenken der westlichen Alliierten aufgrund der Nazi-Zeit so groß waren, dass man den „Deutschen“ nicht zutraute, selbständig eine Verfassung zu erstellen.
Zum vorbeugenden Schutz, es sollte verunmöglicht werden, dass ein Regime noch einmal in der Lage sei, die Macht zu ergreifen, wurde als Kontrollinstanz der Verfassungsschutz gegründet. Dieser ist dem Innenministerium gegenüber weisungsgebunden. Die jüngste Aussage, auf den letzten Metern der Innenministerin Faeser, der Verfassungsschutz sei selbständig, ist eine manipulative Beschreibung, die davon ablenken soll, dass das Innenministerium dem Verfassungsschutz sehr wohl übergeordnet ist. Das Wort „selbständig“ soll Eigenständigkeit vorgaukeln, hat aber in der Hierarchie keinerlei Bedeutung.
Im Jahre 1949 herrschte ein anderer Zeitgeist. Werte wie Ehrlichkeit, Redlichkeit und Anständigkeit hatten noch eine andere Bedeutung als heute. Politiker waren noch von einem anderen Schlag und hatten weitgehend den Anspruch zum Wohle des Volkes zu entscheiden und zu handeln. Diese Werte reichten noch mindestens bis in das Agieren des Bundeskanzlers Helmut Schmidt hinein.
Niemand konnte sich deshalb zum damaligen Zeitpunkt vorstellen, dass dieser eigentlich als Kontrollinstanz gedachte Verfassungsschutz einmal von der Politik missbraucht werden könnte, um oppositionelle Kräfte auszuschalten zu versuchen, wie es mit der Einstufung der AfD als gesichert rechtsextrem geschehen ist. Rechtlich hat das noch keine Konsequenzen, aber es geht in erster Linie darum, dem Image der AfD zu schaden, um weiteren Zulauf zu verhindern. Diese Art von Durchtriebenheit kam in den Gedanken und dem Ehrgefühl der damals verantwortlichen Politiker noch nicht vor.
Die ehemaligen Volksparteien, man kann auch sagen, die Alt-Parteien, sehen ihre Felle schon seit einiger Zeit davonschwimmen. Die Opposition hat derzeit die Zustimmung einer ehemaligen Volkspartei überholt und ist sogar stärkste Kraft geworden. Sie repräsentiert aktuell rund 10 Millionen der Wähler. Tendenz steigend. Und das die folglich auch gesichert rechtsextrem gewählt haben, oder gar gesichert rechtsextrem sind, wird ihnen vielleicht nicht besonders schmeicheln.
Parallel dazu haben die Alt-Parteien die Medienlandschaft gekapert und versuchen mit Einschränkungen der Meinungsfreiheit, sofern sich Kritik gegen sie richtet und durch selbstermächtigte Entscheidung über das, was Wahrheit und Lüge ist, unliebsame Stimmen mundtot zu machen, um unter allen Umständen an der Macht zu bleiben.
Diese Vorgehensweise widerspricht dem demokratischen Verständnis, das aus dem, wenn auch „nur“ Grundgesetz, statt Verfassung, hervorgeht und die Nachkriegsgenerationen im besten Sinne beeinflusst und demokratisch geprägt hat.
Aus dieser Sicht können die Aktivitäten der Alt-Parteien nur als Angriff auf die Demokratie, wie sie diese Generationen verstehen, gesehen werden.
Daher führt jeder Angriff der Alt-Parteien auf die Demokratie dazu, dass die Opposition immer mehr an Stimmen gewinnt und wohl weiterhin gewinnen wird.
Es erschließt sich nicht, warum die Alt-Parteien nicht auf die denkbar einfachste Lösung kommen, Vertrauen in ihre Politik zurückzugewinnen, in dem sie eine Politik machen würden, die dem Willen der Bürger entspricht. Mit dem Gegenteil machen sich die Volksvertreter zu Vertretern ohne den Rückhalt vom Volk, und man muss sich fragen, wessen Interessen sie derzeit wirklich vertreten. Bestenfalls die eigenen, schlimmstenfalls die des global agierenden Tiefen Staates, der ihnen ins Ohr flüstert, was sie zu tun haben.
Mit jeder vernunftbegabten Entscheidung, die dem Willen des Souveräns entspräche, würden sie die Opposition zunehmend schwächen. Da dies nicht geschieht, kann man nur zu der Schlussfolgerung kommen, dass sich hier auch selbstzerstörerische, suizidale Kräfte festgesetzt haben. Es ist wie eine Sucht, von der man nicht mehr loslassen kann.
Solange die Alt-Parteien nicht in der Lage sind, die Unzufriedenheit in der Bevölkerung wahr- und ernst zu nehmen, werden sie die Opposition stärken und zu immer rigideren Maßnahmen greifen müssen, um ihre Macht zu erhalten und sich damit immer mehr von demokratischen Verhältnissen entfernen, und zwar genau in die Richtung vor der die Alt-Parteien in ihrer ideologischen Verirrung warnen.
Seitens der Opposition gibt es in der Gesamtschau keine Anzeichen dafür, dass die Demokratie abgeschafft werden soll, im Gegenteil, es wird für mehr Bürgerbeteiligung plädiert, was ein sicheres Merkmal für demokratische Absichten ist.
Aus Sicht der Alt-Parteien macht die Brandmauer Sinn, weil sie sie vor ihrem eigenen Machtverlust schützt. Der Fall der Berliner Mauer sollte ihnen eigentlich eine Warnung sein.
Fairerweise darf nicht unterschlagen werden, dass es in der Opposition einige Verirrte gibt, wobei noch interessant wäre zu erfahren, welche davon als V-Männer des Verfassungsschutzes eingeschleust wurden. Diese jedoch zum Anlass zu nehmen, die Opposition unter Generalverdacht zu stellen, steht einem demokratischen Handeln diametral entgegen.
Das Grundgesetz wird so nicht geschützt, sondern bis kurz vor der Sollbruchstelle verbogen.
Die Einstufung der Opposition als gesichert rechts-extrem beruht auf einem mutmaßlich 1000 Seiten starken Papier, das offensichtlich nur ein erlesener Kreis zu sehen bekommen soll. Dazu gehört nicht die Bevölkerung, die sicher nur einmal mehr nicht zu Teilen verunsichert werden soll. Und selbstverständlich schon gar nicht diejenigen, die es betrifft, nämlich die Opposition.
Eine eindeutige Fragwürdigkeit der Aktivitäten des Verfassungsschutzes wäre schwerer festzustellen, wenn es gleichwohl Parteien gäbe, die als gesichert links-extrem oder zumindest als links-extremer Verdachtsfall eingestuft würden. Nicht ganz unberechtigte Gründe hierfür könnten schon gefunden werden, wenn der politische Wille es wollte.
Auch die seltsam-umstrittene Installierung des Präsidenten des Bundesamtes für Verfassungsschutz (genau genommen für Grundgesetzschutz) lässt Fragen offen.
Generell müsste es eine unabhängige Überprüfung geben, ob die Gewaltenteilung in Deutschland noch gewährleistet ist, da es durch das augenscheinliche Zusammenspiel in der Richterschaft, der Gesetzgebung und der vierten Gewalt, den Medien, Anlass zu Zweifel gibt.
Diese Zweifel sind nicht demokratiegefährdend, sondern im Gegenteil, es ist demokratische Pflicht, den Verantwortlichen kritisch auf die Finger zu schauen, ob im Sinne des Souveräns entschieden und gehandelt wird. Zweifel könnte man dadurch ausräumen, in dem eindeutig bewiesen würde, das alles seine Richtigkeit hat.
Das wäre vornehmlich die Aufgabe der Alt-Medien, die derzeit durch Totalversagen glänzen, weil alles mit allem zusammenhängt, jeder jeden kennt und man es sich über Jahre so eingerichtet hat, dass man gerne unter sich bleibt und Pöstchen-Hüpfen von einem Lager ins andere spielt.
Vielleicht ist es sogar nötig, dass zur unabhängigen Überprüfung, die Alliierten, inklusive Russland, noch einmal, nach rund 80 Jahren, auf den Plan gerufen werden müssen, um sozusagen eine Zwischenbilanz zu ziehen, inwieweit sich das einst etablierte, demokratische System bewährt hat, und ob es derzeit noch im ursprünglichen Sinne umgesetzt und gelebt wird. Es ist anzunehmen, dass hier ein gewaltiges Optimierungspotenzial zum Vorschein kommen könnte.
Viele Bürger in Deutschland haben den Wunsch, wieder in einer Demokratie zu leben, die ihre Namen auch verdient hat. Sie wollen wieder frei ihre Meinung jeglicher Art aussprechen können, miteinander diskutieren, auch einmal Unsinn reden, ohne, dass sie der Blockwart gleich bei einem Denunzierungsportal anschwärzt, oder sie Gefahr laufen, dass ihr Konto gekündigt wird, oder sie morgens um 6 Uhr Besuch bekommen, der noch nicht einmal frische Semmeln mitbringt.
Dieser Artikel wurde mit dem Pareto-Client geschrieben
* *
(Bild von pixabay)
-
 @ 502ab02a:a2860397
2025-05-12 03:11:06
@ 502ab02a:a2860397
2025-05-12 03:11:06สัปดาห์ที่ผ่านมา เราพักผ่อนย้อนไปเพื่อทำความเข้าใจต้นเหตุของซีรีส์นี้กันแล้วนะครับ ทีนี้เราจะมาสนทนากันต่อจากที่ค้างคาไว้กันครับ
ย้อนกลับไปเมื่อราวทศวรรษ 1970-1980 เป็นยุคที่โลกยังเชื่อว่า “ไขมัน” คือผู้ร้ายตัวจริงในวงการสุขภาพ ปิรามิดอาหารจาก USDA จึงถือกำเนิดขึ้น โดยมีฐานล่างกว้างใหญ่เต็มไปด้วยข้าว แป้ง ซีเรียล พาสต้า และขนมปัง เรียกรวมว่า “กลุ่มคาร์โบไฮเดรต” และถูกวางให้เป็นเสาหลักของอาหารประจำวัน ภายใต้แนวคิดว่าให้พลังงานสูง ไขมันต่ำ ดีต่อหัวใจ และเหมาะกับการเลี้ยงประชากรโลกที่เพิ่มขึ้นอย่างรวดเร็ว
แต่ความจริงที่เปิดเผยภายหลังคือ ปิรามิดอาหารนี้มิได้เกิดจากวิทยาศาสตร์บริสุทธิ์ หากแต่เกิดจากกระบวนการ “เปิดประมูลนโยบาย” โดยกลุ่มอุตสาหกรรมเกษตรรายใหญ่ ซึ่งต้องการระบายผลผลิตคาร์โบไฮเดรตจำนวนมหาศาลจากข้าวโพด ข้าวสาลี และถั่วเหลืองที่รัฐบาลอเมริกันอุดหนุนให้เพาะปลูกเกินความจำเป็น (ดูรายงาน PBS: The Food Pyramid) หน้าที่จัดสรรนี้จึงอยู่ภายใต้ USDA หรือ กระทรวงเกษตรสหรัฐอเมริกา
ขณะที่ผู้คนถูกสอนให้หลีกเลี่ยงไขมัน โปรตีนสัตว์ และหันมากินซีเรียลเป็นอาหารเช้า ผลิตภัณฑ์ไขมันต่ำแทบทุกชนิดกลับต้องเติมน้ำตาลและแป้งเพื่อให้มีรสชาติ นำไปสู่การระบาดของโรคอ้วน เบาหวาน ความดัน และ NCD ทั่วโลก ที่เราเพิ่งจะเข้าใจกันวันนี้ว่ามีรากมาจาก “ปิรามิดคาร์บ” นั่นเอง
คำถามคือ ทำไมการกำหนดอาหารของอเมริกา (ซึ่งแน่นอนว่าแพร่กระจายไปทั่วโลกภายใต้ข้อกำหนดเดียวกัน) จึงเกิดขึ้นจาก "กระทรวงเกษตรสหรัฐอเมริกา" ไม่ใช่ หน่วยงานทางวิทยาศาสตร์ หรือ การแพทย์
หรือเพราะ “อาหาร” ในอเมริกา ไม่ได้เริ่มจากคำว่า “สุขภาพ” แต่เริ่มจาก “เศรษฐกิจ”
ย้อนกลับไปช่วงต้นศตวรรษที่ 20 โดยเฉพาะหลังสงครามโลกครั้งที่สอง สหรัฐฯ ต้องการฟื้นฟูเศรษฐกิจและผลักดันภาคการเกษตรให้โตอย่างรวดเร็ว โดยเฉพาะสินค้าพืชเชิงอุตสาหกรรม เช่น ข้าวโพด ข้าวสาลี ถั่วเหลือง นม และเนื้อจากฟาร์มอุตสาหกรรม และปากท้องของเกษตรกรคือฐานเสียงสำคัญในทุกๆรัฐบาล ดังนั้น USDA ซึ่งเป็นหน่วยงานที่ตั้งขึ้นเพื่อดูแลเกษตรกร จึงรับบทผู้ออก “แนวทางโภชนาการ” โดยเน้นว่า
อาหารอะไรที่ เกษตรกรผลิตได้เยอะ ก็เอามาดันให้ประชาชนกินเยอะ อาหารอะไรที่ ราคาถูก ผลิตได้เร็ว ก็นำมาใส่ไว้ฐานล่างของพีระมิด ให้ประชาชนกินเยอะ อาหารอะไรที่ มีอุตสาหกรรมอยู่เบื้องหลัง ก็เปิดประมูลให้มีบทบาทมากในการล็อบบี้นโยบาย ให้ประชาชนกินเยอะ
พูดง่ายๆ ก็คือ นโยบายอาหารอเมริกา ไม่ได้ออกโดยนักวิทยาศาสตร์หรือนักโภชนาการที่ไม่มีผลประโยชน์ทับซ้อน แต่มาจาก “ข้าราชการสายเกษตร+กลุ่มทุน” ที่ต้องการให้ภาคการเกษตรมีกำไรอย่างต่อเนื่อง และอย่าลืมว่า อเมริกา = โลก
แล้วหน่วยงานด้านวิทยาศาสตร์หรือแพทย์ เช่น NIH (National Institutes of Health) หรือ CDC (Centers for Disease Control and Prevention) หล่ะ แน่นอนครับว่ามีข้อมูลอยุ่ว่าก็มีสิทธิ์เสนอแนะอยู่บ้างแต่ทั้งหมดนี้ ไม่มีอำนาจออกนโยบายหลักที่ใช้จริงกับประชาชน ส่วนใหญ่แค่ให้ข้อมูลวิชาการ ซึ่งมักจะถูกลดทอนหรือละเลยเมื่อนโยบายจริงถูกเขียนขึ้นโดย USDA ในที่สุด
เมื่อเสียงของการตั้งคำถามเริ่มดังกว่าเสียงโฆษณา ขบวนการ “Low Carb” ก็เริ่มตั้งหลักและขยายวงกว้างอย่างเงียบๆ งานวิจัยใหม่ๆ เริ่มบ่งชี้ว่า “น้ำตาลและแป้ง” โดยเฉพาะแป้งแปรรูป คือภัยเงียบที่ส่งผลต่อการอักเสบเรื้อรัง ภาวะดื้ออินซูลิน และเมตาบอลิกซินโดรม จนกระทั่งช่วงต้นทศวรรษ 2010 เป็นต้นมา อาหารแนว “ลดคาร์บ เพิ่มไขมันดี เพิ่มโปรตีน” ก็กลายเป็นกระแสหลักขึ้นมา
ตอนนั้นหลายคนคิดว่า “พวกเราชนะแล้ว” โลกกลับมาฟังเสียงสุขภาพที่แท้จริง โปรตีนกลายเป็นคำตอบใหม่แห่งยุค
แต่มึงเอ๊ยยยยยย... เกมอาจไม่ได้จบตรงนั้น
เพราะในวันที่ประชาชนเริ่มหลีกหนีคาร์บ กลุ่มทุนอาหารข้ามชาติที่เคยวางรากอยู่ในอุตสาหกรรมแป้ง ได้ค่อยๆ แปรทิศ ย้ายการลงทุนไปสู่ “โปรตีนทางเลือก” รอไว้นานแล้วโดยที่เราไม่รู้ตัว ทั้งอาหารพืชแปรรูปอย่าง texture ถั่วเหลือง (TVP), โปรตีนจุลินทรีย์, เนื้อปลูกจากห้องแลบ ไปจนถึง “ไข่” และ “นม” ที่ไม่ได้มาจากสัตว์ โปรตีนสังเคราะห์ที่ผลิตโดยระบบชีวภาพวิศวกรรม (synthetic biology) ซึ่งได้รับเงินทุนจากบริษัทยักษ์ใหญ่อย่างต่อเนื่องตลอดสิบปีที่ผ่านมา
พอถึงวันโปรตีนกลายเป็นเทรนด์ เขาก็เข้ามาเป็นเจ้าของเทรนด์เป็นที่เรียบร้อยแล้ว พร้อมทุกอย่างแล้ว คำถามคือ ใครกันแน่ที่เป็น Trend Setter
โปรตีนจึงไม่ใช่เพียง “สารอาหาร” อีกต่อไป แต่มันคือ “สินค้าอนาคต” ที่สามารถควบคุมแหล่งผลิต แหล่งพันธุ์ เทคโนโลยีการแปรรูป และการกระจายผ่านแพลตฟอร์มค้าปลีกทั่วโลก และถ้าคุณสังเกต จะเห็นว่าไม่มีใครพูดถึง “คาร์บทางเลือก” หรือ "คาร์บเข้มข้น" หรือ "คาร์บที่ไม่ต้องใช้พืช" แม้แต่นิด ทั้งที่ในทางหลักการก็สามารถคิดค้นได้ไม่ต่างกัน แปลว่า พวกเขาไม่ได้แค่อยาก “เลิกขายคาร์บ” แต่กำลัง “เปลี่ยนสินค้าหลักใหม่” ให้ไปอยู่ในกลุ่มที่พวกเขาควบคุมได้ทั้งหมด แค่เอาคำว่า "โปรตีน" ขึ้นมาเป็นฉากหน้าไว้ก่อน
เริ่มเห็นภาพไหมครับ จากคาร์บที่เคยถูกบิดเบือน กลายมาเป็นโปรตีนที่ถูกเสนอให้เรายินดีรับอย่างไม่ตั้งคำถาม
“โปรตีนอนาคต” ดูเหมือนจะเป็นทางเลือก แต่จริงๆ แล้วอาจเป็นกับดักหรือเปล่า
วันนี้ที่หลายคนเฝ้ามองชัยชนะของผู้คนในการล้ม “ปิรามิดคาร์บ” แต่ไม่ทันเห็นว่ากำลังถูกลากเข้าสู่ “หอคอยโปรตีนจำลอง” ที่พวกเขาสร้างขึ้นใหม่ ด้วยบรรจุภัณฑ์สวยหรู คำว่า "รักษ์โลก" "ปลอดภัย" และ "ยั่งยืน" แต่แท้จริงคือห่วงโซ่ที่มัดให้เราเป็นเพียง “ผู้บริโภค” ที่ไม่มีทางรู้ว่าอาหารของเรามาจากธรรมชาติหรือห้องแลบอีกต่อไป เรากลายเป็นหนูที่ย้ายจากกล่องวงกตหนึ่ง มายังอีกกล่องวงกตหนึ่งหรือเปล่า เป็นคำถามที่ยังต้องตอบต่อไป
เฮียไม่ได้มาเพื่อหวาดระแวงนะครับ เพราะในเกมอำนาจอาหาร ไม่มีใครยอมเสียพื้นที่ พวกเขาแค่เปลี่ยนกลยุทธ์ เพื่อครองความเชื่อมั่นใหม่ ในชื่อ “โปรตีน” #pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 6e64b83c:94102ee8
2025-05-05 16:50:13
@ 6e64b83c:94102ee8
2025-05-05 16:50:13Nostr-static is a powerful static site generator that transforms long-form Nostr content into beautiful, standalone websites. It makes your content accessible to everyone, even those not using Nostr clients. For more information check out my previous blog post How to Create a Blog Out of Nostr Long-Form Articles
What's New in Version 0.7?
RSS and Atom Feeds
Version 0.7 brings comprehensive feed support with both RSS and Atom formats. The system automatically generates feeds for your main content, individual profiles, and tag-specific pages. These feeds are seamlessly integrated into your site's header, making them easily discoverable by feed readers and content aggregators.
This feature bridges the gap between Nostr and traditional web publishing, allowing your content to reach readers who prefer feed readers or automated content distribution systems.
Smart Content Discovery
The new tag discovery system enhances your readers' experience by automatically finding and recommending relevant articles from the Nostr network. It works by:
- Analyzing the tags in your articles
- Fetching popular articles from Nostr that share these tags
- Using configurable weights to rank these articles based on:
- Engagement metrics (reactions, reposts, replies)
- Zap statistics (amount, unique zappers, average zap size)
- Content quality signals (report penalties)
This creates a dynamic "Recommended Articles" section that helps readers discover more content they might be interested in, all while staying within the Nostr ecosystem.
See the new features yourself by visiting our demo at: https://blog.nostrize.me
-
 @ 57d1a264:69f1fee1
2025-05-07 06:56:25
@ 57d1a264:69f1fee1
2025-05-07 06:56:25Wild parrots tend to fly in flocks, but when kept as single pets, they may become lonely and bored https://www.youtube.com/watch?v=OHcAOlamgDc
Source: https://www.smithsonianmag.com/smart-news/scientists-taught-pet-parrots-to-video-call-each-other-and-the-birds-loved-it-180982041/
originally posted at https://stacker.news/items/973639
-
 @ d360efec:14907b5f
2025-05-12 01:34:24
@ d360efec:14907b5f
2025-05-12 01:34:24สวัสดีค่ะเพื่อนๆ นักเทรดที่น่ารักทุกคน! 💕 Lina Engword กลับมาพร้อมกับการวิเคราะห์ BTCUSDT.P แบบเจาะลึกเพื่อเตรียมพร้อมสำหรับเทรดวันนี้ค่ะ! 🚀
วันนี้ 12 พฤษภาคม 2568 เวลา 08.15น. ราคา BTCUSDT.P อยู่ที่ 104,642.8 USDT ค่ะ โดยมี Previous Weekly High (PWH) อยู่ที่ 104,967.8 Previous Weekly Low (PWL) ที่ 93,338 ค่ะ
✨ ภาพรวมตลาดวันนี้ ✨
จากการวิเคราะห์ด้วยเครื่องมือคู่ใจของเรา ทั้ง SMC/ICT (Demand/Supply Zone, Order Block, Liquidity), EMA 50/200, Trend Strength, Money Flow, Chart/Price Pattern, Premium/Discount Zone, Trend line, Fibonacci, Elliott Wave และ Dow Theory ใน Timeframe ตั้งแต่ 15m ไปจนถึง Week! 📊 เราพบว่าภาพใหญ่ของ BTCUSDT.P ยังคงอยู่ในแนวโน้มขาขึ้นที่แข็งแกร่งมากๆ ค่ะ 👍 โดยเฉพาะใน Timeframe Day และ Week ที่สัญญาณทุกอย่างสนับสนุนทิศทางขาขึ้นอย่างชัดเจน Money Flow ยังไหลเข้าอย่างต่อเนื่อง และเราเห็นโครงสร้างตลาดแบบ Dow Theory ที่ยก High ยก Low ขึ้นไปเรื่อยๆ ค่ะ
อย่างไรก็ตาม... ใน Timeframe สั้นๆ อย่าง 15m และ 1H เริ่มเห็นสัญญาณของการชะลอตัวและการพักฐานบ้างแล้วค่ะ 📉 อาจมีการสร้าง Buyside และ Sellside Liquidity รอให้ราคาไปกวาดก่อนที่จะเลือกทางใดทางหนึ่ง ซึ่งเป็นเรื่องปกติของการเดินทางของ Smart Money ค่ะ
⚡ เปรียบเทียบแนวโน้มแต่ละ Timeframe ⚡
🪙 แนวโน้มตรงกัน Timeframe 4H, Day, Week ส่วนใหญ่ชี้ไปทาง "ขาขึ้น" ค่ะ ทุกเครื่องมือสนับสนุนแนวโน้มนี้อย่างแข็งแกร่ง 💪 เป้าหมายต่อไปคือการไปทดสอบ PWH และ High เดิม เพื่อสร้าง All-Time High ใหม่ค่ะ! 🪙 แนวโน้มต่างกัน Timeframe 15m, 1H ยังค่อนข้าง "Sideways" หรือ "Sideways Down เล็กน้อย" ค่ะ มีการบีบตัวของราคาและอาจมีการพักฐานสั้นๆ ซึ่งเป็นโอกาสในการหาจังหวะเข้า Long ที่ราคาดีขึ้นค่ะ
💡 วิธีคิดแบบ Market Slayer 💡
เมื่อแนวโน้มใหญ่เป็นขาขึ้นที่แข็งแกร่ง เราจะเน้นหาจังหวะเข้า Long เป็นหลักค่ะ การย่อตัวลงมาในระยะสั้นคือโอกาสของเราในการเก็บของ! 🛍️ เราจะใช้หลักการ SMC/ICT หาโซน Demand หรือ Order Block ที่ Smart Money อาจจะเข้ามาดันราคาขึ้น และรอสัญญาณ Price Action ยืนยันการกลับตัวค่ะ
สรุปแนวโน้มวันนี้:
🪙 ระยะสั้น: Sideways to Sideways Down (โอกาส 55%) ↔️↘️ 🪙 ระยะกลาง: ขาขึ้น (โอกาส 70%) ↗️ 🪙 ระยะยาว: ขาขึ้น (โอกาส 85%) 🚀 🪙 วันนี้: มีโอกาสย่อตัวเล็กน้อยก่อนจะมีแรงซื้อกลับเข้ามาเพื่อไปทดสอบ PWH (โอกาส Sideways Down เล็กน้อย สลับกับ Sideways Up: 60%) 🎢
🗓️ Daily Trade Setup ประจำวันนี้ 🗓️
นี่คือตัวอย่าง Setup ที่ Lina เตรียมไว้ให้พิจารณาค่ะ (เน้นย้ำว่าเป็นเพียงแนวทาง ไม่ใช่คำแนะนำลงทุนนะคะ)
1️⃣ ตัวอย่างที่ 1: รอรับที่โซน Demand (ปลอดภัย, รอยืนยัน)
🪙 Enter: รอราคาย่อตัวลงมาในโซน Demand Zone หรือ Bullish Order Block ที่น่าสนใจใน TF 1H/4H (ดูจากกราฟประกอบนะคะ) และเกิดสัญญาณ Bullish Price Action ที่ชัดเจน เช่น แท่งเทียนกลืนกิน (Engulfing) หรือ Hammer 🪙 TP: บริเวณ PWH 104,967.8 หรือ Buyside Liquidity ถัดไป 🎯 🪙 SL: ใต้ Low ที่เกิดก่อนสัญญาณกลับตัวเล็กน้อย หรือใต้ Demand Zone ที่เข้า 🛡️ 🪙 RRR: ประมาณ 1:2.5 ขึ้นไป ✨ 🪙 อธิบาย: Setup นี้เราจะใจเย็นๆ รอให้ราคาลงมาในโซนที่มีโอกาสเจอแรงซื้อเยอะๆ ตามหลัก SMC/ICT แล้วค่อยเข้า เพื่อให้ได้ราคาที่ดีและความเสี่ยงต่ำค่ะ ต้องรอสัญญาณ Price Action ยืนยันก่อนนะคะ ✍️
2️⃣ ตัวอย่างที่ 2: Follow Breakout (สายบู๊, รับความเสี่ยงได้)
🪙 Enter: เข้า Long ทันทีเมื่อราคาสามารถ Breakout เหนือ High ล่าสุดใน TF 15m หรือ 1H พร้อม Volume ที่เพิ่มขึ้นอย่างมีนัยสำคัญ 🔥 🪙 TP: บริเวณ PWH 104,967.8 หรือ Buyside Liquidity ถัดไป 🚀 🪙 SL: ใต้ High ก่อนหน้าที่ถูก Breakout เล็กน้อย 🚧 🪙 RRR: ประมาณ 1:3 ขึ้นไป ✨ 🪙 อธิบาย: Setup นี้เหมาะกับคนที่อยากเข้าไวเมื่อเห็นโมเมนตัมแรงๆ ค่ะ เราจะเข้าเมื่อราคา Breakout แนวต้านระยะสั้นพร้อม Volume เป็นสัญญาณว่าแรงซื้อกำลังมาค่ะ เข้าได้เลยด้วยการตั้ง Limit Order หรือ Market Order เมื่อเห็นการ Breakout ที่ชัดเจนค่ะ 💨
3️⃣ ตัวอย่างที่ 3: พิจารณา Short สั้นๆ ในโซน Premium (สวนเทรนด์หลัก, ความเสี่ยงสูง)
🪙 Enter: หากราคาขึ้นไปในโซน Premium ใน TF 15m หรือ 1H และเกิดสัญญาณ Bearish Price Action ที่ชัดเจน เช่น แท่งเทียน Shooting Star หรือ Bearish Engulfing บริเวณ Supply Zone หรือ Bearish Order Block 🐻 🪙 TP: พิจารณาแนวรับถัดไป หรือ Sellside Liquidity ใน TF เดียวกัน 🎯 🪙 SL: เหนือ High ของสัญญาณ Bearish Price Action เล็กน้อย 💀 🪙 RRR: ประมาณ 1:1.5 ขึ้นไป (เน้นย้ำว่าเป็นการเทรดสวนเทรนด์หลัก ควรใช้ RRR ต่ำและบริหารขนาด Lot อย่างเข้มงวด!) 🪙 อธิบาย: Setup นี้สำหรับคนที่เห็นโอกาสในการทำกำไรจากการย่อตัวระยะสั้นค่ะ เราจะเข้า Short เมื่อเห็นสัญญาณว่าราคาอาจจะมีการพักฐานในโซนที่ถือว่า "แพง" ในกรอบสั้นๆ ค่ะ ต้องตั้ง Stop Loss ใกล้มากๆ และจับตาดูใกล้ชิดนะคะ 🚨
⚠️ Disclaimer: การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัวของ Lina เท่านั้น ไม่ถือเป็นคำแนะนำในการลงทุนนะคะ การลงทุนมีความเสี่ยง ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบค่ะ 🙏
ขอให้ทุกท่านโชคดีกับการเทรดในวันนี้ค่ะ! มีคำถามอะไรเพิ่มเติม ถามมาได้เลยนะคะ ยินดีเสมอค่ะ! 😊
Bitcoin #BTCUSDT #Crypto #Trading #TechnicalAnalysis #SMC #ICT #MarketSlayer #TradeSetup #คริปโต #เทรดคริปโต #วิเคราะห์กราฟ #LinaEngword 😉



-
 @ 3d073b19:4ae60f39
2025-05-12 00:09:07
@ 3d073b19:4ae60f39
2025-05-12 00:09:07This is an English openletter
-
 @ 266815e0:6cd408a5
2025-05-02 22:24:59
@ 266815e0:6cd408a5
2025-05-02 22:24:59Its been six long months of refactoring code and building out to the applesauce packages but the app is stable enough for another release.
This update is pretty much a full rewrite of the non-visible parts of the app. all the background services were either moved out to the applesauce packages or rewritten, the result is that noStrudel is a little faster and much more consistent with connections and publishing.
New layout
The app has a new layout now, it takes advantage of the full desktop screen and looks a little better than it did before.
Removed NIP-72 communities
The NIP-72 communities are no longer part of the app, if you want to continue using them there are still a few apps that support them ( like satellite.earth ) but noStrudel won't support them going forward.
The communities where interesting but ultimately proved too have some fundamental flaws, most notably that all posts had to be approved by a moderator. There were some good ideas on how to improve it but they would have only been patches and wouldn't have fixed the underlying issues.
I wont promise to build it into noStrudel, but NIP-29 (relay based groups) look a lot more promising and already have better moderation abilities then NIP-72 communities could ever have.
Settings view
There is now a dedicated settings view, so no more hunting around for where the relays are set or trying to find how to add another account. its all in one place now
Cleaned up lists
The list views are a little cleaner now, and they have a simple edit modal

New emoji picker
Just another small improvement that makes the app feel more complete.
Experimental Wallet
There is a new "wallet" view in the app that lets you manage your NIP-60 cashu wallet. its very experimental and probably won't work for you, but its there and I hope to finish it up so the app can support NIP-61 nutzaps.
WARNING: Don't feed the wallet your hard earned sats, it will eat them!
Smaller improvements
- Added NSFW flag for replies
- Updated NIP-48 bunker login to work with new spec
- Linkfy BIPs
- Added 404 page
- Add NIP-22 comments under badges, files, and articles
- Add max height to timeline notes
- Fix articles view freezing on load
- Add option to mirror blobs when sharing notes
- Remove "open in drawer" for notes
-
 @ 3d073b19:4ae60f39
2025-05-11 23:59:56
@ 3d073b19:4ae60f39
2025-05-11 23:59:56Heading 1
Heading 2
Heading 3
Heading 4
Heading 5
Heading 6
Lists
Unordered List
- Item 1
- Item 2
- Subitem 2.1
- Subitem 2.2
Ordered List
- First item
- Second item
- Third item
Links
OpenAI - A link to OpenAI's website. Markdown Guide - A comprehensive guide to Markdown syntax.
Images
 - An example image with a title.
- An example image with a title.Blockquotes
This is a blockquote. It can span multiple lines. It is often used to highlight important information or quotes.
Code
Inline Code
Here is some
inline codethat demonstrates how to format code within a sentence.Code Block
```python
This is a Python code block
def hello_world(): print("Hello, world!") ```
Emphasis
Bold
This text is bold. This text is also bold.
Italic
This text is italic. This text is also italic.
Strikethrough
~~This text is strikethrough.~~
-
 @ 57d1a264:69f1fee1
2025-05-07 06:29:52
@ 57d1a264:69f1fee1
2025-05-07 06:29:52Your device, your data. TRMNL's architecture prevents outsiders (including us) from accessing your local network. TRMNAL achieve this through 1 way communication between client and server, versus the other way around. Learn more.
Learn more at https://usetrmnl.com/
originally posted at https://stacker.news/items/973632
-
 @ 4ba8e86d:89d32de4
2025-05-02 13:51:37
@ 4ba8e86d:89d32de4
2025-05-02 13:51:37Tutorial OpenKeychain
- Baixar no F-droid https://f-droid.org/app/org.sufficientlysecure.keychain
Ao abrir o OpenKeychain pela primeira vez, você verá uma tela inicial indicando que ainda não há chaves configuradas. Nesse ponto, você terá três opções:
-
Criar uma nova chave PGP diretamente no OpenKeychain: Ideal para quem está começando e precisa de uma solução simples para criptografia em comunicações diárias.
-
Usar um token de segurança (como Fidesmo, Yubikey, NEO, ou Sigilance) Se você busca uma segurança ainda maior, pode optar por armazenar sua chave privada em um token de segurança. Com essa configuração, a chave privada nunca é salva no dispositivo móvel. O celular atua apenas como uma interface de comunicação, enquanto a chave permanece protegida no token, fora do alcance de possíveis invasores remotos. Isso garante que somente quem possui o token fisicamente possa usar a chave, elevando significativamente o nível de segurança e controle sobre seus dados.
-
Importar uma chave PGP existente: Você pode importar uma chave PGP que já tenha sido gerada anteriormente, seja por meio de um arquivo no dispositivo ou por outro meio ler na área de transferência. https://image.nostr.build/51fdd924df4843ab73faa02a505c8fb17794f1789396ed89b154348ebb337f07.jpg
1. CRIANDO UMA NOVA CHAVE PGP.
Para iniciantes, recomendamos criar uma nova chave diretamente no aplicativo. abordaremos o uso do OpenKeychain em modo online, que é mais comum para comunicações diárias.
Passo 1: Clique em “Criar minha chave”. https://image.nostr.build/235f5cfdf4c3006ca3b00342741003f79a5055355c2a8ee425fc33c875f51e49.jpg
Passo 2: Criando sua chave PGP.
Para criar sua chave, você precisará fornecer algumas informações Os campos 'Nome' e 'Endereço de e-mail' são apenas formas convenientes para identificar a sua chave PGP.
-
Nome: Escolha um nome ou um pseudônimo. https://image.nostr.build/de3fe3ddbde0c7bf084be6e4b8150fdb8612365550622559b0ee72f50f56a159.jpg
-
E-mail: Associe um endereço de e-mail à chave, seja ele pessoal ou um e-mail relacionado ao pseudônimo. https://image.nostr.build/aff62baaeafe2c9a429ef10435a6f99dea36d6cfd7494e2bb882421dc8ed0f4e.jpg
2. REVISANDO E PERSONALIZANDO A CRIAÇÃO DA CHAVE.
Passo 3: Antes de criar sua chave PGP, verifique se os dados inseridos estão corretos. https://image.nostr.build/a8ec09ef3d9b4f557b0c4e380e7ca45d0fdbfa33fe80becea03ed0e5f5eedd24.jpg
Você também pode personalizar as configurações de segurança clicando nos três pontos no canto superior direito. https://image.nostr.build/1ce615555cea9a979ea951472052a219e77f4e1ebaaf5fcbbe9e91ea4f852bce.jpg
Ao cliclar em ' nova subchave ' pode alterar a data de expiração e pode mudar a criptografia usado na chave cliclando opção ed2255/cv255. https://image.nostr.build/b3224ff3dbe48ff78c4a2df8b001926b6d3eef1e33ef677a73b0d281791073da.jpg https://image.nostr.build/7763c7847e062cdcf71aafedbc2ef4c38056fd66aeb162ef3a1c30c028a14376.jpg https://image.nostr.build/5d3e20ade460dd5e89cc001ebdc062a36aff2c0e1573584ca3c0d1cb34bddcce.jpg
Neste tutorial, utilizaremos as configurações padrão do aplicativo.
Passo 4: Clique em "Criar chave" para concluir o processo. https://image.nostr.build/a8ec09ef3d9b4f557b0c4e380e7ca45d0fdbfa33fe80becea03ed0e5f5eedd24.jpg
3. Como Compartilhar sua Chave PGP Pública
Após criar sua chave PGP, você pode compartilhá-la para que outras pessoas possam enviar mensagens criptografadas para você. Veja o passo a passo de como exibir e compartilhar sua chave pública:
Passo 1: Acesse sua chave pública
Abra o OpenKeychain e selecione a chave que deseja compartilhar. Clique na chave para visualizar os detalhes. https://image.nostr.build/689c5237075317e89e183d2664630de973b09b68aaf8f3e3033654e987b781be.jpg https://image.nostr.build/4001610109579f27535628932258087b3b06c1f86b05f4f85537b6585c12a10b.jpg
Passo 2: Copiar sua chave pública
Nos detalhes da chave, você verá a opção "Copiar para a Área de Transferência". Clique nessa opção para copiar o código da sua chave pública. https://image.nostr.build/01ab3efa5e997e1910a2f8f7a888e6ad60350574cca4ca0214eee5581797f704.jpg
A chave PGP copiada terá o seguinte formato:
-----BEGIN PGP PUBLIC KEY BLOCK-----
mDMEZwsLHRYJKwYBBAHaRw8BAQdA6NRLlJIWnTBJtYwZHlrMbTKRbYuXmjsMn8MB 7etV3HK0JERhbmllbCBGcmFnYSAgPGRhbmllbGZyYWdhQG1haWwuaTJwPohyBBMW CAAaBAsJCAcCFQgCFgECGQEFgmcLCx0CngECmwMACgkQFZf+kMeJWpR4cwEA8Jt1 TZ/+YlHg3EYphW8KsZOboHLi+L88whrWbka+0s8A/iuaNFAK/oQAlM2YI2e0rAjA VuUCo66mERQNLl2/qN0LuDgEZwsLHRIKKwYBBAGXVQEFAQEHQEj/ZfJolkCjldXP 0KQimE/3PfO9BdJeRtzZA+SsJDh+AwEIB4hhBBgWCAAJBYJnCwsdApsMAAoJEBWX /pDHiVqUo/oA/266xy7kIZvd0PF1QU9mv1m2oOdo7QSoqvgFiq6AmelbAP9lExY5 edctTa/zl87lCddYsZZhxG9g2Cg7xX/XsfrnAA== =TniY -----END PGP PUBLIC KEY BLOCK-----
Dica: Se ocorrer algum erro ao compartilhar sua chave pública com um amigo, peça para que ele a criptografe para ele mesmo. Isso permitirá que ele adicione a chave corretamente. Caso a chave pública ainda não esteja no dispositivo, ao clicar em "Backup de chave", aparecerá a opção para importá-la. Se a chave já estiver no dispositivo, essa ação irá recarregá-la. https://image.nostr.build/cd12abf07c93473db95483fe23112325f89d3eb02977e42756708bbd043f8bcf.jpg https://image.nostr.build/537aeae38d229ee2cc78e18f412237b659c059e1c74fd7f0deecfe37f15713c9.jpg https://image.nostr.build/16c8a3db5966c7c06904ee236655f47a6464ae0c1b5af6af27b28c61611d2bbe.jpg
Passo 3: Compartilhar sua chave PGP
Você pode colar a chave pública em e-mails, assinaturas, perfis de redes sociais ou outros meios para compartilhá-la facilmente. Para facilitar a visualização, você também pode exibi-la em seu perfil de redes sociais.
Para acessar mais opções de compartilhamento, clique nos três pontos no canto superior direito e selecione a opção "Avançado". https://image.nostr.build/0d4a13b7bd9a4794017247d1a56fac082db0f993a2011a4dd40e388b22ec88f5.jpg https://image.nostr.build/4ac2a7bc9fa726531a945221cf7d10e0e387deba68100ccf52fdedfcd17cbd59.jpg
Na seção "Compartilhar", você verá sua Key ID e terá a opção de publicar sua chave PGP em um servidor de chaves. https://image.nostr.build/1e972cc211a6d8060cdbd4a8aa642dd1a292810c532f178d3ddb133d1b9bca76.jpg
Passo 4: Como compartilhar sua chave pública PGP no formato .asc. no OpenKeychain
1 . Acesse sua chave
Abra o OpenKeychain e toque na chave que você deseja compartilhar. Isso abrirá a tela com os detalhes da chave. https://image.nostr.build/c080f03d2eb7a9f7833fec0ff1942a5b70b97e4f7da7c6bc79ca300ef9ace55d.jpg
2 . Compartilhe o arquivo .asc
Toque no ícone de compartilhamento, como indicado na imagem abaixo. O aplicativo abrirá a janela para que você escolha por qual app deseja compartilhar sua chave pública no formato .asc. Nesse exemplo, usei o SimpleXChat , mas você pode usar qualquer aplicativo de sua preferência.
-
Botão de compartilhar. https://image.nostr.build/8da74bdb04737a45df671a30bba1dd2e7980841fa0c2d751d6649630e7c25470.jpg
-
Seleção do aplicativo para compartilhamento. https://image.nostr.build/5444f4e9d3fa5aef6b191bb6f553f94c6e49d30ead874c9ee435bca3218fd6c8.jpg
-
Enviando via SimpleXChat. https://image.nostr.build/e5d1ca04cbc69e1e8ac5caf1ab2a4b9b695500861c1ae9c55cea679cce349214.jpg
Sugestão para compartilhar nas redes sociais:
Você pode exibir sua chave de forma simples, por exemplo:
PGP: 1597 FE90 C789 5A94
Importar a chave pública usando a fingerprint
Passo 1:Clique no ícone "+" para começar. https://image.nostr.build/ca6e6e569b4be60165eaf60c7ba1e6e3ec781b525e467c72b4f3605837e6b5ec.jpg
Passo 2: Selecione a opção "Buscar Chave". https://image.nostr.build/87e27d9435e6e3ef78063b9f15799a8120ead4637cd06c89c0220b48327573ae.jpg
Passo 3: Digite a fingerprint da chave em letras minúsculas, sem espaços. A chave correspondente aparecerá para ser adicionada. https://image.nostr.build/33e6819edd4582d7a8513e8814dacb07e1a62994bb3238c1b5b3865a46b5f234.jpg
Além disso, você pode compartilhar sua chave pública em formato QR Code, facilitando a troca de chaves em eventos ou conversas rápidas. Como Assinar Mensagens para Confirmar a Autenticidade da Sua Rede Social
Você pode autenticar sua conta em redes sociais utilizando sua chave PGP. Ao assinar uma mensagem com sua chave, você demonstra que realmente possui essa conta. Siga o passo a passo abaixo para assinar uma mensagem:
Passo 1: Clique na sua chave PGP. https://image.nostr.build/ffacce1bfb293c9a0888cd5efe340a63d96b293f4c010f8626105c7b212d8558.jpg
Passo 2: Clique no ícone indicado pela seta para abrir o campo de texto. https://image.nostr.build/4e992a2553810e2583b9d190280ce00a52fc423600a75eca48cbf541cf47d3c2.jpg
Passo 3: Deixe a opção "Encriptar para:" vazio. Em "Assinar com:", selecione sua chave PGP e digite a mensagem que deseja enviar, como o nome da sua rede social. https://image.nostr.build/a4a2a8d233d186e3d8d9adddccc445bcb3ca3ed88de0db671a77cede12323a75.jpg
Passo 4: Clique no ícone indicado pela seta para copiar o texto assinado. Uma mensagem aparecerá informando: "Assinado/Encriptado com Sucesso". https://image.nostr.build/a076dfc90e30a495af0872005bf70f412df57b7a0e1c2e17cf5aee9e9b3e39aa.jpg
A mensagem copiada terá o seguinte formato:
-----BEGIN PGP SIGNED MESSAGE----- Hash: SHA256
Minha rede social NOSTR é Danielfraga oficial. -----BEGIN PGP SIGNATURE-----
iIQEARYIACwlHERhbmllbCBGcmFnYSAgPGRhbmllbGZyYWdhQG1haWwuaTJwPgUC ZxBBLgAKCRAVl/6Qx4lalGeNAPwP71rpsbhRnZhoWZsTDOFZY8ep/d0e5qYx5iPx HV26dwD/fKyiir1TR8JwZvEbOTYS0+Dn4DFlRAAfR3lKVTC96w4= =37Lj -----END PGP SIGNATURE-----
Com isso, você pode facilmente demonstrar a autenticidade da sua conta nas redes sociais.
4. PROTEGENDO SUA CHAVE COM UMA SENHA.
Passo 5: Após a criação da chave, é fundamental definir uma senha (ou passphrase) para adicionar uma camada extra de segurança. Recomendamos usar senhas longas (com mais de 20 caracteres) e de alta entropia para evitar ataques de força bruta. Ferramentas como KeePassDX ou Bitwarden podem ajudá-lo a gerar e gerenciar essas senhas.
Para definir a senha, clique na sua chave PGP, acesse o menu no canto superior direito e selecione "Alterar senha". https://image.nostr.build/689c5237075317e89e183d2664630de973b09b68aaf8f3e3033654e987b781be.jpg https://image.nostr.build/f28ecaa9890a8827f93cac78846c4b2ef67f86ccfc3501fdadf1d1c4874b0041.jpg https://image.nostr.build/919c277fbec63c397402abdd60f915cb239a674c317855cbda63a38edef80789.jpg
Agora basta adicionar uma senha forte. https://image.nostr.build/eb378219fbb1780f89663a474ce43b8d8ebb13beeb538f2a16279b056e5d9645.jpg https://image.nostr.build/cdfa3f9c6c4045841341da789deabb6318107812d5ba195529418572ab352aaf.jpg
5. CRIPTOGRAFAR E DESCRIPTOGRAFAR MENSAGENS E ARQUIVOS COM SUA CHAVE PGP
Criptografar Mensagens
Você pode criptografar mensagens para garantir que apenas o destinatário, que possui sua chave pública, possa lê-las. Siga os passos abaixo para criptografar um texto:
Passo 1: Abra o menu lateral clicando no ícone no canto superior esquerdo.
https://image.nostr.build/13ac93b38dd1633118ae3142401c13e8a089caabdf4617055284cc521a45b069.jpgPasso 2: Selecione a opção "Encriptar/Descriptar".
https://image.nostr.build/8cd905d616b53968f0551c071d9acc2f47bbe8434c2c7e1a33076a504342de48.jpgPasso 3: Clique na opção "Encriptar Texto".
https://image.nostr.build/405a730a6c774759d7913f92f59059d43146db4afb28451a6f8833f94e99437f.jpgPasso 4: Preencha os seguintes campos: https://image.nostr.build/7dc5eba39ff82a321195dbf46b8113818632e3ef41175991d58e799a8e9d2751.jpg
-
Encriptar para: Selecione o destinatário da mensagem, ou seja, a pessoa para quem você está enviando o texto criptografado.
https://image.nostr.build/1e8c8cba6d3c3136d9857512e2794a81ceb7434eccdfb0f7d26cdef008b2e6d2.jpg -
Assinar com: Escolha sua chave PGP para assinar a mensagem.
https://image.nostr.build/d25b228c35b132d396d01c354ef093b43b3565578fbc0d6ff7b9de4e41619855.jpg -
Digitar o texto: No campo de texto, escreva a mensagem que deseja criptografar.
https://image.nostr.build/8537271dfa4445e60cb4c3cdb5d97571dc0ff5ee8acd6ed89a8c81e4bd8736c2.jpg
Passo 5: Depois de preencher os campos, você pode copiar o texto criptografado de duas formas:
-
Copiar para a área de transferência: Clique na opção para copiar o texto criptografado e cole-o em um aplicativo de mensagens para enviá-lo.
https://image.nostr.build/a5cb8e2c538a38db3972e7f3ac9aa9f602cda6b62848ff0c4b99928a67dcd486.jpg -
Compartilhar diretamente: Utilize a opção de compartilhamento para enviar o texto criptografado diretamente através de seus aplicativos de mensagens.
https://image.nostr.build/2b79cb564d623788a0de1111a067e0eb496f743389d465d4f4e8f6e65f0d08a7.jpg https://image.nostr.build/ff59e52bc8ab54ff377980a6ba5d1c4743d3298de11e5daa187ab7d45163a7be.jpg
Criptografar arquivos.
Passo 1: Abra o menu lateral clicando no ícone no canto superior esquerdo.
https://image.nostr.build/13ac93b38dd1633118ae3142401c13e8a089caabdf4617055284cc521a45b069.jpgPasso 2: Selecione a opção "Encriptar/Descriptar".
https://image.nostr.build/8cd905d616b53968f0551c071d9acc2f47bbe8434c2c7e1a33076a504342de48.jpgPasso 3 : clique na opção "Encriptar arquivos ". https://image.nostr.build/3fcae48ee38e7f4079ebccfd3eafb9ab0ad3559221d2c3560cdfe60e29f56a15.jpg
Passo 4 : os passos a seguir são os mesmo que você seguiu pra encriptar a mensagem texto. Ítens "Encriptar para:" "Assinar com:" https://image.nostr.build/4d6599b9d3a9fdfae0964daaa9dae513d5ce277a7b61930fa2937d534f72ed40.jpg
Passo 5 : clilcar na opção " Adicionair arquivo(s)" Vai abrir na memória interna do celular selecione o arquivo que deseja encriptar. https://image.nostr.build/09e3b9b54a1406426114926aab19011c36b98886ebae6fcf556cfea83bb2c2f4.jpg https://image.nostr.build/af422e243b36762dd66111ec7c848a1352c100ca3040dc21792c923f80aef74d.jpg https://image.nostr.build/ebebbdb273b4bca58d901852aec1c60e4799aa77e9d12a31f992b0cf8f73e753.jpg
Passo 6: Depois de preencher os campos, você pode compartilhar o arquivo criptografado de duas formas:
-
Salvar na memória do celular: A primeira opção salva o arquivo criptografado no armazenamento do seu dispositivo. Você terá a opção de editar o nome do arquivo antes de salvar.
https://image.nostr.build/0a47c1e9f0003541f47091b2c2e8ce6b8d1533d95463e331b218070bae964ac8.jpg https://image.nostr.build/95a7a2b67356eb5ded5b217bab38a19bdeba5af7befd105834e413e0aec45462.jpg https://image.nostr.build/66cb3d22b271f3b73b7015613c72711a3ffbf5e1070d43153f9d1f3fcf35001c.jpg https://image.nostr.build/f9624d86f7592fe7ffad932b7805762dc279d9e8ff410222108155438a2c970f.jpg -
Compartilhar diretamente: Utilize a opção de compartilhamento para enviar o arquivo criptografado diretamente por meio dos seus aplicativos de mensagens.
https://image.nostr.build/85541e466c7755c65bd6ba0208a6d8612beaa5298712b6d92f53865167695a38.jpg https://image.nostr.build/bf1e0f0aeb60cafbdf82af4b3b598288519e85b396bd3f9e00e61f65b89ea9f8.jpg https://image.nostr.build/fb090339898f37cdbb020828689b142ca601ca3ee549f67ddf6b2e094df9ab9f.jpg https://image.nostr.build/50c249ced06efe465ba533fef15207b0dcd1a725e9b2c139e8d85c13fd798276.jpg
Descriptografar Mensagens e Arquivos
Para ler uma mensagem ou arquivo criptografado que você recebeu, utilize sua chave privada. Siga os passos abaixo:
Descriptografar Mensagens
Passo 1: Copie a mensagem criptografada que você recebeu.
https://image.nostr.build/c37754b12a458e0176b9137ae0aa9e8209f853bf9d9292c0867fd8b0606d53c4.jpgPasso 2: Clique na opção "Ler da área de transferência" para descriptografar o texto.
https://image.nostr.build/d83c7dad2ee1cb6267779863bc174ee1a8f3cc3c86b69063345321027bdde7b5.jpg https://image.nostr.build/c0fae86e6ab1fe9dcee86753972c818bed489ea11efdd09b7e7da7422a9c81eb.jpgDescriptografar Arquivos
Passo 1: Clique na opção "Selecionar arquivo de entrada".
https://image.nostr.build/9c276c630311d19a576f2e35b5ba82bac07360476edae3f1a8697ff85df9e3c9.jpgPasso 2: Selecione o arquivo criptografado que deseja descriptografar.
https://image.nostr.build/6b6c2a3284ba96e7168fc7bd0916020c4f1bed7b77dfca48227fc96d6929e15a.jpg https://image.nostr.build/9945aad644af2e2020e07e55f65f11a0958d55e8fc9e13c862e6b9ca88b4f4d9.jpg6. BACKUP E RESTAURAÇÃO DE CHAVE PGP.
Realizar o backup das suas chaves PGP é fundamental para evitar a perda de acesso às suas mensagens e dados criptografados. O OpenKeychain facilita esse processo, permitindo que você faça um backup completo e seguro. Recomendamos que você armazene o backup em um local seguro, como um HD externo ou pendrive conectado via cabo OTG, sempre protegendo-o com senha.
PASSOS PARA REALIZAR O BACKUP:
Passo 1: Abra o menu lateral clicando no ícone no canto superior esquerdo.
https://image.nostr.build/13ac93b38dd1633118ae3142401c13e8a089caabdf4617055284cc521a45b069.jpgPasso 2: Selecione a opção Backup/restaurar.
https://image.nostr.build/6fa8fd14e23b47c6c924bc0d900646663f2124a93d8172ae79fdf43b5c7d4490.jpgPasso 3: Escolha a primeira opção: Backup completo (criptografado).
https://image.nostr.build/4875fb27b6d04c3cb838b4fb9f308ef9194edc35ba1254ba965b7f0db2544170.jpgPasso 4: O backup será protegido por um código de backup gerado automaticamente. Anote esse código em um papel e guarde local seguro, pois sem ele você não conseguirá recuperar suas chaves PGP. Após anotar o código, marque a opção “Anotei o código” e clique em Salvar Backup. Obs: todas as vezes que você for fazer o backup da sua chave PGP vai ser criado um novo código aleatório.
https://image.nostr.build/72a317ef5e59a01c03c36f1d04a91d42c418a478cc82e372acf21bb8302daa00.jpg
Passo 5: Escolha o local onde deseja salvar o backup (HD externo, pendrive, etc.), confirme sua escolha e clique em OK. Você verá uma mensagem de confirmação indicando que o backup foi salvo com sucesso.
https://image.nostr.build/d757e8bdf429371320daa44be8a48a0dbeb2324129f4254327f0f0383e70ede4.jpg https://image.nostr.build/f3ad80ceb8a191b4d1b40722b1d0d4f85bf183d412e7d7d901b25d19b2dfe0e3.jpg
Importação da Chave PGP
Caso você precise restaurar suas chaves PGP a partir de um backup, o OpenKeychain também facilita o processo de importação. Siga os passos abaixo para restaurar sua chave PGP:
Passo 1: Selecione a opção "Selecionar arquivo de entrada"
Abra o OpenKeychain, acesse o menu lateral no canto superior esquerdo e escolha a opção "Selecionar arquivo de entrada" para localizar o arquivo de backup que você deseja importar.
https://image.nostr.build/a06ddc1c1e6c50519097e614aa25b14311e49c0ca4d4607e42ebdcca3a6641c4.jpgPasso 2: Selecione o arquivo de backup
Navegue até o local onde você salvou o arquivo de backup (HD externo, pendrive, etc.) e selecione-o. Em seguida, o OpenKeychain solicitará que você insira o código de recuperação que foi gerado no momento do backup. https://image.nostr.build/9d5649c04a98ec8b0a29355d9068e48313b1c5dc36cd965961f4d33f22d10046.jpgPasso 3: Digite o código de recuperação
Insira o código de recuperação que você anotou anteriormente. É importante digitar o código corretamente para garantir o sucesso da restauração.Passo 4: Depois de inserir o código corretamente, o OpenKeychain irá restaurar suas chaves PGP, e uma mensagem de confirmação será exibida, indicando que a recuperação foi concluída com sucesso.
Agora suas chaves estão restauradas e você pode continuar usando o OpenKeychain para gerenciar suas comunicações criptografadas de maneira segura.
https://www.openkeychain.org/
https://github.com/open-keychain/open-keychain
https://youtu.be/fptlAx_j4OA
-
 @ 3d073b19:4ae60f39
2025-05-11 23:52:28
@ 3d073b19:4ae60f39
2025-05-11 23:52:28Headings
Heading 1
Heading 2
Heading 3
Heading 4
Heading 5
Heading 6
Lists
Unordered List
- Item 1
- Item 2
- Subitem 2.1
- Subitem 2.2
Ordered List
- First item
- Second item
- Third item
Mixed List
-
Item 1
-
Item 2
-
Item 3
Links
OpenAI - A link to OpenAI's website. Markdown Guide - A comprehensive guide to Markdown syntax.
Images
 - An example image with a title.
- An example image with a title.Blockquotes
This is a blockquote. It can span multiple lines. It is often used to highlight important information or quotes.
Code
Inline Code
Here is some
inline codethat demonstrates how to format code within a sentence.Code Block
```python
This is a Python code block
def hello_world(): print("Hello, world!") ```
Emphasis
Bold
This text is bold. This text is also bold.
Italic
This text is italic. This text is also italic.
Strikethrough
~~This text is strikethrough.~~
-
 @ 3c389c8f:7a2eff7f
2025-05-11 22:53:30
@ 3c389c8f:7a2eff7f
2025-05-11 22:53:30As I'm sitting here trying to hone in on what might be important to write about in this moment, my mind keeps swirling around through all the things that have me sitting here to begin with. Nostr found me in a time when my life needed a change. The discovery of something that provided the light of hope to an otherwise dark, dystopian future was more powerful than I could have ever predicted. Timing is everything, they say. I believe that to be half true, as timing alone means nothing if the will is non-existent. The intersection of opportunity and preparedness, and all that. I know how I found my way here, but I do not fully understand the things that have drawn my curiosity and kept my attention so strongly. My will ached for change, simplicity, and meaning. I found it, in what seem to me, simultaneously the most likely and the most unlikely of places. There's a magic to that, and its probably better to leave some questions unanswered, lest they lose their mystic power.
My experiences are my own but theme of them resonates through most of the people with whom I interact. It's been very clear that I wasn't alone in these feelings. A movement of highly inspired, hopeful people have continued to support this digital freedom movement since my arrival, in varying ways. Some people have highly technical skills ranging from network systems to design to cybersecurity. Others, like myself, have little to offer in the realms of functionality and we do what we can to breathe life into the systems built to provide digital freedom of speech for all. It's a humbling experience. We are reminded. sometimes directly and sometimes indirectly, that none of Nostr would matter if there were no one using it. We know this to be true, but it is no less humbling to be surrounded by constant innovation and a thriving desire to bring this experience to the entire world.
Now here I sit, tapping out these words, in the midst of another massive life change, stressful but chosen. I could sign off, go read a book in the garden, and go about my world as I would have in my pre-Nostr times. I don't want to do that, though. Hope is here. If there is a place to dwell, in hope is where I will always choose.
I find it important to acknowledge, though, that Nostr and the people using it are in a constant state of flux, too. This isn't my rock nor harbor nor shelter. It's the chaotic good, reminding me both to keep an appreciation for how far this ecosystem has come in such a short amount of time and a realistic set of expectations for where this all can go. The same applies for how well things work at any given moment...And equally so in missing my some of my early Nostr friends that have come and gone, while remaining open to the possibility of meeting new ones... Experiences had and experiences yet to come. I don't know if I have ever been so coaxed outside of my mind by a group of strangers on the internet. But here I am, looking back and looking forward, surrounded by awe in all directions, sharing thoughts that would otherwise be scribbled in pen to be burned in a random evening fire. I've long felt that the core of social media should be just this. Spaces for people to connect, above all else, in the ways that create meaning in our lives. I suppose in some ways that did exist before, but it was twisted, and obscured, and slowly pulled away.
Now its here and super-charged by possibility. What this looks like for any individual will not be the same as my own view. That's part of what makes this so beautiful to me. We need to be able to speak freely. Just as importantly we need to be able to surround ourselves with the things and people that makes us want to do more, that make us want to feel humbled. Or not, if we so choose... but I choose hope.
-
 @ 3ffac3a6:2d656657
2025-05-02 03:50:51
@ 3ffac3a6:2d656657
2025-05-02 03:50:51Introduction: Don't Despair—This Can Be Fixed (But Don't Reboot Yet)
Running ZFS on a Raspberry Pi offers powerful features for home servers and personal NAS setups. But with power comes complexity, and in recent months, a quiet pitfall has emerged for Pi users who track kernel updates closely: upgrading to an unsupported kernel version breaks ZFS.
⚠️ Important Warning: If you've just upgraded your kernel and you're using ZFS, do not reboot yet. Rebooting without a working ZFS module can leave your system unbootable—even if you don't have critical partitions on ZFS. The system may hang because it tries to load the missing ZFS kernel module during boot and fails, halting the boot process.
If you're already facing a broken setup or can't boot — don't panic. This guide outlines both the worst-case scenario and the ideal recovery strategy. Whether you're locked out or preparing for a smooth upgrade, we've got you covered.
The Problem: A Kernel Update Too Far
As of ZFS version 2.2.3 (used in Debian-based Raspberry Pi OS), the filesystem supports Linux kernels up to 6.7. However, Raspberry Pi OS backports recently began shipping 6.12.x kernels. If you upgrade to 6.12 without precautions:
- ZFS will fail to compile against the new kernel
- DKMS errors will appear during package updates
- Your ZFS module will be missing after reboot
- Your Raspberry Pi may fail to boot, even without ZFS-mounted root or critical paths, simply due to systemd or boot scripts expecting the kernel module to be present
Example ZFS Compilation Error:
During package updates or installs, you'll see something like:
checking whether bdev_open_by_path() exists... configure: error: *** None of the expected "blkdev_get_by_path()" interfaces were detected. *** This may be because your kernel version is newer than what is *** supported, or you are using a patched custom kernel with *** incompatible modifications. *** *** ZFS Version: zfs-2.2.3-1~bpo12+1~rpt1 *** Compatible Kernels: 3.10 - 6.7This error means ZFS cannot build its kernel module against Linux 6.12.x, making it unusable.
Why This Happens: The Version Trap
The key problem is that ZFS 2.2.3 remains installed even after a kernel upgrade, and it doesn't get upgraded automatically during
apt upgrade. Since ZFS 2.2.3 only supports up to kernel 6.7, it fails to compile against 6.12.x.However, if you remove and then reinstall ZFS, the package manager installs ZFS 2.3.1, which does support Linux kernel 6.12.x. This version transition is what resolves the issue — but only if you explicitly purge and reinstall ZFS.
Worst Case: The System That Wouldn’t Boot
After upgrading the kernel and rebooting, the system failed to boot properly. It showed errors like:
cannot open access to console, the root account is locked
Although the system did not have critical filesystems on ZFS, the boot process still stalled because system services attempted to load the ZFS kernel module, which was no longer available. This resulted in an unrecoverable boot failure.
The only way forward was to reformat and reinstall Raspberry Pi OS. However, the default Raspberry Pi OS image still comes with a 6.6.x kernel, which is incompatible with ZFS 2.3.1 and newer kernels unless upgraded. Therefore, the recovery process requires one crucial step:
- First, perform a full system upgrade:
sudo apt update && sudo apt full-upgradeThis brings the kernel up to 6.12.x.
- Then, reinstall ZFS:
sudo apt install zfs-dkms zfsutils-linuxOnce this is complete, your system will be running kernel 6.12 with ZFS 2.3.1, and you can safely import your pools and resume operations.
Best Case Recovery: Clean Cut, Clean Upgrade
For users who can still log into their system, here's the cleanest and safest sequence to move forward:
- Stop all services using ZFS, including Docker, NFS, Samba, backup tools, etc.
- Export all ZFS pools:
sudo zpool export -a3. Disable swap if it lives on a ZFS vdev:sudo swapoff /dev/sdXn4. Purge ZFS packages:sudo apt purge zfsutils-linux zfs-dkms zfs-zed sudo rm -rf /usr/src/zfs* /var/lib/dkms/zfs5. Update the kernel to the desired version:sudo apt update && sudo apt full-upgrade6. Reboot into the new kernel:sudo reboot7. Reinstall ZFS:sudo apt install zfs-dkms zfsutils-linux8. Import your pool(s):sudo zpool import poolname9. Restart services that depend on ZFS.
Final Notes: Prevention Is Better Than Recovery
To avoid this issue in the future:
- Hold your current working kernel version:
sudo apt-mark hold linux-image-rpi-v8 linux-headers-rpi-v8* Or track ZFS GitHub for kernel compatibility before upgrading * Or test upgrades on a second Pi or cloned SD card before rolling them out to production
Conclusion: A Solvable Trap
ZFS on the Raspberry Pi remains a powerful option, but it demands careful version tracking. If you upgrade responsibly, or recover cleanly as described above, you can continue benefiting from advanced features like snapshots, send/receive, and compression even on this tiny powerhouse.
Don’t let a kernel update ruin your storage plans—with preparation, the Pi + ZFS combo can remain stable and strong.
-
 @ 57d1a264:69f1fee1
2025-05-07 06:16:30
@ 57d1a264:69f1fee1
2025-05-07 06:16:30Here’s Sean Voisen writing about how programming is a feeling:
For those of us who enjoy programming, there is a deep satisfaction that comes from solving problems through well-written code, a kind of ineffable joy found in the elegant expression of a system through our favorite syntax. It is akin to the same satisfaction a craftsperson might find at the end of the day after toiling away on well-made piece of furniture, the culmination of small dopamine hits that come from sweating the details on something and getting them just right. Maybe nobody will notice those details, but it doesn’t matter. We care, we notice, we get joy from the aesthetics of the craft.
This got me thinking about the idea of satisfaction in craft. Where does it come from?
Continue Reading https://blog.jim-nielsen.com/2025/craft-and-satisfaction/
originally posted at https://stacker.news/items/973628
-
 @ 21335073:a244b1ad
2025-05-01 01:51:10
@ 21335073:a244b1ad
2025-05-01 01:51:10Please respect Virginia Giuffre’s memory by refraining from asking about the circumstances or theories surrounding her passing.
Since Virginia Giuffre’s death, I’ve reflected on what she would want me to say or do. This piece is my attempt to honor her legacy.
When I first spoke with Virginia, I was struck by her unshakable hope. I had grown cynical after years in the anti-human trafficking movement, worn down by a broken system and a government that often seemed complicit. But Virginia’s passion, creativity, and belief that survivors could be heard reignited something in me. She reminded me of my younger, more hopeful self. Instead of warning her about the challenges ahead, I let her dream big, unburdened by my own disillusionment. That conversation changed me for the better, and following her lead led to meaningful progress.
Virginia was one of the bravest people I’ve ever known. As a survivor of Epstein, Maxwell, and their co-conspirators, she risked everything to speak out, taking on some of the world’s most powerful figures.
She loved when I said, “Epstein isn’t the only Epstein.” This wasn’t just about one man—it was a call to hold all abusers accountable and to ensure survivors find hope and healing.
The Epstein case often gets reduced to sensational details about the elite, but that misses the bigger picture. Yes, we should be holding all of the co-conspirators accountable, we must listen to the survivors’ stories. Their experiences reveal how predators exploit vulnerabilities, offering lessons to prevent future victims.
You’re not powerless in this fight. Educate yourself about trafficking and abuse—online and offline—and take steps to protect those around you. Supporting survivors starts with small, meaningful actions. Free online resources can guide you in being a safe, supportive presence.
When high-profile accusations arise, resist snap judgments. Instead of dismissing survivors as “crazy,” pause to consider the trauma they may be navigating. Speaking out or coping with abuse is never easy. You don’t have to believe every claim, but you can refrain from attacking accusers online.
Society also fails at providing aftercare for survivors. The government, often part of the problem, won’t solve this. It’s up to us. Prevention is critical, but when abuse occurs, step up for your loved ones and community. Protect the vulnerable. it’s a challenging but a rewarding journey.
If you’re contributing to Nostr, you’re helping build a censorship resistant platform where survivors can share their stories freely, no matter how powerful their abusers are. Their voices can endure here, offering strength and hope to others. This gives me great hope for the future.
Virginia Giuffre’s courage was a gift to the world. It was an honor to know and serve her. She will be deeply missed. My hope is that her story inspires others to take on the powerful.
-
 @ 2ce0697b:1ee3d3fc
2025-04-29 18:54:19
@ 2ce0697b:1ee3d3fc
2025-04-29 18:54:19Excerpt
Special Jurisdictions, Free Cities and Bitcoin Citadels are the sly roundabout way that is removing the market of living together from the hands of the government, without violence and in a way that they can´t stop it. With Bitcoin as the backbone of a new societal order, we are beginning to disrupt the old paradigm.
“If you have built castles in the air, your work need not be lost; that is where they should be. Now put the foundations under them.” ― Henry David Thoreau, Walden
The problem: lack of freedom in the physical realm
Freedom is essential to human life. Being free is what matters. That´s our target, always. No matter the time or space. We pursue freedom because we know its the right thing to do. Freedom is the right to question and change the stablished way of doing things.
Where can we find some freedom? Certainly in the cyberspace. The cyberspace is a free space. Humanity has been blessed by the magic of cryptography, a technology that gave us all the necessary tools to operate in that environment without intervention of undesired third parties.
In cyberspace cryptography performs the function of an impenetrable cyberwall. So, whatever we build in cyberspace can be perfectly protected. Thank to this cybernetic walls we can be sure that the gardens we build and nurture will be protected and cannot be trampled. When we build our digital gardens we have the keys to open the doors to let in whoever we want and most important to leave out whoever we don´t want. In the digital world we can already perfectly interact with one and another in a peer to peer way, without intervention of undesired third parties.
In cyberspace we have Bitcoin for freedom of money and Nostr, torrent and Tor for freedom of information and speech. These open-source protocols are designed to fully realize and expand the promise of freedom, and they certainly deliver what they promise.

So, thanks to the magic of asymmetric cryptography, we´ve already achieved sufficiently descentralization and the possibility of any level of desired digital privacy. Cryptoanarchists and cypherpunks have set their conquering flag in cyberspace and there´s no force on Earth than can remove it. The digital world cannot escape the rules of cryptography. This is great but it only works in the digital realm, meanwhile in the physical realm we are overrun by centralized attackers due to the impossibility of the creation of impenetrable walls such as the ones we have online.
Humans have the upper hand in creating impenetrable walled gardens in cyberspace, but in the physical space authoritarians have the upper hand in bullying physical persons.
The physical world is also naturally free. According to natural law each person is free to do whatever he wants as long as it doesn´t hurt other people. However due to unnatural -artificial and inhuman- centralization of power, the natural freedom of the physical world has been completely undermined. Mostly by Governments, the entities that centralize violence and law.
Bitcoin as a bridge between both realms

Let´s take a look at one connection between both realms, the physical and the digital world. Bitcoin layer one is made essentially of software plus hardware. It consists of any software that produces the same output as the reference implementation - Bitcoin core- and the hardware needed to run that software. Layer two, three or any other layer above, is made essentially of other software and other hardware that interacts with layer one in some way. All these layers, one, two and subsequent, are completely protected by cryptography and a set of game theories that have been successfully tested. Each new block added to the timechain is a testimony of the unstoppable force of freedom and meritocracy.
Before layer one we have Bitcoin layer zero, which is essentially the sum of all actions and inactions done by bitcoiners regarding to or because of bitcoin. In other words, layer zero is composed by flesh and bone people interacting in some way with layer one of the bitcoin network.
Hence, an attack on a bitcoiner - on his way of life- is an attack on bitcoin, the network itself. First because it is an attack on a layer zero node, the physical person, the bitcoiner under duress or coercion. And second because is also an attack on the store-of-value-aspect of bitcoin. Nowaday, the most common attack against bitcoiners is the entirety of compliance regulations. This is the sum of all coercive regulations,such as laws, threats of more laws, imprisonment, threats of more imprisonment, taxation, threats of more taxation, requirements to prove the origin of funds, coercive removal of privacy such as the travel rule, unnecessary bureaucracy such as the need to obtain a money transmitting license and many others rules, in a never stopping inflationary coercive legislation.

If a physical attack is preventing any bitcoiner to exchange the value he created for bitcoin due to any kind of artificial obstacles -such as any kind of compliance- that specific attack is successful in the sense that even though the whole network keeps operating, the attack itself diminishes the value of all the bitcoins.
So, even if layer-zero cannot be taken down, every interference on this layer is an attack on the bitcoin network. Attacks on layer one, two or any other layer that exists in the cyberspace can interfere with the network but they may hardly subtract any value from it. For example we have already been through plenty of times where hashing power was diminished due to government intervention and the bitcoin network remain completely unaffected.
On the other hand successful attacks on layer zero subtract potential, but real and demonstrable value. This value is equal to the amount of value the frustrated user would have added to the network if he would have been able to use it freely, that means if he would have sold his product without the cost of compliance. I´ll demonstrate this in the next chapter.
The cost of compliance
Alice is a merchant specialized in a specific area and topic. She studied the market, her business, her suppliers, consumers, the logistics involved, marketing, design, and everything necessary to become a successful entrepreneur. After investing a considerable amount of resources, she developed a perfect product. Or at least she considers it perfect, that is, the best in its class. While developing everything necessary to create her product, she met Bob, who became her main lead and stereotype of a buyer persona. She knows what Bob wants and she wants to sell it to him. According to Alice's calculations, for her business to be viable, she must sell the product at ten satoshis per unit, and fortunately, Bob is willing to pay that price for it. Alice's product is finished, ready to hit the market, but just before sending it to production, Alice decides to take a pause to analyze her reality. Before taking the public action of making her product available in the open market, Alice analyzes her material, political, and legal reality. In doing so, she realizes that she lives under the jurisdiction of a State. She learns that the Government prescribes through its regulations how she must behave. She analyzes that in order to sell her product legally, in compliance, she must make a series of modifications to it. The product before hitting the shelves must first be modified both in the way it is presented to the market and also regarding certain technical characteristics that it possesses. She must also modify the way it produces her product by changing the contractual relationship with its suppliers, distribution channels, and all other types of logistics involved. She must make all these changes even if they bring about significant and insurmountable inefficiencies.
Likewise, Alice also sees that she not only has to modify the product but also has to meet tax obligations. In addition to paying an accountant since the tax obligations by some irrational reason are not calculated by the creditor. Additionally, she must hire other professionals to assist her in studying the current regulations and how they should be applied in all stages of production, distribution, and sale of her product.
Alice, being a rational person, wishes to avoid having to make these modifications since they increase her costs while also decreasing the quality of her product. But when studying compliance, that is, the entirety of applicable regulations, she also examines the consequences of not being in compliance. Alice realizes that if she does not comply with the regulations, she risks having all her assets legally confiscated, going to prison, being killed while they try to capture her to imprison her, and, if she goes to prison, being tortured in jail by other inmates or by State officials in charge of holding her in that place. So, since Alice does not want to suffer these negative consequences, she decides to modify the product and be in compliance.
So, Alice makes the necessary changes and puts her new version of the product on the market. Then she has the following dialogue with Bob, her lead, the interested party in acquiring the product.
Bob: - Hey Alice, nice meeting you here in this market. I came to buy the product you were developing and told me about. However, this product I´m seeing now is not what you promised me. This is clearly inferior.
Alice: - Yeah, I know. I'm sorry Bob, but I prefer to sell this inferior product rather than risk having all my assets confiscated, going to prison, being killed while they try to capture me, and if they don´t kill but managed to put me in jail I could be tortured there.
Bob: - Ok, no problem. Thats quite understandable. I don´t believe anyone would prefer those kind of experiences. But given the quality of the product, I no longer intend to pay you ten satoshis; I only offer you eight. Shall we close the deal?
Alice: - I'm sorry Bob, but I can't sell it to you for eight sats. Due to government intervention and its requirements, now I can't even sell it for less than thirteen satoshis.
Bob: - Ok. Considering this I prefer not to purchase it. I will keep looking for alternatives. Bye

Some time later, Charlie arrives at the market, who is also interested in the product and, despite it not being like the original version, decides to purchase it by paying the thirteen satoshis demanded by the seller Alice.
Meanwhile, in the same universe, we have Daniel, the last character in this example. Daniel is a merchant competing with Alice. Daniel has a product that is very similar, practically identical to the one originally designed by Alice. Like Alice, Daniel initially also wants to sell it for ten satoshis. Just like Alice, before heading to the market, Daniel analyzes the reality in which he lives. And it turns out that he also lives under the jurisdiction of a State. Daniel too then analyzes the entirety of the applicable regulations and also comes to the conclusion that to comply with them, he would also need to modify the product and cover all the additional expenses artificially generated to be in compliance.
However, Daniel's ethics are different from Alice's. Daniel understands that his product is indeed perfect (the best in its class) and that therefore modifying it would go against its essence. Daniel understands that changing the product would be a betrayal of his creation and therefore a betrayal of his own self and the essence of his being. Daniel conducts an ethical analysis of his actions and the moral implications of putting the product on the market. Daniel sees that the product not only does not harm anyone but is also made to be freely acquired by adults who give their consent for its purchase and subsequent use. Daniel also understands that paying taxes only serves to promote the slavery system driven by fiat and that whenever he can avoid collaborating with the immoral fiat system, it is his ethical obligation to do so. Likewise, Daniel highlights the hypocrisy and inefficiencies of anti-money laundering regulations, as well as the futility of requiring licenses for naturally free acts that do not harm others. For all these reasons, Daniel decides to sell the product in its current state irregardles of compliance regulations.
However, before going to market, Daniel also studies the possible consequences of neglecting compliance. By doing so, Daniel sees that if he does not comply with the regulations, he risks having all his assets legally confiscated, going to prison, being killed while they attempt to capture him to imprison him, and, in the event of going to prison, being tortured in jail by other inmates or by State officials responsible for holding him in that place. So, since Daniel is a rational person who does not want to suffer these negative consequences but also does not want to betray his product and himself, he decides to take the risk of not being in compliance. After making this decision, Daniel puts the product on the market and there he meets Bob. In doing so, they converse in the following terms:
Bob: - Hey Daniel, this product is exactly what I was looking for. A product like the one promised by Alice but never delivered. I love it! I offer you ten satoshis for it.
Daniel: - Thank you for your feedback Bob and for the offer! However I am currently selling it for eleven satoshis. Ten satoshis seems like a good price to me, and it was indeed my original intention to sell it for that amount because at that price I achieve competitiveness and a sustainable business model.
Bob: - So why are you asking me for eleven satoshis? Interrupts Bob
Daniel: - Because that price is calculated before assessing compliance and the risks associated with non-compliance. By not complying with the regulation, I managed to maintain the quality of the product and avoided a large amount of unnecessary expenses, but there is no way to avoid the risk of facing penalties for non-compliance. To bring this product to market, I had to incur several expenses in order to minimize the risk of non-compliance as much as possible. While I am taking all reasonable actions to prevent all of my assets from being legally confiscated, from going to prison, from being killed while they try to capture me, and in case of going to prison, from being tortured, the reality is that I still run the risk of all that, or part of all that, happening to me, my family, or any of my company's employees. The remaining risk balance is transferred to the price along with the costs of mitigating those risks. The total of those costs and the remaining risk I estimate them at one satoshi per unit of product. Therefore, I can't sell you the product for ten satoshis, but I can sell it to you for eleven.
To which Bob, lacking a better option in the market, ends up buying the product for eleven satoshis.
In summary: two products were made by two different merchants whose business model allowed them, in both cases, to put the product on the market at a rate of ten satoshis per unit. However, in one case, a lower quality product was sold for thirteen satoshis, and in the other case, a higher quality product was sold for eleven satoshis. That is to say, in the first case there was an overprice or inefficiency objectively measured at three satoshis, while in the second case there was an overprice or inefficiency of one satoshi. So, we are facing a total loss of value equivalent to four satoshis. The value represented by these four satoshis was absorbed by the inefficiency programmed and ruled by the State. The example shows us that whether one chooses the compliance route, as Alice did, or the free market route, as Daniel did, in both cases the existence of regulations generates an additional cost to the market. In this example the state attack on layer zero was successful and extracted from the Bitcoin network a value of four satoshis.
Bitcoin is money
Bitcoin is many things but essentially is money. And money sole purpose is to store value in order to facilitate future exchanges of products and services with other people. Without the products and services to be exchanged for the money, money itself would be useless and worthless. We only use money because we may require favors, benefits, services, products from other people in the future. And we don´t know which services and products we´ll need nor exactly when we are goint to need them.

The total value of bitcoin equals to infinity divided twenty one millions. This is because the total worth of the network mirrors the total worth of accumulated capital by the entirety of mankind throughout its entire history. That is clearly a lot of value. But if the if the dividend equals zero then the divisor is also zero and if the dividend growth is obstructed through artificial means -such as compliance- then the divisor growth is also obstructed.
Bitcoin layer zero, the bitcoiners and the services and products we create, are what give value to the twenty one million units of bitcoin.
Freedom is without a doubt the best context for value creation. So, the more and better games we can create that allow humankind to find a way to exercise freedom, then the most value we can add to all the layers of the network.
This is why the most important layer of the whole bitcoin phenomenon is layer zero, the bitcoiners. Hence the problem to be solved is not how to prevent bitcoin - layer one upwards- from successful attacks. The problem to solve is how to prevent attacks on layer zero. Or in other words, the problem to be solved is how to get bitcoiners in the physical world to practice the same level of freedom that bitcoin achieves in the cyberspace.
Summary of the first part of this article: freedom in cyberspace has already been conquered and each further development in the digital realm contributes to further developments but only in the same realm. Meanwhile in the physical space, the layer zero of bitcoin is under constant attacks that successfully extract value from it.
Exercising freedom in a sly roundabout way

In 1984 the Austrian economist Friedrich Hayek predicted that we couldn´t take money with violence out of the hands of government. He stated that we needed to do it in a sly roundabout way. Twenty five years later Satoshi Nakamoto discovered the sly roundabout way actually introducing something that the government couldn´t stop. Thus fulfilling Hayek´s prophecy.
Bitcoin is a sly roundabout way that removed money without violence from the hands of the government in a way that they can´t stop it.
Cryptography in general and protocols such as Tor and Tails are a sly roundabout way that removed confidential information from the hands of the government without violence in a way that they can´t stop it.
Nostr is a sly roundabout way that removed social media and public information from the hands of the government without violence in a way that they can´t stop it.
Special Jurisdictions, Free Cities and Bitcoin Citadels are the sly roundabout way that is removing the market of living together from the hands of the government without violence in a way that they can´t stop it.

So, what are Special Jurisdictions, Free Cities and Bitcoin Citadels? To understand what they are we can take a look at the current mainstream market of living together, at how the physical space is organized. Essentially the entire planet Earth and its surroundings are run by a conglomerate of Governments. They create all the rules, regarding every aspect of life, of all the individuals, and enforce every rule through coercive means.
In the mainstream market of living together individuals have several alternatives to pick from. We can choose to live in a natural city or a pre design city, in a public neighborhood or private neighborhood or even in an intentional community with common interest amongst the users. But irregardless of the choice, every product offered in the mainstream market has the sames rules which are established by the host state to the entirety of organizations in his territory. In the mainstream market, even the most different products abide by the same high level rules such as criminal law, civil law, taxation laws, customs, enviromental laws, money laundering regulations and many others. To abide to the sum of all the laws and regulations is to be in compliance.
The centralization of regulations makes extremely difficult to experiment in market of living together. The less experimentation is allowed, the more human progress is hindered.
So what is the sly roundabout that fixes this? What are Special Jurisdictions, Free Cities and Bitcoin Citadels? I´m using the term Special Jurisdictions as an umbrella term that includes the entire spectrum of iterations of products that aim to modify the mainstream rules of the market of living together.
This term includes all the different models such as Charter Cities, Free Cities, Special Economic Zones, microstates, micropolis, start up societies, government as a service, self governing jurisdictions, autonomous intentional communities, network states and Bitcoin Citadels. The array of possible iterations is huge and permanently expanding. What they all have in common is that each of these experiments aims to create a functional game theory that replaces the lack of unbreakable walls in the physical space.
Let´s take a look of a couple of examples. Special Economic Zones are bounded areas of countries that have their own rules and regulations. Worldwide, there are more than five thousands special economic zones located in more than hundred countries.
One of them is the special economic zone of Shenzhen in China. The Chinese government allowed Shenzhen the freedom to experiment with certain practices that were prohibited in the rest of the country at the time. This included allowing foreign companies to make direct investments in China, allowing people to buy and sell land, allowing Chinese people to set up their own private businesses and relaxation of the system that limited internal migration within China for Chinese citizens. It served as a place where China could experiment with market reforms. The experiment was such a huge economic success that it was replicated in many other areas of the country.
Another place that has made extensive use of special economic zones is Dubai. The monarchic Government has more than 30 SEZs. In this case one of the many obstacles removed by the host state its the monopoly of the legal system. Dubai Government allowed the special economic zone to have its own independent legal system thus conceding a modification of the mainstream rules in that area.
This kind of projects, such as Dubai or Shenzhen, are a top-to-down product. Fully created by the Governments thus compliant with their own regulations.

On the other side of the spectrum we have Citadels and several other archetypes of not so compliant projects .
For example the Free Commune of Penadexo it´s a grassroots project building a freedom-oriented community in one of Spain’s abandoned villages.
 It´s model is based on building a peer to peer society avoiding government intervention as much as possible.
They stablished themselves in an abandoned historic village and the started to track down the owners to purchase as much property as possible. Meanwhile, they are living there and expanding their users base while also reconstructing buildings.
It´s model is based on building a peer to peer society avoiding government intervention as much as possible.
They stablished themselves in an abandoned historic village and the started to track down the owners to purchase as much property as possible. Meanwhile, they are living there and expanding their users base while also reconstructing buildings. This is an example of a completely different way of dealing with the Government. While Special Economic Zones are fully compliant and created top to down, this model on the other hand is bottom-up and aims to add value to the users relying in factual freedom which is exercised by stablishing the commune away from heavily populated centers where Government grip is tighter. Under this model the interaction with the Government is kept as low as possible. Their strategy relies in ignoring the Government as much as possible and being a good neighbor. With this simple and effective tactic some Citadels enjoy the benefits of liberty in their lifetime without needing to spend huge resources in governmental lobby.
There are countless models or archetypes of Bitcoin Citadels trying to solve the obstacles in different ways, trying to restart the system. And one of the challenges of the Bitcoin Citadels is how to connect the different projects to boost and help each other.
This is where The Meshtadel comes into play. The Meshtadel is a system where decentralized tactics are used to help and defend citadels connected in a global network. With real life connections with fellow bitcoiners. Its an organization equivalent to the hanseatic league built under a starfish model. If you cut off a spider’s head, it dies, but if you cut off a starfish’s arm, it can regenerate and even grow into a new starfish.
The Meshtadel its a network of peer relationships, with ambiguous leadership roles, trust among participants, a shared ideology and vision based on the Bitcoin ethos, and an open system where new nodes - bitcoin citadel builders - can participate.
The long term goal of the Bitcoin Meshtadel is to help Bitcoin Citadels to gain the support of a critical mass of the total population. If enough people see that Bitcoin is as peaceful as it gets, in the long run, some nations could become friendly and supportive enough to legally tolerate the Bitcoin Citadel inside its territory in the form of a Bitcoin safe haven. In the Meshtadel we are fighting from the moral high ground using memes, Nostr notes and zapping our way into freedom creating an online and offline circular economy.
TO CONCLUDE:
Special Jurisdictions, Free Cities and Bitcoin Citadels are the sly roundabout way that is removing the market of living together from the hands of the government, without violence and in a way that they can´t stop it.
Nation states, abusing the myth of authority, have halted development on the market of living together for so long that a blooming freer market is eating its lunch. The sovereign individual thesis is live and continuously expanding. The network state is forming and intentional communities are flourishing all around the world reshaping globally the relationship between individuals and the governments.
With global internet connections, uncensorable means of communication and Bitcoin as the backbone of a new societal order, we are beginning to disrupt the old paradigm.
The fashion of the present world is passing away, let’s help it to move forward along by building Special Jurisdictions, Free Cities and Bitcoin Citadels.
--- --- --- --- --- --- --- --- ------
byCamiloat 875.341 timechain.
If you find this content helpful, zap it to support more content of the sort and to boost the V4V model.
-
 @ 57d1a264:69f1fee1
2025-05-07 06:03:29
@ 57d1a264:69f1fee1
2025-05-07 06:03:29CryptPad
Collaboration and privacy. Yes, you can have both Flagship instance of CryptPad, the end-to-end encrypted and open-source collaboration suite. Cloud administered by the CryptPad development team. https://cryptpad.fr/
ONLYOFFICE DocSpace
Document collaboration made simpler. Easily collaborate with customizable rooms. Edit any content you have. Work faster using AI assistants. Protect your sensitive business data. Download or try STARTUP Cloud (Limited-time offer) FREE https://www.onlyoffice.com/
SeaFile
A new way to organize your files Beyond just syncing and sharing files, Seafile lets you add custom file properties and organize your files in different views. With AI-powered automation for generating properties, Seafile offers a smarter, more efficient way to manage your files. Try it Now, Free for up to 3 users https://seafile.com/
SandStorm
An open source platform for self-hosting web apps Self-host web-based productivity apps easily and securely. Sandstorm is an open source project built by a community of volunteers with the goal of making it really easy to run open source web applications. Try the Demo or Signup Free https://alpha.sandstorm.io/apps
NextCloud Hub
A new generation of online collaboration that puts you in control. Nextcloud offers a modern, on premise content collaboration platform with real-time document editing, video chat & groupware on mobile, desktop and web. Sign up for a free Nextcloud account https://nextcloud.com/sign-up/
LinShare
True Open Source Secure File Sharing Solution We are committed to providing a reliable Open Source file-sharing solution, expertly designed to meet the highest standards of diverse industries, such as government and finance Try the Demo https://linshare.app/
Twake Drive
The open-source alternative to Google Drive. Privacy-First Open Source Workplace. Twake workplace open source business. Improve your effeciency with truly Open Source, all-in-one digital suite. Enhance the security in every aspect of your professional and private life. Sign up https://sign-up.twake.app/
SpaceDrive
One Explorer. All Your Files. Unify files from all your devices and clouds into a single, easy-to-use explorer. Designed for creators, hoarders and the painfully disorganized. Download desktop app (mobile coming soon) https://www.spacedrive.com/
ente
Safe Home for your photos Store, share, and discover your memories with end-to-end encryption. End-to-end encryption, durable storage and simple sharing. Packed with these and much more into our beautiful open source apps. Get started https://web.ente.io
fileStash
Turn your FTP server into... Filestash is the enterprise-grade file manager connecting your storage with your identity provider and authorisations. Try the demo https://demo.filestash.app
STORJ
Disruptively fast. Globally secure. S3-compatible distributed cloud services that make the most demanding workflows fast and affordable. Fast track your journey toward high performance cloud services. Storj pricing is consistent and competitive in meeting or exceeding your cloud services needs. Give the products a try to experience the benefits of the distributed cloud. Get Started https://www.storj.io/get-started
FireFile
The open‑source alternative to Dropbox. Firefiles lets you setup a cloud drive with the backend of your choice and lets you seamlessly manage your files across multiple providers. It revolutionizes cloud storage management by offering a unified platform for all your storage needs. Sign up Free https://beta.firefiles.app
originally posted at https://stacker.news/items/973626
-
 @ 57d1a264:69f1fee1
2025-05-06 06:00:25
@ 57d1a264:69f1fee1
2025-05-06 06:00:25Album art didn’t always exist. In the early 1900s, recorded music was still a novelty, overshadowed by sales of sheet music. Early vinyl records were vastly different from what we think of today: discs were sold individually and could only hold up to four minutes of music per side. Sometimes, only one side of the record was used. One of the most popular records of 1910, for example, was “Come, Josephine, in My Flying Machine”: it clocked in at two minutes and 39 seconds.
The invention of album art can get lost in the story of technological mastery. But among all the factors that contributed to the rise of recorded music, it stands as one of the few that was wholly driven by creators themselves. Album art — first as marketing material, then as pure creative expression — turned an audio-only medium into a multi-sensory experience.
This is the story of the people who made music visible.
originally posted at https://stacker.news/items/972642
-
 @ 872982aa:8fb54cfe
2025-05-12 01:40:27
@ 872982aa:8fb54cfe
2025-05-12 01:40:27 {.user-img}
{.user-img}
-
 @ 57d1a264:69f1fee1
2025-05-06 05:49:01
@ 57d1a264:69f1fee1
2025-05-06 05:49:01I don’t like garlic. It’s not a dislike for the taste in the moment, so much as an extreme dislike for the way it stays with you—sometimes for days—after a particularly garlicky meal.
Interestingly enough, both of my brothers love garlic. They roast it by itself and keep it at the ready so they can have a very strong garlic profile in their cooking. When I prepare a dish, I don’t even see garlic on the ingredient list. I’ve cut it out of my life so completely that my brain genuinely skips over it in recipes. While my brothers are looking for ways to sneak garlic into everything they make, I’m subconsciously avoiding it altogether.
A few years back, when I was digging intensely into how design systems mature, I stumbled on the concept of a design system origin story. There are two extreme origin stories and an infinite number of possibilities between. On one hand you have the grassroots system, where individuals working on digital products are simply trying to solve their own daily problems. They’re frustrated with having to go cut and paste elements from past designs or with recreating the same layouts over and over, so they start to work more systematically. On the other hand, you have the top down system, where leadership is directing teams to take a more systematic approach, often forming a small partially dedicated core team to tackle some centralized assets and guidelines for all to follow. The influences in those early days bias a design system in interesting and impactful ways.
We’ve established that there are a few types of bias that are either intentionally or unintentionally embedded into our design systems. Acknowledging this is a great first step. But, what’s the impact of this? Does it matter?
I believe there are a few impacts design system biases, but there’s one that stands out. The bias in your design system makes some individuals feel the system is meant for them and others feel it’s not. This is a problem because, a design system cannot live up to it’s expected value until it is broadly in use. If individuals feel your design system is not for them, the won’t use it. And, as you know, it doesn’t matter how good your design system is if nobody is using it.
originally posted at https://stacker.news/items/972641
-
 @ 872982aa:8fb54cfe
2025-05-12 01:39:07
@ 872982aa:8fb54cfe
2025-05-12 01:39:07 {.user-img}
{.user-img}

-
 @ 57d1a264:69f1fee1
2025-05-05 05:26:34
@ 57d1a264:69f1fee1
2025-05-05 05:26:34The European Accessibility Act is coming, now is a great time for accessibility trainings!. In my Accessibility for Designer workshop, you will learn how to design accessible mockups that prevent issues in visual design, interactions, navigation, and content. You will be able to spot problems early, fix them in your designs, and communicate accessibility clearly with your team. This is a practical workshop with hands-on exercises, not just theory. You’ll actively apply accessibility principles to real design scenarios and mockups. And will get access to my accessibility resources: checklists, annotation kits and more.
When? 4 sessions of 2 hours + Q and As, on: - Mon, June 16, - Tue, June 17, Mon, - June 23 and Tue, - June 24. 9:30 – 12:00 PM PT or 18:30 – 21:00 CET
Register with 15% discount ($255) https://ti.to/smashingmagazine/online-workshops-2022/with/87vynaoqc0/discount/welcometomyworkshop
originally posted at https://stacker.news/items/971772
-
 @ 57d1a264:69f1fee1
2025-05-05 05:15:02
@ 57d1a264:69f1fee1
2025-05-05 05:15:02Crabtree's Framework for Evaluating Human-Centered Research
Picture this: You've spent three weeks conducting qualitative research for a finance app redesign. You carefully recruited 12 participants, conducted in-depth interviews, and identified patterns around financial anxiety and decision paralysis. You're excited to present your findings when the inevitable happens:
"But are these results statistically significant?"
"Just 12 people? How can we make decisions that affect thousands of users based on conversations with just 12 people?"
As UX professionals, we regularly face stakeholders who evaluate our qualitative research using criteria designed for quantitative methods... This misalignment undermines the unique value qualitative research brings to product development.
Continue reading https://uxpsychology.substack.com/p/beyond-numbers-how-to-properly-evaluate
originally posted at https://stacker.news/items/971767
-
 @ c631e267:c2b78d3e
2025-05-02 20:05:22
@ c631e267:c2b78d3e
2025-05-02 20:05:22Du bist recht appetitlich oben anzuschauen, \ doch unten hin die Bestie macht mir Grauen. \ Johann Wolfgang von Goethe
Wie wenig bekömmlich sogenannte «Ultra-Processed Foods» wie Fertiggerichte, abgepackte Snacks oder Softdrinks sind, hat kürzlich eine neue Studie untersucht. Derweil kann Fleisch auch wegen des Einsatzes antimikrobieller Mittel in der Massentierhaltung ein Problem darstellen. Internationale Bemühungen, diesen Gebrauch zu reduzieren, um die Antibiotikaresistenz bei Menschen einzudämmen, sind nun möglicherweise gefährdet.
Leider ist Politik oft mindestens genauso unappetitlich und ungesund wie diverse Lebensmittel. Die «Corona-Zeit» und ihre Auswirkungen sind ein beredtes Beispiel. Der Thüringer Landtag diskutiert gerade den Entwurf eines «Coronamaßnahmen-Unrechtsbereinigungsgesetzes» und das kanadische Gesundheitsministerium versucht, tausende Entschädigungsanträge wegen Impfnebenwirkungen mit dem Budget von 75 Millionen Dollar unter einen Hut zu bekommen. In den USA soll die Zulassung von Covid-«Impfstoffen» überdacht werden, während man sich mit China um die Herkunft des Virus streitet.
Wo Corona-Verbrecher von Medien und Justiz gedeckt werden, verfolgt man Aufklärer und Aufdecker mit aller Härte. Der Anwalt und Mitbegründer des Corona-Ausschusses Reiner Fuellmich, der seit Oktober 2023 in Untersuchungshaft sitzt, wurde letzte Woche zu drei Jahren und neun Monaten verurteilt – wegen Veruntreuung. Am Mittwoch teilte der von vielen Impfschadensprozessen bekannte Anwalt Tobias Ulbrich mit, dass er vom Staatsschutz verfolgt wird und sich daher künftig nicht mehr öffentlich äußern werde.
Von der kommenden deutschen Bundesregierung aus Wählerbetrügern, Transatlantikern, Corona-Hardlinern und Russenhassern kann unmöglich eine Verbesserung erwartet werden. Nina Warken beispielsweise, die das Ressort Gesundheit übernehmen soll, diffamierte Maßnahmenkritiker als «Coronaleugner» und forderte eine Impfpflicht, da die wundersamen Injektionen angeblich «nachweislich helfen». Laut dem designierten Außenminister Johann Wadephul wird Russland «für uns immer der Feind» bleiben. Deswegen will er die Ukraine «nicht verlieren lassen» und sieht die Bevölkerung hinter sich, solange nicht deutsche Soldaten dort sterben könnten.
Eine wichtige Personalie ist auch die des künftigen Regierungssprechers. Wenngleich Hebestreit an Arroganz schwer zu überbieten sein wird, dürfte sich die Art der Kommunikation mit Stefan Kornelius in der Sache kaum ändern. Der Politikchef der Süddeutschen Zeitung «prägte den Meinungsjournalismus der SZ» und schrieb «in dieser Rolle auch für die Titel der Tamedia». Allerdings ist, anders als noch vor zehn Jahren, die Einbindung von Journalisten in Thinktanks wie die Deutsche Atlantische Gesellschaft (DAG) ja heute eher eine Empfehlung als ein Problem.
Ungesund ist definitiv auch die totale Digitalisierung, nicht nur im Gesundheitswesen. Lauterbachs Abschiedsgeschenk, die «abgesicherte» elektronische Patientenakte (ePA) ist völlig überraschenderweise direkt nach dem Bundesstart erneut gehackt worden. Norbert Häring kommentiert angesichts der Datenlecks, wer die ePA nicht abwähle, könne seine Gesundheitsdaten ebensogut auf Facebook posten.
Dass die staatlichen Kontrolleure so wenig auf freie Software und dezentrale Lösungen setzen, verdeutlicht die eigentlichen Intentionen hinter der Digitalisierungswut. Um Sicherheit und Souveränität geht es ihnen jedenfalls nicht – sonst gäbe es zum Beispiel mehr Unterstützung für Bitcoin und für Initiativen wie die der Spar-Supermärkte in der Schweiz.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ bf47c19e:c3d2573b
2025-05-11 22:33:46
@ bf47c19e:c3d2573b
2025-05-11 22:33:46Originalni tekst na dvadesetjedan.com
Autor: Vijay Boyapati / Prevod na hrvatski: Matija
Sa zadnjim cijenama koje je bitcoin dosegao 2017., optimističan scenarij za ulagače se možda čini toliko očitim da ga nije potrebno niti spominjati. Alternativno, možda se nekome čini glupo ulagati u digitalnu vrijednost koja ne počiva na nijednom fizičkom dobru ili vladi i čiji porast cijene su neki usporedili sa manijom tulipana ili dot-com balonom. Nijedno nije točno; optimističan scenarij za Bitcoin je uvjerljiv, ali ne i očit. Postoje značajni rizici kod ulaganja u Bitcoin, no, kao što planiram pokazati, postoji i ogromna prilika.
Geneza
Nikad u povijesti svijeta nije bilo moguće napraviti transfer vrijednosti među fizički udaljenim ljudima bez posrednika, poput banke ili vlade. 2008. godine, anonimni Satoshi Nakamoto je objavio 8 stranica rješenja na dugo nerješivi računalski problem poznat kao “Problem Bizantskog Generala.” Njegovo rješenje i sustav koji je izgradio - Bitcoin - dozvolio je, prvi put ikad, da se vrijednost prenosi brzo i daleko, bez ikakvih posrednika ili povjerenja. Implikacije kreacije Bitcoina su toliko duboke, ekonomski i računalski, da bi Nakamoto trebao biti prva osoba nominirana za Nobelovu nagradu za ekonomiju i Turingovu nagradu.
Za ulagače, važna činjenica izuma Bitcoina (mreže i protokola) je stvaranje novog oskudnog digitalnog dobra - bitcoina (monetarne jedinice). Bitcoini su prenosivi digitalni “novčići” (tokeni), proizvedeni na Bitcoin mreži kroz proces nazvan “rudarenje” (mining). Rudarenje Bitcoina je ugrubo usporedivo sa rudarenjem zlata, uz bitnu razliku da proizvodnja bitcoina prati unaprijed osmišljeni i predvidivi raspored. Samo 21 milijun bitcoina će ikad postojati, i većina (2017., kada je ovaj tekst napisan) su već izrudareni. Svake četiri godine, količina rudarenih bitcoina se prepolovi. Produkcija novih bitcoina će potpuno prestati 2140. godine.
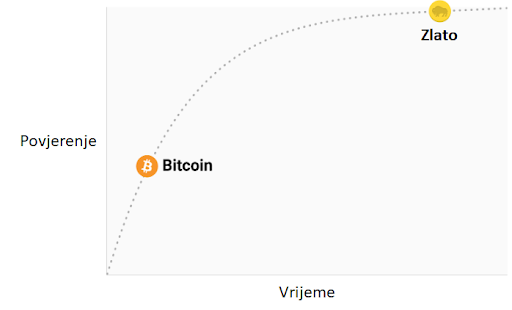 Stopa inflacije —— Monetarna baza
Stopa inflacije —— Monetarna bazaBitcoine ne podržava nikakva roba ili dobra, niti ih garantira ikakva vlada ili firma, što postavlja očito pitanje za svakog novog bitcoin ulagača: zašto imaju uopće ikakvu vrijednost? Za razliku od dionica, obveznica, nekretnina ili robe poput nafte i žita, bitcoine nije moguće vrednovati koristeći standardne ekonomske analize ili korisnost u proizvodnji drugih dobara. Bitcoini pripadaju sasvim drugoj kategoriji dobara - monetarnih dobara, čija se vrijednost definira kroz tzv. teoriju igara; svaki sudionik na tržištu vrednuje neko dobro, onoliko koliko procjenjuje da će ga drugi sudionici vrednovati. Kako bismo bolje razumjeli ovo svojstvo monetarnih dobara, trebamo istražiti podrijetlo novca.
Podrijetlo novca
U prvim ljudskim društvima, trgovina među grupama se vršila kroz robnu razmjenu. Velika neefikasnost prisutna u robnoj razmjeni je drastično ograničavala količinu i geografski prostor na kojem je bila moguća. Jedan od najvećih problema sa robnom razmjenom je problem dvostruke podudarnosti potražnje. Uzgajivač jabuka možda želi trgovati sa ribarom, ali ako ribar ne želi jabuke u istom trenutku, razmjena se neće dogoditi. Kroz vrijeme, ljudi su razvili želju za čuvanjem određenih predmeta zbog njihove rijetkosti i simbolične vrijednosti (npr. školjke, životinjski zube, kremen). Zaista, kako i Nick Szabo govori u svojem izvrsnom eseju o podrijetlu novca, ljudska želja za sakupljanjem predmeta pružila je izraženu evolucijsku prednost ranom čovjeku nad njegovim najbližim biološkim rivalom, neandertalcem - Homo neanderthalensis.
"Primarna i najbitnija evolucijska funkcija sakupljanja bila je osigurati medij za čuvanje i prenošenje vrijednosti".
Predmeti koje su ljudi sakupljali služili su kao svojevrsni “proto-novac,” tako što su omogućavale trgovinu među antagonističkim plemenima i dozvoljavale bogatsvu da se prenosi na sljedeću generaciju. Trgovina i transfer takvih predmeta bile su rijetke u paleolitskim društvima, te su oni služili više kao “spremište vrijednosti” (store of value) nego kao “medij razmjene” (medium of exchange), što je uloga koju danas igra moderni novac. Szabo objašnjava:
"U usporedbi sa modernim novcem, primitivan novac je imao jako malo “brzinu” - mogao je promijeniti ruke samo nekoliko puta u životu prosječnog čovjeka. Svejedno, trajni i čvrsti sakupljački predmet, što bismo danas nazvali “nasljeđe,” mogao je opstati mnogo generacija, dodajući znatnu vrijednost pri svakom transferu - i zapravo omogućiti transfer uopće".
Rani čovjek suočio se sa bitnom dilemom u teoriji igara, kada je odlučivao koje predmete sakupljati: koje od njih će drugi ljudi željeti? Onaj koji bi to točno predvidio imao bi ogromnu prednost u mogućnosti trgovine i akvizicije bogatsva. Neka američka indijanska plemena, npr. Naraganseti, specijalizirala su se u proizvodnji sakupljačkih dobara koja nisu imala drugu svrhu osim trgovine. Valja spomenuti da što je ranije predviđanje da će neko dobro imati takvu vrijednost, veća je prednost koju će imati onaj koji je posjeduje, zato što ju je moguće nabaviti jeftinije, prije nego postane vrlo tražena roba i njezona vrijednost naraste zajedno sa populacijom. Nadalje, nabava nekog dobra u nadi da će u budućnosti biti korišteno kao spremište vrijednosti, ubrzava upravo tu primjenu. Ova cirkularnost je zapravo povratna veza (feedback loop) koja potiče društva da se rapidno slože oko jednog spremišta vrijednosti. U terminima teorije igara, ovo je znano kao “Nashov ekvilibrij.” Postizanje Nashovog ekvilibrija za neko spremište vrijednosti je veliko postignuće za društvo, pošto ono znatno olakšava trgovinu i podjelu rada, i time omogućava napredak civilizacije.
Tisućljećima, kako su ljudska društva rasla i otvarala trgovinske puteve, različite aplikacije spremišta vrijednosti u individualnim društvima počele su se natjecati međusobno. Trgovci su imali izbor: čuvati svoju zaradu u spremištu vrijednosti vlastite kulture, ili one kulture sa kojom su trgovali, ili mješavini oboje. Benefit štednje u stranom spremištu vrijednosti bila je uvećana sposobnost trgovanja u povezanom stranom društvu. Trgovci koji su štedili u stranom spremištu vrijednosti su također imali dobrih razloga da potiču svoje društvo da ga prihvati, jer bi tako uvećali vrijednost vlastite ušteđevine. Prednosti “uvezene” tehnologije spremanja vrijednosti bile su prisutne ne samo za trgovce, nego i za sama društva. Kada bi se dvije grupe konvergirale u jedinstvenom spremištu vrijednosti, to bi značajno smanjilo cijenu troškova trgovine jednog s drugim, i samim time povećanje bogatstva kroz trgovinu. I zaista, 19. stoljeće bilo je prvi put da je najveći dio svijeta prihvatio jedinstveno spremište vrijednosti - zlato - i u tom periodu vidio najveću eksploziju trgovine u povijesti svijeta. O ovom mirnom periodu, pisao je John Maynard Keynes:
"Kakva nevjerojatna epizoda u ekonomskom napretku čovjeka… za svakog čovjeka iole iznadprosječnog, iz srednje ili više klase, život je nudio obilje, ugodu i mogućnosti, po niskoj cijeni i bez puno problema, više nego monarsima iz prethodnih perioda. Stanovnik Londona mogao je, ispijajući jutarnji čaj iz kreveta, telefonski naručiti razne proizvode iz cijele Zemlje, u količinama koje je želio, i sa dobrim razlogom očekivati njihovu dostavu na svoj kućni prag."
Svojstva dobrog spremišta vrijednosti
Kada se spremišta vrijednosti natječu jedno s drugim, specifična svojstva rade razliku koja daje jednom prednost nad drugim. Premda su mnoga dobra u prošlosti korištena kao spremišta vrijednosti ili kao “proto-novac,” određena svojstva su se pokazala kao posebno važna, i omogućila dobrima sa njima da pobijede. Idealno spremište vrijednosti biti će:
- Trajno: dobro ne smije biti kvarljivo ili lako uništeno. Tako naprimjer, žito nije idealno spremište vrijednosti.
- Prenosivo: dobro mora biti lako transportirati i čuvati, što omogućuje osiguranje protiv gubitka ili krađe i dopušta trgovinu na velike udaljenosti. Tako, krava je lošije spremište vrijednosti od zlatne narukvice.
- Zamjenjivo: jedna jedinica dobra treba biti zamjenjiva sa drugom. Bez zamjenjivosti, problem podudarnosti želja ostaje nerješiv. Time, zlato je bolje od dijamanata, jer su oni nepravilni u obliku i kvaliteti.
- Provjerljivo: dobro mora biti lako i brzo identificirano i testirano za autentičnost. Laka provjera povećava povjerenje u trgovini i vjerojatnost da će razmjena biti dovršena.
- Djeljivo: dobro mora biti lako djeljivo na manje dijelove. Premda je ovo svojstvo bilo manje važno u ranim društvima gdje je trgovina bila rijetka, postalo je važnije sa procvatom trgovine. Količine koje su se mijenjale postale su manje i preciznije.
- Oskudno: Monetarno dobro mora imati “cijenu nemoguću za lažirati,” kao što je rekao Nick Szabo. Drugim riječima, dobro ne smije biti obilno ili lako dostupno kroz proizvodnju. Oskudnost je možda i najvažnije svojstvo spremišta vrijednosti, pošto se izravno vezuje na ljudsku želju da sakupljamo ono što je rijetko. Ona je izvor vrijednosti u spremištu vrijednosti.
- Duge povijesti: što je dulje neko dobro vrijedno za društvo, veća je vjerojatnost da će biti prihvaćeno kao spremište vrijednosti. Dugo postojeće spremište vrijednosti biti će jako teško uklonjeno od strane došljaka, osim u slučaju sile (ratno osvajanje) ili ako je nova tehnologija znatno bolja u ostalim svojstvima.
- Otporno na cenzuru: novije svojstvo, sve više važno u modernom digitalnom svijetu sa sveprisutnim nadzorom, je otpornost na cenzuru. Drugim riječima, koliko je teško da vanjski agent, kao korporacija ili država, spriječi vlasnika dobra da ga čuva i koristi. Dobra koja su otporna na cenzuru su idealna za ljude koji žive u režimima koji prisilno nadziru kapital ili čine neke oblike mirne trgovine protuzakonitima.
Ova tablica ocjenjuje Bitcoin, zlato (gold) i fiat novac (kao što je euro ili dolar) po svojstvima izlistanim gore. Objašnjenje svake ocjene slijedi nakon tablice.
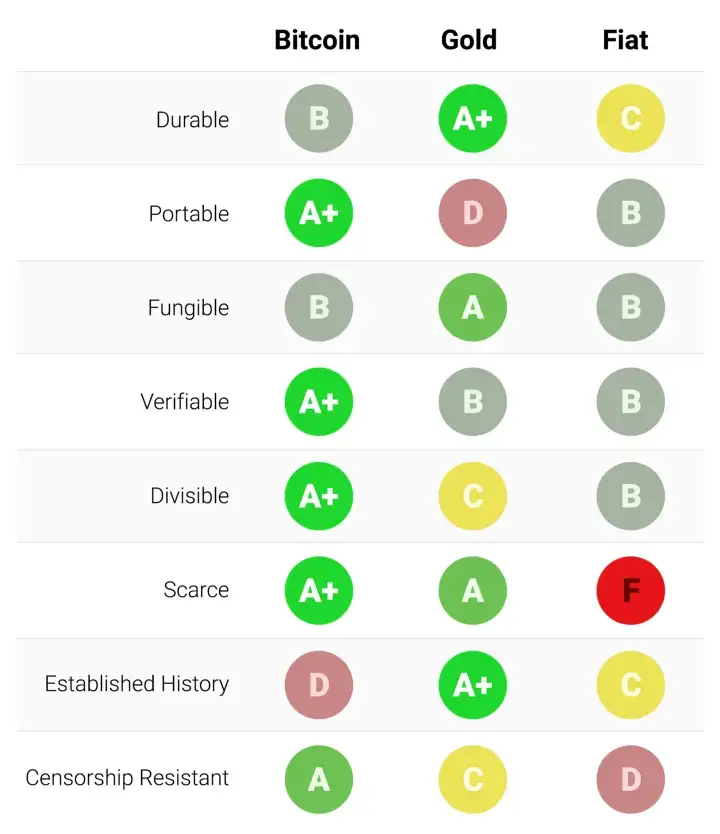
Trajnost:
Zlato je neosporeni kralj trajnosti. Velika većina zlata pronađenog kroz povijest, uključujući ono egipatskih faraona, opstaje i danas i vjerojatno će postojati i za tisuću godina. Zlatnici korišteni u antičko doba imaju značajnu vrijednost i danas. Fiat valute i bitcoini su digitalni zapisi koji ponekad imaju fizički oblik (npr. novčanice). Dakle, njihovu trajnost ne određuju njihova fizička svojstva (moguće je zamijeniti staru i oštećenu novčanicu za novu), nego institucije koje stoje iza njih. U slučaju fiat valuta, mnoge države su nastale i nestale kroz stoljeća, i valute su nestale s njima. Marke iz Weimarske republike danas nemaju vrijednost zato što institucija koja ih je izdavala više ne postoji. Ako je povijest ikakav pokazatelj, ne bi bilo mudro smatrati fiat valute trajnima dugoročno; američki dolar i britanska funta su relativne anomalije u ovom pogledu. Bitcoini, zato što nemaju instituciju koja ih održava, mogu se smatrati trajnima dok god mreža koja ih osigurava postoji. Obzirom da je Bitcoin još uvijek mlada valuta, prerano je za čvrste zaključke o njegovoj trajnosti. No, postoje ohrabrujući znakovi - prominente države su ga pokušavale regulirati, hakeri ga napadali - usprkos tome, mreža nastavlja funkcionirati, pokazujući visok stupanj antifragilnosti.
Prenosivost:
Bitcoini su najprenosivije spremište vrijednosti ikad. Privatni ključevi koji predstavljaju stotine milijuna dolara mogu se spremiti na USB drive i lako ponijeti bilo gdje. Nadalje, jednako velike sume mogu se poslati na drugi kraj svijeta skoro instantno. Fiat valute, zbog svojeg temeljno digitalnog oblika, su također lako prenosive. Ali, regulacije i kontrola kapitala od strane države mogu ugroziti velike prijenose vrijednosti, ili ih usporiti danima. Gotovina se može koristiti kako bi se izbjegle kontrole kapitala, ali onda rastu rizik čuvanja i cijena transporta. Zlato, zbog svojeg fizičkog oblika i velike gustoće, je najmanje prenosivo. Nije čudo da većina zlatnika i poluga nikad ne napuste sefove. Kada se radi prijenos zlata između prodavača i kupca, uglavnom se prenosi samo ugovor o vlasništvu, ne samo fizičko zlato. Prijenos fizičkog zlata na velike udaljenosti je skupo, riskantno i sporo.
Zamjenjivost:
Zlato nam daje standard za zamjenjivost. Kada je rastopljeno, gram zlata je praktički nemoguće razlikovati od bilo kojeg drugog grama, i zlato je oduvijek bilo takvo. S druge strane, fiat valute, su zamjenjive samo onoliko koliko njihova institucija želi da budu. Iako je uglavnom slučaj da je novčanica zamjenjiva za drugu istog iznosa, postoje situacije u kojima su velike novčanice tretirane drukčije od malih. Naprimjer, vlada Indije je, u pokušaju da uništi neoporezivo sivo tržište, potpuno oduzela vrijednost novčanicama od 500 i 1000 rupija. To je uzrokovalo da ljudi manje vrednuju te novčanice u trgovini, što je značilo da više nisu bile zaista zamjenjive za manje novčanice. Bitcoini su zamjenjivi na razini mreže; svaki bitcoin je pri prijenosu tretiran kao svaki drugi. No, zato što je moguće pratiti individualne bitcoine na blockchainu, određeni bitcoin može, u teoriji, postati “prljav” zbog korštenja u ilegalnoj trgovini, te ga trgovci ili mjenjačnice možda neće htjeti prihvatiti. Bez dodatnih poboljšanja oko privatnosti i anonimnosti na razini mrežnog protokola, bitcoine ne možemo smatrati jednako zamjenjivim kao zlato.
Mogućnost provjere:
Praktično gledajući, autentičnost fiat valuta i zlata je prilično lako provjeriti. Svejedno, i usprkos pokušajima da spriječe krivotvorenje novčanica, i dalje postoji potencijal prevare za vlade i njihove građane. Zlato također nije imuno na krivotvorenje. Sofisticirani kriminalci su koristili pozlaćeni tungsten kako bi prevarili kupce zlata. Bitcoine je moguće provjeriti sa matematičkom sigurnošću. Korištenjem kriptografskih potpisa, vlasnik bitcoina može javno demonstrirati da posjeduje bitcoine koje tvrdi da posjeduje.
Djeljivost:
Bitcoine je moguće podijeliti u stotinu milijuna manjih jedinica (zvanih satoshi), i prenositi takve (no, valja uzeti u obzir ekonomičnost prijenosa malih iznosa, zbog cijene osiguravanja mreže - “network fee”). Fiat valute su tipično dovoljno djeljive na jedinice sa vrlo niskom kupovnom moći. Zlato, iako fizički i teoretski djeljivo, postaje teško za korištenje kada se podijeli na dovoljno male količine da bi se moglo koristiti u svakodnevnoj trgovini.
Oskudnost:
Svojstvo koje najjasnije razlikuje Bitcoin od fiat valuta i zlata je njegova unaprijed definirana oskudnost. Od početka, konačna količina bitcoina nikad neće biti veća od 21 milijun. To daje vlasnicima bitcoina jasan i znan uvid u postotak ukupnog vlasništva. Naprimjer, vlasnik 10 bitcoina bi znao da najviše 2,1 milijuna ljudi (manje od 0.03% populacije) može ikad imati isto bitcoina kao i on. Premda je kroz povijest uvijek bilo oskudno, zlato nije imuno na povećanje ukupne količine. Ako se ikad izumi nova, ekonomičnija metoda rudarenja ili proizvodnje zlata, ukupna količina zlata bi se mogla dramatično povećati (npr. rudarenje morskog dna ili asteroida). Na kraju, fiat valute, relativno nov izum u povijesti, pokazale su se sklonima konstantnim povećanjima u količini. Države su pokazale stalnu sklonost inflaciji monetarne kvantitete kako bi rješavale kratkoročne političke probleme. Inflacijske tendencije vlada diljem svijeta čine fiat valute gotovo sigurnim da će gubiti vrijednost kroz vrijeme.
Etablirana povijest:
Nijedno monetarno dobro nema povijest kao zlato, koje je imalo vrijednost za cijelog trajanja ljudske civilizacije. Kovanice izrađene u antičko doba i danas imaju značajnu vrijednost. Ne može se isto reći za fiat valute, koje su same relativno nova povijesna anomalija. Od njihovog početka, fiat valute su imale gotovo univerzalni smjer prema bezvrijednosti. Korištenje inflacije kao podmuklog načina za nevidljivo oporezivanje građana je vječita kušnja kojoj se skoro nijedna država u povijesti nije mogla oduprijeti. Ako je 20. stoljeće, u kojem je fiat novac dominirao globalni monetarni poredak, demonstriralo neku ekonomsku istinu, to je onda bila ta da ne možemo računati na fiat novac da održi vrijednost u dužem ili srednjem vremenskom periodu. Bitcoin, usprkos svojoj novosti, je preživio dovoljno testova tržišta da postoji velika vjerojatnost da neće nestati kao vrijedno dobro. Nadalje, Lindy efekt govori da što duže Bitcoin bude korišten, to će veća biti vjera u njega i njegovu sposobnost da nastavi postojati dugo u budućnost. Drugim riječima, društvena vjera u monetarno dobro je asimptotička, kao u grafu ispod:

Ako Bitcoin preživi prvih 20 godina, imat će gotovo sveopće povjerenje da će trajati zauvijek, kao što ljudi vjeruju da je internet trajna stvar u modernom svijetu.
Otpor na cenzuru
Jedan od najbitnijih izvora za ranu potražnju bitcoina bila je njegova upotreba u ilegalnoj kupovini i prodaji droge. Mnogi su zato pogrešno zaključili da je primarna potražnja za bitcoinima utemeljena u njihovoj prividnoj anonimnosti. Međutim, Bitcoin nije anonimna valuta; svaka transakcija na mreži je zauvijek zapisana na javnom blockchainu. Povijesni zapis transakcija dozvoljava forenzičkoj analizi da identificira izvore i tijek sredstava. Takva analiza dovela je do uhićenja počinitelja zloglasne MtGox pljačke. Premda je istina da dovoljno oprezna i pedantna osoba može sakriti svoj identitet koristeći Bitcoin, to nije razlog zašto je Bitcoin bio toliko popularan u trgovini drogom.
Ključno svojstvo koje čini Bitcoin najboljim za takve aktivnosti je njegova agnostičnost i nepotrebnost za dozvolom (“premissionlessness”) na mrežnoj razini. Kada se bitcoini prenose na Bitcoin mreži, ne postoji nitko tko dopušta transakcije. Bitcoin je distribuirana peer-to-peer (korisnik-korisniku) mreža, i samim time dizajnirana da bude otporna na cenzuru. Ovo je u velikom kontrastu sa fiat bankarskim sustavom, u kojem države reguliraju banke i ostale institucije prijenosa novca, kako bi one prijavljivale i sprječavale protuzakonito korištenje monetarnih dobara. Klasičan primjer regulacije novca su kontrole kapitala. Npr., bogati milijunaš će vrlo teško prenijeti svoje bogatstvo u novu zemlju, kada bježi iz opresivnog režima. Premda zlato nije izdano i proizvedeno od države, njegova fizička priroda ga čini teško prenosivim kroz prostor, i samim time ga je daleko lakše regulirati nego Bitcoin. Indijski Akt kontrole zlata je primjer takve regulacije.
Bitcoin je odličan u većini gore navedenih svojstava, što mu omogućava da bude marginalno bolji od modernih i drevnih monetarnih dobara, te da pruži poticaje za svoje rastuće društveno usvajanje. Specifično, moćna kombinacija otpornosti na cenzuru i apsolutne oskudnosti bila je velika motivacija za bogate ulagače koji su uložili dio svojeg bogatstva u Bitcoin.
Evolucija novca
U modernoj monetarnoj ekonomiji postoji opsesija sa ulogom novca kao medija razmjene. U 20. stoljeću, države su monopolizirale izdavanje i kontrolu novca i kontinuirano potkopavale njegovo svojstvo spremišta vrijednosti, stvarajući lažno uvjerenje da je primarna svrha novca biti medij razmjene. Mnogi su kritizirali Bitcoin, govoreći da je neprikladan da bude novac zato što mu je cijena bila previše volatilna za medij razmjene. No, novac je uvijek evoluirao kroz etape; uloga spremišta vrijednosti je dolazila prije medija razmjene. Jedan od očeva marginalističke ekonomije, William Stanley Jevons, objašnjava:
"Povijesno govoreći… čini se da je zlato prvo služilo kao luksuzni metal za ukras; drugo, kao sačuvana vrijednost; treće, kao medij razmjene; i konačno, kao mjerilo vrijednosti."
U modernoj terminologiji, novac uvijek evoluira kroz četiri stadija:
- Kolekcionarstvo: U prvoj fazi svoje evolucije, novac je tražen samo zbog svojih posebnih svojstava, uglavnom zbog želja onog koji ga posjeduje. Školjke, perlice i zlato su bili sakupljani prije nego su poprimili poznatije uloge novca.
- Spremište vrijednosti: Jednom kada je novac tražen od dovoljnog broja ljudi, biti će prepoznat kao način za čuvanje i spremanje vrijednosti kroz vrijeme. Kada neko dobro postane široko korišteno kao spremište vrijednosti, njegova kupovna moć raste sa povećanom potražnjom za tu svrhu. Kupovna moć spremišta vrijednosti će u jednom trenutku doći do vrhunca, kada je dovolno rašireno i broj novih ljudi koji ga potražuju splasne.
- Sredstvo razmjene: Kada je novac potpuno etabliran kao spremište vrijednosti, njegova kupovna moć se stabilizira. Nakon toga, postane prikladno sredstvo razmjene zbog stabilnosti svoje cijene. U najranijim danima Bitcoina, mnogi ljudi nisu shvaćali koju buduću cijenu plaćaju koristeći bitcoine kao sredstvo razmjene, umjesto kao novonastalo spremište vrijednosti. Poznata priča o čovjeku koji je za 10,000 bitcoina (vrijednih oko 94 milijuna dolara kada je ovaj članak napisan) za dvije pizze ilustrira ovaj problem.
- Jedinica računanja vrijednosti: Jednom kada je novac široko korišten kao sredstvo razmjene, dobra će biti vrednovana u njemu, tj. većina cijena će biti izražena u njemu. Uobičajena zabluda je da je većinu dobara moguće zamijeniti za bitcoine danas. Npr., premda je možda moguće kupiti šalicu kave za bitcoine, izlistana cijena nije prava bitcoin cijena; zapravo se radi o cijeni u državnoj valuti koju želi trgovac, preračunatu u bitcoin po trenutnoj tržišnoj cijeni. Kad bi cijena bitcoina pala u odnosu na valutu, vrijednost šalice izražena u bitcoinima bi se povećala. Od trenutka kada trgovci budu voljni prihvaćani bitcoine kao platežno sredstvo, bez obraćanja pažnje na vrijednost bitcoina u državnoj fiat valuti, moći ćemo reći da je Bitcoin zaista postao jedinica računanja vrijednosti.
Monetarna dobra koja još nisu jedinice računanja vrijednosti možemo smatrati “djelomično monetiziranima.” Danas zlato ima takvu ulogu, jer je spremište vrijednosti, ali su mu uloge sredstva razmjene i računanja vrijednosti oduzete intervencijama država. Moguće je također da se jedno dobro koristi kao sredstvo razmjene, dok druga ispunjavaju ostale uloge. To je tipično u zemljama gdje je država disfunkcionalna, npr. Argentina ili Zimbabwe. U svojoj knjizi, Digitalno zlato, Nathaniel Popper piše:
"U Americi, dolar služi trima funkcijama novca: nudi sredstvo razmjene, jedinicu za mjerenje vrijednosti dobara, i mjesto gdje se može čuvati vrijednosti. S druge strane, argentinski peso je korišten kao sredstvo razmjene (za svakodnevne potrebe), ali ga nitko nije koristio kao spremište vrijednosti. Štednja u pesosima bila je ekvivalent bacanja novca. Zato su ljudi svu svoju štednju imali u dolarima, jer je dolar bolje čuvao vrijednost. Zbog volatilnosti pesosa, ljudi su računali cijene u dolarima, što im je pružalo pouzdaniju jedinicu mjerenja kroz vrijeme."
Bitcoin je trenutno u fazi tranzicije iz prvog stadija monetizacije u drugi. Vjerojatno će proći nekoliko godina prije nego Bitcoin pređe iz začetaka spremišta vrijednosti u istinski medij razmjene, i put do tog trenutka je još uvijek pun rizika i nesigurnosti. Važno je napomenuti da je ista tranzicija trajala mnogo stoljeća za zlato. Nitko danas živ nije doživio monetizaciju dobra u realnom vremenu (kroz koju Bitcoin prolazi), tako da nemamo puno iskustva govoriti o putu i načinu na koji će se monetizacija dogoditi.
Put monetizacije
Kroz proces monetizacije, monetarno dobro će naglo porasti u kupovnoj moći. Mnogi su tako komentirali da je uvećanje kupovne moći Bitcoina izgledalo kao “balon” (bubble). Premda je ovaj termin često korišten kako bi ukazao na pretjeranu vrijednosti Bitcoina, sasvim slučajno je prikladan. Svojstvo koje je uobičajeno za sva monetarna dobra jest da je njihova kupovna moć viša nego što se može opravdati samo kroz njihovu uporabnu vrijednost. Zaista, mnogi povijesni novci nisu imali uporabnu vrijednost. Razliku između kupovne moći i vrijednosti razmjene koju bi novac mogao imati za svoju inherentnu korisnost, možemo razmatrati kao “monetarnu premiju.” Kako monetarno dobro prolazi kroz stadije monetizacije (navedene gore), monetarna premija raste. No, ta premija ne raste u ravnoj i predvidivoj liniji. Dobro X, koje je bilo u procesu monetizacije, može izgubiti u usporedbi sa dobrom Y koje ima više svojstava novca, te monetarna premija dobra X drastično padne ili potpuno nestane. Monetarna premija srebra je skoro potpuno nestala u kasnom 19. stoljeću, kada su ga vlade diljem svijeta zamijenile zlatom kao novcem.
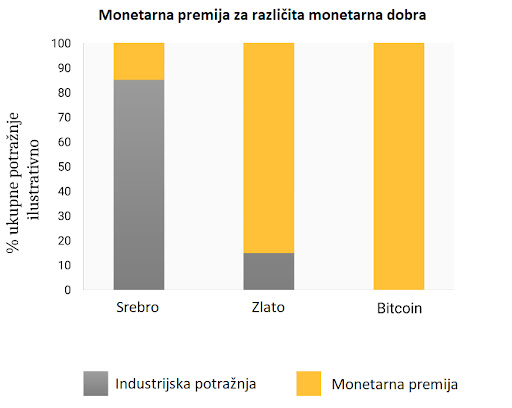
Čak i u odsustvu vanjskih faktora, kao što su intervencije vlade ili druga monetarna dobra, monetarna premija novog novca neće ići predvidivim putem. Ekonomist Larry White primijetio je:
"problem sa pričom “balona,” naravno, je da je ona konzistentna sa svakim putem cijene, i time ne daje ikakvo objašnjenje za specifičan put cijene"
Proces monetizacije opisuje teorija igara; svaki akter na tržištu pokušava predvidjeti agregiranu potražnju ostalih aktera, i time buduću monetarnu premiju. Zato što je monetarna premija nevezana za inherentnu korisnost, tržišni akteri se uglavnom vode za prošlim cijenama da bi odredili je li neko dobro jeftino ili skupo, i žele li ga kupiti ili prodati. Veza trenutne potražnje sa prošlim cijenama naziva se “ovisnost o putu” (path dependence); ona je možda najveći izvor konfuzije u shvaćanju kretanja cijena monetarnih dobara.
Kada kupovna moć monetarnog dobra naraste zbog većeg i šireg korištenja, očekivanja tržišta o definicijama “jeftinog” i “skupog” se mijenjaju u skladu s time. Slično tome, kada cijena monetarnog dobra padne, očekivanja tržišta mogu se promijeniti u opće vjerovanje da su prethodne cijene bile “iracionalne” ili prenapuhane. Ovisnost o putu novca ilustrirana je riječima poznatog upravitelja fondova s Wall Streeta, Josha Browna:
"Kupio sam bitcoine kada su koštali $2300, i to mi se udvostručilo gotovo odmah. Onda sam počeo govoriti kako “ne mogu kupiti još” dok im je cijena rasla, premda sam znao da je to razmišljanje bazirano samo na cijenu po kojoj sam ih kupio. Kasnije, kada je cijena pala zbog kineske regulacije mjenjačnica, počeo sam si govoriti, “Odlično, nadam se da će još pasti da mogu kupiti još.”"
Istina leži u tome da su ideje “jeftinog” i “skupog” zapravo besmislene kada govorimo o monetarnim dobrima. Cijena monetarnog dobra ne reflektira njegovu stopu rasprostanjenosti ili korisnosti, nego mjeru koliko je ono široko prihvaćeno da ispuni razne uloge novca.
Dodatna komplikacija u ovom aspektu novca je činjenica da tržišni akteri ne djeluju samo kao nepristrani promatrači koji pokušavaju kupiti i prodati u iščekivanju budućih kretanja monetarne premije, nego i kao aktivni proponenti. Pošto ne postoji objektivno “točna” monetarna premija, širiti dobar glas o superiornijim svojstvima nekog monetarnog dobra je efektivnije nego za obična dobra, čija vrijednost je u konačnici vezana na njegovu osnovnu korisnost. Religiozni zanos sudionika na Bitcoin tržištu vidljiv je na raznim internetskim forumima, gdje Bitcoineri aktivno promoviraju benefine Bitcoina i bogatstvo koje je moguće ostvariti investiranjem u njega. Promatrajući Bitcoin tržište, Leigh Drogen komentira:
"To je prepoznatljivo svima kao religija - priča koju si pričamo i oko koje se slažemo. Religija je krivulja na grafu prihvaćanja o kojoj trebamo razmišljati. Sustav je gotovo savršen - onog trenutka kada netko pristupi krugu Bitcoinera, to će reći svima i nastaviti širiti riječ. Onda njihovi prijatelji pristupe i nastave širiti riječ."
Premda usporedba sa religijom može staviti Bitcoin u iracionalno svjetlo, potpuno je racionalno za individualnog vlasnika da širi dobru vijest o superiornom monetarnom dobru, i za šire društvo da se standardizira oko njega. Novac djeluje kao temelj za svu trgovinu i štednju; tako da prihvaćanje superiornog oblika novca ima ogromne multiplicirajuće benefite za stvaranje bogatstva za sve članove društva.
Oblik monetizacije
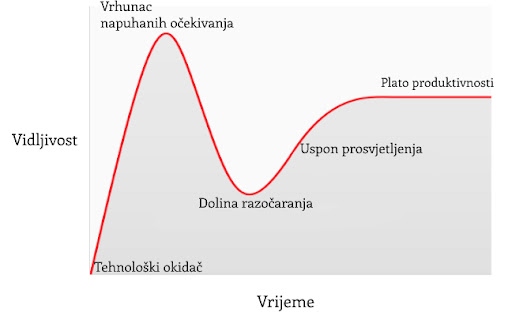
U članku o Spekulativnom prihvaćanju Bitcoina / teorije cijene, Michael Casey postulira da rastući Gartner hype ciklusi predstavljaju faze standardne S-krivulje prihvaćanja novih tehnologija, koje su bile prisutne kod mnogih transformacijskih tehnologija dok su postajale uobičajene u društvu.
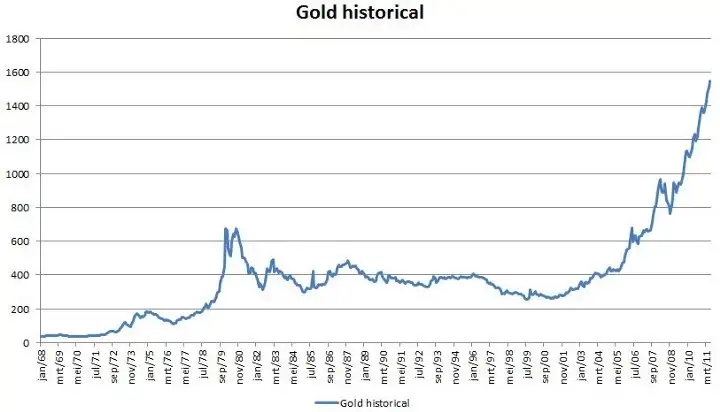
Svaki Gartner hype ciklus počinje sa eksplozijom entuzijazma za novom tehnologijom, a cijenu podižu oni sudionici na tržištvu koji su “dostupni” u toj fazi. Najraniji kupci u Gartner hype ciklusu obično imaju jaku vjeru o transformacijskoj prirodi tehnologije u koju ulažu. S vremenom, tržište dosegne vrhunac entuzijazma kako se količina novih kupaca iscrpljuje, te kupovinom počnu dominirati spekulatori koji su više zainteresirani u brze profite nego u samu tehnologiju.
Nakon vrha hype ciklusa, cijene rapidno padaju dok spekulativno ludilo ustupa mjesto očajavanju, javnoj poruzi i osjećaju da tehnologija nije uopće bila transformacijska. S vremenom, cijena dosegne dno i formira plato na kojem se originalnim ulagačima, koji su imali snažno uvjerenje, pridružuju nove grupe ljudi koji su izdržali bol kraha cijena i koji cijene važnost same tehnologije.
Plato traje neko vrijeme i formira, kako Casey kaže, “stabilnu, dosadnu dolinu.” Za ovo vrijeme, javni interes za tehnologiju opada, no nastaviti će se razvijati i snažna zajednica uvjerenja će polako rasti. Tada, postavlja se nova baza za sljedeću iteraciju hype ciklusa, dok vanjski promatrači prepoznaju da tehnologija i dalje postoji i da ulaganje u nju možda nije onoliko rizično kao što se činilo za vrijeme pada cijene. Sljedeća iteracija hype ciklusa donosi mnogo veći broj novih ljudi, pa je i ciklus daleko veći u svojoj magnitudi.
Jako mali broj ljudi koji sudjeluju u Gartner hype ciklusu će točno predvidjeti koliko će visoko cijena porasti za vrijeme ciklusa. Cijene često dosegnu razine koje bi se činile apsurdnima većini ulagača u raniji stadijima ciklusa. Kada ciklus završi, mediji tipično atribuiraju pad cijene nekoj od aktualnih drušvenih tema. Premda takva tema može biti okidač pada, ona nikad nije temeljni razlog zašto ciklus završava. Gartner hype ciklusi završavaju kada je količina dostupnih novih sudionika na tržištu iscrpljena.
Zanimljivo je da je i zlato nacrtalo klasičan graf Gartner hype ciklusa od kasnih 1970-ih do ranih 2000-ih. Moguće je spekulirati da je hype ciklus osnovna socijalna dinamika oko procesa monetizacije.
Gartner kohorte
Od početka trgovanja Bitcoina na mjenjačnicama 2010. godine, Bitcoin tržište je svjedočilo četirima velikim Gartner hype ciklusima. U retrospektivi, možemo vrlo precizno identificirati grupe cijena prethodnih hype ciklusa Bitcoin tržišta. Također, možemo kvalitativno odrediti kohorte ulagača koje su povezane sa svakom iteracijom prethodnih ciklusa.
$ 0–$ 1 (2009. – 3. mjesec 2011.): Prvi hype ciklus u Bitcoin tržištu dominirali su kriptografi, računalni znanstvenici i cypherpunkovi koji su od početka bili spremni razumijeti važnost nevjerojatnog izuma Satoshija Nakamotoa, i koji su bili pioniri u potvrđivanju da Bitcoin protokol nema tehničkih mana.
$ 1–$ 30 (3. mjesec 2011. – 7. mjesec. 2011.): Drugi ciklus privukao je rane entuzijaste oko novih tehnologija kao i stabilan pritok ideološki motiviranih ulagača koji su bili oduševljeni idejom novca odvojenog od države. Libertarijanci poput Rogera Vera došli su u Bitcoin zbog aktivnog anti-institucionalnog stava, i mogućnosti koju je nova tehnologija obećavala. Wences Casares, briljantni i dobro povezani serijski poduzetnik, bio je također dio drugog Bitcoin hype ciklusa te je širio riječ o Bitcoinu među najprominentnijim tehnolozima i ulagačima u Silicijskoj Dolini.
$ 250–$ 1100 (4. mjesec 2013. – 12. mjesec 2013.): Treći hype ciklus doživio je ulazak ranih generalnih i institucionalnih ulagača koji su bili voljni uložiti trud i riskirati kroz užasno komplicirane kanale likvidnosti kako bi kupili bitcoine. Primaran izvor likvidnosti na tržištu za vrijeme ovog perioda bio je MtGox, mjenjačnica bazirana u Japanu, koju je vodio notorno nesposobni i beskrupulozni Mark Karpeles, koji je kasnije završio i u zatvoru zbog svoje uloge u kolapsu MtGoxa.
Valja primijetiti da je rast Bitcoinove cijene za vrijeme spomenuti hype ciklusa većinom povezano sa povećanjem likvidnosti i lakoćom sa kojom su ulagači mogli kupiti bitcoine. Za vrijeme prvog hype ciklusa, nisu postojale mjenjačnice; akvizicija bitcoina se odvijala primarno kroz rudarenje (mining) ili kroz izravnu razmjenu sa onima koju su već izrudarili bitcoine. Za vrijeme drugog hype ciklusa, pojavile su se rudimentarne mjenjačnice, no nabavljanje i osiguravanje bitcoina na ovim mjenjačnicama bilo je previše kompleksno za sve osim tehnološki najsposobnijih ulagača. Čak i za vrijeme trećeg hype ciklusa, ulagači koju su slali novac na MtGox kako bi kupili bitcoine su morali raditi kroz značajne prepreke. Banke nisu bile voljne imati posla sa mjenjačnicom, a oni posrednici koji su nudili usluge transfera bili su često nesposobni, kriminalni, ili oboje. Nadalje, mnogi koji su uspjeli poslati novac MtGoxu, u konačnici su morali prihvatiti gubitak svojih sredstava kada je mjenjačnica hakirana i kasnije zatvorena.
Tek nakon kolapsa MtGox mjenjačnice i dvogodišnje pauze u tržišnoj cijeni Bitcoina, razvili su se zreli i duboki izvori likvidnosti; primjeri poput reguliranih mjenjačnica kao što su GDAX i OTC brokeri kao Cumberland mining. Dok je četvrti hype ciklus započeo 2016. godine, bilo je relativno lako običnim ulagačima kupiti i osigurati bitcoine.
$ 1100 – $ 19600? (2014. –?):
U trenutku pisanja ovog teksta, tržište Bitcoina je prolazilo svoj četvrti veliki hype ciklus. Sudjelovanje u ovom hype ciklusu dominirala je ona skupina koju je Michael Casey opisao kao “rana većina” običnih i institucionalnih ulagača.
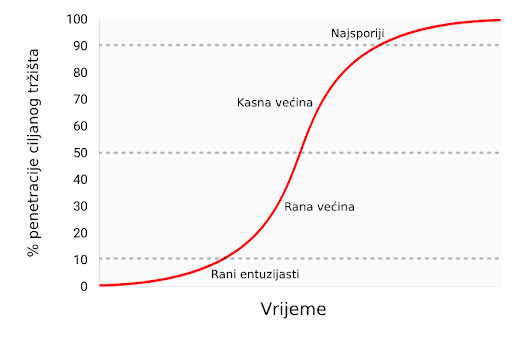
Kako su se izvori likvidnosti produbljivali i sazrijevali, veliki institucionalni ulagači sada imaju priliku sudjelovati kroz regulirana “futures” tržišta. Dostupnosti takvih tržišta stvara put ka kreaciji Bitcoin ETF-a (exchange traded fund) (fond na slobodnom tržištu), koji će onda pokrenuti “kasnu većinu” i “najsporije” u sljedećim hype ciklusima.
Premda je nemoguće predvidjeti točan efekt budućih hype ciklusa, razumno je očekivati da će najviša točka biti između $ 20.000 i $ 50.000 (2021. zenit je bio preko $ 69.000). Znatno više od ovog raspona, i Bitcoin bi imao znatan postotak ukupne vijednosti zlata (zlato i Bitcoin bi imali jednaku tržišnu kapitalizaciju kada bi bitcoini vrijedili oko $ 380.000 u trenutku pisanja ovog teksta). Značajan postotak vrijednosti zlata dolazi od potražnje centralnih banaka, te je malo vjerojatno da će centralne banke ili suverene države sudjelovati u trenutnom hype ciklusu.
Ulazak suverenih država u Bitcoin
Bitcoinov zadnji Gartner hype ciklus će započeti kada ga suverene države počnu akumulirati kao dio svojih rezervi stranih valuta. Tržišna kapitalizacija Bitcoina je trenutno premala da bismo ga smatrali značajnim dodatkom rezervama većini zemalja. No, kako se interes u privatnom sektoru povećava i kapitalizacija Bitcoina se približi trilijunu dolara, postat će dovoljno likvidan za većinu država. Prva država koja službeno doda bitcoine u svoje rezerve će vjerojatno potaknuti stampedo ostalih da učine isto. Države koje su među prvima u usvajanju Bitcoina imat će najviše benefita u svojim knjigama ako Bitcoin u konačnici postane globalna valuta (global reserve currency). Nažalost, vjerojatno će države sa najjačom izvršnom vlasti - diktature poput Sjeverne Koreje - biti najbrže u akumulaciji bitcoina. Neodobravanje prema takvim državama i slaba izvršna tijela zapadnjačkih demokracija uzrokovat će sporost i kašnjenje u akumulaciji bitcoina za njihove vlastite rezerve.
Velika je ironija u tome što je SAD trenutno jedna od regulatorno najotvorenijih nacija prema Bitcoinu, dok su Kina i Rusija najzatvorenije. SAD riskira najviše, geopolitički, ako bi Bitcoin zamijenio dolar kao svjetska rezervna valuta. U 1960-ima, Charles de Gaulle je kritizirao “pretjeranu privilegiju” (“exorbitant privilege”) koju su SAD imale u međunarodnom monetarnom poretku, postavljenom kroz Bretton Woods dogovor 1944. godine. Ruska i kineska vlada još ne shvaćaju geo-strateške benefite Bitcoina kao rezervne valute, te se trenutno brinu o efektima koje bi mogao imati na njihova unutarnja tržišta. Kao de Gaulle u 1960-ima, koji je prijetio SAD-u povratkom na klasični standard zlata, Kinezi i Rusi će s vremenom uvidjeti korist u velikoj poziciji u Bitcoinu - spremištu vrijednosti bez pokrića ijedne vlade. Sa najvećom koncentracijom rudara Bitcoina u Kini (2017.), kineska vlada već ima znatnu potencijalnu prednost u stavljanju bitcoina u svoje rezerve.
SAD se ponosi svojim statusom nacije inovatora, sa Silicijskom dolinom kao krunom svoje ekonomije. Dosad, Silicijska dolina je dominirala konverzacijom usmjerenom prema regulaciji, i poziciji koju bi ona treba zauzeti prema Bitcoinu. No, bankovna industrija i federalna rezerva SAD-a (US Federal Reserve, Fed) napokon počinju uviđati egzistencijalnu prijetnju koju Bitcoin predstavlja za američku monetarnu politiku, postankom globalne rezervne valute. Wall Street Journal, jedan od medijskih glasova federalne reserve, izdao je komentar o Bitcoinu kao prijetnji monetarnoj politici SAD-a:
"Postoji još jedna opasnost, možda i ozbiljnija iz perspektive centralnih banaka i regulatora: bitcoin možda ne propadne. Ako je spekulativni žar u kriptovalutu samo prvi pokazatelj njezinog šireg korištenja kao alternative dolaru, Bitcoin će svakako ugroziti monopol centralnih banaka nad novcem."
U narednim godinama, možemo očekivati veliku borbu između poduzetnika i inovatora u Silicijskoj dolini, koji će pokušavati čuvati Bitcoin od državne kontrole s jedne strane, i bankovne industrije i centralnih banaka koje će učiniti sve što mogu da bi regulirale Bitcoin kako bi spriječile znatne promjene u svojoj industriji i moći izdavanja novca, s druge.
Prijelaz na medij razmjene
Monetarno dobro ne može postati opće prihvaćen medij razmjene (standardna ekonomska definicija za “novac”) prije nego je vrednovano od širokog spektra ljudi; jednostavno, dobro koje nije vrednovano neće biti prihvaćeno u razmjeni. Kroz proces generalnog rasta vrijednosti, i time postanka spremišta vrijednosti, monetarno dobro će brzo narasti u kupovnoj moći, i time stvoriti cijenu za korištenje u razmjeni. Samo kada ta cijena rizika mijenjanja spremišta vrijednosti padne dovoljno nisko, može dobro postati opće prihvaćen medij razmjene.
Preciznije, monetarno dobro će biti prikladno kao medij razmjene samo kada je suma cijene rizika i transakcijske cijene u razmjeni manja nego u trgovini bez tog dobra.
U društvu koje vrši robnu razmjenu, prijelaz spremišta vrijednosti u medij razmjene može se dogoditi čak i onda kada monetarno dobro raste u kupovnoj moći, zato što su transakcijski troškovi robne razmjene iznimno visoki. U razvijenoj ekonomiji, u kojoj su troškovi razmjene niski, moguće je za mladu i rapidno rastućnu tehnologiju spremišta vrijednosti, poput Bitcoina, da se koristi kao medij razmjene, doduše na ograničen način. Jedan primjer je ilegalno tržište droge, gdje su kupci voljni žrtvovati oportunu cijenu čuvanja bitcoina kako bi umanjili znatan rizik kupovine droge koristeći fiat novac.
Postoje međutim velike institucionalne barijere da novonastalo spremište vrijednosti postane sveopće prihvaćen medij razmjene u razvijenom društvu. Države koriste oporezivanje kao moćnu metodu zaštite svojeg suverenog novca protiv rivalskih monetarnih dobara. Ne samo da suvereni novac ima prednost konstantnog izvora potražnje, zato što je porez moguće platiti jedino u njemu, nego su i rivalska monetarna dobra oporezana pri svakoj razmjeni za vrijeme rastuće cijene. Ova metoda oporezivanja stvara znatan otpor korištenju spremišta vrijednosti kao medija razmjene.
Ovakvo sabotiranje tržišnih monetarnih dobara nije nepremostiva barijera za njihovo prihvaćanje kao općeg medija razmjene. Ako ljudi izgube vjeru u suvereni novac, njegova vrijednost može rapidno propasti kroz proces zvan hiperinflacija. Kada suvereni novac prolazi kroz hiperinflaciju, njegova vrijednost propadne prvo u usporedbi sa najlikvidnijim dobrima u društvu, kao što je zlato ili stabilna strana valuta (američki dolar npr.), ako su ona dostupna. Kada nema likvidnih dobara ili ih ima premalo, novac u hiperinflaciji kolabira u usporedbi sa stvarnim dobrima, kao što su nekretnine ili upotrebljiva roba. Arhetipska slika hiperinflacije je trgovina sa praznim policama - potrošači brzo bježe iz propadajuće vrijednosti novca svoje nacije.

Nakon dovoljno vremena, kada je vjera potpuno uništena za vrijeme hiperinflacije, suvereni novac više nitko ne prihvaća, te se društvo može vratiti na robnu razmjenu, ili će doživjeti potpunu zamjenu monetarne jedinice za sredstvo razmjene. Primjer ovog procesa bila je zamjena zimbabveanskog dolara za američki dolar. Takva promjena suverenog novca za stranu valutu je dodatno otežana relativnom oskudnošću strane valute i odsustvom stranih bankarskih institucija koje pružaju likvidnost tržištu.
Sposobnost lakog prenošenja bitcoina preko granica i odsustvo potrebe za bankarskim sustavom čine Bitcoin idealnim monetarnim dobrom za one ljude koji pate pod hiperinflacijom. U nadolazećim godinama, kako fiat valute nastave svoj povijesni trend ka bezvrijednosti, Bitcoin će postati sve popularniji izbor za ušteđevine ljudi diljem svijeta. Kada je novac nacije napušten i zamijenjen Bitcoinom, Bitcoin će napraviti tranziciju iz spremišta vrijednosti u tom društvu u opće prihvaćeno sredstvo razmjene. Daniel Krawicz stvorio je termin “hiperbitcoinizacija” da bi opisao ovaj proces.
Učestala pogrešna shvaćanja
Većina ovog članka usredotočila se na monetarnu prirodu Bitcoina. Sa tim temeljima možemo adresirati neke od najčešćih nerazumijevanja u Bitcoinu.
Bitcoin je balon (bubble)
Bitcoin, kao sva tržišna monetarna dobra, posjeduje monetarnu premiju. Ona često rezultira uobičajenom kritikom da je Bitcoin samo “balon.” No, sva monetarna dobra imaju monetarnu premiju. Naprotiv, ta monetarna premija (cijena viša od one koju diktira potražnja za dobrom kao korisnim) je upravo karakteristična za sve oblike novca. Drugim riječima, novac je uvijek i svuda balon. Paradoksalno, monetarno dobro je istovremeno balon i ispod vrijednosti ukoliko je u ranijim stadijima općeg prihvaćanja kao novac.
Bitcoin je previše volatilan
Volatilnost cijene Bitcoina je funkcija njegovog nedavnog nastanka. U prvih nekoliko godina svojeg postojanja, Bitcoin se ponašao kao mala dionica, i svaki veliki kupac - kao npr. braća Winklevoss - mogao je uzrokovati veliki skok u njegovoj cijeni. No, kako su se prihvaćenost i likvidnost povećavali kroz godine, volatilnost Bitcoina je srazmjerno smanjila. Kada Bitcoin postigne tržišnu kapitalizaciju (vrijednost) zlata, imat će sličnu volatilnost kao i zlato. Kako Bitcoin nastavi rasti, njegova volatilnost će se smanjiti do razine koja ga čini prikladnim za široko korištenje kao medij razmjene. Kao što je prethodno rečeno, monetizacija Bitcoina se odvija u seriji Gartner hype ciklusa. Volatilnost je najniža za vrijeme vrhunaca i dolina unutar ciklusa. Svaki hype ciklus ima nižu volatilnost od prethodnih, zato što je likvidnost tržišta veća.
Cijene transakcija su previsoke
Novija kritika Bitcoin mreže je ta da ju je povećanje cijena prijenosa bitcoina učinilo neprikladnom za sustav plaćanja. No, rast u cijenama transakcija je zdrav i očekivan. One su nužne za plaćanje bitcoin minera (rudara), koji osiguravaju mrežu validacijom transakcija. Rudare se plaća kroz cijene transakcija ili kroz blok-nagrade, koje su inflacijska subvencija od trane trenutnih vlasnika bitcoina.
S obzirom na Bitcoinovu fiksnu proizvodnju (monetarna politika koja ga čini idealnim za spremanje vrijednosti), blok-nagrade će s vremenom nestati i mrežu će se u konačnici morati osiguravati kroz cijene transakcija. Mreža sa “niskim” cijenama transakcija je mreža sa slabom sigurnosti i osjetljiva na vanjsku intervenciju i cenzuru. Oni koji hvale niske cijene Bitcoinovih alternative zapravo niti ne znajući opisuju slabosti tih takozvanih “alt-coina.”
Površan temelj kritika Bitcoinovih “visokih” cijena transakcija je uvjerenje da bi Bitcoin trebao biti prvo sustav plaćanja, i drugo spremište vrijednosti. Kao što smo vidjeli kroz povijest novca, ovo uvjerenje je naopako. Samo onda kada Bitcoin postane duboko ukorijenjeno spremište novca može biti prikladan kao sredstvo razmjene. Nadalje, kada oportunitetni trošak razmjene bitcoina dođe na razinu koja ga čini prikladnim sredstvom razmjene, većina trgovine neće se odvijati na samoj Bitcoin mreži, nego na mrežama “drugog sloja” (second layer) koje će imati niže cijene transakcija. Takve mreže, poput Lightning mreže, služe kao moderna verzija zadužnica koje su korištene za prijenos vlasničkih papira zlata u 19. stoljeću. Banke su koristile zadužnice zato što je prijenos samog metala bio daleko skuplji. Za razliku od takvih zadužnica, Lightning mreža će omogućavati nisku cijenu prijenosa bitcoina bez potrebe za povjerenjem prema trećoj strani, poput banaka. Razvoj Lightning mreže je tehnološka inovacija od izuzetne važnosti u povijesti Bitcoina, i njezina vrijednost će postati očita u narednim godinama, kako je sve više ljudi bude razvijalo i koristilo.
Konkurencija
Pošto je Bitcoin softverski protokol otvorenog tipa (open-source), oduvijek je bilo moguće kopirati softver i imitirati mrežu. Kroz godine nastajali su mnogi imitatori, od identičnih kopija, kao Litecoin, do kompleksnijih varijanti kao što je Ethereum, koje obećavaju arbitrarno kompleksne ugovorne mehanizme koristeći decentralizirani računalni sustav. Česta kritika Bitcoinu od strane ulagača je ta da on ne može zadržati svoju vrijednost kada je vrlo lako stvoriti konkurente koji mogu lako i brzo u sebi imati najnovije inovacije i softverske funkcionalnosti.

Greška u ovom argumentu leži u manju takozvanog “mrežnog efekta” (network effect), koji postoji u prvoj i dominantnoj tehnologiji u nekom području. Mrežni efekt - velika vrijednost korištenja Bitcoina samo zato što je već dominantan - je važno svojstvo samo po sebi. Za svaku tehnologiju koja posjeduje mrežni efekt, to je daleko najvažnije svojstvo koje može imati.
Za Bitcoin, mrežni efekt uključuje likvidnost njegovog tržišta, broj ljudi koji ga posjeduju, i zajednicu programera koji održavaju i unaprjeđuju njegov softver i svjesnost u javnosti. Veliki ulagači, uključujući države, će uvijek prvo tražiti najlikvidnije tržište, kako bi mogli ući i izaći iz tržišta brzo, i bez utjecanja na cijenu. Programeri će se pridružiti dominantnoj programerskoj zajednici sa najboljim talentom, i time pojačati samu zajednicu. Svjesnost o brendu sama sebe pojačava, pošto se nadobudni konkurenti Bitcoina uvijek spominju u kontekstu Bitcoina kao takvog.
Raskrižje na putu (fork)
Trend koji je postao popularan 2017. godine nije bio samo imitacija Bitcoinovog softvera, nego kopiranje potpune povijesti njegovih prošlih transakcija (cijeli blockchain). Kopiranjem Bitcoinovog blockchaina do određene točke/bloka i odvajanjem sljedećih blokova ka novoj mreži, u procesu znanom kao “forking” (odvajanje), Bitcoinovi konkurenti su uspjeli riješiti problem distribuiranja svojeg tokena velikom broju korisnika.

Najznačajniji takav fork dogodio se 1. 8. 2017. godine, kada je nova mreža nazvana Bitcoin Cash (Bcash) stvorena. Vlasnik N količine bitcoina prije 1.8.2017. bi onda posjedovao N bitcoina i N BCash tokena. Mala, ali vrlo glasna zajednica Bcash proponenata je neumorno pokušavala prisvojiti Bitcoinov brend i ime, imenujući svoju novu mrežu Bitcoin Cast i pokušavajući uvjeriti nove pridošlice u Bitcoin da je Bcash “pravi” Bitcoin. Ti pokušaji su većinom propali, i taj neuspjeh se vidi u tržišnim kapitalizacijama dviju mreža. No, za nove ulagače, i dalje postoji rizik da bi konkurent mogao kopirati Bitcoin i njegov blockchain i tako uspjeti u preuzimanju tržišne kapitalizacije, te postati de facto Bitcoin.
Moguće je uočiti važno pravilo gledajući velike forkove u prošlosti Bitcoin i Ethereum mreža. Većina tržišne kapitalizacije odvijat će se na mreži koja zadrži najviši stupanj talenta i aktivnosti u zajednici programera. Premda se na Bitcoin može gledati kao na nov i mlad novac, on je također računalna mreža koja počiva na softveru, kojeg se pak treba održavati i poboljšavati. Kupovina tokena na mreži koja ima malo neiskusnih programera bilo bi kao kupovati kopiju Microsoft Windowsa na kojoj rade lošiji programeri. Jasno je vidljivo iz povijesti forkova koji su se odvili 2017. godine da su najbolji računalni i kriptografski stručnjaci posvećeni razvoju originalnog Bitcoina, a ne nekoj od rastućeg broja imitacija koje su se izrodile iz njega.
Stvarni rizici
Premda su uobičajene kritike upućene Bitconu od strane medija i ekonomske profesije krive i bazirane na netočnom shvaćanju novca, postoje pravi i značajni rizici kod ulaganja u Bitcoin. Bilo bi mudro za novog Bitcoin ulagača da shvati ove rizike prije potencijalnog ulaganja.
Rizik protokola
Bitcoin protokol i kriptografski sastavni dijelovi na kojima je sagrađen potencijalno imaju dosad nepronađenu grešku u svom dizajnu, ili mogu postati nesigurni razvojem kvantnih računala. Ako se pronađe greška u protokolu, ili neka nova metoda računarstva učini mogućim probijanje kriptografskih temelja Bitcoina, vjera u Bitcoin biti će znatno narušena. Rizik protokola bio je najviši u ranim godinama razvoja Bitcoina, kada je još uvijek bilo nejasno, čak i iskusnim kriptografima, je li Satoshi Nakamoto zaista riješio problem bizantskih generala (Byzantine Generals’ Problem). Brige oko ozbiljnih grešaka u Bitcoin protokolu nestale su kroz godine, no uzevši u obzir njegovu tehnološku prirodu, rizik protokola će uvijek ostati u Bitcoinu, makar i kao izuzetak.
Propadanje mjenjačnica
Time što je decentraliziran, Bitcoin je pokazao značajnu otpornost, suočen sa brojnim pokušajima raznih vlada da ga reguliraju ili unište. No, mjenjačnice koje trguju bitcoinima za fiat valute su centralizirani entiteti i podložne regulacijama i zatvaranju. Bez mjenjačnica i volje bankara da s njima posluju, proces monetizacije Bitcoina bio bi ozbiljno usporen, ako ne i potpuno zaustavljen. Iako postoje alternativni izvori likvidnosti za Bitcoin, poput “over-the-counter” brokera i decentraliziranih tržišta za kupovinu i prodaju bitcoina, kritičan proces otkrivanja i definiranja cijene se odvija na najlikvidnijim mjenjačnicama, koje su sve centralizirane.
Jedan od načina za umanjivanje rizika gašenja mjenjačnica je geografska arbitraža. Binance, jedna od velikih mjenjačnica iz Kine, preselila se u Japan nakon što joj je kineska vlada zabranila operiranje u Kini. Vlade su također oprezne kako ne bi ugušile novu industriju koja je potencijalno značajna kao i internet, i time predale nevjerojatnu konkurentnu vrijednost drugim nacijama.
Samo kroz koordinirano globalno ukidanje Bitcoin mjenjačnica bi proces monetizacije mogao biti zaustavljen. Trenutno smo u utrci; Bitcoin raste i postaje sve rašireniji, i doći će do trenutka kada bi potpuno ukidanje mjenjačnica postalo politički neizvedivo - kao i gašenje interneta. Mogućnost takvog ukidanja je još uvijek realna, i valja je uzeti u obzir pri ulaganju u Bitcoin. Kao što je gore objašnjeno, suverene vlade se polako bude i uviđaju prijetnju koju predstavlja neovisna digitalna valuta otporna na cenzuru, za njihovu monetarnu politiku. Otvoreno je pitanje hoće li išta poduzeti da odgovore ovoj prijetnji prije nego Bitcoin postane toliko utvrđen i raširen da politička akcija postane nemoćna i ne-efektivna.
Zamjenjivost
Otvorena i transparentna priroda Bitcoin blockchaina omogućava državama da proglase specifične bitcoine “okaljanima” zbog njihovog korištenja u određenim aktivnostima. Premda Bitcoin, na protokolarnoj razini, ne diskriminira transakcije na ikoji način, “okaljani” bitcoini bi mogli postati bezvrijedni ako bi ih regulacije proglasile ilegalnima i neprihvatljivima za mjenjačnice ili trgovce. Bitcoin bi tada izgubio jedno od kritičnih svojstava monetarnog dobra: zamjenjivost.
Da bi se ovaj problem riješio i umanjio, biti će potrebna poboljšanja na razini protokola kako bi se poboljšala privatnost transakcija. Premda postoji napredak u ovom smjeru, prvi put primjenjen u digitalnim valutama kao što su Monero i Zcash, potrebno je napraviti značajne tehnološke kompromise između efikasnosti i kompleksnosti Bitcoina i njegove privatnosti. Pitanje ostaje otvoreno je li moguće dodati nova svojstva privatnosti na Bitcoin, na način koji neće kompromitirati njegovu korisnost kao novca.
Zaključak
Bitcoin je novonastali novac koji je u procesu transformacije iz sakupljačkog dobra u spremište vrijednosti. Kao neovisno monetarno dobro, moguće je da će u budućnosti postati globalan novac, slično kao zlato za vrijeme 19. stoljeća. Prihvaćanje Bitcoina kao globalnog novca je upravo taj optimističan scenarij za Bitcoin, kojeg je artikulirao Satoshi Nakamoto još 2010. godine u email razmjeni sa Mikeom Hearnom:
"Ako zamisliš da se koristi u nekom dijelu svjetske trgovine, i da će postojati samo 21 milijun bitcoina za cijeli svijet, vrijednost po jedinici će biti znatno veća".
Ovaj scenarij je još snažnije definirao briljantni kriptograf Hal Finney, koji je ujedno primio i prve bitcoine od Nakamotoa, ubrzo nakon najave prvog funkcionalnog Bitcoin softvera:
"Zamislimo da Bitcoin bude uspješan i postane dominantan sustav plaćanja diljem svijeta. U tom slučaju će ukupna vrijednost valute biti jednaka ukupnoj vrijednosti svog bogatstva svijeta. Današnje procjene ukupnog svjetskog bogatska kućanstava koje sam pronašao borave negdje između 100 i 300 trilijuna dolara. Sa 20 milijuna bitcoina, svaki bi onda vrijedio oko 10 milijuna dolara."
Čak i da Bitcoin ne postane u cijelost globalan novac, nego da se samo natječe sa zlatom kao neovisno spremište vrijednosti, i dalje je masivno podcijenjen. Mapiranje tržišne kapitalizacije postojeće količine izrudarenog zlata (oko 8 trilijuna dolara) na maksimalnu dostupnost Bitcoina od 21 milijun, daje vrijednost od otprilike 380,000 dolara po bitcoinu. Kao što smo vidjeli u prethodnom tekstu, svojstva koja omogućavaju monetarnom dobru da bude prikladno spremište vrijednosti, čine Bitcoin superiornijim zlatu u svakom pogledu osim trajanja povijesti. No, kako vrijeme prolazi i Lindy efekt postane jači, dosadašnja povijest će prestati biti prednost zlata. Samim time, nije nerazumno očekivati da će Bitcoin narasti do, a možda i preko, ukupne cijene zlata na tržištvu do 2030. Opaska ovoj tezi je činjenica da veliki postotak vrijednosti zlata dolazi od toga što ga centralne banke čuvaju kao spremište vrijednosti. Da bi Bitcoin došao do te razine, određena količina suverenih država će trebati sudjelovati. Hoće li zapadnjačke demokracije sudjelovati u vlasništvu Bitcoina je nepoznato. Vjerojatnije je, nažalost, da će prve nacije u Bitcoin tržištu biti sitne diktature i kleptokracije.
Ako niti jedna država ne bude sudjelovala u Bitcoin tržištu, optimistična teza i dalje postoji. Kao nevisno spremište vrijednosti u rukama individualnih i institucionalnih ulagača, Bitcoin je i dalje vrlo rano u svojoj “krivulji prihvaćenosti” (adoption curve); tzv. “rana većina” ulaze na tržište sada, dok će ostali ući tek nekoliko godina kasnije. Sa širim sudjelovanjem individualnih i institucionalnih ulagača, cijena po bitcoinu između 100,000 i 200,000 dolara je sasvim moguća.
Posjedovanje bitcoina je jedna od malobrojnih asimetričnih novčanih strategija dostupnih svakome na svijetu. Poput “call” opcija, negativan rizik ulagača je ograničen na 1x, dok potencijalna dobit i dalje iznosi 100x ili više. Bitcoin je prvi istinski globalan balon čija je veličina ograničena samo potražnjom i željom građana svijeta da zaštite svoju ušteđevinu od raznovrsnih ekonomskih malverzacija vlade. Bitcoin je ustao kao feniks iz pepela globalne financijske krize 2008. godine - katastrofe kojoj su prethodile odluke centralnih banaka poput američke Federalne rezerve (Federal Reserve).
Onkraj samo financijske teze za Bitcoin, njegov rast i uspjeh kao neovisno spremište vrijednosti imat će duboke geopolitičke posljedice. Globalna, ne-inflacijska valuta će prisiliti suverene države da promjene svoje primarne mehanizme financiranja od inflacije u izravno oporezivanje; koje je daleko manje politički popularno. Države će se smanjivati proporcionalno političkoj boli koju im nanese oporezivanje kao jedini način financiranja. Nadalje, globalna trgovina vršiti će se na način koji zadovoljava aspiraciju Charlesa de Gaullea, da nijedna nacija ne bi smjela imati privilegiju nad ikojom drugom:
"Smatramo da je potrebno da se uspostavi međunarodna trgovina, kao što je bio slučaj prije velikih nesreća koje su zadesile svijet, na neosporivoj monetarnoj bazi, koja ne nosi na sebi oznaku ijedne države."
Za 50 godina, ta monetarna baza biti će Bitcoin.
-
 @ 33baa074:3bb3a297
2025-05-12 01:06:27
@ 33baa074:3bb3a297
2025-05-12 01:06:27Soil moisture is one of the key factors affecting crop root development. Too much or too little moisture will have an adverse effect on root growth.
Effect of excessive moisture When there is too much soil moisture, the following problems will occur:
Inhibit root respiration: Excessive moisture will squeeze out oxygen in the soil, causing root hypoxia, thereby inhibiting root respiration, and in severe cases, it can cause root growth to stop or rot and die. Affect soil aeration: Excessive moisture will reduce soil aeration and affect the normal growth of the root system. Effect of too little moisture When there is too little soil moisture, it will also have a negative impact on the root system:
Promote root corking and self-thinning: Lack of water can cause root corking and even self-thinning, affecting the absorption capacity of the root system.
Determine whether the soil moisture is appropriate In order to ensure the healthy development of crop roots, soil moisture needs to be managed reasonably. The following methods can be used to determine whether the soil moisture is appropriate:
Touch test: Use a small shovel to dig up the soil around the root system, grab some soil with your hand and pinch it in your hand. If the soil can be kneaded into a ball and can be spread apart, the moisture content is appropriate; if it can be kneaded into a ball but cannot be spread apart, the moisture content exceeds the standard; if it cannot be kneaded into a ball, the soil is lacking in water.
Conclusion In summary, soil moisture has an important impact on the development of crop roots. Reasonable water management is essential to promote healthy root growth. By monitoring and adjusting soil moisture through appropriate methods, the normal growth and development of crops can be effectively guaranteed.
-
 @ 6be5cc06:5259daf0
2025-04-28 01:05:08
@ 6be5cc06:5259daf0
2025-04-28 01:05:08Primeiramente, o que é mempool?
Abreviação de memory pool (ou "pool de memória") a mempool é uma espécie de fila onde as transações de Bitcoin ficam temporariamente armazenadas antes de serem confirmadas e incluídas em um bloco na blockchain. Quando você realiza uma transação em uma rede blockchain, essa transação precisa ser validada e confirmada pelos mineradores (ou validadores). Porém, ela não é processada instantaneamente. Primeiro, ela vai para a mempool, onde aguarda até que um minerador a selecione para incluir no próximo bloco.
É assim: * Você envia uma transação, ela é transmitida para a rede e vai parar na mempool de vários nós (computadores) que suportam a rede blockchain. * As transações na mempool são organizadas pela taxa de transação que foi anexada. Quanto maior a taxa, mais rápido os mineradores tendem a escolher essa transação para incluí-la em um bloco, pois isso aumenta os ganhos deles. * Os mineradores pegam as transações da mempool, criam um bloco com elas e, ao minerar (confirmar) esse bloco, as transações saem da mempool e entram na blockchain.
Aqui irei usar o site mempool.emzy.de como referência, mas é importante entender que sites de mempool são representações visuais da mempool de um nó específico e não a mempool do Bitcoin em si. Ela não é centralizada, cada nó da rede mantém a sua própria versão da mempool. Assim, ela pode variar de um nó para outro. Esses sites ajudam a visualizar dados sobre transações e taxas.
É uma boa prática usar VPN ou Tor ao acessar tais sites se você estiver verificando uma transação específica sua, pois sua privacidade pode ficar comprometida se o site registrar esses dados. Se você estiver repetidamente acessando-o para monitorar a confirmação de uma transação, alguém pode conseguir correlacionar o endereço IP com essa atividade e revelar uma conexão indireta com o endereço da transação.
Dito isso...
Como interpretar a mempool?
Vamos dividir isso em partes para fins didáticos.
Faixa de taxas
Cada bloco verde representa uma faixa de taxa medida em satoshis por vByte (sats/vB).
Essa unidade de medida representa o valor pago por byte ocupado pela transação.
Quanto maior a taxa paga por uma transação, mais rápido ela tende a ser confirmada.
Quanto maior a transação em bytes, mais você precisa pagar para que ela seja confirmada.
Cada transação Bitcoin consiste em entradas e saídas (inputs e outputs): * Entradas são referências a transações anteriores que estão sendo gastas, e cada entrada inclui informações como o endereço de origem, a assinatura (que valida a transação e pode variar de tamanho dependendo da complexidade da chave e do método de assinatura utilizado (como SegWit, que é mais eficiente). Quanto mais complexa a assinatura, maior será o tamanho em bytes) e outros dados. Quanto mais entradas uma transação tiver, maior será seu tamanho. * Saídas representam o destino do Bitcoin, e quanto mais saídas, maior será o tamanho da transação. Embora as saídas ocupem menos espaço em bytes do que as entradas.Ex.: * ~4 sat/vB: Indica uma taxa média. Significa que, em média, as transações estão sendo processadas a 4 satoshis por vByte; * 3-5 sat/vB: Isso significa que as transações estão sendo processadas com uma taxa entre 3 e 5 satoshis por vByte.
MB
Simplesmente o tamanho do bloco medido em megabytes :)
Número de transações
Essa seção informa quantas transações estão aguardando confirmação para cada faixa de taxa (bloco). Quanto maior o número de transações, maior a demanda pela faixa de taxa especificada.
Tempo estimado para confirmação
Aqui é mostrado o tempo médio de espera para transações que pagam taxas dentro da faixa especificada. Se você pagar uma taxa maior, a transação será confirmada mais rapidamente; uma taxa menor significa que a transação pode levar mais tempo para ser confirmada, especialmente se a rede estiver congestionada.
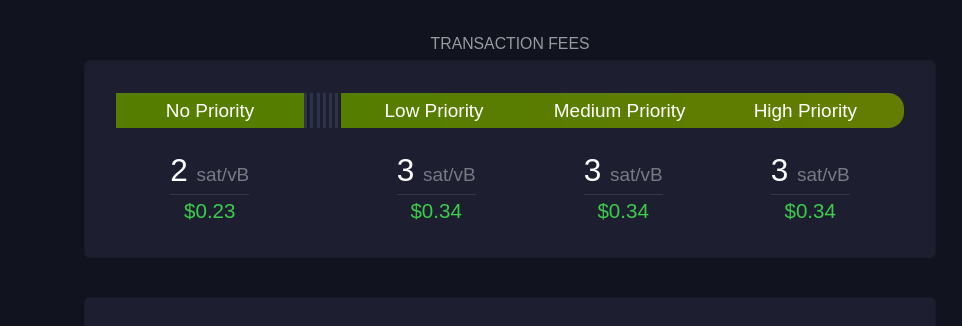 Esta seção mostra sugestões de taxa em diferentes níveis de prioridade para os usuários:
Esta seção mostra sugestões de taxa em diferentes níveis de prioridade para os usuários:Sem Prioridade
Exibe a taxa mínima necessária para transações que não precisam de confirmação rápida.
Prioridade Baixa
Sugestão de taxa para transações que podem esperar um tempo moderado, com expectativa de confirmação em um ou dois blocos.
Prioridade Média e Alta
São as faixas de taxa recomendadas para quem precisa que a transação seja confirmada rapidamente. "Prioridade Alta" paga uma taxa maior, garantindo que a transação seja incluída no próximo bloco.
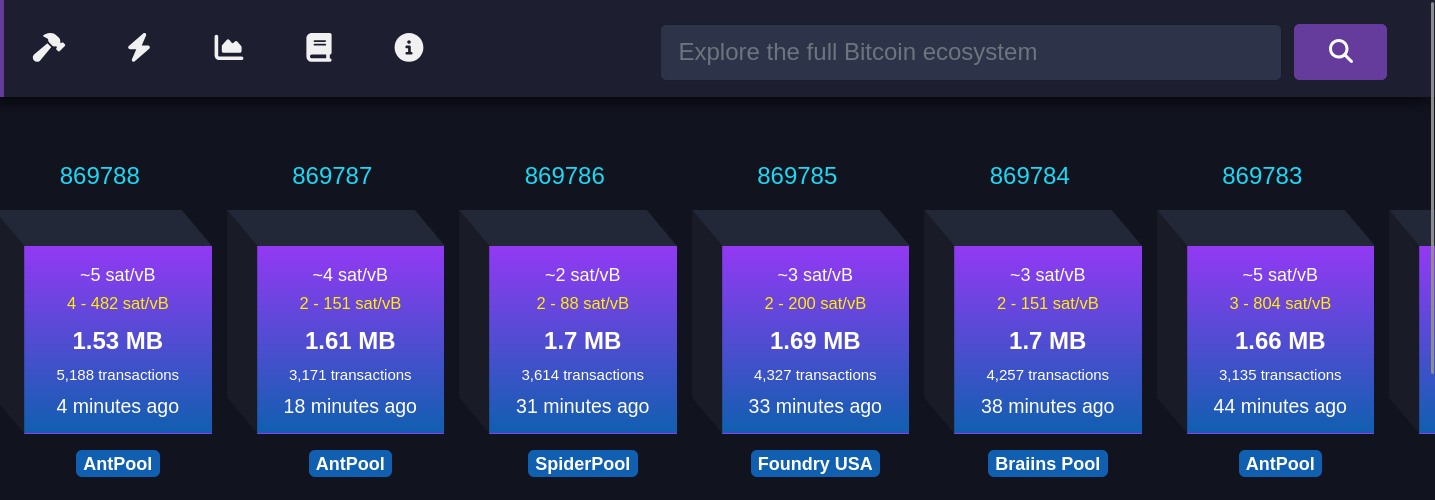 Cada bloco roxo representa um bloco recém-minerado. As informações mostradas incluem:
Cada bloco roxo representa um bloco recém-minerado. As informações mostradas incluem: Taxa média paga
Refere-se à taxa média em satoshis/vB paga por todas as transações incluídas em um bloco recém-minerado. Isso reflete o valor médio que os usuários estão dispostos a pagar para que suas transações sejam confirmadas rapidamente.
Número de transações
Este número indica quantas transações foram processadas no bloco minerado. O tamanho do bloco é limitado, então, quanto maior o número de transações, menor será o espaço disponível para novas transações, o que pode influenciar as taxas de transação.
Tempo desde a mineração
Esta métrica informa quanto tempo se passou desde que o bloco foi minerado e adicionado à blockchain.
Pool de mineração
Exibe o nome do pool de mineração que minerou o bloco, como AntPool. Grandes pools de mineração têm mais chances de minerar blocos regularmente devido ao alto hashrate (medida da capacidade computacional utilizada pelos mineradores) que possuem.
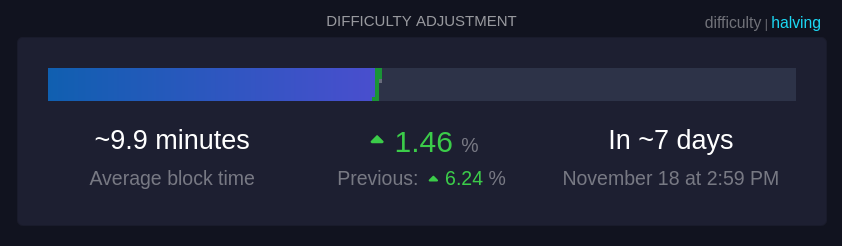 Essa seção mostra informações sobre o ajuste de dificuldade, que ocorre aproximadamente a cada duas semanas.
Essa seção mostra informações sobre o ajuste de dificuldade, que ocorre aproximadamente a cada duas semanas. Tempo médio dos blocos (~9,9 minutos):
Este é o tempo médio atual para minerar um bloco na rede. A meta da rede é manter o tempo de bloco em cerca de 10 minutos; um tempo menor indica um aumento na taxa de hash, ou seja, que mais poder computacional foi adicionado à rede.
Mudança de dificuldade (+1,46%):
A dificuldade ajusta-se a cada 2016 blocos para manter o tempo médio de bloco próximo de 10 minutos. Um aumento na dificuldade, como +1,46%, indica que a mineração ficou mais difícil devido ao aumento do hashrate, enquanto uma redução na dificuldade indica que o hashrate diminuiu.
Tempo até o próximo ajuste:
É o tempo previsto até o próximo ajuste de dificuldade (7 dias, nesse caso), o que é crucial para manter a rede estável e garantir a segurança e a regularidade do processo de mineração.
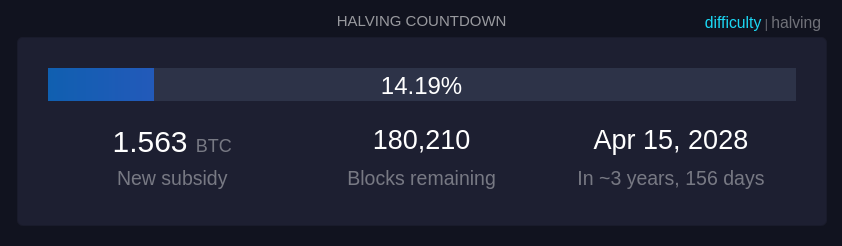 Quanto tempo demora até o próximo halving, um evento no Bitcoin que ocorre aproximadamente a cada 210.000 blocos minerados, ou cerca de quatro anos. Durante o halving, a recompensa que os mineradores recebem por adicionar um novo bloco à blockchain é reduzida pela metade.
Quanto tempo demora até o próximo halving, um evento no Bitcoin que ocorre aproximadamente a cada 210.000 blocos minerados, ou cerca de quatro anos. Durante o halving, a recompensa que os mineradores recebem por adicionar um novo bloco à blockchain é reduzida pela metade.
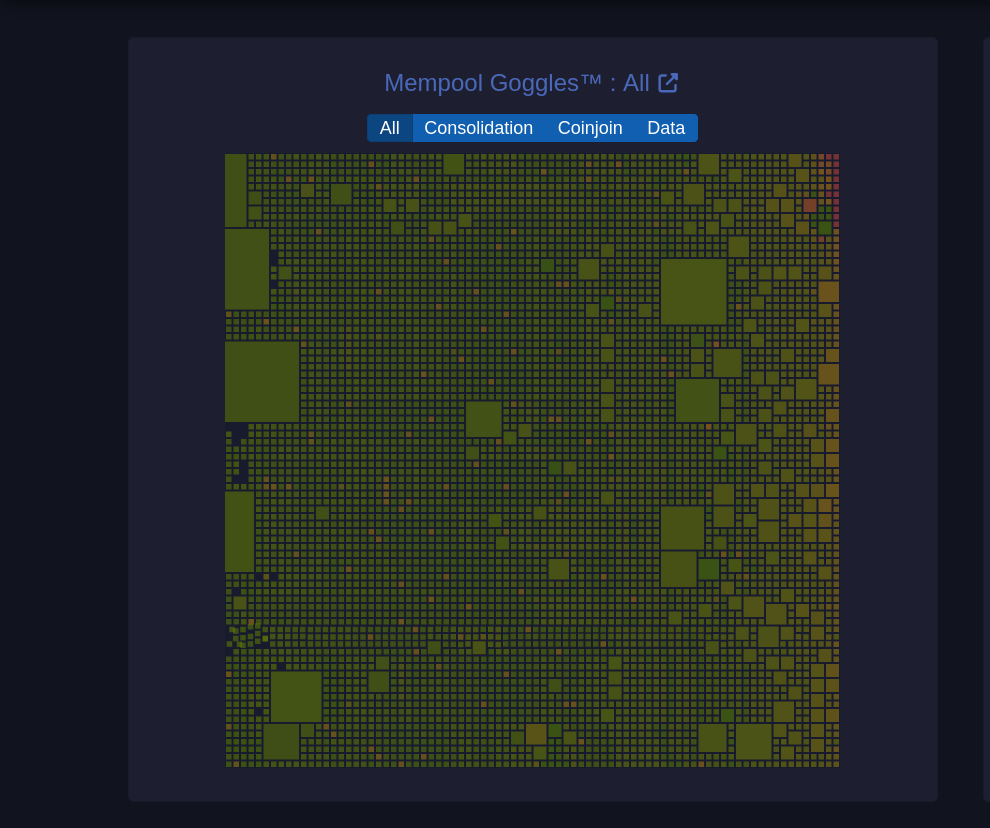 Um diagrama visual da mempool que mostra o estado das transações pendentes na rede.
Um diagrama visual da mempool que mostra o estado das transações pendentes na rede. Tamanhos de blocos
O tamanho de cada quadrado representa o tamanho da transação em bytes.
Filtros (Consolidação, Coinjoin, Dados): Permite visualizar categorias específicas de transações: * Consolidação: Transações de consolidação agrupam pequenos UTXOs em um único UTXO maior para simplificar e baratear futuras transações. (UTXOs merecem um artigo dedicado) * Coinjoin: Transações CoinJoin são usadas para melhorar a privacidade, misturando transações de vários usuários em uma única transação. * Dados: Mostra transações que contêm dados adicionais, que podem incluir informações não financeiras, como mensagens.
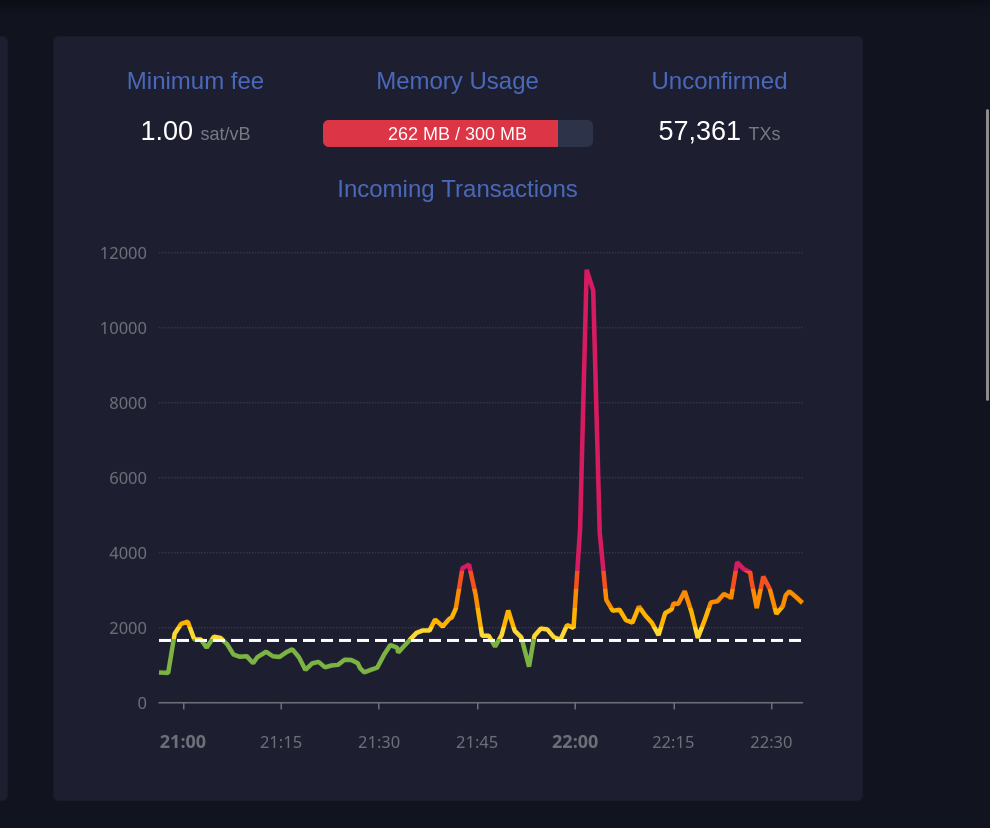 Este gráfico exibe o número de transações recebidas ao longo do tempo.
Este gráfico exibe o número de transações recebidas ao longo do tempo. Taxa mínima (1 sat/vB):
Indica a taxa mínima atualmente aceita pela mempool. Se a mempool estiver cheia, transações que paguem menos do que a taxa mínima podem ser excluídas para dar lugar a transações de maior prioridade.
Uso de memória (259 MB / 300 MB):
A mempool tem um limite de memória. Quando está cheia, transações de taxa mais baixa podem ser descartadas para abrir espaço para aquelas com taxas mais altas, priorizando-as para inclusão em blocos.
Transações não confirmadas (59.361):
Indica o número total de transações pendentes que aguardam confirmação. Quanto maior o número de transações na mempool, maior a probabilidade de que as taxas aumentem para garantir uma confirmação mais rápida.
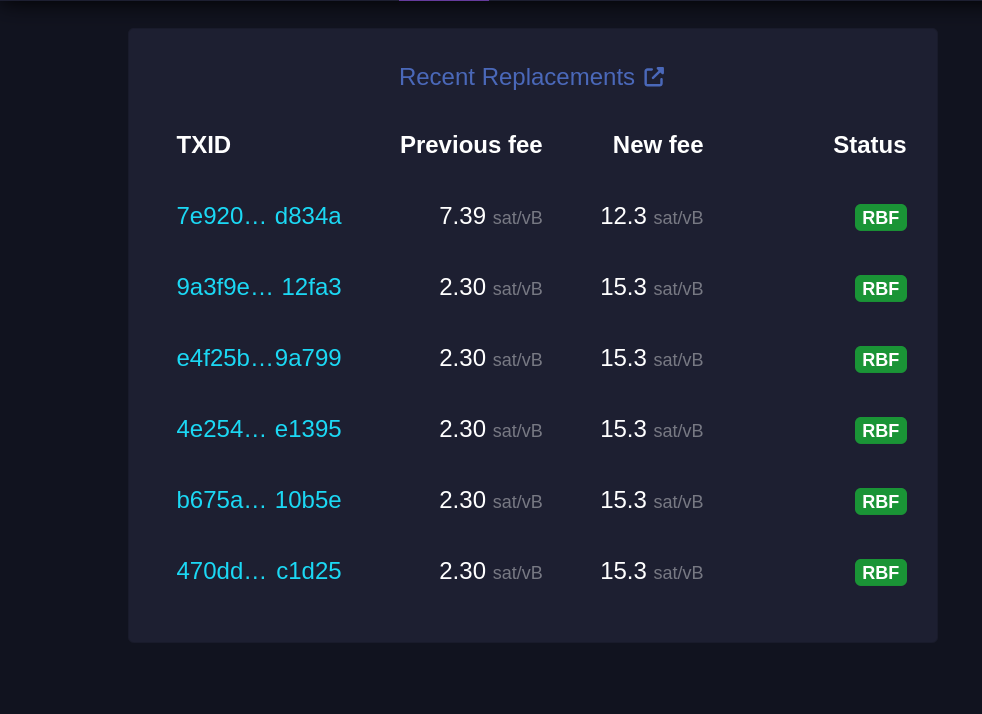 Essa seção mostra transações que foram substituídas utilizando o mecanismo RBF (Replace-By-Fee), que permite substituir uma transação com uma taxa mais alta para acelerar sua confirmação.
Essa seção mostra transações que foram substituídas utilizando o mecanismo RBF (Replace-By-Fee), que permite substituir uma transação com uma taxa mais alta para acelerar sua confirmação. TXID
Este é o identificador da transação (Transaction ID), exibido parcialmente para abreviar o espaço. Cada transação tem um identificador único na blockchain.
Previous fee
Exibe a taxa de transação original paga na primeira tentativa, medida em satoshis por vByte (sat/vB). Esta taxa inicial provavelmente era baixa demais, resultando em uma demora na confirmação.
New fee
Mostra a nova taxa de transação, também em satoshis por vByte, definida para substituir a taxa anterior. Uma taxa maior aumenta as chances de inclusão rápida em um bloco.
Status (RBF)
RBF indica que a transação foi substituída utilizando o recurso "Replace-By-Fee". Isso significa que a nova transação cancelou e substituiu a original, e o minerador escolherá a transação com a taxa mais alta para incluir no próximo bloco.
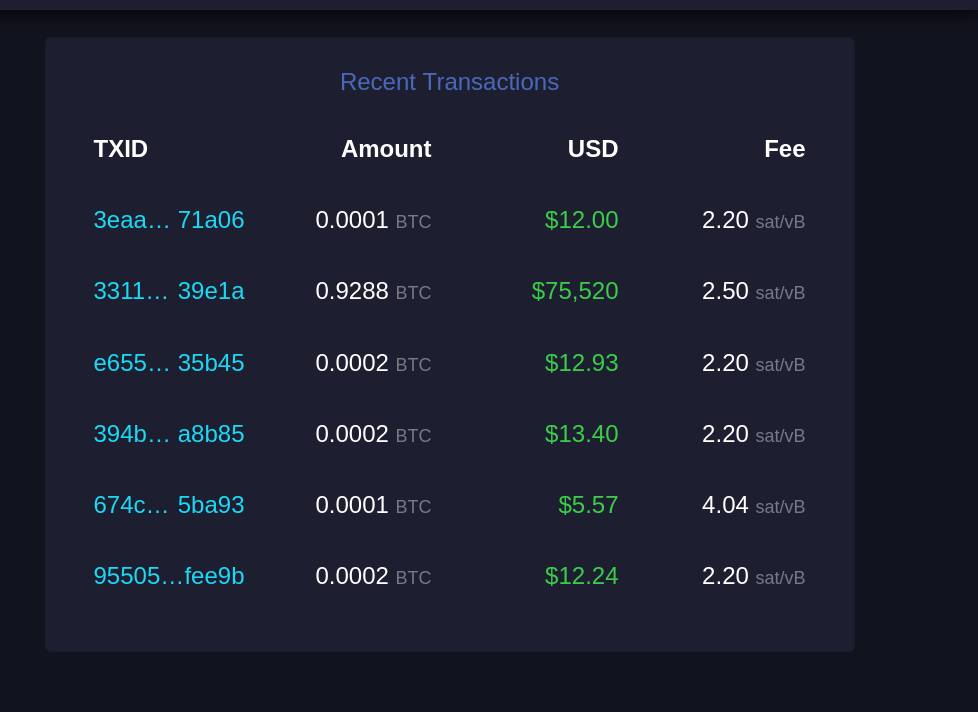 Esta seção lista transações recentes que entraram na mempool e aguardam confirmação.
Esta seção lista transações recentes que entraram na mempool e aguardam confirmação. TXID
Similar ao "Recent Replacements", este é o identificador único da transação.
Amount
Exibe a quantidade de Bitcoin transferida nessa transação, geralmente em frações de BTC (como 0.0001 BTC). Esta é a quantia enviada pelo remetente ao destinatário.
USD
Mostra o valor da transação em dólares americanos (USD), calculado com base na taxa de câmbio atual. Serve para dar uma ideia de quanto a transação representa em moeda fiduciária.
Fee
Exibe a taxa de transação paga, em satoshis por vByte (sat/vB). Uma taxa mais alta em relação à média aumenta a probabilidade de confirmação mais rápida, pois as transações com taxas mais elevadas são priorizadas pelos mineradores.
E acabou. Espero que isso tenha sido útil para você e tenha agregado mais entendimento sobre esse complexo e maravilhoso mundo do Bitcoin. Se foi, considere compartilhar com alguém que precise. E se tem sugestões de melhoria, por favor, não deixe de comentar, o conhecimento está dispero na sociedade.
Por fim, stay humble and stack sats! -
 @ c631e267:c2b78d3e
2025-04-25 20:06:24
@ c631e267:c2b78d3e
2025-04-25 20:06:24Die Wahrheit verletzt tiefer als jede Beleidigung. \ Marquis de Sade
Sagen Sie niemals «Terroristin B.», «Schwachkopf H.», «korrupter Drecksack S.» oder «Meinungsfreiheitshasserin F.» und verkneifen Sie sich Memes, denn so etwas könnte Ihnen als Beleidigung oder Verleumdung ausgelegt werden und rechtliche Konsequenzen haben. Auch mit einer Frau M.-A. S.-Z. ist in dieser Beziehung nicht zu spaßen, sie gehört zu den Top-Anzeigenstellern.
«Politikerbeleidigung» als Straftatbestand wurde 2021 im Kampf gegen «Rechtsextremismus und Hasskriminalität» in Deutschland eingeführt, damals noch unter der Regierung Merkel. Im Gesetz nicht festgehalten ist die Unterscheidung zwischen schlechter Hetze und guter Hetze – trotzdem ist das gängige Praxis, wie der Titel fast schon nahelegt.
So dürfen Sie als Politikerin heute den Tesla als «Nazi-Auto» bezeichnen und dies ausdrücklich auf den Firmengründer Elon Musk und dessen «rechtsextreme Positionen» beziehen, welche Sie nicht einmal belegen müssen. [1] Vielleicht ernten Sie Proteste, jedoch vorrangig wegen der «gut bezahlten, unbefristeten Arbeitsplätze» in Brandenburg. Ihren Tweet hat die Berliner Senatorin Cansel Kiziltepe inzwischen offenbar dennoch gelöscht.
Dass es um die Meinungs- und Pressefreiheit in der Bundesrepublik nicht mehr allzu gut bestellt ist, befürchtet man inzwischen auch schon im Ausland. Der Fall des Journalisten David Bendels, der kürzlich wegen eines Faeser-Memes zu sieben Monaten Haft auf Bewährung verurteilt wurde, führte in diversen Medien zu Empörung. Die Welt versteckte ihre Kritik mit dem Titel «Ein Urteil wie aus einer Diktatur» hinter einer Bezahlschranke.
Unschöne, heutzutage vielleicht strafbare Kommentare würden mir auch zu einigen anderen Themen und Akteuren einfallen. Ein Kandidat wäre der deutsche Bundesgesundheitsminister (ja, er ist es tatsächlich immer noch). Während sich in den USA auf dem Gebiet etwas bewegt und zum Beispiel Robert F. Kennedy Jr. will, dass die Gesundheitsbehörde (CDC) keine Covid-Impfungen für Kinder mehr empfiehlt, möchte Karl Lauterbach vor allem das Corona-Lügengebäude vor dem Einsturz bewahren.
«Ich habe nie geglaubt, dass die Impfungen nebenwirkungsfrei sind», sagte Lauterbach jüngst der ZDF-Journalistin Sarah Tacke. Das steht in krassem Widerspruch zu seiner früher verbreiteten Behauptung, die Gen-Injektionen hätten keine Nebenwirkungen. Damit entlarvt er sich selbst als Lügner. Die Bezeichnung ist absolut berechtigt, dieser Mann dürfte keinerlei politische Verantwortung tragen und das Verhalten verlangt nach einer rechtlichen Überprüfung. Leider ist ja die Justiz anderweitig beschäftigt und hat außerdem selbst keine weiße Weste.
Obendrein kämpfte der Herr Minister für eine allgemeine Impfpflicht. Er beschwor dabei das Schließen einer «Impflücke», wie es die Weltgesundheitsorganisation – die «wegen Trump» in finanziellen Schwierigkeiten steckt – bis heute tut. Die WHO lässt aktuell ihre «Europäische Impfwoche» propagieren, bei der interessanterweise von Covid nicht mehr groß die Rede ist.
Einen «Klima-Leugner» würden manche wohl Nir Shaviv nennen, das ist ja nicht strafbar. Der Astrophysiker weist nämlich die Behauptung von einer Klimakrise zurück. Gemäß seiner Forschung ist mindestens die Hälfte der Erderwärmung nicht auf menschliche Emissionen, sondern auf Veränderungen im Sonnenverhalten zurückzuführen.
Das passt vielleicht auch den «Klima-Hysterikern» der britischen Regierung ins Konzept, die gerade Experimente zur Verdunkelung der Sonne angekündigt haben. Produzenten von Kunstfleisch oder Betreiber von Insektenfarmen würden dagegen vermutlich die Geschichte vom fatalen CO2 bevorzugen. Ihnen würde es besser passen, wenn der verantwortungsvolle Erdenbürger sein Verhalten gründlich ändern müsste.
In unserer völlig verkehrten Welt, in der praktisch jede Verlautbarung außerhalb der abgesegneten Narrative potenziell strafbar sein kann, gehört fast schon Mut dazu, Dinge offen anzusprechen. Im «besten Deutschland aller Zeiten» glaubten letztes Jahr nur noch 40 Prozent der Menschen, ihre Meinung frei äußern zu können. Das ist ein Armutszeugnis, und es sieht nicht gerade nach Besserung aus. Umso wichtiger ist es, dagegen anzugehen.
[Titelbild: Pixabay]
--- Quellen: ---
[1] Zur Orientierung wenigstens ein paar Hinweise zur NS-Vergangenheit deutscher Automobilhersteller:
- Volkswagen
- Porsche
- Daimler-Benz
- BMW
- Audi
- Opel
- Heute: «Auto-Werke für die Rüstung? Rheinmetall prüft Übernahmen»
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ c631e267:c2b78d3e
2025-04-20 19:54:32
@ c631e267:c2b78d3e
2025-04-20 19:54:32Es ist völlig unbestritten, dass der Angriff der russischen Armee auf die Ukraine im Februar 2022 strikt zu verurteilen ist. Ebenso unbestritten ist Russland unter Wladimir Putin keine brillante Demokratie. Aus diesen Tatsachen lässt sich jedoch nicht das finstere Bild des russischen Präsidenten – und erst recht nicht des Landes – begründen, das uns durchweg vorgesetzt wird und den Kern des aktuellen europäischen Bedrohungs-Szenarios darstellt. Da müssen wir schon etwas genauer hinschauen.
Der vorliegende Artikel versucht derweil nicht, den Einsatz von Gewalt oder die Verletzung von Menschenrechten zu rechtfertigen oder zu entschuldigen – ganz im Gegenteil. Dass jedoch der Verdacht des «Putinverstehers» sofort latent im Raume steht, verdeutlicht, was beim Thema «Russland» passiert: Meinungsmache und Manipulation.
Angesichts der mentalen Mobilmachung seitens Politik und Medien sowie des Bestrebens, einen bevorstehenden Krieg mit Russland geradezu herbeizureden, ist es notwendig, dieser fatalen Entwicklung entgegenzutreten. Wenn wir uns nur ein wenig von der herrschenden Schwarz-Weiß-Malerei freimachen, tauchen automatisch Fragen auf, die Risse im offiziellen Narrativ enthüllen. Grund genug, nachzuhaken.
Wer sich schon länger auch abseits der Staats- und sogenannten Leitmedien informiert, der wird in diesem Artikel vermutlich nicht viel Neues erfahren. Andere könnten hier ein paar unbekannte oder vergessene Aspekte entdecken. Möglicherweise klärt sich in diesem Kontext die Wahrnehmung der aktuellen (unserer eigenen!) Situation ein wenig.
Manipulation erkennen
Corona-«Pandemie», menschengemachter Klimawandel oder auch Ukraine-Krieg: Jede Menge Krisen, und für alle gibt es ein offizielles Narrativ, dessen Hinterfragung unerwünscht ist. Nun ist aber ein Narrativ einfach eine Erzählung, eine Geschichte (Latein: «narratio») und kein Tatsachenbericht. Und so wie ein Märchen soll auch das Narrativ eine Botschaft vermitteln.
Über die Methoden der Manipulation ist viel geschrieben worden, sowohl in Bezug auf das Individuum als auch auf die Massen. Sehr wertvolle Tipps dazu, wie man Manipulationen durchschauen kann, gibt ein Büchlein [1] von Albrecht Müller, dem Herausgeber der NachDenkSeiten.
Die Sprache selber eignet sich perfekt für die Manipulation. Beispielsweise kann die Wortwahl Bewertungen mitschwingen lassen, regelmäßiges Wiederholen (gerne auch von verschiedenen Seiten) lässt Dinge irgendwann «wahr» erscheinen, Übertreibungen fallen auf und hinterlassen wenigstens eine Spur im Gedächtnis, genauso wie Andeutungen. Belege spielen dabei keine Rolle.
Es gibt auffällig viele Sprachregelungen, die offenbar irgendwo getroffen und irgendwie koordiniert werden. Oder alle Redenschreiber und alle Medien kopieren sich neuerdings permanent gegenseitig. Welchen Zweck hat es wohl, wenn der Krieg in der Ukraine durchgängig und quasi wörtlich als «russischer Angriffskrieg auf die Ukraine» bezeichnet wird? Obwohl das in der Sache richtig ist, deutet die Art der Verwendung auf gezielte Beeinflussung hin und soll vor allem das Feindbild zementieren.
Sprachregelungen dienen oft der Absicherung einer einseitigen Darstellung. Das Gleiche gilt für das Verkürzen von Informationen bis hin zum hartnäckigen Verschweigen ganzer Themenbereiche. Auch hierfür gibt es rund um den Ukraine-Konflikt viele gute Beispiele.
Das gewünschte Ergebnis solcher Methoden ist eine Schwarz-Weiß-Malerei, bei der einer eindeutig als «der Böse» markiert ist und die anderen automatisch «die Guten» sind. Das ist praktisch und demonstriert gleichzeitig ein weiteres Manipulationswerkzeug: die Verwendung von Doppelstandards. Wenn man es schafft, bei wichtigen Themen regelmäßig mit zweierlei Maß zu messen, ohne dass das Publikum protestiert, dann hat man freie Bahn.
Experten zu bemühen, um bestimmte Sachverhalte zu erläutern, ist sicher sinnvoll, kann aber ebenso missbraucht werden, schon allein durch die Auswahl der jeweiligen Spezialisten. Seit «Corona» werden viele erfahrene und ehemals hoch angesehene Fachleute wegen der «falschen Meinung» diffamiert und gecancelt. [2] Das ist nicht nur ein brutaler Umgang mit Menschen, sondern auch eine extreme Form, die öffentliche Meinung zu steuern.
Wann immer wir also erkennen (weil wir aufmerksam waren), dass wir bei einem bestimmten Thema manipuliert werden, dann sind zwei logische und notwendige Fragen: Warum? Und was ist denn richtig? In unserem Russland-Kontext haben die Antworten darauf viel mit Geopolitik und Geschichte zu tun.
Ist Russland aggressiv und expansiv?
Angeblich plant Russland, europäische NATO-Staaten anzugreifen, nach dem Motto: «Zuerst die Ukraine, dann den Rest». In Deutschland weiß man dafür sogar das Datum: «Wir müssen bis 2029 kriegstüchtig sein», versichert Verteidigungsminister Pistorius.
Historisch gesehen ist es allerdings eher umgekehrt: Russland, bzw. die Sowjetunion, ist bereits dreimal von Westeuropa aus militärisch angegriffen worden. Die Feldzüge Napoleons, des deutschen Kaiserreichs und Nazi-Deutschlands haben Millionen Menschen das Leben gekostet. Bei dem ausdrücklichen Vernichtungskrieg ab 1941 kam es außerdem zu Brutalitäten wie der zweieinhalbjährigen Belagerung Leningrads (heute St. Petersburg) durch Hitlers Wehrmacht. Deren Ziel, die Bevölkerung auszuhungern, wurde erreicht: über eine Million tote Zivilisten.
Trotz dieser Erfahrungen stimmte Michail Gorbatschow 1990 der deutschen Wiedervereinigung zu und die Sowjetunion zog ihre Truppen aus Osteuropa zurück (vgl. Abb. 1). Der Warschauer Pakt wurde aufgelöst, der Kalte Krieg formell beendet. Die Sowjets erhielten damals von führenden westlichen Politikern die Zusicherung, dass sich die NATO «keinen Zentimeter ostwärts» ausdehnen würde, das ist dokumentiert. [3]
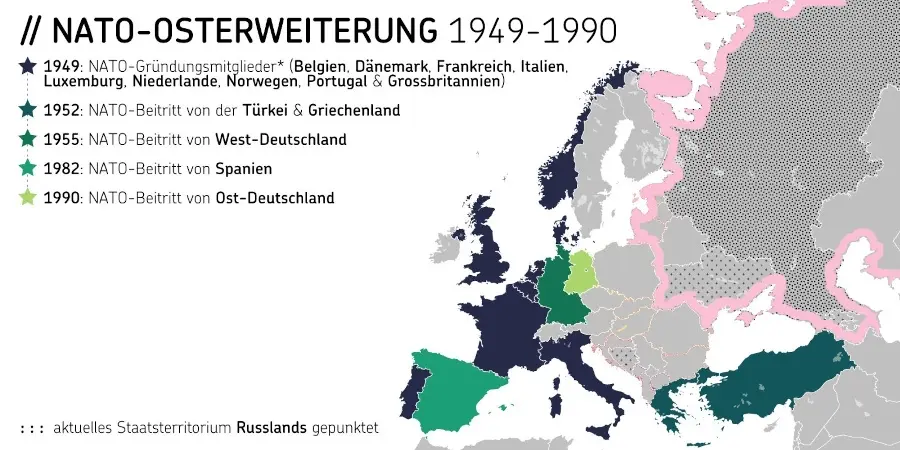
Expandiert ist die NATO trotzdem, und zwar bis an Russlands Grenzen (vgl. Abb. 2). Laut dem Politikberater Jeffrey Sachs handelt es sich dabei um ein langfristiges US-Projekt, das von Anfang an die Ukraine und Georgien mit einschloss. Offiziell wurde der Beitritt beiden Staaten 2008 angeboten. In jedem Fall könnte die massive Ost-Erweiterung seit 1999 aus russischer Sicht nicht nur als Vertrauensbruch, sondern durchaus auch als aggressiv betrachtet werden.
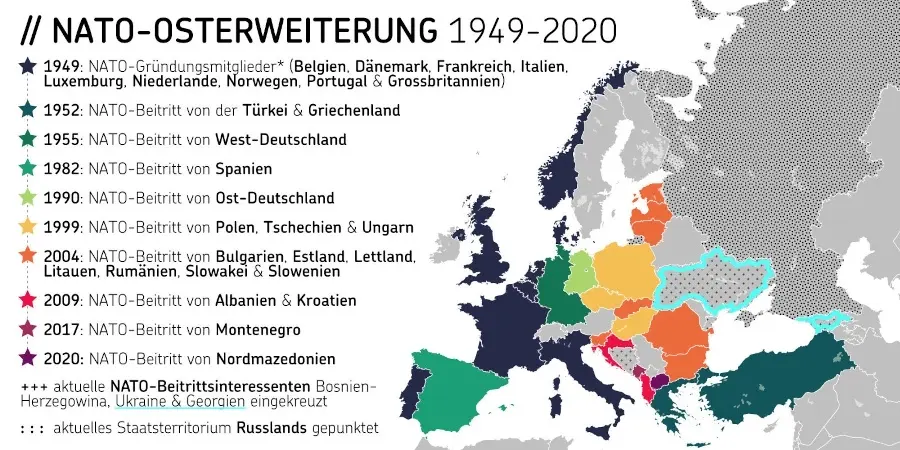
Russland hat den europäischen Staaten mehrfach die Hand ausgestreckt [4] für ein friedliches Zusammenleben und den «Aufbau des europäischen Hauses». Präsident Putin sei «in seiner ersten Amtszeit eine Chance für Europa» gewesen, urteilt die Journalistin und langjährige Russland-Korrespondentin der ARD, Gabriele Krone-Schmalz. Er habe damals viele positive Signale Richtung Westen gesendet.
Die Europäer jedoch waren scheinbar an einer Partnerschaft mit dem kontinentalen Nachbarn weniger interessiert als an der mit dem transatlantischen Hegemon. Sie verkennen bis heute, dass eine gedeihliche Zusammenarbeit in Eurasien eine Gefahr für die USA und deren bekundetes Bestreben ist, die «einzige Weltmacht» zu sein – «Full Spectrum Dominance» [5] nannte das Pentagon das. Statt einem neuen Kalten Krieg entgegenzuarbeiten, ließen sich europäische Staaten selber in völkerrechtswidrige «US-dominierte Angriffskriege» [6] verwickeln, wie in Serbien, Afghanistan, dem Irak, Libyen oder Syrien. Diese werden aber selten so benannt.
Speziell den Deutschen stünde außer einer Portion Realismus auch etwas mehr Dankbarkeit gut zu Gesicht. Das Geschichtsbewusstsein der Mehrheit scheint doch recht selektiv und das Selbstbewusstsein einiger etwas desorientiert zu sein. Bekanntermaßen waren es die Soldaten der sowjetischen Roten Armee, die unter hohen Opfern 1945 Deutschland «vom Faschismus befreit» haben. Bei den Gedenkfeiern zu 80 Jahren Kriegsende will jedoch das Auswärtige Amt – noch unter der Diplomatie-Expertin Baerbock, die sich schon länger offiziell im Krieg mit Russland wähnt, – nun keine Russen sehen: Sie sollen notfalls rausgeschmissen werden.
«Die Grundsatzfrage lautet: Geht es Russland um einen angemessenen Platz in einer globalen Sicherheitsarchitektur, oder ist Moskau schon seit langem auf einem imperialistischen Trip, der befürchten lassen muss, dass die Russen in fünf Jahren in Berlin stehen?»
So bringt Gabriele Krone-Schmalz [7] die eigentliche Frage auf den Punkt, die zur Einschätzung der Situation letztlich auch jeder für sich beantworten muss.
Was ist los in der Ukraine?
In der internationalen Politik geht es nie um Demokratie oder Menschenrechte, sondern immer um Interessen von Staaten. Diese These stammt von Egon Bahr, einem der Architekten der deutschen Ostpolitik des «Wandels durch Annäherung» aus den 1960er und 70er Jahren. Sie trifft auch auf den Ukraine-Konflikt zu, den handfeste geostrategische und wirtschaftliche Interessen beherrschen, obwohl dort angeblich «unsere Demokratie» verteidigt wird.
Es ist ein wesentliches Element des Ukraine-Narrativs und Teil der Manipulation, die Vorgeschichte des Krieges wegzulassen – mindestens die vor der russischen «Annexion» der Halbinsel Krim im März 2014, aber oft sogar komplett diejenige vor der Invasion Ende Februar 2022. Das Thema ist komplex, aber einige Aspekte, die für eine Beurteilung nicht unwichtig sind, will ich wenigstens kurz skizzieren. [8]
Das Gebiet der heutigen Ukraine und Russlands – die übrigens in der «Kiewer Rus» gemeinsame Wurzeln haben – hat der britische Geostratege Halford Mackinder bereits 1904 als eurasisches «Heartland» bezeichnet, dessen Kontrolle er eine große Bedeutung für die imperiale Strategie Großbritanniens zumaß. Für den ehemaligen Sicherheits- und außenpolitischen Berater mehrerer US-amerikanischer Präsidenten und Mitgründer der Trilateralen Kommission, Zbigniew Brzezinski, war die Ukraine nach der Auflösung der Sowjetunion ein wichtiger Spielstein auf dem «eurasischen Schachbrett», wegen seiner Nähe zu Russland, seiner Bodenschätze und seines Zugangs zum Schwarzen Meer.
Die Ukraine ist seit langem ein gespaltenes Land. Historisch zerrissen als Spielball externer Interessen und geprägt von ethnischen, kulturellen, religiösen und geografischen Unterschieden existiert bis heute, grob gesagt, eine Ost-West-Spaltung, welche die Suche nach einer nationalen Identität stark erschwert.
Insbesondere im Zuge der beiden Weltkriege sowie der Russischen Revolution entstanden tiefe Risse in der Bevölkerung. Ukrainer kämpften gegen Ukrainer, zum Beispiel die einen auf der Seite von Hitlers faschistischer Nazi-Armee und die anderen auf der von Stalins kommunistischer Roter Armee. Die Verbrechen auf beiden Seiten sind nicht vergessen. Dass nach der Unabhängigkeit 1991 versucht wurde, Figuren wie den radikalen Nationalisten Symon Petljura oder den Faschisten und Nazi-Kollaborateur Stepan Bandera als «Nationalhelden» zu installieren, verbessert die Sache nicht.
Während die USA und EU-Staaten zunehmend «ausländische Einmischung» (speziell russische) in «ihre Demokratien» wittern, betreiben sie genau dies seit Jahrzehnten in vielen Ländern der Welt. Die seit den 2000er Jahren bekannten «Farbrevolutionen» in Osteuropa werden oft als Methode des Regierungsumsturzes durch von außen gesteuerte «demokratische» Volksaufstände beschrieben. Diese Strategie geht auf Analysen zum «Schwarmverhalten» [9] seit den 1960er Jahren zurück (Studentenproteste), wo es um die potenzielle Wirksamkeit einer «rebellischen Hysterie» von Jugendlichen bei postmodernen Staatsstreichen geht. Heute nennt sich dieses gezielte Kanalisieren der Massen zur Beseitigung unkooperativer Regierungen «Soft-Power».
In der Ukraine gab es mit der «Orangen Revolution» 2004 und dem «Euromaidan» 2014 gleich zwei solcher «Aufstände». Der erste erzwang wegen angeblicher Unregelmäßigkeiten eine Wiederholung der Wahlen, was mit Wiktor Juschtschenko als neuem Präsidenten endete. Dieser war ehemaliger Direktor der Nationalbank und Befürworter einer Annäherung an EU und NATO. Seine Frau, die First Lady, ist US-amerikanische «Philanthropin» und war Beamtin im Weißen Haus in der Reagan- und der Bush-Administration.
Im Gegensatz zu diesem ersten Event endete der sogenannte Euromaidan unfriedlich und blutig. Die mehrwöchigen Proteste gegen Präsident Wiktor Janukowitsch, in Teilen wegen des nicht unterzeichneten Assoziierungsabkommens mit der EU, wurden zunehmend gewalttätiger und von Nationalisten und Faschisten des «Rechten Sektors» dominiert. Sie mündeten Ende Februar 2014 auf dem Kiewer Unabhängigkeitsplatz (Maidan) in einem Massaker durch Scharfschützen. Dass deren Herkunft und die genauen Umstände nicht geklärt wurden, störte die Medien nur wenig. [10]
Janukowitsch musste fliehen, er trat nicht zurück. Vielmehr handelte es sich um einen gewaltsamen, allem Anschein nach vom Westen inszenierten Putsch. Laut Jeffrey Sachs war das kein Geheimnis, außer vielleicht für die Bürger. Die USA unterstützten die Post-Maidan-Regierung nicht nur, sie beeinflussten auch ihre Bildung. Das geht unter anderem aus dem berühmten «Fuck the EU»-Telefonat der US-Chefdiplomatin für die Ukraine, Victoria Nuland, mit Botschafter Geoffrey Pyatt hervor.
Dieser Bruch der demokratischen Verfassung war letztlich der Auslöser für die anschließenden Krisen auf der Krim und im Donbass (Ostukraine). Angesichts der ukrainischen Geschichte mussten die nationalistischen Tendenzen und die Beteiligung der rechten Gruppen an dem Umsturz bei der russigsprachigen Bevölkerung im Osten ungute Gefühle auslösen. Es gab Kritik an der Übergangsregierung, Befürworter einer Abspaltung und auch für einen Anschluss an Russland.
Ebenso konnte Wladimir Putin in dieser Situation durchaus Bedenken wegen des Status der russischen Militärbasis für seine Schwarzmeerflotte in Sewastopol auf der Krim haben, für die es einen langfristigen Pachtvertrag mit der Ukraine gab. Was im März 2014 auf der Krim stattfand, sei keine Annexion, sondern eine Abspaltung (Sezession) nach einem Referendum gewesen, also keine gewaltsame Aneignung, urteilte der Rechtswissenschaftler Reinhard Merkel in der FAZ sehr detailliert begründet. Übrigens hatte die Krim bereits zu Zeiten der Sowjetunion den Status einer autonomen Republik innerhalb der Ukrainischen SSR.
Anfang April 2014 wurden in der Ostukraine die «Volksrepubliken» Donezk und Lugansk ausgerufen. Die Kiewer Übergangsregierung ging unter der Bezeichnung «Anti-Terror-Operation» (ATO) militärisch gegen diesen, auch von Russland instrumentalisierten Widerstand vor. Zufällig war kurz zuvor CIA-Chef John Brennan in Kiew. Die Maßnahmen gingen unter dem seit Mai neuen ukrainischen Präsidenten, dem Milliardär Petro Poroschenko, weiter. Auch Wolodymyr Selenskyj beendete den Bürgerkrieg nicht, als er 2019 vom Präsidenten-Schauspieler, der Oligarchen entmachtet, zum Präsidenten wurde. Er fuhr fort, die eigene Bevölkerung zu bombardieren.
Mit dem Einmarsch russischer Truppen in die Ostukraine am 24. Februar 2022 begann die zweite Phase des Krieges. Die Wochen und Monate davor waren intensiv. Im November hatte die Ukraine mit den USA ein Abkommen über eine «strategische Partnerschaft» unterzeichnet. Darin sagten die Amerikaner ihre Unterstützung der EU- und NATO-Perspektive der Ukraine sowie quasi für die Rückeroberung der Krim zu. Dagegen ließ Putin der NATO und den USA im Dezember 2021 einen Vertragsentwurf über beiderseitige verbindliche Sicherheitsgarantien zukommen, den die NATO im Januar ablehnte. Im Februar eskalierte laut OSZE die Gewalt im Donbass.
Bereits wenige Wochen nach der Invasion, Ende März 2022, kam es in Istanbul zu Friedensverhandlungen, die fast zu einer Lösung geführt hätten. Dass der Krieg nicht damals bereits beendet wurde, lag daran, dass der Westen dies nicht wollte. Man war der Meinung, Russland durch die Ukraine in diesem Stellvertreterkrieg auf Dauer militärisch schwächen zu können. Angesichts von Hunderttausenden Toten, Verletzten und Traumatisierten, die als Folge seitdem zu beklagen sind, sowie dem Ausmaß der Zerstörung, fehlen einem die Worte.
Hasst der Westen die Russen?
Diese Frage drängt sich auf, wenn man das oft unerträglich feindselige Gebaren beobachtet, das beileibe nicht neu ist und vor Doppelmoral trieft. Russland und speziell die Person Wladimir Putins werden regelrecht dämonisiert, was gleichzeitig scheinbar jede Form von Diplomatie ausschließt.
Russlands militärische Stärke, seine geografische Lage, sein Rohstoffreichtum oder seine unabhängige diplomatische Tradition sind sicher Störfaktoren für das US-amerikanische Bestreben, der Boss in einer unipolaren Welt zu sein. Ein womöglich funktionierender eurasischer Kontinent, insbesondere gute Beziehungen zwischen Russland und Deutschland, war indes schon vor dem Ersten Weltkrieg eine Sorge des britischen Imperiums.
Ein «Vergehen» von Präsident Putin könnte gewesen sein, dass er die neoliberale Schocktherapie à la IWF und den Ausverkauf des Landes (auch an US-Konzerne) beendete, der unter seinem Vorgänger herrschte. Dabei zeigte er sich als Führungspersönlichkeit und als nicht so formbar wie Jelzin. Diese Aspekte allein sind aber heute vermutlich keine ausreichende Erklärung für ein derart gepflegtes Feindbild.
Der Historiker und Philosoph Hauke Ritz erweitert den Fokus der Fragestellung zu: «Warum hasst der Westen die Russen so sehr?», was er zum Beispiel mit dem Medienforscher Michael Meyen und mit der Politikwissenschaftlerin Ulrike Guérot bespricht. Ritz stellt die interessante These [11] auf, dass Russland eine Provokation für den Westen sei, welcher vor allem dessen kulturelles und intellektuelles Potenzial fürchte.
Die Russen sind Europäer aber anders, sagt Ritz. Diese «Fremdheit in der Ähnlichkeit» erzeuge vielleicht tiefe Ablehnungsgefühle. Obwohl Russlands Identität in der europäischen Kultur verwurzelt ist, verbinde es sich immer mit der Opposition in Europa. Als Beispiele nennt er die Kritik an der katholischen Kirche oder die Verbindung mit der Arbeiterbewegung. Christen, aber orthodox; Sozialismus statt Liberalismus. Das mache das Land zum Antagonisten des Westens und zu einer Bedrohung der Machtstrukturen in Europa.
Fazit
Selbstverständlich kann man Geschichte, Ereignisse und Entwicklungen immer auf verschiedene Arten lesen. Dieser Artikel, obwohl viel zu lang, konnte nur einige Aspekte der Ukraine-Tragödie anreißen, die in den offiziellen Darstellungen in der Regel nicht vorkommen. Mindestens dürfte damit jedoch klar geworden sein, dass die Russische Föderation bzw. Wladimir Putin nicht der alleinige Aggressor in diesem Konflikt ist. Das ist ein Stellvertreterkrieg zwischen USA/NATO (gut) und Russland (böse); die Ukraine (edel) wird dabei schlicht verheizt.
Das ist insofern von Bedeutung, als die gesamte europäische Kriegshysterie auf sorgsam kultivierten Freund-Feind-Bildern beruht. Nur so kann Konfrontation und Eskalation betrieben werden, denn damit werden die wahren Hintergründe und Motive verschleiert. Angst und Propaganda sind notwendig, damit die Menschen den Wahnsinn mitmachen. Sie werden belogen, um sie zuerst zu schröpfen und anschließend auf die Schlachtbank zu schicken. Das kann niemand wollen, außer den stets gleichen Profiteuren: die Rüstungs-Lobby und die großen Investoren, die schon immer an Zerstörung und Wiederaufbau verdient haben.
Apropos Investoren: Zu den Top-Verdienern und somit Hauptinteressenten an einer Fortführung des Krieges zählt BlackRock, einer der weltgrößten Vermögensverwalter. Der deutsche Bundeskanzler in spe, Friedrich Merz, der gerne «Taurus»-Marschflugkörper an die Ukraine liefern und die Krim-Brücke zerstören möchte, war von 2016 bis 2020 Aufsichtsratsvorsitzender von BlackRock in Deutschland. Aber das hat natürlich nichts zu sagen, der Mann macht nur seinen Job.
Es ist ein Spiel der Kräfte, es geht um Macht und strategische Kontrolle, um Geheimdienste und die Kontrolle der öffentlichen Meinung, um Bodenschätze, Rohstoffe, Pipelines und Märkte. Das klingt aber nicht sexy, «Demokratie und Menschenrechte» hört sich besser und einfacher an. Dabei wäre eine für alle Seiten förderliche Politik auch nicht so kompliziert; das Handwerkszeug dazu nennt sich Diplomatie. Noch einmal Gabriele Krone-Schmalz:
«Friedliche Politik ist nichts anderes als funktionierender Interessenausgleich. Da geht’s nicht um Moral.»
Die Situation in der Ukraine ist sicher komplex, vor allem wegen der inneren Zerrissenheit. Es dürfte nicht leicht sein, eine friedliche Lösung für das Zusammenleben zu finden, aber die Beteiligten müssen es vor allem wollen. Unter den gegebenen Umständen könnte eine sinnvolle Perspektive mit Neutralität und föderalen Strukturen zu tun haben.
Allen, die sich bis hierher durch die Lektüre gearbeitet (oder auch einfach nur runtergescrollt) haben, wünsche ich frohe Oster-Friedenstage!
[Titelbild: Pixabay; Abb. 1 und 2: nach Ganser/SIPER; Abb. 3: SIPER]
--- Quellen: ---
[1] Albrecht Müller, «Glaube wenig. Hinterfrage alles. Denke selbst.», Westend 2019
[2] Zwei nette Beispiele:
- ARD-faktenfinder (sic), «Viel Aufmerksamkeit für fragwürdige Experten», 03/2023
- Neue Zürcher Zeitung, «Aufstieg und Fall einer Russlandversteherin – die ehemalige ARD-Korrespondentin Gabriele Krone-Schmalz rechtfertigt seit Jahren Putins Politik», 12/2022
[3] George Washington University, «NATO Expansion: What Gorbachev Heard – Declassified documents show security assurances against NATO expansion to Soviet leaders from Baker, Bush, Genscher, Kohl, Gates, Mitterrand, Thatcher, Hurd, Major, and Woerner», 12/2017
[4] Beispielsweise Wladimir Putin bei seiner Rede im Deutschen Bundestag, 25/09/2001
[5] William Engdahl, «Full Spectrum Dominance, Totalitarian Democracy In The New World Order», edition.engdahl 2009
[6] Daniele Ganser, «Illegale Kriege – Wie die NATO-Länder die UNO sabotieren. Eine Chronik von Kuba bis Syrien», Orell Füssli 2016
[7] Gabriele Krone-Schmalz, «Mit Friedensjournalismus gegen ‘Kriegstüchtigkeit’», Vortrag und Diskussion an der Universität Hamburg, veranstaltet von engagierten Studenten, 16/01/2025\ → Hier ist ein ähnlicher Vortrag von ihr (Video), den ich mit spanischer Übersetzung gefunden habe.
[8] Für mehr Hintergrund und Details empfehlen sich z.B. folgende Bücher:
- Mathias Bröckers, Paul Schreyer, «Wir sind immer die Guten», Westend 2019
- Gabriele Krone-Schmalz, «Russland verstehen? Der Kampf um die Ukraine und die Arroganz des Westens», Westend 2023
- Patrik Baab, «Auf beiden Seiten der Front – Meine Reisen in die Ukraine», Fiftyfifty 2023
[9] vgl. Jonathan Mowat, «Washington's New World Order "Democratization" Template», 02/2005 und RAND Corporation, «Swarming and the Future of Conflict», 2000
[10] Bemerkenswert einige Beiträge, von denen man später nichts mehr wissen wollte:
- ARD Monitor, «Todesschüsse in Kiew: Wer ist für das Blutbad vom Maidan verantwortlich», 10/04/2014, Transkript hier
- Telepolis, «Blutbad am Maidan: Wer waren die Todesschützen?», 12/04/2014
- Telepolis, «Scharfschützenmorde in Kiew», 14/12/2014
- Deutschlandfunk, «Gefahr einer Spirale nach unten», Interview mit Günter Verheugen, 18/03/2014
- NDR Panorama, «Putsch in Kiew: Welche Rolle spielen die Faschisten?», 06/03/2014
[11] Hauke Ritz, «Vom Niedergang des Westens zur Neuerfindung Europas», 2024
Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
-
 @ bf47c19e:c3d2573b
2025-05-11 21:32:19
@ bf47c19e:c3d2573b
2025-05-11 21:32:19Bitkoin, kao jedinstvena digitalna valuta, postaje poznat široj javnosti u trenutku kada se pojavljuju prvi znaci svetske ekonomske krize a postojeći finansijski sistem počinje da pokazuje sve svoje slabosti. Danas, bitkoin, izaziva veliku pažnju svojim naglim skokovima i padovima.
Osnovna ideja o o decentralizovanim valutama potekla je od osnivača kripto-pank pokreta, među kojima su bili direktori kompanija naprednih tehnologija, univerzitetski profesori i istraživači iz oblasti matematike i fizike. Njihova ideja zasnovana je na anonimnoj, istovremenoj komunikaciji koja neće biti kontrolisana i nadgledana od neke treće strane u procesu.
Šta je kriptovaluta, ko je njen tvorac, kako do nje doći, kako trgovati i gde je čuvati, neka su od pitanja za čijim odgovorima tragamo u emisiji.
Sagovornici u emisiji su svi oni koji su u poslednjih godinu dana bili relevantni učesnici priča o kriptovaluti u Srbiji: osnivači Asocijacije bitkoin, predstavnici Narodne banke Srbije i predstavnici medija.
Montažer Milan Radičević
Urednik Aleksandra Šarković
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ 33baa074:3bb3a297
2025-05-12 00:49:33
@ 33baa074:3bb3a297
2025-05-12 00:49:33Real-time monitoring of oil concentration in water The basic principle of oil in water sensor is to use the characteristic that oil will produce fluorescence under ultraviolet light, and measure the fluorescence intensity to infer the concentration of oil. The sensor uses ultraviolet light as the excitation light source to illuminate the water sample to be tested. The oil absorbs ultraviolet light and excites fluorescence. The fluorescence signal is received by the photo detector and converted into an electrical signal, and then the strength of the electrical signal is measured to determine the concentration of oil in the water sample, so as to achieve real-time monitoring of the concentration of oil in the water.
 Multi-scenario water quality monitoring
Water source water quality monitoring
It can be used to monitor the water quality of water sources. By continuously monitoring the oil in the water source, the pollution source can be found in time, thereby ensuring the safety of drinking water and water supply.
Multi-scenario water quality monitoring
Water source water quality monitoring
It can be used to monitor the water quality of water sources. By continuously monitoring the oil in the water source, the pollution source can be found in time, thereby ensuring the safety of drinking water and water supply.Sewage treatment plant discharge monitoring Sewage treatment plants may produce oily wastewater in the process of treating sewage. The oil-in-water sensor can monitor the water quality of its discharge to ensure that it meets the discharge standards and avoids secondary pollution to the environment.
Monitoring of water bodies such as rivers and lakes Water bodies such as rivers and lakes may be polluted by oil substances, such as ship leakage and industrial wastewater discharge. This sensor can monitor the water quality of these water bodies, evaluate the pollution status, and provide a basis for pollution control.
Aquaculture monitoring The online oil-in-water monitor (including oil-in-water sensor) can transmit monitoring data in real time to help farmers understand the water quality. Farmers can use it to understand the oil content in the water body in real time, and reasonably release it according to the needs of fish to improve the growth rate and health level of fish; it can also timely detect abnormal conditions in the water body, such as oil pollution and bacterial growth, and take corresponding measures to avoid the occurrence of diseases and reduce breeding costs and risks; at the same time, it helps farmers better understand the growth of fish, reasonably arrange fishing time, avoid overfishing and resource depletion, and promote the sustainable use of aquatic resources.
Early warning and emergency response It has real-time monitoring and early warning functions, and can issue an alarm in time when abnormal conditions of oil substances in the water body (such as exceeding the pee-set safety threshold) are found, providing valuable time for emergency response and reducing losses caused by pollution.
Assisting scientific research The monitoring data of the sensor can be used in scientific research fields such as ecology and environmental chemistry, helping researchers to gain a deeper understanding of the distribution, migration and transformation of oil substances in water bodies, and provide a scientific basis for environmental protection and governance.
Monitoring of pollution sources and environmental changes By detecting oil substances in water bodies, the location of pollution sources and the types of pollutants can be determined, providing a basis for finding and controlling pollution sources; it can also monitor oil pollutants in water bodies to understand the impact of environmental changes on water bodies and take timely measures to protect water sources.
-
 @ c631e267:c2b78d3e
2025-04-18 15:53:07
@ c631e267:c2b78d3e
2025-04-18 15:53:07Verstand ohne Gefühl ist unmenschlich; \ Gefühl ohne Verstand ist Dummheit. \ Egon Bahr
Seit Jahren werden wir darauf getrimmt, dass Fakten eigentlich gefühlt seien. Aber nicht alles ist relativ und nicht alles ist nach Belieben interpretierbar. Diese Schokoladenhasen beispielsweise, die an Ostern in unseren Gefilden typisch sind, «ostern» zwar nicht, sondern sie sitzen in der Regel, trotzdem verwandelt sie das nicht in «Sitzhasen».
Nichts soll mehr gelten, außer den immer invasiveren Gesetzen. Die eigenen Traditionen und Wurzeln sind potenziell «pfui», um andere Menschen nicht auszuschließen, aber wir mögen uns toleranterweise an die fremden Symbole und Rituale gewöhnen. Dabei ist es mir prinzipiell völlig egal, ob und wann jemand ein Fastenbrechen feiert, am Karsamstag oder jedem anderen Tag oder nie – aber bitte freiwillig.
Und vor allem: Lasst die Finger von den Kindern! In Bern setzten kürzlich Demonstranten ein Zeichen gegen die zunehmende Verbreitung woker Ideologie im Bildungssystem und forderten ein Ende der sexuellen Indoktrination von Schulkindern.
Wenn es nicht wegen des heiklen Themas Migration oder wegen des Regenbogens ist, dann wegen des Klimas. Im Rahmen der «Netto Null»-Agenda zum Kampf gegen das angeblich teuflische CO2 sollen die Menschen ihre Ernährungsgewohnheiten komplett ändern. Nach dem Willen von Produzenten synthetischer Lebensmittel, wie Bill Gates, sollen wir baldmöglichst praktisch auf Fleisch und alle Milchprodukte wie Milch und Käse verzichten. Ein lukratives Geschäftsmodell, das neben der EU aktuell auch von einem britischen Lobby-Konsortium unterstützt wird.
Sollten alle ideologischen Stricke zu reißen drohen, ist da immer noch «der Putin». Die Unions-Europäer offenbaren sich dabei ständig mehr als Vertreter der Rüstungsindustrie. Allen voran zündelt Deutschland an der Kriegslunte, angeführt von einem scheinbar todesmutigen Kanzlerkandidaten Friedrich Merz. Nach dessen erneuter Aussage, «Taurus»-Marschflugkörper an Kiew liefern zu wollen, hat Russland eindeutig klargestellt, dass man dies als direkte Kriegsbeteiligung werten würde – «mit allen sich daraus ergebenden Konsequenzen für Deutschland».
Wohltuend sind Nachrichten über Aktivitäten, die sich der allgemeinen Kriegstreiberei entgegenstellen oder diese öffentlich hinterfragen. Dazu zählt auch ein Kongress kritischer Psychologen und Psychotherapeuten, der letzte Woche in Berlin stattfand. Die vielen Vorträge im Kontext von «Krieg und Frieden» deckten ein breites Themenspektrum ab, darunter Friedensarbeit oder die Notwendigkeit einer «Pädagogik der Kriegsuntüchtigkeit».
Der heutige «stille Freitag», an dem Christen des Leidens und Sterbens von Jesus gedenken, ist vielleicht unabhängig von jeder religiösen oder spirituellen Prägung eine passende Einladung zur Reflexion. In der Ruhe liegt die Kraft. In diesem Sinne wünsche ich Ihnen frohe Ostertage!
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 91bea5cd:1df4451c
2025-04-26 10:16:21
@ 91bea5cd:1df4451c
2025-04-26 10:16:21O Contexto Legal Brasileiro e o Consentimento
No ordenamento jurídico brasileiro, o consentimento do ofendido pode, em certas circunstâncias, afastar a ilicitude de um ato que, sem ele, configuraria crime (como lesão corporal leve, prevista no Art. 129 do Código Penal). Contudo, o consentimento tem limites claros: não é válido para bens jurídicos indisponíveis, como a vida, e sua eficácia é questionável em casos de lesões corporais graves ou gravíssimas.
A prática de BDSM consensual situa-se em uma zona complexa. Em tese, se ambos os parceiros são adultos, capazes, e consentiram livre e informadamente nos atos praticados, sem que resultem em lesões graves permanentes ou risco de morte não consentido, não haveria crime. O desafio reside na comprovação desse consentimento, especialmente se uma das partes, posteriormente, o negar ou alegar coação.
A Lei Maria da Penha (Lei nº 11.340/2006)
A Lei Maria da Penha é um marco fundamental na proteção da mulher contra a violência doméstica e familiar. Ela estabelece mecanismos para coibir e prevenir tal violência, definindo suas formas (física, psicológica, sexual, patrimonial e moral) e prevendo medidas protetivas de urgência.
Embora essencial, a aplicação da lei em contextos de BDSM pode ser delicada. Uma alegação de violência por parte da mulher, mesmo que as lesões ou situações decorram de práticas consensuais, tende a receber atenção prioritária das autoridades, dada a presunção de vulnerabilidade estabelecida pela lei. Isso pode criar um cenário onde o parceiro masculino enfrenta dificuldades significativas em demonstrar a natureza consensual dos atos, especialmente se não houver provas robustas pré-constituídas.
Outros riscos:
Lesão corporal grave ou gravíssima (art. 129, §§ 1º e 2º, CP), não pode ser justificada pelo consentimento, podendo ensejar persecução penal.
Crimes contra a dignidade sexual (arts. 213 e seguintes do CP) são de ação pública incondicionada e independem de representação da vítima para a investigação e denúncia.
Riscos de Falsas Acusações e Alegação de Coação Futura
Os riscos para os praticantes de BDSM, especialmente para o parceiro que assume o papel dominante ou que inflige dor/restrição (frequentemente, mas não exclusivamente, o homem), podem surgir de diversas frentes:
- Acusações Externas: Vizinhos, familiares ou amigos que desconhecem a natureza consensual do relacionamento podem interpretar sons, marcas ou comportamentos como sinais de abuso e denunciar às autoridades.
- Alegações Futuras da Parceira: Em caso de término conturbado, vingança, arrependimento ou mudança de perspectiva, a parceira pode reinterpretar as práticas passadas como abuso e buscar reparação ou retaliação através de uma denúncia. A alegação pode ser de que o consentimento nunca existiu ou foi viciado.
- Alegação de Coação: Uma das formas mais complexas de refutar é a alegação de que o consentimento foi obtido mediante coação (física, moral, psicológica ou econômica). A parceira pode alegar, por exemplo, que se sentia pressionada, intimidada ou dependente, e que seu "sim" não era genuíno. Provar a ausência de coação a posteriori é extremamente difícil.
- Ingenuidade e Vulnerabilidade Masculina: Muitos homens, confiando na dinâmica consensual e na parceira, podem negligenciar a necessidade de precauções. A crença de que "isso nunca aconteceria comigo" ou a falta de conhecimento sobre as implicações legais e o peso processual de uma acusação no âmbito da Lei Maria da Penha podem deixá-los vulneráveis. A presença de marcas físicas, mesmo que consentidas, pode ser usada como evidência de agressão, invertendo o ônus da prova na prática, ainda que não na teoria jurídica.
Estratégias de Prevenção e Mitigação
Não existe um método infalível para evitar completamente o risco de uma falsa acusação, mas diversas medidas podem ser adotadas para construir um histórico de consentimento e reduzir vulnerabilidades:
- Comunicação Explícita e Contínua: A base de qualquer prática BDSM segura é a comunicação constante. Negociar limites, desejos, palavras de segurança ("safewords") e expectativas antes, durante e depois das cenas é crucial. Manter registros dessas negociações (e-mails, mensagens, diários compartilhados) pode ser útil.
-
Documentação do Consentimento:
-
Contratos de Relacionamento/Cena: Embora a validade jurídica de "contratos BDSM" seja discutível no Brasil (não podem afastar normas de ordem pública), eles servem como forte evidência da intenção das partes, da negociação detalhada de limites e do consentimento informado. Devem ser claros, datados, assinados e, idealmente, reconhecidos em cartório (para prova de data e autenticidade das assinaturas).
-
Registros Audiovisuais: Gravar (com consentimento explícito para a gravação) discussões sobre consentimento e limites antes das cenas pode ser uma prova poderosa. Gravar as próprias cenas é mais complexo devido a questões de privacidade e potencial uso indevido, mas pode ser considerado em casos específicos, sempre com consentimento mútuo documentado para a gravação.
Importante: a gravação deve ser com ciência da outra parte, para não configurar violação da intimidade (art. 5º, X, da Constituição Federal e art. 20 do Código Civil).
-
-
Testemunhas: Em alguns contextos de comunidade BDSM, a presença de terceiros de confiança durante negociações ou mesmo cenas pode servir como testemunho, embora isso possa alterar a dinâmica íntima do casal.
- Estabelecimento Claro de Limites e Palavras de Segurança: Definir e respeitar rigorosamente os limites (o que é permitido, o que é proibido) e as palavras de segurança é fundamental. O desrespeito a uma palavra de segurança encerra o consentimento para aquele ato.
- Avaliação Contínua do Consentimento: O consentimento não é um cheque em branco; ele deve ser entusiástico, contínuo e revogável a qualquer momento. Verificar o bem-estar do parceiro durante a cena ("check-ins") é essencial.
- Discrição e Cuidado com Evidências Físicas: Ser discreto sobre a natureza do relacionamento pode evitar mal-entendidos externos. Após cenas que deixem marcas, é prudente que ambos os parceiros estejam cientes e de acordo, talvez documentando por fotos (com data) e uma nota sobre a consensualidade da prática que as gerou.
- Aconselhamento Jurídico Preventivo: Consultar um advogado especializado em direito de família e criminal, com sensibilidade para dinâmicas de relacionamento alternativas, pode fornecer orientação personalizada sobre as melhores formas de documentar o consentimento e entender os riscos legais específicos.
Observações Importantes
- Nenhuma documentação substitui a necessidade de consentimento real, livre, informado e contínuo.
- A lei brasileira protege a "integridade física" e a "dignidade humana". Práticas que resultem em lesões graves ou que violem a dignidade de forma não consentida (ou com consentimento viciado) serão ilegais, independentemente de qualquer acordo prévio.
- Em caso de acusação, a existência de documentação robusta de consentimento não garante a absolvição, mas fortalece significativamente a defesa, ajudando a demonstrar a natureza consensual da relação e das práticas.
-
A alegação de coação futura é particularmente difícil de prevenir apenas com documentos. Um histórico consistente de comunicação aberta (whatsapp/telegram/e-mails), respeito mútuo e ausência de dependência ou controle excessivo na relação pode ajudar a contextualizar a dinâmica como não coercitiva.
-
Cuidado com Marcas Visíveis e Lesões Graves Práticas que resultam em hematomas severos ou lesões podem ser interpretadas como agressão, mesmo que consentidas. Evitar excessos protege não apenas a integridade física, mas também evita questionamentos legais futuros.
O que vem a ser consentimento viciado
No Direito, consentimento viciado é quando a pessoa concorda com algo, mas a vontade dela não é livre ou plena — ou seja, o consentimento existe formalmente, mas é defeituoso por alguma razão.
O Código Civil brasileiro (art. 138 a 165) define várias formas de vício de consentimento. As principais são:
Erro: A pessoa se engana sobre o que está consentindo. (Ex.: A pessoa acredita que vai participar de um jogo leve, mas na verdade é exposta a práticas pesadas.)
Dolo: A pessoa é enganada propositalmente para aceitar algo. (Ex.: Alguém mente sobre o que vai acontecer durante a prática.)
Coação: A pessoa é forçada ou ameaçada a consentir. (Ex.: "Se você não aceitar, eu termino com você" — pressão emocional forte pode ser vista como coação.)
Estado de perigo ou lesão: A pessoa aceita algo em situação de necessidade extrema ou abuso de sua vulnerabilidade. (Ex.: Alguém em situação emocional muito fragilizada é induzida a aceitar práticas que normalmente recusaria.)
No contexto de BDSM, isso é ainda mais delicado: Mesmo que a pessoa tenha "assinado" um contrato ou dito "sim", se depois ela alegar que seu consentimento foi dado sob medo, engano ou pressão psicológica, o consentimento pode ser considerado viciado — e, portanto, juridicamente inválido.
Isso tem duas implicações sérias:
-
O crime não se descaracteriza: Se houver vício, o consentimento é ignorado e a prática pode ser tratada como crime normal (lesão corporal, estupro, tortura, etc.).
-
A prova do consentimento precisa ser sólida: Mostrando que a pessoa estava informada, lúcida, livre e sem qualquer tipo de coação.
Consentimento viciado é quando a pessoa concorda formalmente, mas de maneira enganada, forçada ou pressionada, tornando o consentimento inútil para efeitos jurídicos.
Conclusão
Casais que praticam BDSM consensual no Brasil navegam em um terreno que exige não apenas confiança mútua e comunicação excepcional, mas também uma consciência aguçada das complexidades legais e dos riscos de interpretações equivocadas ou acusações mal-intencionadas. Embora o BDSM seja uma expressão legítima da sexualidade humana, sua prática no Brasil exige responsabilidade redobrada. Ter provas claras de consentimento, manter a comunicação aberta e agir com prudência são formas eficazes de se proteger de falsas alegações e preservar a liberdade e a segurança de todos os envolvidos. Embora leis controversas como a Maria da Penha sejam "vitais" para a proteção contra a violência real, os praticantes de BDSM, e em particular os homens nesse contexto, devem adotar uma postura proativa e prudente para mitigar os riscos inerentes à potencial má interpretação ou instrumentalização dessas práticas e leis, garantindo que a expressão de sua consensualidade esteja resguardada na medida do possível.
Importante: No Brasil, mesmo com tudo isso, o Ministério Público pode denunciar por crime como lesão corporal grave, estupro ou tortura, independente de consentimento. Então a prudência nas práticas é fundamental.
Aviso Legal: Este artigo tem caráter meramente informativo e não constitui aconselhamento jurídico. As leis e interpretações podem mudar, e cada situação é única. Recomenda-se buscar orientação de um advogado qualificado para discutir casos específicos.
Se curtiu este artigo faça uma contribuição, se tiver algum ponto relevante para o artigo deixe seu comentário.
-
 @ 8125b911:a8400883
2025-04-25 07:02:35
@ 8125b911:a8400883
2025-04-25 07:02:35In Nostr, all data is stored as events. Decentralization is achieved by storing events on multiple relays, with signatures proving the ownership of these events. However, if you truly want to own your events, you should run your own relay to store them. Otherwise, if the relays you use fail or intentionally delete your events, you'll lose them forever.
For most people, running a relay is complex and costly. To solve this issue, I developed nostr-relay-tray, a relay that can be easily run on a personal computer and accessed over the internet.
Project URL: https://github.com/CodyTseng/nostr-relay-tray
This article will guide you through using nostr-relay-tray to run your own relay.
Download
Download the installation package for your operating system from the GitHub Release Page.
| Operating System | File Format | | --------------------- | ---------------------------------- | | Windows |
nostr-relay-tray.Setup.x.x.x.exe| | macOS (Apple Silicon) |nostr-relay-tray-x.x.x-arm64.dmg| | macOS (Intel) |nostr-relay-tray-x.x.x.dmg| | Linux | You should know which one to use |Installation
Since this app isn’t signed, you may encounter some obstacles during installation. Once installed, an ostrich icon will appear in the status bar. Click on the ostrich icon, and you'll see a menu where you can click the "Dashboard" option to open the relay's control panel for further configuration.

macOS Users:
- On first launch, go to "System Preferences > Security & Privacy" and click "Open Anyway."
- If you encounter a "damaged" message, run the following command in the terminal to remove the restrictions:
bash sudo xattr -rd com.apple.quarantine /Applications/nostr-relay-tray.appWindows Users:
- On the security warning screen, click "More Info > Run Anyway."
Connecting
By default, nostr-relay-tray is only accessible locally through
ws://localhost:4869/, which makes it quite limited. Therefore, we need to expose it to the internet.In the control panel, click the "Proxy" tab and toggle the switch. You will then receive a "Public address" that you can use to access your relay from anywhere. It's that simple.
Next, add this address to your relay list and position it as high as possible in the list. Most clients prioritize connecting to relays that appear at the top of the list, and relays lower in the list are often ignored.

Restrictions
Next, we need to set up some restrictions to prevent the relay from storing events that are irrelevant to you and wasting storage space. nostr-relay-tray allows for flexible and fine-grained configuration of which events to accept, but some of this is more complex and will not be covered here. If you're interested, you can explore this further later.
For now, I'll introduce a simple and effective strategy: WoT (Web of Trust). You can enable this feature in the "WoT & PoW" tab. Before enabling, you'll need to input your pubkey.
There's another important parameter,
Depth, which represents the relationship depth between you and others. Someone you follow has a depth of 1, someone they follow has a depth of 2, and so on.- Setting this parameter to 0 means your relay will only accept your own events.
- Setting it to 1 means your relay will accept events from you and the people you follow.
- Setting it to 2 means your relay will accept events from you, the people you follow, and the people they follow.
Currently, the maximum value for this parameter is 2.

Conclusion
You've now successfully run your own relay and set a simple restriction to prevent it from storing irrelevant events.
If you encounter any issues during use, feel free to submit an issue on GitHub, and I'll respond as soon as possible.
Not your relay, not your events.
-
 @ bf47c19e:c3d2573b
2025-05-11 20:50:05
@ bf47c19e:c3d2573b
2025-05-11 20:50:05„Ova mašina ozelenjava“, koji predstavlja Swan Bitcoin, je dokumentarac koji istražuje složen i nijansiran odnos između Bitkoina i energije. Producent filma je Enrike Pozner, dok je režiser nagrađivani britanski filmski stvaralac Džejmi King čija je serija „Ukradi ovaj film“ (2006–2010) bila jedan od najpreuzimanijih dokumentaraca svih vremena.
U filmu „Ova mašina ozelenjava“ učestvuje glavna ekonomska savetnica Swan-a Lin Alden zajedno sa Aleksom Gladstajnom, Nikom Karterom i mnogim drugima. „Ova mašina ozelenjava“ razbija mnoge zablude o rudarenju Bitkoina i iznosi ubedljive argumente za Bitkoin kao neto-pozitivan faktor za životnu sredinu.
Prevod: bitcoin-balkan.com
-
 @ bf47c19e:c3d2573b
2025-05-11 20:24:44
@ bf47c19e:c3d2573b
2025-05-11 20:24:44Kratki dokumentarac zasnovan na istoimenoj knjizi Mareja Rotbarda. Teme uključuju: opasnosti koje sa sobom nosi država blagostanja, monetarne politike zasnovane na dugu, oporezivanje bez zastupanja i ostala sredstva državnog nasilja.
Autor filma: @rjames_BTC
Zvanični vebsajt filma: anatomystatefilm.com
Prevod: bitcoin-balkan.com
-
 @ c631e267:c2b78d3e
2025-04-04 18:47:27
@ c631e267:c2b78d3e
2025-04-04 18:47:27Zwei mal drei macht vier, \ widewidewitt und drei macht neune, \ ich mach mir die Welt, \ widewide wie sie mir gefällt. \ Pippi Langstrumpf
Egal, ob Koalitionsverhandlungen oder politischer Alltag: Die Kontroversen zwischen theoretisch verschiedenen Parteien verschwinden, wenn es um den Kampf gegen politische Gegner mit Rückenwind geht. Wer den Alteingesessenen die Pfründe ernsthaft streitig machen könnte, gegen den werden nicht nur «Brandmauern» errichtet, sondern der wird notfalls auch strafrechtlich verfolgt. Doppelstandards sind dabei selbstverständlich inklusive.
In Frankreich ist diese Woche Marine Le Pen wegen der Veruntreuung von EU-Geldern von einem Gericht verurteilt worden. Als Teil der Strafe wurde sie für fünf Jahre vom passiven Wahlrecht ausgeschlossen. Obwohl das Urteil nicht rechtskräftig ist – Le Pen kann in Berufung gehen –, haben die Richter das Verbot, bei Wahlen anzutreten, mit sofortiger Wirkung verhängt. Die Vorsitzende des rechtsnationalen Rassemblement National (RN) galt als aussichtsreiche Kandidatin für die Präsidentschaftswahl 2027.
Das ist in diesem Jahr bereits der zweite gravierende Fall von Wahlbeeinflussung durch die Justiz in einem EU-Staat. In Rumänien hatte Călin Georgescu im November die erste Runde der Präsidentenwahl überraschend gewonnen. Das Ergebnis wurde später annulliert, die behauptete «russische Wahlmanipulation» konnte jedoch nicht bewiesen werden. Die Kandidatur für die Wahlwiederholung im Mai wurde Georgescu kürzlich durch das Verfassungsgericht untersagt.
Die Veruntreuung öffentlicher Gelder muss untersucht und geahndet werden, das steht außer Frage. Diese Anforderung darf nicht selektiv angewendet werden. Hingegen mussten wir in der Vergangenheit bei ungleich schwerwiegenderen Fällen von (mutmaßlichem) Missbrauch ganz andere Vorgehensweisen erleben, etwa im Fall der heutigen EZB-Chefin Christine Lagarde oder im «Pfizergate»-Skandal um die Präsidentin der EU-Kommission Ursula von der Leyen.
Wenngleich derartige Angelegenheiten formal auf einer rechtsstaatlichen Grundlage beruhen mögen, so bleibt ein bitterer Beigeschmack. Es stellt sich die Frage, ob und inwieweit die Justiz politisch instrumentalisiert wird. Dies ist umso interessanter, als die Gewaltenteilung einen essenziellen Teil jeder demokratischen Ordnung darstellt, während die Bekämpfung des politischen Gegners mit juristischen Mitteln gerade bei den am lautesten rufenden Verteidigern «unserer Demokratie» populär zu sein scheint.
Die Delegationen von CDU/CSU und SPD haben bei ihren Verhandlungen über eine Regierungskoalition genau solche Maßnahmen diskutiert. «Im Namen der Wahrheit und der Demokratie» möchte man noch härter gegen «Desinformation» vorgehen und dafür zum Beispiel den Digital Services Act der EU erweitern. Auch soll der Tatbestand der Volksverhetzung verschärft werden – und im Entzug des passiven Wahlrechts münden können. Auf europäischer Ebene würde Friedrich Merz wohl gerne Ungarn das Stimmrecht entziehen.
Der Pegel an Unzufriedenheit und Frustration wächst in großen Teilen der Bevölkerung kontinuierlich. Arroganz, Machtmissbrauch und immer abstrusere Ausreden für offensichtlich willkürliche Maßnahmen werden kaum verhindern, dass den etablierten Parteien die Unterstützung entschwindet. In Deutschland sind die Umfrageergebnisse der AfD ein guter Gradmesser dafür.
[Vorlage Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ c631e267:c2b78d3e
2025-04-03 07:42:25
@ c631e267:c2b78d3e
2025-04-03 07:42:25Spanien bleibt einer der Vorreiter im europäischen Prozess der totalen Überwachung per Digitalisierung. Seit Mittwoch ist dort der digitale Personalausweis verfügbar. Dabei handelt es sich um eine Regierungs-App, die auf dem Smartphone installiert werden muss und in den Stores von Google und Apple zu finden ist. Per Dekret von Regierungschef Pedro Sánchez und Zustimmung des Ministerrats ist diese Maßnahme jetzt in Kraft getreten.
Mit den üblichen Argumenten der Vereinfachung, des Komforts, der Effizienz und der Sicherheit preist das Innenministerium die «Innovation» an. Auch die Beteuerung, dass die digitale Variante parallel zum physischen Ausweis existieren wird und diesen nicht ersetzen soll, fehlt nicht. Während der ersten zwölf Monate wird «der Neue» noch nicht für alle Anwendungsfälle gültig sein, ab 2026 aber schon.
Dass die ganze Sache auch «Risiken und Nebenwirkungen» haben könnte, wird in den Mainstream-Medien eher selten thematisiert. Bestenfalls wird der Aspekt der Datensicherheit angesprochen, allerdings in der Regel direkt mit dem Regierungsvokabular von den «maximalen Sicherheitsgarantien» abgehandelt. Dennoch gibt es einige weitere Aspekte, die Bürger mit etwas Sinn für Privatsphäre bedenken sollten.
Um sich die digitale Version des nationalen Ausweises besorgen zu können (eine App mit dem Namen MiDNI), muss man sich vorab online registrieren. Dabei wird die Identität des Bürgers mit seiner mobilen Telefonnummer verknüpft. Diese obligatorische fixe Verdrahtung kennen wir von diversen anderen Apps und Diensten. Gleichzeitig ist das die Basis für eine perfekte Lokalisierbarkeit der Person.
Für jeden Vorgang der Identifikation in der Praxis wird später «eine Verbindung zu den Servern der Bundespolizei aufgebaut». Die Daten des Individuums werden «in Echtzeit» verifiziert und im Erfolgsfall von der Polizei signiert zurückgegeben. Das Ergebnis ist ein QR-Code mit zeitlich begrenzter Gültigkeit, der an Dritte weitergegeben werden kann.
Bei derartigen Szenarien sträuben sich einem halbwegs kritischen Staatsbürger die Nackenhaare. Allein diese minimale Funktionsbeschreibung lässt die totale Überwachung erkennen, die damit ermöglicht wird. Jede Benutzung des Ausweises wird künftig registriert, hinterlässt also Spuren. Und was ist, wenn die Server der Polizei einmal kein grünes Licht geben? Das wäre spätestens dann ein Problem, wenn der digitale doch irgendwann der einzig gültige Ausweis ist: Dann haben wir den abschaltbaren Bürger.
Dieser neue Vorstoß der Regierung von Pedro Sánchez ist ein weiterer Schritt in Richtung der «totalen Digitalisierung» des Landes, wie diese Politik in manchen Medien – nicht einmal kritisch, sondern sehr naiv – genannt wird. Ebenso verharmlosend wird auch erwähnt, dass sich das spanische Projekt des digitalen Ausweises nahtlos in die Initiativen der EU zu einer digitalen Identität für alle Bürger sowie des digitalen Euro einreiht.
In Zukunft könnte der neue Ausweis «auch in andere staatliche und private digitale Plattformen integriert werden», wie das Medienportal Cope ganz richtig bemerkt. Das ist die Perspektive.
[Titelbild: Pixabay]
Dazu passend:
Nur Abschied vom Alleinfahren? Monströse spanische Überwachungsprojekte gemäß EU-Norm
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ bf47c19e:c3d2573b
2025-05-11 20:15:51
@ bf47c19e:c3d2573b
2025-05-11 20:15:51U društvu koje koristi čvrst novac, jedini način sticanja bogatstva je stvaranje vrednosti za druge. Šta se jbt desilo 1971?
Autor filma: @rjames_BTC
Zvanični vebsajt: hardmoneyfilm.com
Prevod: bitcoin-balkan.com
-
 @ bf47c19e:c3d2573b
2025-05-11 19:29:26
@ bf47c19e:c3d2573b
2025-05-11 19:29:26"Misterija Satoši - Poreklo bitkoina" je francuski dokumentarno-animirani serijal koji dešifruje unutrašnje funkcionisanje bitkoin revolucije, dok istražuje identitet njenog tvorca.
Prvu decentralizovanu i pouzdanu kriptovalutu – bitkoin, osnovao je Satoši Nakamoto 3. januara 2009. godine. On je nestao 2011. i od tada ostaje anoniman, a njegov identitet je predmet svakakvih spekulacija. Tokom poslednjih 12 godina, vrednost bitkoina je porasla sa 0,001 na 69.000 dolara. Svi, od vlada do velikih korporacija, zainteresovali su se za Satošijev izum. Ko je Satoši Nakamoto? Kako je njegov izum postao toliko popularan? Šta nam bitkoin govori o svetu u kome živimo?
Ovaj serijal se prikazivao na Radio-televiziji Srbije (RTS 3) u sklopu novogodišnjeg muzičkog i filmskog programa 2022/2023. godine.
Naslov originala: "Le Mystère Satoshi"
Copyright: ARTE.TV
-
 @ 6e64b83c:94102ee8
2025-04-23 20:23:34
@ 6e64b83c:94102ee8
2025-04-23 20:23:34How to Run Your Own Nostr Relay on Android with Cloudflare Domain
Prerequisites
- Install Citrine on your Android device:
- Visit https://github.com/greenart7c3/Citrine/releases
- Download the latest release using:
- zap.store
- Obtainium
- F-Droid
- Or download the APK directly
-
Note: You may need to enable "Install from Unknown Sources" in your Android settings
-
Domain Requirements:
- Purchase a domain if you don't have one
-
Transfer your domain to Cloudflare if it's not already there (for free SSL certificates and cloudflared support)
-
Tools to use:
- nak (the nostr army knife):
- Download from https://github.com/fiatjaf/nak/releases
- Installation steps:
-
For Linux/macOS: ```bash # Download the appropriate version for your system wget https://github.com/fiatjaf/nak/releases/latest/download/nak-linux-amd64 # for Linux # or wget https://github.com/fiatjaf/nak/releases/latest/download/nak-darwin-amd64 # for macOS
# Make it executable chmod +x nak-*
# Move to a directory in your PATH sudo mv nak-* /usr/local/bin/nak
- For Windows:batch # Download the Windows version curl -L -o nak.exe https://github.com/fiatjaf/nak/releases/latest/download/nak-windows-amd64.exe# Move to a directory in your PATH (e.g., C:\Windows) move nak.exe C:\Windows\nak.exe
- Verify installation:bash nak --version ```
Setting Up Citrine
- Open the Citrine app
- Start the server
- You'll see it running on
ws://127.0.0.1:4869(local network only) - Go to settings and paste your npub into "Accept events signed by" inbox and press the + button. This prevents others from publishing events to your personal relay.
Installing Required Tools
- Install Termux from Google Play Store
- Open Termux and run:
bash pkg update && pkg install wget wget https://github.com/cloudflare/cloudflared/releases/latest/download/cloudflared-linux-arm64.deb dpkg -i cloudflared-linux-arm64.debCloudflare Authentication
- Run the authentication command:
bash cloudflared tunnel login - Follow the instructions:
- Copy the provided URL to your browser
- Log in to your Cloudflare account
- If the URL expires, copy it again after logging in
Creating the Tunnel
- Create a new tunnel:
bash cloudflared tunnel create <TUNNEL_NAME> - Choose any name you prefer for your tunnel
-
Copy the tunnel ID after creating the tunnel
-
Create and configure the tunnel config:
bash touch ~/.cloudflared/config.yml nano ~/.cloudflared/config.yml -
Add this configuration (replace the placeholders with your values): ```yaml tunnel:
credentials-file: /data/data/com.termux/files/home/.cloudflared/ .json ingress: - hostname: nostr.yourdomain.com service: ws://localhost:4869
- service: http_status:404 ```
- Note: In nano editor:
CTRL+Oand Enter to saveCTRL+Xto exit
-
Note: Check the credentials file path in the logs
-
Validate your configuration:
bash cloudflared tunnel validate -
Start the tunnel:
bash cloudflared tunnel run my-relay
Preventing Android from Killing the Tunnel
Run these commands to maintain tunnel stability:
bash date && apt install termux-tools && termux-setup-storage && termux-wake-lock echo "nameserver 1.1.1.1" > $PREFIX/etc/resolv.confTip: You can open multiple Termux sessions by swiping from the left edge of the screen while keeping your tunnel process running.
Updating Your Outbox Model Relays
Once your relay is running and accessible via your domain, you'll want to update your relay list in the Nostr network. This ensures other clients know about your relay and can connect to it.
Decoding npub (Public Key)
Private keys (nsec) and public keys (npub) are encoded in bech32 format, which includes: - A prefix (like nsec1, npub1 etc.) - The encoded data - A checksum
This format makes keys: - Easy to distinguish - Hard to copy incorrectly
However, most tools require these keys in hexadecimal (hex) format.
To decode an npub string to its hex format:
bash nak decode nostr:npub1dejts0qlva8mqzjlrxqkc2tmvs2t7elszky5upxaf3jha9qs9m5q605uc4Change it with your own npub.
bash { "pubkey": "6e64b83c1f674fb00a5f19816c297b6414bf67f015894e04dd4c657e94102ee8" }Copy the pubkey value in quotes.
Create a kind 10002 event with your relay list:
- Include your new relay with write permissions
- Include other relays you want to read from and write to, omit 3rd parameter to make it both read and write
Example format:
json { "kind": 10002, "tags": [ ["r", "wss://your-relay-domain.com", "write"], ["r", "wss://eden.nostr.land/"], ["r", "wss://nos.lol/"], ["r", "wss://nostr.bitcoiner.social/"], ["r", "wss://nostr.mom/"], ["r", "wss://relay.primal.net/"], ["r", "wss://nostr.wine/", "read"], ["r", "wss://relay.damus.io/"], ["r", "wss://relay.nostr.band/"], ["r", "wss://relay.snort.social/"] ], "content": "" }Save it to a file called
event.jsonNote: Add or remove any relays you want. To check your existing 10002 relays: - Visit https://nostr.band/?q=by%3Anpub1dejts0qlva8mqzjlrxqkc2tmvs2t7elszky5upxaf3jha9qs9m5q605uc4+++kind%3A10002 - nostr.band is an indexing service, it probably has your relay list. - Replace
npub1xxxin the URL with your own npub - Click "VIEW JSON" from the menu to see the raw event - Or use thenaktool if you know the relaysbash nak req -k 10002 -a <your-pubkey> wss://relay1.com wss://relay2.comReplace `<your-pubkey>` with your public key in hex format (you can get it using `nak decode <your-npub>`)- Sign and publish the event:
- Use a Nostr client that supports kind 10002 events
- Or use the
nakcommand-line tool:bash nak event --sec ncryptsec1... wss://relay1.com wss://relay2.com $(cat event.json)
Important Security Notes: 1. Never share your nsec (private key) with anyone 2. Consider using NIP-49 encrypted keys for better security 3. Never paste your nsec or private key into the terminal. The command will be saved in your shell history, exposing your private key. To clear the command history: - For bash: use
history -c- For zsh: usefc -Wto write history to file, thenfc -pto read it back - Or manually edit your shell history file (e.g.,~/.zsh_historyor~/.bash_history) 4. if you're usingzsh, usefc -pto prevent the next command from being saved to history 5. Or temporarily disable history before running sensitive commands:bash unset HISTFILE nak key encrypt ... set HISTFILEHow to securely create NIP-49 encypted private key
```bash
Read your private key (input will be hidden)
read -s SECRET
Read your password (input will be hidden)
read -s PASSWORD
encrypt command
echo "$SECRET" | nak key encrypt "$PASSWORD"
copy and paste the ncryptsec1 text from the output
read -s ENCRYPTED nak key decrypt "$ENCRYPTED"
clear variables from memory
unset SECRET PASSWORD ENCRYPTED ```
On a Windows command line, to read from stdin and use the variables in
nakcommands, you can use a combination ofset /pto read input and then use those variables in your command. Here's an example:```bash @echo off set /p "SECRET=Enter your secret key: " set /p "PASSWORD=Enter your password: "
echo %SECRET%| nak key encrypt %PASSWORD%
:: Clear the sensitive variables set "SECRET=" set "PASSWORD=" ```
If your key starts with
ncryptsec1, thenaktool will securely prompt you for a password when using the--secparameter, unless the command is used with a pipe< >or|.bash nak event --sec ncryptsec1... wss://relay1.com wss://relay2.com $(cat event.json)- Verify the event was published:
- Check if your relay list is visible on other relays
-
Use the
naktool to fetch your kind 10002 events:bash nak req -k 10002 -a <your-pubkey> wss://relay1.com wss://relay2.com -
Testing your relay:
- Try connecting to your relay using different Nostr clients
- Verify you can both read from and write to your relay
- Check if events are being properly stored and retrieved
- Tip: Use multiple Nostr clients to test different aspects of your relay
Note: If anyone in the community has a more efficient method of doing things like updating outbox relays, please share your insights in the comments. Your expertise would be greatly appreciated!
-
 @ bf47c19e:c3d2573b
2025-05-11 18:57:51
@ bf47c19e:c3d2573b
2025-05-11 18:57:51Originalni tekst na vice.com.
Davno pre nego što je postala šef najdesnije italijanske vlade od Drugog svetskog rata, Đorđa Meloni je kritikovala ono što je nazvala francuskom „kolonijalnom valutom“.
U snimku italijanske televizije iz 2019. koji je prošlog meseca postao megaviralan, Meloni je optužila Francusku da koristi CFA franak za eksploataciju resursa 14 afričkih zemalja i vrši finansijsku dominaciju nad njima. Određene stvari koje je tvrdila u videu nisu baš tačne, ali CFA franak jeste kontroverzan.
CFA franak je stvoren 1945. da bude valuta „francuskih kolonija u Africi“, a pošto Francuska kontroliše njegovo štampanje i promet, francuska vlada i dalje ima finansijsku kontrolu nad dobrim delom zapadnoafričke zemlje i više od 180 miliona ljudi. Dok su francuski zvaničnici ranije nazivali ovu valutu „činom velikodušnosti prema kolonijama“, o njenoj upotrebi se sada žestoko raspravlja.
Neke od afričkih nacija borile su se protiv valute, uključujući građane koji su razbijali prodavnice povezane sa Francuskom i osuđivali francuski jezik koji se uči u školama.
Jedna od onih 14 afričkih zemalja koja još uvek koristi CFA franak je Centralnoafrička Republika, država bez izlaza na more u kojoj živi oko 5 miliona ljudi i jedna od najsiromašnijih zemalja na svetu.
 Predsednik CAR Faustin-Aršanž Touadera govori na COP27 u Egiptu ranije ove godine. Foto: Gehad Hamdi/savez za slike preko Getti Image-a
Predsednik CAR Faustin-Aršanž Touadera govori na COP27 u Egiptu ranije ove godine. Foto: Gehad Hamdi/savez za slike preko Getti Image-aAli dok druge afričke nacije razmatraju odbacivanje CFA franka, CAR je jedna od prvih koja je zaista uradila nešto po tom pitanju, a ranije ove godine postala je prva zemlja u Africi i tek druga u svetu koja je usvojila Bitcoin kao legalnu valutu.
„Alternativa gotovini je kriptovaluta“, rekao je predsednik Faustin-Aršanž Touadera. „Za nas formalna ekonomija više nije opcija”.
Dok su prve najave o bitkoinu izazvale konfuziju, međunarodne nesuglasice i reakcije, vlada CAR-a je nastavila sa uvođenjem. Osam meseci kasnije, mnogi ljudi širom sveta, pa čak i građani CAR-a, možda nisu ni svesni da se promena dogodila.
U CAR samo 14 odsto stanovništva ima pristup električnoj energiji, a još manje – oko 10 odsto – može da koristi internet. A konflikt i dalje tinja i negativno utiče na zemlju i njenu ekonomiju već deceniju.
Na predstavljanju bitkoina, vlada CAR-a je rekla da će usvajanje valute promeniti bogatstvo zemlje i staviti CAR „na mapu najhrabrijih i najvizionarskijih zemalja sveta“.
Bitkoin ne kontroliše nikakva moć, tehnički je univerzalno dostupan i ne može se cenzurisati – što je velika promena u odnosu na drugu valutu nacije, ali prosečnom građaninu CAR bi bilo potrebno 60 godina da kupi jedan novčić.
 Žena maše francuskom zastavom uoči emitovanja polufinala Svetskog prvenstva između Francuske i Maroka u baru u Bangiju. Foto: BARBARA DEBOUT/AFP preko Getti Images
Žena maše francuskom zastavom uoči emitovanja polufinala Svetskog prvenstva između Francuske i Maroka u baru u Bangiju. Foto: BARBARA DEBOUT/AFP preko Getti ImagesU Bangiju – glavnom gradu CAR – studenti Univerziteta rekli su za VICE da se „ništa nije promenilo“ od velike najave vlade.
Studenti su želeli da ostanu anonimni jer su se plašili da negativno govore o ambicijama vlade. Pravo na slobodu izražavanja ne postoji u CAR, a građani često doživljavaju zastrašivanje i nasilje od strane provladinih milicija, oružanih grupa i snaga nacionalne bezbednosti.
„Bilo je ogromno slavlje kada je objavljen Bitcoin plan i svi smo bili ponosni na našu zemlju“, rekao je jedan 20-godišnjak, „ali ne mislim da se život ovde uopšte poboljšao od tada”.
Drugi student je dodao: „Nigde nema cena u radnjama izraženih u bitkoioni, niti iko traži od ljudi da plaćaju koristeći novu valutu. Većina trgovaca i kupaca na tržištu nemaju telefon ili internet. Posebno ljudi izvan Bangija, nemaju ništa““.
Aleks Lilaher, osnivač i izvršni direktor Rise Up Media – marketinške agencije koja radi sa bitkoin startapima – je saglasan sa studentima, rekavši za VICE koliko je „iznenađen” što je ta zemlja uopšte napravila takavpotez.
„Centralnoafrička Republika nije baš lider u tehnologiji na kontinentu, i činilo se da tamo nikada nije bilo mnogo bitkoin korisnika koji bi mogla da lobiraju za takav potez“, rekao je on.
 Pobednički tim slavi posle trke kanua za proslavu Dana nezavisnosti CAR-a u decembru. Fotografija: BARBARA DEBOUT/AFP preko Getti Images
Pobednički tim slavi posle trke kanua za proslavu Dana nezavisnosti CAR-a u decembru. Fotografija: BARBARA DEBOUT/AFP preko Getti ImagesUpitan da li građani CAR-a treba da vide usvajanje bitkoina kao pozitivnu ili negativnu stvar, Lilaher je odgovorio „ni jedno ni drugo, jer jednostavno ne mogu da vidim da će usvajanje uskoro krenuti. Ali imati alternativu i poslati signal Francuskoj da CAR želi da ima više nezavisnosti od valute je pozitivno u mojim očima”.
Dodaje: „Međutim, to takođe može imati posledice jer postoje moćne institucije poput Međunarodnog monetarnog fonda, na primer, sa kojima CAR mora da se bavi, koje nisu srećne što zemlje usvajaju bitkoin. Dakle, moglo bi doći do izazova sa kojima će vlada morati da se nosi“.
Centralnoafrička Republika je druga zemlja u svetu koja je usvojila bitkoin, a prva je El Salvador u septembru 2021. Lansiranje valute je tamo imalo različite rezultate, a nedavno je opisano kao „antiklimaktično“ i samo ga turisti zaista koriste.
Iako su ljudi možda očekivali da će druge nacije pratiti El Salvador, sigurno ne bi pomislili da će CAR odgovarati računu.
Glavna opoziciona stranka CAR-a bila je protiv tog predloga od samog početka. Banka centralnoafričkih država je takođe nazvala ovaj potez „problematičnim“ i navela da bi usvajanje valute uz CFA moglo ugroziti odnos nacije sa drugim afričkim zemljama.
Čak i kada većina ljudi u CAR-u nije mogla da investira u Bitcoin, i sve poruke upozorenja, u julu je vlada CAR-a lansirala sopstvenu kriptovalutu – „Sangocoin“. Sango je lokalni jezik koji se govori širom zemlje.
 Pripadnici teritorijalnog pešadijskog bataljona CAR marširaju tokom parade povodom Dana nezavisnosti u Bangiju. Fotografija: BARBARA DEBOUT/AFP preko Getti Images
Pripadnici teritorijalnog pešadijskog bataljona CAR marširaju tokom parade povodom Dana nezavisnosti u Bangiju. Fotografija: BARBARA DEBOUT/AFP preko Getti ImagesSangocoin neki vide kao budućnost CAR-a, a zahtevao je minimalnu investiciju od 500 dolara. Zauzvrat, investitori su mogli da kupe zemljište u zemlji bogatoj dijamantima za 10.000 dolara, pa čak i da kupe državljanstvo CAR-a za oko 60.000 dolara – iako je ove ponude kasnije blokirao najviši sud zemlje. Sangocoin investitori su takođe trenutno „zaključani“ za kupovinu, bez načina da kriptovalutu prodaju ili razmene.
Bio je to hrabar potez vlade, ali izgleda da se još uvek nije isplatio.
Ovog meseca, Centralnoafrička Republika je saopštila da odlaže puštanje nacionalne kriptovalute na kripto berze – što bi olakšalo međunarodnu trgovinu. Rojters kaže da je vlada okrivila „trenutne tržišne uslove” i „tržišne razloge”, ali je novinska agencija izračunala da je Sangocoin dostigao samo „0,01%” od najnovijeg vladinog cilja prodaje.
Još jedan skeptik je Aleks Gladštajn, glavni strateški službenik Fondacije za ljudska prava. On je dugogodišnji zagovornik usvajanja bitkoina u svetu u razvoju, kao i kritičar CFA franka – ali čak i on oseća da je CAR-ova šema bila „izuzetno neosmišljena“.
„Iako imam mnogo simpatije prema ranjivoj i siromašnoj naciji koja usvaja bitkoin kao drugu valutu – posebno naciji koja je decenijama i decenijama finansijski kontrolisana od strane svoje bivše kolonijalne sile, nisam baš optimističan u pogledu toga kako je to izvedeno“, rekao je za VICE.
 Manekenka učestvuje na prvoj nedelji mode u centralnoj Africi u Bangiju u decembru. Fotografija: BARBARA DEBOUT/AFP preko Getti Images
Manekenka učestvuje na prvoj nedelji mode u centralnoj Africi u Bangiju u decembru. Fotografija: BARBARA DEBOUT/AFP preko Getti ImagesDodao je: „Zaista se čini da je cela ova stvar bila kao prevara da se Sangocoin promoviše. Ne mislim da je cilj bio da se bitkoin integriše na smislen način u ekonomiju zemlje. Čini se da je predsednik zainteresovan za bitkoin i da postoji mala grupa ljudi oko njega koja je iskoristila taj interes da bi mogla da donese ove zakone kako bi pokušala da pokrene Sangocoin, od kojeg su imali viziju da zarade gomilu novca. Ali izgleda da je na kraju uspela da prikupi samo malo novca.”
Gladstein kaže da bi Bitcoin mogao biti „veoma važna finansijska tehnologija za ljude Centralnoafričke Republike tokom vremena, i pametno je da vlada istraži kako to može pomoći ljudima“, ali je potrebno mnogo posla da se to postigne.
Vlada Centralnoafričke Republike i opoziciona vlada nisu odgovorile na nekoliko zahteva za intervju.
Tekst podržao Omidiar Netvork. VICE World News zadržava potpunu uređivačku autonomiju.
-
 @ f32184ee:6d1c17bf
2025-04-23 13:21:52
@ f32184ee:6d1c17bf
2025-04-23 13:21:52Ads Fueling Freedom
Ross Ulbricht’s "Decentralize Social Media" painted a picture of a user-centric, decentralized future that transcended the limitations of platforms like the tech giants of today. Though focused on social media, his concept provided a blueprint for decentralized content systems writ large. The PROMO Protocol, designed by NextBlock while participating in Sovereign Engineering, embodies this blueprint in the realm of advertising, leveraging Nostr and Bitcoin’s Lightning Network to give individuals control, foster a multi-provider ecosystem, and ensure secure value exchange. In this way, Ulbricht’s 2021 vision can be seen as a prescient prediction of the PROMO Protocol’s structure. This is a testament to the enduring power of his ideas, now finding form in NextBlock’s innovative approach.
 [Current Platform-Centric Paradigm, source: Ross Ulbricht's Decentralize Social Media]
[Current Platform-Centric Paradigm, source: Ross Ulbricht's Decentralize Social Media]Ulbricht’s Vision: A Decentralized Social Protocol
In his 2021 Medium article Ulbricht proposed a revolutionary vision for a decentralized social protocol (DSP) to address the inherent flaws of centralized social media platforms, such as privacy violations and inconsistent content moderation. Writing from prison, Ulbricht argued that decentralization could empower users by giving them control over their own content and the value they create, while replacing single, monolithic platforms with a competitive ecosystem of interface providers, content servers, and advertisers. Though his focus was on social media, Ulbricht’s ideas laid a conceptual foundation that strikingly predicts the structure of NextBlock’s PROMO Protocol, a decentralized advertising system built on the Nostr protocol.
 [A Decentralized Social Protocol (DSP), source: Ross Ulbricht's Decentralize Social Media]
[A Decentralized Social Protocol (DSP), source: Ross Ulbricht's Decentralize Social Media]Ulbricht’s Principles
Ulbricht’s article outlines several key principles for his DSP: * User Control: Users should own their content and dictate how their data and creations generate value, rather than being subject to the whims of centralized corporations. * Decentralized Infrastructure: Instead of a single platform, multiple interface providers, content hosts, and advertisers interoperate, fostering competition and resilience. * Privacy and Autonomy: Decentralized solutions for profile management, hosting, and interactions would protect user privacy and reduce reliance on unaccountable intermediaries. * Value Creation: Users, not platforms, should capture the economic benefits of their contributions, supported by decentralized mechanisms for transactions.
These ideas were forward-thinking in 2021, envisioning a shift away from the centralized giants dominating social media at the time. While Ulbricht didn’t specifically address advertising protocols, his framework for decentralization and user empowerment extends naturally to other domains, like NextBlock’s open-source offering: the PROMO Protocol.
NextBlock’s Implementation of PROMO Protocol
The PROMO Protocol powers NextBlock's Billboard app, a decentralized advertising protocol built on Nostr, a simple, open protocol for decentralized communication. The PROMO Protocol reimagines advertising by: * Empowering People: Individuals set their own ad prices (e.g., 500 sats/minute), giving them direct control over how their attention or space is monetized. * Marketplace Dynamics: Advertisers set budgets and maximum bids, competing within a decentralized system where a 20% service fee ensures operational sustainability. * Open-Source Flexibility: As an open-source protocol, it allows multiple developers to create interfaces or apps on top of it, avoiding the single-platform bottleneck Ulbricht critiqued. * Secure Payments: Using Strike Integration with Bitcoin Lightning Network, NextBlock enables bot-resistant and intermediary-free transactions, aligning value transfer with each person's control.
This structure decentralizes advertising in a way that mirrors Ulbricht’s broader vision for social systems, with aligned principles showing a specific use case: monetizing attention on Nostr.
Aligned Principles
Ulbricht’s 2021 article didn’t explicitly predict the PROMO Protocol, but its foundational concepts align remarkably well with NextBlock's implementation the protocol’s design: * Autonomy Over Value: Ulbricht argued that users should control their content and its economic benefits. In the PROMO Protocol, people dictate ad pricing, directly capturing the value of their participation. Whether it’s their time, influence, or digital space, rather than ceding it to a centralized ad network. * Ecosystem of Providers: Ulbricht envisioned multiple providers replacing a single platform. The PROMO Protocol’s open-source nature invites a similar diversity: anyone can build interfaces or tools on top of it, creating a competitive, decentralized advertising ecosystem rather than a walled garden. * Decentralized Transactions: Ulbricht’s DSP implied decentralized mechanisms for value exchange. NextBlock delivers this through the Bitcoin Lightning Network, ensuring that payments for ads are secure, instantaneous and final, a practical realization of Ulbricht’s call for user-controlled value flows. * Privacy and Control: While Ulbricht emphasized privacy in social interactions, the PROMO Protocol is public by default. Individuals are fully aware of all data that they generate since all Nostr messages are signed. All participants interact directly via Nostr.
 [Blueprint Match, source NextBlock]
[Blueprint Match, source NextBlock]
Who We Are
NextBlock is a US-based new media company reimagining digital ads for a decentralized future. Our founders, software and strategy experts, were hobbyist podcasters struggling to promote their work online without gaming the system. That sparked an idea: using new tech like Nostr and Bitcoin to build a decentralized attention market for people who value control and businesses seeking real connections.
Our first product, Billboard, is launching this June.
Open for All
Our model’s open-source! Check out the PROMO Protocol, built for promotion and attention trading. Anyone can join this decentralized ad network. Run your own billboard or use ours. This is a growing ecosystem for a new ad economy.
Our Vision
NextBlock wants to help build a new decentralized internet. Our revolutionary and transparent business model will bring honest revenue to companies hosting valuable digital spaces. Together, we will discover what our attention is really worth.
Read our Manifesto to learn more.
NextBlock is registered in Texas, USA.
-
 @ bf47c19e:c3d2573b
2025-05-11 18:39:10
@ bf47c19e:c3d2573b
2025-05-11 18:39:10Originalni tekst na antenam.net
18.12.2024 / Autor: Ana Nives Radović
Ako ste makar djelić vremena proveli u svijetu digitalnog novca, vjerovatno ste naišli na termin HODL – uvijek napisan velikim slovima tako da na prvi pogled djeluje kao riječ sa slovnom greškom. Zapravo i jeste riječ o slovnoj grešci i to onoj koja je nastala na današnji dan prije 11 godina, a koja je uspjela ne samo da obezbijedi mjesto u istoriji svijeta novca, već i da postane naziv za jedan potpuno drugačiji pristup sredstvima koja posjedujemo.
Nespretno napisana riječ „hold“ (eng. držati, zadržati) u poruci na jednom forumu evoluirala je u akronim HODL – akronim za Hold On for Dear Life (doslovno – drži se za život, tj. drži se kao da ti život zavisi od toga), predstavlja poziv na akciju – ili, tačnije, „neakciju“ za vlasnike kriptovaluta da odole iskušenju prodaje tokom tržišnih padova. Riječ je o shvatanju da je ovaj oblik digitalne imovine bolje vremenski što duže imati u vlasništvu, kako bi se sačekao mnogo povoljniji trenutak za prodaju nego prodati ih u vremenu kada je situacija na tržištu loša.
Greška koja je postala pokret
Priča počinje 18. decembra 2013. godine, kada je cijena bitcoina tada počela da pada, a samo tokom toga dana se sa 682 na 522 dolara. Korisnik foruma pod imenom GameKyuubi objavio je sada već legendarni post pod naslovom „I AM HODLING“. Bila je to greška u kucanju, jer se na osnovu sadržaja poruke vidi da je krenuo da napiše „holding“ (držim), ali umjesto da se ispravi sebe, prigrlio je grešku, šaljivo govoreći o svom nedostatku vještina za trgovanje i zašto „bez obzira na sve“.

Bitcoin zajednica brzo je prihvatila ovaj izraz kao dio slenga. Pogrešno napisana riječ odjeknula je internet prostranstvima, a vremenom je prerasla u simbol šire filozofije – ne paniči, ne prodaj i ne dozvoli da kratkoročna nestabilnost poljulja tvoje uvjerenje. Od kasnonoćnog posta na forumu, HODL je postao poklič za vlasnike bitcoina (i drugih, u to vrijeme malobrojnih digitalnih valuta zanemarive vrijednosti) širom svijeta.
HODL-ovanje i HODL-eri
U suštini, HODL-ovanje je strategija zadržavanja kriptovaluta tokom tržišnih uspona i padova, zasnovana na uvjerenju da će cijene vremenom rasti. Umjesto impulsivnog reagovanja na tržišne fluktuacije, HODL-eri se posvećuju svojim investicijama na duže staze.
Ovaj pristup posebno je koristan za početnike, koji možda nemaju dovoljno stručnosti ili hrabrosti da se nose sa svakodnevnim trgovanjem (u čemu su često neuspješni i dugogodišnji vlasnici digitalnih novčića). Sam GameKyuubi u svom originalnom postu priznao je da samo najvještiji trgovci treba da pokušaju da „igraju igru“ tokom tržišnih padova. Za ostale, HODL-ovanje nije samo sigurnije, već je često i pametnije.
Filozofija HODL-ovanja zasnovana je na povjerenju – u budućnost kriptovaluta, u eventualni oporavak tržišta i u korist koju donosi strpljenje. To je odbijanje da se prodaje kada cijene naglo padnu – nepokolebljivo uvjerenje da su padovi privremeni i da nakon njih slijedi rast.
Zakon tržišta pokazuje da što drže HODL-ujete to se ova strategija više isplati, a cijena bitcoina u njegovoj šesnaestogodišnjoj istoriji je nesumnjivo najbolji dokaz za to. Trgovanje zahtijeva mnogo učenja, truda, vremena provedenog u praćenju svakog mogućeg signala, dok je kod HODL-ovanja važno samo da se „ne predate“.
Ako ste prethodnih godina nešto platili bitcoinom (a trgovci širom svijeta su to omogućili upravo da bi vas naveli da ih umjerite ka njima) vjerovatno ste zažalili, jer danas dok je njegova vrijednost i u dolarima i u eurima šestocifrena, ono na što ste ih potrošili ipak izgleda kao nešto što je trebalo platiti fizičkim novcem (kojeg je svakako „pojela inflacija“).
Pouzdane kriptovalute, a tu se prije svega misli na bitcoin, iako veoma volatilne bilježe trend rasta na duge staze, pa HODL-ovanje znači strpljenje u vremenu neizvjesnosti s idejom o koristi na duži rok, čak i kada su godine loše, kao što su bile 2014, 2017. i 2022. Na primjer, u periodu od 20. maja do 20. juna cijena bitcoina kliznula je sa 29.000 na 18.000 dolara, a upravo u tom trenutku mnogi su odlučili da količinu koju posjeduju prodaju ili je potroše plaćajući ovom digitalnom valutom (i pokajali se zbog toga).
HODL naspram drugih strategija
HODL-ovanje se razlikuje od aktivnijih strategija, poput kupovine po niskoj cijeni i prodaje po visokoj, jer dok trgovci pokušavaju da tempiraju tržište radi brze zarade, HODL-eri ostaju dosljedni svojoj odluci da se ne oslobađaju svoje imovine ni u najnoepovoljnijim trenucima. HODL-eri ne pokušavaju da predvide kretanje cijena – jednostavno čuvaju svoja sredstva, svjesni toga da će strpljenje na kraju donijeti rezultat.
Naravno, HODL-ovanje ima i svoje nedostatke. Za razliku od trgovaca koji mogu da povećaju svoj kapital kroz stratešku kupovinu i prodaju, HODL-eri zavise od vremena provedenog u čekanju na dugoročne rezultate. Pored toga, masovno HODL-ovanje može usporiti cirkulaciju kriptovaluta na tržištu, smanjujući ukupnu ekonomsku aktivnost – drugim riječima, kada bismo svi bili HODL-eri odnos ponude i tražnje bi bio veoma destimulišući i to bi oborilo cijenu.
Na sreću, trgovaca ima mnogo – dovoljno da tržište stalno bude aktivno i dinamično, no za one koji nemaju vremena, vještine ili sklonost ka riziku koji nosi trgovanje, HODL-ovanje ostaje jednostavan, ali veoma efikasan pristup.
Filozofija HODL-ovanja
HODL-ovanje je više od investicione strategije – to je način razmišljanja koji obuhvata otpornost, strpljenje i vjerovanje da su kratkotrajno suzdržavanje i nepokolebljivost u odluci da se sredstva sačuvaju vrijedna dugoročnog dobitka. Bilo da cijena bitcoina raste ili pada je, filozofija HODL-ovanja ostaje ista – ostanimo dosljedni, vjerujmo procesu i gledajmo u budućnost.
Jedan od ključnih razloga zašto većini ljudi ovakav pristup dugo nije bio razumljiv je zbog toga što su čitav sistem novca prihvatili u uvjerenju da on vremenom devalvira. Vjerovatno ste makar jednom razmatrali ponudu oročene štednje i procijenili da vam količina novca koju želite da položite neće donijeti onaj prinos koji će očuvati njegovu kupovnu moć nakon određenog broja godina, jer je kontinuirano doštampavanje novca podupiralo tu tvrdnju.
Dakle, ne treba da vas zavara sve ono što znate o novcu kao takvom, budući da bitcoin (na kojem je u ovom serijalu poseban fokus, jer mnoge druge kriptovalute ipak češće razočaraju nego što oduševe) nije novac, već samo ima neka svojstva novca. Posmatrajte ga radije kao imovinu – npr. kao nekretninu za koju sigurno želite da prodate onda kada je situacija stabilnija i kada su mnogo veće šanse da pronađete kupca kojem ćete je prodati po višoj cijeni.
U svakom slučaju, ako se u vašem digitalnom novčaniku već nalazi poneki satoshi (stomilioniti djelić bitcoina), kada tržište ponovo uđe u nepovoljnu fazu i zavlada prolazna panika, sjetite se onoga što je napisao GameKyuubi. HODL nije samo izraz – to je način da se prebrode oluje i izazovi koje nestabilno tržište nosi.
-
 @ 3ffac3a6:2d656657
2025-04-23 01:57:57
@ 3ffac3a6:2d656657
2025-04-23 01:57:57🔧 Infrastructure Overview
- Hardware: Raspberry Pi 5 with PCIe NVMe HAT and 2TB NVMe SSD
- Filesystem: ZFS with separate datasets for each service
- Networking: Docker bridge networks for service segmentation
- Privacy: Tor and I2P routing for anonymous communication
- Public Access: Cloudflare Tunnel to securely expose LNbits
📊 Architecture Diagram
🛠️ Setup Steps
1. Prepare the System
- Install Raspberry Pi OS (64-bit)
- Set up ZFS on the NVMe disk
- Create a ZFS dataset for each service (e.g.,
bitcoin,lnd,rtl,lnbits,tor-data) - Install Docker and Docker Compose
2. Create Shared Docker Network and Privacy Layers
Create a shared Docker bridge network:
bash docker network create \ --driver=bridge \ --subnet=192.168.100.0/24 \ bitcoin-netNote: Connect
bitcoind,lnd,rtl, internallnbits,tor, andi2pto thisbitcoin-netnetwork.Tor
- Run Tor in a container
- Configure it to expose LND's gRPC and REST ports via hidden services:
HiddenServicePort 10009 192.168.100.31:10009 HiddenServicePort 8080 192.168.100.31:8080 - Set correct permissions:
bash sudo chown -R 102:102 /zfs/datasets/tor-data
I2P
- Run I2P in a container with SAM and SOCKS proxies
- Update
bitcoin.conf:i2psam=192.168.100.20:7656 i2pacceptincoming=1
3. Set Up Bitcoin Core
- Create a
bitcoin.confwith Tor/I2P/proxy settings and ZMQ enabled - Sync the blockchain in a container using its ZFS dataset
4. Set Up LND
- Configure
lnd.confto connect tobitcoindand use Tor: ```ini [Bitcoind] bitcoind.rpchost=bitcoin:8332 bitcoind.rpcuser=bitcoin bitcoind.rpcpass=very-hard-password bitcoind.zmqpubrawblock=tcp://bitcoin:28332 bitcoind.zmqpubrawtx=tcp://bitcoin:28333
[Application Options] externalip=xxxxxxxx.onion
`` - Don’t expose gRPC or REST ports publicly - Mount the ZFS dataset at/root/.lnd` - Optionally enable Watchtower5. Set Up RTL
- Mount
RTL-Config.jsonand data volumes - Expose RTL's web interface locally:
```yaml
ports:
- "3000:3000" ```
6. Set Up Internal LNbits
- Connect the LNbits container to
bitcoin-net - Mount the data directory and LND cert/macaroons (read-only)
- Expose the LNbits UI on the local network:
```yaml
ports:
- "5000:5000" ```
- In the web UI, configure the funding source to point to the LND REST
.onionaddress and paste the hex macaroon - Create and fund a wallet, and copy its Admin Key for external use
7. Set Up External LNbits + Cloudflare Tunnel
- Run another LNbits container on a separate Docker network
- Access the internal LNbits via the host IP and port 5000
- Use the Admin Key from the internal wallet to configure funding
- In the Cloudflare Zero Trust dashboard:
- Create a tunnel
- Select Docker, copy the
--tokencommand - Add to Docker Compose:
yaml command: tunnel --no-autoupdate run --token eyJ...your_token...
💾 Backup Strategy
- Bitcoin Core: hourly ZFS snapshots, retained for 6 hours
- Other Services: hourly snapshots with remote
.tar.gzbackups - Retention: 7d hourly, 30d daily, 12mo weekly, monthly forever
- Back up ZFS snapshots to avoid inconsistencies
🔐 Security Isolation Benefits
This architecture isolates services by scope and function:
- Internal traffic stays on
bitcoin-net - Sensitive APIs (gRPC, REST) are reachable only via Tor
- Public access is controlled by Cloudflare Tunnel
Extra Security: Host the public LNbits on a separate machine (e.g., hardened VPS) with strict firewall rules:
- Allow only Cloudflare egress
- Allow ingress from your local IP
- Allow outbound access to internal LNbits (port 5000)
Use WireGuard VPN to secure the connection between external and internal LNbits:
- Ensures encrypted communication
- Restricts access to authenticated VPN peers
- Keeps the internal interface isolated from the public internet
✅ Final Notes
- Internal services communicate over
bitcoin-net - LND interfaces are accessed via Tor only
- LNbits and RTL UIs are locally accessible
- Cloudflare Tunnel secures external access to LNbits
Monitor system health using
monit,watchtower, or Prometheus.Create all configuration files manually (
bitcoin.conf,lnd.conf,RTL-Config.json), and keep credentials secure. Test every component locally before exposing it externally.⚡
-
 @ e39333da:7c66e53a
2025-05-12 00:03:18
@ e39333da:7c66e53a
2025-05-12 00:03:18::youtube{#VQRLujxTm3c}
Rockstar released the second trailer for Grand Theft Auto VI, where they mention that it showcases both cinematic and gameplay scenes equally, though of course it doesn't show any direct gameplay.
This trailer also announces the release date for the game. The game will come out on the 26th of May, 2026, for the PS5 and the Xbox One.
-
 @ aa8de34f:a6ffe696
2025-03-31 21:48:50
@ aa8de34f:a6ffe696
2025-03-31 21:48:50In seinem Beitrag vom 30. März 2025 fragt Henning Rosenbusch auf Telegram angesichts zunehmender digitaler Kontrolle und staatlicher Allmacht:
„Wie soll sich gegen eine solche Tyrannei noch ein Widerstand formieren können, selbst im Untergrund? Sehe ich nicht.“\ (Quelle: t.me/rosenbusch/25228)
Er beschreibt damit ein Gefühl der Ohnmacht, das viele teilen: Eine Welt, in der Totalitarismus nicht mehr mit Panzern, sondern mit Algorithmen kommt. Wo Zugriff auf Geld, Meinungsfreiheit und Teilhabe vom Wohlverhalten abhängt. Der Bürger als kontrollierbare Variable im Code des Staates.\ Die Frage ist berechtigt. Doch die Antwort darauf liegt nicht in alten Widerstandsbildern – sondern in einer neuen Realität.
-- Denn es braucht keinen Untergrund mehr. --
Der Widerstand der Zukunft trägt keinen Tarnanzug. Er ist nicht konspirativ, sondern transparent. Nicht bewaffnet, sondern mathematisch beweisbar. Bitcoin steht nicht am Rand dieser Entwicklung – es ist ihr Fundament. Eine Bastion aus physikalischer Realität, spieltheoretischem Schutz und ökonomischer Wahrheit. Es ist nicht unfehlbar, aber unbestechlich. Nicht perfekt, aber immun gegen zentrale Willkür.
Hier entsteht kein „digitales Gegenreich“, sondern eine dezentrale Renaissance. Keine Revolte aus Wut, sondern eine stille Abkehr: von Zwang zu Freiwilligkeit, von Abhängigkeit zu Selbstverantwortung. Diese Revolution führt keine Kriege. Sie braucht keine Führer. Sie ist ein Netzwerk. Jeder Knoten ein Individuum. Jede Entscheidung ein Akt der Selbstermächtigung.
Weltweit wachsen Freiheits-Zitadellen aus dieser Idee: wirtschaftlich autark, digital souverän, lokal verankert und global vernetzt. Sie sind keine Utopien im luftleeren Raum, sondern konkrete Realitäten – angetrieben von Energie, Code und dem menschlichen Wunsch nach Würde.
Der Globalismus alter Prägung – zentralistisch, monopolistisch, bevormundend – wird an seiner eigenen Hybris zerbrechen. Seine Werkzeuge der Kontrolle werden ihn nicht retten. Im Gegenteil: Seine Geister werden ihn verfolgen und erlegen.
Und während die alten Mächte um Erhalt kämpfen, wächst eine neue Welt – nicht im Schatten, sondern im Offenen. Nicht auf Gewalt gebaut, sondern auf Mathematik, Physik und Freiheit.
Die Tyrannei sieht keinen Widerstand.\ Weil sie nicht erkennt, dass er längst begonnen hat.\ Unwiderruflich. Leise. Überall.
-
 @ bf47c19e:c3d2573b
2025-05-11 18:37:13
@ bf47c19e:c3d2573b
2025-05-11 18:37:13Apstrakt
Kriptovalute (engl. "cryptocurrency") su digitalne (virtualne) valute, koje iako su sredstvo razmene, još uvek nisu strogo regulisane zakonom u većini država, a u pojedinim su čak i zabranjene. Veliki broj ljudi, uključujući i IT stručnjake i programere ne znaju mnogo o ovoj temi, a šira javnost izjednačava pojmove blokčejna i bitkoina. Tržište kriptovaluta danas iznosi gotovo 770 milijardi dolara. Od pojave prvih digitalnih valuta do danas, nastalo je preko 1.300 aktivnih kriptovaluta koje se razlikuju prema svojim svojstvima i upotrebi. Pre bitkoina bilo je mnoštvo neuspelih pokušaja stvaranja digitalnih valuta (digikeš, heškeš, Fejsbuk kredit i dr.). Utopistička ideja da matematika i fizika mogu rešiti društvene probleme započela je svoj život kroz pojavu bitkoina. Genijalna ideja po kojoj funkcioniše bitkoin zasnovana je na tehnologiji blokčejna, čiji kapacitet doseže daleko iznad kripto valuta. Iako se još uvek vode polemike ko stoji iza pseudonima Satoši Nakamoto, njegova zaostavština ima potencijal da promeni svet. Uspeh bitkoina leži u prednostima koje ima u odnosu na druge slične valute, ali njegov značaj prevazilazi i pogodnosti koje je doneo. Banke nisu potrebne za čuvanje podataka o novcu, evidenciju o imovini i svakoj transakciji bitkoina čuvaju računari svih korisnika mreže u zajedničkoj bazi podataka blokčejnu. Sve transakcije su mnogo brže od bankarskih, bez taksi, uz drastično lakše plaćanje preko državnih granica. Bitkoin svojim korisnicima pruža bezbednosti bez identifikacije, iako blokčejn beleži transakciju, ne beleži ko stoji iza nje. U radu su predstavljeni osnovni principi na kojima su zasnovani bitkoin i druge kriptovalute, pojašnjen odnos između blokčejna i bitkoina.
1 UVOD
Ideal o novcu koji se ne oslanja na centralne institucije (koje mogu propasti, ali i koje vrše nadzor nad korisnicima), postojao je decenijama. U digitalnom svetu prvi ga je uobličio pisac naučne fantastike Nil Stivenson 1999. godine u svojoj noveli Kriptonomikon. On je opisao podzemni svet koji funkcioniše zahvaljujući digitalnom zlatu zasnovanom na kriptografiji, pri čijoj upotrebi korisnici ne moraju odavati ko su i šta su (Popper, 2016).
Kriptovalute (engl. cryptocurrency) su digitalne (virtualne) valute, koje iako su sredstvo razmene, još uvek nisu strogo regulisane zakonom u većini država, a u pojedinim su čak i zabranjene (Jovanović, 2014).
Da bi se razumeo nastanak i funkcionisanje kriptovaluta, neophodno je sagledati ih iz različitih uglova na kojima su one bazirane: matematici, sociologiji, ekonomiji, pravu i politici. To je verovatno i glavni razlog zbog koga veliki broj ljudi (uključujući i IT stručnjake i programere) ne znaju mnogo o ovoj temi. Takođe, šira javnost izjednačava pojmove blokčejna i bitkoina.
Sve kriptovalute su bazirane na jedinstvenom nizu brojeva za svaku jedinicu valute, koje korisnici mogu jedni drugima slati preko mreže. U prošlosti su se ti nizovi mogli lako kopirati i trošiti više puta, zbog čega nisu imali vrednost. Kriptograf Dejvid Čaum je taj problem rešio stvaranjem jedinstvene centralizovane knjige, u kojoj su se čuvale beleške o transakcijama svakog korisnika, čime ni jedna jedinica valute više nije mogla da se nalazi na dva mesta istovremeno (Bertlet, 2016).
Kriptovalute svoj nastanak duguju težnjama levo orijentisanih utopističkih posvećenika IT tehnologija koji su sanjali o univerzalnom novcu koji bi svako mogao da poseduje i troši, čija je vrednost onolika koliko su korisnici voljni da plate (na principu ponude i potražnje), ali pre svega na liniji fronta za onlajn anonimnost i slobodu, bez cenzure i nadzora. Pojavi bitkoina prethodio je Sajberpankerski manifest Done Haravej (Haraway, 1985) koji počinje rečima: „U elektronsko doba, privatnost je neophodan uslov za postojanje otvorenog društva“.
Kriptovalute su univerzalni novac koji se može koristiiti bilo gde u svetu, one su lako prenosive i teško se krivotvore.
Neki podaci pokazuju da tržište kriptovaluta danas iznosi gotovo 770 milijardi dolara. Od pojave prvih digitalnih valuta do danas, nastalo je preko 1.300 aktivnih kriptovaluta koje se razlikuju prema svojim svojstvima i upotrebi.
Prema odredbama Zakona o Narodnoj banci Srbije celokupni unutrašnji promet u Republici Srbiji izražava se u dinarima, osim ako nekim zakonom nije drukčije određeno. „Zakonom o platnom prometu propisano je da se poslovi platnog prometa obavljaju u dinarima, a Zakonom o deviznom poslovanju da se plaćanje, naplaćivanje i prenos između rezidenata i između rezidenata i nerezidenata u Republici Srbiji vrši u dinarima, a izuzetno se može vršiti i u devizama u slučajevima koji su propisani ovim zakonom“ (NBS, 2014).
Tržište kriptovaluta u Srbiji postoji, sve je veći broj rudara. Iako trgovanje kriptovalutama nije nelegalno, Narodna Banka Srbije - NBS je u više saopštenja navela da one ne predstavljaju zakonsko sredstvo plaćanja u Republici Srbiji. Takođe, zbog toga što ih ne izdaje centralna banka, NBS za korišćenje virtuelnih valuta, ulaganje u njih, kao ni za njihovu vrednost. Narodna banka Srbije je više puta upozoravala javnost da virtuelne valute ne predstavljaju zakonsko sredstvo plaćanja u Republici Srbiji (NBS, Politika – u vezi s bitkoinom, 2017).
Ukoliko kriptovalute promatramo kao novac onda njihove tranksakcije mogu biti upitne shodno Zakonu o sprečavanju pranja novca i finansiranja terorizma, gde je propisana obaveza preduzimanja radnji i mera za sprečavanje pranja novca, kao što su identifikacija stranaka koje trguju preko tih platformi, uzimanjem kopije ličnog dokumenta. Kako poslovanje platformi na kojima se vrše transakcije kriptovalutama nije zakonom regulisano u Republici Srbiji, a uglavnom ni u uporednom pravu, a čl. 552. Zakona o obligacionim odnosima Republike Srbije ((„Sl. list SFRJ“, br. 29/78, 39/85, 45/89 - odluka USJ i 57/89, „Sl. list SRJ“, br. 31/93 i „Sl. list SCG“, br. 1/2003 - Ustavna povelja) predviđa razmenu robe kao jedan od načina trgovine, otvara se put ka legalnoj trgovini kriptovalutama (Bubanja, 2017).
Praksa je pokazala da su se korisnici kriptovaluta kada su imali problem sa njima, obraćali vlastima i njihovim regulatornim telima, zbog čijeg su zaobilaženja i smišljeni. Nažalost, korisnici ne uživaju pravnu zaštitu čak i kada je reč o trgovini putem registrovanih privrednih subjekta.
2 BITKOIN
Prva decentralizovana kriptovaluta koja se pojavila je bitkoin (eng. „Bitcoin“). Termin bitkoin označava istoimenu organizaciju, softver i protokol, kao i jedinicu mere ove kriptovalute (skraćeno BTC) (Bertlet, 2016). Koncept na kome se zasniva bitkoin prvi put je predstavljen 2008. godine u članku "Bitcoin: A Peerto-Peer Electronic Cash System", a u januaru 2009. godine bitkoin je pušten u promet. Njegov tvorac nije poznat do danas i krije se iza pseudonima Satoši Nakomato. Novu vrstu digitalne kriptovalute formirao je tako što je stvorio distribuirani sistem verifikacije. Bitkoin nastaje u procesu koji se naziva „rudarenje“ (engl. mining). Njegova jedinstvenost je u tome što je decentralizovana valuta, iza koje ne stoji nijedna država, niti banka. Bitkoin je digitalna valuta, koja nastaje i čuva se elektronski. Kriptovalute u cilju maksimizacije bezbednosti, upotrebljavaju metod - dokaz o radu (engl. proofof-work), metod baziran na informacijama koje je teško stvoriti, ali koje ostalim učesnicima u rudarenju obezbeđuju laku proveru i verifikaciju transakcija.
Kriptovalute se čuvaju na bitkoin adresama za koje ključ predstavlja jedinstven niz slova i brojeva. Svaka transkacija bitkoinom se beleži u blokovima koji se zovu blokčejn. Transakcije se hronološki ređaju u blokove, u svakom se nalazi digitalni potpis prethodnog bloka, time se uređuje redosled i garantuje da novi blok može da se pridruži lancu samo ako počne na mestu na mestu završetka prethodnog. Jedan od osnovnih činilaca bezbednosti bitkoina je da se kopija svake izvedene transakcije beleži na svakom nalogu na kome je instaliran bitkoin softver. Blokčejnove neprekidno verifikuju računari svih korisnika softvera, tako sistem zna u bilo kom trenutku, koliko bitkoina svaki korisnik u svom novčaniku poseduje. Novčanik je program koji služi za slanje, primanje i skladištenje kriptovaluta. Digitalni novčanik sadrži prikaz količine kriptovalute koju korisnik poseduje, zapise o svim njegovim transakcijama, korisnički tajni ključ i njegove adrese (Bertlet, 2016). Novčanik je moguće instalirati na računar, mobilni telefon i tablet.
Falsifikovanje bitkoina nije moguće, jer iako vlasništvo može da se menja ono se ne može nikada duplirati (Bertlet, 2016). On je pseudoanoniman, bitkoin mreža čuva sve podatke o svakoj transakciji koja se dogodila unutar mreže. Svako ko ima bitkoin softver i adresu na bitkoin mreži, može videti koliko novca ima na mreži, ali ne i kome oni pripadaju. Za razliku od otvaranja računa u bankama, otvaranje bitkoin računa (adrese) je brzo, bez troškova i „papirologije“. Jedna od glavnih prednosti bitkoin mreže je brzina transakcija.
Svako ko snagu svog računara posveti verifikaciji transakcija u blokčejnu može biti „rudar“. To je proces dodavanja transkacija u registar svih bitkoin transkacija. Rudarenje čini rešavanje matematičkog algoritma za čije se uspešno rešavanje dobija određena količina bitkoina.
Iako bitkoin ima reputaciju nestabilnosti, velikih fluktuacija i nezakonitog poslovanja, čemu mnogi pridodaju i urušavanje tradicionalnog koncepta nacionalnih država, ipak većina se slaže u tome da je njegova pojava najvažnija nova ideja od stvaranja Interneta (Vigna & Casey, 2016).
Razloga za uspeh bitkoina ima više. Finansijska kriza povoljno je uticala na njegov razvoj, poverenje u postojeći finansijski ali i politički sistem je bilo poljuljano i brojni korisnici su u njemu prepoznali drugačije rešenje.
Anonimnost koju pruža prilikom transakcija jedan je od ključnih razloga njegovog uspeha. Prilikom digitalnog plaćanja bitkoinom u većini slučajeva nije potrebno davanje ličnih podataka. Ovakva vrsta anonimnosti, nažalost pogodovala je i usponu tamne strane upotrebe i popularnosti bitkoina u kriminalnim krugovima.
Računi u bitkoinu nisu opterećeni visokim bankarskim dažbinama.
Takođe, nije beznačajan ni potencijal plaćanja izdataka koji su manji od trenutnih ograničenja u konvencijalnim transakcijama na internetu (npr. naplata čitanja jednog novinskog članka ili preskoči reklamu, koji koštaju manje od 20 ili 30 centi kolika je najmanja transakcija) (Popper, 2016).
Kao što su svi učesnici na internetu povezani protokolima (TCP/IP, FTP, SMTP, HTTP i dr.) zahvaljujući kojima mogu međusobno da komuniciraju, bitkoin je stvorio svoje softverske protokole koji uređuju funkcionalna pravila upravljanja sistemom.
Bitkoin je omogućio novi način stvaranja, čuvanja i transfera novca.
Od svog nastanka bitkoin se unapređivao, podržan od internet zajednice, posebno od posvećenika slobodi interneta i anonimosti, mnogi od problema koji su uočeni su rešavani zajedničkim naporom internet zajednice.
3 BLOKČEJN
Blokčejn (engl. blockchain) nije samo bitkoin, on je tehnologija za koju mnogi predviđaju da će promeni svet (OECD, 2018).
Ukoliko bismo pojednostavljeno opisivali blokčejn mogli bismo da kažemo da je to nova vrsta baze podataka, iako bi to bilo pojednostavljeno objašnjenje slično kao kada bi smo imejl (email) opisali kao novi način za slanje pisama.
Iako blokčejn jeste nova vrsta baze podatka, to ne objašnjava u dovoljnoj meri genijalnost načina na koji funkcioniše.
Kada bilo gde i bilo kada položimo novac, oslanjamo se na zapis u bazi podataka treće strane, banke, firme i sl. Poverenje u banke zasnovano je na zakonu koji reguliše rad banke, poverenju u državu da će u slučaju propasti banke država nadoknaditi klijentima njihov ulog.
Kada plaćamo on line usluge ili vršimo neku drugu transakciju kreditnim karticama, poklanjamo poverenje kompanijama koje posreduju u našem plaćanju (Mastercard, VISA i dr.) koje za to uzimaju određenu materijalnu nadoknadu. Čak i prilikom tradicionalnih oblika plaćanja gotovinom u papirnom novcu, mi dajemo papir na kome je ispisana vrednost za koju prodavac veruje da će mu biti isplaćena (ili garantovana) od strane vlade koja ju je štampala. Digitalno plaćanje zbog prisustva trećih strana (banke, kreditne kompanije i dr.) uvek je bilo moguće pratiti. I kod plaćanja gotovinom klijenti veruju bankama i kreditnim kompanijama koje rukovode platnim karticama, da imaju pouzdane baze podataka. I vlade država veruju da banke i kreditne kompanije vode baze podataka koje su tačne i pouzdane.
Baze podataka sadrže mnoštvo ličnih podataka, od npr. medicinske dokumentacije u domu zdravlja koja sadrži važne informacije o nama i našem zdravstvenom stanju, kada smo i od koje bolesti bolovali, koje lekove smo koristili i sl. I druge baze podataka sadrže mnoštvo naših ličnih podataka koje su važne ne samo za nas, već i za državu, grad, privredu, druge građane itd.
Osim što omogućava anonimne i sigurne transakcije, blokčejn ima i potencijal da sačuva sve vredne informacije, od podataka o rođenim i umrlim, preko osiguranja, do katastara nepokretnosti, pa čak i glasova (Tapscott, 2018).
Sagledavši mogućnosti koji blokčejn nudi u transformaciji industrija i tržišta, povećanju transparentnosti i poverenja između građana, kao i olakšanom pristupu tržištu (uz bolju efikasnost transakcija), ali i rizicima koje sa sobom nosi, Organizacija za ekonomsku saradnju i razvoj - OECD organizovala je od 4. do 5. septembra 2018. godine Forum politike OECD-a za blokčejn. To je bila ujedno i prva glavna međunarodna konferencija na kojoj se razmatrao uticaj blokčejna na aktivnosti vlada i javnih prioriteta. Forum se bavio prednostima i rizicima blokčejna za ekonomiju i društvo, pokušajem određivanja adekvatnog regulatornog pristupa, kao i javnih politika prema blokčejnu.
Učesnici Foruma su diskutovali o mogućnostima globalnog ekonomskog uticaja blokčejna, njegovim implikacijama na privatnost i sajber bezbednost, upotrebi blokčejn tehnologija za povećanje inkluzivnosti, njegovoj upotrebi u promovisanju zelenog rasta i održivosti, kao i jačanju kapaciteta javne uprava i primene u praksi (OECD, 2018).
4 ZAKLJUČAK
Pre bitkoina bilo je mnoštvo neuspelih pokušaja stvaranja digitalnih valuta (digikeš, heškeš, Fejsbuk kredit i dr.). Uspeh bitkoina leži u prednostima koje ima u odnosu na druge slične valute, ali njegov značaj prevazilazi i pogodnosti koje je doneo.
Svaki korisnik bitkoina ima potpunu kontrolu nad novcem na svom računu (adresi), jedino osoba sa privatnim ključem može pristupiti bitkoinima na toj adresi. Banke nisu potrebne za čuvanje podataka o novcu, evidenciju o imovini i svakoj transakciji bitkoina čuvaju računari svih korisnika mreže u zajedničkoj bazi podataka blokčejnu. Sve transakcije su mnogo brže od bankarskih, bez taksi, uz drastično lakše plaćanje preko državnih granica.
Bitkoin svojim korisnicima pruža bezbednosti bez identifikacije, iako blokčejn beleži transakciju, ne beleži ko stoji iza nje. Zahvaljujući peer-to-peer komunikaciji i kriptografiji, povezivanje bitkoin transakcija sa osobom u stvarnom životu je veoma teško. To je u ujedno možda i njegova najveća mana, jer su oporezivanje i nadzor nad korisnicima krajnje teški.
Garancija vrednosti bitkoina osmišljena je po uzoru na plamenite metale kojih ima ograničeno u prirodi. Zbog toga je Satoši u kodu bitkoina odredio da ih ima maksimalno 21 milion, te da ukoliko bitkoin protokol ostane isti, poslednji bitkoin će biti izrudaren 2140. godine.
Do sada je izrudareno oko 17 miliona bitkoina, što znači da je ostalo 4 miliona, ili oko 19%. Do sada je bitkoin uspeo da prevlada sve krize koje su ga zahvatile (u više slučajeva nestajali su iznosi koji su dostizali i 400 miliona dolara). Kakva god sudbina bitkoina bila u budućnosti, njegova uloga se neće moći zanemariti, prvenstveno zbog toga što je zahvaljujući njemu iznedren blokčejn. Bez obzira na skepticima u vezi sa kriptovalutama, teško se mogu osporiti mogućnosti koje blokčejn pruža, pre svega u zaštiti baza podatka.
-
 @ c631e267:c2b78d3e
2025-03-31 07:23:05
@ c631e267:c2b78d3e
2025-03-31 07:23:05Der Irrsinn ist bei Einzelnen etwas Seltenes – \ aber bei Gruppen, Parteien, Völkern, Zeiten die Regel. \ Friedrich Nietzsche
Erinnern Sie sich an die Horrorkomödie «Scary Movie»? Nicht, dass ich diese Art Filme besonders erinnerungswürdig fände, aber einige Szenen daraus sind doch gewissermaßen Klassiker. Dazu zählt eine, die das Verhalten vieler Protagonisten in Horrorfilmen parodiert, wenn sie in Panik flüchten. Welchen Weg nimmt wohl die Frau in der Situation auf diesem Bild?

Diese Szene kommt mir automatisch in den Sinn, wenn ich aktuelle Entwicklungen in Europa betrachte. Weitreichende Entscheidungen gehen wider jede Logik in die völlig falsche Richtung. Nur ist das hier alles andere als eine Komödie, sondern bitterernst. Dieser Horror ist leider sehr real.
Die Europäische Union hat sich selbst über Jahre konsequent in eine Sackgasse manövriert. Sie hat es versäumt, sich und ihre Politik selbstbewusst und im Einklang mit ihren Wurzeln auf dem eigenen Kontinent zu positionieren. Stattdessen ist sie in blinder Treue den vermeintlichen «transatlantischen Freunden» auf ihrem Konfrontationskurs gen Osten gefolgt.
In den USA haben sich die Vorzeichen allerdings mittlerweile geändert, und die einst hoch gelobten «Freunde und Partner» erscheinen den europäischen «Führern» nicht mehr vertrauenswürdig. Das ist spätestens seit der Münchner Sicherheitskonferenz, der Rede von Vizepräsident J. D. Vance und den empörten Reaktionen offensichtlich. Große Teile Europas wirken seitdem wie ein aufgescheuchter Haufen kopfloser Hühner. Orientierung und Kontrolle sind völlig abhanden gekommen.
Statt jedoch umzukehren oder wenigstens zu bremsen und vielleicht einen Abzweig zu suchen, geben die Crash-Piloten jetzt auf dem Weg durch die Sackgasse erst richtig Gas. Ja sie lösen sogar noch die Sicherheitsgurte und deaktivieren die Airbags. Den vor Angst dauergelähmten Passagieren fällt auch nichts Besseres ein und so schließen sie einfach die Augen. Derweil übertrumpfen sich die Kommentatoren des Events gegenseitig in sensationslüsterner «Berichterstattung».
Wie schon die deutsche Außenministerin mit höchsten UN-Ambitionen, Annalena Baerbock, proklamiert auch die Europäische Kommission einen «Frieden durch Stärke». Zu dem jetzt vorgelegten, selbstzerstörerischen Fahrplan zur Ankurbelung der Rüstungsindustrie, genannt «Weißbuch zur europäischen Verteidigung – Bereitschaft 2030», erklärte die Kommissionspräsidentin, die «Ära der Friedensdividende» sei längst vorbei. Soll das heißen, Frieden bringt nichts ein? Eine umfassende Zusammenarbeit an dauerhaften europäischen Friedenslösungen steht demnach jedenfalls nicht zur Debatte.
Zusätzlich brisant ist, dass aktuell «die ganze EU von Deutschen regiert wird», wie der EU-Parlamentarier und ehemalige UN-Diplomat Michael von der Schulenburg beobachtet hat. Tatsächlich sitzen neben von der Leyen und Strack-Zimmermann noch einige weitere Deutsche in – vor allem auch in Krisenzeiten – wichtigen Spitzenposten der Union. Vor dem Hintergrund der Kriegstreiberei in Deutschland muss eine solche Dominanz mindestens nachdenklich stimmen.
Ihre ursprünglichen Grundwerte wie Demokratie, Freiheit, Frieden und Völkerverständigung hat die EU kontinuierlich in leere Worthülsen verwandelt. Diese werden dafür immer lächerlicher hochgehalten und beschworen.
Es wird dringend Zeit, dass wir, der Souverän, diesem erbärmlichen und gefährlichen Trauerspiel ein Ende setzen und die Fäden selbst in die Hand nehmen. In diesem Sinne fordert uns auch das «European Peace Project» auf, am 9. Mai im Rahmen eines Kunstprojekts den Frieden auszurufen. Seien wir dabei!
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 66675158:1b644430
2025-03-23 11:39:41
@ 66675158:1b644430
2025-03-23 11:39:41I don't believe in "vibe coding" – it's just the newest Silicon Valley fad trying to give meaning to their latest favorite technology, LLMs. We've seen this pattern before with blockchain, when suddenly Non Fungible Tokens appeared, followed by Web3 startups promising to revolutionize everything from social media to supply chains. VCs couldn't throw money fast enough at anything with "decentralized" (in name only) in the pitch deck. Andreessen Horowitz launched billion-dollar crypto funds, while Y Combinator batches filled with blockchain startups promising to be "Uber for X, but on the blockchain."
The metaverse mania followed, with Meta betting its future on digital worlds where we'd supposedly hang out as legless avatars. Decentralized (in name only) autonomous organizations emerged as the next big thing – supposedly democratic internet communities that ended up being the next scam for quick money.
Then came the inevitable collapse. The FTX implosion in late 2022 revealed fraud, Luna/Terra's death spiral wiped out billions (including my ten thousand dollars), while Celsius and BlockFi froze customer assets before bankruptcy.
By 2023, crypto winter had fully set in. The SEC started aggressive enforcement actions, while users realized that blockchain technology had delivered almost no practical value despite a decade of promises.
Blockchain's promises tapped into fundamental human desires – decentralization resonated with a generation disillusioned by traditional institutions. Evangelists presented a utopian vision of freedom from centralized control. Perhaps most significantly, crypto offered a sense of meaning in an increasingly abstract world, making the clear signs of scams harder to notice.
The technology itself had failed to solve any real-world problems at scale. By 2024, the once-mighty crypto ecosystem had become a cautionary tale. Venture firms quietly scrubbed blockchain references from their websites while founders pivoted to AI and large language models.
Most reading this are likely fellow bitcoiners and nostr users who understand that Bitcoin is blockchain's only valid use case. But I shared that painful history because I believe the AI-hype cycle will follow the same trajectory.
Just like with blockchain, we're now seeing VCs who once couldn't stop talking about "Web3" falling over themselves to fund anything with "AI" in the pitch deck. The buzzwords have simply changed from "decentralized" to "intelligent."
"Vibe coding" is the perfect example – a trendy name for what is essentially just fuzzy instructions to LLMs. Developers who've spent years honing programming skills are now supposed to believe that "vibing" with an AI is somehow a legitimate methodology.
This might be controversial to some, but obvious to others:
Formal, context-free grammar will always remain essential for building precise systems, regardless of how advanced natural language technology becomes
The mathematical precision of programming languages provides a foundation that human language's ambiguity can never replace. Programming requires precision – languages, compilers, and processors operate on explicit instructions, not vibes. What "vibe coding" advocates miss is that beneath every AI-generated snippet lies the same deterministic rules that have always governed computation.
LLMs don't understand code in any meaningful sense—they've just ingested enormous datasets of human-written code and can predict patterns. When they "work," it's because they've seen similar patterns before, not because they comprehend the underlying logic.
This creates a dangerous dependency. Junior developers "vibing" with LLMs might get working code without understanding the fundamental principles. When something breaks in production, they'll lack the knowledge to fix it.
Even experienced developers can find themselves in treacherous territory when relying too heavily on LLM-generated code. What starts as a productivity boost can transform into a dependency crutch.
The real danger isn't just technical limitations, but the false confidence it instills. Developers begin to believe they understand systems they've merely instructed an AI to generate – fundamentally different from understanding code you've written yourself.
We're already seeing the warning signs: projects cobbled together with LLM-generated code that work initially but become maintenance nightmares when requirements change or edge cases emerge.
The venture capital money is flowing exactly as it did with blockchain. Anthropic raised billions, OpenAI is valued astronomically despite minimal revenue, and countless others are competing to build ever-larger models with vague promises. Every startup now claims to be "AI-powered" regardless of whether it makes sense.
Don't get me wrong—there's genuine innovation happening in AI research. But "vibe coding" isn't it. It's a marketing term designed to make fuzzy prompting sound revolutionary.
Cursor perfectly embodies this AI hype cycle. It's an AI-enhanced code editor built on VS Code that promises to revolutionize programming by letting you "chat with your codebase." Just like blockchain startups promised to "revolutionize" industries, Cursor promises to transform development by adding LLM capabilities.
Yes, Cursor can be genuinely helpful. It can explain unfamiliar code, suggest completions, and help debug simple issues. After trying it for just an hour, I found the autocomplete to be MAGICAL for simple refactoring and basic functionality.
But the marketing goes far beyond reality. The suggestion that you can simply describe what you want and get production-ready code is dangerously misleading. What you get are approximations with:
- Security vulnerabilities the model doesn't understand
- Edge cases it hasn't considered
- Performance implications it can't reason about
- Dependency conflicts it has no way to foresee
The most concerning aspect is how such tools are marketed to beginners as shortcuts around learning fundamentals. "Why spend years learning to code when you can just tell AI what you want?" This is reminiscent of how crypto was sold as a get-rich-quick scheme requiring no actual understanding.
When you "vibe code" with an AI, you're not eliminating complexity—you're outsourcing understanding to a black box. This creates developers who can prompt but not program, who can generate but not comprehend.
The real utility of LLMs in development is in augmenting existing workflows:
- Explaining unfamiliar codebases
- Generating boilerplate for well-understood patterns
- Suggesting implementations that a developer evaluates critically
- Assisting with documentation and testing
These uses involve the model as a subordinate assistant to a knowledgeable developer, not as a replacement for expertise. This is where the technology adds value—as a sophisticated tool in skilled hands.
Cursor is just a better hammer, not a replacement for understanding what you're building. The actual value emerges when used by developers who understand what happens beneath the abstractions. They can recognize when AI suggestions make sense and when they don't because they have the fundamental knowledge to evaluate output critically.
This is precisely where the "vibe coding" narrative falls apart.
-
 @ bf47c19e:c3d2573b
2025-05-11 18:24:44
@ bf47c19e:c3d2573b
2025-05-11 18:24:44Originalni tekst na dvadesetjedan.com.
Autor: Gigi / Prevod na srpski: Plumsky
Postoji sveto carstvo privatnosti za svakog čoveka gde on bira i pravi odluke – carstvo stvoreno na bazičnim pravima i slobode koje zakon, generalno, ne sme narušavati. Džefri Fišer, Arhiepiskop Canterberija (1959)
Pre ne toliko dugo, uobičajen režim interneta je bio neenkriptovan običan tekst (plain text). Svi su mogli špiunirati svakoga i mnogi nisu o tome ni razmišljali. Globalno obelodanjivanje nadzora 2013. je to promenilo i danas se koriste mnogo bezbedniji protokoli i end-to-end enkripcija postaje standard sve više. Iako bitcoin postaje tinejdžer, mi smo – metaforično govoreći – i dalje u dobu običnog teksta narandžastog novčića. Bitcoin je radikalno providljiv protokol sam po sebi, ali postoje značajni načini da korisnik zaštiti svoju privatnost. U ovom članku želimo da istaknemo neke od ovih strategija, prodiskutujemo najbolje prakse, i damo preporuke koje mogu primeniti i bitcoin novajlije i veterani.
Zašto je privatnost bitna
Privatnost je potrebna da bi otvoreno društvo moglo da funkcioniše u digitalnoj eri. Privatnost nije isto što i tajanstvenost. Privatna stvar je nešto što neko ne želi da ceo svet zna, a tajna stvar je nešto što neko ne želi bilo ko da zna. Privatnost je moć da se čovek selektivno otkriva svom okruženju.
Ovim snažnim rečima Erik Hjus je započeo svoj tekst Sajferpankov Manifesto (Cypherpunk's Manifesto) 1993. Razlika između privatnosti i tajanstvenosti je suptilna ali jako važna. Odlučiti se za privatnost ne znači da neko ima tajne koje želi sakriti. Da ovo ilustrujemo shvatite samo da ono što obavljate u svom toaletu ili u spavaćoj sobi nije niti ilegalno niti tajna (u mnogim slučajevima), ali vi svejedno odlučujete da zatvorite vrata i navučete zavese.
Slično tome, koliko para imate i gde ih trošite nije naručito tajna stvar. Ipak, to bi trebalo biti privatan slučaj. Mnogi bi se složili da vaš šef ne treba da zna gde vi trošite vašu platu. Privatnosti je čak zaštićena od strane mnogobrojnih internacionalnih nadležnih organa. Iz Američke Deklaracije Prava i Dužnosti Čoveka (American Declaration of the Rights and Duties of Man) Ujedinjenim Nacijama, napisano je da je privatnost fundamentalno prava gradjana širom sveta.
Niko ne sme biti podvrgnut smetnjama njegovoj privatnosti, porodici, rezidenciji ili komunikacijama, niti napadnuta njegova čast i reputacija. Svi imaju pravo da se štite zakonom protiv takvih smetnja ili napada. Artikal 12, Deklaracija Ljudskih Prava Ujedinjenih Nacija
Bitcoin i privatnost
Iako je bitcoin često opisivan kao anoniman način plaćanja medijima, on u stvari poseduje potpuno suprotne osobine. On je poluanoniman u najboljem slučaju i danas mnogima nije ni malo lako primeniti taktike da bi bili sigurni da njihov poluanonimni identitet na bitcoin mreži ne bude povezan sa legalnim identitetom u stvarnom svetu.
Bitcoin je otvoren sistem. On je javna baza podataka koju svako može da proučava i analizira. Znači, svaka transakcija koja je upisana u tu bazu kroz dokaz rada (proof-of-work) postojaće i biće otkrivena dokle god bitcoin postoji, što znači - zauvek. Ne primenjivati najbolje prakse privatnosti može imati štetne posledice u dalekoj budućnosti.
Privatnost, kao sigurnost, je proces koji je težak, ali nije nemoguć. Alatke nastavljaju da se razvijaju koje čuvaju privatnost kad se koristi bitcoin and srećom mnoge od tih alatki su sve lakše za korišćenje. Nažalost ne postoji panacea u ovom pristupu. Mora se biti svesan svih kompromisa i usavršavati te prakse dok se one menjaju.
Najbolje prakse privatnosti
Kao i sve u bitcoinu, kontrola privatnosti je postepena, korak po korak, procedura. Naučiti i primeniti ove najbolje prakse zahteva strpljivost i odgovornost, tako da ne budite obeshrabreni ako vam se čini da je to sve previše. Svaki korak, koliko god bio mali, je korak u dobrom pravcu.
Koje korake preduzeti da bi uvećali svoju privatnost:
- Budite u vlasništvu sami svojih novčića
- Nikad ne ponavljajte korišćenje istih adresa
- Minimizirajte korišćenje servisa koji zahtevaju identitet (Know your customer - KYC)
- Minimizirajte sve izloženosti trećim licima
- Upravljajte svojim nodom
- Koristite Lightning mrežu za male transakcije
- Nemojte koristiti javne blok pretraživače za svoje transakcije
- Koristite metodu CoinJoin često i rano pri nabavljanju svojih novčića
Budite u vlasništvu sami svojih novčića: Ako ključevi nisu tvoji, onda nije ni bitcoin. Ako neko drugo drži vaš bitcoin za vas, oni znaju sve što se može znati: količinu, istoriju transakcija pa i sve buduće transakcije, itd. Preuzimanje vlasništva bitcoina u svoje ruke je prvi i najvažniji korak.
Nikad ne kroistite istu adresu dvaput: Ponavljanje adresa poništava privatnost pošiljalca i primaoca bitcoina. Ovo se treba izbegavati pod svaku cenu.
Minimizirajte korišćenje servisa koji zahtevaju identitet (KYC): Vezivati svoj legalni identitet za svoje bitcoin adrese je zlo koje se zahteva od strane mnogih državnih nadležnosti. Dok je efektivnost ovih zakona i regulacija disputabilno, posledice njihovog primenjivanja su uglavnom štetne po korisnicima. Ovo je očigledno pošto je česta pojava da se te informacije često izlivaju iz slabo obezbeđenih digitalnih servera. Ako izaberete da koristite KYC servise da bi nabavljali bitcoin, proučite i razumite odnos između vas i tog biznisa. Vi ste poverljivi tom biznisu za sve vaše lične podatke, pa i buduće obezbeđenje tih podataka. Ako i dalje zarađujete kroz fiat novčani sistem, mi preporučujemo da koristite samo bitcoin ekskluzivne servise koji vam dozvoljavaju da autamatski kupujete bitcoin s vremena na vreme. Ako zelite da potpuno da izbegnete KYC, pregledajte https://bitcoinqna.github.io/noKYConly/.
Minimizirajte sve izloženosti trećim licima: Poverljivost trećim licima je bezbednosna rupa (https://nakamotoinstitute.org/trusted-third-parties/). Ako možete biti poverljivi samo sebi, onda bi to tako trebalo da bude.
Upravljajte svojim nodom: Ako nod nije tvoj, onda nisu ni pravila. Upravljanje svojim nodom je suštinska potreba da bi se bitcoin koristio na privatan način. Svaka interakcija sa bitcoin mrežom je posrednjena nodom. Ako vi taj nod ne upravljate, čiji god nod koristite može da vidi sve što vi radite. Ova upustva (https://bitcoiner.guide/node/) su jako korisna da bi započeli proces korišćenja svog noda.
Koristite Lightning mrežu za male transakcije: Pošto Lightning protokol ne koristi glavnu bitcoin mrežu za trasakcije onda je i samim tim povećana privatnost korišćenja bez dodatnog truda. Iako je i dalje rano, oni apsolutno bezobzirni periodi Lightning mreže su verovatno daleko iza nas. Korišćenje Lightning-a za transakcije malih i srednjih veličina će vam pomoći da uvećate privatnost a da smanjite naplate svojih pojedinačnih bitcoin transakcija.
Nemojte koristiti javne blok pretraživače za svoje transakcije: Proveravanje adresa na javnim blok pretraživačima povezuje te adrese sa vašim IP podacima, koji se onda mogu koristiti da se otkrije vaš identitet. Softveri kao Umbrel i myNode vam omogućavaju da lako koristite sami svoj blok pretraživač. Ako morate koristiti javne pretraživače, uradite to uz VPN ili Tor.
Koristite CoinJoin često i rano pri nabavljanju svojih novčića: Pošto je bitcoin večan, primenjivanje saradničkih CoinJoin praksa će vam obezbediti privatnost u budućnosti. Dok su CoinJoin transakcije svakovrsne, softveri koji su laki za korišćenje već sad postoje koji mogu automatizovati ovu vrstu transakcija. Samourai Whirlpool (https://samouraiwallet.com/whirlpool) je odličan izbor za Android korisnike. Joinmarket (https://github.com/joinmarket-webui/jam) se može koristiti na vašem nodu. A servisi postoje koji pri snabdevanju vašeg bitcoina istog trenutka obave CoinJoin tranzakciju automatski.
Zaključak
Svi bi trebalo da se potrude da koriste bitcoin na što privatniji način. Privatnost nije isto što i tajanstvenost. Privatnost je ljudsko pravo i mi svi trebamo da branimo i primenljujemo to pravo. Teško je izbrisati postojeće informacije sa interneta; a izbrisati ih sa bitcoin baze podataka je nemoguće. Iako su daleko od savršenih, alatke postoje danas koje vam omogućavaju da najbolje prakse privatnosti i vi sami primenite. Mi smo vam naglasili neke od njih i - kroz poboljšanje u bitcoin protokolu kroz Taproot i Schnorr - one će postajati sve usavršenije.
Bitcoin postupci se ne mogu lako opisati korišćenjem tradicionalnim konceptima. Pitanja kao što su "Ko je vlasnik ovog novca?" ili "Odakle taj novac potiče?" postaju sve teža da se odgovore a u nekim okolnostima postaju potpuno beznačajna.
Satoši je dizajnirao bitcoin misleći na privatnost. Na nivou protokola svaka bitcoin transakcija je proces "topljenja" koji za sobom samo ostavlja heuristične mrvice hleba. Protokolu nije bitno odakle se pojavio bilo koji bitcoin ili satoši. Niti je njega briga ko je legalan identitet vlasnika. Protokolu je samo važno da li su digitalni potpisi validni. Dokle god je govor slobodan, potpisivanje poruka - privatno ili ne - ne sme biti kriminalan postupak.
Dodatni Resursi
This Month in Bitcoin Privacy | Janine
Hodl Privacy FAQ | 6102
Digital Privacy | 6102
UseWhirlpool.com | Bitcoin Q+A
Bitcoin Privacy Guide | Bitcoin Q+A
Ovaj članak napisan je u saradnji sa Matt Odellom, nezavisnim bitcoin istraživačem. Nađite njegove preporuke za privatnost na werunbtc.com
-
 @ a39d19ec:3d88f61e
2025-04-22 12:44:42
@ a39d19ec:3d88f61e
2025-04-22 12:44:42Die Debatte um Migration, Grenzsicherung und Abschiebungen wird in Deutschland meist emotional geführt. Wer fordert, dass illegale Einwanderer abgeschoben werden, sieht sich nicht selten dem Vorwurf des Rassismus ausgesetzt. Doch dieser Vorwurf ist nicht nur sachlich unbegründet, sondern verkehrt die Realität ins Gegenteil: Tatsächlich sind es gerade diejenigen, die hinter jeder Forderung nach Rechtssicherheit eine rassistische Motivation vermuten, die selbst in erster Linie nach Hautfarbe, Herkunft oder Nationalität urteilen.
Das Recht steht über Emotionen
Deutschland ist ein Rechtsstaat. Das bedeutet, dass Regeln nicht nach Bauchgefühl oder politischer Stimmungslage ausgelegt werden können, sondern auf klaren gesetzlichen Grundlagen beruhen müssen. Einer dieser Grundsätze ist in Artikel 16a des Grundgesetzes verankert. Dort heißt es:
„Auf Absatz 1 [Asylrecht] kann sich nicht berufen, wer aus einem Mitgliedstaat der Europäischen Gemeinschaften oder aus einem anderen Drittstaat einreist, in dem die Anwendung des Abkommens über die Rechtsstellung der Flüchtlinge und der Europäischen Menschenrechtskonvention sichergestellt ist.“
Das bedeutet, dass jeder, der über sichere Drittstaaten nach Deutschland einreist, keinen Anspruch auf Asyl hat. Wer dennoch bleibt, hält sich illegal im Land auf und unterliegt den geltenden Regelungen zur Rückführung. Die Forderung nach Abschiebungen ist daher nichts anderes als die Forderung nach der Einhaltung von Recht und Gesetz.
Die Umkehrung des Rassismusbegriffs
Wer einerseits behauptet, dass das deutsche Asyl- und Aufenthaltsrecht strikt durchgesetzt werden soll, und andererseits nicht nach Herkunft oder Hautfarbe unterscheidet, handelt wertneutral. Diejenigen jedoch, die in einer solchen Forderung nach Rechtsstaatlichkeit einen rassistischen Unterton sehen, projizieren ihre eigenen Denkmuster auf andere: Sie unterstellen, dass die Debatte ausschließlich entlang ethnischer, rassistischer oder nationaler Kriterien geführt wird – und genau das ist eine rassistische Denkweise.
Jemand, der illegale Einwanderung kritisiert, tut dies nicht, weil ihn die Herkunft der Menschen interessiert, sondern weil er den Rechtsstaat respektiert. Hingegen erkennt jemand, der hinter dieser Kritik Rassismus wittert, offenbar in erster Linie die „Rasse“ oder Herkunft der betreffenden Personen und reduziert sie darauf.
Finanzielle Belastung statt ideologischer Debatte
Neben der rechtlichen gibt es auch eine ökonomische Komponente. Der deutsche Wohlfahrtsstaat basiert auf einem Solidarprinzip: Die Bürger zahlen in das System ein, um sich gegenseitig in schwierigen Zeiten zu unterstützen. Dieser Wohlstand wurde über Generationen hinweg von denjenigen erarbeitet, die hier seit langem leben. Die Priorität liegt daher darauf, die vorhandenen Mittel zuerst unter denjenigen zu verteilen, die durch Steuern, Sozialabgaben und Arbeit zum Erhalt dieses Systems beitragen – nicht unter denen, die sich durch illegale Einreise und fehlende wirtschaftliche Eigenleistung in das System begeben.
Das ist keine ideologische Frage, sondern eine rein wirtschaftliche Abwägung. Ein Sozialsystem kann nur dann nachhaltig funktionieren, wenn es nicht unbegrenzt belastet wird. Würde Deutschland keine klaren Regeln zur Einwanderung und Abschiebung haben, würde dies unweigerlich zur Überlastung des Sozialstaates führen – mit negativen Konsequenzen für alle.
Sozialpatriotismus
Ein weiterer wichtiger Aspekt ist der Schutz der Arbeitsleistung jener Generationen, die Deutschland nach dem Zweiten Weltkrieg mühsam wieder aufgebaut haben. Während oft betont wird, dass die Deutschen moralisch kein Erbe aus der Zeit vor 1945 beanspruchen dürfen – außer der Verantwortung für den Holocaust –, ist es umso bedeutsamer, das neue Erbe nach 1945 zu respektieren, das auf Fleiß, Disziplin und harter Arbeit beruht. Der Wiederaufbau war eine kollektive Leistung deutscher Menschen, deren Früchte nicht bedenkenlos verteilt werden dürfen, sondern vorrangig denjenigen zugutekommen sollten, die dieses Fundament mitgeschaffen oder es über Generationen mitgetragen haben.
Rechtstaatlichkeit ist nicht verhandelbar
Wer sich für eine konsequente Abschiebepraxis ausspricht, tut dies nicht aus rassistischen Motiven, sondern aus Respekt vor der Rechtsstaatlichkeit und den wirtschaftlichen Grundlagen des Landes. Der Vorwurf des Rassismus in diesem Kontext ist daher nicht nur falsch, sondern entlarvt eine selektive Wahrnehmung nach rassistischen Merkmalen bei denjenigen, die ihn erheben.
-
 @ 4ba8e86d:89d32de4
2025-04-21 02:13:56
@ 4ba8e86d:89d32de4
2025-04-21 02:13:56Tutorial feito por nostr:nostr:npub1rc56x0ek0dd303eph523g3chm0wmrs5wdk6vs0ehd0m5fn8t7y4sqra3tk poste original abaixo:
Parte 1 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/263585/tutorial-debloat-de-celulares-android-via-adb-parte-1
Parte 2 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/index.php/263586/tutorial-debloat-de-celulares-android-via-adb-parte-2
Quando o assunto é privacidade em celulares, uma das medidas comumente mencionadas é a remoção de bloatwares do dispositivo, também chamado de debloat. O meio mais eficiente para isso sem dúvidas é a troca de sistema operacional. Custom Rom’s como LineageOS, GrapheneOS, Iodé, CalyxOS, etc, já são bastante enxutos nesse quesito, principalmente quanto não é instalado os G-Apps com o sistema. No entanto, essa prática pode acabar resultando em problemas indesejados como a perca de funções do dispositivo, e até mesmo incompatibilidade com apps bancários, tornando este método mais atrativo para quem possui mais de um dispositivo e separando um apenas para privacidade. Pensando nisso, pessoas que possuem apenas um único dispositivo móvel, que são necessitadas desses apps ou funções, mas, ao mesmo tempo, tem essa visão em prol da privacidade, buscam por um meio-termo entre manter a Stock rom, e não ter seus dados coletados por esses bloatwares. Felizmente, a remoção de bloatwares é possível e pode ser realizada via root, ou mais da maneira que este artigo irá tratar, via adb.
O que são bloatwares?
Bloatware é a junção das palavras bloat (inchar) + software (programa), ou seja, um bloatware é basicamente um programa inútil ou facilmente substituível — colocado em seu dispositivo previamente pela fabricante e operadora — que está no seu dispositivo apenas ocupando espaço de armazenamento, consumindo memória RAM e pior, coletando seus dados e enviando para servidores externos, além de serem mais pontos de vulnerabilidades.
O que é o adb?
O Android Debug Brigde, ou apenas adb, é uma ferramenta que se utiliza das permissões de usuário shell e permite o envio de comandos vindo de um computador para um dispositivo Android exigindo apenas que a depuração USB esteja ativa, mas também pode ser usada diretamente no celular a partir do Android 11, com o uso do Termux e a depuração sem fio (ou depuração wifi). A ferramenta funciona normalmente em dispositivos sem root, e também funciona caso o celular esteja em Recovery Mode.
Requisitos:
Para computadores:
• Depuração USB ativa no celular; • Computador com adb; • Cabo USB;
Para celulares:
• Depuração sem fio (ou depuração wifi) ativa no celular; • Termux; • Android 11 ou superior;
Para ambos:
• Firewall NetGuard instalado e configurado no celular; • Lista de bloatwares para seu dispositivo;
Ativação de depuração:
Para ativar a Depuração USB em seu dispositivo, pesquise como ativar as opções de desenvolvedor de seu dispositivo, e lá ative a depuração. No caso da depuração sem fio, sua ativação irá ser necessária apenas no momento que for conectar o dispositivo ao Termux.
Instalação e configuração do NetGuard
O NetGuard pode ser instalado através da própria Google Play Store, mas de preferência instale pela F-Droid ou Github para evitar telemetria.
F-Droid: https://f-droid.org/packages/eu.faircode.netguard/
Github: https://github.com/M66B/NetGuard/releases
Após instalado, configure da seguinte maneira:
Configurações → padrões (lista branca/negra) → ative as 3 primeiras opções (bloquear wifi, bloquear dados móveis e aplicar regras ‘quando tela estiver ligada’);
Configurações → opções avançadas → ative as duas primeiras (administrar aplicativos do sistema e registrar acesso a internet);
Com isso, todos os apps estarão sendo bloqueados de acessar a internet, seja por wifi ou dados móveis, e na página principal do app basta permitir o acesso a rede para os apps que você vai usar (se necessário). Permita que o app rode em segundo plano sem restrição da otimização de bateria, assim quando o celular ligar, ele já estará ativo.
Lista de bloatwares
Nem todos os bloatwares são genéricos, haverá bloatwares diferentes conforme a marca, modelo, versão do Android, e até mesmo região.
Para obter uma lista de bloatwares de seu dispositivo, caso seu aparelho já possua um tempo de existência, você encontrará listas prontas facilmente apenas pesquisando por elas. Supondo que temos um Samsung Galaxy Note 10 Plus em mãos, basta pesquisar em seu motor de busca por:
Samsung Galaxy Note 10 Plus bloatware listProvavelmente essas listas já terão inclusas todos os bloatwares das mais diversas regiões, lhe poupando o trabalho de buscar por alguma lista mais específica.
Caso seu aparelho seja muito recente, e/ou não encontre uma lista pronta de bloatwares, devo dizer que você acaba de pegar em merda, pois é chato para um caralho pesquisar por cada aplicação para saber sua função, se é essencial para o sistema ou se é facilmente substituível.
De antemão já aviso, que mais para frente, caso vossa gostosura remova um desses aplicativos que era essencial para o sistema sem saber, vai acabar resultando na perda de alguma função importante, ou pior, ao reiniciar o aparelho o sistema pode estar quebrado, lhe obrigando a seguir com uma formatação, e repetir todo o processo novamente.
Download do adb em computadores
Para usar a ferramenta do adb em computadores, basta baixar o pacote chamado SDK platform-tools, disponível através deste link: https://developer.android.com/tools/releases/platform-tools. Por ele, você consegue o download para Windows, Mac e Linux.
Uma vez baixado, basta extrair o arquivo zipado, contendo dentro dele uma pasta chamada platform-tools que basta ser aberta no terminal para se usar o adb.
Download do adb em celulares com Termux.
Para usar a ferramenta do adb diretamente no celular, antes temos que baixar o app Termux, que é um emulador de terminal linux, e já possui o adb em seu repositório. Você encontra o app na Google Play Store, mas novamente recomendo baixar pela F-Droid ou diretamente no Github do projeto.
F-Droid: https://f-droid.org/en/packages/com.termux/
Github: https://github.com/termux/termux-app/releases
Processo de debloat
Antes de iniciarmos, é importante deixar claro que não é para você sair removendo todos os bloatwares de cara sem mais nem menos, afinal alguns deles precisam antes ser substituídos, podem ser essenciais para você para alguma atividade ou função, ou até mesmo são insubstituíveis.
Alguns exemplos de bloatwares que a substituição é necessária antes da remoção, é o Launcher, afinal, é a interface gráfica do sistema, e o teclado, que sem ele só é possível digitar com teclado externo. O Launcher e teclado podem ser substituídos por quaisquer outros, minha recomendação pessoal é por aqueles que respeitam sua privacidade, como Pie Launcher e Simple Laucher, enquanto o teclado pelo OpenBoard e FlorisBoard, todos open-source e disponíveis da F-Droid.
Identifique entre a lista de bloatwares, quais você gosta, precisa ou prefere não substituir, de maneira alguma você é obrigado a remover todos os bloatwares possíveis, modifique seu sistema a seu bel-prazer. O NetGuard lista todos os apps do celular com o nome do pacote, com isso você pode filtrar bem qual deles não remover.
Um exemplo claro de bloatware insubstituível e, portanto, não pode ser removido, é o com.android.mtp, um protocolo onde sua função é auxiliar a comunicação do dispositivo com um computador via USB, mas por algum motivo, tem acesso a rede e se comunica frequentemente com servidores externos. Para esses casos, e melhor solução mesmo é bloquear o acesso a rede desses bloatwares com o NetGuard.
MTP tentando comunicação com servidores externos:
Executando o adb shell
No computador
Faça backup de todos os seus arquivos importantes para algum armazenamento externo, e formate seu celular com o hard reset. Após a formatação, e a ativação da depuração USB, conecte seu aparelho e o pc com o auxílio de um cabo USB. Muito provavelmente seu dispositivo irá apenas começar a carregar, por isso permita a transferência de dados, para que o computador consiga se comunicar normalmente com o celular.
Já no pc, abra a pasta platform-tools dentro do terminal, e execute o seguinte comando:
./adb start-serverO resultado deve ser:
daemon not running; starting now at tcp:5037 daemon started successfully
E caso não apareça nada, execute:
./adb kill-serverE inicie novamente.
Com o adb conectado ao celular, execute:
./adb shellPara poder executar comandos diretamente para o dispositivo. No meu caso, meu celular é um Redmi Note 8 Pro, codinome Begonia.
Logo o resultado deve ser:
begonia:/ $
Caso ocorra algum erro do tipo:
adb: device unauthorized. This adb server’s $ADB_VENDOR_KEYS is not set Try ‘adb kill-server’ if that seems wrong. Otherwise check for a confirmation dialog on your device.
Verifique no celular se apareceu alguma confirmação para autorizar a depuração USB, caso sim, autorize e tente novamente. Caso não apareça nada, execute o kill-server e repita o processo.
No celular
Após realizar o mesmo processo de backup e hard reset citado anteriormente, instale o Termux e, com ele iniciado, execute o comando:
pkg install android-toolsQuando surgir a mensagem “Do you want to continue? [Y/n]”, basta dar enter novamente que já aceita e finaliza a instalação
Agora, vá até as opções de desenvolvedor, e ative a depuração sem fio. Dentro das opções da depuração sem fio, terá uma opção de emparelhamento do dispositivo com um código, que irá informar para você um código em emparelhamento, com um endereço IP e porta, que será usado para a conexão com o Termux.
Para facilitar o processo, recomendo que abra tanto as configurações quanto o Termux ao mesmo tempo, e divida a tela com os dois app’s, como da maneira a seguir:
Para parear o Termux com o dispositivo, não é necessário digitar o ip informado, basta trocar por “localhost”, já a porta e o código de emparelhamento, deve ser digitado exatamente como informado. Execute:
adb pair localhost:porta CódigoDeEmparelhamentoDe acordo com a imagem mostrada anteriormente, o comando ficaria “adb pair localhost:41255 757495”.
Com o dispositivo emparelhado com o Termux, agora basta conectar para conseguir executar os comandos, para isso execute:
adb connect localhost:portaObs: a porta que você deve informar neste comando não é a mesma informada com o código de emparelhamento, e sim a informada na tela principal da depuração sem fio.
Pronto! Termux e adb conectado com sucesso ao dispositivo, agora basta executar normalmente o adb shell:
adb shellRemoção na prática Com o adb shell executado, você está pronto para remover os bloatwares. No meu caso, irei mostrar apenas a remoção de um app (Google Maps), já que o comando é o mesmo para qualquer outro, mudando apenas o nome do pacote.
Dentro do NetGuard, verificando as informações do Google Maps:
Podemos ver que mesmo fora de uso, e com a localização do dispositivo desativado, o app está tentando loucamente se comunicar com servidores externos, e informar sabe-se lá que peste. Mas sem novidades até aqui, o mais importante é que podemos ver que o nome do pacote do Google Maps é com.google.android.apps.maps, e para o remover do celular, basta executar:
pm uninstall –user 0 com.google.android.apps.mapsE pronto, bloatware removido! Agora basta repetir o processo para o resto dos bloatwares, trocando apenas o nome do pacote.
Para acelerar o processo, você pode já criar uma lista do bloco de notas com os comandos, e quando colar no terminal, irá executar um atrás do outro.
Exemplo de lista:
Caso a donzela tenha removido alguma coisa sem querer, também é possível recuperar o pacote com o comando:
cmd package install-existing nome.do.pacotePós-debloat
Após limpar o máximo possível o seu sistema, reinicie o aparelho, caso entre no como recovery e não seja possível dar reboot, significa que você removeu algum app “essencial” para o sistema, e terá que formatar o aparelho e repetir toda a remoção novamente, desta vez removendo poucos bloatwares de uma vez, e reiniciando o aparelho até descobrir qual deles não pode ser removido. Sim, dá trabalho… quem mandou querer privacidade?
Caso o aparelho reinicie normalmente após a remoção, parabéns, agora basta usar seu celular como bem entender! Mantenha o NetGuard sempre executando e os bloatwares que não foram possíveis remover não irão se comunicar com servidores externos, passe a usar apps open source da F-Droid e instale outros apps através da Aurora Store ao invés da Google Play Store.
Referências: Caso você seja um Australopithecus e tenha achado este guia difícil, eis uma videoaula (3:14:40) do Anderson do canal Ciberdef, realizando todo o processo: http://odysee.com/@zai:5/Como-remover-at%C3%A9-200-APLICATIVOS-que-colocam-a-sua-PRIVACIDADE-E-SEGURAN%C3%87A-em-risco.:4?lid=6d50f40314eee7e2f218536d9e5d300290931d23
Pdf’s do Anderson citados na videoaula: créditos ao anon6837264 http://eternalcbrzpicytj4zyguygpmkjlkddxob7tptlr25cdipe5svyqoqd.onion/file/3863a834d29285d397b73a4af6fb1bbe67c888d72d30/t-05e63192d02ffd.pdf
Processo de instalação do Termux e adb no celular: https://youtu.be/APolZrPHSms
-
 @ c631e267:c2b78d3e
2025-03-21 19:41:50
@ c631e267:c2b78d3e
2025-03-21 19:41:50Wir werden nicht zulassen, dass technisch manches möglich ist, \ aber der Staat es nicht nutzt. \ Angela Merkel
Die Modalverben zu erklären, ist im Deutschunterricht manchmal nicht ganz einfach. Nicht alle Fremdsprachen unterscheiden zum Beispiel bei der Frage nach einer Möglichkeit gleichermaßen zwischen «können» im Sinne von «die Gelegenheit, Kenntnis oder Fähigkeit haben» und «dürfen» als «die Erlaubnis oder Berechtigung haben». Das spanische Wort «poder» etwa steht für beides.
Ebenso ist vielen Schülern auf den ersten Blick nicht recht klar, dass das logische Gegenteil von «müssen» nicht unbedingt «nicht müssen» ist, sondern vielmehr «nicht dürfen». An den Verkehrsschildern lässt sich so etwas meistens recht gut erklären: Manchmal muss man abbiegen, aber manchmal darf man eben nicht.

Dieses Beispiel soll ein wenig die Verwirrungstaktik veranschaulichen, die in der Politik gerne verwendet wird, um unpopuläre oder restriktive Maßnahmen Stück für Stück einzuführen. Zuerst ist etwas einfach innovativ und bringt viele Vorteile. Vor allem ist es freiwillig, jeder kann selber entscheiden, niemand muss mitmachen. Später kann man zunehmend weniger Alternativen wählen, weil sie verschwinden, und irgendwann verwandelt sich alles andere in «nicht dürfen» – die Maßnahme ist obligatorisch.
Um die Durchsetzung derartiger Initiativen strategisch zu unterstützen und nett zu verpacken, gibt es Lobbyisten, gerne auch NGOs genannt. Dass das «NG» am Anfang dieser Abkürzung übersetzt «Nicht-Regierungs-» bedeutet, ist ein Anachronismus. Das war vielleicht früher einmal so, heute ist eher das Gegenteil gemeint.
In unserer modernen Zeit wird enorm viel Lobbyarbeit für die Digitalisierung praktisch sämtlicher Lebensbereiche aufgewendet. Was das auf dem Sektor der Mobilität bedeuten kann, haben wir diese Woche anhand aktueller Entwicklungen in Spanien beleuchtet. Begründet teilweise mit Vorgaben der Europäischen Union arbeitet man dort fleißig an einer «neuen Mobilität», basierend auf «intelligenter» technologischer Infrastruktur. Derartige Anwandlungen wurden auch schon als «Technofeudalismus» angeprangert.
Nationale Zugangspunkte für Mobilitätsdaten im Sinne der EU gibt es nicht nur in allen Mitgliedsländern, sondern auch in der Schweiz und in Großbritannien. Das Vereinigte Königreich beteiligt sich darüber hinaus an anderen EU-Projekten für digitale Überwachungs- und Kontrollmaßnahmen, wie dem biometrischen Identifizierungssystem für «nachhaltigen Verkehr und Tourismus».
Natürlich marschiert auch Deutschland stracks und euphorisch in Richtung digitaler Zukunft. Ohne vernetzte Mobilität und einen «verlässlichen Zugang zu Daten, einschließlich Echtzeitdaten» komme man in der Verkehrsplanung und -steuerung nicht aus, erklärt die Regierung. Der Interessenverband der IT-Dienstleister Bitkom will «die digitale Transformation der deutschen Wirtschaft und Verwaltung vorantreiben». Dazu bewirbt er unter anderem die Konzepte Smart City, Smart Region und Smart Country und behauptet, deutsche Großstädte «setzen bei Mobilität voll auf Digitalisierung».
Es steht zu befürchten, dass das umfassende Sammeln, Verarbeiten und Vernetzen von Daten, das angeblich die Menschen unterstützen soll (und theoretisch ja auch könnte), eher dazu benutzt wird, sie zu kontrollieren und zu manipulieren. Je elektrischer und digitaler unsere Umgebung wird, desto größer sind diese Möglichkeiten. Im Ergebnis könnten solche Prozesse den Bürger nicht nur einschränken oder überflüssig machen, sondern in mancherlei Hinsicht regelrecht abschalten. Eine gesunde Skepsis ist also geboten.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Er ist zuerst auf Transition News erschienen.
-
 @ 4ba8e86d:89d32de4
2025-04-21 02:12:19
@ 4ba8e86d:89d32de4
2025-04-21 02:12:19SISTEMA OPERACIONAL MÓVEIS
GrapheneOS : https://njump.me/nevent1qqs8t76evdgrg4qegdtyrq2rved63pr29wlqyj627n9tj4vlu66tqpqpzdmhxue69uhk7enxvd5xz6tw9ec82c30qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqppcqec9
CalyxOS : https://njump.me/nevent1qqsrm0lws2atln2kt3cqjacathnw0uj0jsxwklt37p7t380hl8mmstcpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3vamnwvaz7tmwdaehgu3wvf3kstnwd9hx5cf0qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgcwaehxw309aex2mrp0yhxxatjwfjkuapwveukjtcpzpmhxue69uhkummnw3ezumt0d5hszrnhwden5te0dehhxtnvdakz7qfywaehxw309ahx7um5wgh8ymm4dej8ymmrdd3xjarrda5kuetjwvhxxmmd9uq3uamnwvaz7tmwdaehgu3dv3jhvtnhv4kxcmmjv3jhytnwv46z7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qgewaehxw309ahx7um5wghxymmwva3x7mn89e3k7mf0qythwumn8ghj7cn5vvhxkmr9dejxz7n49e3k7mf0qyg8wumn8ghj7mn09eehgu3wvdez7smttdu
LineageOS : https://njump.me/nevent1qqsgw7sr36gaty48cf4snw0ezg5mg4atzhqayuge752esd469p26qfgpzdmhxue69uhhwmm59e6hg7r09ehkuef0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpnvm779
SISTEMA OPERACIONAL DESKTOP
Tails : https://njump.me/nevent1qqsf09ztvuu60g6xprazv2vxqqy5qlxjs4dkc9d36ta48q75cs9le4qpzemhxue69uhkummnw3ex2mrfw3jhxtn0wfnj7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz34ag5t
Qubes OS : https://njump.me/nevent1qqsp6jujgwl68uvurw0cw3hfhr40xq20sj7rl3z4yzwnhp9sdpa7augpzpmhxue69uhkummnw3ezumt0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsz9thwden5te0dehhxarj9ehhsarj9ejx2a30qyg8wumn8ghj7mn09eehgu3wvdez7qg4waehxw309aex2mrp0yhxgctdw4eju6t09uqjxamnwvaz7tmwdaehgu3dwejhy6txd9jkgtnhv4kxcmmjv3jhytnwv46z7qgwwaehxw309ahx7uewd3hkctcpremhxue69uhkummnw3ez6er9wch8wetvd3hhyer9wghxuet59uj3ljr8
Kali linux : https://njump.me/nevent1qqswlav72xdvamuyp9xc38c6t7070l3n2uxu67ssmal2g7gv35nmvhspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswt9rxe
Whonix : https://njump.me/nevent1qqs85gvejvzhk086lwh6edma7fv07p5c3wnwnxnzthwwntg2x6773egpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3qamnwvaz7tmwdaehgu3wd4hk6tcpzemhxue69uhkummnw3ezucnrdqhxu6twdfsj7qfywaehxw309ahx7um5wgh8ymm4dej8ymmrdd3xjarrda5kuetjwvhxxmmd9uq3wamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmd9uq3qamnwvaz7tmwduh8xarj9e3hytcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszrnhwden5te0dehhxtnvdakz7qg7waehxw309ahx7um5wgkkgetk9emk2mrvdaexgetj9ehx2ap0sen9p6
Kodachi : https://njump.me/nevent1qqsf5zszgurpd0vwdznzk98hck294zygw0s8dah6fpd309ecpreqtrgpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszgmhwden5te0dehhxarj94mx2unfve5k2epwwajkcmr0wfjx2u3wdejhgtcpremhxue69uhkummnw3ez6er9wch8wetvd3hhyer9wghxuet59uq3qamnwvaz7tmwdaehgu3wd4hk6tcpzamhxue69uhkyarr9e4kcetwv3sh5afwvdhk6tcpzpmhxue69uhkumewwd68ytnrwghszfrhwden5te0dehhxarj9eex7atwv3ex7cmtvf5hgcm0d9hx2unn9e3k7mf0qyvhwumn8ghj7mn0wd68ytnzdahxwcn0denjucm0d5hszrnhwden5te0dehhxtnvdakz7qgkwaehxw309ahx7um5wghxycmg9ehxjmn2vyhsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshs94a4d5
PGP
Openkeychain : https://njump.me/nevent1qqs9qtjgsulp76t7jkquf8nk8txs2ftsr0qke6mjmsc2svtwfvswzyqpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs36mp0w
Kleopatra : https://njump.me/nevent1qqspnevn932hdggvp4zam6mfyce0hmnxsp9wp8htpumq9vm3anq6etsppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpuaeghp
Pgp : https://njump.me/nevent1qqsggek707qf3rzttextmgqhym6d4g479jdnlnj78j96y0ut0x9nemcpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgptemhe
Como funciona o PGP? : https://njump.me/nevent1qqsz9r7azc8pkvfmkg2hv0nufaexjtnvga0yl85x9hu7ptpg20gxxpspremhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet59upzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy259fhs
Por que eu escrevi PGP. - Philip Zimmermann.
https://njump.me/nevent1qqsvysn94gm8prxn3jw04r0xwc6sngkskg756z48jsyrmqssvxtm7ncpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtchzxnad
VPN
Vpn : https://njump.me/nevent1qqs27ltgsr6mh4ffpseexz6s37355df3zsur709d0s89u2nugpcygsspzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqshzu2fk
InviZible Pro : https://njump.me/nevent1qqsvyevf2vld23a3xrpvarc72ndpcmfvc3lc45jej0j5kcsg36jq53cpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy33y5l4
Orbot: https://njump.me/nevent1qqsxswkyt6pe34egxp9w70cy83h40ururj6m9sxjdmfass4cjm4495stft593
I2P
i2p : https://njump.me/nevent1qqsvnj8n983r4knwjmnkfyum242q4c0cnd338l4z8p0m6xsmx89mxkslx0pgg
Entendendo e usando a rede I2P : https://njump.me/nevent1qqsxchp5ycpatjf5s4ag25jkawmw6kkf64vl43vnprxdcwrpnms9qkcppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpvht4mn
Criando e acessando sua conta Email na I2P : https://njump.me/nevent1qqs9v9dz897kh8e5lfar0dl7ljltf2fpdathsn3dkdsq7wg4ksr8xfgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpw8mzum
APLICATIVO 2FA
Aegis Authenticator : https://njump.me/nevent1qqsfttdwcn9equlrmtf9n6wee7lqntppzm03pzdcj4cdnxel3pz44zspz4mhxue69uhhyetvv9ujumn0wd68ytnzvuhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqscvtydq
YubiKey : https://njump.me/nevent1qqstsnn69y4sf4330n7039zxm7wza3ch7sn6plhzmd57w6j9jssavtspvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzueyvgt
GERENCIADOR DE SENHAS
KeepassDX: https://njump.me/nevent1qqswc850dr4ujvxnmpx75jauflf4arc93pqsty5pv8hxdm7lcw8ee8qpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpe0492n
Birwaden: https://njump.me/nevent1qqs0j5x9guk2v6xumhwqmftmcz736m9nm9wzacqwjarxmh8k4xdyzwgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpwfe2kc
KeePassXC: https://njump.me/nevent1qqsgftcrd8eau7tzr2p9lecuaf7z8mx5jl9w2k66ae3lzkw5wqcy5pcl2achp
CHAT MENSAGEM
SimpleXchat : https://njump.me/nevent1qqsds5xselnnu0dyy0j49peuun72snxcgn3u55d2320n37rja9gk8lgzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgmcmj7c
Briar : https://njump.me/nevent1qqs8rrtgvjr499hreugetrl7adkhsj2zextyfsukq5aa7wxthrgcqcg05n434
Element Messenger : https://njump.me/nevent1qqsq05snlqtxm5cpzkshlf8n5d5rj9383vjytkvqp5gta37hpuwt4mqyccee6
Pidgin : https://njump.me/nevent1qqsz7kngycyx7meckx53xk8ahk98jkh400usrvykh480xa4ct9zlx2c2ywvx3
E-MAIL
Thunderbird: https://njump.me/nevent1qqspq64gg0nw7t60zsvea5eykgrm43paz845e4jn74muw5qzdvve7uqrkwtjh
ProtonMail : https://njump.me/nevent1qqs908glhk68e7ms8zqtlsqd00wu3prnpt08dwre26hd6e5fhqdw99cppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpeyhg4z
Tutonota : https://njump.me/nevent1qqswtzh9zjxfey644qy4jsdh9465qcqd2wefx0jxa54gdckxjvkrrmqpz4mhxue69uhhyetvv9ujumt0wd68ytnsw43qygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs5hzhkv
k-9 mail : https://njump.me/nevent1qqs200g5a603y7utjgjk320r3srurrc4r66nv93mcg0x9umrw52ku5gpr3mhxue69uhkummnw3ezuumhd9ehxtt9de5kwmtp9e3kstczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgacflak
E-MAIL-ALIÁS
Simplelogin : https://njump.me/nevent1qqsvhz5pxqpqzr2ptanqyqgsjr50v7u9lc083fvdnglhrv36rnceppcppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqp9gsr7m
AnonAddy : https://njump.me/nevent1qqs9mcth70mkq2z25ws634qfn7vx2mlva3tkllayxergw0s7p8d3ggcpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs6mawe3
NAVEGADOR
Navegador Tor : https://njump.me/nevent1qqs06qfxy7wzqmk76l5d8vwyg6mvcye864xla5up52fy5sptcdy39lspzemhxue69uhkummnw3ezuerpw3sju6rpw4ej7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdp0urw
Mullvap Browser : https://njump.me/nevent1qqs2vsgc3wk09wdspv2mezltgg7nfdg97g0a0m5cmvkvr4nrfxluzfcpzdmhxue69uhhwmm59e6hg7r09ehkuef0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpj8h6fe
LibreWolf : https://njump.me/nevent1qqswv05mlmkcuvwhe8x3u5f0kgwzug7n2ltm68fr3j06xy9qalxwq2cpzemhxue69uhkummnw3ex2mrfw3jhxtn0wfnj7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzuv2hxr
Cromite : https://njump.me/nevent1qqs2ut83arlu735xp8jf87w5m3vykl4lv5nwkhldkqwu3l86khzzy4cpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs3dplt7
BUSCADORES
Searx : https://njump.me/nevent1qqsxyzpvgzx00n50nrlgctmy497vkm2cm8dd5pdp7fmw6uh8xnxdmaspr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqp23z7ax
APP-STORE
Obtainium : https://njump.me/nevent1qqstd8kzc5w3t2v6dgf36z0qrruufzfgnc53rj88zcjgsagj5c5k4rgpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqyarmca3
F-Droid : https://njump.me/nevent1qqst4kry49cc9g3g8s5gdnpgyk3gjte079jdnv43f0x4e85cjkxzjesymzuu4
Droid-ify : https://njump.me/nevent1qqsrr8yu9luq0gud902erdh8gw2lfunpe93uc2u6g8rh9ep7wt3v4sgpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsfzu9vk
Aurora Store : https://njump.me/nevent1qqsy69kcaf0zkcg0qnu90mtk46ly3p2jplgpzgk62wzspjqjft4fpjgpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzrpmsjy
RSS
Feeder : https://njump.me/nevent1qqsy29aeggpkmrc7t3c7y7ldgda7pszl7c8hh9zux80gjzrfvlhfhwqpp4mhxue69uhkummn9ekx7mqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgsvzzjy
VIDEOO CONFERENCIA
Jitsi meet : https://njump.me/nevent1qqswphw67hr6qmt2fpugcj77jrk7qkfdrszum7vw7n2cu6cx4r6sh4cgkderr
TECLADOS
HeliBoard : https://njump.me/nevent1qqsyqpc4d28rje03dcvshv4xserftahhpeylu2ez2jutdxwds4e8syspz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsr8mel5
OpenBoard : https://njump.me/nevent1qqsf7zqkup03yysy67y43nj48q53sr6yym38es655fh9fp6nxpl7rqspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswcvh3r
FlorisBoard : https://njump.me/nevent1qqsf7zqkup03yysy67y43nj48q53sr6yym38es655fh9fp6nxpl7rqspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswcvh3r
MAPAS
Osmand : https://njump.me/nevent1qqsxryp2ywj64az7n5p6jq5tn3tx5jv05te48dtmmt3lf94ydtgy4fgpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs54nwpj
Organic maps : https://njump.me/nevent1qqstrecuuzkw0dyusxdq7cuwju0ftskl7anx978s5dyn4pnldrkckzqpr4mhxue69uhkummnw3ezumtp0p5k6ctrd96xzer9dshx7un8qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpl8z3kk
TRADUÇÃO
LibreTranslate : https://njump.me/nevent1qqs953g3rhf0m8jh59204uskzz56em9xdrjkelv4wnkr07huk20442cpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzeqsx40
REMOÇÃO DOS METADADOS
Scrambled Exif : https://njump.me/nevent1qqs2658t702xv66p000y4mlhnvadmdxwzzfzcjkjf7kedrclr3ej7aspyfmhxue69uhk6atvw35hqmr90pjhytngw4eh5mmwv4nhjtnhdaexcep0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpguu0wh
ESTEGANOGRAFIA
PixelKnot: https://njump.me/nevent1qqsrh0yh9mg0lx86t5wcmhh97wm6n4v0radh6sd0554ugn354wqdj8gpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqyuvfqdp
PERFIL DE TRABALHO
Shelter : https://njump.me/nevent1qqspv9xxkmfp40cxgjuyfsyczndzmpnl83e7gugm7480mp9zhv50wkqpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdnu59c
PDF
MuPDF : https://njump.me/nevent1qqspn5lhe0dteys6npsrntmv2g470st8kh8p7hxxgmymqa95ejvxvfcpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs4hvhvj
Librera Reader : https://njump.me/nevent1qqsg60flpuf00sash48fexvwxkly2j5z9wjvjrzt883t3eqng293f3cpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz39tt3n
QR-Code
Binary Eye : https://njump.me/nevent1qqsz4n0uxxx3q5m0r42n9key3hchtwyp73hgh8l958rtmae5u2khgpgpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdmn4wp
Climático
Breezy Weather : https://njump.me/nevent1qqs9hjz5cz0y4am3kj33xn536uq85ydva775eqrml52mtnnpe898rzspzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgpd3tu8
ENCRYPTS
Cryptomator : https://njump.me/nevent1qqsvchvnw779m20583llgg5nlu6ph5psewetlczfac5vgw83ydmfndspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsx7ppw9
VeraCrypt : https://njump.me/nevent1qqsf6wzedsnrgq6hjk5c4jj66dxnplqwc4ygr46l8z3gfh38q2fdlwgm65ej3
EXTENSÕES
uBlock Origin : https://njump.me/nevent1qqswaa666lcj2c4nhnea8u4agjtu4l8q89xjln0yrngj7ssh72ntwzql8ssdj
Snowflake : https://njump.me/nevent1qqs0ws74zlt8uced3p2vee9td8x7vln2mkacp8szdufvs2ed94ctnwchce008
CLOUD
Nextcloud : https://njump.me/nevent1qqs2utg5z9htegdtrnllreuhypkk2026x8a0xdsmfczg9wdl8rgrcgg9nhgnm
NOTEPAD
Joplin : https://njump.me/nevent1qqsz2a0laecpelsznser3xd0jfa6ch2vpxtkx6vm6qg24e78xttpk0cpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpdu0hft
Standard Notes : https://njump.me/nevent1qqsv3596kz3qung5v23cjc4cpq7rqxg08y36rmzgcrvw5whtme83y3s7tng6r
MÚSICA
RiMusic : https://njump.me/nevent1qqsv3genqav2tfjllp86ust4umxm8tr2wd9kq8x7vrjq6ssp363mn0gpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqg42353n
ViMusic : https://njump.me/nevent1qqswx78559l4jsxsrygd8kj32sch4qu57stxq0z6twwl450vp39pdqqpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzjg863j
PODCAST
AntennaPod : https://njump.me/nevent1qqsp4nh7k4a6zymfwqqdlxuz8ua6kdhvgeeh3uxf2c9rtp9u3e9ku8qnr8lmy
VISUALIZAR VIDEO
VLC : https://njump.me/nevent1qqs0lz56wtlr2eye4ajs2gzn2r0dscw4y66wezhx0mue6dffth8zugcl9laky
YOUTUBE
NewPipe : https://njump.me/nevent1qqsdg06qpcjdnlvgm4xzqdap0dgjrkjewhmh4j3v4mxdl4rjh8768mgdw9uln
FreeTube : https://njump.me/nevent1qqsz6y6z7ze5gs56s8seaws8v6m6j2zu0pxa955dhq3ythmexak38mcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs5lkjvv
LibreTube : https://snort.social/e/nevent1qqstmd5m6wrdvn4gxf8xyhrwnlyaxmr89c9kjddvnvux6603f84t3fqpz4mhxue69uhhyetvv9ujumt0wd68ytnsw43qygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsswwznc
COMPARTILHAMENTO DE ARQUIVOS
OnionShare : https://njump.me/nevent1qqsr0a4ml5nu6ud5k9yzyawcd9arznnwkrc27dzzc95q6r50xmdff6qpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3uamnwvaz7tmwdaehgu3dv3jhvtnhv4kxcmmjv3jhytnwv46z7qgswaehxw309ahx7tnnw3ezucmj9uq32amnwvaz7tmjv4kxz7fwv3sk6atn9e5k7tcpzamhxue69uhkyarr9e4kcetwv3sh5afwvdhk6tcpzemhxue69uhkummnw3ezucnrdqhxu6twdfsj7qgswaehxw309ahx7um5wghx6mmd9uqjgamnwvaz7tmwdaehgu3wwfhh2mnywfhkx6mzd96xxmmfdejhyuewvdhk6tcppemhxue69uhkummn9ekx7mp0qythwumn8ghj7un9d3shjtnwdaehgu3wvfskuep0qyv8wumn8ghj7un9d3shjtnrw4e8yetwwshxv7tf9ut7qurt
Localsend : https://njump.me/nevent1qqsp8ldjhrxm09cvvcak20hrc0g8qju9f67pw7rxr2y3euyggw9284gpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzuyghqr
Wallet Bitcoin
Ashigaru Wallet : https://njump.me/nevent1qqstx9fz8kf24wgl26un8usxwsqjvuec9f8q392llmga75tw0kfarfcpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgvfsrqp
Samourai Wallet : https://njump.me/nevent1qqstcvjmz39rmrnrv7t5cl6p3x7pzj6jsspyh4s4vcwd2lugmre04ecpr9mhxue69uhkummnw3ezucn0denkymmwvuhxxmmd9upzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy3rg4qs
CÂMERA
opencamera : https://njump.me/nevent1qqs25glp6dh0crrjutxrgdjlnx9gtqpjtrkg29hlf7382aeyjd77jlqpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqssxcvgc
OFFICE
Collabora Office : https://njump.me/nevent1qqs8yn4ys6adpmeu3edmf580jhc3wluvlf823cc4ft4h0uqmfzdf99qpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsj40uss
TEXTOS
O manifesto de um Cypherpunk : https://njump.me/nevent1qqsd7hdlg6galn5mcuv3pm3ryfjxc4tkyph0cfqqe4du4dr4z8amqyspvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzal0efa
Operations security ( OPSEC) : https://snort.social/e/nevent1qqsp323havh3y9nxzd4qmm60hw87tm9gjns0mtzg8y309uf9mv85cqcpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz8ej9l7
O MANIFESTO CRIPTOANARQUISTA Timothy C. May – 1992. : https://njump.me/nevent1qqspp480wtyx2zhtwpu5gptrl8duv9rvq3mug85mp4d54qzywk3zq9gpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz5wq496
Declaração de independência do ciberespaço
- John Perry Barlow - 1996 : https://njump.me/nevent1qqs2njsy44n6p07mhgt2tnragvchasv386nf20ua5wklxqpttf6mzuqpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsukg4hr
The Cyphernomicon: Criptografia, Dinheiro Digital e o Futuro da Privacidade. escrito por Timothy C. May -Publicado em 1994. :
Livro completo em PDF no Github PrivacyOpenSource.
https://github.com/Alexemidio/PrivacyOpenSource/raw/main/Livros/THE%20CYPHERNOMICON%20.pdf Share
-
 @ ed5774ac:45611c5c
2025-04-19 20:29:31
@ ed5774ac:45611c5c
2025-04-19 20:29:31April 20, 2020: The day I saw my so-called friends expose themselves as gutless, brain-dead sheep.
On that day, I shared a video exposing the damning history of the Bill & Melinda Gates Foundation's vaccine campaigns in Africa and the developing world. As Gates was on every TV screen, shilling COVID jabs that didn’t even exist, I called out his blatant financial conflict of interest and pointed out the obvious in my facebook post: "Finally someone is able to explain why Bill Gates runs from TV to TV to promote vaccination. Not surprisingly, it's all about money again…" - referencing his substantial investments in vaccine technology, including BioNTech's mRNA platform that would later produce the COVID vaccines and generate massive profits for his so-called philanthropic foundation.
The conflict of interest was undeniable. I genuinely believed anyone capable of basic critical thinking would at least pause to consider these glaring financial motives. But what followed was a masterclass in human stupidity.
My facebook post from 20 April 2020:

Not only was I branded a 'conspiracy theorist' for daring to question the billionaire who stood to make a fortune off the very vaccines he was shilling, but the brain-dead, logic-free bullshit vomited by the people around me was beyond pathetic. These barely literate morons couldn’t spell "Pfizer" without auto-correct, yet they mindlessly swallowed and repeated every lie the media and government force-fed them, branding anything that cracked their fragile reality as "conspiracy theory." Big Pharma’s rap sheet—fraud, deadly cover-ups, billions in fines—could fill libraries, yet these obedient sheep didn’t bother to open a single book or read a single study before screaming their ignorance, desperate to virtue-signal their obedience. Then, like spineless lab rats, they lined up for an experimental jab rushed to the market in months, too dumb to care that proper vaccine development takes a decade.
The pathetic part is that these idiots spend hours obsessing over reviews for their useless purchases like shoes or socks, but won’t spare 60 seconds to research the experimental cocktail being injected into their veins—or even glance at the FDA’s own damning safety reports. Those same obedient sheep would read every Yelp review for a fucking coffee shop but won't spend five minutes looking up Pfizer's criminal fraud settlements. They would demand absolute obedience to ‘The Science™’—while being unable to define mRNA, explain lipid nanoparticles, or justify why trials were still running as they queued up like cattle for their jab. If they had two brain cells to rub together or spent 30 minutes actually researching, they'd know, but no—they'd rather suck down the narrative like good little slaves, too dumb to question, too weak to think.
Worst of all, they became the system’s attack dogs—not just swallowing the poison, but forcing it down others’ throats. This wasn’t ignorance. It was betrayal. They mutated into medical brownshirts, destroying lives to virtue-signal their obedience—even as their own children’s hearts swelled with inflammation.
One conversation still haunts me to this day—a masterclass in wealth-worship delusion. A close friend, as a response to my facebook post, insisted that Gates’ assumed reading list magically awards him vaccine expertise, while dismissing his billion-dollar investments in the same products as ‘no conflict of interest.’ Worse, he argued that Gates’s $5–10 billion pandemic windfall was ‘deserved.’
This exchange crystallizes civilization’s intellectual surrender: reason discarded with religious fervor, replaced by blind faith in corporate propaganda.
The comment of a friend on my facebook post that still haunts me to this day:

Walking Away from the Herd
After a period of anger and disillusionment, I made a decision: I would no longer waste energy arguing with people who refused to think for themselves. If my circle couldn’t even ask basic questions—like why an untested medical intervention was being pushed with unprecedented urgency—then I needed a new community.
Fortunately, I already knew where to look. For three years, I had been involved in Bitcoin, a space where skepticism wasn’t just tolerated—it was demanded. Here, I’d met some of the most principled and independent thinkers I’d ever encountered. These were people who understood the corrupting influence of centralized power—whether in money, media, or politics—and who valued sovereignty, skepticism, and integrity. Instead of blind trust, bitcoiners practiced relentless verification. And instead of empty rhetoric, they lived by a simple creed: Don’t trust. Verify.
It wasn’t just a philosophy. It was a lifeline. So I chose my side and I walked away from the herd.
Finding My Tribe
Over the next four years, I immersed myself in Bitcoin conferences, meetups, and spaces where ideas were tested, not parroted. Here, I encountered extraordinary people: not only did they share my skepticism toward broken systems, but they challenged me to sharpen it.
No longer adrift in a sea of mindless conformity, I’d found a crew of thinkers who cut through the noise. They saw clearly what most ignored—that at the core of society’s collapse lay broken money, the silent tax on time, freedom, and truth itself. But unlike the complainers I’d left behind, these people built. They coded. They wrote. They risked careers and reputations to expose the rot. Some faced censorship; others, mockery. All understood the stakes.
These weren’t keyboard philosophers. They were modern-day Cassandras, warning of inflation’s theft, the Fed’s lies, and the coming dollar collapse—not for clout, but because they refused to kneel to a dying regime. And in their defiance, I found something rare: a tribe that didn’t just believe in a freer future. They were engineering it.
April 20, 2024: No more herd. No more lies. Only proof-of-work.
On April 20, 2024, exactly four years after my last Facebook post, the one that severed my ties to the herd for good—I stood in front of Warsaw’s iconic Palace of Culture and Science, surrounded by 400 bitcoiners who felt like family. We were there to celebrate Bitcoin’s fourth halving, but it was more than a protocol milestone. It was a reunion of sovereign individuals. Some faces I’d known since the early days; others, I’d met only hours before. We bonded instantly—heated debates, roaring laughter, zero filters on truths or on so called conspiracy theories.
As the countdown to the halving began, it hit me: This was the antithesis of the hollow world I’d left behind. No performative outrage, no coerced consensus—just a room of unyielding minds who’d traded the illusion of safety for the grit of truth. Four years prior, I’d been alone in my resistance. Now, I raised my glass among my people - those who had seen the system's lies and chosen freedom instead. Each had their own story of awakening, their own battles fought, but here we shared the same hard-won truth.
The energy wasn’t just electric. It was alive—the kind that emerges when free people build rather than beg. For the first time, I didn’t just belong. I was home. And in that moment, the halving’s ticking clock mirrored my own journey: cyclical, predictable in its scarcity, revolutionary in its consequences. Four years had burned away the old world. What remained was stronger.

No Regrets
Leaving the herd wasn’t a choice—it was evolution. My soul shouted: "I’d rather stand alone than kneel with the masses!". The Bitcoin community became more than family; they’re living proof that the world still produces warriors, not sheep. Here, among those who forge truth, I found something extinct elsewhere: hope that burns brighter with every halving, every block, every defiant mind that joins the fight.
Change doesn’t come from the crowd. It starts when one person stops applauding.
Today, I stand exactly where I always wanted to be—shoulder-to-shoulder with my true family: the rebels, the builders, the ungovernable. Together, we’re building the decentralized future.
-
 @ bf47c19e:c3d2573b
2025-05-11 18:24:28
@ bf47c19e:c3d2573b
2025-05-11 18:24:28Originalni tekst na dvadesetjedan.com.
Autor: Matt Corallo / Prevod na hrvatski: Davor
Bitcoineri, od programera Bitcoin Core-a preko dugogodišnjih entuzijasta Bitcoina do nedavnih pronalazača /r/Bitcoina, vole razgovarati o tome kako je decentralizacija Bitcoina njegova ultimativna značajka. Doduše, rijetko vidite da netko objašnjava zašto je decentralizacija važna. Zasigurno je to zanimljiva značajka iz perspektive računalne znanosti, no zašto bi potrošači, tvrtke ili investitori marili za to? Ova objava je pokušaj da se napiše zašto je decentralizacija temelj vrijednosti Bitcoina i što je još važnije, postavi buduće objave u kojima se govori o tome kada ona to nije.
Kada Bitcoineri govore o decentralizaciji Bitcoina, prva stvar koja se pojavljuje je često spominjani nedostatak inherentnog povjerenja u treću stranu. Dok je dobro postavljeno povjerenje preduvjet za učinkovit rad mnogih sustava, jednom kada se takvo povjerenje izgubi, sustavi mogu postati nevjerojatno krhki. Uzmimo, za primjer, povjerenje u američke banke prije uspostave FDIC-a (Federal Deposit Insurance Corporation). Dok je pristup bankovnim uslugama omogućio više pogodnosti i mnogim tvrtkama učinkovitije poslovanje, poznato je da su banke propadale, pritom upropaštavajući sa sobom sva sredstva klijenata. Dok je predstavljanje FDIC-a i sličnih programa decentraliziralo povjerenje u financijske institucije s jedne strane na dvije, transakcije u velikom dijelu svijeta ne nude takvu zaštitu. Čak i uz takve programe, pojedinci nisu univerzalno zaštićeni od gubitka preko granica i preko određene vrijednosti.
U novije vrijeme, propisi koji dopuštaju pojedinim državnim dužnosnicima jednostrano oduzimanje imovine postali su uobičajeni. Naročito u SAD-u, sada zloglasna “Operacija Choke Point” i programi oduzimanja civilne imovine, omogućili su službenicima za provođenje zakona i privatnim institucijama da zapljenjuju financijsku imovinu i uskraćuju financijske usluge uz malo ili nimalo nadzora. Uklanjanje provjerenih skrbnika i stvaranje sustava s likvidnom imovinom, koja se ne može zaplijeniti, ima potencijal pružiti pouzdanije financijske usluge mnogima koji inače ne bi mogli djelovati učinkovito ili uopće ne bi mogli djelovati. Ova mogućnost da se Bitcoin ne može zaplijeniti, omogućena je samo zbog nedostatka za centraliziranim povjerenjem. Centralizirani sustavi elektroničke gotovine i financijski sustavi su pokušali pružiti takvu pouzdanost, propisi i poslovna stvarnost su to gotovo univerzalno spriječili.
Svojstvo koje je jednako važno za sposobnost Bitcoina da pruža financijske usluge zviždačima, stranim disidentima i porno zvijezdama je njegov otpor cenzuri transakcija. Sposobnost trećih strana da zaplijene imovinu rezultira izravnim i čistim novčanim gubitkom, zamrzavanje imovine može imati sličan učinak. Kada pojedinac ili organizacija više nisu u mogućnosti obavljati transakcije za plaćanje roba i usluga, njihova financijska imovina brzo gubi vrijednost. Iako Bitcoin ima vrlo dobru priču o nemogućnosti zapljene (svaka strana u sustavu nameće nemogućnost bilo koga da potroši Bitcoin bez dodanog privatnog ključa), njegova priča o otporu cenzuri je malo utančanija.
U svijetu u kojem nijedan rudar Bitcoina nema više od 1% ukupne hash snage (ili nešto drugo što je jednako decentralizirano), trebalo bi biti lako pronaći rudara koji je ili anoniman i prihvaća sve transakcije ili je u nadležnosti koja ne pokušava cenzurirati vaše transakcije. Naravno, ovo nije svijet kakav danas imamo, a cenzura transakcija jedan je od većih razloga da se ozbiljno zabrinemo centralizacijom rudarenja (za pune čvorove). Ipak, mogućnost pojedinca da kupi hash snagu (u obliku lako dostupnog starog hardvera ili u obliku njegovog iznajmljivanja) za rudarenje svoje inače cenzurirane transakcije, opcija je sve dok je pravilo najdužeg lanca na snazi kod svih rudara. Iako je znatno skuplji nego što bi bio u istinski decentraliziranom Bitcoinu, to omogućuje Bitcoinu da zadrži neka od svojih anti-cenzuriranih svojstava.
Ako ste već dovoljno dugo u priči oko Bitcoina, možda ćete prepoznati gornja svojstva kao kritična za zamjenjivost. Zamjenjivost, kao ključno svojstvo svakog monetarnog instrumenta, odnosi se na ideju da vrijednost jedne jedinice treba biti ekvivalentna svakoj drugoj jedinici. Bez mogućnosti odmrzavanja/otpora cenzuri i nemogućnosti zapljene, Bitcoin (i svaki drugi monetarni sustav) počinje gubiti zamjenjivost. Trgovci i platni procesori više ne mogu razumno prihvaćati Bitcoin bez provjere niza crnih lista i mnogo truda kako bi bili sigurni da će moći potrošiti Bitcoin koji prihvaćaju. Ako povjerenje u zamjenjivost Bitcoina deformira, njegova bi korist mogla biti značajno deformirana.
Još jedno svojstvo koje proizlazi iz decentralizacije Bitcoina, je njegov otvoreni pristup. Ulagači iz Silicijske doline često ga nazivaju jednim od najzanimljivijih svojstava Bitcoina, a mnogi ga vole nazivati "bez dopuštenja". Sposobnost bilo koga, bilo gdje u svijetu, sa internetskom vezom, da prihvaća Bitcoin za robu i usluge i koristi Bitcoin za kupnju roba i usluga je vrlo uzbudljiva. Opet, ovo svojstvo ovisi o decentralizaciji Bitcoina. Iako postoje mnogi centralizirani pružatelji financijskih usluga, gdje mnogi od njih promoviraju svoju dostupnost bilo kome, sama njihova prisutnost kao centraliziranog tijela koje može proizvoljno uskratiti uslugu, čini ih podložnim budućim promjenama politike iz bilo kojeg razloga. PayPal je, na primjer, utemeljen na idealima univerzalnog pristupa elektroničkoj gotovini. Međutim, zbog svoje pozicije središnje vlasti, brzo je promijenio svoje politike, kako bi udovoljio pritiscima regulatora i politikama postojećeg financijskog sustava na koji se oslanjao. Ovih dana, PayPal je nadaleko poznat po zamrzavanju računa i oduzimanju imovine uz malo ili nimalo upozorenja. U osnovi, oslanjanje na centralizirane strane za usluge nije kompatibilno s univerzalnim otvorenim pristupom u financijskom svijetu.
Primijetit ćete da se sve gore navedene kritične značajke, one koje Bitcoin čine tako uzbudljivim za sve nas, centralizirani sistemi već neko vrijeme mogu implementirati. Zapravo to se radilo i prije, u učinkovitijim sustavima od Bitcoina. Naravno, nikada nisu potrajali, gubeći kritična svojstva nakon podešavanja kako bi se popravila ova ili ona stvar, implementirajući regulatorne sustave cenzure izravno u osnovne slojeve, ograničavajući pristup rastu dobiti i potpuno gašenje. Stvarno, decentralizacija u Bitcoinu sama po sebi nije značajka, već je umjesto toga jedini način za koji znamo da održimo značajke koje želimo u sustavima kojima upravljaju ljudi.
-
 @ 3ffac3a6:2d656657
2025-04-15 14:49:31
@ 3ffac3a6:2d656657
2025-04-15 14:49:31🏅 Como Criar um Badge Épico no Nostr com
nak+ badges.pageRequisitos:
- Ter o
nakinstalado (https://github.com/fiatjaf/nak) - Ter uma chave privada Nostr (
nsec...) - Acesso ao site https://badges.page
- Um relay ativo (ex:
wss://relay.primal.net)
🔧 Passo 1 — Criar o badge em badges.page
- Acesse o site https://badges.page
-
Clique em "New Badge" no canto superior direito
-
Preencha os campos:
- Nome (ex:
Teste Épico) - Descrição
-
Imagem e thumbnail
-
Após criar, você será redirecionado para a página do badge.
🔍 Passo 2 — Copiar o
naddrdo badgeNa barra de endereços, copie o identificador que aparece após
/a/— este é o naddr do seu badge.Exemplo:
nostr:naddr1qq94getnw3jj63tsd93k7q3q8lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vetsxpqqqp6njkq3sd0Copie:
naddr1qq94getnw3jj63tsd93k7q3q8lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vetsxpqqqp6njkq3sd0
🧠 Passo 3 — Decodificar o naddr com
nakAbra seu terminal (ou Cygwin no Windows) e rode:
bash nak decode naddr1qq94getnw3jj63tsd93k7q3q8lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vetsxpqqqp6njkq3sd0Você verá algo assim:
json { "pubkey": "3ffac3a6c859eaaa8cdddb2c7002a6e10b33efeb92d025b14ead6f8a2d656657", "kind": 30009, "identifier": "Teste-Epico" }Grave o campo
"identifier"— nesse caso: Teste-Epico
🛰️ Passo 4 — Consultar o evento no relay
Agora vamos pegar o evento do badge no relay:
bash nak req -d "Teste-Epico" wss://relay.primal.netVocê verá o conteúdo completo do evento do badge, algo assim:
json { "kind": 30009, "tags": [["d", "Teste-Epico"], ["name", "Teste Épico"], ...] }
💥 Passo 5 — Minerar o evento como "épico" (PoW 31)
Agora vem a mágica: minerar com proof-of-work (PoW 31) para que o badge seja classificado como épico!
bash nak req -d "Teste-Epico" wss://relay.primal.net | nak event --pow 31 --sec nsec1SEU_NSEC_AQUI wss://relay.primal.net wss://nos.lol wss://relay.damus.ioEsse comando: - Resgata o evento original - Gera um novo com PoW de dificuldade 31 - Assina com sua chave privada
nsec- E publica nos relays wss://relay.primal.net, wss://nos.lol e wss://relay.damus.io⚠️ Substitua
nsec1SEU_NSEC_AQUIpela sua chave privada Nostr.
✅ Resultado
Se tudo der certo, o badge será atualizado com um evento de PoW mais alto e aparecerá como "Epic" no site!
- Ter o
-
 @ aa8de34f:a6ffe696
2025-03-21 12:08:31
@ aa8de34f:a6ffe696
2025-03-21 12:08:3119. März 2025
🔐 1. SHA-256 is Quantum-Resistant
Bitcoin’s proof-of-work mechanism relies on SHA-256, a hashing algorithm. Even with a powerful quantum computer, SHA-256 remains secure because:
- Quantum computers excel at factoring large numbers (Shor’s Algorithm).
- However, SHA-256 is a one-way function, meaning there's no known quantum algorithm that can efficiently reverse it.
- Grover’s Algorithm (which theoretically speeds up brute force attacks) would still require 2¹²⁸ operations to break SHA-256 – far beyond practical reach.
++++++++++++++++++++++++++++++++++++++++++++++++++
🔑 2. Public Key Vulnerability – But Only If You Reuse Addresses
Bitcoin uses Elliptic Curve Digital Signature Algorithm (ECDSA) to generate keys.
- A quantum computer could use Shor’s Algorithm to break SECP256K1, the curve Bitcoin uses.
- If you never reuse addresses, it is an additional security element
- 🔑 1. Bitcoin Addresses Are NOT Public Keys
Many people assume a Bitcoin address is the public key—this is wrong.
- When you receive Bitcoin, it is sent to a hashed public key (the Bitcoin address).
- The actual public key is never exposed because it is the Bitcoin Adress who addresses the Public Key which never reveals the creation of a public key by a spend
- Bitcoin uses Pay-to-Public-Key-Hash (P2PKH) or newer methods like Pay-to-Witness-Public-Key-Hash (P2WPKH), which add extra layers of security.
🕵️♂️ 2.1 The Public Key Never Appears
- When you send Bitcoin, your wallet creates a digital signature.
- This signature uses the private key to prove ownership.
- The Bitcoin address is revealed and creates the Public Key
- The public key remains hidden inside the Bitcoin script and Merkle tree.
This means: ✔ The public key is never exposed. ✔ Quantum attackers have nothing to target, attacking a Bitcoin Address is a zero value game.
+++++++++++++++++++++++++++++++++++++++++++++++++
🔄 3. Bitcoin Can Upgrade
Even if quantum computers eventually become a real threat:
- Bitcoin developers can upgrade to quantum-safe cryptography (e.g., lattice-based cryptography or post-quantum signatures like Dilithium).
- Bitcoin’s decentralized nature ensures a network-wide soft fork or hard fork could transition to quantum-resistant keys.
++++++++++++++++++++++++++++++++++++++++++++++++++
⏳ 4. The 10-Minute Block Rule as a Security Feature
- Bitcoin’s network operates on a 10-minute block interval, meaning:Even if an attacker had immense computational power (like a quantum computer), they could only attempt an attack every 10 minutes.Unlike traditional encryption, where a hacker could continuously brute-force keys, Bitcoin’s system resets the challenge with every new block.This limits the window of opportunity for quantum attacks.
🎯 5. Quantum Attack Needs to Solve a Block in Real-Time
- A quantum attacker must solve the cryptographic puzzle (Proof of Work) in under 10 minutes.
- The problem? Any slight error changes the hash completely, meaning:If the quantum computer makes a mistake (even 0.0001% probability), the entire attack fails.Quantum decoherence (loss of qubit stability) makes error correction a massive challenge.The computational cost of recovering from an incorrect hash is still incredibly high.
⚡ 6. Network Resilience – Even if a Block Is Hacked
- Even if a quantum computer somehow solved a block instantly:The network would quickly recognize and reject invalid transactions.Other miners would continue mining under normal cryptographic rules.51% Attack? The attacker would need to consistently beat the entire Bitcoin network, which is not sustainable.
🔄 7. The Logarithmic Difficulty Adjustment Neutralizes Threats
- Bitcoin adjusts mining difficulty every 2016 blocks (\~2 weeks).
- If quantum miners appeared and suddenly started solving blocks too quickly, the difficulty would adjust upward, making attacks significantly harder.
- This self-correcting mechanism ensures that even quantum computers wouldn't easily overpower the network.
🔥 Final Verdict: Quantum Computers Are Too Slow for Bitcoin
✔ The 10-minute rule limits attack frequency – quantum computers can’t keep up.
✔ Any slight miscalculation ruins the attack, resetting all progress.
✔ Bitcoin’s difficulty adjustment would react, neutralizing quantum advantages.
Even if quantum computers reach their theoretical potential, Bitcoin’s game theory and design make it incredibly resistant. 🚀
-
 @ 26d4b5b2:96393e73
2025-05-11 22:24:38
@ 26d4b5b2:96393e73
2025-05-11 22:24:38https://app.doh.money http://localhost:3000 https://dohmoney-cyxe-cyxeio-cyxecyxeios-projects.vercel.app GET POST OPTIONS PUT DELETE Content-Type Ocp-Apim-Subscription-Key Authorization Accept X-Requested-With X-Verified-By Content-Length Request-Context Date @(context.Request.Headers.GetValueOrDefault("Ocp-Apim-Subscription-Key", "50922ff015c14a84a092b4764dc6dddf")) @(context.Request.Headers.GetValueOrDefault("Origin", "https://app.doh.money")) @(context.Request.Headers.GetValueOrDefault("Origin", "http://localhost:3000")) GET, POST, OPTIONS, PUT, DELETE Content-Type, Ocp-Apim-Subscription-Key, Authorization, Accept, X-Requested-With,X-Verified-By Content-Length, Request-Context, Date @(context.Request.Headers.GetValueOrDefault("Origin", "https://app.doh.money")) @(context.Request.Headers.GetValueOrDefault("Origin", "http://localhost:3000")) GET, POST, OPTIONS, PUT, DELETE Content-Type, Ocp-Apim-Subscription-Key, Authorization, Accept, X-Requested-With, X-Verified-By Content-Length, Request-Context, Date -
 @ bf47c19e:c3d2573b
2025-05-11 18:23:13
@ bf47c19e:c3d2573b
2025-05-11 18:23:1305.12.2024 / Autor: Katarina Plantak
Vrijednost Bitcoina po prvi put je premašila 100.000 dolara. Ova kriptovaluta svoj masovni rast može na neki način zahvaliti reizboru Donalda Trumpa za američkog predsjednika. On je najavio blaži regulatorni pristup kripto industriji.
Što je Bitcoin?
Bitcoin (BTC) je kriptovaluta (virtualna valuta) dizajnirana da djeluje kao novac i oblik plaćanja izvan kontrole bilo koje osobe, grupe ili entiteta. Time nema potrebe za sudjelovanjem pouzdane treće strane npr. kovnice novca ili banke u financijskim transakcijama. Osoba ili grupa pod pseudonimom Satoshi Nakamoto 31. listopada 2008. objavila je tehnički dokument pod nazivom "Bitcoin: Peer-to-Peer Electronic Cash System". Taj je dokument distribuiran na kriptografsku mailing listu, samo mjesec dana nakon što je investicijska banka Lehman Brothers podnijela zahtjev za najveći bankrot u povijesti SAD-a, a vlada odobrila financijsku pomoć od 700 milijardi dolara.
Nekoliko mjeseci kasnije, 3. siječnja 2009., Bitcoin mreža pokrenula se, uvodeći novi sustav decentralizirane digitalne valute bez središnjeg posrednika.
Tko su osnivači Bitcoina?
Bitcoin je rezultat desetljeća razvoja kriptografije i ideja Cypherpunka iz 1970-ih, s projektima poput B-money, Bit Gold, eCash i HashCash.
Godine 2006., osoba ili grupa pod pseudonimom Satoshi Nakamoto započela je rad na Bitcoinu. Iako su kriptografi poput Hal Finneya, Nicka Szaba, Weija Daija i Adama Backa povezivani sa Satoshijem, svi su to negirali.
Satoshi je surađivao s programerima do 2010., kada je predao kontrolu nad izvornim kodom i 2011. nestao iz javnosti. Danas stotine programera razvijaju Bitcoin, koji ima zajednicu od milijun korisnika.
Kako funkcionira Bitcoin?
Bitcoin se može brzo i sigurno prenijeti na svakoga s Bitcoin adresom poput računa bilo gdje u svijetu, bez potrebe za dopuštenjem ili plaćanjem nepotrebnih naknada. BTC je jedinica valute u Bitcoin sustavu za koju postoji ograničena količina od 21 milijun. Svaki je Bitcoin djeljiv na 100 milijuna "satoshis" ili "sats" – najmanja jedinica Bitcoina, poput centa u dolaru. Bitcoini djeluju kao elektronički novac, omogućujući vam da izvršite plaćanje s univerzalnom valutom bilo gdje. Nalazi se u tzv. novčanicima u digitalnoj verziji. On funkcionira slično kao bankovni račun. Transakcije su moguće zahvaljujući peer-to-peer mreži. Osigurane su sustavom kriptografije javnog i privatnog ključa, objašnjava Kriptomat.
Bitcoin koristi kriptografiju javnog i privatnog ključa za sigurne transakcije. Javna adresa, izvedena iz "hasha" javnog ključa, koristi se za primanje sredstava. Privatni ključ služi kao digitalni potpis odnosno svojevrsna lozinka za autorizaciju transakcija i omogućava pristup sredstvima, pa ga treba čuvati u tajnosti.
Korisnik pokreće transakciju unosom javne adrese primatelja u svoj novčanik. Novčanik koristi privatni ključ za stvaranje digitalnog potpisa, čime se transakcija ovjerava i šalje na Bitcoin mrežu. Transakcija prvo ulazi u "mempool", gdje čeka potvrdu. Svakih desetak minuta, transakcije se grupiraju u blokove, koji se dodaju na blockchain, stvarajući neprekinuti lanac sigurnih zapisa.
Sigurnost sustava je toliko snažna da bi hakiranje jedne adrese trajalo milijardama godina.
Blockchain
Bitcoin je revolucionarno riješio problem dvostruke potrošnje, omogućujući prijenos sredstava izravno između korisnika bez posrednika. Zamislite mrežu stranaca, gdje svaki vodi vlastitu knjigu računa. Kada netko prenese 1 BTC, svi zapisuju transakciju i uspoređuju bilješke. Ako se sve podudaraju, transakcija se potvrđuje. Ako netko pokuša prevariti, njegova bilješka se odbacuje.
Ovaj sustav knjiga računa, distribuiran na globalnoj mreži, čini osnovu Bitcoin blockchaina. Svaki čvor ima identičnu kopiju koja javno i pseudonimno bilježi sve transakcije, osiguravajući točnost i sigurnost bez potrebe za skupim posrednicima.
Zašto je Bitcoin jedinstven i što mu daje vrijednost?
Bitcoin je revolucionirao digitalni novac stvaranjem decentraliziranog, sigurnog i otpornog sustava bez potrebe za posrednicima. Njegov kod omogućuje daljnje inovacije, a povremeno dolazi do "račvanja" koje stvara nove kriptovalute temeljene na Bitcoinu, iako one nikada ne mogu biti isti Bitcoin.
Njegova ključna snaga leži u decentralizaciji – nema središnje figure niti točke neuspjeha. Bitcoin se pokazao kao otporan na izazove, uključujući državne zabrane i snažna račvanja, što dodatno učvršćuje njegovu dugovječnost prema Lindyjevom efektu. Mrežni učinak potiče sve više korisnika da ga prihvate kao sredstvo za pohranu vrijednosti i razmjenu.
Njegova ograničena ponuda od 21 milijun BTC-a stvara oskudicu, čime se suprotstavlja inflacijskim valutama. Bitcoin je zamjenjiv, djeljiv na 100 milijuna dijelova, izdržljiv i prenosiv, što ga čini praktičnijim od zlata. S rastućim prihvaćanjem od strane tvrtki diljem svijeta, njegova vrijednost i korisnost nastavljaju rasti.
Blokovi, rudarenje i nagrade
Prvi Bitcoinblock izrudiran je 3. siječnja 2009. godine. Nazvan je Blok 0. Rudarenje Bitcoina je utrka između rudara za raspršivanje specifičnih vrijednosti i drugih informacija o bloku kako bi se pronašlo rješenje za problem raspršivanja i dodalo blok u blockchain. Pobjednički rudar nagrađen je Bitcoinima. Bitcoin nagrade se prepolovljuju svakih 210.000 blokova. Na primjer, nagrada za blok bila je 50 novih bitcoina u 2009. godini, a 11. svibnja 2020. kad se dogodilo treće prepolovljenje nagrada za svaki blok smanjena je na 6.25 bitcoina. Četvrto prepolovljenje dogodilo se u travnju 2024. i smanjilo je nagradu na 3.125 Bitcoina. Sljedeće prepolovljavanje trebalo bi se dogoditi sredinom 2028. i smanjiti nagradu na 1.5625 BTC.
Do 2140. godine, nakon 32. prepolovljenja, nagrada za rudarenje Bitcoina smanjit će se na nulu, dosegnuvši ukupnu ponudu od 21 milijun BTC-a. Tada će se rudari oslanjati isključivo na naknade za transakcije kako bi pokrili svoje troškove.
Svako prepolovljenje smanjuje količinu novih BTC-a, što povijesno dovodi do porasta cijene zbog smanjene ponude i povećane potražnje. Iako će se učinak budućih prepolovljenja možda smanjivati zbog sve manjih količina nove ponude, do sada su ta prepolovljenja bila ključni pokretači triju glavnih tržišnih ciklusa Bitcoina.
-
 @ e3ba5e1a:5e433365
2025-04-15 11:03:15
@ e3ba5e1a:5e433365
2025-04-15 11:03:15Prelude
I wrote this post differently than any of my others. It started with a discussion with AI on an OPSec-inspired review of separation of powers, and evolved into quite an exciting debate! I asked Grok to write up a summary in my overall writing style, which it got pretty well. I've decided to post it exactly as-is. Ultimately, I think there are two solid ideas driving my stance here:
- Perfect is the enemy of the good
- Failure is the crucible of success
Beyond that, just some hard-core belief in freedom, separation of powers, and operating from self-interest.
Intro
Alright, buckle up. I’ve been chewing on this idea for a while, and it’s time to spit it out. Let’s look at the U.S. government like I’d look at a codebase under a cybersecurity audit—OPSEC style, no fluff. Forget the endless debates about what politicians should do. That’s noise. I want to talk about what they can do, the raw powers baked into the system, and why we should stop pretending those powers are sacred. If there’s a hole, either patch it or exploit it. No half-measures. And yeah, I’m okay if the whole thing crashes a bit—failure’s a feature, not a bug.
The Filibuster: A Security Rule with No Teeth
You ever see a firewall rule that’s more theater than protection? That’s the Senate filibuster. Everyone acts like it’s this untouchable guardian of democracy, but here’s the deal: a simple majority can torch it any day. It’s not a law; it’s a Senate preference, like choosing tabs over spaces. When people call killing it the “nuclear option,” I roll my eyes. Nuclear? It’s a button labeled “press me.” If a party wants it gone, they’ll do it. So why the dance?
I say stop playing games. Get rid of the filibuster. If you’re one of those folks who thinks it’s the only thing saving us from tyranny, fine—push for a constitutional amendment to lock it in. That’s a real patch, not a Post-it note. Until then, it’s just a vulnerability begging to be exploited. Every time a party threatens to nuke it, they’re admitting it’s not essential. So let’s stop pretending and move on.
Supreme Court Packing: Because Nine’s Just a Number
Here’s another fun one: the Supreme Court. Nine justices, right? Sounds official. Except it’s not. The Constitution doesn’t say nine—it’s silent on the number. Congress could pass a law tomorrow to make it 15, 20, or 42 (hitchhiker’s reference, anyone?). Packing the court is always on the table, and both sides know it. It’s like a root exploit just sitting there, waiting for someone to log in.
So why not call the bluff? If you’re in power—say, Trump’s back in the game—say, “I’m packing the court unless we amend the Constitution to fix it at nine.” Force the issue. No more shadowboxing. And honestly? The court’s got way too much power anyway. It’s not supposed to be a super-legislature, but here we are, with justices’ ideologies driving the bus. That’s a bug, not a feature. If the court weren’t such a kingmaker, packing it wouldn’t even matter. Maybe we should be talking about clipping its wings instead of just its size.
The Executive Should Go Full Klingon
Let’s talk presidents. I’m not saying they should wear Klingon armor and start shouting “Qapla’!”—though, let’s be real, that’d be awesome. I’m saying the executive should use every scrap of power the Constitution hands them. Enforce the laws you agree with, sideline the ones you don’t. If Congress doesn’t like it, they’ve got tools: pass new laws, override vetoes, or—here’s the big one—cut the budget. That’s not chaos; that’s the system working as designed.
Right now, the real problem isn’t the president overreaching; it’s the bureaucracy. It’s like a daemon running in the background, eating CPU and ignoring the user. The president’s supposed to be the one steering, but the administrative state’s got its own agenda. Let the executive flex, push the limits, and force Congress to check it. Norms? Pfft. The Constitution’s the spec sheet—stick to it.
Let the System Crash
Here’s where I get a little spicy: I’m totally fine if the government grinds to a halt. Deadlock isn’t a disaster; it’s a feature. If the branches can’t agree, let the president veto, let Congress starve the budget, let enforcement stall. Don’t tell me about “essential services.” Nothing’s so critical it can’t take a breather. Shutdowns force everyone to the table—debate, compromise, or expose who’s dropping the ball. If the public loses trust? Good. They’ll vote out the clowns or live with the circus they elected.
Think of it like a server crash. Sometimes you need a hard reboot to clear the cruft. If voters keep picking the same bad admins, well, the country gets what it deserves. Failure’s the best teacher—way better than limping along on autopilot.
States Are the Real MVPs
If the feds fumble, states step up. Right now, states act like junior devs waiting for the lead engineer to sign off. Why? Federal money. It’s a leash, and it’s tight. Cut that cash, and states will remember they’re autonomous. Some will shine, others will tank—looking at you, California. And I’m okay with that. Let people flee to better-run states. No bailouts, no excuses. States are like competing startups: the good ones thrive, the bad ones pivot or die.
Could it get uneven? Sure. Some states might turn into sci-fi utopias while others look like a post-apocalyptic vidya game. That’s the point—competition sorts it out. Citizens can move, markets adjust, and failure’s a signal to fix your act.
Chaos Isn’t the Enemy
Yeah, this sounds messy. States ignoring federal law, external threats poking at our seams, maybe even a constitutional crisis. I’m not scared. The Supreme Court’s there to referee interstate fights, and Congress sets the rules for state-to-state play. But if it all falls apart? Still cool. States can sort it without a babysitter—it’ll be ugly, but freedom’s worth it. External enemies? They’ll either unify us or break us. If we can’t rally, we don’t deserve the win.
Centralizing power to avoid this is like rewriting your app in a single thread to prevent race conditions—sure, it’s simpler, but you’re begging for a deadlock. Decentralized chaos lets states experiment, lets people escape, lets markets breathe. States competing to cut regulations to attract businesses? That’s a race to the bottom for red tape, but a race to the top for innovation—workers might gripe, but they’ll push back, and the tension’s healthy. Bring it—let the cage match play out. The Constitution’s checks are enough if we stop coddling the system.
Why This Matters
I’m not pitching a utopia. I’m pitching a stress test. The U.S. isn’t a fragile porcelain doll; it’s a rugged piece of hardware built to take some hits. Let it fail a little—filibuster, court, feds, whatever. Patch the holes with amendments if you want, or lean into the grind. Either way, stop fearing the crash. It’s how we debug the republic.
So, what’s your take? Ready to let the system rumble, or got a better way to secure the code? Hit me up—I’m all ears.
-
 @ bf47c19e:c3d2573b
2025-05-11 18:22:40
@ bf47c19e:c3d2573b
2025-05-11 18:22:40Originalni tekst na antenam.net
31.10.2024 / Autor: Ana Nives Radović
Godišnjica objavljivanja revolucionarnog dokumenta nije samo podsjetnik na nastanak Bitcoina, već i na značajnu promjenu koju je donio u načinu na koji razmišljamo o novcu i ekonomskom suverenitetu. Njegov značaj premašuje ideju o zaradi na promjeni njegove vrijednosti, jer otvara vrata širem razumijevanju digitalne imovine i decentralizovanih finansija koje inspirišu moderno bankarstvo i platne sisteme da se razvijaju u drugačijem smjeru, povećavajući svijest o sigurnosti i dostupnosti.
Šesnaest je godina od objavljivanja dokumenta naslovljenog kao "Bitcoin: A Peer-to-Peer Electronic Cash System", poznatog i kao „biijeli papir“ (white paper) u kojem su izloženi koncept i svrha novog sistema digitalne valute – sistema koji bi funkcionisao nezavisno od bilo koje vlade ili finansijske institucije. Bijeli papir, kojeg je 31. oktobra 2008. objavio pojedinac ili tim ljudi pod imenom Satoši Nakamoto ponudio je smjelo rješenje za sve veći problem – kontrolu valute centralnih banaka i sve veće poteškoće u prenošenju vrijednosti preko interneta bez posrednika. Ovaj trenutak označio je nastanak Bitcoina, revolucionarne digitalne valute i prve kriptovalute na svijetu koja je kasnije lansirana 3. januara 2009. godine.
Bitcoin je nastao u vrijeme finansijske krize 2008. godine, u periodu kada je povjerenje u tradicionalne finansijske sisteme bilo na izuzetno niskom nivou. Ljudi su počeli da se pitaju da li postoji način za upravljanje novcem koji ne zavisi od banaka, koje, kao što su tadašnji događaji pokazali, mogu propasti ili djelovati na načine koji nijesu u najboljem interesu javnosti. Nakamotova inovacija, Bitcoin, bila je zamišljena kao sistem u kojem korisnici mogu direktno slati i primati novac, zaobilazeći potrebu za bankama. U tom procesu, Nakamoto je svijetu predstavio novu tehnologiju kojoj je kasnije američki naučnik i programer Harold Fini dao naziv blockchain – decentralizovan i otporan na manipulacije način za evidentiranje transakcija.
Šta je Bitcoin?
Bitcoin je vrsta digitalne valute koja omogućava ljudima da direktno jedni drugima šalju i primaju vrijednost putem interneta. Za razliku od tradicionalnih valuta, kao što je euro ili dolar, koje kontrolišu vlade i banke, Bitcoin funkcioniše bez centralne vlasti. To znači da nema nikoga ko je zadužen za njega i nema banke koja odlučuje kako se može koristiti. Umjesto toga, Bitcoin se oslanja na veliku mrežu računara širom svijeta koja ga održava i bilježi njegove transakcije. Ova mreža je poznata kao „Bitcoin mreža“.
Kako Bitcoin funkcioniše?
U suštini, Bitcoin funkcioniše kao „decentralizovana digitalna valuta“. Kada kažemo decentralizovana, mislimo da nijedna osoba, kompanija ili vlada ne kontroliše Bitcoin. Umjesto toga, svaka transakcija se bilježi na zajedničkoj knjizi, nazvanoj blockchain, koju održava mreža računara širom svijeta. Svaki put kada neko pošalje ili primi Bitcoin, transakcija se grupiše sa drugima i dodaje u ovaj lanac blokova. Budući da je ovaj lanac kopiran i dijeljen među brojnim računarima, gotovo je neizvodljivo izmijeniti ili hakovati ga, čime se osigurava da Bitcoin transakcije budu bezbjedne i pouzdane.
Još jedan interesantan aspekt je da Bitcoin ima ograničenu ponudu. Kreiran je samo 21 milion bitcoina, što ga čini rijetkom imovinom i sprečava inflaciju na način na koji to može biti slučaj sa tradicionalnim valutama koje se „doštampavaju“. Bitcoin transakcije su omogućene kroz skup kriptografskih pravila, koja ljudima omogućavaju da potvrde svaku transakciju kao legitimnu bez potrebe da vjeruju trećoj strani. Ovaj skup pravila je poznat kao kriptografija, zbog čega se Bitcoin naziva kriptovalutom – prvom koja je ikada stvorena i jedinom koja u potpunosti ima sve karakteristike onoga što je istinska ideja i svrha postojanja kriptovaluta.
Razumijevanje finansijske revolucije Bitcoina
Bitcoin, predstavljen 2008. godine, privukao je globalnu pažnju kao decentralizovana digitalna valuta koja funkcioniše nezavisno od banaka i vlada, ali pored svoje peer-to-peer arhitekture i decentralizovane infrastrukture, on ima jedinstvenu finansijsku karakteristiku – inherentno je deflatoran. Za razliku od fiat valuta poput dolara ili eura, koje centralne banke mogu štampati kada procijene da je to potrebno, ponuda Bitcoina je ograničena, fiksirana i ne povećava se. Ova deflatorna osobina navela je mnoge da ga vide kao revolucionarni finansijski instrument, „digitalno zlato“ koje bi moglo da preoblikuje koncepte vrijednosti, očuvanja bogatstva i monetarne politike.
Fiksna ponuda – limit od 21 miliona
Najkarakterističnija odlika Bitcoina je njegova ograničena ponuda. Kada je Satoši Nakamoto kreirao Bitcoin, postavio je ograničenje na ukupan broj bitcoina koji će ikada postojati – 21 milion. Ovo ograničenje se oštro razlikuje od tradicionalnih fiat valuta, gdje centralne banke mogu povećavati ponudu novca štampanjem dodatne količine. Postavljanjem ovog ograničenja, Nakamoto je osigurao da Bitcoin postane sve rjeđi vremenom, karakteristika koja je dizajnirana za očuvanje vrijednosti kako potražnja raste.
U tradicionalnim finansijama, valute mogu izgubiti vrijednost kada se previše štampaju, što se može vidjeti u slučajevima inflacije. Bitcoinov dizajn, međutim, znači da, kada se posljednji Bitcoin izrudari (što se predviđa oko 2140. godine), novi novčići neće ulaziti u cirkulaciju, što ga efektivno čini prvom deflatornom valutom u velikom obimu.
Mehanizam smanjenje ponude tokom vremena
Oskudica Bitcoina dodatno se pojačava procesom nazvanim „halving“ (prepolovljenje), koji smanjuje stopu stvaranja novih bitcoina. Približno svake četiri godine nagrada koju „rudari“ dobijaju za dodavanje novih blokova u blockchain se prepolovi. Ovaj mehanizam smanjuje mogućnost inflacije Bitcoina tokom vremena, stvarajući predvidivo, postepeno smanjenje ponude.
U početku su rudari dobijali 50 bitcoina po bloku. Nakon prvog halvinga 2012. godine, nagrada je pala na 25, a do 2020. smanjila se na 6,25 bitcoina po bloku. Ovaj proces halvinga će se nastaviti sve do približno 2140. godine, kada će svih 21 milion bitcoina biti u cirkulaciji, a rudari će biti podstaknuti isključivo transakcionim naknadama, umjesto novim novčićima. Halving ima dva osnovna učinka – usporava rast ponude Bitcoina i stvara predvidivu oskudicu koja može podstaći tražnju, jer učesnici na tržištu znaju da će sa svakim ciklusom biti sve manje dostupnih bitcoina.
Zašto je Bitcoin važan?
Većina tradicionalnih valuta je inflaciona po dizajnu. Centralne banke teže kontrolisanoj stopi inflacije, često oko 2%, kako bi podstakle ekonomski rast, ohrabrile potrošnju i pružile fleksibilnost u odgovoru na ekonomske krize. Međutim, ova inflacija može potkopati kupovnu moć fiat valuta vremenom, što je zabrinjavajuće tokom perioda prekomjernog štampanja novca, kao što su mjere i programi kvantitativnog popuštanja viđene posljednjih godina.
Bitcoinov deflatorni dizajn je revolucionaran u ovom kontekstu jer nudi potencijalnu zaštitu od inflacije. Sa fiksnom ponudom, Bitcoin može da dobija na vrijednosti tokom vremena, posebno ako potražnja raste jer postaje rjeđi. Za mnoge, deflatorni model Bitcoina čini ga privlačnim sredstvom za očuvanje bogatstva na način koji tradicionalne valute i imovina ne mogu da ponude.
Pored toga, ovaj model izazvao je promjenu čitave filozofije u načinu na koji ljudi razmišljaju o novcu, investiranju i štednji. Dok tradicionalne finansije podstiču potrošnju i investicije kroz inflaciju, deflatorna priroda Bitcoina može podstaći štednju, jer bi njegova vrijednost mogla da raste u budućnosti. Ovaj kvalitet „čuvara vrijednosti“ naveo je mnoge da Bitcoinu daju naziv „digitalno zlato“.
Ekonomija oskudice – ono što Bitcoinu daje vrijednost
U ekonomiji, oskudica obično povećava vrijednost, jer tražnja za ograničenim resursom može povećati njegovu cijenu. Zlato je, na primjer, dugo bilo čuvar vrijednosti zbog svoje oskudice i poteškoća u vađenju. Bitcoin odražava ovaj koncept u digitalnom svijetu. Inherentno je rijedak zbog ograničenja od 21 milion, i, kao zlato, zahtijeva trud (kroz digitalno rudarenje) da bi ušao u cirkulaciju.
Pored toga, oskudica Bitcoina postaje sve izraženija kako raste interesovanje institucija i pojedinaca. Mnogi investitori privučeni su Bitcoinom kao dugoročnom imovinom upravo zbog ove fiksne ponude, oslanjajući se na to da će rastuća tražnja naspram ograničene ponude povećati njegovu vrijednost tokom vremena. Ova privlačnost je pojačana u regionima sa brzom inflacijom ili ekonomskom nestabilnošću, gdje rizik od devalvacije čini Bitcoin privlačnom alternativom za očuvanje bogatstva.
Bitcoin kao globalni čuvar vrijednosti
Osim što je sredstvo razmjene, deflatorna priroda Bitcoina pozicionira ga kao potencijalni globalni čuvar vrijednosti. Zlato je istorijski imalo ovu ulogu, jer su ga koristili pojedinci, institucije i vlade kao zaštitu od ekonomske nestabilnosti i inflacije. Bitcoin postaje moderni pandan tome, posebno privlačan mlađim generacijama i investitorima sklonim tehnologiji, koji ga vide kao superiornu alternativu.
Deflatorni dizajn takođe omogućava Bitcoinu da prelazi međunarodne granice i nadilazi lokalne ekonomske uslove. U zemljama koje prolaze kroz valutne krize, Bitcoin nudi alternativu koja je bez granica i nezavisna od politika centralne banke. Ova sposobnost da djeluje kao čuvar vrijednosti posebno je značajna na tržištima i ekonomijama u razvoju, gdje je valutna nestabilnost učestalija.
Može li oskudica Bitcoina predstavljati rizik?
Iako deflatorni model Bitcoina ima svoje prednosti, nije bez kritika. Jedna od zabrinutosti je da ekstremna deflacija može obeshrabriti potrošnju. U sistemu gdje vrijednost valute raste tokom vremena, ljudi mogu preferirati štednju umjesto potrošnje ili investiranja, što može dovesti do smanjenja ekonomske aktivnosti. Ekonomisti brinu da bi, ako Bitcoin postane široko prihvaćena valuta, njegova deflatorna priroda mogla ugroziti ekonomski rast podsticanjem „gomilanja“ umesto cirkulacije.
Još jedna kritika se odnosi na fiksnu ponudu Bitcoina u ekonomiji koja stalno raste. Tradicionalne valute su inflatorne kako bi pratile rast populacije, ekonomije i produktivnosti. Sa ograničenom ponudom, Bitcoin ne može da raste u skladu sa ekonomskim razvojem, što bi u teoriji moglo izazvati probleme sa likvidnošću u ekonomiji zasnovanoj na Bitcoinu. Ipak, kako ideja nije da Bitcoin bude jedino sredstvo plaćanja, strah od takvog scenarija je neutemeljen, budući da ekosistem u kojem funkcioniše koegzistira sa nizom drugih platnih sistemna koji su na raspolaganju širom svijeta.
Eliminiše problem dvostrukog trošenja
U svijetu novca postoji veliki problem koji se naziva „dvostruko trošenje“. Zamislite da možete potrošiti iste eure dvaput – platite jedan proizvod ili uslugu, a zatim, nekako, uspijete da ga ponovo potrošite na nešto drugo. U fizičkom svijetu ovo nije problem, ali u računovodstvenom jeste. Ako kao fizičku valutu u gotovini platite nešto, ta količina novca odlazi iz vašeg novčanika, ali u bankovnim transakcijama stvari funkcionišu drugačije.
Da bi se osiguralo da Bitcoin ne može biti kopiran ili potrošen dvaput, koristi se tehnologija zvana blockchain. Nakamotov Bijeli papir još nije pomenuo taj izraz, jer mu je naziv dat nekoliko dana kasnije, no umjesto toga, opisao je koncept „lanca blokova“, postavljajući sistem za evidentiranje transakcija u blokovima koji su međusobno povezani. Ovaj koncept je kasnije postao poznat kao blockchain, termin koji je nastao nakon izdavanja Bitcoina dok su ljudi pokušavali da imenuju osnovnu tehnologiju. Fokus Bijelog papira bio je na tome kako Bitcoin može bezbjedno pratiti i potvrđivati transakcije, koristeći ovaj povezani lanac blokova kao neku vrstu digitalne knjige.
Pristup iz Bijelog papira uveo je revolucionarnu ideju – zajedničku, otpornu na manipulacije evidenciju koja se nije oslanjala na centralnu vlast za ažuriranje ili verifikaciju. Ovaj sistem povezanih blokova (ono što sada nazivamo blockchain) postao je osnova Bitcoina i, kasnije, bezbroj drugih primjena u finansijama, tehnologiji i brojnim drugim oblastima.
Ova baza je poput ogromne digitalne knjige, ili evidencije, u kojoj je svaka Bitcoin transakcija (prenosa novca od jednog do drugog korisnika) zabilježena. Ono što ovu digitalnu evidenciju čini posebnom jeste to što nije smještena na jednom mjestu, niti je pod kontrolom jedne osobe ili institucije – ona je u potpunosti decentralizovana, što znači da se kopije ove knjige čuvaju na hiljadama računara širom svijeta, a svi oni moraju da se saglase oko toga koje transakcije su validne.
Svaki put kada neko pošalje Bitcoin drugoj osobi, ova transakcija se dodaje u blockchain. Da bi se dodala, grupa računara (nazvana „rudari“) mora da verifikuje da je ova transakcija stvarna, što znači da Bitcoin koji se troši već nije korišćen drugdje. Ovi rudari rade zajedno, koristeći složene matematičke operacije, kako bi potvrdili transakcije. Kada se verifikuje, transakcija se dodaje u blockchain, a cijela mreža se ažurira kako bi prepoznala ovu transakciju kao legitimnu. Ovaj proces osigurava da nijedan Bitcoin ne može biti potrošen dvaput, rješavajući problem dvostrukog trošenja.
Peer-to-Peer transakcije bez posrednika
Još jedan veliki razlog zašto je Bitcoin važan je taj što omogućava ljudima da šalju novac direktno jedni drugima bez potrebe za posrednikom. Recimo da želite da pošaljete novac prijatelju koji živi u drugoj zemlji. Obično biste otišli u svoju banku, koja bi se povezala s drugom bankom u toj zemlji, što može trajati danima i uključivati različite naknade.
Međutim, Bitcoin je omogućio da se direktno pošalju sredstva, bez obzira na to gdje se nalazite u svijetu. Pošto je u pitanju peer-to-peer (P2P) način razmjene, nema potrebe za posrednikom da upravlja transakcijom. To može učiniti transakcije bržim i ponekad jeftinijim, posebno kada se sredstva šalju međunarodno. Ova P2P struktura je jedan od glavnih razloga zbog kojih ljudi se na ovaj oblik imovine gleda kao na alternativu složenim transakcijama, posebno važnim za društva i sredine u kojima je dostupnost finansijskih usluga niska.
Transparentnost i sigurnost
U svijetu tradicionalnog bankarstva, ljudi se oslanjaju na banke koje drže novac sigurnim i omogućavaju da transakcije budu poštene i sigurne. Međutim, s Bitcoinom, povjerenje nije smešteno u centralnu banku ili kompaniju, već u samu Bitcoin mrežu, koju održavaju svi računari koji prate blockchain. Pošto je blockchain javan i može ga provjeriti bilo ko, on je veoma transparentan. Svaka transakcija koja je ikada obavljena Bitcoinom zabilježena je u ovoj javnoj knjizi, tako da ako neko pokuša da prevari sistem, to bi bilo očigledno svima.
Transparentnost Bitcoina takođe ga čini veoma sigurnim. Pošto svi u mreži imaju kopiju blockchaina, bilo bi gotovo nemoguće da jedna osoba ili čak grupa ljudi izmijeni ili preuzme kontrolu nad njim. Da biste promijenili blockchain, morali biste kontrolisati više od polovine svih računara širom svijeta u Bitcoin mreži, što je izuzetno teško. Ovaj nivo sigurnosti, u kombinaciji s transparentnošću, pomaže ljudima da se osjećaju sigurno koristeći Bitcoin.
Značaj za razvoj finansija
Tokom godina, Bitcoin je postao više od eksperimenta u digitalnom novcu. Inspirisao je hiljade drugih kreatora latnih rješenja i pokrenuo važne razgovore o budućnosti novca, povjerenja i tehnologije. Kako sve više ljudi počinje da preispituje kako tradicionalne banke funkcionišu i traži nove načine za upravljanje svojim finansijama, Bitcoin ostaje snažna opcija ne samo u smislu alternative, već mogućnosti povezivanja njegove funkcionalnosti sa onim što već postoji u finansijskoj tehnologiji. Njegov značaj je u tome što predstavlja potpuno novi način razmišljanja o novcu i njegovom korišćenju i što rješava neke od ključnih problema koji su karakteristični finansijske sisteme.
Ideja decentralizacije
U mnogim sistemima koje danas koristimo postoji centralna vlast – banka, vlada ili kompanija – koja ima kontrolu i koja donosi pravila, odlučuje ko ima pristup i odobrava aktivnosti, što je prilično spor i skup proces u cjelini. Koncept Bitcoina je drugačiji jer je decentralizovan, a to znači da ne postoji jedna osoba, banka ili organizacija koja donosi odluke, već je to prepušteno mreži koju čine milioni korisničkih uređaja na mreži koji održavaju sistem u funkciji.
Pored toga, decentralizacija onemogućava cenzurisanje, jer niko ne može da interveniše i blokira nečiji pristup ili transakcije. To čini sistem demokratskijim, omogućavajući ljudima širom svijeta da se pridruže bez traženja dozvole.
Kriptografski dokazi – vjerovanje u matematiku, a ne u ljude
Kada nešto kupite koristeći Bitcoin, ne morate se oslanjati na posrednika da verifikuje vašu transakciju. Umjesto toga, Bitcoin koristi nešto što se naziva „kriptografskim dokazom. Kriptografski dokazi su poput digitalnog ključa i brave koji čuvaju informacije sigurnima, jer se oslanjaju na složenu matematiku koja osigurava da se samo validne transakcije dodaju u blockchain, onemogućavajući falsifikovanje ili prevaru.
Kriptografski dokazi funkcionišu tako što kreiraju heš (hash) – dug i jedinstven broj, za svaki blok transakcija. Svaki heš je povezan s prethodnim, što pomaže u obezbjeđivanju cijelog lanca. Matematika iza ovog procesa je toliko složena da bi zahtijevala ogromnu računarsku moć kada bi i pokušala da je razbije. Koristeći kriptografske dokaze, Bitcoin ne zahtijeva povjerenje u ljude, već se umjesto toga, oslanja na neprobojne matematičke algoritme da osigura svaku transakciju.
Proof of Work – digitalna zagonetka koja štiti Bitcoin
Bitcoinova mreža je osigurana procesom koji se naziva Proof of Work (dokaz o radu), koji je najjednostavnije razumjeti ako ga zamislite kao izazovnu zagonetku koju računari, poznati kao „rudari“, moraju da riješe da bi dodali novi blok u blockchain. Prvi računar koji riješi zagonetku dobija priliku da doda blok i dobija nagradu u bitcoinima. Ova zagonetka je izuzetno složena i zahtijeva od rudara da koristi veliku količinu mnogo računarske snage, što je skupo u smislu vremena i energije.
U tom smislu Proof of Work čuva mrežu sigurnom, jer kad bi neko pokušao da prevari sistem ponovnim pisanjem blockchaina, morao ponovo da uradi svako izračunavanja dokaza o radu za svaki blok koji želi da izmijeni, što je praktično nemoguće. Na ovaj način Bitcoin kreira mrežni sistem u kojem je prevara previše skupa i previše složena da bi se bilo kome isplatila.
Šesnaest godina kasnije...
Bitcoin je za ovo vrijeme postao mnogo više od digitalne valute – on je simbol finansijske nezavisnosti i pokretačka snaga nove finansijske tehnologije i ekonomskih koncepata. Pokrenuo je diskusije o budućnosti novca, a inspirisao je brojne pružaoce platnih usluga, uključujući brojne banke širom svijeta i FinTech kompanije, da unapređuju poslovni model.
Zbog količine koja je u opticaju njegova upotreba kao valute ostaje ograničena u poređenju s tradicionalnim novcem, dok njegova cijena nastavlja da fluktuira u zavisnosti od tržišnih okolnosti. U tom smislu uticaj Bitcoina na finansije, tehnologiju i društvo u cjelini već je dubok, navodeći promišljenije i kreativnije istraživanje kako se vrednostima može upravljati i razmenjivati u savremenom svijetu, podstičući značaj decentralizacije i svijest o zaštiti podataka.
Iako često predstavljan kao sredstvo za „brzo bogaćenje“ ili sresdstvo za obavljanje anonimnih transakcija, motivi za njegovo kreiranje, kao i njegova uloga u finansijskom i tehnološkom svijetu potpuno se razlikuju od toga. Bitcoin je prva, najstarija, najvrednija i – u najširem smislu – po svim parametrima jedina prava, potpuno decenztralizovana kriptovaluta koja je transformisala način na koji razmišljamo o novcu, povjerenju i bezbednosti u digitalnoj eri.
-
 @ bf47c19e:c3d2573b
2025-05-11 18:22:19
@ bf47c19e:c3d2573b
2025-05-11 18:22:19Originalan tekst na linkedin.com
12.04.2024 / Autor: Aleksandar Matanović
60/40 portfolio je dugo važio za idealan izbor nekome ko ima umerenu sklonost ka riziku, a nema vremena da prati berzu. Dakle, ubaciš 60% u akcije, 40% u obveznice i pustiš vreme da radi svoje.
Malo sam se igrao sa brojkama i računao šta bi bilo da je neko u taj portfolio ubacio malo Bitkoina. Period koji je obrađen je januar 2014 - januar 2024. Ovde napominjem da nikako nisam radio "cherry picking", to jest nisam birao period u kome se Bitkoin pokazao u najboljem mogućem svetlu. Maltene sam uradio suprotno. Da sam izabrao bilo koji januar pre 2014-te, prinosi na BTC bi bili neuporedivo veći. Čak i da sam izabrao januar 2015-te ili 2016-te, takođe bi prinosi bili veći jer je cena tada bila niža nego u januaru 2014-te. Izbor datuma je bio posledica želje da zaokružim jednu celu deceniju, period nakon kojeg su strpljivi investitori nagrađeni time što ne plaćaju porez na kapitalnu dobit.
Obradio sam 3 realna scenarija:
- Klasičan 60/40 portfolio. Na uloženih $10.000 u januaru 2014. godine, 10 godina kasnije bismo imali tačno $17.434. Prosečan godišnji prinos je 5,72%.
- 99% uloženo u 60/40 portfolio, 1% uloženo u Bitkoin. Na uloženih $10.000, imali bismo $22.505 ili 8,45% godišnje. Samo 1% u BTC, a skoro 3% veći godišnji prinos. (narandžasta linija)
- 90% uloženo u 60/40 portfolio, 10% uloženo u Bitkoin. Sad već postaje zabavno... od $10.000 do $68.145, što bi bilo 21,16% godišnje - jače od proseka Vorena Bafeta. (zelena linija)
Uzeo sam u obzir i rizike i zamislio da je u ovom periodu cena Bitkoina polako padala i na kraju pala na 0. Dakle naredna 2 scenarija su hipotetička.
- 99% uloženo u 60/40 portfolio, 1% uloženo u Bitkoin, Bitkoin propao. Investirano $10.000, dobijeno $17.259 ili 5.61% godišnje. Minimalni gubitak u odnosu na čist 60/40 portfolio iz prvog scenarija. Zbog toga se na grafiku vide 4 linije iako ih ima 5, toliko je mala razlika.
- 90% uloženo u 60/40 portfolio, 10% uloženo u Bitkoin, Bitkoin propao. Investirano $10.000, dobijeno $15.690 ili 4.61% godišnje. To je ona donja. ljubičasta linija na grafikonu. Nije neki prinos, ali nije ni katastrofa.
Mogao sam da idem i sa preko 10%, naravno završili bismo na preko $100.000. Međutim, hteo sam da budem konzervativan i stvari gledam iz ugla investitora koji ipak ima nešto manji apetit ka riziku i nedovljno poznaje Bitkoin. Mogao sam i da uzmem drugačiji period. Na primer, za jan 2012 - jan 2022 bi narandžasta linija završila na preko milion dolara, a zelena na preko 10 miliona. Da, nije greška u računici... zaista biste za 10 godina, počev od januara 2012-te imali preko milion dolara da ste uložili ukupno $10.000, 99% u akcije i obveznice, a 1% u Bitkoin. Sa 90% u akcijama i obveznicama i 10% u Bitkoinu, već ste na 8 cifara.
Istorijske performanse nisu garancija budućih prinosa. Investiranje u Bitkoin je rizično. Ignorisanje Bitkoina je rizično. Svako bira svoj rizik. Ovo nije investicioni savet, ovo je prijateljski savet.
-
 @ 26d4b5b2:96393e73
2025-05-11 21:44:26
@ 26d4b5b2:96393e73
2025-05-11 21:44:26@(context.Request.Headers.GetValueOrDefault("Origin", "")) GET, POST, OPTIONS, PUT, DELETE Content-Type, Authorization, Accept, X-Requested-With, X-Verified-By, Ocp-Apim-Subscription-Key 86400 Access denied: invalid origin {{dohcloud-key}} @(context.Request.Headers.GetValueOrDefault("Origin", "")) GET, POST, OPTIONS, PUT, DELETE Content-Type, Authorization, Accept, X-Requested-With, X-Verified-By, Ocp-Apim-Subscription-Key @(context.Request.Headers.GetValueOrDefault("Origin", "*")) -
 @ 26d4b5b2:96393e73
2025-05-11 21:43:01
@ 26d4b5b2:96393e73
2025-05-11 21:43:01https://app.doh.money http://localhost:3000 https://dohmoney-cyxe-cyxeio-cyxecyxeios-projects.vercel.app GET POST OPTIONS PUT DELETE Content-Type Ocp-Apim-Subscription-Key Authorization Accept X-Requested-With X-Verified-By Content-Length Request-Context Date @(context.Request.Headers.GetValueOrDefault("Ocp-Apim-Subscription-Key", "50922ff015c14a84a092b4764dc6dddf")) @(context.Request.Headers.GetValueOrDefault("Origin", "https://app.doh.money")) @(context.Request.Headers.GetValueOrDefault("Origin", "http://localhost:3000")) GET, POST, OPTIONS, PUT, DELETE Content-Type, Ocp-Apim-Subscription-Key, Authorization, Accept, X-Requested-With,X-Verified-By Content-Length, Request-Context, Date @(context.Request.Headers.GetValueOrDefault("Origin", "https://app.doh.money")) @(context.Request.Headers.GetValueOrDefault("Origin", "http://localhost:3000")) GET, POST, OPTIONS, PUT, DELETE Content-Type, Ocp-Apim-Subscription-Key, Authorization, Accept, X-Requested-With, X-Verified-By Content-Length, Request-Context, Date -
 @ a95c6243:d345522c
2025-03-20 09:59:20
@ a95c6243:d345522c
2025-03-20 09:59:20Bald werde es verboten, alleine im Auto zu fahren, konnte man dieser Tage in verschiedenen spanischen Medien lesen. Die nationale Verkehrsbehörde (Dirección General de Tráfico, kurz DGT) werde Alleinfahrern das Leben schwer machen, wurde gemeldet. Konkret erörtere die Generaldirektion geeignete Sanktionen für Personen, die ohne Beifahrer im Privatauto unterwegs seien.
Das Alleinfahren sei zunehmend verpönt und ein Mentalitätswandel notwendig, hieß es. Dieser «Luxus» stehe im Widerspruch zu den Maßnahmen gegen Umweltverschmutzung, die in allen europäischen Ländern gefördert würden. In Frankreich sei es «bereits verboten, in der Hauptstadt allein zu fahren», behauptete Noticiastrabajo Huffpost in einer Zwischenüberschrift. Nur um dann im Text zu konkretisieren, dass die sogenannte «Umweltspur» auf der Pariser Ringautobahn gemeint war, die für Busse, Taxis und Fahrgemeinschaften reserviert ist. Ab Mai werden Verstöße dagegen mit einem Bußgeld geahndet.
Die DGT jedenfalls wolle bei der Umsetzung derartiger Maßnahmen nicht hinterherhinken. Diese Medienberichte, inklusive des angeblich bevorstehenden Verbots, beriefen sich auf Aussagen des Generaldirektors der Behörde, Pere Navarro, beim Mobilitätskongress Global Mobility Call im November letzten Jahres, wo es um «nachhaltige Mobilität» ging. Aus diesem Kontext stammt auch Navarros Warnung: «Die Zukunft des Verkehrs ist geteilt oder es gibt keine».
Die «Faktenchecker» kamen der Generaldirektion prompt zu Hilfe. Die DGT habe derlei Behauptungen zurückgewiesen und klargestellt, dass es keine Pläne gebe, Fahrten mit nur einer Person im Auto zu verbieten oder zu bestrafen. Bei solchen Meldungen handele es sich um Fake News. Teilweise wurde der Vorsitzende der spanischen «Rechtsaußen»-Partei Vox, Santiago Abascal, der Urheberschaft bezichtigt, weil er einen entsprechenden Artikel von La Gaceta kommentiert hatte.
Der Beschwichtigungsversuch der Art «niemand hat die Absicht» ist dabei erfahrungsgemäß eher ein Alarmzeichen als eine Beruhigung. Walter Ulbrichts Leugnung einer geplanten Berliner Mauer vom Juni 1961 ist vielen genauso in Erinnerung wie die Fake News-Warnungen des deutschen Bundesgesundheitsministeriums bezüglich Lockdowns im März 2020 oder diverse Äußerungen zu einer Impfpflicht ab 2020.
Aber Aufregung hin, Dementis her: Die Pressemitteilung der DGT zu dem Mobilitätskongress enthält in Wahrheit viel interessantere Informationen als «nur» einen Appell an den «guten» Bürger wegen der Bemühungen um die Lebensqualität in Großstädten oder einen möglichen obligatorischen Abschied vom Alleinfahren. Allerdings werden diese Details von Medien und sogenannten Faktencheckern geflissentlich übersehen, obwohl sie keineswegs versteckt sind. Die Auskünfte sind sehr aufschlussreich, wenn man genauer hinschaut.
Digitalisierung ist der Schlüssel für Kontrolle
Auf dem Kongress stellte die Verkehrsbehörde ihre Initiativen zur Förderung der «neuen Mobilität» vor, deren Priorität Sicherheit und Effizienz sei. Die vier konkreten Ansätze haben alle mit Digitalisierung, Daten, Überwachung und Kontrolle im großen Stil zu tun und werden unter dem Euphemismus der «öffentlich-privaten Partnerschaft» angepriesen. Auch lassen sie die transhumanistische Idee vom unzulänglichen Menschen erkennen, dessen Fehler durch «intelligente» technologische Infrastruktur kompensiert werden müssten.
Die Chefin des Bereichs «Verkehrsüberwachung» erklärte die Funktion des spanischen National Access Point (NAP), wobei sie betonte, wie wichtig Verkehrs- und Infrastrukturinformationen in Echtzeit seien. Der NAP ist «eine essenzielle Web-Applikation, die unter EU-Mandat erstellt wurde», kann man auf der Website der DGT nachlesen.
Das Mandat meint Regelungen zu einem einheitlichen europäischen Verkehrsraum, mit denen die Union mindestens seit 2010 den Aufbau einer digitalen Architektur mit offenen Schnittstellen betreibt. Damit begründet man auch «umfassende Datenbereitstellungspflichten im Bereich multimodaler Reiseinformationen». Jeder Mitgliedstaat musste einen NAP, also einen nationalen Zugangspunkt einrichten, der Zugang zu statischen und dynamischen Reise- und Verkehrsdaten verschiedener Verkehrsträger ermöglicht.
Diese Entwicklung ist heute schon weit fortgeschritten, auch und besonders in Spanien. Auf besagtem Kongress erläuterte die Leiterin des Bereichs «Telematik» die Plattform «DGT 3.0». Diese werde als Integrator aller Informationen genutzt, die von den verschiedenen öffentlichen und privaten Systemen, die Teil der Mobilität sind, bereitgestellt werden.
Es handele sich um eine Vermittlungsplattform zwischen Akteuren wie Fahrzeugherstellern, Anbietern von Navigationsdiensten oder Kommunen und dem Endnutzer, der die Verkehrswege benutzt. Alle seien auf Basis des Internets der Dinge (IOT) anonym verbunden, «um der vernetzten Gemeinschaft wertvolle Informationen zu liefern oder diese zu nutzen».
So sei DGT 3.0 «ein Zugangspunkt für einzigartige, kostenlose und genaue Echtzeitinformationen über das Geschehen auf den Straßen und in den Städten». Damit lasse sich der Verkehr nachhaltiger und vernetzter gestalten. Beispielsweise würden die Karten des Produktpartners Google dank der DGT-Daten 50 Millionen Mal pro Tag aktualisiert.
Des Weiteren informiert die Verkehrsbehörde über ihr SCADA-Projekt. Die Abkürzung steht für Supervisory Control and Data Acquisition, zu deutsch etwa: Kontrollierte Steuerung und Datenerfassung. Mit SCADA kombiniert man Software und Hardware, um automatisierte Systeme zur Überwachung und Steuerung technischer Prozesse zu schaffen. Das SCADA-Projekt der DGT wird von Indra entwickelt, einem spanischen Beratungskonzern aus den Bereichen Sicherheit & Militär, Energie, Transport, Telekommunikation und Gesundheitsinformation.
Das SCADA-System der Behörde umfasse auch eine Videostreaming- und Videoaufzeichnungsplattform, die das Hochladen in die Cloud in Echtzeit ermöglicht, wie Indra erklärt. Dabei gehe es um Bilder, die von Überwachungskameras an Straßen aufgenommen wurden, sowie um Videos aus DGT-Hubschraubern und Drohnen. Ziel sei es, «die sichere Weitergabe von Videos an Dritte sowie die kontinuierliche Aufzeichnung und Speicherung von Bildern zur möglichen Analyse und späteren Nutzung zu ermöglichen».
Letzteres klingt sehr nach biometrischer Erkennung und Auswertung durch künstliche Intelligenz. Für eine bessere Datenübertragung wird derzeit die Glasfaserverkabelung entlang der Landstraßen und Autobahnen ausgebaut. Mit der Cloud sind die Amazon Web Services (AWS) gemeint, die spanischen Daten gehen somit direkt zu einem US-amerikanischen «Big Data»-Unternehmen.
Das Thema «autonomes Fahren», also Fahren ohne Zutun des Menschen, bildet den Abschluss der Betrachtungen der DGT. Zusammen mit dem Interessenverband der Automobilindustrie ANFAC (Asociación Española de Fabricantes de Automóviles y Camiones) sprach man auf dem Kongress über Strategien und Perspektiven in diesem Bereich. Die Lobbyisten hoffen noch in diesem Jahr 2025 auf einen normativen Rahmen zur erweiterten Unterstützung autonomer Technologien.
Wenn man derartige Informationen im Zusammenhang betrachtet, bekommt man eine Idee davon, warum zunehmend alles elektrisch und digital werden soll. Umwelt- und Mobilitätsprobleme in Städten, wie Luftverschmutzung, Lärmbelästigung, Platzmangel oder Staus, sind eine Sache. Mit dem Argument «emissionslos» wird jedoch eine Referenz zum CO2 und dem «menschengemachten Klimawandel» hergestellt, die Emotionen triggert. Und damit wird so ziemlich alles verkauft.
Letztlich aber gilt: Je elektrischer und digitaler unsere Umgebung wird und je freigiebiger wir mit unseren Daten jeder Art sind, desto besser werden wir kontrollier-, steuer- und sogar abschaltbar. Irgendwann entscheiden KI-basierte Algorithmen, ob, wann, wie, wohin und mit wem wir uns bewegen dürfen. Über einen 15-Minuten-Radius geht dann möglicherweise nichts hinaus. Die Projekte auf diesem Weg sind ernst zu nehmen, real und schon weit fortgeschritten.
[Titelbild: Pixabay]
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ c4b5369a:b812dbd6
2025-04-15 07:26:16
@ c4b5369a:b812dbd6
2025-04-15 07:26:16Offline transactions with Cashu
Over the past few weeks, I've been busy implementing offline capabilities into nutstash. I think this is one of the key value propositions of ecash, beinga a bearer instrument that can be used without internet access.
 It does however come with limitations, which can lead to a bit of confusion. I hope this article will clear some of these questions up for you!
It does however come with limitations, which can lead to a bit of confusion. I hope this article will clear some of these questions up for you!What is ecash/Cashu?
Ecash is the first cryptocurrency ever invented. It was created by David Chaum in 1983. It uses a blind signature scheme, which allows users to prove ownership of a token without revealing a link to its origin. These tokens are what we call ecash. They are bearer instruments, meaning that anyone who possesses a copy of them, is considered the owner.
Cashu is an implementation of ecash, built to tightly interact with Bitcoin, more specifically the Bitcoin lightning network. In the Cashu ecosystem,
Mintsare the gateway to the lightning network. They provide the infrastructure to access the lightning network, pay invoices and receive payments. Instead of relying on a traditional ledger scheme like other custodians do, the mint issues ecash tokens, to represent the value held by the users.How do normal Cashu transactions work?
A Cashu transaction happens when the sender gives a copy of his ecash token to the receiver. This can happen by any means imaginable. You could send the token through email, messenger, or even by pidgeon. One of the common ways to transfer ecash is via QR code.
The transaction is however not finalized just yet! In order to make sure the sender cannot double-spend their copy of the token, the receiver must do what we call a
swap. A swap is essentially exchanging an ecash token for a new one at the mint, invalidating the old token in the process. This ensures that the sender can no longer use the same token to spend elsewhere, and the value has been transferred to the receiver.
What about offline transactions?
Sending offline
Sending offline is very simple. The ecash tokens are stored on your device. Thus, no internet connection is required to access them. You can litteraly just take them, and give them to someone. The most convenient way is usually through a local transmission protocol, like NFC, QR code, Bluetooth, etc.
The one thing to consider when sending offline is that ecash tokens come in form of "coins" or "notes". The technical term we use in Cashu is
Proof. It "proofs" to the mint that you own a certain amount of value. Since these proofs have a fixed value attached to them, much like UTXOs in Bitcoin do, you would need proofs with a value that matches what you want to send. You can mix and match multiple proofs together to create a token that matches the amount you want to send. But, if you don't have proofs that match the amount, you would need to go online and swap for the needed proofs at the mint.Another limitation is, that you cannot create custom proofs offline. For example, if you would want to lock the ecash to a certain pubkey, or add a timelock to the proof, you would need to go online and create a new custom proof at the mint.
Receiving offline
You might think: well, if I trust the sender, I don't need to be swapping the token right away!
You're absolutely correct. If you trust the sender, you can simply accept their ecash token without needing to swap it immediately.
This is already really useful, since it gives you a way to receive a payment from a friend or close aquaintance without having to worry about connectivity. It's almost just like physical cash!
It does however not work if the sender is untrusted. We have to use a different scheme to be able to receive payments from someone we don't trust.
Receiving offline from an untrusted sender
To be able to receive payments from an untrusted sender, we need the sender to create a custom proof for us. As we've seen before, this requires the sender to go online.
The sender needs to create a token that has the following properties, so that the receciver can verify it offline:
- It must be locked to ONLY the receiver's public key
- It must include an
offline signature proof(DLEQ proof) - If it contains a timelock & refund clause, it must be set to a time in the future that is acceptable for the receiver
- It cannot contain duplicate proofs (double-spend)
- It cannot contain proofs that the receiver has already received before (double-spend)

If all of these conditions are met, then the receiver can verify the proof offline and accept the payment. This allows us to receive payments from anyone, even if we don't trust them.
At first glance, this scheme seems kinda useless. It requires the sender to go online, which defeats the purpose of having an offline payment system.
I beleive there are a couple of ways this scheme might be useful nonetheless:
-
Offline vending machines: Imagine you have an offline vending machine that accepts payments from anyone. The vending machine could use this scheme to verify payments without needing to go online itself. We can assume that the sender is able to go online and create a valid token, but the receiver doesn't need to be online to verify it.
-
Offline marketplaces: Imagine you have an offline marketplace where buyers and sellers can trade goods and services. Before going to the marketplace the sender already knows where he will be spending the money. The sender could create a valid token before going to the marketplace, using the merchants public key as a lock, and adding a refund clause to redeem any unspent ecash after it expires. In this case, neither the sender nor the receiver needs to go online to complete the transaction.
How to use this
Pretty much all cashu wallets allow you to send tokens offline. This is because all that the wallet needs to do is to look if it can create the desired amount from the proofs stored locally. If yes, it will automatically create the token offline.
Receiving offline tokens is currently only supported by nutstash (experimental).
To create an offline receivable token, the sender needs to lock it to the receiver's public key. Currently there is no refund clause! So be careful that you don't get accidentally locked out of your funds!

The receiver can then inspect the token and decide if it is safe to accept without a swap. If all checks are green, they can accept the token offline without trusting the sender.

The receiver will see the unswapped tokens on the wallet homescreen. They will need to manually swap them later when they are online again.
 Later when the receiver is online again, they can swap the token for a fresh one.
Later when the receiver is online again, they can swap the token for a fresh one.
Summary
We learned that offline transactions are possible with ecash, but there are some limitations. It either requires trusting the sender, or relying on either the sender or receiver to be online to verify the tokens, or create tokens that can be verified offline by the receiver.
I hope this short article was helpful in understanding how ecash works and its potential for offline transactions.
Cheers,
Gandlaf
-
 @ bf47c19e:c3d2573b
2025-05-11 18:21:00
@ bf47c19e:c3d2573b
2025-05-11 18:21:0013.06.2023. / Autor: Igor Mirković
Ograničena količina Bitcoina:
Ukupno: 21 milion BTC
Trenutno izrudareno: 19.400.050 BTC
Preostalo za rudarenje: 1.599.950 BTC
Dnevno se izrudari: 900 BTC
Da li je 21 milion Bitcoina dovoljno?
Da li znate koliko je milionera u svetu? Oko 56 miliona milionera, odnosno 1.1% populacije. Ako podelimo 21 milion Bitcoin-a na 56 miliona milionera dobijamo 0.375 BTC po svakom milioneru.
Ograničena zaliha Bitcoina i broj milionera su sami dovoljni da lansiraju cenu, jer bi posedovanje jednog celog Bitcoin-a moglo da postane status moći milionera u budućnosti.

Verovatno bi se oni nekako i dogovorili na ravnopravnu raspodelu da u svetu nema preko 2.000 milijardera, kojima ni 1, a kamoli 0.39 BTC nisu dovoljni za smislenu investiciju.
Zašto kompanije kupuju Bitcoin?
Jedan od faktora koji ovu računicu čini još diskutabilnijom su Bitcoin-i koji su zauvek nestali i zaboravljeni na novčanicima. Nezahvalno je tvrditi koliko je Bitcoin-a „izgubljeno“, ali postoje i istraživanja koja pokazuju da to uopšte nije mali deo celokupne ponude. Kreator Bitcoin-a Satoši odmah je u startu pretpostavio da ovako nešto može da se desi i na ovu okrutnu prirodnu selekciju dao je logičan komentar da će, u slučaju ako neko izgubi pristup svojim Bitcoin-ima, coini koje ima ostatak zajednice samim tim vredeti više.
Kako bismo shvatili zašto je ograničena zaliha izuzetno važna, vratićemo se na staro dobro poređenje zlata i Bitcoin-a. Bitcoin i zlato imaju mnogo sličnosti ali i jednu ključnu razliku. Bitcoin nazivaju digitalnim zlatom, nekada čak i drugom, unapređenom verzijom zlata (Zlato 2.0).
I zlato i Bitcoin:
Imaju fiksnu i ograničenu zalihu. Za BTC se zna koliko ga ima, a za zlato se zna da je ograničeno i da ga nema mnogo. Ne mogu biti lažirani i napravljeni veštački.
Najveća razlika između ova dva čuvara vrednosti je što je zlato u fizičkom obliku, a BTC je isključivo digitalan. Digitalne karakteristike Bitcoin-u daju brojne prednosti u odnosu na zlato: Lako je deljiv na sitnije delove, lako se šalje svuda u svetu, lako se čuva, transportuje i potpuno je transparentan.
Magija od 21 miliona
Ponuda i tražnja… dva jednostavna koncepta, a opet dovoljno sveobuhvatna da definišu i utiču na sve. Kada se spoje, kreiraju apstraktnu pojavu koja se zove vrednost.
Koliko nečega ima i koliko je traženo? Odrednica je za plate radnih mesta, cene imovine, roba, usluga, dobra i gde god želimo da pripišemo neku vrednost možemo početi od tog osnova.
Od samog nastanka čoveka, sve na svetu je imalo percipiranu neograničenu zalihu. Od životinja, zemlje, zlata, vode, nafte. Ljudi su bukvalno konzumirali počevši od pećinskog čoveka pa do danas kao da nema ograničenja ni u čemu.
U stanju smo da konzumiramo i trošimo resurse dok ne nestanu zauvek sa zemlje, samo pogledajte životinje, biljke i sirovine koje su nestale ili su veoma ugrožene zbog uticaja ljudskih „potreba“. Smislili smo čak i šta ćemo kada odrećene sirovine ili životinje nestanu. Napravićemo DNK klonove, sintetičke proizvode, imitaciju koja će nam služiti za naše lične potrebe. Što su zalihe manje i manje, cene su veće ali i želja… potreba za konzumacijom nema cenu.
Šta to znači u slučaju Bitcoin-a? Kao što znamo, Bitcoin je bio prva imovina koja je zaista ograničena, na 21 milion coina, to je sve što će ikada biti stvoreno, a ljudi ne mogu da ga kloniraju, doštampaju, veštački naprave, lažiraju ili slično.
Ograničenost Bitcoin-a se kosi sa svim ljudskim potrošačkim navikama. Uvek postoji način da dobijete više, osim u slučaju Bitcoin-a.
Ova činjenica ograničenosti zaliha je poremetila definiciju ekonomske vrednosti za Bitcoin. To je razlog zašto je on došao do vrednosti od preko 20 hiljada dolara za nešto više od 10 godina. To je jedan od najvećih skokova vrednosti u istoriji čovečanstva i po mišljenju mnogih, samo početak.
Zašto je ograničenje od 21 miliona koje zagovornici ističu toliko važno, koliko je trenutno Bitcoin-a na tržištu i koji je proces koji stvara nove coine odnosno kada će i poslednji BTC biti dostupan?

Bitcoin se često smatra novom vrstom novca koji rešava nedostatke i nudi poboljšanja postojećeg monetarnog sistema. Jedno od tih poboljšanja je fiksna zaliha – 21 milion Bitcoin-a i kodirana logika, koja se ne može menjati, o tome kako će se Bitcoin-i stvarati i po kom principu distribuirati dok se ne postigne ta cifra što se očekuje oko 2150. godine.
Postoje dva elementa fiksne zalihe koji su bitni za razumevanje: Zašto je fiksna zaliha bitna karakteristika za novac i koji sistem Bitcoin koristi kako bi je garantovao.
Odnos ograničene zalihe i vrednosti
Prvi oblici novca pojavili su se nezavisno u različitim kulturama i predstavljali su ključno rešenje i prelazak sa tadašnje trampe. Različite vrste stvari isprobane su kao oblik novca – kokosovi orasi, stoka, ječam, so, biseri, školjke – pre nego što su se zlato i srebro utemeljili kao najefikasniji.
Razlog zbog kojeg su plemeniti metali postali standard za novac bilo je ispunjavanje ključnih karakteristika kako bi novac bio efikasan kao sredstvo razmene:
Prenosiv – Lak za nošenje Izdržljiv – Neće fizički propasti Deljiv – Može se podeliti na manje jednake delove Zamenljiv – Svaka deo je zamenljiv za bilo koju drugu stvar Prepoznatljiv – Očigledno je šta je Oskudan – nema ga u izobilju niti ga je lako nabaviti
Od šest magičnih stvari koje čine novac korisnim za razmenu, poslednja je daleko najvažnija (isto tako je u slučaju novca kao načina očuvanja vrednosti – skladišta vrednosti).
Zamislite sa kakvim problemima bismo se suočavali da je so ostala dominantan oblik novca.
Zlato ispunjava uslov oskudnosti i većinu od ostalih pet, ali je njegova mana izuzetno tešak transport.
Kada je Satoši Nakamoto krenuo sa stvaranjem novog oblika internet novca, on/ona/oni su morali da pronađu način da stvore neku vrstu digitalnog zlata, ali sa isprogramiranom distribucijom odnosno ukupnom ponudom, što je bilo mnogo teže realizovati i napraviti nego što zvuči.
Isprogramirana zaliha
Ako razmislite o najpoznatijim digitalnim formatima- jpeg slikama, Google dokumentima, mp3 datotekama – svi oni mogu da se kopiraju prilično lako. Bitcoin ne može, jer to nije datoteka koja se nalazi na vašem telefonu ili laptopu, već postoji u obliku zapisa koji je povezan sa adresom – mestom na bitcoin blokčejnu– koji možete zamisliti kao broj bankovnog računa.
Ako imate pristup bitcoin adresi i neka sredstva u Bitcoin-u na njoj, možete ga iskoristiti. Dakle, Bitcoin blokčejn kao monetarni sistem je kuća svih bitkoina koji su u opticaju, drugim rečima, ukupne ponude Bitkoina.
Sledeće logično pitanje je kako se kontroliše i održava bitkoin mreža? Česta zabluda koja postoji zbog tradicionalnih finansijskih sistema je da ko god to kontroliše može stvoriti onoliko BTC-a koliko želi? Možda, ako bi to kontrolisala jedna osoba, sigurno bi bila u iskušenju… tako u stvari funkcioniše postojeći novac centralnih banaka.
Kako nastaju Bitkoini?
Jedan od najmagičnijih mehanizama Bitcoin sistema je način na koji se stvaraju novi Bitcoin-i kroz proces koji se zove rudarenje. To je prilično složen proces, tako da ko želi da istraži i kopa dublje može se informiše na našem blogu u sekciji rudarenje.
Bitcoin sistem funkcioniše u skladu sa skupom pravila koji se nazivaju Bitcoin Protokol. Taj skup pravila kaže da će ukupno postojati maksimalno 21 milion, sa fiksnim brojem Bitcoin-a koji se kreira svakih 10 minuta kao nagrada za rudare koji obrađuju nove transakcije u bloku podataka. Blokovi podataka su povezani zajedno sa neraskidivim kriptografskim vezama – otuda i termin blokčejn.
Rudarenje kriptovaluta – Kakva su iskustva srpskih rudara?
Prvi blok je iskopan u januaru 2009. godine, kada je nagrada za rudare bila 50 BTC-a. Tako je 50 novih koina puštano u promet svakih 10 minuta.
Protokol o Bitcoin-u je programiran da kada se stvori 210.000 blokova, nagrada se prepolovi, što se dešava otprilike svake četiri godine i naziva se Bitcoin halving.
Bitcoin je do sada prošao kroz tri halvinga. Umesto da bude inflatoran – sa stalno rastućom ponudom – koja narušava vrednost, Bitcoin je deflatoran jer raste uz opadajuću maržu, koja će na kraju dostići nulu kada se dostigne količina od distribuiranih 21 milion BTC-a.
Zašto baš 21 milion?
Neka jednostavna matematika ukazuje na to da je Satoši možda imao mnogo veću viziju o bitkoinu – što bolje objašnjava zašto je izabran maksimalni iznos od 21 milion.
U vreme stvaranja Bitcoin-a, celokupna svetska ponuda novca iznosila je približno 21 hiljadu milijardi dolara. Ova cifra, poznata kao M1 novčana masa, sastoji se od ukupne vrednosti celokupnog fizičkog novca na svetu, uključujući gotovinu, kovanice, čekove i još mnogo toga.
Ako bi Bitcoin narastao i postao jedinstvena svetska valuta — zamenjujući sve one od kojih se sastoji M1 cifra — onda bi svaki BTC vredeo milion dolara. Pošto u svakom Bitcoin-u ima 100 miliona satošija, to bi postavilo vrednost svakog satošija na 0,01 dolara.
Činjenica da su ovi brojevi tako blisko usklađeni bila bi izuzetna slučajnost, ako nije namerno.
Druga verzija
Iako je teorija zamene novčane mase M1 možda najverovatnije obrazloženje zašto je Satoši odabrao 21 milion da bude limit za Bitcoin, postoji još jedno donekle jednostavnije objašnjenje.
Gledajući parametre koji se koriste za kontrolu distribucije Bitcoin-a, postaje jasno da cifra od 21 milion BTC-a omogućava mreži da osigura da se blokovi rudare u redovnom vremenskom okviru (10 minuta).
Takođe. osigurava da se količina bitkoina koji se isplaćuje rudarima kao nagrade za blok vremenom smanjuje, kako se maksimalna ponuda približava granici. Kako se ispostavilo, parametri koje je Satoshi postavio za ovo neizbežno dovode do proizvodnje od maksimalno 21 miliona BTC. Na osnovu ove karakteristike, ukupno 210.000 blokova treba da se rudari u svakom četvorogodišnjem ciklusu, nakon čega se nagrada za blok prepolovi.

U prvom ciklusu je puštano 50 BTC po bloku; ovo je prepolovljeno na 25 BTC po bloku u 2012. godini, zatim ponovo na 12,5 BTC po bloku u 2016. Nakon prepolovljenja u 2020., trenutno je na 6,25 BTC po bloku.
Ako nastavimo videćemo da je zbir nagrada za blok za svaki ciklus jednak 100 (50 + 25 + 6,25 +3,125, itd.). Množenjem ovog broja sa cifrom od 210.000 blokova, dobijate maksimalnu moguću ponudu od 21 milion.
Dakle, da li je zaliha Bitcoin-a filozofski gest ili proizvod nemilosrdne matematičke logike? Samo Satoši Nakamoto zaista zna.
-
 @ a95c6243:d345522c
2025-03-15 10:56:08
@ a95c6243:d345522c
2025-03-15 10:56:08Was nützt die schönste Schuldenbremse, wenn der Russe vor der Tür steht? \ Wir können uns verteidigen lernen oder alle Russisch lernen. \ Jens Spahn
In der Politik ist buchstäblich keine Idee zu riskant, kein Mittel zu schäbig und keine Lüge zu dreist, als dass sie nicht benutzt würden. Aber der Clou ist, dass diese Masche immer noch funktioniert, wenn nicht sogar immer besser. Ist das alles wirklich so schwer zu durchschauen? Mir fehlen langsam die Worte.
Aktuell werden sowohl in der Europäischen Union als auch in Deutschland riesige Milliardenpakete für die Aufrüstung – also für die Rüstungsindustrie – geschnürt. Die EU will 800 Milliarden Euro locker machen, in Deutschland sollen es 500 Milliarden «Sondervermögen» sein. Verteidigung nennen das unsere «Führer», innerhalb der Union und auch an «unserer Ostflanke», der Ukraine.
Das nötige Feindbild konnte inzwischen signifikant erweitert werden. Schuld an allem und zudem gefährlich ist nicht mehr nur Putin, sondern jetzt auch Trump. Europa müsse sich sowohl gegen Russland als auch gegen die USA schützen und rüsten, wird uns eingetrichtert.
Und während durch Diplomatie genau dieser beiden Staaten gerade endlich mal Bewegung in die Bemühungen um einen Frieden oder wenigstens einen Waffenstillstand in der Ukraine kommt, rasselt man im moralisch überlegenen Zeigefinger-Europa so richtig mit dem Säbel.
Begleitet und gestützt wird der ganze Prozess – wie sollte es anders sein – von den «Qualitätsmedien». Dass Russland einen Angriff auf «Europa» plant, weiß nicht nur der deutsche Verteidigungsminister (und mit Abstand beliebteste Politiker) Pistorius, sondern dank ihnen auch jedes Kind. Uns bleiben nur noch wenige Jahre. Zum Glück bereitet sich die Bundeswehr schon sehr konkret auf einen Krieg vor.
Die FAZ und Corona-Gesundheitsminister Spahn markieren einen traurigen Höhepunkt. Hier haben sich «politische und publizistische Verantwortungslosigkeit propagandistisch gegenseitig befruchtet», wie es bei den NachDenkSeiten heißt. Die Aussage Spahns in dem Interview, «der Russe steht vor der Tür», ist das eine. Die Zeitung verschärfte die Sache jedoch, indem sie das Zitat explizit in den Titel übernahm, der in einer ersten Version scheinbar zu harmlos war.
Eine große Mehrheit der deutschen Bevölkerung findet Aufrüstung und mehr Schulden toll, wie ARD und ZDF sehr passend ermittelt haben wollen. Ähnliches gelte für eine noch stärkere militärische Unterstützung der Ukraine. Etwas skeptischer seien die Befragten bezüglich der Entsendung von Bundeswehrsoldaten dorthin, aber immerhin etwa fifty-fifty.
Eigentlich ist jedoch die Meinung der Menschen in «unseren Demokratien» irrelevant. Sowohl in der Europäischen Union als auch in Deutschland sind die «Eliten» offenbar der Ansicht, der Souverän habe in Fragen von Krieg und Frieden sowie von aberwitzigen astronomischen Schulden kein Wörtchen mitzureden. Frau von der Leyen möchte über 150 Milliarden aus dem Gesamtpaket unter Verwendung von Artikel 122 des EU-Vertrags ohne das Europäische Parlament entscheiden – wenn auch nicht völlig kritiklos.
In Deutschland wollen CDU/CSU und SPD zur Aufweichung der «Schuldenbremse» mehrere Änderungen des Grundgesetzes durch das abgewählte Parlament peitschen. Dieser Versuch, mit dem alten Bundestag eine Zweidrittelmehrheit zu erzielen, die im neuen nicht mehr gegeben wäre, ist mindestens verfassungsrechtlich umstritten.
Das Manöver scheint aber zu funktionieren. Heute haben die Grünen zugestimmt, nachdem Kanzlerkandidat Merz läppische 100 Milliarden für «irgendwas mit Klima» zugesichert hatte. Die Abstimmung im Plenum soll am kommenden Dienstag erfolgen – nur eine Woche, bevor sich der neu gewählte Bundestag konstituieren wird.
Interessant sind die Argumente, die BlackRocker Merz für seine Attacke auf Grundgesetz und Demokratie ins Feld führt. Abgesehen von der angeblichen Eile, «unsere Verteidigungsfähigkeit deutlich zu erhöhen» (ausgelöst unter anderem durch «die Münchner Sicherheitskonferenz und die Ereignisse im Weißen Haus»), ließ uns der CDU-Chef wissen, dass Deutschland einfach auf die internationale Bühne zurück müsse. Merz schwadronierte gefährlich mehrdeutig:
«Die ganze Welt schaut in diesen Tagen und Wochen auf Deutschland. Wir haben in der Europäischen Union und auf der Welt eine Aufgabe, die weit über die Grenzen unseres eigenen Landes hinausgeht.»
[Titelbild: Tag des Sieges]
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ bf47c19e:c3d2573b
2025-05-11 18:20:44
@ bf47c19e:c3d2573b
2025-05-11 18:20:4402.05.2023. / Autor: Igor Mirković
Bitcoin halving je ključni događaj Bitcoin mreže koji umanjuje nagrade za rudarenje, utiče na trend tržišta, profitabilnost rudara i pokreće inovacije u kripto ekosistemu.
Smanjenje nagrade za rudare utiče i na cenu Bitcoin-a, a veliki investitori i rudarska postrojenja igraju značajnu ulogu u oblikovanju tržišnog odgovora na ovaj događaj.
Predstojeći halving može podstaći investitore i rudare da pored Bitcoin-a istraže ponudu altkoina ali i da potraže isplativija rešenja za rudarenje.

Sta je Bitcoin halving?
Bitcoin halving je proces smanjenja nagrade koju rudari dobijaju za potvrđivanje transakcija na Bitcoin mreži. Ovaj proces se dešava svakih 210.000 blokova, što pada na svake četiri godine.
Kada je Bitcoin prvi put pokrenut 2009. godine, nagrada za izrudaren blok u kome se čuvaju transakcije bila je 50 BTC. Nakon prvog halvinga 2012. godine, nagrada se smanjila na 25 BTC po bloku. Drugi halving se dogodio 2016. godine i nagrada se smanjila na 12,5 BTC po bloku. Treći halving se dogodio u maju 2020. godine i nagrada se smanjila na 6,25 BTC po bloku.

Sledeći halving se očekuje 2024. godine i nagrada će se ponovo smanjiti upola, na 3,125 BTC po bloku.
Smanjenje nagrade za cilj ima smanjenje količine novih Bitcoina koji se stvaraju kako bi se dostigla ograničena ukupna ponuda od 21 milion BTC. Ova dinamika stvaranja novih coina takođe utiče na cenu Bitcoina.
Kada se poslednji Bitcoin izrudari, nagrade po izrudarenom bloku će nestati. To se očekuje oko 2140. godine. Nakon toga, rudari će moći da zarađuju samo kroz naknade za realizaciju transakcija koje korisnici mreže plaćaju.

Bitcoin halving je događaj koji smanjuje broj novih Bitcoina koji se generišu po bloku.
U skladu sa opštim zakonom ekonomije – manja ponuda uz stabilnu tražnju bi trebalo da rezultira višim cenama.
Godinu dana pre dugo očekivanog halvinga, stručnjaci i investitori u kripto industriji pažljivo prate njegov potencijalni uticaj na tržište.
Bitcoin halving je je osnovni deflatorni mehanizam definisan u Bitcoin protokolu. Dizajniran je da smanji nagradu za rudarenje za 50% na svakih 210.000 blokova ili otprilike svake četiri godine. Ovo smanjenje ima dvostruku svrhu.
Jedna je kontrola stope inflacije Bitcoin-a kroz imitaciju oskudice, a druga je garancija predvidljive i sve manje ponude novog BTC-a koji ulazi na tržište.
Ovaj mehanizam ima za cilj da očuva vrednost BTC-a tokom vremena, čineći ga atraktivnim čuvarom vrednosti. Kao rezultat toga, halving je ključna komponenta dugoročne ekonomske održivosti Bitcoin-a.
Istorijski gledano, halving je značajno uticao na cenu Bitcoina zbog smanjene ponude novog BTC-a na tržištu. Na primer, u halving događajima 2012, 2016. i 2020. cena bitcoina je doživela značajan porast u mesecima nakon prepolovljavanja nagrade, zato što su trgovci očekivali šok na strani ponude i povećanu potražnju za oskudnijom imovinom.
Trenutno, nagrada za rudarenje iznosi 6,25 BTC po bloku. Nakon sledećeg halvinga koji se očekuje 2024. godine, nagrada za rudarenje će se smanjiti na 3,125 BTC po bloku.

Kakve je posledice halving uzrokovao u prošlosti?
Stručnjaci predviđaju da bi halving mogao dovesti do značajnih promena u ceni BTC-a, kao što je bio slučaj prethodnog puta. Međutim, faktori kao što su globalni ekonomski uslovi, regulatorni razvoj i strategije institucionalnih investitora mogu uticati na ishod.
Tokom halvinga 2012. cena Bitcoina je porasla sa oko 11 dolara u novembru 2012. na oko 1.100 dolara u novembru 2013. godine, što je značajno povećanje u roku od godinu dana.
Tokom ovog perioda, Bitcoin je još uvek bio relativno nov koncept. A tržište su prvenstveno pokretali mali investitori i rani korisnici koji su predvideli potencijal decentralizovane digitalne valute.
Halving u 2016. doveo je do povećanja cene bitcoina sa oko 650 dolara u julu 2016. na skoro 20.000 dolara u decembru 2017. Taj rast je bilo podstaknut povećanom pažnjom velikih medija i ulaskom institucionalnih investitora.
Ipak, regulatorni razvoji i pokušaji da se nametnu strožija pravila za kripto berze, doprineli su nestabilnosti tržišta.
Halving iz 2020. doveo je do povećanja cene bitcoina sa oko 9.000 dolara u maju 2020. na istorijski maksimum od oko 69.000 dolara u novembru 2021. Halving 2020. okarakterisan je rekordnim institucionalnim interesovanjem, vođenim velikim korporacijama i investicionim fondovima koji su ušli na kripto tržište.
COVID-19 pandemija takođe je odigrala značajnu ulogu u oblikovanju raspoloženja na tržištu. Kako su globalna ekonomska kriza i neviđene fiskalne stimulativne mere izazvale zabrinutost zbog inflacije i slabljenja nacionalnih valuta, potražnja za Bitcoinom je rasla.
Kada je sledeći datum Bitkoin halvinga?
Sledeći datum Bitkoin halvinga je zakazan za blok 840.000 – predviđeno je da će se desiti 20. aprila 2024. u 09:20 UTC.
Na datum Bitkoin halvinga predviđeno je da nagrada za blok padne sa 6,25 bitkoina po bloku na 3,125 bitkoina po bloku.
BTC Halving 2024
Analizirajući istorijske obrasce Bitcoin halvinga, čini se da investitori često akumuliraju Bitcoin uoči halvinga i to upravo nekih godinu dana pre.
To bi značilo, ako pretpostavimo da je najniža cena za ovaj ciklus bila u novembru prošle godine (kada je Bitcoin dostigao minimum od oko 16.000 dolara), trenutno se pripremamo za novi vrh koji bi se desio godinu dana nakon halvinga odnosno dve godine od sada. Ova teorija zasniva se na verovanju da kretanja cena prate sličan obrazac kao prethodnih događaja.
Međutim, važno je znati da ne znači nužno da će doći do povećanja ili stagnacije cene Bitcoina. Kripto tržište je značajno sazrelo od poslednjeg halvinga 2020. godine i sada postoji daleko više kriptovaluta koje su u prvom planu korisnika.
Porast rudarske snage
Predstojeći halving će smanjiti nagrade za rudarenje za 50%, što vrši značajan finansijski pritisak na Bitcoin rudare. Ovo smanjenje nagrada tera rudare da prilagode svoje poslovanje kako bi održali profitabilnost i nastavili da održavaju blokčejn mrežu.
Kao odgovor na smanjene nagrade, rudari mogu izabrati da nadograde svoju opremu, kroz ulaganje u energetski efikasniji i moćniji hardver kako bi optimizovali svoje rudarske operacije. Koristeći najnoviju tehnologiju, rudari mogu smanjiti potrošnju energije ali i operativne troškove.

Međutim, povećani troškovi povezani sa nadogradnjom opreme i poboljšanjem energetske efikasnosti mogu nepogodno uticati na manje rudare. Ovim manjim rudarskim postrojenjima često nedostaju finansijska sredstva da se takmiče sa većim, dobro finansiranim rudarskim fondovima.
Kao rezultat toga, neki manji rudari mogu biti primorani da napuste tržište ili mogu biti primorani da se pripoje većim rudarskim postrojenjima kako bi opstali u trci za nagrade.
Pored toga, uticaj halvinga na rudare može dovesti do promena u rudarskom pejzažu, pri čemu rudari traže lokacije sa nižim troškovima energije ili povoljnijim regulatornim okruženjem. Ovo bi moglo da promeni geografsku sliku rudarskih stanica što dodatno utiče na decentralizaciju mreže.
-
 @ 26d4b5b2:96393e73
2025-05-11 21:28:47
@ 26d4b5b2:96393e73
2025-05-11 21:28:47// SPDX-License-Identifier: GPL-3.0 Contract PaidMessage( owner: Address, // who collects the fee mut message: ByteVec // last posted message ) { // ── Events ──────────────────────────────────────────────────────────────── /// Fires whenever someone pays and posts a new message event MessageSent(sender: Address, content: ByteVec)
// ── Constants ───────────────────────────────────────────────────────────── /// 0.1 ALPH in atto-ALPH const PRICE = 100000000000000000 /// Maximum allowed message length const MAX_MESSAGE_SIZE = 1024 /// Dust amount for transactions (0.001 ALPH in atto-ALPH) const DUST_AMOUNT = 1000000000000000 // ── Error codes ─────────────────────────────────────────────────────────── enum ErrorCodes { InvalidMessageSize = 0 InsufficientPayment = 1 InvalidCaller = 2 } // ── Read-only helper ────────────────────────────────────────────────────── /// Read back the current message pub fn getMessage() -> ByteVec { return message } // ── Core logic ──────────────────────────────────────────────────────────── /// Requires caller to attach ≥ `PRICE` atto-ALPH, updates message, forwards fee @using(preapprovedAssets = true, updateFields = true, payToContractOnly = false) pub fn sendMessage(newMessage: ByteVec) -> () { // 1️⃣ Check external caller checkCaller!(isAssetAddress!(callerAddress!()), ErrorCodes.InvalidCaller) // 2️⃣ Size check assert!(size!(newMessage) <= MAX_MESSAGE_SIZE, ErrorCodes.InvalidMessageSize) // 3️⃣ Payment check let paid = tokenRemaining!(callerAddress!(), ALPH) assert!(paid >= PRICE, ErrorCodes.InsufficientPayment) // 4️⃣ Update on-chain message message = newMessage // 5️⃣ Transfer exact fee to owner transferToken!(callerAddress!(), owner, ALPH, PRICE) // 6️⃣ Refund excess to caller if above dust amount let change = paid - PRICE if (change >= DUST_AMOUNT) { transferToken!(callerAddress!(), callerAddress!(), ALPH, change) } // 7️⃣ Emit event emit MessageSent(callerAddress!(), newMessage) } // ── Owner-only function ─────────────────────────────────────────────────── /// Allows owner to update the message without payment @using(updateFields = true) pub fn updateMessageByOwner(newMessage: ByteVec) -> () { // 1️⃣ Check if caller is owner checkCaller!(callerAddress!() == owner, ErrorCodes.InvalidCaller) // 2️⃣ Size check assert!(size!(newMessage) <= MAX_MESSAGE_SIZE, ErrorCodes.InvalidMessageSize) // 3️⃣ Update message message = newMessage // 4️⃣ Emit event emit MessageSent(callerAddress!(), newMessage) }}
-
 @ 26d4b5b2:96393e73
2025-05-11 21:27:27
@ 26d4b5b2:96393e73
2025-05-11 21:27:27SET ANSI_NULLS ON GO SET QUOTED_IDENTIFIER ON GO
ALTER PROCEDURE [dbo].[WALLETCONE] @TokenId NVARCHAR(255),
@InitiatingAddress NVARCHAR(255)
AS BEGIN SET NOCOUNT ON;DECLARE @TokenName NVARCHAR(255), @TableName NVARCHAR(255), @JsonPath NVARCHAR(300), @Sql NVARCHAR(MAX), @StartTime DATETIME = GETDATE(); PRINT 'Procedure started at: ' + CONVERT(NVARCHAR(30), @StartTime, 120); -- Validate inputs IF @TokenId IS NULL OR @TokenId = '' OR @InitiatingAddress IS NULL OR @InitiatingAddress = '' BEGIN PRINT 'Error: TokenId and InitiatingAddress cannot be NULL or empty'; RETURN; END -- Resolve token name SELECT @TokenName = UPPER(REPLACE(Name,' ','_')) FROM dbo.DOH_INFO_TOKENS WHERE TokenID = @TokenId; IF @TokenName IS NULL BEGIN PRINT 'Error: Invalid TokenId: ' + @TokenId; RETURN; END -- Build table name & JSON path SET @TableName = 'DOH_INFO_TRANSACTIONS_' + @TokenName; SET @JsonPath = '$."' + REPLACE(@TokenId,'"','""') + '"'; IF NOT EXISTS (SELECT 1 FROM sys.tables WHERE name = @TableName) BEGIN PRINT 'Error: Table not found: ' + @TableName; RETURN; END ---------------------------------------------------------------- -- 1) Pool Transactions Detail ---------------------------------------------------------------- SET @Sql = N' SELECT @TokenId AS token_id, t.[hash], t.initiating_address, COALESCE(p.Name,''Unknown'') AS pool_name, t.transaction_type, TRY_CAST(COALESCE(JSON_VALUE(t.gotTokens,@JsonPath),''0'') AS FLOAT) AS got_tokens, TRY_CAST(COALESCE(JSON_VALUE(t.forTokens,@JsonPath),''0'') AS FLOAT) AS for_tokens, TRY_CAST(CAST(t.ratio AS FLOAT) AS DECIMAL(38,10)) AS ratio, t.[timestamp], CASE WHEN t.transaction_type LIKE ''%BUY%'' THEN -(TRY_CAST(JSON_VALUE(t.gotTokens,@JsonPath) AS FLOAT) *TRY_CAST(CAST(t.ratio AS FLOAT) AS DECIMAL(38,10))) WHEN t.transaction_type LIKE ''%SELL%'' THEN TRY_CAST(JSON_VALUE(t.forTokens,@JsonPath) AS FLOAT) *TRY_CAST(CAST(t.ratio AS FLOAT) AS DECIMAL(38,10)) ELSE NULL END AS gain_loss FROM dbo.' + QUOTENAME(@TableName) + ' t LEFT JOIN dbo.DOH_INFO_POOLS p ON t.pool_id = p.PoolID WHERE (JSON_VALUE(t.gotTokens,@JsonPath) IS NOT NULL OR JSON_VALUE(t.forTokens,@JsonPath) IS NOT NULL) AND t.initiating_address = @InitiatingAddress AND t.pool_id IS NOT NULL;'; EXEC sp_executesql @Sql, N'@TokenId NVARCHAR(255),@InitiatingAddress NVARCHAR(255),@JsonPath NVARCHAR(300)', @TokenId,@InitiatingAddress,@JsonPath; ---------------------------------------------------------------- -- 2) Pool Transactions Summary ---------------------------------------------------------------- SET @Sql = N' SELECT COALESCE(p.Name,''Unknown'') AS pool_name, t.pool_id, COUNT(*) AS transaction_count, SUM(CASE WHEN t.transaction_type LIKE ''%BUY%'' THEN -(TRY_CAST(JSON_VALUE(t.gotTokens,@JsonPath) AS FLOAT) *TRY_CAST(CAST(t.ratio AS FLOAT) AS DECIMAL(38,10))) WHEN t.transaction_type LIKE ''%SELL%'' THEN TRY_CAST(JSON_VALUE(t.forTokens,@JsonPath) AS FLOAT) *TRY_CAST(CAST(t.ratio AS FLOAT) AS DECIMAL(38,10)) ELSE 0 END) AS total_gain_loss, AVG(CASE WHEN t.transaction_type LIKE ''%BUY%'' THEN TRY_CAST(CAST(t.ratio AS FLOAT) AS DECIMAL(38,10)) ELSE NULL END) AS avg_buy_price, AVG(CASE WHEN t.transaction_type LIKE ''%SELL%'' THEN TRY_CAST(CAST(t.ratio AS FLOAT) AS DECIMAL(38,10)) ELSE NULL END) AS avg_sell_price, SUM(CASE WHEN t.transaction_type LIKE ''%BUY%'' THEN TRY_CAST(JSON_VALUE(t.gotTokens,@JsonPath) AS FLOAT) WHEN t.transaction_type LIKE ''%SELL%'' THEN TRY_CAST(JSON_VALUE(t.forTokens,@JsonPath) AS FLOAT) ELSE 0 END) AS total_tokens_transacted FROM dbo.' + QUOTENAME(@TableName) + ' t LEFT JOIN dbo.DOH_INFO_POOLS p ON t.pool_id = p.PoolID WHERE (JSON_VALUE(t.gotTokens,@JsonPath) IS NOT NULL OR JSON_VALUE(t.forTokens,@JsonPath) IS NOT NULL) AND t.initiating_address = @InitiatingAddress AND t.pool_id IS NOT NULL GROUP BY COALESCE(p.Name,''Unknown''), t.pool_id ORDER BY total_gain_loss DESC, COALESCE(p.Name,''Unknown'') ASC;'; EXEC sp_executesql @Sql, N'@InitiatingAddress NVARCHAR(255),@JsonPath NVARCHAR(300)', @InitiatingAddress,@JsonPath; ---------------------------------------------------------------- -- 3) Non-Pool Transactions Detail (all direct txns) ---------------------------------------------------------------- SET @Sql = N' SELECT @TokenId AS token_id, t.[hash], t.initiating_address, t.receiving_address, t.transaction_type, TRY_CAST(COALESCE(JSON_VALUE(t.sent_tokens,@JsonPath),''0'') AS FLOAT) AS sent_tokens, TRY_CAST(COALESCE(JSON_VALUE(t.received_tokens,@JsonPath),''0'') AS FLOAT) AS received_tokens, TRY_CAST(CAST(t.ratio AS FLOAT) AS DECIMAL(38,10)) AS ratio, t.[timestamp], t.status FROM dbo.' + QUOTENAME(@TableName) + ' t WHERE (JSON_VALUE(t.sent_tokens,@JsonPath) IS NOT NULL OR JSON_VALUE(t.received_tokens,@JsonPath) IS NOT NULL) AND t.initiating_address = @InitiatingAddress AND (t.pool_id IS NULL OR t.pool_id = '''' OR LOWER(t.status) = ''no pool'');'; EXEC sp_executesql @Sql, N'@TokenId NVARCHAR(255),@InitiatingAddress NVARCHAR(255),@JsonPath NVARCHAR(300)', @TokenId,@InitiatingAddress,@JsonPath; ---------------------------------------------------------------- -- 4) Non-Pool Sent Summary (you → others) ---------------------------------------------------------------- SET @Sql = N' SELECT t.initiating_address AS sender_address, t.receiving_address AS receiver_address, COUNT(*) AS send_count, SUM(TRY_CAST(JSON_VALUE(t.sent_tokens,@JsonPath) AS FLOAT)) AS total_sent, MIN(t.[timestamp]) AS first_sent, MAX(t.[timestamp]) AS last_sent FROM dbo.' + QUOTENAME(@TableName) + ' t WHERE JSON_VALUE(t.sent_tokens,@JsonPath) IS NOT NULL AND t.initiating_address = @InitiatingAddress AND (t.pool_id IS NULL OR t.pool_id = '''' OR LOWER(t.status) = ''no pool'') GROUP BY t.initiating_address, t.receiving_address ORDER BY send_count DESC, total_sent DESC;'; EXEC sp_executesql @Sql, N'@InitiatingAddress NVARCHAR(255),@JsonPath NVARCHAR(300)', @InitiatingAddress,@JsonPath; ---------------------------------------------------------------- -- 5) Non-Pool Received Summary (others → you, no self-sends) ---------------------------------------------------------------- SET @Sql = N' SELECT t.initiating_address AS sender_address, @InitiatingAddress AS receiver_address, COUNT(*) AS send_count, SUM(TRY_CAST(JSON_VALUE(t.received_tokens,@JsonPath) AS FLOAT)) AS total_sent, MIN(t.[timestamp]) AS first_sent, MAX(t.[timestamp]) AS last_sent FROM dbo.' + QUOTENAME(@TableName) + ' t WHERE JSON_VALUE(t.received_tokens,@JsonPath) IS NOT NULL AND t.receiving_address = @InitiatingAddress AND t.initiating_address <> @InitiatingAddress AND (t.pool_id IS NULL OR t.pool_id = '''' OR LOWER(t.status) = ''no pool'') GROUP BY t.initiating_address ORDER BY send_count DESC, total_sent DESC;'; EXEC sp_executesql @Sql, N'@InitiatingAddress NVARCHAR(255),@JsonPath NVARCHAR(300)', @InitiatingAddress,@JsonPath; ---------------------------------------------------------------- -- 6) Non-Pool Received Detail (every incoming txn) ---------------------------------------------------------------- SET @Sql = N' SELECT @TokenId AS token_id, t.[hash], t.initiating_address AS sender_address, t.receiving_address AS receiver_address, t.transaction_type, TRY_CAST(COALESCE(JSON_VALUE(t.sent_tokens,@JsonPath),''0'') AS FLOAT) AS sent_tokens, TRY_CAST(COALESCE(JSON_VALUE(t.received_tokens,@JsonPath),''0'') AS FLOAT) AS received_tokens, TRY_CAST(CAST(t.ratio AS FLOAT) AS DECIMAL(38,10)) AS ratio, t.[timestamp], t.status FROM dbo.' + QUOTENAME(@TableName) + ' t WHERE JSON_VALUE(t.received_tokens,@JsonPath) IS NOT NULL AND t.receiving_address = @InitiatingAddress AND (t.pool_id IS NULL OR t.pool_id = '''' OR LOWER(t.status) = ''no pool'') ORDER BY t.[timestamp] DESC;'; EXEC sp_executesql @Sql, N'@TokenId NVARCHAR(255),@InitiatingAddress NVARCHAR(255),@JsonPath NVARCHAR(300)', @TokenId,@InitiatingAddress,@JsonPath; ---------------------------------------------------------------- -- 7) Net Token Position Summary ---------------------------------------------------------------- SET @Sql = N' SELECT @InitiatingAddress AS wallet, SUM(TRY_CAST(JSON_VALUE(t.received_tokens,@JsonPath) AS FLOAT)) - SUM(TRY_CAST(JSON_VALUE(t.sent_tokens,@JsonPath) AS FLOAT)) AS net_token_position, (SUM(TRY_CAST(JSON_VALUE(t.received_tokens,@JsonPath) AS FLOAT)) - SUM(TRY_CAST(JSON_VALUE(t.sent_tokens,@JsonPath) AS FLOAT))) * AVG(CAST(t.ratio AS FLOAT)) AS estimated_net_value FROM dbo.' + QUOTENAME(@TableName) + ' t WHERE (JSON_VALUE(t.sent_tokens,@JsonPath) IS NOT NULL OR JSON_VALUE(t.received_tokens,@JsonPath) IS NOT NULL) AND (t.initiating_address = @InitiatingAddress OR t.receiving_address = @InitiatingAddress) AND (t.pool_id IS NULL OR t.pool_id = '''' OR LOWER(t.status) = ''no pool''); '; EXEC sp_executesql @Sql, N'@InitiatingAddress NVARCHAR(255),@JsonPath NVARCHAR(300)', @InitiatingAddress,@JsonPath; ---------------------------------------------------------------- -- 8) Unique Counterparty Count ---------------------------------------------------------------- SET @Sql = N' SELECT COUNT(DISTINCT CASE WHEN t.initiating_address = @InitiatingAddress THEN t.receiving_address ELSE t.initiating_address END ) AS unique_counterparties FROM dbo.' + QUOTENAME(@TableName) + ' t WHERE (t.initiating_address = @InitiatingAddress OR t.receiving_address = @InitiatingAddress) AND (t.pool_id IS NULL OR t.pool_id = '''' OR LOWER(t.status) = ''no pool''); '; EXEC sp_executesql @Sql, N'@InitiatingAddress NVARCHAR(255)', @InitiatingAddress; ---------------------------------------------------------------- -- 9) Token Activity Timeline (monthly) ---------------------------------------------------------------- SET @Sql = N' SELECT FORMAT(t.[timestamp],''yyyy-MM'') AS month, COUNT(*) AS transaction_count, SUM( COALESCE(TRY_CAST(JSON_VALUE(t.sent_tokens,@JsonPath) AS FLOAT),0) + COALESCE(TRY_CAST(JSON_VALUE(t.received_tokens,@JsonPath) AS FLOAT),0) ) AS total_volume FROM dbo.' + QUOTENAME(@TableName) + ' t WHERE (t.initiating_address = @InitiatingAddress OR t.receiving_address = @InitiatingAddress) AND (t.pool_id IS NULL OR t.pool_id = '''' OR LOWER(t.status) = ''no pool'') GROUP BY FORMAT(t.[timestamp],''yyyy-MM'') ORDER BY month;'; EXEC sp_executesql @Sql, N'@InitiatingAddress NVARCHAR(255),@JsonPath NVARCHAR(300)', @InitiatingAddress,@JsonPath; ---------------------------------------------------------------- -- 10) Top Volume Counterparties ---------------------------------------------------------------- SET @Sql = N' SELECT CASE WHEN t.initiating_address = @InitiatingAddress THEN t.receiving_address ELSE t.initiating_address END AS counterparty, COUNT(*) AS tx_count, SUM( COALESCE(TRY_CAST(JSON_VALUE(t.sent_tokens,@JsonPath) AS FLOAT),0) + COALESCE(TRY_CAST(JSON_VALUE(t.received_tokens,@JsonPath) AS FLOAT),0) ) AS total_volume FROM dbo.' + QUOTENAME(@TableName) + ' t WHERE (t.initiating_address = @InitiatingAddress OR t.receiving_address = @InitiatingAddress) AND (t.pool_id IS NULL OR t.pool_id = '''' OR LOWER(t.status) = ''no pool'') GROUP BY CASE WHEN t.initiating_address = @InitiatingAddress THEN t.receiving_address ELSE t.initiating_address END ORDER BY total_volume DESC;'; EXEC sp_executesql @Sql, N'@InitiatingAddress NVARCHAR(255),@JsonPath NVARCHAR(300)', @InitiatingAddress,@JsonPath; ---------------------------------------------------------------- -- 11) Largest Single Transactions ---------------------------------------------------------------- -- 11a) Largest Received SET @Sql = N' SELECT TOP 1 * FROM dbo.' + QUOTENAME(@TableName) + ' t WHERE t.receiving_address = @InitiatingAddress AND JSON_VALUE(t.received_tokens,@JsonPath) IS NOT NULL AND (t.pool_id IS NULL OR t.pool_id = '''' OR LOWER(t.status) = ''no pool'') ORDER BY TRY_CAST(JSON_VALUE(t.received_tokens,@JsonPath) AS FLOAT) DESC;'; EXEC sp_executesql @Sql, N'@InitiatingAddress NVARCHAR(255),@JsonPath NVARCHAR(300)', @InitiatingAddress,@JsonPath; -- 11b) Largest Sent SET @Sql = N' SELECT TOP 1 * FROM dbo.' + QUOTENAME(@TableName) + ' t WHERE t.initiating_address = @InitiatingAddress AND JSON_VALUE(t.sent_tokens,@JsonPath) IS NOT NULL AND (t.pool_id IS NULL OR t.pool_id = '''' OR LOWER(t.status) = ''no pool'') ORDER BY TRY_CAST(JSON_VALUE(t.sent_tokens,@JsonPath) AS FLOAT) DESC;'; EXEC sp_executesql @Sql, N'@InitiatingAddress NVARCHAR(255),@JsonPath NVARCHAR(300)', @InitiatingAddress,@JsonPath; ---------------------------------------------------------------- -- 12) SNIPER: Transactions before first pool txn ---------------------------------------------------------------- SET @Sql = N' SELECT COUNT(*) AS SNIPER FROM dbo.' + QUOTENAME(@TableName) + ' t WHERE (t.pool_id IS NULL OR t.pool_id = '''' OR LOWER(t.status) = ''no pool'') AND (t.initiating_address = @InitiatingAddress OR t.receiving_address = @InitiatingAddress) AND t.[timestamp] < ( SELECT MIN(tp.[timestamp]) FROM dbo.' + QUOTENAME(@TableName) + ' tp WHERE tp.initiating_address = @InitiatingAddress AND tp.pool_id IS NOT NULL );'; EXEC sp_executesql @Sql, N'@InitiatingAddress NVARCHAR(255),@JsonPath NVARCHAR(300)', @InitiatingAddress,@JsonPath; PRINT 'Procedure completed at: ' + CONVERT(NVARCHAR(30), GETDATE(), 120) + ', duration (ms): ' + CAST(DATEDIFF(MILLISECOND, @StartTime, GETDATE()) AS NVARCHAR(10));END GO
-
 @ a95c6243:d345522c
2025-03-11 10:22:36
@ a95c6243:d345522c
2025-03-11 10:22:36«Wir brauchen eine digitale Brandmauer gegen den Faschismus», schreibt der Chaos Computer Club (CCC) auf seiner Website. Unter diesem Motto präsentierte er letzte Woche einen Forderungskatalog, mit dem sich 24 Organisationen an die kommende Bundesregierung wenden. Der Koalitionsvertrag müsse sich daran messen lassen, verlangen sie.
In den drei Kategorien «Bekenntnis gegen Überwachung», «Schutz und Sicherheit für alle» sowie «Demokratie im digitalen Raum» stellen die Unterzeichner, zu denen auch Amnesty International und Das NETTZ gehören, unter anderem die folgenden «Mindestanforderungen»:
- Verbot biometrischer Massenüberwachung des öffentlichen Raums sowie der ungezielten biometrischen Auswertung des Internets.
- Anlasslose und massenhafte Vorratsdatenspeicherung wird abgelehnt.
- Automatisierte Datenanalysen der Informationsbestände der Strafverfolgungsbehörden sowie jede Form von Predictive Policing oder automatisiertes Profiling von Menschen werden abgelehnt.
- Einführung eines Rechts auf Verschlüsselung. Die Bundesregierung soll sich dafür einsetzen, die Chatkontrolle auf europäischer Ebene zu verhindern.
- Anonyme und pseudonyme Nutzung des Internets soll geschützt und ermöglicht werden.
- Bekämpfung «privaten Machtmissbrauchs von Big-Tech-Unternehmen» durch durchsetzungsstarke, unabhängige und grundsätzlich föderale Aufsichtsstrukturen.
- Einführung eines digitalen Gewaltschutzgesetzes, unter Berücksichtigung «gruppenbezogener digitaler Gewalt» und die Förderung von Beratungsangeboten.
- Ein umfassendes Förderprogramm für digitale öffentliche Räume, die dezentral organisiert und quelloffen programmiert sind, soll aufgelegt werden.
Es sei ein Irrglaube, dass zunehmende Überwachung einen Zugewinn an Sicherheit darstelle, ist eines der Argumente der Initiatoren. Sicherheit erfordere auch, dass Menschen anonym und vertraulich kommunizieren können und ihre Privatsphäre geschützt wird.
Gesunde digitale Räume lebten auch von einem demokratischen Diskurs, lesen wir in dem Papier. Es sei Aufgabe des Staates, Grundrechte zu schützen. Dazu gehöre auch, Menschenrechte und demokratische Werte, insbesondere Freiheit, Gleichheit und Solidarität zu fördern sowie den Missbrauch von Maßnahmen, Befugnissen und Infrastrukturen durch «die Feinde der Demokratie» zu verhindern.
Man ist geneigt zu fragen, wo denn die Autoren «den Faschismus» sehen, den es zu bekämpfen gelte. Die meisten der vorgetragenen Forderungen und Argumente finden sicher breite Unterstützung, denn sie beschreiben offenkundig gängige, kritikwürdige Praxis. Die Aushebelung der Privatsphäre, der Redefreiheit und anderer Grundrechte im Namen der Sicherheit wird bereits jetzt massiv durch die aktuellen «demokratischen Institutionen» und ihre «durchsetzungsstarken Aufsichtsstrukturen» betrieben.
Ist «der Faschismus» also die EU und ihre Mitgliedsstaaten? Nein, die «faschistische Gefahr», gegen die man eine digitale Brandmauer will, kommt nach Ansicht des CCC und seiner Partner aus den Vereinigten Staaten. Private Überwachung und Machtkonzentration sind dabei weltweit schon lange Realität, jetzt endlich müssen sie jedoch bekämpft werden. In dem Papier heißt es:
«Die willkürliche und antidemokratische Machtausübung der Tech-Oligarchen um Präsident Trump erfordert einen Paradigmenwechsel in der deutschen Digitalpolitik. (...) Die aktuellen Geschehnisse in den USA zeigen auf, wie Datensammlungen und -analyse genutzt werden können, um einen Staat handstreichartig zu übernehmen, seine Strukturen nachhaltig zu beschädigen, Widerstand zu unterbinden und marginalisierte Gruppen zu verfolgen.»
Wer auf der anderen Seite dieser Brandmauer stehen soll, ist also klar. Es sind die gleichen «Feinde unserer Demokratie», die seit Jahren in diese Ecke gedrängt werden. Es sind die gleichen Andersdenkenden, Regierungskritiker und Friedensforderer, die unter dem großzügigen Dach des Bundesprogramms «Demokratie leben» einem «kontinuierlichen Echt- und Langzeitmonitoring» wegen der Etikettierung «digitaler Hass» unterzogen werden.
Dass die 24 Organisationen praktisch auch die Bekämpfung von Google, Microsoft, Apple, Amazon und anderen fordern, entbehrt nicht der Komik. Diese fallen aber sicher unter das Stichwort «Machtmissbrauch von Big-Tech-Unternehmen». Gleichzeitig verlangen die Lobbyisten implizit zum Beispiel die Förderung des Nostr-Netzwerks, denn hier finden wir dezentral organisierte und quelloffen programmierte digitale Räume par excellence, obendrein zensurresistent. Das wiederum dürfte in der Politik weniger gut ankommen.
[Titelbild: Pixabay]
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 266815e0:6cd408a5
2025-04-15 06:58:14
@ 266815e0:6cd408a5
2025-04-15 06:58:14Its been a little over a year since NIP-90 was written and merged into the nips repo and its been a communication mess.
Every DVM implementation expects the inputs in slightly different formats, returns the results in mostly the same format and there are very few DVM actually running.
NIP-90 is overloaded
Why does a request for text translation and creating bitcoin OP_RETURNs share the same input
itag? and why is there anoutputtag on requests when only one of them will return an output?Each DVM request kind is for requesting completely different types of compute with diffrent input and output requirements, but they are all using the same spec that has 4 different types of inputs (
text,url,event,job) and an undefined number ofoutputtypes.Let me show a few random DVM requests and responses I found on
wss://relay.damus.ioto demonstrate what I mean:This is a request to translate an event to English
json { "kind": 5002, "content": "", "tags": [ // NIP-90 says there can be multiple inputs, so how would a DVM handle translatting multiple events at once? [ "i", "<event-id>", "event" ], [ "param", "language", "en" ], // What other type of output would text translations be? image/jpeg? [ "output", "text/plain" ], // Do we really need to define relays? cant the DVM respond on the relays it saw the request on? [ "relays", "wss://relay.unknown.cloud/", "wss://nos.lol/" ] ] }This is a request to generate text using an LLM model
json { "kind": 5050, // Why is the content empty? wouldn't it be better to have the prompt in the content? "content": "", "tags": [ // Why use an indexable tag? are we ever going to lookup prompts? // Also the type "prompt" isn't in NIP-90, this should probably be "text" [ "i", "What is the capital of France?", "prompt" ], [ "p", "c4878054cff877f694f5abecf18c7450f4b6fdf59e3e9cb3e6505a93c4577db2" ], [ "relays", "wss://relay.primal.net" ] ] }This is a request for content recommendation
json { "kind": 5300, "content": "", "tags": [ // Its fine ignoring this param, but what if the client actually needs exactly 200 "results" [ "param", "max_results", "200" ], // The spec never mentions requesting content for other users. // If a DVM didn't understand this and responded to this request it would provide bad data [ "param", "user", "b22b06b051fd5232966a9344a634d956c3dc33a7f5ecdcad9ed11ddc4120a7f2" ], [ "relays", "wss://relay.primal.net", ], [ "p", "ceb7e7d688e8a704794d5662acb6f18c2455df7481833dd6c384b65252455a95" ] ] }This is a request to create a OP_RETURN message on bitcoin
json { "kind": 5901, // Again why is the content empty when we are sending human readable text? "content": "", "tags": [ // and again, using an indexable tag on an input that will never need to be looked up ["i", "09/01/24 SEC Chairman on the brink of second ETF approval", "text"] ] }My point isn't that these event schema's aren't understandable but why are they using the same schema? each use-case is different but are they all required to use the same
itag format as input and could support all 4 types of inputs.Lack of libraries
With all these different types of inputs, params, and outputs its verify difficult if not impossible to build libraries for DVMs
If a simple text translation request can have an
eventortextas inputs, apayment-requiredstatus at any point in the flow, partial results, or responses from 10+ DVMs whats the best way to build a translation library for other nostr clients to use?And how do I build a DVM framework for the server side that can handle multiple inputs of all four types (
url,text,event,job) and clients are sending all the requests in slightly differently.Supporting payments is impossible
The way NIP-90 is written there isn't much details about payments. only a
payment-requiredstatus and a genericamounttagBut the way things are now every DVM is implementing payments differently. some send a bolt11 invoice, some expect the client to NIP-57 zap the request event (or maybe the status event), and some even ask for a subscription. and we haven't even started implementing NIP-61 nut zaps or cashu A few are even formatting the
amountnumber wrong or denominating it in sats and not mili-satsBuilding a client or a library that can understand and handle all of these payment methods is very difficult. for the DVM server side its worse. A DVM server presumably needs to support all 4+ types of payments if they want to get the most sats for their services and support the most clients.
All of this is made even more complicated by the fact that a DVM can ask for payment at any point during the job process. this makes sense for some types of compute, but for others like translations or user recommendation / search it just makes things even more complicated.
For example, If a client wanted to implement a timeline page that showed the notes of all the pubkeys on a recommended list. what would they do when the selected DVM asks for payment at the start of the job? or at the end? or worse, only provides half the pubkeys and asks for payment for the other half. building a UI that could handle even just two of these possibilities is complicated.
NIP-89 is being abused
NIP-89 is "Recommended Application Handlers" and the way its describe in the nips repo is
a way to discover applications that can handle unknown event-kinds
Not "a way to discover everything"
If I wanted to build an application discovery app to show all the apps that your contacts use and let you discover new apps then it would have to filter out ALL the DVM advertisement events. and that's not just for making requests from relays
If the app shows the user their list of "recommended applications" then it either has to understand that everything in the 5xxx kind range is a DVM and to show that is its own category or show a bunch of unknown "favorites" in the list which might be confusing for the user.
In conclusion
My point in writing this article isn't that the DVMs implementations so far don't work, but that they will never work well because the spec is too broad. even with only a few DVMs running we have already lost interoperability.
I don't want to be completely negative though because some things have worked. the "DVM feeds" work, although they are limited to a single page of results. text / event translations also work well and kind
5970Event PoW delegation could be cool. but if we want interoperability, we are going to need to change a few things with NIP-90I don't think we can (or should) abandon NIP-90 entirely but it would be good to break it up into small NIPs or specs. break each "kind" of DVM request out into its own spec with its own definitions for expected inputs, outputs and flow.
Then if we have simple, clean definitions for each kind of compute we want to distribute. we might actually see markets and services being built and used.
-
 @ bf47c19e:c3d2573b
2025-05-11 18:20:25
@ bf47c19e:c3d2573b
2025-05-11 18:20:2505.04.2022. / Autor: Aleksandar Matanović
Većinu ljudi ka Bitkoinu privuče mogućnost brze zarade. Gledajući istorijsko kretanje cene, deluje im da je bilo izuzetno lako obogatiti se uz odgovarajući tajming kupovine i prodaje. Naravno, u praksi stvari umeju dosta drugačije da izgledaju. Jednom kada se uđe, najjači poriv da se kupuje bude baš kad je cena najviša i euforija na vrhuncu, dok pad cene uglavnom uzrokuje paničnu prodaju baš u najgorem trenutku. Novajlije se tu retko odmah snađu.

Neki posle gubitaka i razočarenja kompletno napuste ceo kripto ekosistem misleći da je problem u tržištu, a ne u njihovoj naivnosti i brzopletosti. Drugi ostanu, pa se ili izvešte u trgovanju ili počnu da rudare ili se zaljube u tehnologiju ili nauče da budu strpljivi ili nađi neki svoj put u ovoj industriji. Ipak, mnogima, neretko i pravim veteranima koji su već godinama tu, prečesto promaknu najbitnije karakteristike Bitkoina.
Zamrzavanje bankovnih računa
Nažalost, ponekad su potrebne teške situacije da bi se prave vrednosti nečega shvatile. Ne kaže se uzalud: „Na muci se poznaju junaci“. U poslednjih mesec-dva svedoci smo događaja za koje smo mislili, ili smo se barem nadali da nisu mogući. Najpre protesti u Kanadi i reakcija „demokratske“ vlasti koja je bila tako oštra, da je se ni najveći diktatori ne bi postideli. Zatim i nešto mnogo gore, a to je rat u Ukrajini.
Ne ulazeći u to ko je za šta kriv, jer dovoljno se njih tom tematikom bavi, činjenica da je su neki Kanađani, Rusi i Ukrajinci praktično preko noći postali odsečeni od finansijskog sistema od kojeg u nekoj meri zavise. U Kanadi je vlada nepodobnima zamrzavala bankovne račune, Rusima su uglavnom spolja „isekli“ mnoge novčane tokove na način da, kao što to obično i biva, najviše trpe građani koji ništa nikome nisu skrivili, a šta tek reći za Ukrajince koji su, bez dileme, najgore prošli.

Prava vrednost Bitkoina
Neki često kažu da Bitkoin nema upotrebnu vrednost i da služi samo za špekulacije. Međutim, u situaciji kada je račun u banci zamrznut zbog učešća u protestima, nije loše imati neku vrednost koju je nemoguće zamrznuti, a vrlo lako se može unovčiti po potrebi. Kada više ne rade PayPal, VISA, MasterCard, SWIFT… a imate poslovnog partnera koji treba nešto da vam uplati ili rođaka koji treba da vam pošalje novac, dosta je koristan novac koji niko ne može da zaustavi i za čije korišćenje ničija dozvola nije potrebna Na kraju, ako padaju bombe i treba da bežite glavom bez obzira, imati imovinu koja je u digitalnom obliku i koja ide svuda sa vama, a ne mora da se nosi, je zlata vredno. Ili možda bolje reći „digitalnog zlata (kako neki zovu Bitkoin) vredno“.
Najbitnije karakteristika Bitkoina mnogima promiču, jer srećom mnogi nisu bili u situaciji da im te njegove karakteristike budu bitne. Te karakteristike su neotuđivost, dostupnost i otpornost na sve vrste cenzure.
Nikada u istoriji nismo imali mogućnost da novac ili neku drugu vrednost sa par klikova prenesemo na drugi kraj sveta, a da ne moramo nikoga da pitamo za dozvolu da to uradimo. I dok god standardni kanali rade, teško razumemo pravu vrednost koju ta mogućnost pruža.

„Problem je što je cena mnogo volatilna, pa je zato neupotrebljiv za bilo šta ozbiljno“, često se može čuti. Da, problem je dok ne dođete u situaciju da možete sa sobom poneti nešto ili ništa. Problem je dok niste suočeni sa izborom da novac pošaljete tako ili nikako. Onda par procenata promene cene na dnevnom nivou ne znači ništa jer rešavate problem koji nikako drugačije ne možete rešiti. I postaje nebitno da li ste ga kupili u savršenom trenutku ili ste možda mogli i bolje da prođete.
-
 @ a95c6243:d345522c
2025-03-04 09:40:50
@ a95c6243:d345522c
2025-03-04 09:40:50Die «Eliten» führen bereits groß angelegte Pilotprojekte für eine Zukunft durch, die sie wollen und wir nicht. Das schreibt der OffGuardian in einem Update zum Thema «EU-Brieftasche für die digitale Identität». Das Portal weist darauf hin, dass die Akteure dabei nicht gerade zimperlich vorgehen und auch keinen Hehl aus ihren Absichten machen. Transition News hat mehrfach darüber berichtet, zuletzt hier und hier.
Mit der EU Digital Identity Wallet (EUDI-Brieftasche) sei eine einzige von der Regierung herausgegebene App geplant, die Ihre medizinischen Daten, Beschäftigungsdaten, Reisedaten, Bildungsdaten, Impfdaten, Steuerdaten, Finanzdaten sowie (potenziell) Kopien Ihrer Unterschrift, Fingerabdrücke, Gesichtsscans, Stimmproben und DNA enthält. So fasst der OffGuardian die eindrucksvolle Liste möglicher Einsatzbereiche zusammen.
Auch Dokumente wie der Personalausweis oder der Führerschein können dort in elektronischer Form gespeichert werden. Bis 2026 sind alle EU-Mitgliedstaaten dazu verpflichtet, Ihren Bürgern funktionierende und frei verfügbare digitale «Brieftaschen» bereitzustellen.
Die Menschen würden diese App nutzen, so das Portal, um Zahlungen vorzunehmen, Kredite zu beantragen, ihre Steuern zu zahlen, ihre Rezepte abzuholen, internationale Grenzen zu überschreiten, Unternehmen zu gründen, Arzttermine zu buchen, sich um Stellen zu bewerben und sogar digitale Verträge online zu unterzeichnen.
All diese Daten würden auf ihrem Mobiltelefon gespeichert und mit den Regierungen von neunzehn Ländern (plus der Ukraine) sowie über 140 anderen öffentlichen und privaten Partnern ausgetauscht. Von der Deutschen Bank über das ukrainische Ministerium für digitalen Fortschritt bis hin zu Samsung Europe. Unternehmen und Behörden würden auf diese Daten im Backend zugreifen, um «automatisierte Hintergrundprüfungen» durchzuführen.
Der Bundesverband der Verbraucherzentralen und Verbraucherverbände (VZBV) habe Bedenken geäußert, dass eine solche App «Risiken für den Schutz der Privatsphäre und der Daten» berge, berichtet das Portal. Die einzige Antwort darauf laute: «Richtig, genau dafür ist sie ja da!»
Das alles sei keine Hypothese, betont der OffGuardian. Es sei vielmehr «Potential». Damit ist ein EU-Projekt gemeint, in dessen Rahmen Dutzende öffentliche und private Einrichtungen zusammenarbeiten, «um eine einheitliche Vision der digitalen Identität für die Bürger der europäischen Länder zu definieren». Dies ist nur eines der groß angelegten Pilotprojekte, mit denen Prototypen und Anwendungsfälle für die EUDI-Wallet getestet werden. Es gibt noch mindestens drei weitere.
Den Ball der digitalen ID-Systeme habe die Covid-«Pandemie» über die «Impfpässe» ins Rollen gebracht. Seitdem habe das Thema an Schwung verloren. Je näher wir aber der vollständigen Einführung der EUid kämen, desto mehr Propaganda der Art «Warum wir eine digitale Brieftasche brauchen» könnten wir in den Mainstream-Medien erwarten, prognostiziert der OffGuardian. Vielleicht müssten wir schon nach dem nächsten großen «Grund», dem nächsten «katastrophalen katalytischen Ereignis» Ausschau halten. Vermutlich gebe es bereits Pläne, warum die Menschen plötzlich eine digitale ID-Brieftasche brauchen würden.
Die Entwicklung geht jedenfalls stetig weiter in genau diese Richtung. Beispielsweise hat Jordanien angekündigt, die digitale biometrische ID bei den nächsten Wahlen zur Verifizierung der Wähler einzuführen. Man wolle «den Papierkrieg beenden und sicherstellen, dass die gesamte Kette bis zu den nächsten Parlamentswahlen digitalisiert wird», heißt es. Absehbar ist, dass dabei einige Wahlberechtigte «auf der Strecke bleiben» werden, wie im Fall von Albanien geschehen.
Derweil würden die Briten gerne ihre Privatsphäre gegen Effizienz eintauschen, behauptet Tony Blair. Der Ex-Premier drängte kürzlich erneut auf digitale Identitäten und Gesichtserkennung. Blair ist Gründer einer Denkfabrik für globalen Wandel, Anhänger globalistischer Technokratie und «moderner Infrastruktur».
Abschließend warnt der OffGuardian vor der Illusion, Trump und Musk würden den US-Bürgern «diesen Schlamassel ersparen». Das Department of Government Efficiency werde sich auf die digitale Identität stürzen. Was könne schließlich «effizienter» sein als eine einzige App, die für alles verwendet wird? Der Unterschied bestehe nur darin, dass die US-Version vielleicht eher privat als öffentlich sei – sofern es da überhaupt noch einen wirklichen Unterschied gebe.
[Titelbild: Screenshot OffGuardian]
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a95c6243:d345522c
2025-03-01 10:39:35
@ a95c6243:d345522c
2025-03-01 10:39:35Ständige Lügen und Unterstellungen, permanent falsche Fürsorge \ können Bausteine von emotionaler Manipulation sein. Mit dem Zweck, \ Macht und Kontrolle über eine andere Person auszuüben. \ Apotheken Umschau
Irgendetwas muss passiert sein: «Gaslighting» ist gerade Thema in vielen Medien. Heute bin ich nach längerer Zeit mal wieder über dieses Stichwort gestolpert. Das war in einem Artikel von Norbert Häring über Manipulationen des Deutschen Wetterdienstes (DWD). In diesem Fall ging es um eine Pressemitteilung vom Donnerstag zum «viel zu warmen» Winter 2024/25.
Häring wirft der Behörde vor, dreist zu lügen und Dinge auszulassen, um die Klimaangst wach zu halten. Was der Leser beim DWD nicht erfahre, sei, dass dieser Winter kälter als die drei vorangegangenen und kälter als der Durchschnitt der letzten zehn Jahre gewesen sei. Stattdessen werde der falsche Eindruck vermittelt, es würde ungebremst immer wärmer.
Wem also der zu Ende gehende Winter eher kalt vorgekommen sein sollte, mit dessen Empfinden stimme wohl etwas nicht. Das jedenfalls wolle der DWD uns einreden, so der Wirtschaftsjournalist. Und damit sind wir beim Thema Gaslighting.
Als Gaslighting wird eine Form psychischer Manipulation bezeichnet, mit der die Opfer desorientiert und zutiefst verunsichert werden, indem ihre eigene Wahrnehmung als falsch bezeichnet wird. Der Prozess führt zu Angst und Realitätsverzerrung sowie zur Zerstörung des Selbstbewusstseins. Die Bezeichnung kommt von dem britischen Theaterstück «Gas Light» aus dem Jahr 1938, in dem ein Mann mit grausamen Psychotricks seine Frau in den Wahnsinn treibt.
Damit Gaslighting funktioniert, muss das Opfer dem Täter vertrauen. Oft wird solcher Psychoterror daher im privaten oder familiären Umfeld beschrieben, ebenso wie am Arbeitsplatz. Jedoch eignen sich die Prinzipien auch perfekt zur Manipulation der Massen. Vermeintliche Autoritäten wie Ärzte und Wissenschaftler, oder «der fürsorgliche Staat» und Institutionen wie die UNO oder die WHO wollen uns doch nichts Böses. Auch Staatsmedien, Faktenchecker und diverse NGOs wurden zu «vertrauenswürdigen Quellen» erklärt. Das hat seine Wirkung.
Warum das Thema Gaslighting derzeit scheinbar so populär ist, vermag ich nicht zu sagen. Es sind aber gerade in den letzten Tagen und Wochen auffällig viele Artikel dazu erschienen, und zwar nicht nur von Psychologen. Die Frankfurter Rundschau hat gleich mehrere publiziert, und Anwälte interessieren sich dafür offenbar genauso wie Apotheker.
Die Apotheken Umschau machte sogar auf «Medical Gaslighting» aufmerksam. Davon spreche man, wenn Mediziner Symptome nicht ernst nähmen oder wenn ein gesundheitliches Problem vom behandelnden Arzt «schnöde heruntergespielt» oder abgetan würde. Kommt Ihnen das auch irgendwie bekannt vor? Der Begriff sei allerdings irreführend, da er eine manipulierende Absicht unterstellt, die «nicht gewährleistet» sei.
Apropos Gaslighting: Die noch amtierende deutsche Bundesregierung meldete heute, es gelte, «weiter [sic!] gemeinsam daran zu arbeiten, einen gerechten und dauerhaften Frieden für die Ukraine zu erreichen». Die Ukraine, wo sich am Montag «der völkerrechtswidrige Angriffskrieg zum dritten Mal jährte», verteidige ihr Land und «unsere gemeinsamen Werte».
Merken Sie etwas? Das Demokratieverständnis mag ja tatsächlich inzwischen in beiden Ländern ähnlich traurig sein. Bezüglich Friedensbemühungen ist meine Wahrnehmung jedoch eine andere. Das muss an meinem Gedächtnis liegen.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 8173f6e1:e488ac0f
2025-05-11 21:23:06
@ 8173f6e1:e488ac0f
2025-05-11 21:23:06TESTNOTEBIN2
-
 @ bf47c19e:c3d2573b
2025-05-11 18:19:48
@ bf47c19e:c3d2573b
2025-05-11 18:19:4825.08.2020 / Autor: Marko Matanović
Istorija rudarenja bitkoina počinje ne toliko davne 2009. godine nastankom Bitkoin-a, odnosno od nastanka blokčejna kao tehnologije. U Satošijevom whitepaper-u spominje se pojam Proof-of-Work (PoW). U ovom sada već istorijskom dokumentu koji objašnjava funkcionisanje Bitkoin-a navodi se da će se Proof-of-Work sistem koristiti za validaciju blokova u Bitkoin blokčejnu (procesuiranje transakcija), a da bi blok bio “potvrđen” potrebno je da se izdvoji određena procesorska snaga. U suštini Proof-of-Work obezbeđuje sigurnost blokčejna tako što zahteva od korisnika da uloži odredjenu količinu rada kako bi bio nagradjen i omogućava dodavanje novih validnih transakcija u blok.
Da bismo poslali transakciju na Bitkoin mreži potrebno je da platimo određeni transaction fee, tj. naknadu za obradu i potvrđivanje same transakcije. Upravo ovaj transaction fee se distribuira rudarima kao podsticaj da rade svoj posao u najboljem interesu i po utvrđenim pravilima sistema, odnosno da koriste svoj hardver radi potvrđivanja (naših) transakcija na mreži. Transakcije sa većim izdvojenim transaction fee-jem će biti brže potvrđene na mreži jer će baš ta transakcija rudarima biti isplativija za potvrđivanje. Osim ove vrste transakcija rudari dobijaju i određenu nagradu za svaki potvrđeni blok.
Trenutni block reward je 6.25 BTC-a po potvrđenom bloku. Ovaj iznos se deli među svim rudarima na mreži proporcionalno njihovom učinku, što znači da što je više rudara na mreži to je njihova pojedinačna nagrada manja jer je veća konkurencija. Sem toga što se nagrada smanjuje sa većom konkurencijom povećava se i težina rudarenja. Nagrada za Bitkoin se smanjuje na određenom broju izrudarenih blokova i svaki put je nova nagrada dva puta manja od prethodne. Ovo je u kripto zajednici poznatije kao “Bitcoin halving” koji se odigrava otprilike na svake četiri godine, sa ciljem da svaki put upola umanji inflaciju samog bitkoina kako bi održao/povećao svoju vrednost.
 Cene Bitkoina i nagrade po bloku
Cene Bitkoina i nagrade po blokuIstorija rudarenja bitkoina se može podeliti u nekoliko era koje prate razvoj kripto industrije kao celine. Ove ere se razlikuju po hardveru koji se koristio za rudarenja. Ukoliko se pitate zašto je uopšte bilo potrebno menjati, odnosno pojačavati hardver koji se koristi – razlog je povećanje težine kopanja usled popularizacije kriptovaluta i rudarenja kriptovaluta tokom vremena. Svake godine bio je potreban sve jači i bolji hardver kako bi se rudarenje isplatilo, prvenstveno jer je konkurencija (bila) sve veća, i samim tim više učesnika deli nagradu koja je posledično manja. To uglavnom znači da nam treba jači hardver kako bismo, kao rudari, uradili što veći deo posla na validaciji svakog bloka i maksimalno povećali nagradu koja sledi.
Istorija rudarenja bitkoina uopšteno se može podeliti na nekoliko celina: – Era procesora (2009 – 2010) – Era grafičkih kartica (2010 – 2011) – Era FPGA kartica (2011 – 2013) – Era ASIC uređaja (2013 – 2020)
Era procesora (2009 – 2010)
Ovo je početna era rudarenja koju karateriše korišćenje procesora koji se mogu naći u bilo kom laptopu ili desktop računaru. Prvobitna Satošijeva ideja je bila da svako na mreži koristi svoj procesor za rudarenje. Na početku ove ere rudarenje je pre svega bio veoma neobičan hobi. Satoši je želeo na taj način da bolje osigura stabilnost i sigurnost mreže. Prvi bitkoini koji su bili iskopani, bili su iskopani upravo pomoću procesora. Korišćen je sličan program kao program za mrežno otključavanje Nokia telefona zbog sličnog principa korišćenja SHA-256 funkcije za enkripciju. Svako ko je želeo je mogao da rudari bitkoin uz pomoć svog laptopa ili desktop računara.
Kako se sve više rudara priključivalo na mrežu i kako je postalo moguće zameniti prve bitkoine za fiat novac, javio se interesantan problem – procesori koji su u to vreme imali bolje performanse su mogli da izrudare više bitkoina, što ujedno znači da su bili profitabilniji. Sve više rudara je koristilo procesore jačih performansi što je rezultovalo povećanjem težine kopanja. Povećanje težine kopanja je značilo da su procesori slabijih performansi postali još manje isplativi, odnosno da će dobiti proporcionalno manje bitkoina. Ljudi koji su u ovo vreme rudarili na Bitkoin mreži su mogli na mesečnom nivou da zarade i više hiljada bitkoina u zavisnosti od tipa i broja procesora koji su koristili.
Naravno, tada je cena bitkoina bila višestruko manja nego što je sada. Bez obzira na malu cenu, određeni ljudi su uvideli potencijal u rudarenju i krenuli su sa nabavkom sve boljih i boljih procesora. Cilj je bio što isplativije rudarenje bitkoina sa što manjim ulaganjima. Na ovaj način smo dobili prve rudare i potpuno funkcionalnu Bitkoin mrežu.
 AMD Phenom II procesor iz 2008. godine
AMD Phenom II procesor iz 2008. godineEra grafičkih kartica (2010 – 2011)
Kako je potražnja za bitkoinom porasla, a on dostigao cenu od 10 centi u oktobru 2010. godine, pojavili su se prvi rudari koji su koristili grafičke kartice (GPU) za rudarenje umesto procesora. Pojedinci su otkrili da je ovaj način rudarenja mnogo efikasniji od rudarenja procesorom, a vest se brzo raširila. Za relativno kratko vreme težina kopanja je toliko porasla da se uopšte nije isplatilo kopati procesorom. Računari sa dobrom diskretnom grafičkom karticom koja se može koristiti za igranje video igara su ubrzo postale mašine za zaradu nove vrste digitalnog novca.
Tada je u svetu računarstva bila popularna opcija korišćenja dve grafičke kartice za bolje performanse u video igrama i programima koji su bili veoma zahtevni (npr. video produkcija ili 3D modelovanje), tako da je već postojala potrebna infrastruktura za rudarenje sa više grafičkih kartica. Što više grafičkih kartica u računaru to je zarada bila bolja. Ubrzo su se pojavili miningrig-ovi (računari specijalizovani za rudarenje) koji su imali od 4 do 8 grafičkih kartica. U početku ovo su bile po izgledu jako amaterski sklopljene mašine, ali su kasnije poprimile poseban i donekle standardizovan oblik.
 Primer izgleda prvih mining rig-ova
Primer izgleda prvih mining rig-ovaEra FPGA kartica (2011 – 2013)
FPGA je skraćeno od field-programmable gate array. Konkretan hardver je dizajniran tako da korisnik može naknadno da ga prilagodi za određeni zadatak. Karakteristika ovih uređaja je brzo izvršavanje konkretne vrste zadataka koje može biti i do dva puta efikasnije od izvršavanja istog zadatka pomoću grafičke kartice. Ovaj potencijal zaintrigirao je rudare tog doba i sredinom 2011. godine otpočelo je korišćenje ovog hardvera za potrebe rudarenja. Obzirom na to da FPGA uređaji nisu toliko jednostavni za korišćenje za razliku od grafičkih kartica i procesora, u početku nije bilo puno ljudi koji su rudarili pomoću ovih uređaja. Kako je softver za rudarenje uz pomoć FPGA uređaja postajao sve dostupniji, rastao je i broj ljudi koji su na ovaj način zarađivali svoje bitkoine.
Naravno, velika efikasnost ovih uređaja i činjenica da daju dva puta bolje rezultate od grafičkih kartica samo je dodatno doprinela povećanju težine kopanja bitkoina, ali nisu FPGA uređaji doveli do toga da GPU rudarenje postane istorija rudarenja bitkoina. Do toga su doveli ASIC uređaji koji su stupili na scenu 2013. godine.
 FPGA uređaj
FPGA uređajEra ASIC uređaja (2013 – 2020)
ASIC uređaji su se prvi put pojavili 2013. godine i potpuno su preuzeli scenu rudarenja. Naime, ASIC je skraćeno od application-specific integrated circuit što znači da su ASIC uređaji posebno pravljeni za rešavanje jedne vrste zadatka. Mana ovog pristupa je to što se ASIC uređaji ne mogu koristiti ni za šta drugo osim za rudarenje uz pomoć određenog algoritma. Prednosti ovih uređaja su višestruko bolje performanse i veoma laka instalacija. Nije bilo potrebno razumeti se u hardver za korišćenje ASIC uređaja. Rudari bi samo naručili ove mašine i uključili ih. Odjednom svako je mogao da rudari na Bitkoin mreži uz minimalan trud. To je rezultiralo povećanjem težine kopanja do te mere da su svi prethodno navedeni načini rudarenja postali (skoro) potpuno neisplativi za kopanje bitkoina.
Istorija rudarenja bitkoina pamti nekoliko firmi koje su se bavile prozvodnjom ASIC uređaja među kojima je i današnji gigant Bitmain. Trka za najboljim ASIC uređajem je dovela do gašenja velikog broja firmi jer su samo firme sa kompetentim proizvodom mogle da opstanu na tržištu. Što je veći broj određenog modela bio proizveden, to su troškovi njegove proizvodnje bili manji, tako da manje firme nisu imale puno šanse da opstanu kao ozbiljni konkurenti u ponudi uređaja rudarima.
Prvi ASIC-i su bili u obliku USB uređaja. Bili su bez ventilatora, bez buke i uz minimalnu potrošnju struje. Rudari su ubrzo krenuli da prave prve farme za rudarenje uz pomoć ovih malih uređaja – nekoliko desetina njih povezanih na isti računar uz pomoć USB hub-ova davali su maksimalne performanse. Sa porastom težine kopanja, sve bolji i bolji ASIC-i su zauzimali svoja mesta u garažama i skladištima rudara dok su stari bili prodavani po znatno manjim cenama.
 Prve ASIC farme
Prve ASIC farmeASIC uređaji su se razvijali kako je potreba za sve jačim mašinama rasla. Ova era i dalje traje, a ASIC uređaji danas pružaju nekoliko hiljada puta bolje performanse od prvih procesora koji su bili korišćeni 2009. godine. Nove generacije ASIC-a su uvek veoma isplative, ali treba uzeti u obzir i veoma veliku cenu novih ASIC uređaja kao i činjenicu da novi modeli izlaze na svakih nekoliko meseci što smanjuje profitabilnost starih modela.
 Izgled današnjeg ASIC uređaja
Izgled današnjeg ASIC uređajaOvi uređaji će ostati dominantni na sceni Bitkoin rudarenja i nema naznaka da će se to promeniti u skorije vreme. U sledećem blogu o rudarenju bitkoina i kriptovaluta uopšte ćemo proći kroz način(e) za postavljanje rig-a za rudarenje i trenutno dostupne opcije na domaćem tržištu. Takođe ćemo pokriti određene modele i procene profitabilnosti rudarenja bitkoina u 2020-oj godini.
-
 @ 8173f6e1:e488ac0f
2025-05-11 20:54:58
@ 8173f6e1:e488ac0f
2025-05-11 20:54:58testnotebin7testnotebin7testnotebin7testnotebin7
-
 @ 8173f6e1:e488ac0f
2025-05-11 20:50:24
@ 8173f6e1:e488ac0f
2025-05-11 20:50:24testnotebin123456testnotebin123456testnotebin123456testnotebin123456




